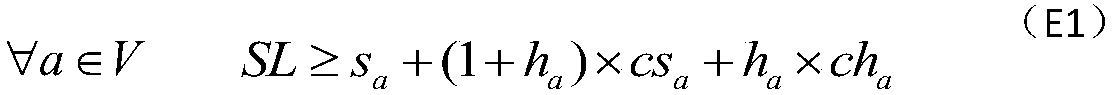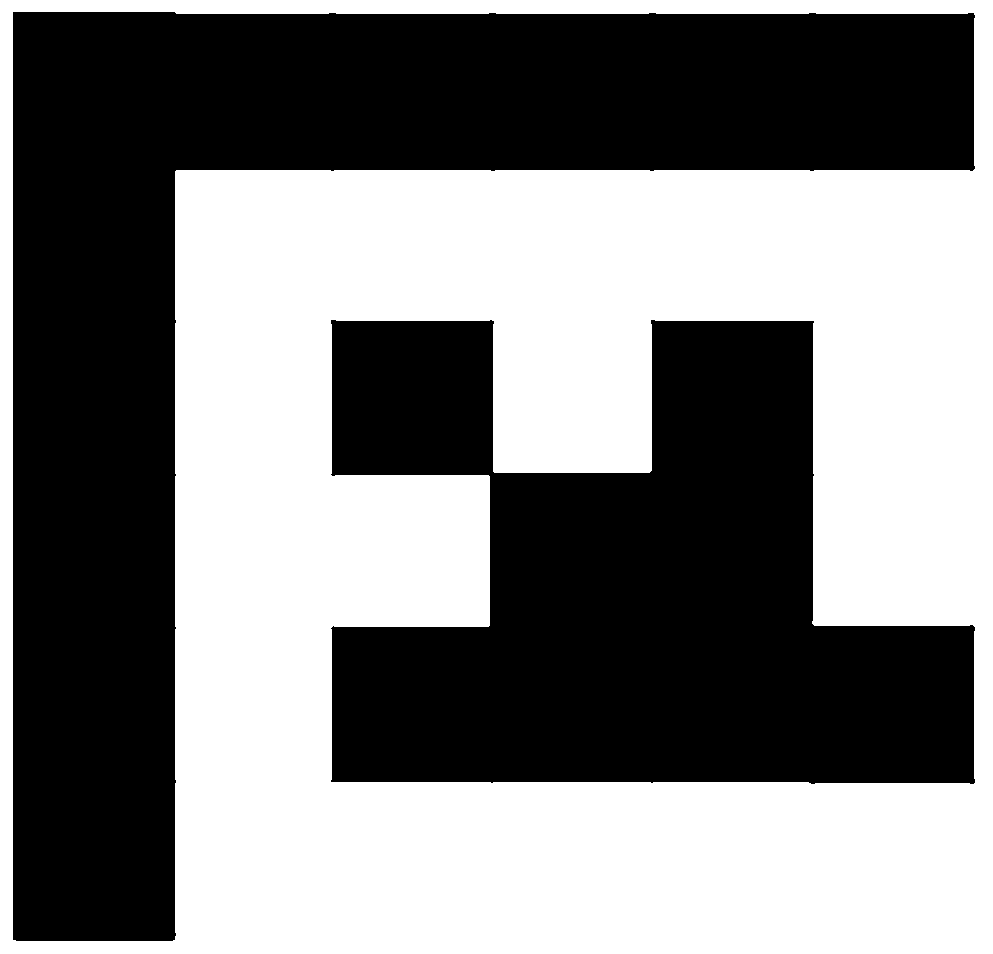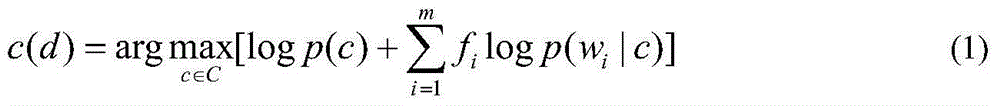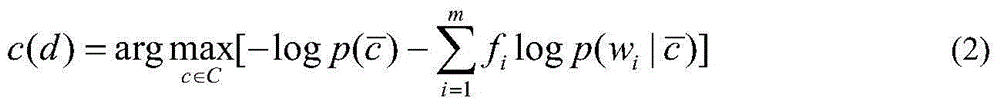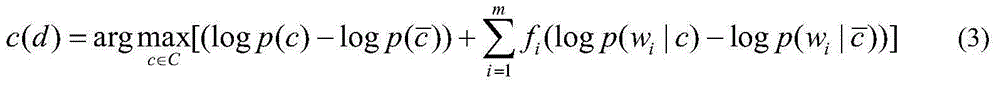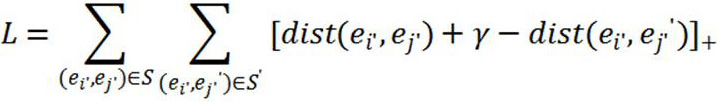Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
176 results about "Temporal complexity" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Temporal Complexity involves the bounds on the time it takes for a given Turing Machine to compute its input. Spatial Complexity involves the bounds on the amount of space a Turing Machine requires to compute its input, where space is crudely understood as the length of the Turing Machine's tape.
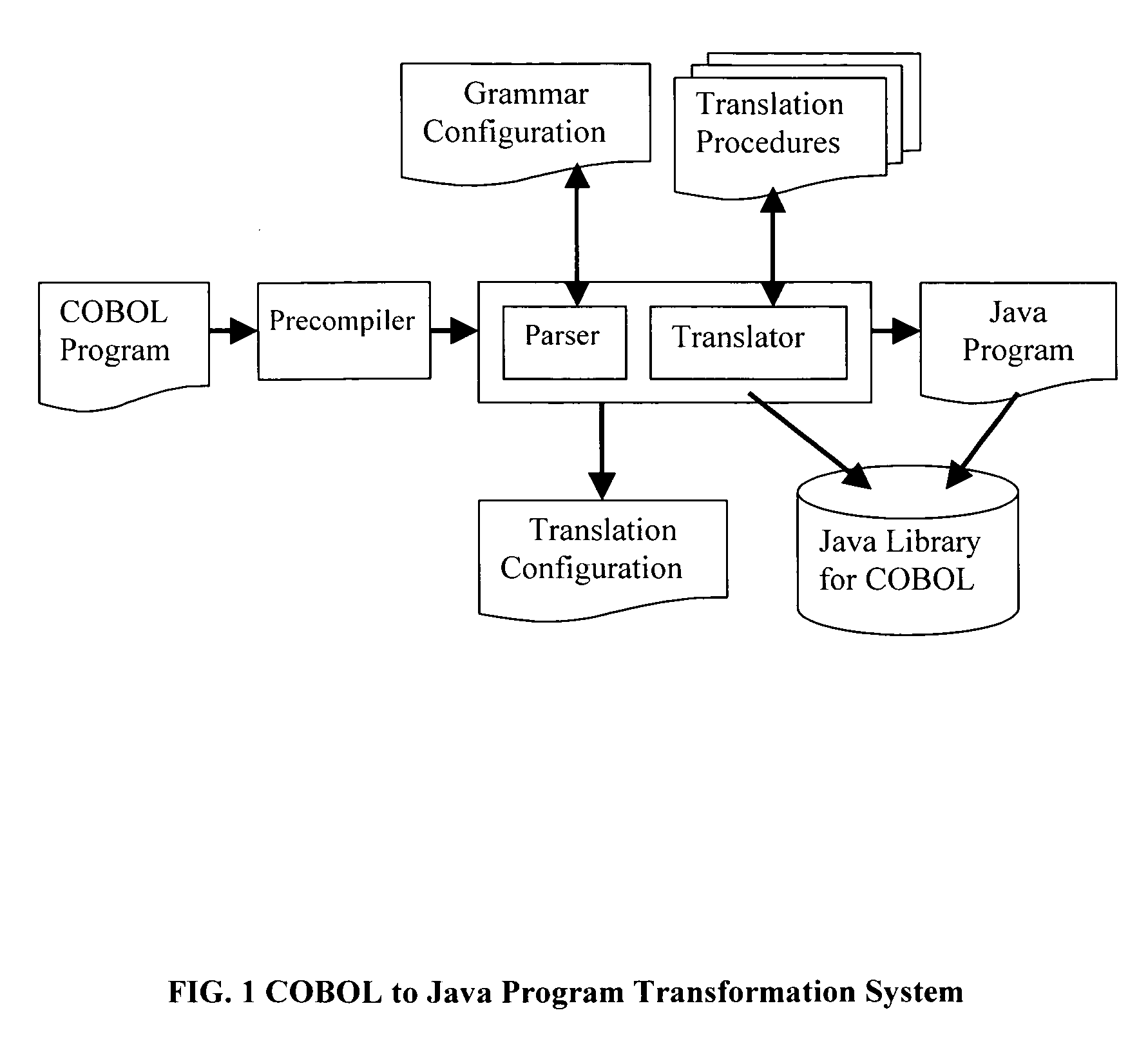
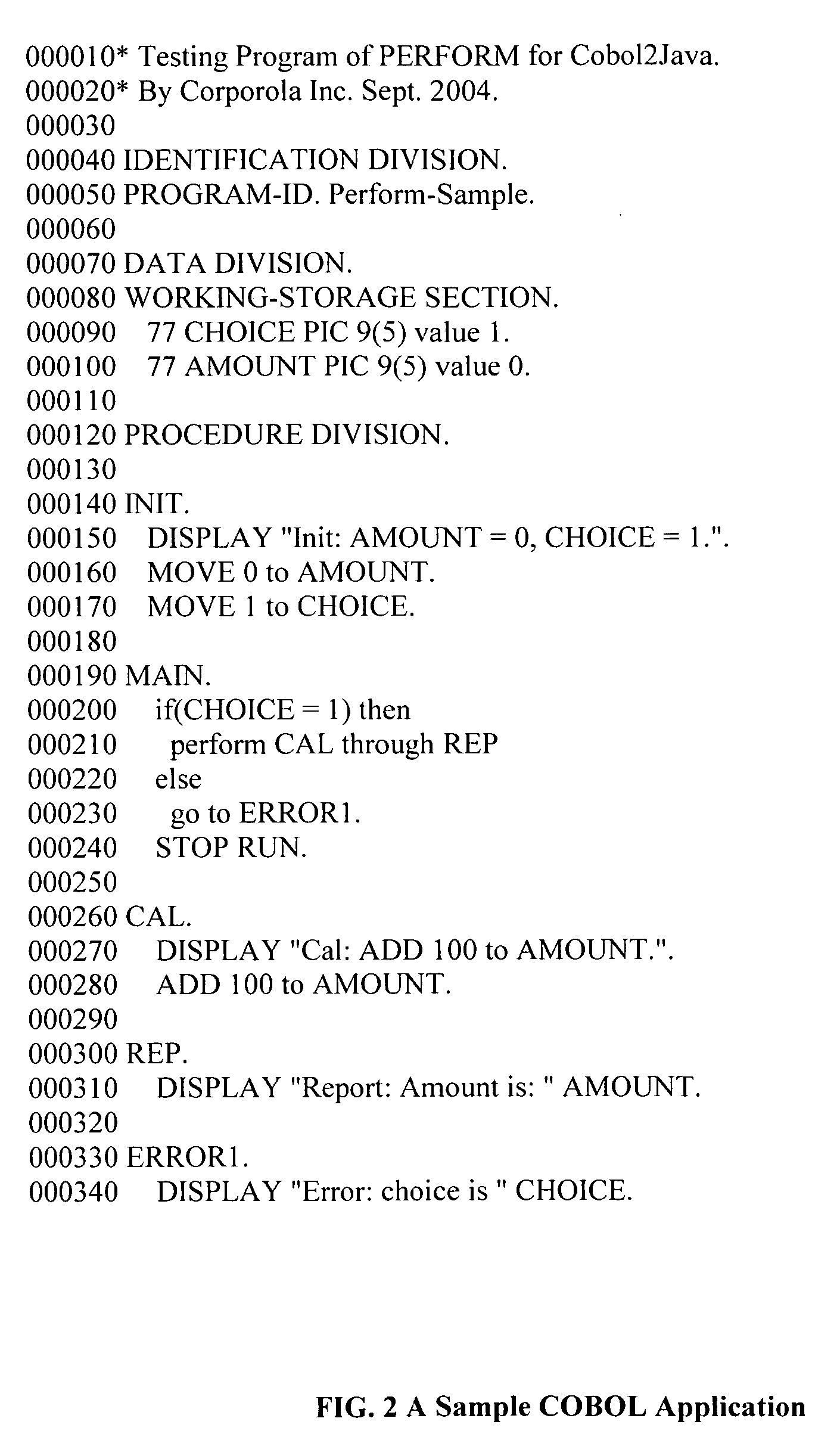
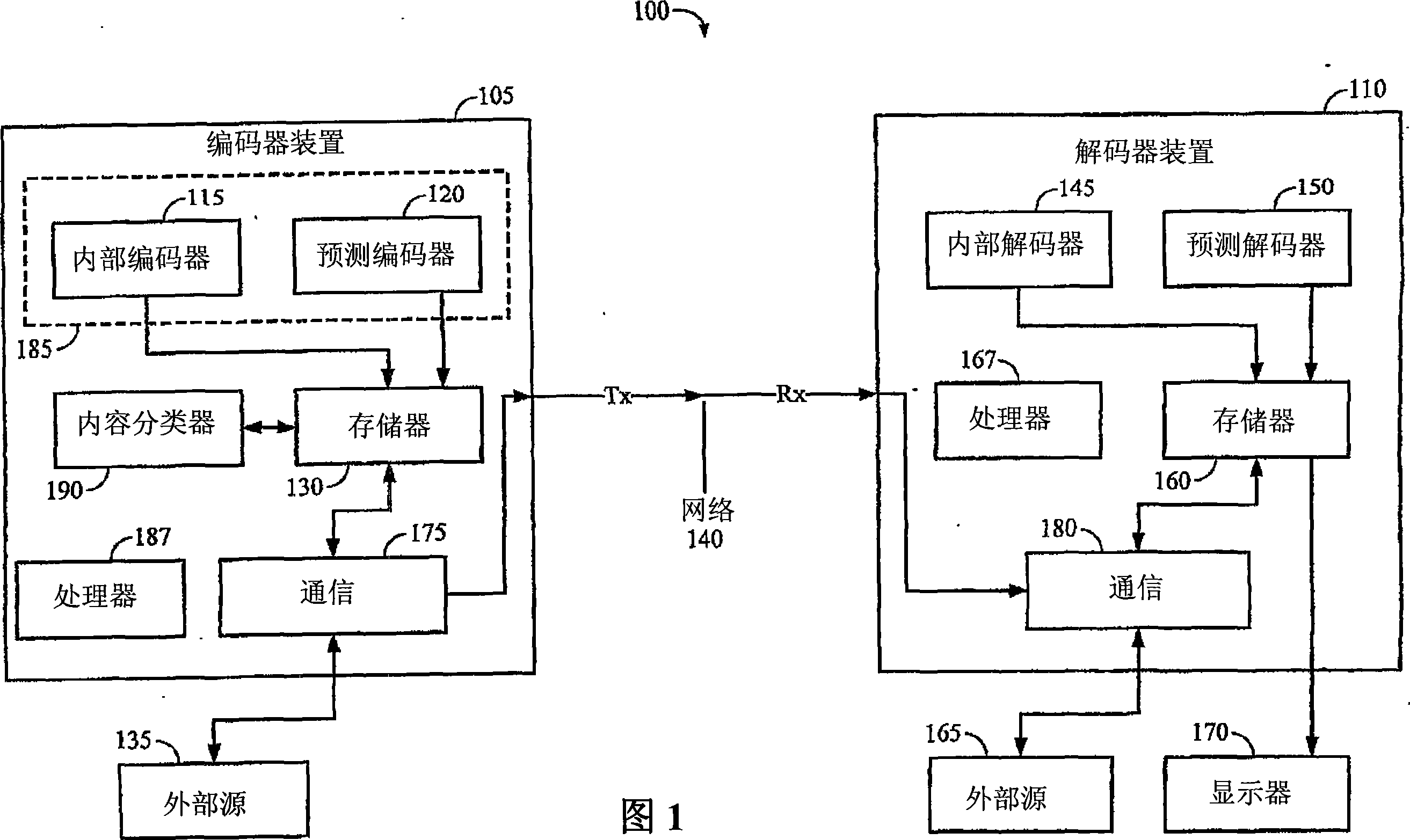
Method for program transformation and apparatus for COBOL to Java program transformation
InactiveUS20060031820A1Maintain maintainabilityImprove maintainabilityProgram controlMemory systemsTime complexityGoto
The present invention relates to a method for program transformation and an apparatus for COBOL to Java program transformation. The method consists of: (1) a new approach for statement-to-statement program transformation, facilitated by a predefined target language library, which keeps original comments, program control flow, functionality, and time complexity; (2) a new approach for goto statement elimination, which uses existing exception handling mechanism in target language and its implementation is hidden in a super class in a library; (3) a new extended BNF to distinguish different occurrences of the same term in a BNF production; (4) a new approach for embedded statement as a special marker statement and a comment, (5) in the description of the above, a program transformation specification language is defined to describe relationship between comments in two languages. (6) an apparatus, as the preferred embodiment of the method, is a COBOL to Java program transformation system Cobol2Java; a sample COBOL application and its Cobol2Java translation are given.
Owner:LI AIZHONG
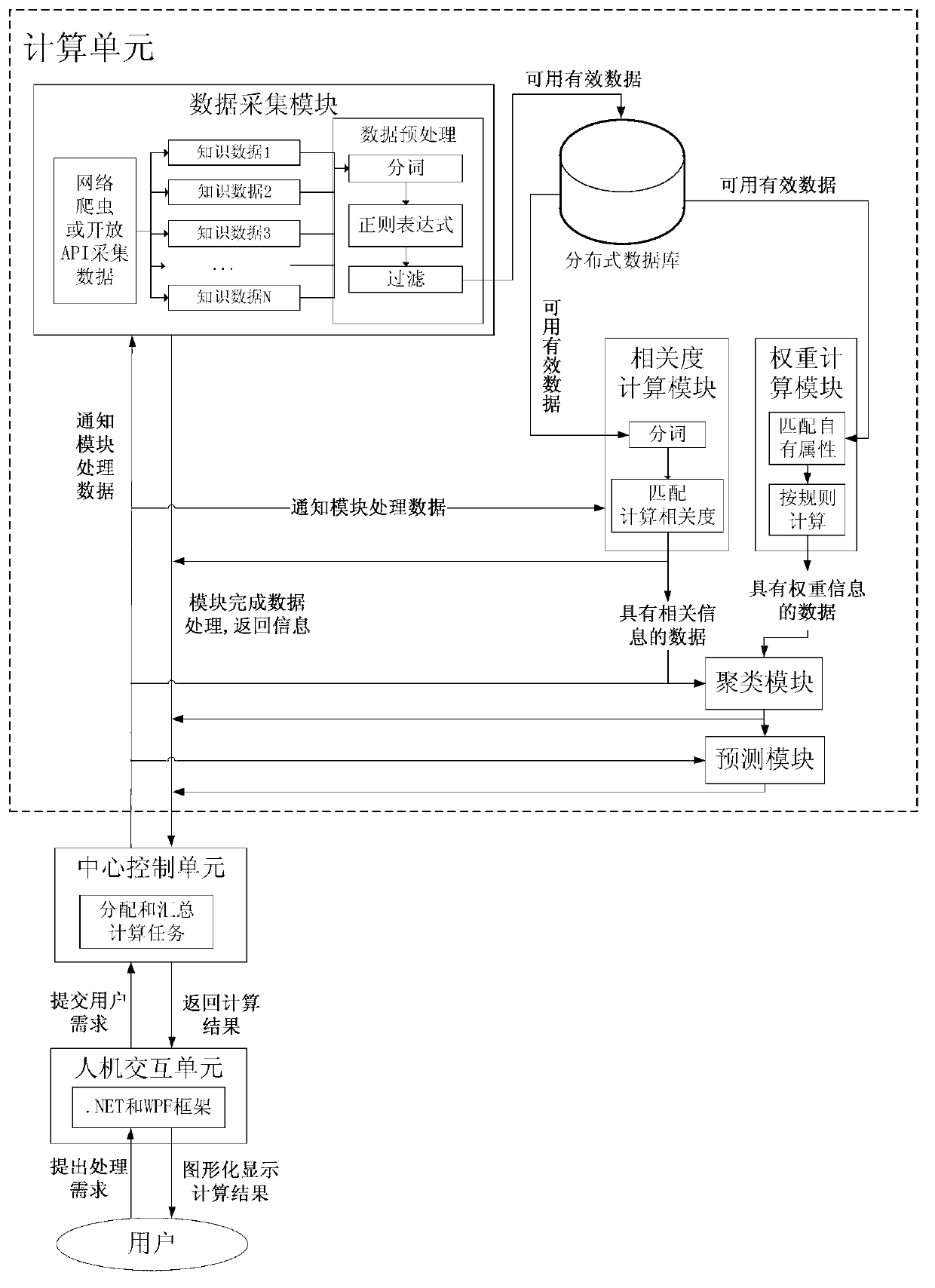
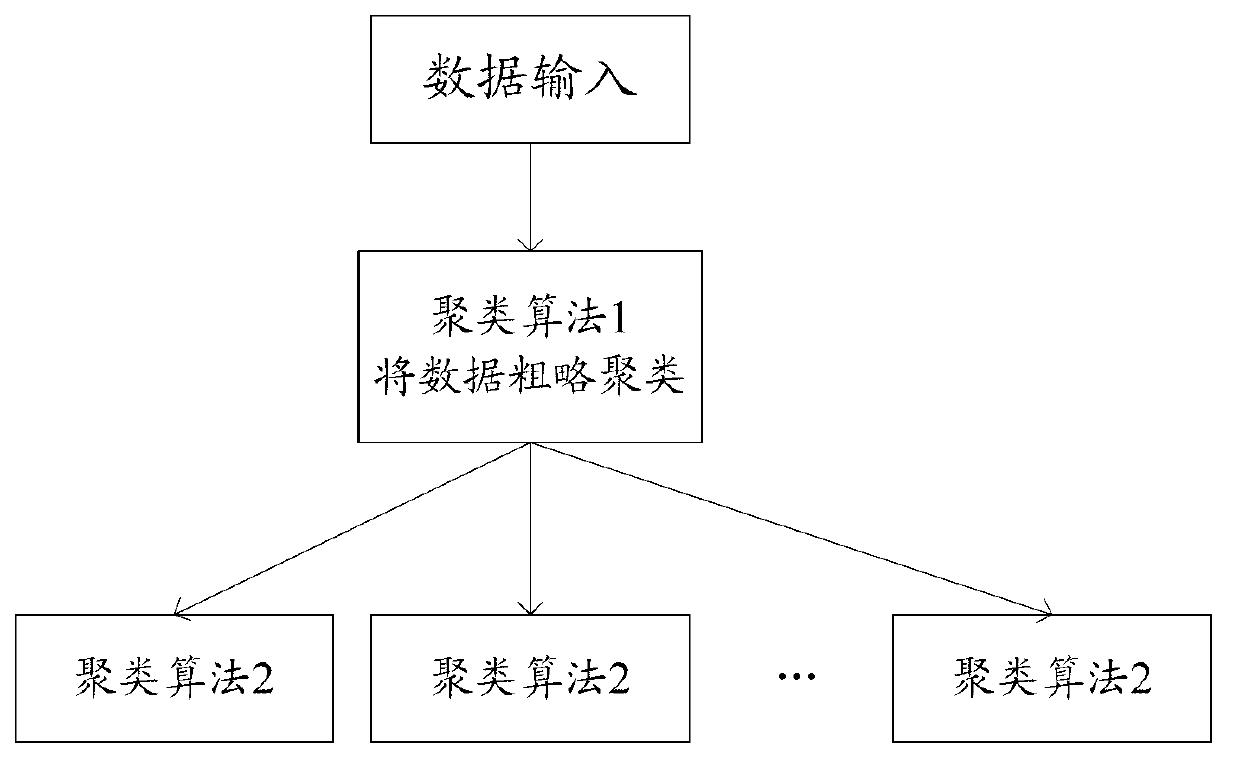
Distributed knowledge data mining device and mining method used for complex network
InactiveCN103136337AReduce time complexityThe result is accurateSpecial data processing applicationsCluster algorithmData dredging
The invention discloses a distributed knowledge data mining device and method used for a complex network. The distributed knowledge data mining device adopts a distributed computing platform which is composed of a control unit, a computing unit and a man-machine interaction unit, wherein the innovation key is to finish the calculated amount needed by a multifarious clustering algorithm in the data mining by different servers so as to improve the efficiency of the data mining. Aiming at different knowledge data, the degrees of relation and the weights of knowledge data also can be computed by applying different standards, so that a more credible result is obtained. A second-level clustering mode is adopted in the knowledge data mining process; the result of the first-level clustering is relatively rough, but the computing complexity is very low; and the computing complexity of the second-level clustering is relatively high, but the result is more precise. By combining the first-level clustering with the second-level clustering efficiently, the distributed knowledge data mining device improves the time complexity and clustering precision greatly in comparison with the traditional first-level clustering mode. According to the invention, as a visual and direct exhibition network structure and a dynamic evolutionary process are adopted, references are provided for the prediction in the fields of disciplinary development and hotspot research.
Owner:BEIJING UNIV OF POSTS & TELECOMM
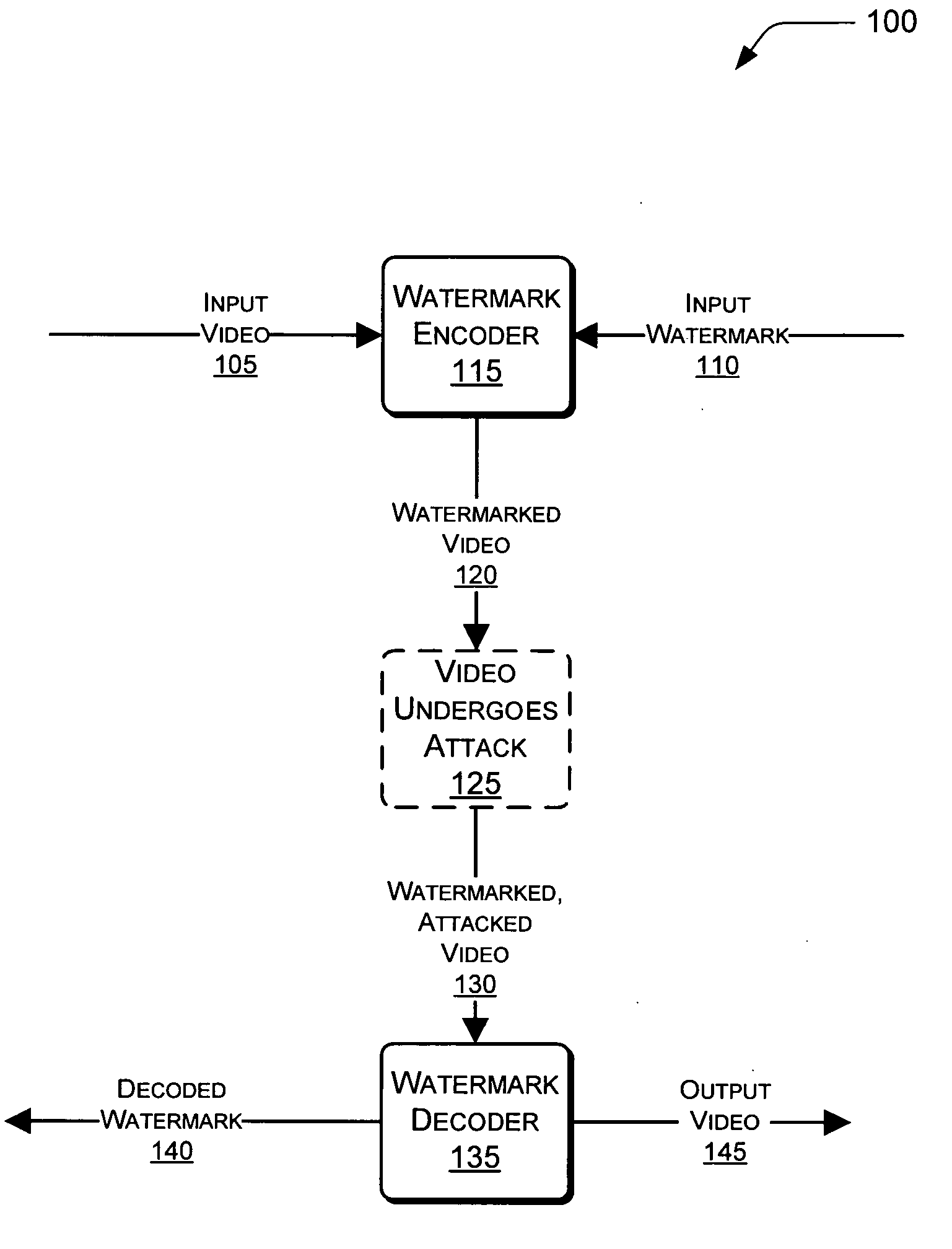
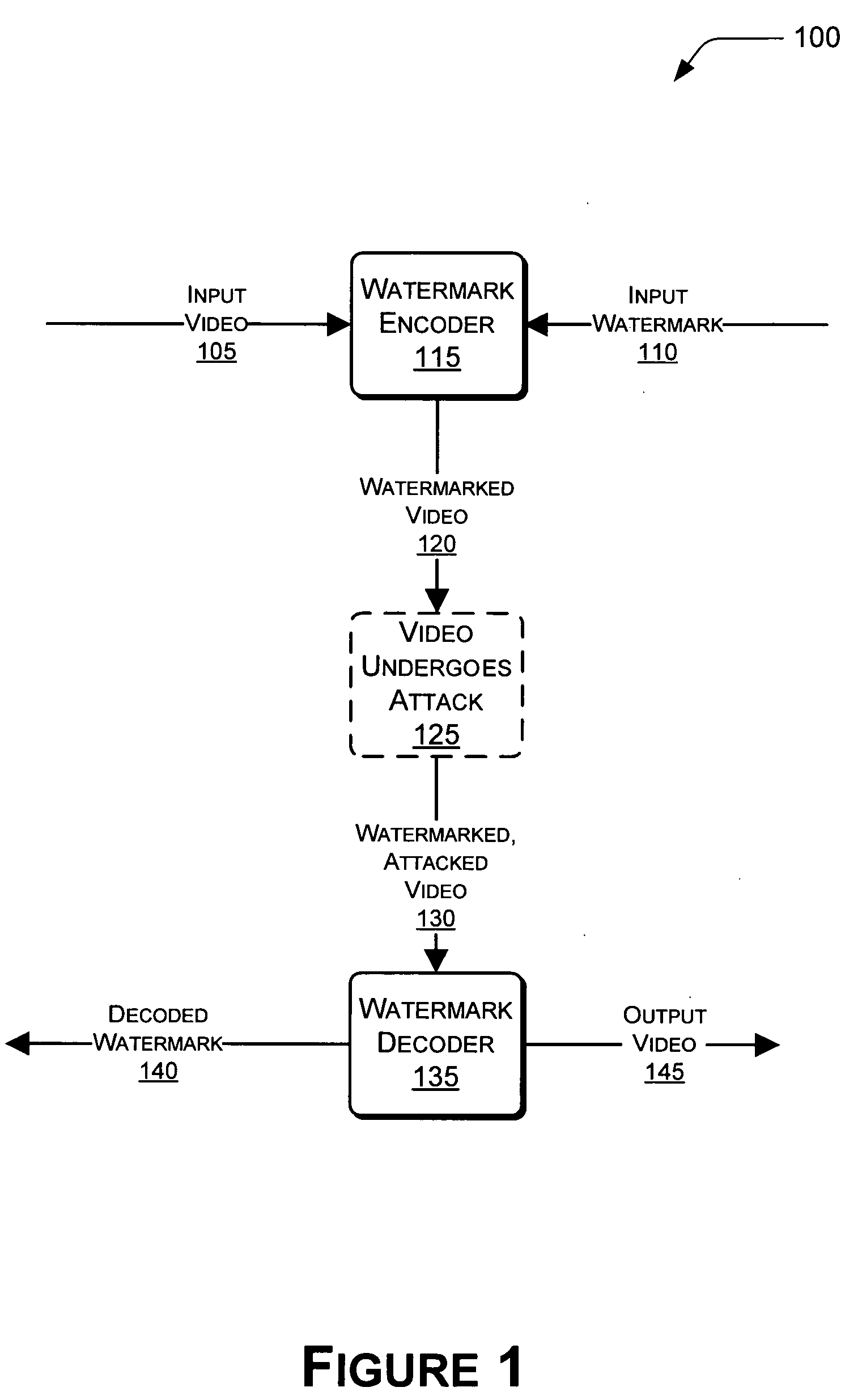
Video fingerprinting using watermarks
InactiveUS20070092103A1Well formedCharacter and pattern recognitionTelevision systemsComputer visionComputer science
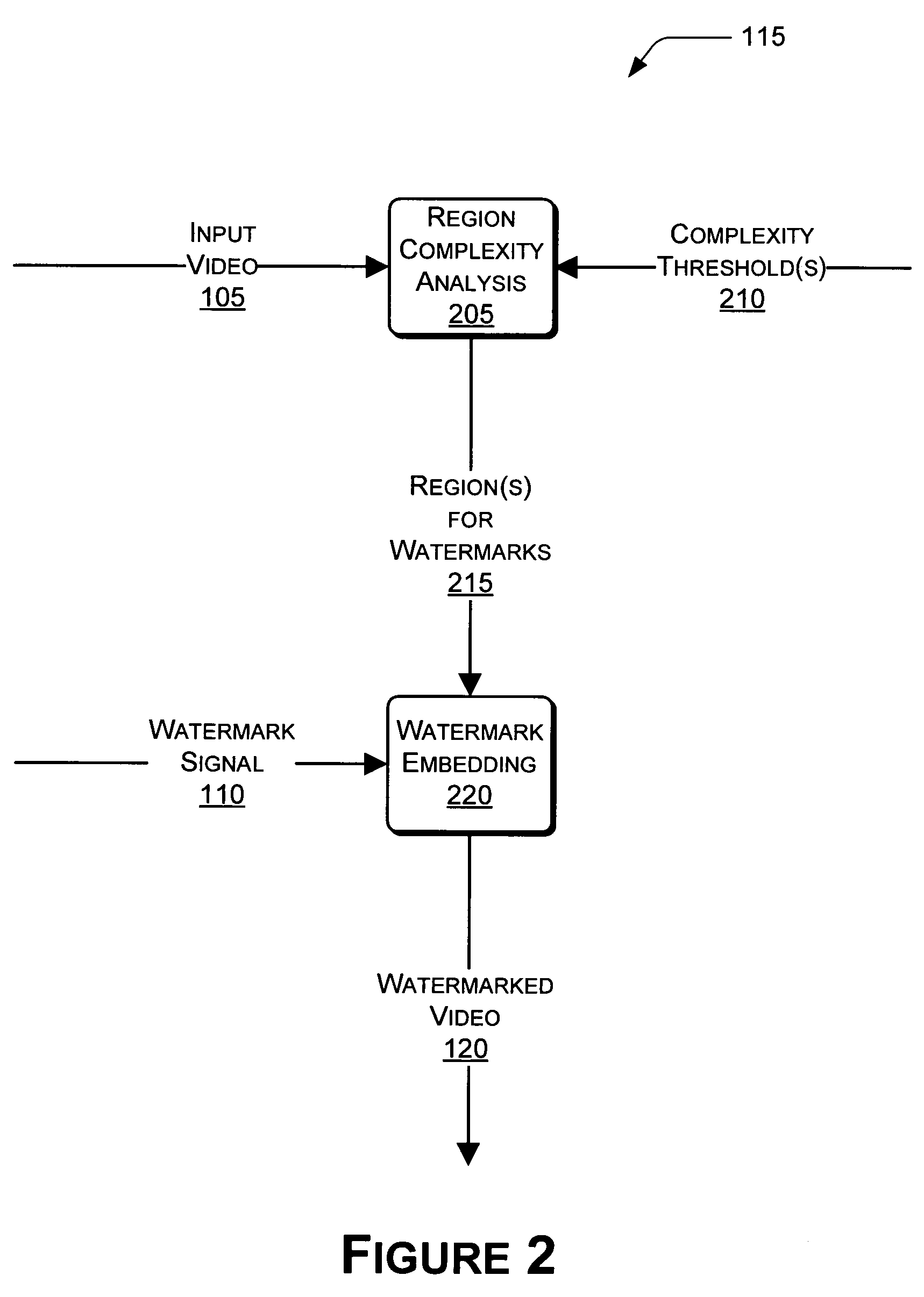
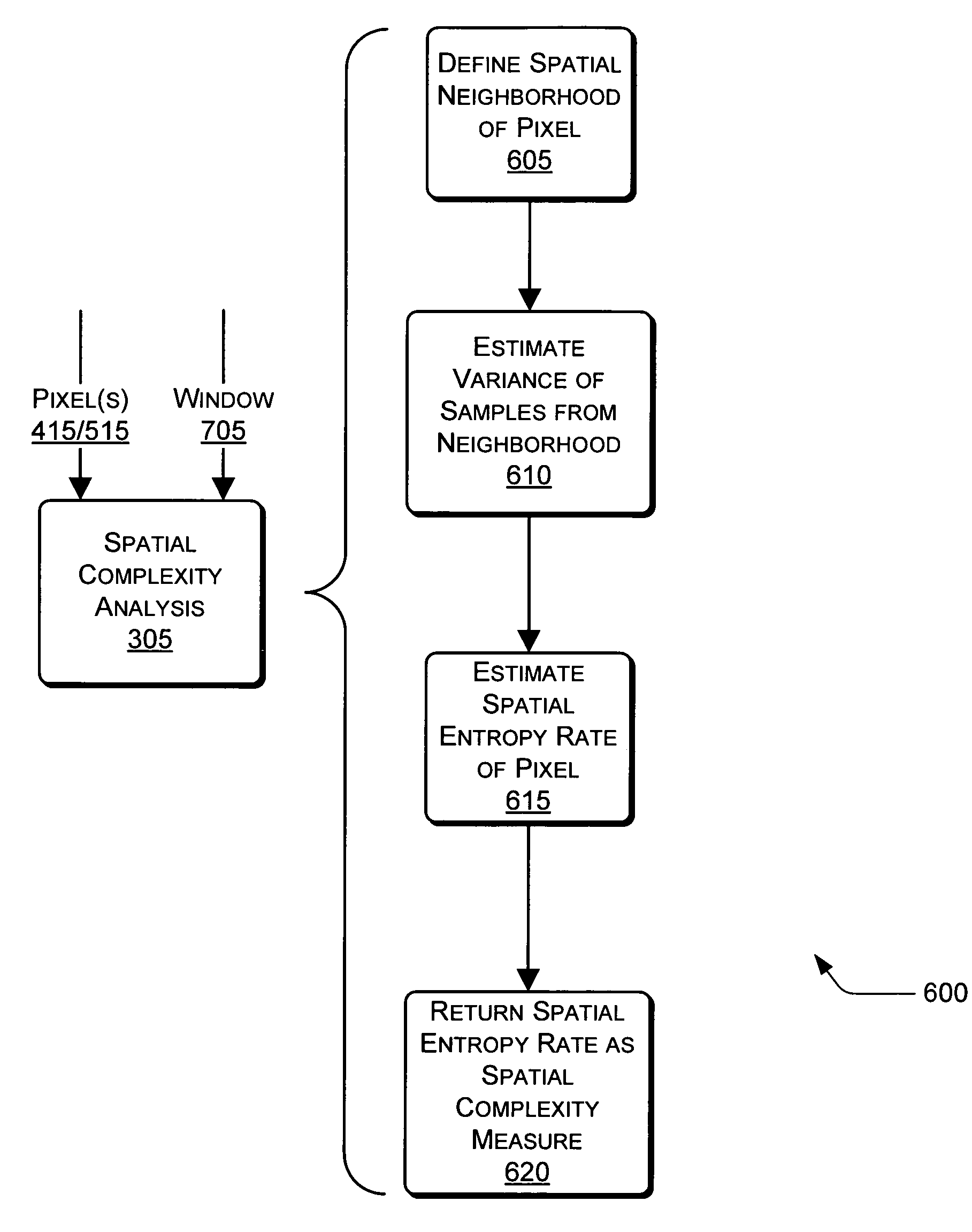
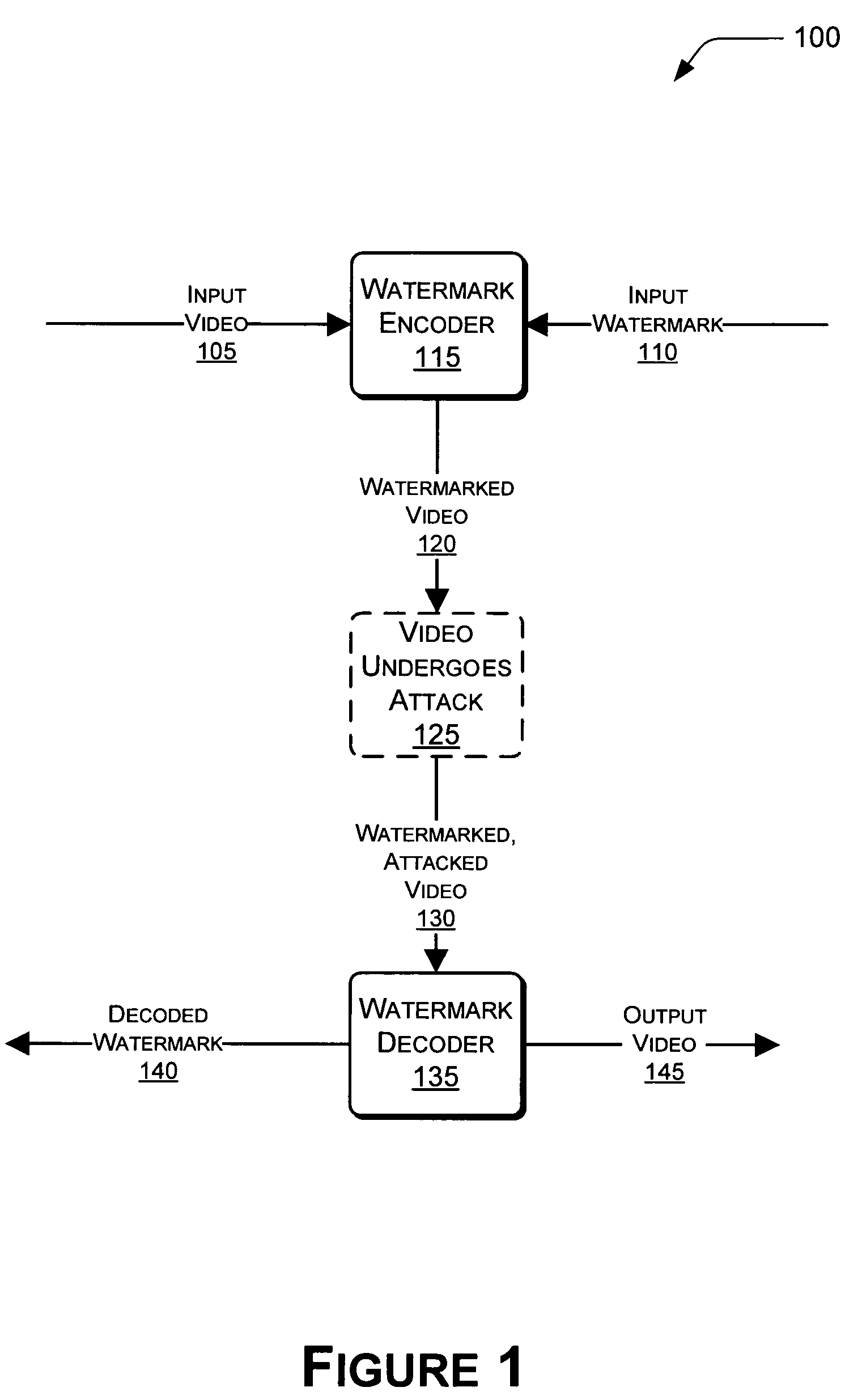
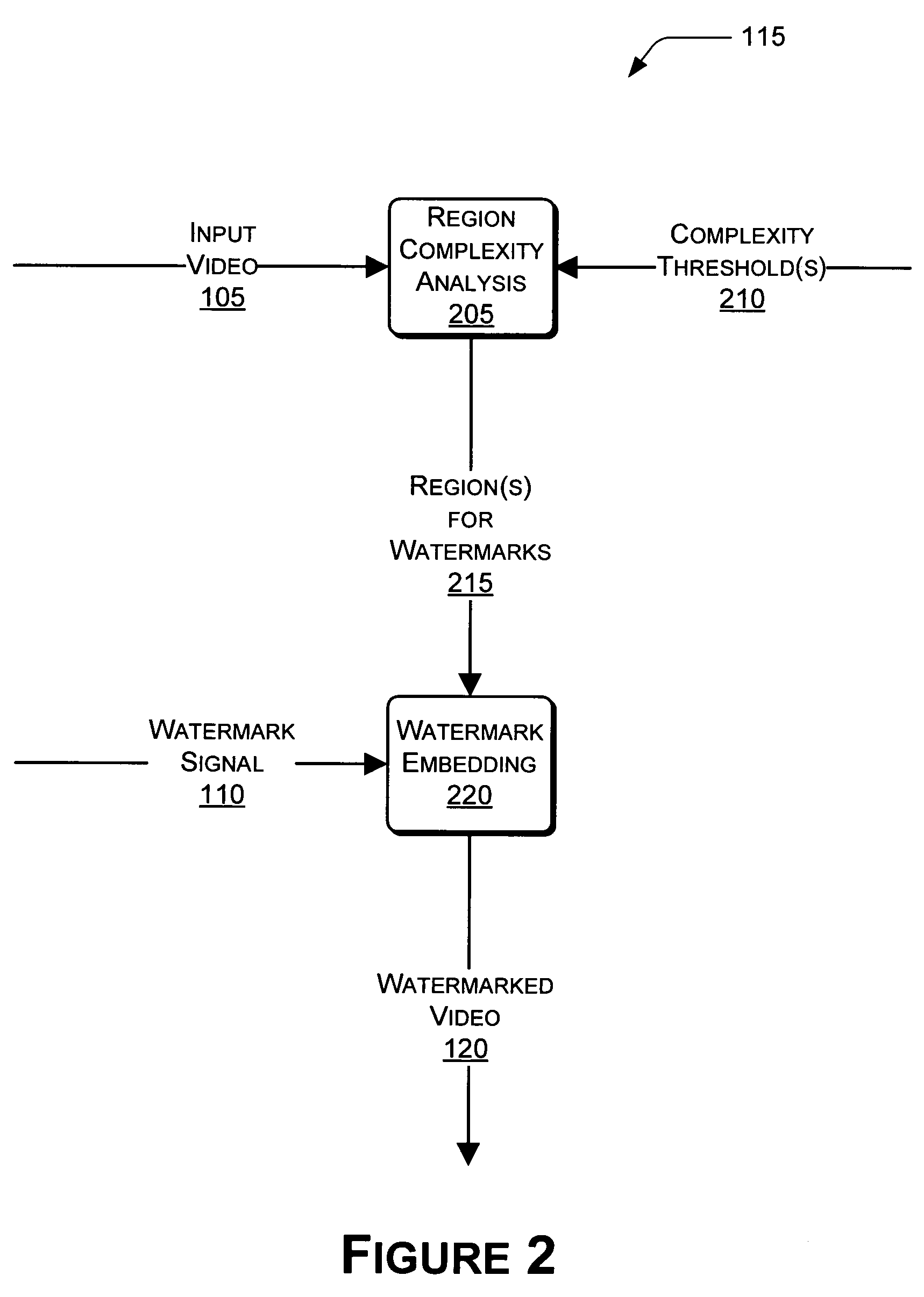
Video fingerprinting using watermarks is described herein. A watermark encoder embeds a watermark into an input video to produce a watermarked video. The watermark encoder can choose particular regions of the video that are sufficiently complex for watermarking. Spatial and temporal complexity analyses can be performed on a per-pixel basis to locate suitable regions of the video. The watermarks can be embedded using a unique codeword associated with a given user. A watermark decoder can receive the watermarked video. In some instances, the watermarked video may have been attacked in some way after being output by the watermark encoder. In these instances, the watermark decoder can extract the watermark from the watermarked video. In turn, the watermark decoder can extract the codeword from the watermark, and compare the extracted codeword to a plurality of known codewords associated with respective users.
Owner:MICROSOFT TECH LICENSING LLC
Video fingerprinting using complexity-regularized video watermarking by statistics quantization
InactiveUS7702127B2Character and pattern recognitionTelevision systemsComputer visionComputer science
Video fingerprinting using watermarks is described herein. A watermark encoder embeds a watermark into an input video to produce a watermarked video. The watermark encoder can choose particular regions of the video that are sufficiently complex for watermarking. Spatial and temporal complexity analyses can be performed on a per-pixel basis to locate suitable regions of the video. The watermarks can be embedded using a unique codeword associated with a given user. A watermark decoder can receive the watermarked video. In some instances, the watermarked video may have been attacked in some way after being output by the watermark encoder. In these instances, the watermark decoder can extract the watermark from the watermarked video. In turn, the watermark decoder can extract the codeword from the watermark, and compare the extracted codeword to a plurality of known codewords associated with respective users.
Owner:MICROSOFT TECH LICENSING LLC
Single pass variable bit rate control strategy and encoder for processing a video frame of a sequence of video frames
InactiveUS20060062292A1Easy to compressQuality improvementColor television with pulse code modulationColor television with bandwidth reductionPattern recognitionVariable bit rate vbr
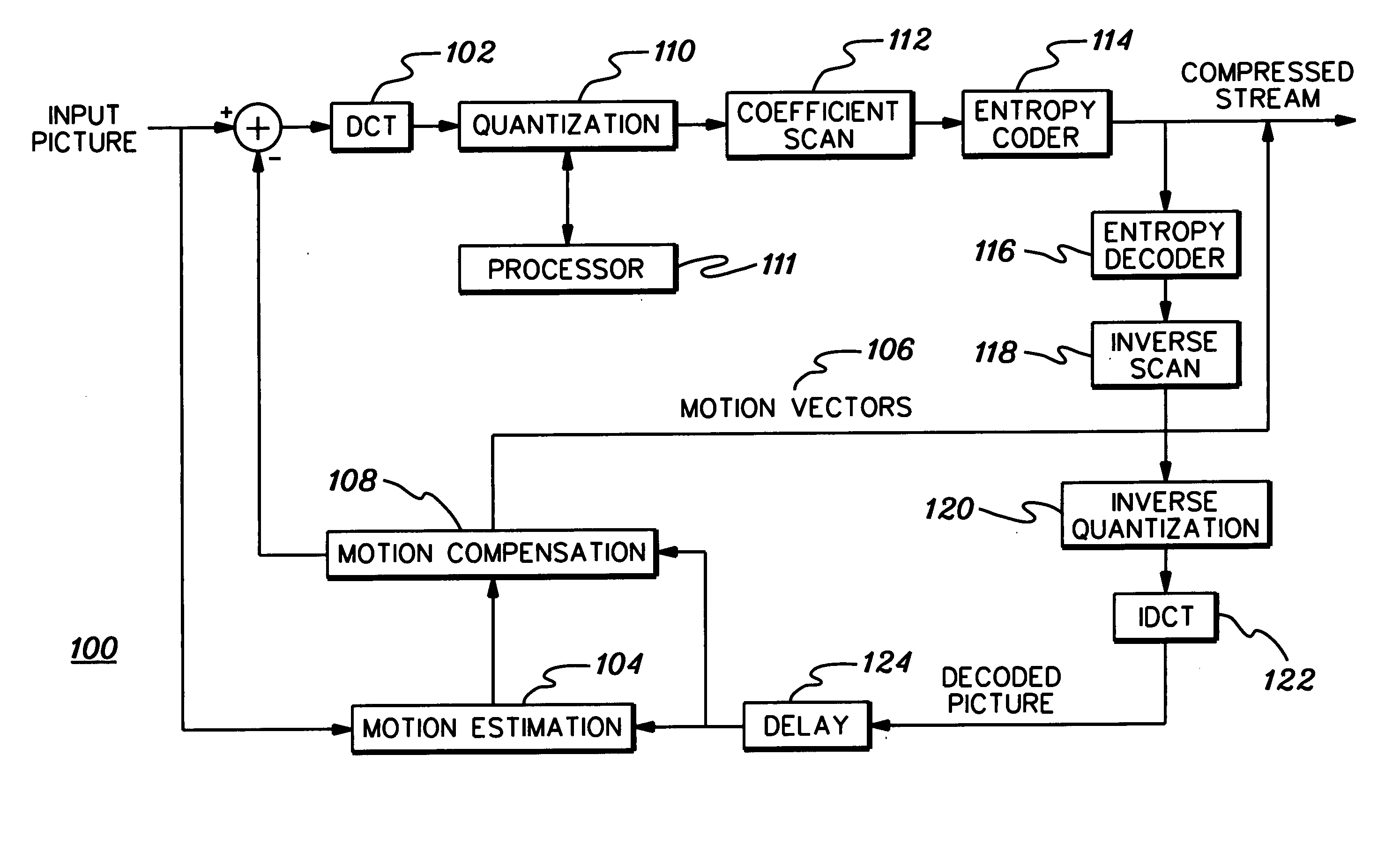
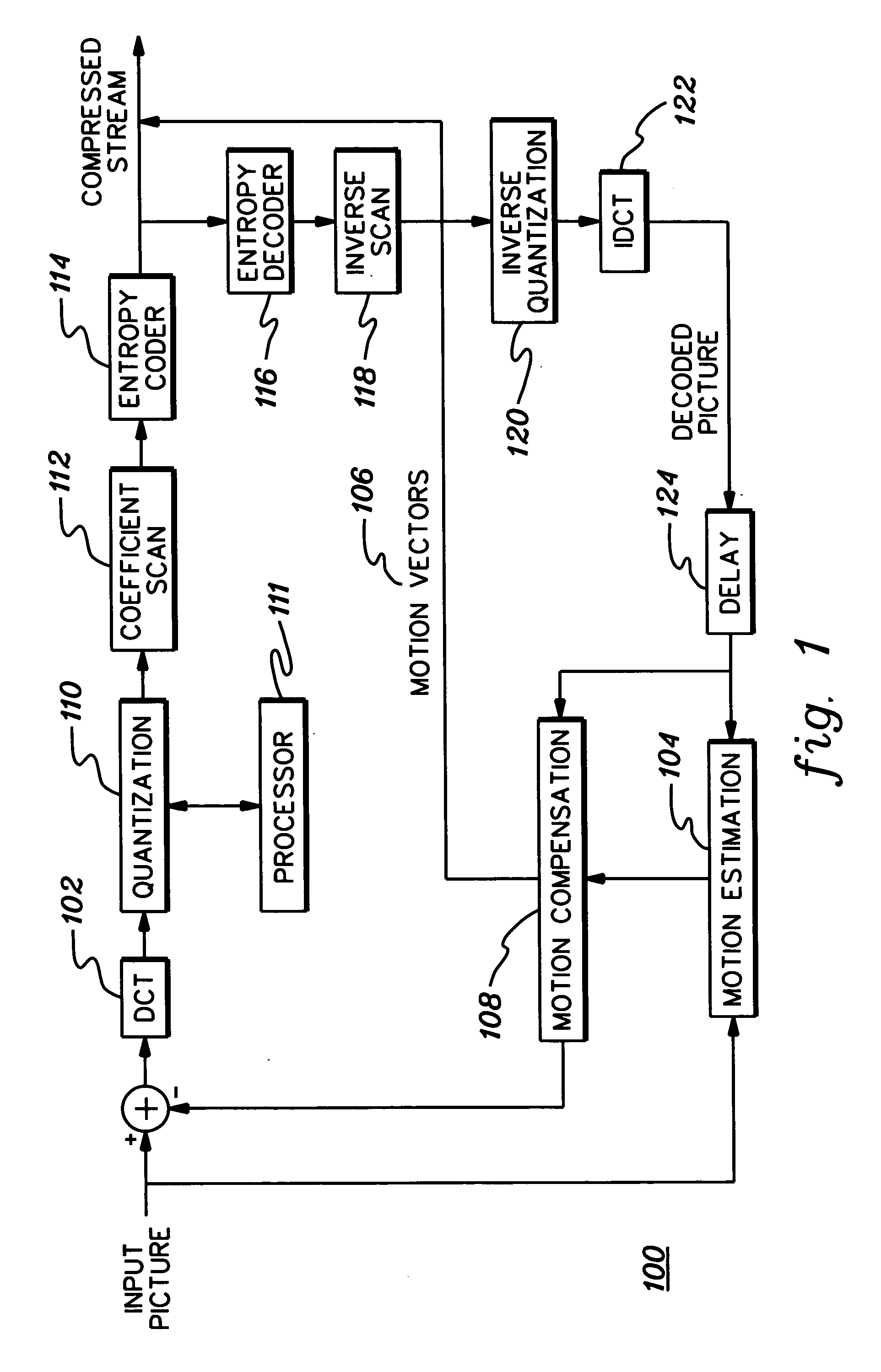
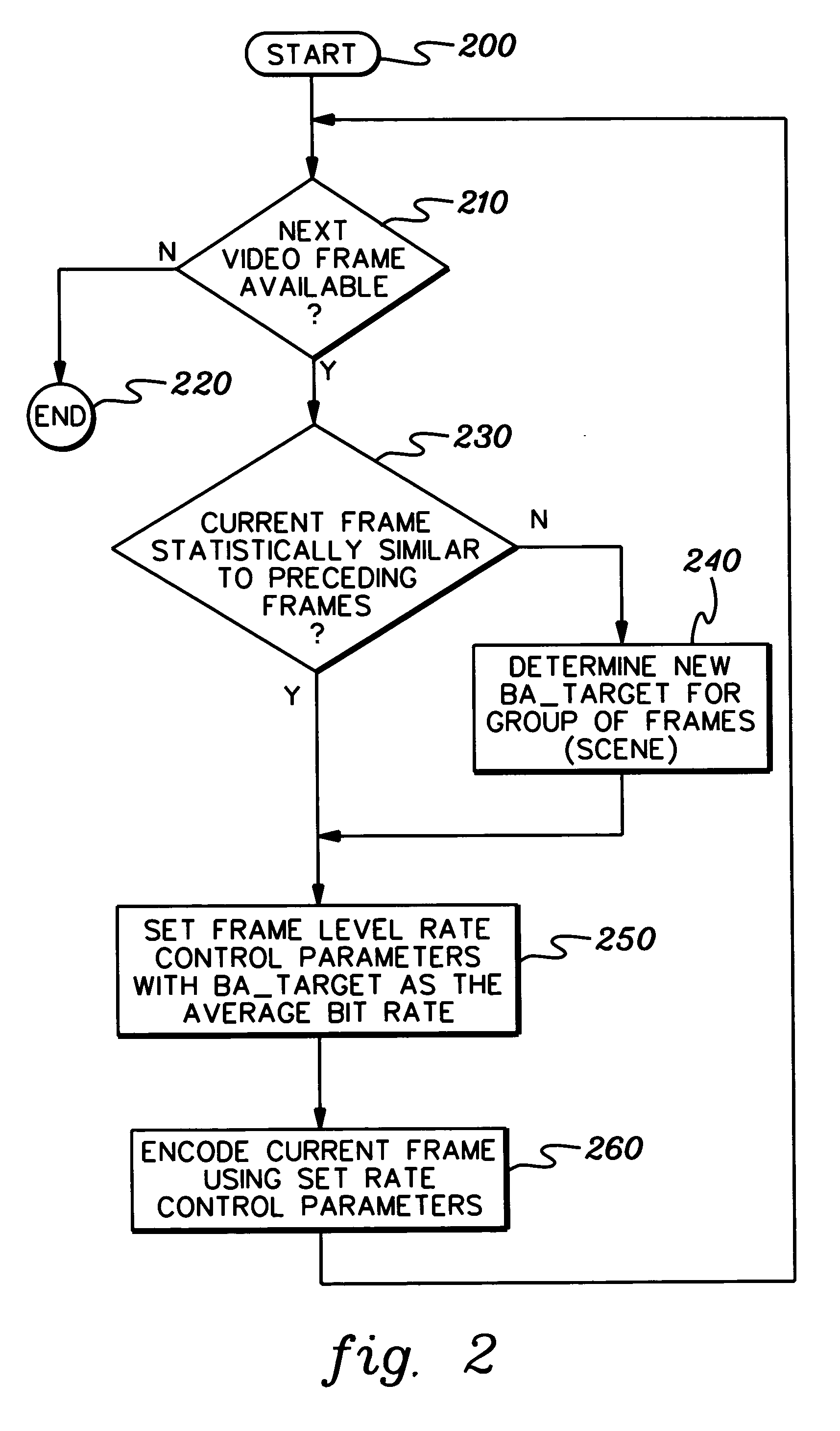
An encode control strategy is provided for variable bit rate encoding of a sequence of video frames in a single pass. The control strategy includes determining whether a video frame has a complexity level statistically outside a defined range from a complexity level of at least one preceding frame of the sequence of video frames, and if so, determining a new average bit rate target for the video frame. The new average bit rate for the video frame is determined employing at least one of spatial complexity and temporal complexity of the video frame. The new average bit rate target for the video frame is used to set frame level bit rate control parameter(s), and the video frame is encoded using the set frame level bit rate control parameter(s).
Owner:GLOBALFOUNDRIES INC
Method of adaptively encoding and decoding motion image and apparatus therefor
InactiveUS7457471B2Improve efficiencyImprove storage efficiencyTelevision system detailsPulse modulation television signal transmissionSelf adaptiveImaging data
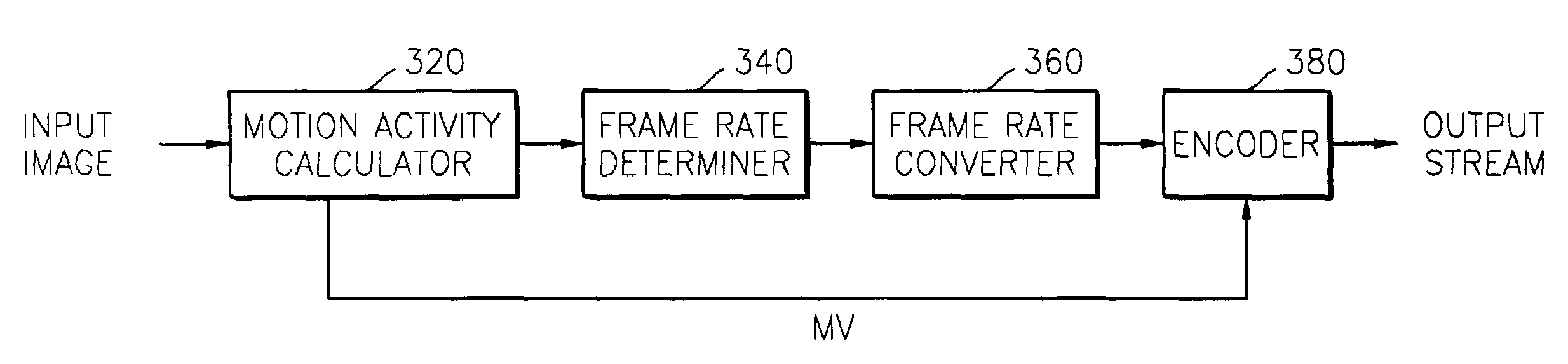
In a method of adaptively encoding input image data of a motion image in accordance with a temporal complexity of the motion image, and an apparatus therefore, the temporal complexity of the input image data is calculated. Next, an original frame rate of the input image data is converted into a converted frame rate based on the calculated temporal complexity. Thereafter, the input image data whose frame rate has been converted is encoded, and the encoding data of the encoded image data is controlled so that the encoded image data has information on the converted frame rate. Accordingly, the input image data is encoded at different frame rates in accordance with the temporal complexity of the input image data. Consequently, the encoded input image data is efficiently stored.
Owner:SAMSUNG ELECTRONICS CO LTD
Method and apparatus for determining encoding mode based on temporal and spatial complexity
ActiveCN101926178AProcessing speedReduce computational complexityTelevision systemsDigital video signal modificationComputation complexityRound complexity
The present invention relates to a method and an apparatus for determining an encoding mode based on temporal and spatial complexity. The encoding-mode-determining apparatus based on temporal complexity is characterized in that it comprises: a temporal complexity calculation unit which calculates the temporal complexity of a macro block; and a mode determining unit which determines the encoding mode based on temporal complexity. The temporal complexity and the spatial complexity of a macroblock can be calculated with higher accuracy, and additionally the optimal encoding mode can be selected based on the calculated complexity. Accordingly, the complexity of the calculation involved in rate-distortion optimization can be reduced and the processing speed can be increased.
Owner:SK PLANET CO LTD
Method for carrying out compression storage on adjacent matrixes of sparse directed graph
The invention discloses a method for carrying out compression storage on adjacent matrixes of a sparse directed graph. The method comprises the steps of carrying out compression storage on the adjacent matrixes of the sparse directed graph by using a triple table; recording the positions of the first effective data of each row in the adjacent matrixes in the triple table to realize application algorithms of a part of related graphs. For the compression storage on the adjacent matrixes of the sparse directed graph, only the row number, the column number and the element value of each effective element in the adjacent matrixes are stored, in certain algorithms, a small space is required to store the number of effective elements of each row in the adjacent matrixes and the subscript of the first effective element of each row in the triple table. According to the method, on one hand, the advantages of the adjacent matrix representation method of the graph are kept, and on other hand, the problems of space waste when the sparse graph is represented by the adjacent matrixes are solved, the operation is simplified in certain algorithms, the time complexity of the algorithm based on the adjacent matrixes is reduced, and the software performance is effectively improved.
Owner:XI'AN POLYTECHNIC UNIVERSITY
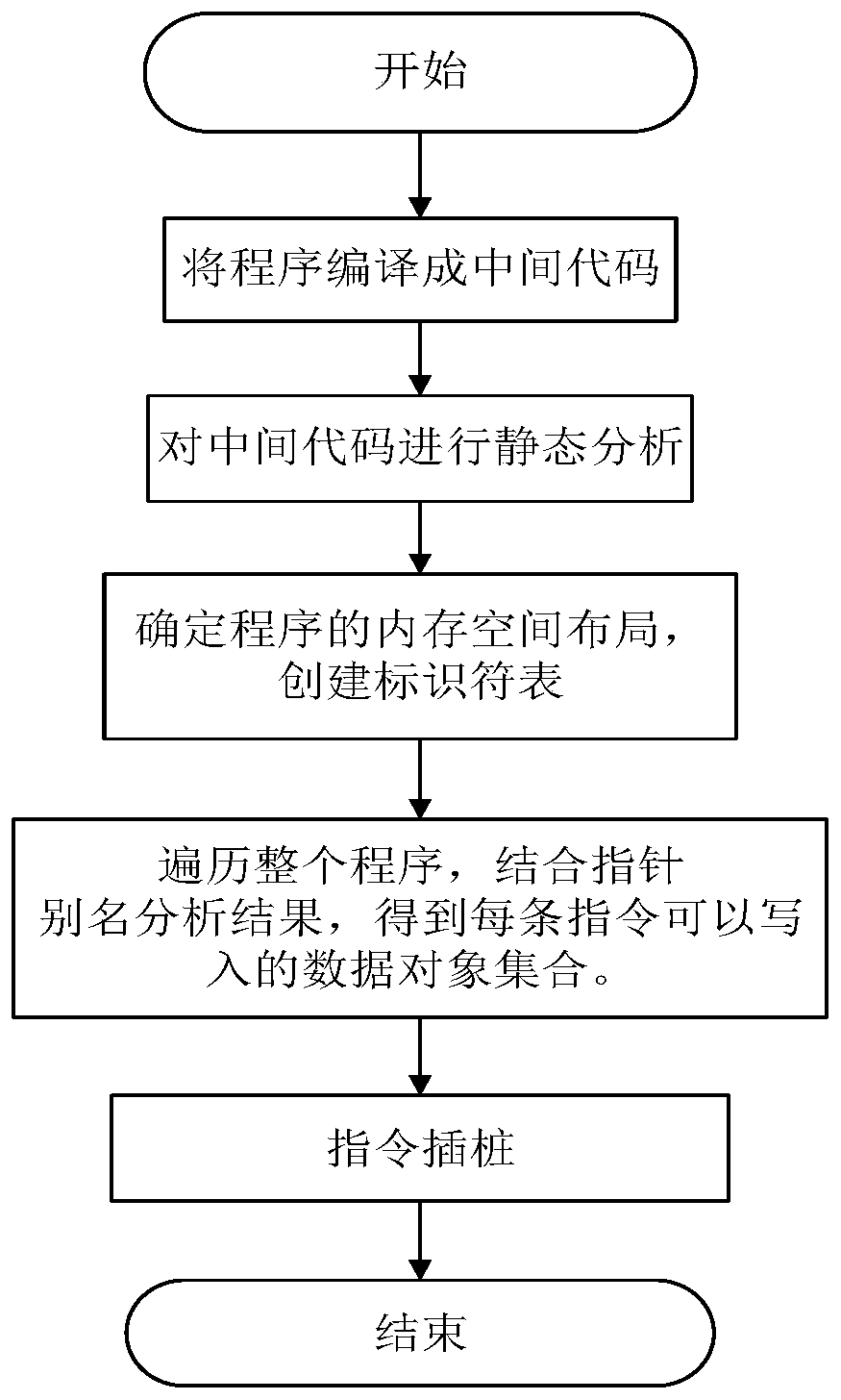
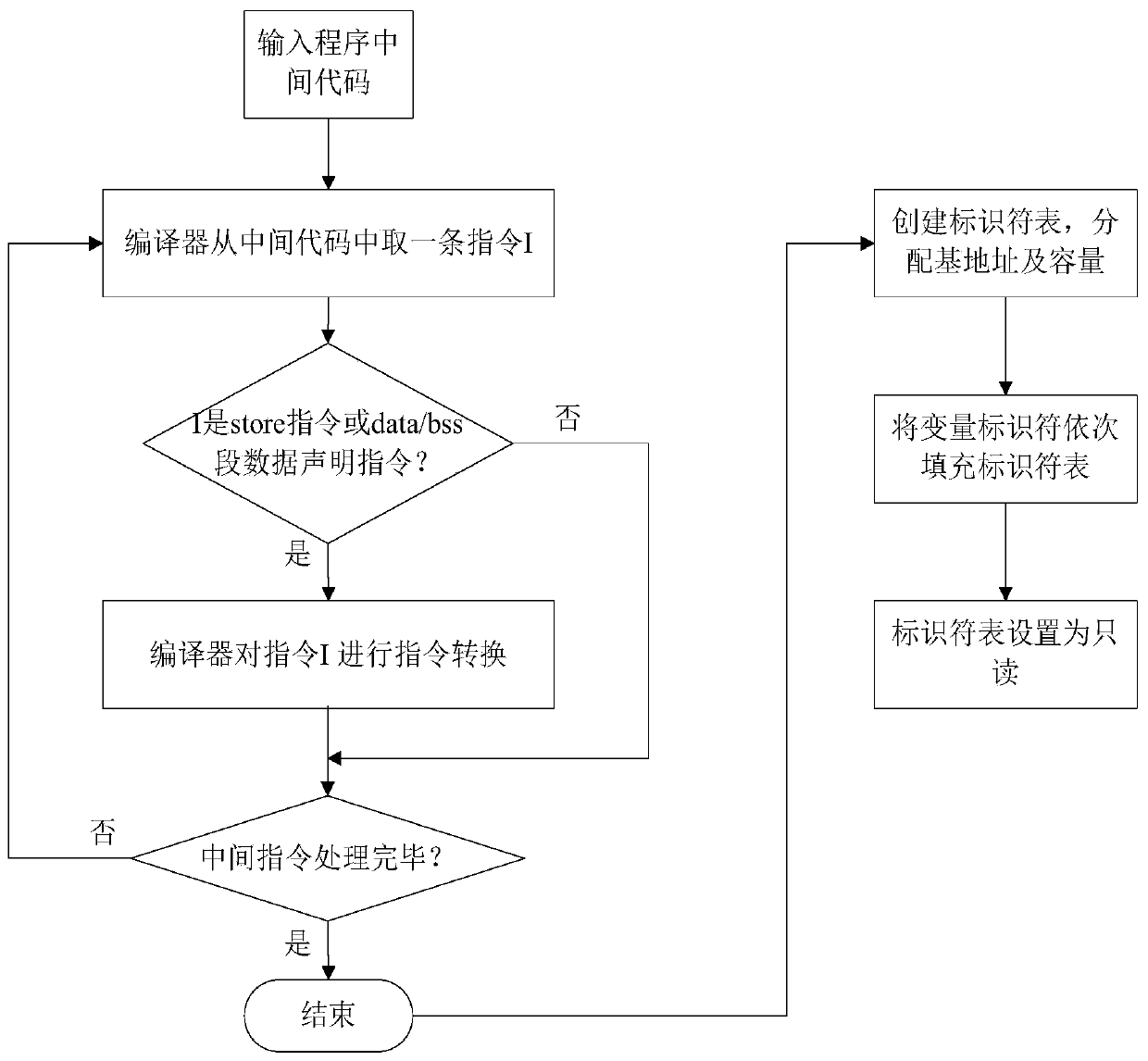
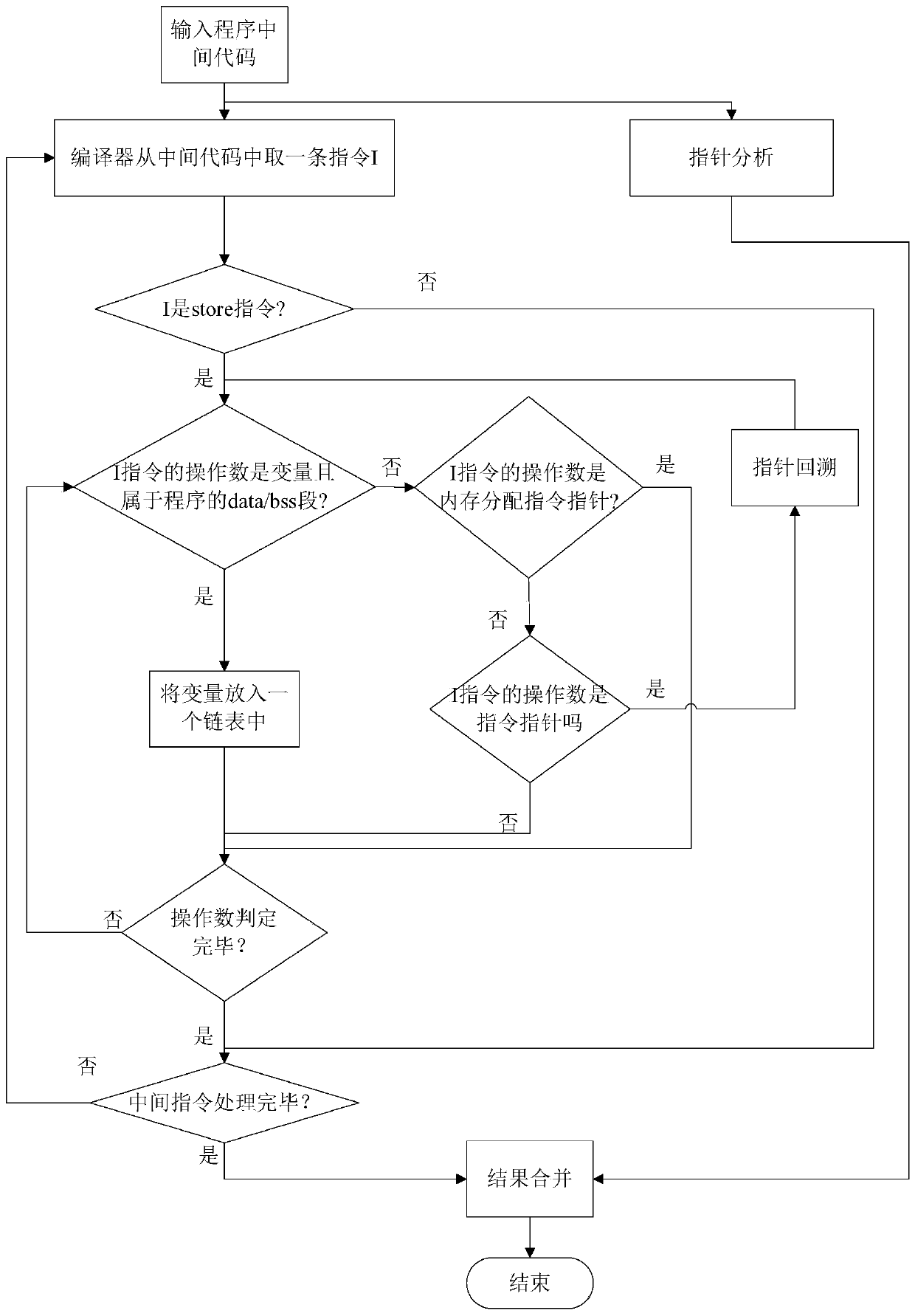
program non-control data attack protection method based on an LLVM compiler
ActiveCN109918903AWill not affect the running processImprove accuracyPlatform integrity maintainanceCode compilationAttackSoftware engineering
The invention provides a program non-control data attack protection method based on an LLVM compiler, and the method comprises the steps: compiling a program source code into an intermediate code fora 64-bit application program which is widely applied at present, carrying out the static analysis of the intermediate code, obtaining a directivity analysis result, and obtaining non-control data which needs to be protected; meanwhile, carrying out instruction instrumentation on the basis of the intermediate code, so that non-control data of the program are prevented from being maliciously tampered. According to the method, the defects of an original static analysis method are overcome, the analysis accuracy is improved, and the security threat caused by malicious tampering of program non-control data by an attacker is solved by utilizing relatively low space and time complexity.
Owner:陕西数图行信息科技有限公司
Content classification for multimedia processing
ActiveCN101171843APulse modulation television signal transmissionDigital video signal modificationSample complexityAudio frequency
An apparatus and method for processing multimedia data, such as, for example, video data, audio data, or both video and audio data for encoding utilizing a determined content classification is claimed. Processing the multimedia data includes determining complexity of multimedia data, classifying the multimedia data based on the determined complexity, and, determining a bit rate for encoding the multimedia data based on its classification. The complexity can include a spatial complexity component and a temporal complexity component of the multimedia data. The multimedia data is classified using content classifications, which are based on a visual quality value for viewing multimedia data, using the spatial complexity, the temporal complexity, or both the spatial complexity and temporal complexity.
Owner:QUALCOMM INC
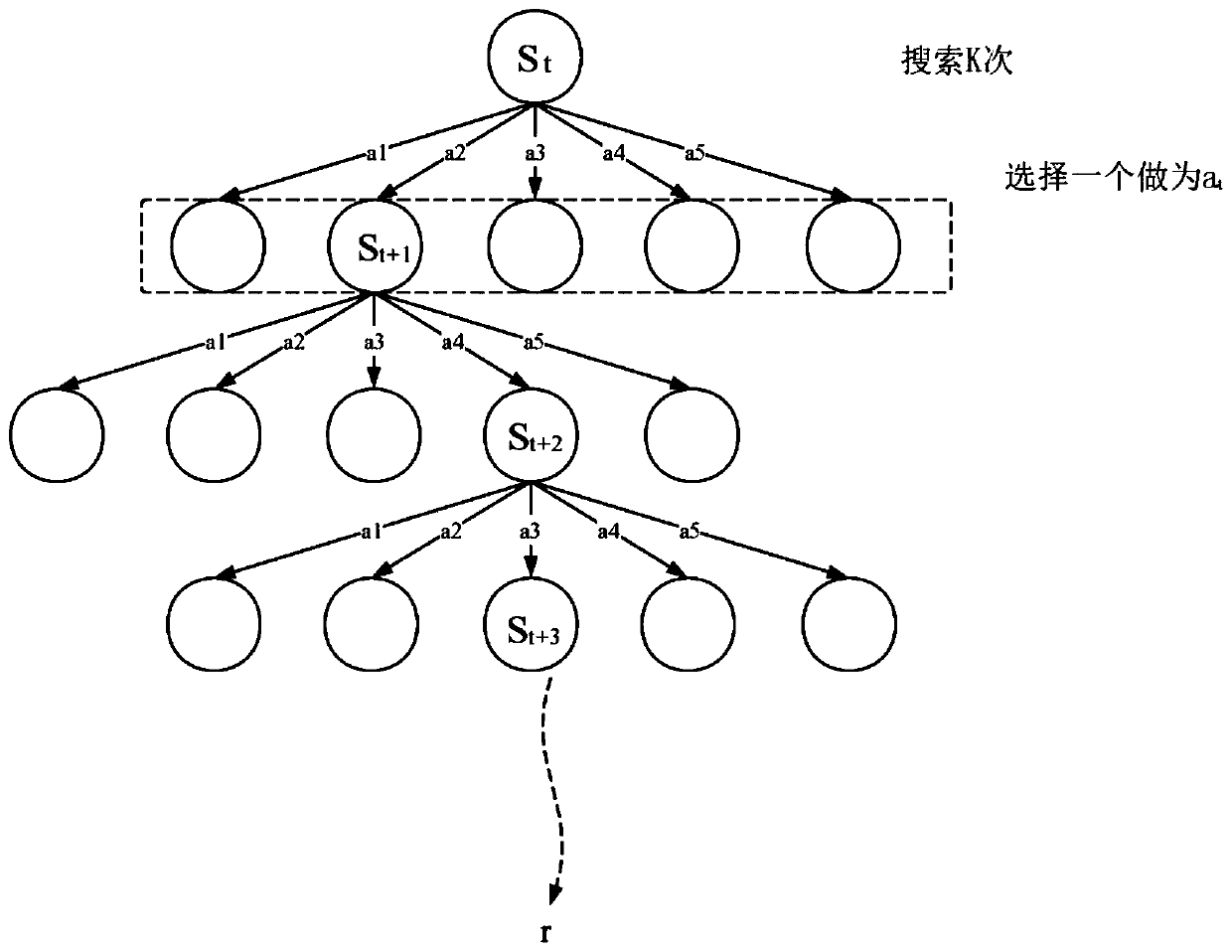
Method for identifying a named entity based on policy value network and tree search
ActiveCN110209770AText database queryingSpecial data processing applicationsInformation processingData set
The invention discloses a method for identifying a named entity based on a policy value network, and belongs to the field of information processing. The method comprises the following steps of firstly, modeling a labeling process of named entity recognition into a Markov decision process (MDP) so that a model for identifying the named entity based on enhanced learning is provided, namely MM-NER. MM-NER is the first to apply the Monte Carlo Tree Search (MCTS) enhanced MDP model to named entity recognition (sequence tag task).A strategy value network is designed on the basis of an MDP state definition to obtain label probability and label sequence accuracy evaluation, and an MCTS is used for simulation, so that a label sequence with more global consciousness is searched out. In the inferenceprocess, the strategy value network is directly used to ensure that the identification effect is basically consistent with the tree search strategy, and the time complexity is greatly reduced. An experimental result of the present invention on the CoNLL2003 named entity identification data set demonstrates the effectiveness of the MM-NER with the K-step exploration decision mechanism.
Owner:BEIJING UNIV OF POSTS & TELECOMM
Attribute weighting method based on decision tree and text classification method
InactiveCN104820702AImprove classification performanceAvoid heuristic search processSpecial data processing applicationsText database clustering/classificationRound complexityText categorization
The invention provides an attribute weighting method based on a decision tree. The attribute weighting method comprises the following steps: firstly, constructing the decision tree by an information gain rate standard, and then, calculating a weight according to the minimum depth of each attribute in a test in the decision tree. The invention simultaneously provides a polynomial nave Bayesian text classification method of the attribute weighting method based on the decision tree, a complementary set nave Bayesian text classification method of the attribute weighting method based on the decision tree and a polynomial and complementary set combination nave Bayesian text classification method of the attribute weighting method based on the decision tree. The attribute weighting method improves the classification precision of the original nave Bayesian text classifier and simultaneously maintains the conciseness and the time complexity of the original nave Bayesian algorithm.
Owner:CHINA UNIV OF GEOSCIENCES (WUHAN)
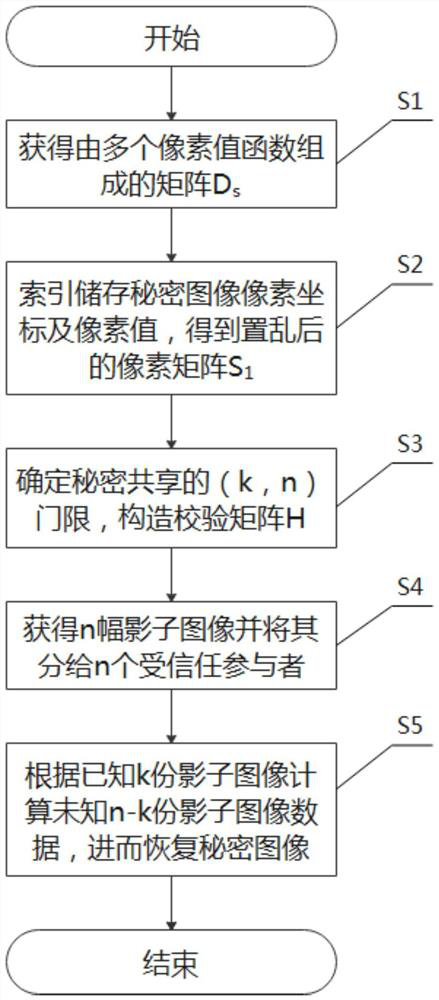
Novel high-security image secret sharing method
ActiveCN112235481AReduce sizeReduce splitKey distribution for secure communicationPictoral communicationEngineeringImaging data
The invention discloses a novel high-security image secret sharing method. The method comprises the steps of obtaining a matrix Ds composed of a plurality of pixel value functions according to a secret image to be shared; indexing and storing pixel coordinates and corresponding pixel values of the secret image, and obtaining a scrambled pixel matrix S1 according to the matrix Ds; determining a (k,n) threshold of secret sharing, and constructing a check matrix H on a finite field GF (2m); obtaining n shadow images and distributing the n shadow images to n trusted participants; and calculatingunknown n-k shadow image data according to the known k shadow images so as to recover the secret image. In order to solve the problems in the prior art that the algorithm time complexity is too high and the sub-secret images are too large in capacity to increase the storage and transmission burden, the image is split and reconstructed by combining a generation matrix and a check matrix of the MDScode, the image recovery accuracy is ensured, and meanwhile, the method has the advantages of reducing the algorithm time complexity, improving the image recovery efficiency, and shortening the secretimage splitting and reconstruction time.
Owner:CHENGDU UNIV OF INFORMATION TECH
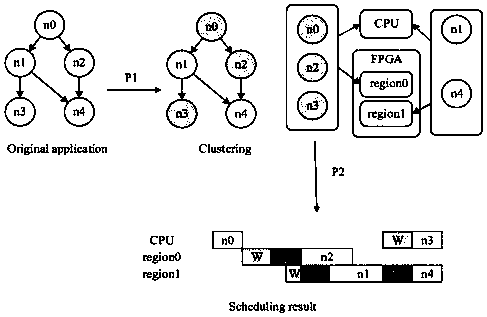
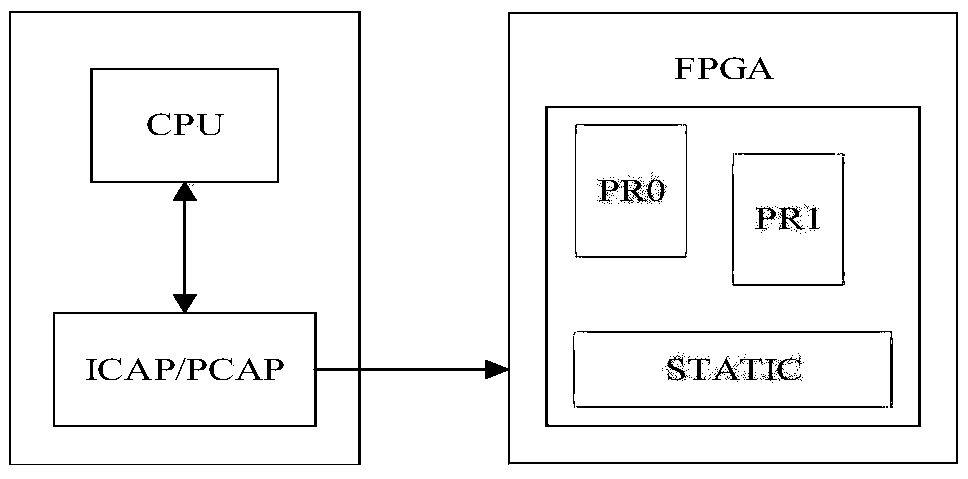
Software and hardware partitioning method for a dynamic part reconfigurable system-on-chip
ActiveCN109656872AFast solutionReduce complexityArchitecture with single central processing unitElectric digital data processingComputer hardwareComputer architecture
The invention relates to a software and hardware partitioning method for a dynamic part reconfigurable system-on-chip. The problems of task mapping, task sequencing, task scheduling, task reconstruction sequencing, inter-task communication and the like in the software and hardware partitioning problem can be solved. According to the method, a software and hardware division problem is described asa refined mathematical model, so that an optimal solution can be obtained by adopting a solver with less time complexity. Meanwhile, according to the method disclosed by the invention, the reconstruction time of all tasks allocated to the reconfigurable area of the FPGA dynamic part is taken into consideration, so that the coincidence degree of the result and the actual application is improved, and the method has higher application value.
Owner:NAT UNIV OF DEFENSE TECH
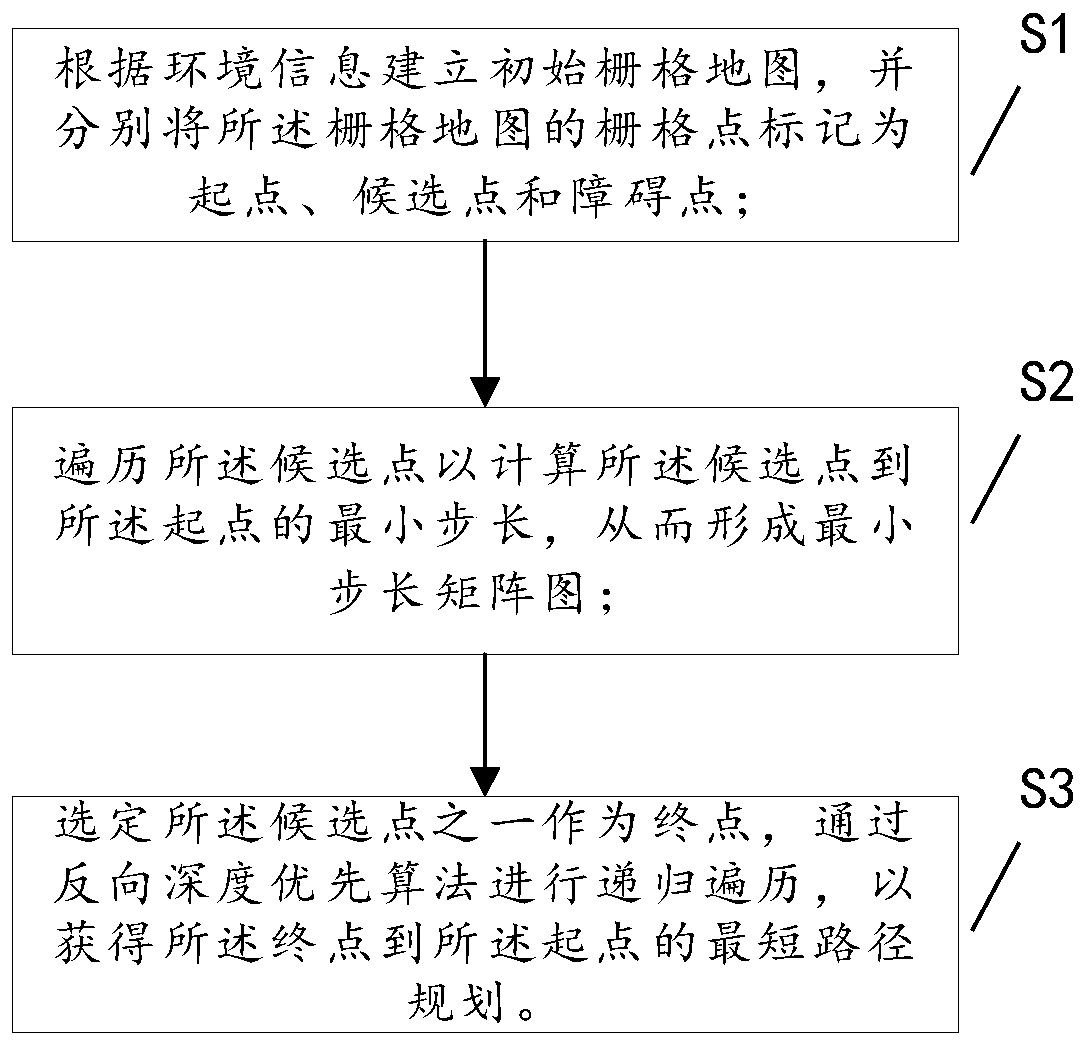
Planning method and system for shortest path
ActiveCN110926491AAvoid the curse of dimensionalityReduce time complexityInstruments for road network navigationShortest path planningRound complexity
The invention discloses a planning method and system for a shortest path. The method comprises the following steps of establishing an initial grid map according to the environmental information, and respectively marking the grid points of the grid map as a starting point, candidate points and obstacle points; traversing the candidate points to calculate the minimum step length from the candidate points to the starting point so as to form a minimum step length matrix graph; and selecting one of the candidate points as an ending point, and performing the recursive traversal through a reverse depth-first algorithm to obtain a shortest path plan from the ending point to the starting point. The method and the system of the scheme are based on a grid map global expansion algorithm, not only solve the problem that the final path is the shortest path, but also greatly reduce the time complexity and the space complexity of the operation.
Owner:海南中智信信息技术有限公司
Content classification for multimedia processing
InactiveCN101697591APulse modulation television signal transmissionDigital video signal modificationSample complexityAudio frequency
The invention relates to an content classification for multimedia processing. An apparatus and method for processing multimedia data, such as, for example, video data, audio data, or both video and audio data for encoding utilizing a determined content classification is claimed. Processing the multimedia data includes determining complexity of multimedia data, classifying the multimedia data based on the determined complexity, and, determining a bit rate for encoding the multimedia data based on its classification. The complexity can include a spatial complexity component and a temporal complexity component of the multimedia data. The multimedia data is classified using content classifications, which are based on a visual quality value for viewing multimedia data, using the spatial complexity, the temporal complexity, or both the spatial complexity and temporal complexity.
Owner:QUALCOMM INC
Method for propagating image label based on minimal cost path
ActiveCN104933442ABlock in timeEffective classificationCharacter and pattern recognitionRound complexityDirected graph
The invention relates to a method for propagating an image label based on a minimal cost path; according to the method, the defect that an undirected graph becomes into a sparse directed graph as the graph only has a plurality of adjacent nodes for each node is resolved by constructing the graph and reconstructing the sparse matrix of the graph; data is quickly classified by the improved minimum spanning tree algorithm so as to reduce the time complexity of the algorithm and achieve the purpose of completely sorting all data. According to the method, the optimal paths of image data samples for obtaining the labels are searched from unmarked image data samples, thus ensuring that each image data sample can be effectively classified, and also ensuring that only one label is propagated for each point; construction of the sparse neighbor matrix is improved, and the problem that propagation of the image data sample labels is incomplete and incorrect due to the neighbor matrix is reduced; as propagation of the algorithm is intercepted among the different labels, the algorithm can be applied to large-scale multi-classification data with multiple labels.
Owner:SHAANXI NORMAL UNIV
Track similarity calculation method based on sorting learning
ActiveCN110443288AImprove accuracyOvercome limitationsCharacter and pattern recognitionTime complexityPoint match
The invention relates to a track similarity calculation method based on sorting learning. The method comprises the following steps: 1) expanding an Euclidean space; 2) calculating similar attributes of the track sequence; 3) normalizing the track sequence; 4) constructing a label of an experiment track by adopting a self-similarity method; 5) constructing a training set, and training the SVM learner; and 6) dividing the test set into an input document set and a label document set, and outputting the rank of the real label of each input document by applying the trained SVM sorting model. The beneficial effects of the invention are that the method irons out the limitations of a conventional track similarity calculation method based on a point matching algorithm, the low accuracy of track matching, the weak resistance to a noise non-uniform sampling rate, and the efficiency problem of a track matching algorithm based on deep learning; according to the method, the time complexity of similarity calculation is greatly reduced, and compared with the prior art, the accuracy of trajectory similarity calculation is improved.
Owner:ZHEJIANG UNIV CITY COLLEGE
Attribute weighting method based on information gain ratios and text classification methods
InactiveCN104809233AImprove classification performanceHigh precisionCharacter and pattern recognitionSpecial data processing applicationsMachine learningTime complexity
The invention provides an attribute weighting method based on information gain ratios. Firstly, the information gain ratio of each attribute is calculated and then by utilizing the information gain ratios, the weight of each attribute is respectively calculated. The invention also provides a polynomial naive Bayesian text classification method relying on the attribute weighting method based on information gain ratios, a complementary set naive Bayesian text classification method relying on the attribute weighting method based on information gain ratios and a polynomial and complementary set integrated naive Bayesian text classification method relying on the attribute weighting method based on information gain ratios. The invention improves the classification precision of the original naive Bayesian text classifier, and also keeps the simplicity and time complexity of the original naive Bayesian algorithm.
Owner:CHINA UNIV OF GEOSCIENCES (WUHAN)
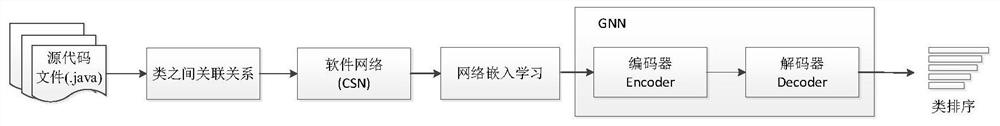
Method for identifying key classes in software system based on graph neural network
ActiveCN111913702AImplement importance rankingRealize identificationCharacter and pattern recognitionNeural architecturesSoftware networkSource code file
The invention discloses a method for identifying key classes in a software system based on a graph neural network, which comprises the following steps of: (1) analyzing a software source code file byusing an open source tool, extracting various association relationships among classes, and constructing a weighted software network model among the classes according to the relationships; (2) learningnodes in the weighted software network by using a network embedding method to obtain embedded vectors of the nodes; (3) constructing a sorting model based on a graph neural network; and (4) trainingthe model by using pairwise sorting loss to realize importance sorting of nodes in the network. The invention has the advantages that under the condition that the recognition precision is ensured, a large software system can be analyzed within extremely low time complexity, and potential key classes can be recognized from the large software system. Developers understand a software structure and improve the stability of a software system.
Owner:HUBEI UNIV
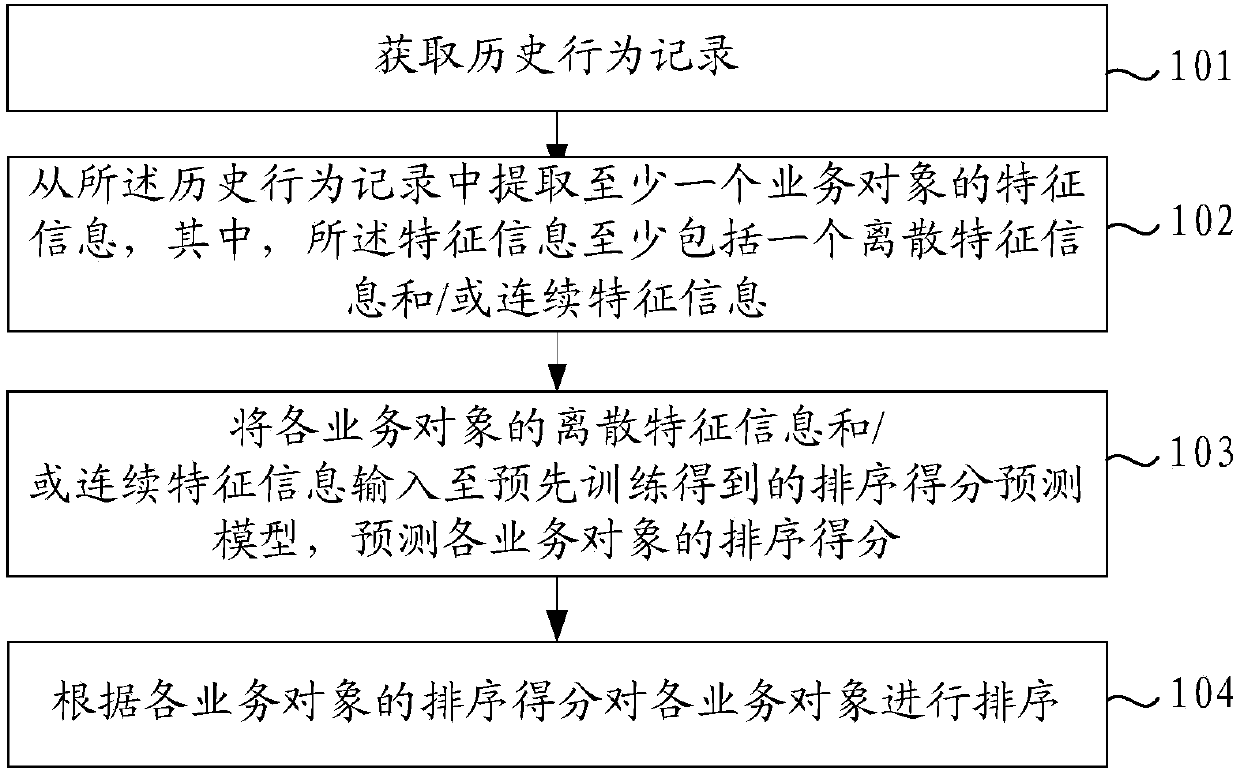
Service object sorting method and device
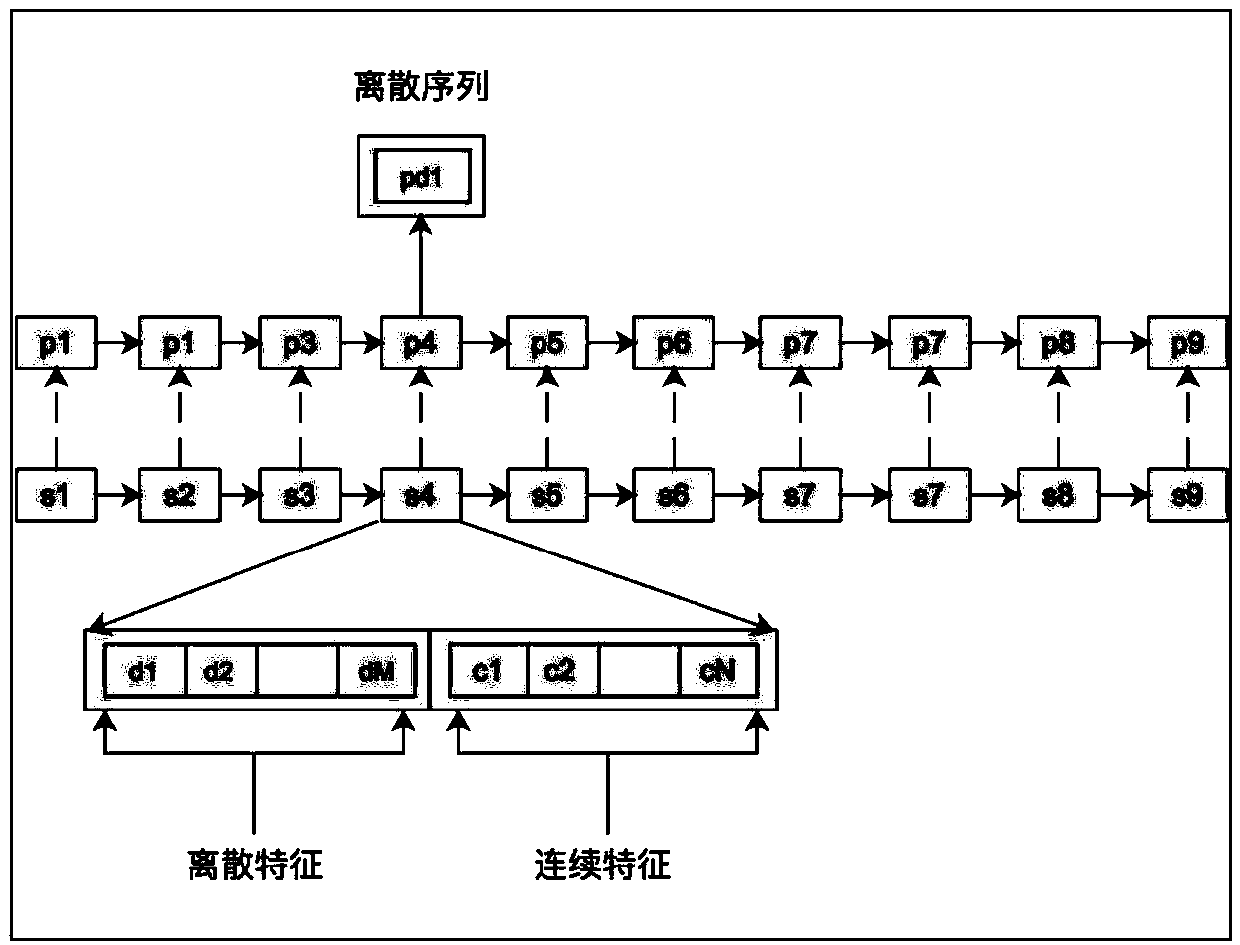
ActiveCN110647696AReduce time complexityForecastingBuying/selling/leasing transactionsFilter algorithmEngineering
The invention provides a service object sorting method and apparatus. The method comprises the steps of obtaining a historical behavior record; extracting feature information of at least one service object from the historical behavior record, wherein the feature information at least comprises one piece of discrete feature information and / or continuous feature information; inputting the discrete feature information and / or the continuous feature information of each service object into a pre-trained sorting score prediction model, and predicting a sorting score of each service object; and sortingthe service objects according to the sorting scores of the service objects. The problems of relatively high time complexity, relatively poor data sparsity and relatively poor recall effect caused bya collaborative filtering algorithm in the prior art are solved. According to the method, the pre-trained sorting score prediction model is adopted to predict the sorting scores of the service objects, and sorting is performed to guide recommendation, so that the time complexity is reduced, the problem of data sparsity is solved, and the recall effect is improved.
Owner:BEIJING SANKUAI ONLINE TECH CO LTD
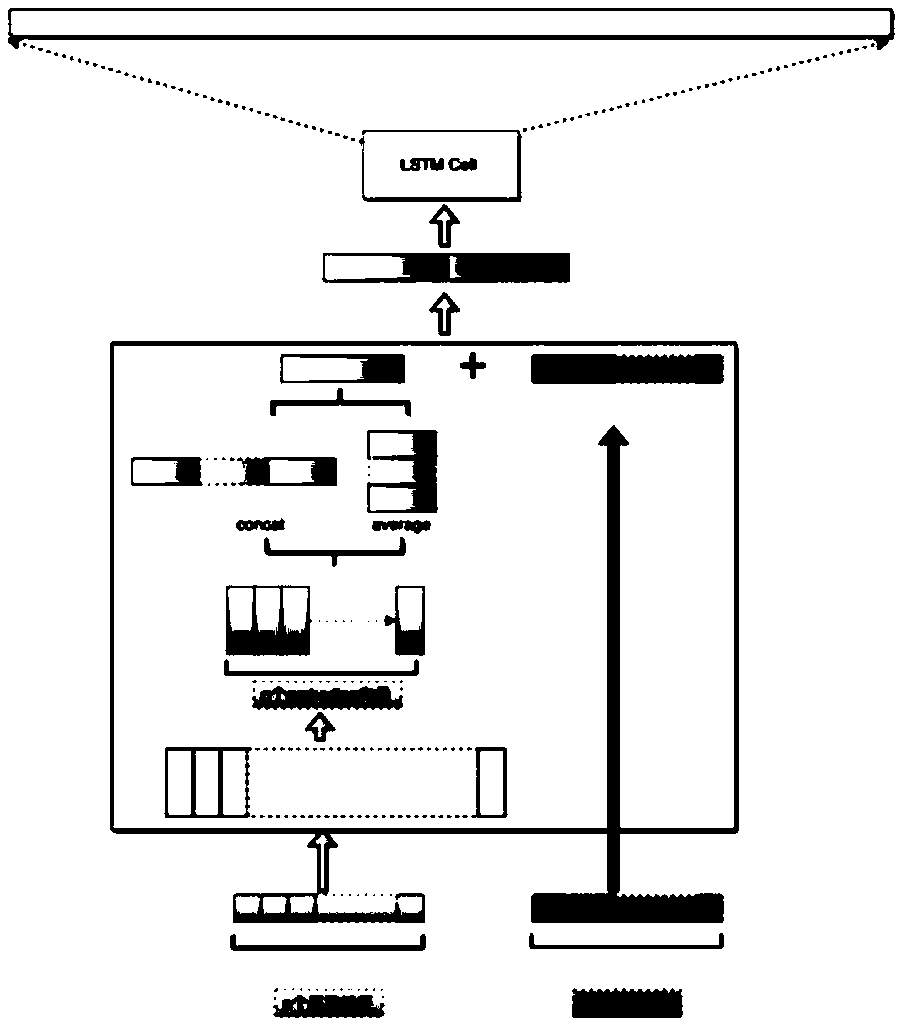
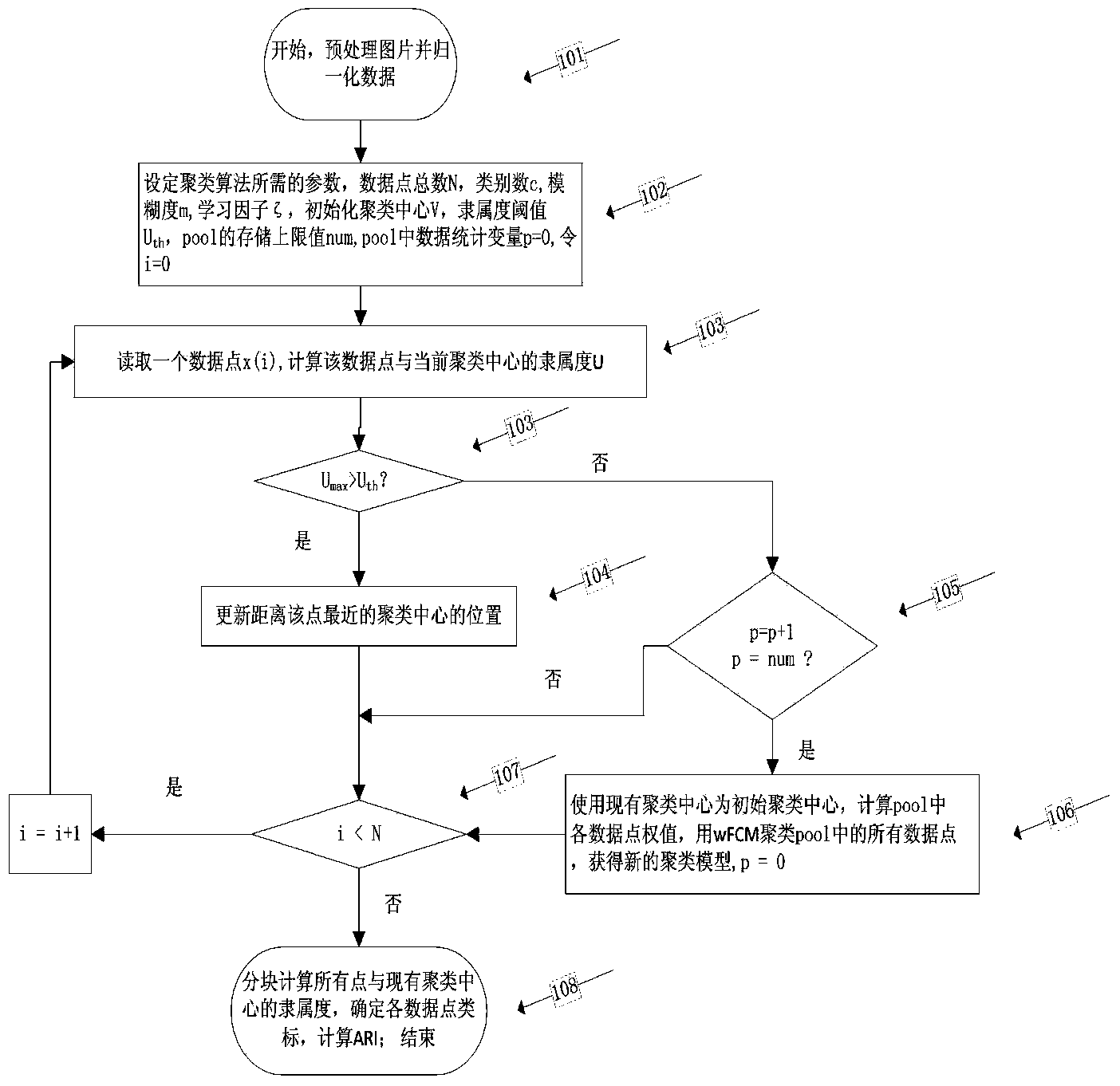
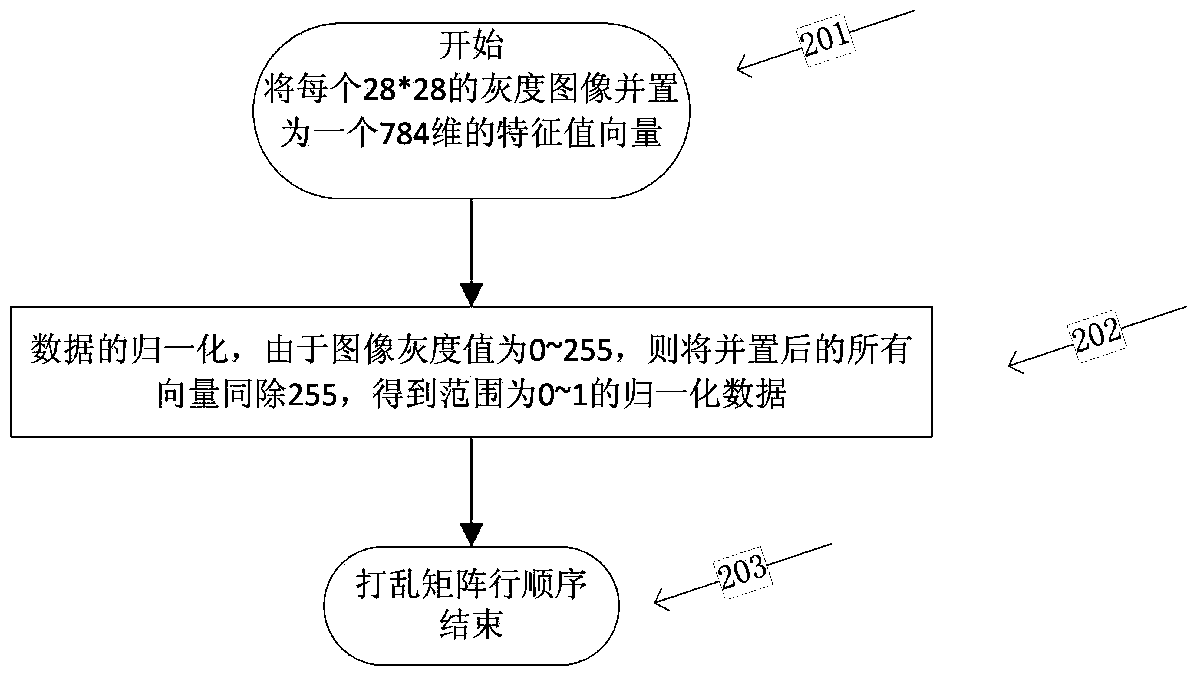
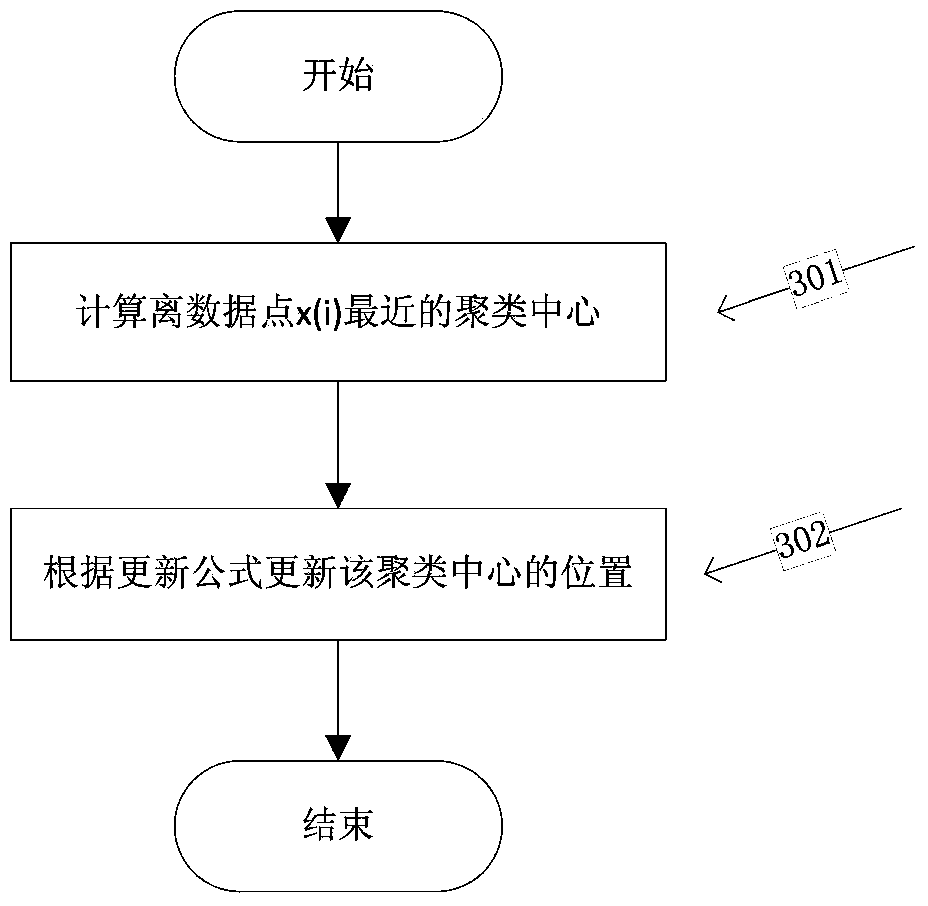
Handwritten numeral recognition method based on point density weighting online FCM clustering
ActiveCN104298987ALower requirementRealize handwritten digit recognitionCharacter and pattern recognitionPattern recognitionPoint density
The invention discloses a handwritten numeral recognition method based on point density weighting online FCM clustering. The method is used for processing the large-scale offline handwritten numeral recognition problem. The method includes the steps that (1), all handwritten numeral image sets are preprocessed; (2), clustering centers are initialized, and data points are made to sequentially enter processing procedures; (3), the membership degree of the current data point and all the clustering centers is calculated; (4), if the membership degree reaches a threshold value, the position of the nearest clustering center is updated; (5), if the membership degree does not reach the threshold value, the current data point is not processed and is temporarily placed in a to-be-processed region; (6), when the to-be-processed region reaches certain standards, data in the to-be-processed region are clustered through a point density weighting FCM algorithm, and the clustering centers are updated; (7), circulation continues until all the data points are processed; (8), the membership degrees of all the data points are calculated through acquired clustering center blocks, the data points are divided into different classes, and data classification is finished through scanning at a time. According to the method, the space complexity and the time complexity can be lowered from the aspect of processing the large-scale handwritten numeral recognition problem.
Owner:XIDIAN UNIV
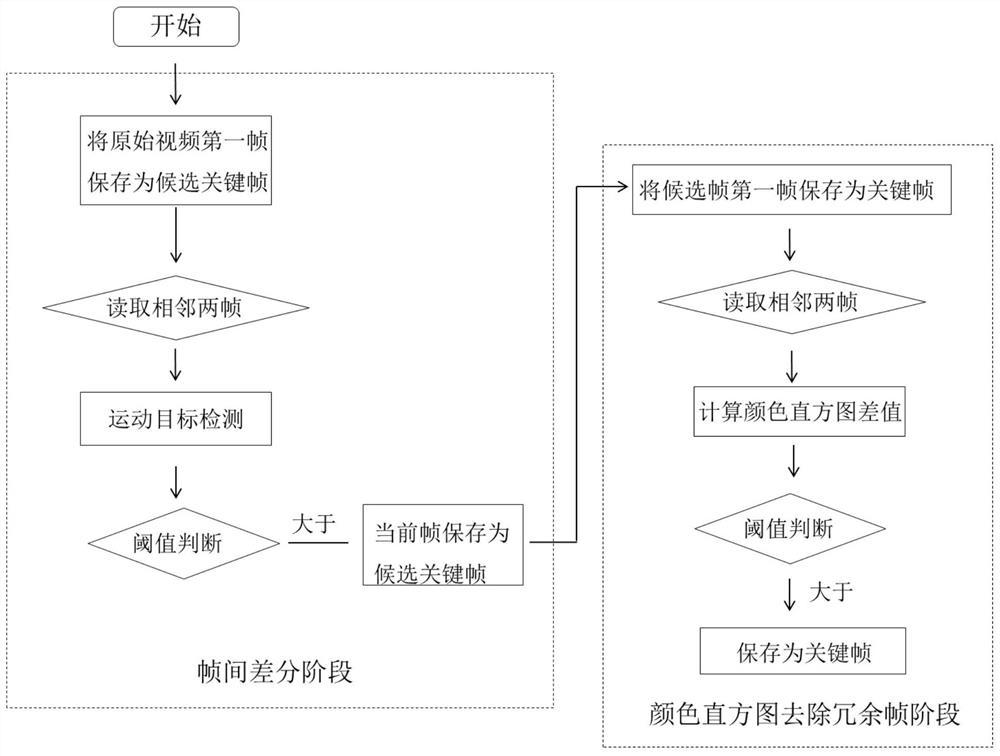
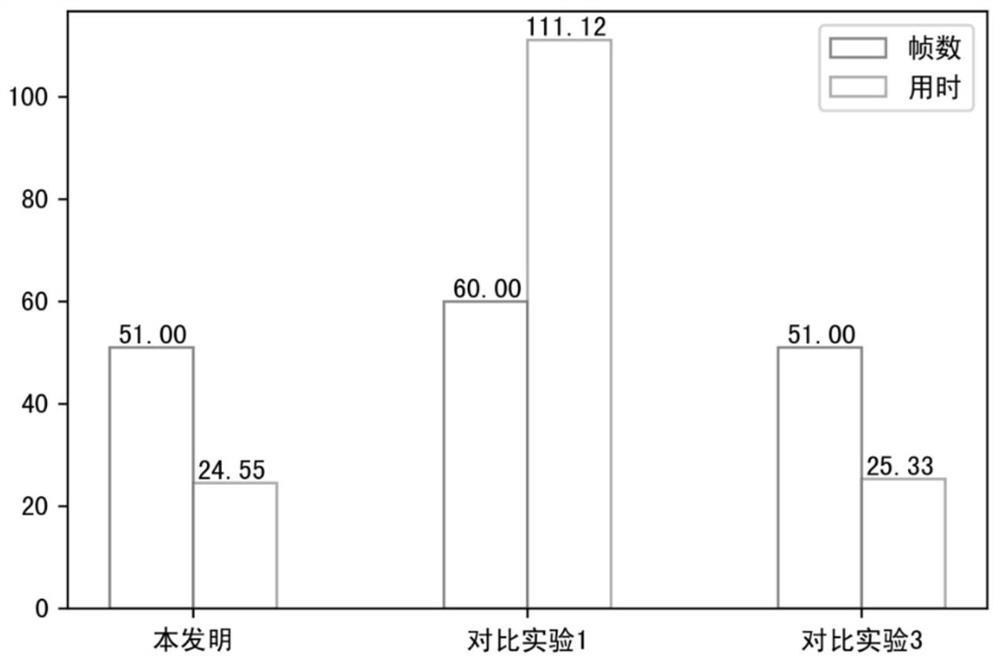
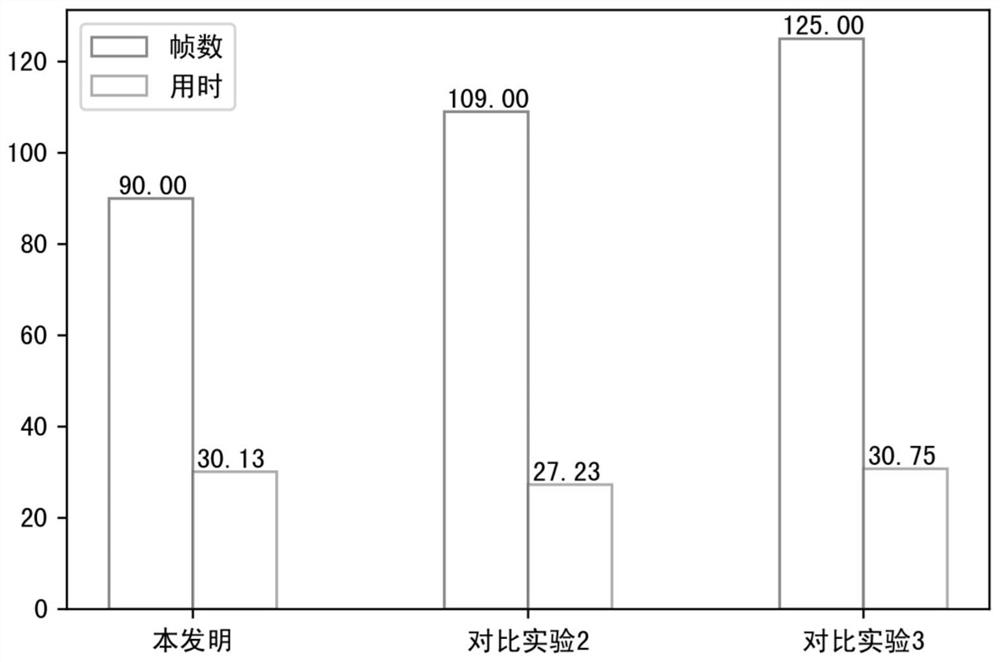
Key frame extraction method based on inter-frame difference and color histogram difference
PendingCN112270247AShorten the timeReduce the number of framesImage enhancementImage analysisFrame differenceVideo sequence
The invention discloses a key frame extraction method based on inter-frame difference and color histogram difference. The method comprises the steps: in the first stage, detecting a moving target in amonitoring video based on inter-frame difference, dividing the monitoring video into a video sequence only containing the moving target, and obtaining candidate key frames; and in the second stage, calculating the color histogram difference value of two adjacent frames in the candidate key frames, setting a threshold value, removing similar image frames, and obtaining a final key frame set. Compared with other key frame extraction technologies, the method has the advantages that the time required for key frame extraction is remarkably shortened, the real-time requirement is met and redundantinformation in the set is reduced as much as possible while relatively high representativeness of the content of the key frame set is ensured, so that the number of key frame frames is relatively small, and thus, the time complexity of task algorithms such as subsequent target identification and pedestrian quantity statistics is reduced.
Owner:杭州卷积云科技有限公司
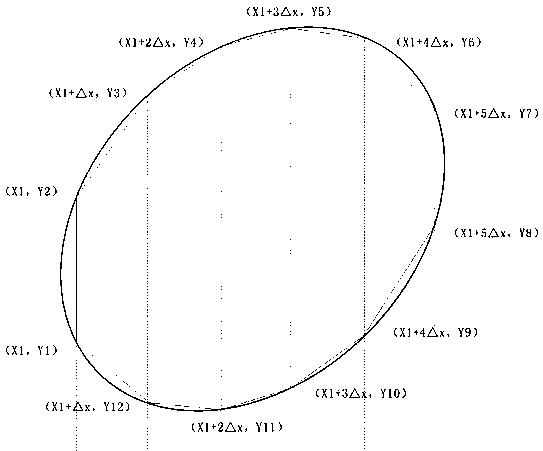
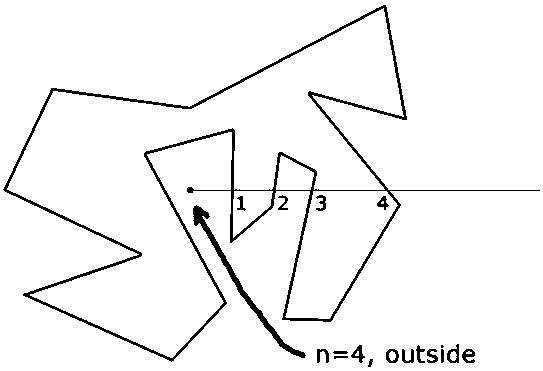
Method for judging the position relation between points and closed graphs through a differential ray method
The invention provides a method for rapidly judging the relation between points and polygons. A traditional ray method is greatly improved. A differential idea is utilized to convert a graph into a polygon formed by point connection, a data structure capable of being quickly retrieved is newly built to store information of the points, and rays of a traditional ray method are converted into rays ofa traditional ray method. Line segment relation judgment and conversion into to-be-checked point The values between the data structures are searched and compared to obtain the intersection times of the rays and the graphs. according to the parity of the value, obtaining the position relation between the point to be checked and the polygon through a general rule of a ray method. The time complexity of the method is O (1), the method has no correlation with the number N of edges, and the performance of the method is greatly improved compared with that of a traditional method in calculation occasions with complex graphs and high precision requirements.
Owner:高静
Efficient intelligent customer service method for a large corpus
PendingCN109658114ASmall amount of calculationReduce overheadCustomer relationshipNatural language data processingCluster algorithmEngineering
The invention relates to an efficient intelligent customer service method for a large corpus. According to the method, the recursion clustering algorithm based on keyword weighting is introduced to pre-classify the corpus, the advantage of lexicon matching is reserved based on keyword weighting, and a similarity calculation mode is adopted, so that the time complexity of similarity calculation isreduced. And meanwhile, the cost expenditure of manual marking and word library construction is avoided, and the complexity and the unsuitability of transfer learning do not exist. The system has goodperformance in the man-machine interaction fields of store automatic after-sale, citizen automatic inquiry, official account automatic reply automatic after-sale questions and answers, citizen cloudautomatic inquiry, social APP automatic chatting and the like.
Owner:WONDERS INFORMATION
Entity alignment method based on heterogeneous graph attention network
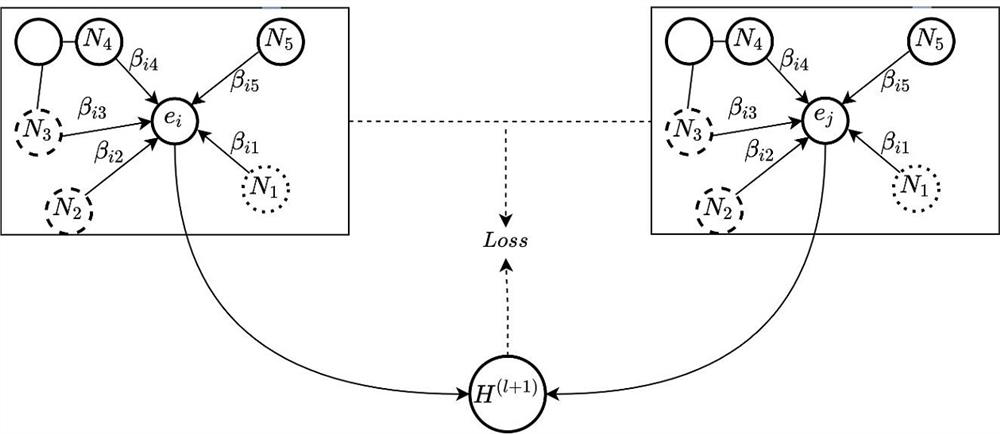
ActiveCN112800770AQuality improvementHigh precisionSemantic analysisNeural architecturesTheoretical computer scienceAttention network
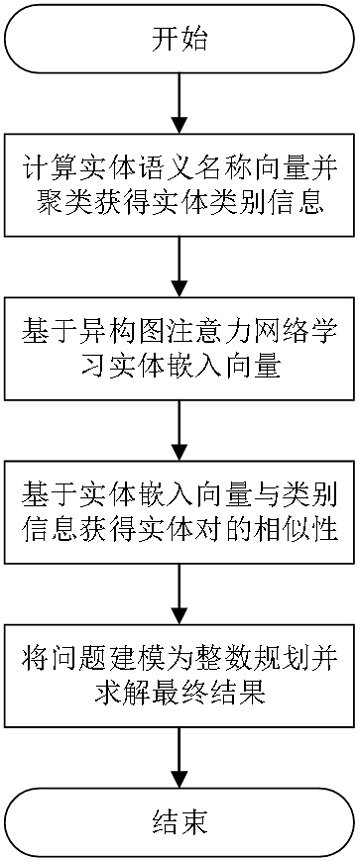
The invention discloses an entity alignment method based on a heterogeneous graph attention network, and the method comprises the steps: dividing entities into different categories based on clustering; secondly, learning an embedded vector of an entity based on the heterogeneous graph attention network; calculating the similarity between different entity categories based on entity embedded vectors, and obtaining the similarity of any entity pair by combining the vector similarity; and finally, modeling an entity alignment problem into an integer programming problem, and solving and obtaining an alignment result meeting a one-to-one alignment constraint. The method is not only low in time complexity, but also high in entity alignment precision.
Owner:南京樯图数据研究院有限公司
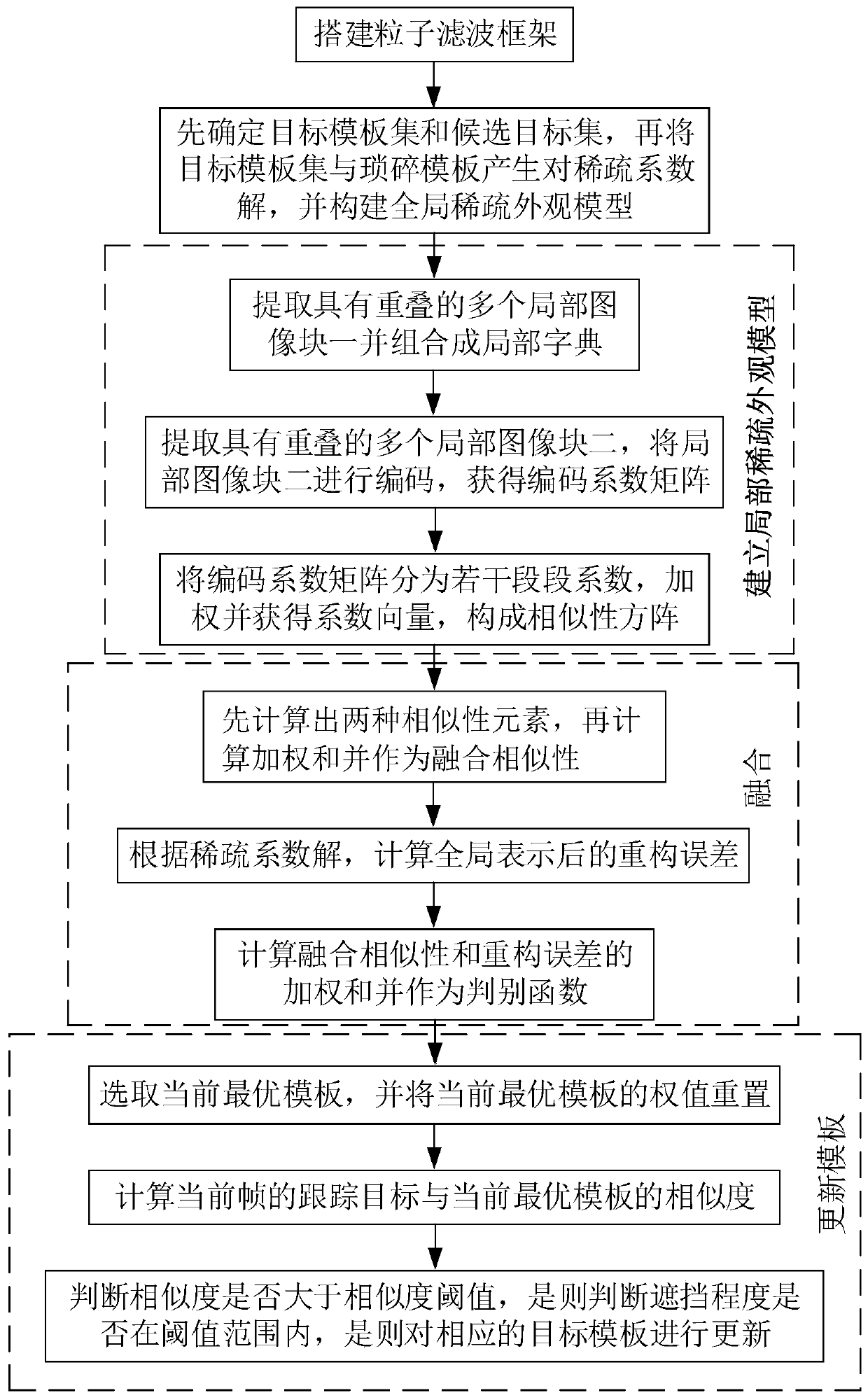
Multi-appearance model fusion target tracking method and device based on sparse representation
ActiveCN110648351AImprove update efficiencyAvoid lossImage enhancementImage analysisProcessingDiscrimination function
The invention discloses a multi-appearance model fusion target tracking method and device based on sparse representation. The method comprises the steps that a particle filtering framework is built; firstly, a target template set and a candidate target set of a tracking image are determined, and then the target template set and a trivial template are subjected to linear programming to generate a sparse coefficient solution; establishing a local sparse appearance model; fusing the global sparse appearance model and the local sparse appearance model: firstly calculating two similarity elements,then calculating a weighted sum of the two elements as fusion similarity, calculating a reconstruction error, and taking the weighted sum of the fusion similarity and the reconstruction error as a discrimination function; and endowing the target template of the target template set with a weight in direct proportion to the importance of the target template, and updating the target template of the target template set. According to the method, the time complexity is reduced, high adaptability is achieved under the conditions that the appearance of the target is greatly changed and the shielding area is large, the target is accurately and robustly tracked, the shielding processing capacity is achieved, and the appearance model updating efficiency is high.
Owner:ANHUI UNIVERSITY
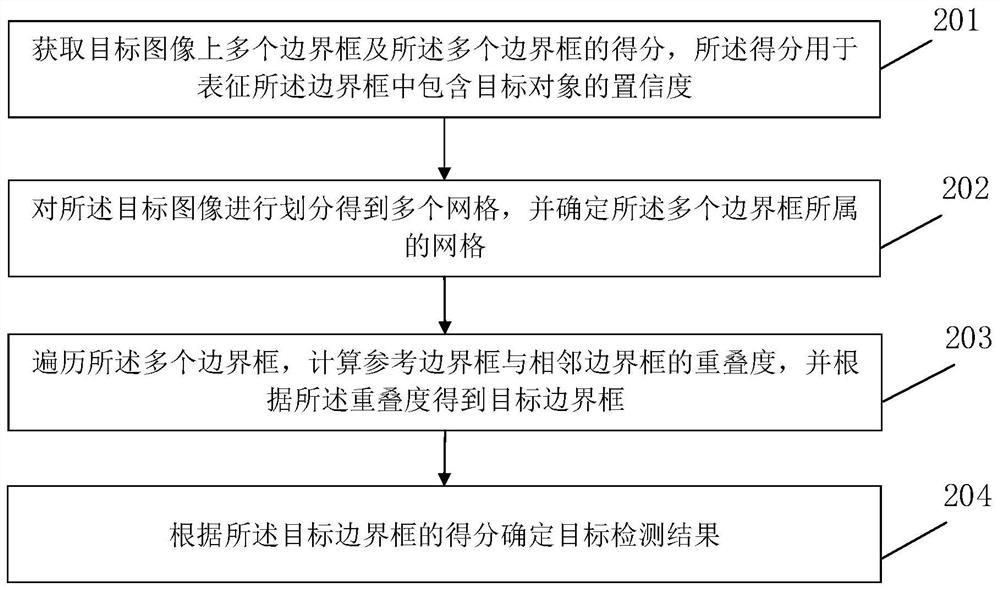
Target detection method and device
The invention discloses a target detection method and device. The method comprises the steps: obtaining a plurality of bounding boxes on a target image and the scores of the bounding boxes, and enabling the scores to be used for representing the confidence of a target object contained in the bounding boxes; dividing the target image to obtain a plurality of grids, and determining the grids to which the plurality of bounding boxes belong; traversing the plurality of bounding boxes, calculating the overlapping degree of a reference bounding box and an adjacent bounding box, and obtaining a target bounding box according to the overlapping degree; and determining a target detection result according to the score of the target bounding box. According to the embodiment of the invention, grid division is carried out on the target image, the grid to which the bounding box belongs is determined, and then the adjacent relation of the bounding box is determined according to the adjacent relation between the grids, so that only the overlapping degree of the reference bounding box and the adjacent bounding box needs to be calculated during NMS algorithm operation, the time complexity of NMS is effectively reduced, and the calculation efficiency is improved. Target detection efficiency is improved.
Owner:HISILICON (SHANGHAI) TECH CO LTD
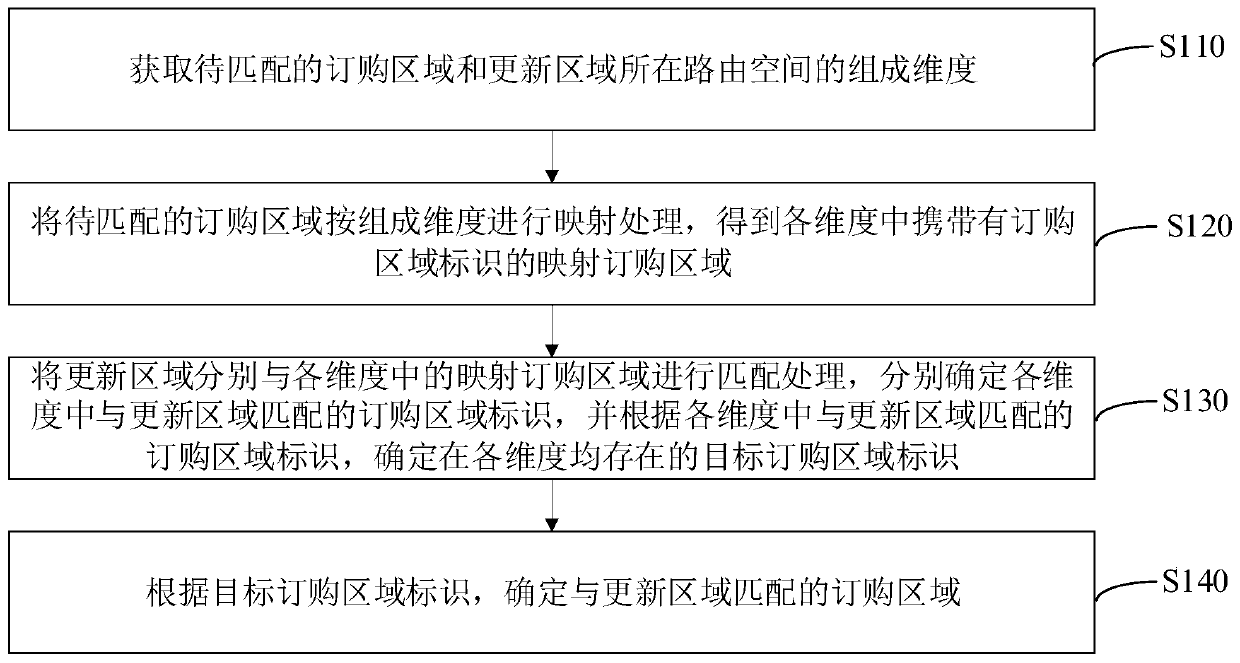
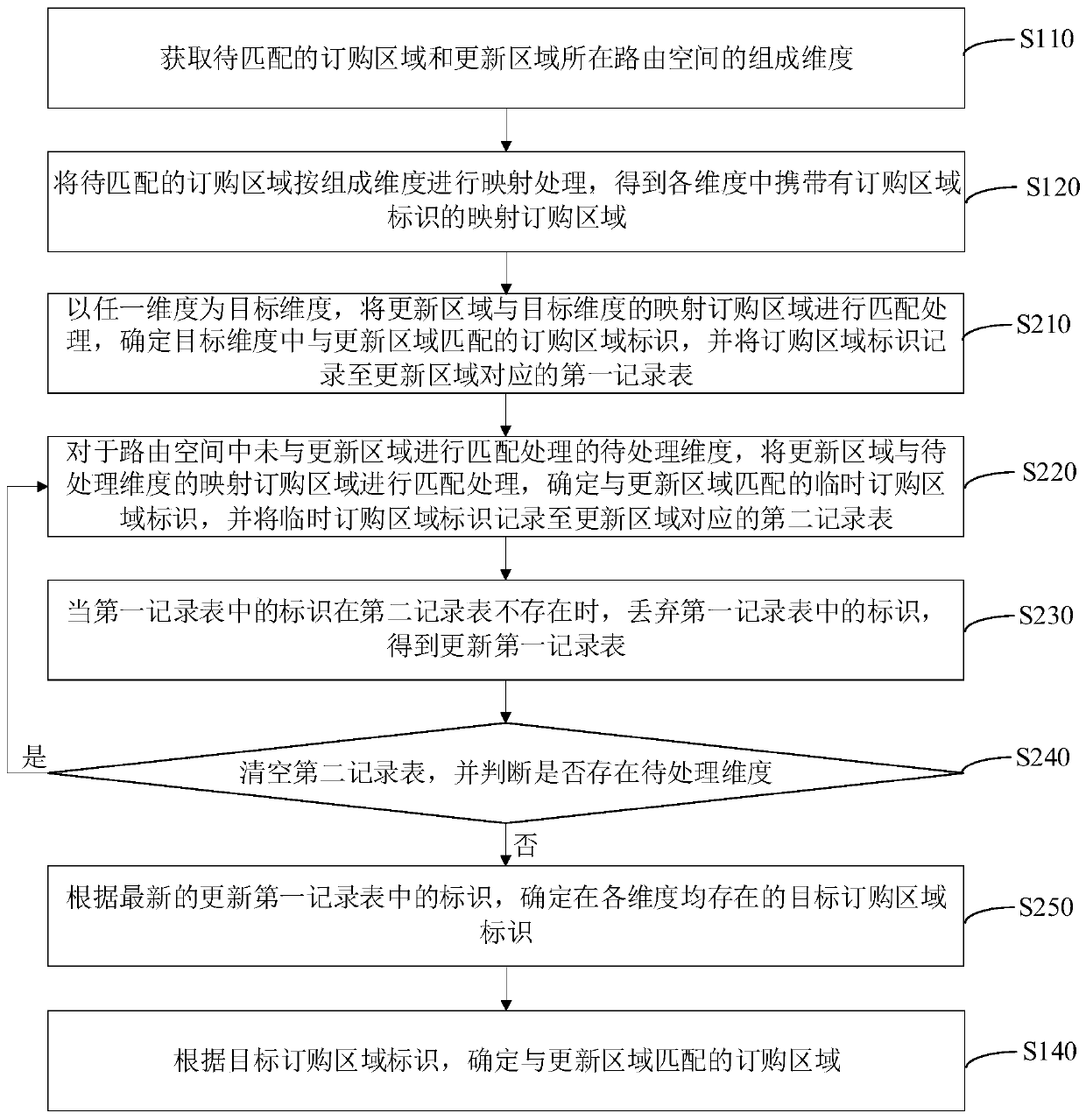
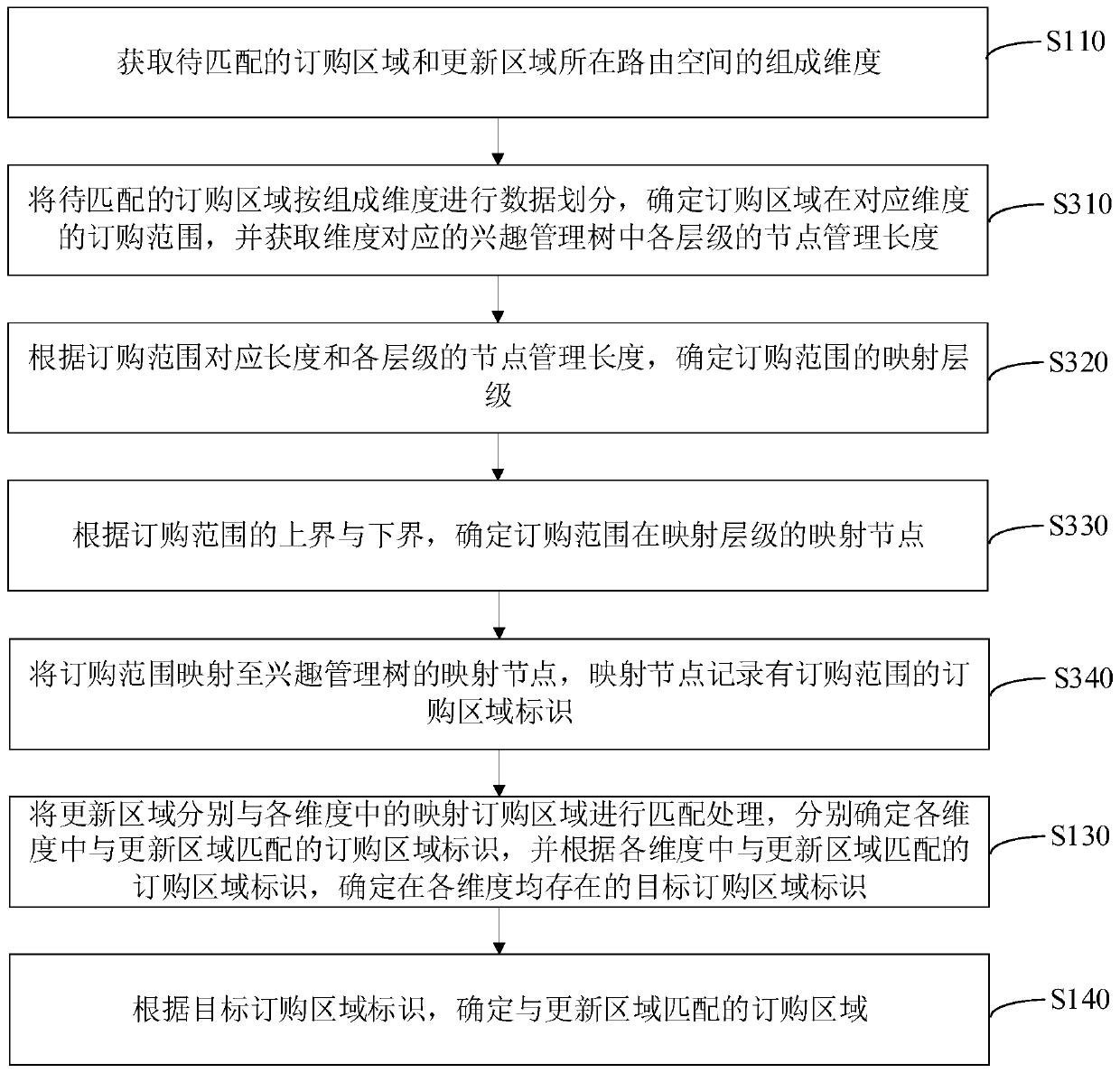
Hierarchical interest matching method and device, computer equipment and storage medium
PendingCN111291085AImplement parallel match processingReduce time complexityDatabase updatingSpecial data processing applicationsAlgorithmTheoretical computer science
The invention relates to a hierarchical interest matching method and device, computer equipment and a storage medium. The method comprises the following steps: obtaining composition dimensions of a routing space where the ordering area and the updating area to be matched are located, carrying out mapping processing on the ordering area to be matched according to the composition dimension; obtaining a mapping ordering area carrying an ordering area identifier in each dimension; matching the updating area with the mapping ordering area in each dimension; and determining an ordering area identifier matched with the updating area in each dimension, determining a target ordering area identifier existing in each dimension according to the ordering area identifier matched with the updating area in each dimension, and determining the ordering area matched with the updating area according to the target ordering area identifier. Through dimension division and data mapping, the time complexity isreduced, only data reading of a mapping ordering area is involved in the matching process, locking is not needed, parallel matching processing is achieved, and the processing efficiency of the interest matching process is improved.
Owner:NAT UNIV OF DEFENSE TECH
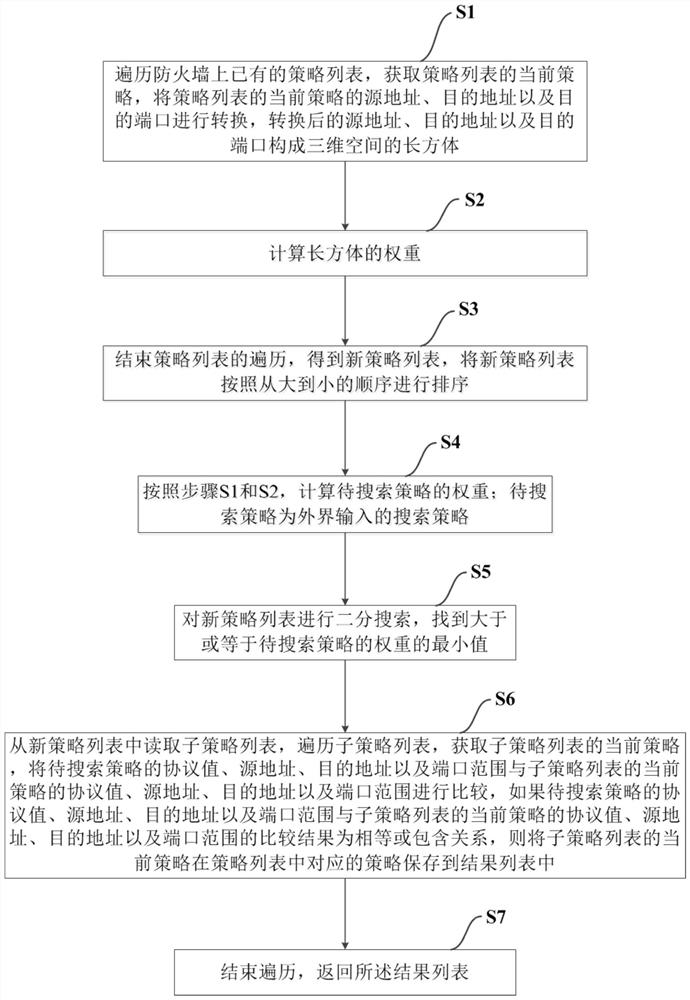
Firewall strategy search method and system based on spatial sorting, terminal and storage medium
ActiveCN111901311AReduce time complexityImprove computing powerTransmissionAlgorithmTheoretical computer science
The invention discloses a firewall strategy search method based on spatial sorting, and compared with the prior art, the algorithm time complexity of the search method is only O(N / 2+log<2>N), so thatthe algorithm time complexity O(N) of the existing search method is greatly reduced, and the calculation performance is remarkably improved. The invention also discloses a search system for realizingthe search method.
Owner:深圳天元云科技有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com