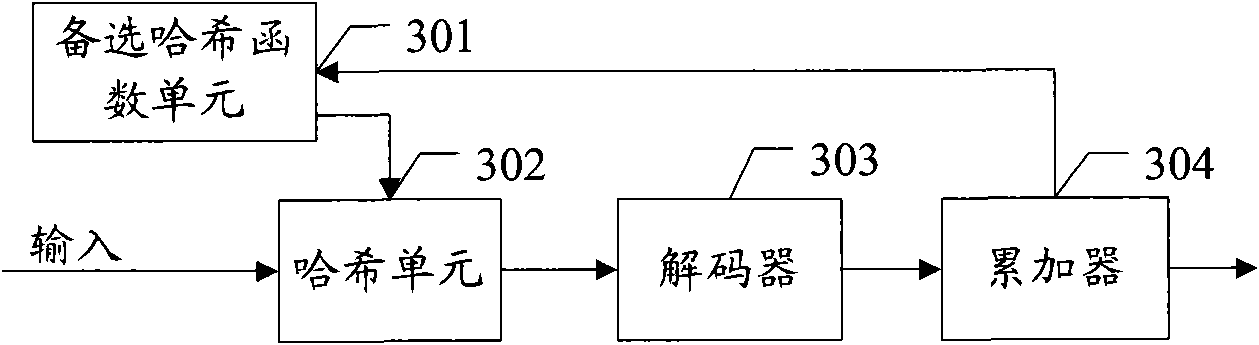
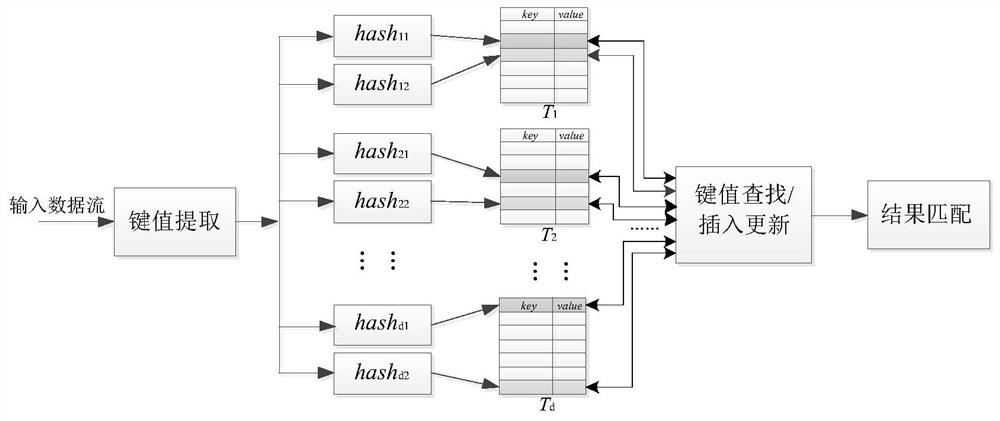
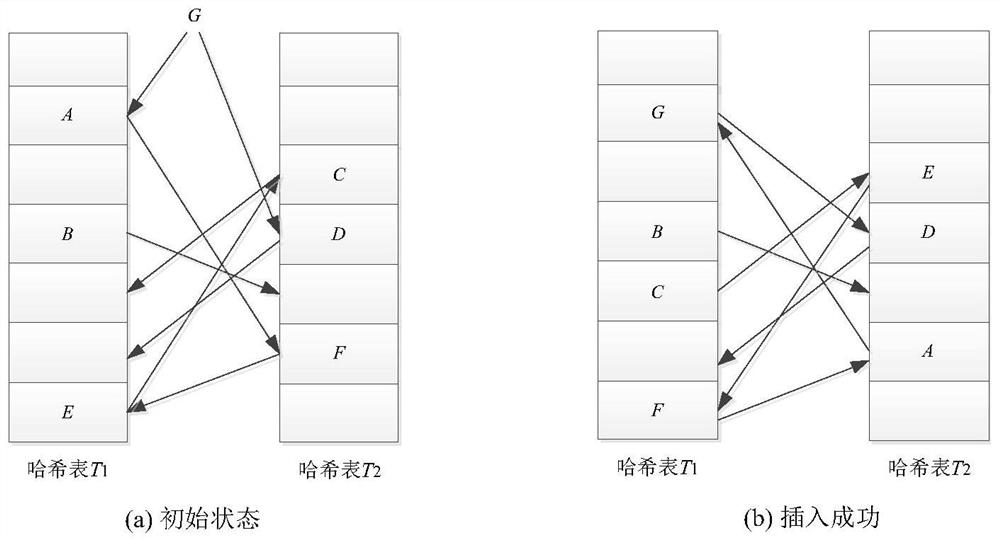
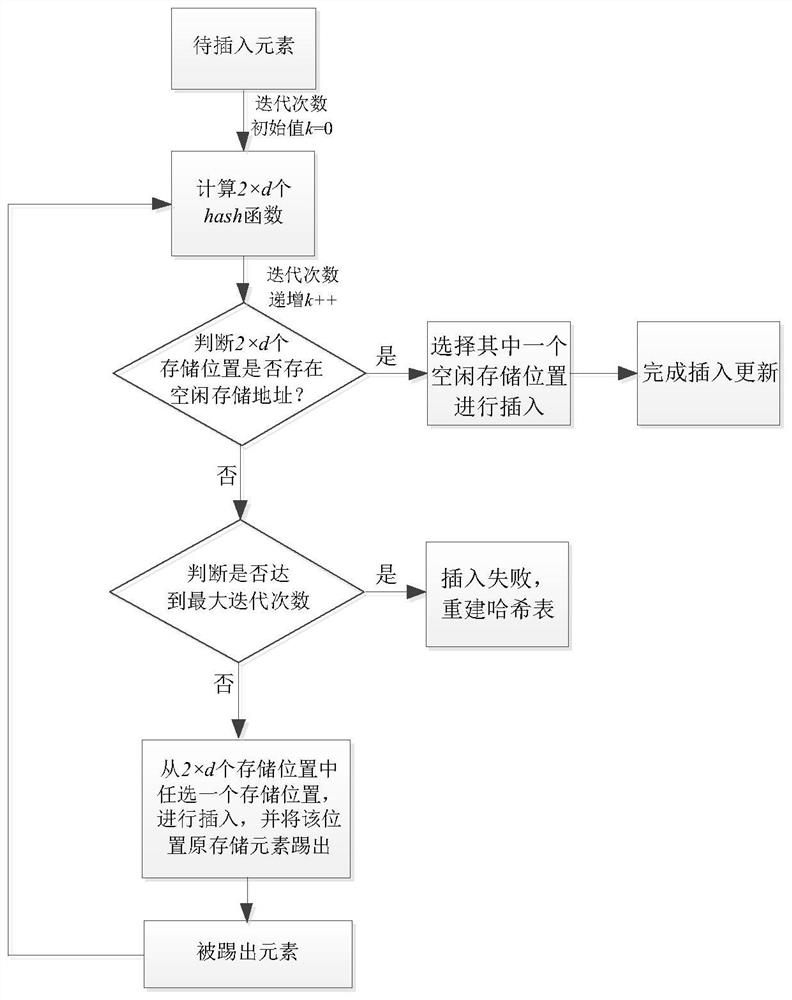
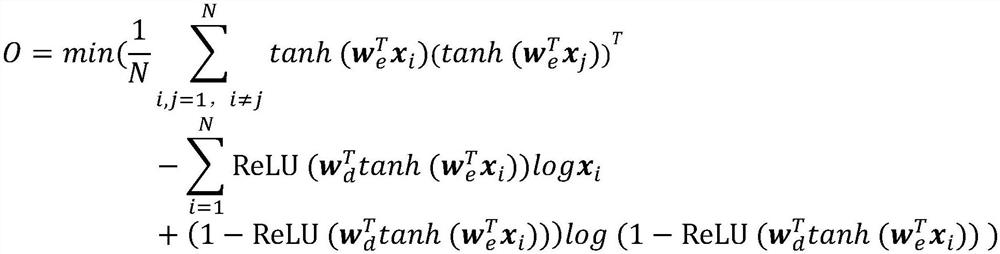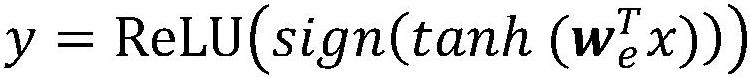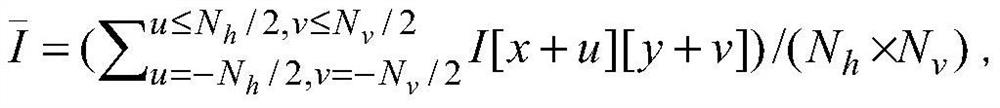Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
53 results about "HashClash" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
HashClash was a distributed computing project to find collisions in the MD5 hash algorithm. It was based at Department of Mathematics and Computer Science at the Eindhoven University of Technology, and Marc Stevens initiated the project as part of his master's degree thesis.
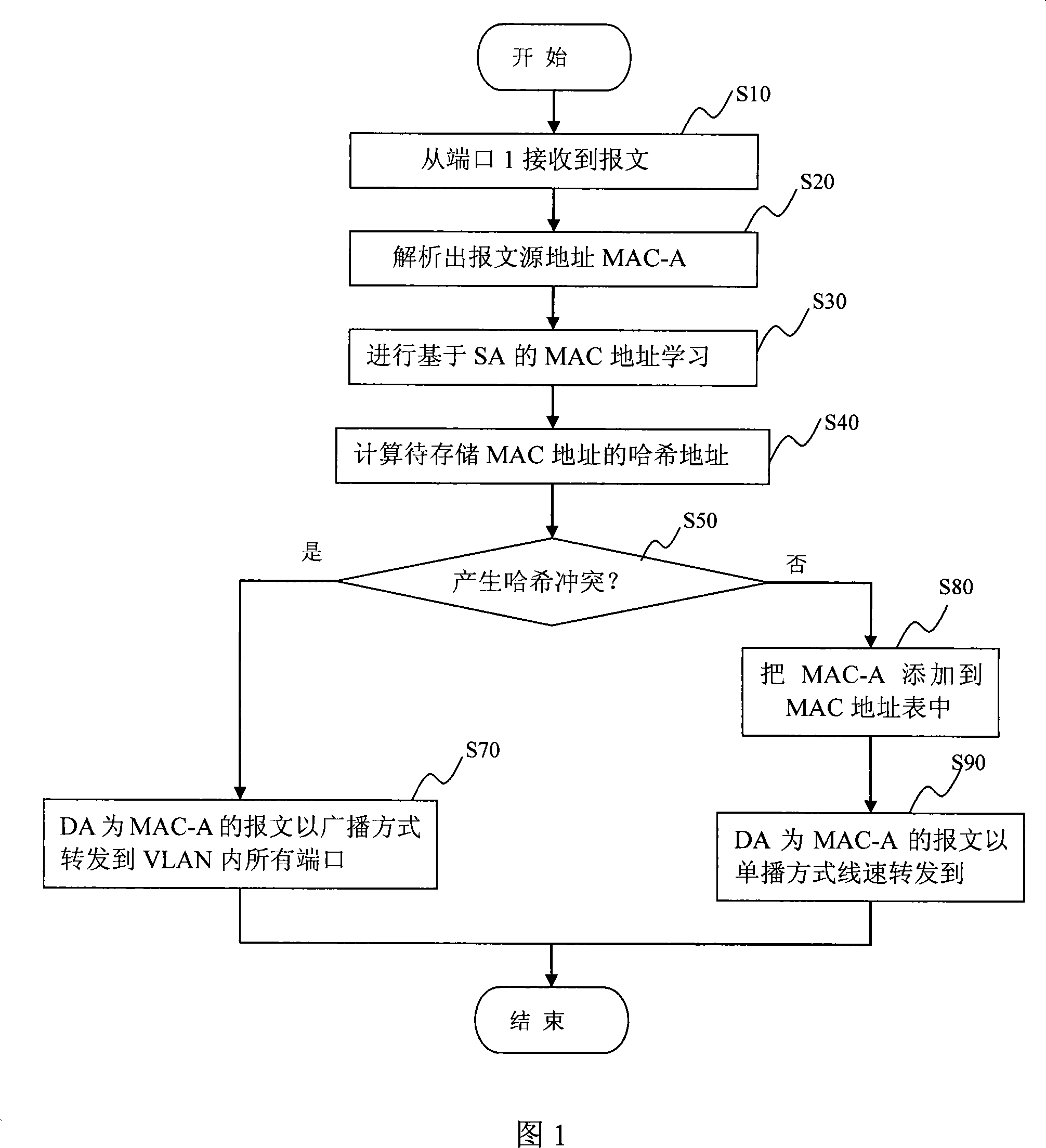
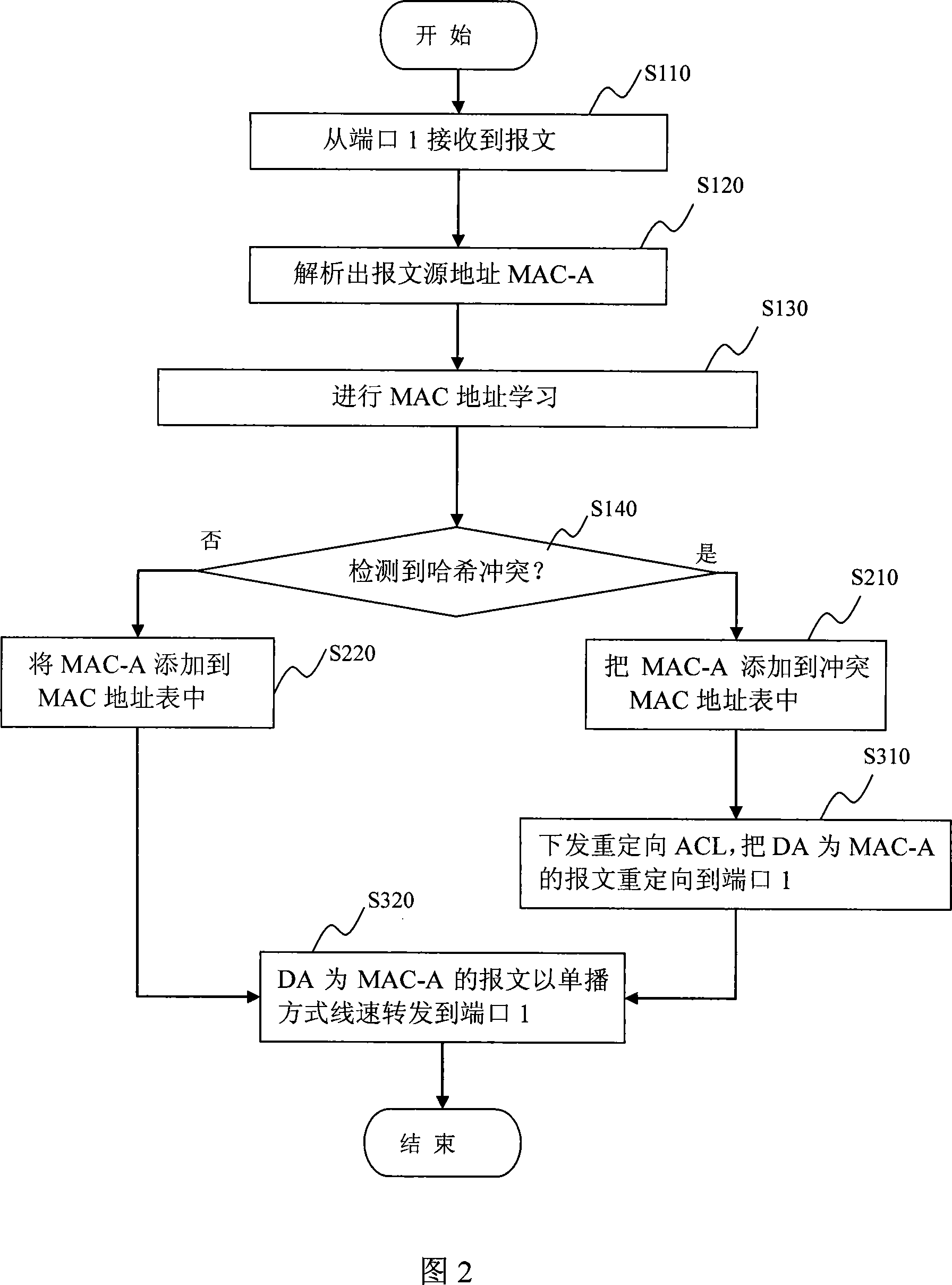
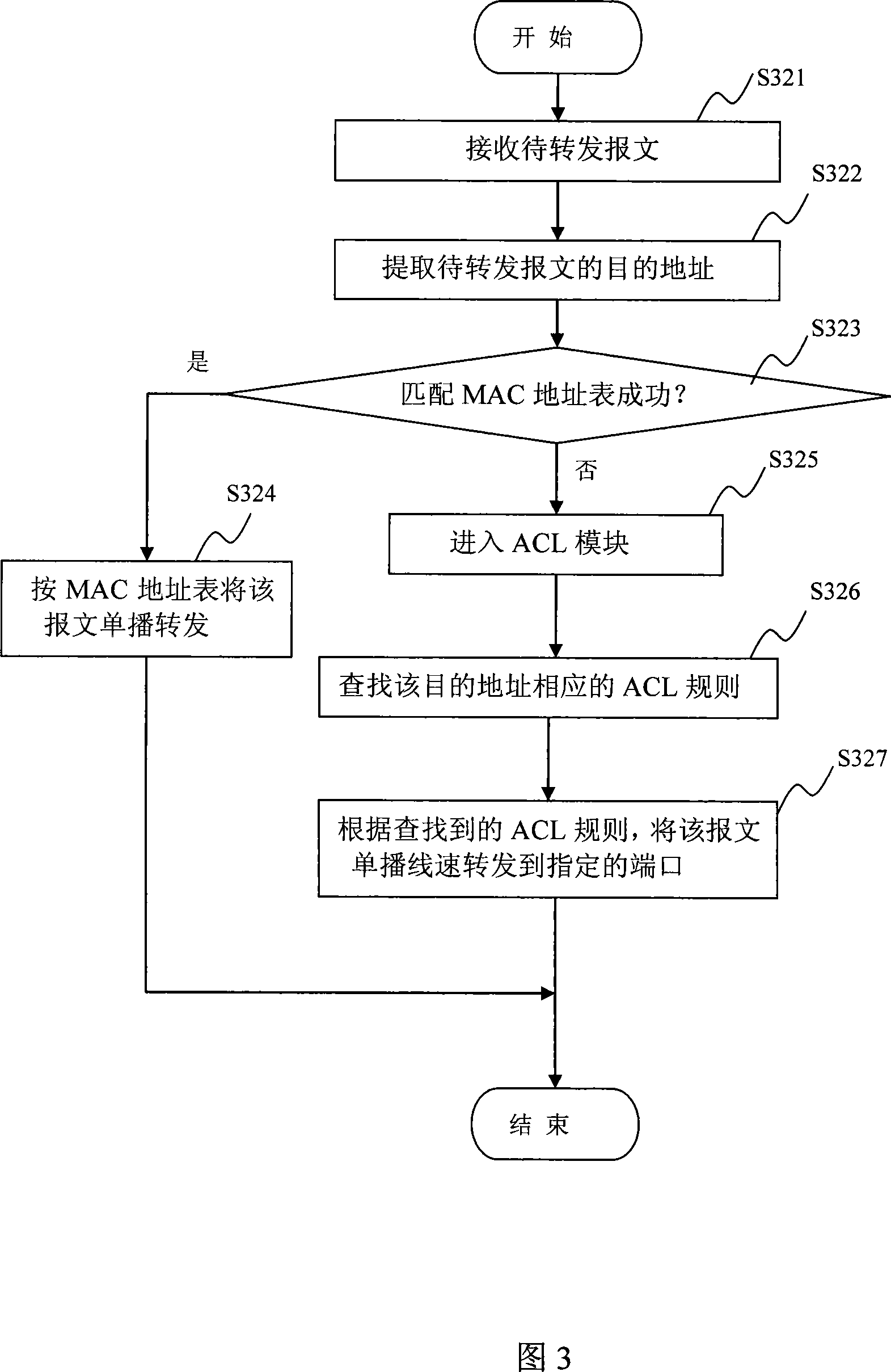
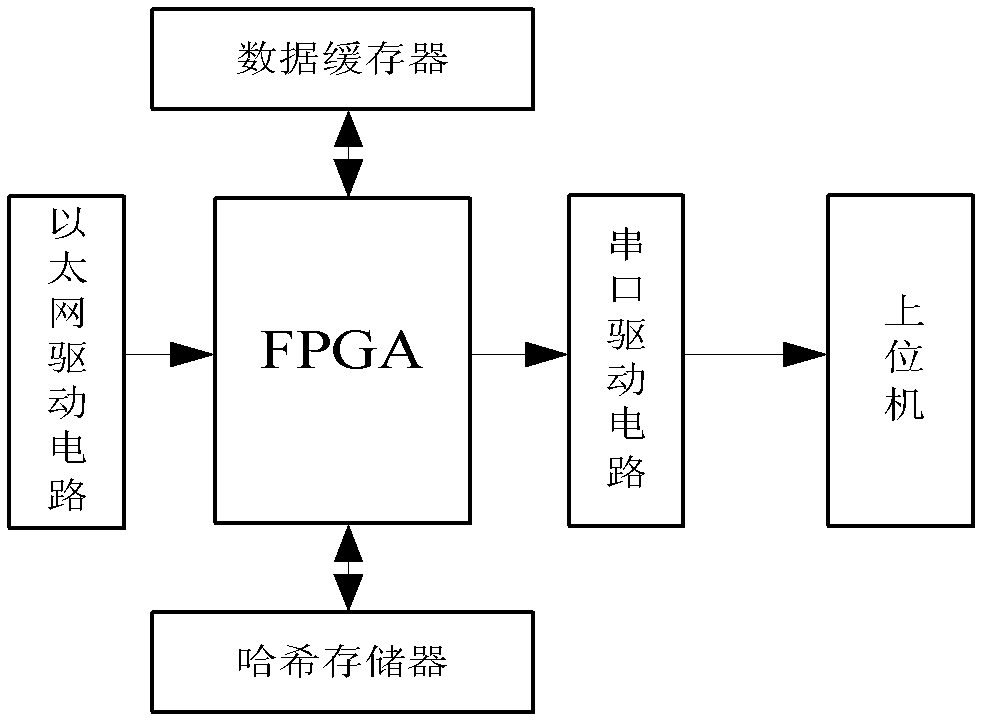
Apparatus and method for solving hash collision and exchange equipment with the same
ActiveCN101232444AIncrease profitPrevent unknown unicast traffic from occupying effective network bandwidthData switching networksReal-time computingWire speed
The invention discloses a Hash collision solution method, which includes the following steps of detecting Hash collision of a MAC address during learning process of the MAC address; storing the collision MAC address in a collision MAC address table in a collision table module except for an address table module; and carrying out unicast wire-speed forwarding to a message with a target address as a collision MAC address according to the collision MAC address. A Hash collision solution device and an exchange device including the same are further provided. Owing to the Hash collision solution method of the invention, the message with the target address as the collision MAC address can be unicast wire-speed forwarded so as to improve utilization ratio of port band width.
Owner:NEW H3C TECH CO LTD
Field programmable gate array-based (FPGA-based) intrusion detection system and method
InactiveCN102571494AReduce consumptionEasy to handleData switching networksIntrusion detection systemBinary tree
The invention relates to a field programmable gate array-based (FPGA-based) intrusion detection system and a FPGA-based intrusion detection method and belongs to the technical field of network security. The invention is characterized in that FPGA-based intrusion detection method is designed and realized; the processing performance is promoted by a realization mode of a hardware circuit; packet classification is realized by selecting a binary tree structure packet classification algorithm; character matching is realized by adopting an exclusive or (XOR) Hash algorithm which is suitable for FPGA processing; the rule updating is realized through performing addition or correction on the basis of the original intrusion rule realization logic; and Hash collision is eliminated through a method of performing independent matching on the Hash collision.
Owner:NORTHEASTERN UNIV
Method and system for processing Hash collision
InactiveCN102880724AAvoid hash collisionsReduce the incidence of hash collisionsSpecial data processing applicationsHash functionAlgorithm
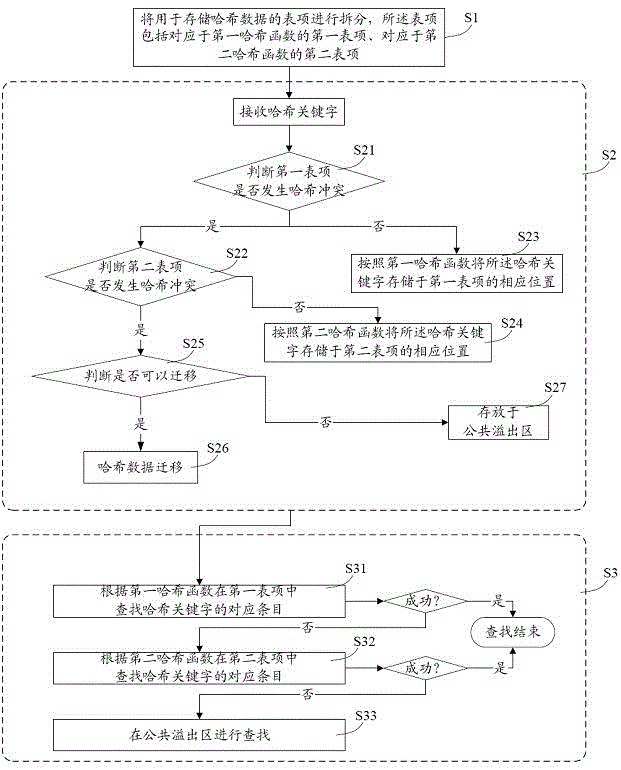
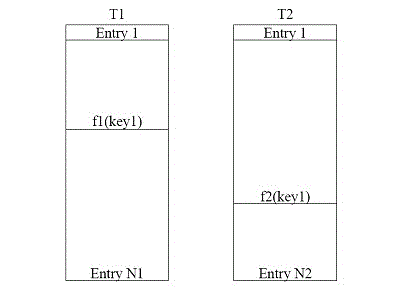
The invention provides a method and a system for processing Hash collision. The method includes separating list items which include a first list item corresponding a first Hash function and a second list item corresponding to a second Hash function and store Hash data; receiving Hash key words and judging whether the Hash collision exists or not, if collision exists in the first list item, storing the Hash key words to the corresponding position of the second list item according to the second Hash function; if no collision exists, storing the Hash key words into the corresponding position of the first list item according to the first Hash function; searching clauses corresponding to the Hash key words sequentially in the first list item and the second list item according to the first Hash function and the second Hash function. On the basis of keeping hardware cost constant, incidence rate of the Hash collision is decrease effectively.
Owner:SUZHOU CENTEC COMM CO LTD
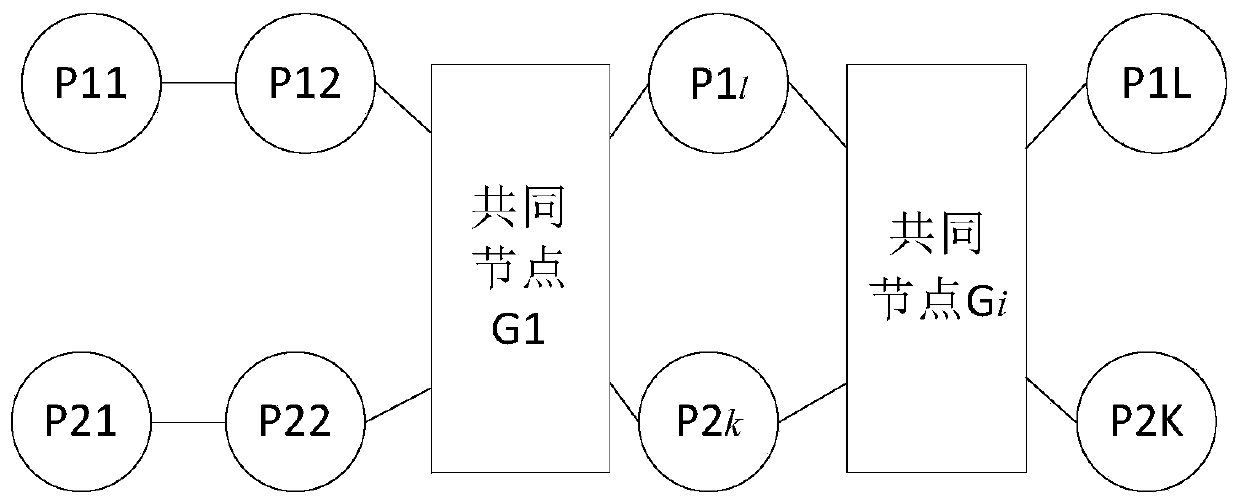
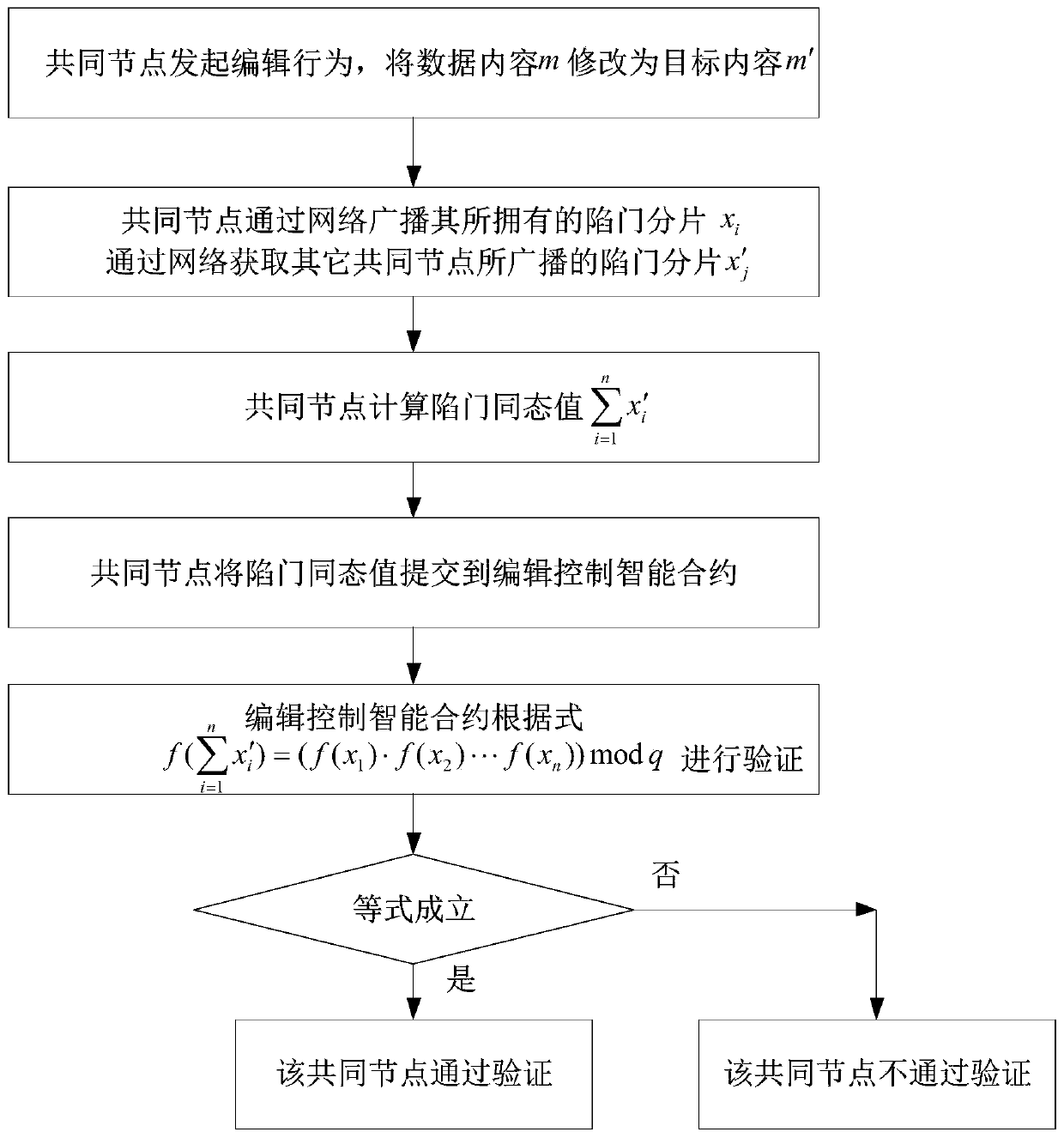
Editable block chain system
ActiveCN111460497AIncrease opennessMeet the needs of modificationDigital data protectionSmart contractTrap door
The invention discloses an editable block chain system, which comprises a first chain and a second chain, wherein the first chain and the second chain are connected through a common node; wherein thefirst chain has an editing control smart contract; wherein the common node is provided with a trap door fragment, and the trap door fragment is used for synthesizing a trap door; the common node is used for initiating an editing behavior, synthesizing a trap door according to the trap door fragment, verifying the trap door through the editing control smart contract, calculating a hash conflict value according to the original content, the original random number and the target content after verification is passed, publishing the target content and the hash conflict value to the second chain; andenabling a node in the second chain to verify the target content and the hash conflict value, and replaces the original content with the target content if the target content and the hash conflict value pass the verification. The system has the advantages that the requirement for data storage safety can be met, and the requirement for data modification under specific conditions can also be met.
Owner:CENT SOUTH UNIV
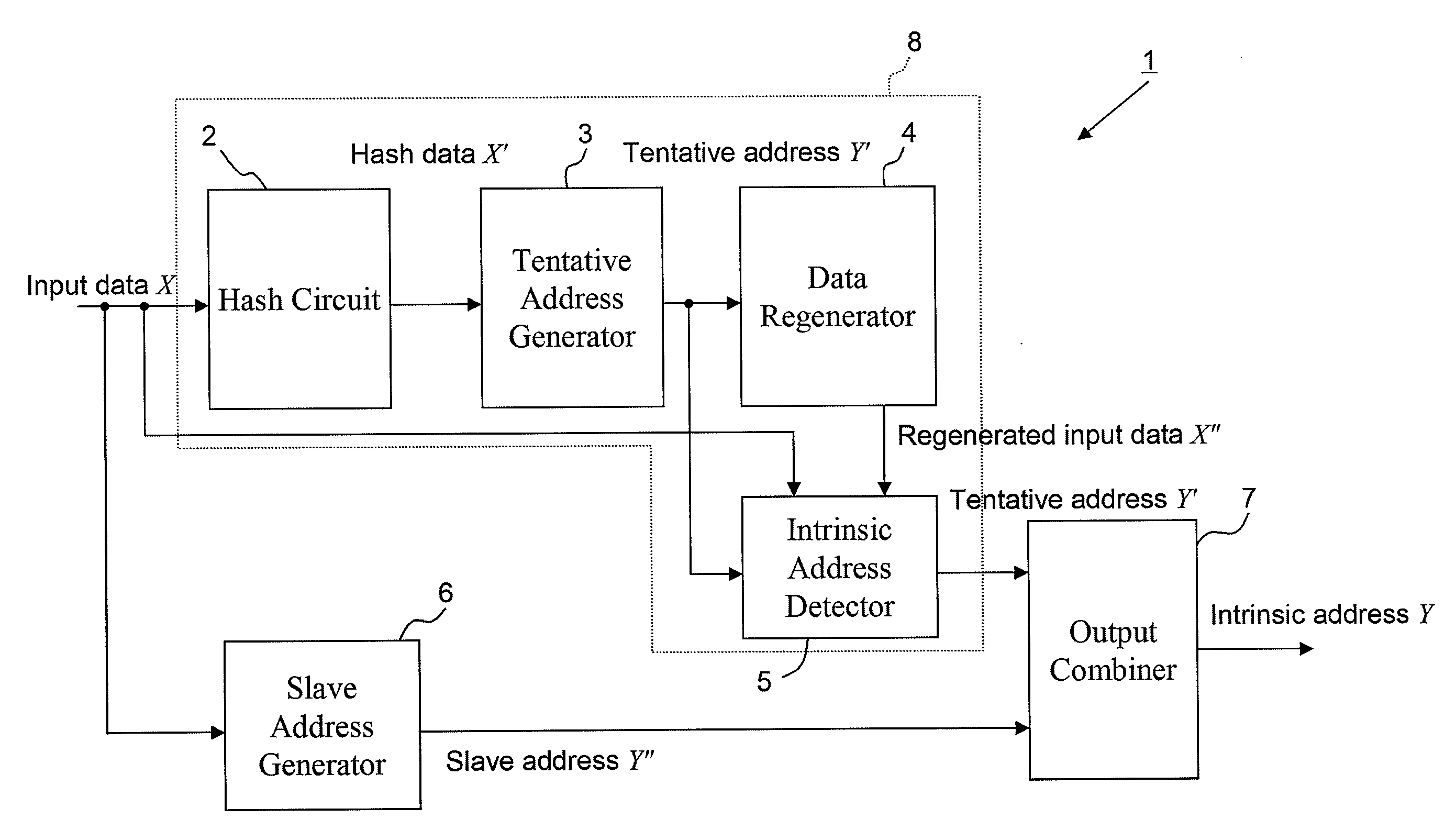
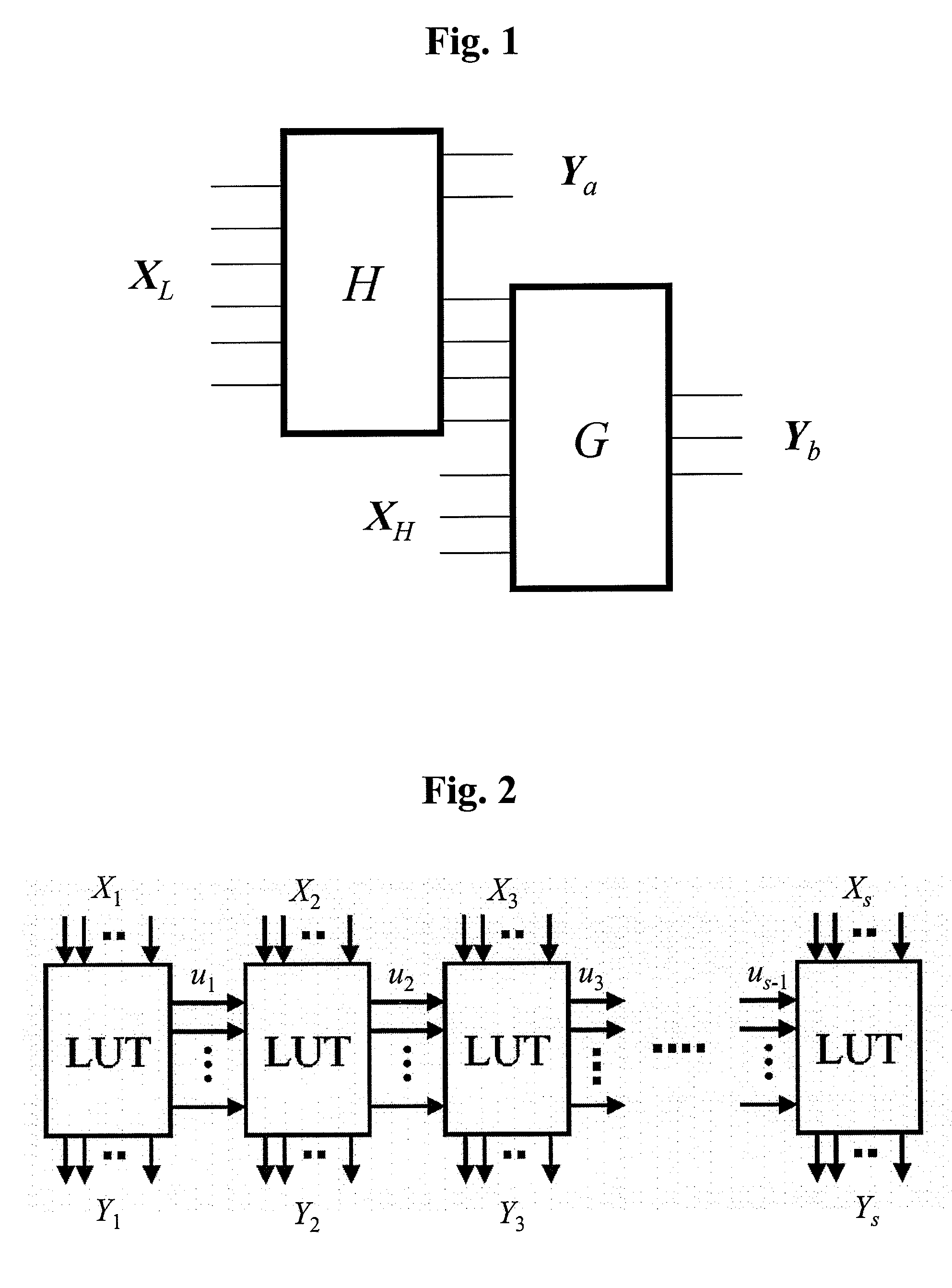
Address generator
InactiveUS20100228947A1Network degradationSuppress power consumptionEnergy efficient ICTDigital data information retrievalAddress generatorComputer science
The address generator has a hash network for producing hashed Y1, which is obtained by hushing X1, to an input vector X=(X1, X2), a tentative address generator Y1 for making an address generation function f(X) to a tentative address A′ when no hash collision occurs and otherwise making one of unique addresses A to A′, a data regenerator for producing X″=f−1(A′), a unique address generator for producing A′ when X″ coincides with X and otherwise producing “invalid value”, a complementary address generator for producing (X) to X, to which the unique address generator produces “invalid value”, and otherwise producing “invalid value”, and an output combiner which produces, when the outputs of the unique address generator and the complementary address generator have values other than the “invalid value”, the values as a unique address A and otherwise produces “invalid value” as A.
Owner:NAT UNIV CORP KYUSHU INST OF TECH (JP)
Method for selecting hash function, and method and device for storing and searching routing table
ActiveCN101667958AAvoid confictSmall footprintDigital data information retrievalError preventionHash functionRouting table
Owner:HUAWEI TECH CO LTD
Data structure for hash operation and hash table storage and query method based on data structure
PendingCN111625534AImprove storage efficiencyImprove update efficiencySpecial data processing applicationsDatabase indexingAlgorithmMemory bank
The invention belongs to the field of computer hash data structures, in particular to a data structure for hash operation and a hash table storage and query method based on the structure. In order toensure the query efficiency, a dual-port memory bank is adopted for hardware implementation, the content of two addresses of the memory bank can be read at the same time, key value comparison can be completed within the determined time, and the method is suitable for achieving efficient query in an assembly line mode. More candidate positions are provided through more hash operations, the probability of hash conflicts is reduced, the insertion, storage and updating efficiency of hash table entries is improved, dynamic change of hash table entry capacity is supported, space waste or performancereduction caused by table entry insertion operation is avoided, and the method is suitable for applications with unknown and constantly changing hash table entries. A CRC algorithm is adopted as a hash function, a hash calculation result has good uniqueness, the hash calculation result can be obtained on the basis of XOR exclusive-OR operation and a parallel pipeline implementation structure during specific implementation, and hardware design implementation is facilitated.
Owner:PLA STRATEGIC SUPPORT FORCE INFORMATION ENG UNIV PLA SSF IEU
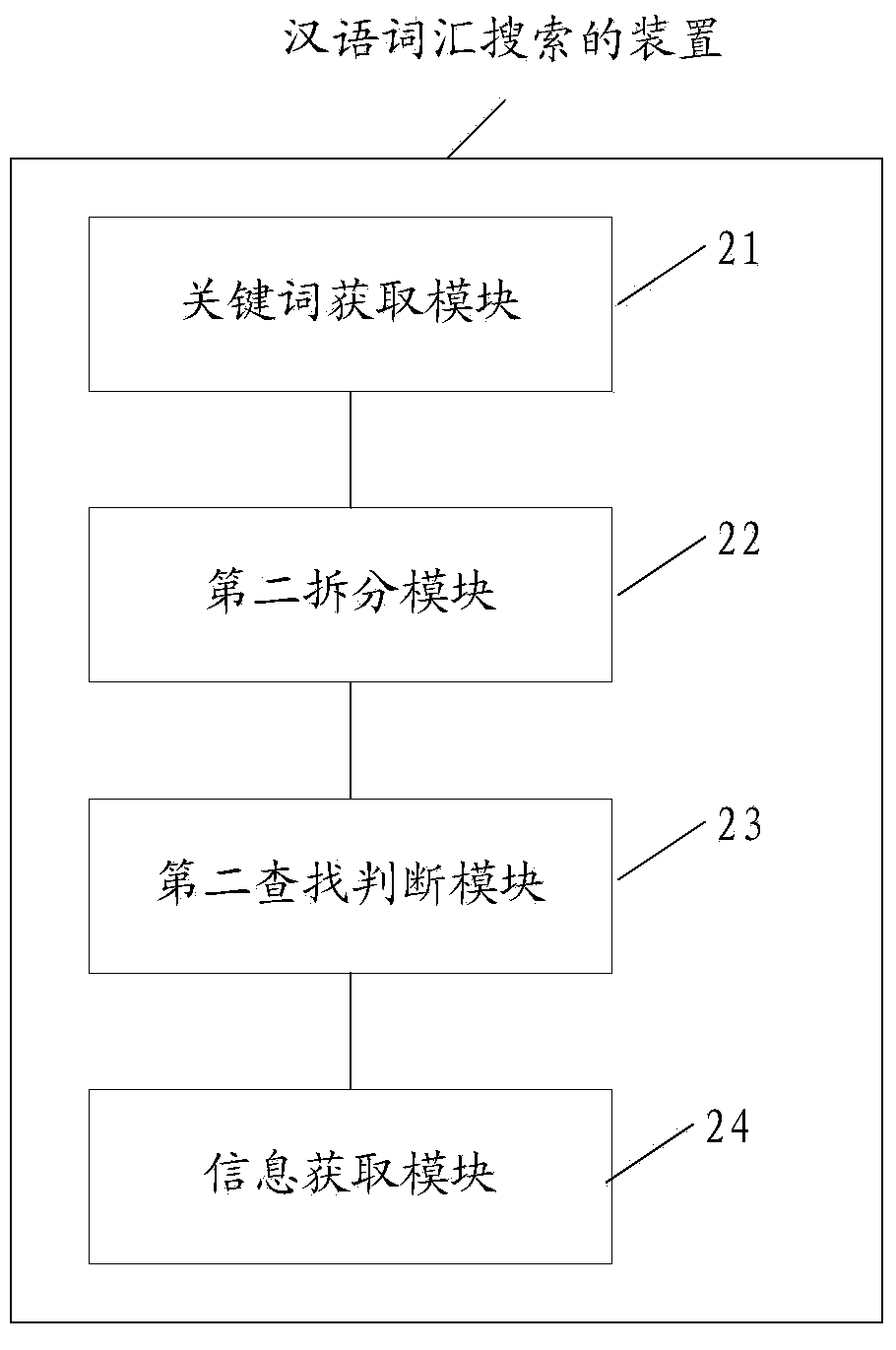
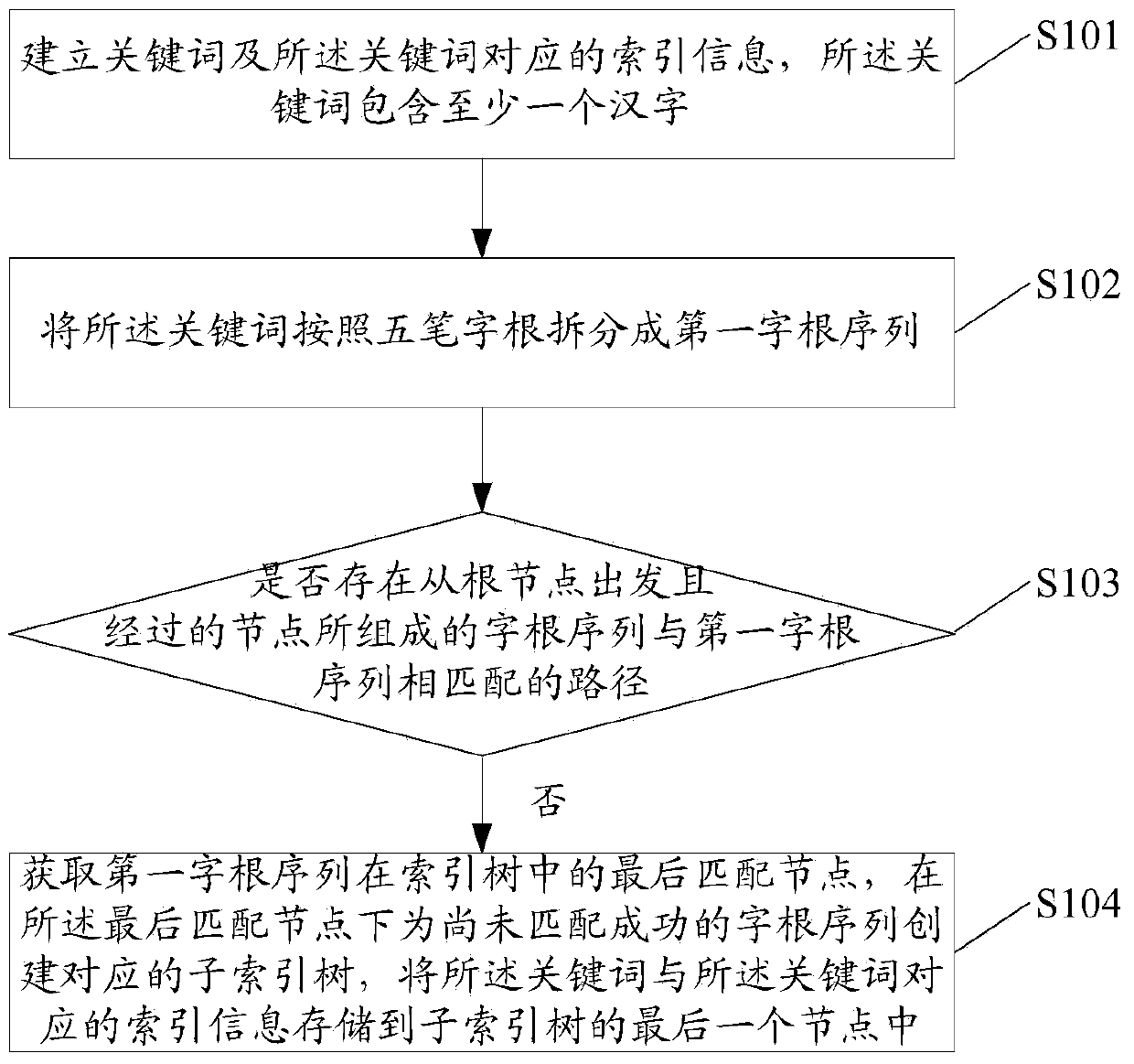
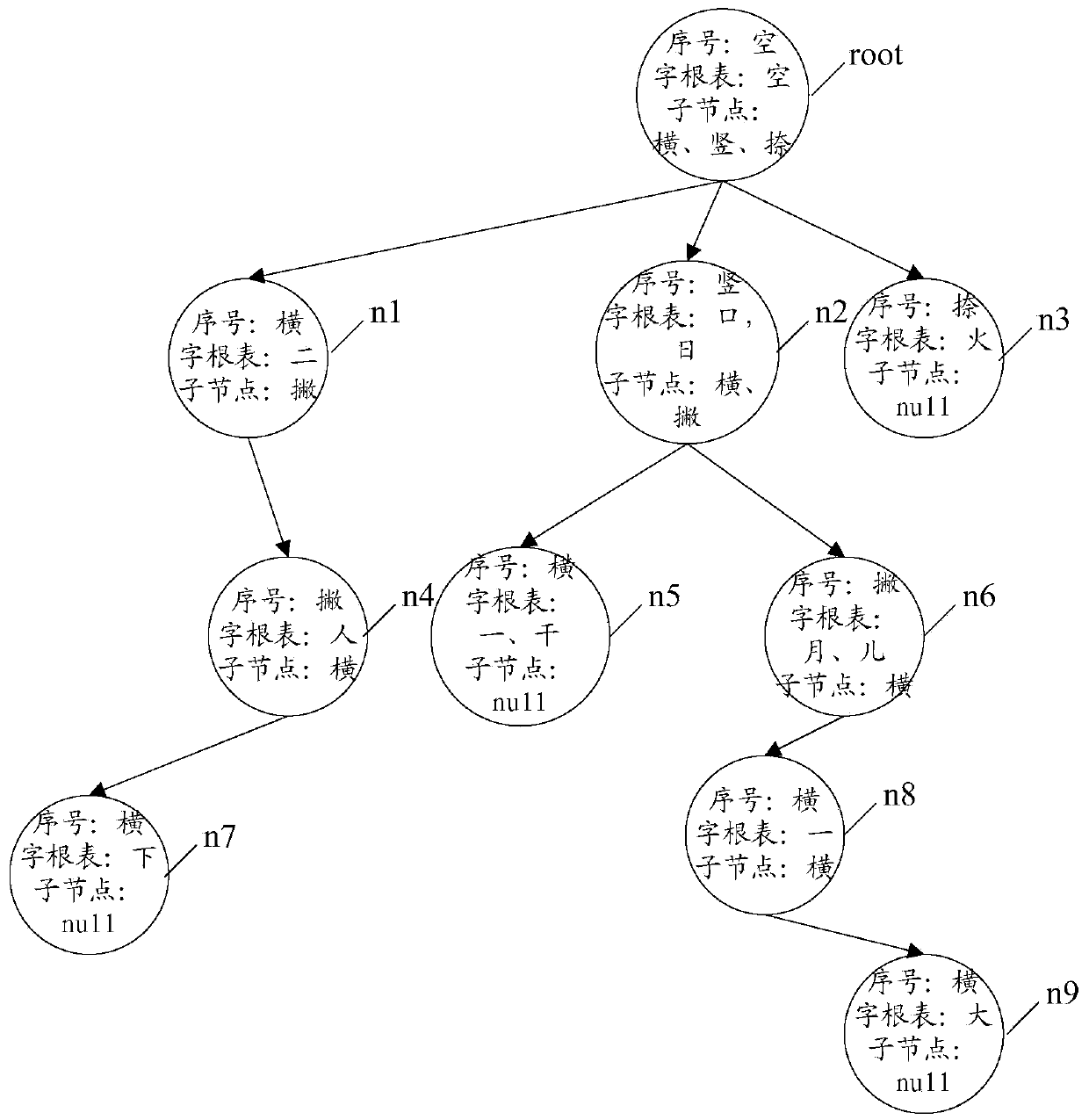
Index tree building method, Chinese vocabulary searching method and related device
InactiveCN103514287AEasy to buildQuick searchWeb data indexingSpecial data processing applicationsData miningChinese characters
Owner:SHENZHEN LONG VISION
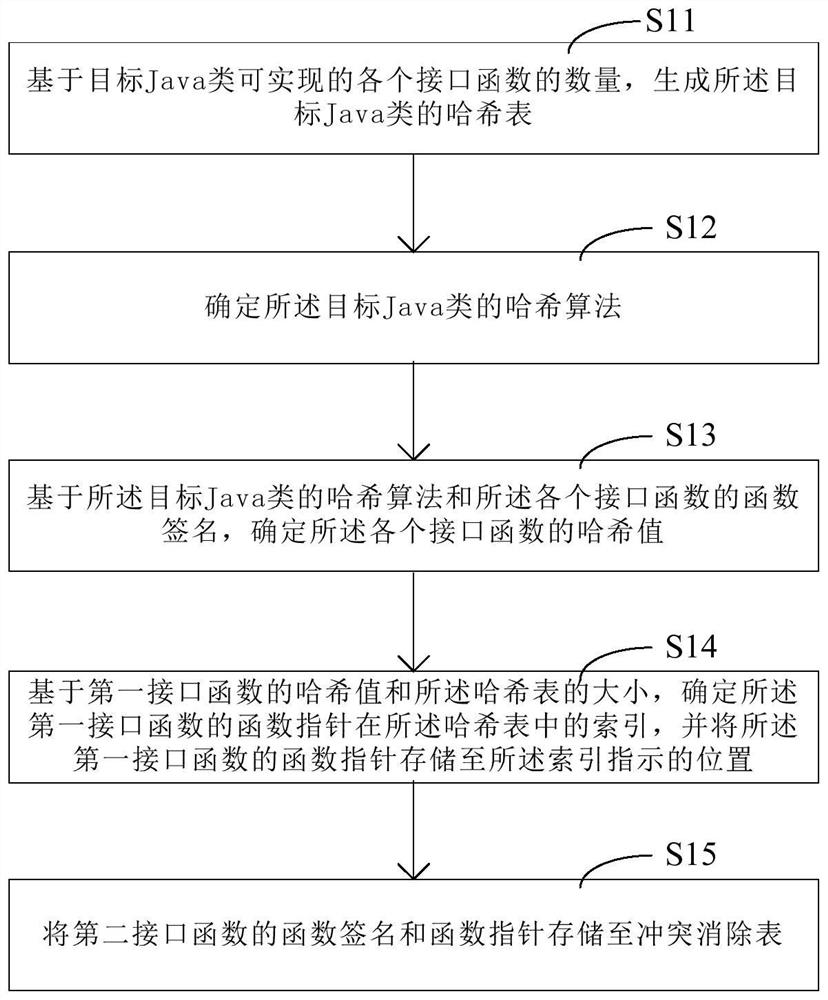
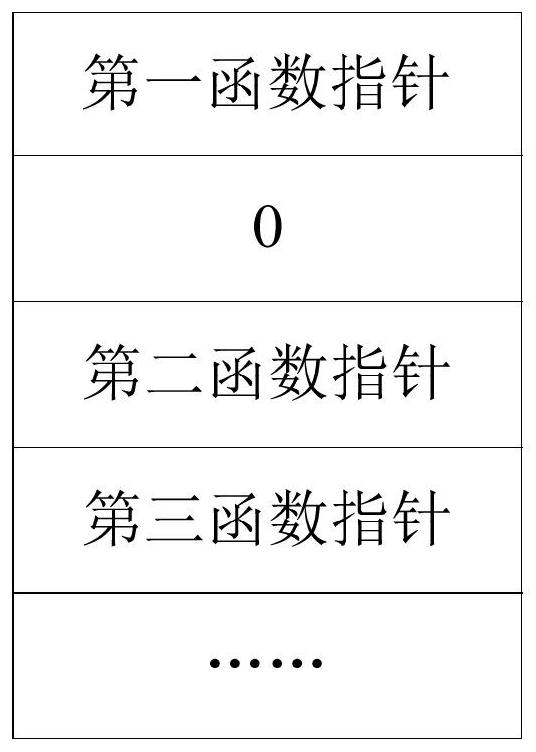
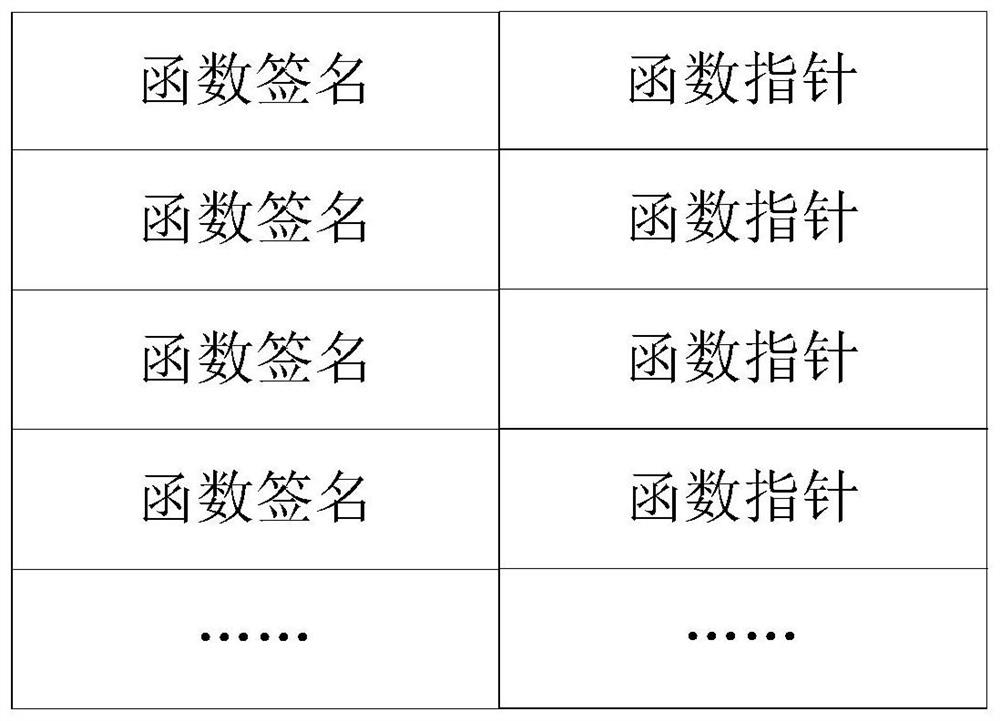
Interface method table generation method and device and function pointer query method and device
PendingCN111638925ASolve wasteSolve the problem of decreased query efficiencyExecution paradigmsHashClashTheoretical computer science
The embodiment of the invention discloses an interface method table generation method and device and a function pointer query method and device. The interface method table generation method comprisesthe following steps of based on the number of interface functions realized by a target Java class, generating a hash table of the target Java class, then, based on a hash algorithm of the target Javaclass and function signatures of all interface functions; determining a hash value of the interface function; determining an index of a function pointer of the first interface function in a hash table, storing a function pointer of the first interface function to a position indicated by the index, wherein the first interface function is an interface function having no hash conflict with other interface functions, storing a function signature and a function pointer of a second interface function in a conflict elimination table, and the second interface function is an interface function having hash conflict with other interface functions. According to the scheme, when the hash table is generated, the size of the hash table is determined according to the product of the number of the interfacefunctions which can be realized by the target Java class and the preset coefficient, so that the problem that the hash table is too large or too small is avoided.
Owner:HUAWEI TECH CO LTD
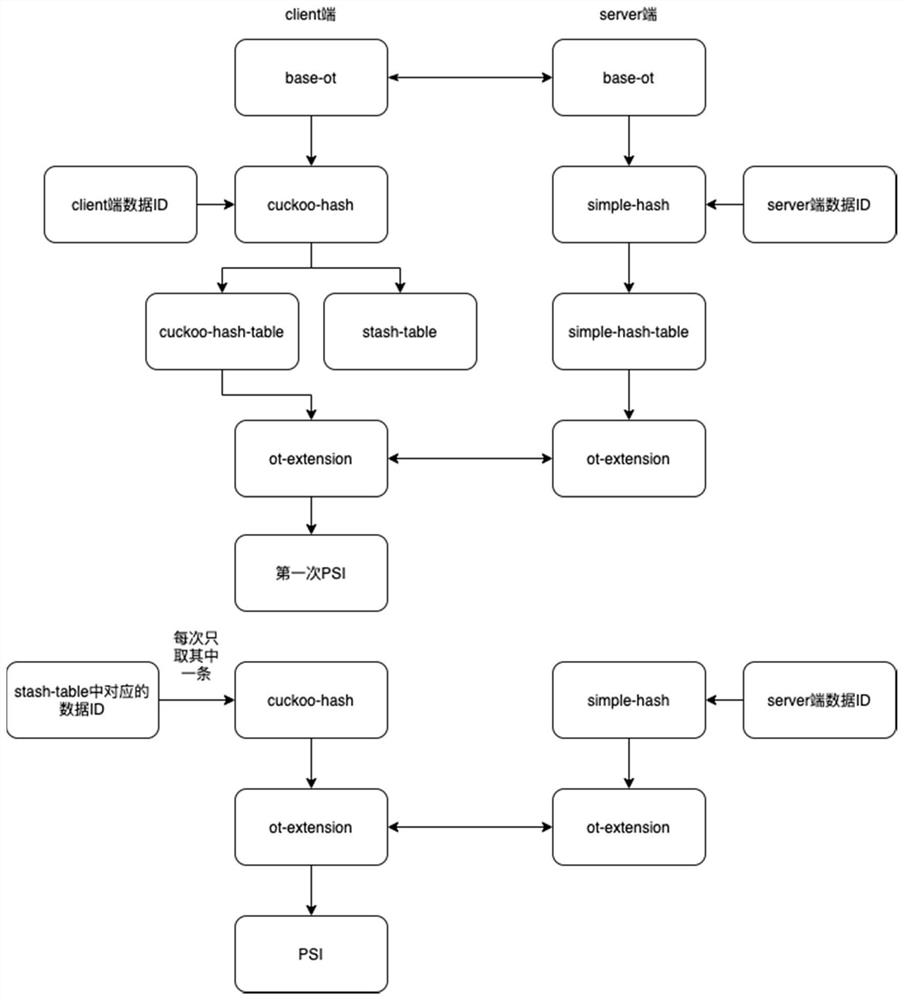
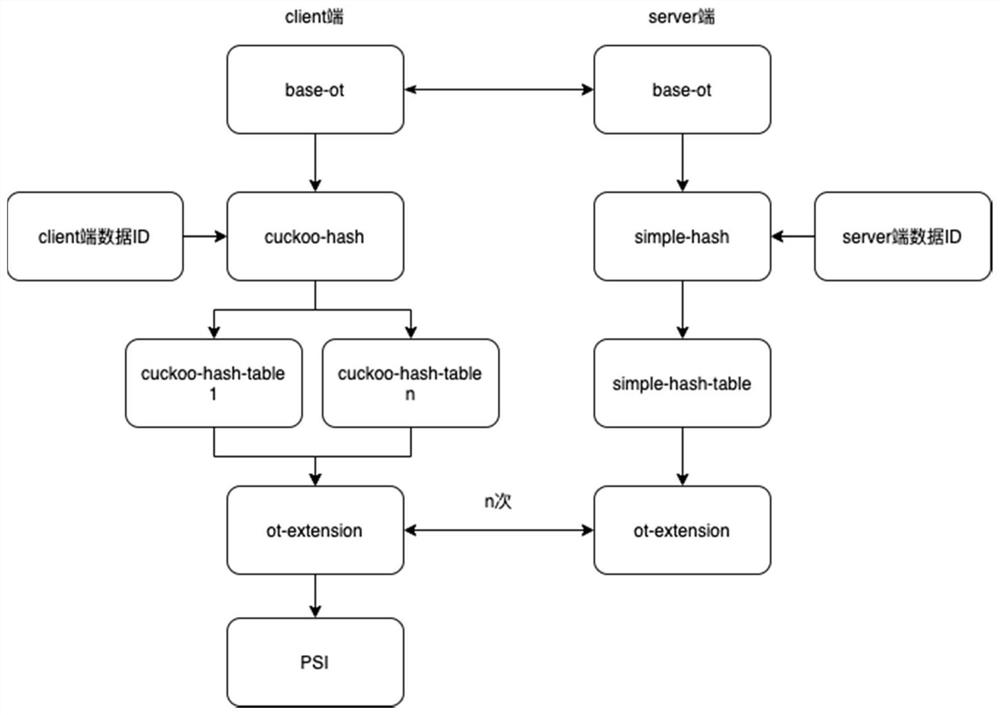
Scalable-ot-based privacy set intersection method and device
PendingCN113961961ASmall amount of calculationImprove computing efficiencyDigital data protectionOther databases indexingAlgorithmTheoretical computer science
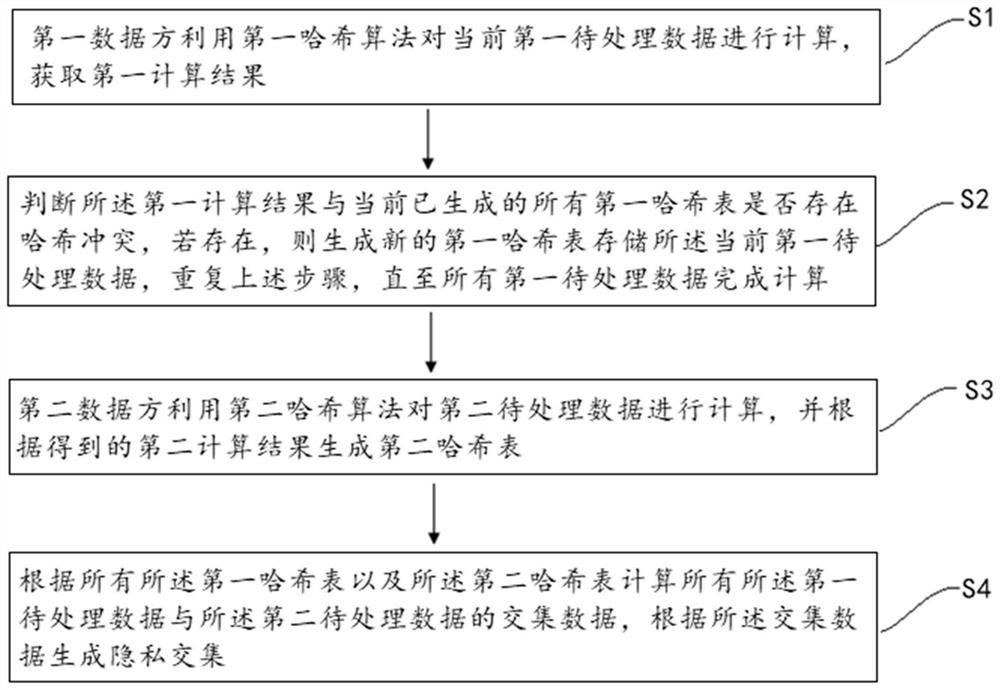
The invention discloses a scalable-ot-based privacy set intersection method and device, and the method comprises the steps that: a first data party calculates current first to-be-processed data through employing a first Hash algorithm, obtains a first calculation result, and judges whether the first calculation result has a Hash conflict with all currently generated first Hash tables or not; if the first calculation result has the Hash conflict with all currently generated first Hash tables, a new first hash table is generated to store the current first to-be-processed data; and the steps are repeated until all the first to-be-processed data are calculated, a second data party calculates second to-be-processed data through a second hash algorithm, a second hash table is generated according to an obtained second calculation result, intersection data of all the first to-be-processed data and the second to-be-processed data is calculated according to all the first hash tables and the second hash tables, and a privacy intersection is generated according to the intersection data. The situation that the intersection result is obtained by repeating the whole calculation process for many times can be avoided, the calculation amount of intersection is greatly reduced, the calculation efficiency is improved, and the whole calculation process is more concise.
Owner:百保上海科技有限公司
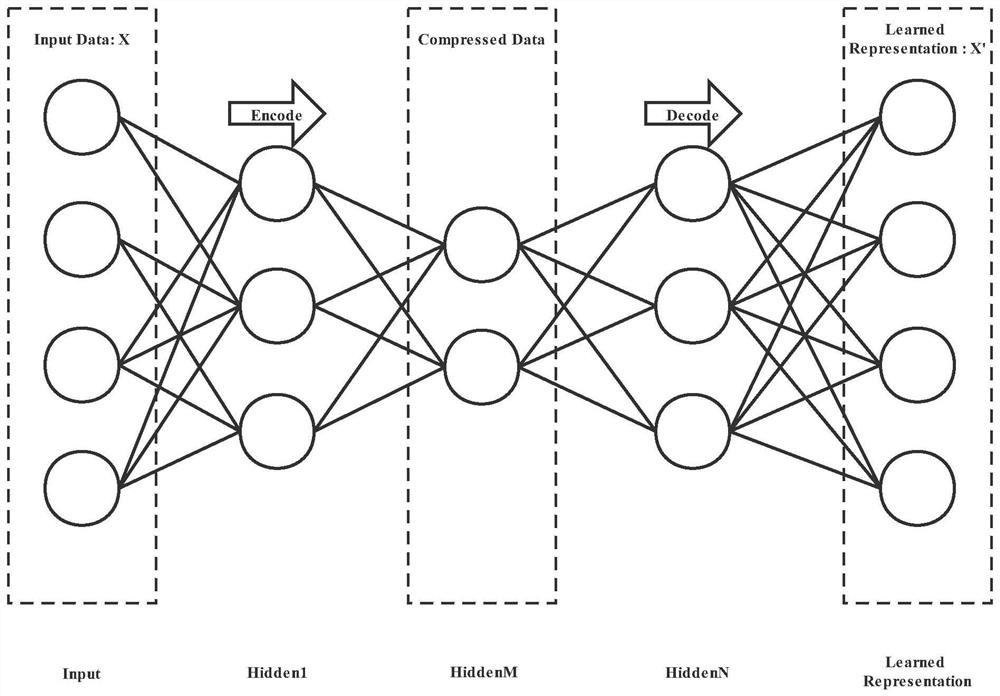
Learning type text hashing method based on auto-encoder
ActiveCN113449849AOperation time improvementImprove efficiencyNeural architecturesText database indexingHash functionData set
The invention discloses a learning type text hashing method based on an auto-encoder. The method comprises the following steps: firstly, constructing a training data set by utilizing actually collected text data and / or text data generated by a program; constructing a Hash function model of a five-layer auto-encoder structure, and training the Hash function model by using the training data set; and inputting the to-be-hashed text data into the Hash function model trained in the step 3 to obtain a Hash value of the to-be-hashed text data. According to the method, the machine learning method is used, the learning type hash function model is constructed to achieve hash of the text type data, compared with a traditional hash method, the method has the advantages that the hash conflict rate is low and improved hash operation time, improves text hash efficiency, and can be suitable for hash processing of large-scale text data.
Owner:GUILIN UNIV OF ELECTRONIC TECH
Method and apparatus for improving hash searching throughput in the event of hash collisions
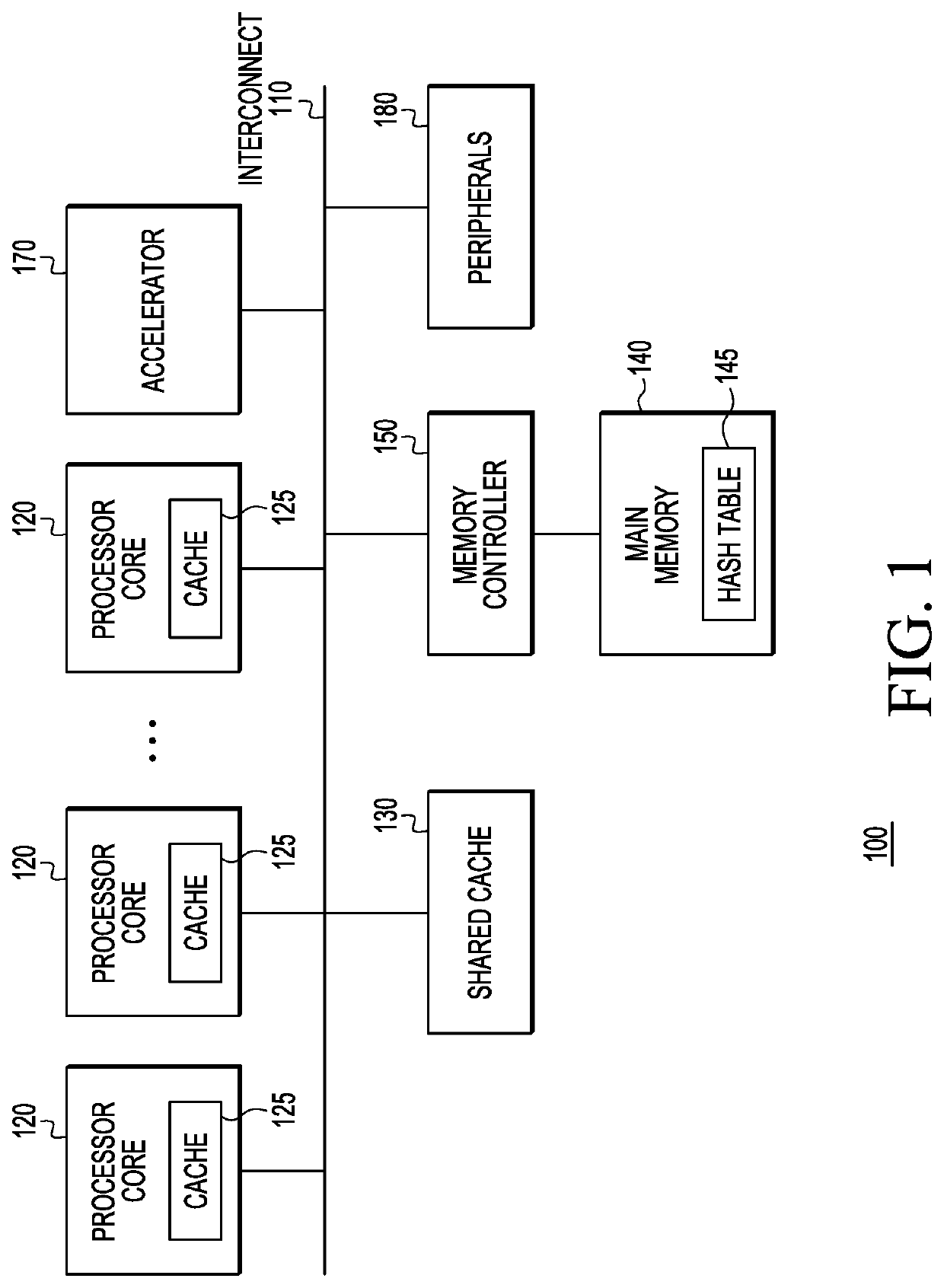
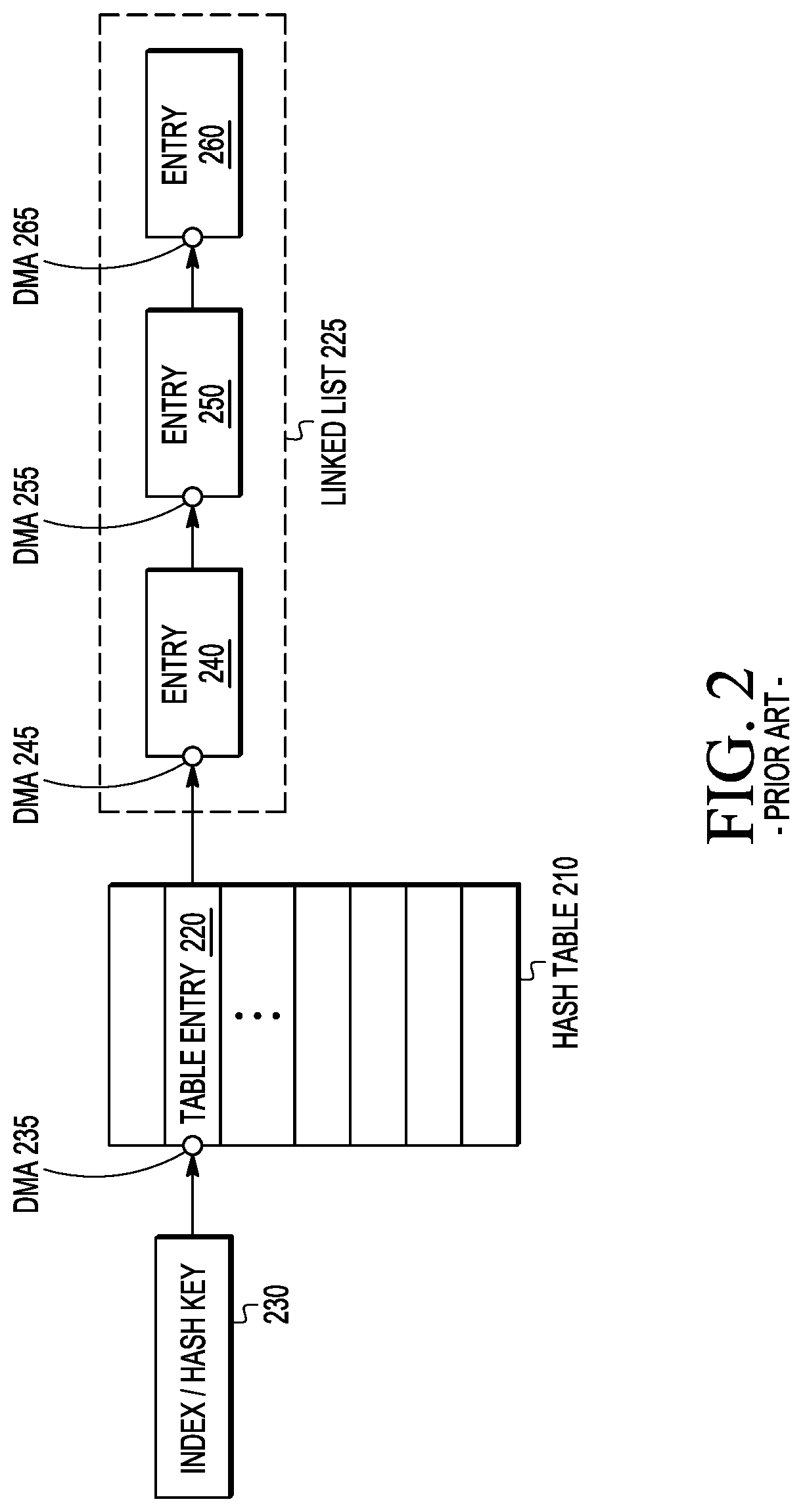
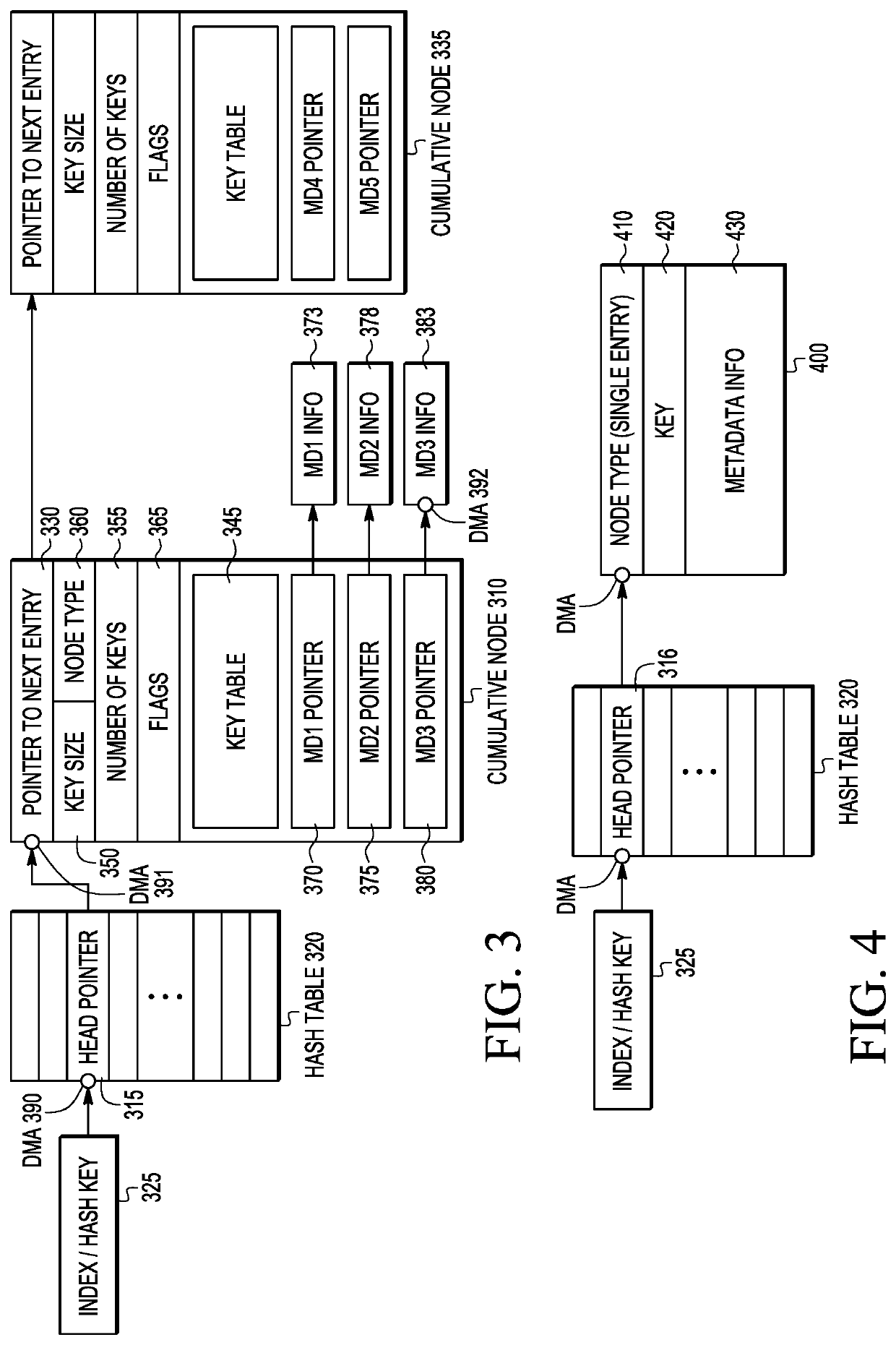
A hash table data structure is provided that reduces the number of DMA operations, and if possible, the number of key comparisons, needed to traverse the table entries to find an entry that matches a key, especially with a bucket having several collisions. A new hash table entry called a “cumulative node” is introduced, which stores keys into a “key table” within the entry and includes pointers to metadata associated with the keys. The number of entries stored in the cumulative node depends on the size of the cumulative node, key size, and the size of the pointer type.
Owner:NXP USA INC
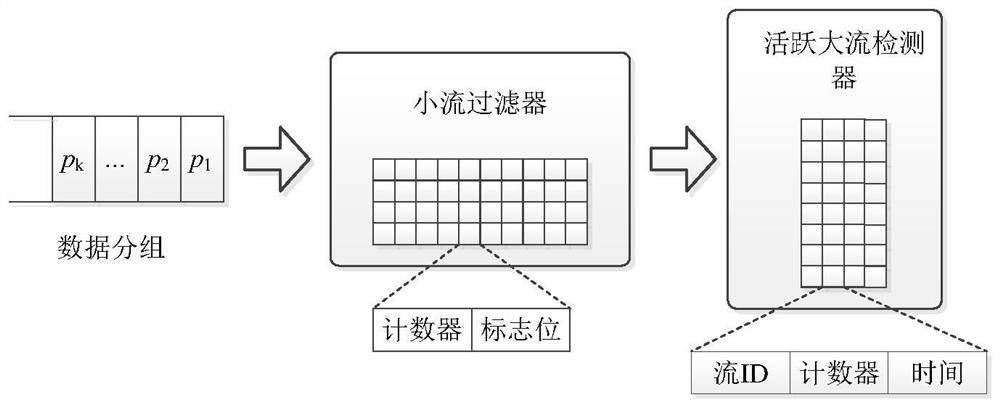
Accurate active large flow detection architecture and method based on small flow filtering
The invention discloses a small flow filtering-based active large flow accurate detection architecture and method, and the architecture comprises a small flow filter which is used for filtering most small flows in a network, reducing the resource overhead, and reducing the Hash conflict rate; and the active large flow detector is used for extracting the active large flow in the network and improving the identification precision of the active large flow. According to the method, the small flow filter is constructed by using the thought of cycle updating, so that the resource overhead is reduced, and meanwhile, the filter can continuously and effectively filter the small flow. Meanwhile, an active large flow detector is constructed based on a Hopscotch Hashing algorithm, and inactive flows are screened out through an LRU strategy while Hash conflicts are reduced, so that Top-k flows in the network are accurately identified.
Owner:CHANGSHA UNIVERSITY OF SCIENCE AND TECHNOLOGY
Data storage method, system and related device
InactiveCN111143288ASolve the problem of accidental deletionEnsure consistencyFile access structuresFile/folder operationsEngineeringData mining
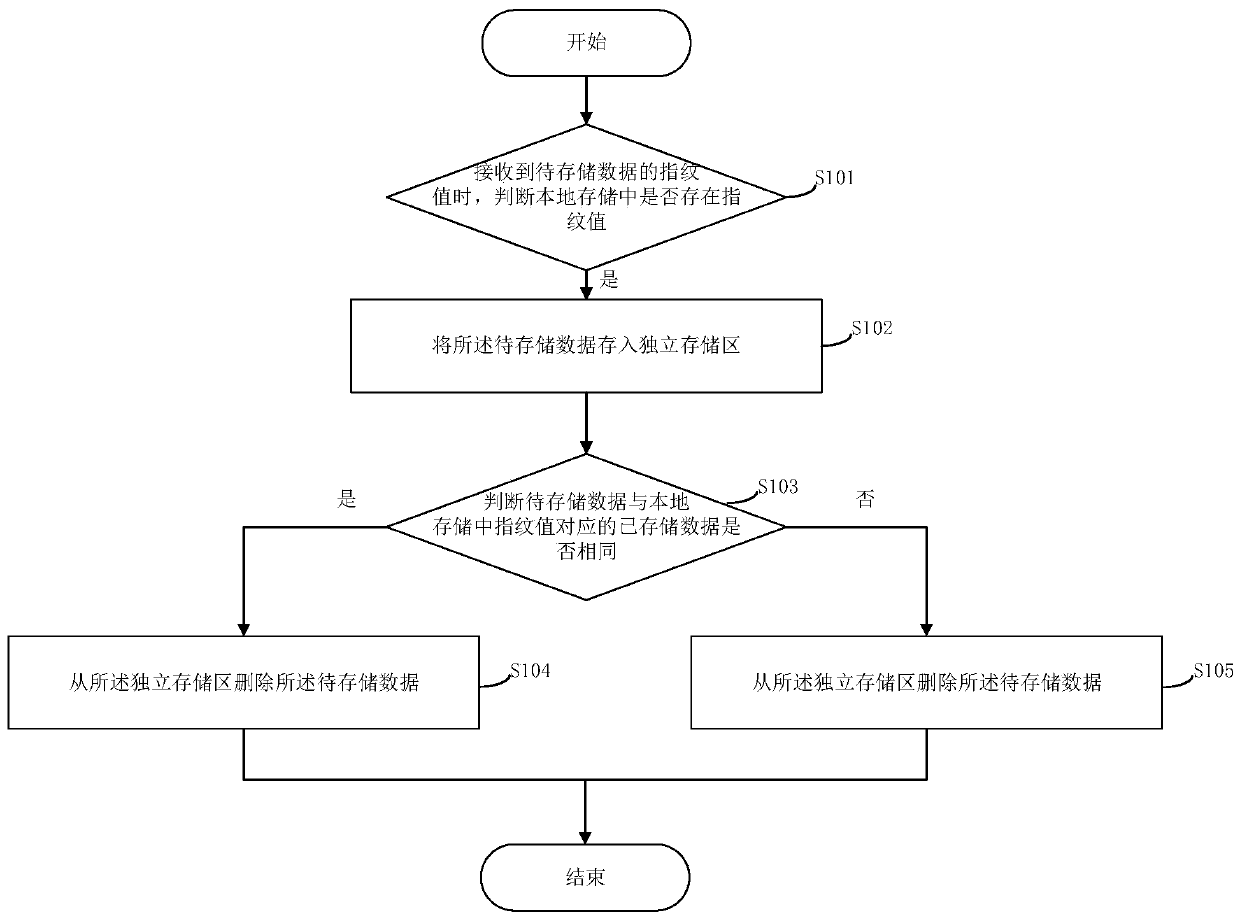
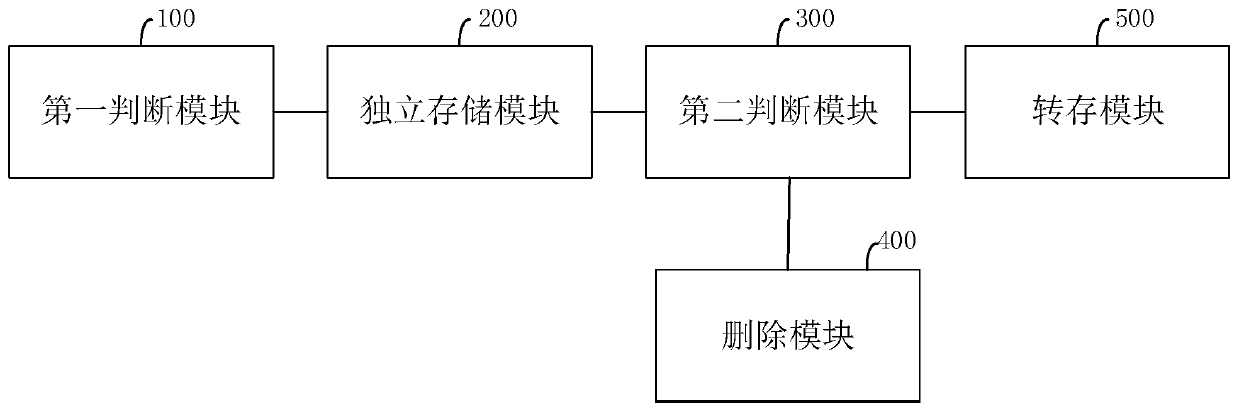
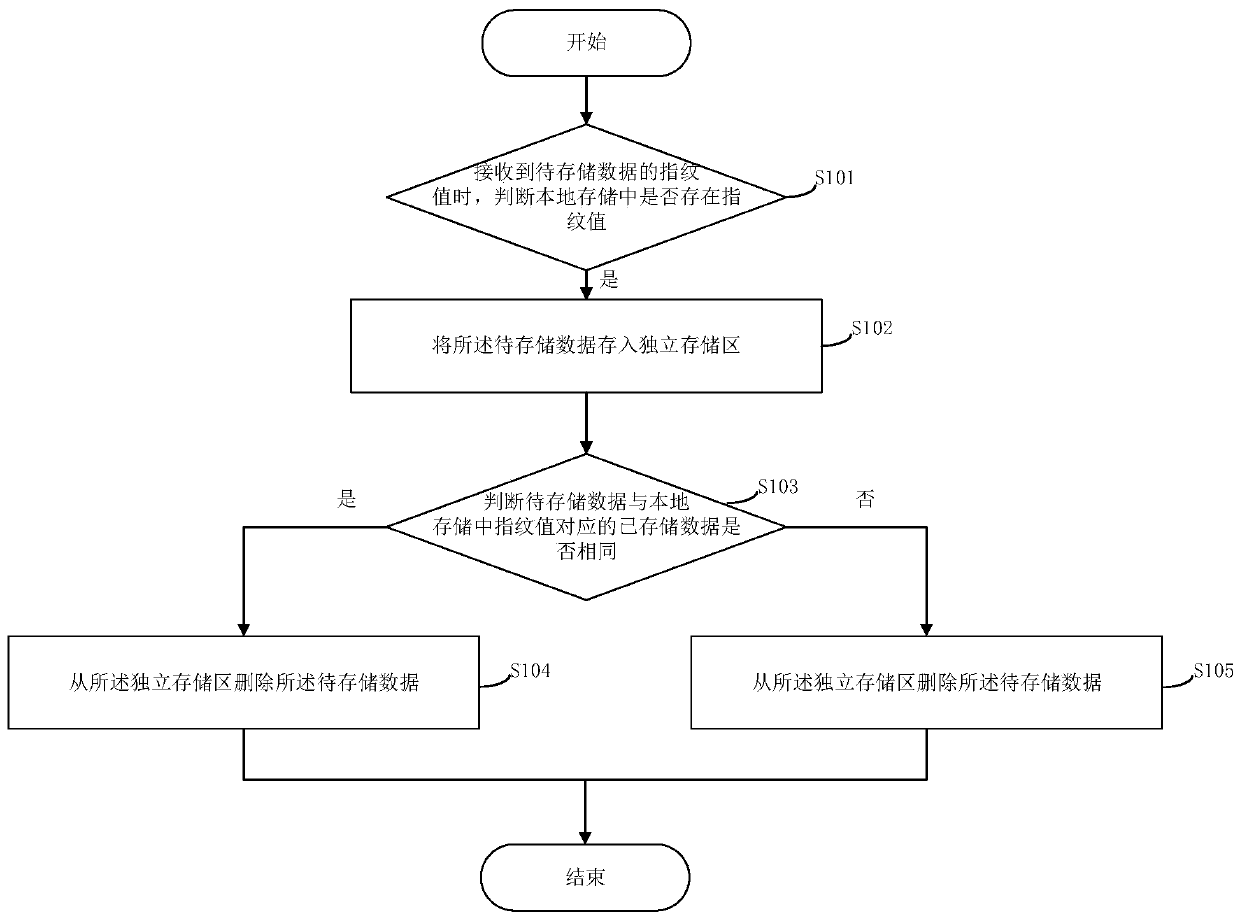
The invention provides a data storage method. The method comprises the steps of judging whether a fingerprint value exists in local storage or not when the fingerprint value of to-be-stored data is received; if yes, storing the to-be-stored data into an independent storage area; judging whether the to-be-stored data is the same as stored data corresponding to the fingerprint value in the local storage or not; if yes, deleting the to-be-stored data from the independent storage area; and if not, transferring the to-be-stored data from the independent storage area to the local storage. Accordingto the method, the problem of data mistaken deletion possibly caused by hash conflicts is solved by utilizing the independent storage area, and the data storage consistency is ensured. The invention further provides a data storage system, a computer readable storage medium and a server, which have the above beneficial effects.
Owner:北京浪潮数据技术有限公司
Method for hash collision detection based on the sorting unit of the bucket
ActiveUS10628487B2Improve efficiencyAvoid alignmentDigital data processing detailsOther databases indexingAlgorithmDirectory
The present disclosure relates to a method for hash collision detection based on the sorting unit of the bucket designed to reduce the future search time by pre-aligning the database in the bucket and to enhance the efficiency in a search within the database. The present disclosure, a method for hash collision detection based on the sorting unit of the bucket using conventional separate chaining method, comprises aligning records in a single bucket of a directory in ascending order or descending order and maintaining the alignment of records in the bucket when new records are added to the directory.
Owner:RES COOPERATION FOUND OF YEUNGNAM UNIV +1
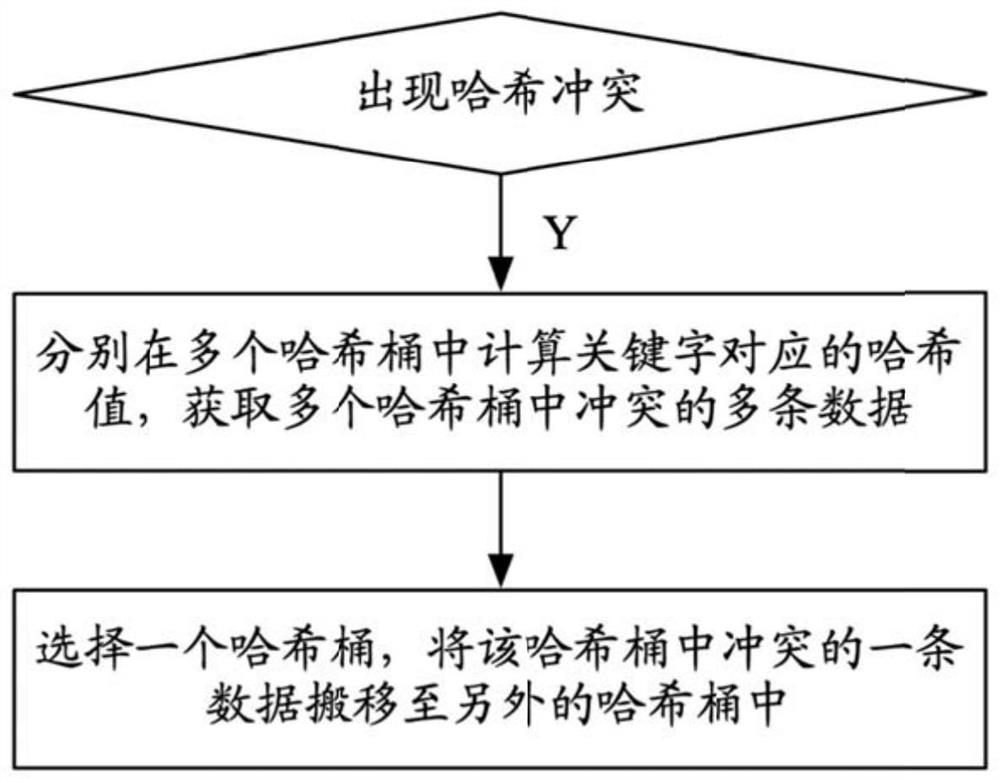
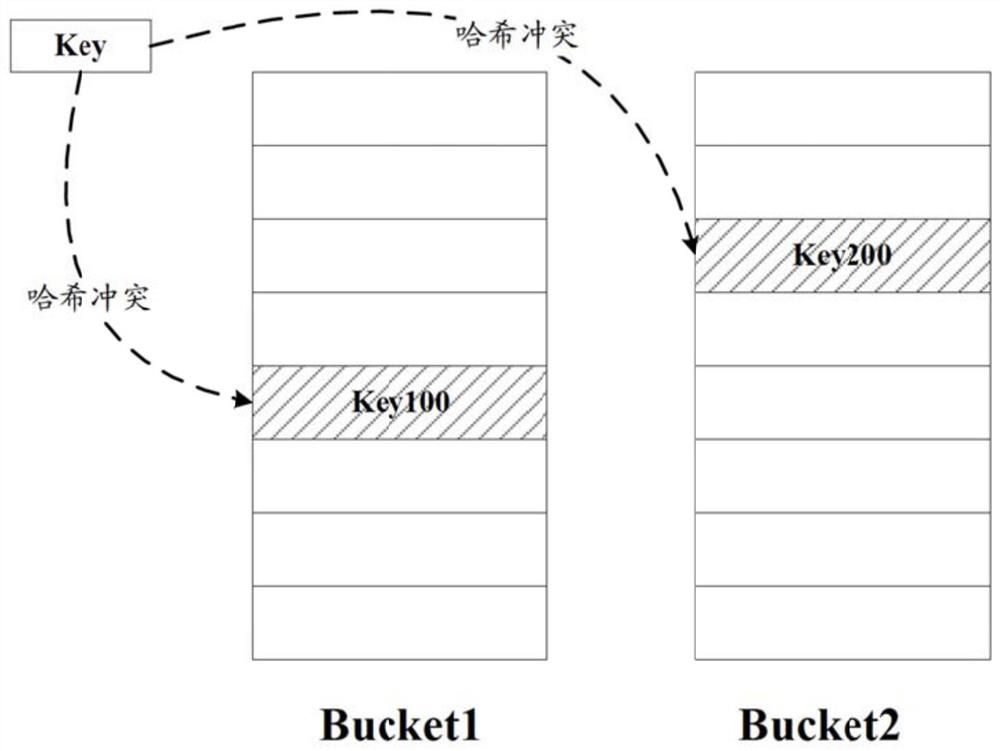
Hash conflict processing method and system
PendingCN112148738AIncrease profitReduce usageInput/output to record carriersEnergy efficient computingDepth-first searchData selection
The invention discloses a hash conflict processing method and system. The method comprises the steps of S1, judging whether a hash conflict occurs in a keyword corresponding to data needing to be added or not; s2, if yes, respectively calculating hash values corresponding to the keywords in a plurality of hash buckets, and obtaining a plurality of conflicting data in the plurality of hash buckets;and S3, selecting a hash bucket, and moving one piece of conflicting data in the hash bucket to another hash bucket. According to the invention, the hash conflict can be effectively solved by using data migration of depth-first search, so that the utilization rate of the storage space is improved, the use of a hash conflict solution table is reduced, and the cost and the power consumption are greatly reduced.
Owner:SUZHOU CENTEC COMM CO LTD
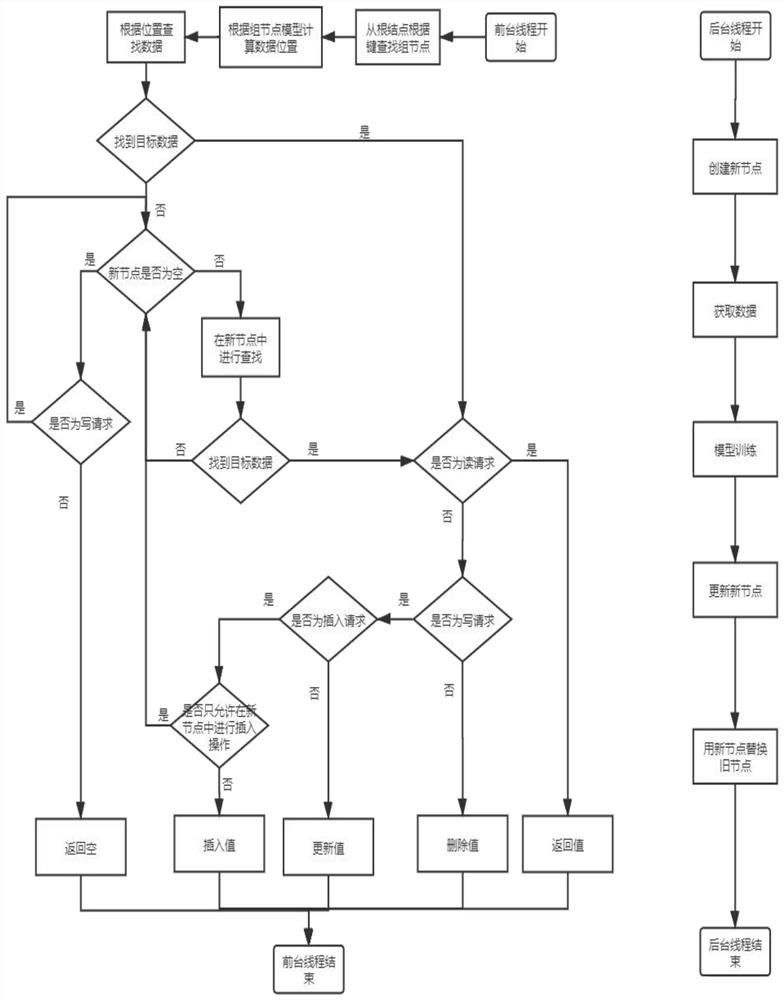
Indexing method and system of concurrent hash index data structure based on machine learning
ActiveCN112434035AImprove performanceEnsure consistencyMachine learningSpecial data processing applicationsEngineeringData mining
Owner:SHANGHAI JIAO TONG UNIV
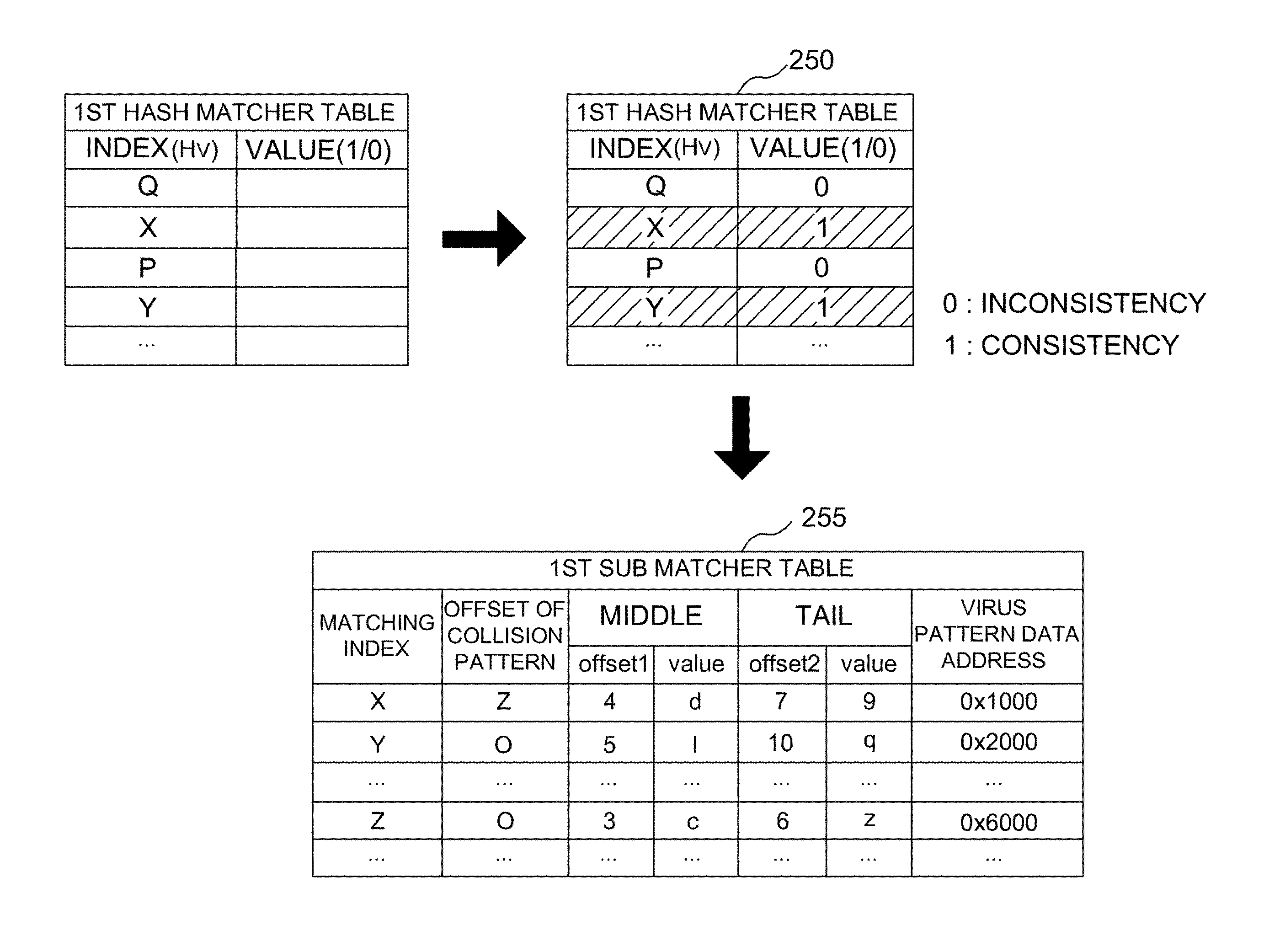
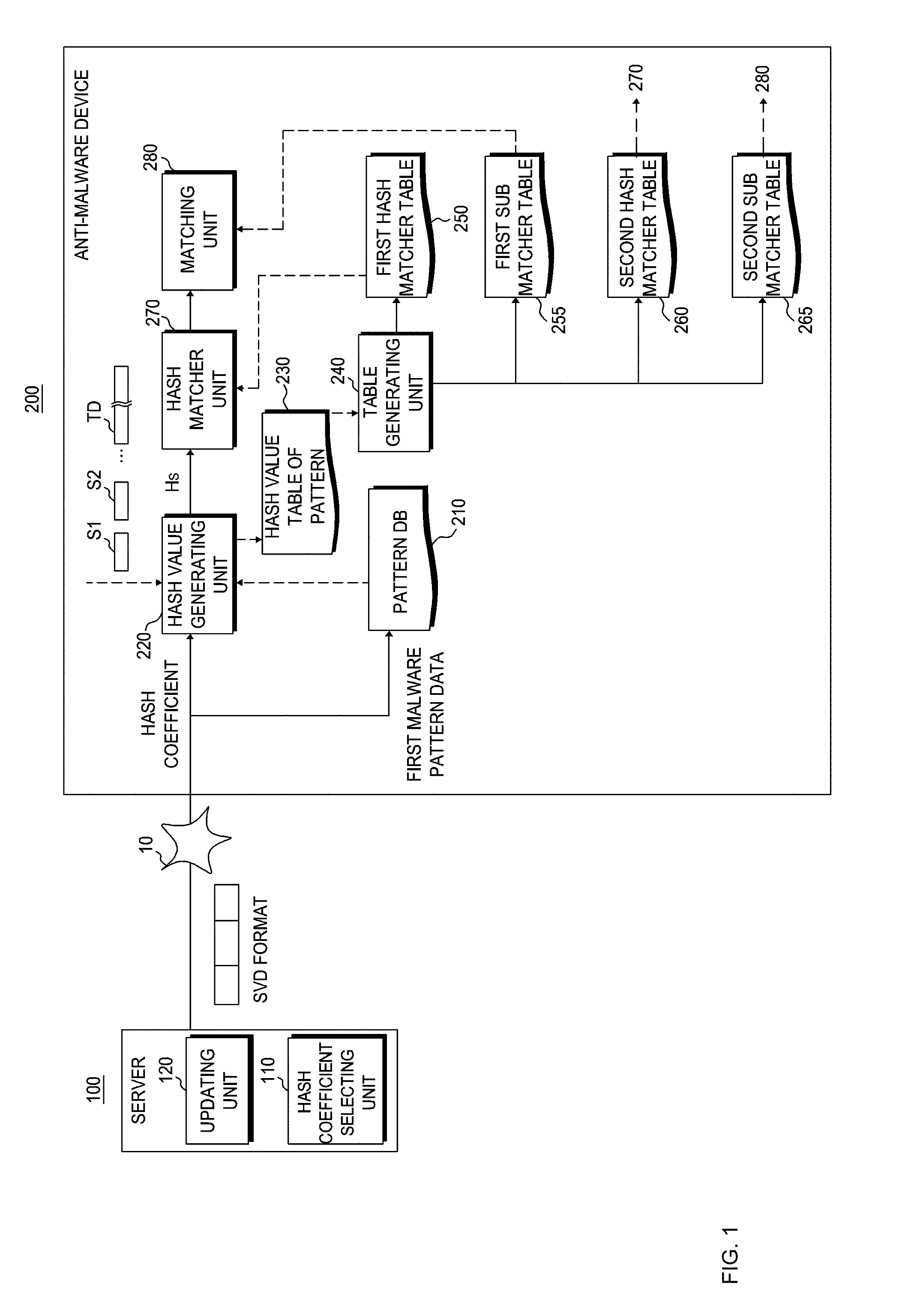
Anti-malware device, server, and method of matching malware patterns
ActiveUS8365288B2Minimize collisionAvoid collisionMemory loss protectionError detection/correctionData packHash function
An efficient virus detection, malware detection, and packet filtering system in a mobile device by providing optimized hash functions from a server to a mobile device that reduce hash collisions during the virus detection, malware detection, and packet filtering in a system-on-chip configuration.
Owner:SAMSUNG SDS CO LTD
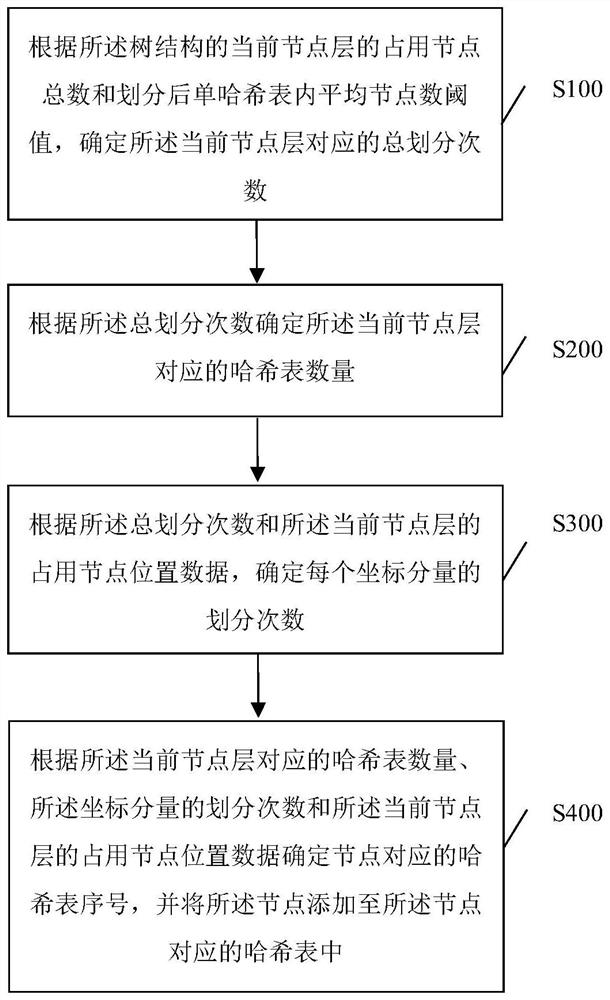
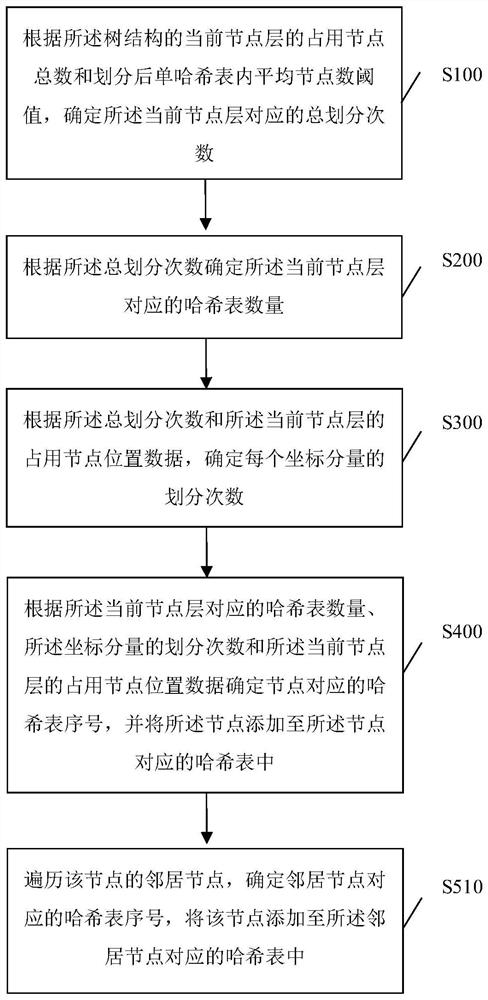
Point cloud dynamic hash division method and device
PendingCN113849495AImprove access performanceImprove insertionSpecial data processing applicationsDatabase indexingPoint cloudTheoretical computer science
The invention discloses a point cloud dynamic Hash division method and equipment, and the method comprises the steps: determining the total number of division times according to the total number of occupied nodes of a current node layer of a tree structure and an average node number threshold value in a single Hash table after division; determining the number of hash tables corresponding to the current node layer; determining the division times of each coordinate component; and determining a hash table corresponding to the node according to the number of hash tables corresponding to the current node layer, the division times of the coordinate component and the occupied node position data of the current node layer, and adding the node into the hash table corresponding to the node. A plurality of hash tables is configured on each node layer, the serial numbers of the hash tables corresponding to the nodes are determined according to the position data of the occupied nodes of the current node layer, the nodes are added to the hash tables corresponding to the nodes, and the nodes in the different hash tables do not have hash conflicts, so that when that the performance is not lost, the access performance of the hash tables is optimized, and the insertion and query efficiency of the hash tables is improved.
Owner:PENG CHENG LAB
Mass data processing method and device
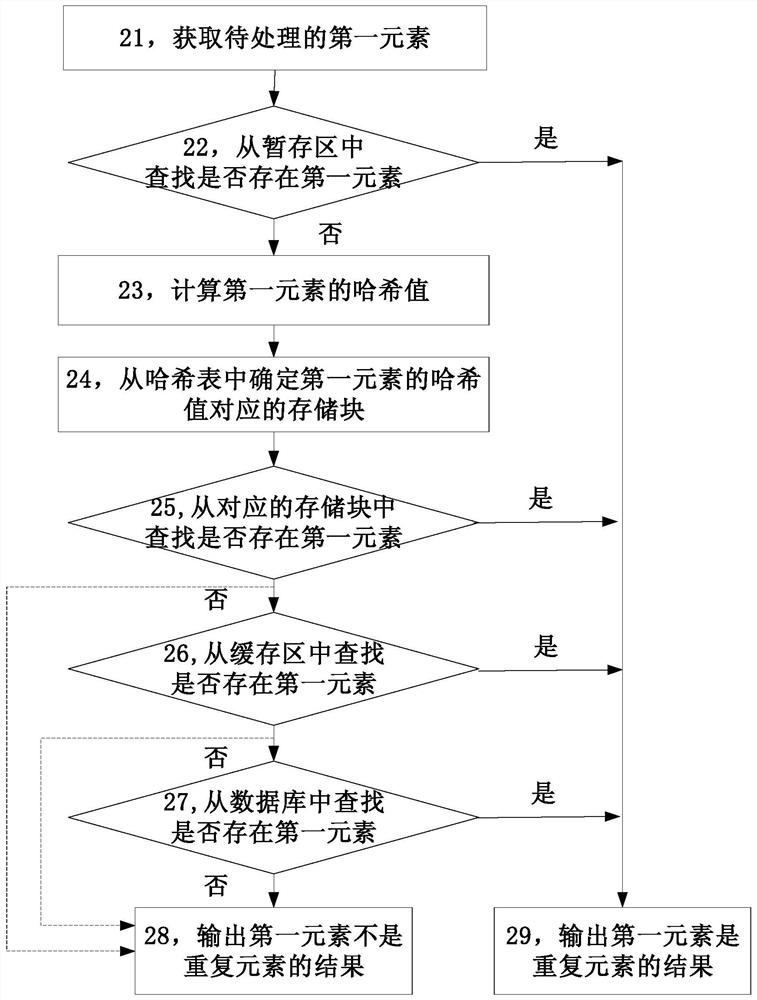
PendingCN111723266AAvoid errors of judgmentJudgment efficiency is lowWeb data indexingWebsite content managementAlgorithmEngineering
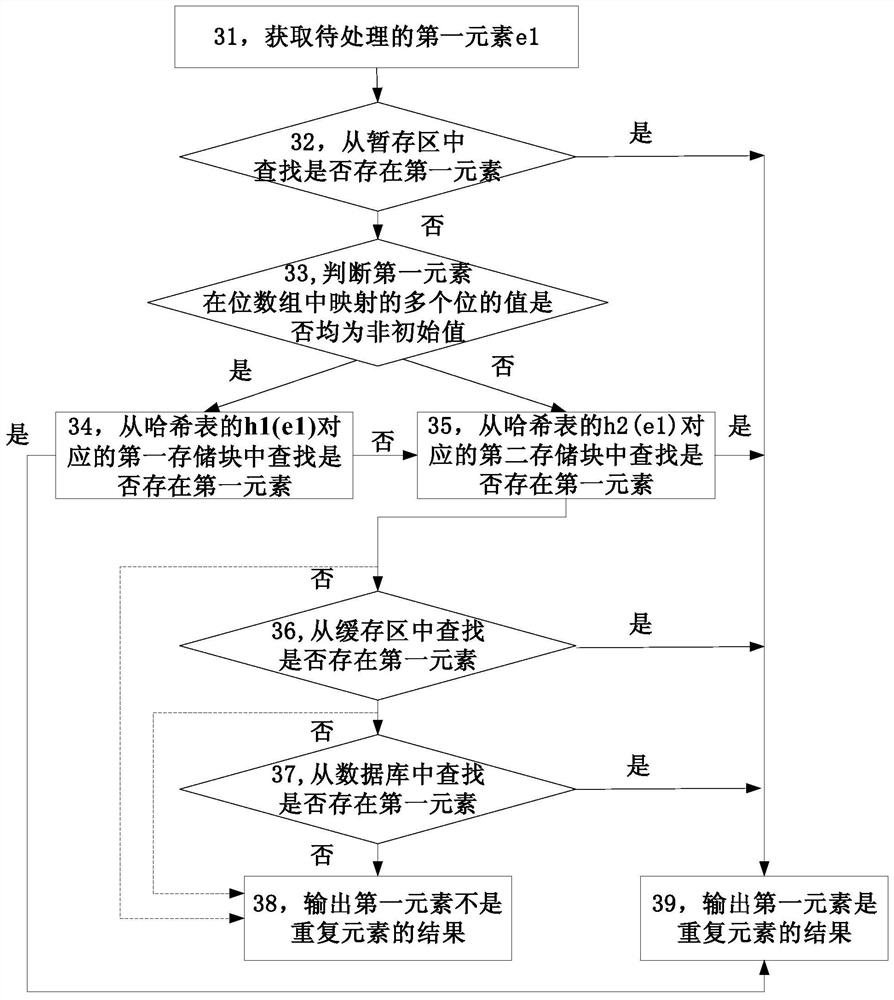
The invention provides a mass data processing method and device, and relates to the field of computers. The method comprises the steps of: positioning the storage position of a first element in a hashtable through the hash value of the first element; searching the first element from elements stored in the storage block at the storage position; due to the fact that the hash value of the element rather than the hash value of the element is searched for, and accurately judging whether the first element is the repetitive element or not, so that the problem of repetitive element judgment errors caused by hash conflicts is solved, the elements are searched for in a small number of elements through positioning, and therefore the judgment efficiency of the repetitive element can be considered atthe same time. The mass data processing method and device are suitable for repeated data judgment scenes of mass data processing.
Owner:BEIJING WODONG TIANJUN INFORMATION TECH CO LTD
FPGA efficient rule matching method and terminal
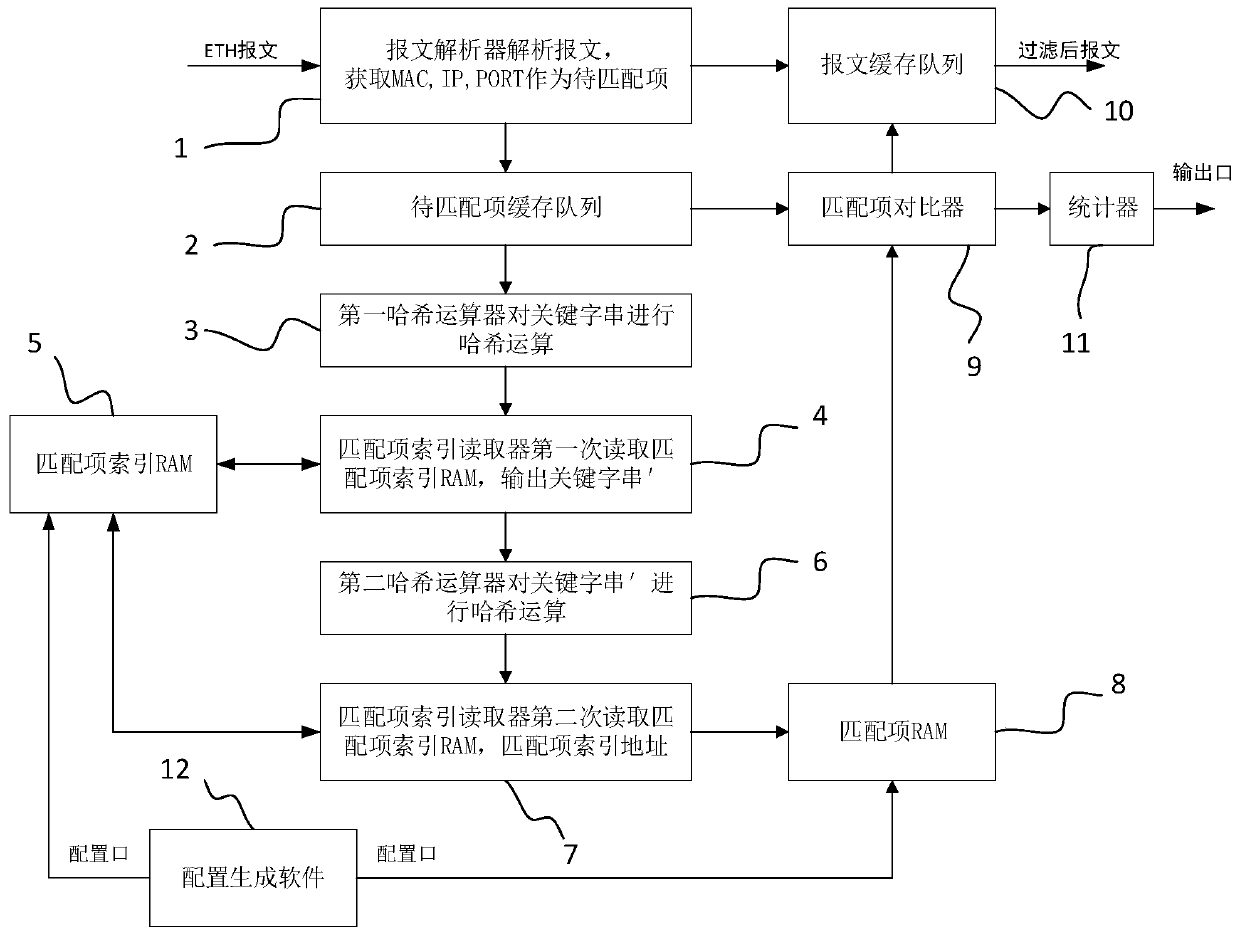
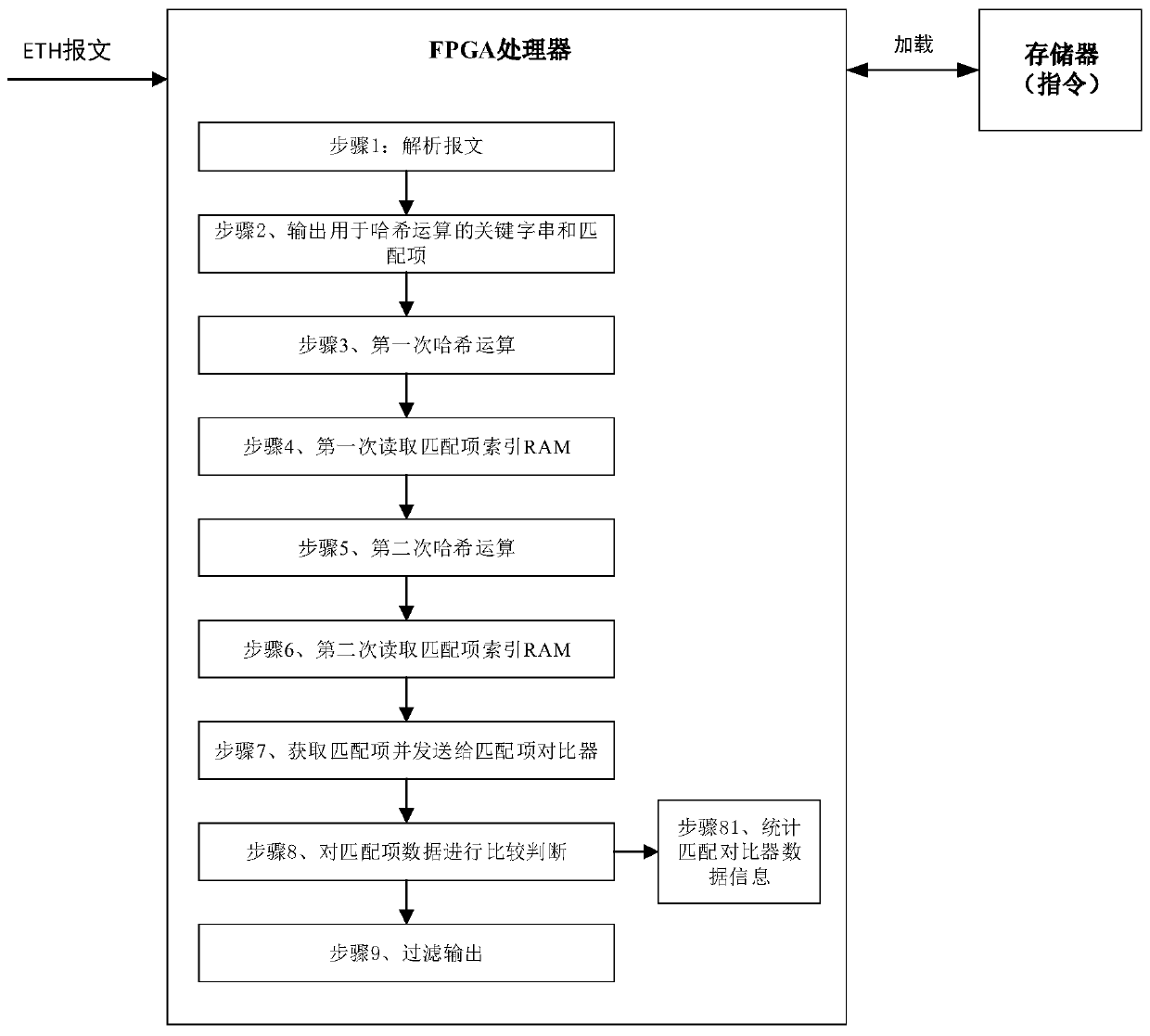
The invention discloses an efficient rule matching method for an FPGA. Filtering the message at a linear speed by using fixed group delay; adding a numerical value to the keyword string of the hash conflict; hash operation is carried out again to solve the Hash conflict problem. The data read from the result of the first hash operation is used as a numerical value C or 0; and after adding the keyword string, carrying out hash operation again, comparing the data read by the result of the second hash operation with the index address of the matching rule, discarding the message which does not meet the requirement in the message cache queue according to the matching result, and outputting the message which meets the requirement, thereby realizing accurate filtering output of the message.
Owner:TAIZHOU YUNYONG ELECTRONICS
A hash table construction method and system for non-volatile memory
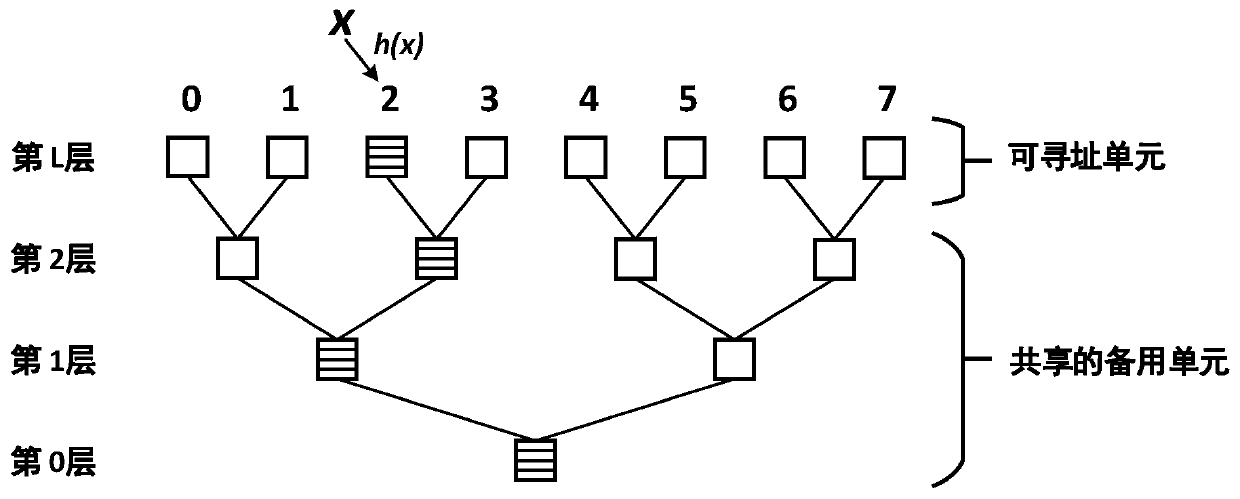
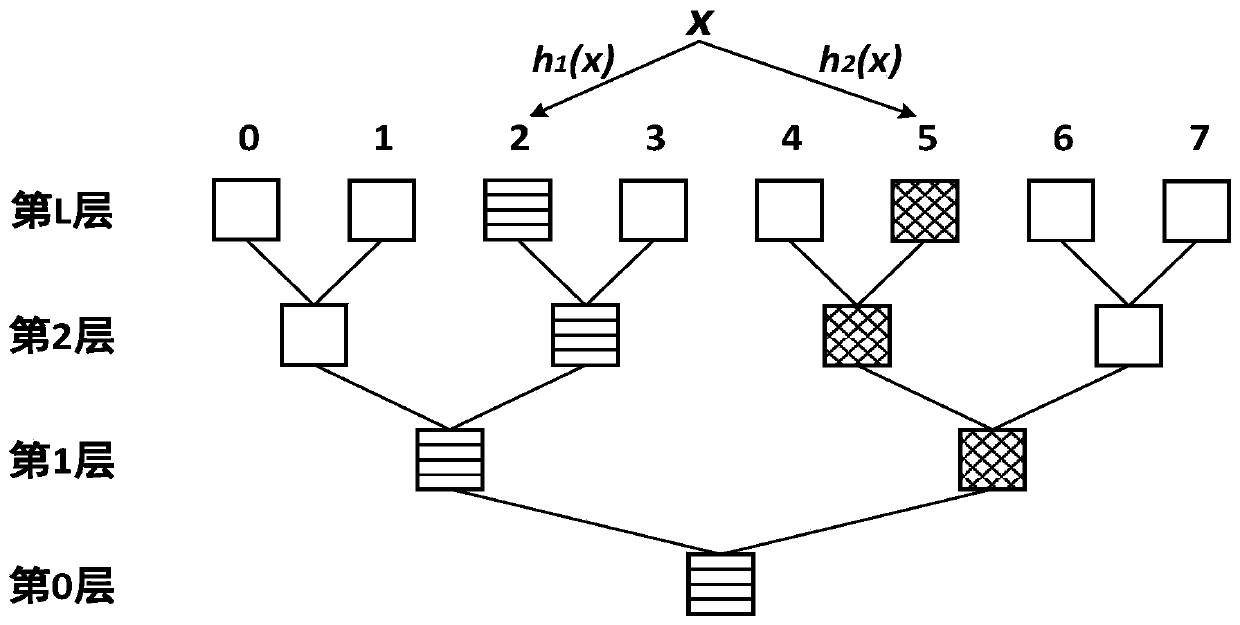
ActiveCN107153707BNo memory writeReduce the probability of insertion failureSpecial data processing applicationsDatabase indexingParallel computingTheoretical computer science
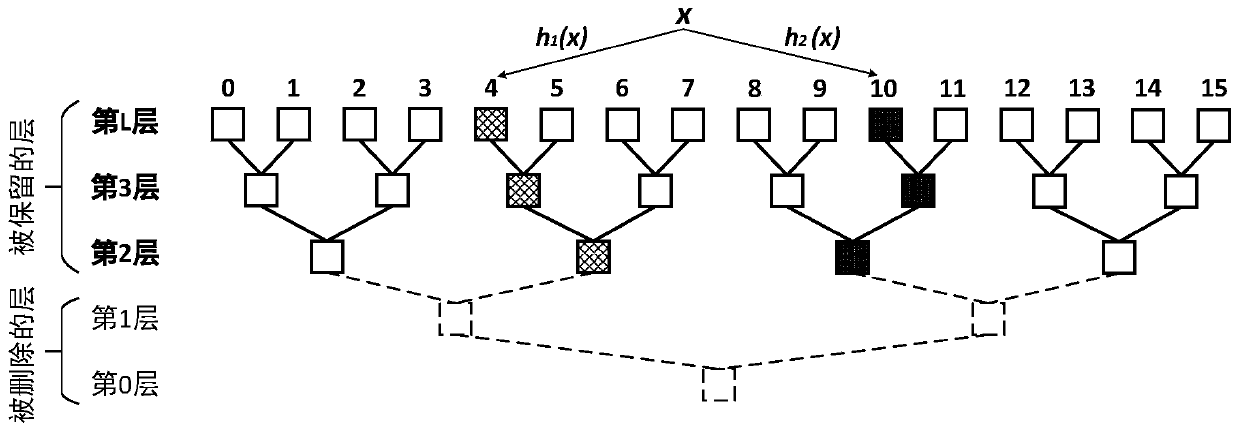
The invention discloses a hash table construction method and system for a nonvolatile memory. The hash table construction method is characterized in that a hash table is constructed and is logically constructed into an inverted complete binary tree, all leaf nodes of the binary tree are addressable units, and all non-leaf nodes are unaddressable units and serve as standby units for the leaf nodes to deal with hash conflicts; all the non-leaf nodes on a path from the leaf nodes to root nodes are used for storing conflict elements of the hash conflicts at the leaf nodes; furthermore, a plurality of layers at the bottom of the binary tree are deleted, and only rest layers at the top are remained; and each element in the hash table corresponds to two different hash positions which are obtained through computation by use of two different hash functions. The invention also provides the hash table construction system for the nonvolatile memory. According to the technical scheme, the constructed hash table cannot cause any additional writing, and high space utilization ratio and low request delay are achieved.
Owner:HUAZHONG UNIV OF SCI & TECH
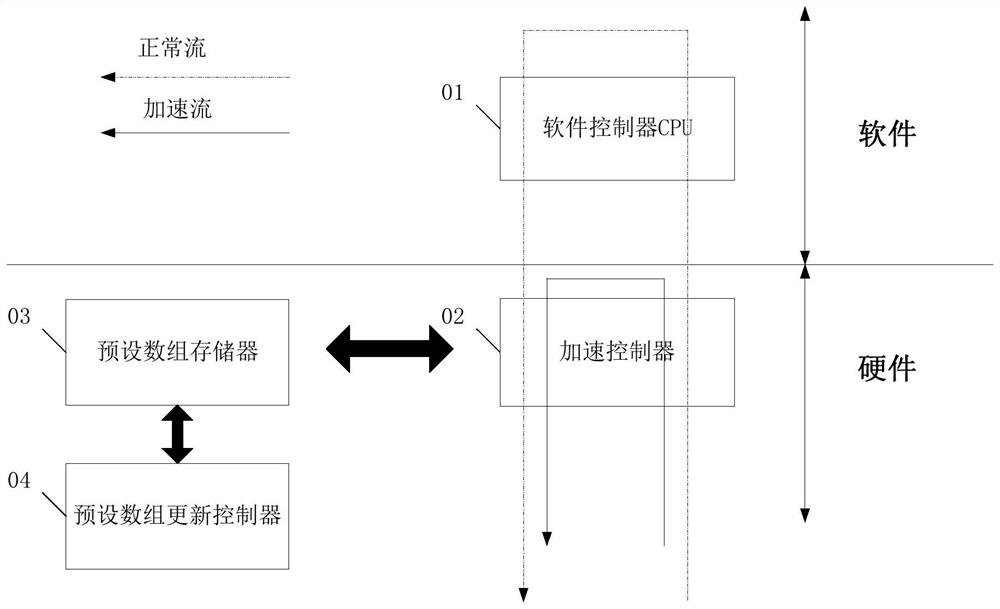
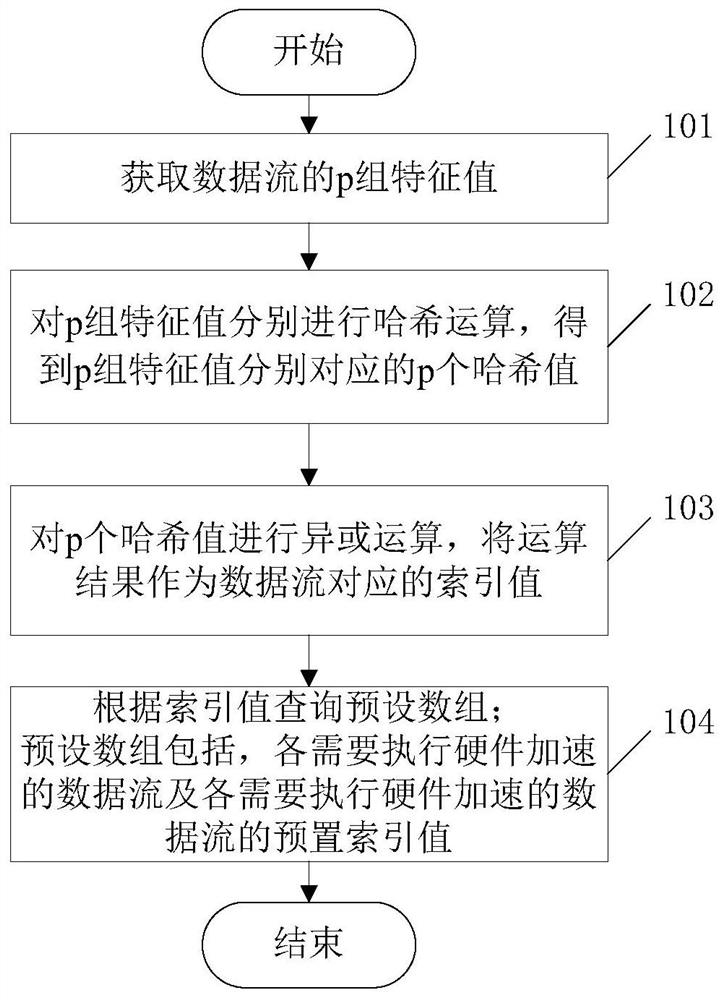
Hardware accelerated query method and system, electronic equipment and storage medium
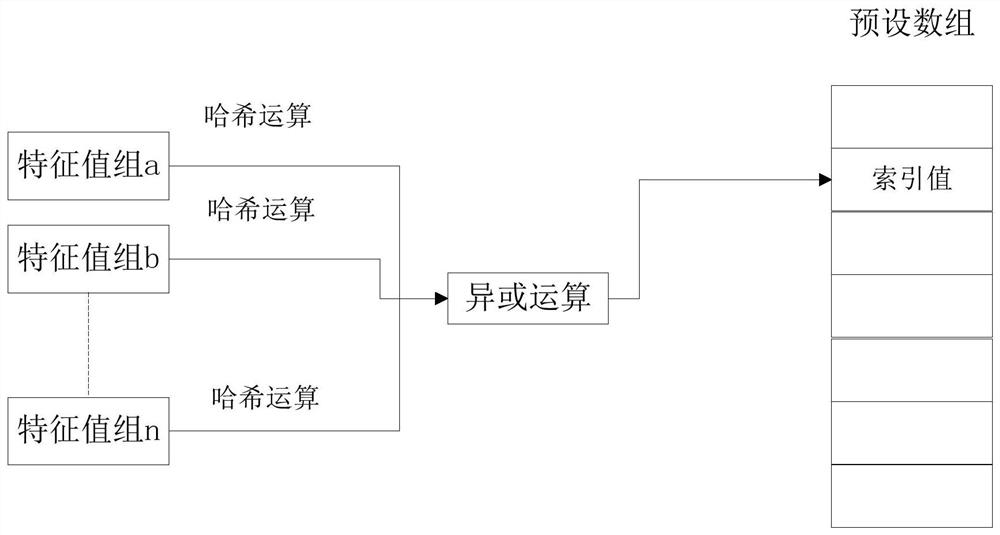
ActiveCN112202677AEvenly distributedReduce regularityEnergy efficient computingData switching networksComputer hardwareData stream
The embodiment of the invention relates to the field of communication, and discloses a hardware accelerated query method and system, electronic equipment and a storage medium. In the embodiment of theinvention, the hardware accelerated query method comprises the following steps: acquiring p groups of characteristic values of a data stream; respectively carrying out hash operation on the p groupsof characteristic values to obtain p hash values respectively corresponding to the p groups of characteristic values; performing exclusive-OR operation on the p hash values, and taking an operation result as an index value corresponding to the data stream; and querying a preset array according to the index value, wherein the preset array comprises each data stream needing to be subjected to hardware acceleration and a preset index value of each data stream needing to be subjected to hardware acceleration. According to the method, the hash algorithm in the hardware accelerated query process ismodified by combining the actual use scene of the home gateway, so that the regularity of the internal characteristic value of the data stream is reduced compared with the operation adopting a singlecharacteristic value, and the hash conflict in the hash algorithm is reduced on the premise of ensuring the actual transmission time.
Owner:CHINA MOBILEHANGZHOUINFORMATION TECH CO LTD +1
Massive Network Data Search Method Based on Data Flow Structure
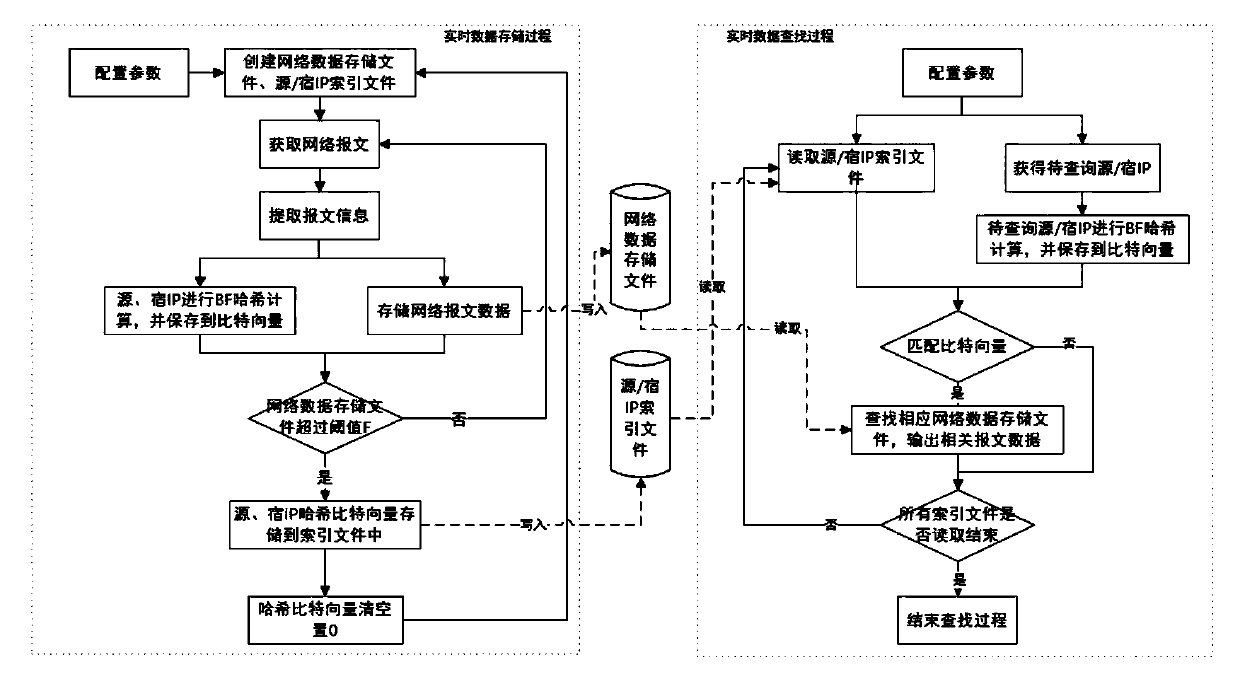
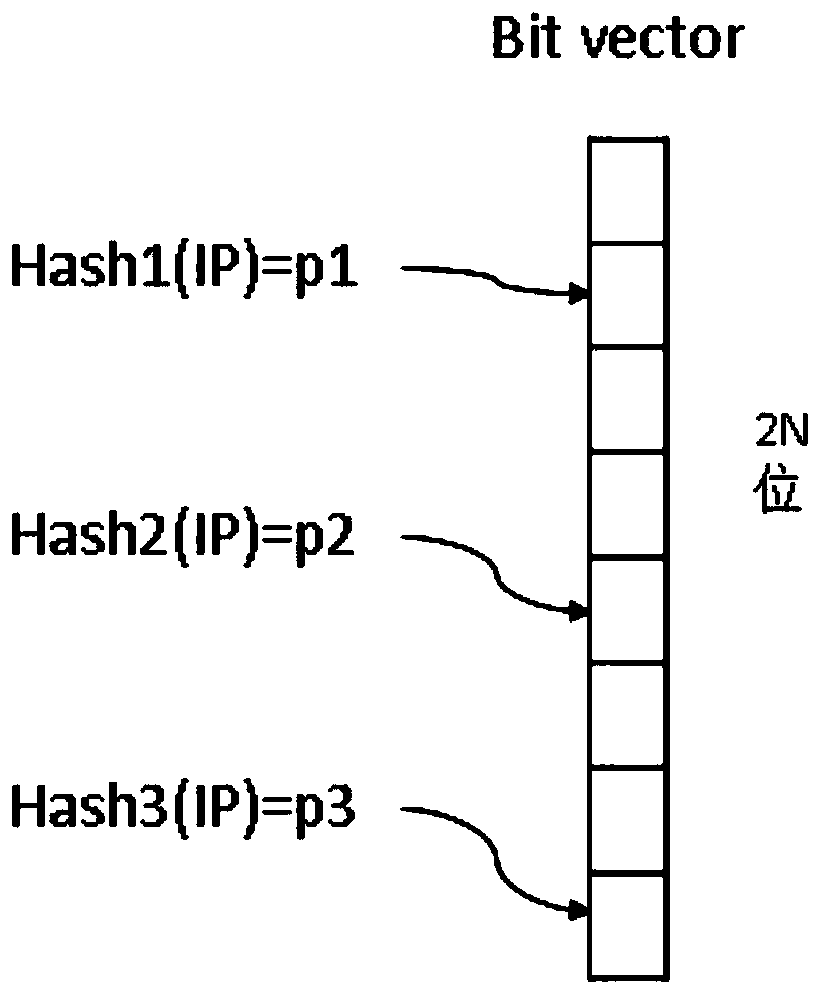
ActiveCN107357843BRealize Hierarchical SearchReduce the probability of conflictText database indexingSpecial data processing applicationsData streamHash function
The invention discloses a mass network data search method based on a data stream structure. The method comprises a real-time data storage method and a real-time query method. Data in a network arrives in a data stream form, so that it is needed to reduce the network data, capture a specific length of each piece of network message data and store valid information according to a specific data file size. According to the method, a Bloom Filter algorithm is used to establish an index file for a source IP and a host IP in each network message; and during real-time query, the index file is searched for first, a data storage file is searched for after matching succeeds, and detailed information is obtained. Through the method, mass network data can be quickly processed, a small storage space is occupied, and a large amount of network detailed information is saved; by use of the Bloom Filter Hash algorithm to establish indexes for the network message data, grading retrieval of file content is realized, the index structure is simple, and the occupied space is small; by use of three different Hash functions for calculation, the Hash conflict rate is low; and during retrieval, index matching search is quick and accurate, and high time and space efficiency is achieved.
Owner:SOUTHEAST UNIV
SCM-based key-value log-type local storage method
ActiveCN107544756BIncrease profitExtended service lifeInput/output to record carriersResource allocationParallel computingTerm memory
The invention provides an SCM (Storage Class Memory)-based Key-Value log-type local-storage method. The storage method comprises the following steps: an SCM dividing step, wherein partition dividing is carried out on an SCM according to functions, that is, the SCM is divided into five different logic partitions of a superblock area, a checkpoint area, a page management area, a static-hash-table area and a data storage area; a multilayer memory management step, wherein three layers of memory management modules are built, the memory is managed at different layers, and dynamic allocation and reclaimation of pages are realized; and a high-concurrency hash-table building step, wherein a static hash table is used to index key-value objects, and a dynamically allocated array is used to store hash-conflicting elements. According to the method realized in the invention, storage space is reasonably scheduled and allocated according to hardware characteristics of a heterogeneous memory medium, autilization rate of the storage medium is increased, service life of hardware is prolonged, and concurrency and data throughput of a hybrid key-value storage system are improved.
Owner:SHANGHAI JIAOTONG UNIV
Rapid stereo matching method based on ZSAD-Census
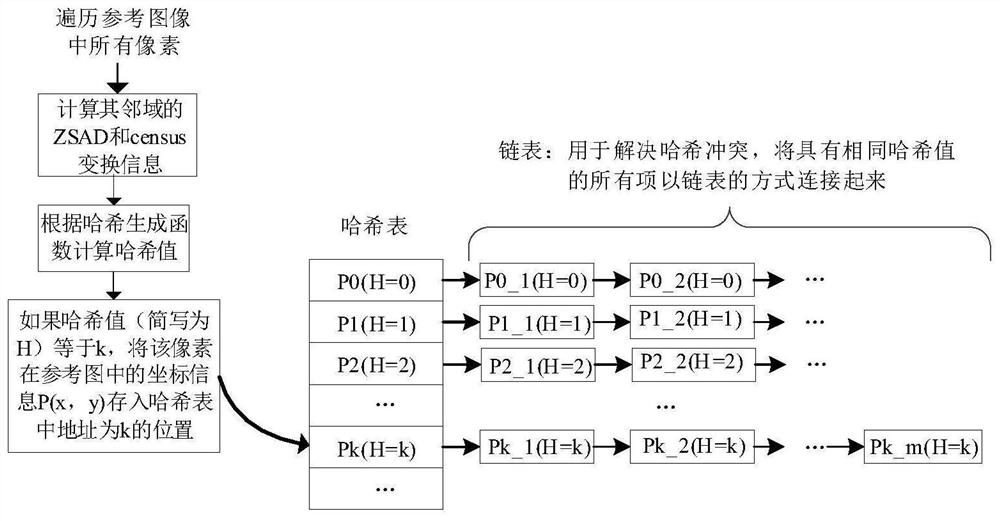
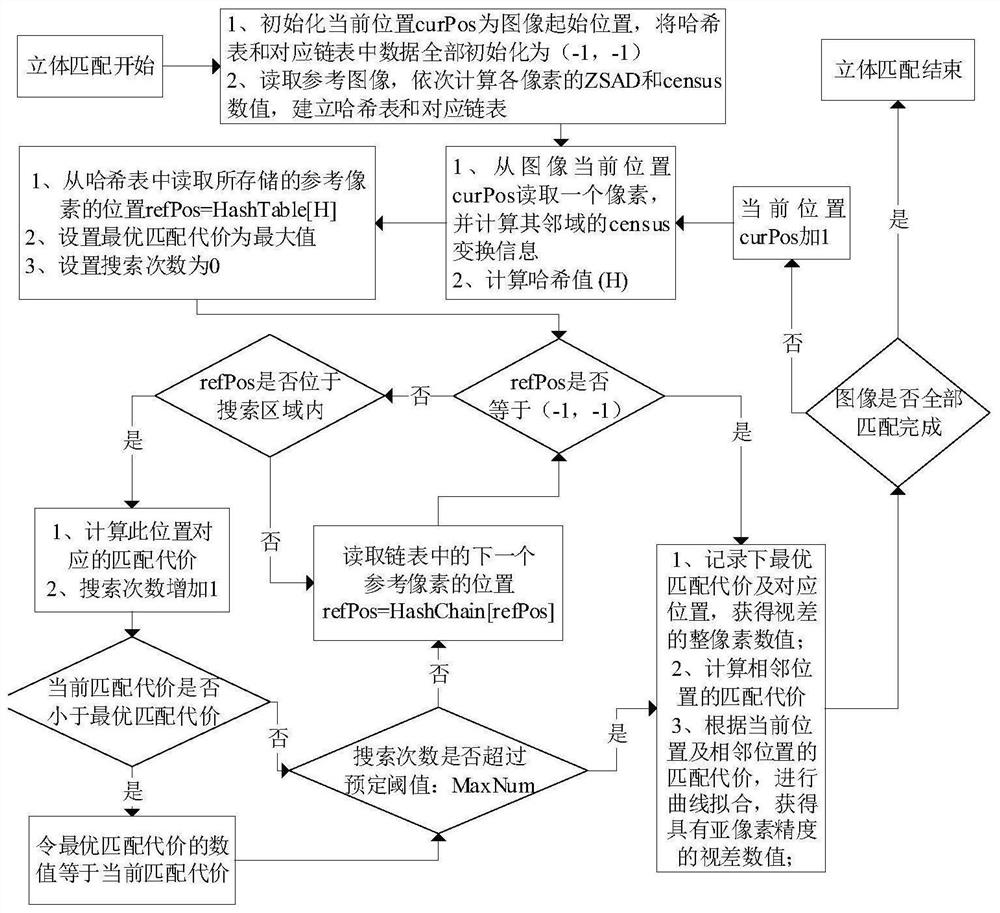
PendingCN113570646AReduce distractionsImprove matching accuracyImage enhancementImage analysisPattern recognitionStereo matching
The invention discloses a rapid stereo matching method based on ZSAD-Census, and the method comprises the following steps: S1, carrying out the initialization configuration before the stereo matching of each frame of image is started; S2, inputting a target image and a reference image, traversing each pixel in the images, and calculating ZSAD information and Census information; S3, jointly using the ZSAD information and the Census information of the reference image, or adopting independent ZSAD information or Census information, constructing a hash function, constructing hash tables through the hash function, wherein each hash table is used for solving hash conflicts by constructing a chain table; and S4, calculating the hash value of the current pixel, and searching the position of the reference pixel with the same hash value as the current pixel. According to the invention, the problems of large power consumption and high area cost in the prior art are solved, and the accuracy and anti-interference performance of a stereo matching algorithm are improved.
Owner:南京物间科技有限公司
High Dimensional Approximate Image Retrieval Method Based on Inverted lsh in Cloud Computing Environment
ActiveCN105760469BShorten the timeResolve discrepancies etc.Still image data queryingEnergy efficient computingDistributed Computing EnvironmentData space
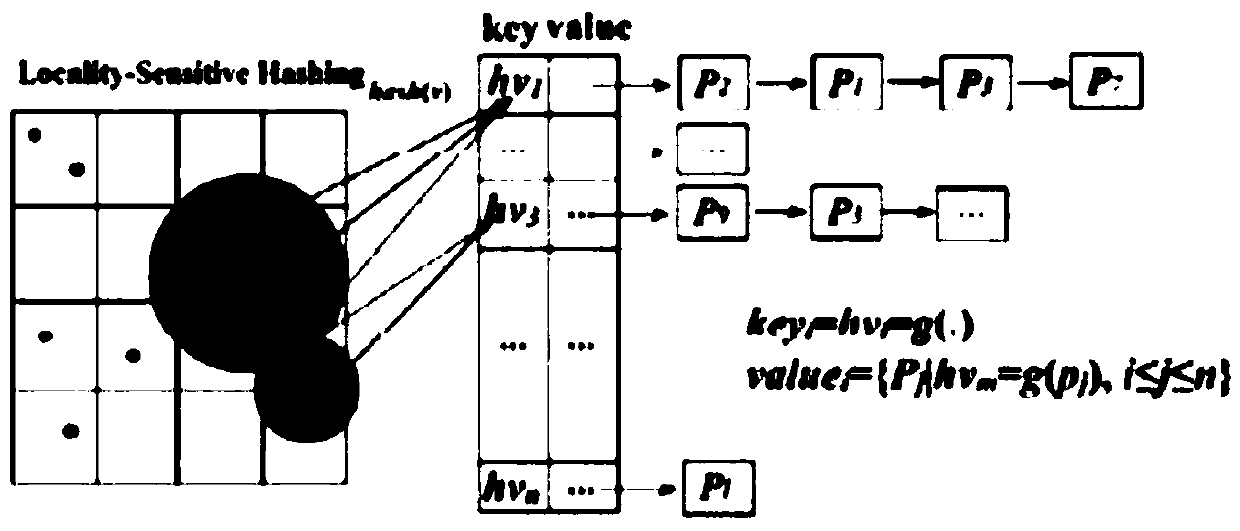
The invention discloses a high-dimensional approximate image retrieval method based on inverted LSH in a cloud computing environment, which belongs to the field of big data and mobile applications. The system establishes a new index structure (LSRP‑tree), which reduces the cost of high-dimensional indexing and improves query efficiency; the new algorithm (H‑c2kNN) formed by combining LSH with MapReduce shows good scalability and efficiency. These two innovative applications solve the approximate retrieval problem in high-dimensional data space. An optimization method based on hash collision counting and sorting is adopted to greatly reduce the amount of intermediate data and speed up data processing. The invention is a system that uses an intelligent mobile platform to search for pictures, including a set of cloud servers and a mobile client. The latter collects and transmits pictures, and the former is responsible for establishing high-dimensional indexes and performing kNN query processing. The invention effectively and advantageously improves the recognition problem of a large number of images and satisfies people's further desire for intelligent mobile information retrieval.
Owner:DALIAN UNIV
Mac address writing method, device and computer-readable storage medium
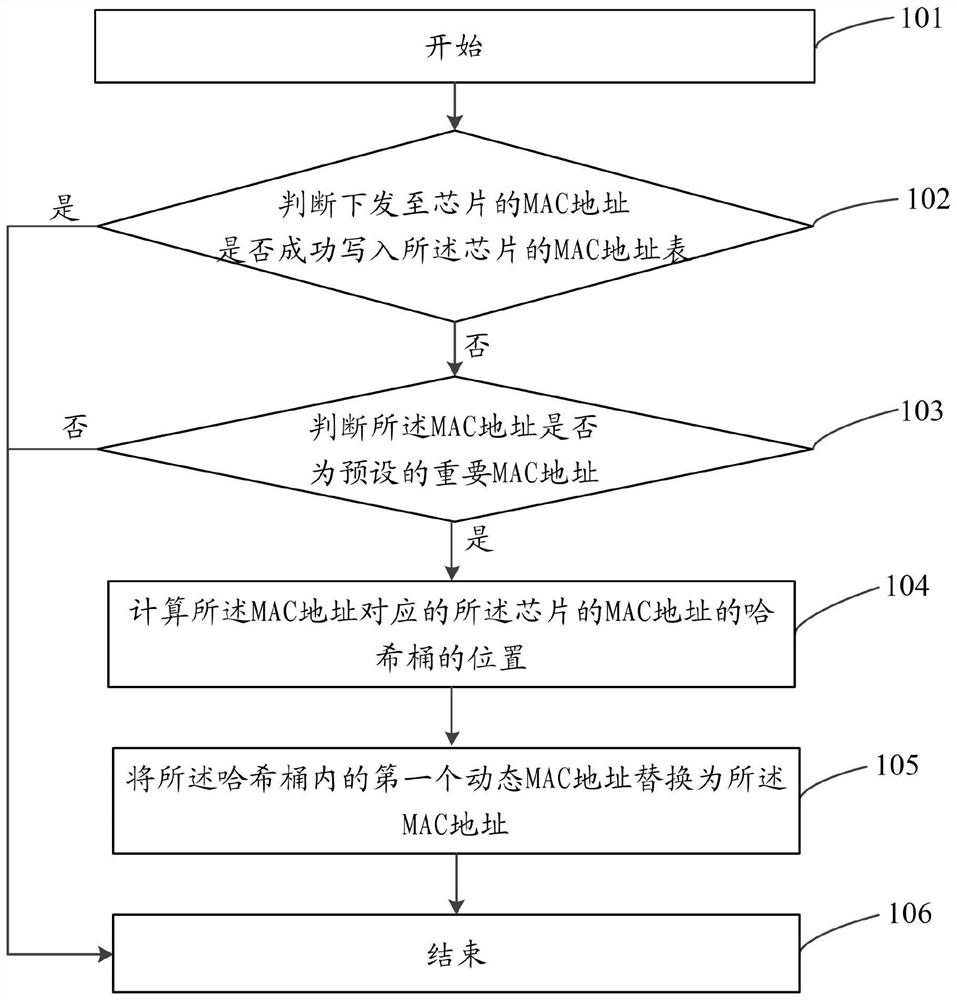
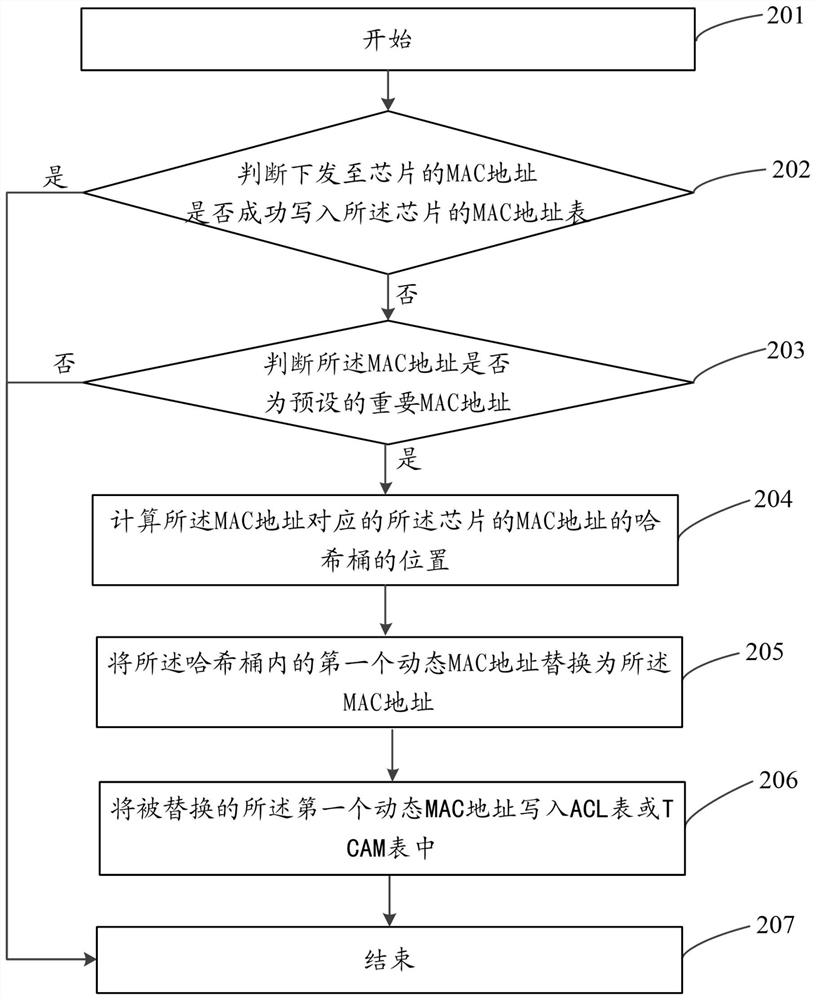
The invention discloses a method and device for writing a MAC address, and a computer-readable storage medium; the method includes: judging whether the MAC address sent to the chip is successfully written into the MAC address table of the chip; if not, judging Whether the MAC address is a preset important MAC address; if so, calculate the position of the hash bucket of the MAC address of the chip corresponding to the MAC address; put the first dynamic MAC address in the hash bucket Replace with the said MAC address. The invention can ensure the robustness of the network and the ease of maintenance of the equipment. This prevents important network forwarding traffic from being abnormal due to MAC address hash collisions.
Owner:NANJING ZHONGXING SOFTWARE
A sparse neural network accelerator and its implementation method
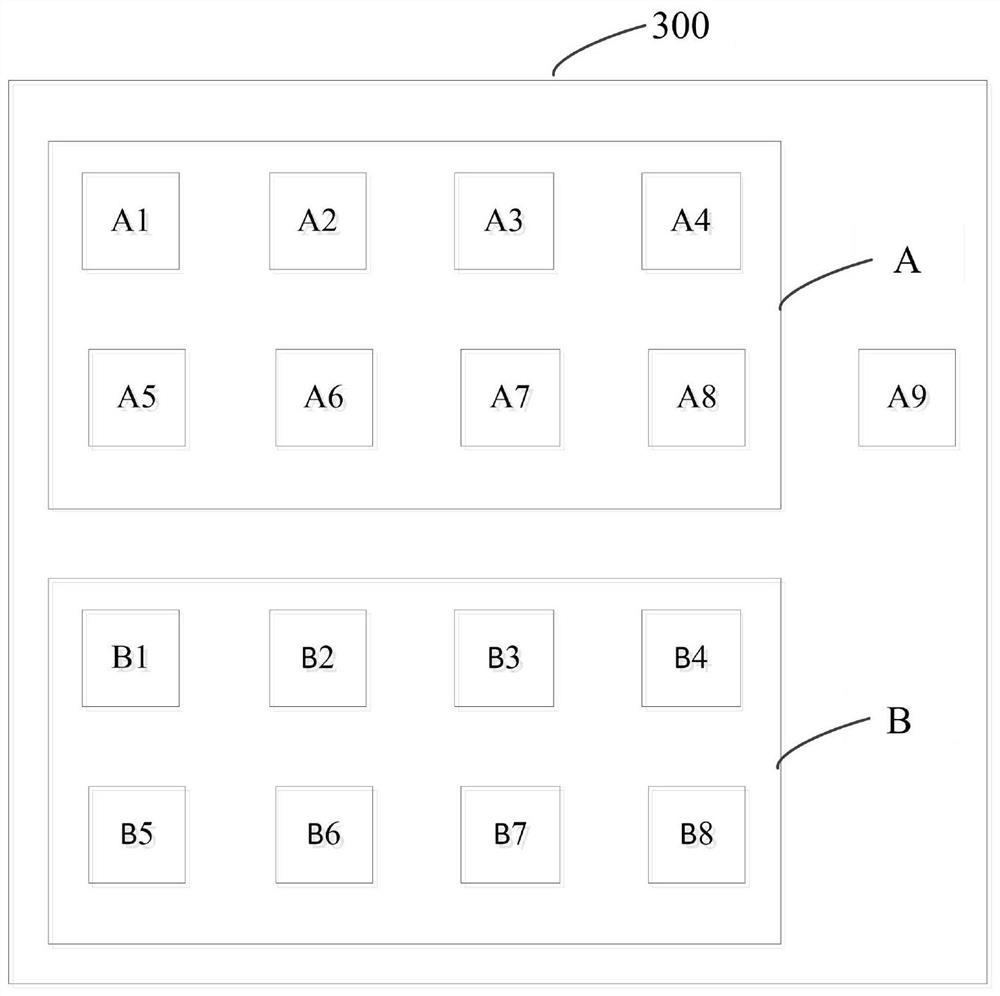
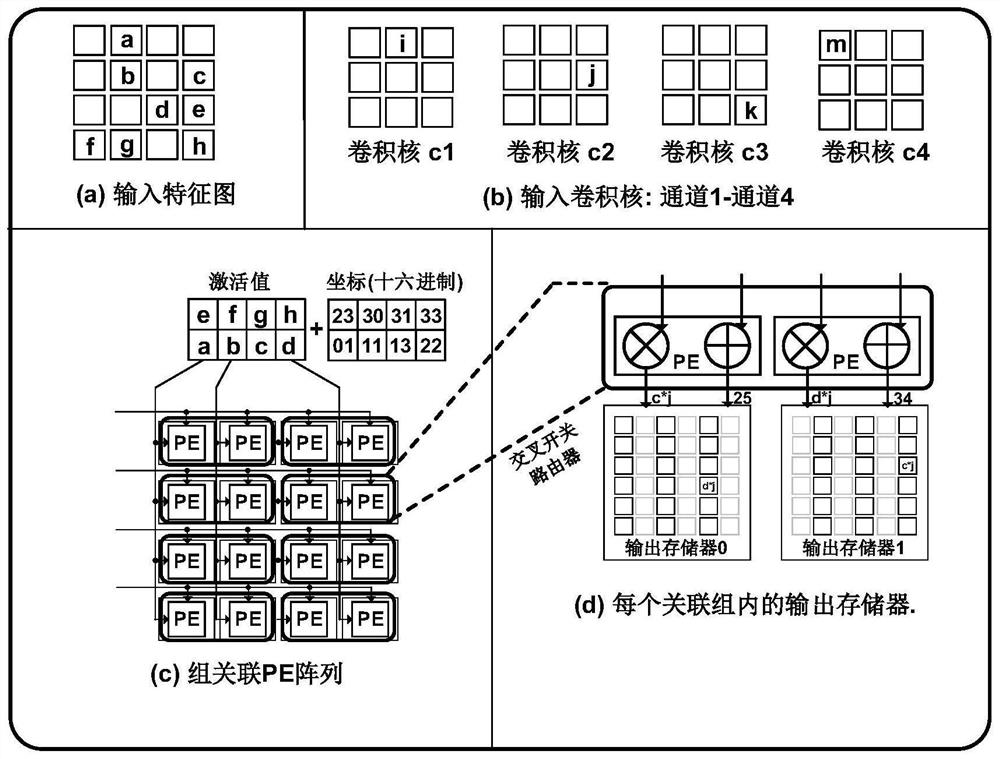
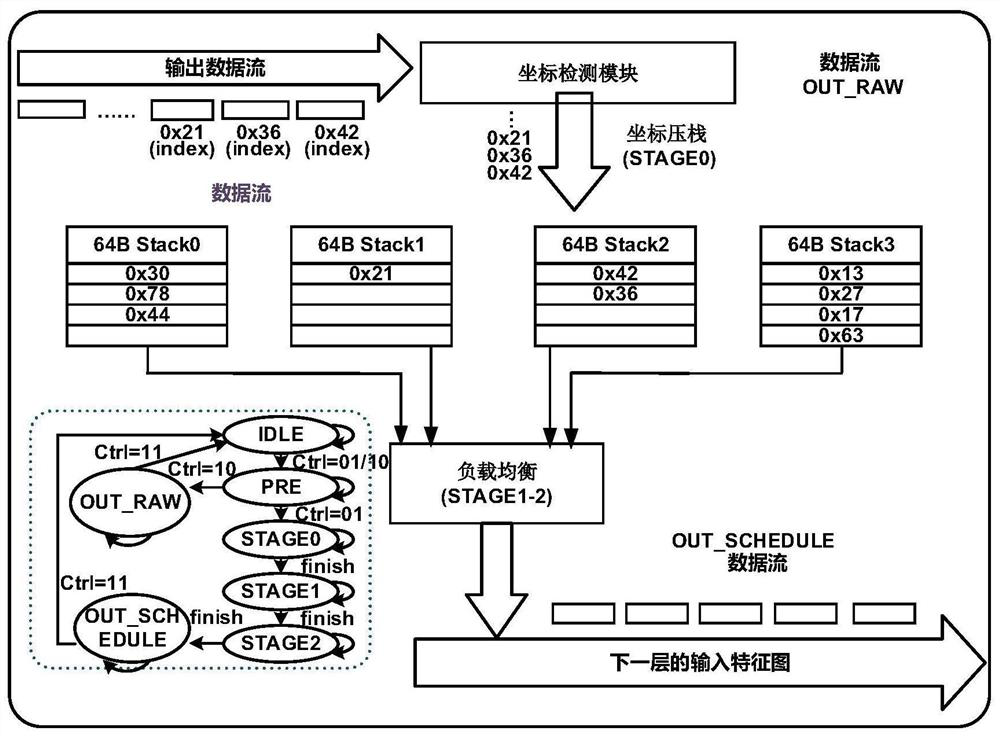
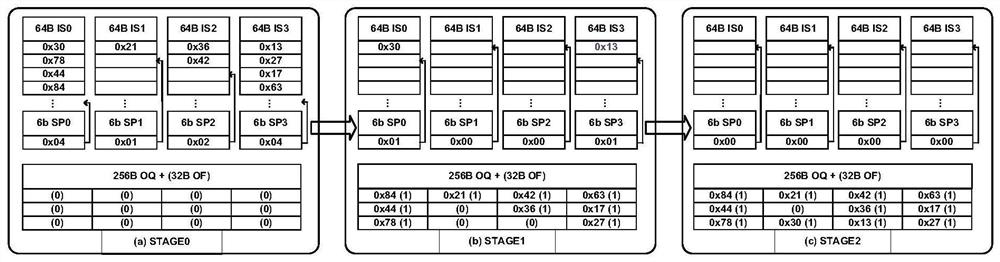
ActiveCN110738310BReduce sizeReduce areaNeural architecturesPhysical realisationAlgorithmTerm memory
The present invention provides a sparse neural network accelerator and its implementation method. The accelerator mainly includes a PE array, an output memory, and a scheduler module. The PE array is divided into multiple PE groups, and each PE group and the corresponding output memory form an associated group. The number of PEs in the association group is equal to the number of output memories; each PE unit in the association group can access any output memory in the association group; PE units in any association group are calculated according to the input activation value and weight value Multiple output results are obtained and written into corresponding multiple output memories according to preset rules; the scheduler module schedules the sequence of output activation values to reduce the probability of hash collisions. The invention divides the original PE array into multiple PE groups, and forms an associated group architecture with the corresponding output memory, which greatly reduces the area of the output memory and reduces power consumption; the scheduler module reduces the probability of hash conflicts and greatly improves the Computational performance of the entire system.
Owner:TSINGHUA UNIV
Method and device for data processing
ActiveCN109076021BImprove load balancingReduce the probability of hash collisionsData switching networksSecuring communicationAlgorithmEngineering
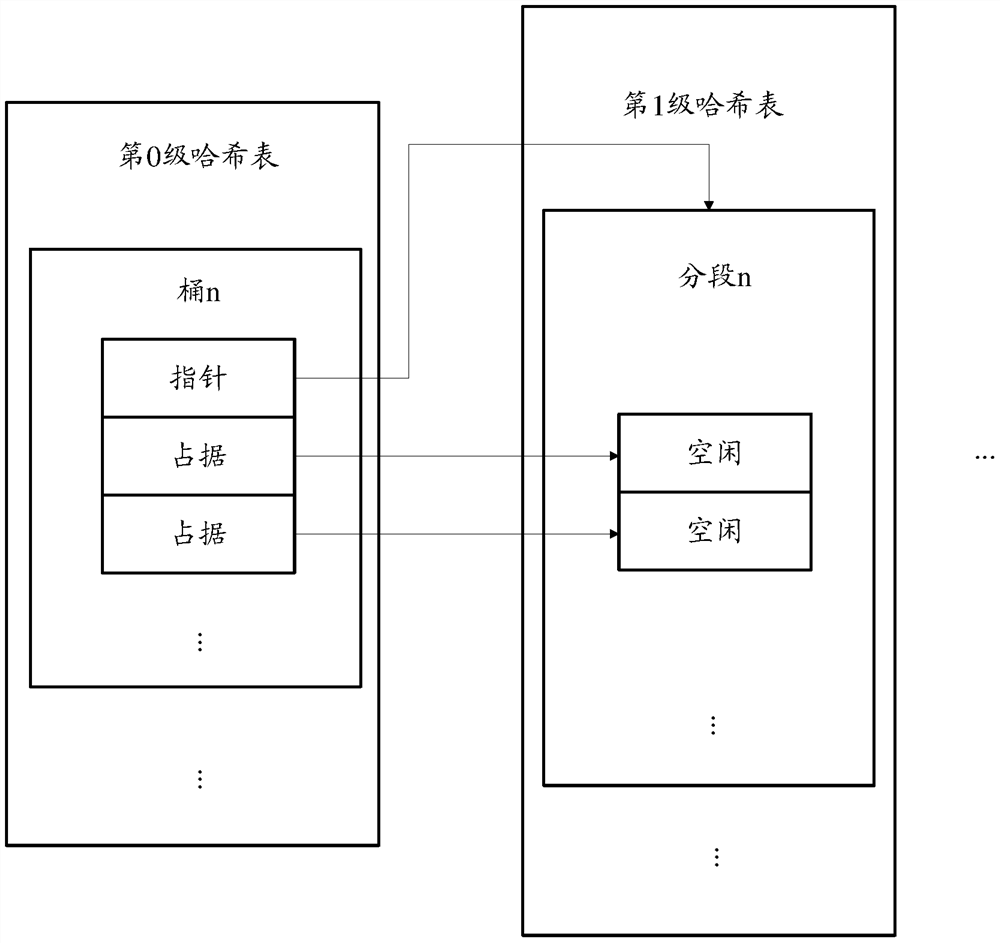
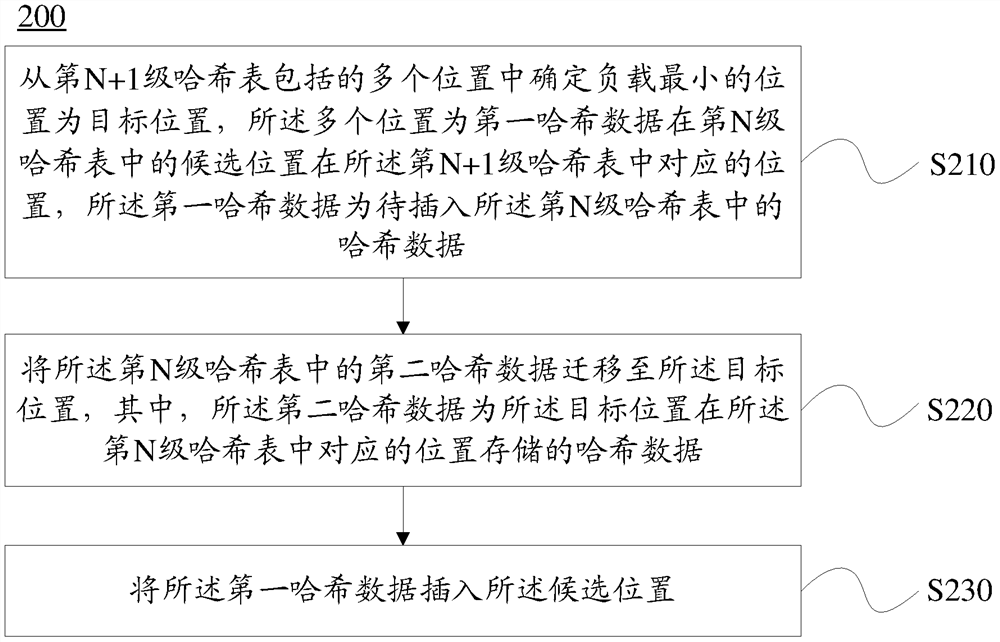
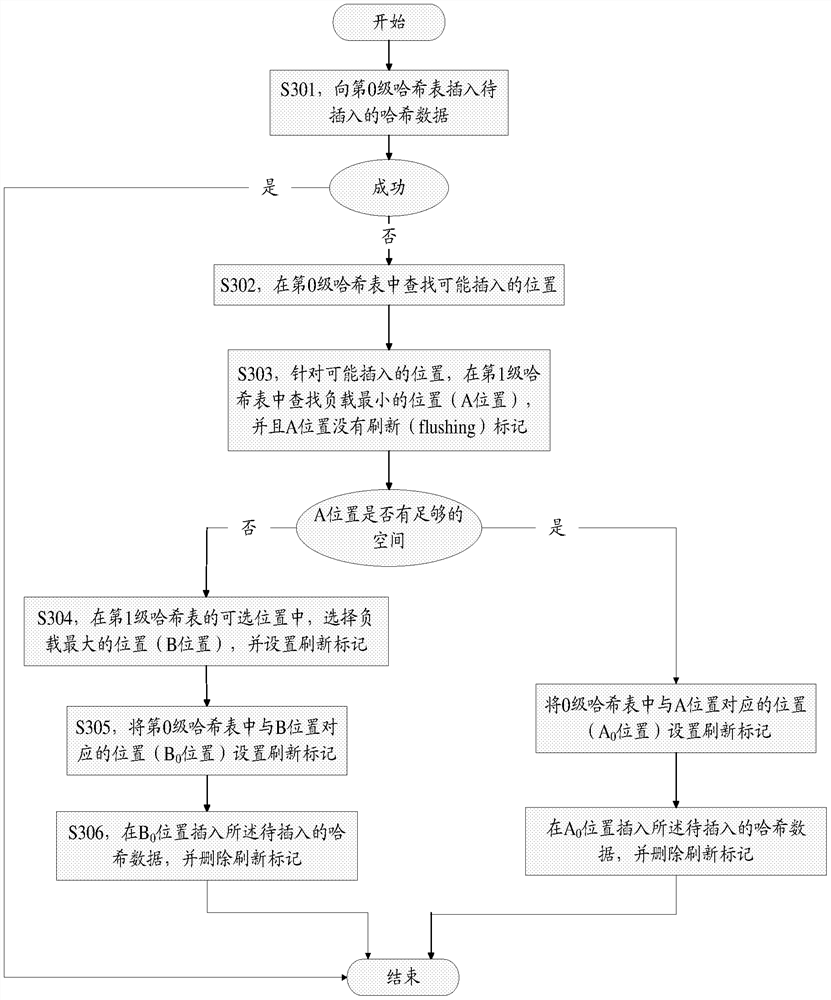
A data processing method (200) and device. The method (200) comprises: determining a position having the smallest load as a target position from among multiple positions included in an N+1th stage hash table, wherein the multiple positions are corresponding positions, in the N+1th stage hash table, of candidate positions of first hash data in an Nth stage hash table, and the first hash data is hash data to be inserted in the Nth stage hash table (S210); migrating second hash data in the Nth stage hash table to the target position, wherein the second hash data is hash data stored at a position in the Nth stage hash table corresponding to the target position (S220); inserting the first hash data into the candidate positions (S230). The described method and device may reduce the probability of hash conflicts in an N+1th stage hash table, and improve the reading and writing efficiency of the N+1th stage hash table.
Owner:HUAWEI TECH CO LTD
Features
- Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com