Scalable-ot-based privacy set intersection method and device
A privacy and collection technology, applied in the field of information processing, can solve the problems of increasing the amount of calculation for secure intersection and reducing the calculation efficiency, and achieve the effect of reducing the amount of calculation, simplifying the calculation process, and improving the calculation efficiency.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0045] The embodiment of the present invention provides a scalable-ot-based privacy set intersection method, which can avoid repeating the entire calculation process multiple times during the intersection calculation, greatly reduces the calculation amount of intersection calculation, and improves calculation efficiency , making the whole calculation process more concise.
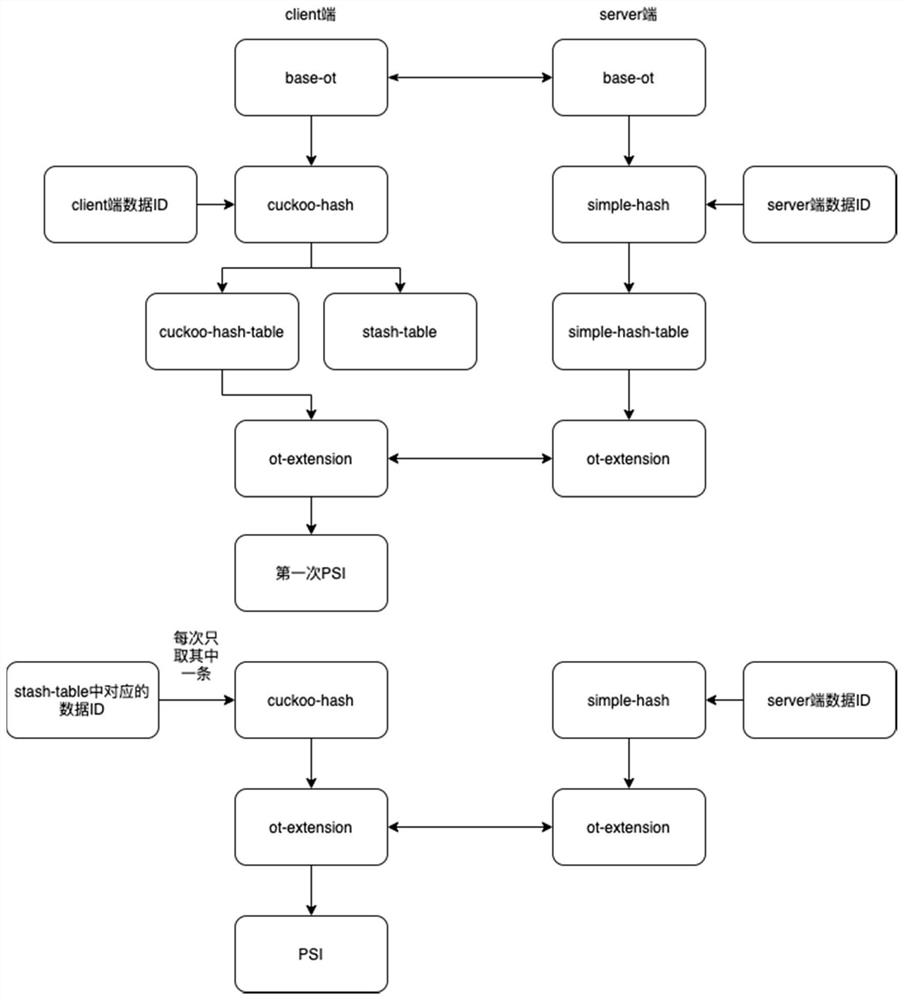
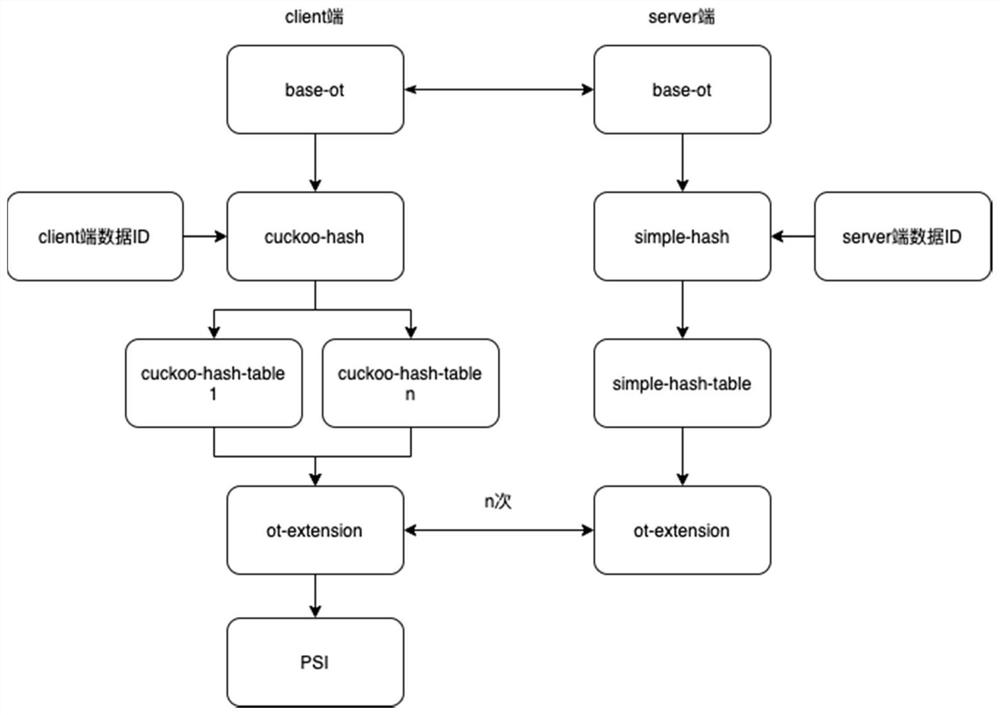
[0046] The privacy set intersection method based on scalable-ot provided by the embodiment of the present invention mainly involves two or more parties. Taking two parties as an example, refer to figure 2 and 3 As shown, the privacy set intersection method based on scalable-ot mainly includes a client (client) and a server (server). Specifically, the scalable-ot-based privacy set intersection method provided by the embodiment of the present invention includes the following steps:
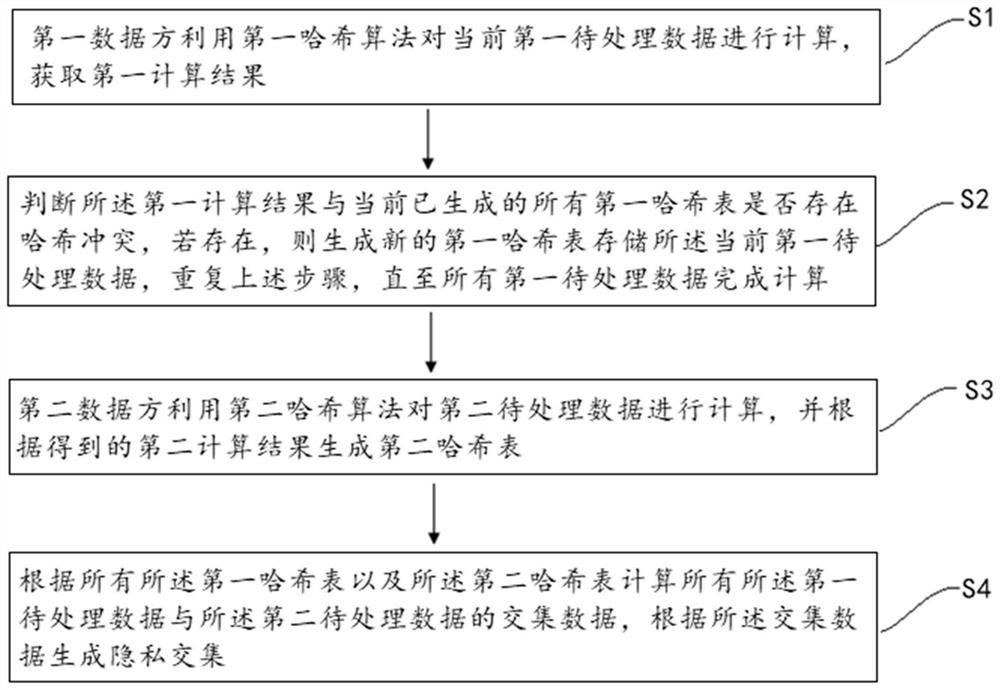
[0047] S1: The first data party uses the first hash algorithm to calculate the current first data to be processed, and obtai...
Embodiment 2
[0068] Corresponding to the above-mentioned first embodiment, the present invention also provides a scalable-ot-based privacy set intersection device, wherein, in this embodiment, for the same or similar content as the above-mentioned first embodiment, you can refer to the above introduction, and follow-up No longer. refer to Figure 4 The device includes:
[0069] The first calculation module is used for the first data party to use the first hash algorithm to calculate the current first data to be processed, and obtain the first calculation result;
[0070] A conflict judging module, configured to judge whether there is a hash conflict between the first calculation result and all the currently generated first hash tables;
[0071] A data storage module, configured to generate a new first hash table to store the current first data to be processed when there is a hash conflict between the first calculation result and all currently generated first hash tables;
[0072] The se...
Embodiment 3
[0082] Corresponding to the first and second embodiments above, the present invention also provides a computer device, including: a processor and a memory, the memory stores a computer program that can run on the processor, and when the computer program is executed by the processor, the above-mentioned A scalable-ot-based privacy set intersection method provided by any embodiment.
[0083] in, Figure 5 A computer device is exemplarily shown, and may specifically include a processor 1510 , a video display adapter 1511 , a disk drive 1512 , an input / output interface 1513 , a network interface 1514 , and a memory 1520 . The processor 1510 , video display adapter 1511 , disk drive 1512 , input / output interface 1513 , network interface 1514 , and the memory 1520 can be communicatively connected through a communication bus 1530 .
[0084] Wherein, the processor 1510 may be implemented by a general-purpose CPU (Central Processing Unit, central processing unit), a microprocessor, an...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com