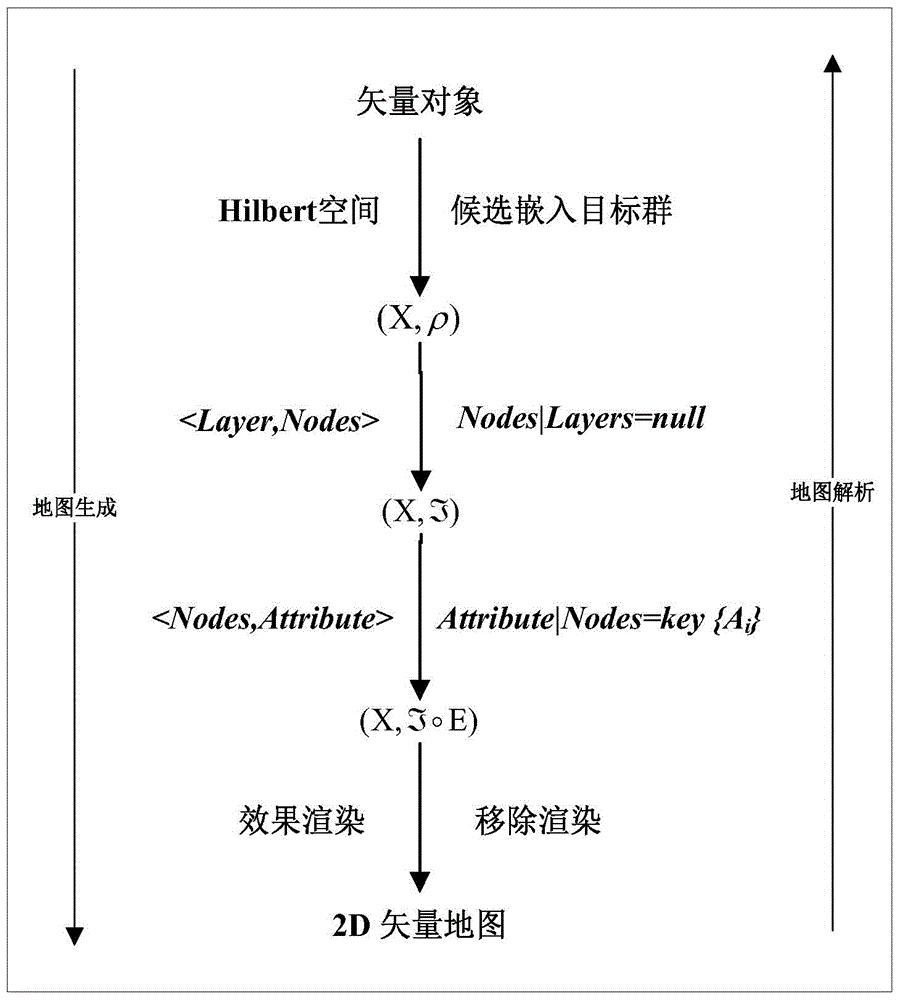
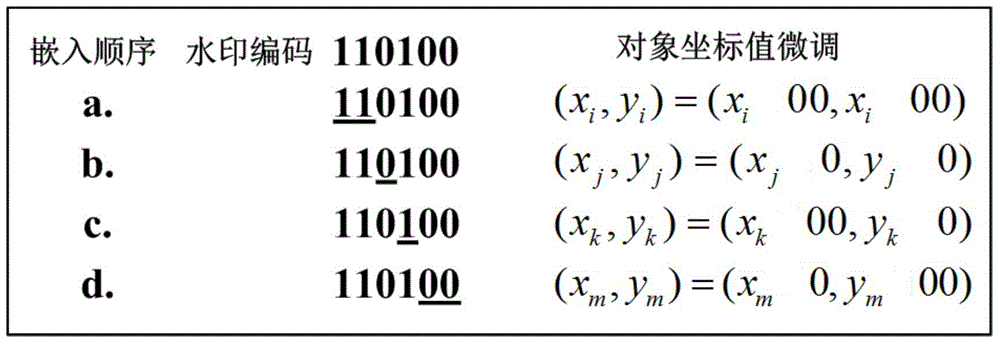
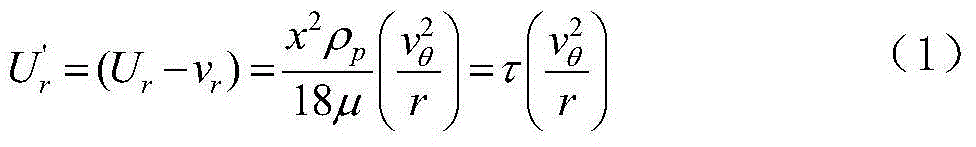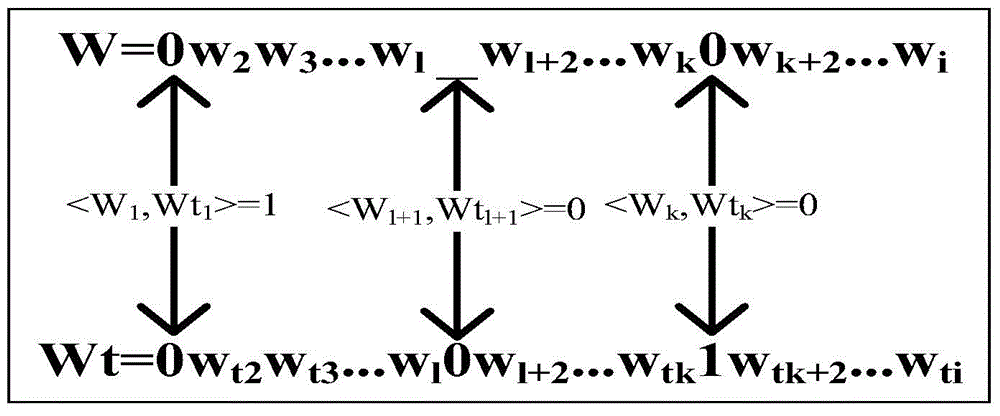Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
75 results about "Content integrity" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Defining Content Integrity. Content specialists have historically defined content integrity as quality content created and delivered in a timely way, with alignment to audience intentions and actions. While this is a good start, the definition assumes there is a simple audience and company relationship that functions in isolation.
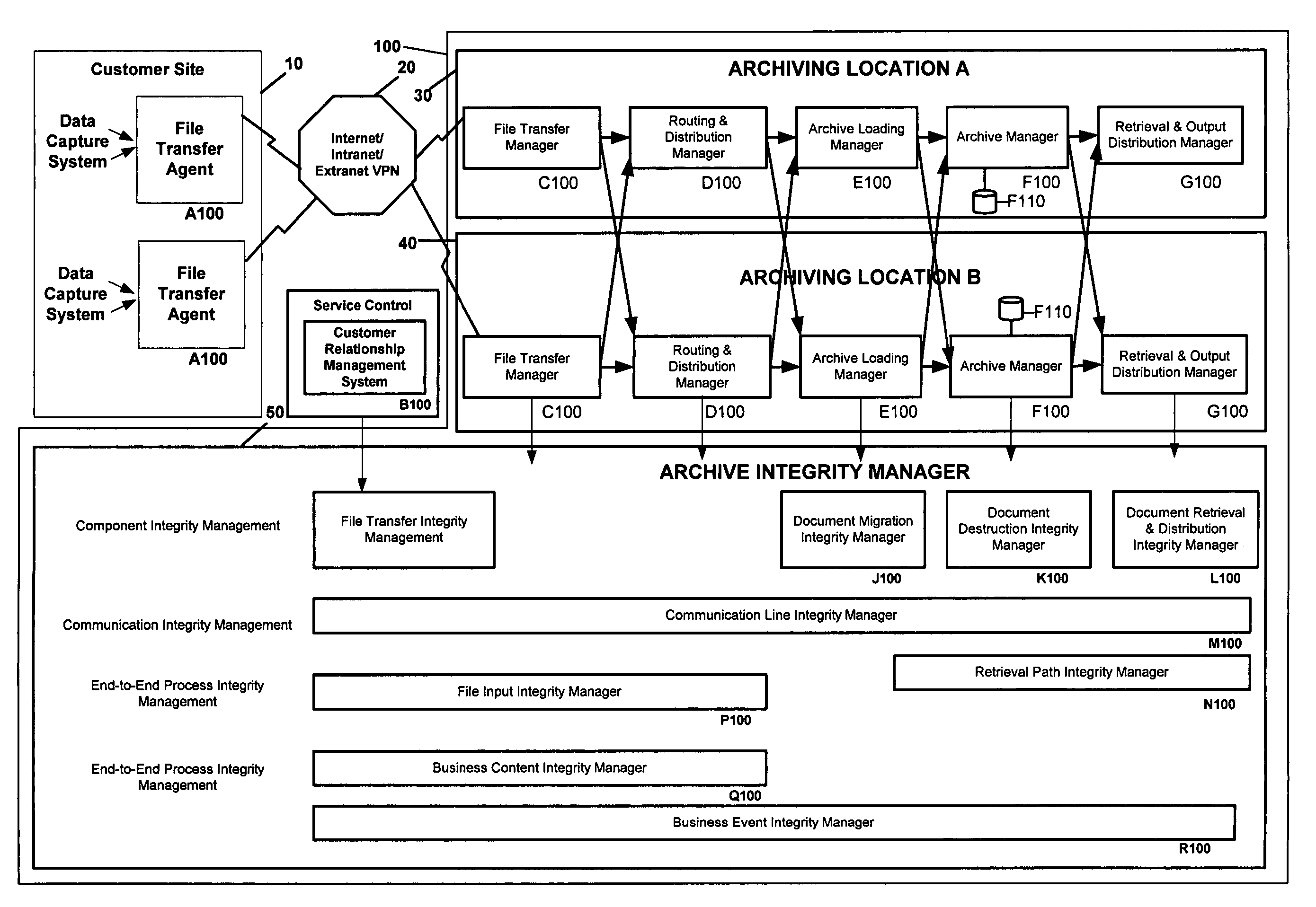
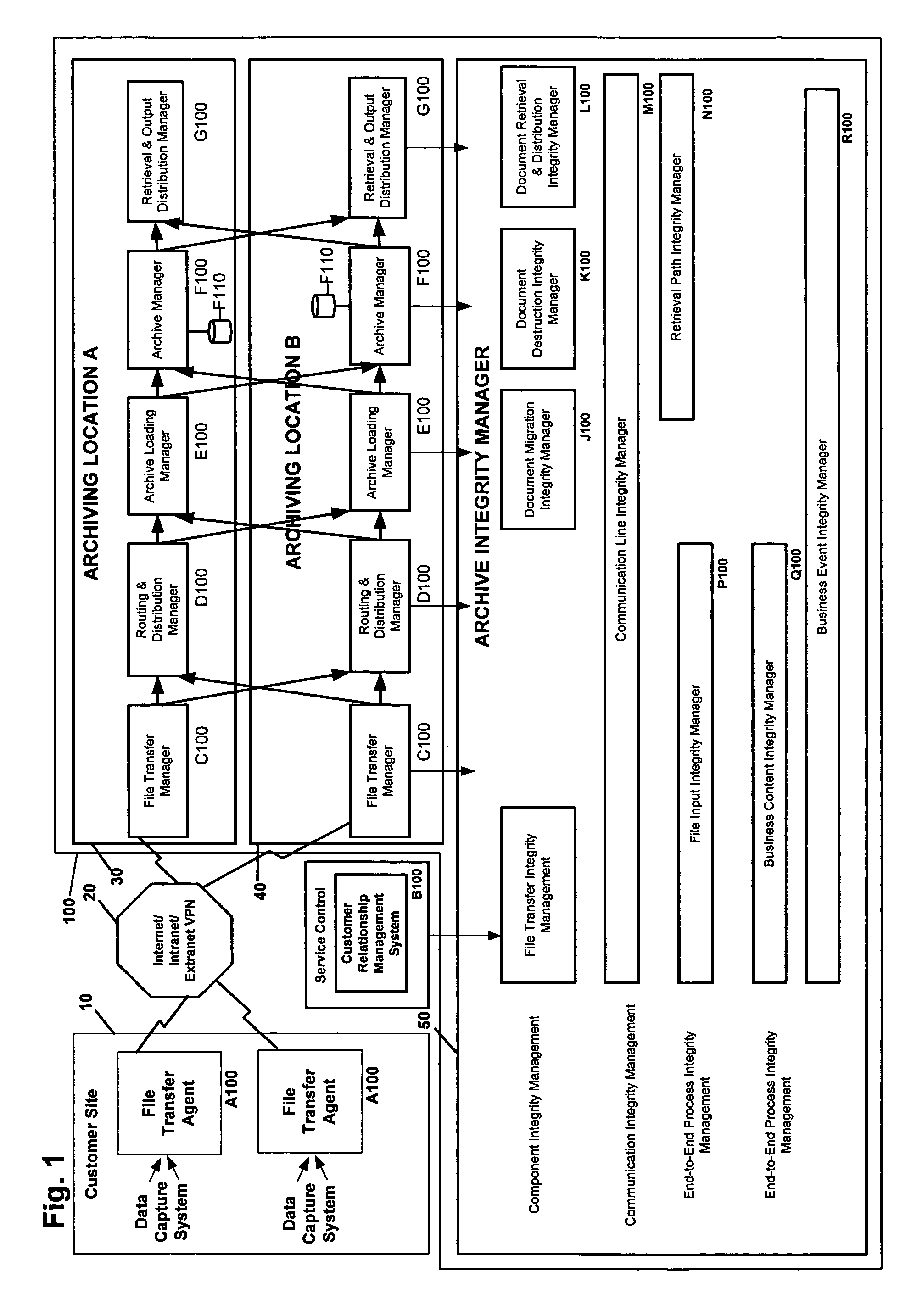
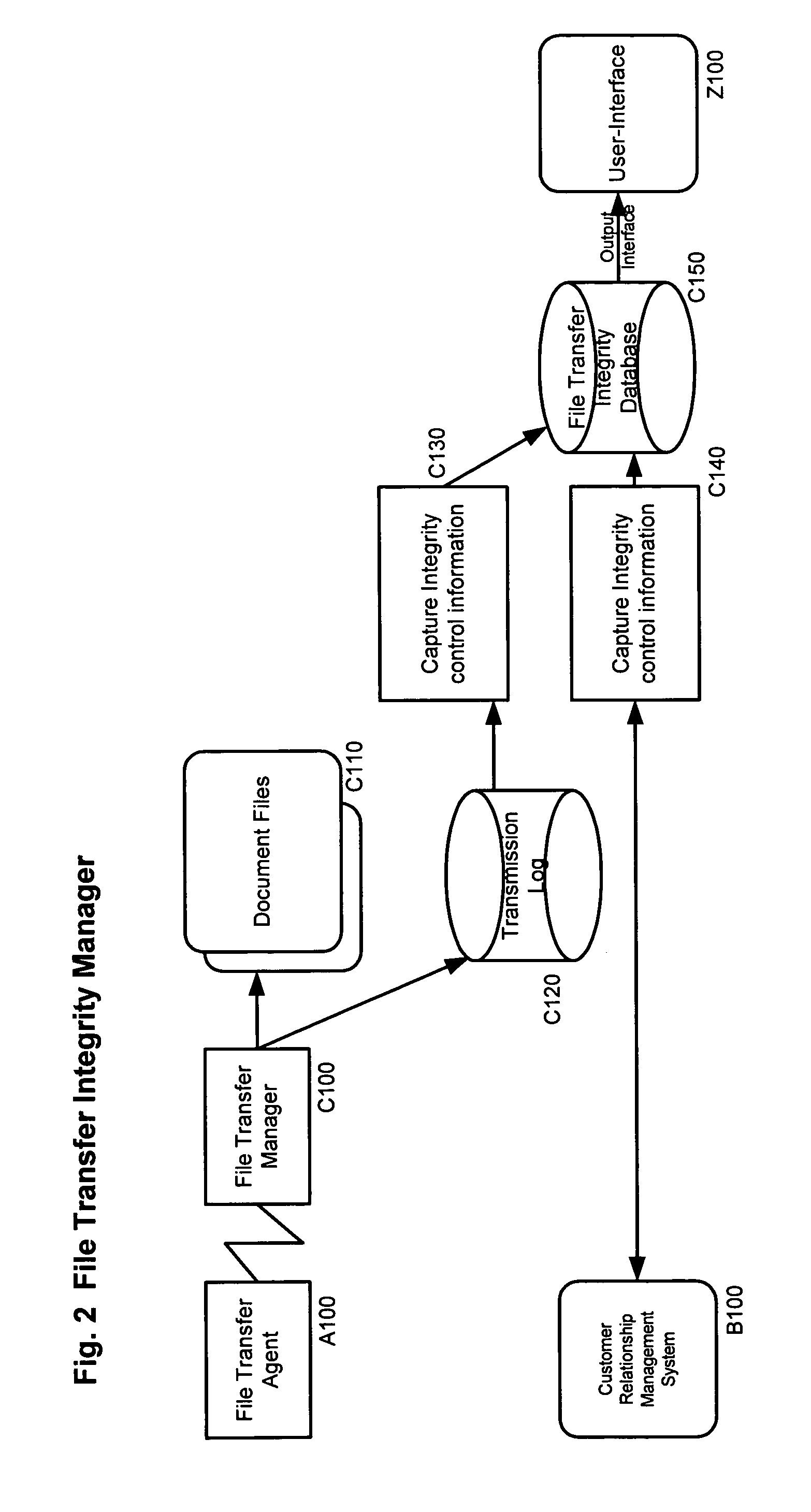
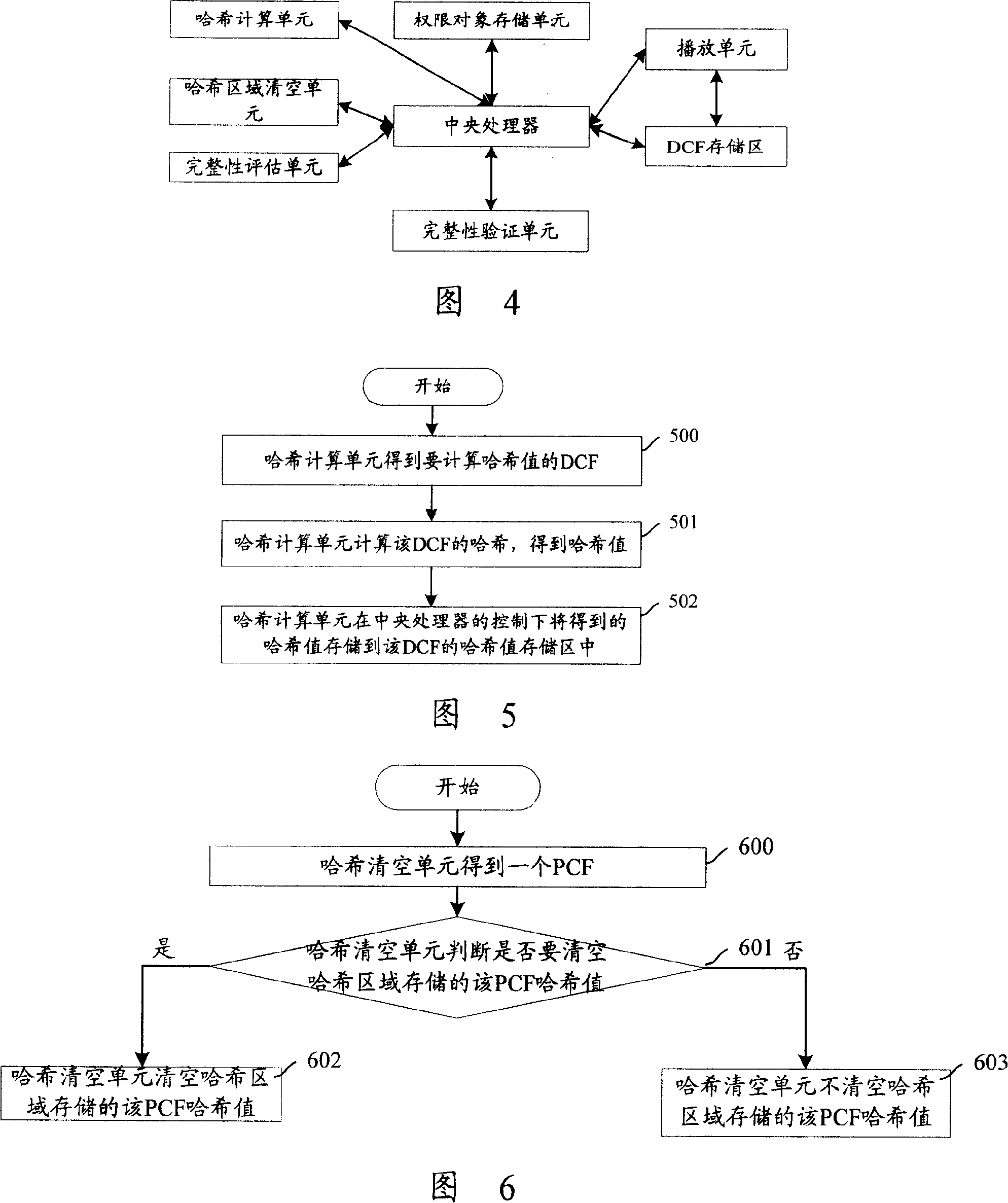
System for archive integrity management and related methods
ActiveUS7069278B2Data processing applicationsDigital data information retrievalEvent triggerData file
A system for archive integrity management and related methods are disclosed. The invention includes one or more integrity manager applications, each of which monitor the integrity of an aspect of a data archive. Some integrity manager applications monitor the integrity of processes executed by the archive system, and other integrity manager applications monitor the integrity of communication paths in the archive system. A file input integrity manager application monitors the integrity of a plurality of processes associated with storing a new data file in the archive. A business content integrity manager application determines what documents are required for a transaction and monitors whether all of the required documents have been received by the archive system. Further, an event integrity manager application executes predetermined events triggered by characteristics of documents stored in the archive system and ensures that all events have been properly executed.
Owner:JPMORGAN CHASE BANK NA
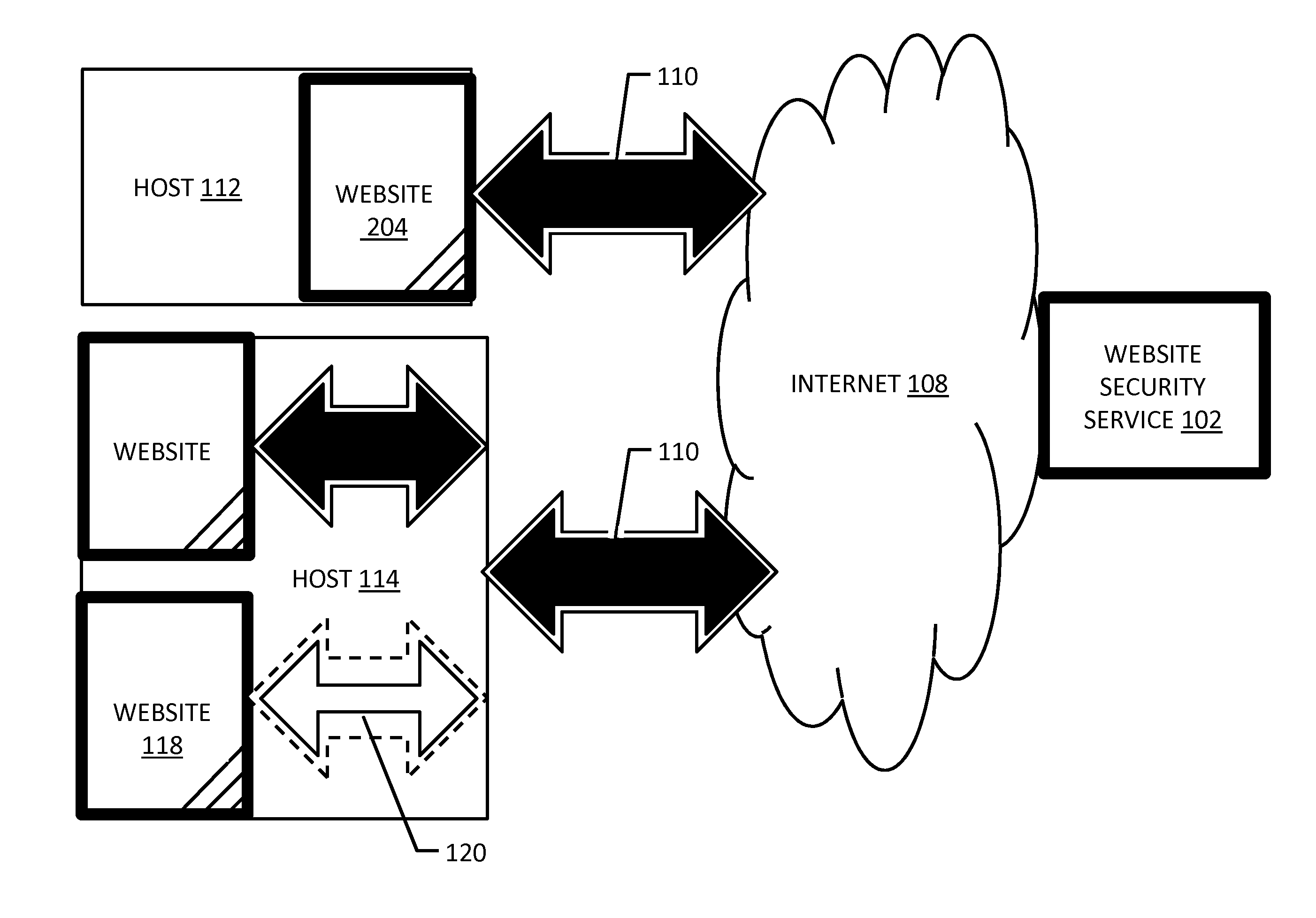
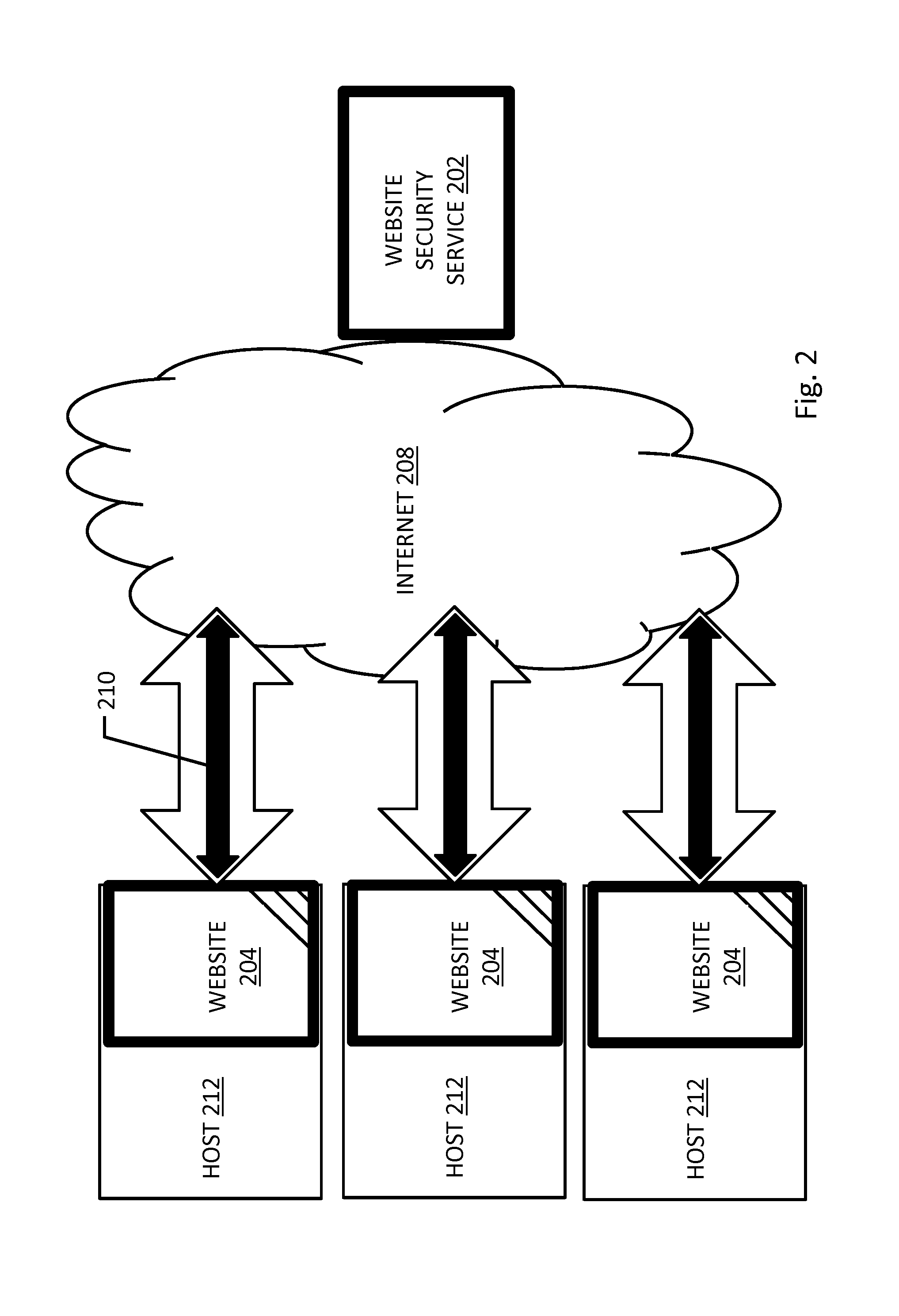
Selective website vulnerability and infection testing
ActiveUS20120036580A1Easy to identifyMemory loss protectionError detection/correctionBandwidth availabilityWorld Wide Web
In embodiments of the present invention improved capabilities are described for selective website vulnerability and infection testing and intelligently paced rigorous direct website testing. By providing robust website content integrity checking while only lightly loading the website hosting server, visitor bandwidth availability is maintained through selective testing and intelligently paced external website exercising. A modular pod-based computing architecture of interconnected severs configured with a sharded database facilitates selective website testing and intelligent direct website test pacing while providing scalability to support large numbers of website testing subscribers.
Owner:SITELOCK
Method and system for website content integrity assurance
InactiveUS20010044820A1Digital data protectionMultiple digital computer combinationsWeb siteInternet privacy
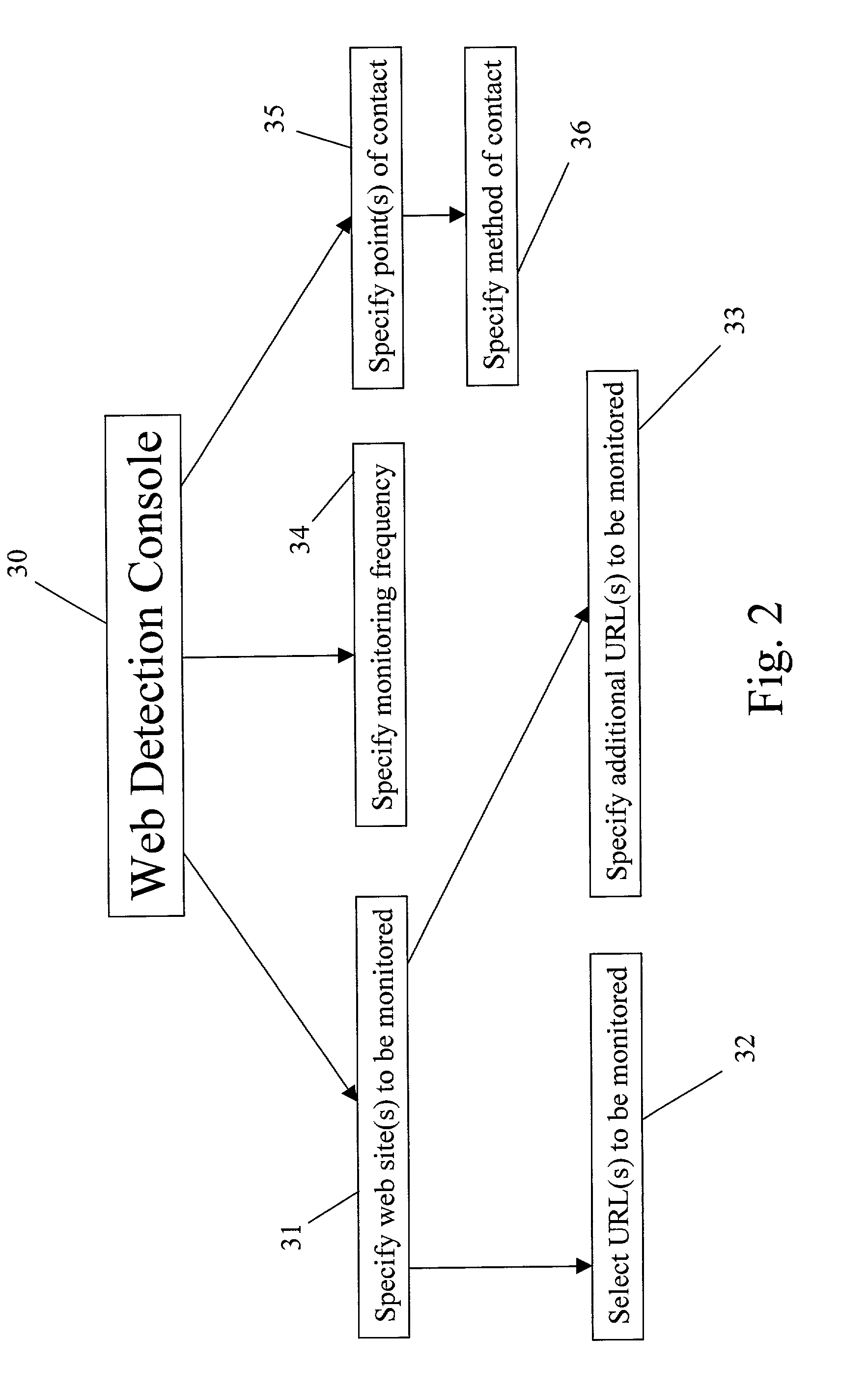
An improved method and system for monitoring and detecting changes to static, dynamic, and active web content is disclosed. The system includes a web detection manager, a web detection agent, and a web detection console. The web detection console configures the web detection manager to monitor at least one web page. The web detection manager requests web site information from the web detection agent. The web detection agent provides the web detection manager with the requested web site information and the web detection manager processes that information to determine whether the content of each web page being monitored has been altered. The web site information includes the encoded content of each web page being monitored.
Owner:PREDICTIVE SYST
Protecting content integrity
InactiveUS20160212101A1Digital data processing detailsUser identity/authority verificationWorld Wide WebWeb content
A request for a resource of web content is received. It is determined whether the request identifies the resource using a transformed identifier that has been generated by transforming an original identifier of the resource. In the event it is determined that the request identifies the resource using the transformed identifier, the transformed identifier is translated back to the original identifier of the resource. The resource is obtained using the original identifier of the resource. The obtained resource is provided as a response to the request for the resource of web content.
Owner:AKAMAI TECH INC
Information hiding method facing to H.264/AVC (automatic volume control) video
InactiveCN102223540AEnsure safetyIncrease hidden capacityTelevision systemsDigital video signal modificationAutomatic controlMotion vector
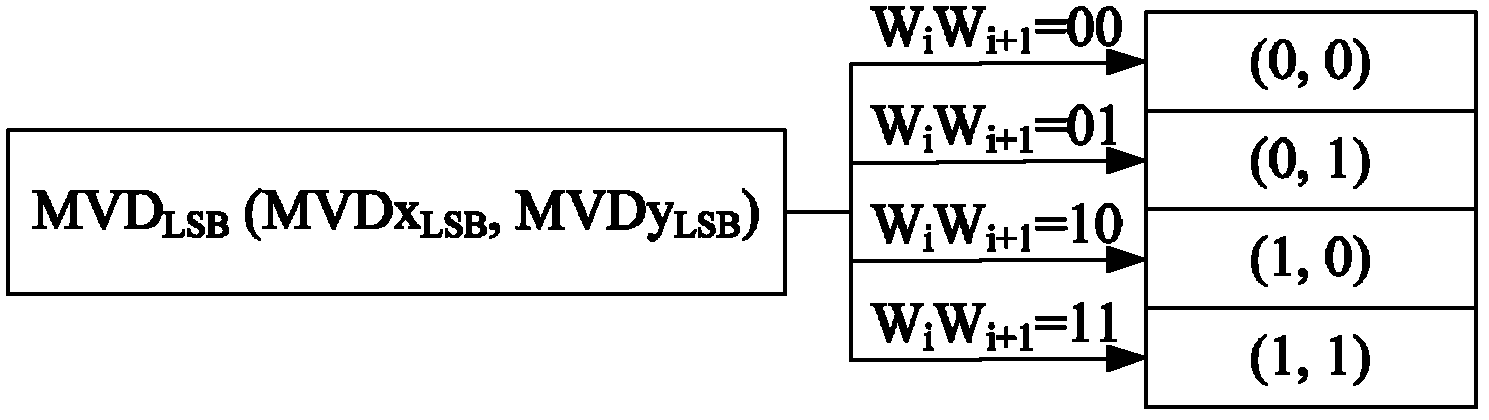
The invention discloses an information hiding method facing to an H.264 / AVC (automatic volume control) video. The embedding of watermark information is realized through modifying a data communication terminal (DCT) coefficient of a frame I, but for a frame B and a frame P, the embedding of the hiding information is realized through modifying motion vector data (MVD), thus on one hand, the embedded watermark information can be used for authenticating the integrity of the content of the video streaming, and on the other hand, whether the video is attacked is judged, and whether the extracted information is credible and the like at an information detection end according to the integrity of the extracted watermark information, thus ensuring the safety of the private information; as the frame P and frame B in a video sequence are divided into a motion subblocks from the size range of 16*16 to 4*4; the smaller subblock division provides a large amount of MVD data which can provide for hiding the private information, thus the video has larger information hiding capacity; and the process extracting the information is simple and rapid, does not need an original video file for reference, and only needs to decode the DCT coefficient of the frame I and the MVD data of the frame B and frame P, thereby effectively improving the instantaneity and the practicability.
Owner:NINGBO UNIV
Multipoint safe videoconference system with IP set-top box based on H.323 protocol
InactiveCN101938624AEasy to embedImprove data transmission qualityTelevision conference systemsTwo-way working systemsMultipoint control unitConference management
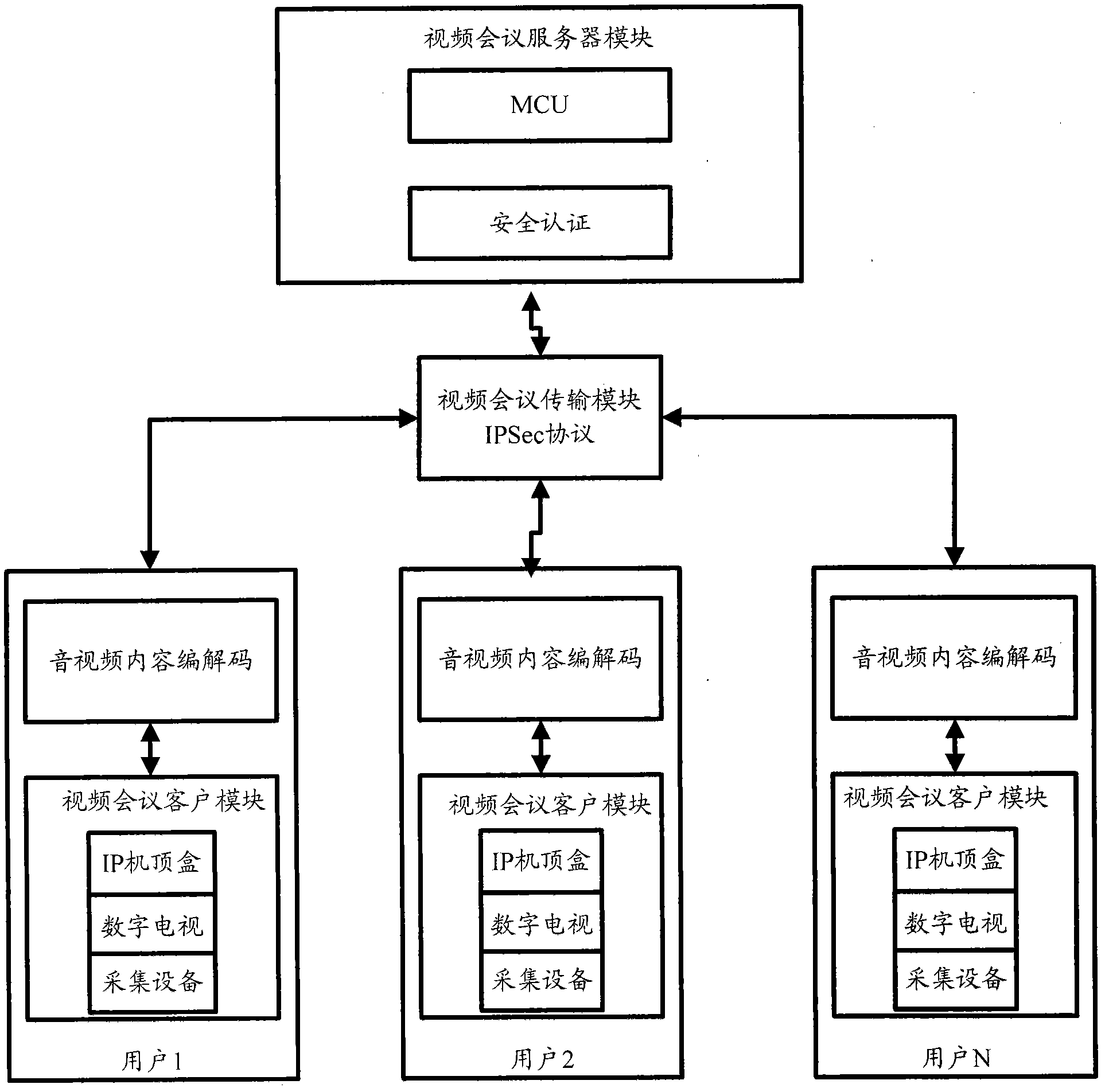
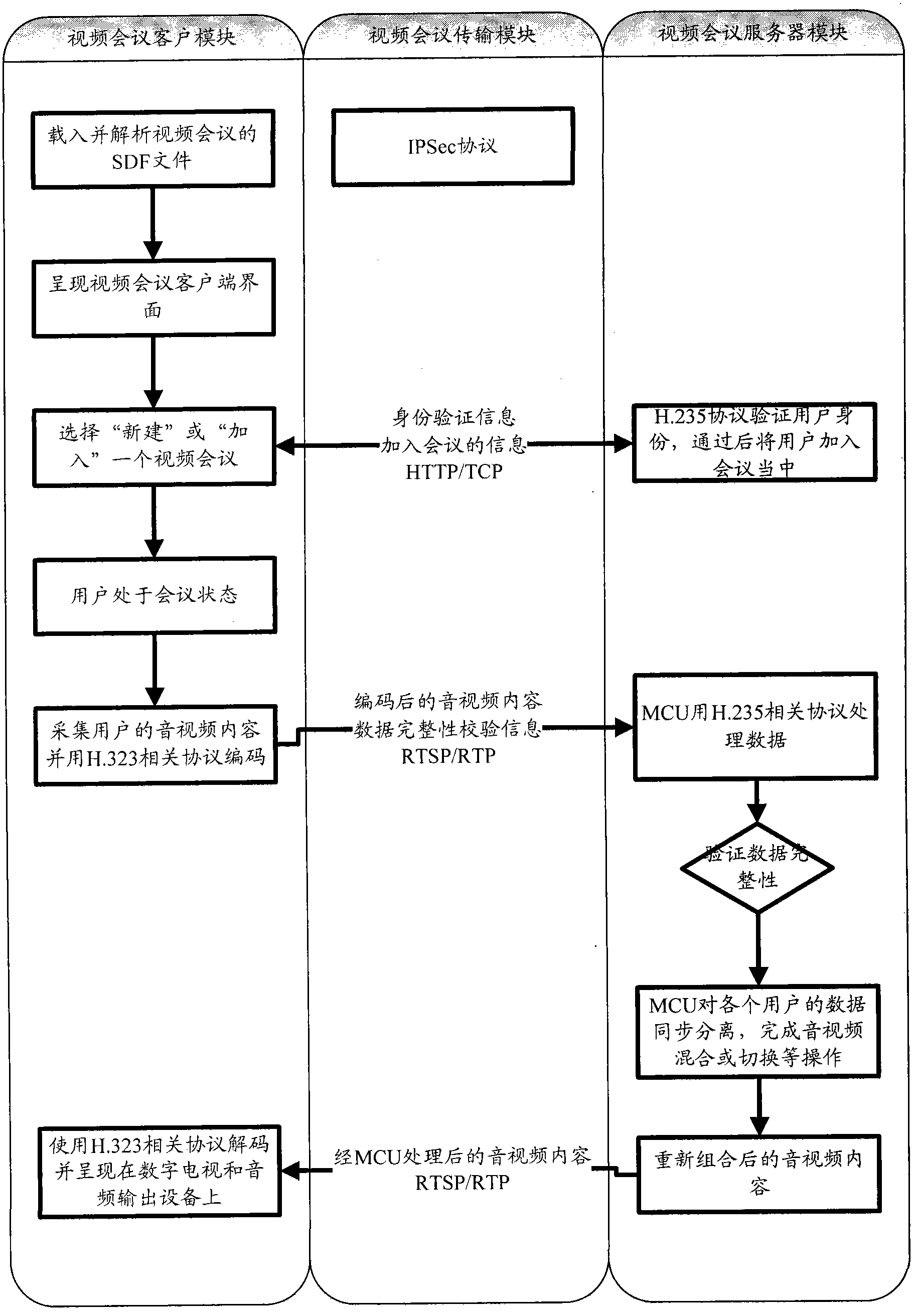
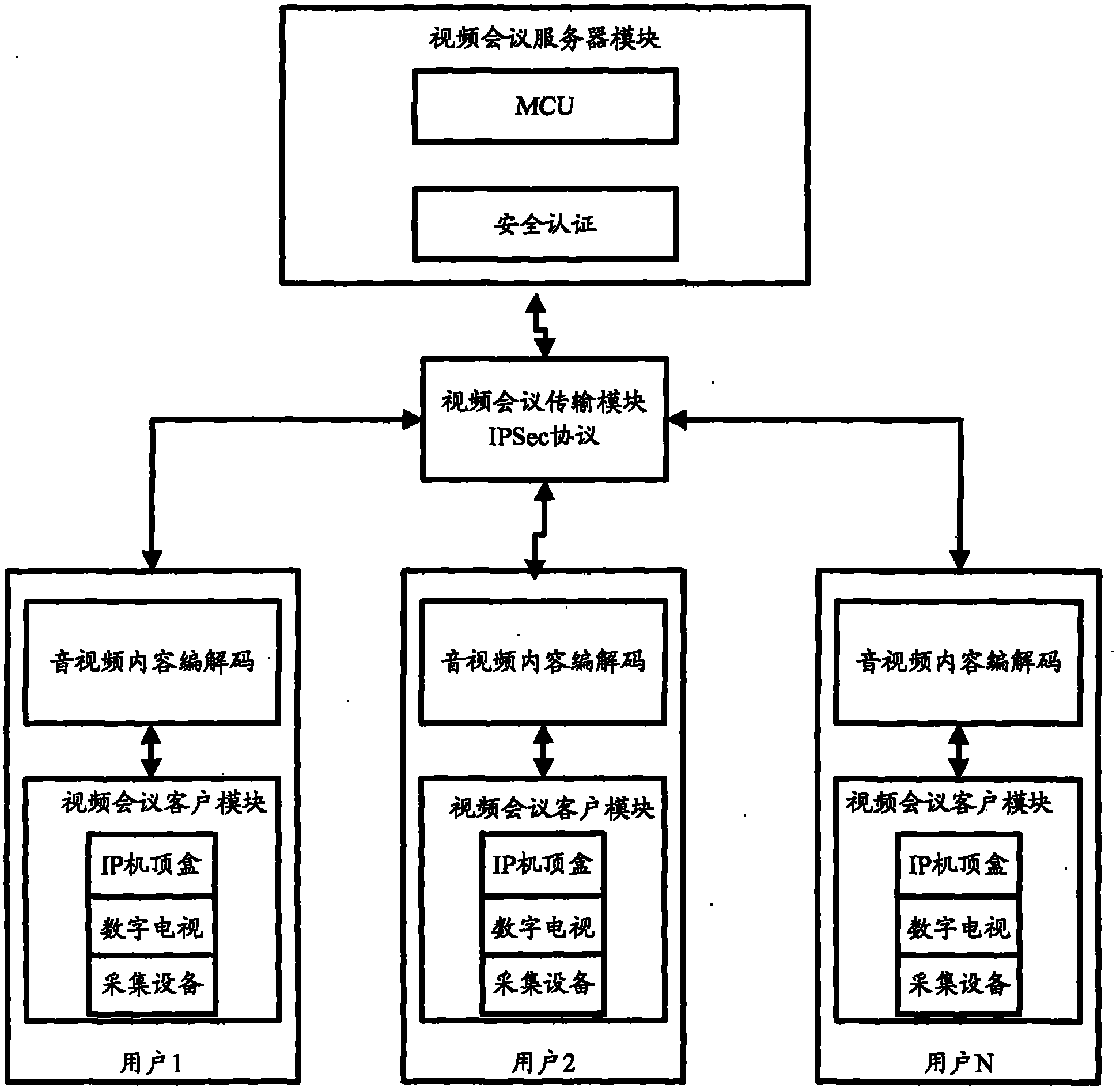
The invention discloses a multipoint safe videoconference system with an IP set-top box based on an H.323 protocol, which comprises a videoconference client module, a videoconference transmission module and a videoconference server module; the videoconference client module comprises the IP set-top box, a digital television and an audio / video acquisition and playing device and is used for realizing the identity verification of a videoconference user and the functions of acquiring, receiving and playing an audio / video content; the videoconference server module consists of a multipoint control unit (MCU) based on the H.323 protocol and is used for realizing functions of conference management, the integrity verification of the audio / video content, the identity verification of a user at a client, and the distribution and the processing of the audio / video content; and the videoconference transmission module realizes the transmission of the audio / video content between the user participating in a conference and a videoconference server by using a digital television network. According to the invention, a digital television user can realize a safe videoconference by the digital television with higher safety.
Owner:SUN YAT SEN UNIV
Reversible watermark method for image certification
InactiveCN1885341AIncrease embedding capacityImprove visual effectsImage data processing detailsWatermark methodBit plane
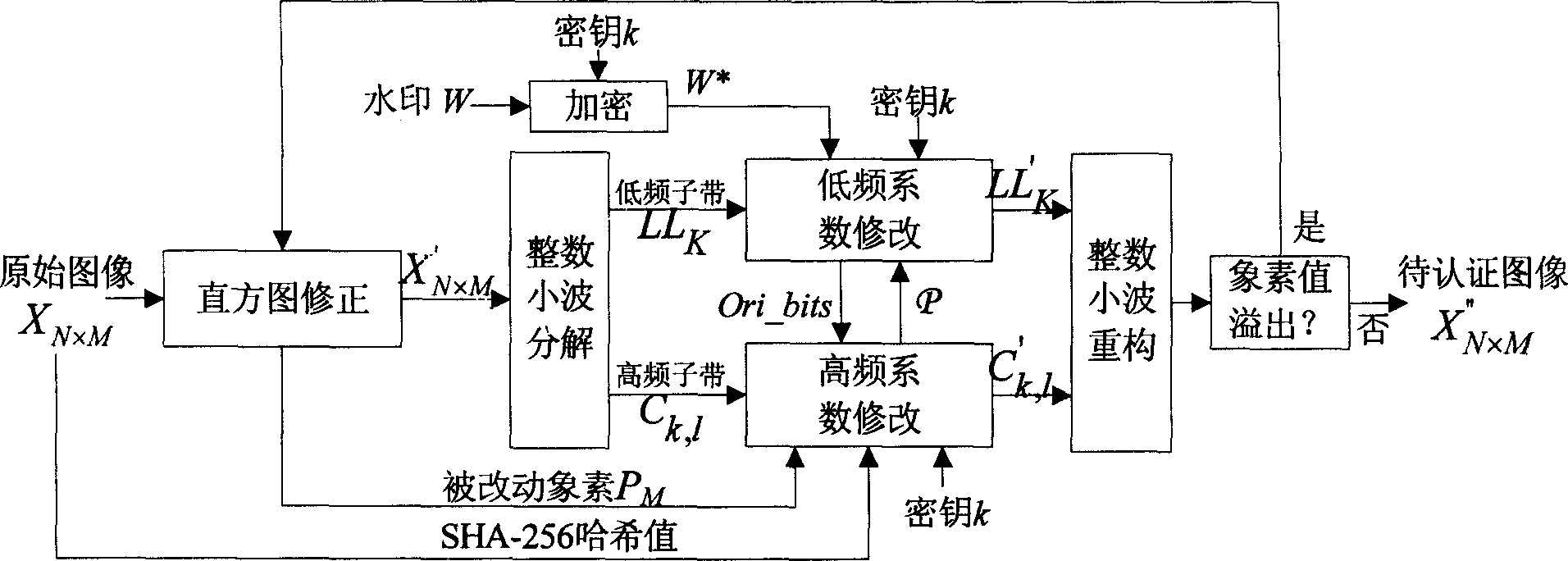
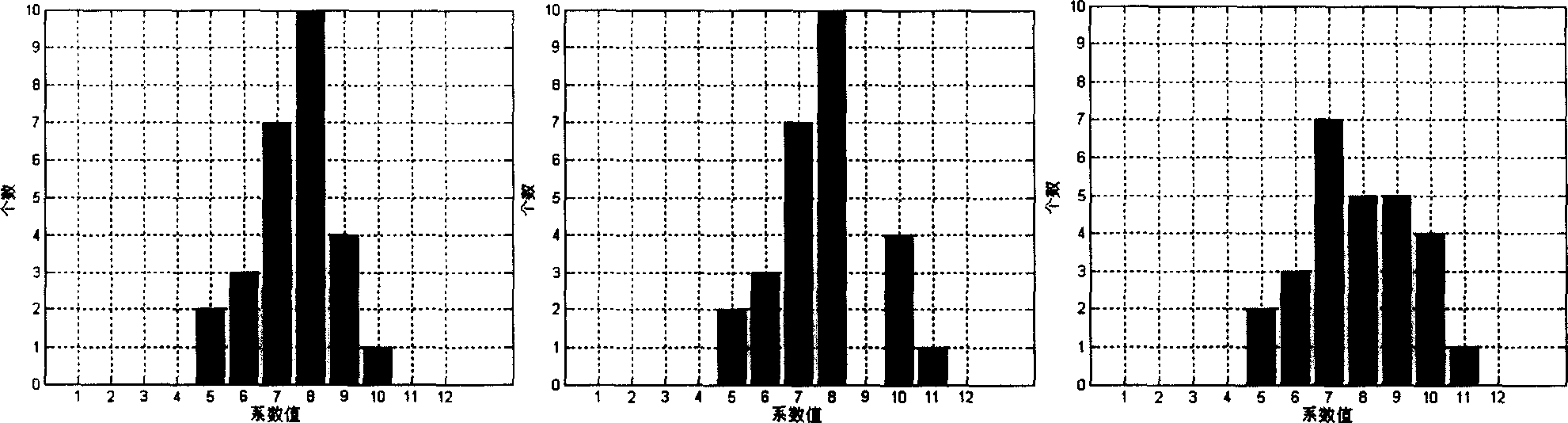
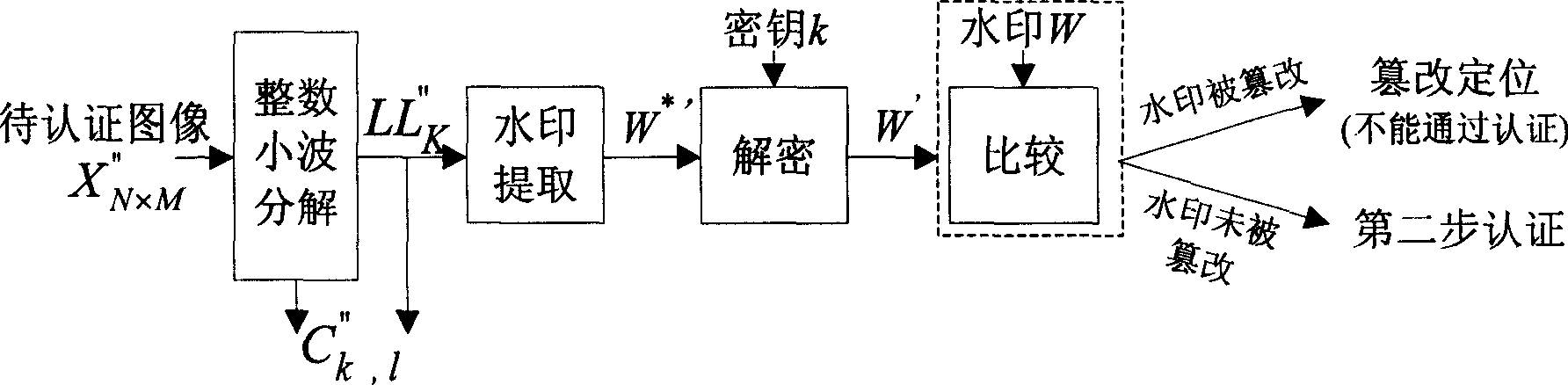
The invention relates to a reversible watermark method used in image identification, belonging to multimedia information safety technique, wherein the invention modifies high-frequency sub-band histogram to embed the SHA-256 Haxi value of original image and the data used to recover image into high-frequency sub-band; via replacing the most low bit plane of low-frequency sub-band to embed the useful watermark into low-frequency sub-band; based on extracted watermark or the differential value picture between extracted watermark and former watermark to process falsification check and positioning; comparing extracted Haxi value and the Haxi value of returned image to process content completeness check. The invention can resist false impact, check and position falsification, to return original image without aberration.
Owner:SUN YAT SEN UNIV
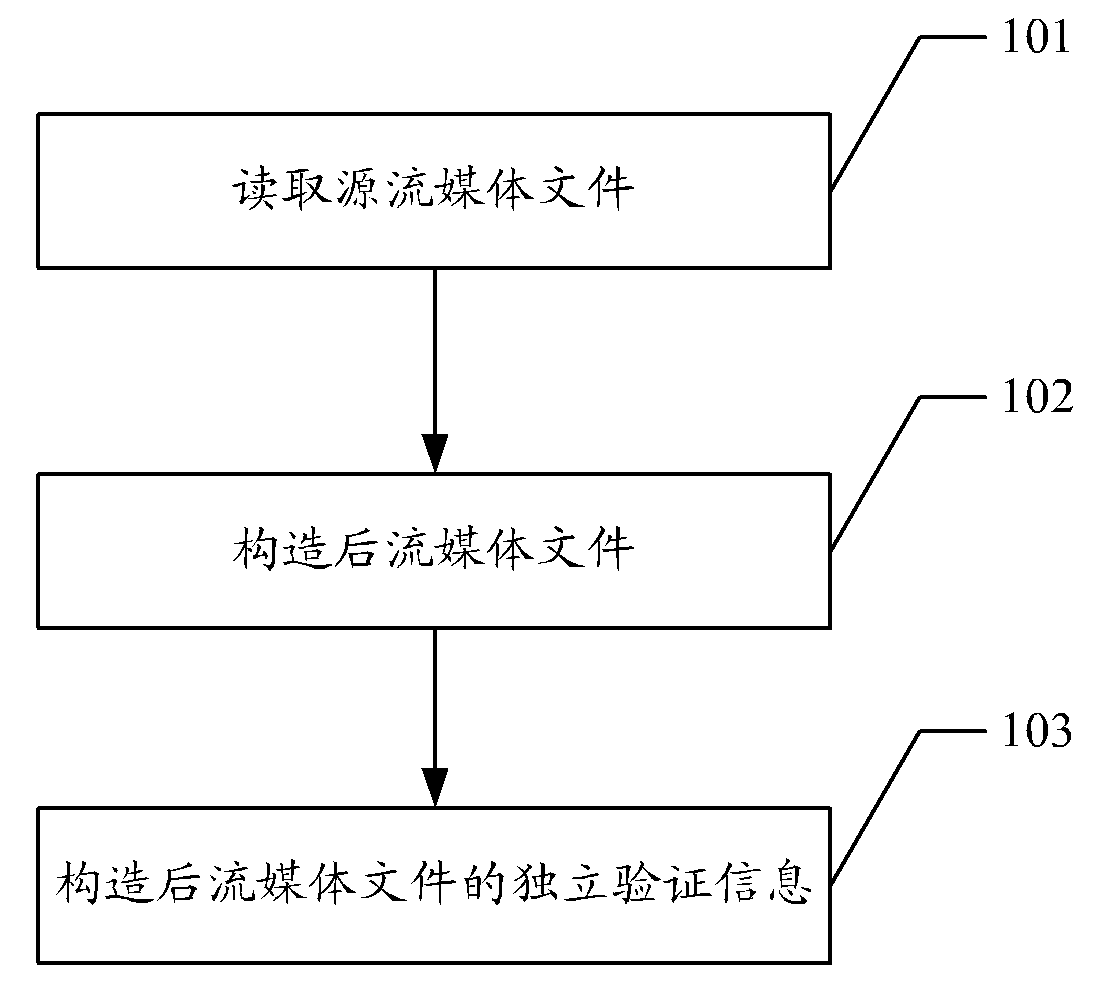
Method, equipment and system for validating completeness of protected contents
ActiveCN101131718ALower latencyImprove experienceDigital data protectionUser deviceComputer security
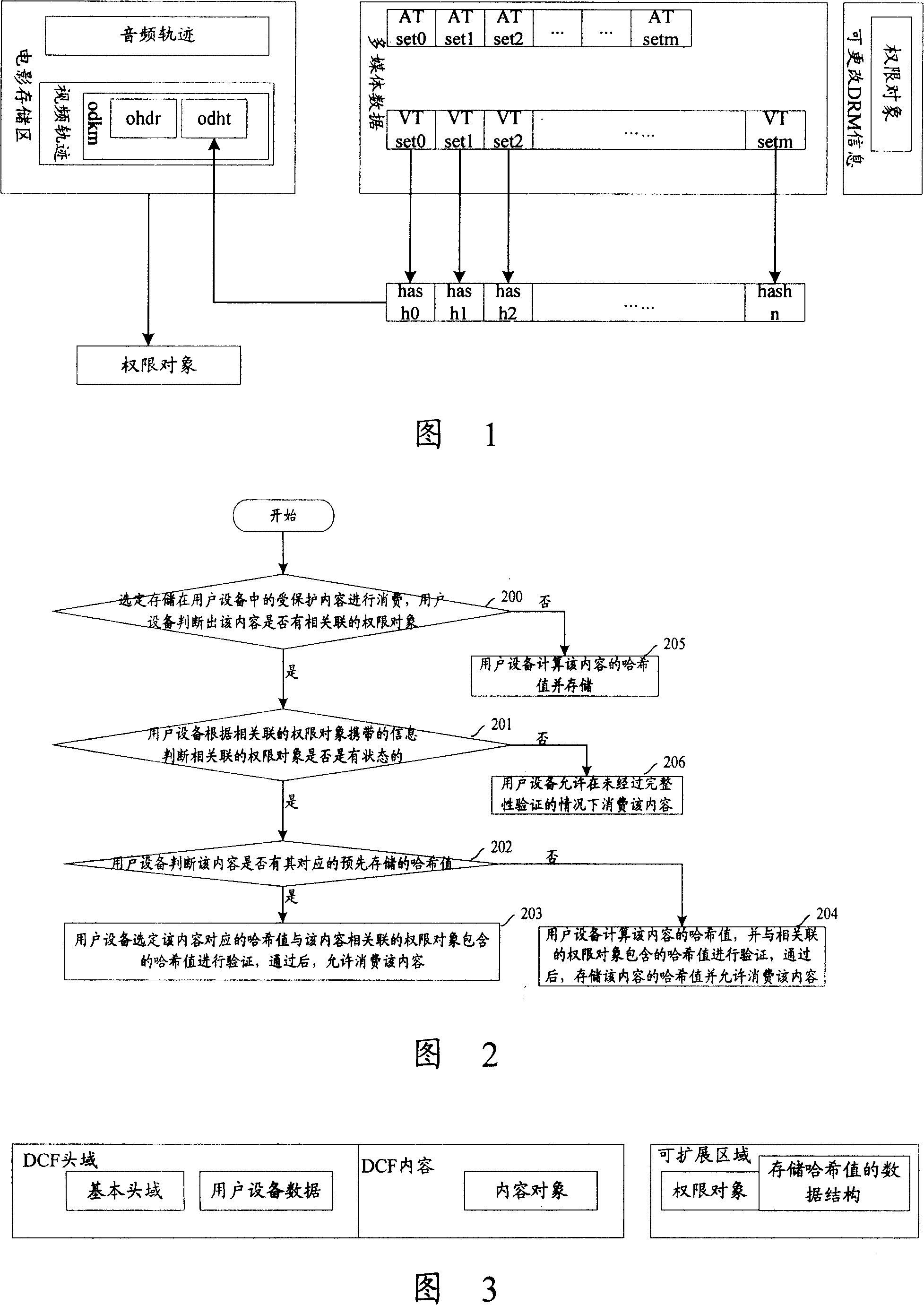
The invention discloses a kind of method, device and system to verify the integrity of the protected content. The method includes: storing the hash value of the protected content of the computer, during verifying the integrity of the protected content before consuming the protected content, users' device compares the hash value of the protected content with hash value of the authority target related to the content, if they are accord, the content passes the verification of the integrity; or does not passes. The invention solves the problem that the users can not experience very well because consuming the content verifying the integrity of the content frequently leads to the delay of consuming the content. Further, the situation of no-consumption authority target consumes the consumed content with the system.
Owner:HUAWEI TECH CO LTD
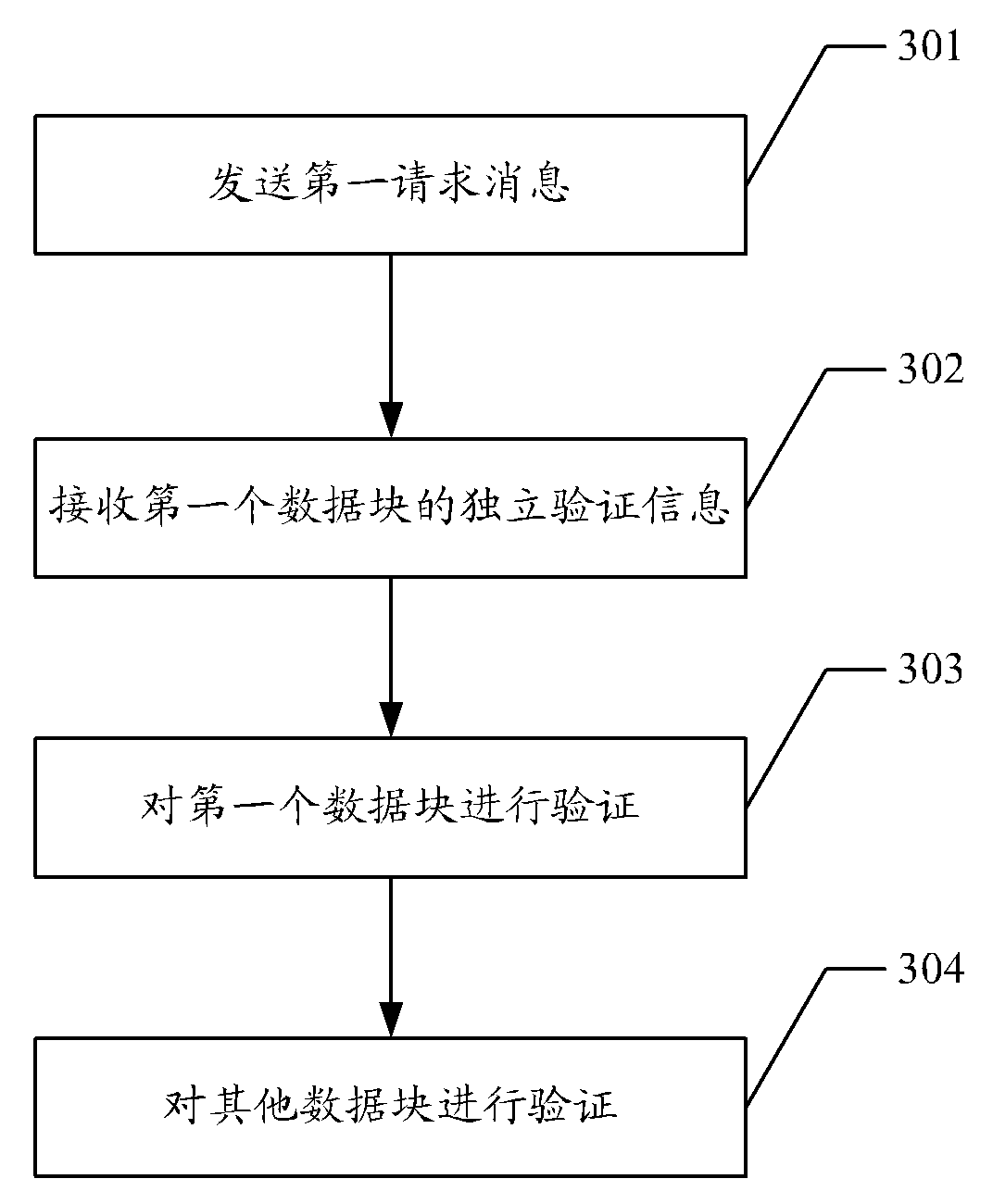
Method, device and system for verifying content integrity of streaming media
InactiveCN102137089AReduce transmission overheadUser identity/authority verificationSelective content distributionTerminal equipmentComputer terminal
The embodiment of the invention discloses a method for verifying the content integrity of a streaming media, further provides a corresponding device and system. In the embodiment of the invention, a streaming media server processes a source streaming media file to obtain a post streaming media file, wherein a data block of the post flow streaming media file carries verification information of a next data block, and the streaming media server further constructs independent verification information of each data block in the post streaming media file and singly saves the independent verification information. Therefore, the embodiment of the invention can ensure that all data blocks of the post streaming media file downloaded by the terminal device are absolutely continuously verified, and the transmission cost is lower after the terminal device downloads the post streaming media file.
Owner:HUAWEI TECH CO LTD
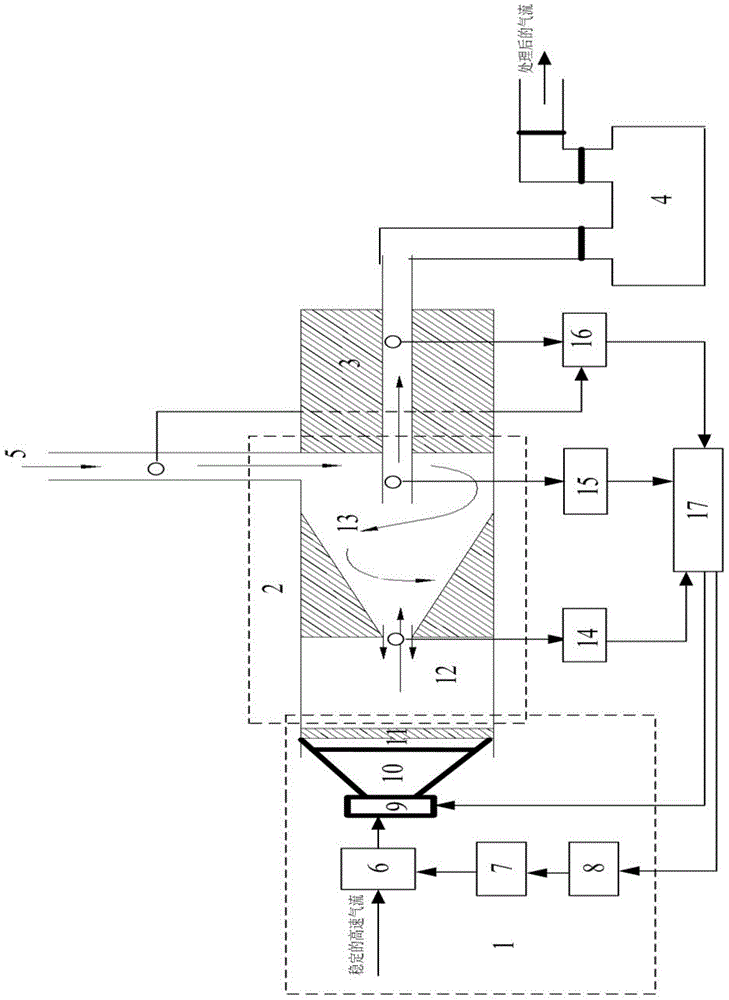
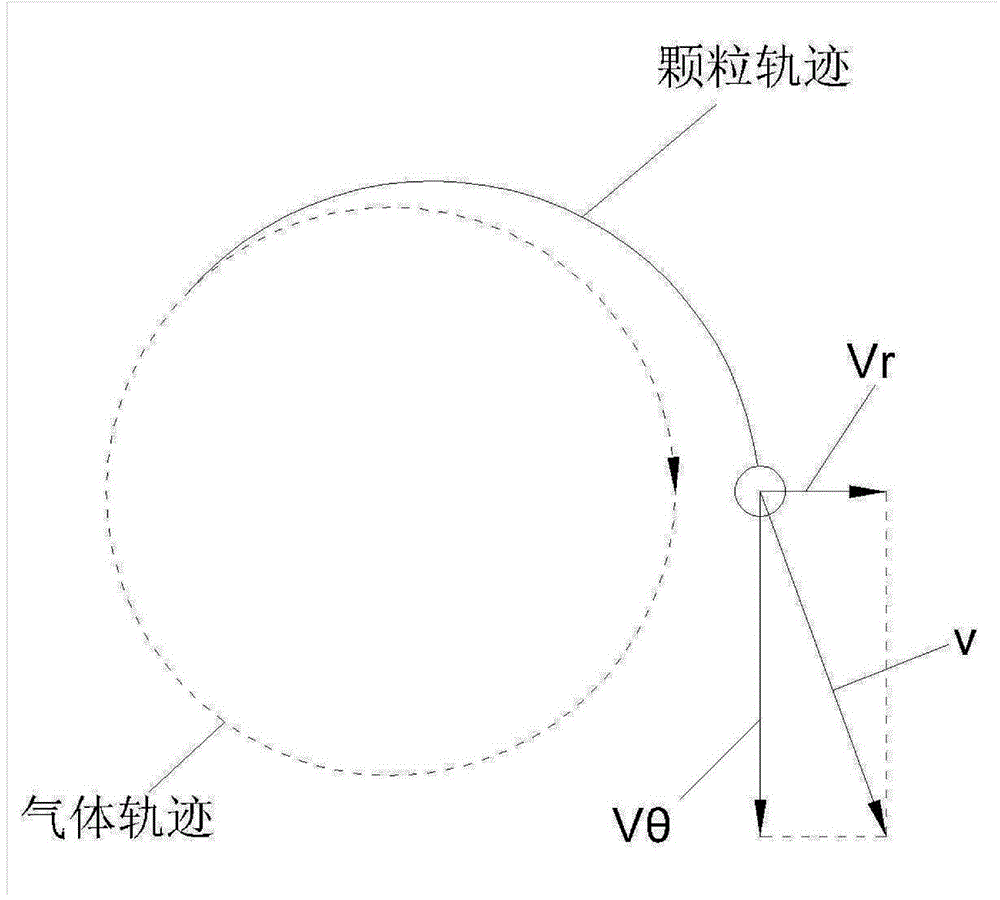
Fine particulate matter removal device and method with combined action of acoustic agglomeration and cyclone separation
InactiveCN104128047AEfficient removalDispersed particle separationEnergy based chemical/physical/physico-chemical processesCycloneImaging processing
The invention discloses a fine particulate matter removal device and method with combined action of acoustic agglomeration and cyclone separation. The device is embedded in each terminal workstation in an MIS system, is used for adding an invisible watermark to an acquired new image, and also provides integrity detection and tampering localization analysis for terminal work management and image processing. The technical method is embedded and integrated into a management information system for authenticating image content integrity and locating a tampered image region, and the method can be expressed as integrated external hardware when in concrete realization. The realization of the whole device scheme is divided into two parts: one, image characteristic information as the watermark is generated by the original image, the watermark information is subjected to chaotic encryption and then embedded into the original image, and the invisibility of the watermark information is realized under a condition without increasing the bandwidth; and two, a watermark-containing medical image is subjected to watermark extraction on a receiving end, the image can be subjected to integrity detection, the tampered image region is located, and thus a strong support is provided for further decision.
Owner:CENT SOUTH UNIV
Selective website vulnerability and infection testing
ActiveUS9246932B2Easy to identifyMemory loss protectionError detection/correctionModularityDirect site
In embodiments of the present invention improved capabilities are described for selective website vulnerability and infection testing and intelligently paced rigorous direct website testing. By providing robust website content integrity checking while only lightly loading the website hosting server, visitor bandwidth availability is maintained through selective testing and intelligently paced external website exercising. A modular pod-based computing architecture of interconnected severs configured with a sharded database facilitates selective website testing and intelligent direct website test pacing while providing scalability to support large numbers of website testing subscribers.
Owner:SITELOCK
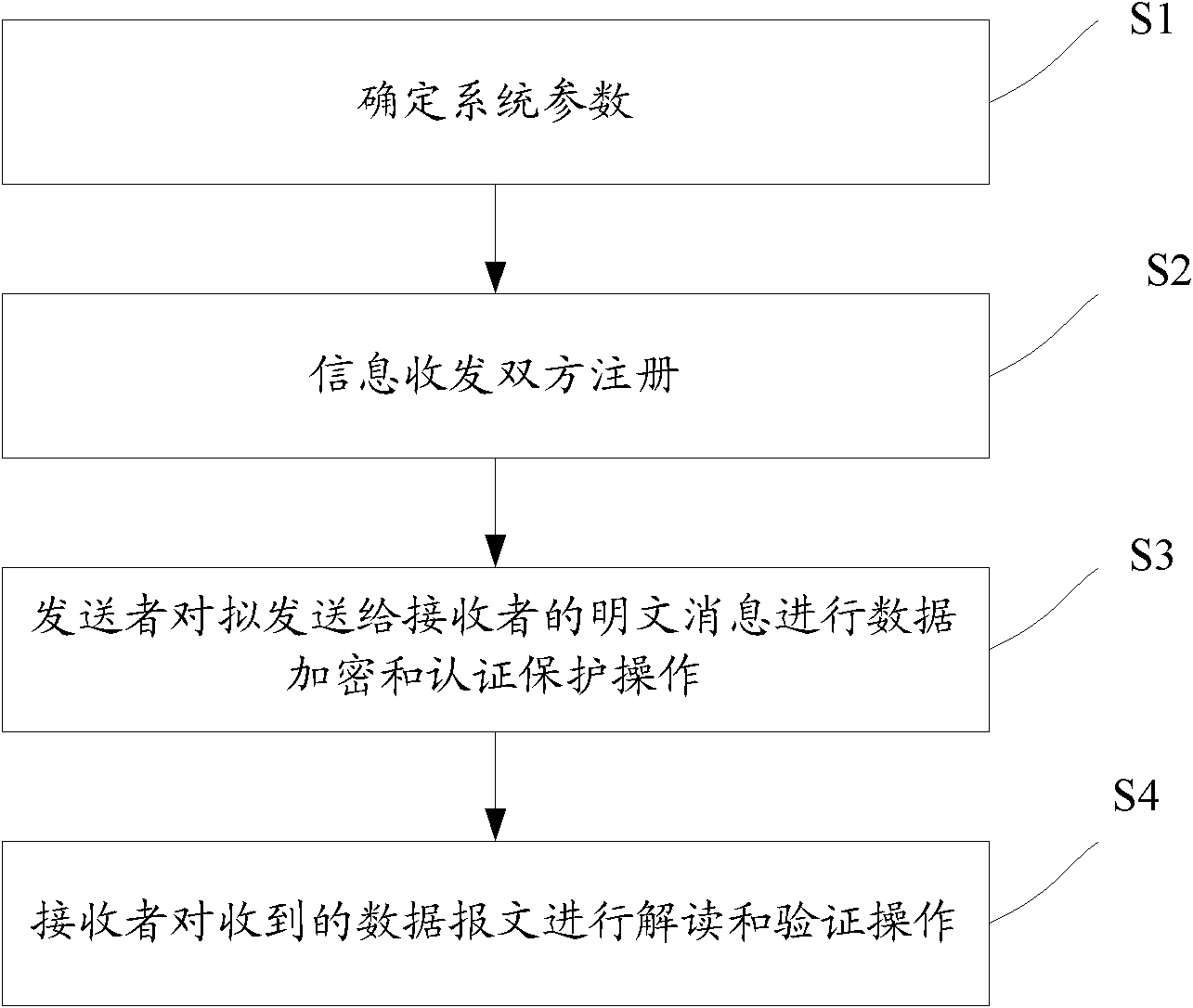
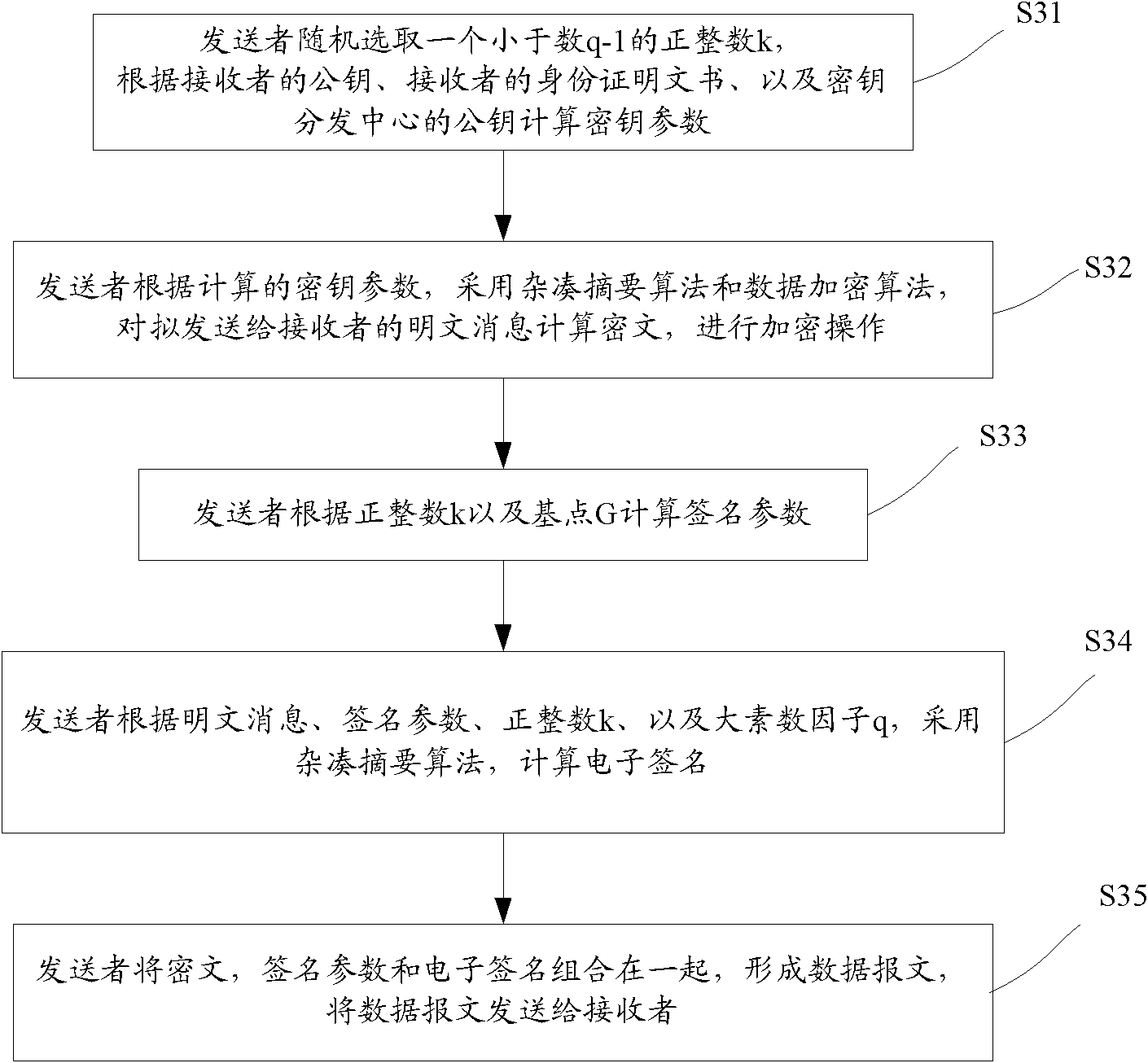
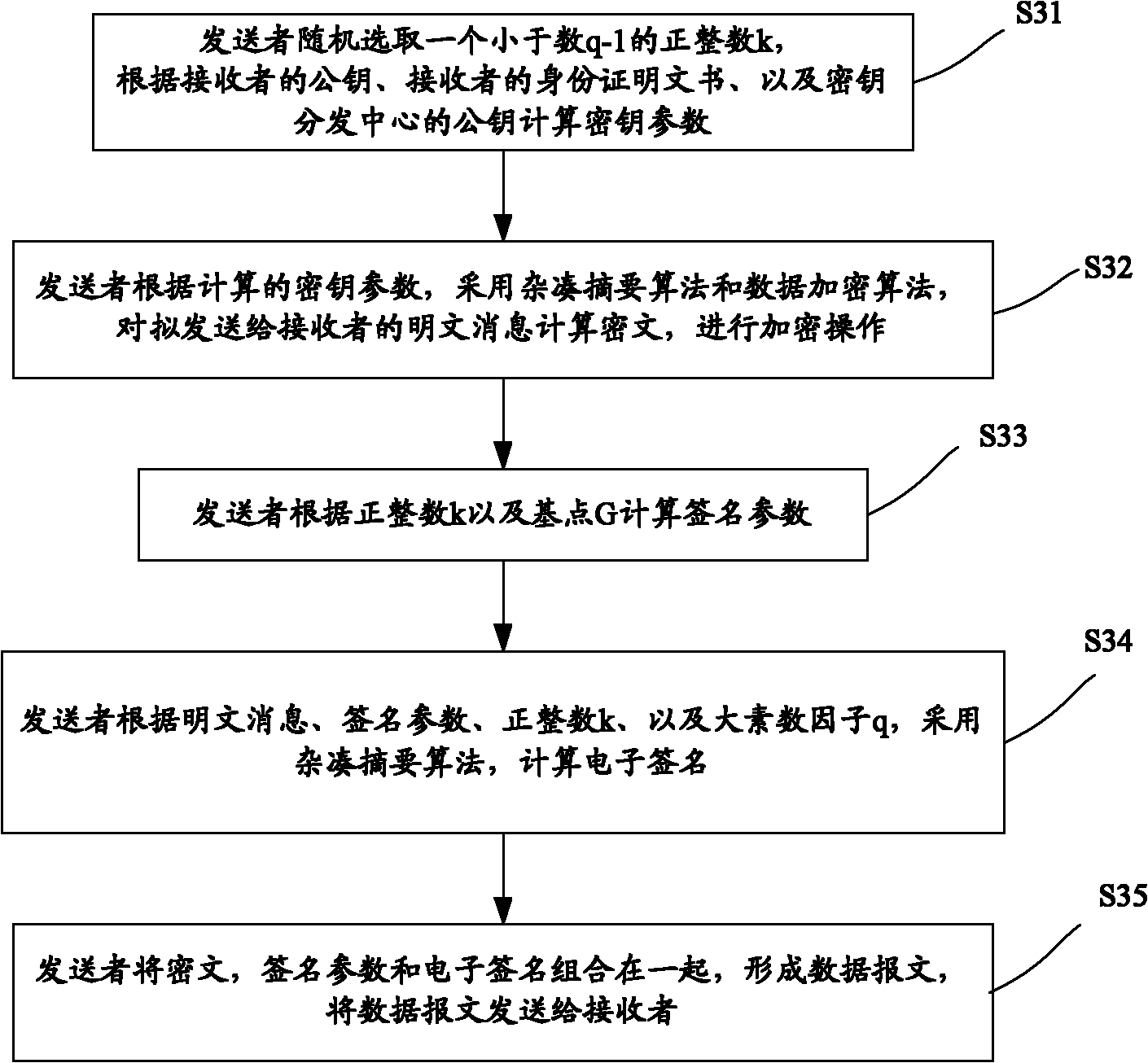
Method for encrypting and authenticating efficient data without authentication center
InactiveCN101931536AGuaranteed confidentialityGuarantee authenticityKey distribution for secure communicationUser identity/authority verificationPlaintextCiphertext
The invention discloses a method for encrypting and authenticating efficient data without an authentication center, which comprises the following steps of: (1) determining system parameters; (2) registering information receiving and transmitting parties; (3) performing data encryption and authentication protection on plaintext messages to be sent to a receiver by a sender; and (4) reading and authenticating the received data messages by the receiver, wherein in the step (3), ciphertexts, signature parameters and electronic signatures are combined by calculating secret key parameters, calculating the ciphertexts and the signature parameters on the plaintext messages according to the secret key parameters and calculating the electronic signatures according to the plaintext messages, the signature parameters and the like to form and send the data messages. Through the method of the invention, data encryption and the authentication of content integrity on the plaintext messages can be performed simultaneously and efficiently, and a series of problems caused by adopting the authentication center in the conventional method can be prevented.
Owner:WUHAN UNIV OF TECH
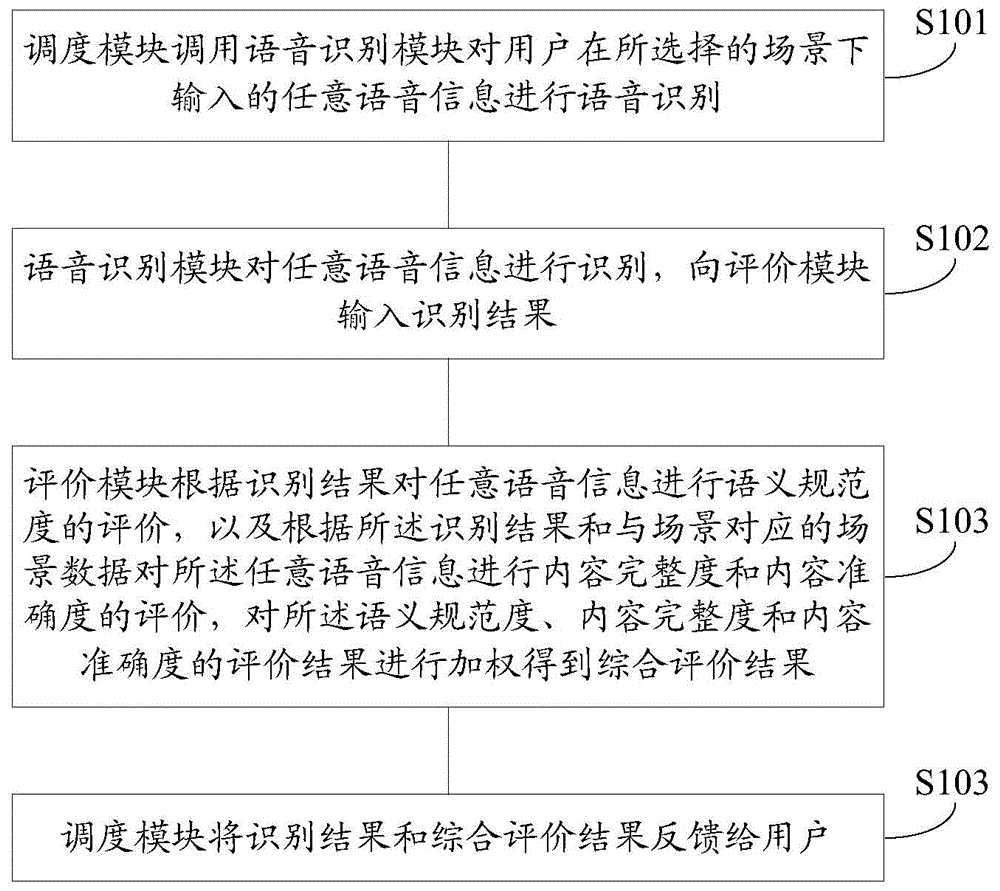
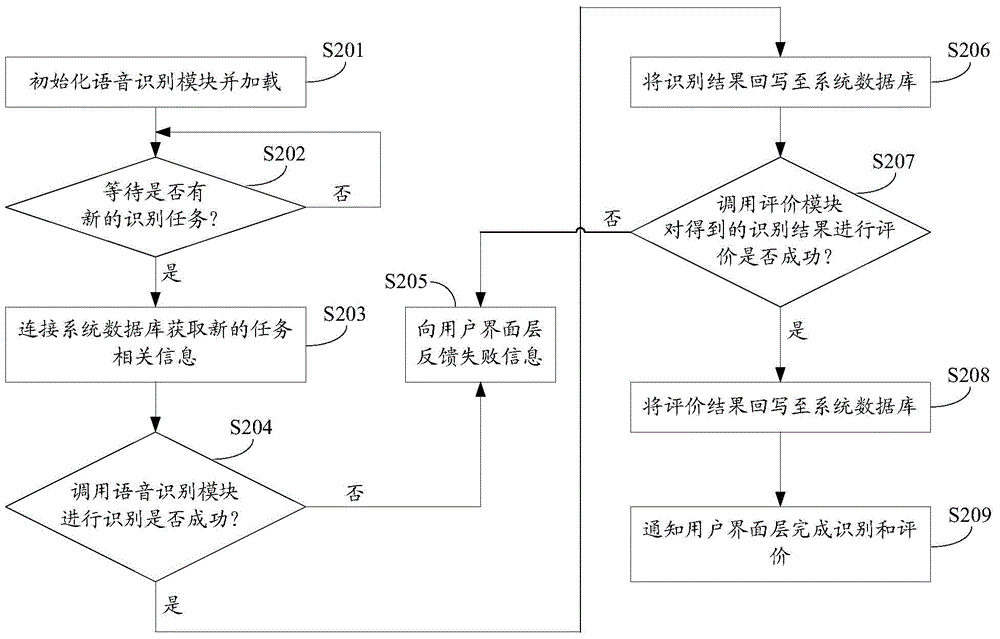
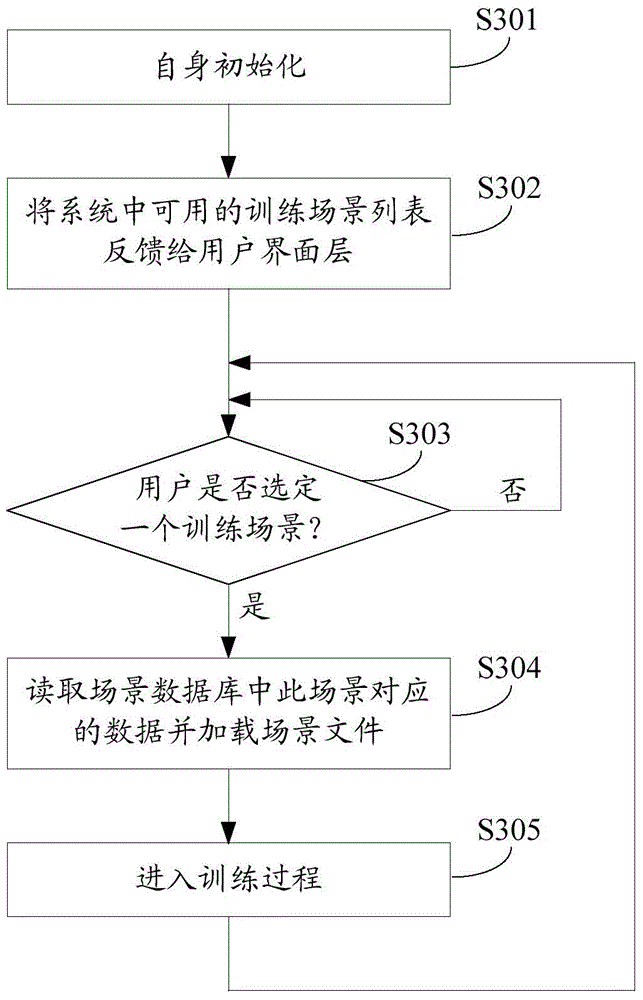
Self-adaption language training method and platform
The invention discloses a self-adaption language training method and platform so that any voice message inputted by a user under a selected scene can be evaluated. The method includes the steps that a scheduling module calls a voice recognition module to conduct voice recognition on any voice message inputted by the user under the selected scene, the voice recognition module recognizes the voice message and inputs a recognition result to an evaluation module, the evaluation module evaluates the semantic standard degree, the content integrity and the content accuracy and weights the semantic standard degree evaluation result, the content integrity evaluation result and the content accuracy evaluation result to obtain a comprehensive evaluation result, and the scheduling module feeds the recognition result and the comprehensive evaluation result back to the user. According to the method and the platform, when expression of the user is evaluated, only a reference replay text and an expected key word text need to be obtained, the language use capacity of the user can be objectively and accurately reflected, and the method and the platform are beneficial for improving the language expression capacity of the user.
Owner:SHENZHEN INST OF ADVANCED TECH CHINESE ACAD OF SCI
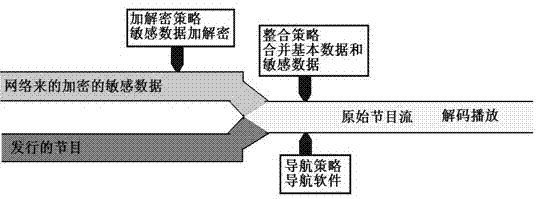
An encryption method for data file distribution
InactiveCN102300093ATo achieve the effect of encryptionBandwidth occupancy is acceptableUser identity/authority verificationTelevision systemsComputer hardwareOriginal data
The invention provides an encryption method for data file distribution, which is characterized in that: the data file is divided into sensitive data and main data, and the two kinds of data are propagated and distributed through different ways, and then the data is synthesized when used at the destination, Revert to the original data file. The encryption method of the present invention has the advantages of adopting the data segmentation technology, breaking the integrity of the content, and better protecting the copyright; saving network bandwidth and making the copyright information instantly controllable.
Owner:HUAZHONG UNIV OF SCI & TECH
Systems and methods for providing object integrity and dynamic permission grants
ActiveUS7565533B2Multiprogramming arrangementsDigital data protectionComputer securityContent integrity
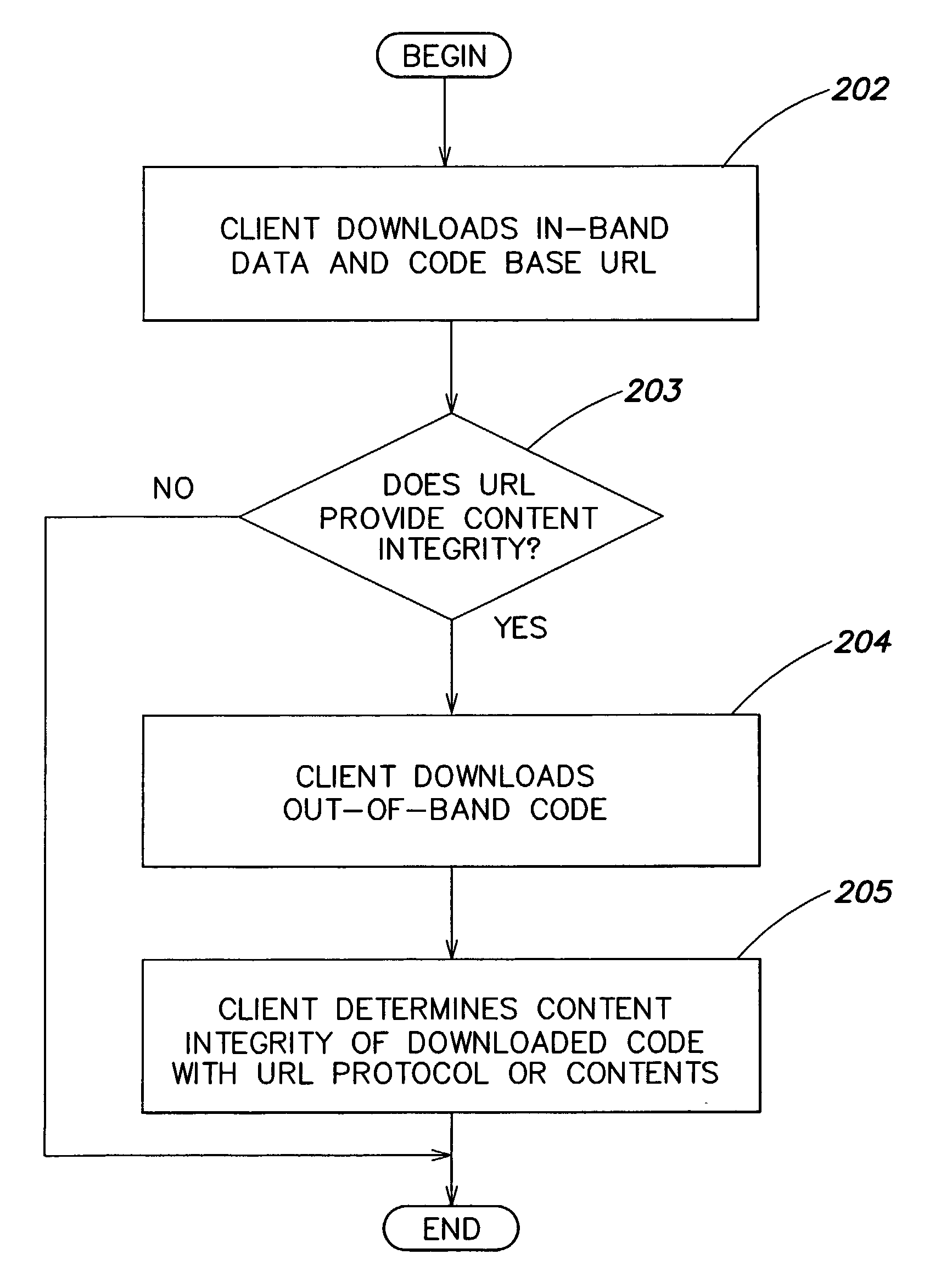
Systems and methods for securing the content integrity of and access to object data and code in a distributed system. Content protecting URLs provide a mechanism for checking code or data transmitted out-of-band. Dynamic permission grants are supported during program execution for code or users unknown prior to runtime.
Owner:ORACLE INT CORP
Vector map watermark method based on space geometric features
InactiveCN104794677AImplement embeddingImplement extractionImage data processing detailsData compressionWatermark method
The invention provides a vector map watermark method based on space geometric features. The vector map watermark method based on the space geometric features comprises the following steps of reading a vector map file; filtering out redundant rendering information; reading a data structure of a vector map object according to three basic map layers such as points, lines and regions; scanning watermark bitmaps and converting the watermark bitmaps into a binary sequence; determining an embedding length of a unit object; determining the scale of a watermark carrier gather; optimizing a map layer object gather; sequentially reading a set watermark coding sequence and writing the set watermark coding sequence at the tail of positioning information; extracting watermark codes in a space relation object by using a secret key; and generating watermark bit maps according to the binary watermark sequence and the sizes of the watermark bitmaps. The similarity between watermarks and the original watermarks is calculated and detected, and the map file cannot be damaged, zero loss of precision of an algorithm can be implemented on the basis that integrity of contents in a map is guaranteed, a vector data compression resistant effect can be achieved, and error rate is low.
Owner:HARBIN ENG UNIV
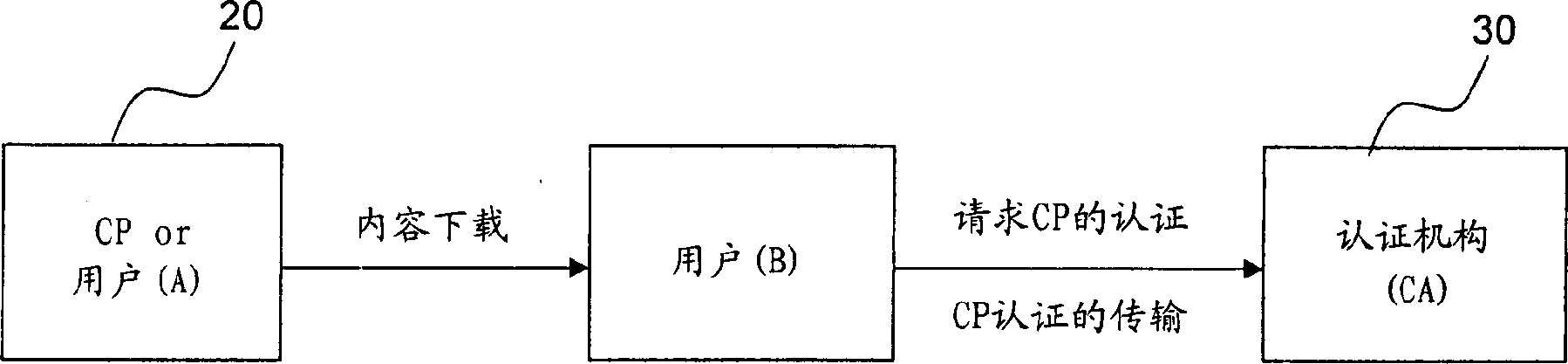
Method for identifying content provider and ensuring content integrity
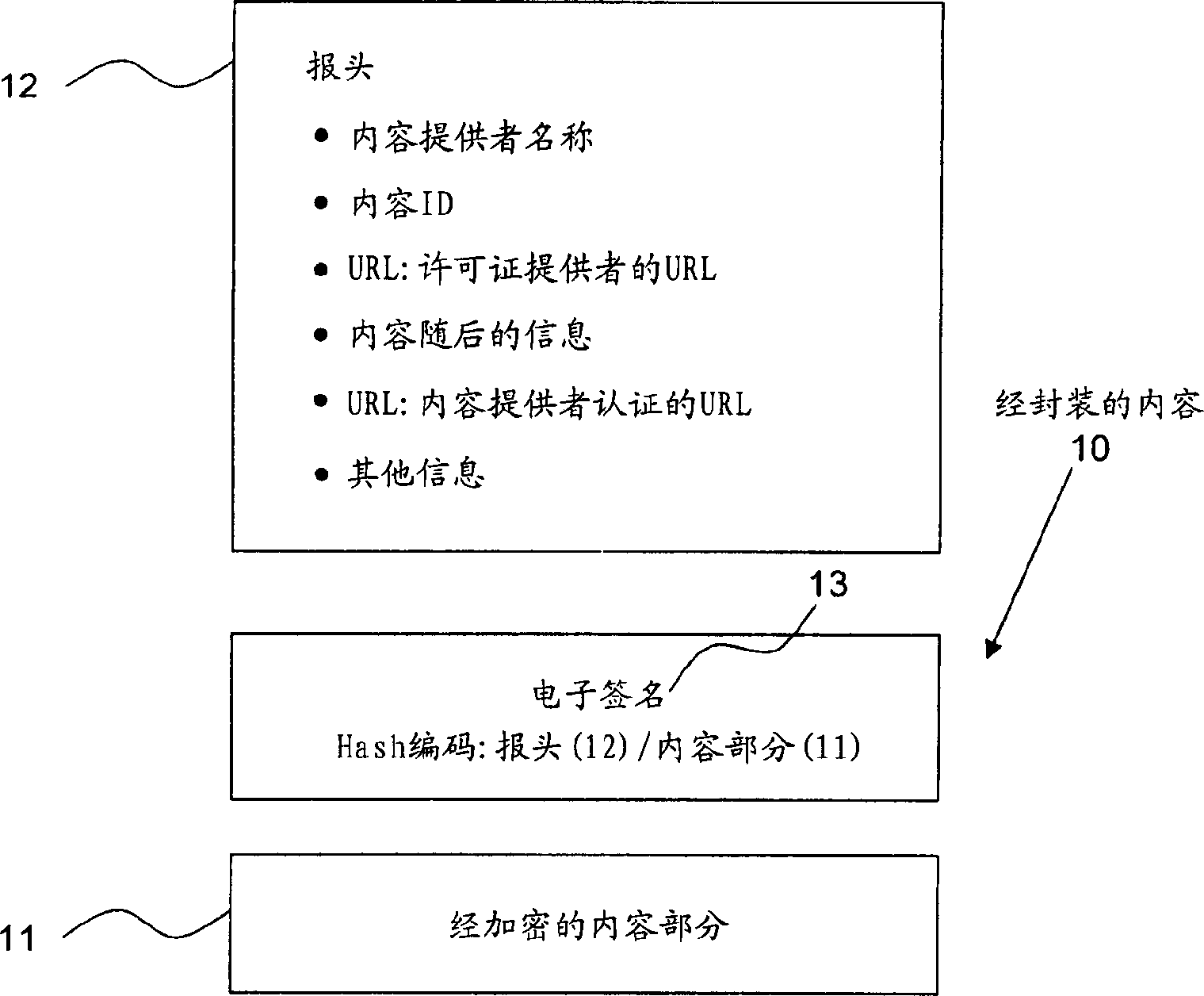
InactiveCN1551562AIntegrity guaranteedVerify electronic signatureUser identity/authority verificationBuying/selling/leasing transactionsUniform resource locatorElectronic signature
A method of authenticating a content provider and assuring content integrity by which the content provider is authenticated and the content integrity is assured upon download, exchange or transfer of a variety of multimedia contents through a wired / wireless communication network. The method of authenticating the content provider and assuring the content integrity, including downloading packaged contents with an electronic signature made thereto into a device of a user through a wired / wireless communication network, finding a URL address from which a certificate for verification of a signature of the content provider is provided, in a header of the contents, acquiring the certificate of the content provider after moving to the URL address, extracting a public key required for the verification of the electronic signature from the acquired certificate, and verifying the electronic signature by using the extracted public key.
Owner:SAMSUNG ELECTRONICS CO LTD
Method and device for assessing browsing quality
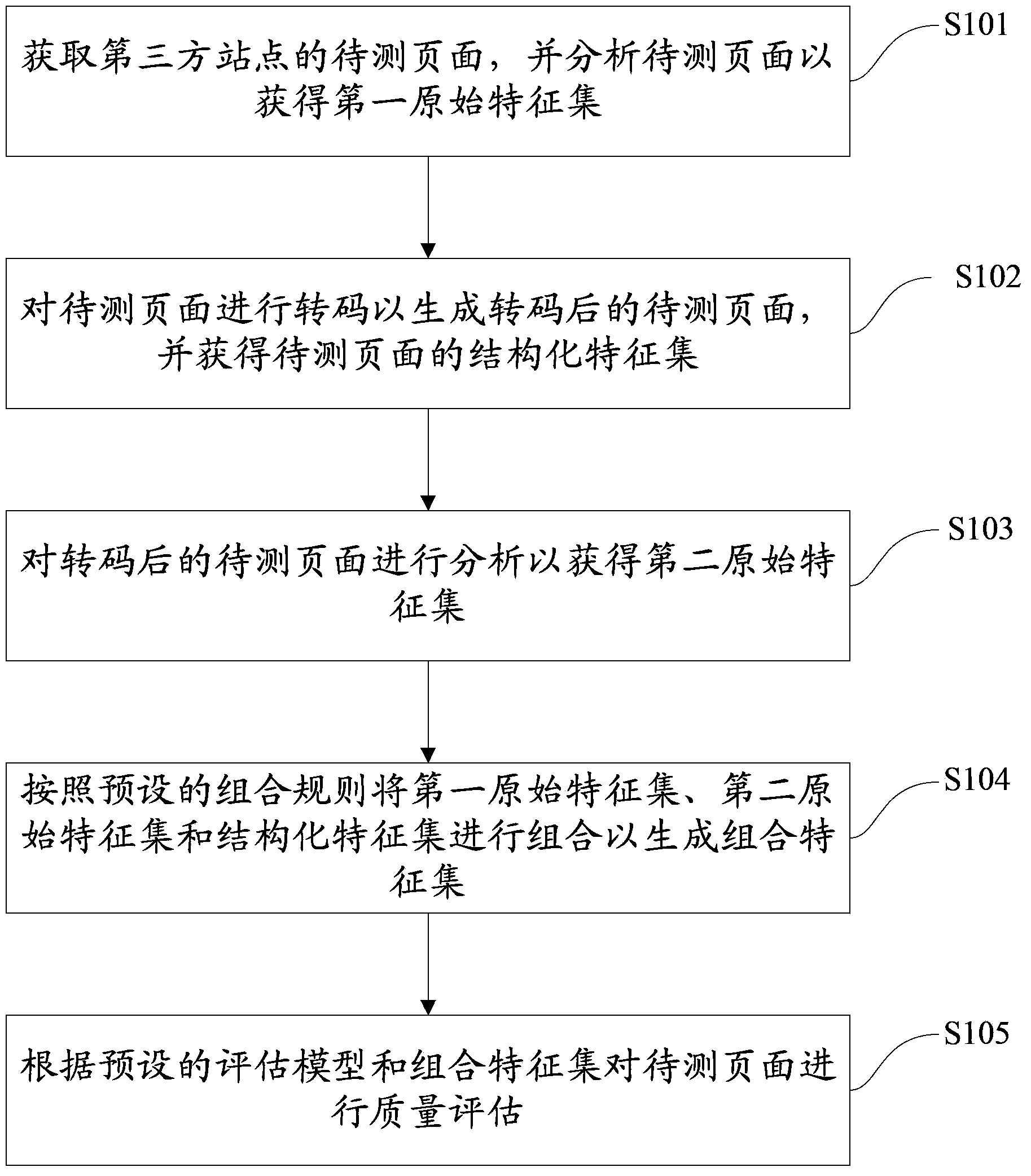
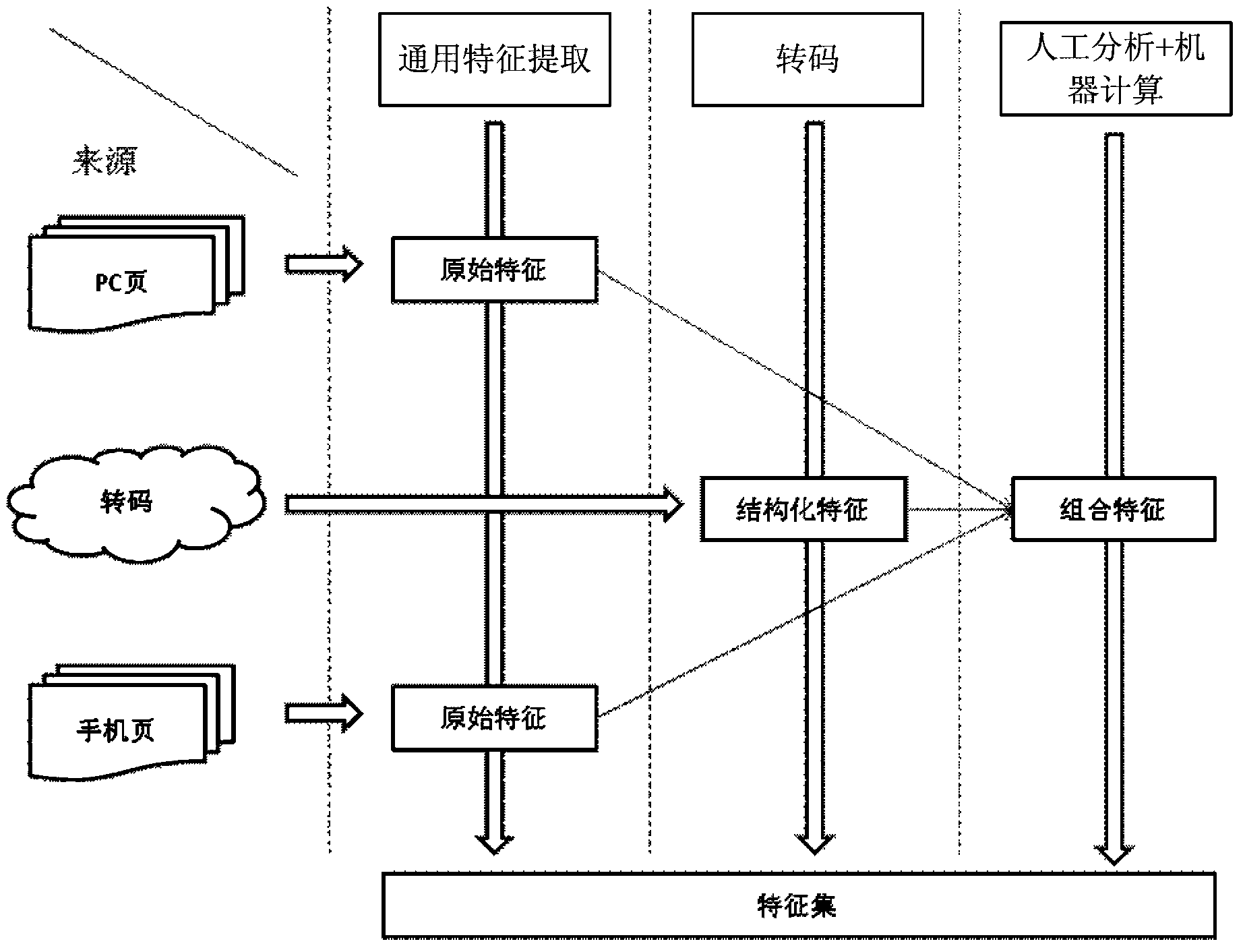
ActiveCN103544170AAchieving Typesetting QualityAchieve presentation speedCharacter and pattern recognitionSpecial data processing applicationsThird partyCombining rules
The invention discloses a method for assessing browsing quality. The method includes the steps that a page, to be detected, of a third party station is obtained, and the page to be detected is analyzed so that a first original characteristic set can be obtained; code transforming is performed on the page to be detected so that a page to be detected after the code transforming can be generated, and a structural characteristic set of the page to be detected is obtained; the page to be detected after the code transforming is analyzed so that a second original characteristic set can be obtained; according to a preset combined rule, the first original characteristic set, the second original characteristic set and the structural characteristic set are combined to generate a combined characteristic set; according to a preset assessment model and the combined characteristic set, the quality of the page to be detected is assessed. The method can be used for assessing the layout quality, content completeness, presentation speed and the like of the page, so that an instruction is provided for a user to get access to the page, and the experience degree of user access can be improved more easily. The invention further discloses a system for assessing the browsing quality.
Owner:BAIDU ONLINE NETWORK TECH (BEIJIBG) CO LTD
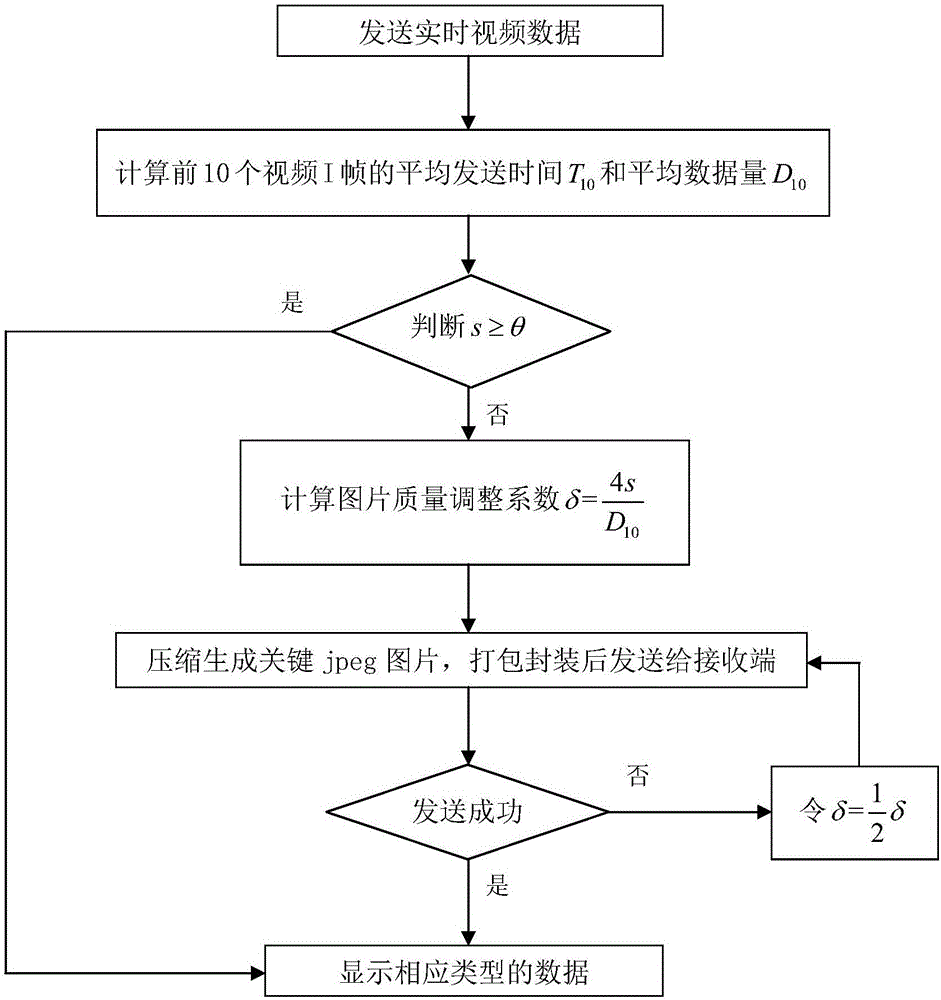
Real-time video self-adapting network transmission optimization method
ActiveCN106162257AReduce load pressureReduce transmission delaySelective content distributionSelf adaptiveSignal source
The invention provides a real-time video self-adapting network transmission optimization method. According to the method, videos and pictures from the same signal source are subjected to self-adapting regulation according to the network quality and subjected to serial transmission in the time sequence, thereby solving the technical problems of real time, smoothness and content integrity of the transmitted real-time video.
Owner:南京云恩通讯科技有限公司
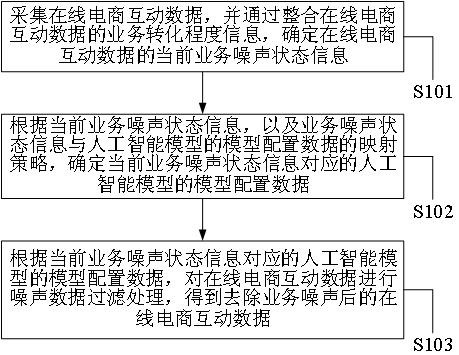
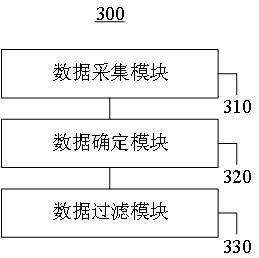
Data information processing method and information service platform in big data service scene
ActiveCN112988845AImprove integrityReduce noiseMarket predictionsRelational databasesInformation processingLow noise
The invention discloses a data information processing method and an information service platform in a big data service scene. The model configuration data and the interaction data are associated, and the current service noise state information of the online e-commerce interaction data is determined based on the service conversion degree information of the online e-commerce interaction data, so the separate data fragments do not need to be split, multiple data fragments do not need to be split when the data fragments are associated with one another, and for online e-commerce noise interaction data of different state information, according to the model configuration data corresponding to the current service noise state information which is trained in advance, so the online e-commerce interaction data after the business noise is removed and the content integrity, the content authenticity and the content accuracy of the data fragments can be improved, so the high-quality online e-commerce interaction data with relatively low noise can be obtained.
Owner:湖南机械之家信息科技有限公司
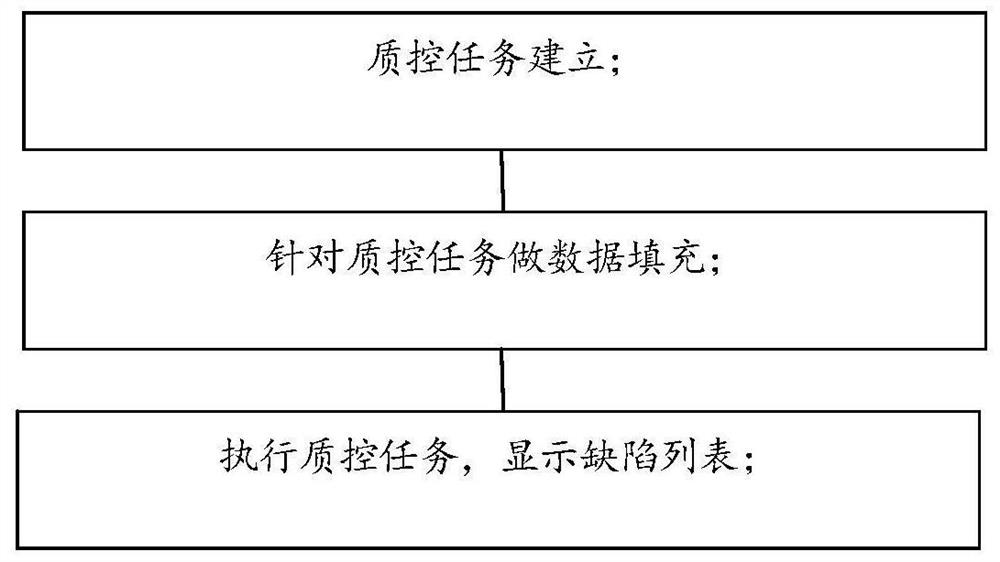
Intelligent case quality control method and system
ActiveCN113707252AImprove basic qualityImprove quality control efficiencyHealthcare resources and facilitiesSpecial data processing applicationsMedical recordDisease
According to the invention, an artificial intelligence technology is taken as a core, and through understanding of medical record semantics, evaluation of diagnosis and treatment paths, searching of defect contents and reason recognition, research and judgment from content integrity, timeliness and the like can be realized, and content quality control on medical record documents from term normalization, data consistency, logic consistency, diagnosis sufficiency, drug interaction and the like can also be realized. Through the basic quality, the link quality and the end quality of the electronic medical record and management, the quality control department not only can timely find and correct errors in the medical record and reduce and avoid medical accidents, errors and disputes, but also can truly reflect the condition of disease diagnosis and treatment of each department.
Owner:ZHONGDA HOSPITAL SOUTHEAST UNIV
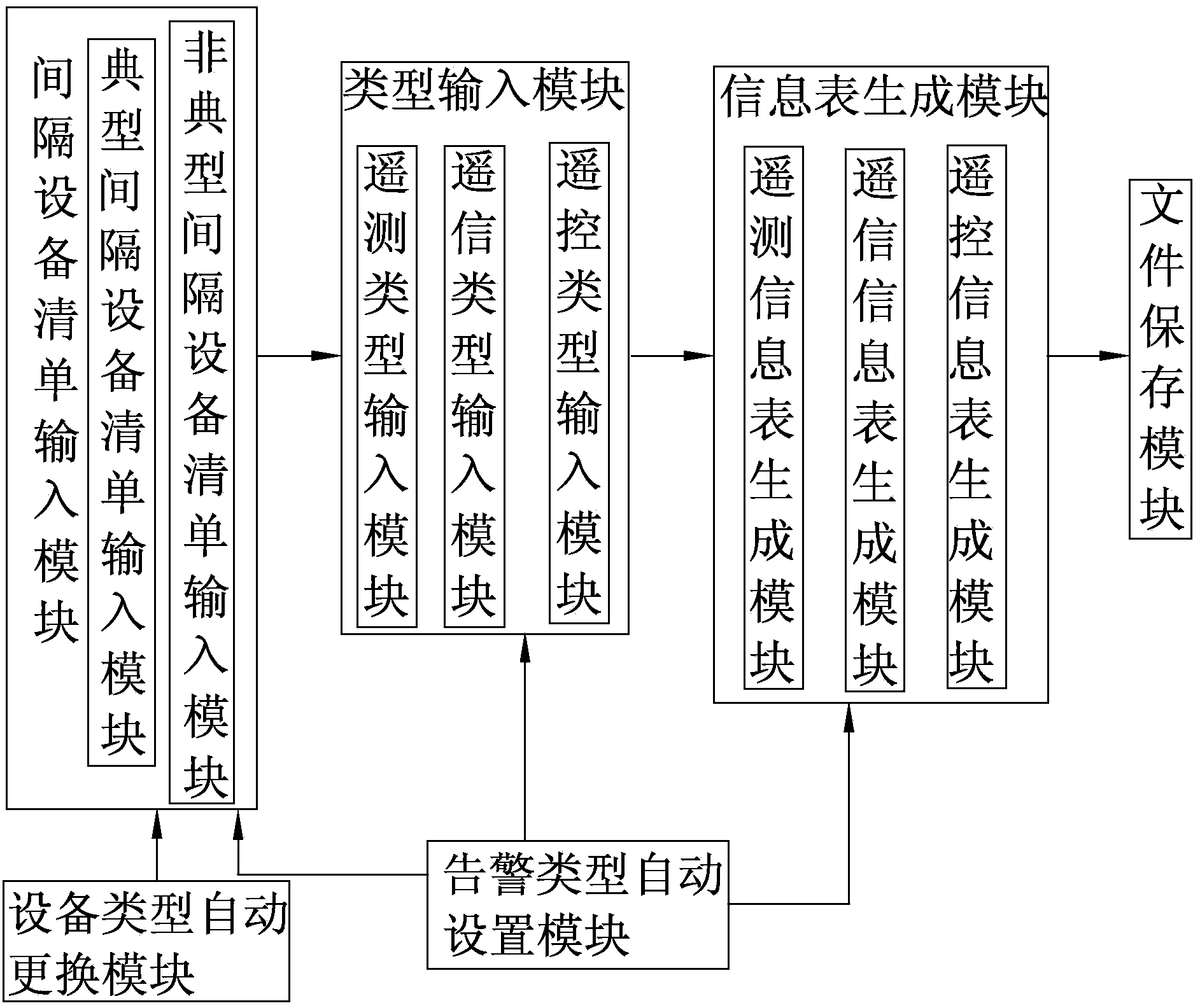
Automatic intelligent substation information sheet generating system
InactiveCN103793370AExcellent collection integrityEffectively control the preparation qualitySpecial data processing applicationsSmart substationRemote control
The invention relates to an automatic intelligent substation information sheet generating system. The generating system comprises an equipment separating list inputting module, a type inputting module connected with the equipment separating list inputting module in a communication mode and an information sheet generating module connected with the equipment separating list inputting module and the type inputting module in a communication mode. An intelligent substation primary equipment separating list and an intelligent substation secondary equipment separating list are input respectively and combined with all configured separating remote measuring, remote signaling and remote control types, and information is automatically extracted from remote measuring, remote signaling and remote control module libraries to generate full-substation remote measuring, remote signaling and remote control information sheets. The automatic intelligent substation information sheet generating system has the advantages that it is only required that dispatching and naming lists of substation equipment separating are input and equipment attributes are selected, the remote measuring, remote signaling and remote control information sheets can be automatically generated, working efficiency is greatly improved, integrity and correctness of content and standardability of text description of the information sheets are ensured, and the automatic intelligent substation information sheet generating system can be widely applied to compilation of telecontrol information of an infrastructural project and a new expansion project of an intelligent substation at all voltage levels in an electric system.
Owner:STATE GRID CORP OF CHINA +1
Application program operation method and device
ActiveCN107092824AImprove operational safetyEnsure safetyComputer security arrangementsApplication softwareOperation safety
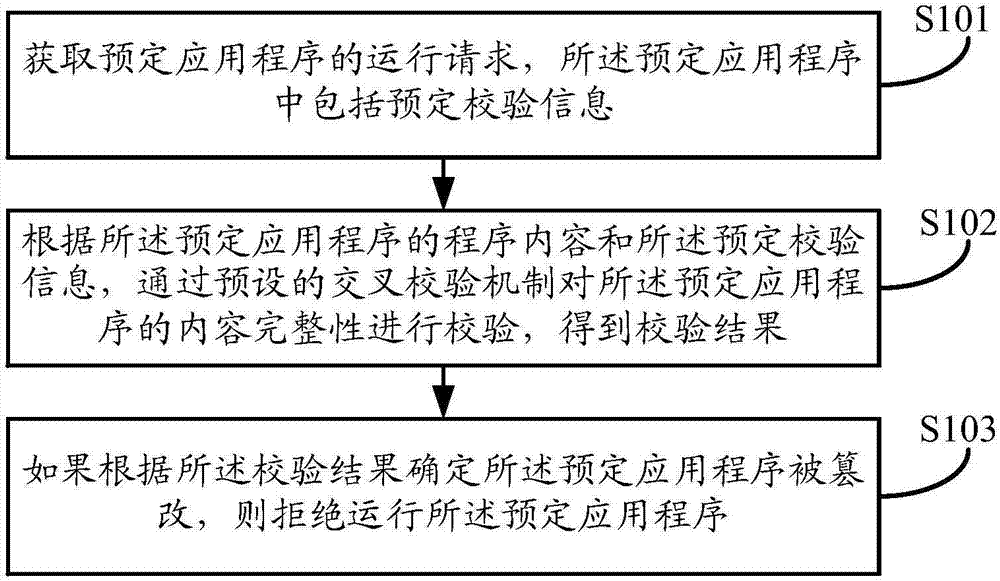
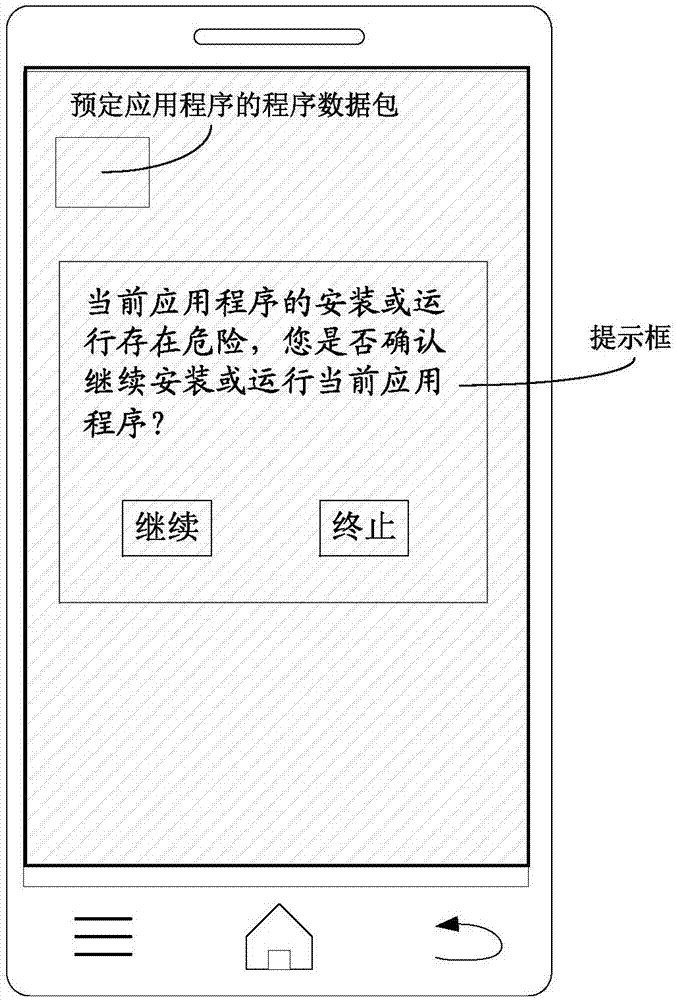
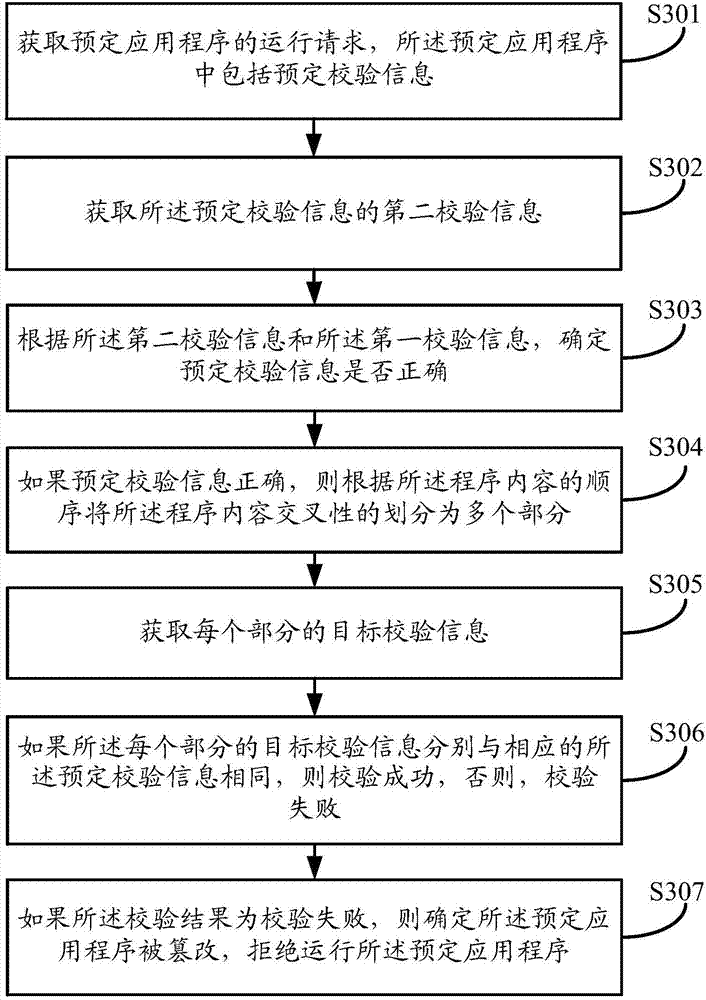
Embodiments of the invention disclose an application program operation method and device. The method comprises the following steps of: obtaining an operation instruction of a predetermined application program, wherein the predetermined application program comprises predetermined verification information; verifying content integrity of the predetermined application program through a preset cross verification mechanism according to a program content of the predetermined application program and the predetermined verification information, so as to obtain a verification result, wherein the cross verification mechanism is used for verifying different parts comprising a same program content in the predetermined application program; and if the fact that the predetermined application program is tampered is determined according to the verification result, refusing to operate the predetermined application program. By utilizing the application program operation method and device disclosed by the invention, the problem that application programs are tampered can be fundamentally solved, the operation safety of the application programs can be improved and the safety of personal information of users is ensured.
Owner:BEIJING BANGCLE TECH CO LTD
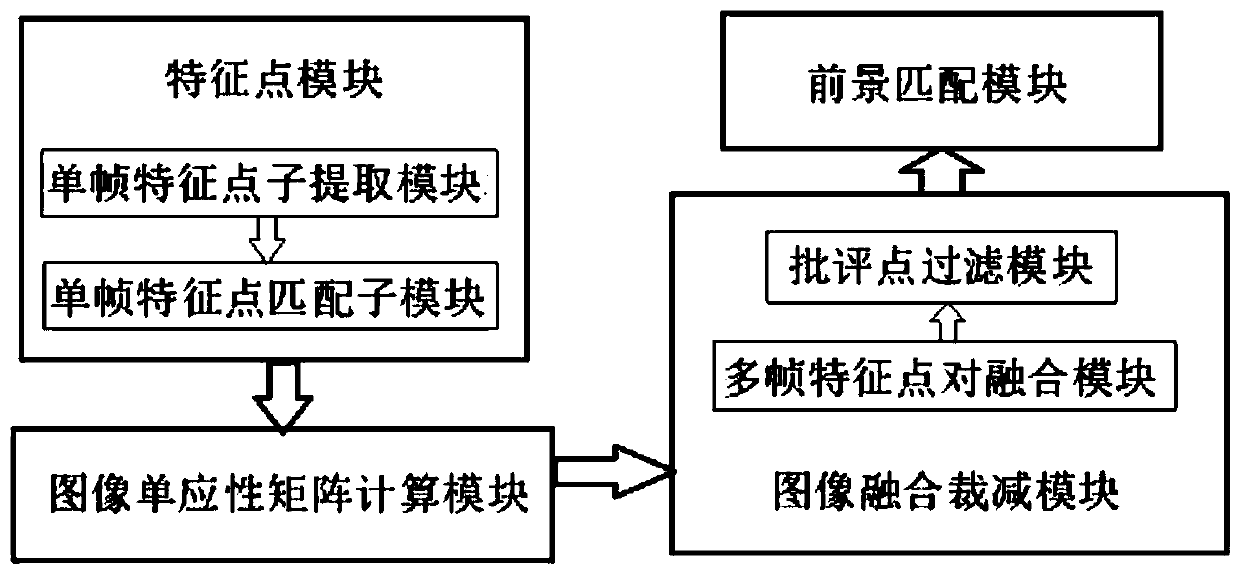
Video stitching method and system based on multi-camera content analysis
InactiveCN111355928AReduce storage costsReduce workloadTelevision system detailsCharacter and pattern recognitionCamera imageComputer graphics (images)
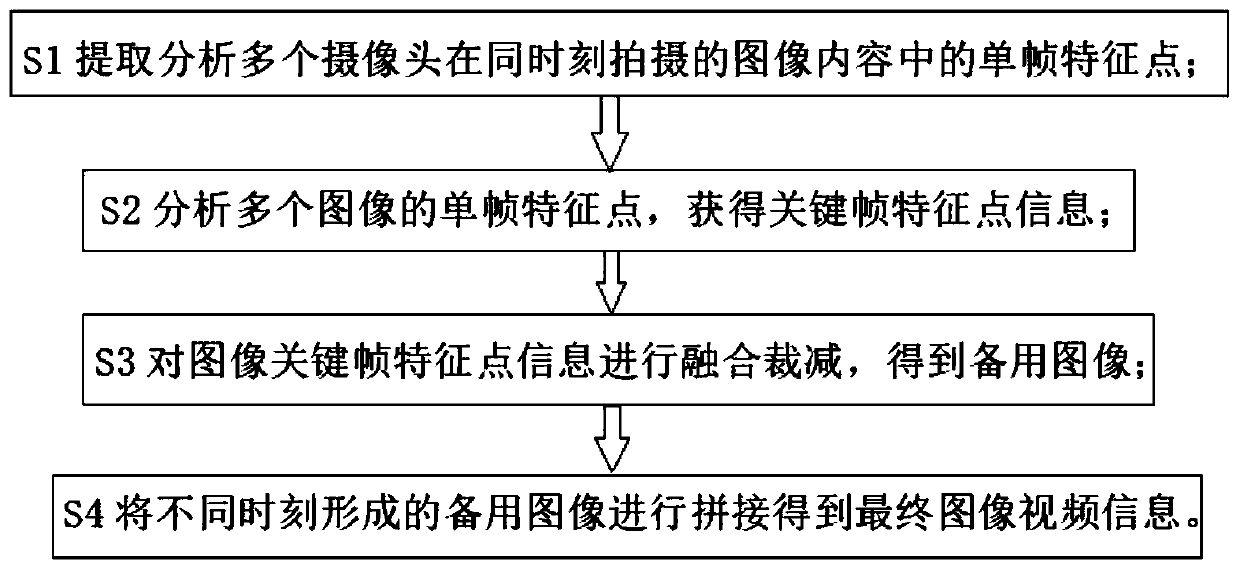
The invention discloses a video splicing method and system based on multi-camera content analysis, and belongs to the field of industrial protection, social monitoring and community security and protection. The system comprises a feature point module, an image homography matrix calculation module, an image fusion cutting module and a foreground matching module. Video processing is carried out by using the method and the system; the final image video information can be obtained after the overlapping region in the multi-angle video is quickly and efficiently removed; the work of performing content analysis processing on multi-scene and multi-camera image videos by applying a single-frame feature point matching technology is realized; the final image video information obtained through processing saves more storage space, reduces the information storage cost, reduces the workload of image video processing, and improves the working efficiency of image video processing while guaranteeing thevideo content integrity and video quality.
Owner:JINAN INSPUR HIGH TECH TECH DEV CO LTD
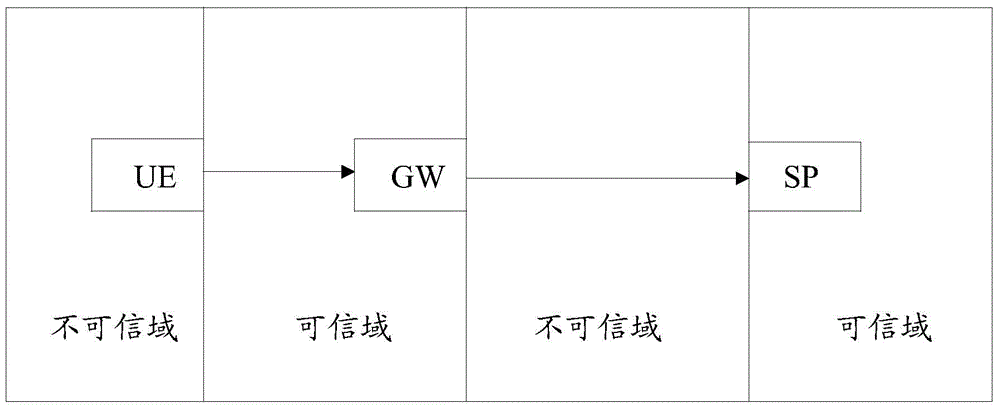
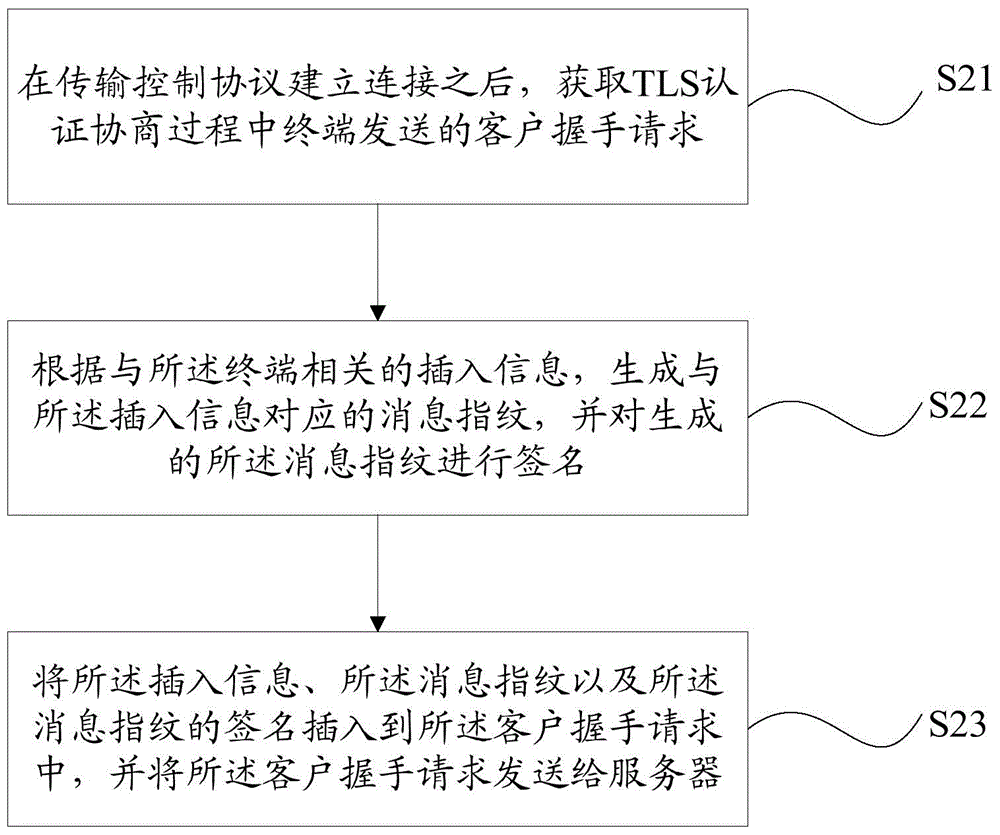
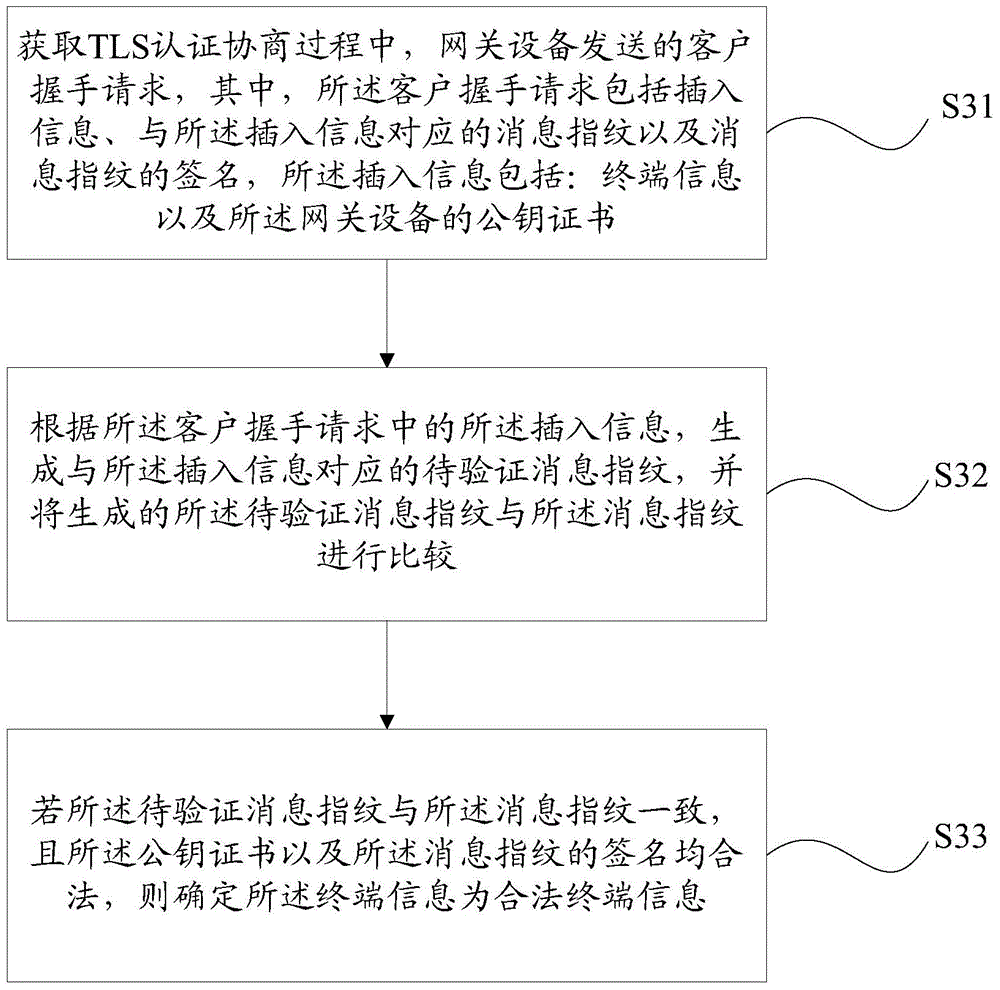
Method, device and system for processing terminal information
ActiveCN105577738AReliably Verified Source AuthenticityReliably Verify IntegrityTransmissionComputer hardwareWeb service
The invention provides a method, device and system for processing terminal information. According to the prior art, when a web service provider obtains terminal information through an intermediate device, the overhead of the intermediate device will be increased when processing HTTP messages, and as a result, the problems of decrease of the concurrent capacity of the intermediate device and information terminal counterfeiting on a transmission path may be brought about, and while, with the method, device and system of the invention adopted, the problems in the prior art can be solved. The method includes the following steps that: after establishing a connection, a transmission control protocol obtains a client handshake request sent by a terminal in a TLS authentication negotiation process; a message fingerprint corresponding to insertion information is generated according to the insertion information related to the terminal, and the generated message fingerprint is signed; and the insertion information, the message fingerprint and the signature of the message fingerprint are inserted into the client handshake request, and the client handshake request is sent to a server. According to the method provided by the embodiment of the invention, the terminal information is carried in a TLS protocol field, a one-way authentication mechanism of the intermediate device and the server is additionally adopted, and it can be ensured that the server end can reliably verify the authenticity of the source of the terminal information and completeness of the content of the information terminal.
Owner:CHINA MOBILE COMM GRP CO LTD
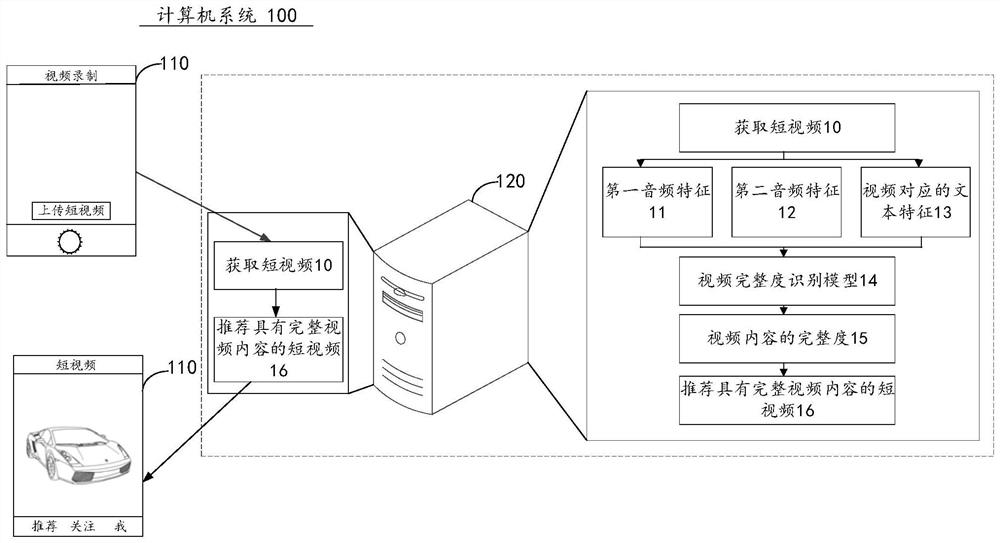
Video content integrity identification method and device, equipment and storage medium
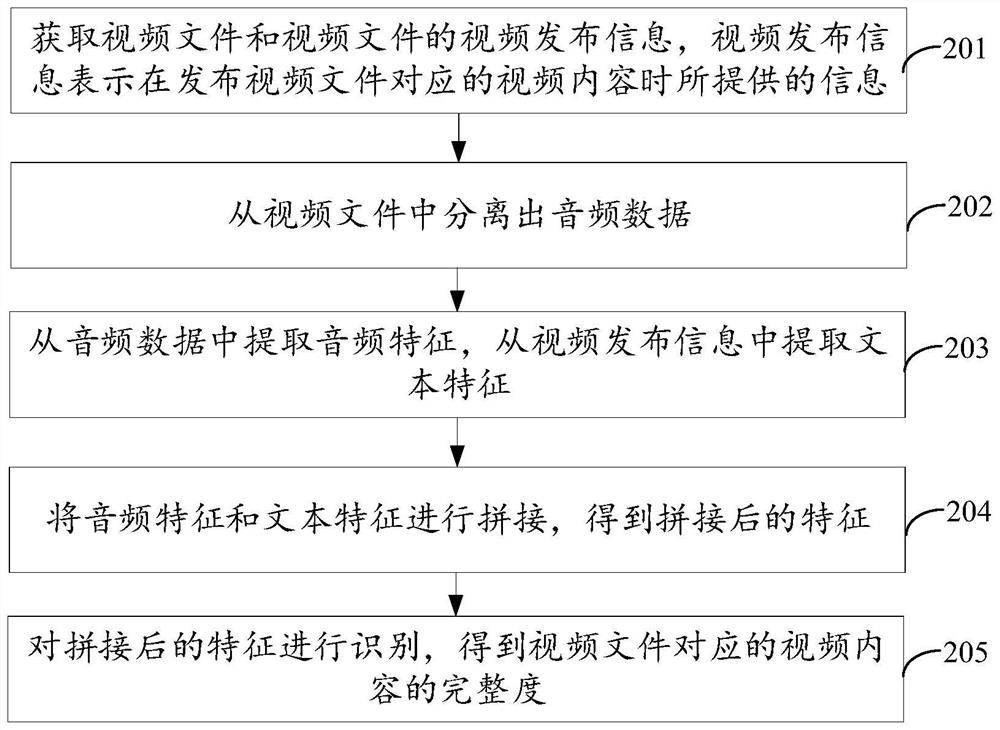
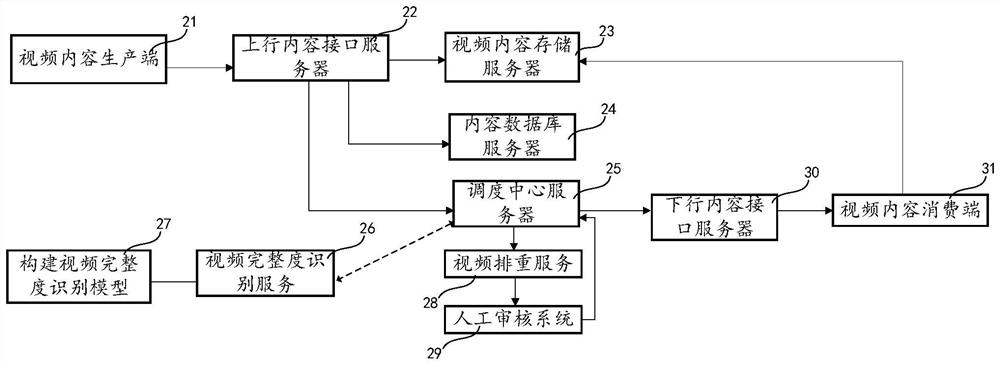
PendingCN112418011AImprove review efficiencyQuality improvementSpeech analysisCharacter and pattern recognitionComputer graphics (images)Information representation
The invention discloses a video content integrity identification method, and device, equipment and a storage medium, and relates to the field of deep learning. A video integrity identification model is constructed through an artificial intelligence technology, and a function of identifying video integrity is realized by utilizing computer equipment. The method comprises the steps of obtaining a video file and video publishing information of the video file, wherein the video publishing information represents information provided when video content corresponding to the video file is published; separating audio data from the video file; extracting audio features from the audio data, and extracting text features from the video release information; splicing the audio features and the text features to obtain spliced features; and identifying the spliced features to obtain the integrity of the video content corresponding to the video file. By identifying the vector after the audio feature andthe text feature corresponding to the video file are spliced, the integrity of the video content is determined by integrating the features of multiple dimensions, so that the accuracy of video integrity auditing is improved.
Owner:TENCENT TECH (SHENZHEN) CO LTD
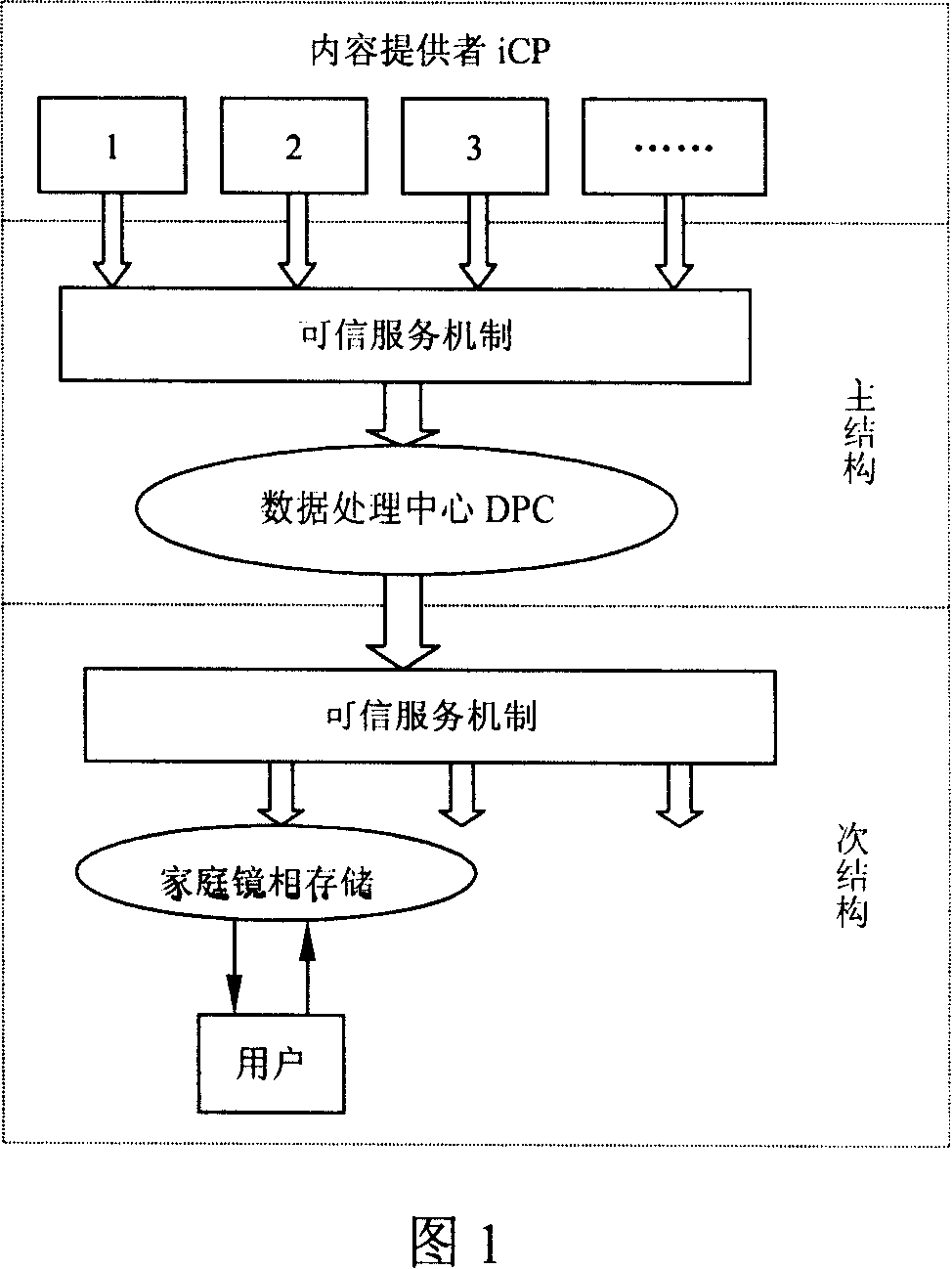
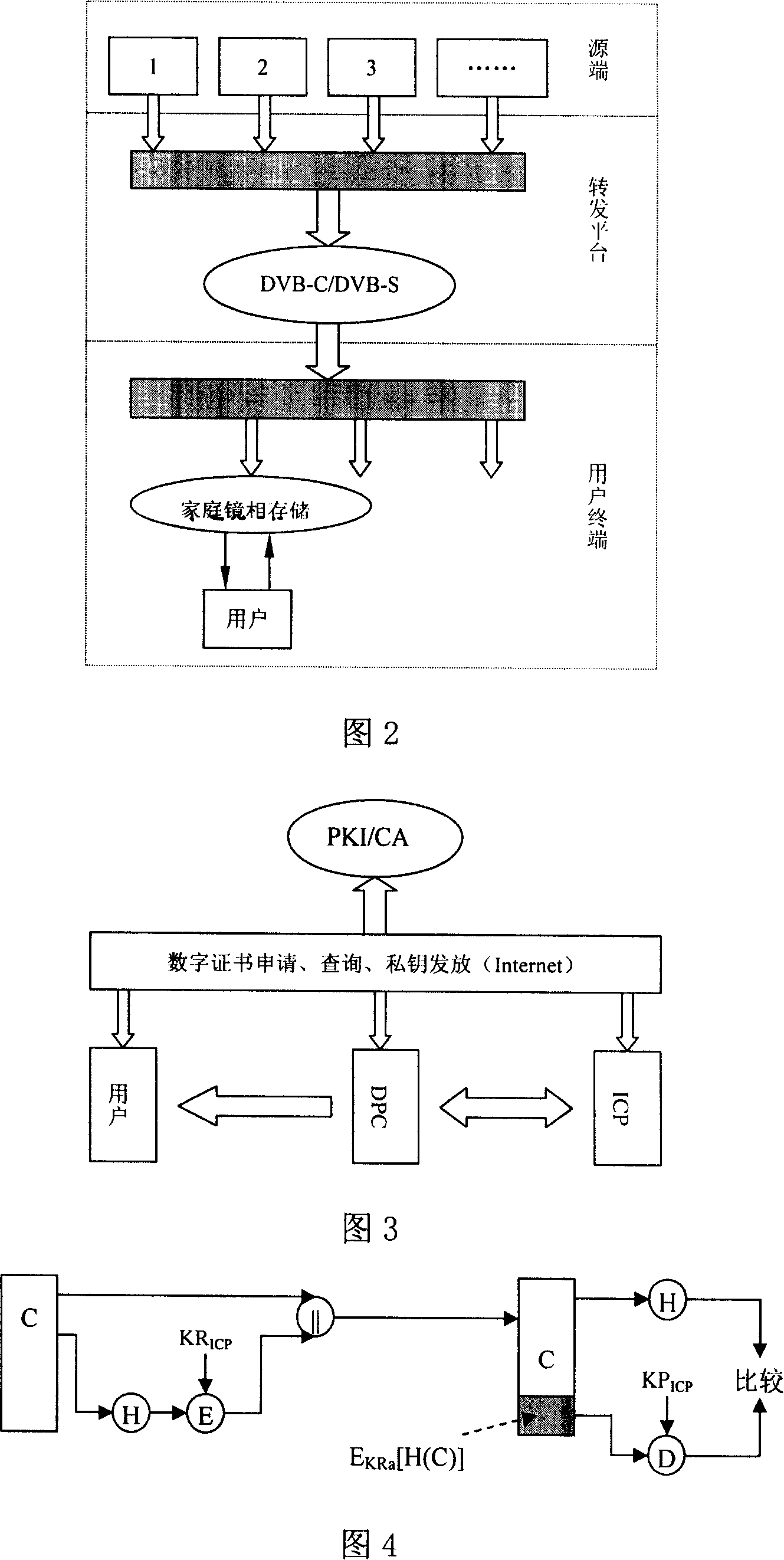
Method of implementing reliable service on complementary structure information network
InactiveCN101136902AEnsure safetyGuaranteed credibilityTransmissionInformation transmissionService guarantee
The invention discloses method for implementing credible service in complemental configurable information network. The said credible services include the credible service of information transmission from information content provider of No.i (iCP) to Data Process Center (DPC), and the credible service provided by DPC to users. The credible service from iCP to DPC includes functions of digital signature, integrality of information content, security, and anti denial capability etc for information content provided by iCP. Content of the credible service from DPC to user includes integrality and security etc. the disclosed credible services guarantee security and confidence level of complemental configurable information network.
Owner:马建国 +1
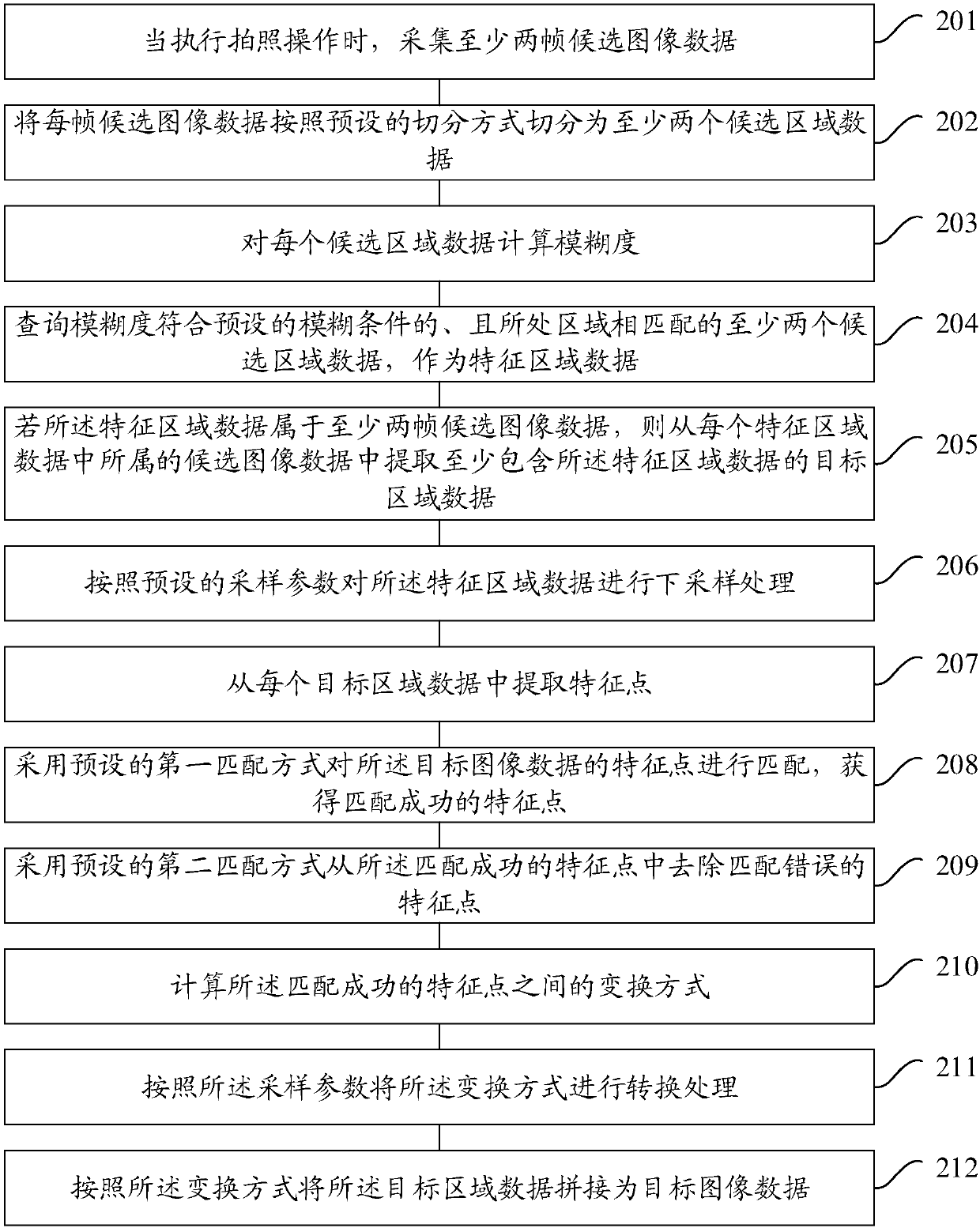
Photographing method and photographing device
ActiveCN108322658AGuaranteed content integrityGuaranteed clarityTelevision system detailsColor television detailsComputer graphics (images)Time-Consuming
The embodiment of the invention provides a photographing method and a photographing device, and the method comprises the following steps: when executing a photographing operation, acquiring at least two frames of candidate image data; respectively extracting at least two target region data, of which fuzzy degree meets a preset fuzzy condition, some regions are superposed and location regions are matched, from the at least two frames of candidate image data; and splicing the target region data into target image data. Due to superposition of some regions, the target region data can be spliced, relevance between the acquired candidate image data is considered, regions of the target region data are matched and consequently content integrity of the spliced image can be guaranteed; proper targetregion data are screened through the fuzzy condition, definition of spliced image data is guaranteed, influence caused by jittering is reduced, additionally configuring independent devices is not needed, cost is reduced, moreover, splicing is simple to operate, processing speed is improved, and time consumed is saved.
Owner:QINGDAO HISENSE MOBILE COMM TECH CO LTD
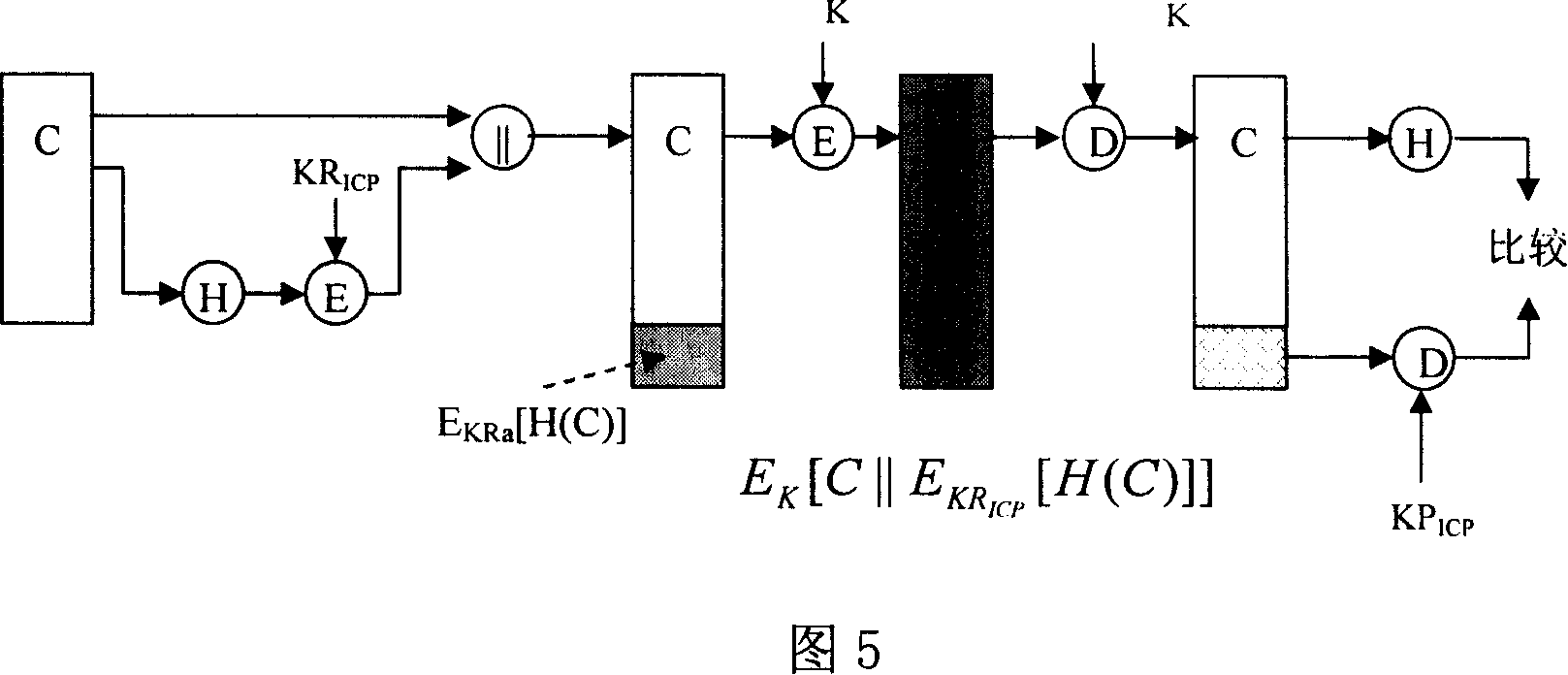
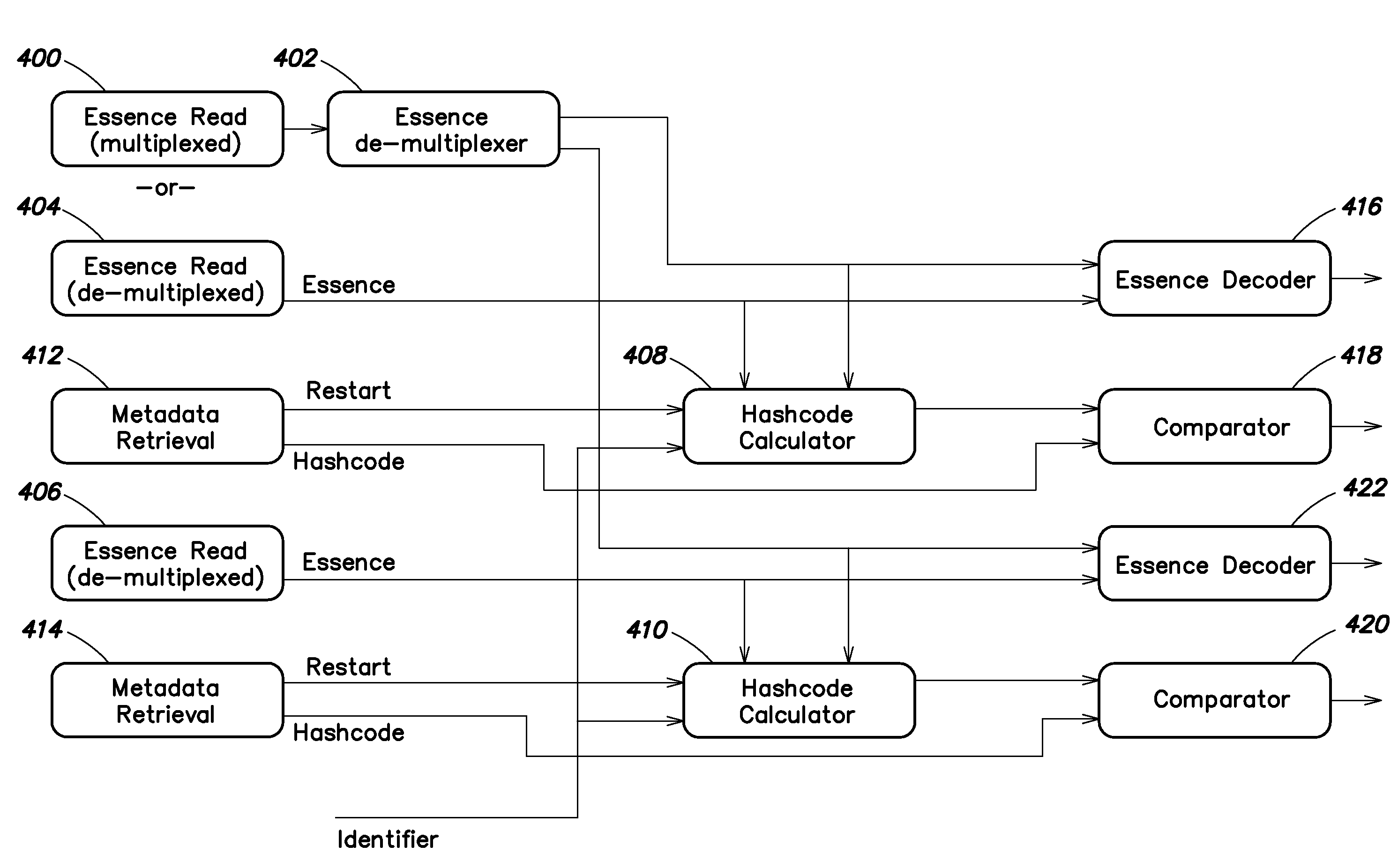
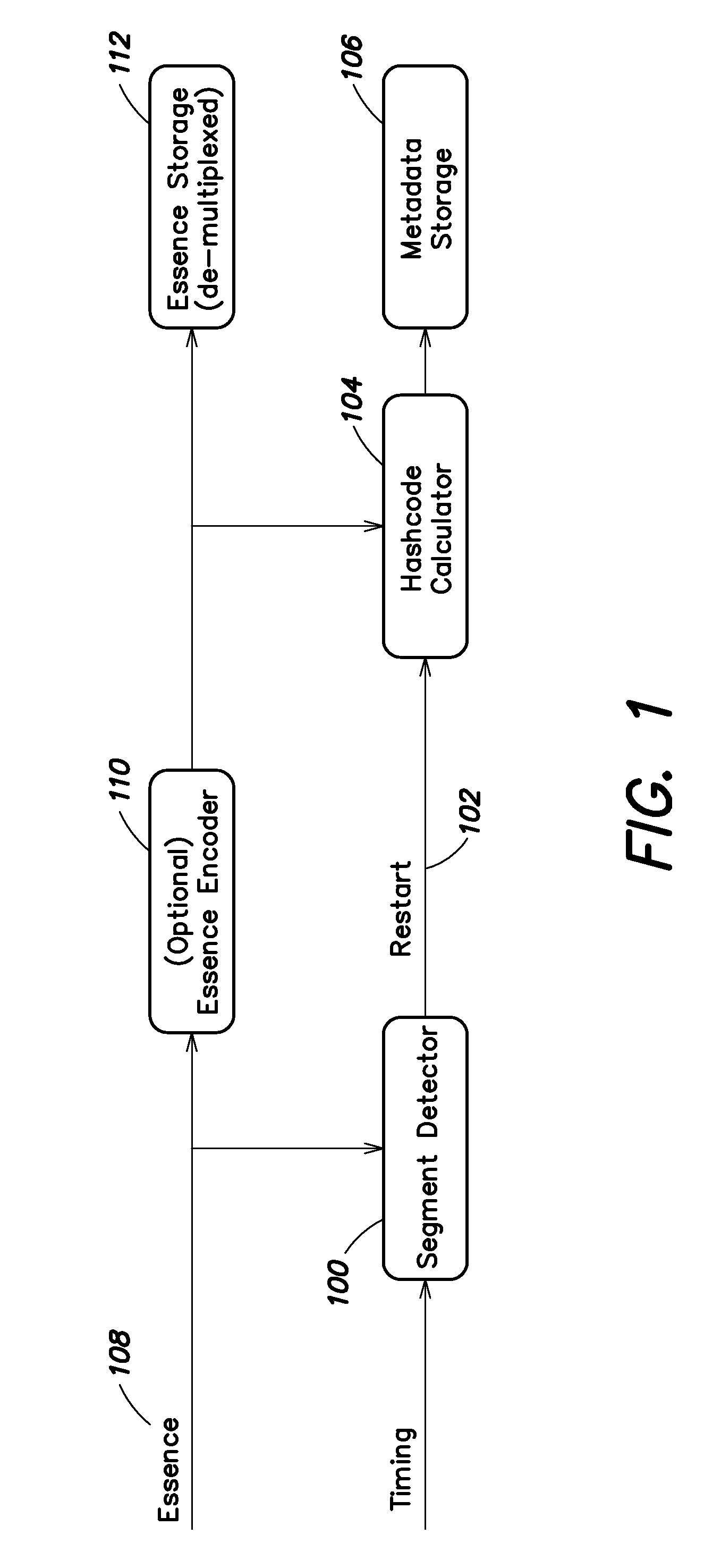
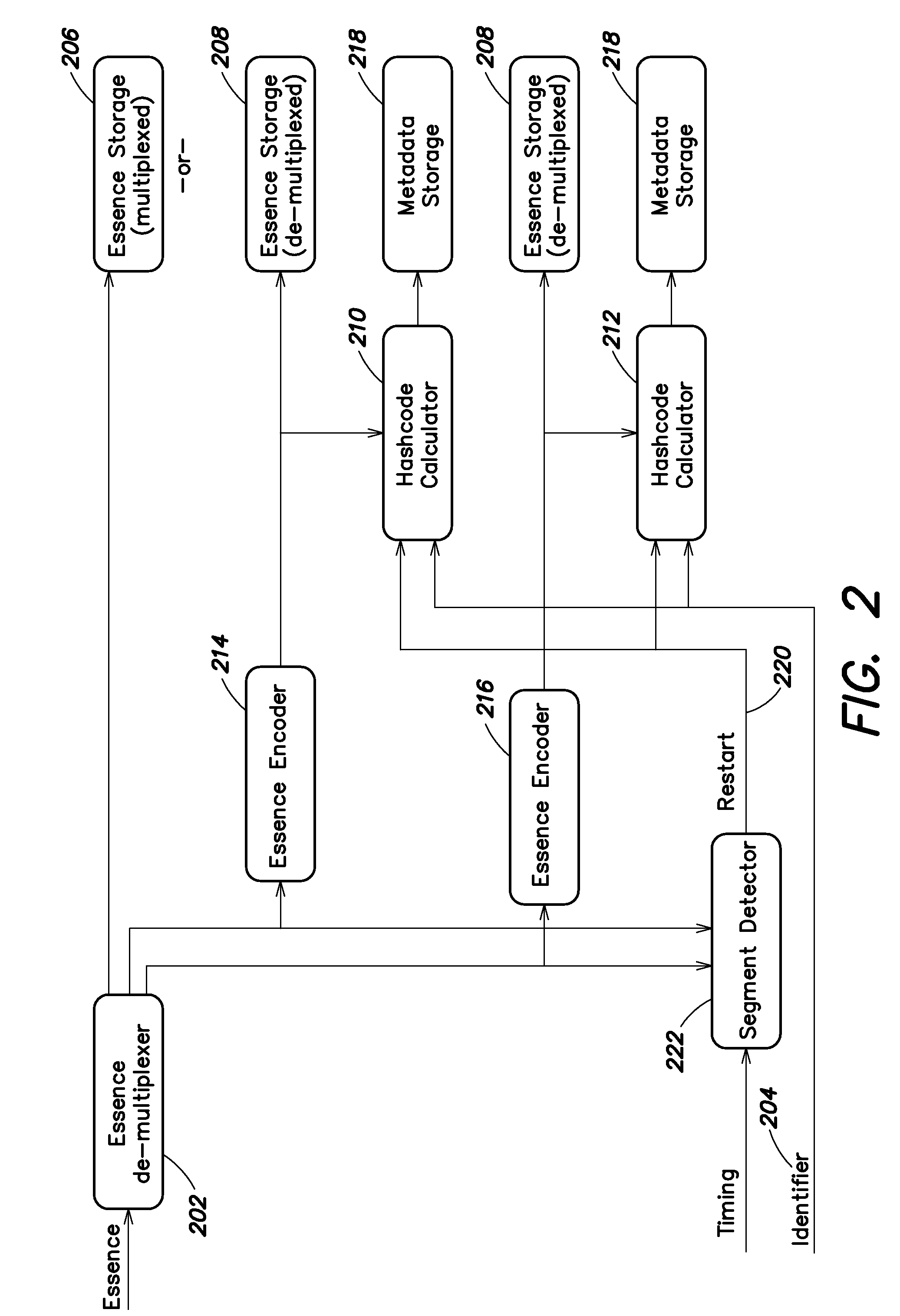
Content Integrity Management System
ActiveUS20110099462A1Efficient verificationCode conversionError detection onlyComputer hardwareManagement system
A method and system are provided for efficiently verifying the integrity of file-based video audio and other essence in a content production system. The method involves creating a sequence of hash codes for the editable units of the essence, which are stored as metadata apart from the content (either in a separate file or in a separate portion of the same file), and are correlated to the content by a time label (which may be an offset or a timecode number). Upon retrieval from storage, the hash codes are generated for the retrieved essence and compared to the stored hash codes to verify that the content has not been modified.
Owner:METAGLUE CORP
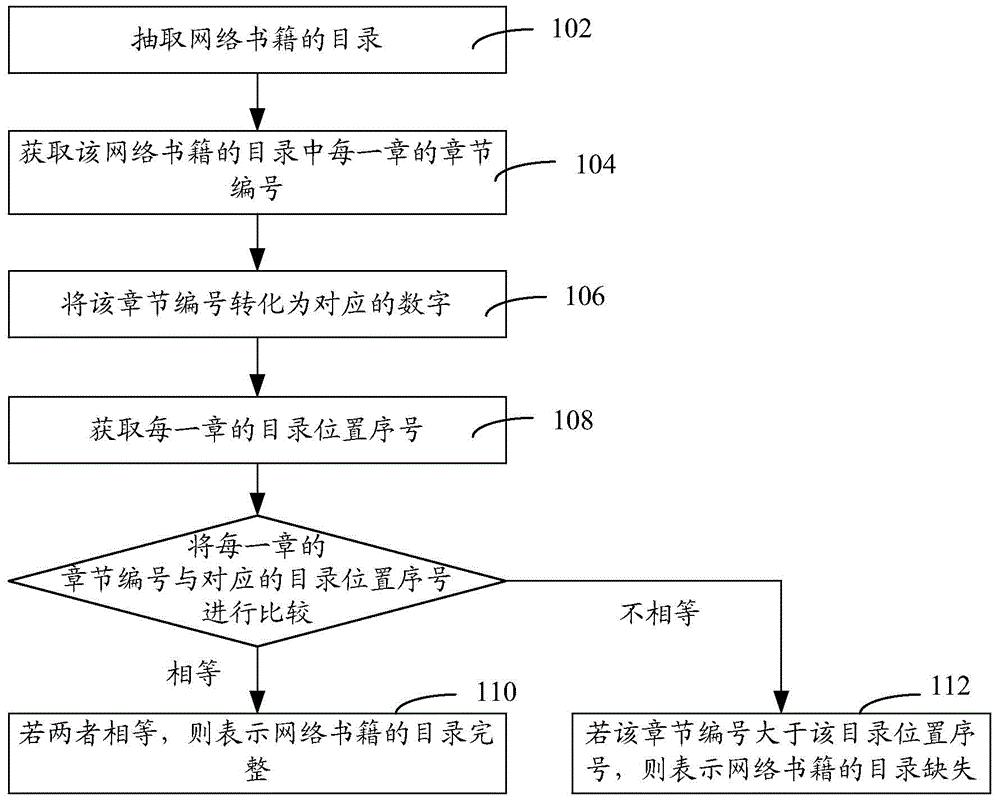
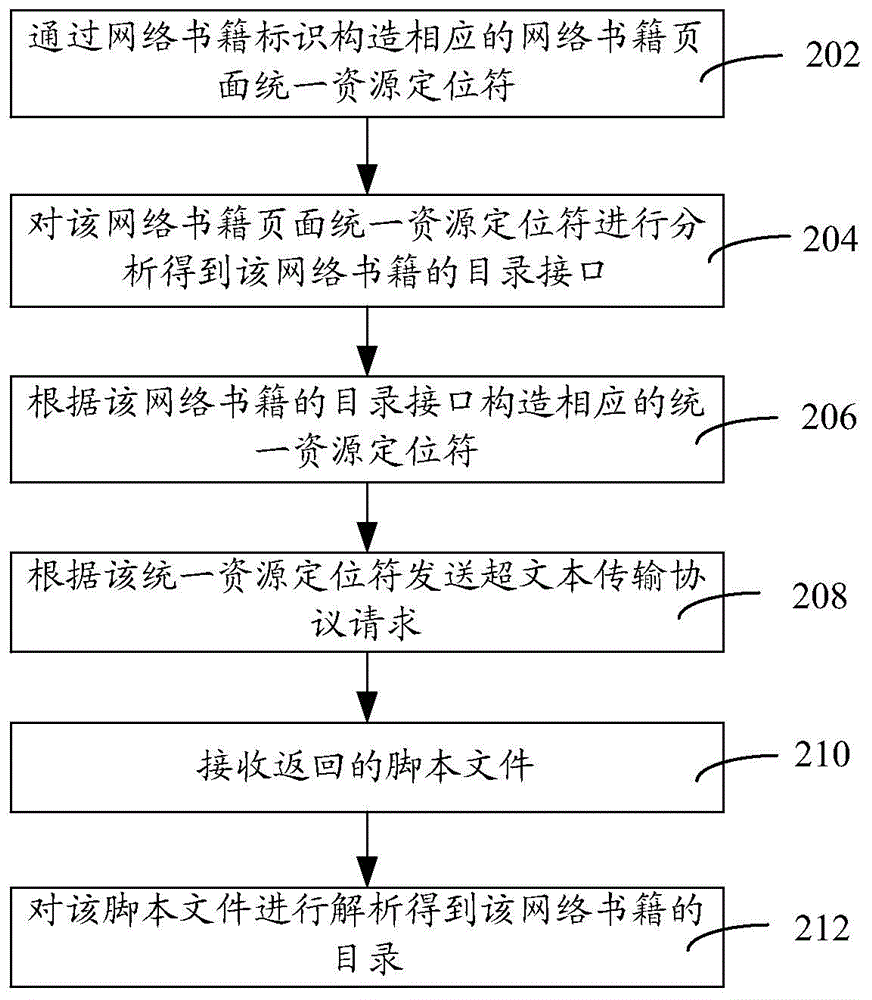
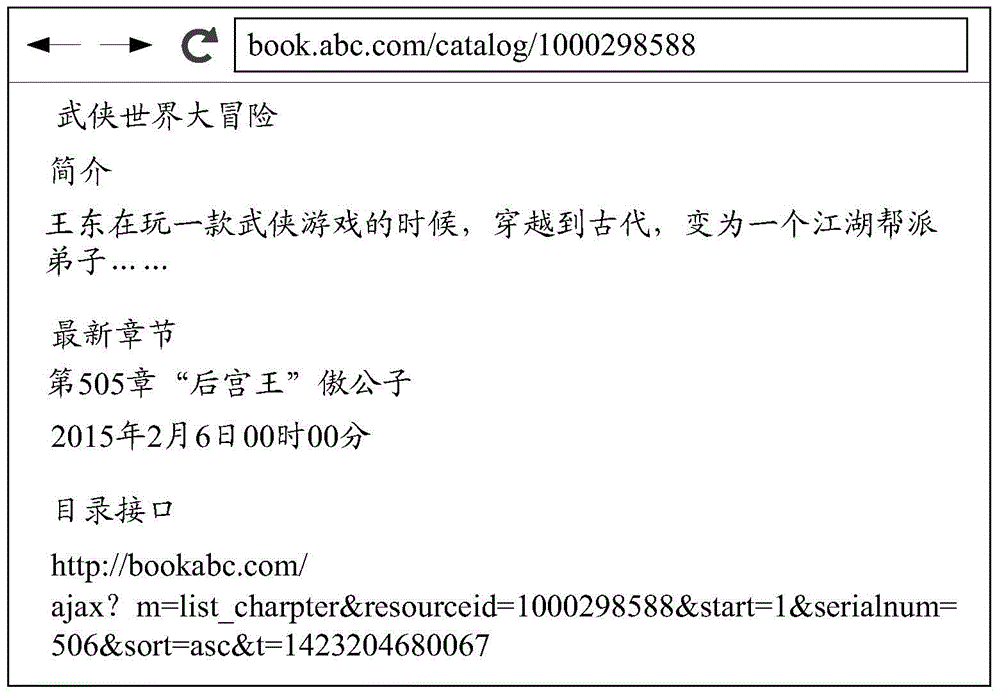
A network book contents integrity detection method and device
ActiveCN106033405AImprove legibilitySpecial data processing applicationsSerial codeDistributed computing
The invention provides a network book contents integrity detection method and device. The method comprises the steps of extracting the contents of a network book; obtaining the chapter number of each chapter in the contents of the network book; converting the chapter numbers into corresponding figures; acquiring the contents position serial number of each chapter; comparing the chamber number of each chapter and the corresponding contents position serial number. If the chamber number of each chapter and the corresponding contents position serial number are equal, it can be determined that the contents of the network book are complete and if the chapter number is greater than the contents position serial number, it can be determined that the contents of the network book are deficient. The network book contents integrity detection method and device are characterized in that extracted network book contents are compared with prestored network book contents; if the two are the same, the extracted network book contents are complete and if the two are not the same, the network book contents are not complete; the method and the device can detect the integrity of extracted network book contents and improve the readability.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com