Method for encrypting and authenticating efficient data without authentication center
A data encryption technology that does not require authentication. It is used in user identity/authority verification and key distribution. It can solve problems such as large computing burden, communication burden and data expansion, inability to perform offline data protection operations, and restrict technology promotion and application. Avoid the computational burden, reduce the workload, and have a good application prospect.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
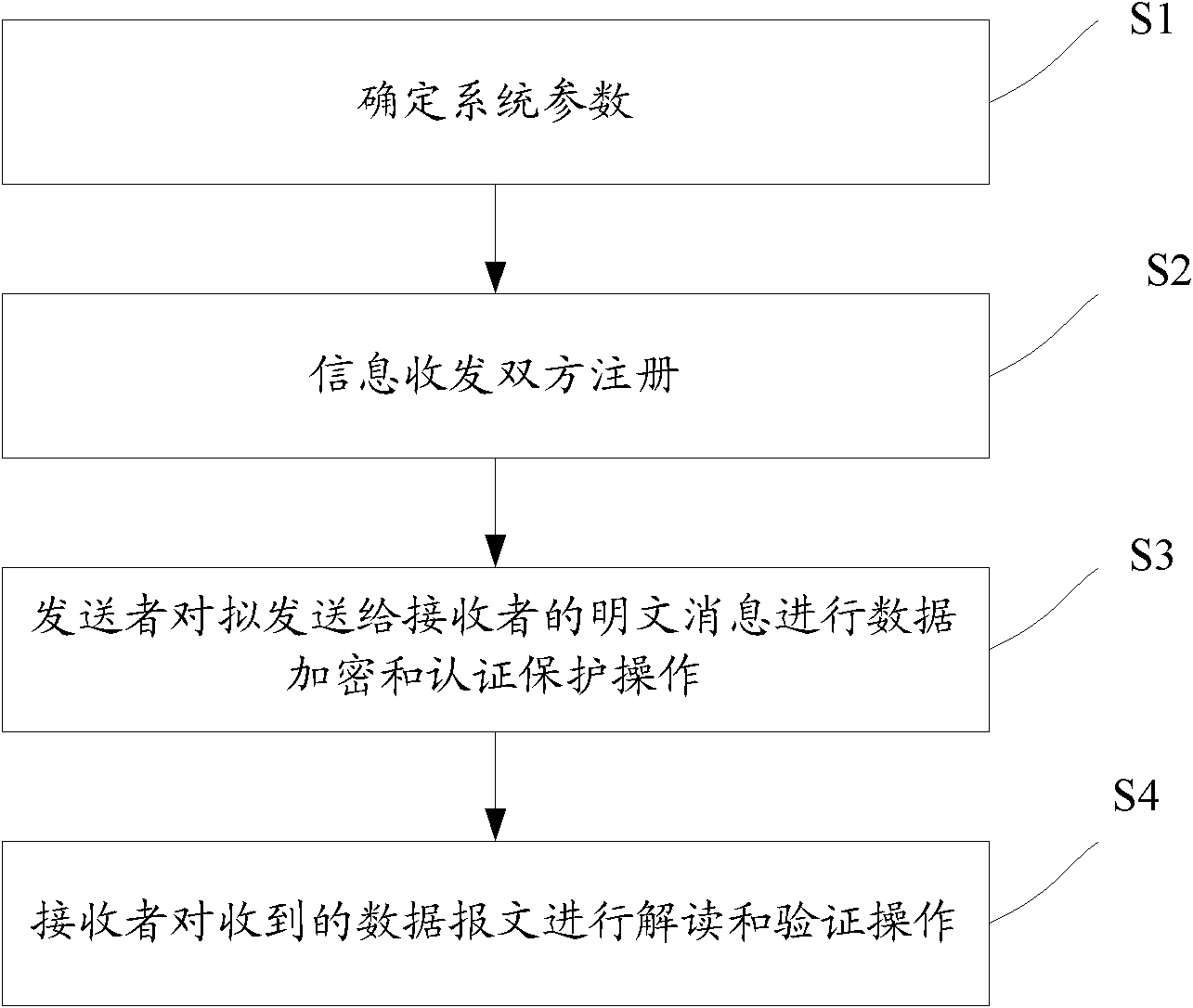
[0019] Embodiments of the present invention will now be described with reference to the drawings, in which like reference numerals represent like elements.
[0020] In this embodiment, the efficient data encryption and authentication method without an authentication center includes the following steps:
[0021] Step S1, determine system parameters: select a large integer p, elliptic curve E(GF(p)): y 2 =x 3 +ax+b(modp) is a safe elliptic curve defined on the finite field GF(p), a base point G is randomly selected on the elliptic curve E, and n=#E(GF(p)) is the elliptic curve E order, q is a large prime factor of n, and the private key of the key distribution center SA is SK SA , where SK SA is a random positive integer less than q-1, then the public key of the key distribution center SA is PK SA =SK SA × G;
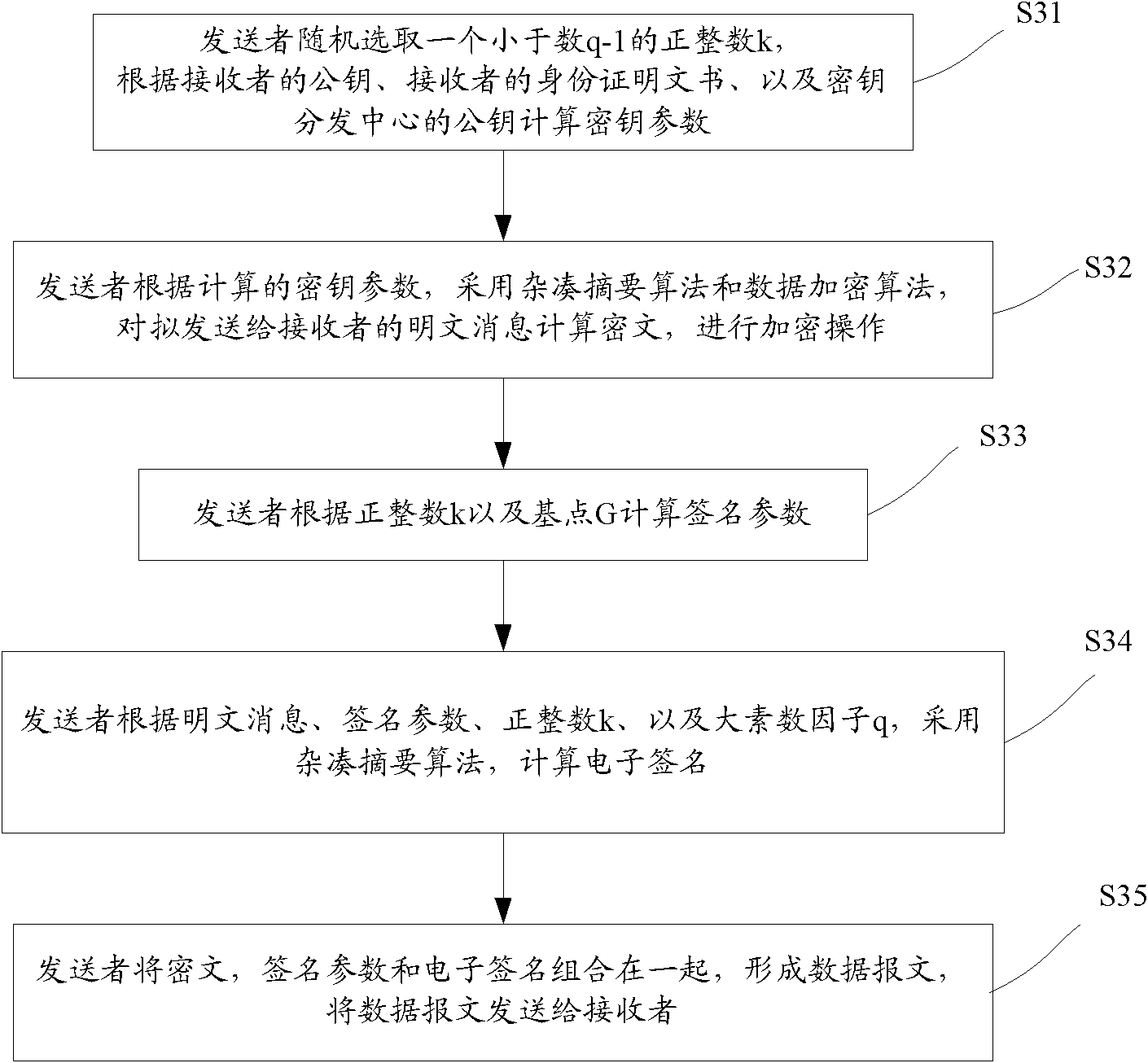
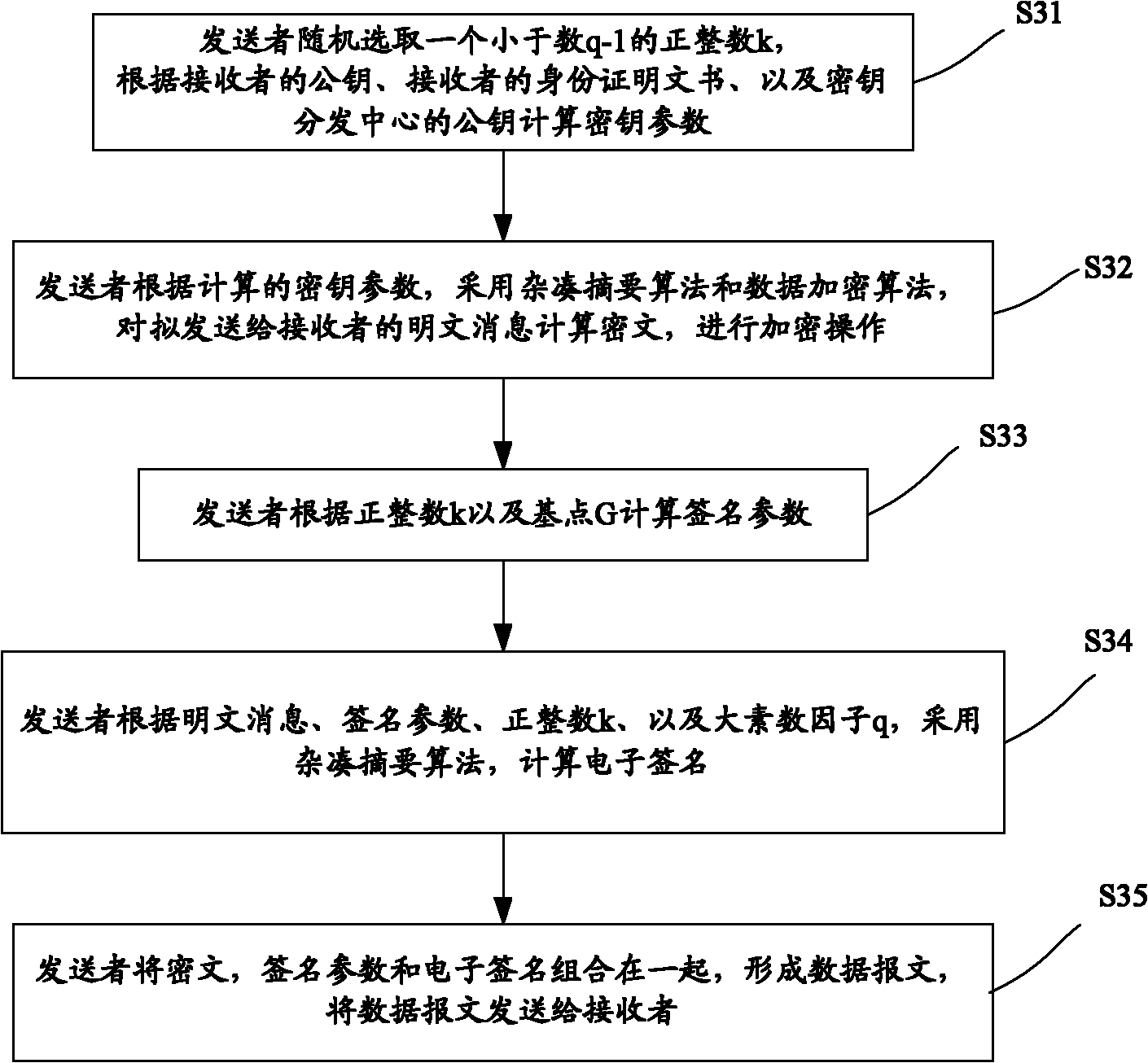
[0022] Step S2, the information sender and receiver, that is, the information sender A and the information receiver B, respectively execute the user registration pr...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com