Method of implementing reliable service on complementary structure information network
A structural information and credible technology, applied in the direction of electrical components, transmission systems, etc., can solve the problem of discounting the credibility of services provided by the Internet
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
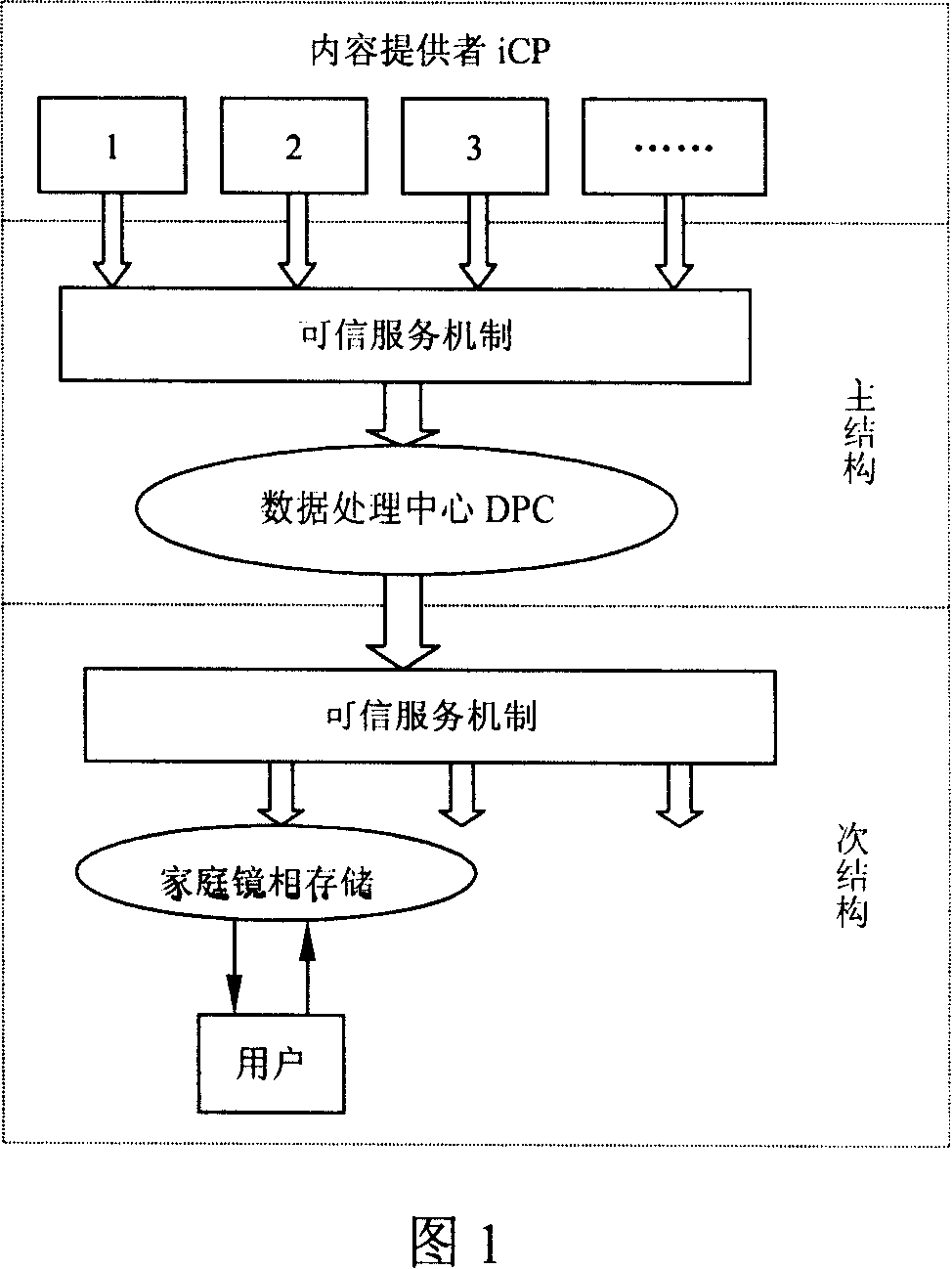
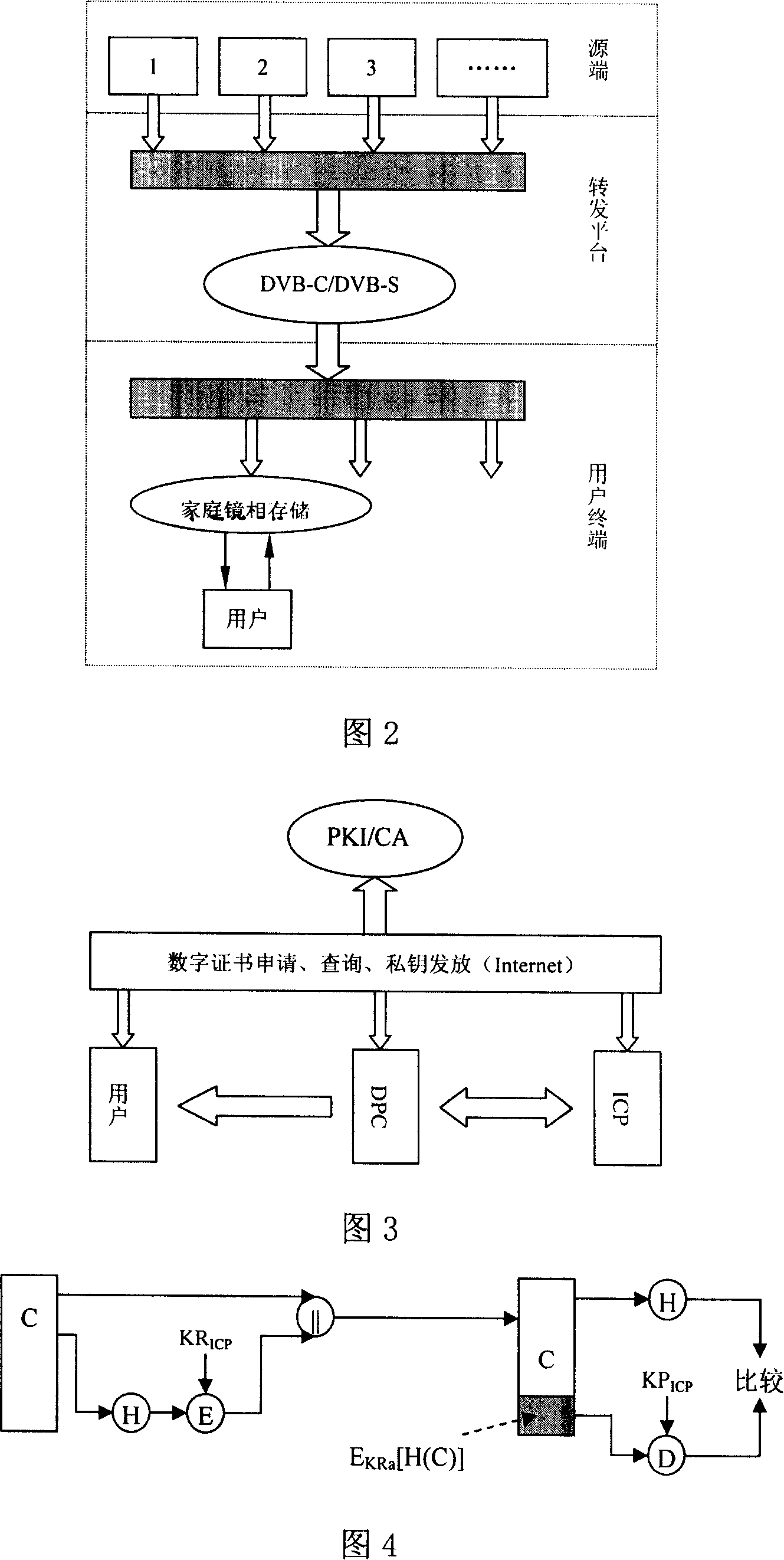
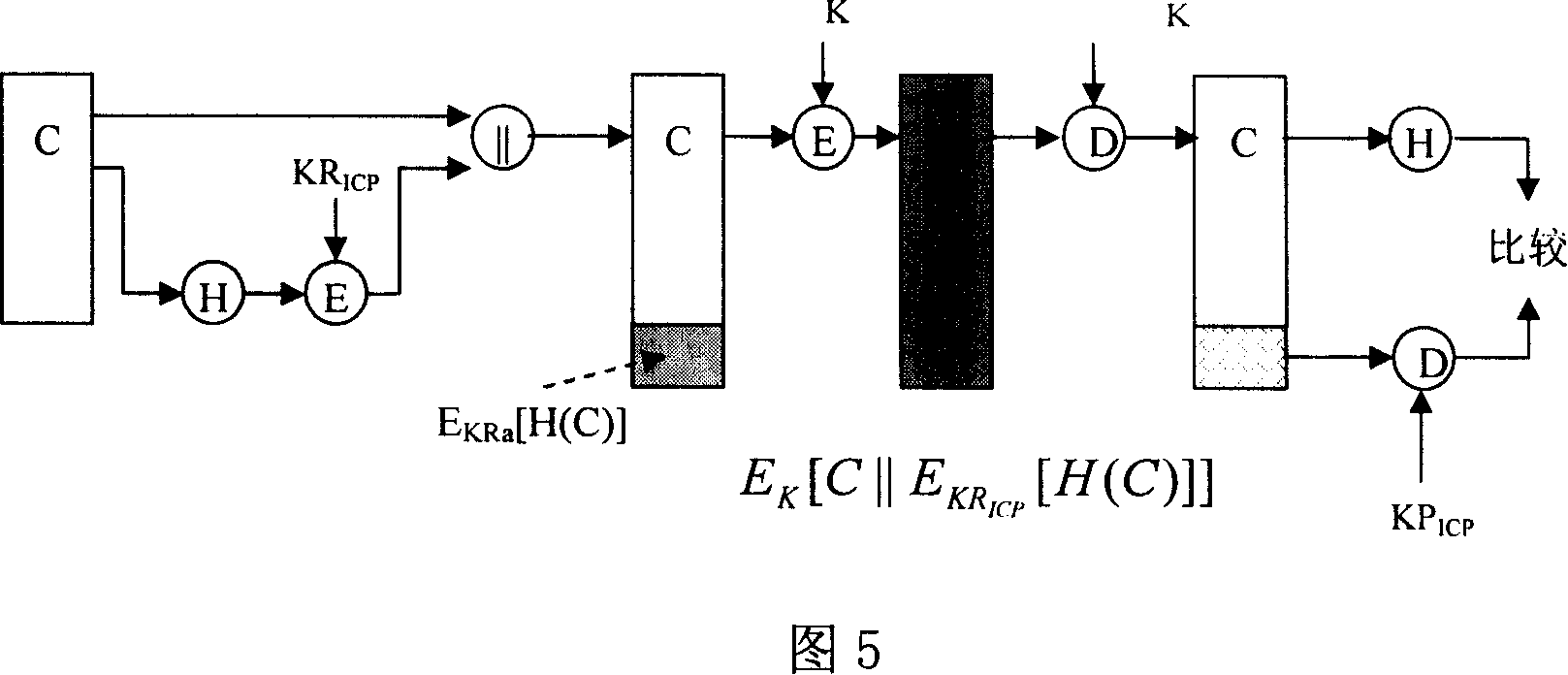
[0013] The invention provides a method for realizing trusted services on a complementary structure information network, including trusted services from information content providers to data processing centers, trusted services from data processing centers to users, and from information content providers to data processing The trusted service of the center includes the digital signature of information content, the integrity of information content, confidentiality, and non-repudiation functions, and the trusted service content from the data processing center to users includes the reliability, integrity, and confidentiality of information. The realization of the trusted service is based on the PKI / CA model, and the UCL indexing method is used to realize the indexing of the parameters. The present invention utilizes the existing UCL indexing method, such as the existing Chinese patent publication numbers CN1684415, CN1684459, and CN1684460 The UCL indexing method described.
[001...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com