Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
50results about How to "Prevent illegal modification" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
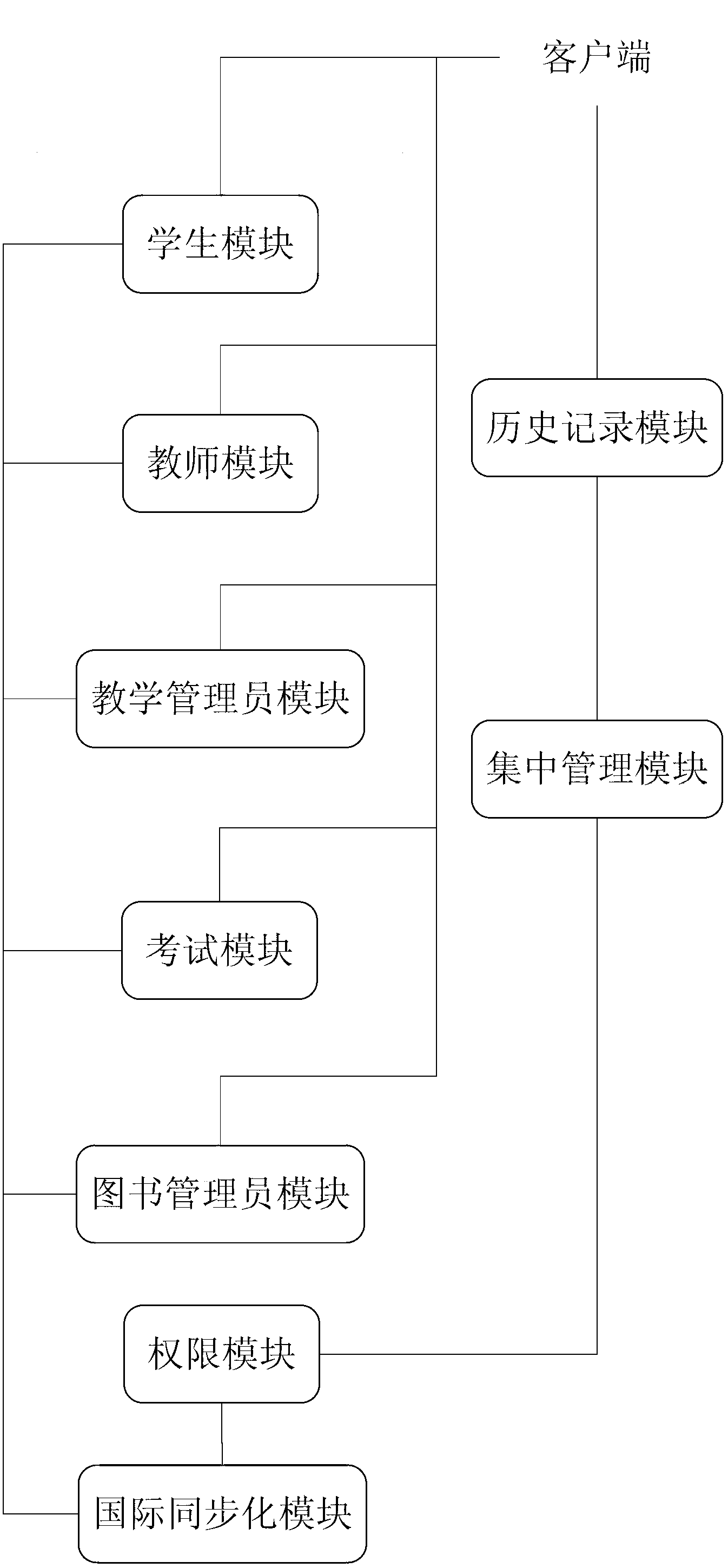
School intelligent information management system and method
The invention relates to the technical field of educational management and particularly discloses a school intelligent information management system and a school intelligent information management method. The school intelligent information management system comprises a client interaction module, an international synchronization module, a centralized management module and a history recording module, wherein the client interaction module is used for carrying out information interaction between the school intelligent information management system and a client and receiving a request of the client; the request comprises selection on language and application modes; the international synchronization module is used for carrying out language processing of languages; the centralized management module is used for carrying out sorting processing on different information in the request; and the history recording module is used for recording the different information subjected to sorting processing and storing the record. According to the invention, synchronization of student and teacher information management and synchronization of attendance management data are implemented, a time management function is added, and institutionalization, systematization, standardization and automation of a work flow of the school intelligent information management system are implemented.
Owner:新疆卡尔罗媒体科技有限公司
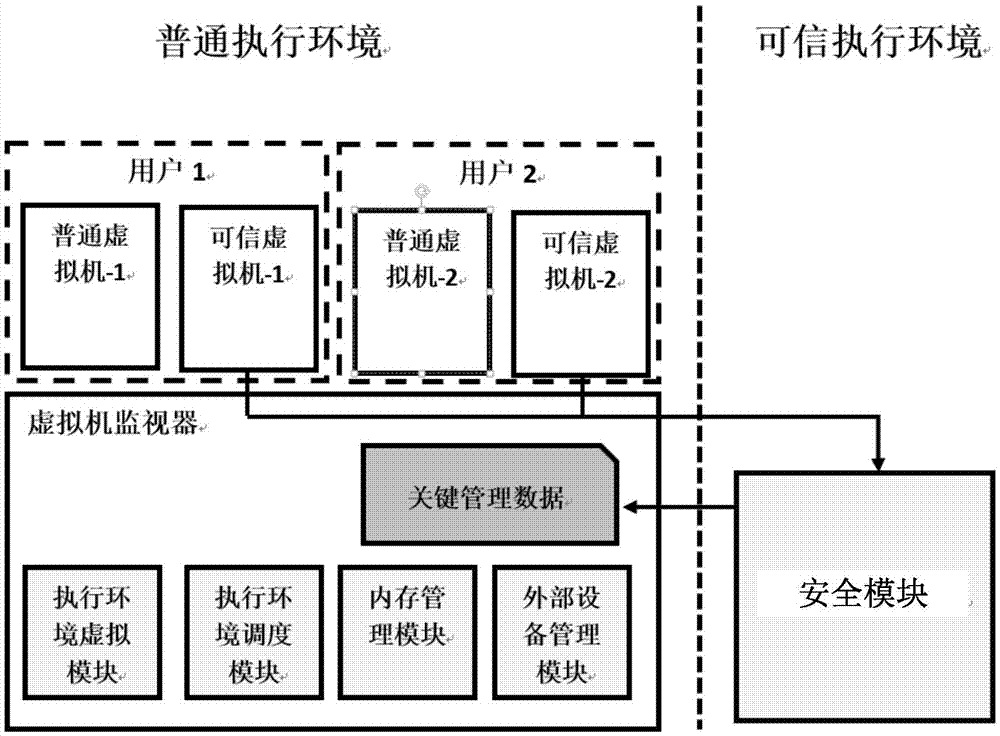
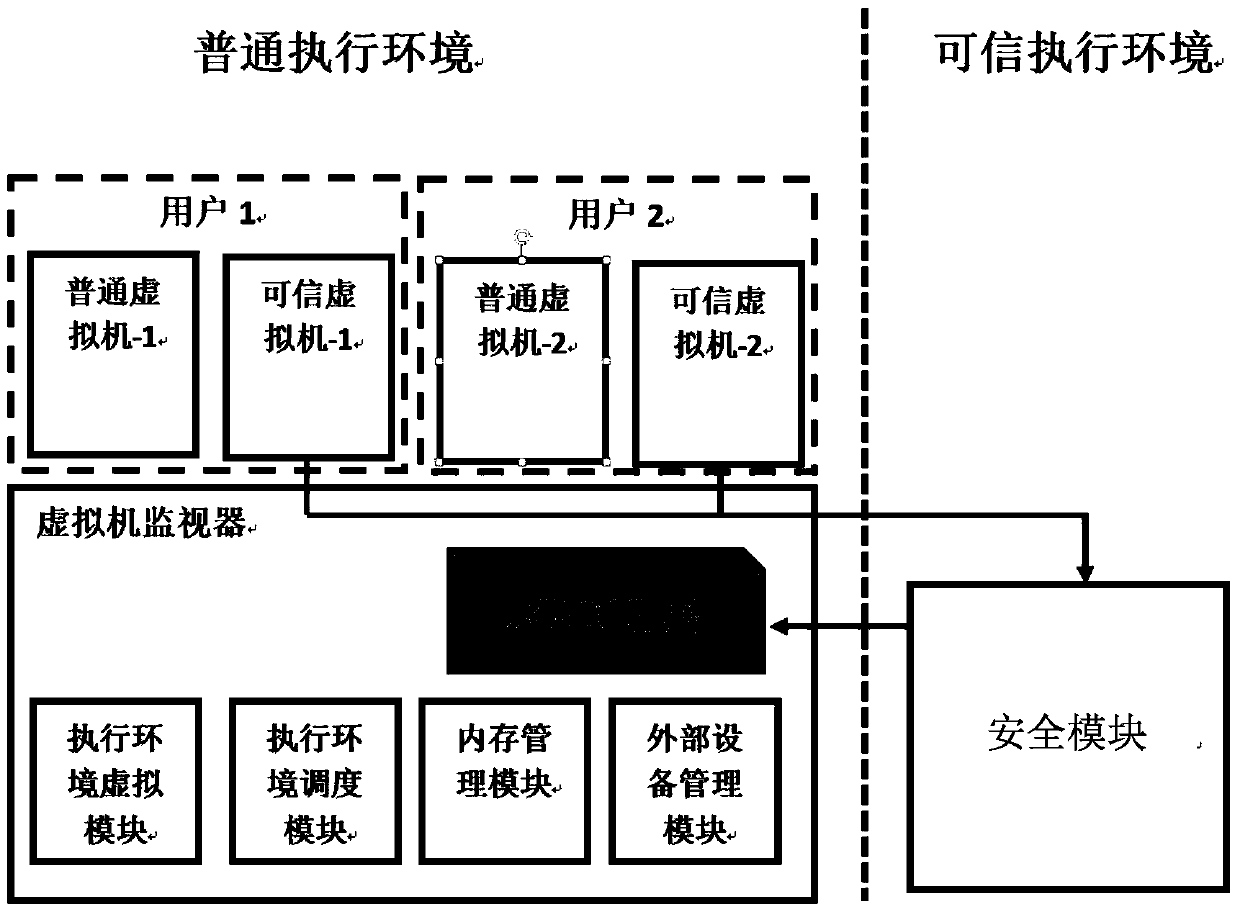
Execution environment virtualization method and apparatus, and virtual execution environment access method and apparatus
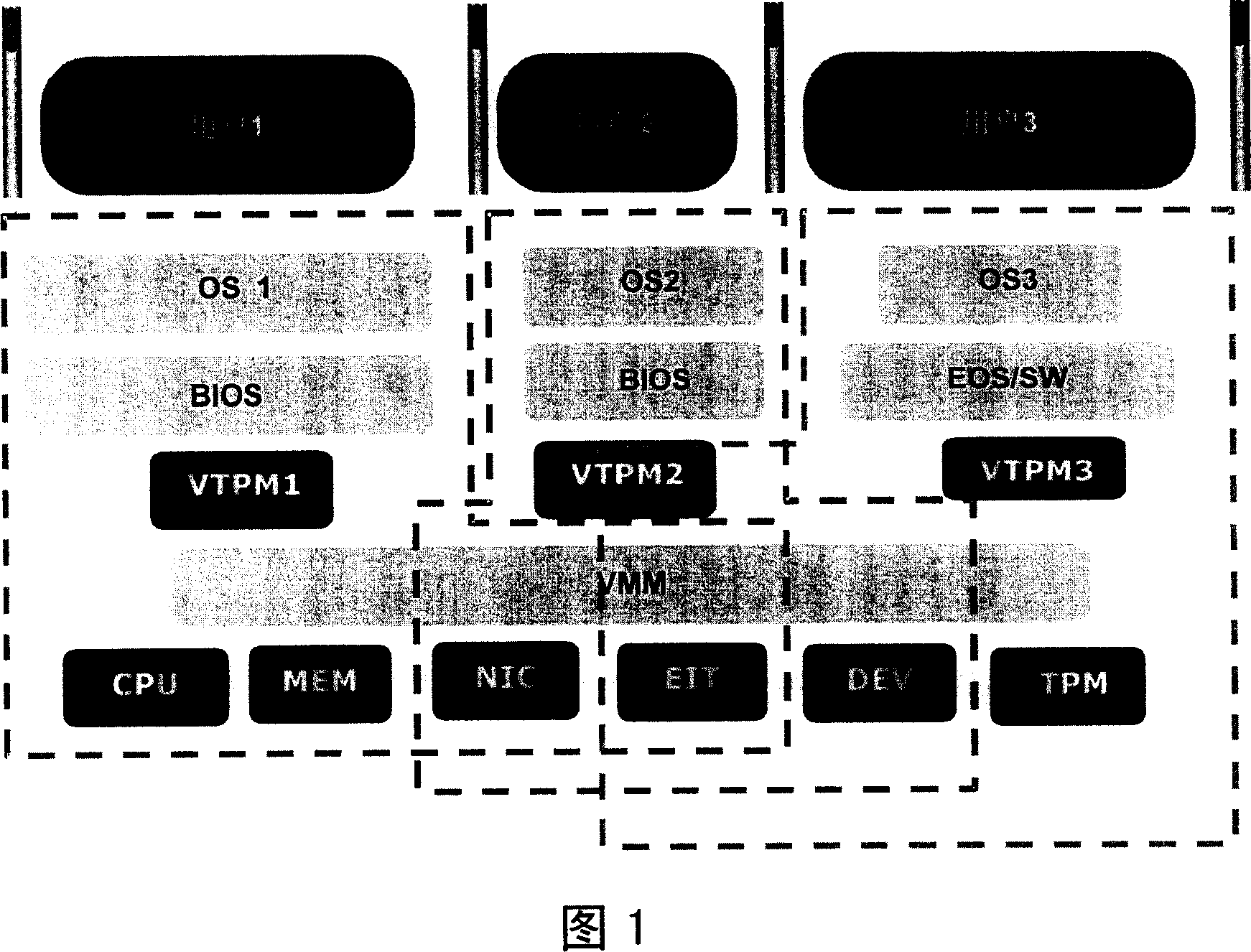
ActiveCN107038128APrevent illegal modificationEnsure data securityMemory architecture accessing/allocationUnauthorized memory use protectionVirtualizationAccess method
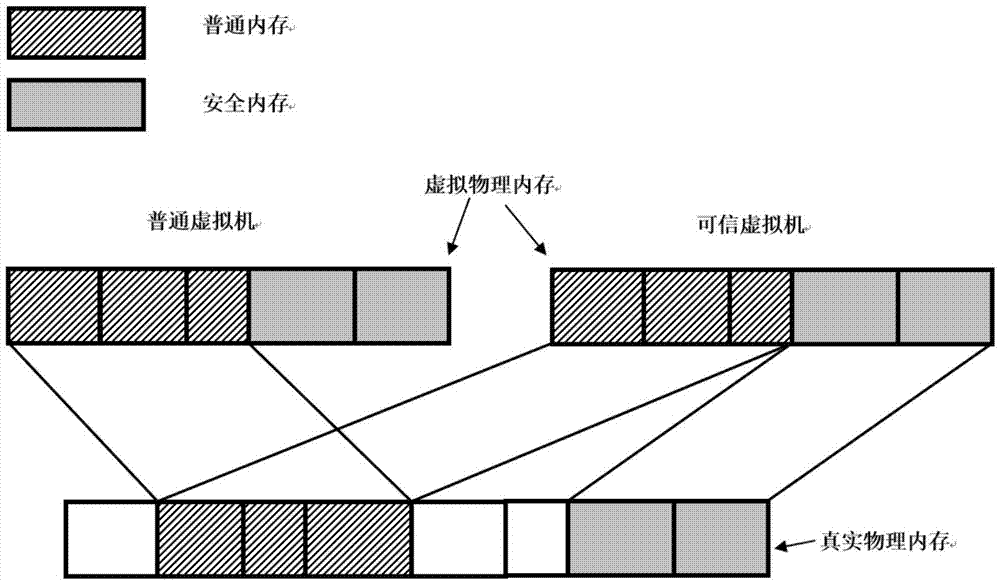
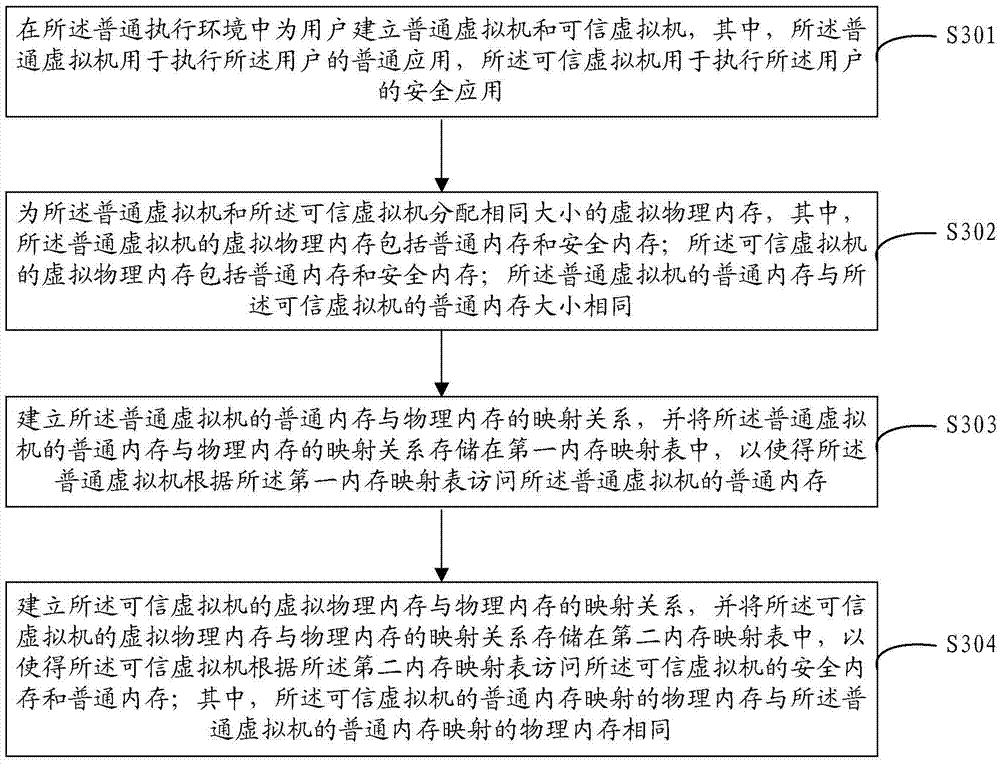
The invention discloses an execution environment virtualization method. The method is applied to a mobile terminal. The mobile terminal has a general execution environment provided by hardware. The method comprises the steps of establishing a general virtual machine and a trusted virtual machine for a user in the general execution environment, wherein the general virtual machine is used for executing a general application of the user, and the trusted virtual machine is used for executing a secure application of the user; performing memory allocation for the general virtual machine and the trusted virtual machine, and establishing a mapping relationship between a general memory of the general virtual machine and a physical memory to obtain a first memory mapping table; and establishing a mapping relationship between a virtual physical memory of the trusted virtual machine and the physical memory to obtain a second memory mapping table. According to the method, the two virtual machines are used to simulate the general execution environment and the trusted execution environment for the user, so that the general application and the secure application can run in the independent execution environments, the execution environments of the secure application and the general application are isolated, and the user data security is ensured.
Owner:HUAWEI TECH CO LTD
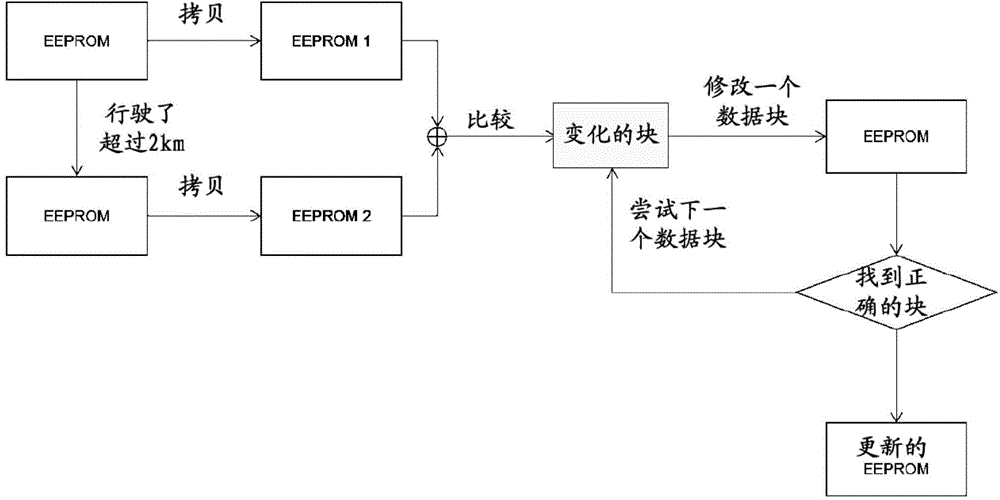
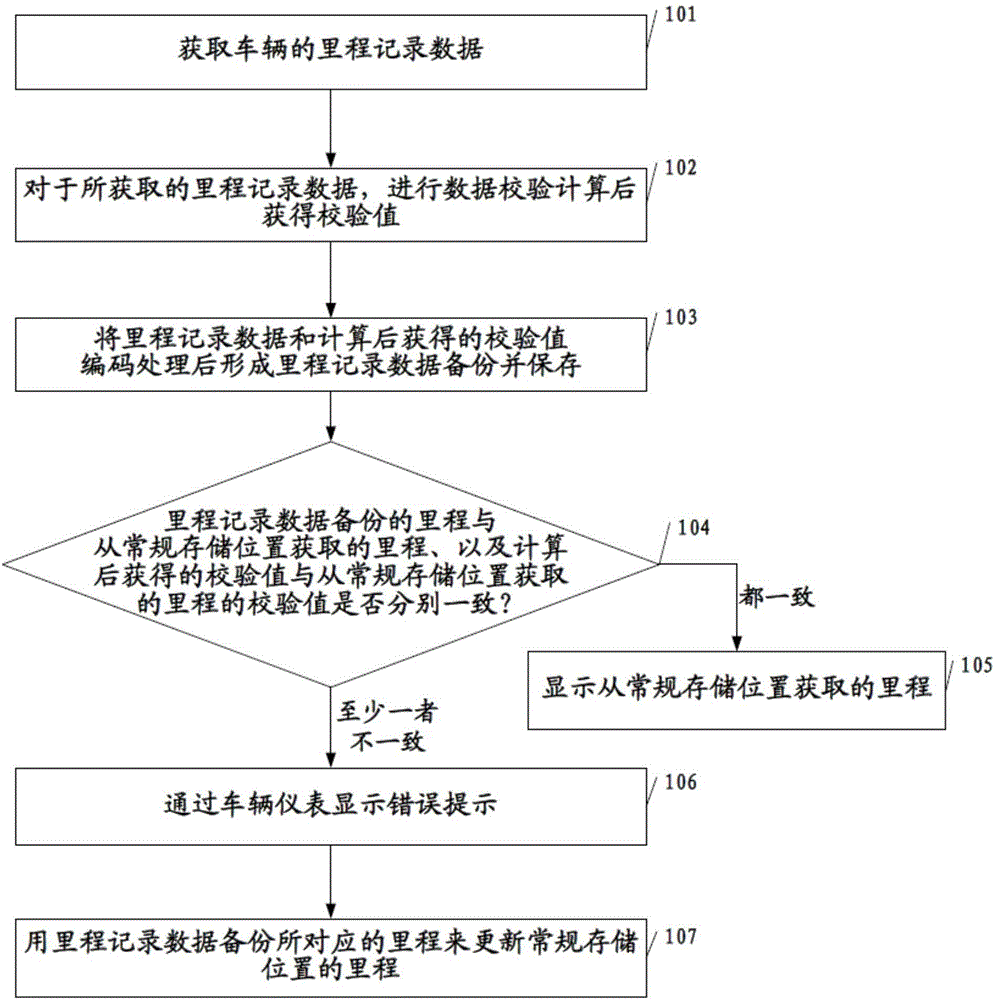
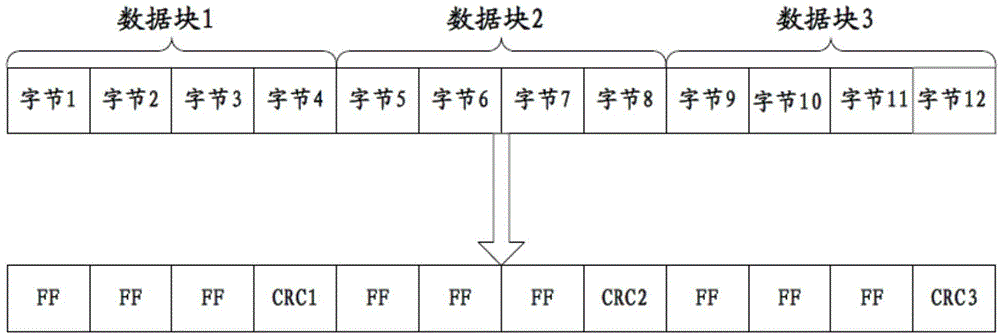
Method and system for preventing vehicle mileage tampering
InactiveCN104978534APrevent illegal modificationImprove reliabilityDigital data protectionRedundant operation error correctionEmbedded systemBackup
The invention provides a method and a system for preventing vehicle mileage tampering. The method comprises the following steps of: obtaining mileage record data of a vehicle; performing data checking calculation on the obtained mileage record data and then obtaining a checking value; performing coding processing on the mileage record data and the checking value obtained after the calculation to form mileage record data backup and storing the mileage record data backup, wherein the storage position of the mileage record data backup is different from a conventional storage position of the mileage record data; during vehicle ignition starting, comparing the mileage corresponding to the mileage record data backup with the mileage obtained from the conventional storage position, and comparing the checking value obtained after the calculation with the checking value corresponding to the mileage obtained from the conventional storage position; if the mileages are consistent and the checking values are consistent, normally displaying the mileage obtained from the conventional storage position by a vehicle instrument; and if at least one item is inconsistent, displaying error prompt through the vehicle instrument. Therefore whether the vehicle running mileage is artificially modified or not can be known, so that the vehicle running mileage is prevented from being illegally tempered.
Owner:CONTINENTAL AUTOMOTIVE WUHU
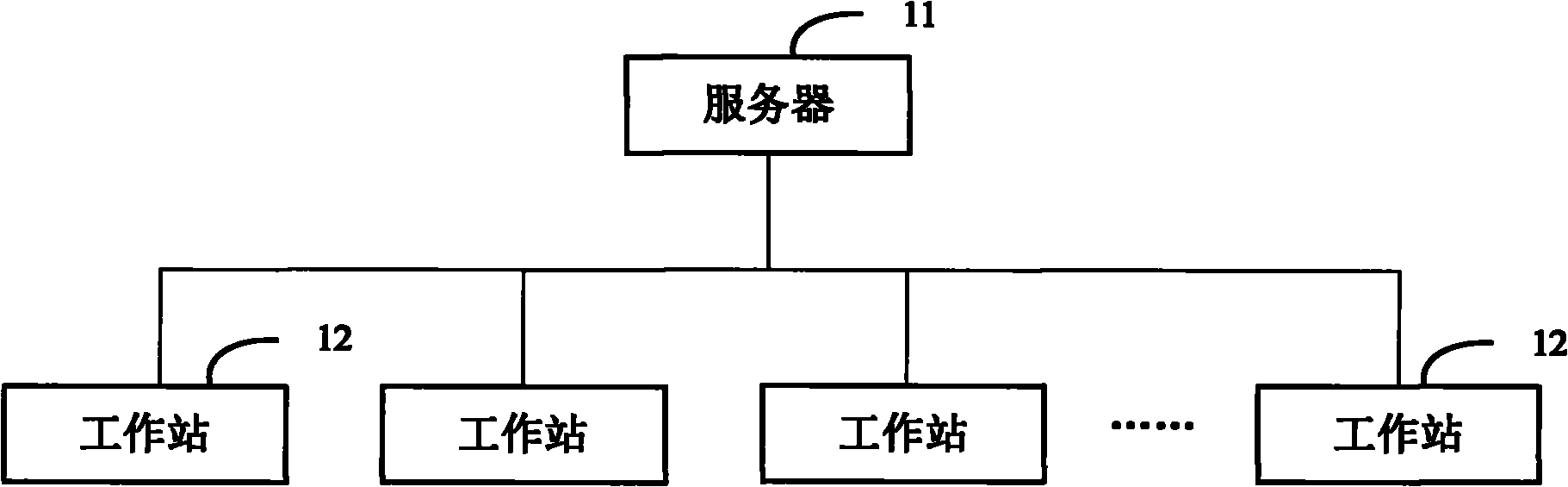
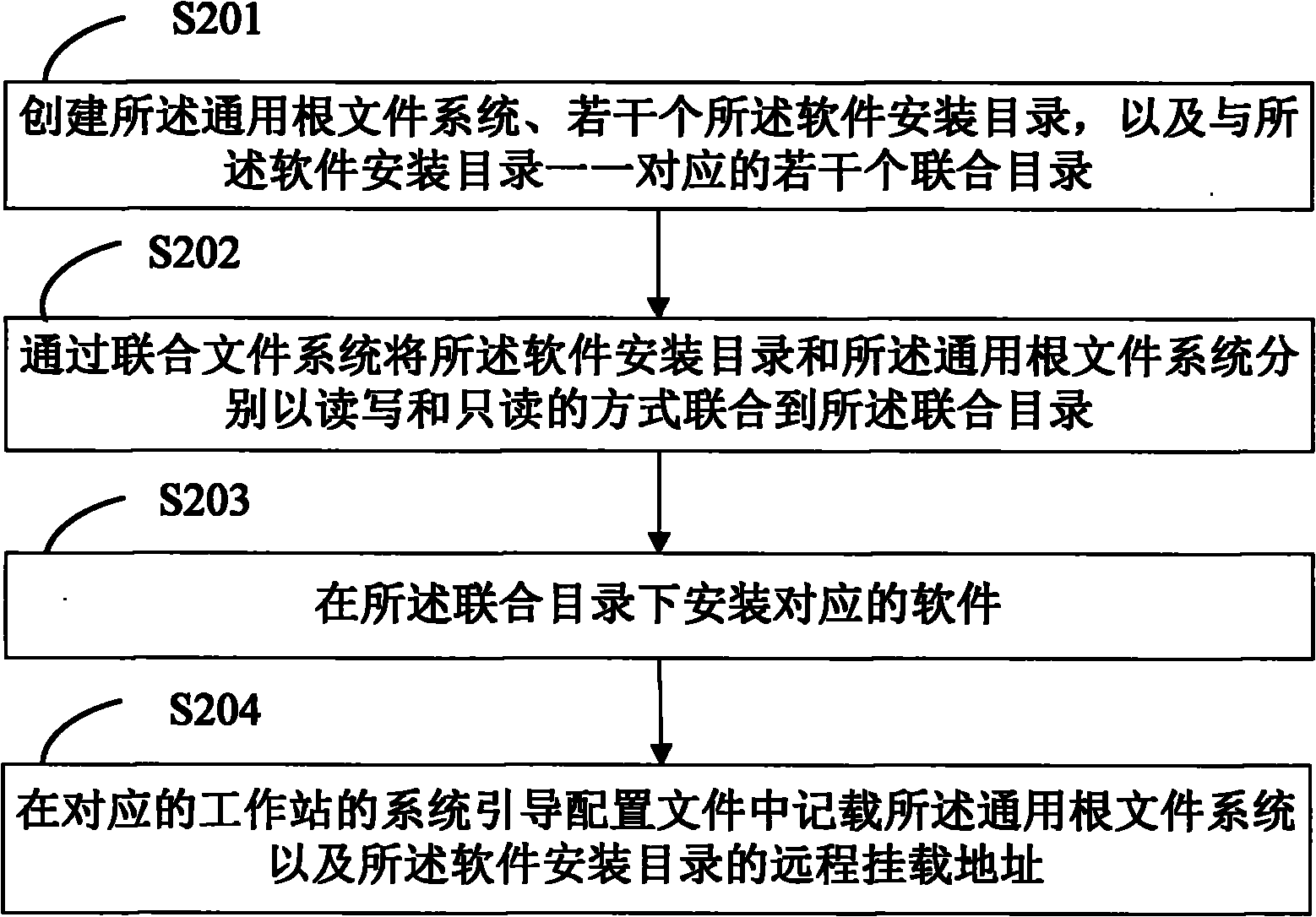
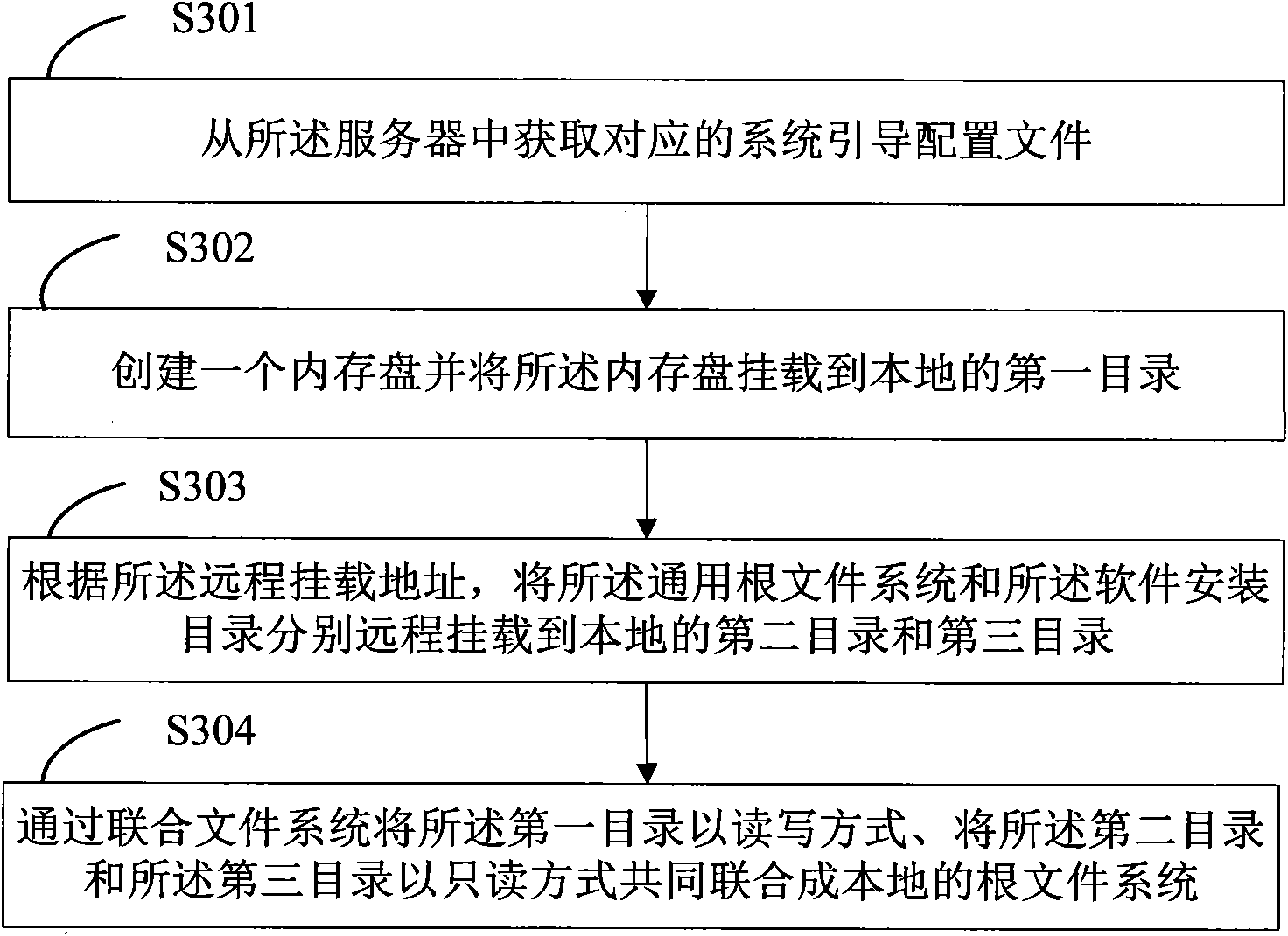
Diskless system, workstation thereof, and building method of local root file by workstation
ActiveCN101944129AReduce occupancyImprove acceleration performanceSpecial data processing applicationsPersonalizationFile system
The invention provides a diskless system, a workstation of the diskless system, and a building method of local root files by the workstation. The diskless system comprises a server and a workstation. The server is used to build a general root file system and a plurality of software installation directories, and install corresponding software in each software installation directory. The workstation is used to build a ram disk in local and mount the ram disk on the first directory in local. The general root file system and the software installation directories are in remote mounted on the second directory and on the third directory respectively in local, and the first directory, the second directory and the third directory are associated to form the local root file system through an associated file system with the way of read-write for the first directory, and the way of read only for the second directory and the third directory. The invention can realize the software individuation of each workstation based on the set of the general root file system.
Owner:江苏航天龙梦信息技术有限公司
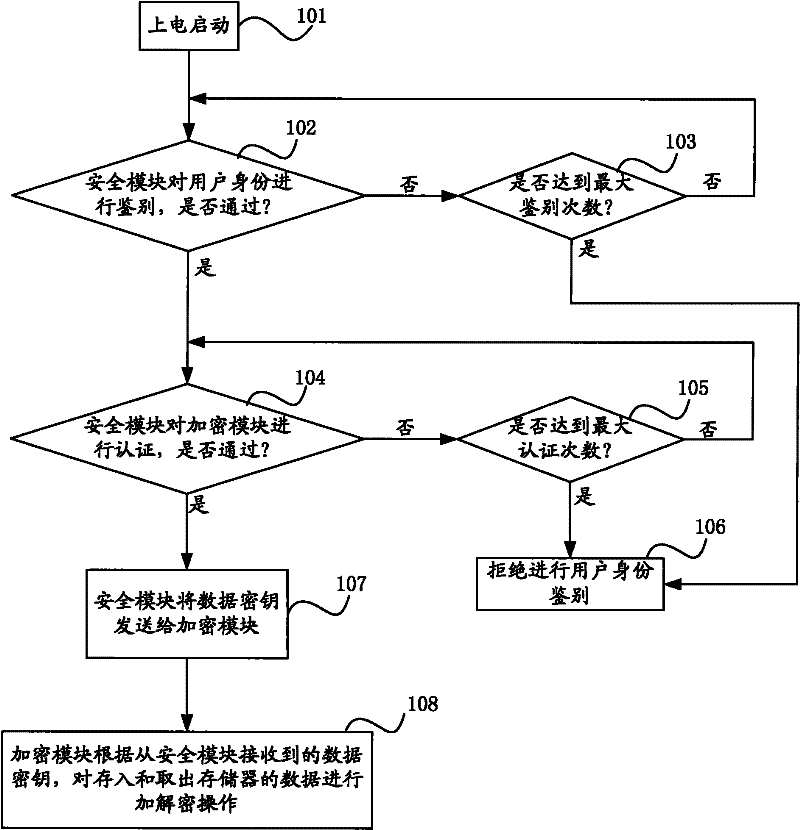
Data security protection method and data security protection device
ActiveCN102236607AGuaranteed reliabilityEnsure safetyUnauthorized memory use protectionInternal/peripheral component protectionComputer memoryMobile phone
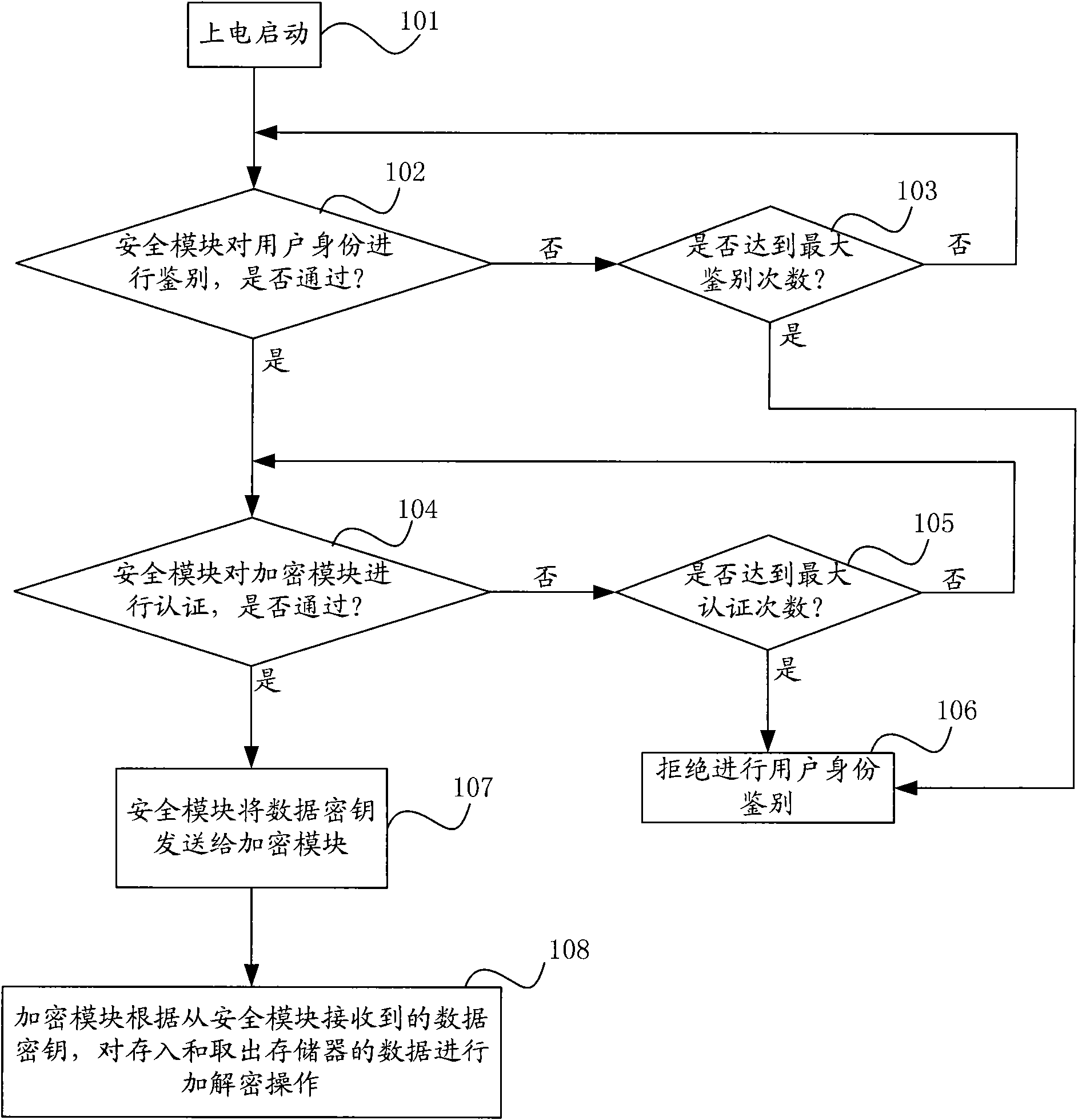
The invention relates to a data security protection method and a data security protection device for protecting data security in a computer memory. The method comprises the following steps that: while starting computer equipment, a security module respectively distinguishes and authenticates a user identity and an encryption module, after passing through the distinguishing and the authentication, the security module transmits a data key to the encryption module, in the following use, the encryption module encrypts the memory data for protection, and if the distinguishing and the authentication are not passed, the computer cannot be started. The device comprises the security module and the encryption module, which are arranged in computer equipment, such as a PC host, a PDA, a mobile phone, a PMP or a digital photo frame and the like, and are connected with each other. The method and the device implement the transparent encryption for the memory data of computer equipment and the distinguishing of user identity, and simultaneously, separately store a key and an encryption algorithm, thereby implementing higher security.
Owner:NATIONZ TECH INC
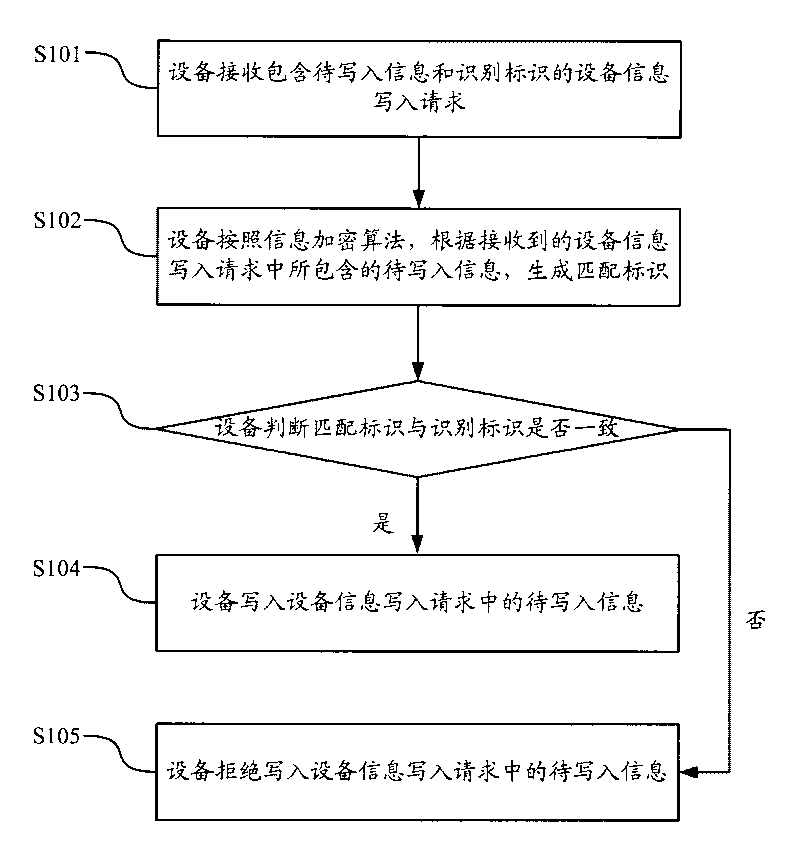
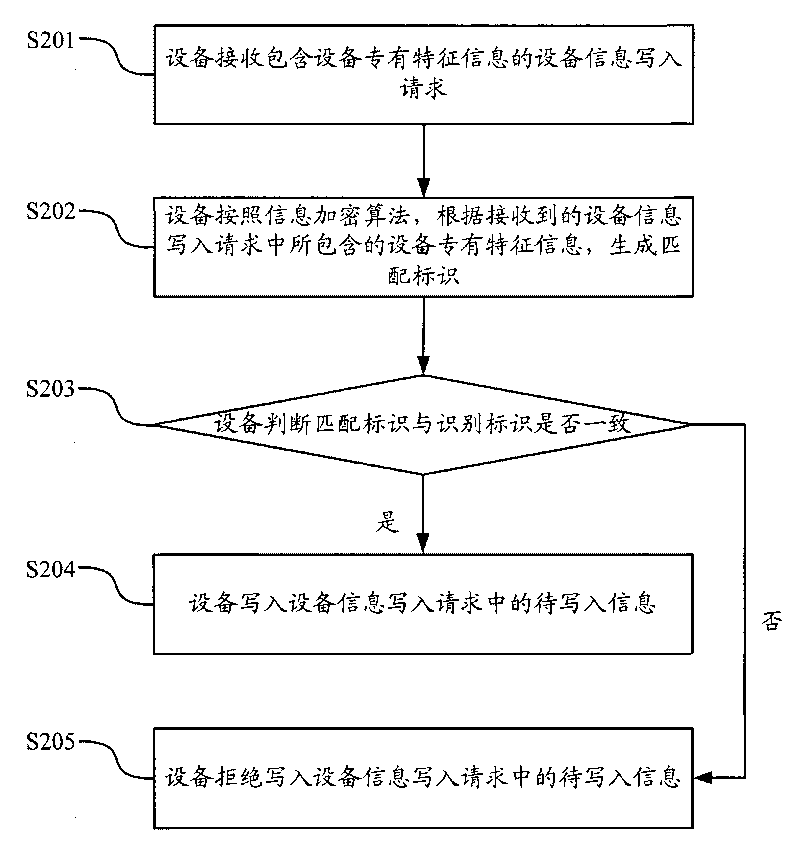
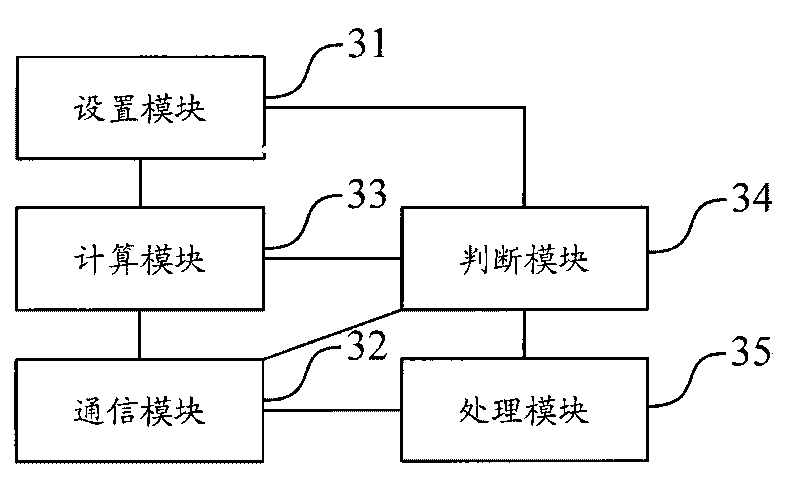
Method and device for preventing proprietary feature information of equipment from being falsified
InactiveCN101714986APrevent illegal modificationProtect legitimate gainsTransmissionEncryptionSoftware engineering
The invention discloses a method and a device for preventing proprietary feature information of equipment from being falsified, which limit the illegal writing of the proprietary information of the equipment by carrying out encryption calculation on the corresponding information through a preset encryption algorithm before the information of the equipment is written in according to the consistency verification of a result of the encryption calculation and a corresponding identification mark so as to prevent from illegally altering the information of the equipment and protect the legal benefit of the equipment manufacturer.
Owner:NEW H3C TECH CO LTD
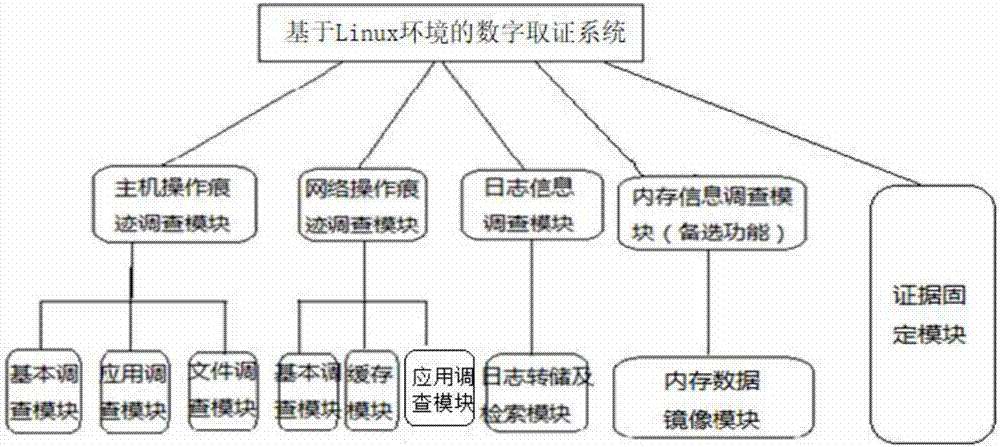
Digital evidence obtaining system based on Linux environment
InactiveCN107332820ARapid positioningEasy traceability analysisPlatform integrity maintainanceTransmissionDatabase fileDigital evidence
The invention discloses a digital evidence obtaining system based on a Linux environment. The system is composed of a host operation trace investigation module, a network operation trace investigation module, a log information investigation module, a memory information investigation module and an evidence fixing module. The host operation trace investigation module comprises a basic operation investigation function and an application information investigation function. The network operation trace investigation module comprises the basic operation investigation function, a network cache investigation function and a network application state investigation function. The log information investigation module comprises a log file analysis and storage function and a keyword search module. The memory information investigation module dumps a memory through adoption of an fmem tool and realizes memory information investigation through combination of a system tool. The evidence fixing module carries out hash processing on an original evidence file and a processed database file. According to the system, workloads of an evidence obtaining investigator are effectively reduced, concepts of evidence obtaining tool engineering and evidence fixing are introduced, and an evidence obtainer is prevented from illegally modifying an evidence file.
Owner:NANJING UNIV OF POSTS & TELECOMM
Method and system for allocating and protecting subscriber software-hardware configuration information
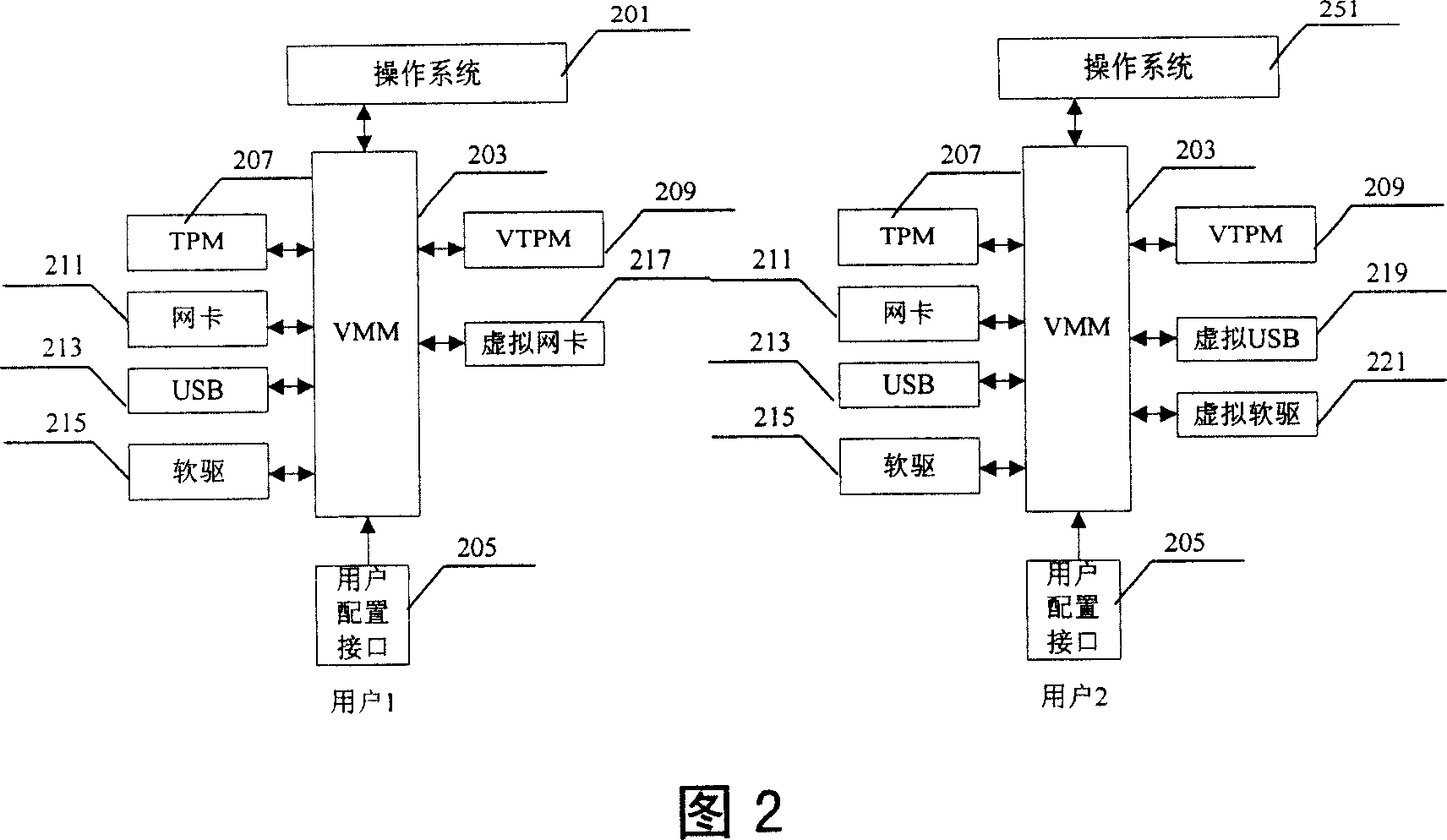
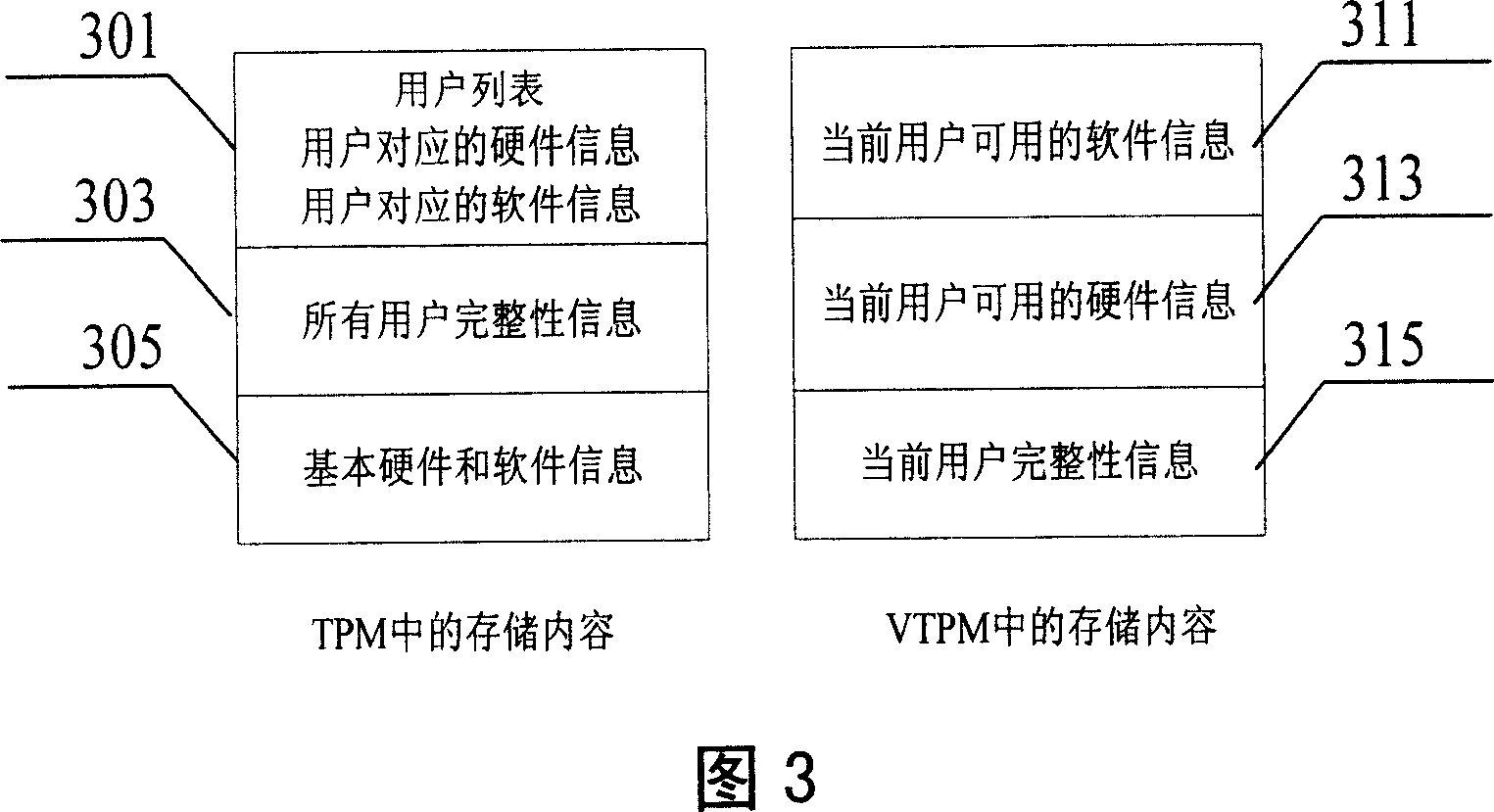
InactiveCN1991662APrevent illegal modificationDigital data processing detailsComputer hardwareUser input
The invention provides a method for allocating and protecting the allocation information of software and hardware, the method includes following steps: the VMM allocates the user's information for the user, the relative hardware information and software information, and stores them in the TPM, when the user input the user's information, the VMM read the relative hardware information and software information from the TPM to form the relative hardware information and software information of present user, and the present hardware information and present software information are stored in the VTPM; the VMM uses the hardware information and software information stored in the VTPM, and constructs the virtual hardware and available software corresponding to present user.
Owner:LENOVO (BEIJING) CO LTD
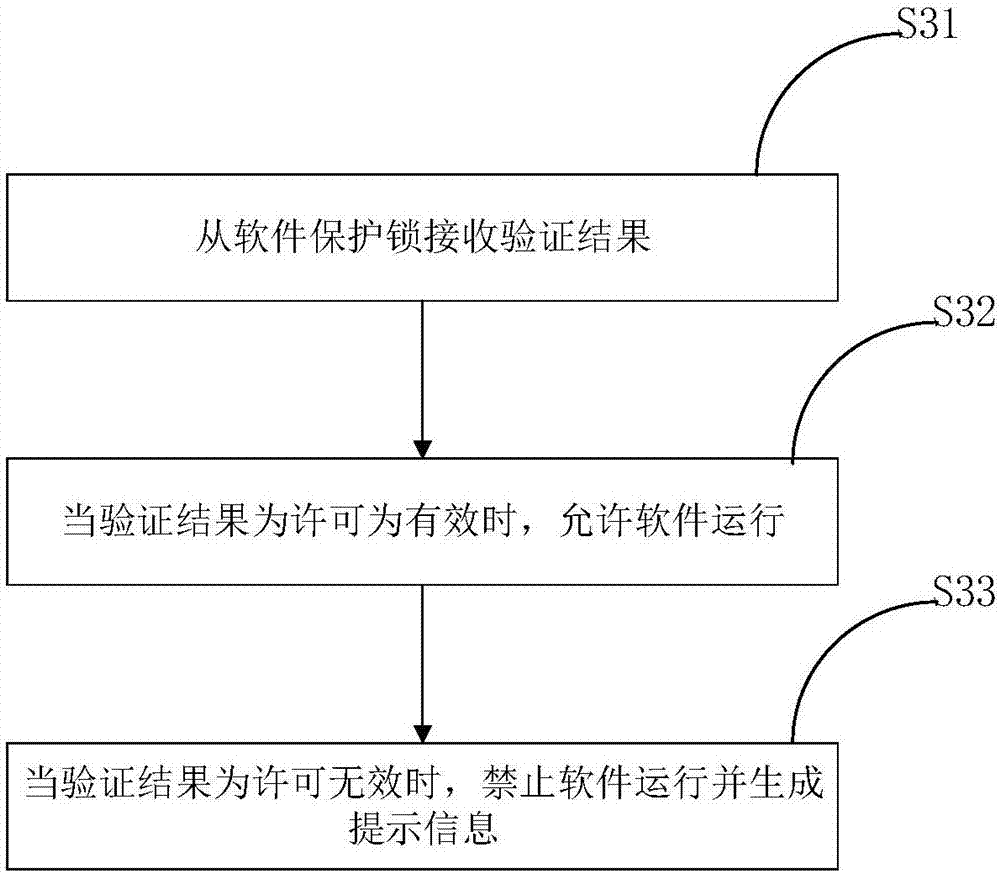
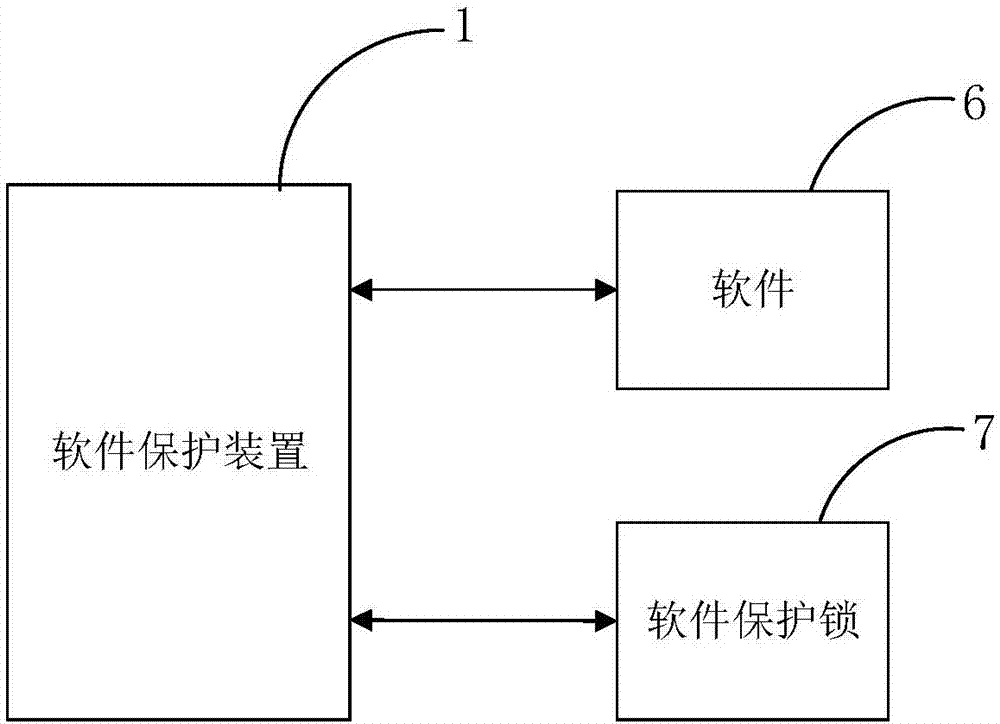
Software protection method and device and software protection lock
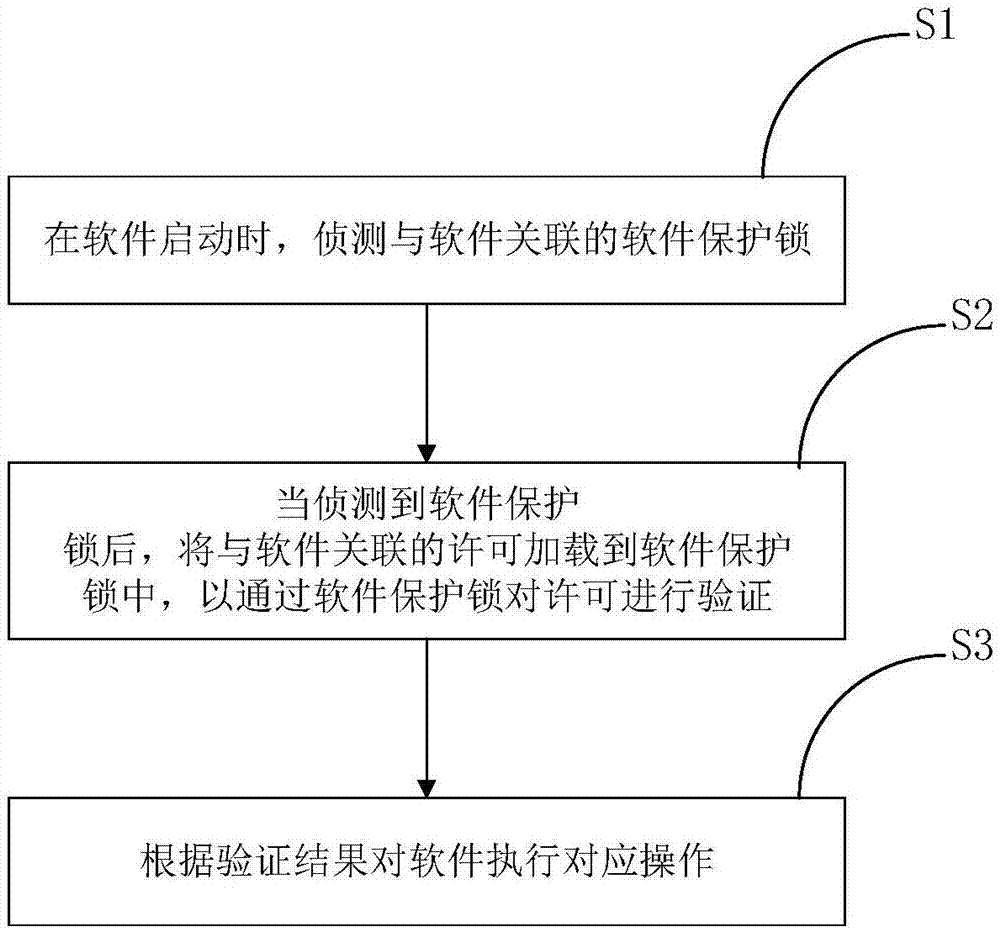
ActiveCN107391966AProtect the right to usePrevent illegal modificationProgram/content distribution protectionSoftware engineeringSoftware protection
The invention discloses a software protection method and device and a software protection lock. The software protection method is used for protecting software and comprises the steps that when software is started, the software protection lock associated with the software is detected; when the software protection lock is detected, a permission associated with the software is loaded into the software protection lock, so that the permission is verified through the software protection lock; corresponding operation is performed on the software according to the verification result. According to the method, the permission does not need to be placed in the software protection lock, so that the situation that the permission is illegally modified by others obtaining the software protection lock is avoided, and interests of a software manufacturer are guaranteed; a user can use a plurality of pieces of protected software by only using one software protection lock, and the use cost is reduced.
Owner:BEIJING SENSESHIELD TECH
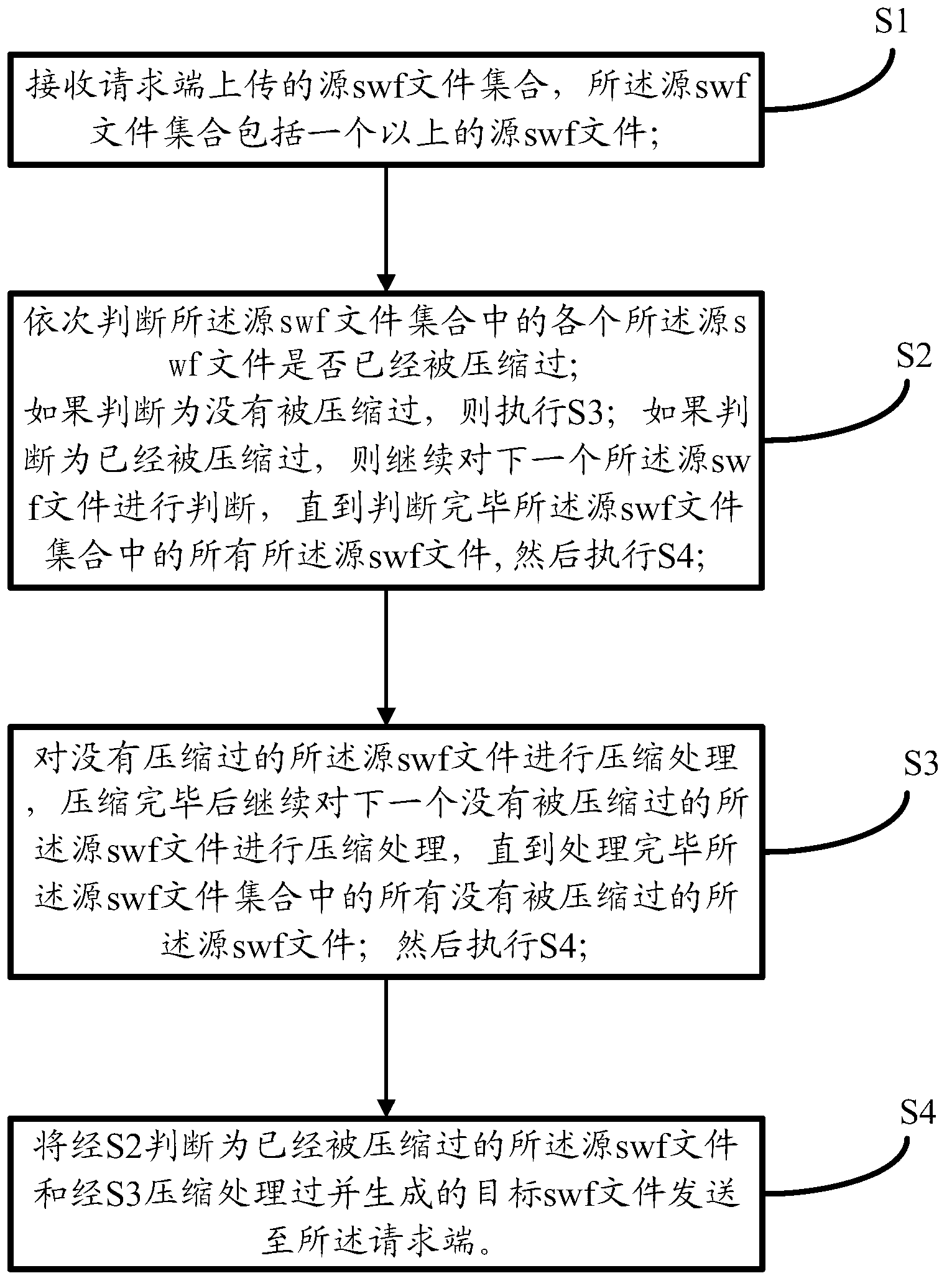
Method for volume compression of swf (shock wave flash) files
ActiveCN102799673AFast compressionImprove work efficiencyCode conversionSpecial data processing applicationsShock waveImage compression
The invention relates to a method for volume compression of swf (shock wave flash) files. The method comprises the following steps: S1, receiving a source swf file set uploaded by the request end, wherein the source swf file set comprises more than one source swf file; S2, successively judging whether the source swf file in the source swf file set has been compressed, if no, carrying out S3, and otherwise, continuously judging the next source swf file; S3, compressing the source swf file which has not been compressed, and then continuously compressing the next source swf file which has not been compressed; and S4, transmitting the source swf file which has been judged to be compressed in S2 and a target swf file which is compressed and generated in S3 to the request end.
Owner:4399 NETWORK
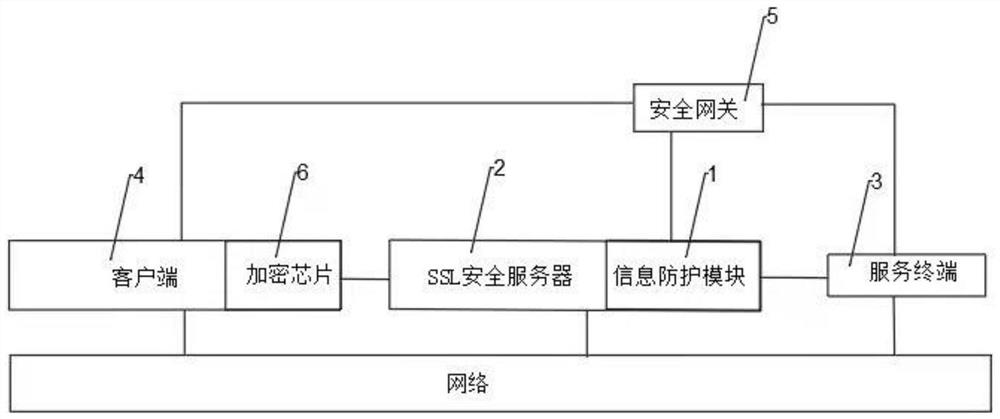
System for establishing communication based on SSL
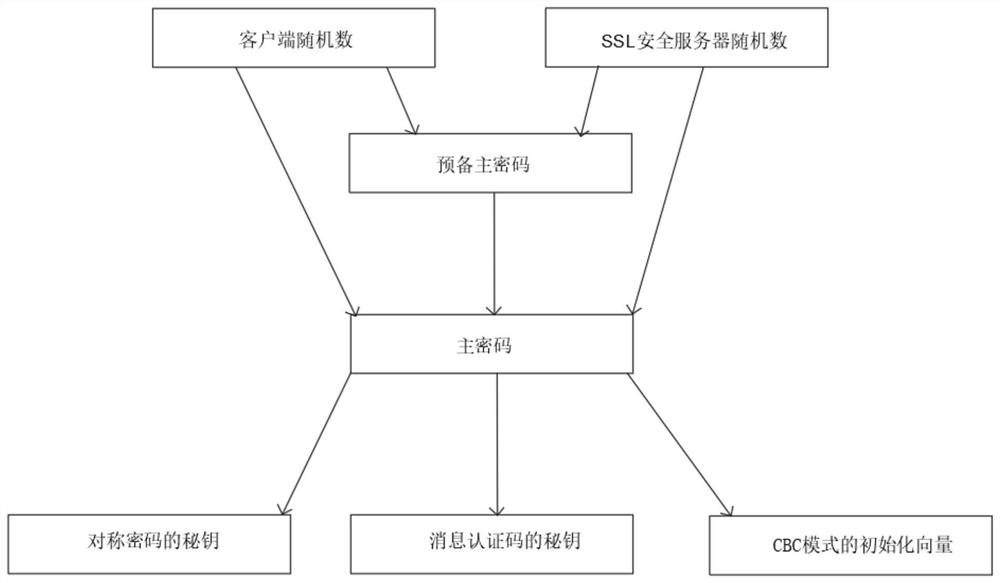
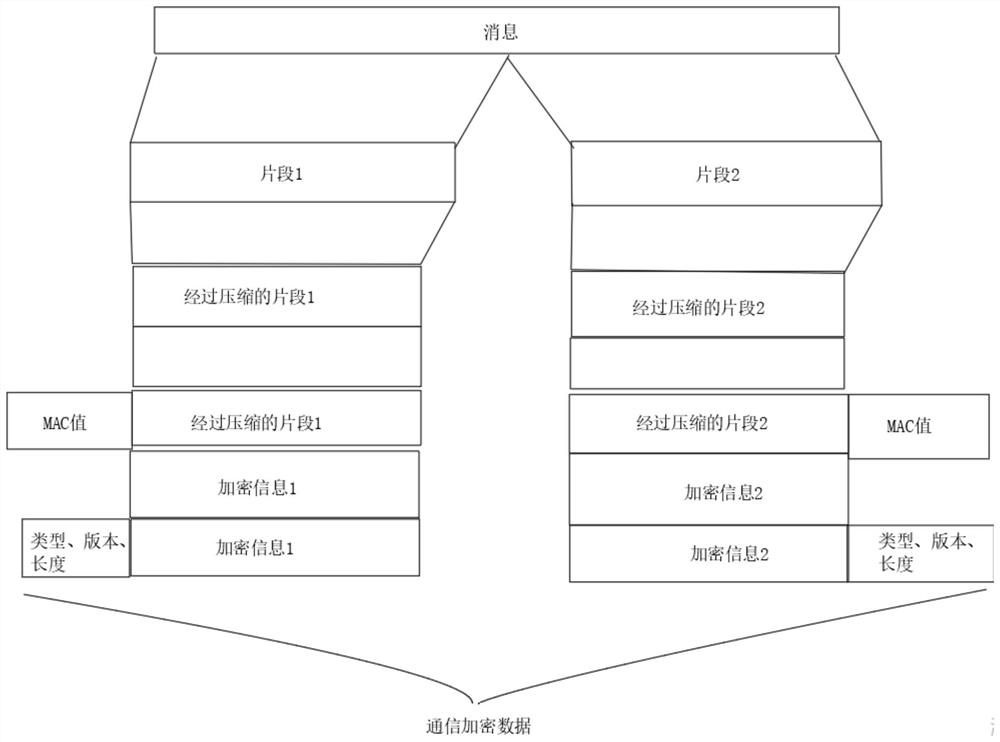
PendingCN113904767APrevent illegal modificationKeep your private key safeKey distribution for secure communicationUser identity/authority verificationProtocol for Carrying Authentication for Network AccessTrust certificate
The invention belongs to the technical field of communication, and particularly relates to a system for establishing communication based on an SSL. The system comprises an information protection module, an SSL security server, a service terminal, a client and an encryption chip; the encryption chip is arranged on a client side, and when the encryption chip is called by the client side, the encryption chip matches a corresponding service terminal security certificate and gives the same to the client side. The system has the advantages that the security gateway or the network bridge captures the data encrypted by the SSL, captures the handshake process of the SSL protocol, extracts the X.509 certificate chain, verifies the legality of the X.509 certificate chain transmitted in the extracted handshake process according to the related standard of the PKI and a trusted certificate list provided by a user, and improves the security of the X.509 certificate chain. And the security gateway or the network bridge allows the SSL connection with the legal certificate chain to pass, and filters and prevents the SSL connection with the illegal certificate chain.
Owner:SHENZHEN WHOLETON INFORMATION TECH
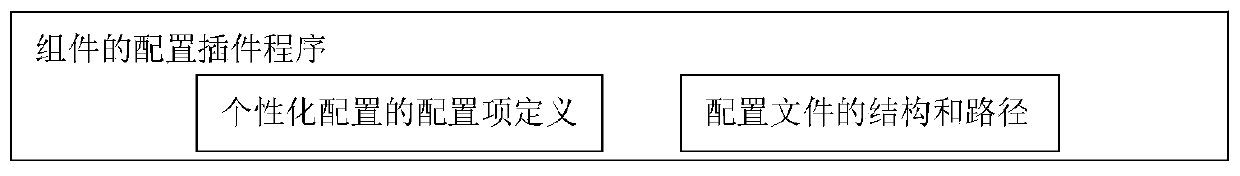
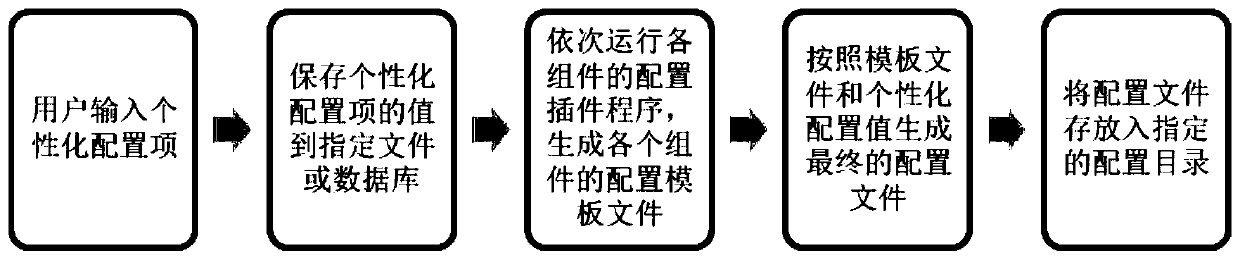
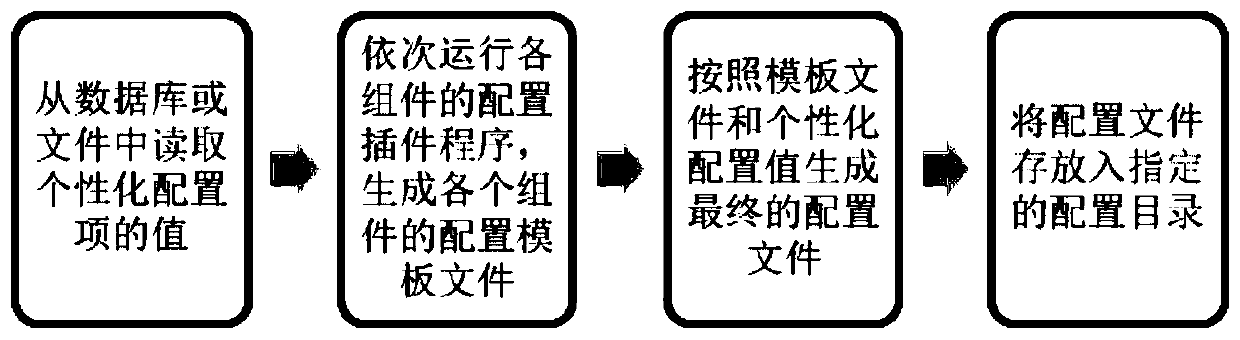
Cloud platform configuration file management method and management system
PendingCN110908730APrevent illegal modificationConvenient operation and maintenance managementPlatform integrity maintainanceProgram loading/initiatingPersonalizationConfiguration item
The invention discloses a cloud platform configuration file management method and management system. Configuration programs of all components are placed under a specified file path in a plug-in mode;each plug-in comprises two parts of content, wherein the first part comprises personalized configuration item definitions needing to be modified, and the second part comprises a structure of a complete configuration file of the component and names and values of all configuration items; in a cloud platform deployment stage, personalized configuration item definitions of all the components are opened to a user input value, and the names and values of the personalized configuration item definitions input by the user are stored in a specific storage area; and an accessory plug-in program is executed to generate a configuration template file of each component, a file defined by the personalized configuration item of the specific storage area and the configuration template file are called to generate a configuration file of the component, and the configuration file of the component is placed in a configuration folder of the component. According to the configuration method and the configuration system provided by the invention, effective and safe management of multiple types of complex configuration files of the cloud platform can be realized.
Owner:FENGHUO COMM SCI & TECH CO LTD
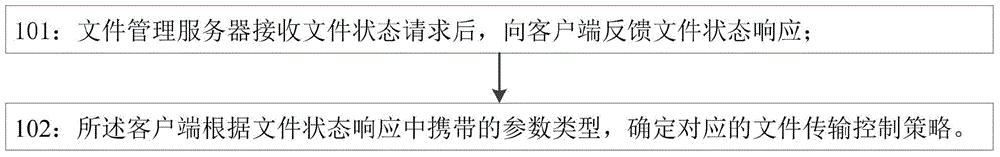
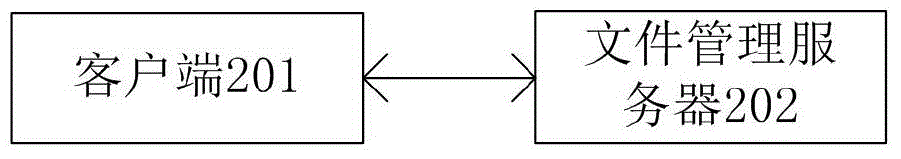
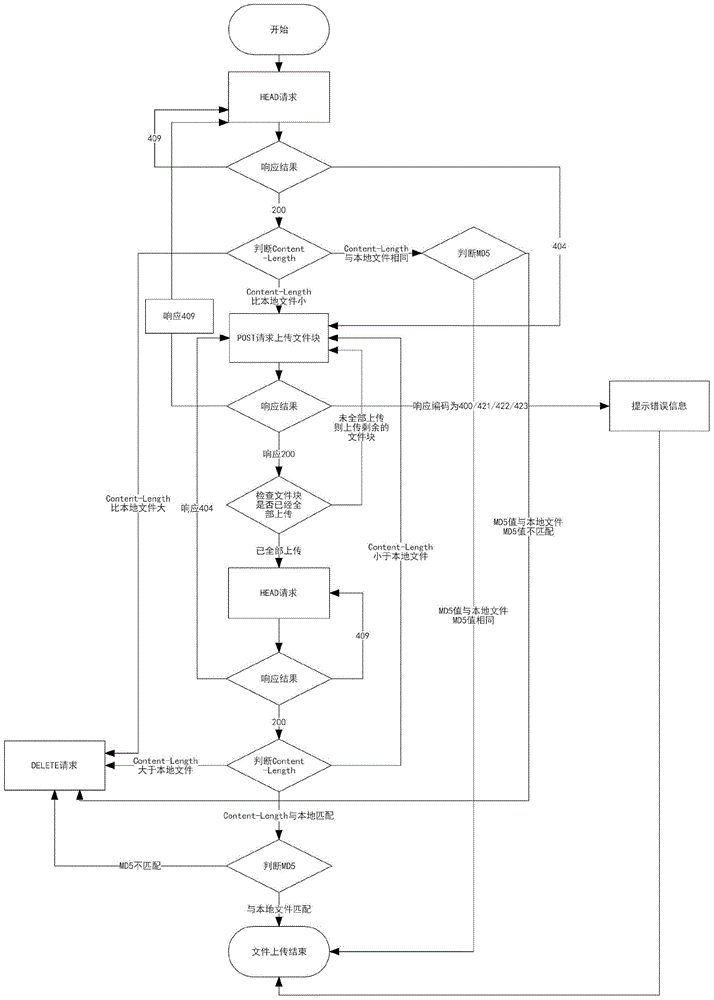
Managing method and system for file transmitting
InactiveCN105007333AImplement segmented transferReduce upload timeTransmissionClient-sideParameter Type
The invention provides a managing method and system for file transmitting. The method comprises following steps. A file managing server receives a file state request first and feeds back a file state response to a client. The client determines the corresponding control strategy of file transmitting based on the types of parameters carried in the corresponding file state response. A managing system for file transmitting is also provided. The system comprises a client, and a file managing server. The client and the file managing server are connected.
Owner:SUZHOU CODYY NETWORK SCI & TECH
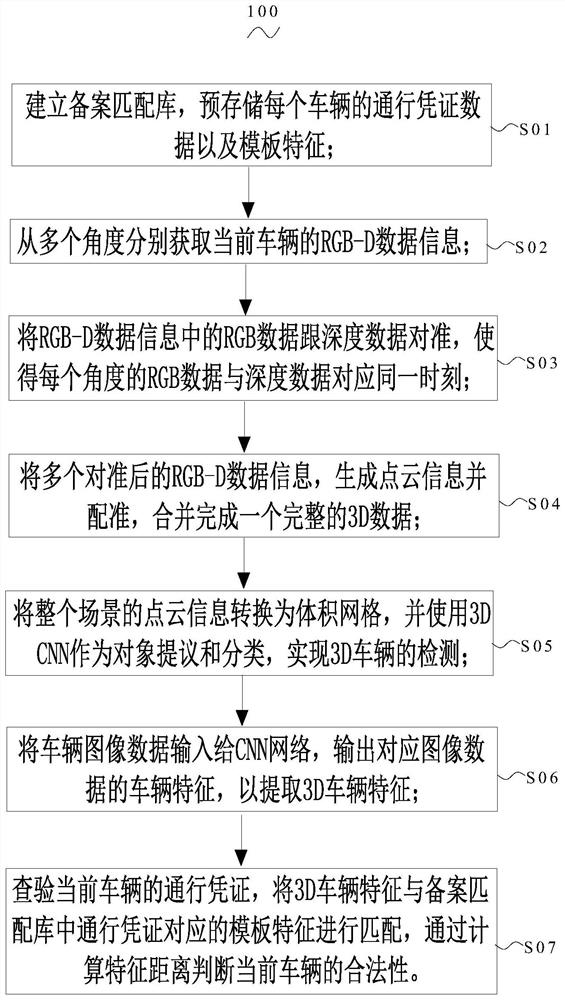
Vehicle panoramic inspection device, system and method
PendingCN113111851APrevent OEMPrevent illegal modificationImage enhancementImage analysisPoint cloudData information
The invention provides a vehicle panoramic inspection device, system and method, and the method comprises the following steps: building a record matching library, and pre-storing the passing voucher data and template features of each vehicle; rGB-D data information of the current vehicle is obtained from multiple angles; checking the passing voucher of the current vehicle, matching the 3D vehicle features with template features corresponding to the passing voucher in a filing matching library, and judging the legality of the current vehicle by calculating a feature distance; according to the vehicle panoramic inspection method, point cloud information is generated through multi-data fusion and registration is carried out to complete vehicle detection and matching, the 3D vehicle identification effect is enhanced, and the accuracy of extraction of 3D vehicle feature identification is improved; by establishing the record matching library, the 3D vehicle features are matched with the template features corresponding to the passing vouchers in the record matching library, so that the vehicle is prevented from being attached to a license plate, fake-licensed and illegally modified, and the legality of the vehicle is ensured.
Owner:SHENZHEN MAXVISION TECH
Ultrasonic data management system and method based on block chain
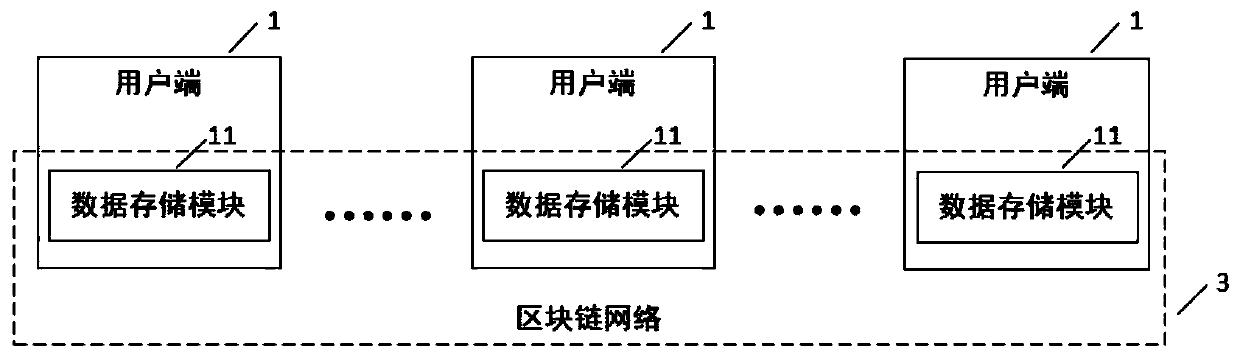
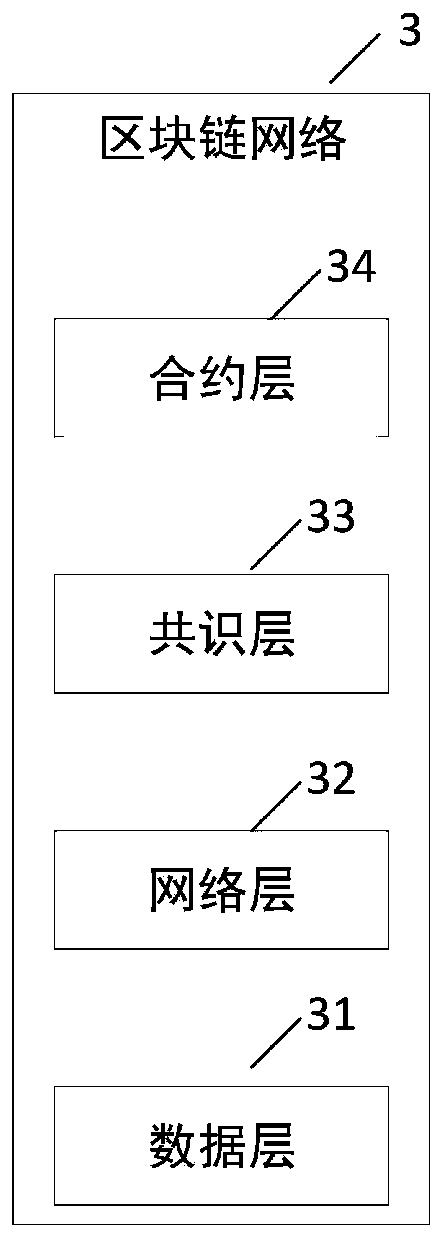
PendingCN111581666APrevent illegal modificationGuaranteed accuracyDigital data protectionData fileEngineering
The invention provides an ultrasonic data management system based on a block chain, and relates to the technical field of data management, the ultrasonic data management system comprises a plurality of user sides and a cloud storage server connected with each user side, each user side comprises a data storage module, and the data storage modules of all the user sides are mutually connected to forma block chain network; the user side processes the ultrasonic data file to obtain an associated ultrasonic identity code and an encryption check code; the ultrasonic data file and the ultrasonic identity code are uploaded to a cloud storage server for storage, and the ultrasonic identity code and the encrypted check code are sent to a block chain network for distributed storage; and data management is performed on the ultrasonic data file stored in the cloud storage server according to the ultrasonic identity code and the encryption check code stored in the blockchain network. The method andsystem have the beneficial effects that illegal modification of the ultrasonic data file stored in the cloud server is effectively prevented, and the accuracy and authority of the ultrasonic data fileare ensured.
Owner:上海深至信息科技有限公司
Cloud storage data modification method
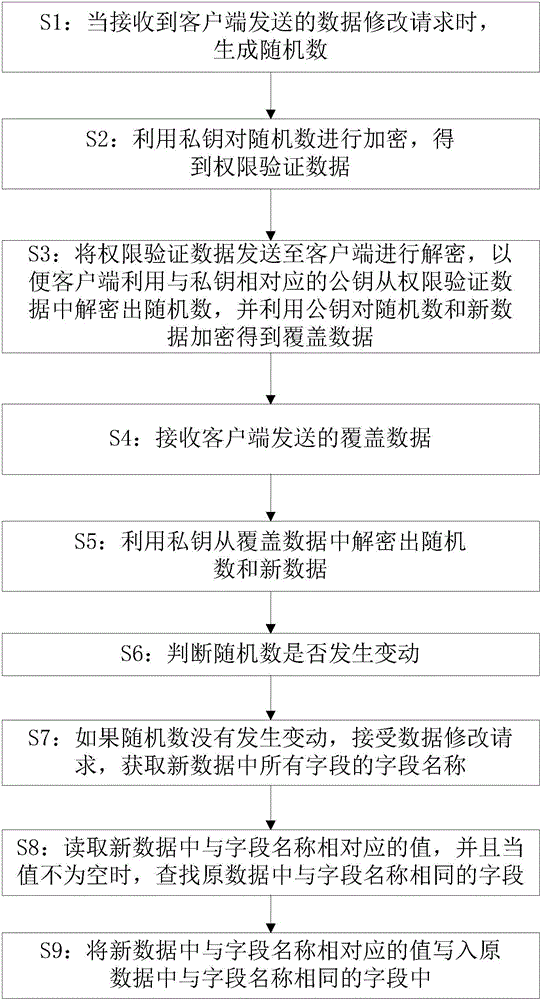
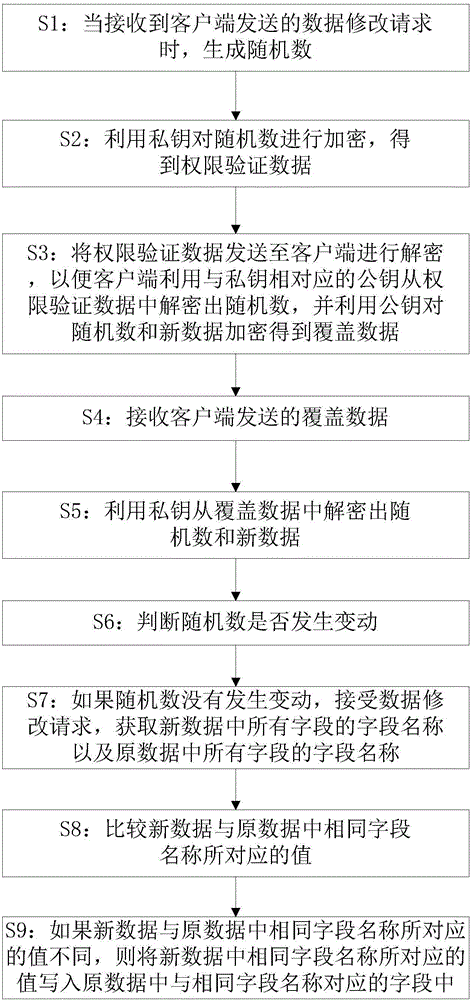
InactiveCN105701421APrevent illegal modificationSmall modificationDigital data protectionTransmissionOriginal dataCloud storage
The present invention provides a cloud disk data modification method, including: when receiving a data modification request sent by a client, generating a random number; using a private key to encrypt the random number to obtain authority verification data; sending the authority verification data to The client decrypts, so that the client uses the public key corresponding to the private key to decrypt the random number from the authority verification data, and uses the public key to encrypt the random number and new data to obtain the coverage data; receive the coverage data sent by the client; Use the private key to decrypt the random number and new data from the covered data; determine whether the random number has changed; if the random number has not changed, obtain the field names of all fields in the new data; read the field names corresponding to the new data value, when the value is not empty, find the field with the same name as the field in the original data; write the value corresponding to the field name in the new data into the field with the same name as the field in the original data. The invention can prevent data from being modified illegally.
Owner:CHENGDU BAOMIHUA INFORMATION TECH
Data security protection method and data security protection device
ActiveCN102236607BGuaranteed reliabilityEnsure safetyUnauthorized memory use protectionInternal/peripheral component protectionComputer memoryMobile phone
The invention relates to a data security protection method and a data security protection device for protecting data security in a computer memory. The method comprises the following steps that: while starting computer equipment, a security module respectively distinguishes and authenticates a user identity and an encryption module, after passing through the distinguishing and the authentication, the security module transmits a data key to the encryption module, in the following use, the encryption module encrypts the memory data for protection, and if the distinguishing and the authentication are not passed, the computer cannot be started. The device comprises the security module and the encryption module, which are arranged in computer equipment, such as a PC host, a PDA, a mobile phone, a PMP or a digital photo frame and the like, and are connected with each other. The method and the device implement the transparent encryption for the memory data of computer equipment and the distinguishing of user identity, and simultaneously, separately store a key and an encryption algorithm, thereby implementing higher security.
Owner:NATIONZ TECH INC
Starting cartridge
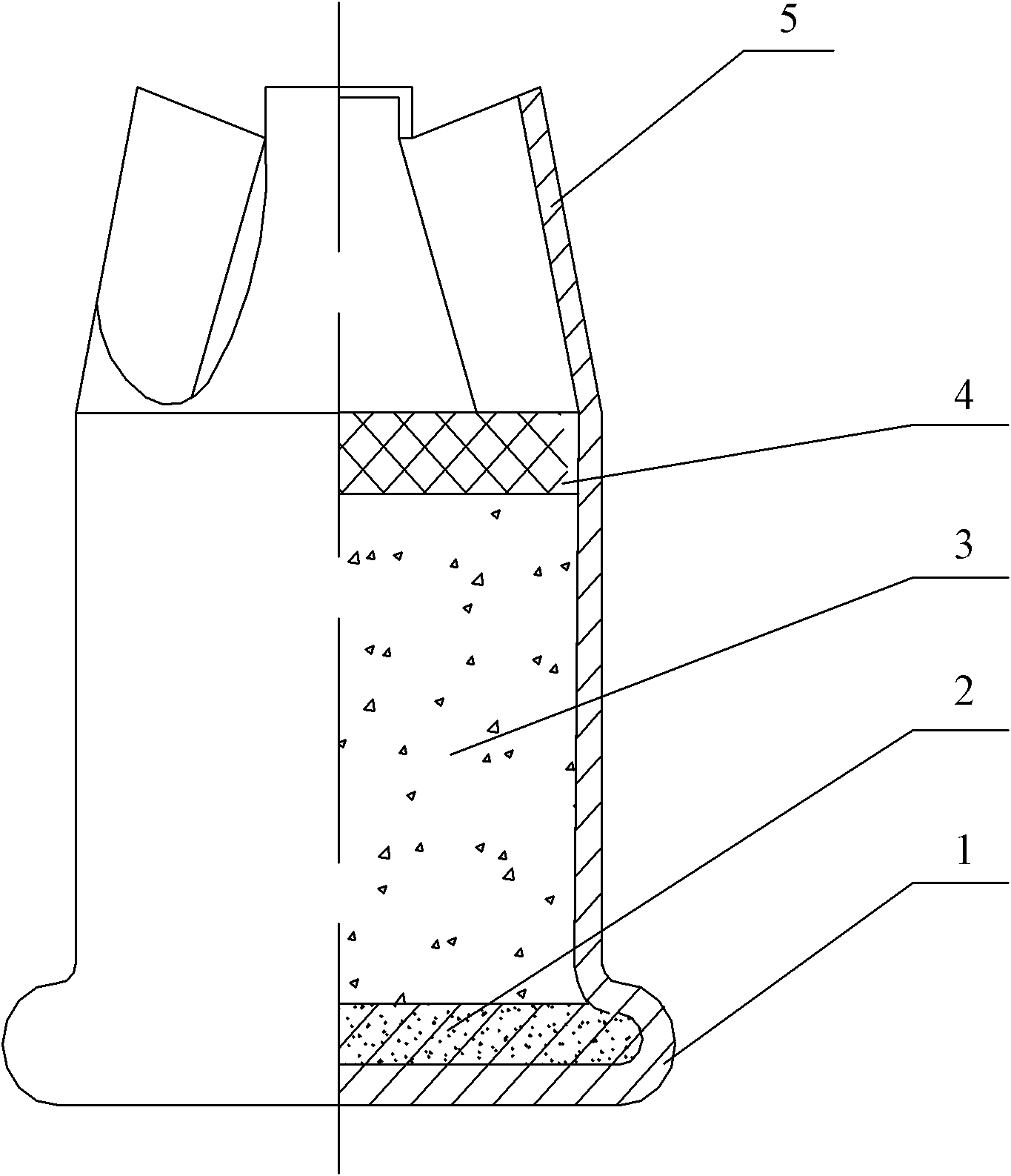
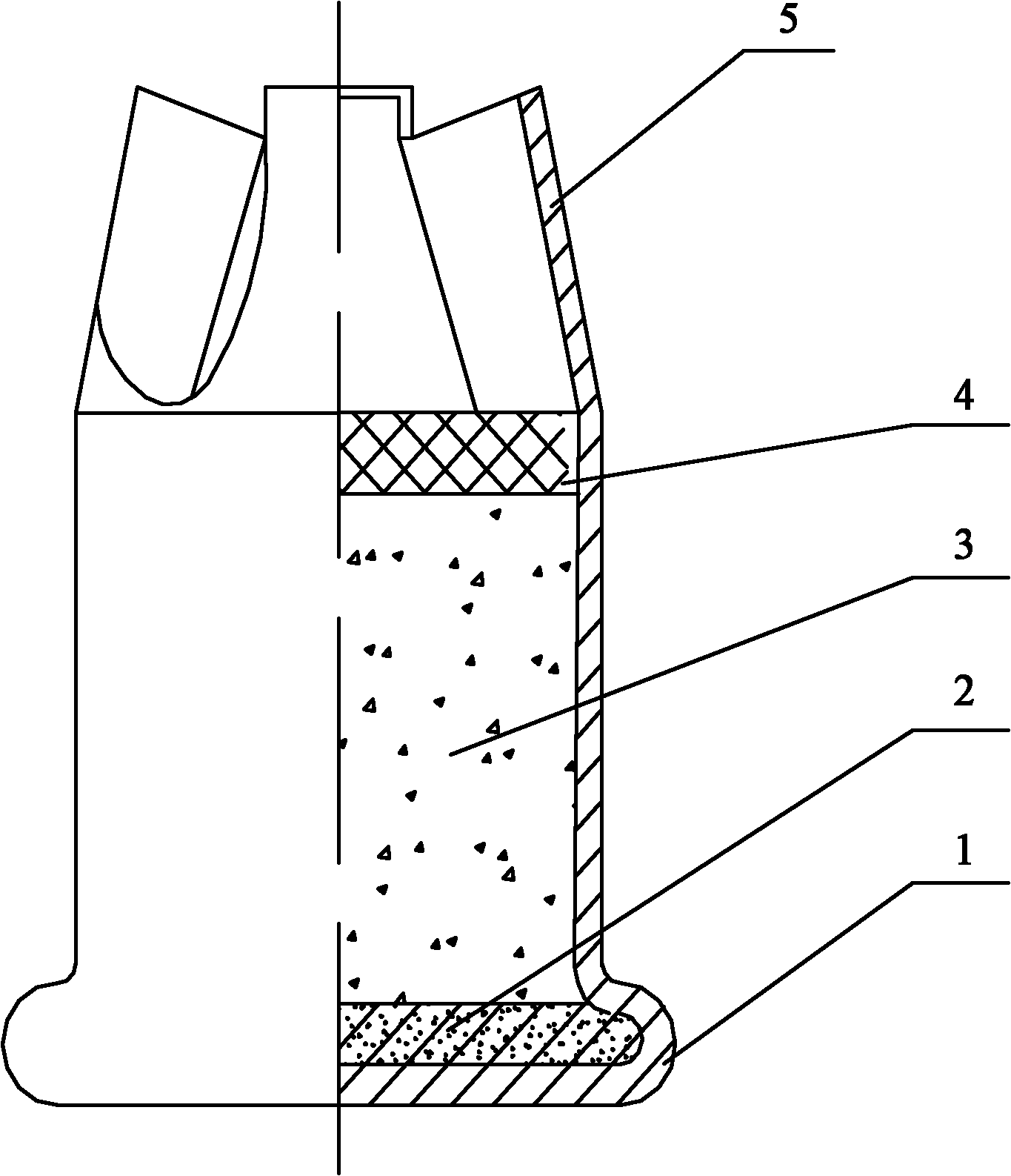
InactiveCN102155881ASmall volumeAvoid modificationAmmunition projectilesProjectilesCombustionSteel ball
The invention discloses a starting cartridge which comprises a cartridge case, a priming composition layer, a smoke agent layer and a sealed paper pad layer, wherein an opening end thereof is closed in a star shape, and the length of the cartridge case is 8-10 mm; the priming composition layer is paved on an inner cavity bottom of the cartridge case; the smoke agent layer is paved on the priming composition layer; and the sealed paper pad layer is arranged on the smoke agent layer, wherein the sealed paper pad layer is adhered on the cartridge case. Since an opening part is closed in the star shape by substituting the original round shape, the inner diameter of the opening part can be 2 mm less than that of the common starting cartridge so as to effectively prevent the reforming of the starting cartridge caused by loadings such as steel balls and the like. The length of the cartridge case is designed as 8-10 mm, which is only 2 / 3 of the normal starting cartridge; the cartridge case is short so that the volume of the powder chamber is small and the loading dosage of the smoke agent is limited. On the one hand, the illegally changed starting cartridge against society can be prevented; on the other hand, the closed opening is in favor of the full combustion of the smoke agent after the starting cartridge is fired, so that the sound and smog can achieve a regulated index requirement when the volume of the powder chamber is small and the loading dosage of the powder is limited.
Owner:重庆长江电工工业集团有限公司
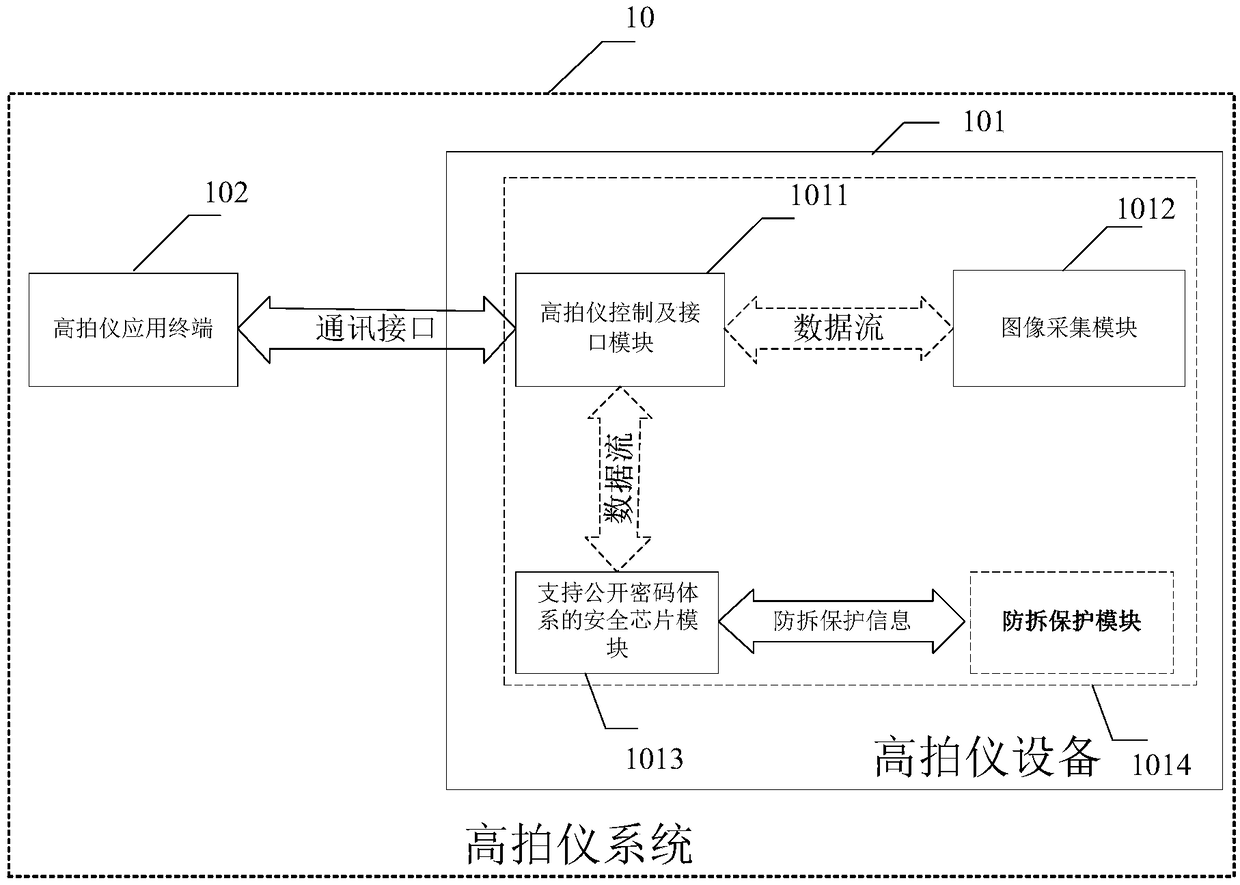
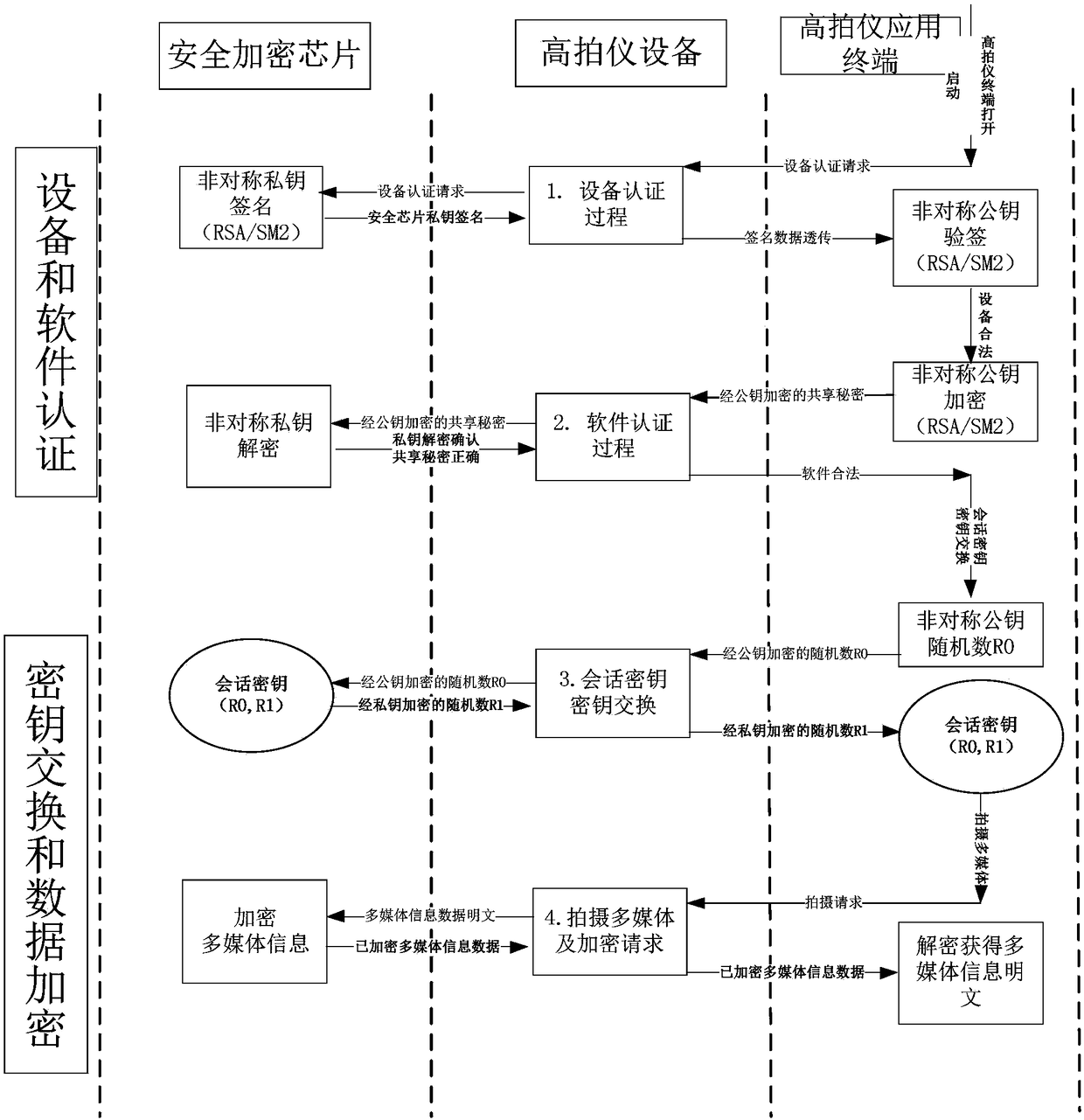
High-speed photographic apparatus system with identity authentication, data encryption and tamper protection functions
InactiveCN108063882AMeet the needs of electronic functionsIntegrity guaranteedPublic key for secure communicationUser identity/authority verificationKey exchangeComputer module
The invention discloses a high-speed photographic apparatus system with identity authentication, data encryption and tamper protection functions. The system at least comprises a high-speed photographic apparatus application terminal, a high-speed photographic apparatus control and interface module, a multimedia information acquisition module, a safety chip module supporting a public key system anda tamper protection module, wherein the high-speed photographic apparatus application terminal and the high-speed photographic apparatus control and interface module are connected by a communicationinterface; the high-speed photographic apparatus control and interface module communicates with the multimedia information acquisition module; the safety chip module supporting the public key system is connected with the high-speed photographic apparatus control and interface module to complete operations of encryption, decryption, signature, signature verification, key exchange and the like; thetamper protection module carries out safety integrity protection of equipment on the high-speed photographic apparatus control and interface module, the multimedia information acquisition module and the safety chip module supporting the public key system.
Owner:SHENZHEN JULINGSHEN TECH CO LTD
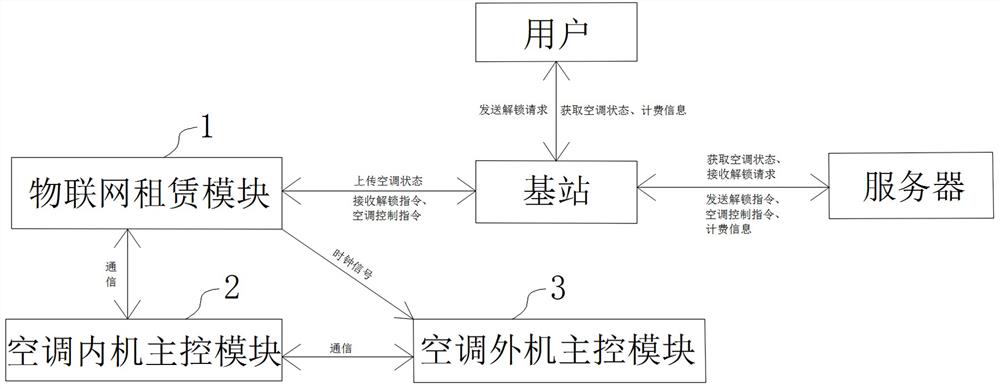
Control device and method for leasing air conditioner and air conditioner
ActiveCN112268351AControl operationsReal-time monitoring of operating conditionsMechanical apparatusSpace heating and ventilation safety systemsThe InternetMechanical engineering
The invention provides a control device and method for leasing an air conditioner and the air conditioner. The control device for leasing the air conditioner comprises an Internet of Things leasing module, an air conditioner indoor unit main control module and an air conditioner outdoor unit main control module, wherein the Internet of Things leasing module is in wireless communication connectionwith a server and a user through a base station; and the air conditioner indoor unit main control module is electrically connected with the Internet of things leasing module and the air conditioner outdoor unit main control module. According to the control device and method, the Internet of things leasing module is additionally arranged on the air conditioner, and interacts with the server and theuser through the base station, so that the functions of locking, unlocking, leasing and returning the air conditioner on line are achieved; meanwhile, a leasing air conditioner operator can achieve the administrator function on the background through the server, and the current regional air conditioner operation condition is monitored and controlled in real time; and moreover, an air conditioneroutdoor unit carries out anti-cracking verification by receiving two paths of verification signals of the Internet of Things leasing module and an air conditioner indoor unit, the air conditioner is locked when two continuous verification fails, and the user is prevented from carrying out illegal modification.
Owner:GREE ELECTRIC APPLIANCES INC
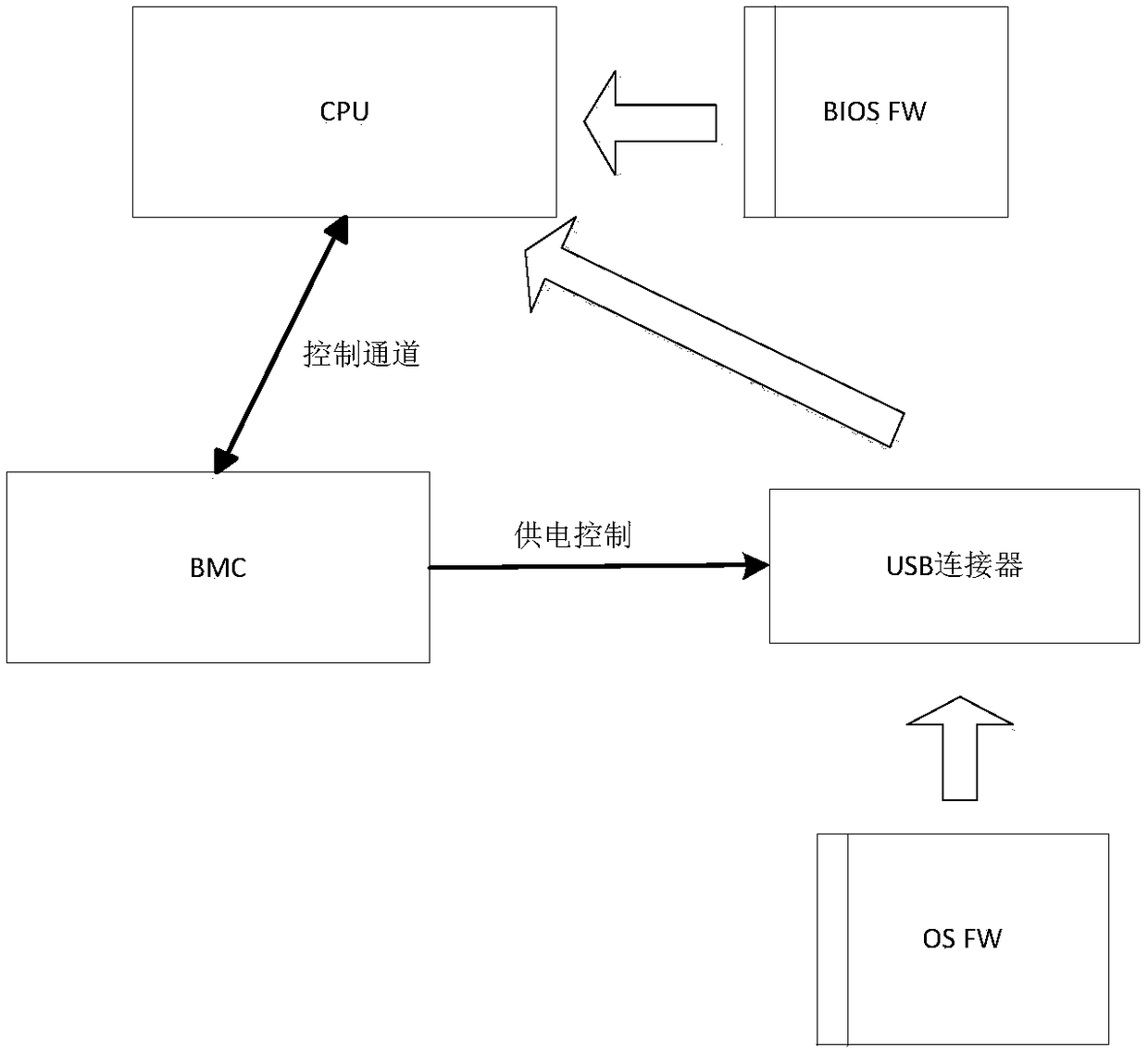
A method to prevent users from modifying os illegally
ActiveCN105160258BAvoid accessPrevent illegal modificationPlatform integrity maintainanceElectricityBIOS
Owner:SUZHOU ZOOM SERVER INC
Virtualization of execution environment, method and device for accessing virtual execution environment
ActiveCN107038128BPrevent illegal modificationEnsure data securityMemory architecture accessing/allocationUnauthorized memory use protectionVirtualizationAccess method
Owner:HUAWEI TECH CO LTD
A campus intelligent security system and working method
ActiveCN110047182BReduce workloadAvoid forgettingIndividual entry/exit registersEngineeringMobile phone
Owner:李悦同
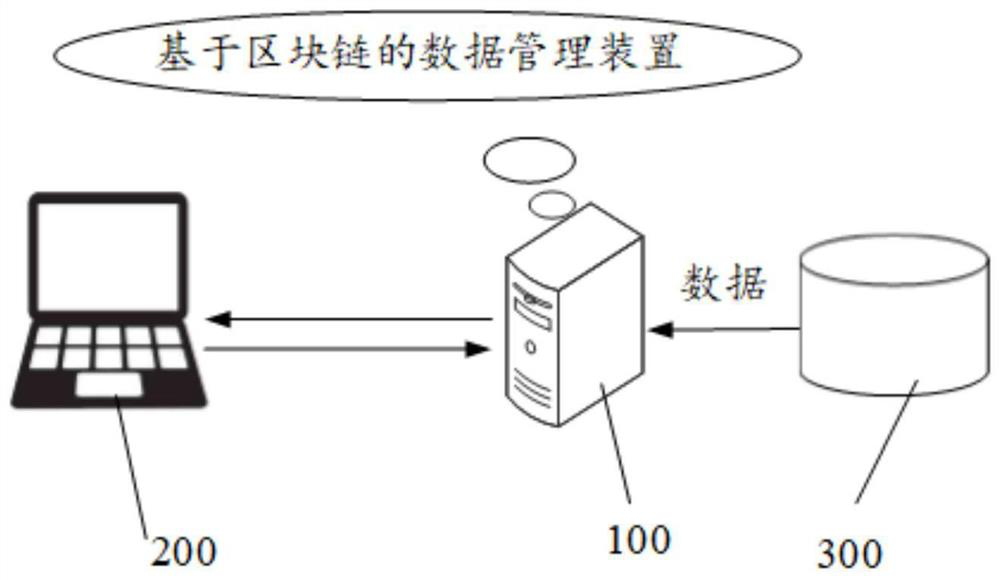
Data management method, device and system based on block chain, equipment and medium
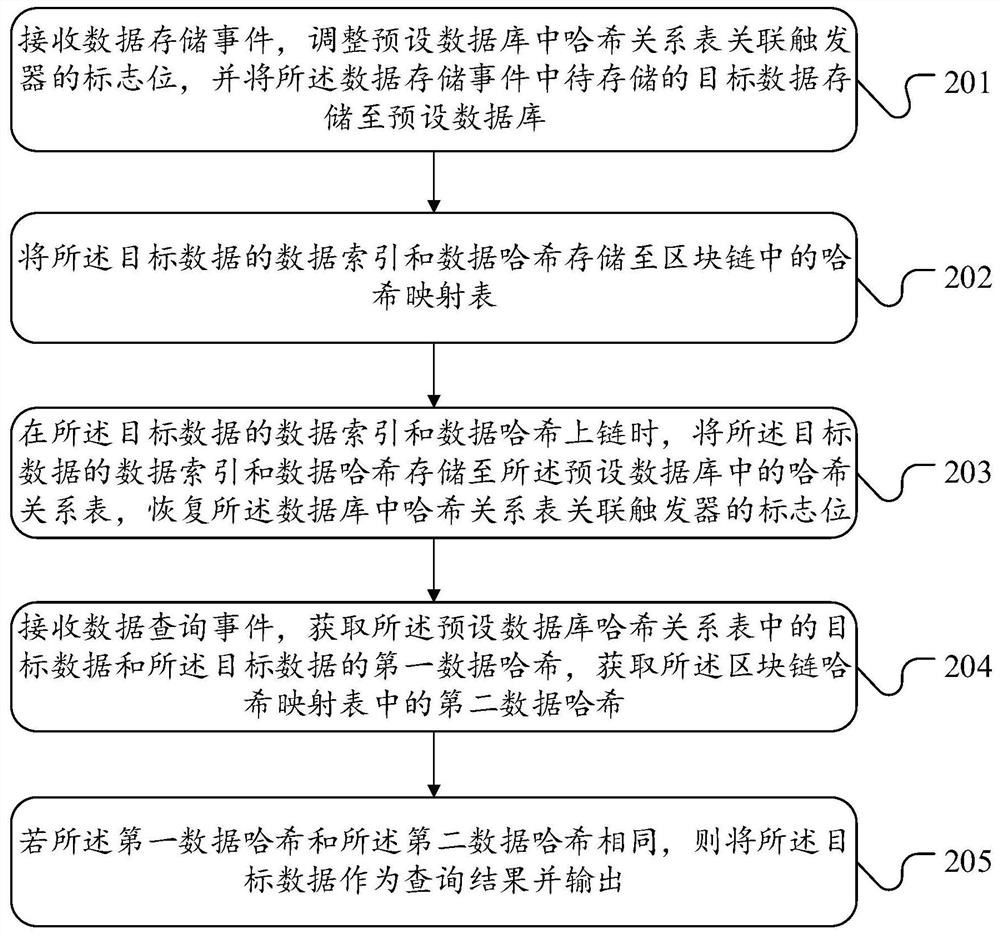
ActiveCN112835906AEnsure data securityReasonable data managementDatabase updatingDigital data protectionData queryRelational table
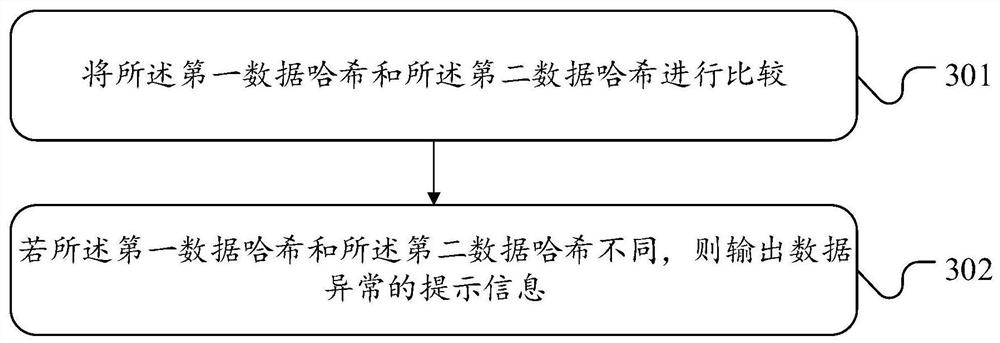
The embodiment of the invention provides a data management method, device and system based on a block chain, equipment and a medium. The method comprises the following steps: receiving a data storage event, adjusting a flag bit of a hash relationship table association trigger in a preset database, and storing target data to be stored in the data storage event to the preset database; storing the data index and the data hash of the target data to a hash mapping table in a block chain and the hash relationship table in the preset database, and recovering the flag bit of the hash relationship table association trigger in the preset database; receiving a data query event, obtaining target data in the preset database hash relationship table and first data hash of the target data, and obtaining second data hash in the hash mapping table in the block chain; if the first data hash is the same as the second data hash, taking the target data as a query result and outputting the query result. According to the method, the data query efficiency and the data security are ensured.
Owner:HANGZHOU QULIAN TECH CO LTD
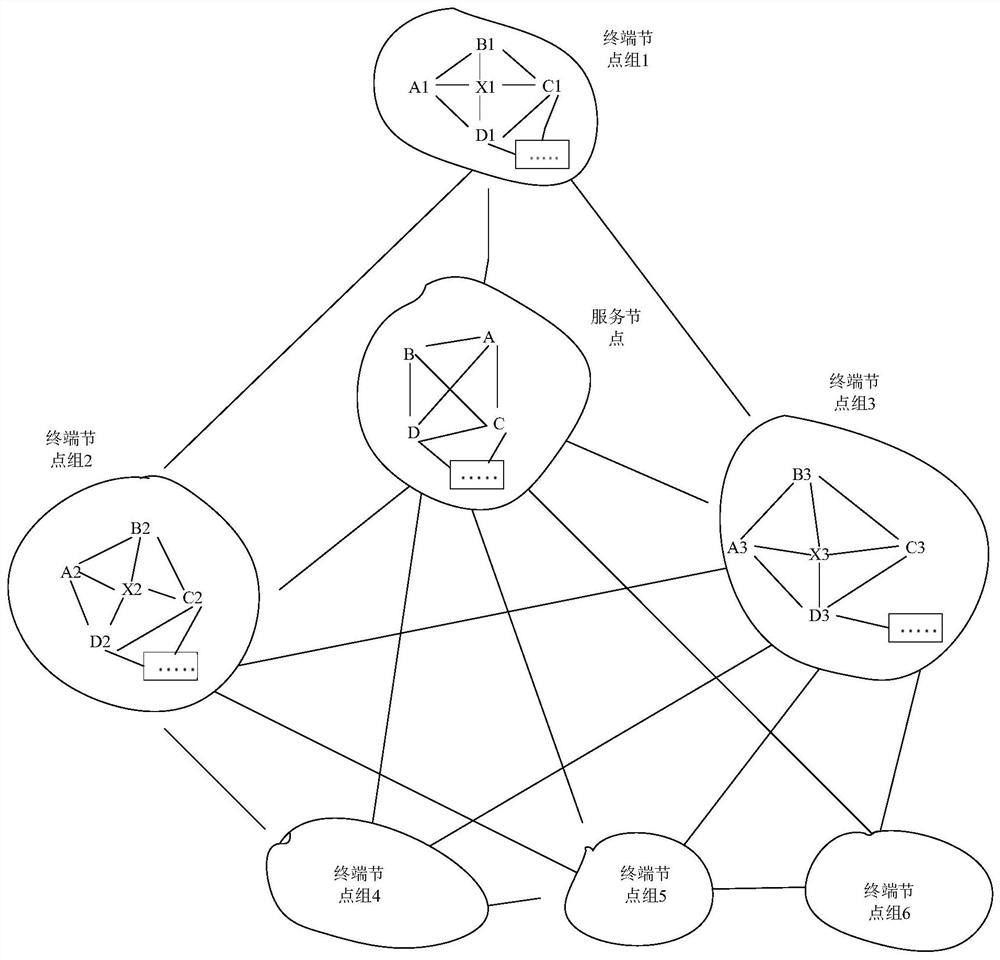
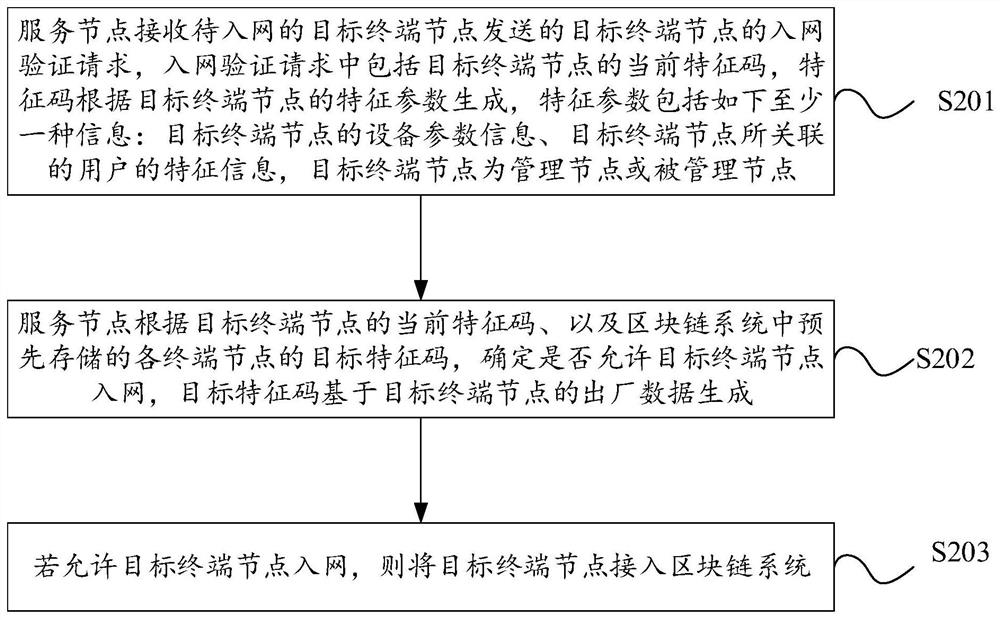
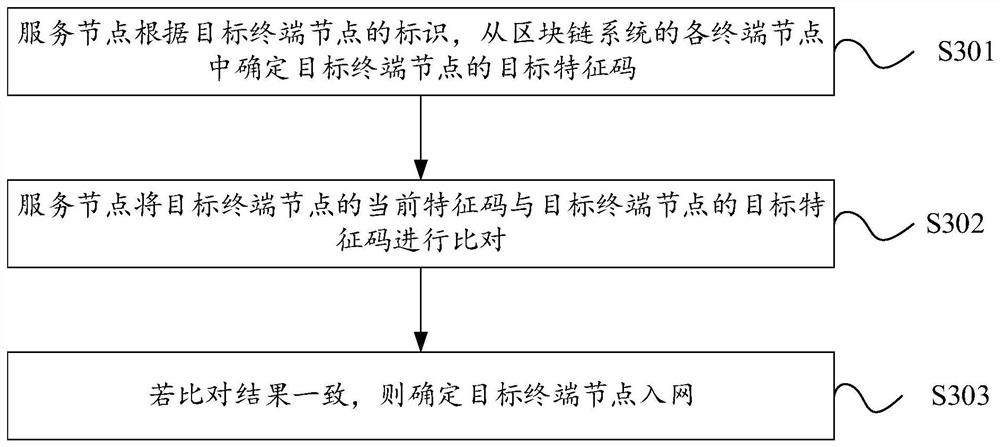
Terminal equipment network access method and device of block chain, server and storage medium
ActiveCN112491893AImprove securityImprove reliabilityDigital data protectionTransmissionTerminal equipmentInformation security
The invention provides a terminal equipment network access method and device of a block chain, a server and a storage medium, and relates to the technical field of information security. The method comprises the steps that a service node receives a network access verification request of a target terminal node sent by the target terminal node to be accessed to the network, the network access verification request comprises a current feature code of the target terminal node, and the feature code is generated according to a feature parameter of the target terminal node; the service node determineswhether to allow the target terminal node to access the network or not according to the current feature code of the target terminal node and a target feature code of each terminal node pre-stored in the blockchain system, and the target feature code is generated based on factory data of the target terminal node; and if the target terminal node is allowed to access the network, the target terminalnode is accessed to the blockchain system. According to the method, the target terminal node can be effectively prevented from being illegally modified or illegally used, and the authority of verification is improved, so that the security and reliability of the blockchain system can be effectively guaranteed.
Owner:秦丽霞
Intermediate node-based data transmission method, system and device, and storage medium
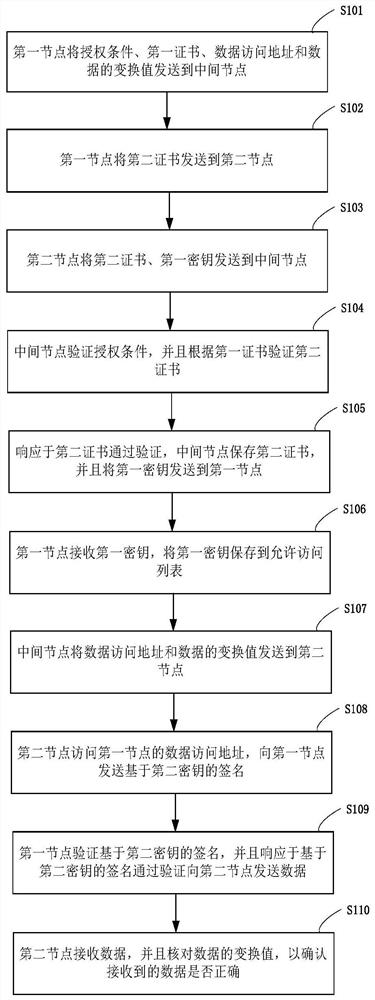
ActiveCN112333175ATransmission process securityPrevent leakageUser identity/authority verificationData accessEngineering
The embodiment of the invention provides an intermediate node-based data transmission method, system and device, and a storage medium. The data transmission method comprises the following steps: a first node sends an authorization condition, a first certificate, a data access address and a conversion value of data to an intermediate node; the first node sends a second certificate to a second node;the second node sends the second certificate and a first secret key to the intermediate node; the intermediate node verifies the authorization condition and verifies the second certificate accordingto the first certificate; in response to the second certificate passing the verification, the intermediate node saves the second certificate and sends the first key to the first node; the first node receives the first secret key and stores the first secret key in an access permission list; and the intermediate node sends the data access address and the conversion value of the data to the second node. Therefore, the data transmission process is ensured to be safe and reliable.
Owner:HEFEI DAPPWORKS TECH CO LTD
Auxiliary data cross-network convergence method and system based on block chain technology
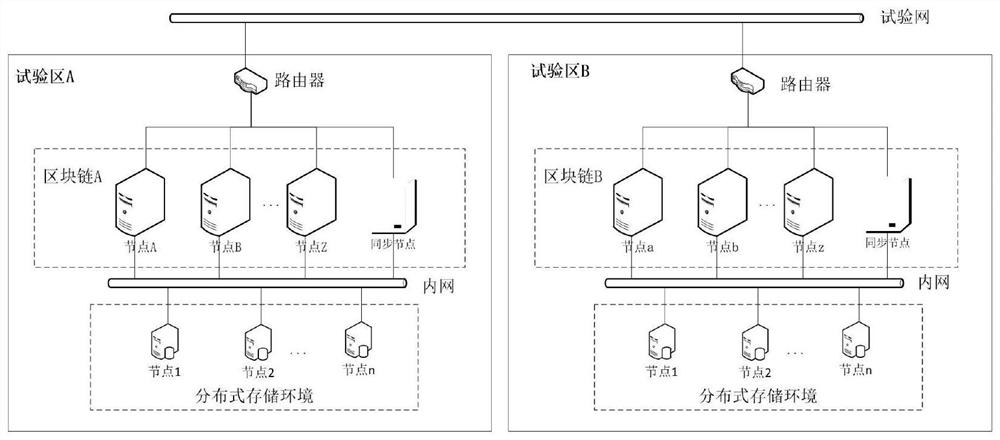
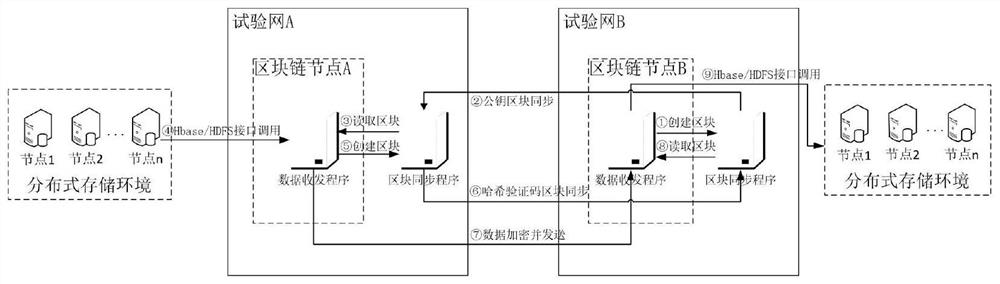
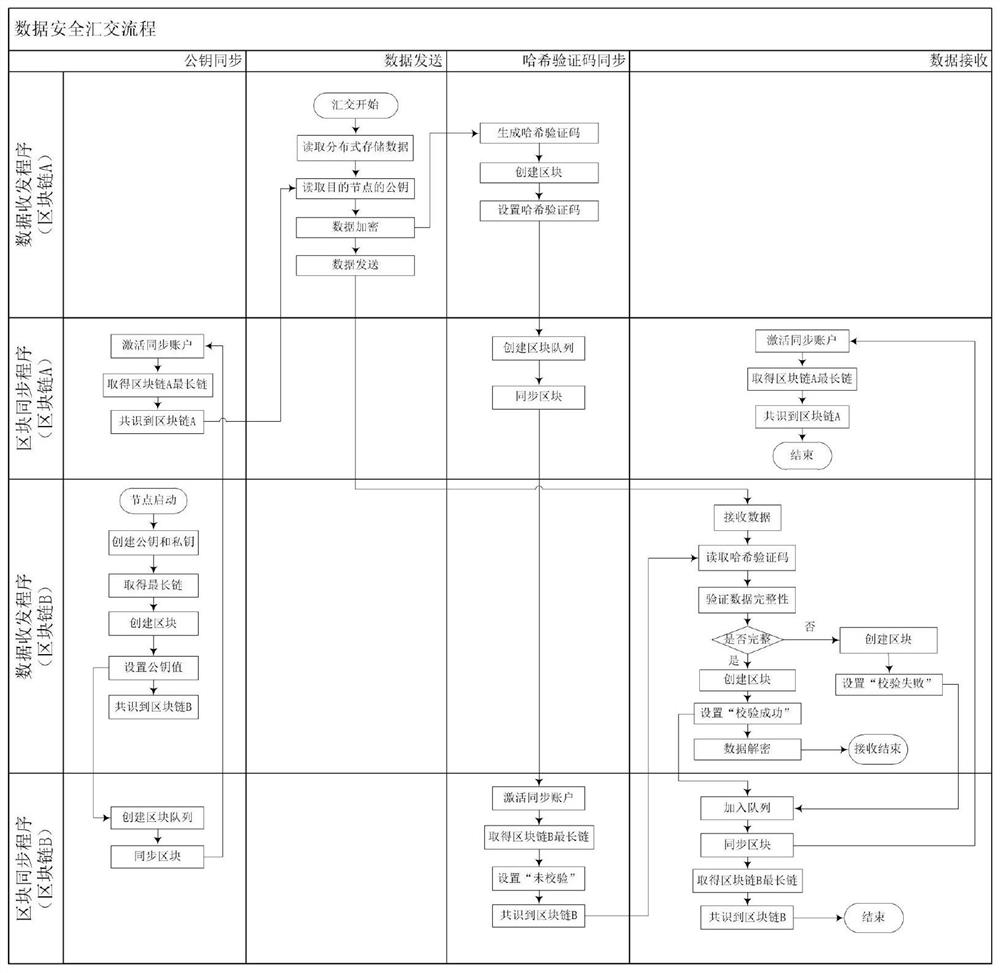
ActiveCN111797161AAccess does not affectPrevent illegal modificationDatabase management systemsEncryption apparatus with shift registers/memoriesNetwork ConvergenceEngineering
The invention provides an auxiliary data cross-network convergence method and system based on a block chain technology. The method comprises the following steps of a data distributed storage and calling step, reading and writing distributed management structured data and unstructured data according to HBase and HDFS components, a data security confluence step, encrypting the data by using an asymmetric encryption algorithm, a block chain operation and synchronization step, performing cross-network synchronization of the data by using the block chain, and a cross-network data transmission step,configuring a route for opening a specified port, and carrying out TCP / IP communication. The method is advantaged in that data transmission is not interrupted, data cannot be stolen, the data is complete and not lost, and cross-network transmission is convenient and safe.
Owner:中国人民解放军92493部队参谋部 +1
Cloud data modification method
InactiveCN105812361APrevent illegal modificationSmall modificationTransmissionOriginal dataCloud data
The invention provides a cloud data modification method, comprising: generating a random number when receiving a data modification request sent by a client; encrypting the random number with a private key to obtain authority verification data; sending the authority verification data to the client The terminal decrypts, so that the client uses the public key corresponding to the private key to decrypt the random number from the authority verification data, and uses the public key to encrypt the random number and new data to obtain the coverage data; receive the coverage data sent by the client; use The private key decrypts the random number and new data from the covered data; judges whether the random number has changed; if the random number has not changed, obtains the field names of all fields in the new data and the original data; compares the new data with the same fields in the original data The value corresponding to the name; if the value is different, the value corresponding to the same field name in the new data is written to the field corresponding to the same field name in the original data. The invention can prevent data from being modified illegally.
Owner:CHENGDU BAOMIHUA INFORMATION TECH
A method and system for processing domain name credit based on blockchain
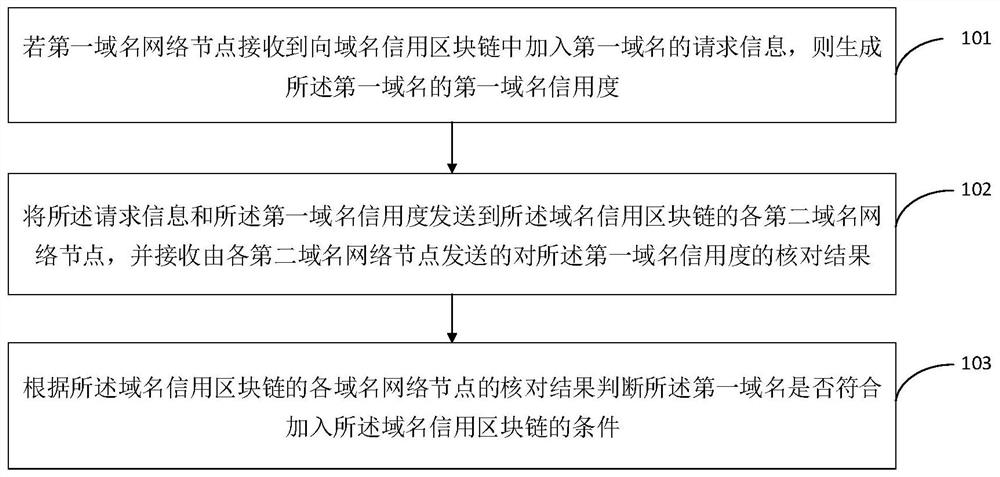
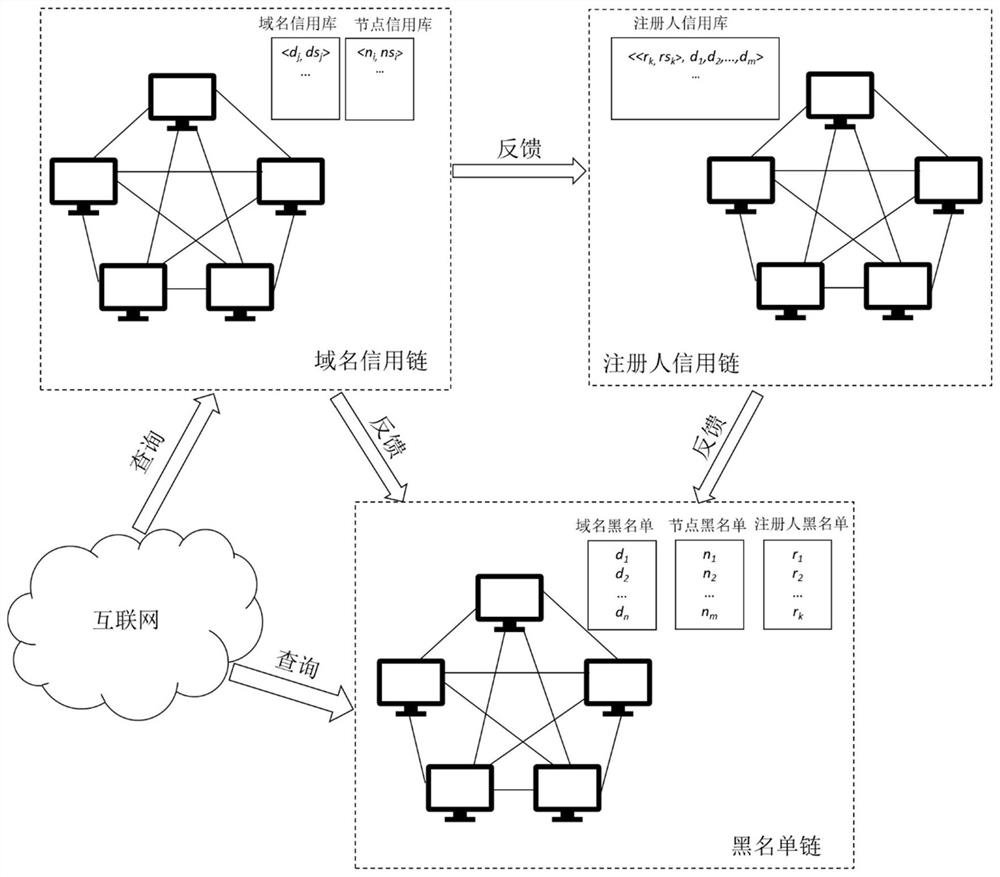
ActiveCN109905388BPrevent illegal modificationAvoid management influenceTransmissionDomain nameComputer network
Embodiments of the present invention provide a blockchain-based domain name credit processing method and system, which maintains the credit of each domain name through the domain name credit blockchain, and avoids illegal modification of the domain name credit. When adding a new first domain name to the domain name credit blockchain, each domain name network node in the domain name credit blockchain needs to check the first domain name credit of the first domain name, and the first domain name can be added to the domain name credit after the verification is passed blockchain. The domain name credit is checked through the decentralized method of the blockchain, which avoids the impact of the failure of a single network node on domain name management, and improves the reliability and authority of the domain name credit in the blockchain. The domain name credit maintained by the domain name credit blockchain can realize the rapid judgment of illegal abuse of domain names, which is conducive to maintaining a healthy network environment.
Owner:CHINA INTERNET NETWORK INFORMATION CENTER
Smart community property service system
InactiveCN112365371ARealize information managementPrevent illegal modificationData processing applicationsDigital data authenticationInformatizationOperational system
The invention relates to the technical field of community property service, and discloses a smart community property service system, which comprises a smart phone SPUi operating community property service system client software and carried by a community user, a smart phone SPSi carried by a community property service grid member, and a cloud computing server CCSSCPS operating the community property service system server software and deployed in a smart community network center, wherein an operation authority authentication module is installed and operates on an operating system of the cloud computing server CCSCS, carries out operation authority authentication on all operation users modifying community property service data in the cloud computing server CCSSCPS, and only when proving thatthe operation users have valid operation authority, allows the community property service data to be modified. According to the system, the technical problem that community property service data is likelty to be invalidly modified by unauthorized users while community property service informatization is realized is solved.
Owner:范丽红
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com