Digital evidence obtaining system based on Linux environment
An environmental and digital technology, applied in transmission systems, electronic digital data processing, instruments, etc., can solve the problems of ineffective forensics work, lagging of forensics work, loss of effective evidence, etc., to facilitate traceability analysis and attack path reproduction, Reduced workload, friendly interface effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0031] The present invention is described in further detail now in conjunction with accompanying drawing.
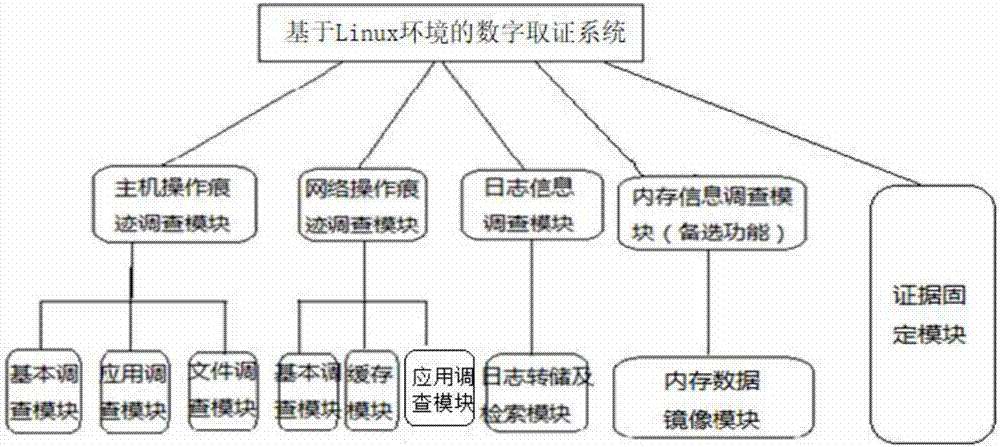
[0032] Such as figure 1 As shown, the digital forensics system based on the Linux environment proposed by the present invention includes a host operation trace investigation module, a network operation trace investigation module, a log information investigation module, a memory information investigation module and an evidence fixation module.
[0033] The host operation trace investigation module is mainly used to extract the basic information and operation records of the system. By providing this information to forensic investigators and analysts, it can not only enable the forensic investigators to establish a "safety baseline" for the system based on their own experience, but also provide some sensitive information. Abnormal information, such as: whether it contains illegal users, unrecommended operations and access, etc. Specifically, this module provides the follow...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com