Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
47 results about "Digital forensics" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Digital forensics (sometimes known as digital forensic science) is a branch of forensic science encompassing the recovery and investigation of material found in digital devices, often in relation to computer crime. The term digital forensics was originally used as a synonym for computer forensics but has expanded to cover investigation of all devices capable of storing digital data. With roots in the personal computing revolution of the late 1970s and early 1980s, the discipline evolved in a haphazard manner during the 1990s, and it was not until the early 21st century that national policies emerged.
Improvements in or relating to digital forensics
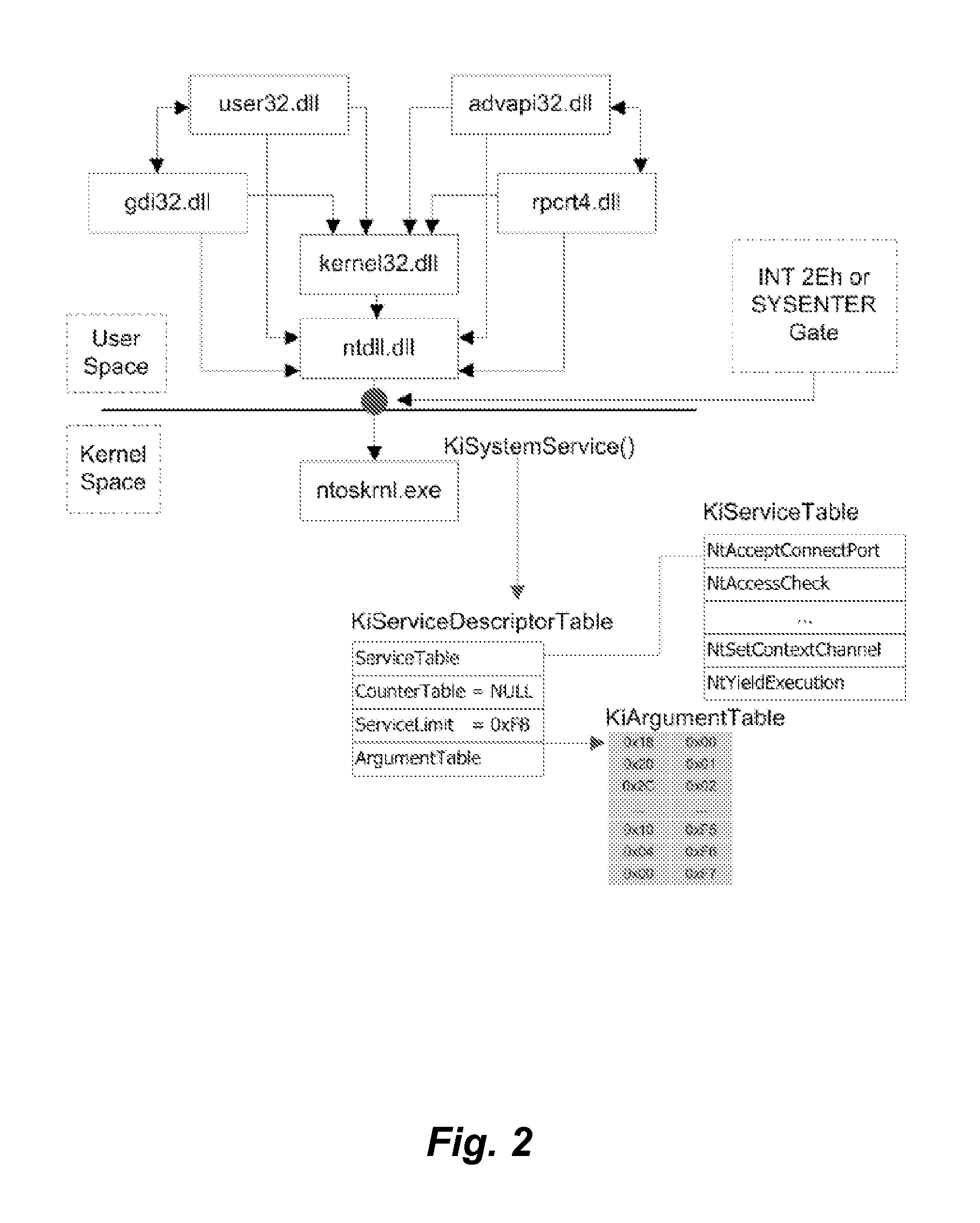
ActiveUS20120011153A1Quick identificationEasy translationDigital data processing detailsPlatform integrity maintainanceSystem callComputer science
New digital forensic techniques and systems are disclosed. System call information is collected from a device under test (DUT) and converted to a sequence format. Thereafter, sequence alignment methods and tools can be used to investigate and identify patterns of behaviour that are suspicious.
Owner:FORTINET
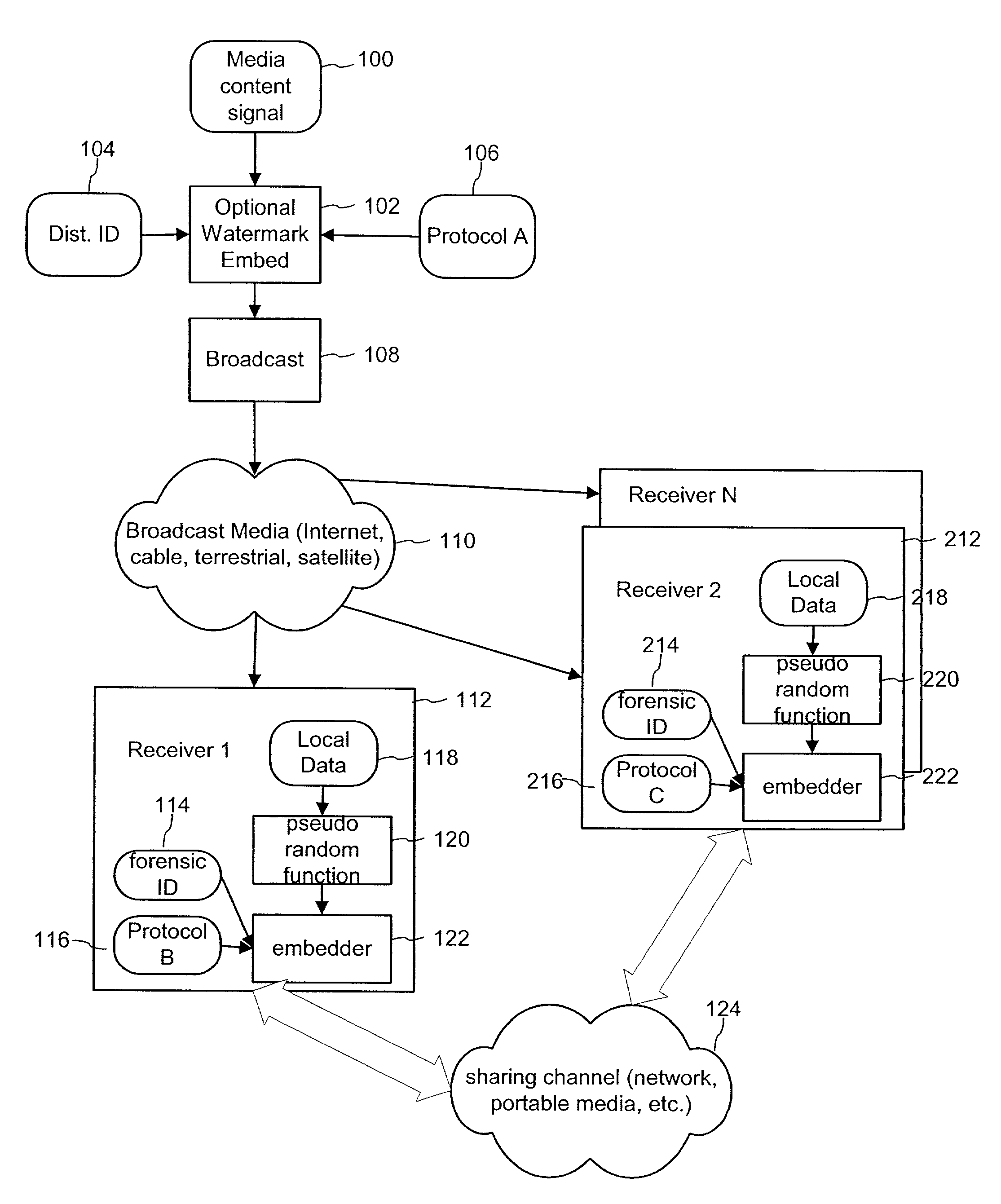
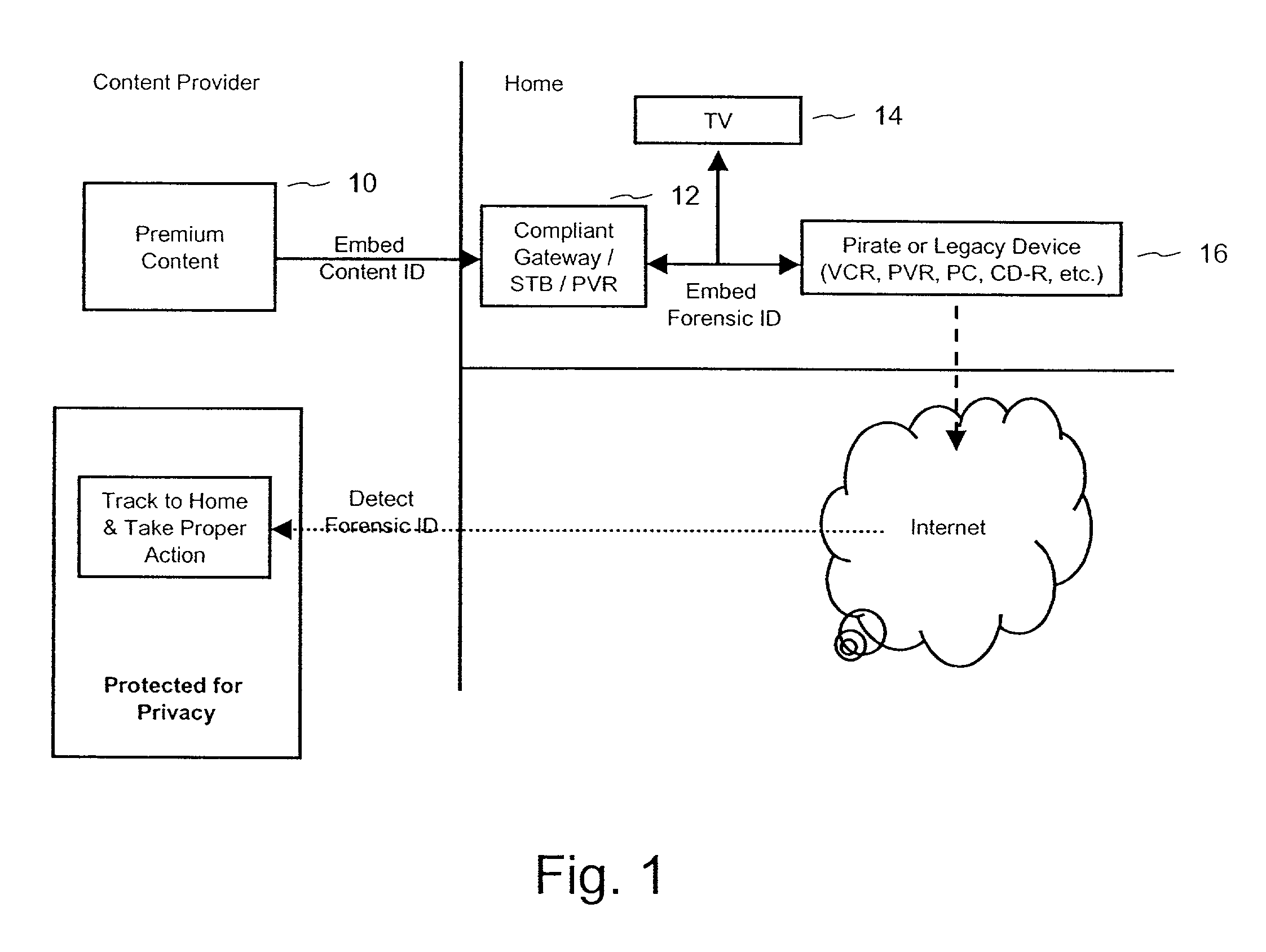
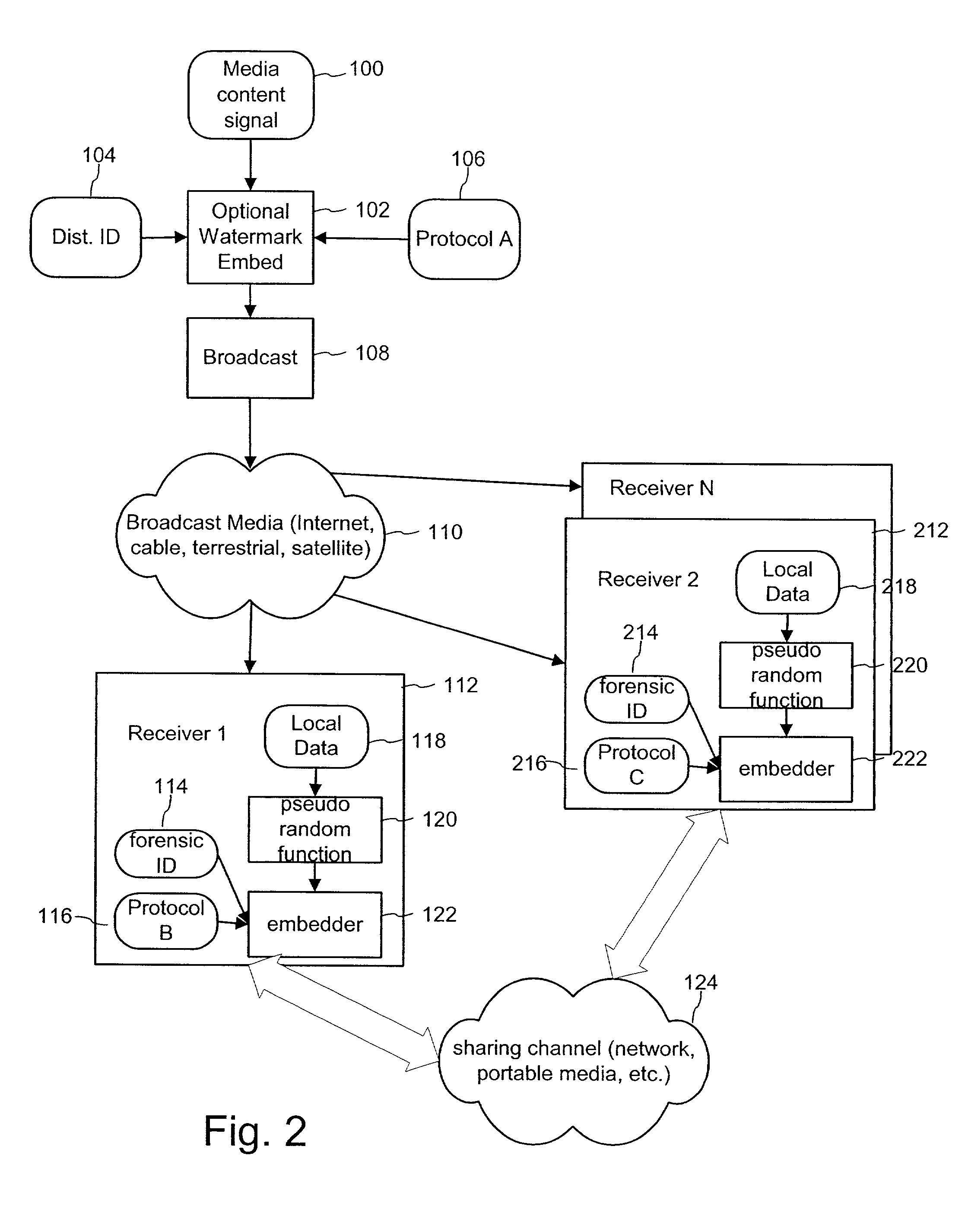
Forensic digital watermarking with variable orientation and protocols
ActiveUS7392392B2Improve the immunityAccurate detectionTelevision system detailsUser identity/authority verificationDigital watermarkingDigital forensics
The invention provides a method of forensic digital watermarking that randomly selects an orientation and / or embedding protocol for a forensic digital watermark signal to be embedded in the content signal. It then embeds the forensic digital watermark signal at the selected orientation in the content signal. The embedding applies a different orientation to the digital forensic watermark for each instance of embedding a forensic watermark. This thwarts averaging and over-embedding attacks and enables generational forensic tracking.
Owner:DIGIMARC CORP (FORMERLY DMRC CORP)
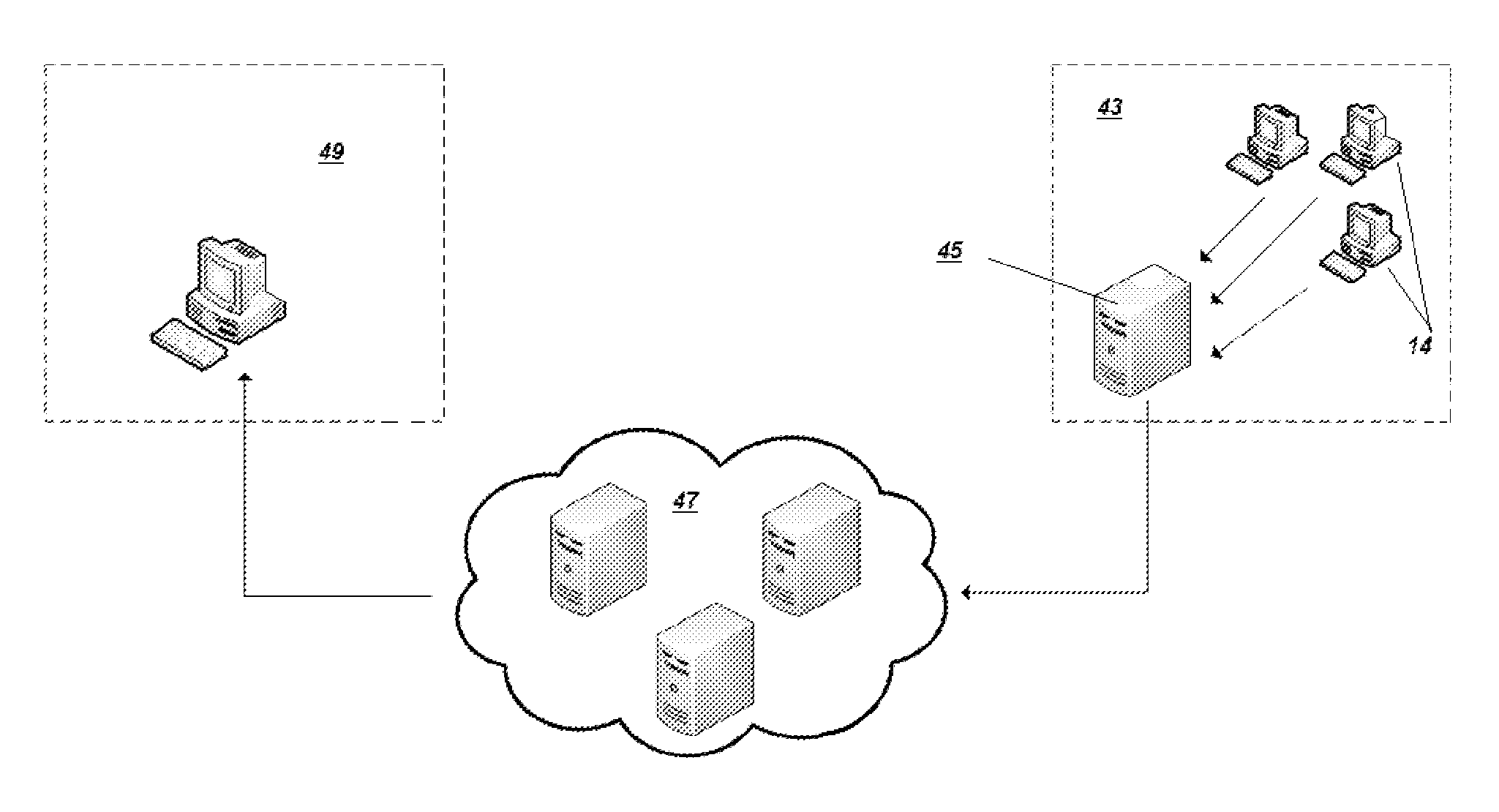
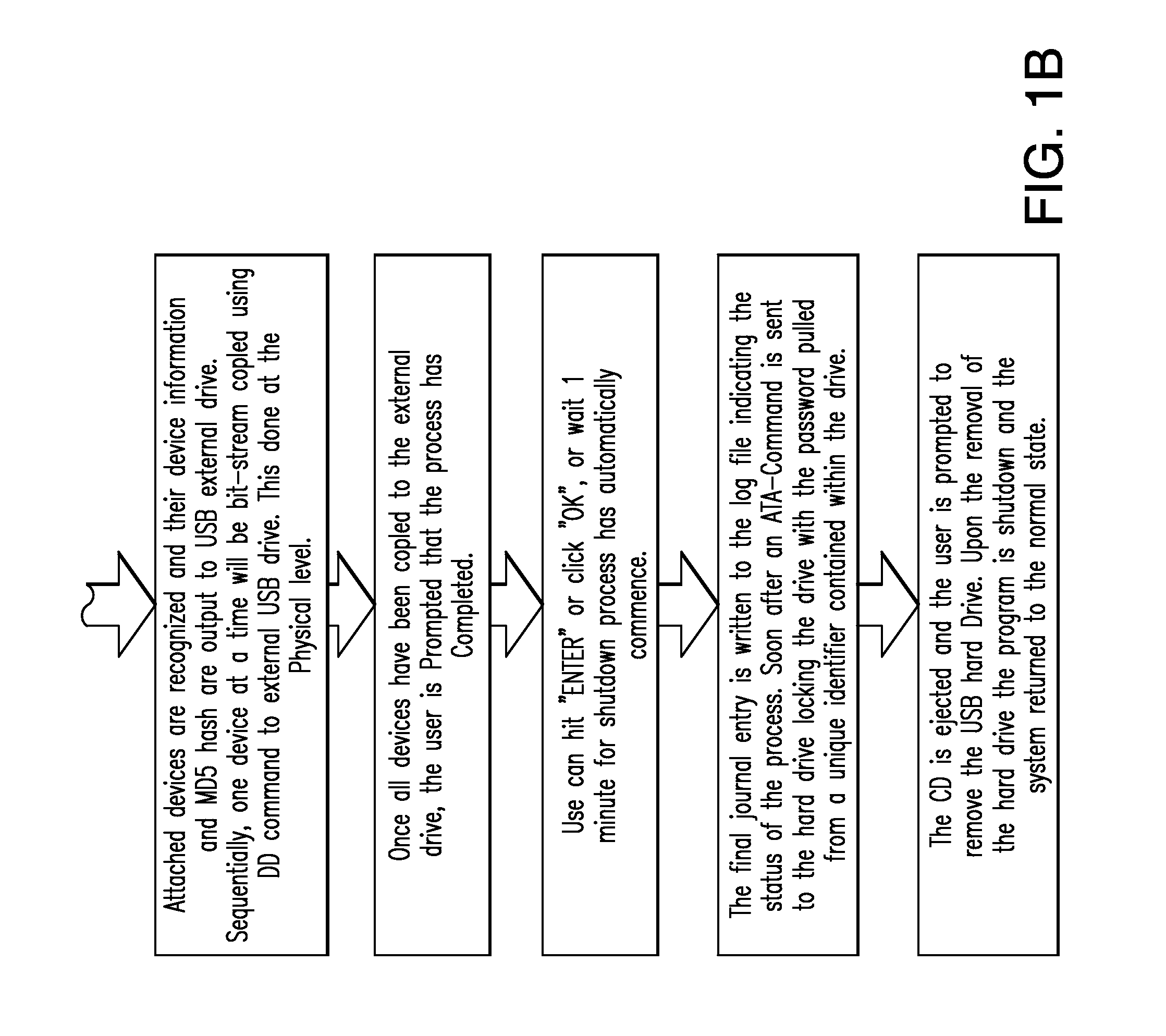
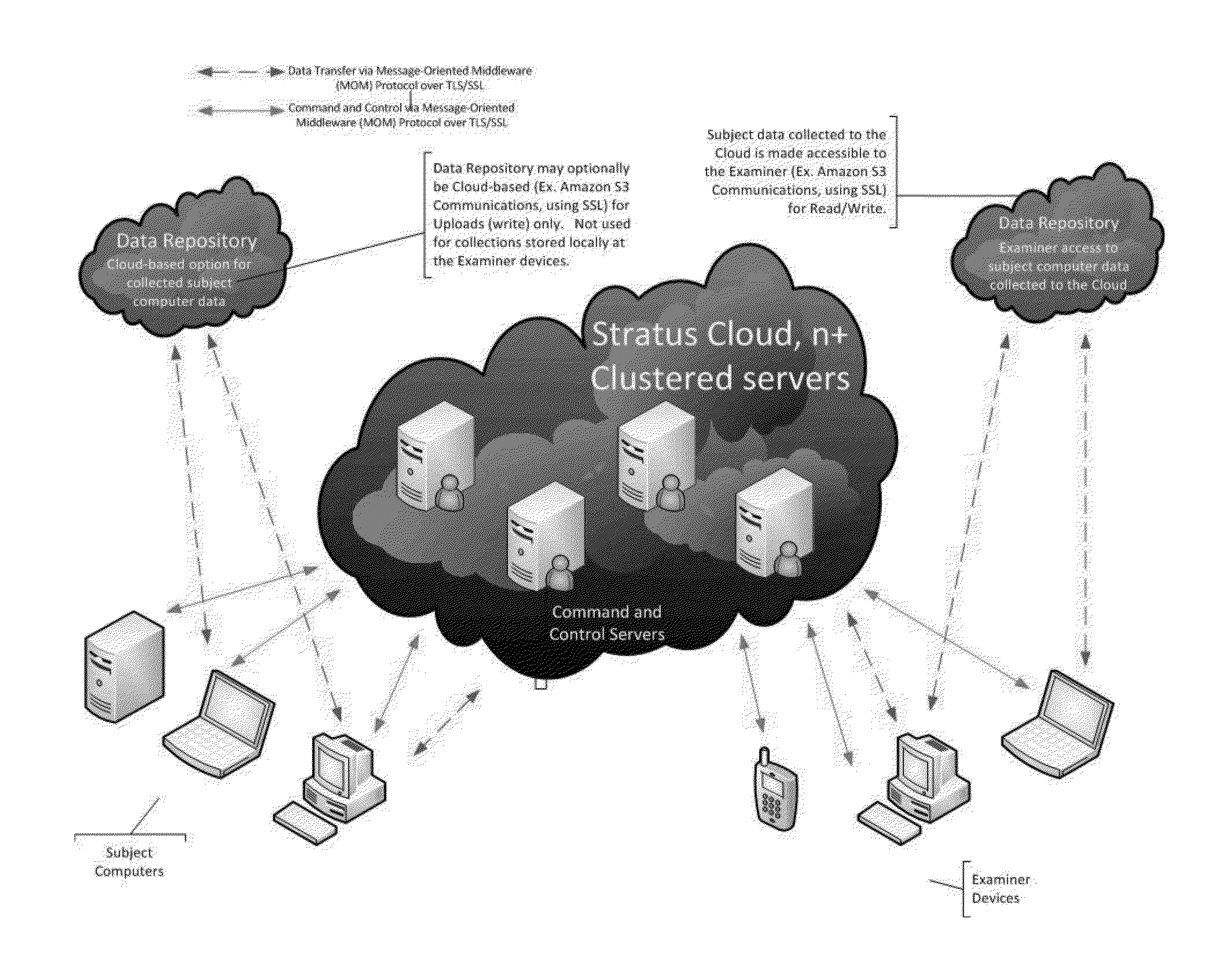
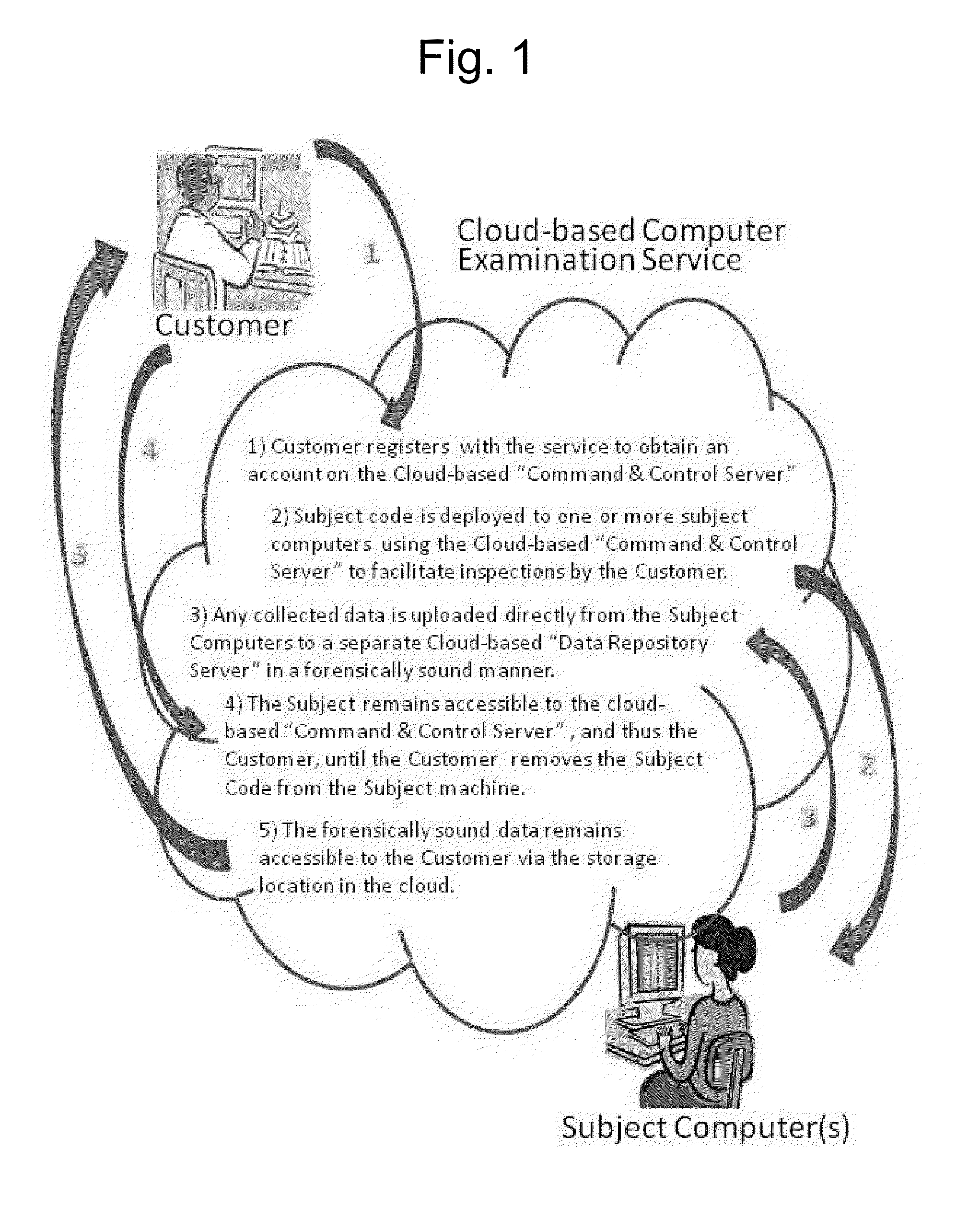
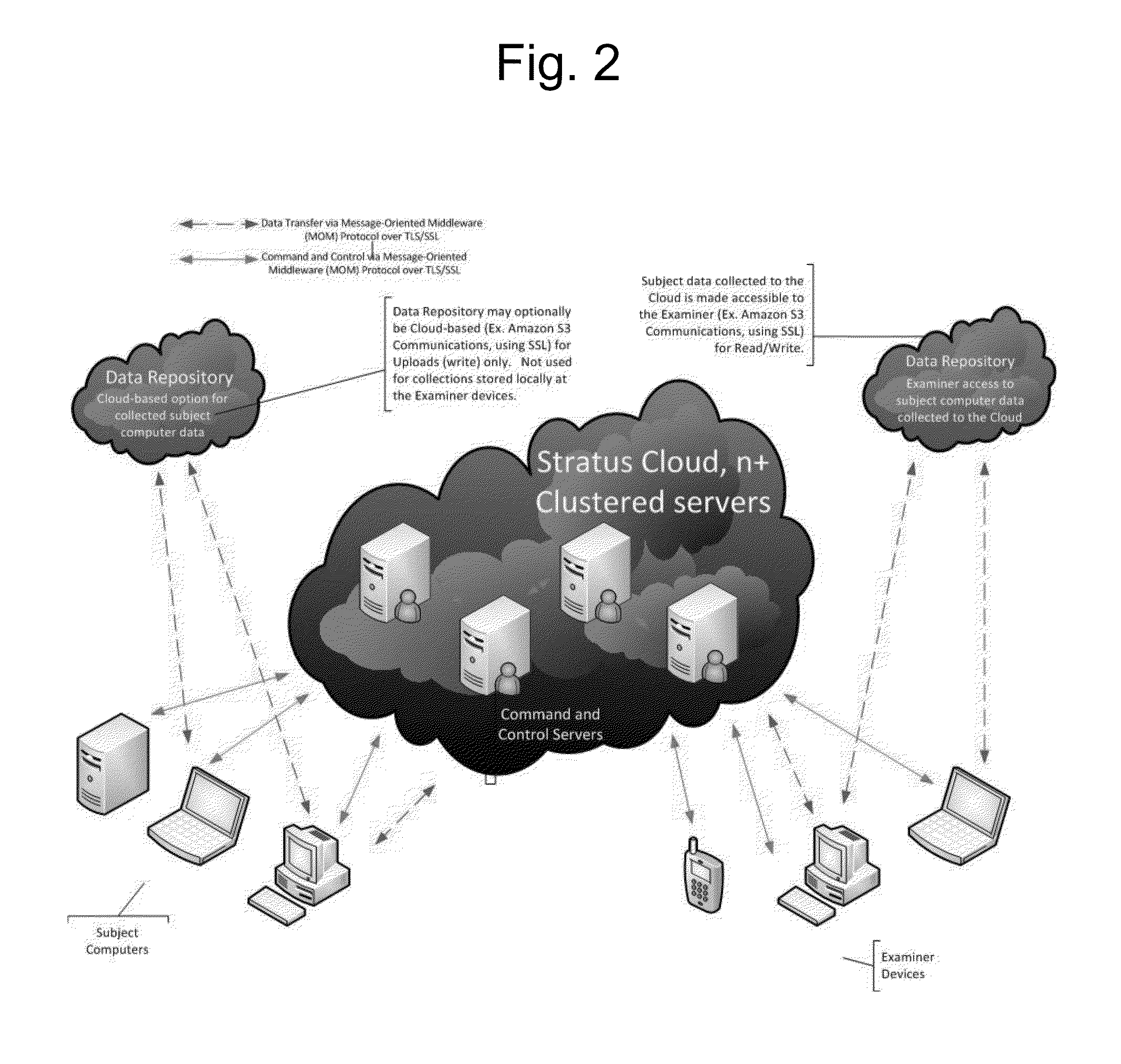
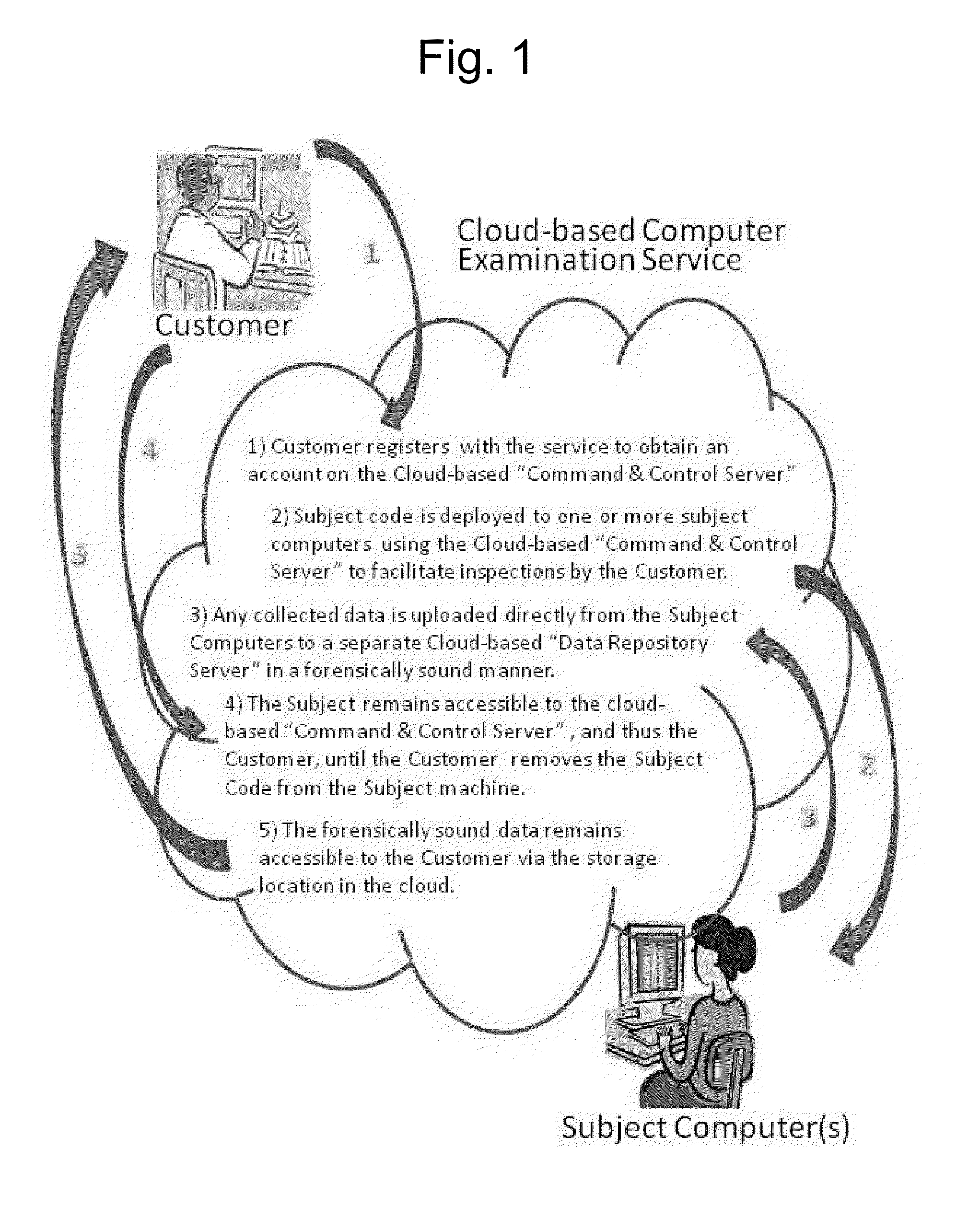
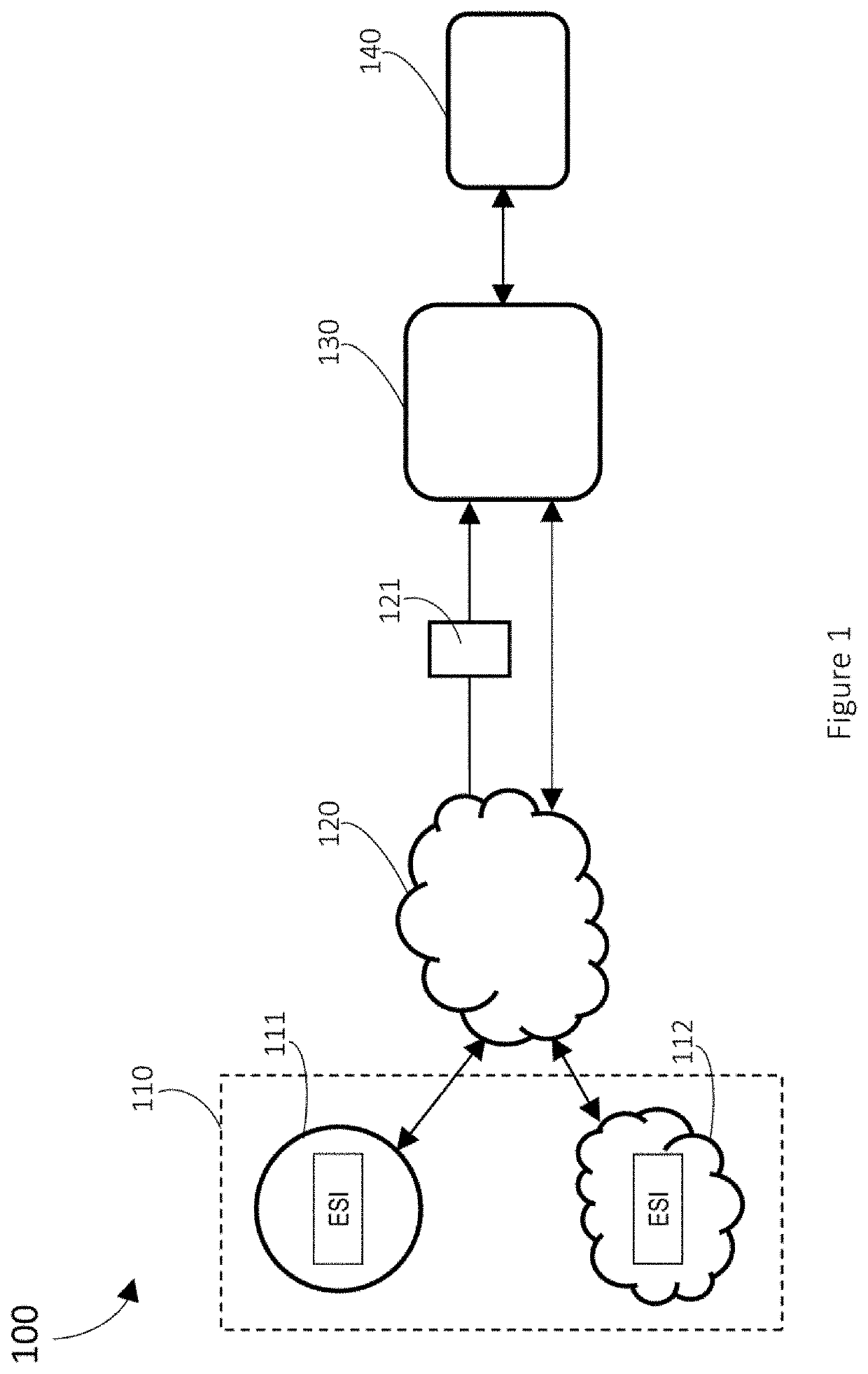
Systems and methods for provisioning digital forensics services remotely over public and private networks
ActiveUS20130218940A1Eliminate needComputer security arrangementsTransmissionPrivate networkElectronic discovery
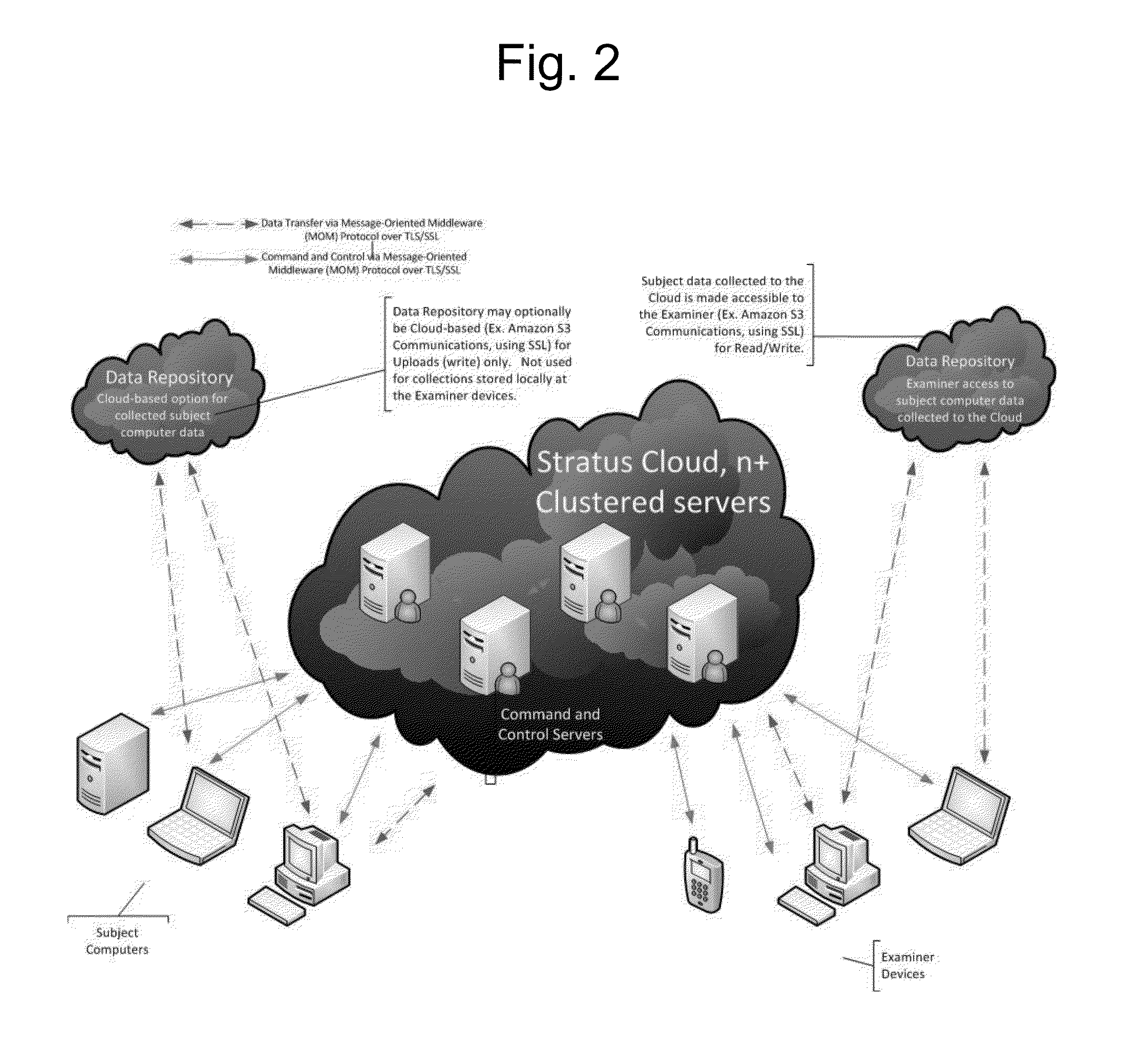
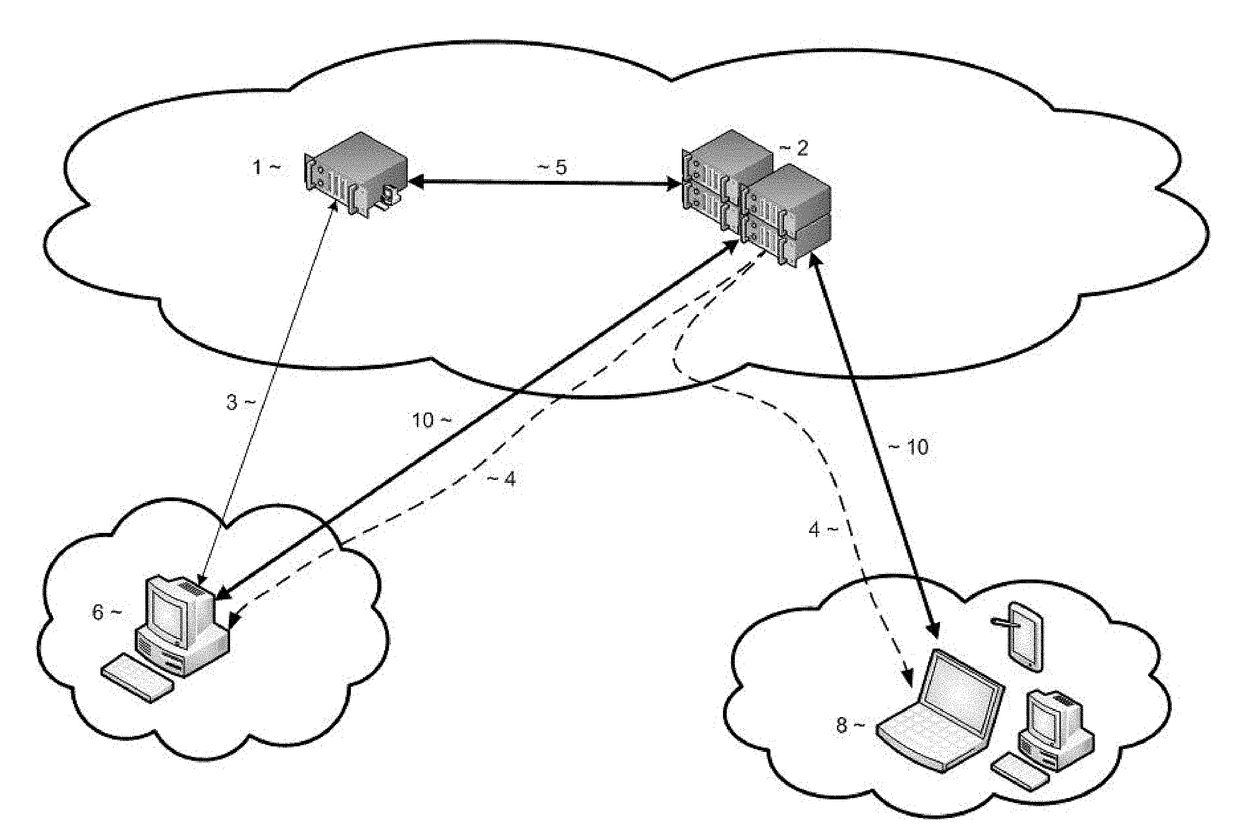
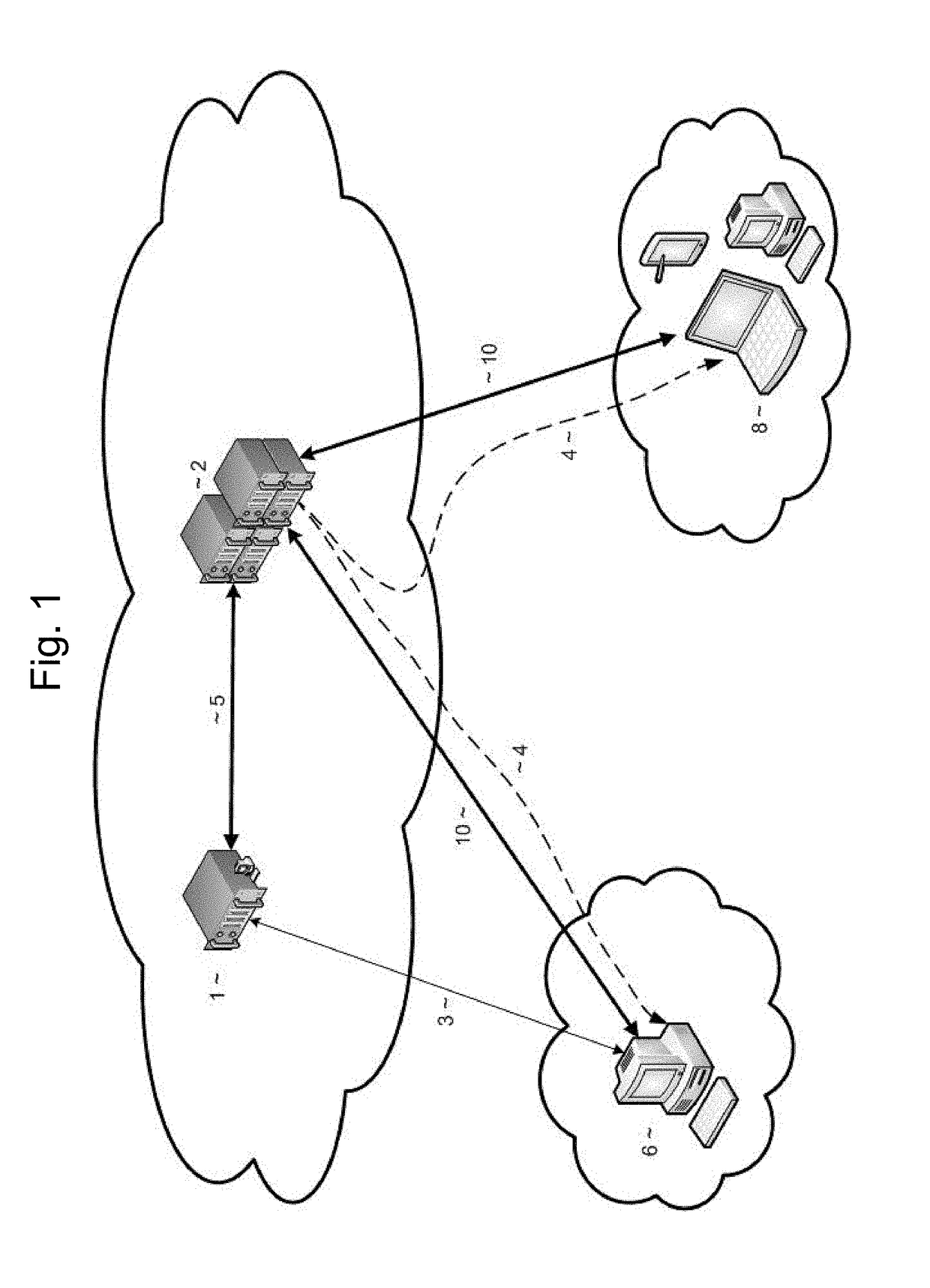
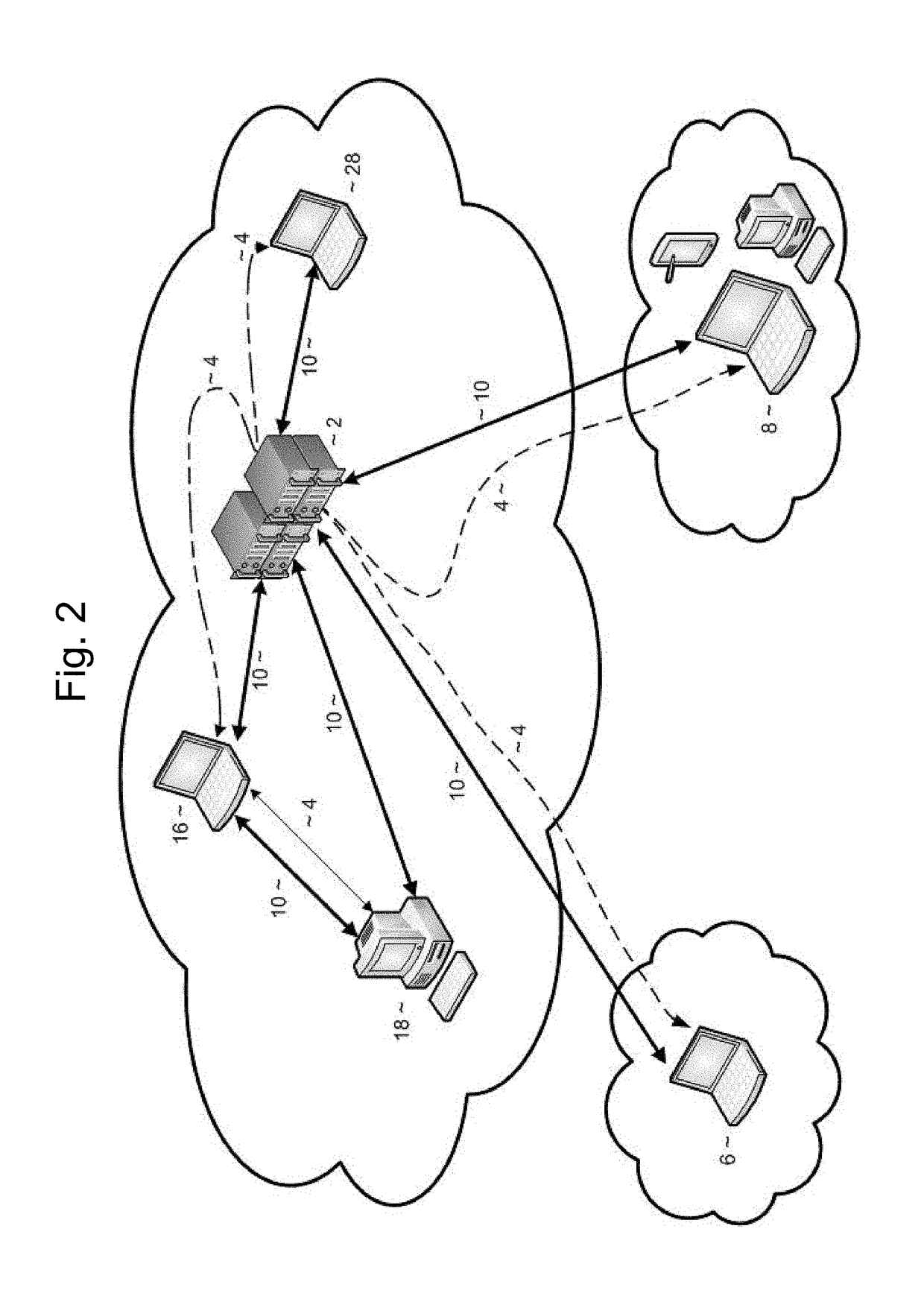
Provided are systems and methods for remote collection, preservation, and analysis of computer-based evidence in the course of conducting a network-based forensics or electronic discovery service. The challenge is to collect and analyze Electronically Stored Information (ESI) in a forensically sound manner over public and private networks. This is achieved via network-based forensics that may be conducted via an end user computer communicating directly with one or more subject computers across public or private networks, or it may be achieved via a “cloud computing” model whereupon the end user obtains, from the Internet, temporary use of shared resources, software, and information for the purpose of conducting digital forensics and eDiscovery upon subject computers.
Owner:SHANNON MATTHEW MARTIN +1
Relevancy ranking information retrieval system and method of using the same
InactiveUS20150112976A1Shorten analysis timeRapid positioningWeb data indexingDigital data processing detailsUser inputData mining
Disclosed herein is a system and method of using the same for a relevancy ranking information retrieval system. In an embodiment, the system is configured for ranking hits in text string searching. A search query for one or more hits relevant to an investigation is received from, as an example and not a limitation, a user. A set of attributes and features of each attribute are extracted related to metadata for each of the one or more hits. A score of each attribute is calculated based on the metadata features, although not limited to ‘metadata’ information as typically defined in digital forensics. Further, weights are assigned to each of the one or more attribute features and a relevancy rank is generated for each of the one or more hits based on assigned weights and the attribute score by using a predefined relevancy-ranking algorithm that may be adjusted by user input.
Owner:BEEBE NICOLE LANG
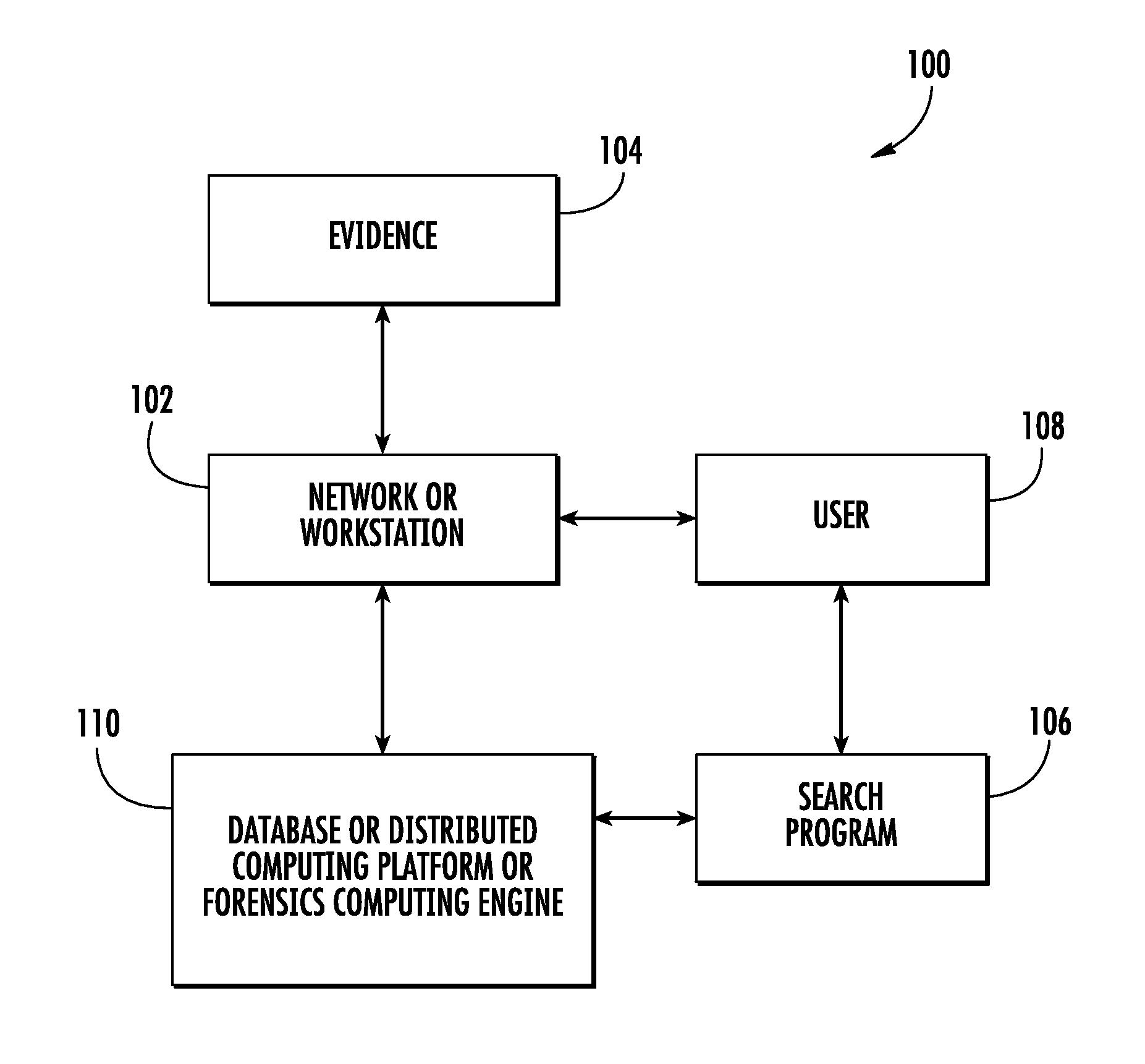
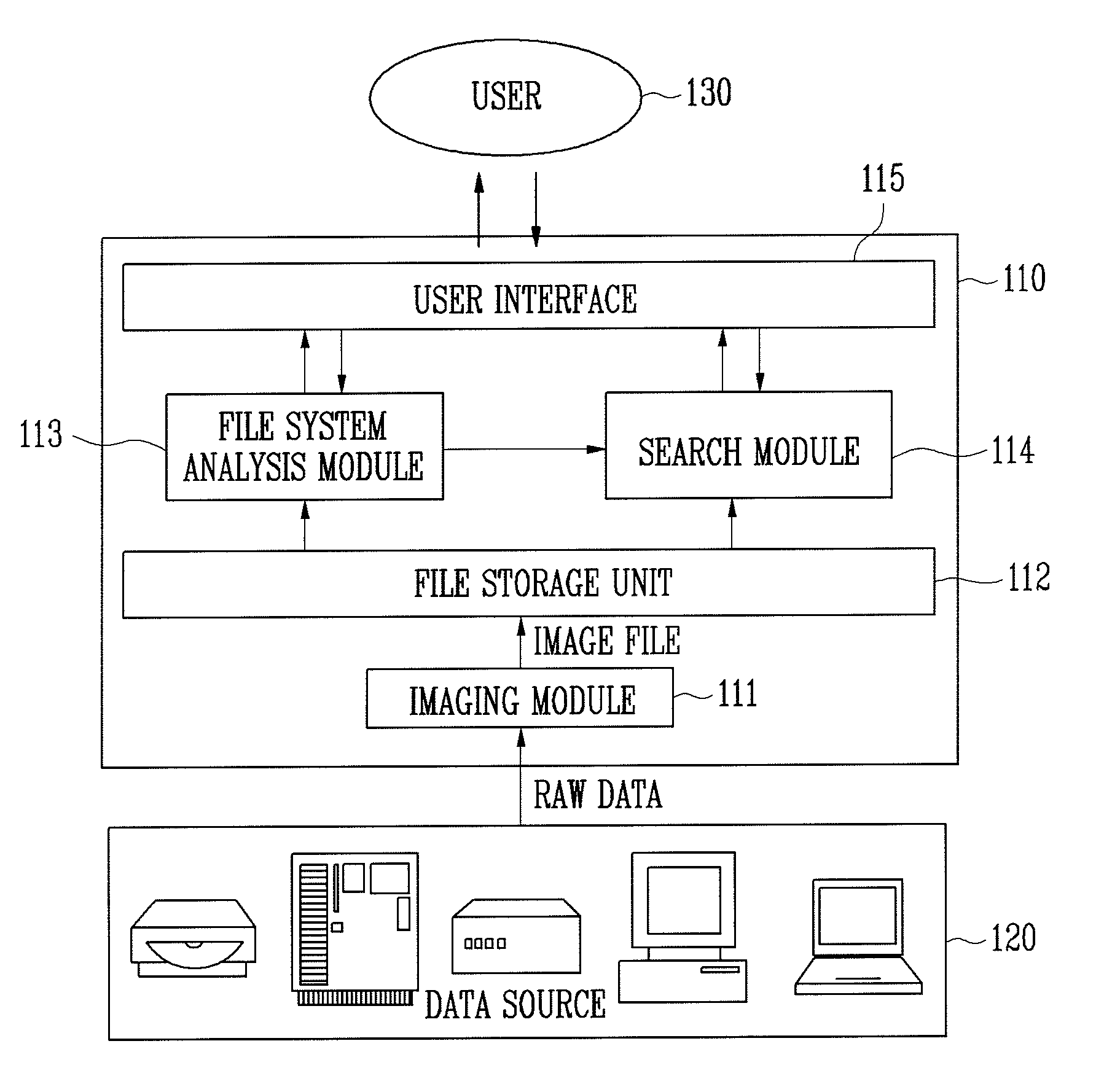
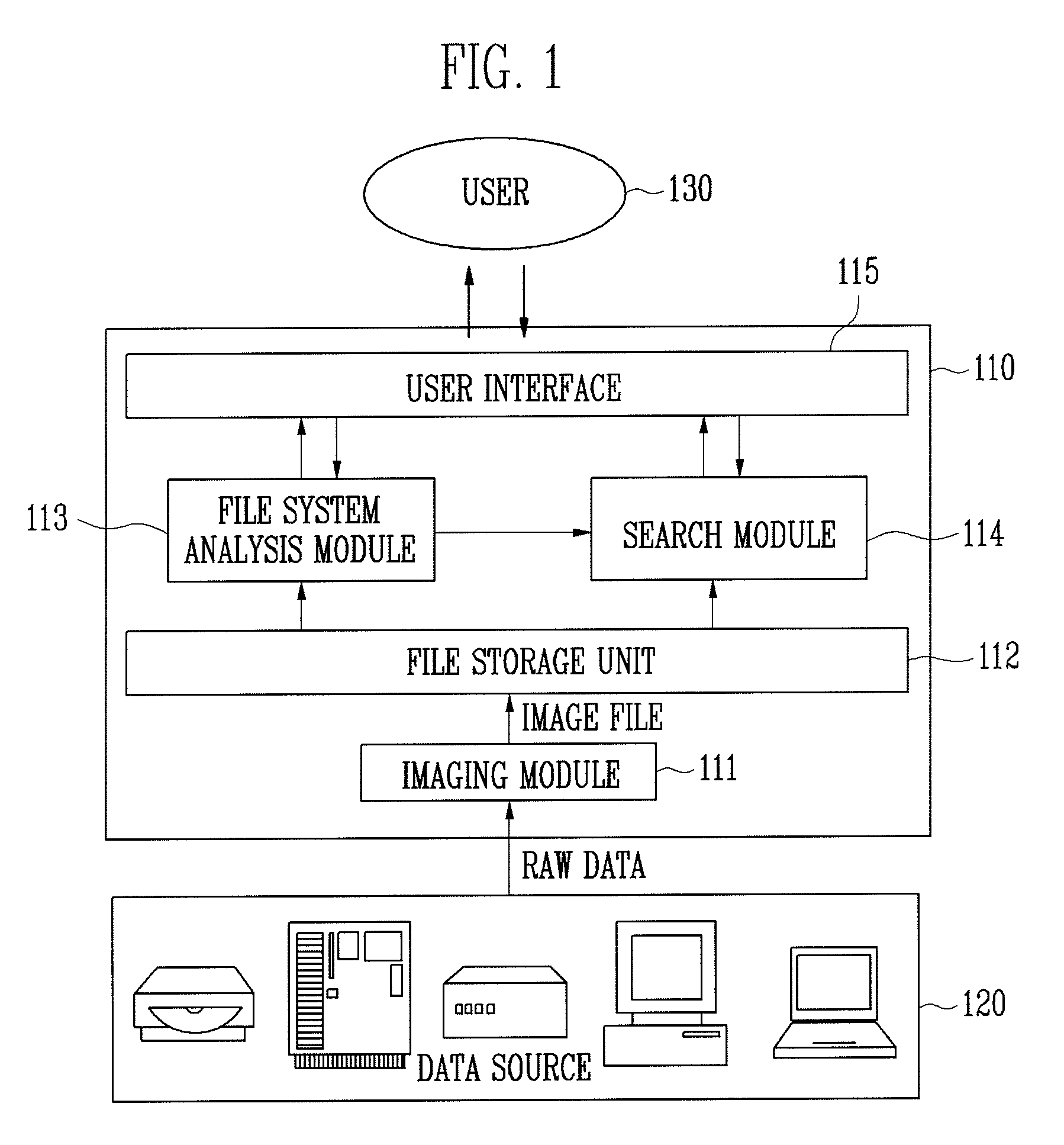
Apparatus and method for searching for digital forensic data
ActiveUS7865493B2Ensure high efficiency and accuracyDigital data information retrievalDigital data processing detailsOperational systemFile system
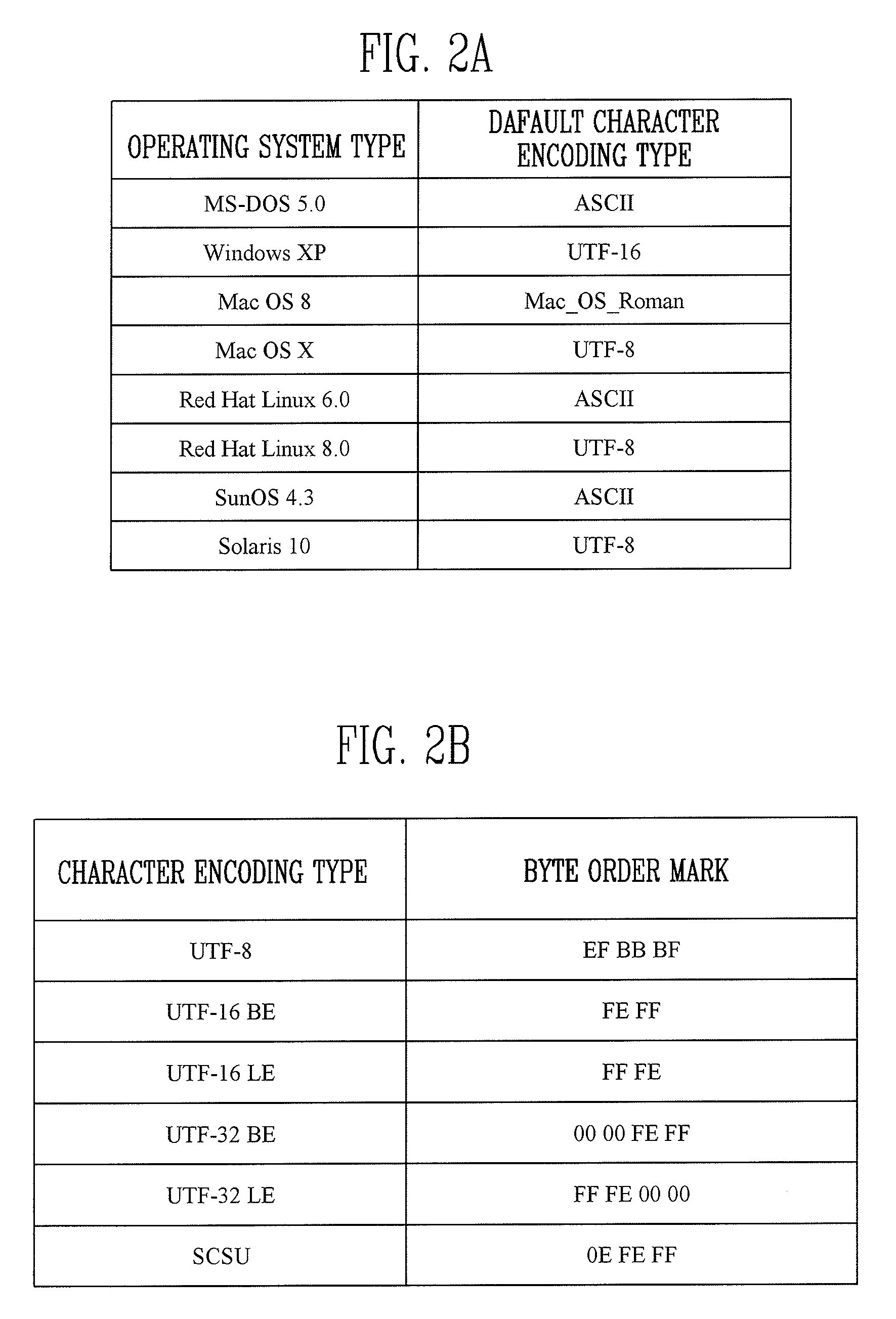
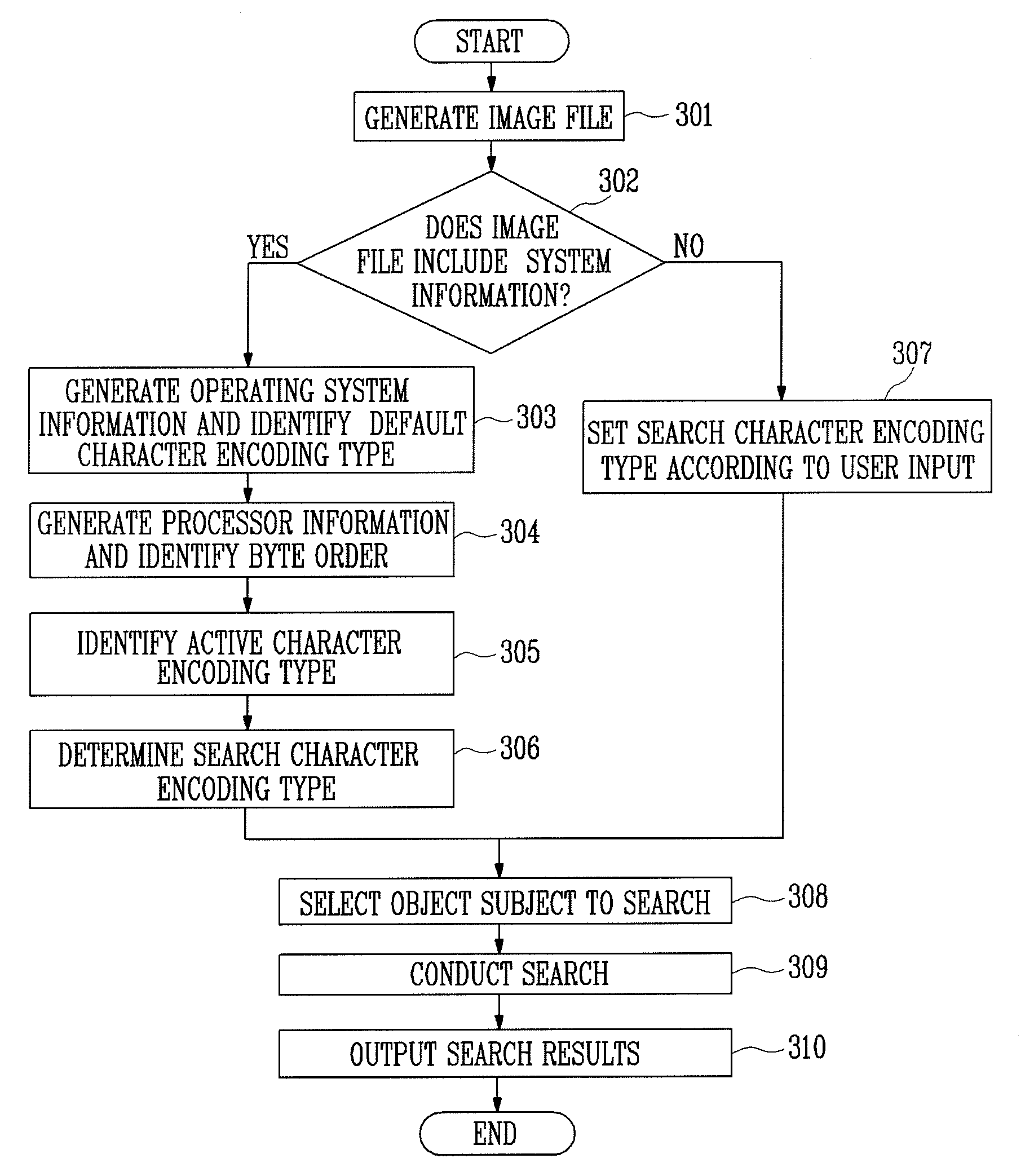
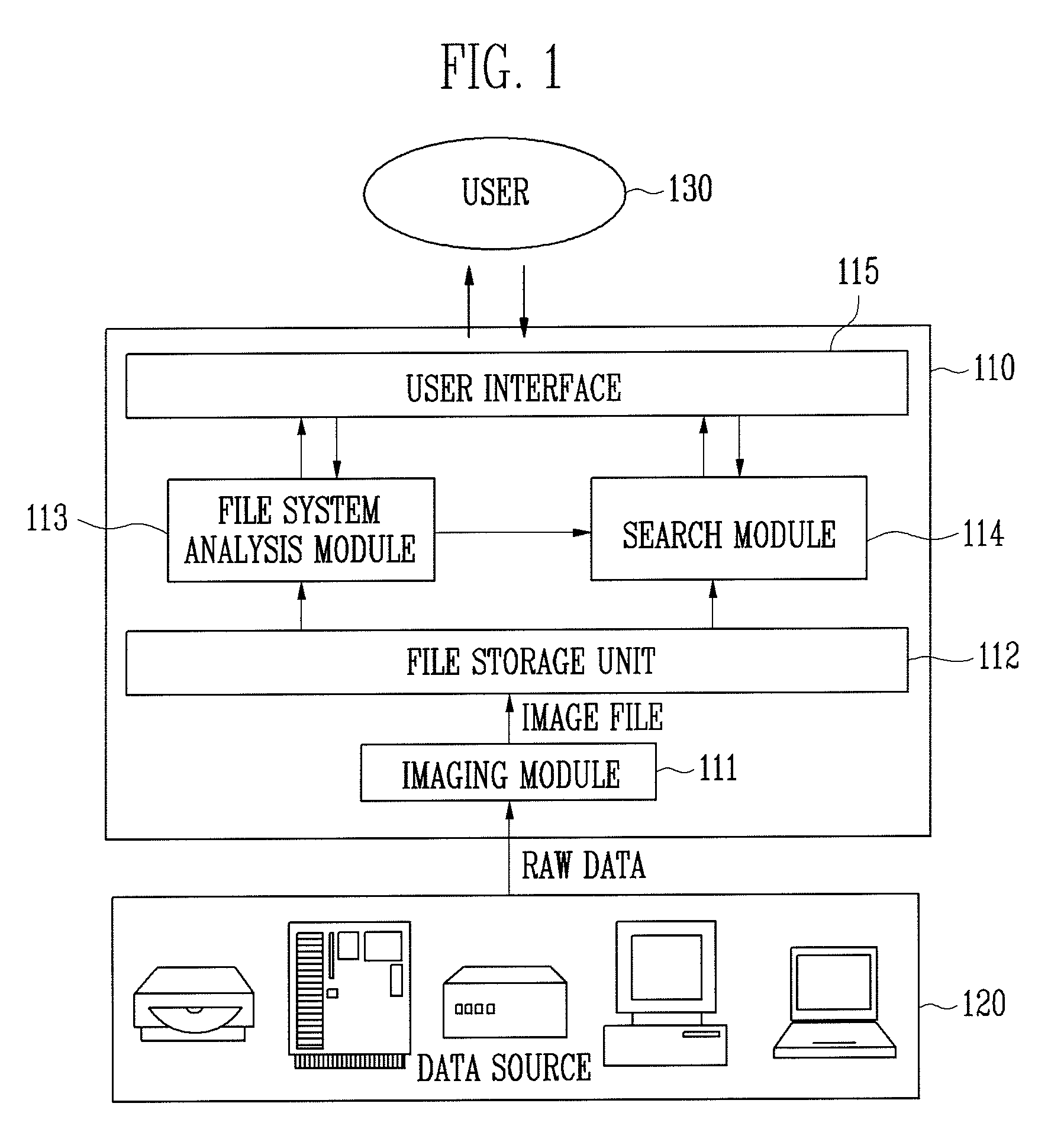
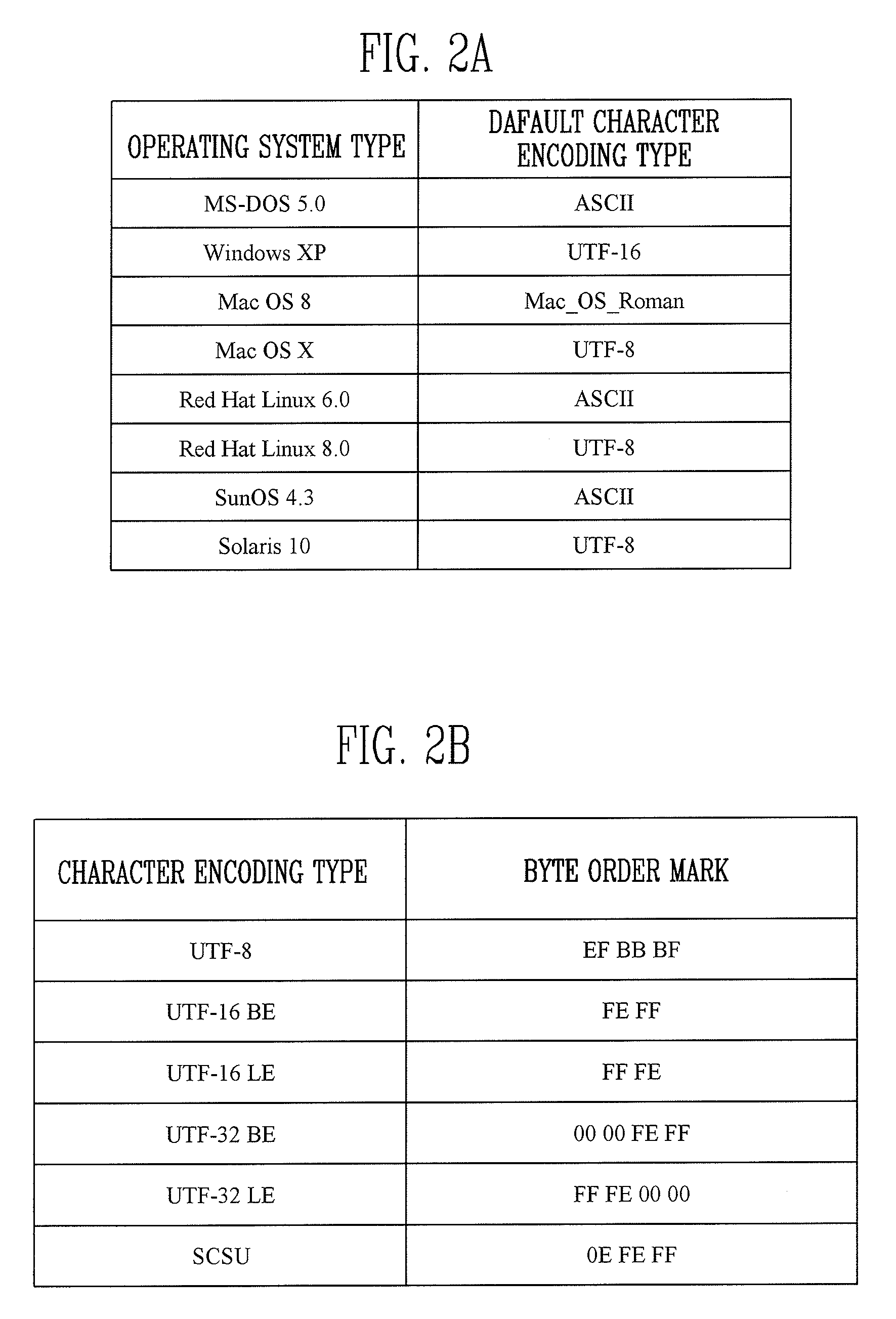
Provided are an apparatus and method for searching for digital forensic data. In particular, provided are an apparatus and method for searching for digital forensic data capable of automatically determining a character encoding type that is used in searching for data. The apparatus for searching for digital forensic data includes: an imaging module for generating an image file from a data source; a file system analysis module for analyzing a file system of the image file to generate file system analysis information; a search module for determining a search character encoding type based on the file system analysis information and searching for the data using the search character encoding type; and a user interface for receiving a command related to a search from a user, transmitting the received command to the file system analysis module and the search module, and outputting the search results to the user. In searching for digital forensic data, information on an operating system, a processor and an active character encoding type, which are actually used by a suspect, is extracted to determine a search character encoding type, so that accuracy and efficiency of searching for data are increased, and time, effort and money spent in determining a character encoding type are reduced.
Owner:ELECTRONICS & TELECOMM RES INST
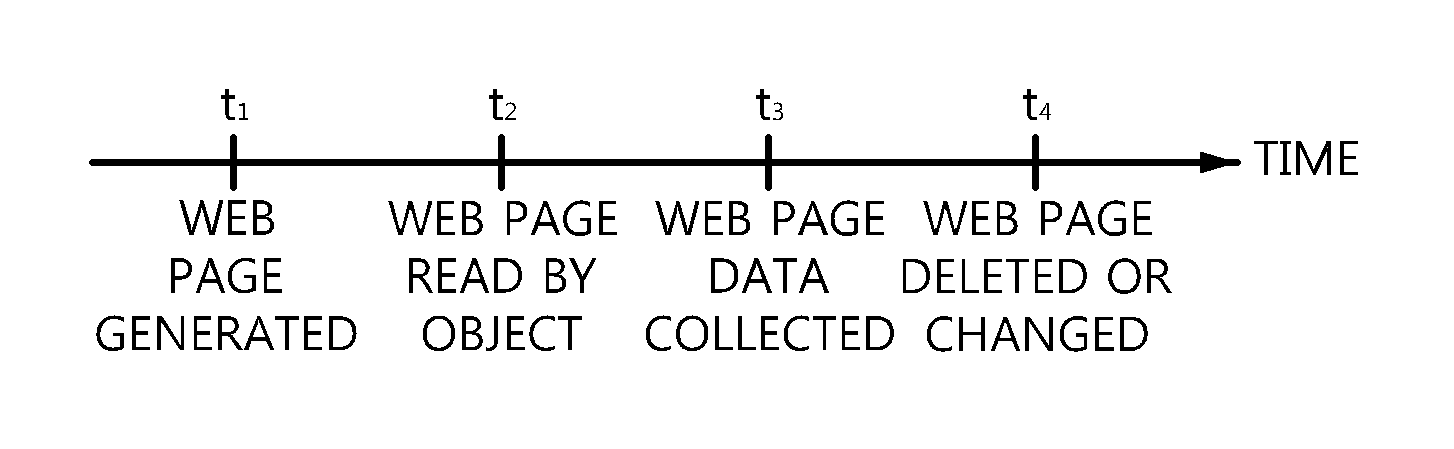
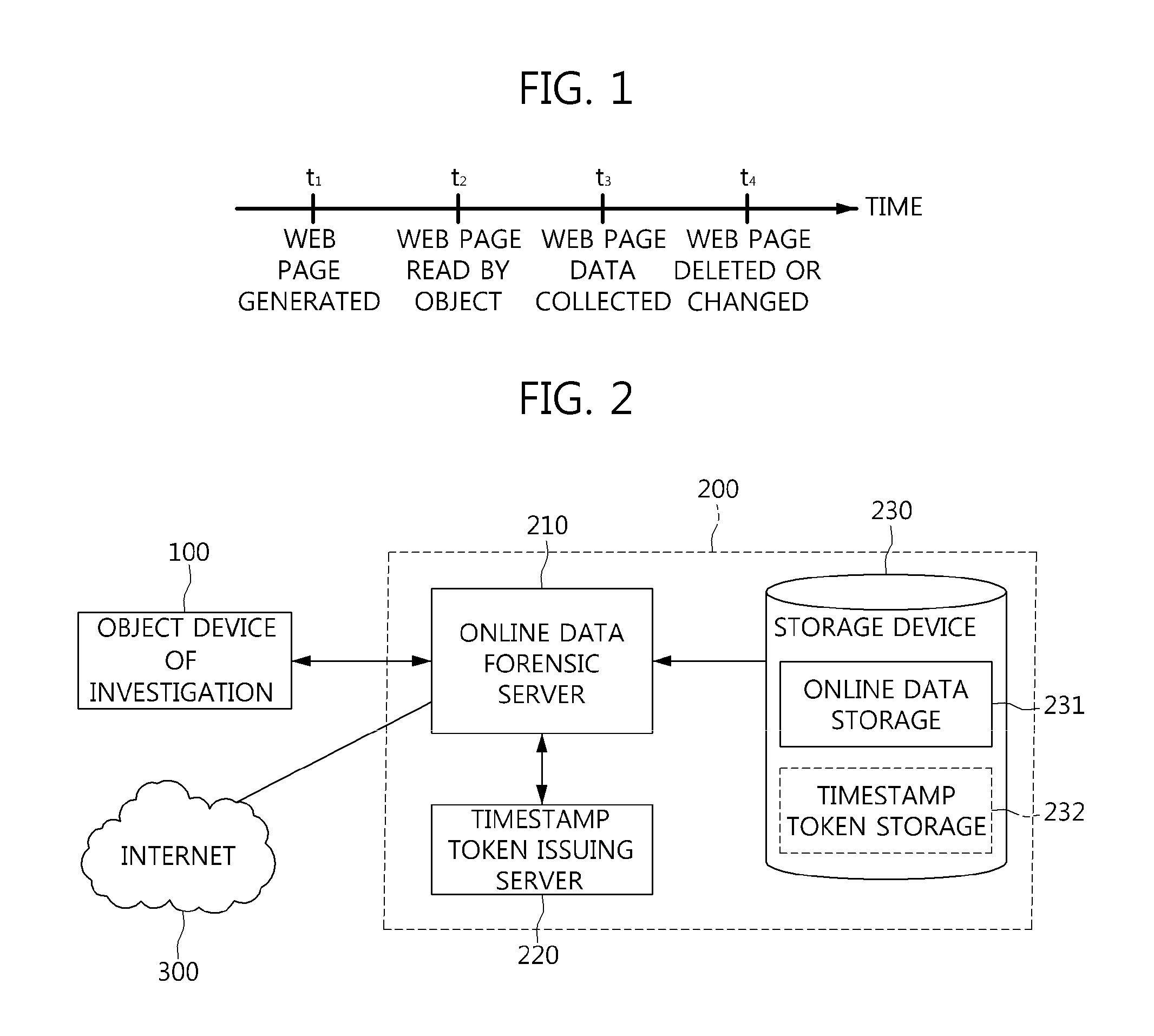
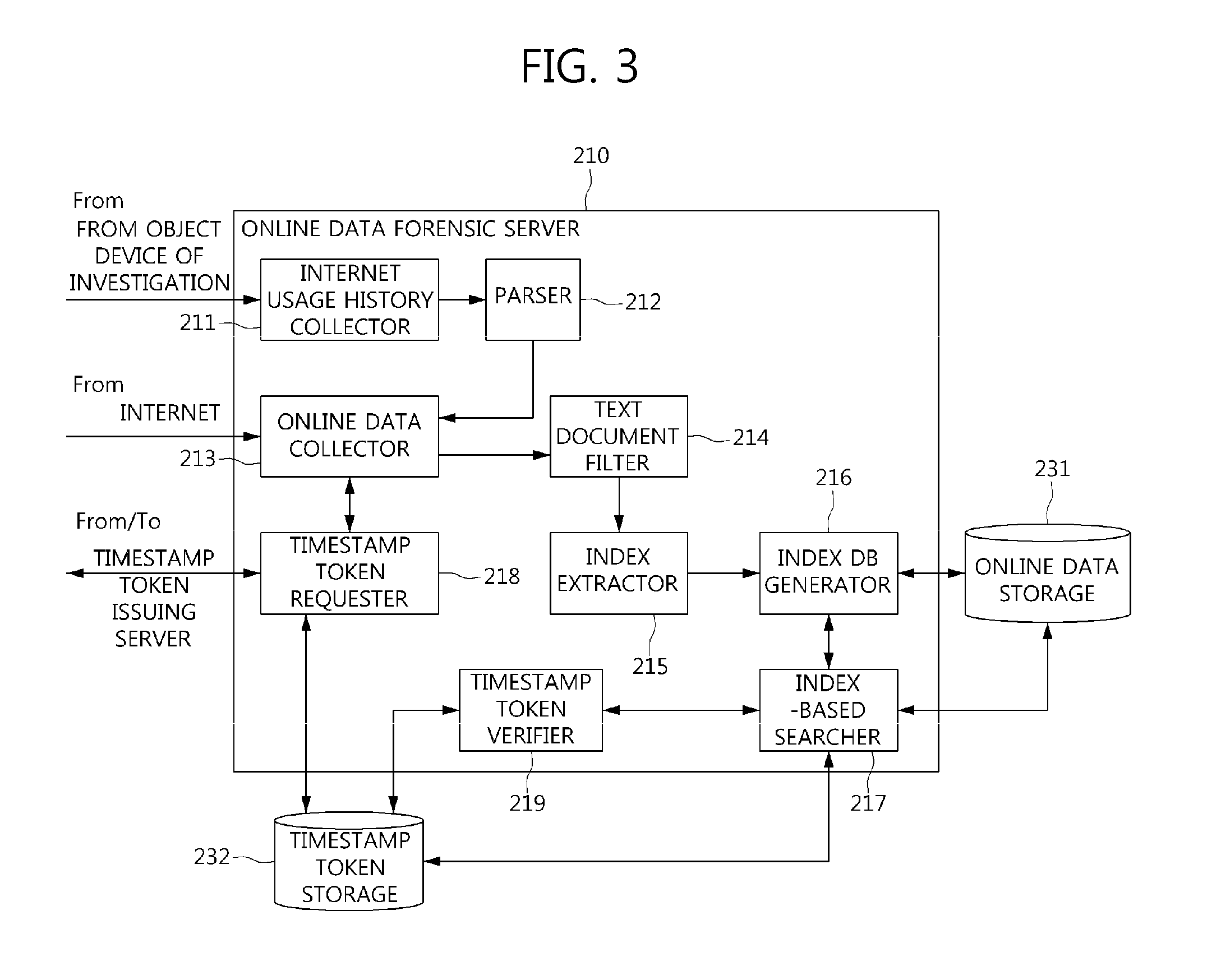
Method for data analysis and digital forensics and system using the same
A system and method for data analysis and digital forensics is provided. The system for data analysis and digital forensics may include: an online data forensic server for collecting and analyzing usage history information from an object device, which is subject to data collection, downloading and collecting data on the Internet based on the usage history information, requesting issuance of a timestamp token for the collected data, and receiving the issued timestamp token; a timestamp token issuing server for issuing the timestamp token for the collected data in response to the request for issuance of the timestamp token and proving the issued timestamp token to the online data forensic server; and a storage device for storing the collected data.
Owner:ELECTRONICS & TELECOMM RES INST
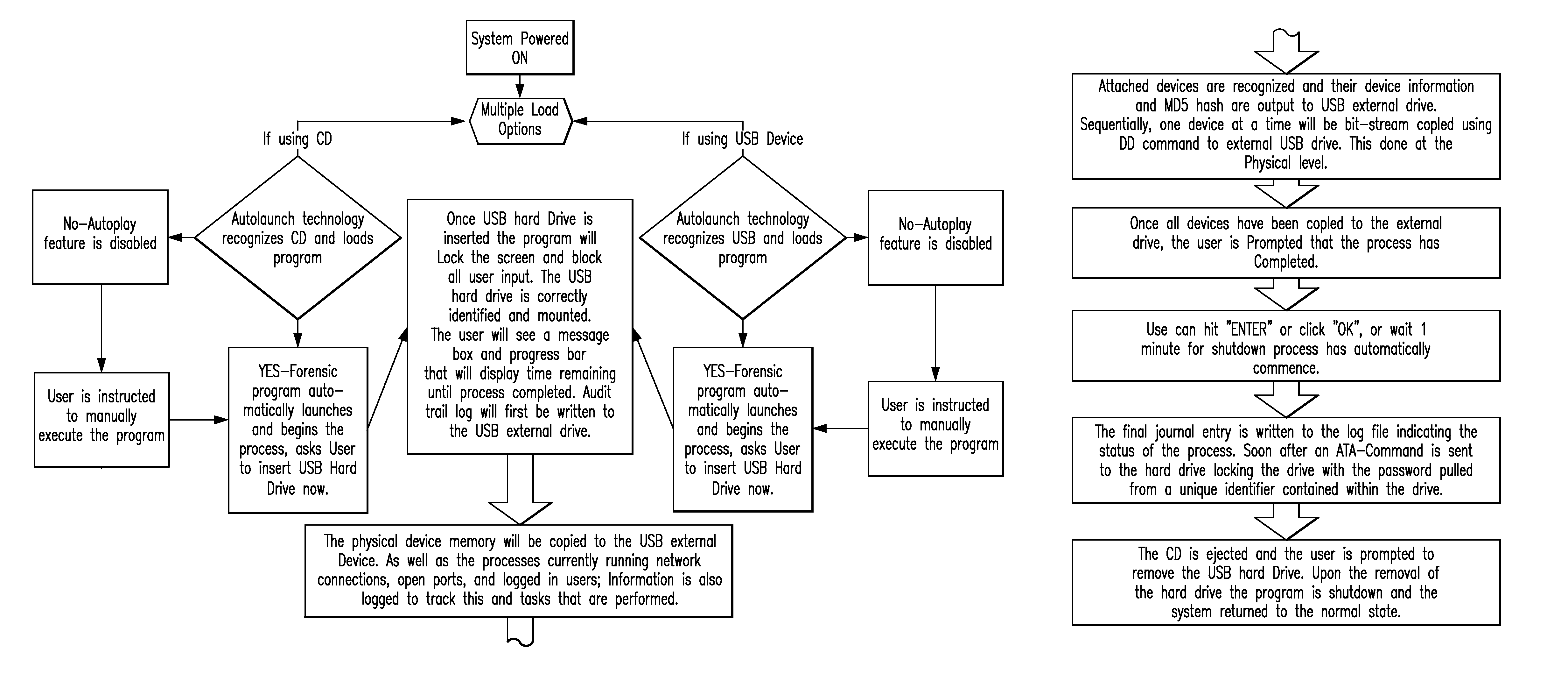
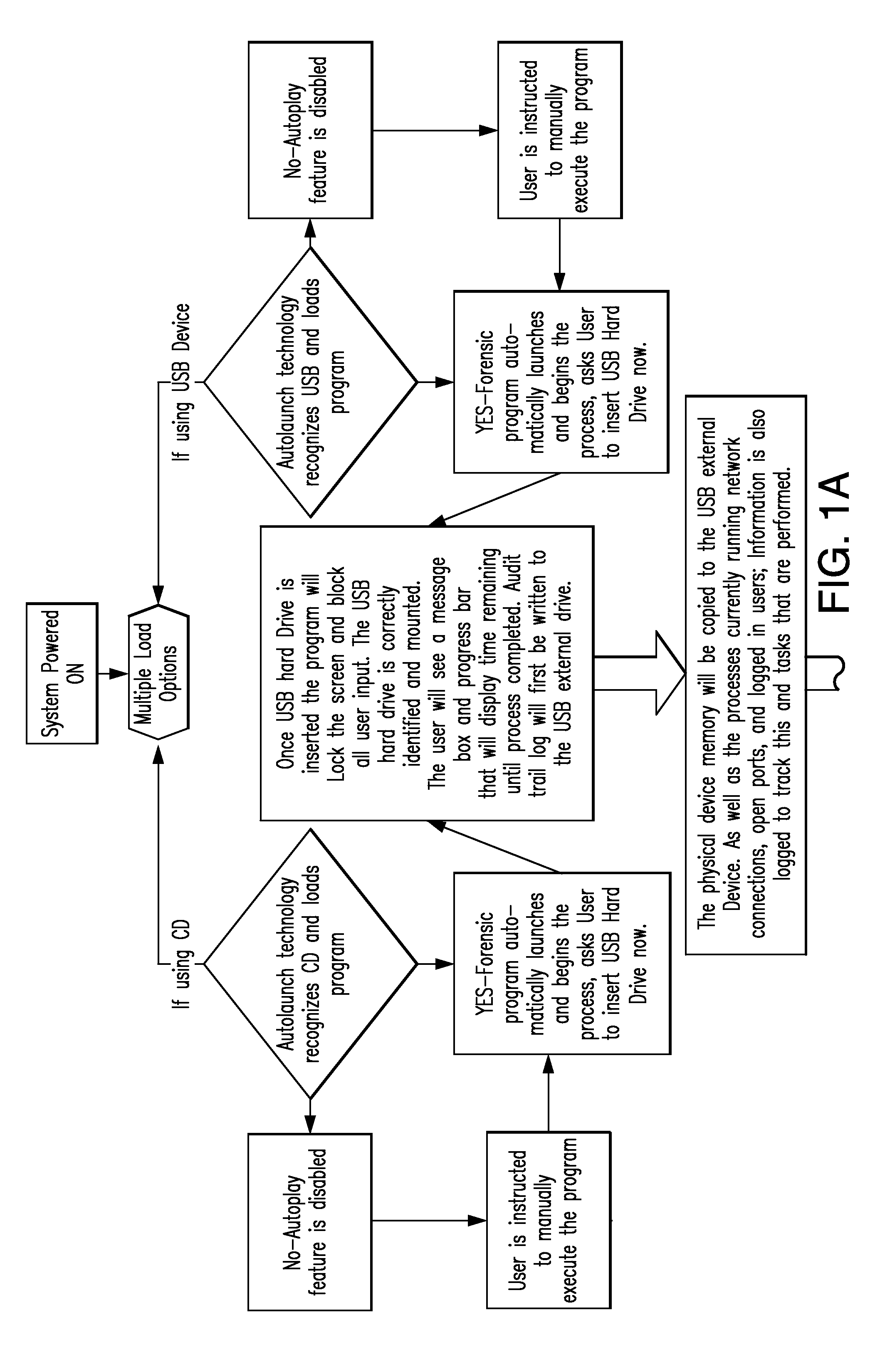
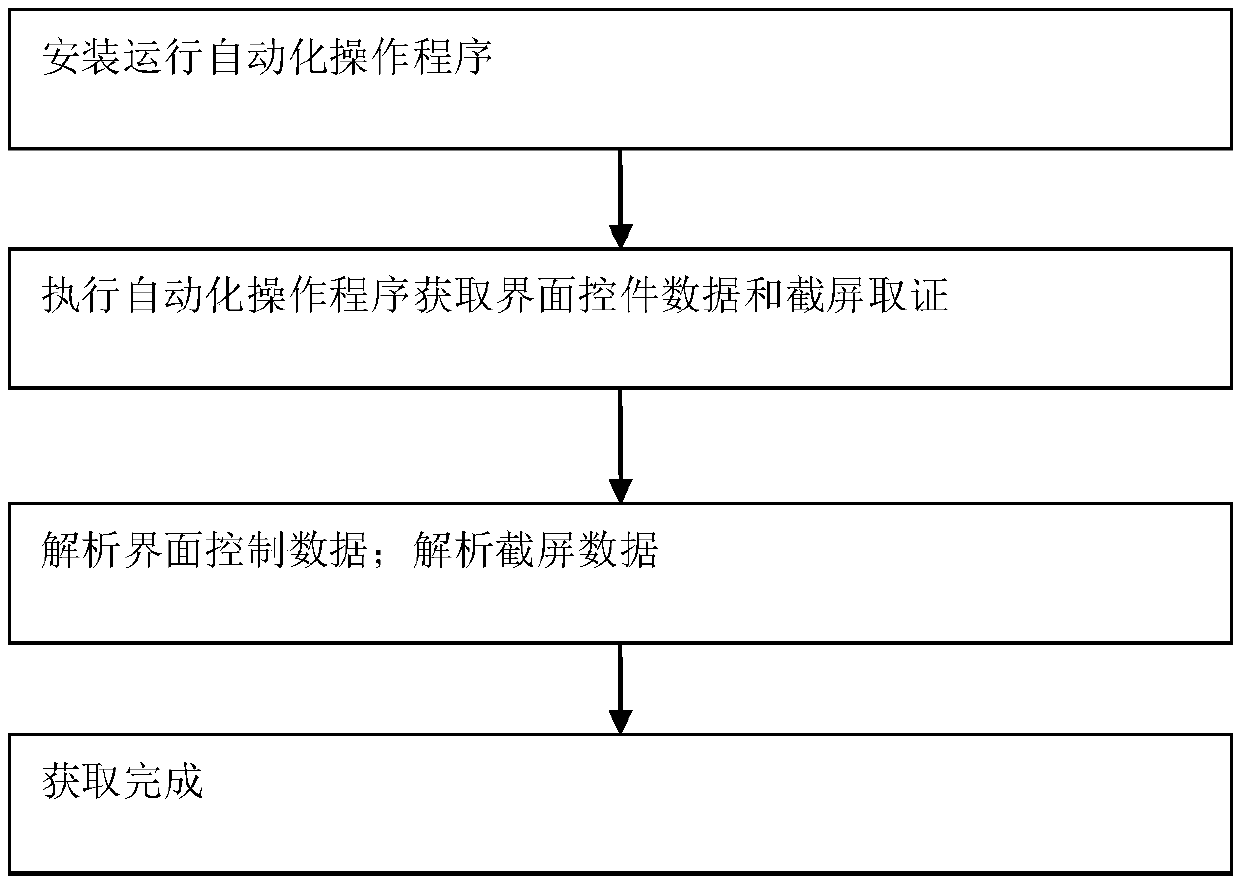
A memory data forensics method based on Android platform automated test tool
InactiveCN109542788AAddress deficienciesSoftware testing/debuggingSoftware deploymentSoftware engineeringAutomatic testing
The invention discloses a memory data forensics method based on an Android platform automated test tool. The method uses the automatic test tool UIAutoMator provided by the Android system to simulatethe operation function of the mobile phone. When the user operates the mobile phone to enter a certain interface, the current page data is generated into an xml file through the automatic test tool UIAutoMator; and when the user operates the mobile phone to enter an interface, the xml file is generated through the automatic test tool UIAutoMator. the above-mentioned xml file is analyzed and data collection is completed; When the automatic test tool UIAutoMater cannot resolve the data in the specific interface, the screenshooting function of the automatic test tool UIAutoMater is called to process the screenshooting of the current specific interface, and then the screenshooting pictures captured are recognized and analyzed to complete the data collection. the method effectively solves the shortcomings of the traditional forensics technology and provides a digital forensics method in the intelligent mobile terminal Android system.
Owner:南京烽火星空通信发展有限公司
Digital forensics
ActiveUS8887274B2Sufficient informationMemory loss protectionError detection/correctionSystem callSequence alignment
New digital forensic techniques and systems are disclosed. System call information is collected from a device under test (DUT) and converted to a sequence format. Thereafter, sequence alignment methods and tools can be used to investigate and identify patterns of behavior that are suspicious.
Owner:FORTINET
Method for authenticating digital images of digital camera
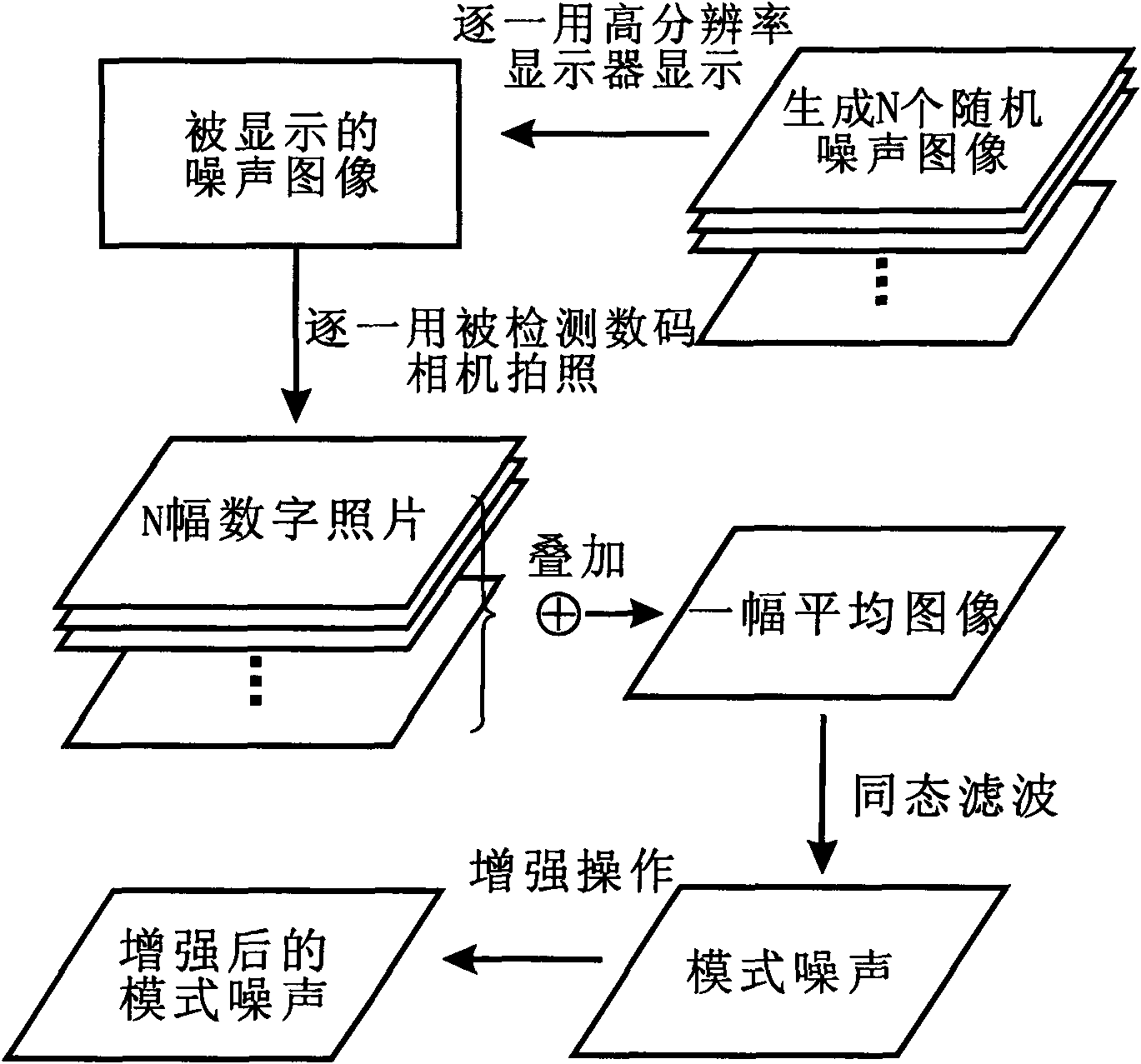
InactiveCN101616238AShorten the timeGuaranteed differenceImage data processing detailsPictoral communicationTamper resistanceDisplay device
The invention discloses a method for authenticating digital images of a digital camera. The method comprises the following steps: acquiring digital images shot by the digital camera, extracting the pattern noise of the digital camera by the acquired digital images, and authenticating the digital images on the basis of the pattern noise; wherein, the method is characterized in that the operation for acquiring the digital images comprises the following steps: selecting a plurality of independent random noise images, and displaying the random noise images on the same display in sequence; and then, shooting the displayed random noise images one by one by the digital camera to be detected, thereby acquiring the required plural digital images. The invention can greatly save time for taking pictures on the premise that the difference in image content is guaranteed, and improves the algorithm efficiency. The invention is applicable to the fields of digital forensics and image authentication as well as source detection, copyright protection, tamper-proofing and the like of digital pictures.
Owner:SUN YAT SEN UNIV
Method and system for achieving synergic forensic analysis on remote forensic target terminal
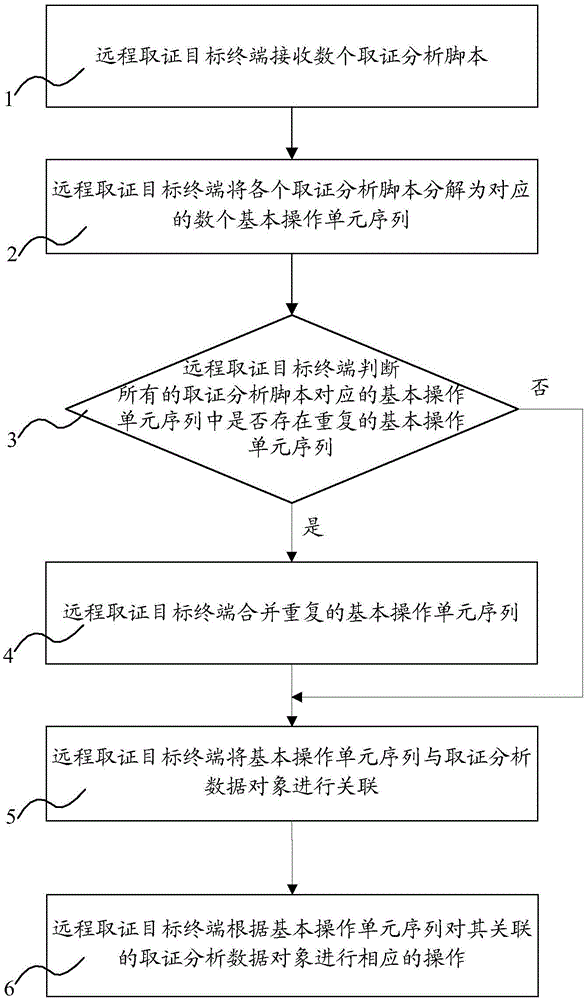
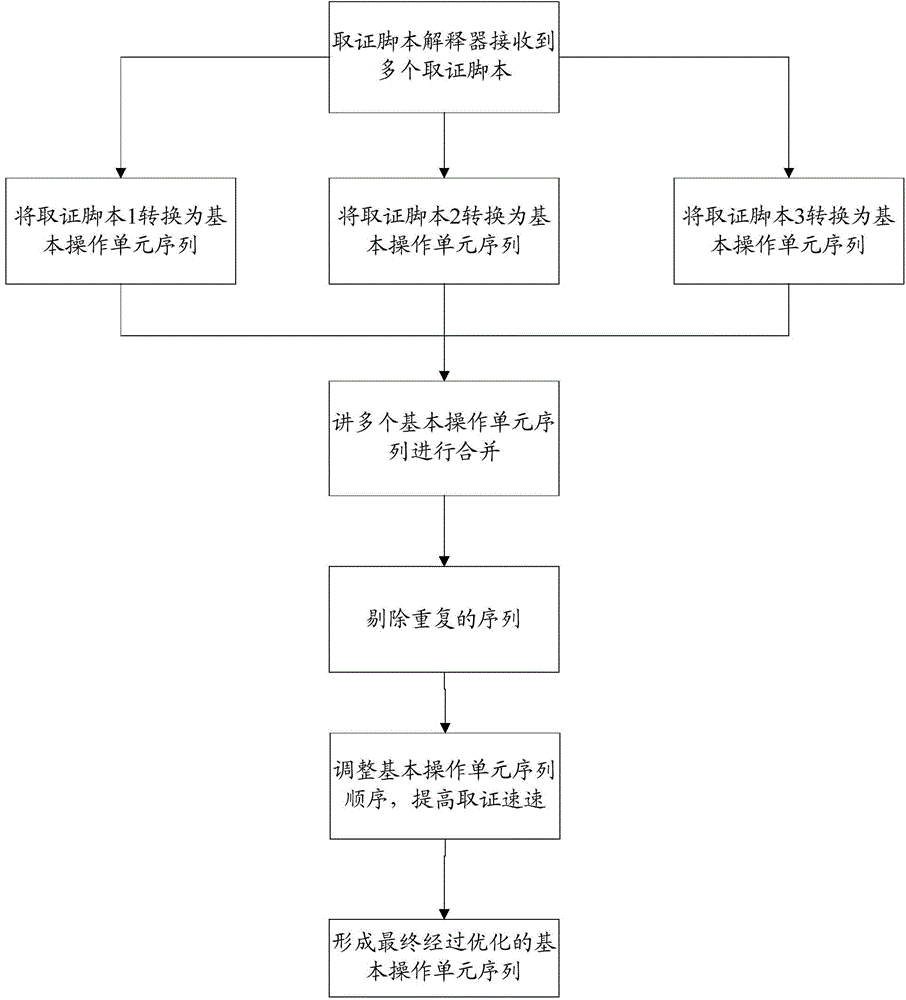
ActiveCN104462996AReduce overheadImprove reliabilityDigital data protectionTransmissionAnalysis dataPrimitive operation
The invention relates to a method for achieving synergic forensic analysis on a remote forensic target terminal. The method comprises the following steps: dividing forensic analysis scripts into a plurality of corresponding basic operation unit sequences through the remote forensic target terminal; judging whether all basic operation unit sequences have repeated basic operation unit sequences or not through the terminal; if the basic operation unit sequences have repeated basic operation unit sequences, combining the repeated basic operation unit sequences, or else associating the basic operation unit sequences with a forensic analysis data target, and performing corresponding operation on the forensic analysis data target associated with the basic operation unit sequences according to the basic operation unit sequences. The invention further provides a system for achieving synergic forensic analysis on the remote forensic target terminal. The system comprises a forensic server and a forensic script interpreter. By adopting the method and the system provided by the invention, the forensic scripts are interpreted into specific forensic behavior and the forensic behavior is reasonably combined and optimized, so that the reliability of digital forensic analysis and the analysis processing efficiency are improved, and the method and the system have a relatively wide application range.
Owner:THE THIRD RES INST OF MIN OF PUBLIC SECURITY
System and method for searching large amount of data at high speed for digital forensic system
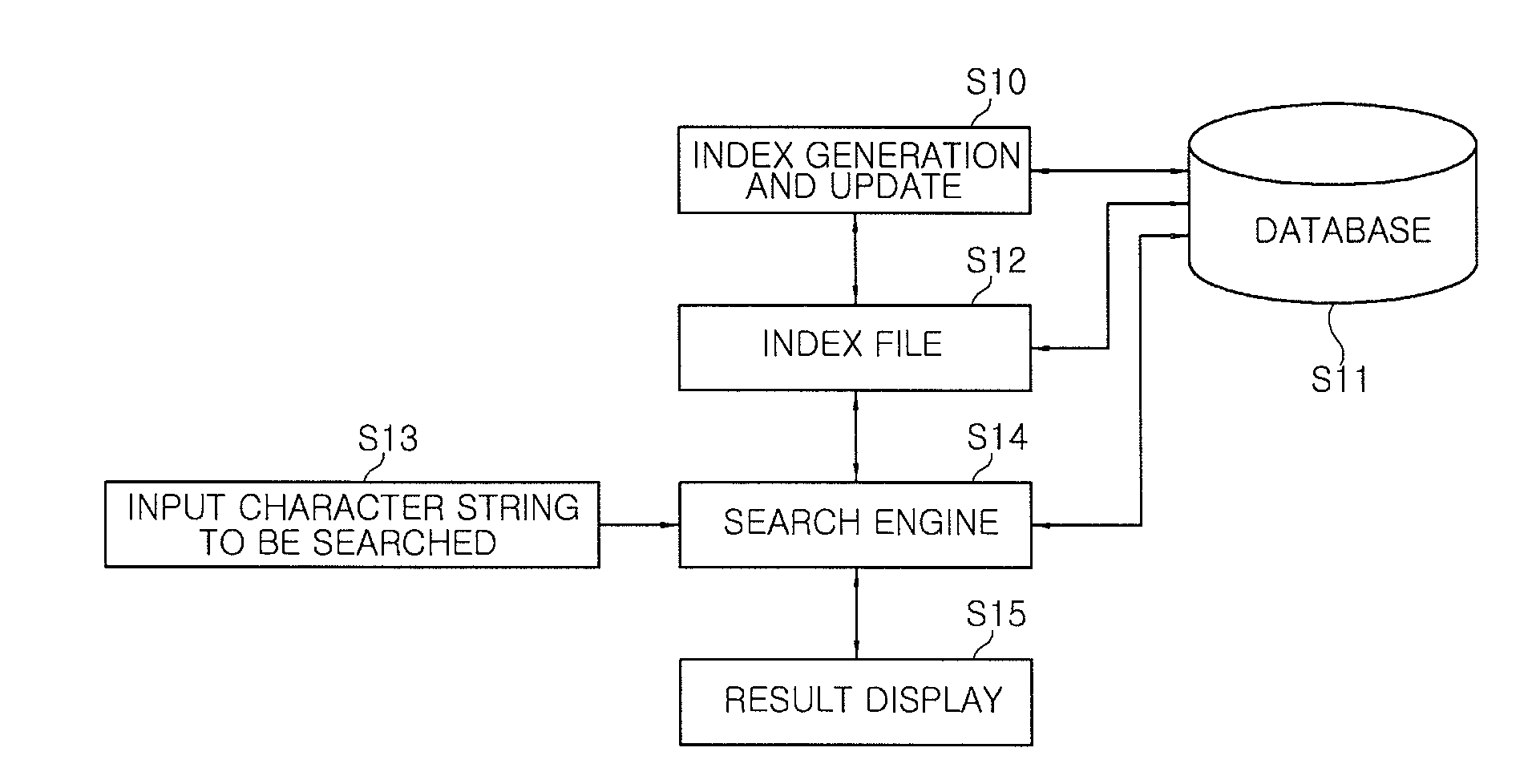
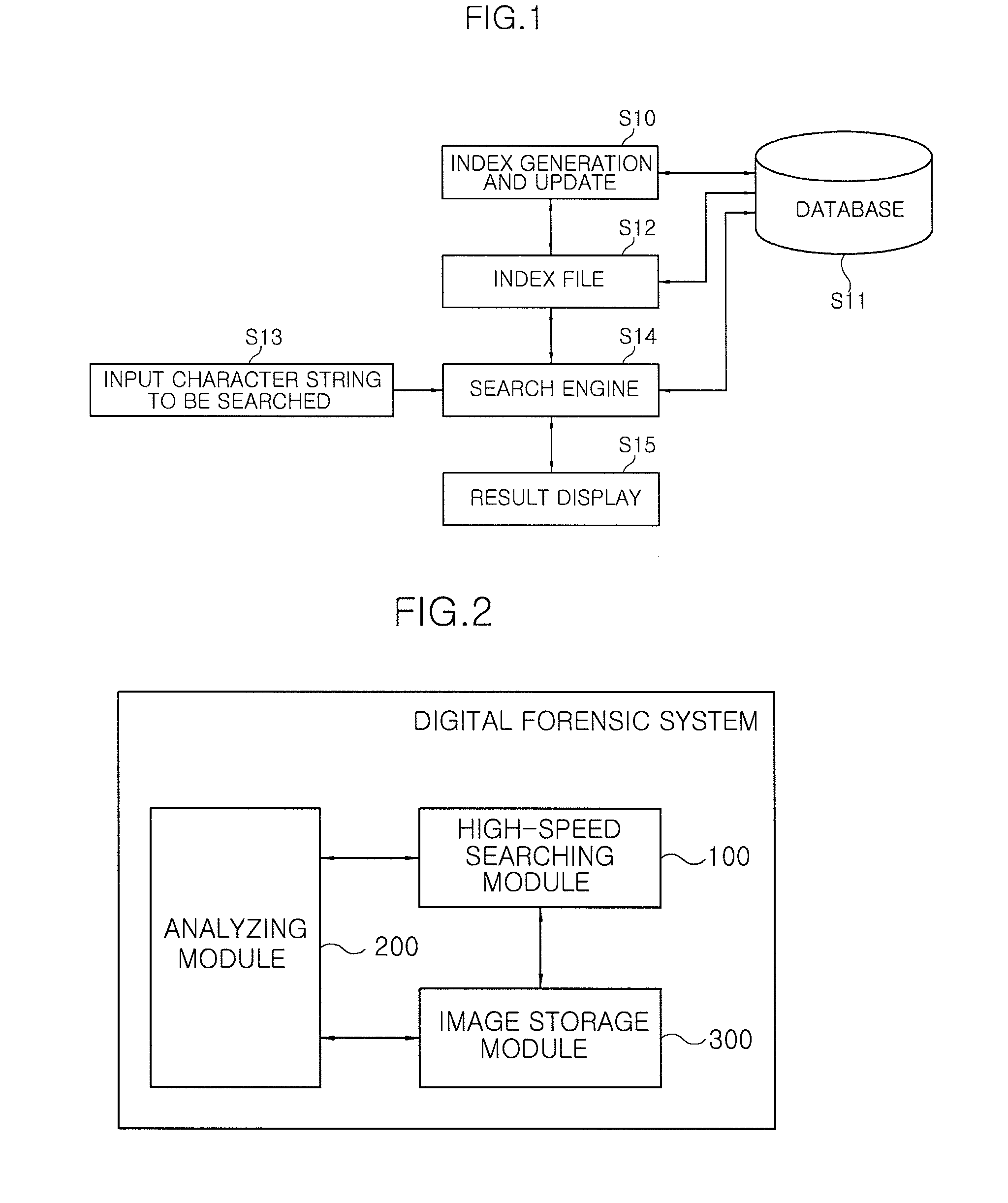
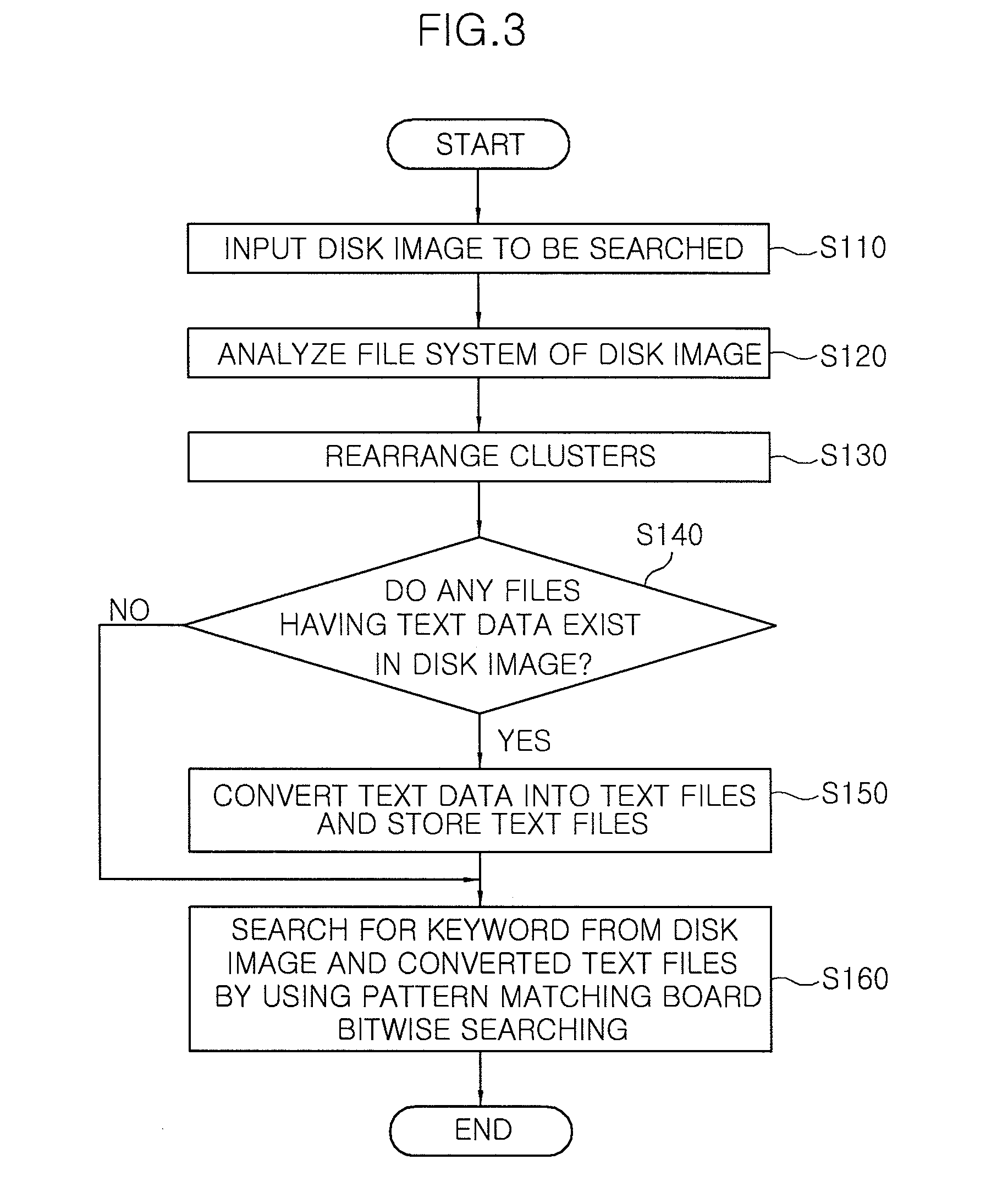
InactiveUS20090138453A1Increase speedHigh-speed searchProgram controlSpecial data processing applicationsImage storageDatabase
Disclosed is a system and method for searching a large amount of data for a digital forensic system. A method of searching a large amount of data at high speed for a digital forensic method includes: allowing an image storage module to receive a disk image to be searched; allowing an analyzing module to analyze the disk image input from the image storage module to generate an index of files existing in the disk image; allowing a high-speed searching module to rearrange clusters by files, the clusters corresponding to the disk image input from the image storage module; allowing the high-speed searching module to extract text data from files having the text data, and store the text data; and allowing the high-speed searching module to search for at least one keyword by using a bitwise searching manner.
Owner:ELECTRONICS & TELECOMM RES INST
Apparatus and method for searching for digital forensic data
ActiveUS20090094203A1Improve accuracyImprove efficiencyDigital data information retrievalDigital data processing detailsOperational systemFile system
Provided are an apparatus and method for searching for digital forensic data. In particular, provided are an apparatus and method for searching for digital forensic data capable of automatically determining a character encoding type that is used in searching for data. The apparatus for searching for digital forensic data includes: an imaging module for generating an image file from a data source; a file system analysis module for analyzing a file system of the image file to generate file system analysis information; a search module for determining a search character encoding type based on the file system analysis information and searching for the data using the search character encoding type; and a user interface for receiving a command related to a search from a user, transmitting the received command to the file system analysis module and the search module, and outputting the search results to the user. In searching for digital forensic data, information on an operating system, a processor and an active character encoding type, which are actually used by a suspect, is extracted to determine a search character encoding type, so that accuracy and efficiency of searching for data are increased, and time, effort and money spent in determining a character encoding type are reduced.
Owner:ELECTRONICS & TELECOMM RES INST
Cost-efficient IOT forensics framework with blockchain
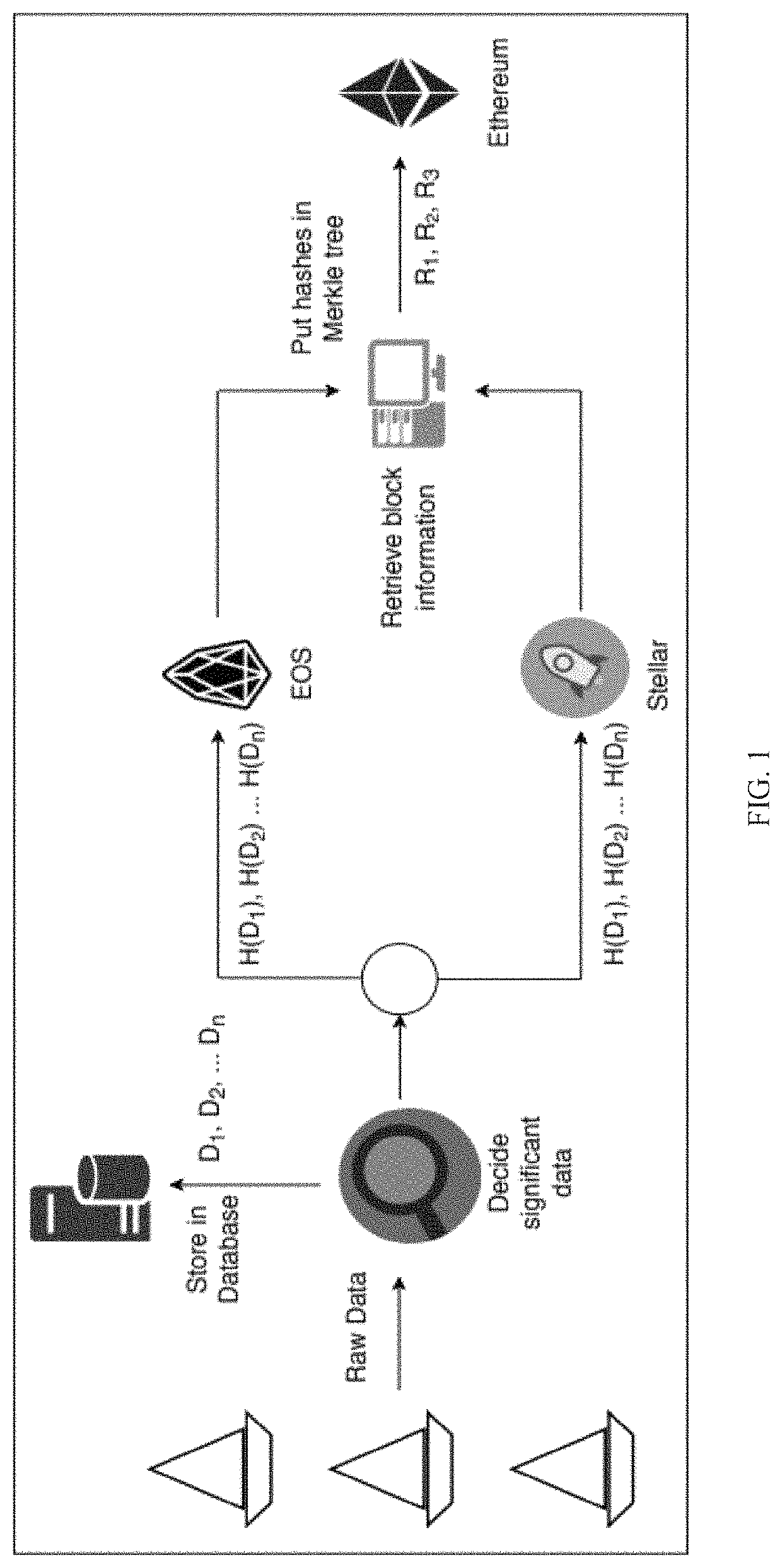
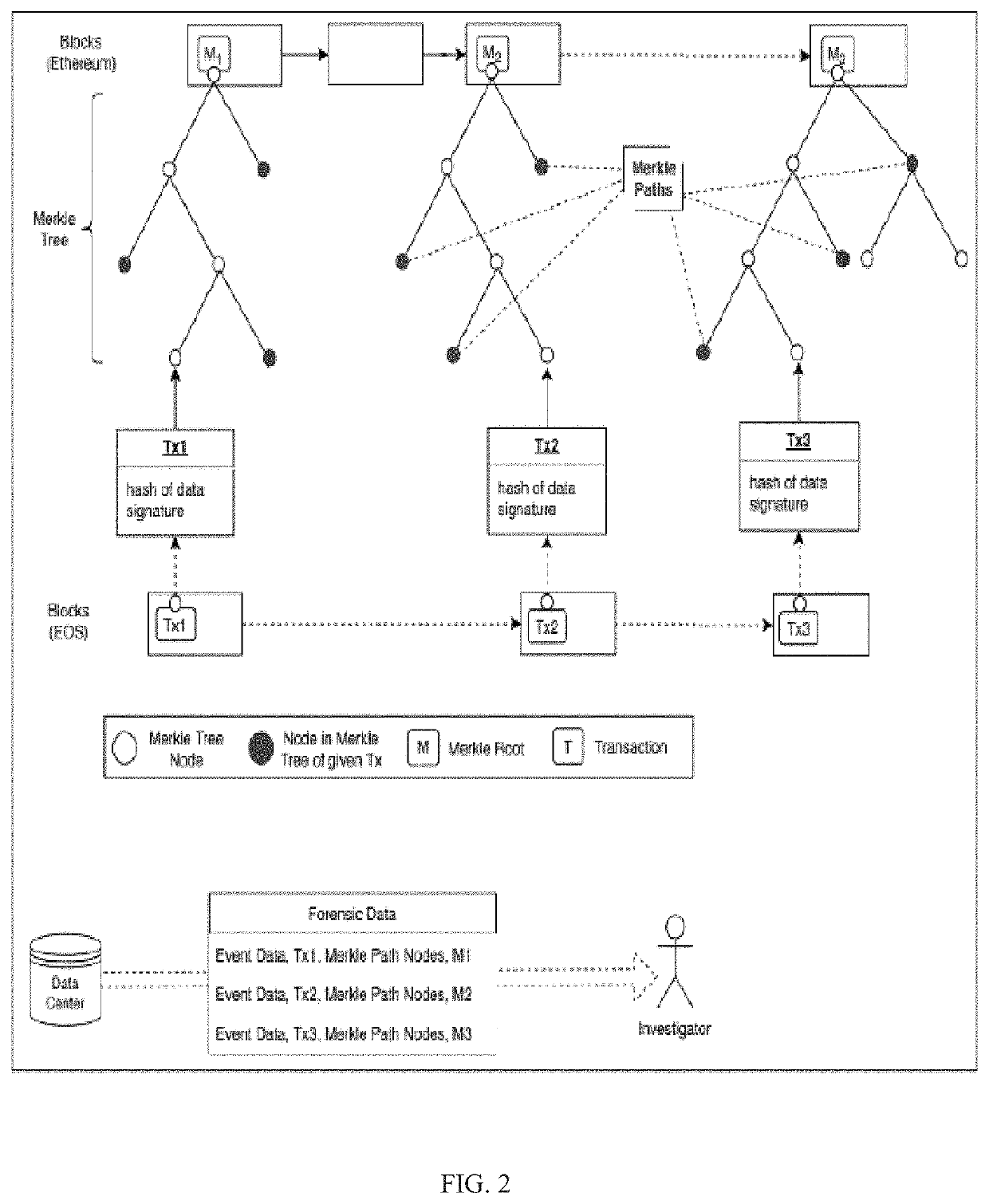
ActiveUS11128463B1Cost-effective and reliableCost effectiveEncryption apparatus with shift registers/memoriesUser identity/authority verificationDatabaseMerkle tree
A cost-effective and reliable digital forensics framework is provided by exploiting multiple blockchain networks in two levels. The selected data collected from sensors on a boat is sent to a remote company database and calculated hash of the data is saved in two blockchain platforms in the first level. Hash of each block is retrieved and inserted onto a Merkle tree on a periodic basis to be stored on another blockchain in the second level which is used to detect any error in the first level blockchains. A secure platform is created with the combination of several blockchains.
Owner:FLORIDA INTERNATIONAL UNIVERSITY
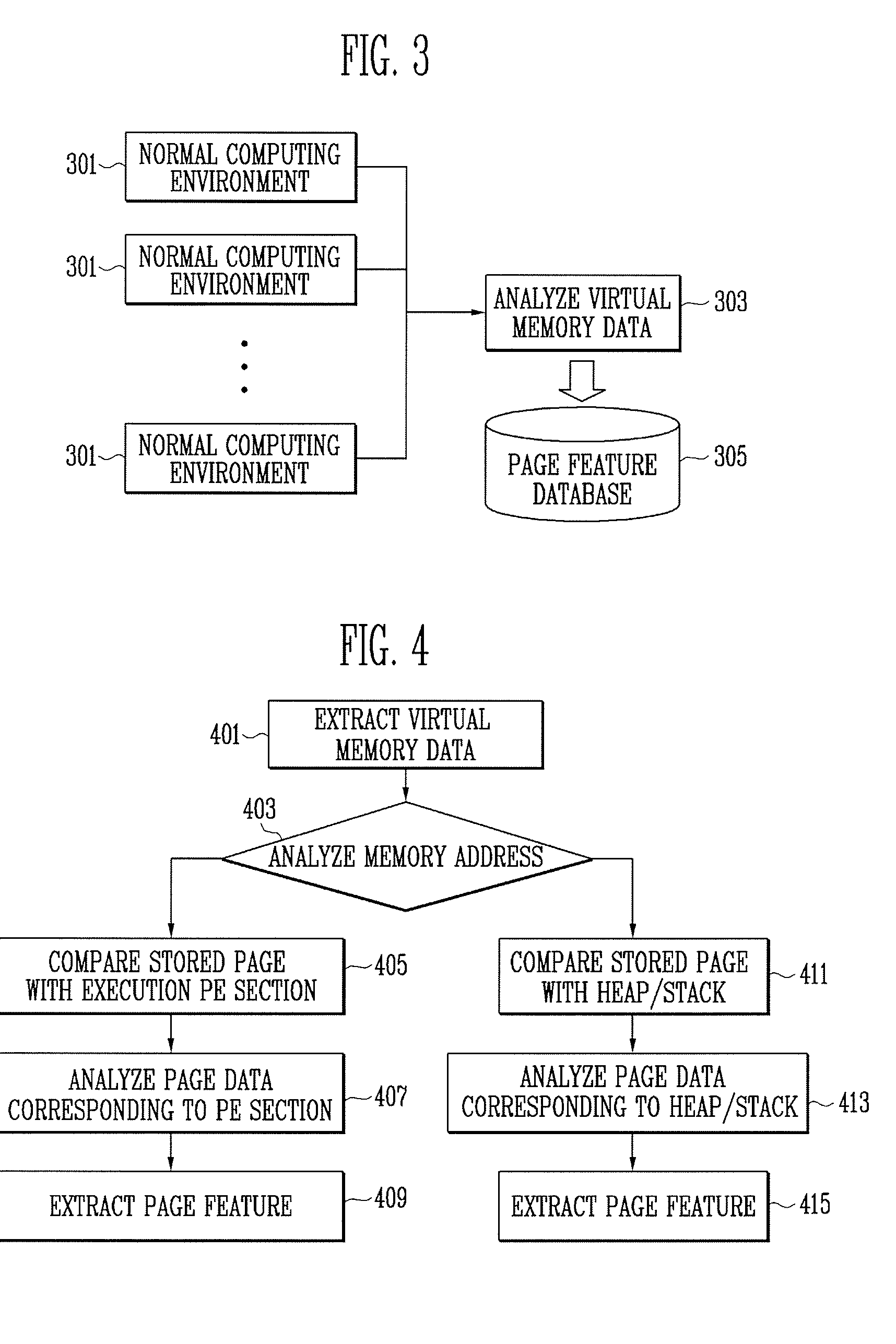
Method and apparatus for digital forensics
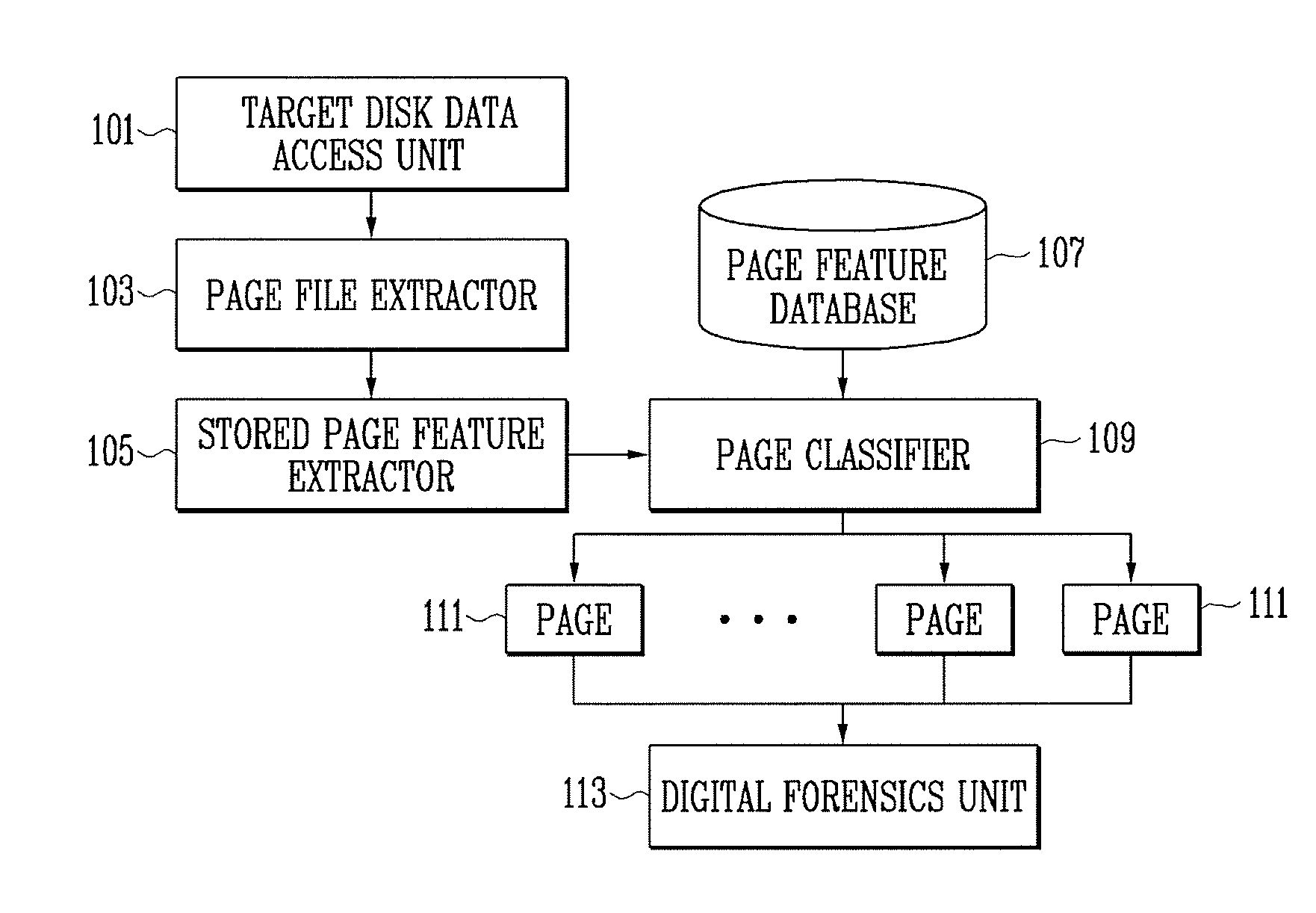
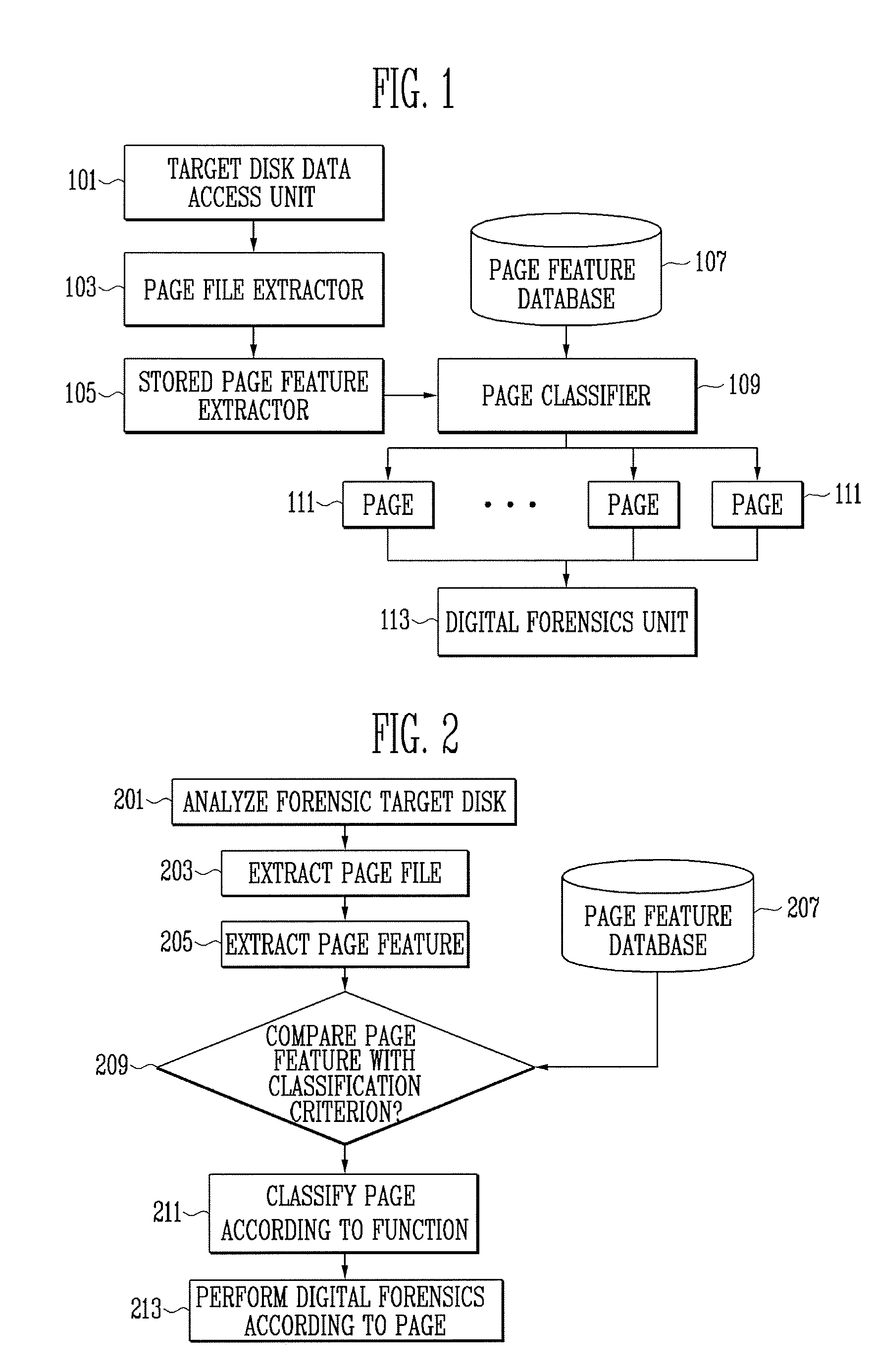
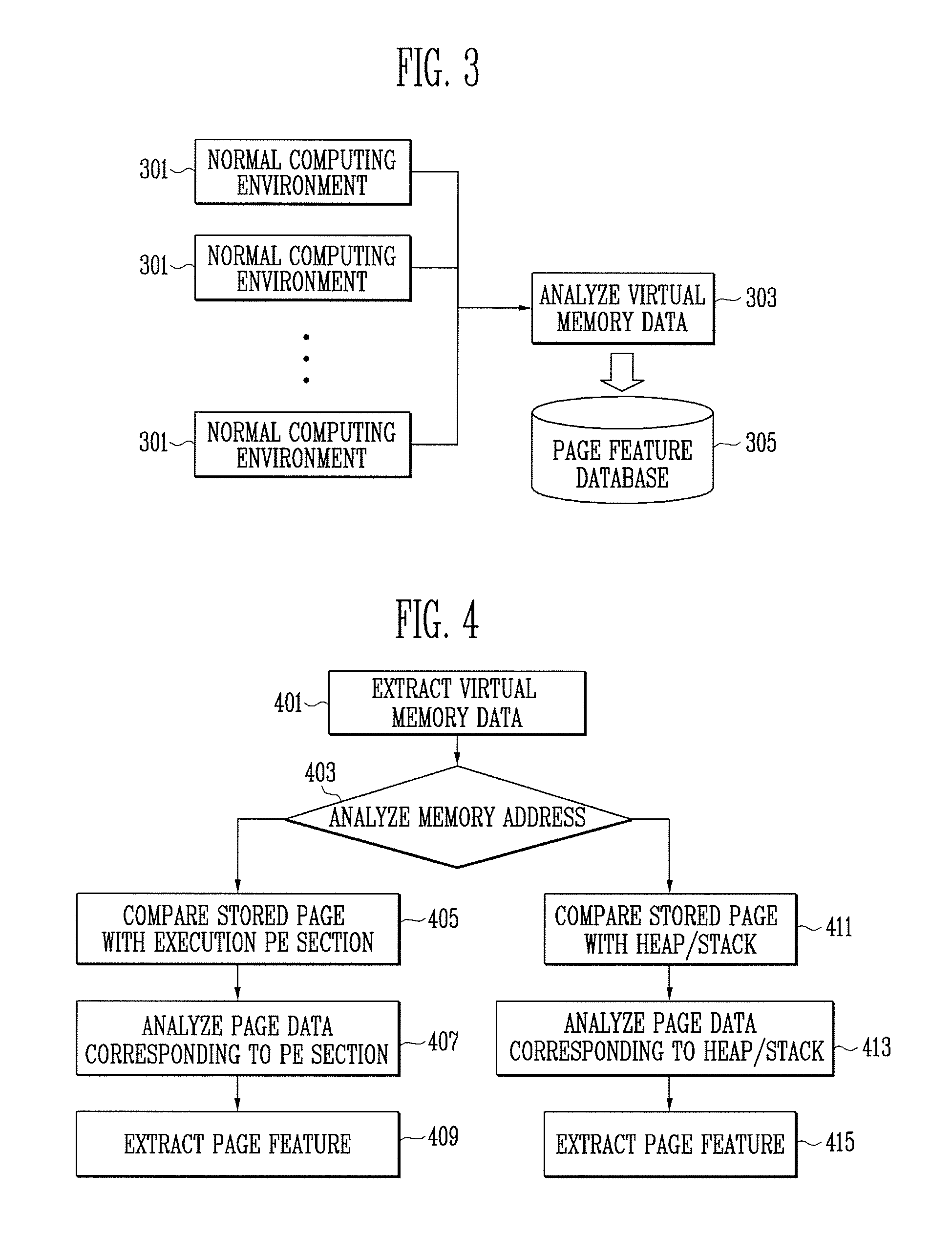
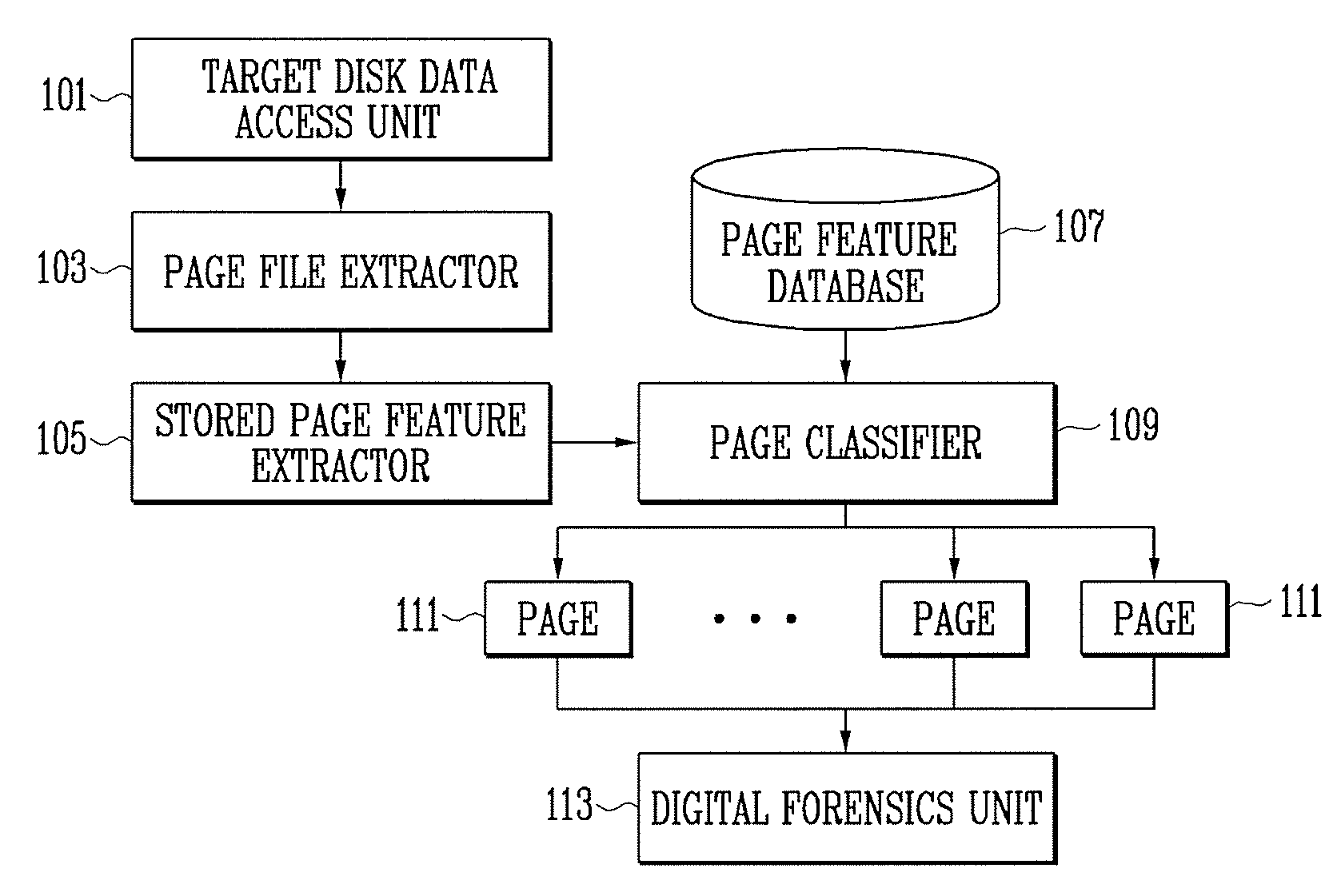
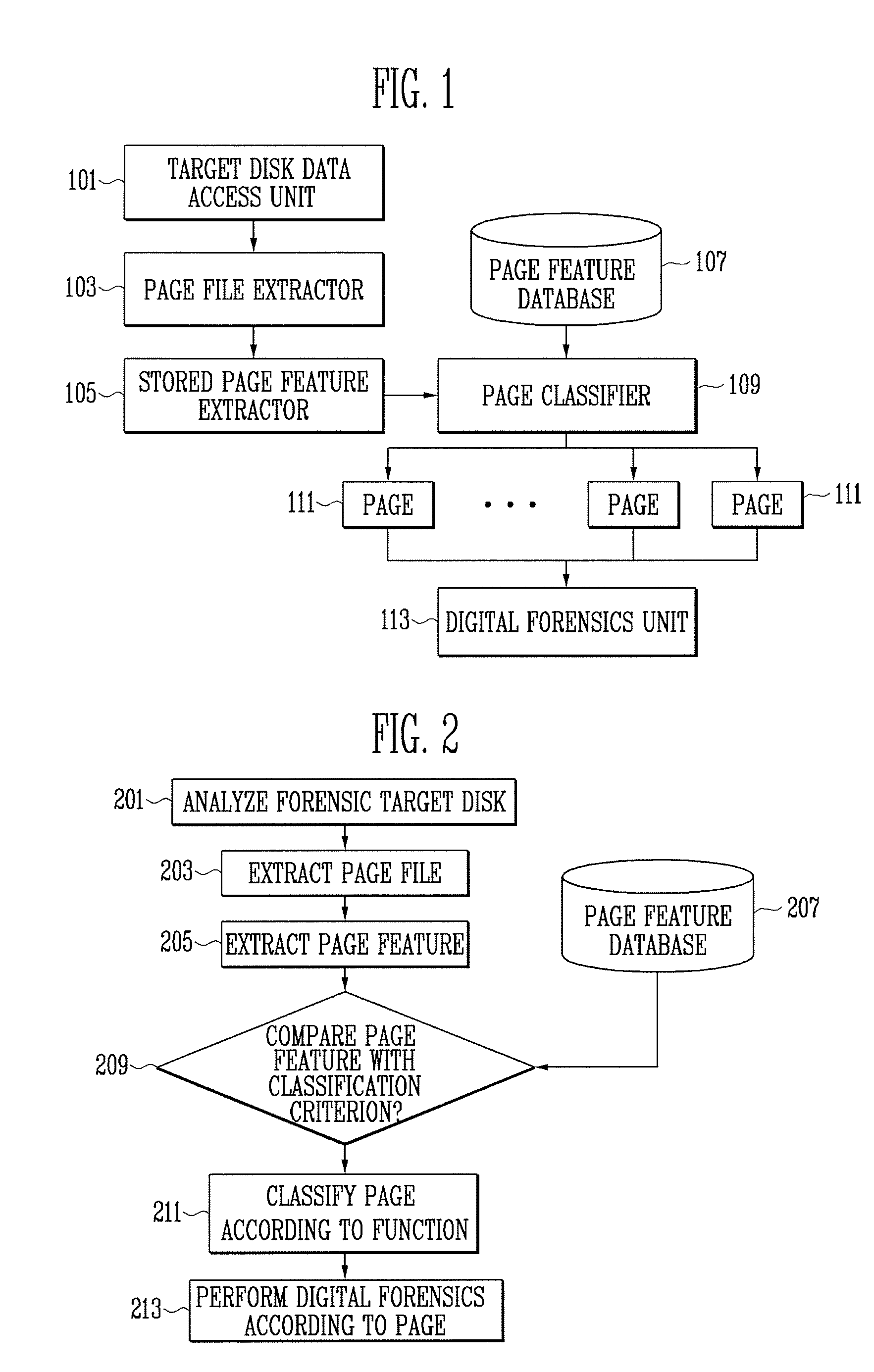
InactiveUS8145586B2Program control using stored programsDigital computer detailsFeature extractionDatabase
A method and apparatus for digital forensics are provided. The apparatus for digital forensics includes a page file extractor for extracting a page file stored in a target storage medium, a stored-page feature extractor for extracting features of pages stored in the extracted page file, a page classifier for comparing the extracted features of the pages with at least one predetermined classification criterion and classifying the pages according to the comparison results, and a digital forensics unit for performing digital forensics according to the classified pages. According to the method and apparatus, it is possible to perform digital forensics using only information of a page file.
Owner:ELECTRONICS & TELECOMM RES INST
YAFFS2 broken file reconstructing method based on history version
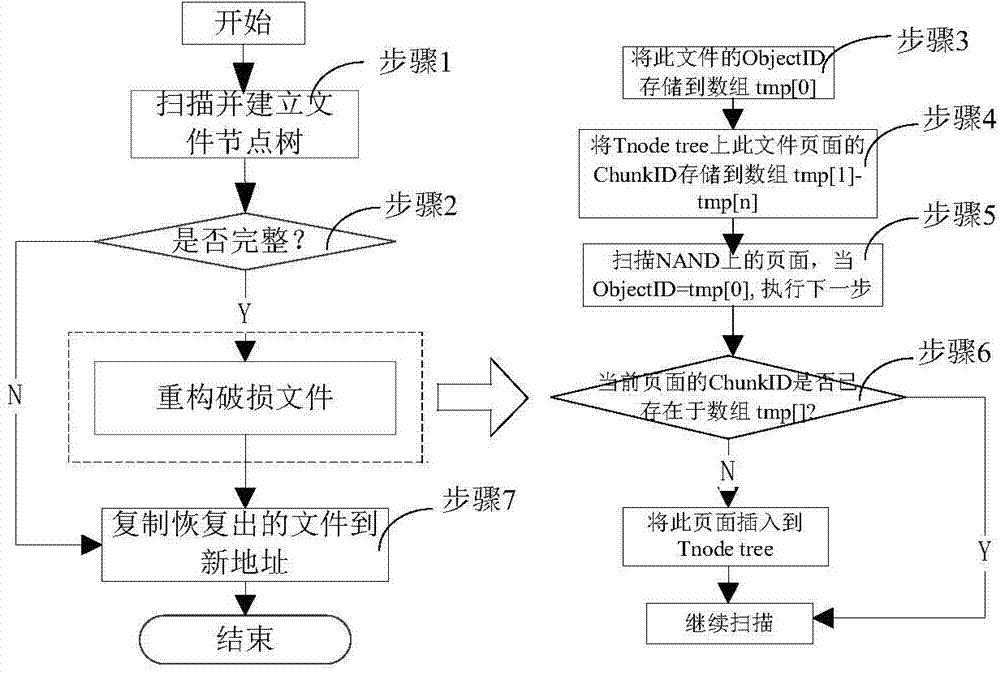
ActiveCN104778099AAchieve the purpose of recoveryMeet the requirements for accessing data stored on the deviceRedundant operation error correctionArray data structureFile system
The invention discloses a YAFFS2 broken file reconstructing method based on a history version. The YAFFS2 broken file reconstructing method comprises the following steps of scanning a NAND flash memory, and establishing a file node tree of the whole file system; judging whether the file is complete or not on the file node tree; storing the object number of the incomplete file into an array tmp[0]; storing the page numbers of all pages of the file on the file node tree into the tmp[1] -tmp[n]; scanning the pages on the NAND, and reading the yaffs_tags of each page; when the object number is tmp[0], implementing the next step; judging whether the object number of the current page exists in the array tmp[] or not; when the object number of the current page exists in the array tmp[], continuing to scan; when the object number of the current page does not exist in the array tmp[], inserting the page into the file node tree; when the incomplete file has been completed, copying all page data into the new specified address, and clearing the array tmp[]. The YAFFS2 broken file reconstructing method has the beneficial effects that the broken file is reconstructed according to the history version of the file, so as to realize the purpose of data recovery; in the digital forensics process, the requirements of completely obtaining the data stored in the equipment as much as possible is met.
Owner:黄炜
Systems and methods for provisioning digital forensics services remotely over public and private networks
ActiveUS9037630B2Eliminate needMultiple digital computer combinationsPlatform integrity maintainanceTTEthernetPrivate network
Provided are systems and methods for remote collection, preservation, and analysis of computer-based evidence in the course of conducting a network-based forensics or electronic discovery service. The challenge is to collect and analyze Electronically Stored Information (ESI) in a forensically sound manner over public and private networks. This is achieved via network-based forensics that may be conducted via an end user computer communicating directly with one or more subject computers across public or private networks, or it may be achieved via a “cloud computing” model whereupon the end user obtains, from the Internet, temporary use of shared resources, software, and information for the purpose of conducting digital forensics and eDiscovery upon subject computers.
Owner:SHANNON MATTHEW MARTIN +1
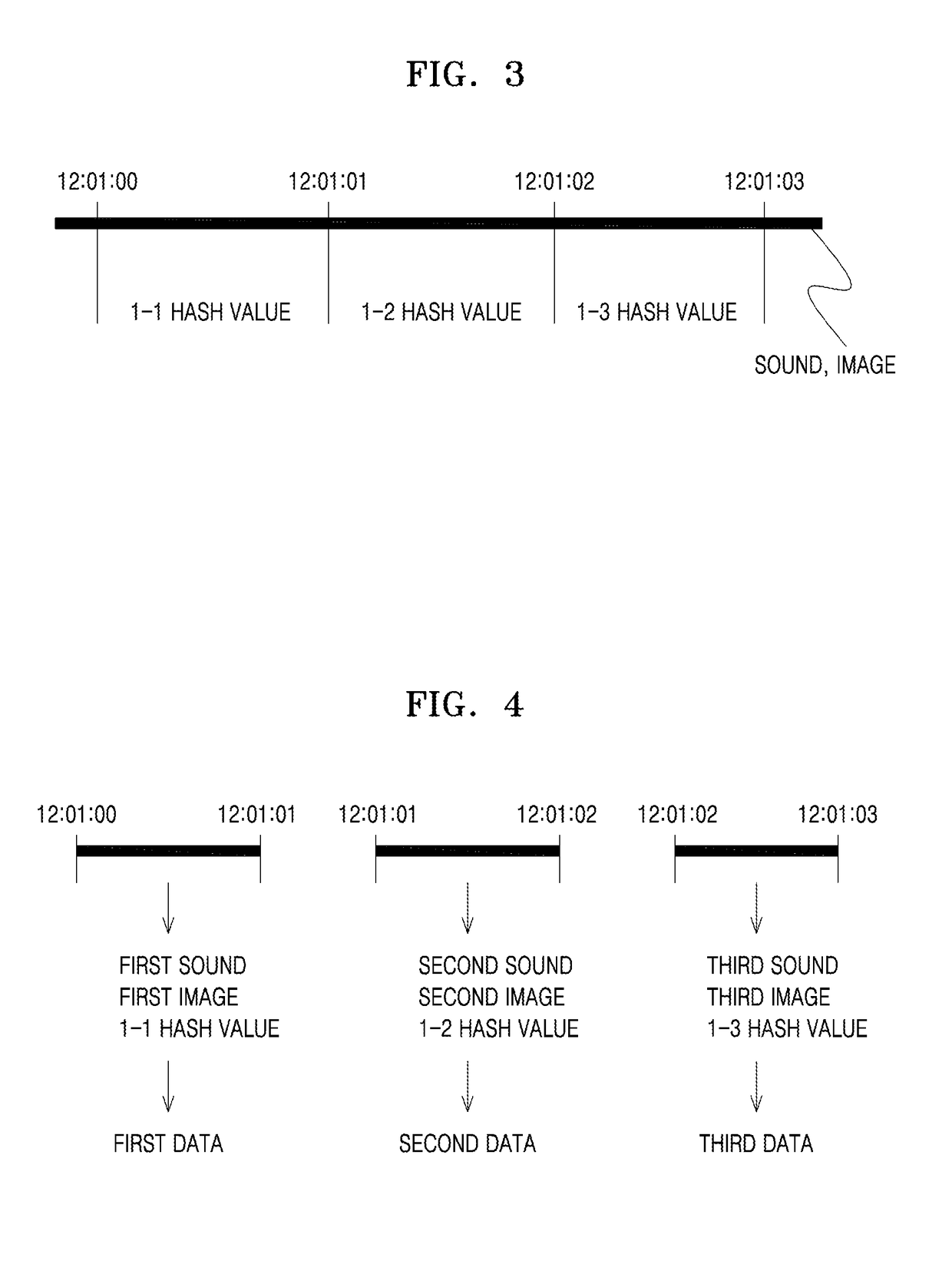
Digital forensic image verification system
InactiveCN108781270AReduce loadGuarantee authenticityBiometric pattern for forensic purposeTelevision system detailsComputer hardwareVerification system
A digital forensic image verification system, according to one embodiment of the present invention, is provided with: a photographing device comprising a photographing unit for generating an image, afirst hash value generation unit for generating a first hash value for the image, and a transmission unit for transmitting the image and the first hash value; and an image saving device comprising a reception unit for receiving the image and the first hash value from the photographing device, a second hash value generation unit for generating a second hash value for the image, and a control unit for comparing the first hash value and the second hash value with each other.
Owner:4DREAM +3
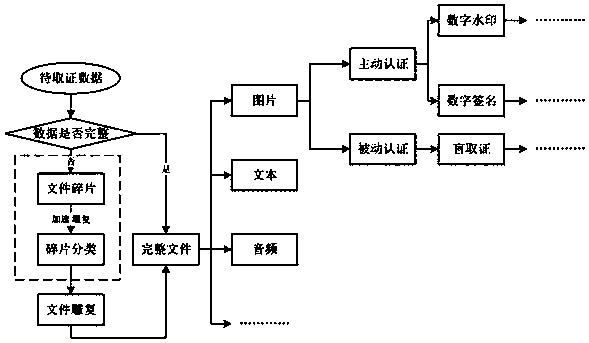
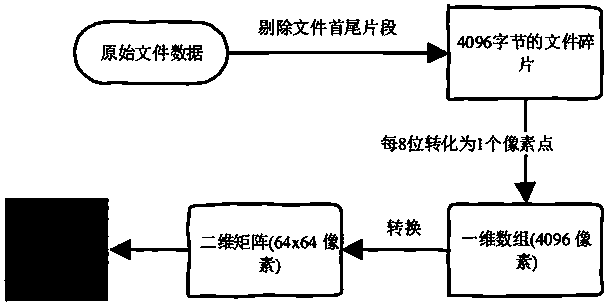
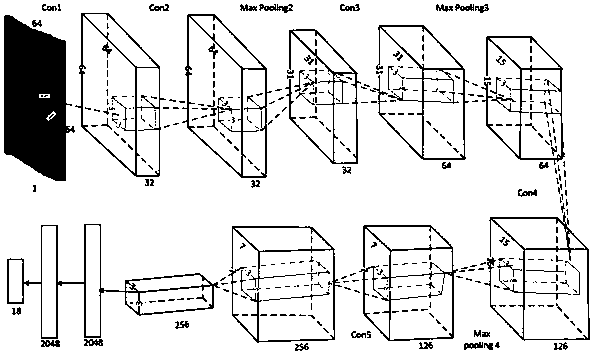
Digital forensic file fragment classification method based on digital image transformation and deep learning
InactiveCN108694414AImplement classificationCharacter and pattern recognitionNeural architecturesClassification methodsCompressibility
The invention provides a digital forensic file fragment classification method based on digital image conversion and deep learning. Firstly, file fragments are converted to grayscale images, and then deep learning is utilized to extract more hidden features of the images to improve performance of file fragment classification. The more hidden features include different texture features, random features and compressibility used for classification. Deep learning uses a modified and optimized CNN model. A first convolutional layer of the model uses a 1x1 ratio convolutional kernel, and the same uses many pipes to enable a network structure to be complicated. All layers have different-numbers-and-scales filtering kernels, and thus feature maps best matching the classification model are obtainedby training through gradient descents and reverse training. According to the method, high-dimensional features of the file fragments are extracted through utilizing the advantages of local connectionand weight sharing of a CNN, and the scheme can also realize high-precision fragment classification for files such as composite files and compressed files which are not easy to classify in previous schemes.
Owner:HARBIN INST OF TECH SHENZHEN GRADUATE SCHOOL
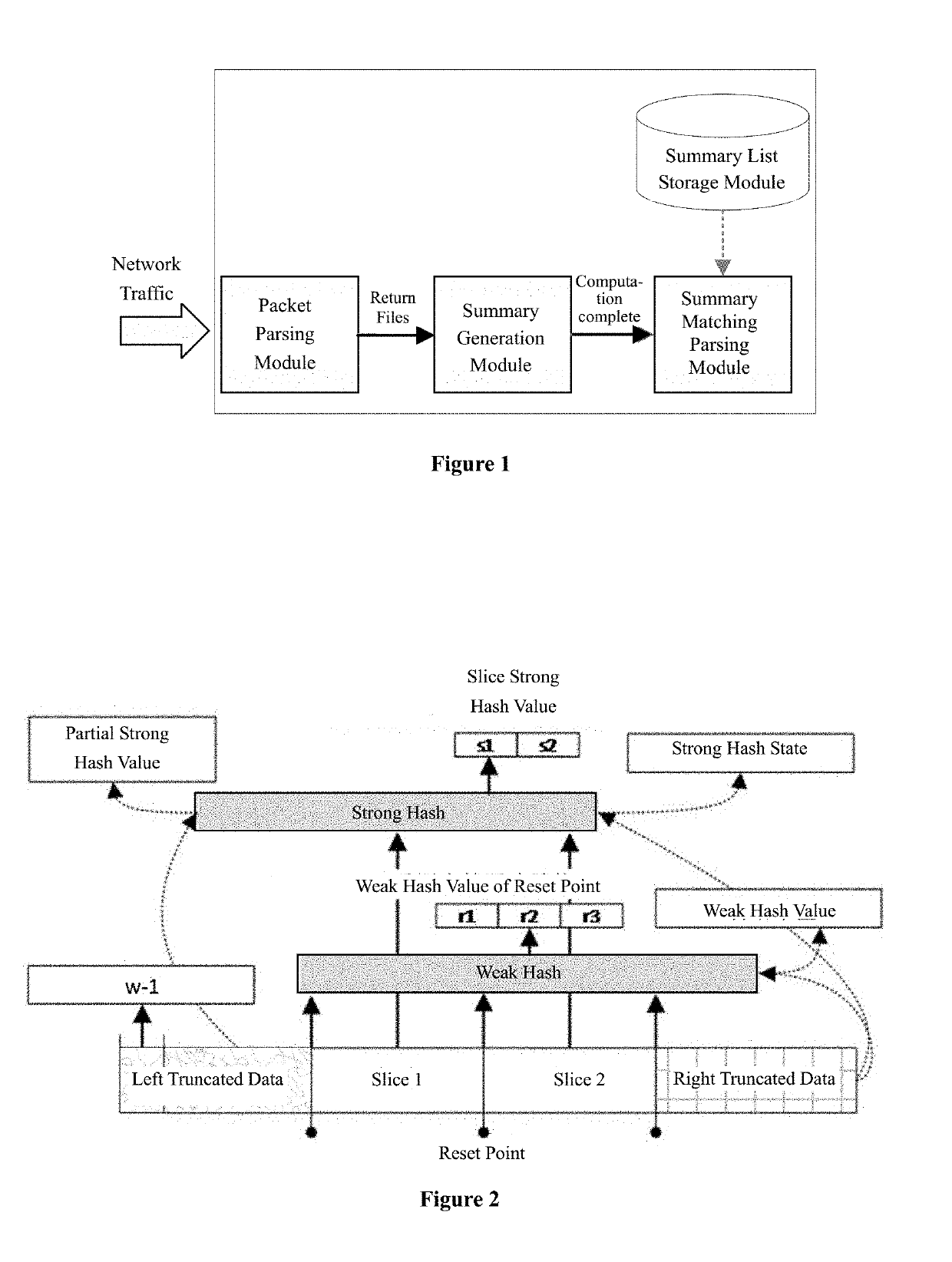
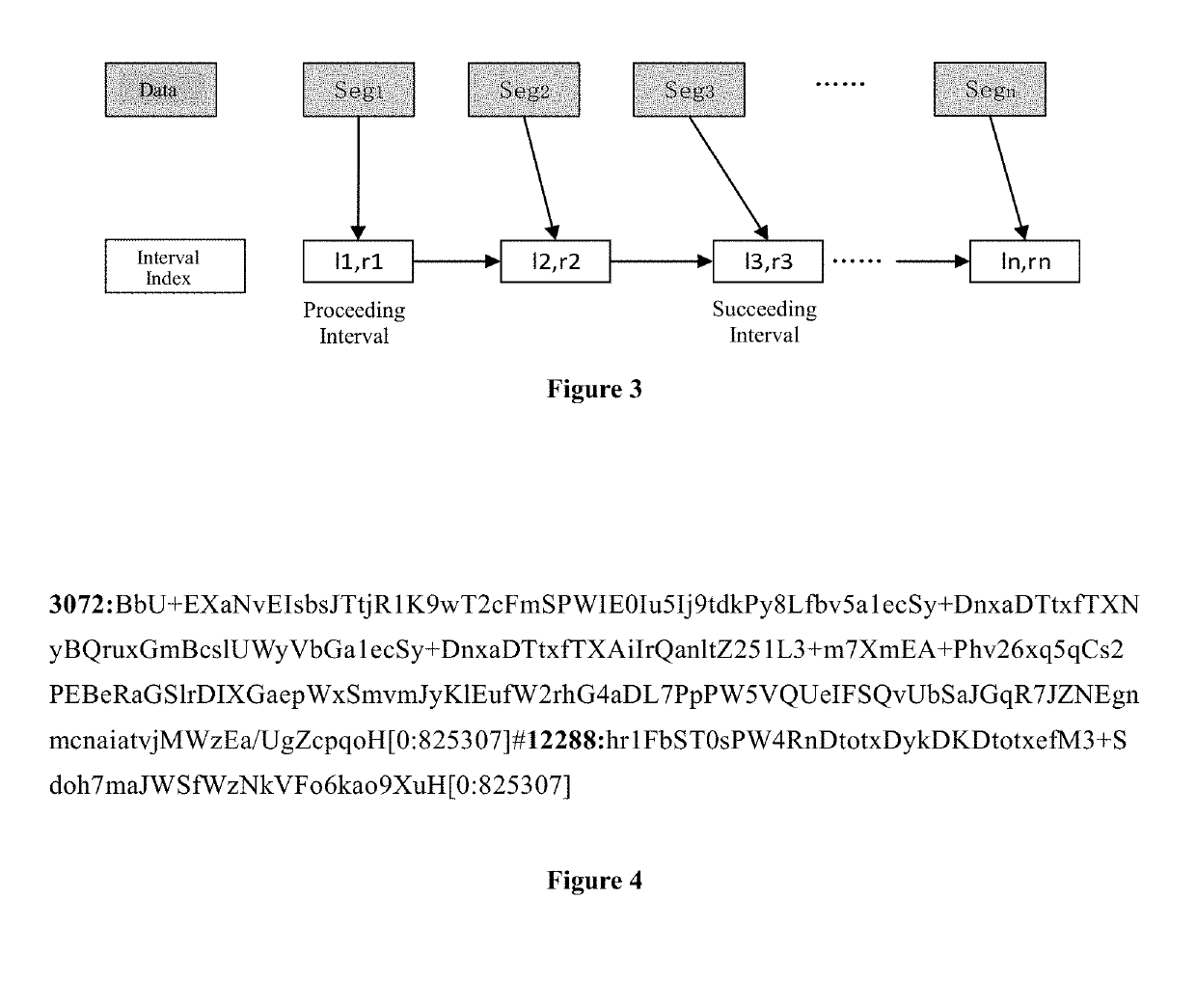
Method, system, and apparatus for monitoring network traffic and generating summary
ActiveUS20190253436A1Efficiently findEliminate needDigital data information retrievalUser identity/authority verificationStreaming dataAlgorithm
The present invention provides a method, a system, and a device for a hash generation and network traffic detection. It uses a method of storing intermediate calculation results to perform hash calculation for streaming data, and uses a matrix multiplication operation as a strong hash algorithm to reduce memory occupation. The present invention can generate hash in real time in the case of streaming data comprising defects, unordered, and overlapping, which is suitable for detecting files from network traffic, and is applicable to virus detection, intrusion detection, data anti-leakage, network content review, digital forensics, digital rights protection, and other fields.
Owner:INST OF INFORMATION ENG CHINESE ACAD OF SCI
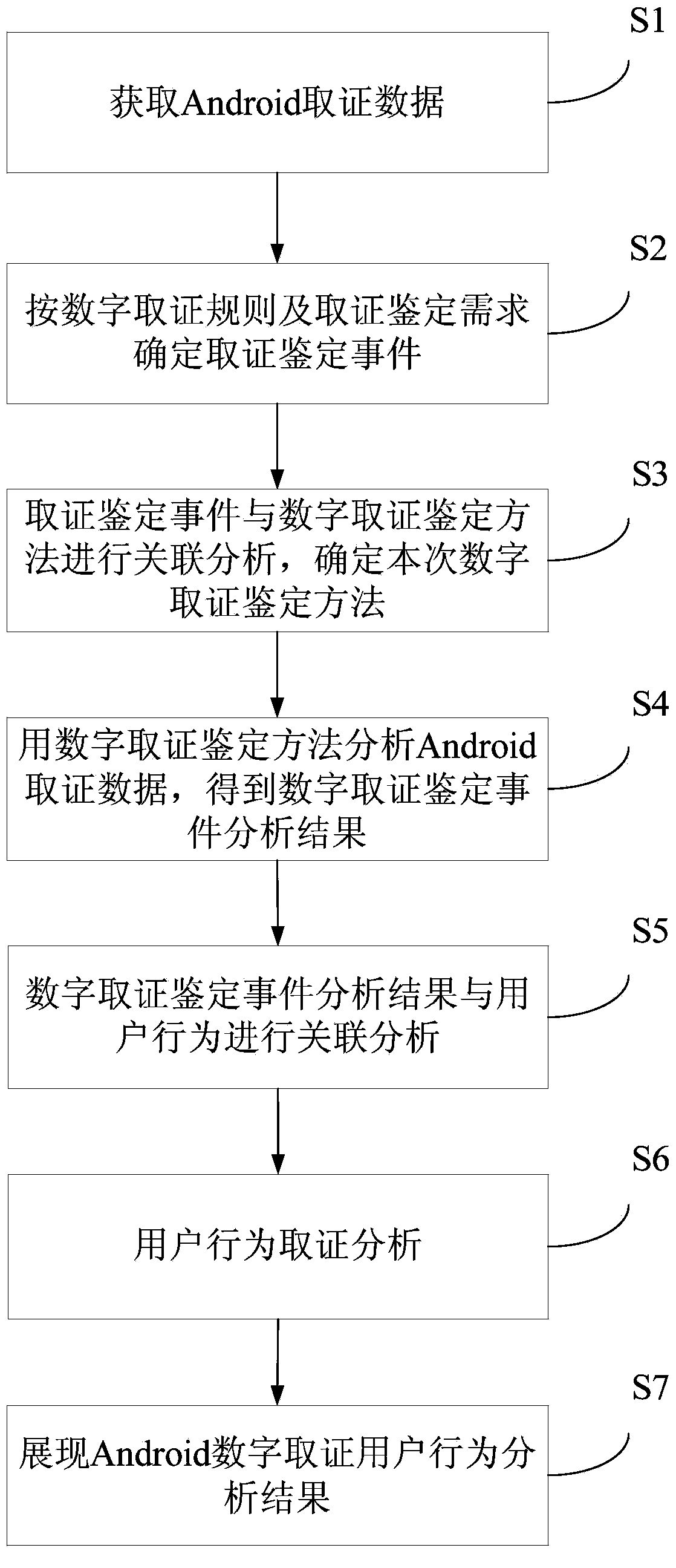
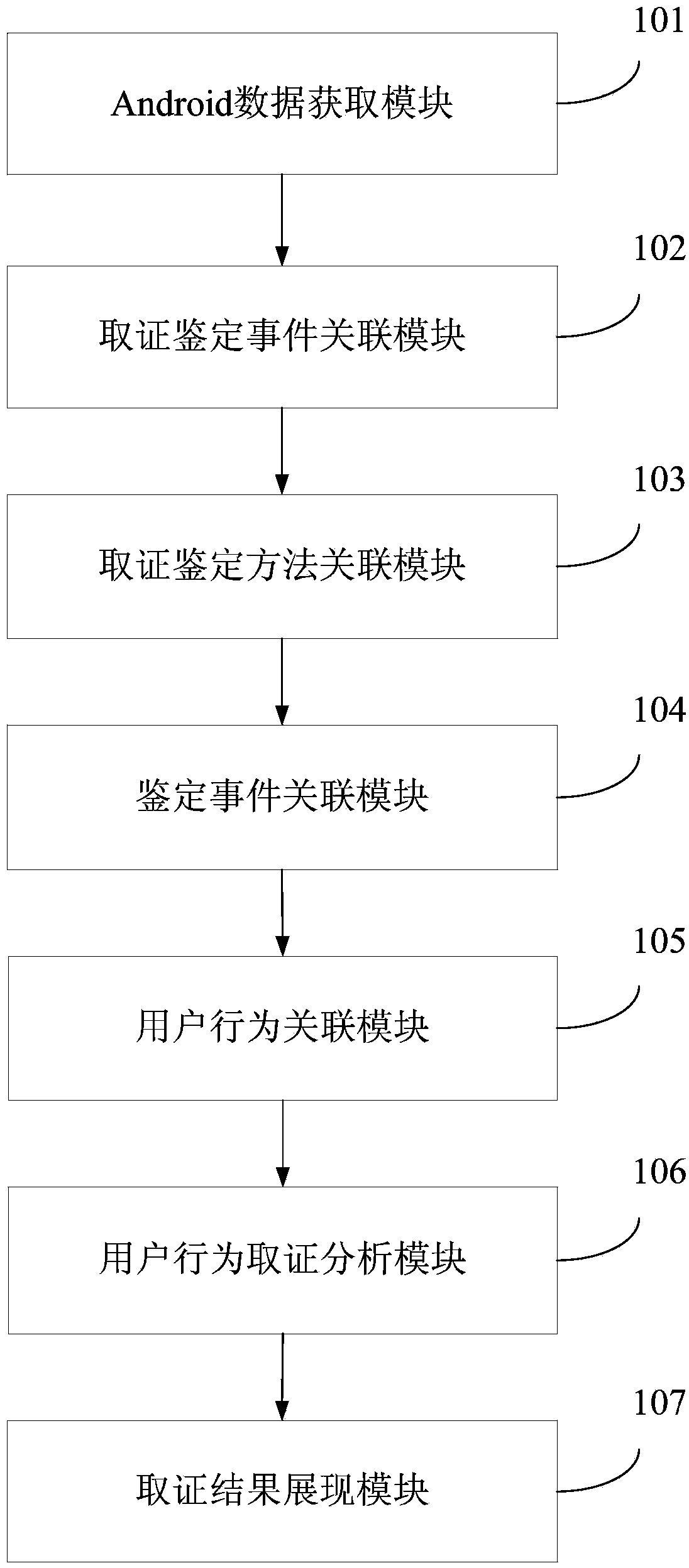
Android digital forensics-oriented user behavior analysis method and system
ActiveCN103853933AStandardize the forensic analysis processImprove efficiencySpecial data processing applicationsData dredgingAndroid forensics
The invention provides an Android digital forensics-oriented user behavior analysis method. The method comprises the following steps: S1, acquiring Android forensics data; S2, determining a forensics identification event according to a digital forensics rule and the forensics identification requirement; S3, performing correlation analysis on the forensics identification event and a digital forensics identification method, and determining the digital forensic identification method; S4, analyzing the Android forensics data by using the digital forensic identification method, and obtaining a digital forensic identification event analysis result; S5, performing correlation analysis on the digital forensic identification event analysis result and a user behavior, and obtaining a correlation analysis result; S6, performing forensics analysis on the user behavior according to the correlation analysis result by using a data mining method, and obtaining an Android digital forensic user behavior analysis result; and S7, showing the Android digital forensic user behavior analysis result. According to the method, the Android digital forensic user behavior analysis result is realized.
Owner:和宇健康科技股份有限公司
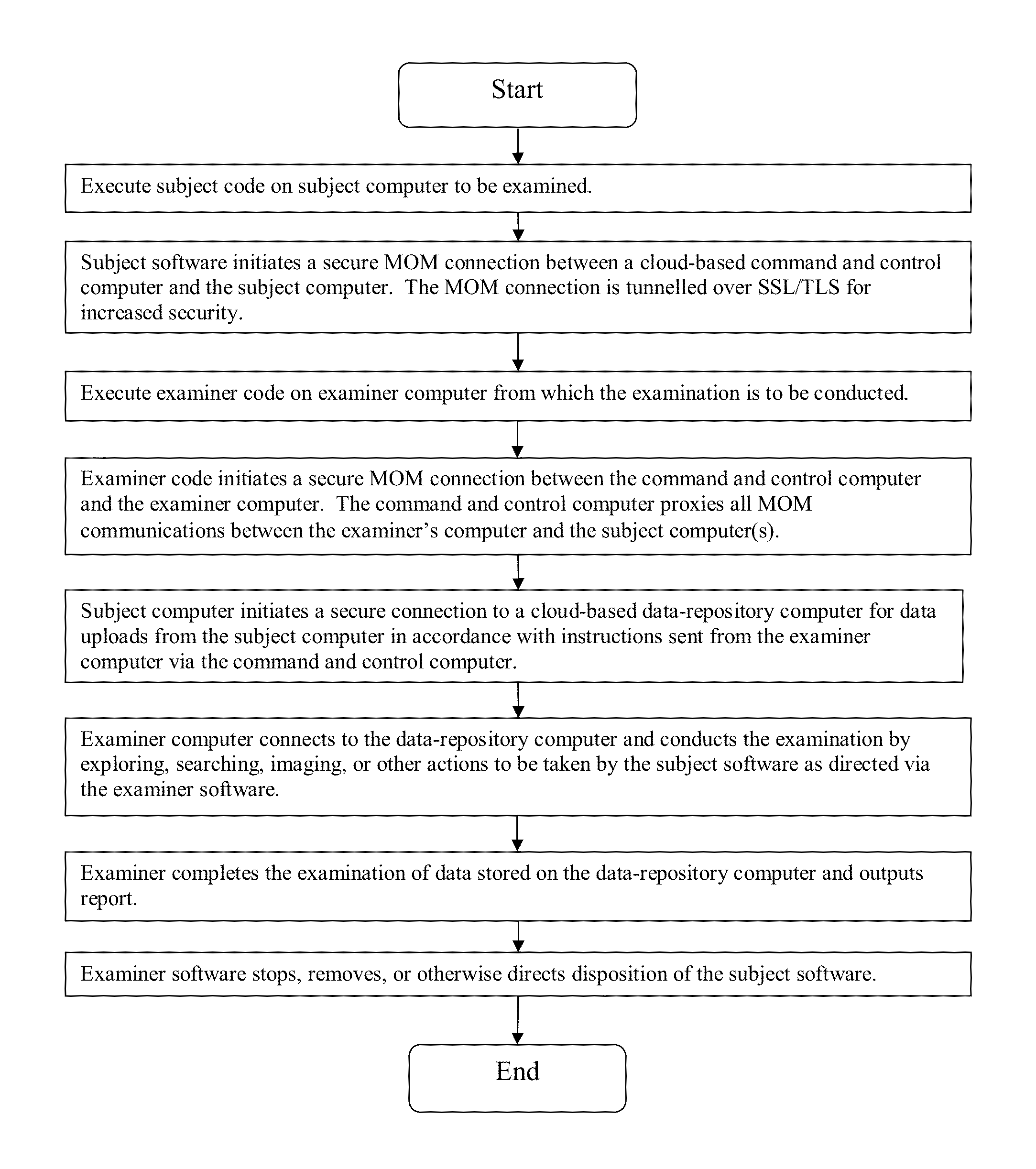
Systems and methods for remote forensics and data security services over public and private networks
Provided are systems and methods for employing remote forensics and data security services over public and private networks by obtaining full access to digital data from the non-transitory computer-readable media of geographically dispersed computing devices such that the entire physical or logical media from each device is fully accessible to one or more user computers over the network. This is achieved via WebSocket technology implemented in point-to-point connection configurations, WebSocket technology implemented in network based digital data software switch configurations, and in combinations thereof. Application of these systems and methods are generally employed for the purpose of conducting remote examinations and remediation efforts upon electronic data comprising non-transitory computer-readable media on a network accessible computing device. As a few examples, the application of these systems and methods may be applied for the purposes of data sharing, remote computer support, data recovery, data loss prevention, data backup, eDiscovery (electronic discovery), digital forensics, remote monitoring, audit compliance, incident response, security incident remediation, and mobile device data management purposes. Examples of computing devices include, but are not limited to, workstations, laptops, tablets, smart phones, network routers, network switches, mobile computing devices, electronic sensors, and any device comprising the Internet of Things (IoT).
Owner:SHANNON MATTHEW MARTIN +1
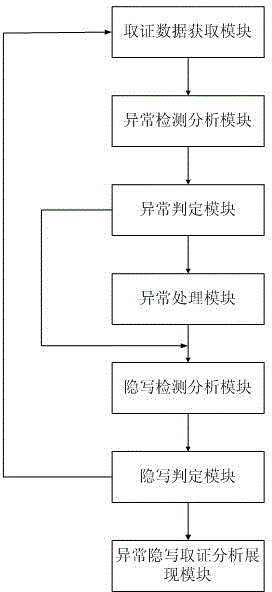
Digital forensics-oriented anomaly steganalysis method and system
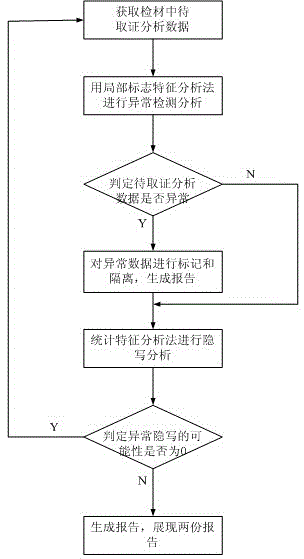
ActiveCN104021227AImprove steganalysis speedHigh precisionDigital data protectionPlatform integrity maintainanceSteganalysisAnalysis data
The invention discloses a digital forensics-oriented anomaly steganalysis method and a system. The method comprises the following steps: 1, obtaining to-be-obtained analyze data in a detection material; 2, carrying out analysis of anomaly on the to-be-obtained analyze data; 3, judging whether the to-be-obtained analyze data is abnormal or not; 4, marking anomaly data as suspicion, moving the suspicion to an observation region to be isolated, and generating an anomaly detection report; 5, carrying out anomaly steganalysis on the to-be-obtained analyze data or the suspicion; 6, judging the probability of the data object analyzed in 5 with abnormal steganalysis; and 7, generating an anomaly steganalysis evaluating report and revealing an anomaly analytic result and an anomaly steganalysis evaluating report. The method disclosed by the invention jointly applies a characteristic analysis method and a method for statistical analysis method to carry out anomaly steganalysis on the to-be-obtained analyze data, so that a digital forensics-oriented anomaly steganalysis scheme can be effectively satisfied, thereby improving the steganalysis speed in the digital forensics process and enhancing the precision of steganalysis.
Owner:麦永浩
Digital forensic image verification system
InactiveUS20180373894A1Reduce load appliedReduce loadBiometric pattern for forensic purposeTelevision system detailsImaging equipmentVerification system
A digital forensic image verification system according to an embodiment of the present disclosure includes an imaging device having a imaging unit configured to produce an image, a first hash value generator configured to generate a first hash value for the image, and a transmitting unit configured to transmit the image and the first hash value; and an image storage device having a receiving unit configured to receive the image and the first hash value from the imaging device, a second hash value generator configured to generate a second hash value for the image, and a controller configured to compare the first hash value and the second hash value with each other.
Owner:HANWHA TECHWIN CO LTD +1
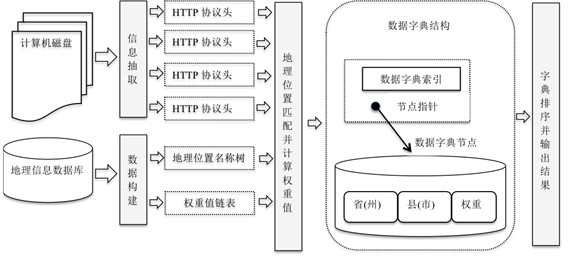
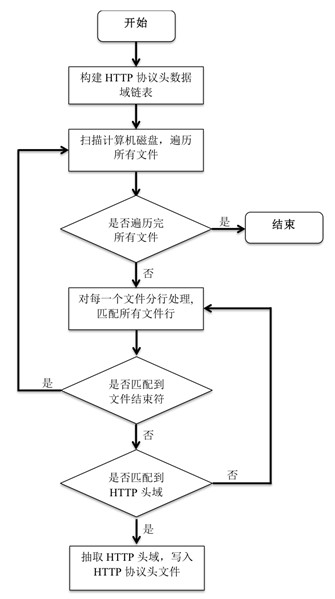
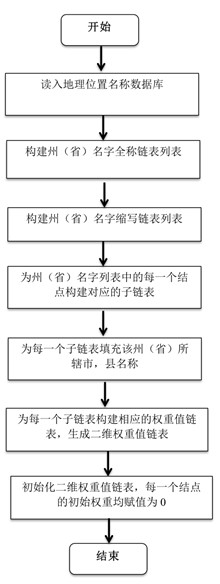
Method for locating geographical position of disk based on protocol head of hyper text transfer protocol (HTTP)
InactiveCN102571976AEasy to identifyTransmissionSpecial data processing applicationsTheoretical computer scienceData domain
The invention discloses a method for locating a geographical position of a computer hard disk. The method comprises the following steps of: extracting protocol head information of a hyper text transfer protocol (HTTP) in the computer hard disk; constructing a geographical position name tree and a two-dimensional weight value linked list, scanning a Cookie data area of the HTTP protocol head, traversing the geographical position name tree for matching the geographical position name tree with each Cookie data area, if the matching succeeds, performing add operation on weights of nodes; constructing a data dictionary, and sequencing the data dictionary according to the sizes of weight values; and scanning a Data area in the HTTP protocol head, and acquiring the time when the computer hard disk is located at a certain historical position, so that strong physical evidence can be provided for criminal investigation work. According to the method, manual intervention is not required in a forensics process, disk scanning, calculation and final result generation can be automatically realized, operating cost is low, deployment is easy, and the method is applied to the field of computer hard disk digital forensics and has a wide application prospect.
Owner:SICHUAN UNIV
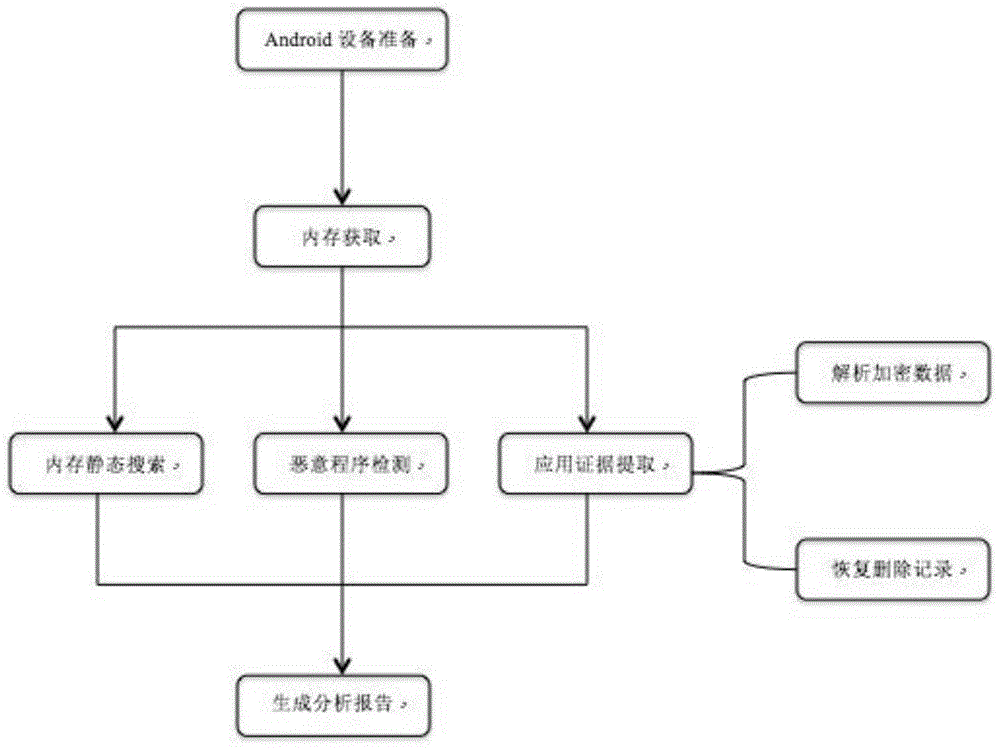
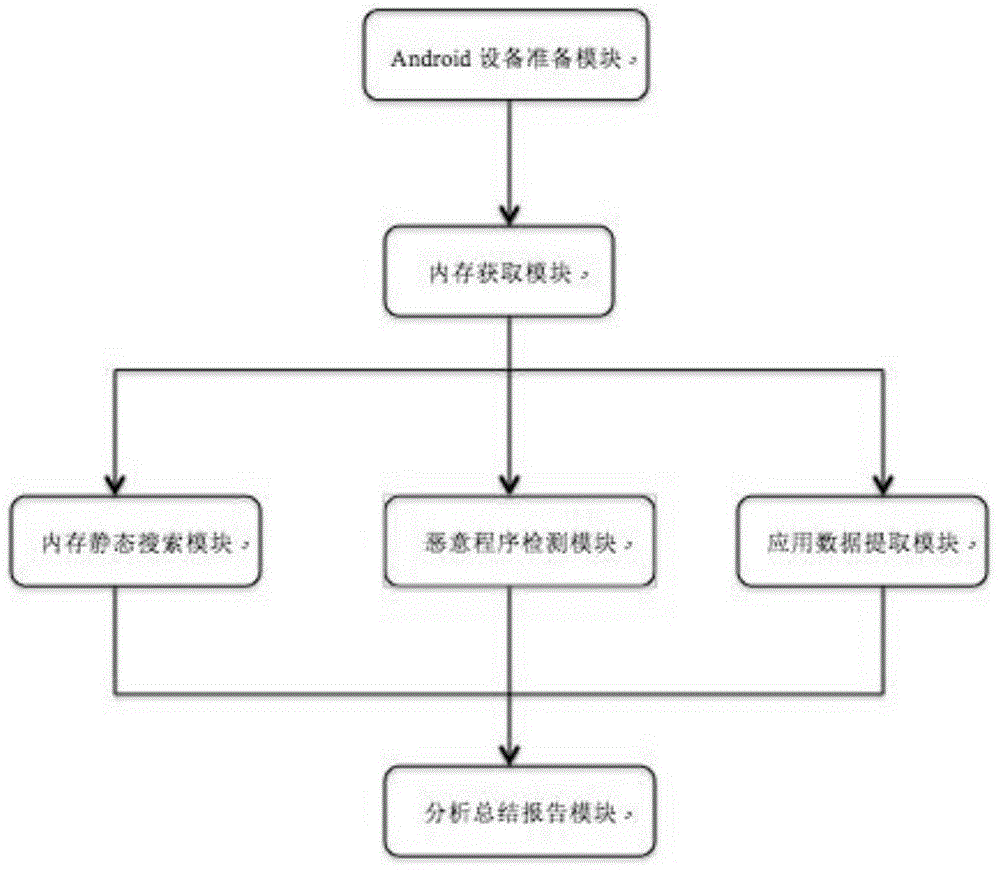
Digital forensic method and system based on Android memory dump technology
InactiveCN104932838AImplement extractionSolve getting encryptedInput/output to record carriersPlatform integrity maintainanceMemory profilingOpen port
The invention discloses a digital forensic method and system based on Android memory dump technology. The system comprises the following steps: determining that the Android equipment has been rooted, and starting a USB debugging function; dumping a physical memory of the Android equipment; statically searching the dumped Android memory to excavate sensitive data; dynamically analyzing the physical memory, listing information such as running processes, open ports and loading modules of the equipment, detecting whether rogue program is existent in the equipment; analyzing structure features stored in the memory through application program data, and extracting locally encrypted and stored application data; detecting different type data of the application program, namely: text, voice, pictures and the like, and attempting to recover deleted data in the memory; searching user information such as username, password and the like in the memory to detect whether the application program can safely protect user privacy; and generating a digital forensic summary report according to the memory analysis result. Through the adoption of the method and system disclosed by the invention, the effectiveness and completeness of the digital forensic at a mobile terminal are improved, and the extensive technical and market application value are realized.
Owner:NANJING UNIV OF POSTS & TELECOMM
Systems and methods for cloud-based collection and processing of digital forensic evidence
Systems and methods for conducting a cloud-based forensic investigation of electronically-stored information are provided. The system includes an investigation requestor device configured to request a forensic investigation including selecting search criteria for the investigation, at least one remote system of the target, wherein the at least one remote system comprises electronically-stored information; a cloud server for storing forensic artifacts collected from the at least one remote system, wherein the forensic artifacts are collected based on the search criteria; and a cloud-based evidence-processing service configured to analyze the forensic artifacts and generate an initial report.
Owner:MAGNET FORENSICS
Method and apparatus for digital forensics
InactiveUS20090299935A1Program control using stored programsMemory adressing/allocation/relocationDatabaseDigital forensics
A method and apparatus for digital forensics are provided. The apparatus for digital forensics includes a page file extractor for extracting a page file stored in a target storage medium, a stored-page feature extractor for extracting features of pages stored in the extracted page file, a page classifier for comparing the extracted features of the pages with at least one predetermined classification criterion and classifying the pages according to the comparison results, and a digital forensics unit for performing digital forensics according to the classified pages. According to the method and apparatus, it is possible to perform digital forensics using only information of a page file.
Owner:ELECTRONICS & TELECOMM RES INST
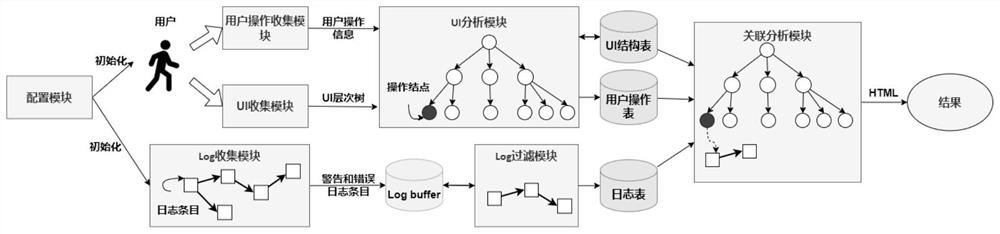
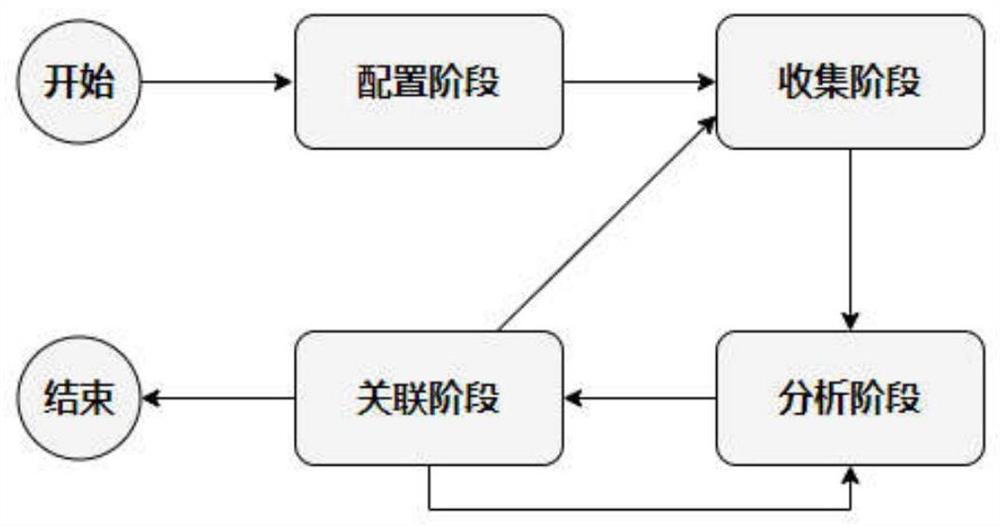
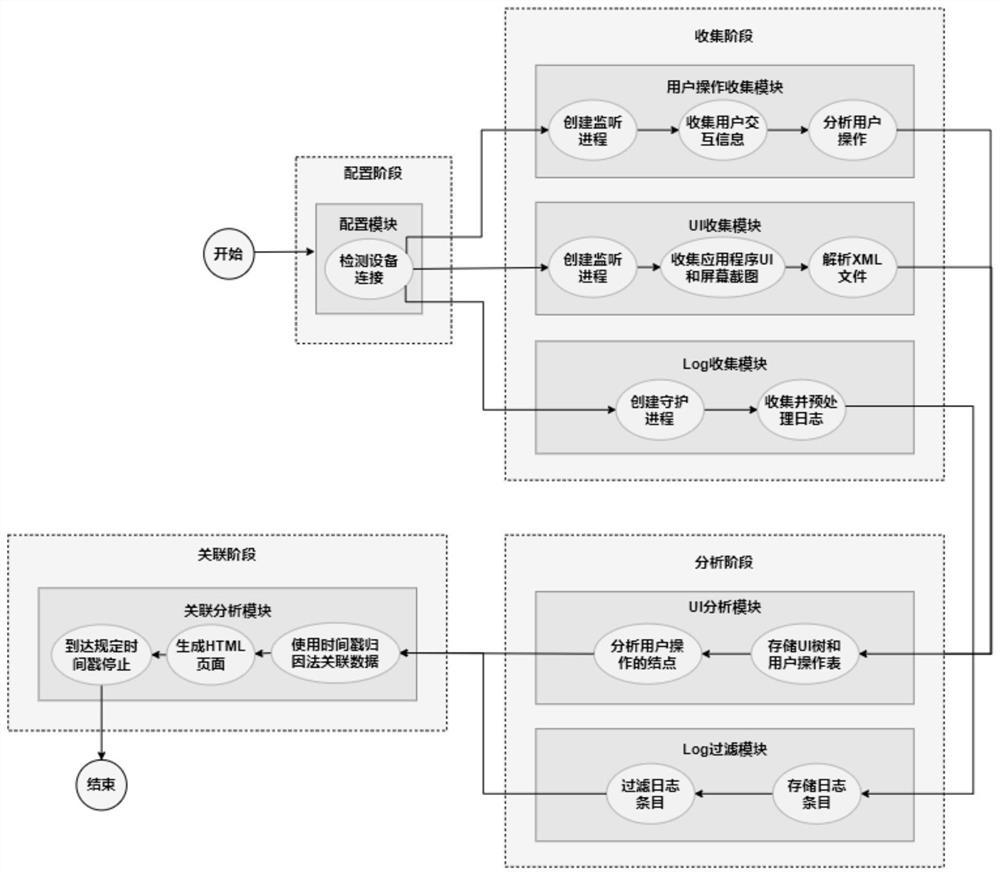
Visual evidence obtaining system for android attack scene reconstruction and implementation method
PendingCN113569234AEasy to understandImprove visualizationDigital data information retrievalPlatform integrity maintainanceAttackSoftware engineering
The invention provides a visual evidence obtaining system for android attack scene reconstruction and an implementation method. The system comprises a configuration module, a user operation collection module, a UI collection module, a UI analysis module, a Log collection module, a Log filtering module and a correlation analysis module. The invention provides a top-down digital forensics tool for Android equipment, high-level application program UI elements are combined with low-level security related system events, and an attack scene is reconstructed. Compared with a previous scene reconstruction method, the method can explain the nature of attacks from a global perspective, and has fine granularity and easy-to-understand context semantics. The system is developed on the basis of a built-in Android debugging bridge toolkit, and can be deployed and run when any Android system runs. The system is easy to deploy, Android equipment does not need to be modified, and compared with an existing method, the method is safer and more flexible, and the visualization effect of a scene reconstruction result is better.
Owner:NANJING UNIV
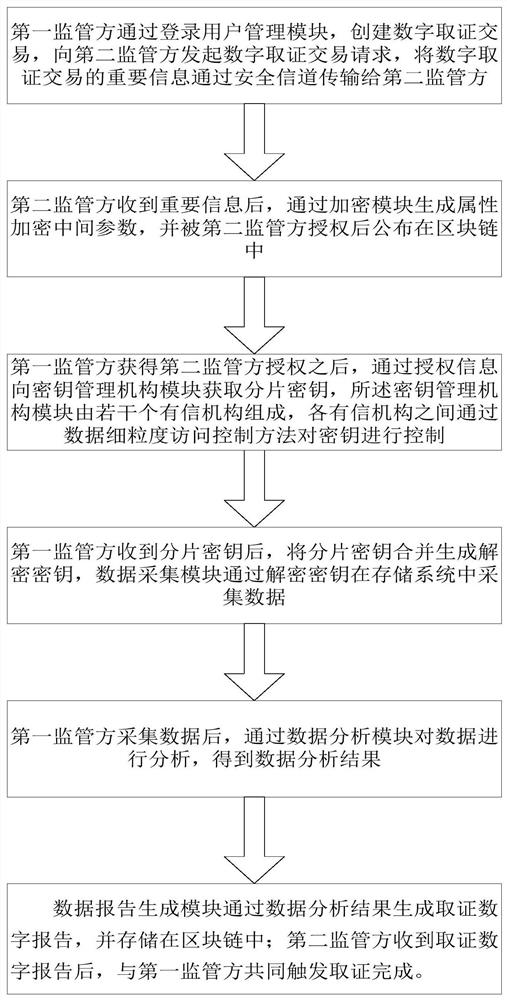
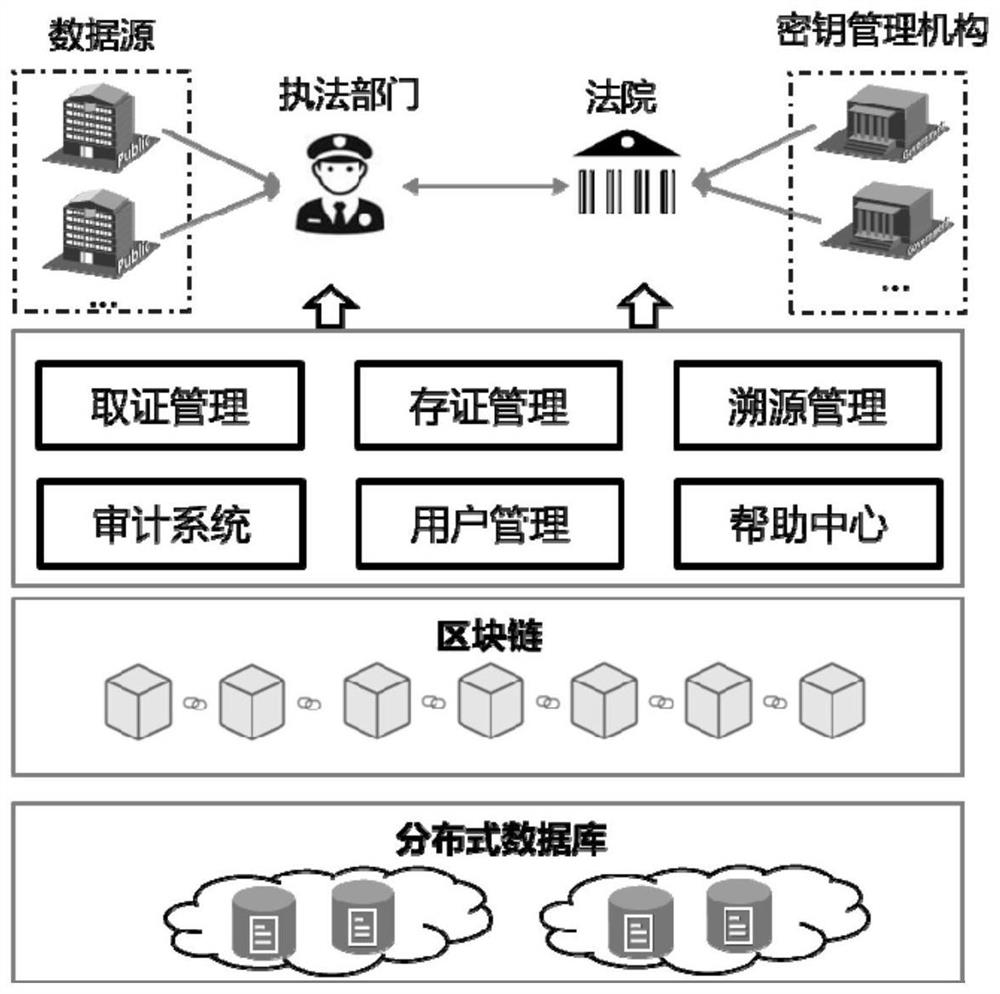
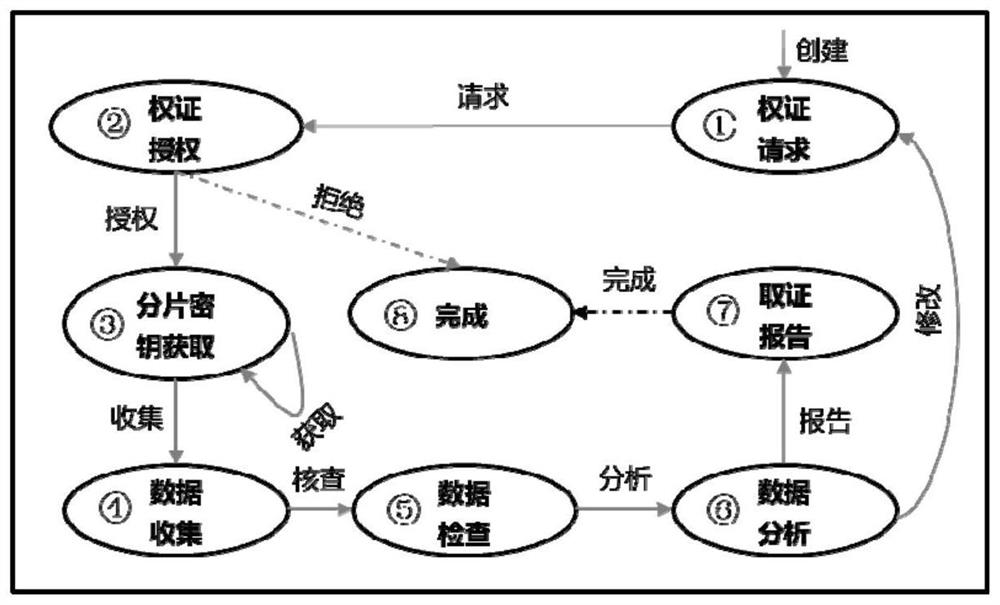
Digital forensics method based on blockchain privacy protection and fine-grained access control
ActiveCN111327597BPrevent abuse of powerSolve the problem of guarding and stealingSecuring communicationShardPrivacy protection
Owner:JINAN UNIVERSITY
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com