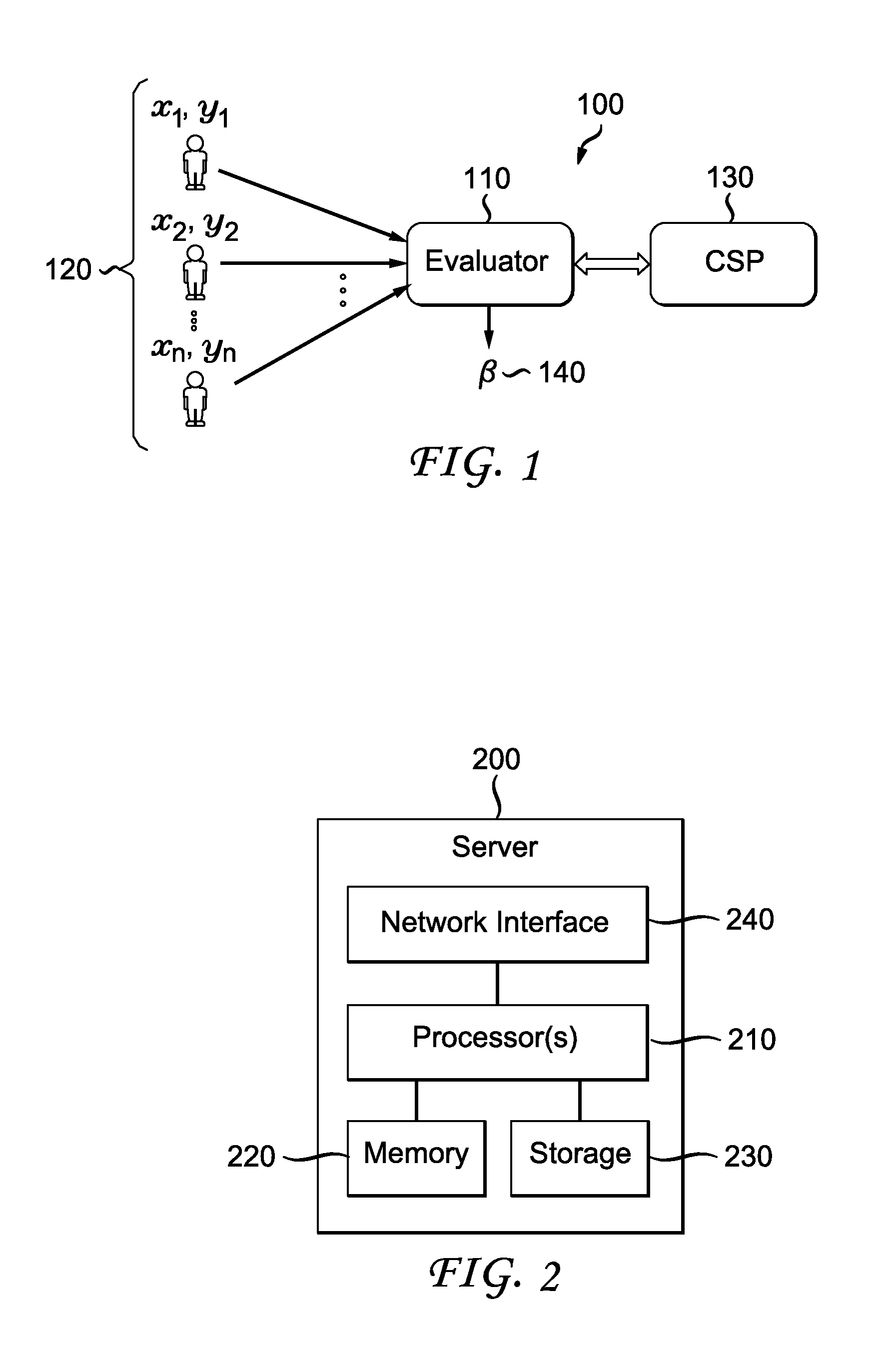
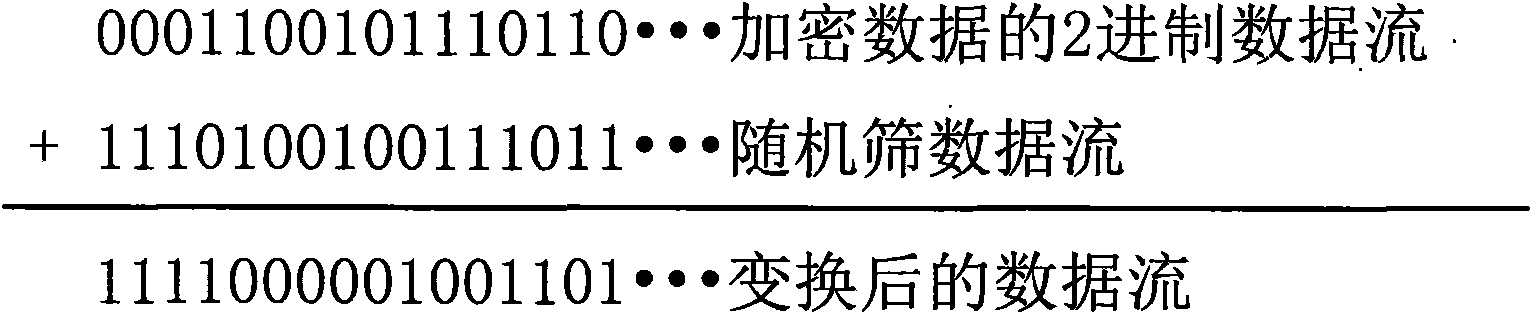
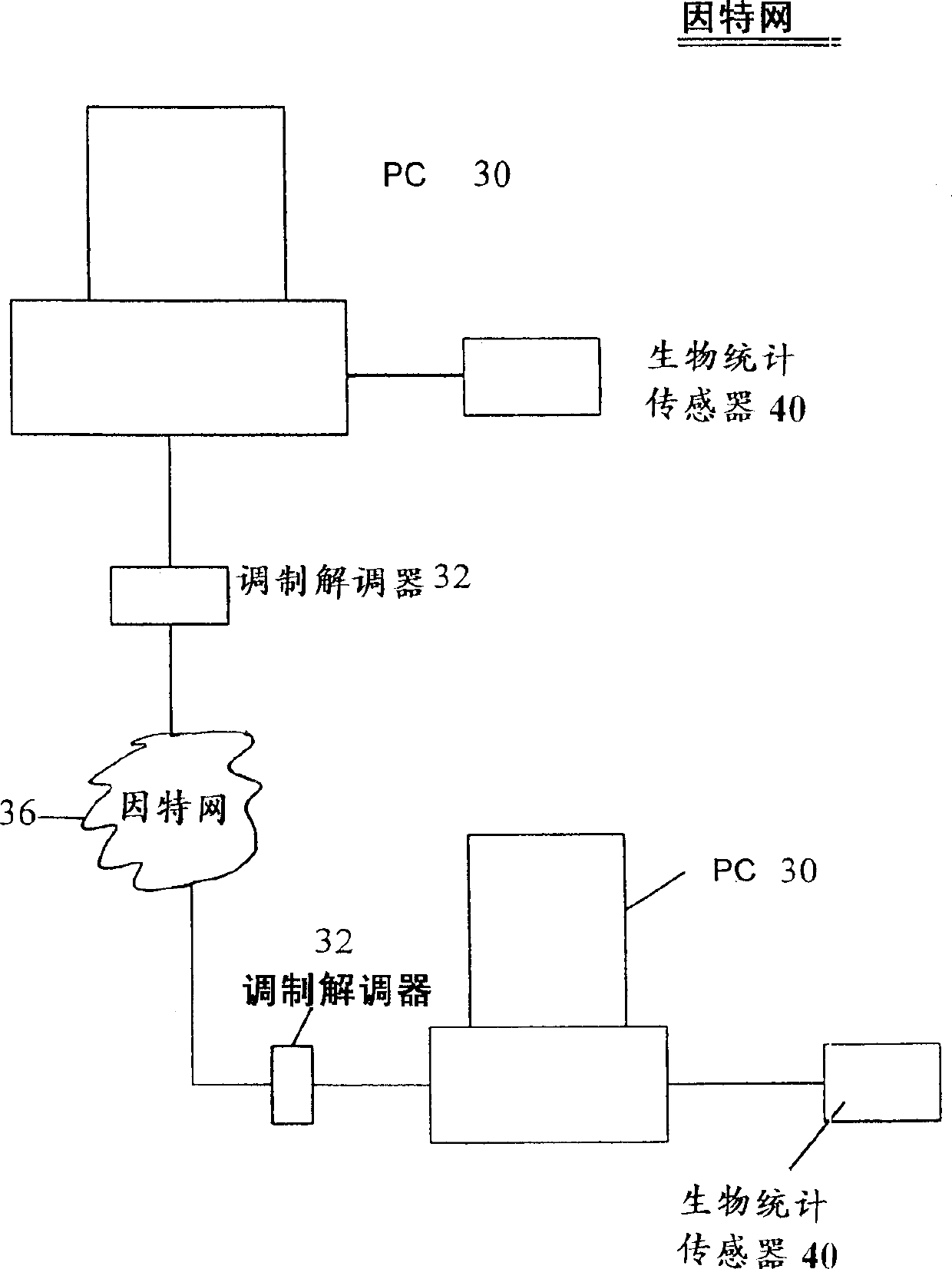
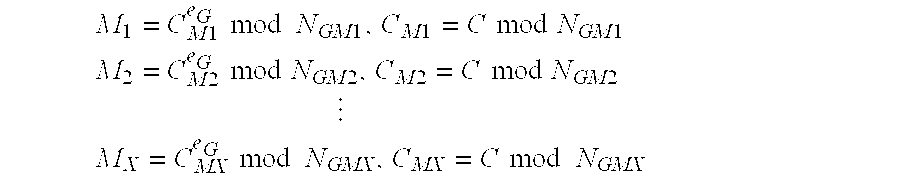Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
111results about How to "Avoid decryption" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Software protection method and system applicable to Android system
InactiveCN102236757AImprove protectionImprove execution efficiencyProgram/content distribution protectionByteSoftware protection
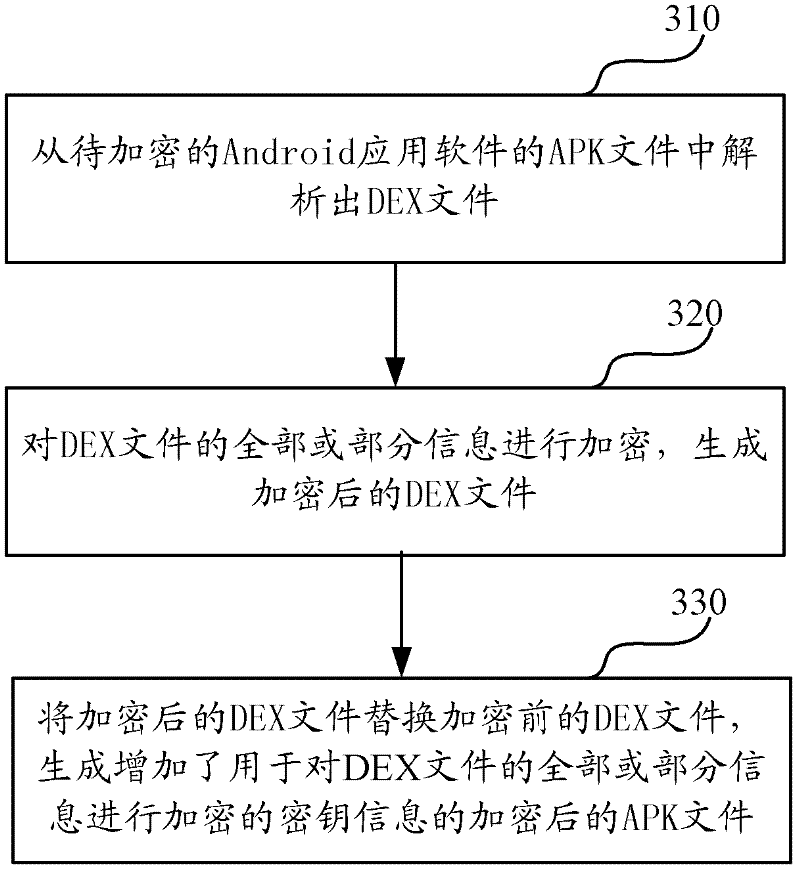
The invention discloses a software protection method and system applicable to an Android system. The method comprises the following steps of: analyzing: analyzing a DEX file from an APK (Android Package) file of Android application software to be encrypted; encrypting: encrypting all or a part of information of the DEX file to generate an encrypted DEX file; and generating, substituting the DEX file before encryption with the encrypted DEX file to generate the APK file formed by encrypting all or a part of the information of the DEX file and a digest file formed by performing MD5 (Message Digest 5) encryption on a key. Since the method only aims at the encryption protection of key information (such as a DEX file header, byte codes in the DEX file and the like) of the DEX file in the APK file, the execution efficiency of encryption and decryption is greatly increased.
Owner:BEIJING UNIV OF POSTS & TELECOMM
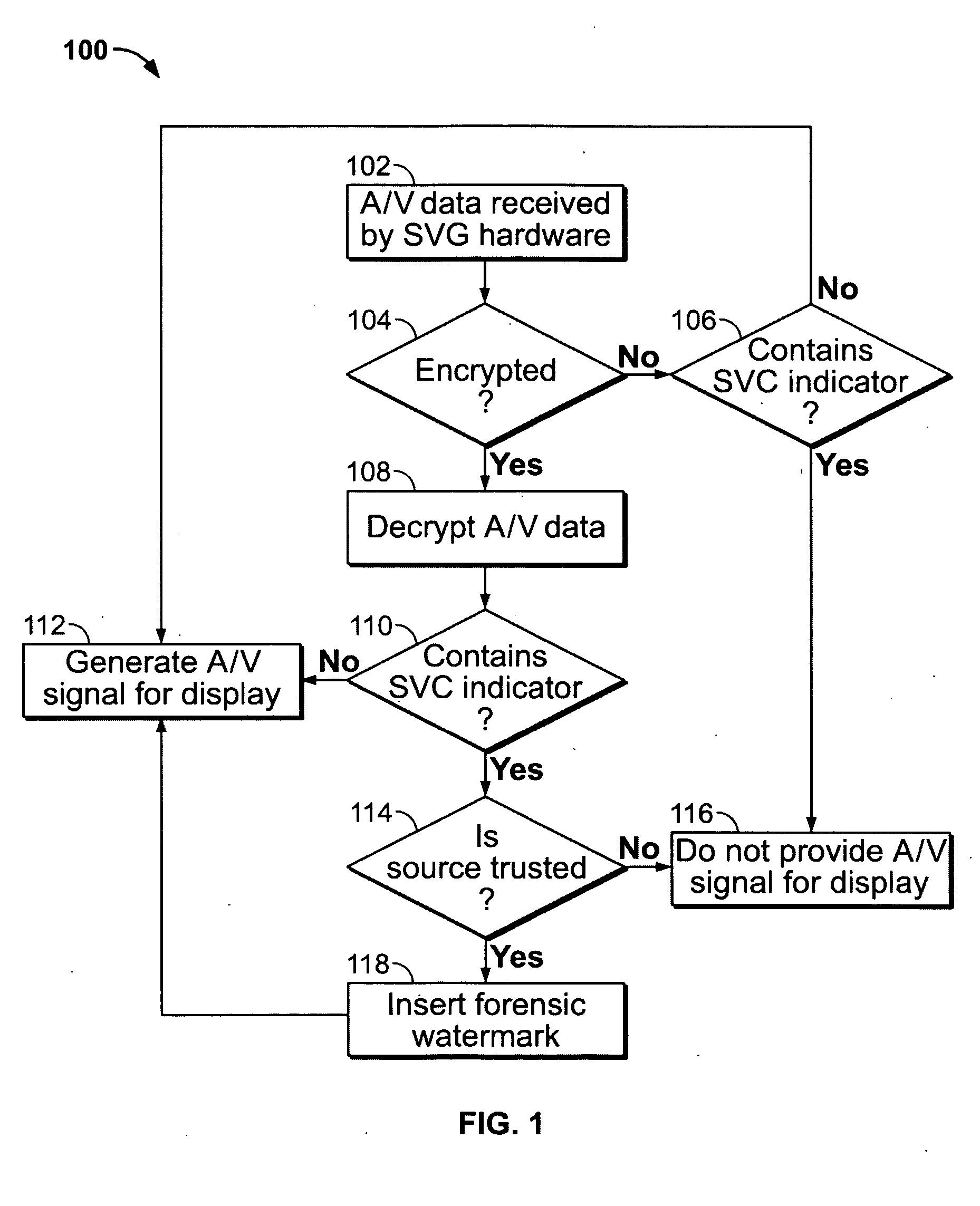
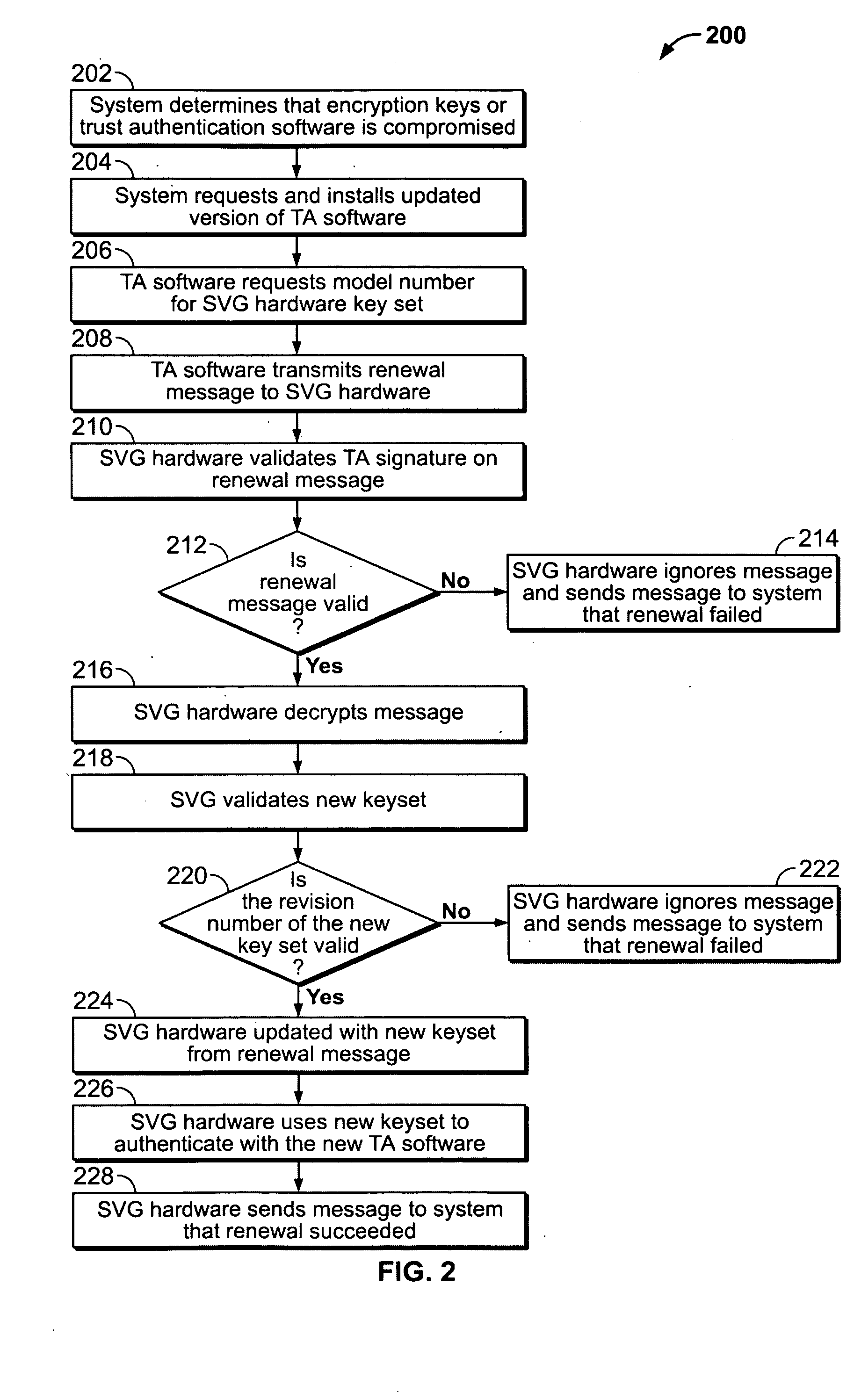
Secure video system for display adaptor
InactiveUS20050123135A1Unauthorized copyingPrevent illegal useTelevision system detailsUser identity/authority verificationGraphicsGraphic system
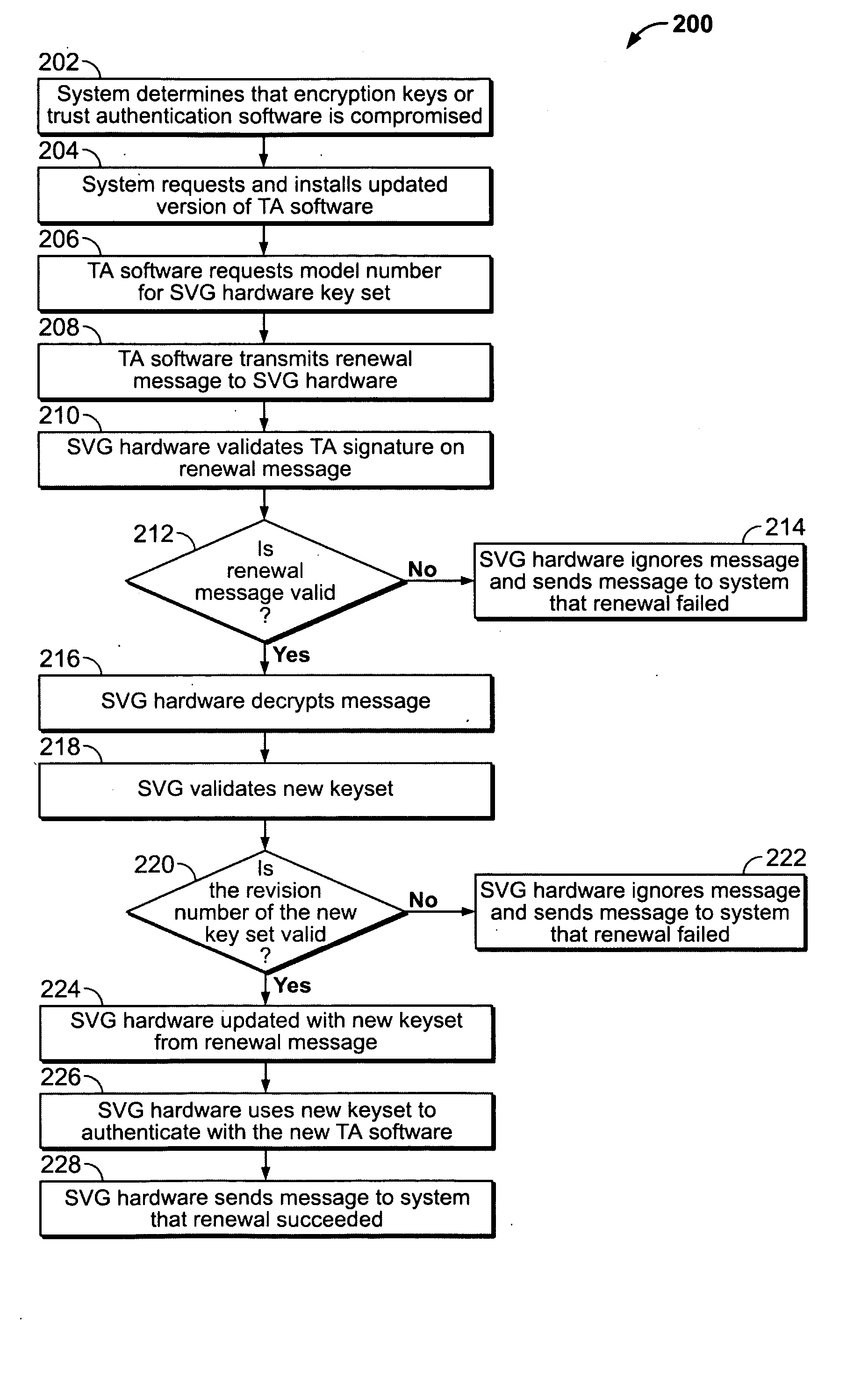
A secure video system for a graphics display adaptor includes a module for decrypting a content signal from a media player or other secure content source. The adaptor may be provided as a component of a computer graphics system, or in a stand-alone special-purpose device. The adaptor may include other features for preventing unauthorized use of protected content, for example authenticating the source of a content signal before providing an output audio or video signal, encrypting the output video signal, responding to commands to renew or revoke cryptographic keysets, and embedding forensic tracking information in an audio or video signal.
Owner:MOTION PICTURE ASSOC OF AMERICA
Content providing system, content reproducing device, content reproducing method, and computer program
InactiveUS20070198413A1Reduce usageAvoid decryptionDigital data protectionProgram/content distribution protectionComputer hardwareComputer program
A content reproducing device decrypts and outputs an encrypted content encrypted by a content key received from a content transmitting device. The content reproducing device includes a content key obtaining unit for obtaining the content key, and a storage unit for storing the key unique to the content transmitting device, usage restriction information to restrict the usage of the key unique to the content transmitting device, and link information indicating linking of the content transmitting device and the content reproducing device. The content reproducing device also includes a key decryption unit for decrypting the content key with the key unique to the content transmitting device in the event that the content reproducing device is included in the stored link information unit, and a usage control unit for restricting usage of the key unique to the content transmitting device, based on the stored usage restriction information.
Owner:SONY CORP
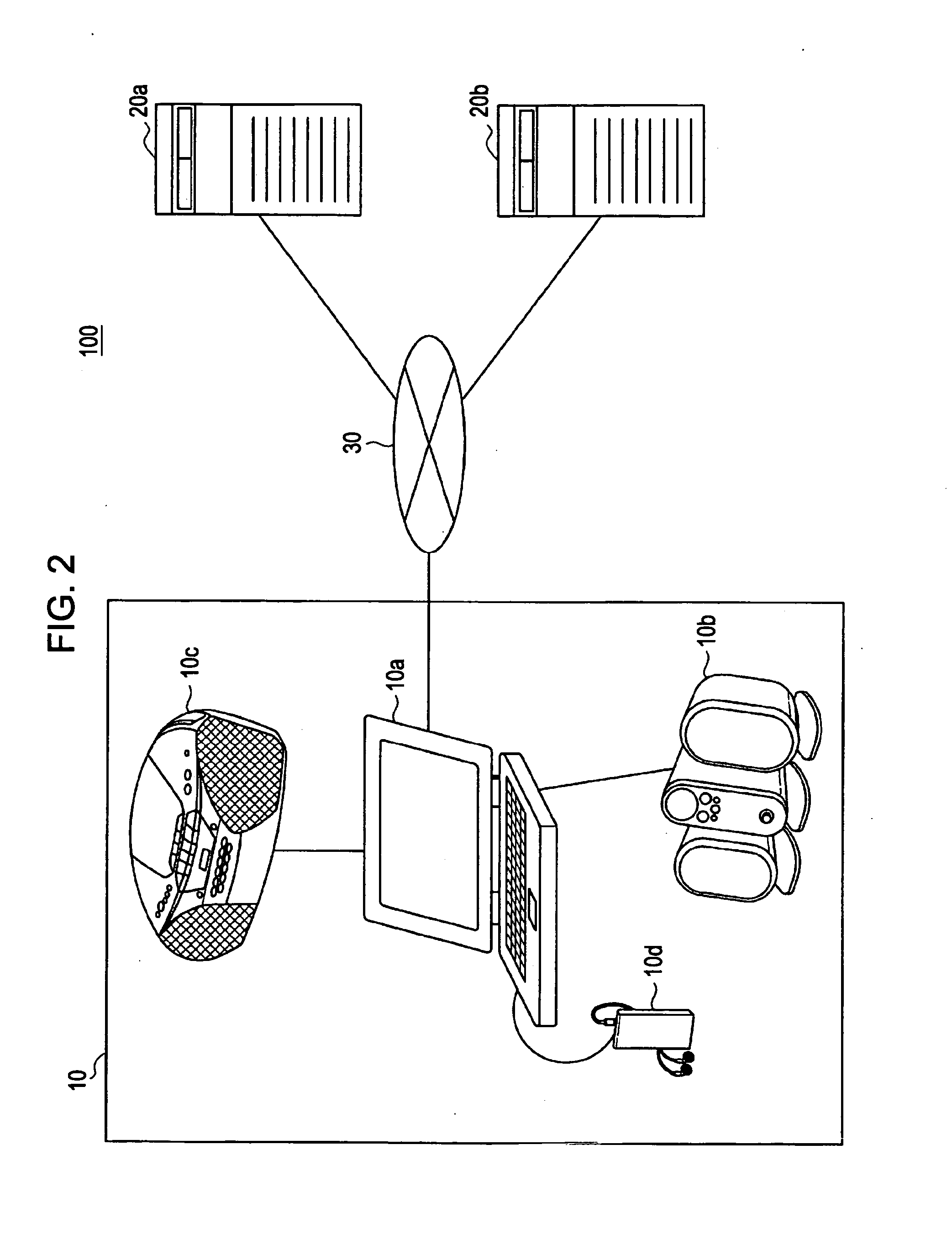
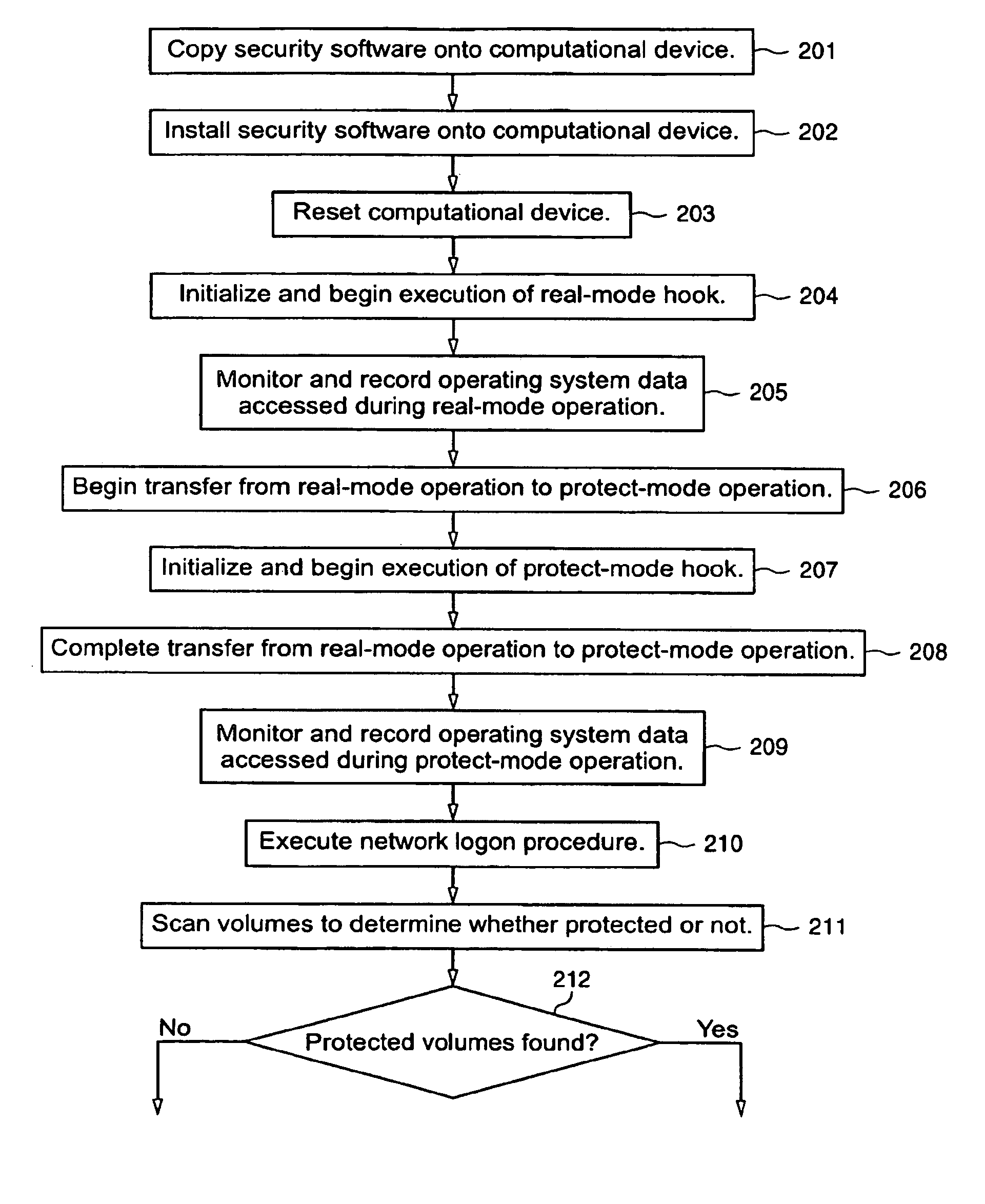
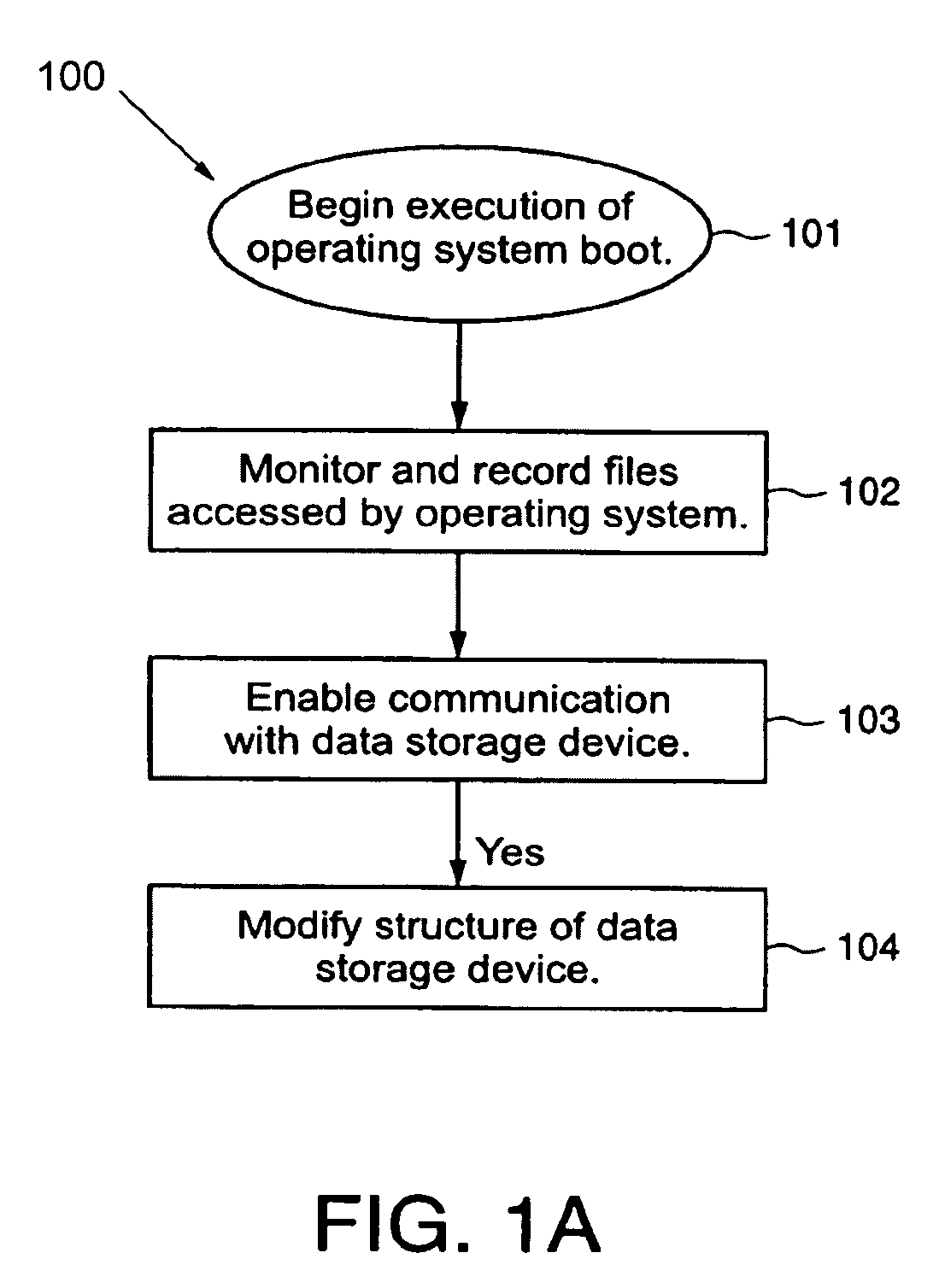
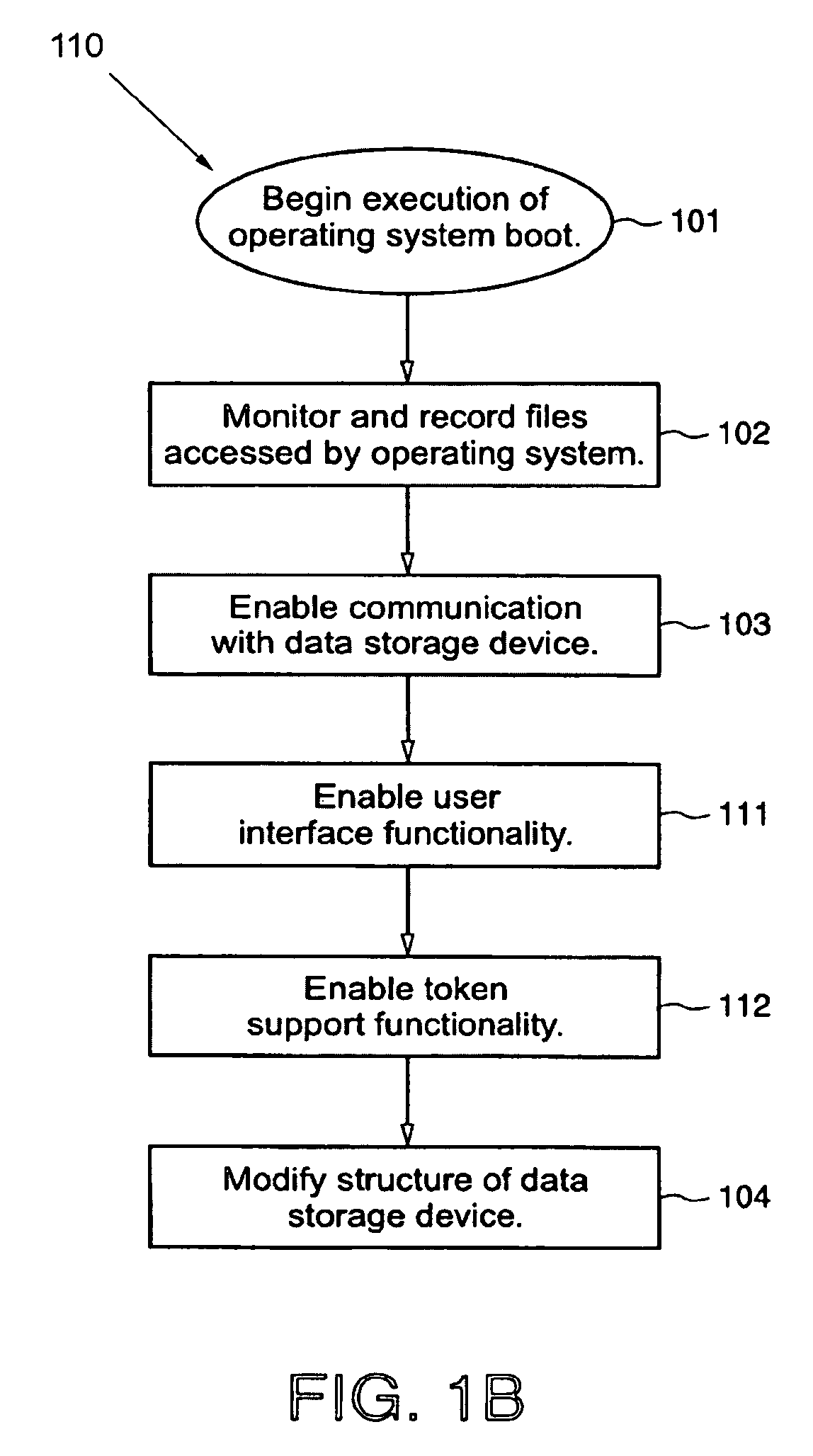
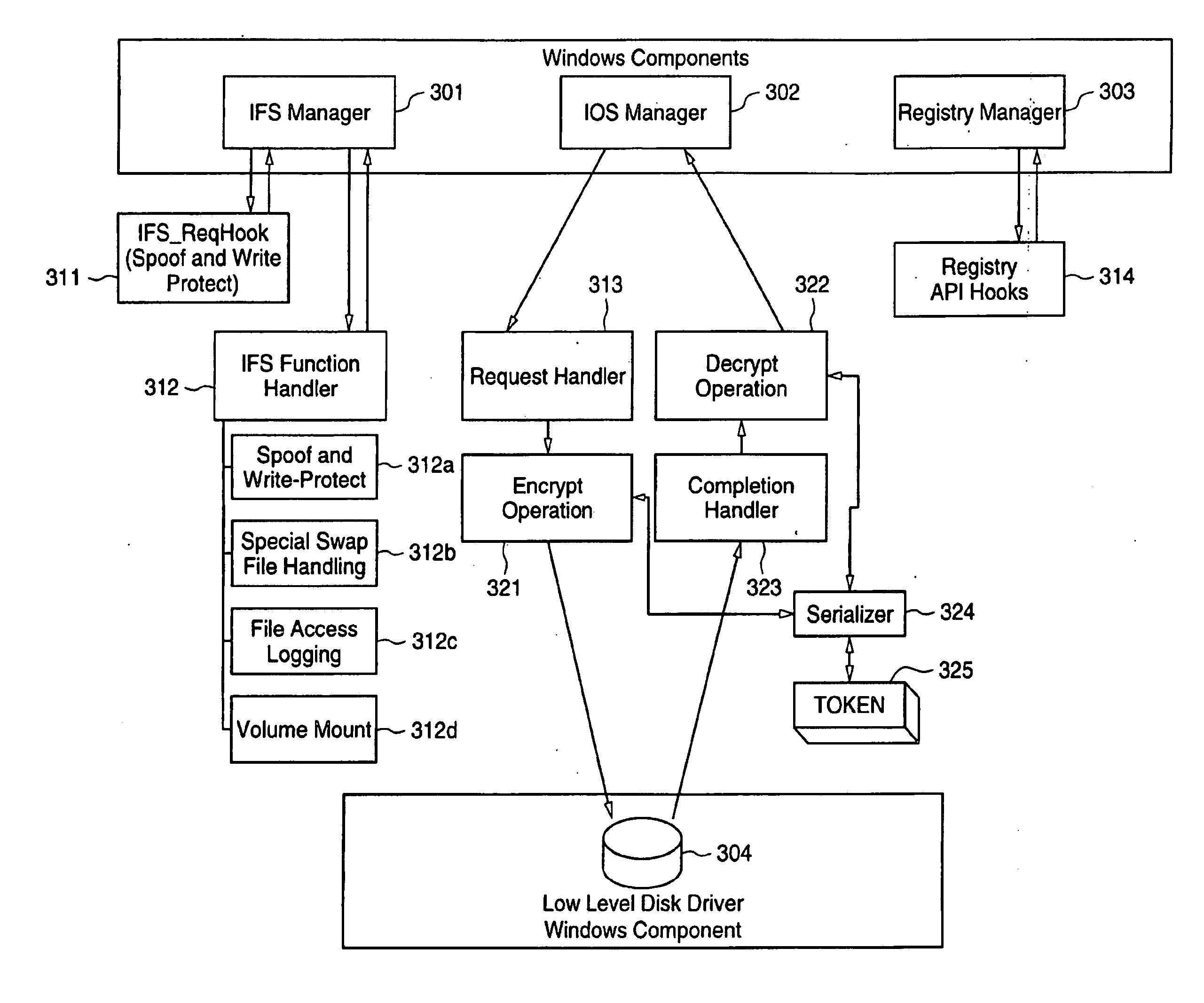
Protected volume on a data storage device with dual operating systems and configurable access and encryption controls
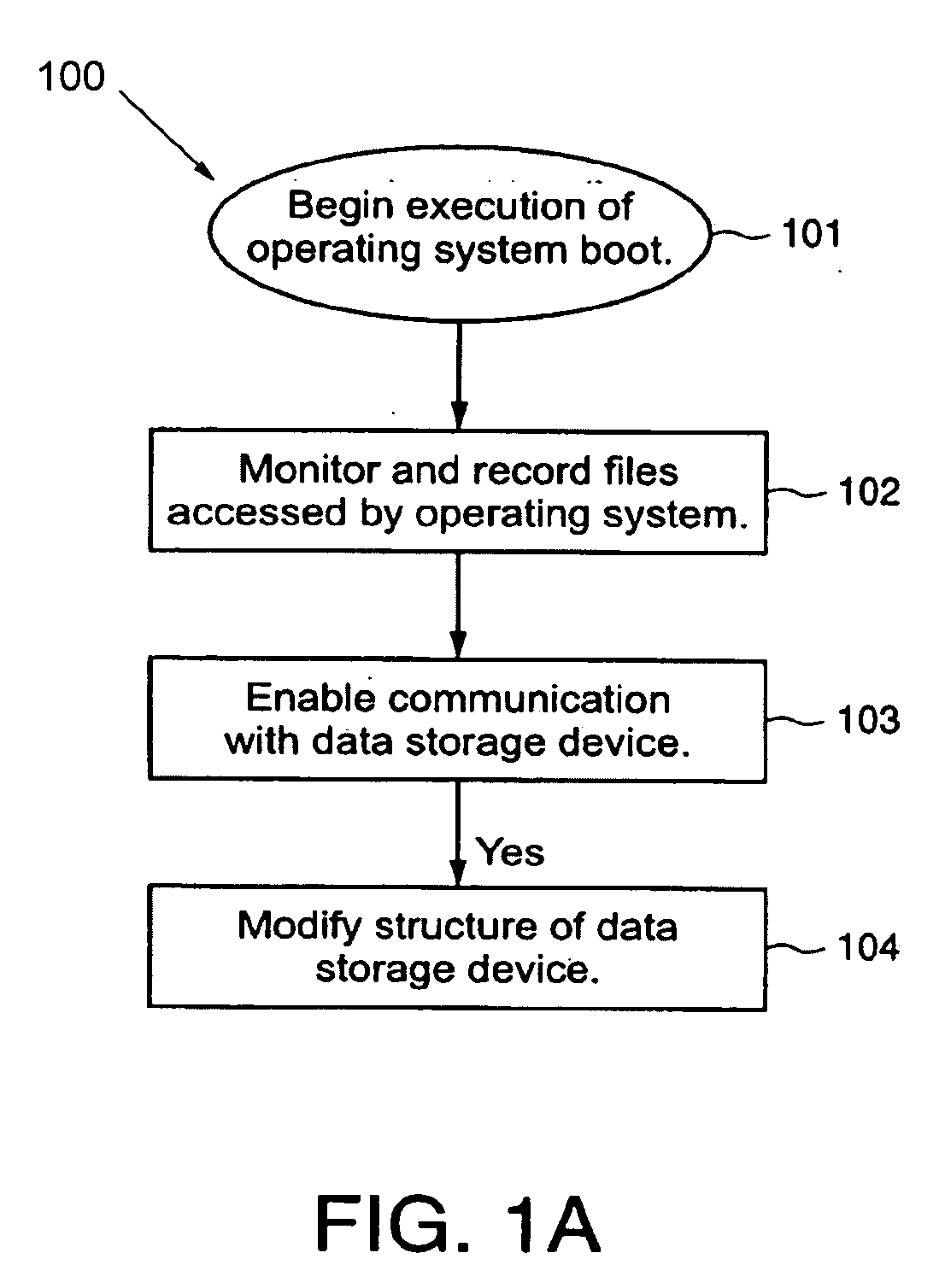
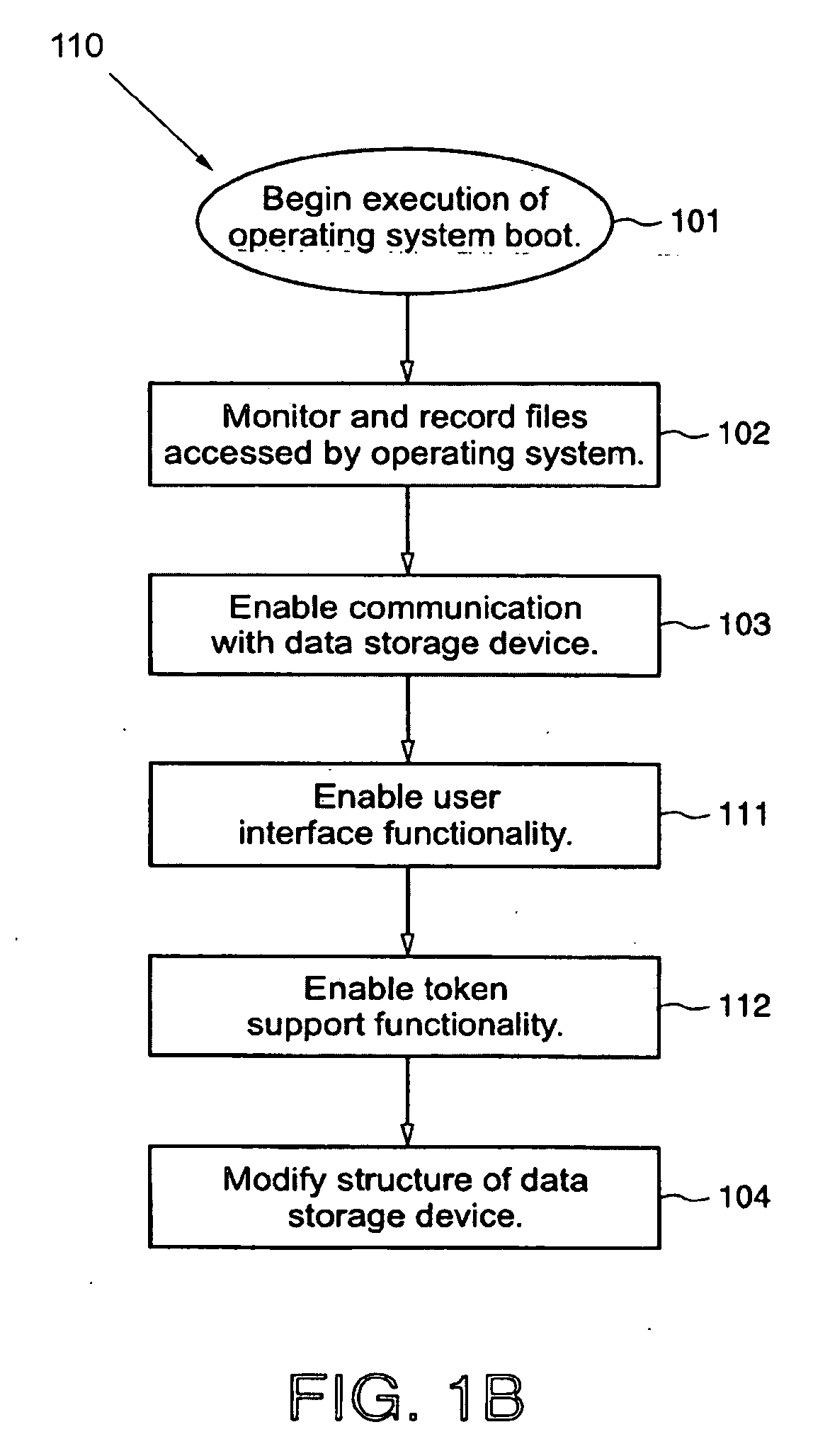
InactiveUS7757100B2Avoid decryptionAvoid accessUser identity/authority verificationDigital computer detailsOperational systemData storing
A method provides a protected region of a data storage device associated with a computational device, where data in the protected region is primarily protected by preventing access without proper access authorization. The method comprises the steps of providing, in an unprotected region of the data storage device, a first operating system and associated operating system data; monitoring operating system data accessed by the computational device until a predetermined functionality becomes available; storing, in the protected region, the monitored operating system data; providing, in the protected region, a second operating system; transferring control of the computational device from the first operating system to the second operating system; storing data in the protected region; and preventing access to the stored data in the protected region without access authorization. In a further embodiment of the method, the second operating system optionally provides a second level of security by preventing decryption of data stored in the protected region without decryption authorization.
Owner:SPEX TECH
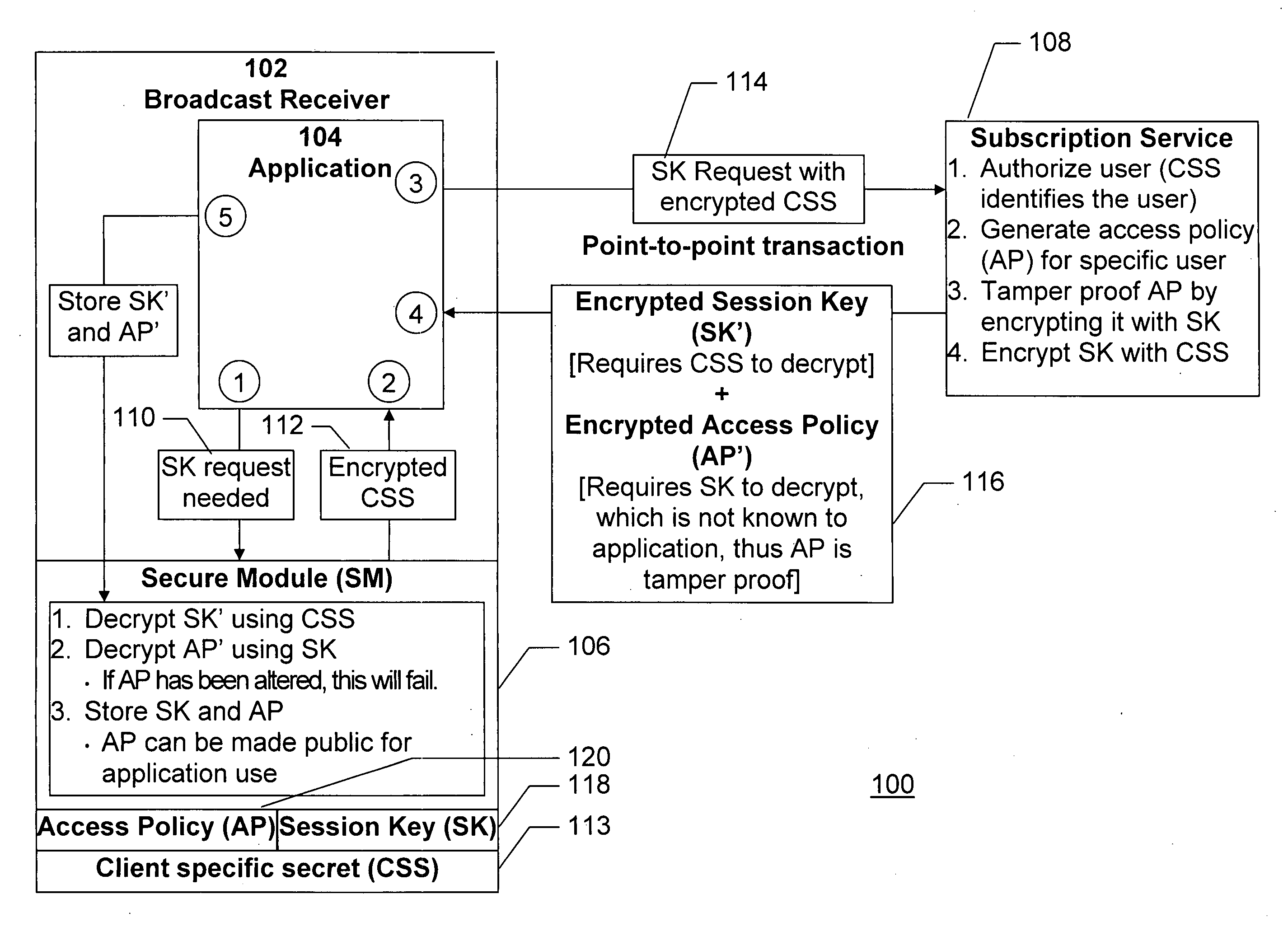
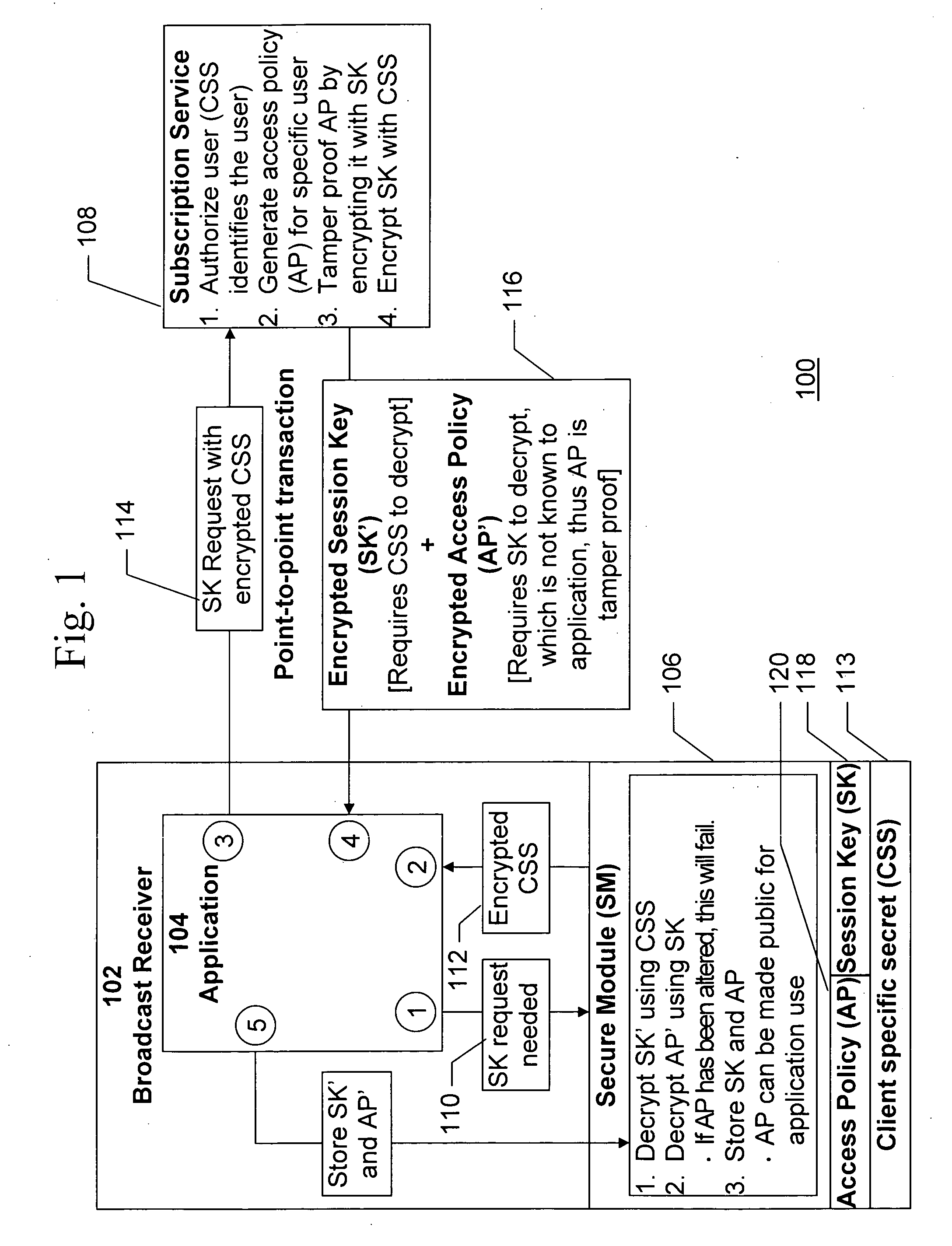
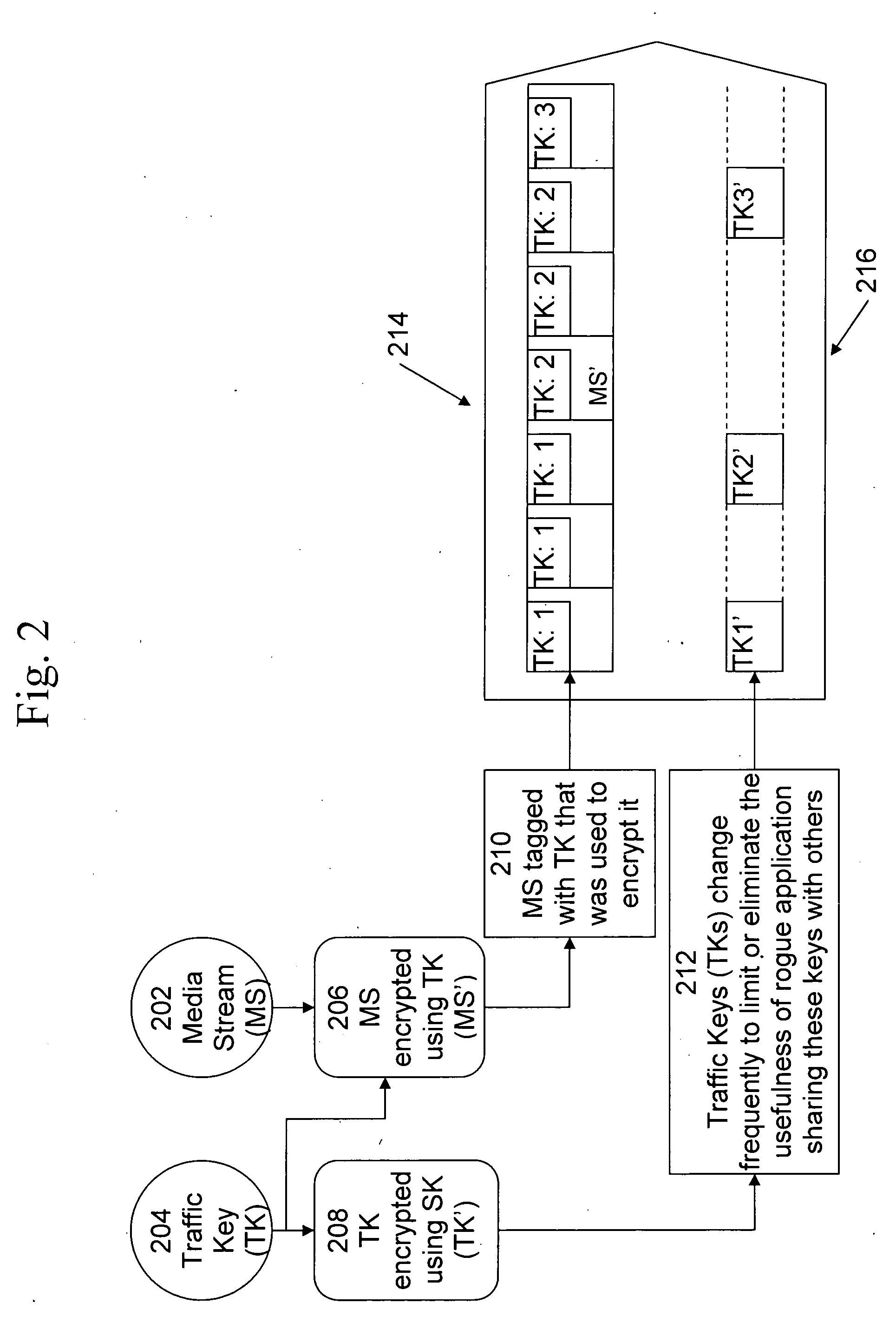
Restriction of broadcast session key use by secure module decryption policy
InactiveUS20070140488A1Avoid decryptionTelevision systemsSelective content distributionTraffic volumePopulation
A method is provided for restricting or enhancing broadcast content access on a per-subscriber basis across a population of subscribers, all of whom have a valid content access key to such content, without necessitating changes to the current standard schemes and protocols for distributing content access keys and broadcasting the traffic keys associated with the broadcast data itself, and without trusting the application that processes the data. A method of handling a multimedia broadcast in a device comprises receiving broadcast content in a media stream encrypted using a traffic key, receiving the traffic key encrypted using a session key, and receiving broadcast attributes encrypted using the traffic key and the session key, wherein use of the media stream by the device is controlled using the broadcast attributes and using an access policy in the device.
Owner:ROUNDBOX
Method and system for preventing unauthorized recording of media content on a Macintosh operating system
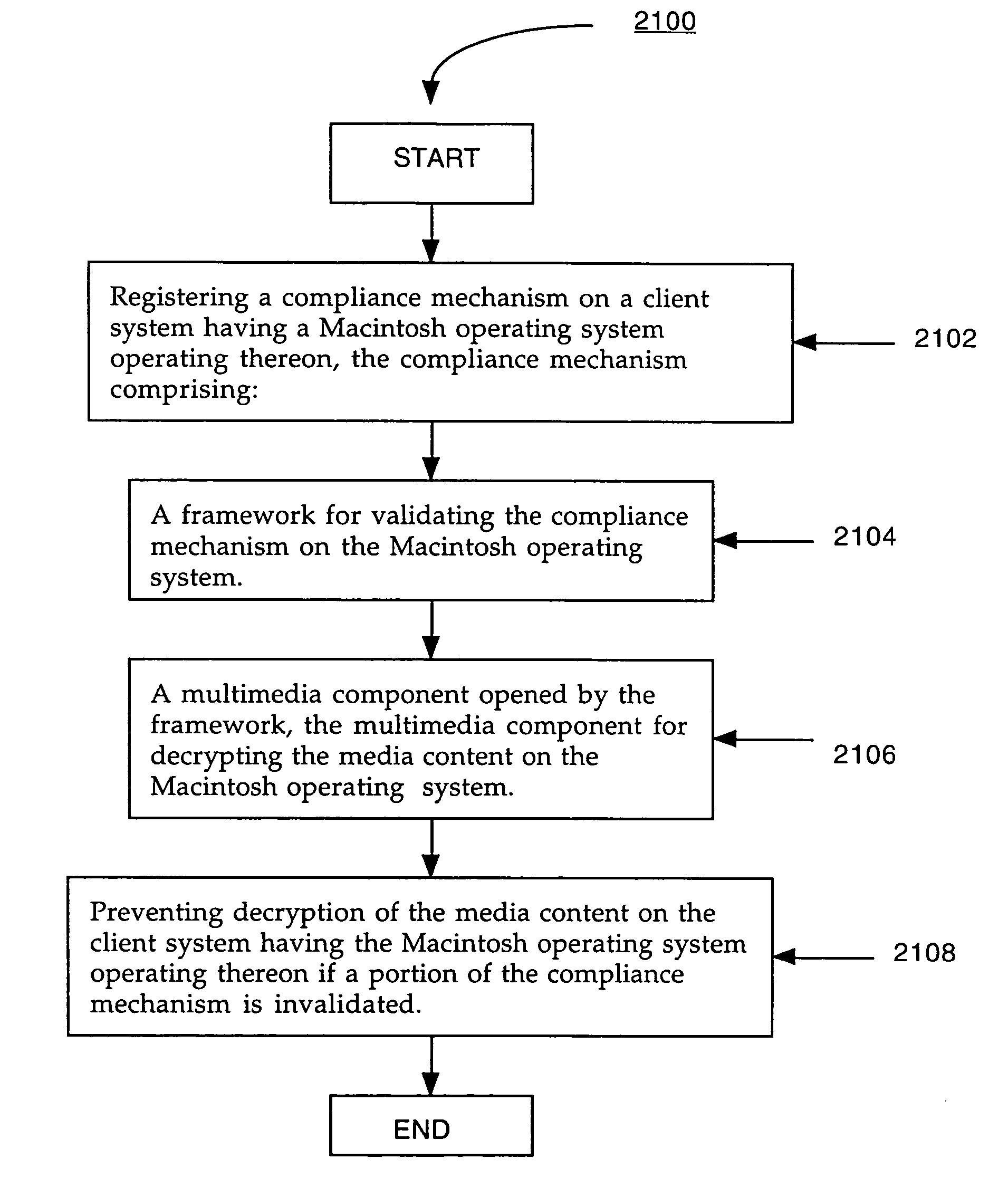
InactiveUS20050172121A1Preventing unauthorized recordingAvoid decryptionDigital data processing detailsCryptography processingComputer hardwarePresent method
A method for preventing unauthorized recording of media content on a Macintosh operating system. The present method registers a compliance mechanism on a client system having the Macintosh operating system operating thereon. The compliance mechanism comprises a framework for validating the compliance mechanism on the client system, and a multimedia component opened by the framework. The present method uses the multimedia component for decrypting the media content on the client system. The present method also prevents decryption of the media content on the client system having the Macintosh operating system operating thereon if a portion of the compliance mechanism is invalidated.
Owner:MUSIC PUBLIC BROADCASTING
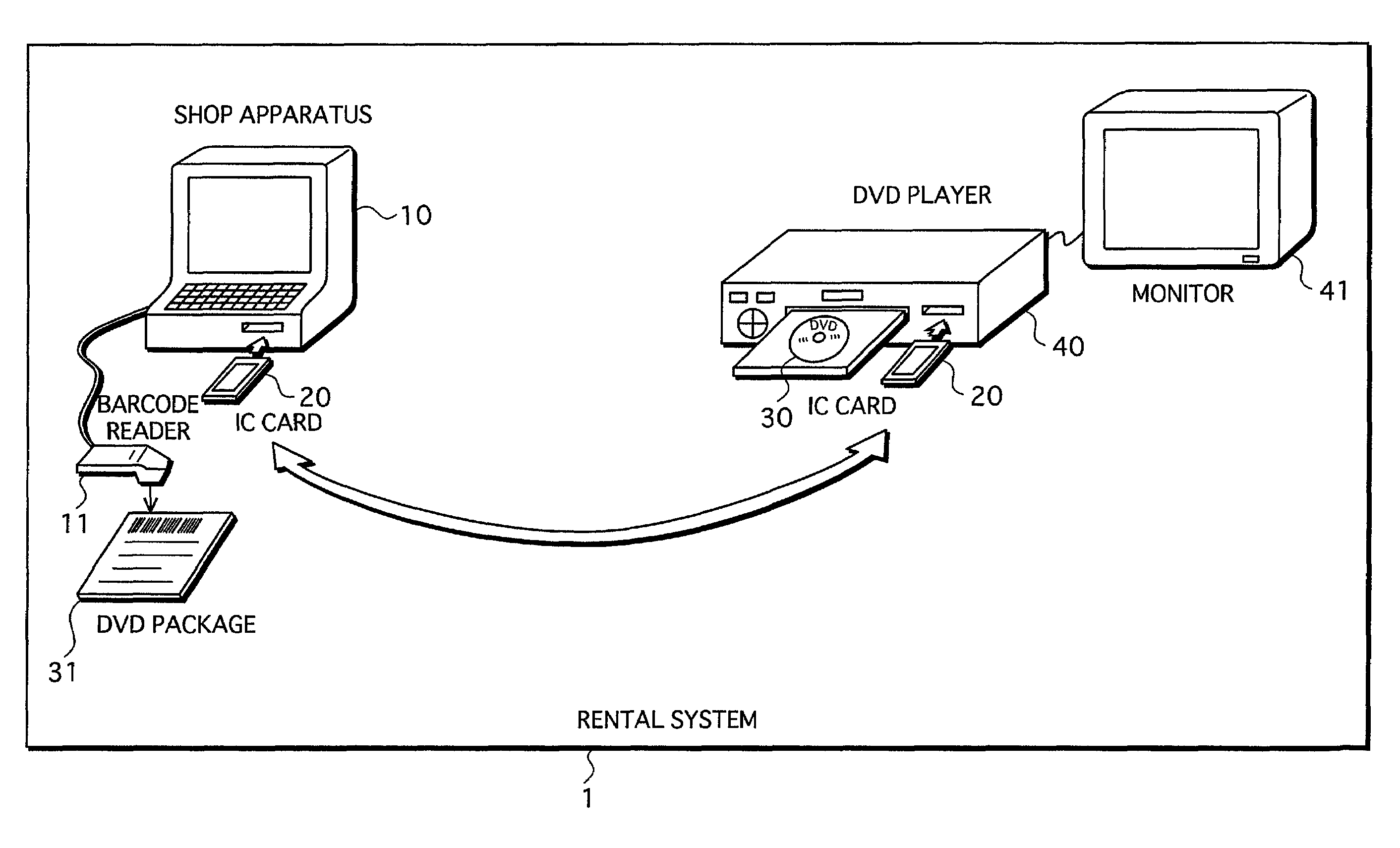
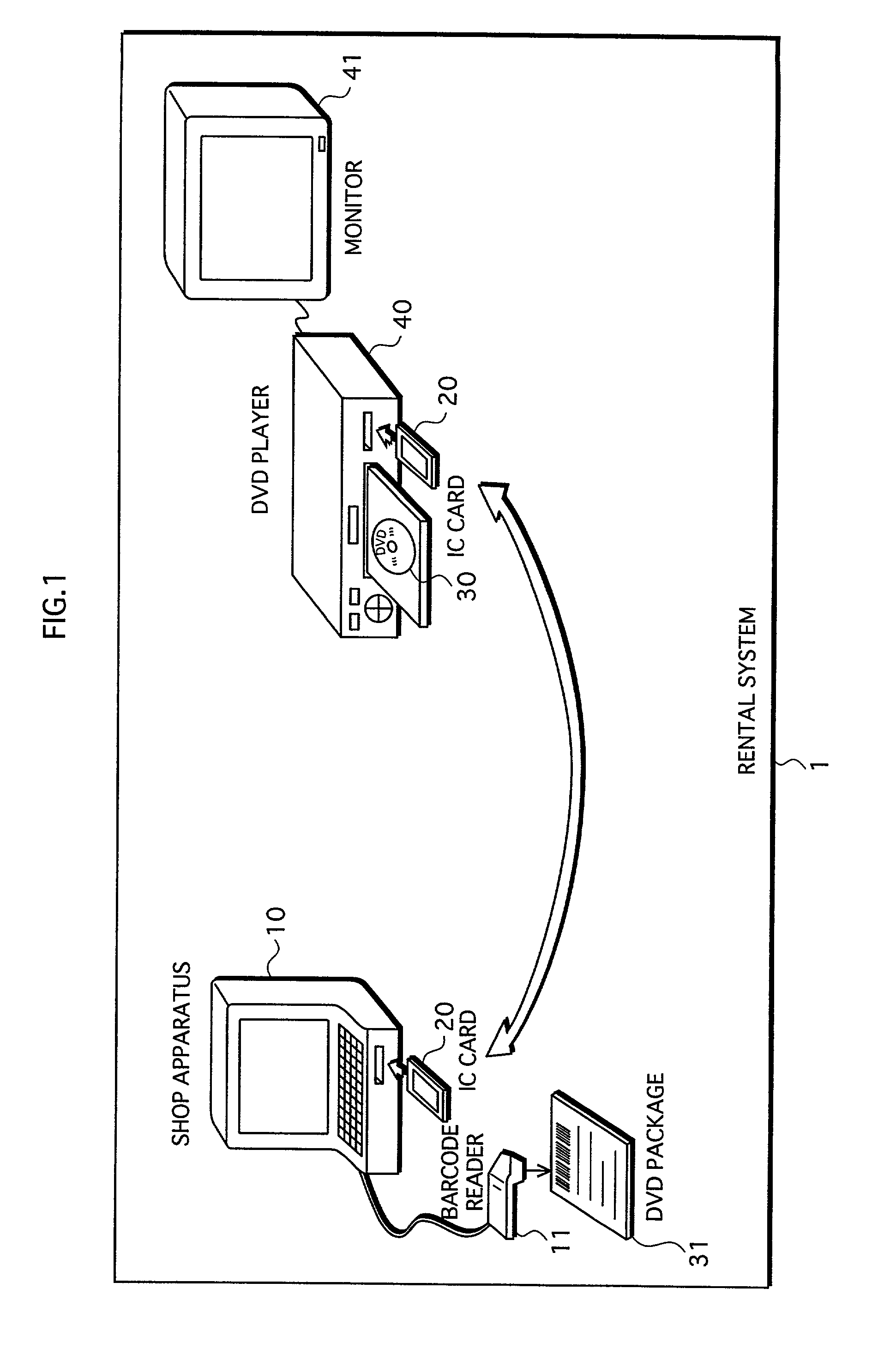
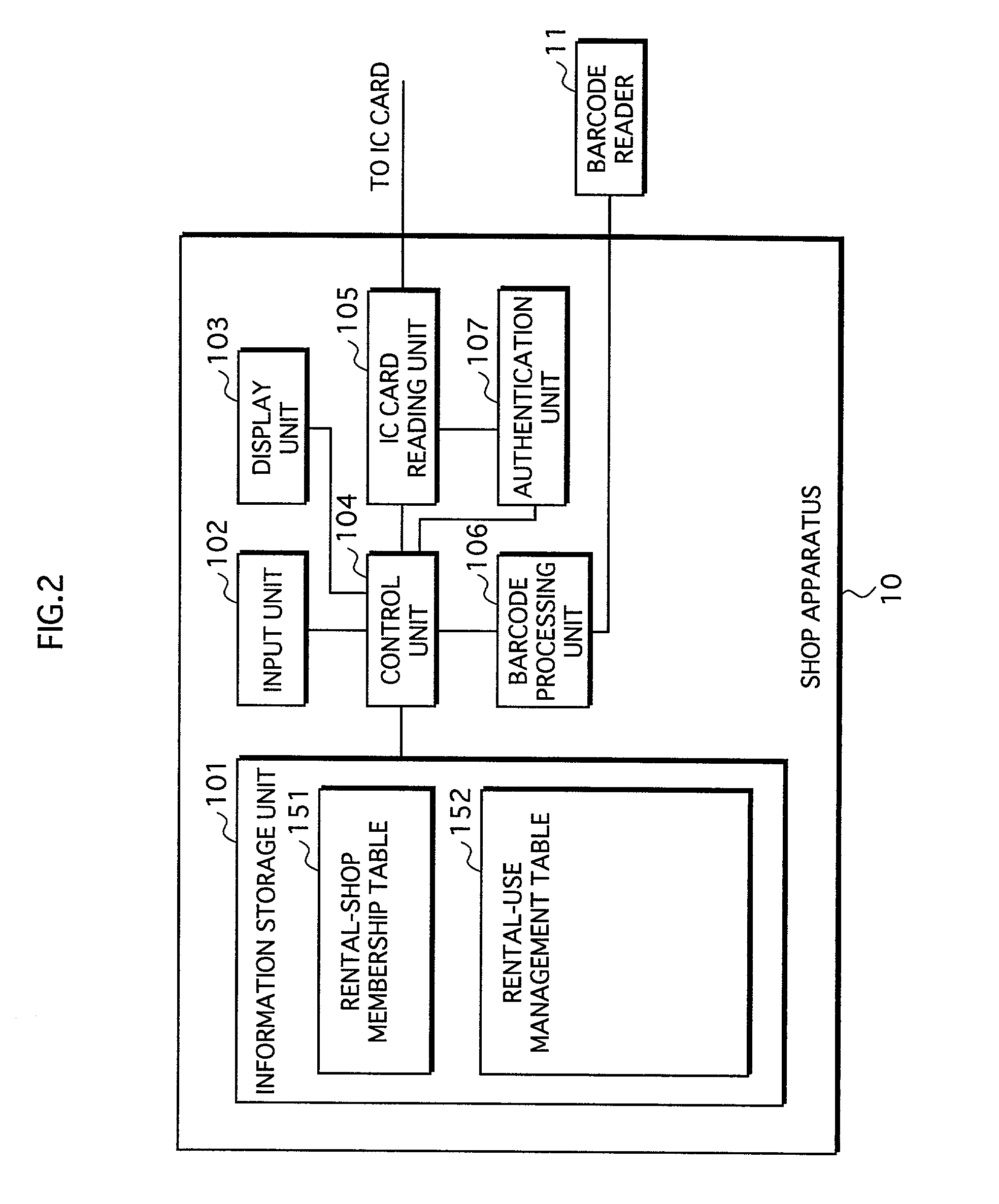
Storage-medium rental system
InactiveUS7020636B2Reduce usageReduce the possibilityElectrophonic musical instrumentsRecord information storageDigital workEncryption
A storage-medium rental system includes a portable storage medium to be rented to the user, a portable semiconductor memory owned by the user, a rental-shop apparatus owned by the rental agent, and a reproduction apparatus owned by the user. The storage medium prestores encrypted content which is generated by encrypting digital work by using a content encryption key. The semiconductor memory has an area for securely storing a content decryption key. The rental-shop apparatus stores a content decryption key for decrypting the encrypted content. The rental-shop apparatus writes the content decryption key to the semiconductor memory. The reproduction apparatus securely reads the content decryption key from the semiconductor memory, reads the encrypted content from the storage medium, decrypts the encrypted content by using the content decryption key, and reproduces the decrypted content.
Owner:PANASONIC CORP
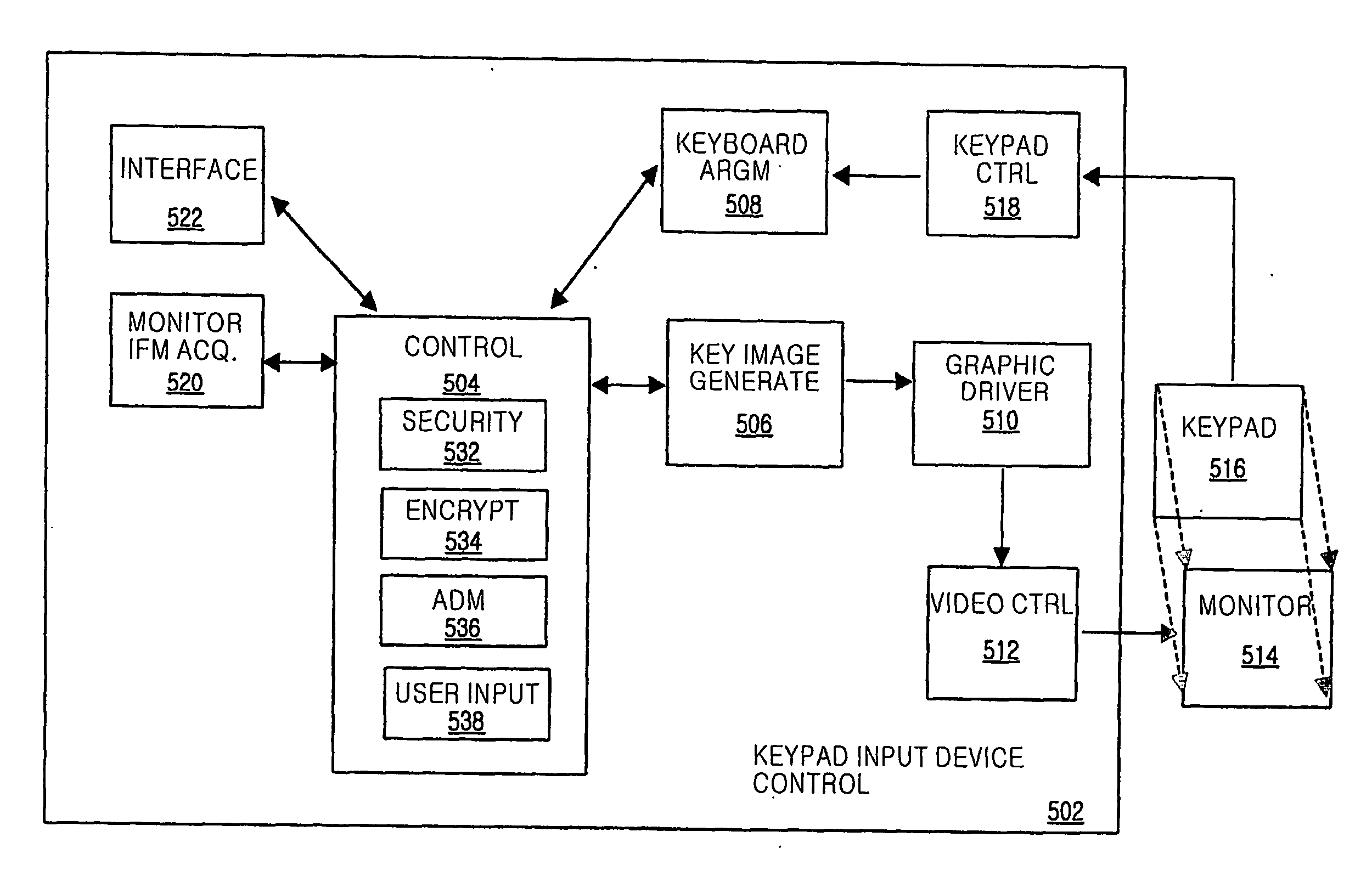
Information inputting system with a variable arrangement of keypad, and control method thereof
InactiveUS20070096946A1Avoid decryptionInhibition of informationElectronic switchingCoding/ciphering apparatusComputer graphics (images)Square Shape
The present invention discloses a keypad matrix element shift arrangement method having an efficient an neighboring numeral traffic line customarily. According to the present invention, an information input apparatus whose key arrangement varies includes a key display section of a square shape for displaying a key image, and a key input section for receiving information of a corresponding key at a predetermined location of the key image displayed by the key display section. The information input apparatus further an input controller for generating an image of predetermined key arrangement selected among a plurality of key images in which numeric keys are shift-arranged so that there is no crossing in an neighboring numeral traffic line, providing the generated image to the key display section, and converting information inputted through the key input section into an actual key value according to the predetermined key arrangement.
Owner:NEXVI CORP
Protected volume on a data storage device with dual operating systems and configurable access and encryption controls
InactiveUS20080263371A1Avoid decryptionAvoid accessDigital computer detailsUnauthorized memory use protectionOperational systemData storing
A method provides a protected region of a data storage device associated with a computational device, where data in the protected region is primarily protected by preventing access without proper access authorization. The method comprises the steps of providing, in an unprotected region of the data storage device, a first operating system and associated operating system data; monitoring operating system data accessed by the computational device until a predetermined functionality becomes available; storing, in the protected region, the monitored operating system data; providing, in the protected region, a second operating system; transferring control of the computational device from the first operating system to the second operating system; storing data in the protected region; and preventing access to the stored data in the protected region without access authorization. In a further embodiment of the method, the second operating system optionally provides a second level of security by preventing decryption of data stored in the protected region without decryption authorization.
Owner:SPEX TECH
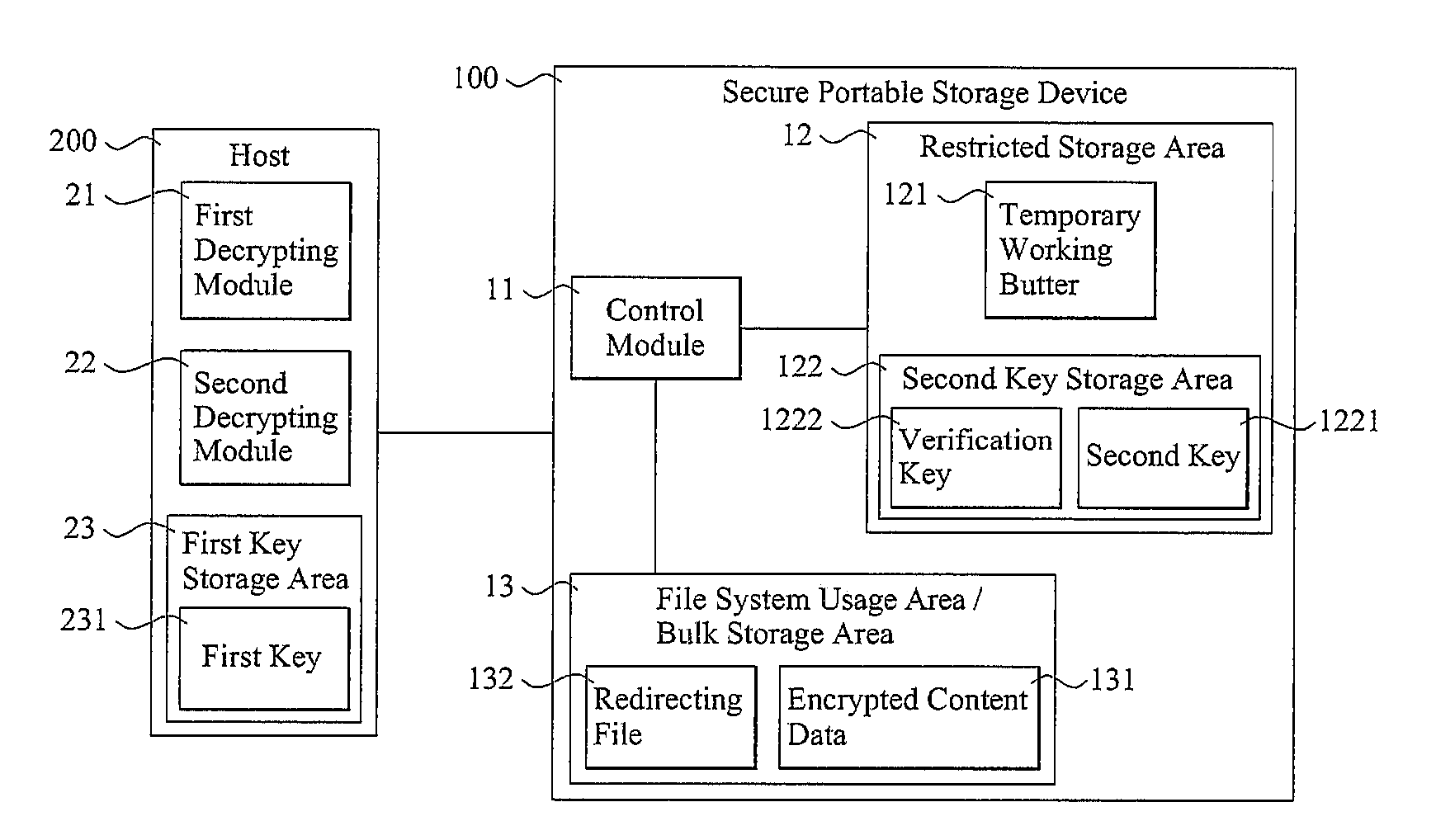
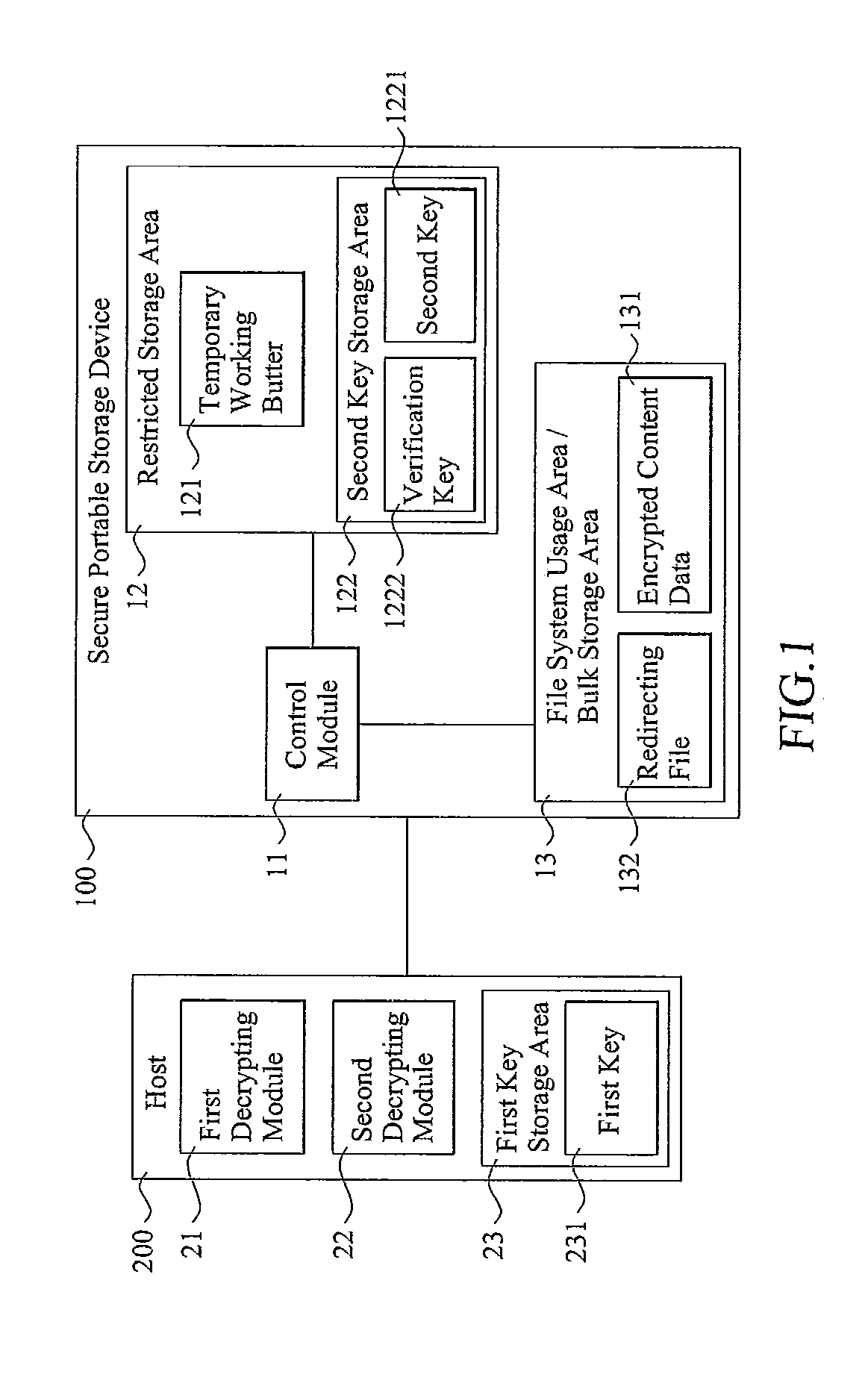
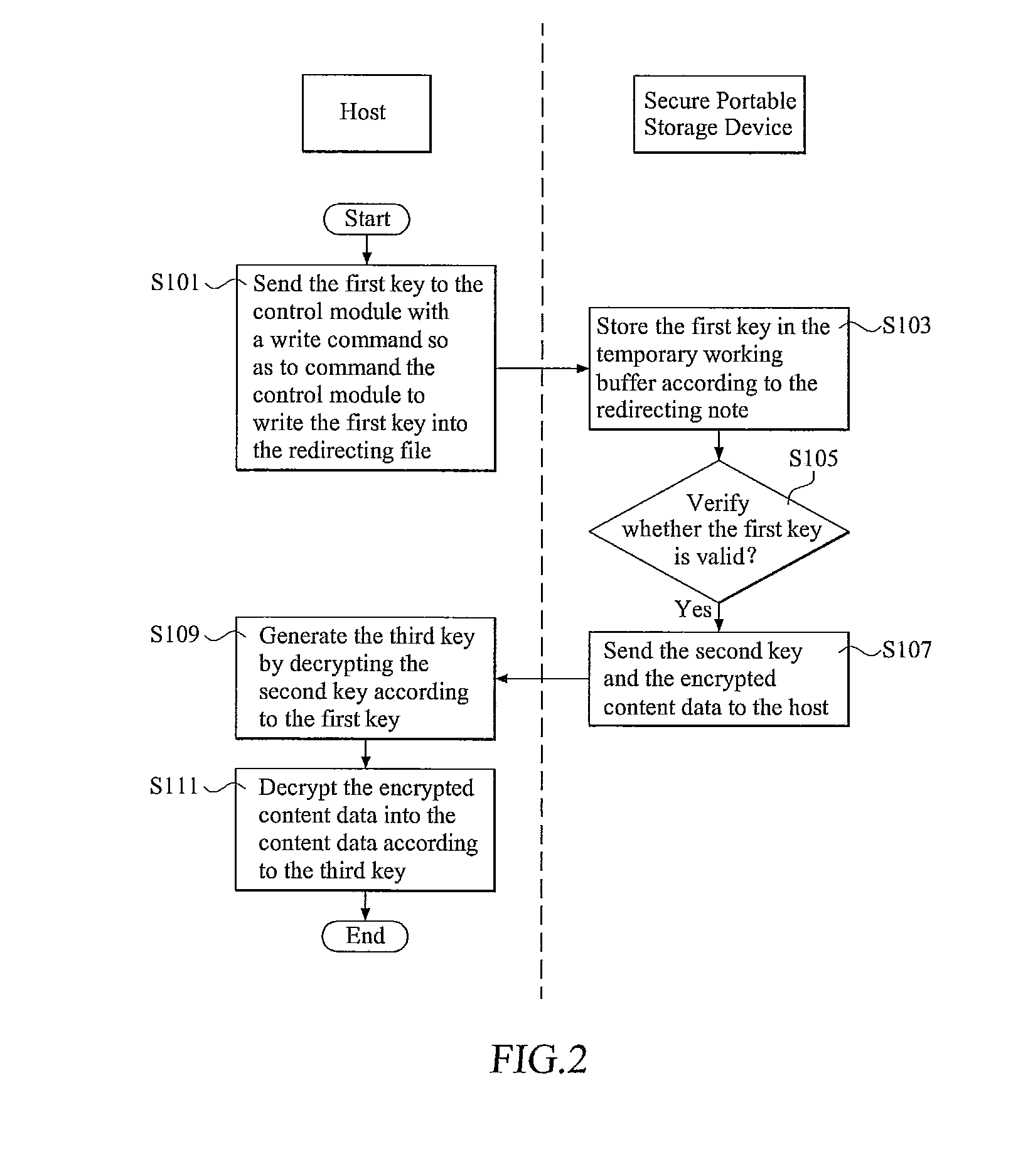
Access control for secure portable storage device
InactiveUS20110022850A1Avoid decryptionUnauthorized memory use protectionHardware monitoringComputer hardwareMedia access control
A secure portable storage device includes a control module. When a host sends a first key to the control module with a write command so as to command the control module to write the first key into a redirecting file, the control module stores the first key in a temporary working buffer and verifies whether the first key is valid; when the first key is valid, the control module sends a second key and an encrypted content data to the host for generating a third key by decrypting the second key according to the first key and decrypting the encrypted content data into a content data according to the third key. Moreover, when the host sends multiple read commands to the control module in sequence, the control module verifies whether a sequence of the read commands received is valid and sends the second key and the encrypted content data to the host for an encryption. Related apparatuses, methods and techniques also are provided.
Owner:ATP ELECTRONICS TAIWAN
Signcryption method of biological features of a plurality of receivers
InactiveCN102710613AOvercome the problem of forgeryPrevent leakageTransmissionDigital signatureSigncryption
The invention discloses a signcryption method of biological features of a plurality of receivers, comprising generating system parameters; extracting features; performing user log-on; encrypting by a sender; and decrypting by receivers. The method employs fuzzy extractor technique to bind the biological features and user keys to protect keys, directly authenticates user identity through the biological features, solves the safety problems of key safety and key abuse in the conventional cryptography, adds digital signature of senders during encryption, verifies identity of senders through certification during decryption, and solves the problem of counterfeiting of senders. The method improves the safety and reliability of whole systems, has the advantages of high safety, high efficiency and no need for storing any secret information by users, and can be applied to the distributed network application field.
Owner:XIDIAN UNIV
Method and apparatus to inhibit illicit copying from a record carrier to a computer-readable data storage device
InactiveUS7065506B1Discourage illicit copyingAvoid decryptionOptical re-recordingFinanceHard disc driveProgram instruction
A technique to prevent illicit copying of a copy-protected CD-ROM into a computer-readable storage drive is presented. In accordance with the present invention, when an authentic copy-protected CD-ROM is inserted into a CD drive and the content of the copy-protected CD-ROM is installed onto a hard disk drive that is linked to the CD drive, the Central Processor Unit (CPU) executes the installer instructions residing in the CD-ROM to create a license file in the hard disk drive. For security reasons, the content of the CD-ROM (e.g., the executable file of the application) is encrypted. When the content of the CD-ROM is copied into the hard disk drive, it remains encrypted. The license file essentially acts as a timer to monitor a predetermined time interval that has been programmed into the license file. If a user attempts to launch the encrypted copied application residing in the hard drive at any time prior to the expiration of the predetermined time interval, the license file readily supplies the key code to enable a filter to decode the encrypted installed application thereby allowing the application to launch. At the expiration of the predetermined time interval, the license file withholds the key code therefore not allowing the installed application to be decrypted and successfully launched. The predetermined time interval can be reset by reinserting the copy-protected CD-ROM into the CD drive to reset the time interval.
Owner:ROVI SOLUTIONS CORP
Method and Apparatus for Dynamic Generation of Symmetric Encryption Keys and Exchange of Dynamic Symmetric Key Infrastructure
InactiveUS20100195824A1Avoid decryptionReduce processing timeKey distribution for secure communicationKey exchangeComputer hardware
A method and apparatus for dynamically generating data encryption keys for encrypting data files and for decrypting encrypted data files via a key exchange method is provided. A dynamically generated an encryption key is generated for each encryption event, so that the key cannot be produced or reproduced. A key exchange component of the invention ensures that only an intended recipient has the means to decrypt a file encrypted with the dynamically generated symmetric encryption keys.
Owner:AUTHENEX
Data encryption method and system
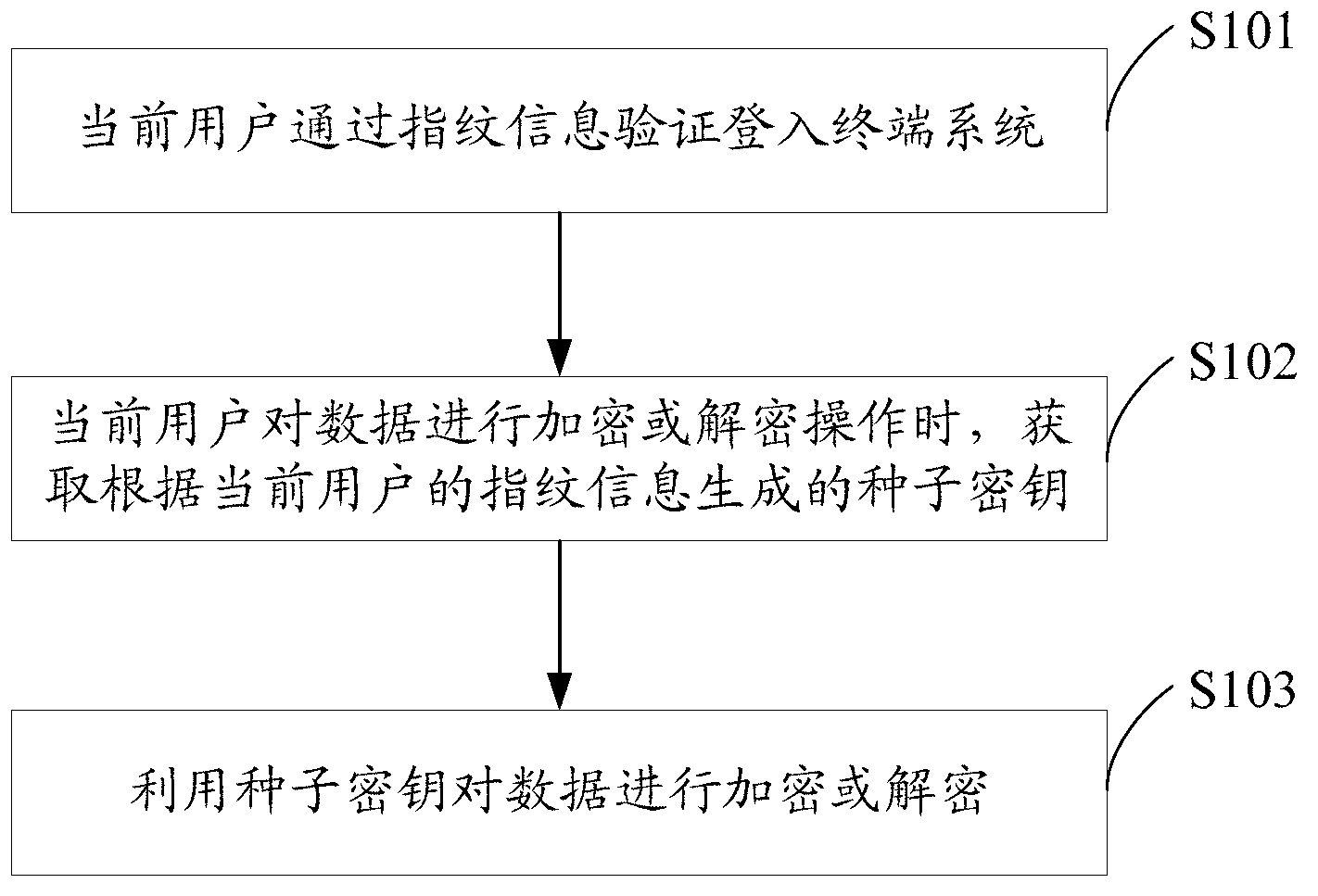
InactiveCN103236930AImprove securityNot easy to loseUser identity/authority verificationCharacter and pattern recognitionComputer scienceTerminal system
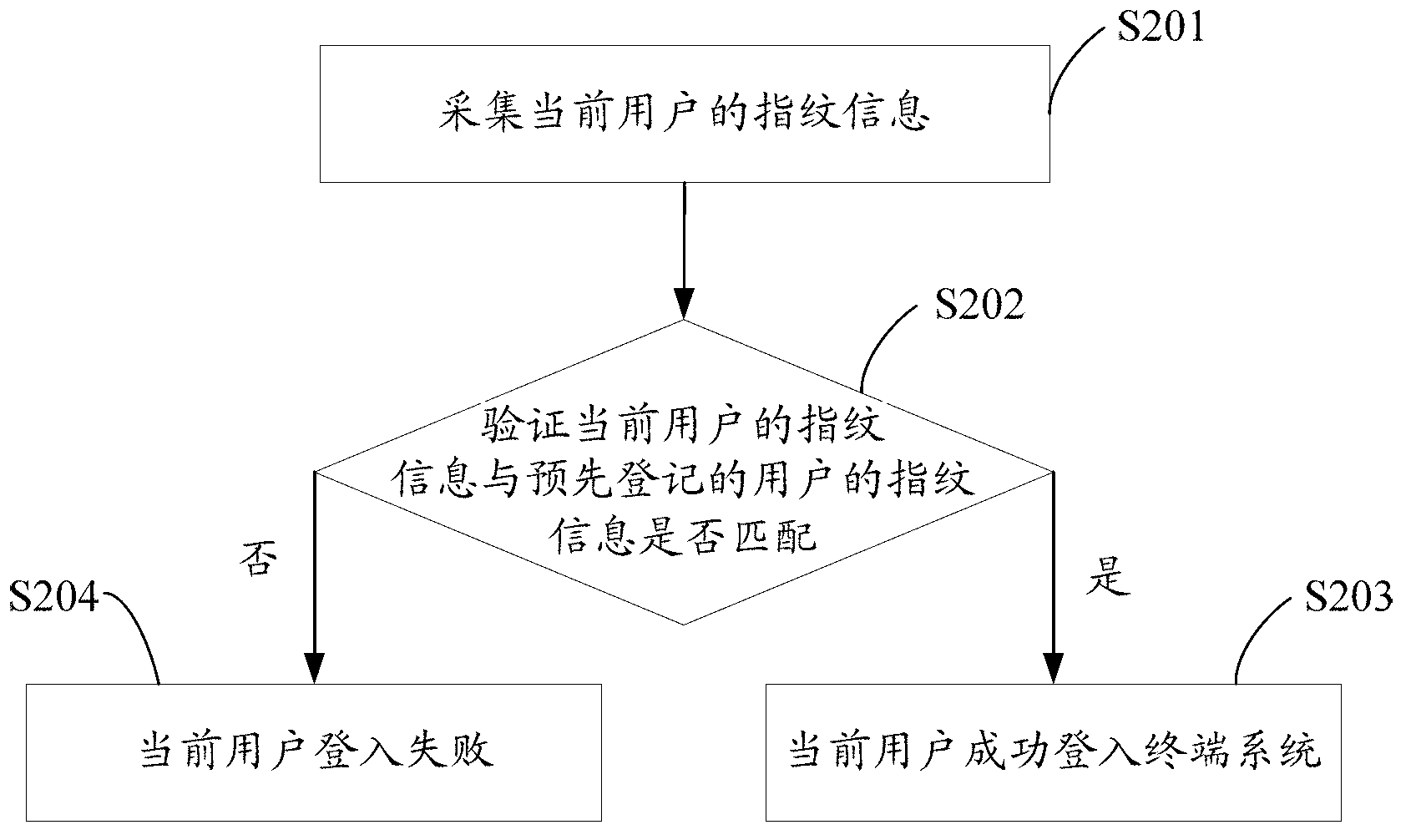
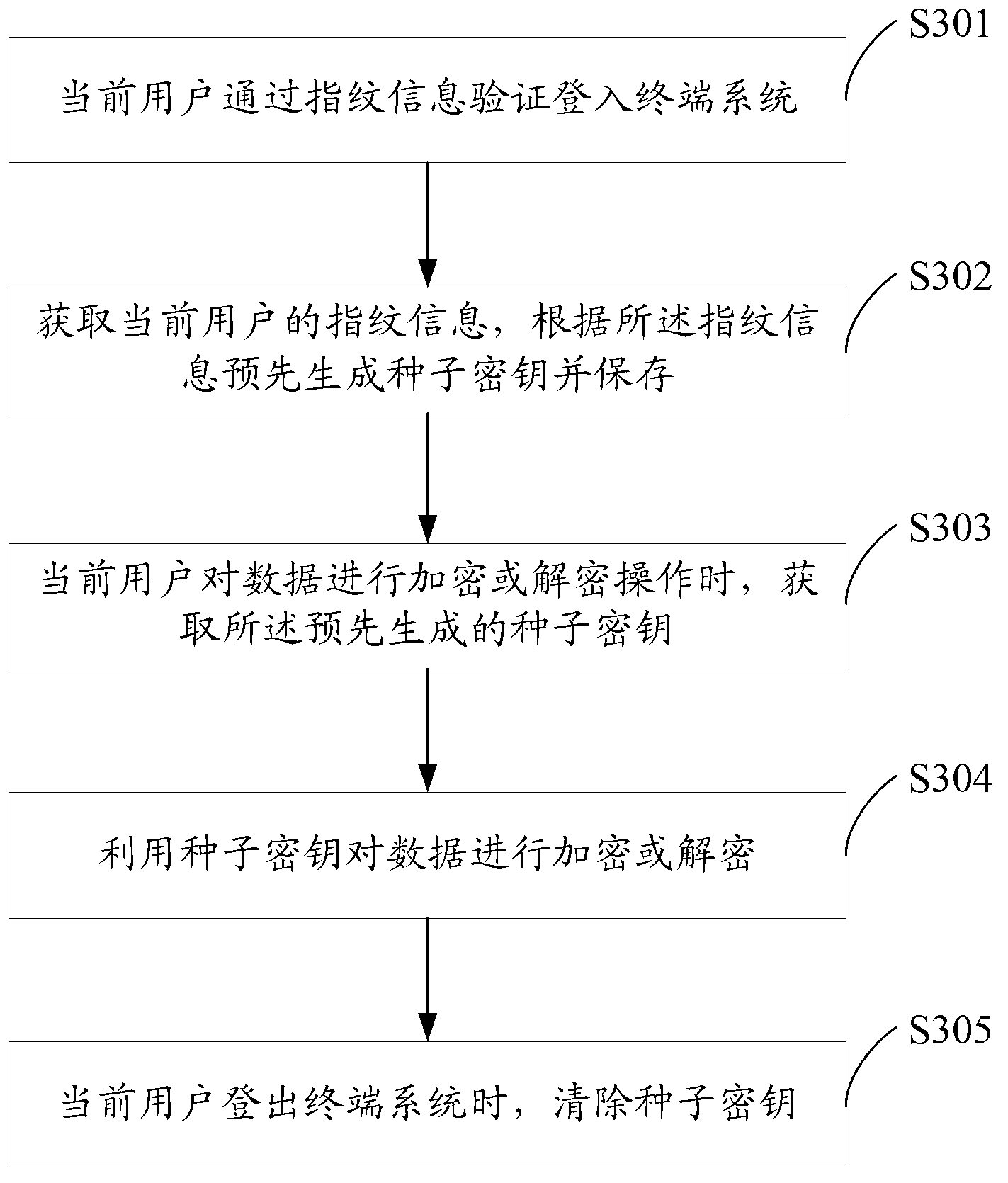
The invention discloses a data encryption method and system. The data encryption method comprises the steps of obtaining a cipher key which is generated according to fingerprint information of a current user when the current user conducts encryption or decryption operation to data; and encrypting or decrypting the data by using the cipher key. Since the fingerprint information of users is different, the cipher keys which are generated according to the fingerprint information are different, i.e. each user owns a unique cipher key and further owns a unique data encryption method. The cipher key is generated according to the fingerprint information through a preset rule in terminal systems. Even though the finger information of the users is illegally copied and stolen, encrypted files in the terminal systems cannot be decrypted in other systems, so that the security of user data is greatly improved.
Owner:NUBIA TECHNOLOGY CO LTD
Efficient Internet-Of-Things (IoT) Data Encryption/Decryption
ActiveUS20210044972A1Lighten the computational burdenAvoid contactUser identity/authority verificationDigital data protectionInternet privacyConfidentiality
Techniques are disclosed for encrypting internet-of-things (IoT) data of an IoT network only once at its inception until its final consumption without intervening encryption / decryption stages / cycles. The present encrypt-decrypt-once design thus eliminates potential exposure of the IoT data in its plaintext form of a traditional approach employing intervening encryption / decryption cycles. The present design is also efficient and reduces the burden on IoT resources by eliminating the need for encrypting and decrypting the data multiple times. To accomplish these objectives, a number of schemes for device enrollment, authentication, key distribution, key derivation, encryption and encoding are disclosed. The devices employ authenticated encryption because it provides confidentiality, integrity, and authenticity assurances on the encrypted data. The final consumption of the IoT data may be at a designated gateway or a corporate system.
Owner:ZETTASET
Encryption device
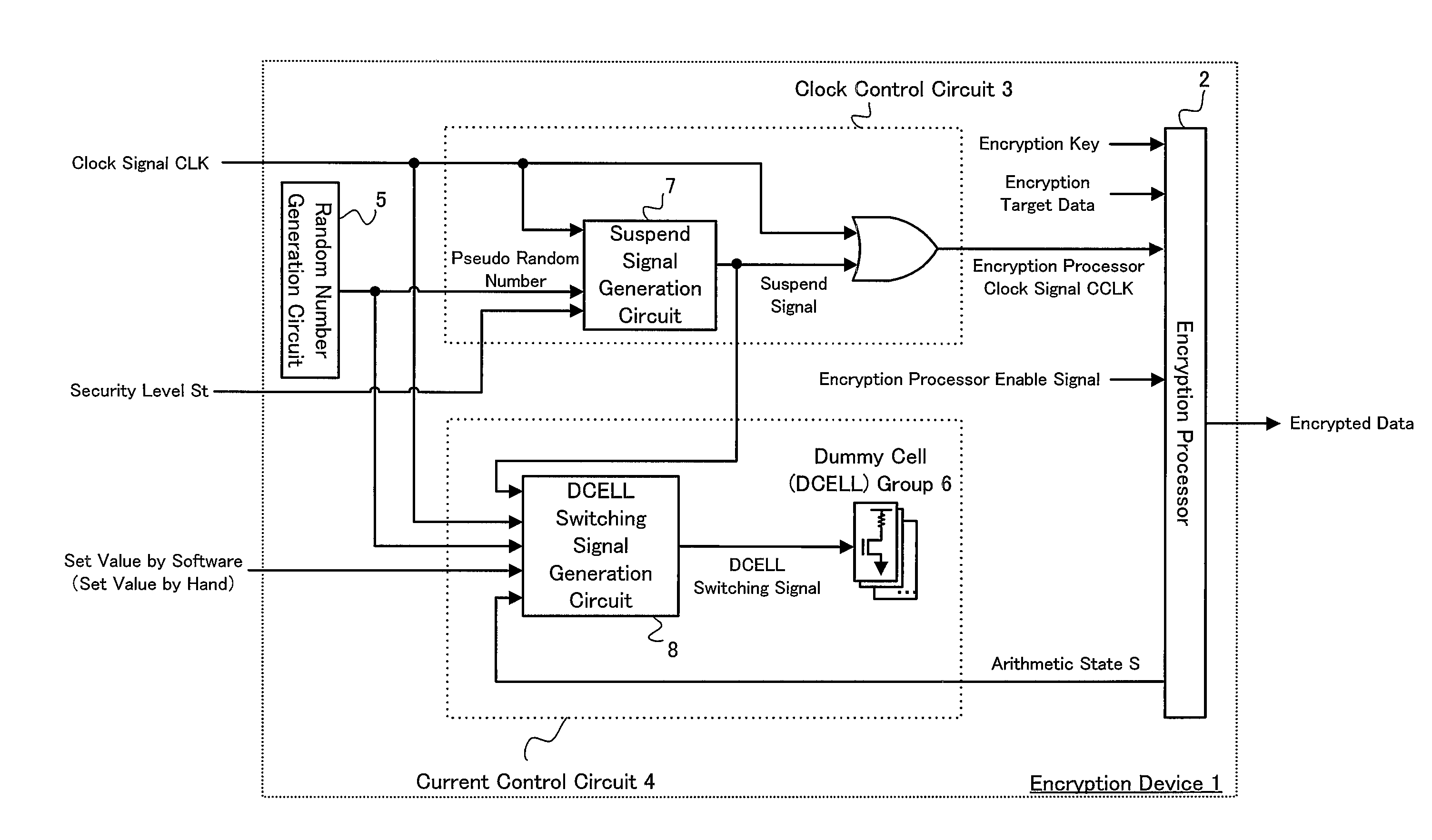
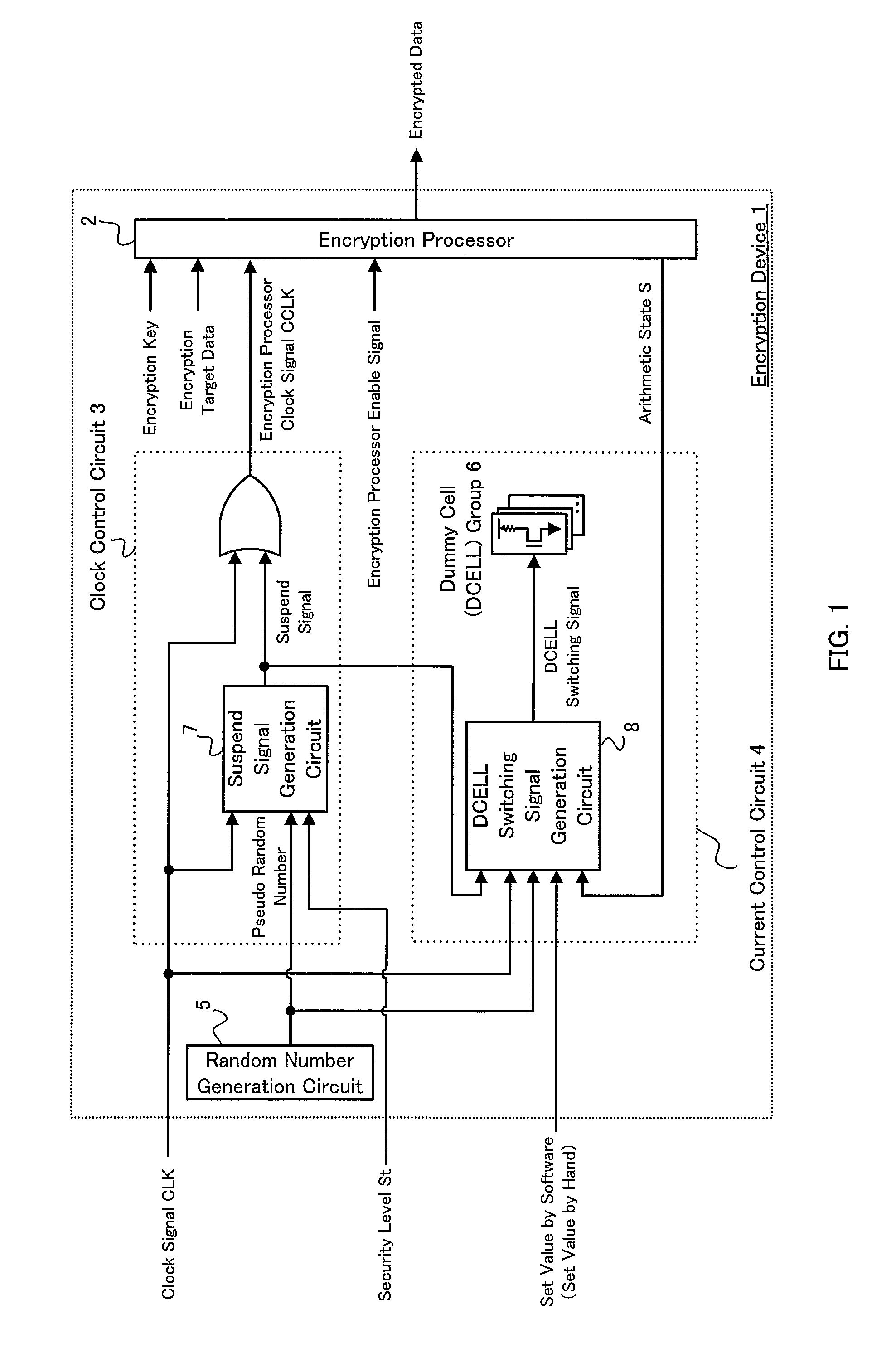
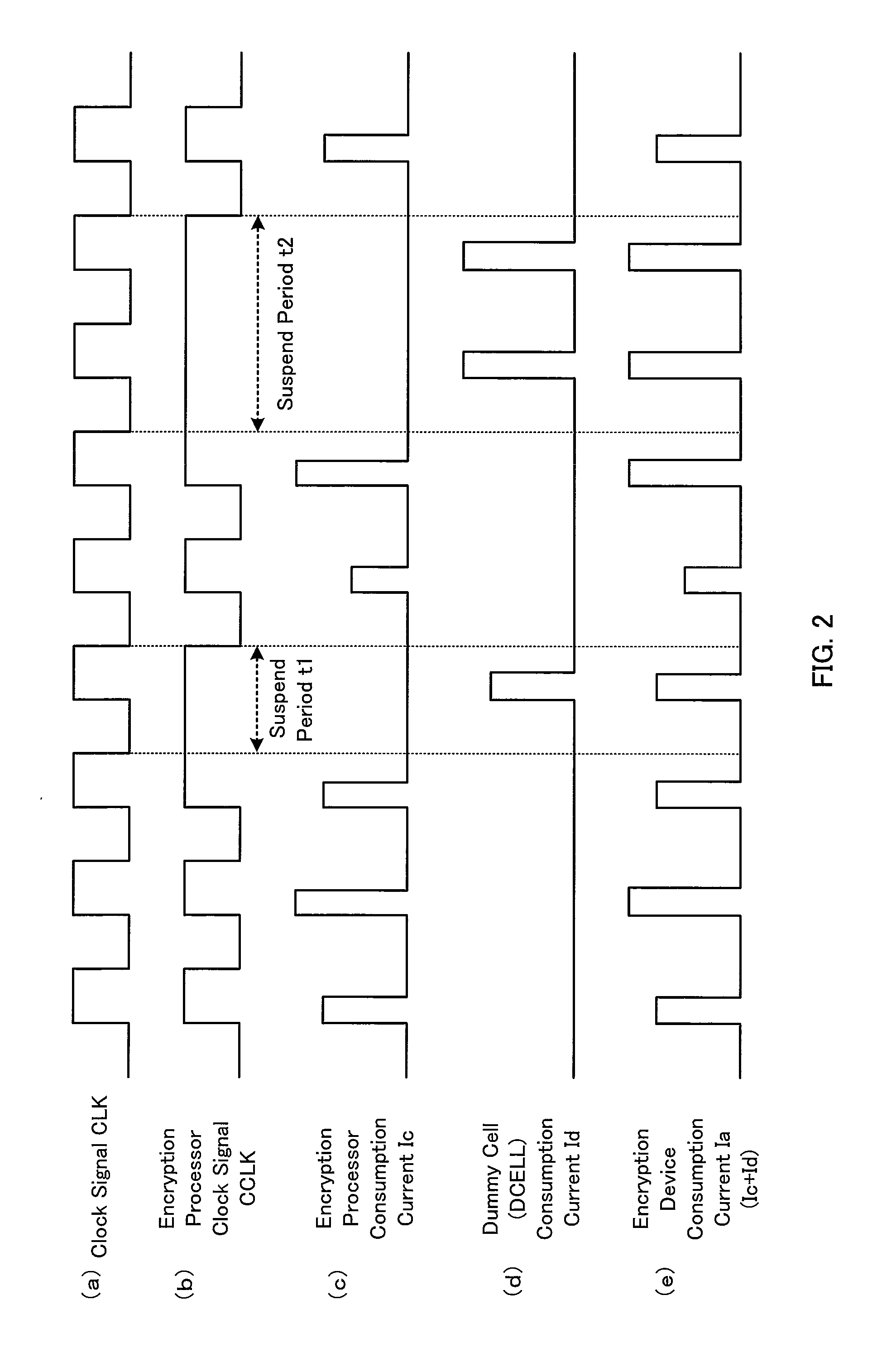
InactiveUS20100067685A1Function increaseAvoid decryptionVolume/mass flow measurementPower supply for data processingCurrent analysisControl circuit
Provided is an encryption device with enhanced function to prevent an encryption key from being decrypted by consumption current analysis, by complicating alignment of consumption current waveforms. The encryption device comprises a clock control circuit adapted to receive a clock signal and a pseudo-random number, and perform a suspend process and a resume process to the clock signal based on the pseudo-random number to generate an encryption processor clock signal; an encryption processor adapted to perform an encryption process to encryption target data in synchronization with the encryption processor clock signal; and a current control circuit adapted to obtain an arithmetic state showing an operational state of the encryption processor to adjust a consumption current amount based on the arithmetic state.
Owner:SHARP KK
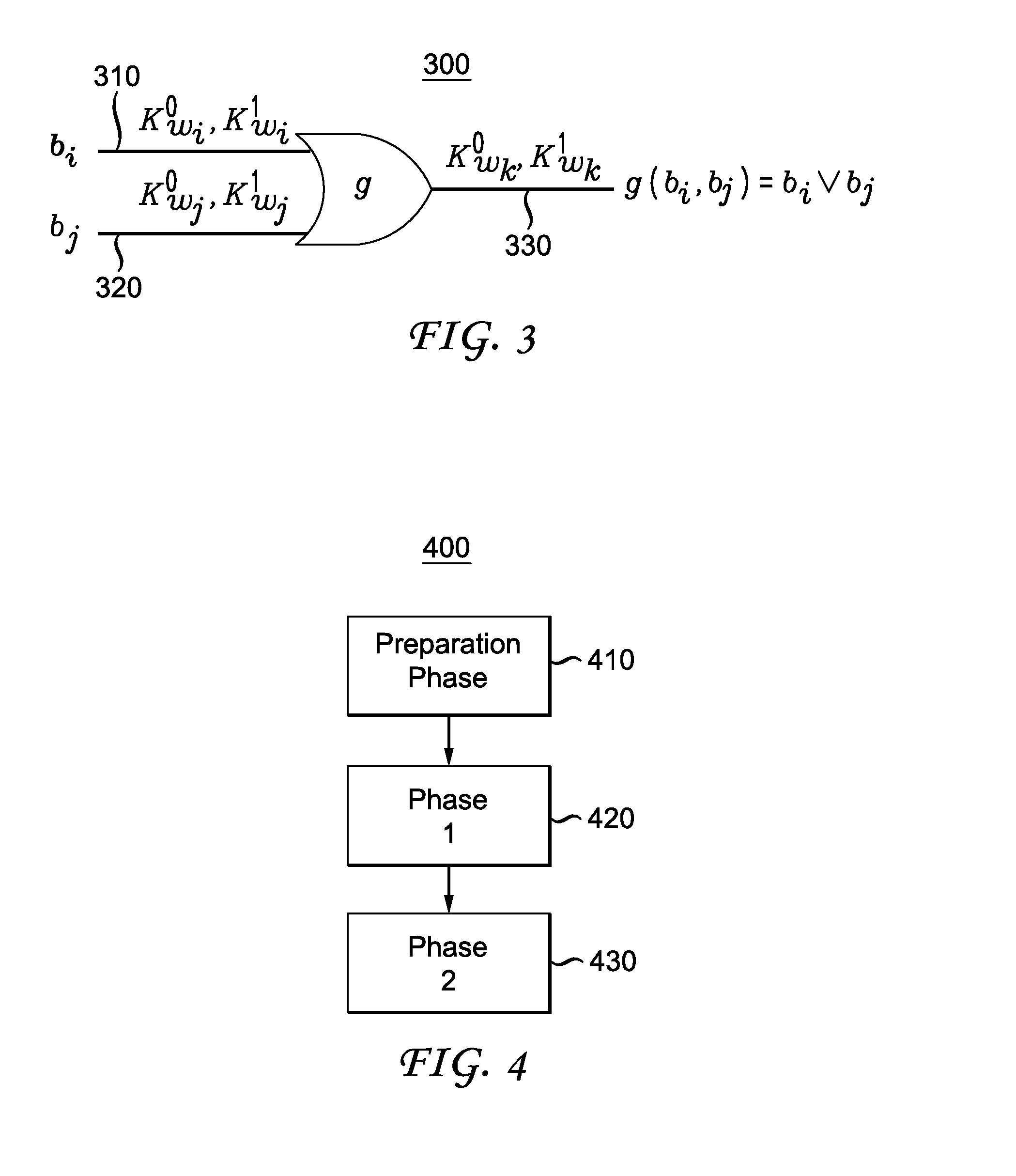
Privacy-preserving ridge regression using masks
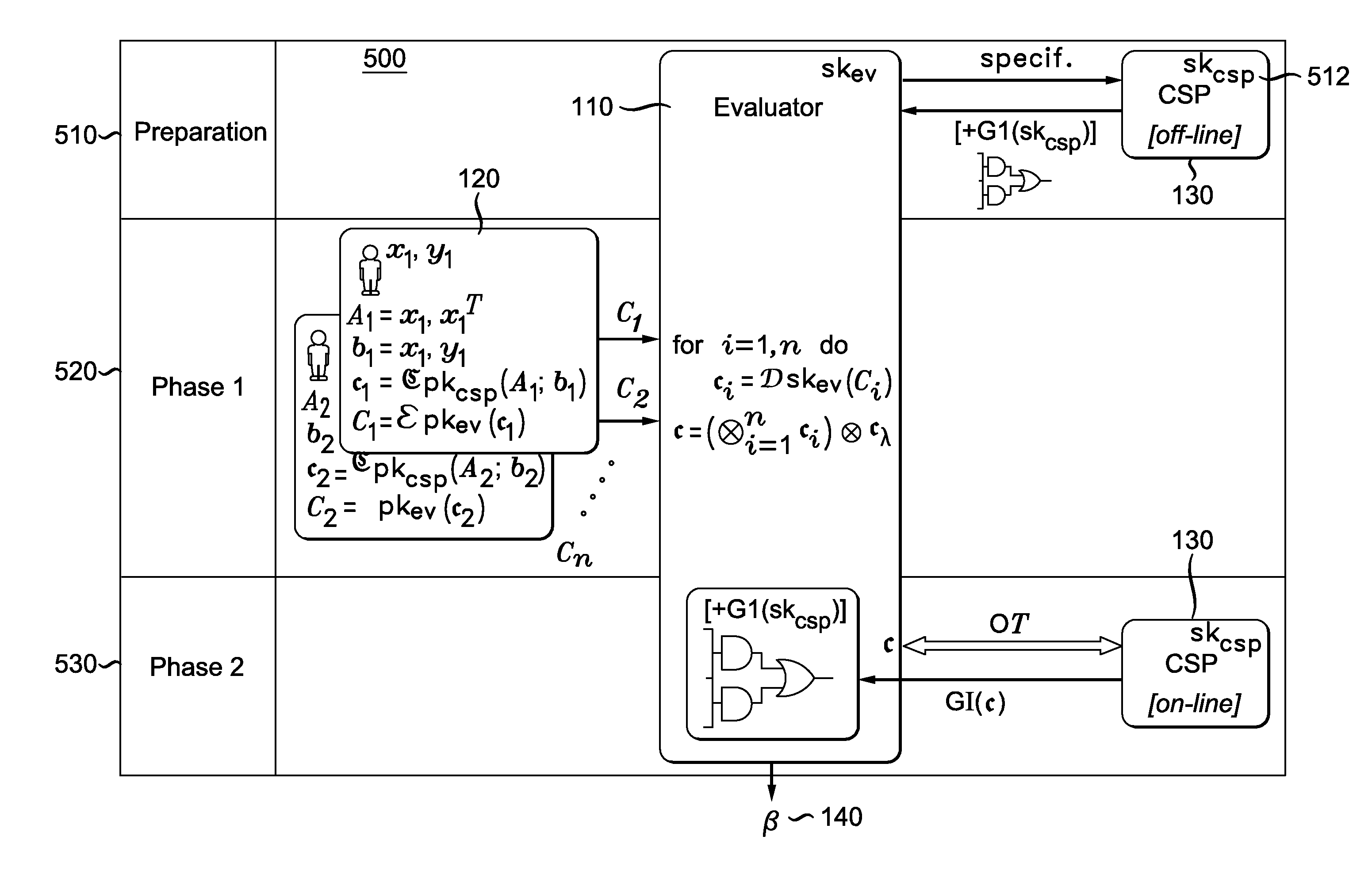
InactiveUS20150381349A1Avoid decryptionFast linearUnauthorized memory use protectionHardware monitoringPrivacy preservingOblivious transfer
A method and system for privacy-preserving ridge regression using masks is provided. The method includes the steps of requesting a garbled circuit from a crypto service provider, collecting data from multiple users that has been formatted and encrypted using homomorphic encryption, summing the data that has been formatted and encrypted using homomorphic encryption, applying prepared masks to the summed data, receiving garbled inputs corresponding to prepared mask from the crypto service provider using oblivious transfer, and evaluating the garbled circuit from the crypto service provider using the garbled inputs and masked data.
Owner:THOMSON LICENSING SA
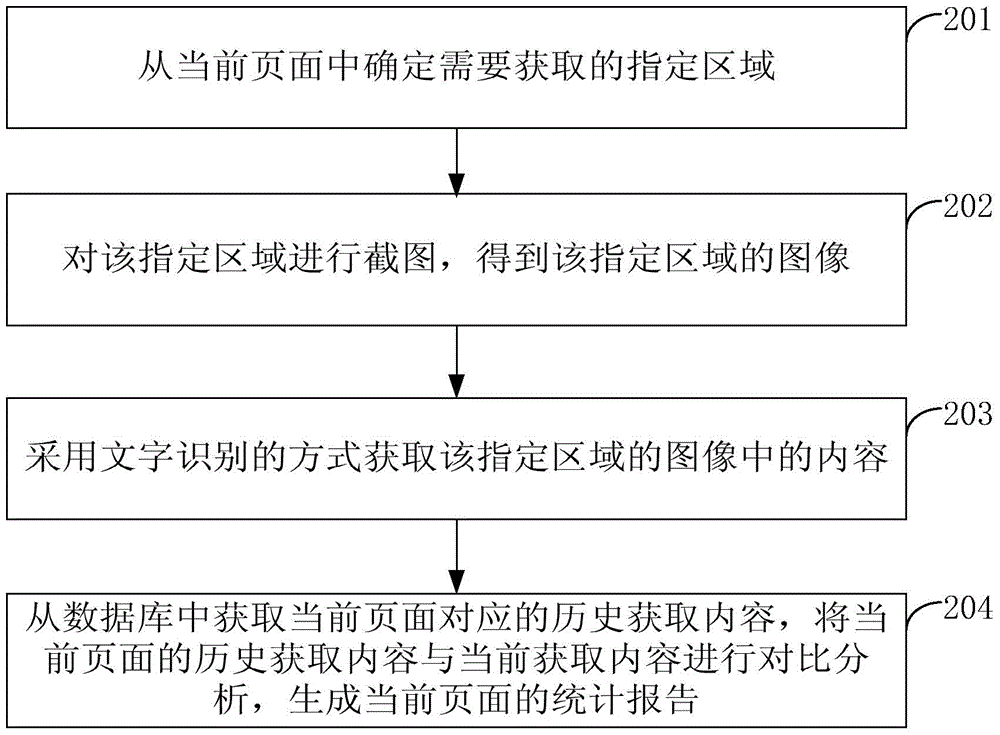
Method and device for acquiring page content
InactiveCN106293365AGet successAvoid decryptionSpecial data processing applicationsInput/output processes for data processingComputer graphics (images)Character recognition
The invention provides a method and a device for acquiring page content. The method comprises the steps of determining a specified area needing to be acquired from a current page; shooting the screen for the specified area, thus acquiring an image of the specified area; and acquiring content of the image of the specified area by a character recognition way. According to the method and device provided by the invention, even the specified area needing to be acquired is encrypted, the image of the specified area needing to be acquired can also be captured, content of the specified area is acquired according to the image of the specified area, successful acquisition of the page content can be ensured, and decryption of the specified area is avoided, so that acquisition efficiency of the page content is improved.
Owner:ALIBABA (CHINA) CO LTD
Method and system for preventing unauthorized recording of media content on a Macintosh operating system
InactiveUS7802095B2Preventing unauthorized recordingAvoid decryptionDigital data processing detailsCryptography processingComputer hardwarePresent method
A method for preventing unauthorized recording of media content on a Macintosh operating system. The present method registers a compliance mechanism on a client system having the Macintosh operating system operating thereon. The compliance mechanism comprises a framework for validating the compliance mechanism on the client system, and a multimedia component opened by the framework. The present method uses the multimedia component for decrypting the media content on the client system. The present method also prevents decryption of the media content on the client system having the Macintosh operating system operating thereon if a portion of the compliance mechanism is invalidated.
Owner:MUSIC PUBLIC BROADCASTING
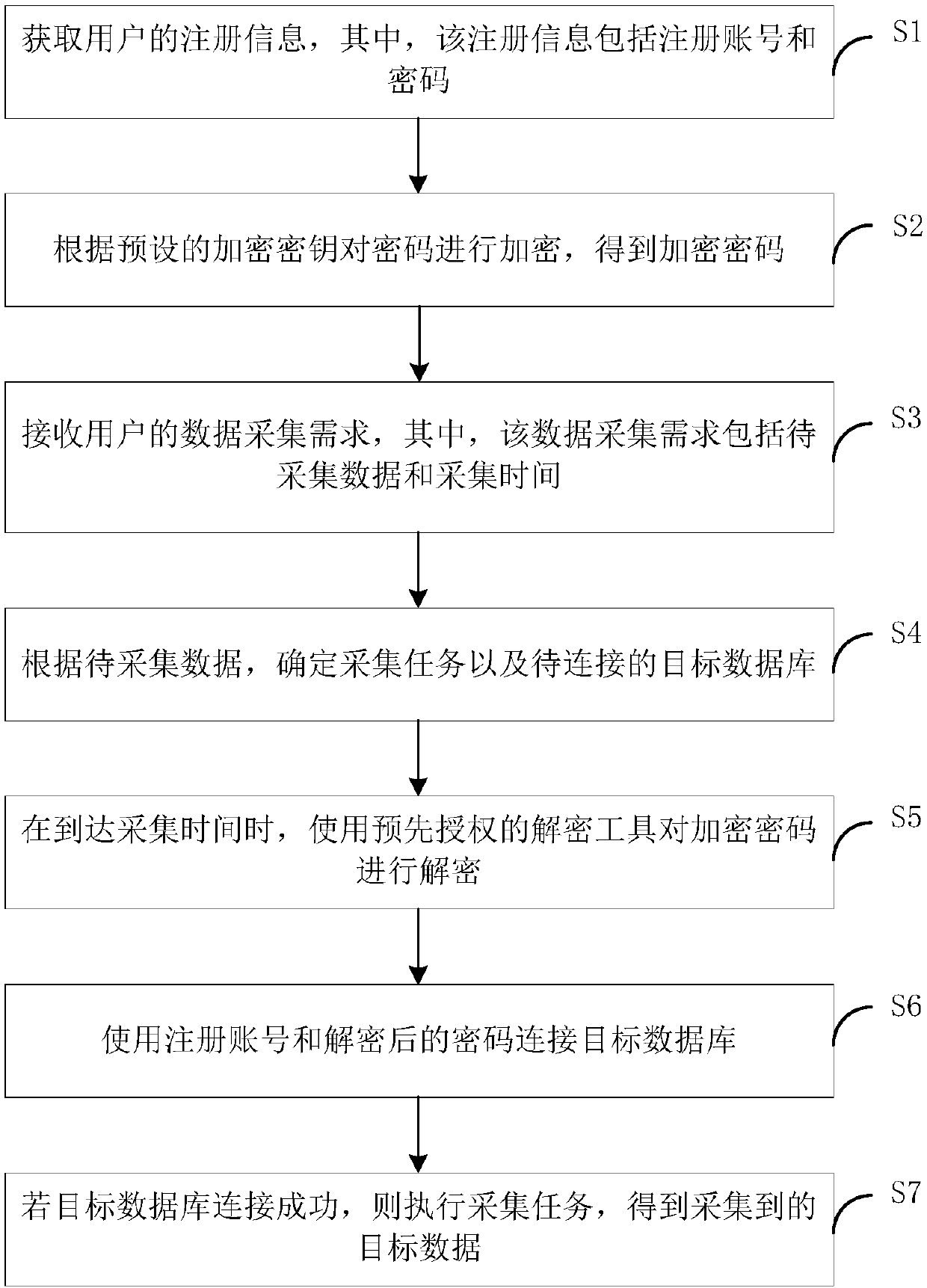
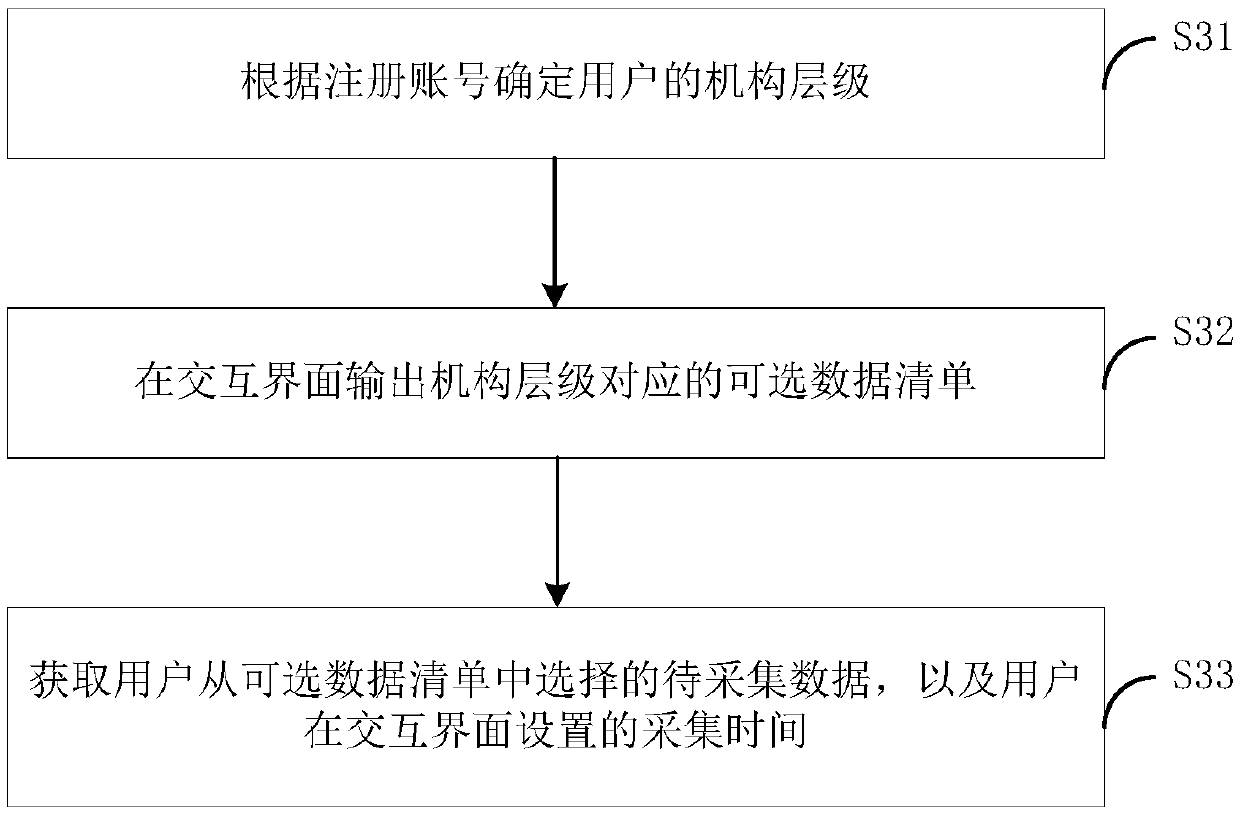
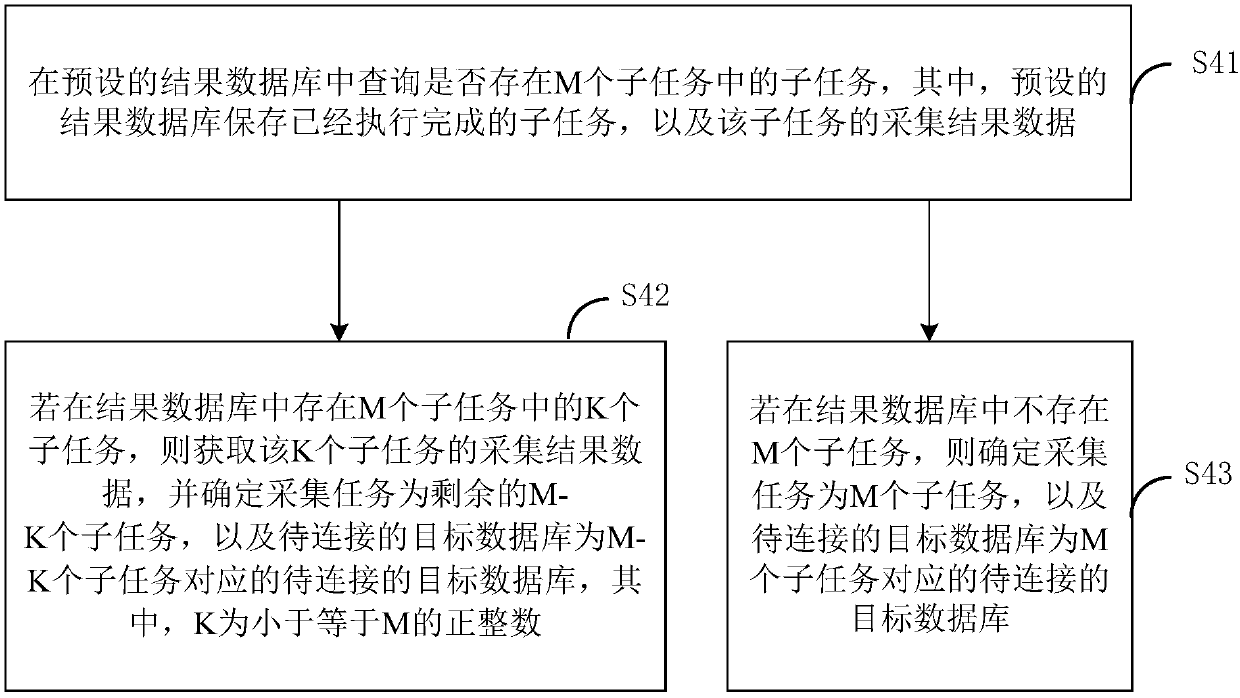
Data collection method and apparatus, terminal device and storage medium
The invention is suitable for the technical field of computers and provides a data collection method and apparatus, a device and a storage medium. The method comprises the steps of obtaining registration information of a user, wherein the registration information comprises a registration account and a password; according to a preset encryption key, encrypting the password to obtain an encrypted password; receiving a data collection demand of the user, wherein the data collection demand comprises to-be-collected data and collection time; according to the to-be-collected data, determining a collection task and a to-be-connected target database; when the collection time is up, decrypting the encrypted password by using a pre-authorized decryption tool; connecting the target database by usingthe registration account and the decrypted password; and if the target database is connected successfully, executing the collection task to obtain collected target data. According to the technical scheme, the leakage risk of the plaintext password is effectively reduced; illegal users are prevented from decrypting the encrypted password; and the data security is improved.
Owner:CHINA PING AN LIFE INSURANCE CO LTD
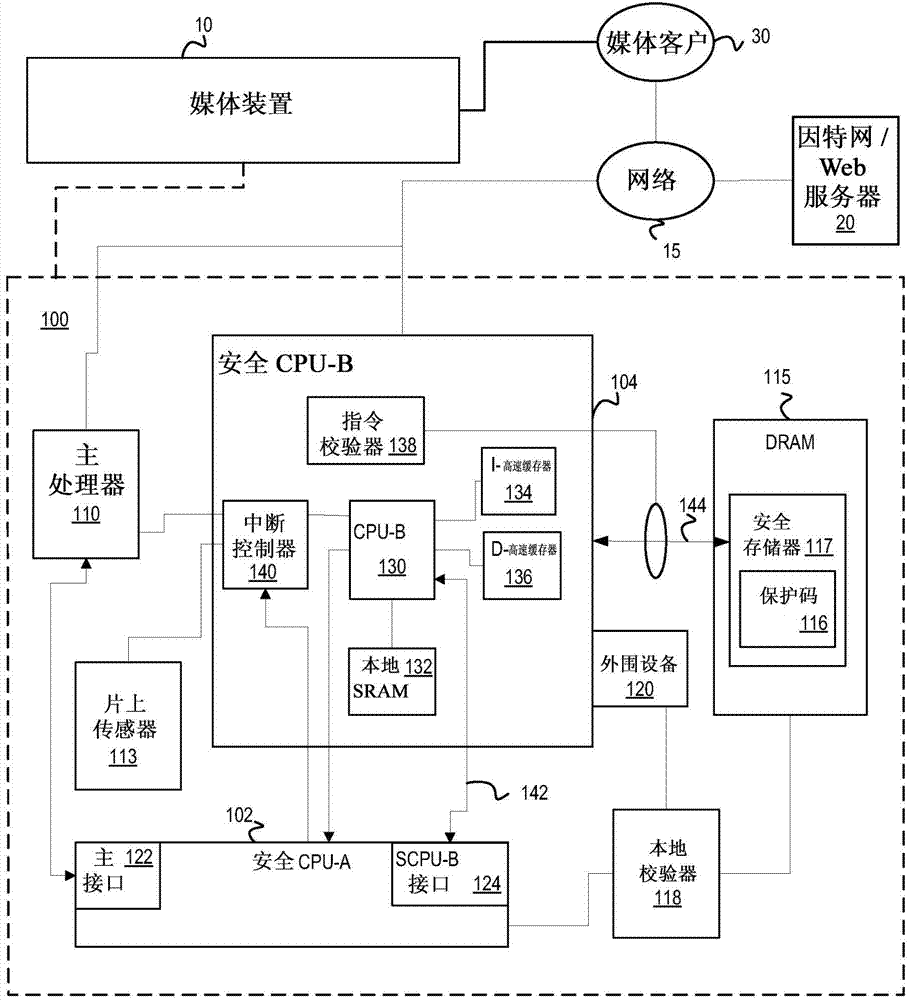
Protecting secure software in a multi-security-CPU system
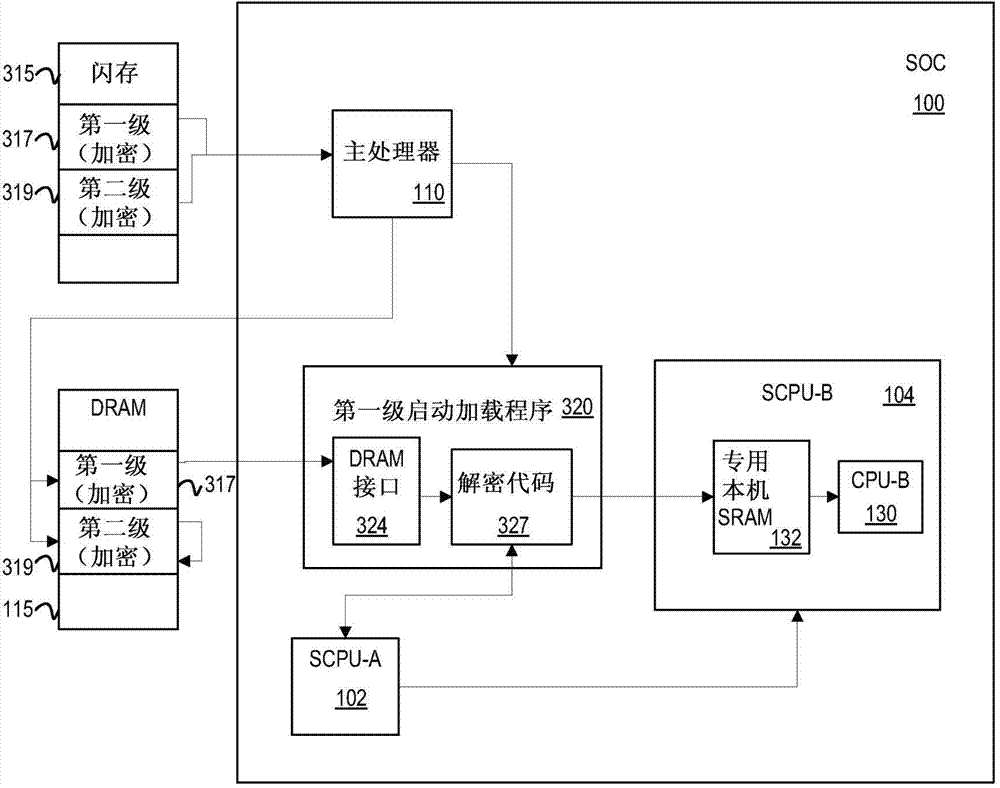
ActiveCN103593603AAvoid decryptionForce writeInternal/peripheral component protectionPlatform integrity maintainanceSecurity softwareBooting
A computing system includes a first central processing unit (CPU) and a second CPU coupled with the first CPU and with a host processor. In response to a request by the host processor to boot the second CPU, the first CPU is configured to execute secure booting of the second CPU by decrypting encrypted code to generate decrypted code executable by the second CPU but that is inaccessible by the host processor.
Owner:AVAGO TECH INT SALES PTE LTD
Public key cryptographic methods and systems
InactiveUS20050220300A1Avoid decryptionSecure communication to robust and efficientDigital data processing detailsPublic key for secure communicationSecure communicationDigital signature
Systems and methods are disclosed for establishing secure communications to a group rather than to an individual recipient. The systems and methods presented include mechanisms for encryption to a group, decryption by one or more group members, digital signature generation and verification, and the addition / removal of group members.
Owner:CRYPTOIP
Electronic book downloading method and purchasing system
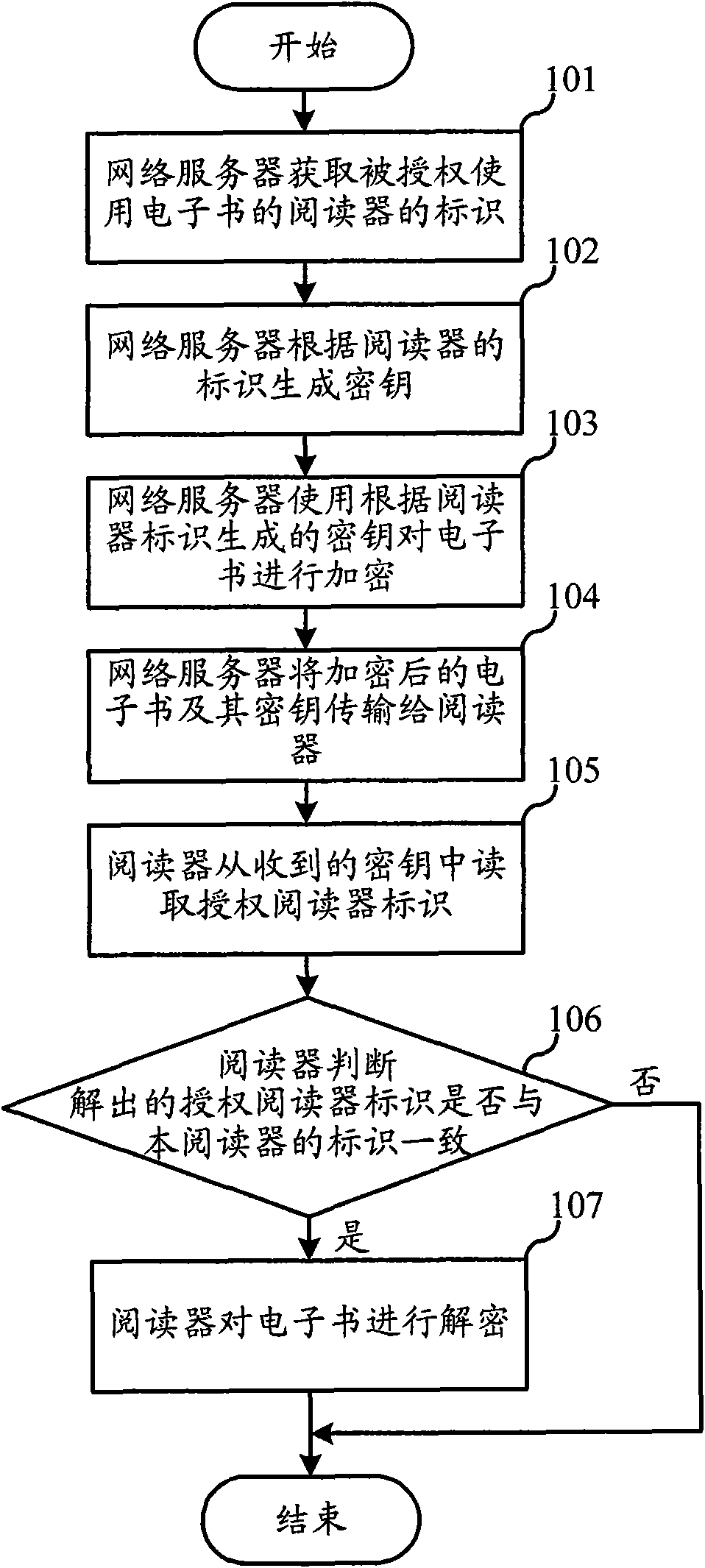
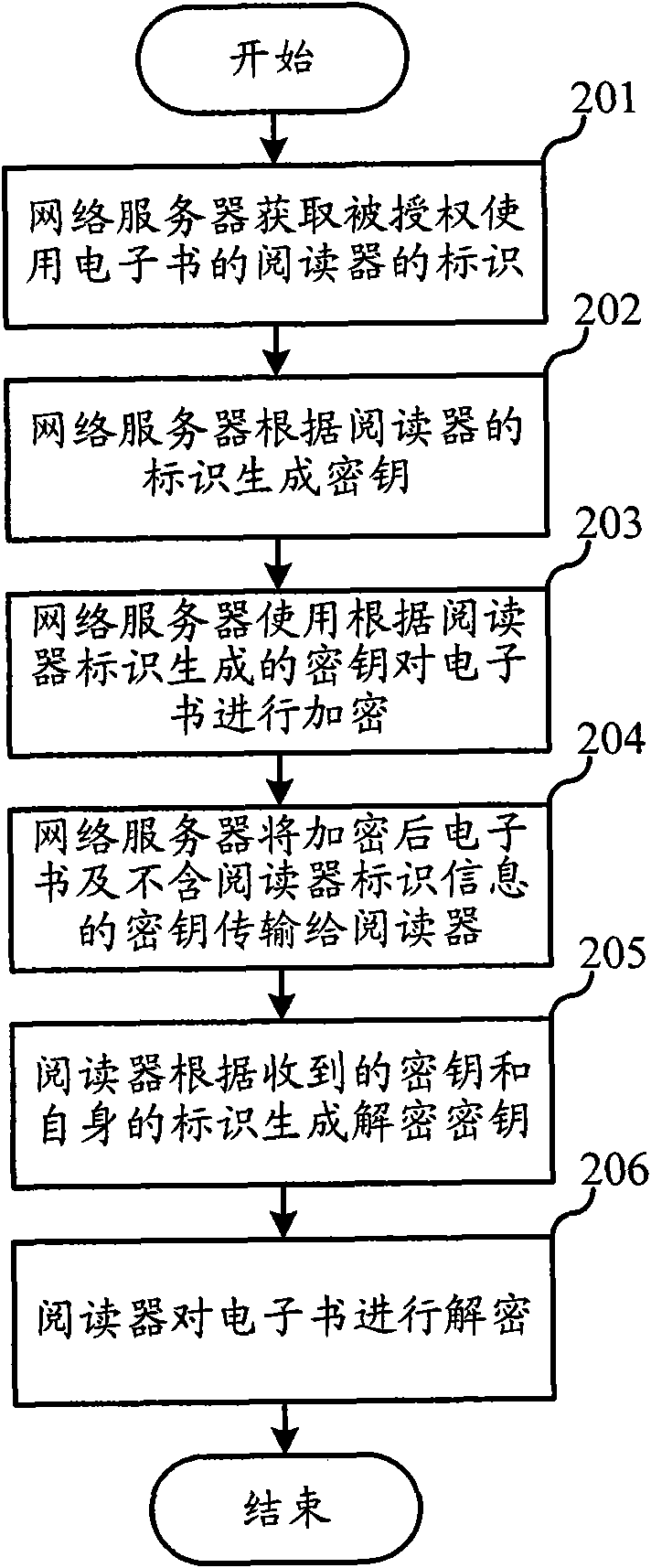
InactiveCN101894222AWill not copyNo piracyEncryption apparatus with shift registers/memoriesProgram/content distribution protectionElectronic bookPurchasing
The invention relates to the field of electronic book distribution and discloses an electronic book downloading method and a purchasing system. In the invention, a key is generated according to the mark of a reader, thus, an encrypted electronic book can only be decrypted by the appointed reader, thereby protecting the downloaded electronic book from being copied and pirated. Before the decryption of the reader, the mark of the authorized reader is read from the key and compared with the mark per se, and the electronic book is decrypted when both the marks are consistent, thereby preventing the electronic book from being decrypted by the unauthorized reader.
Owner:扬州易狄欧电子科技有限公司
File encryption method, file decryption method, file encryption device and equipment
InactiveCN106372517AAvoid EncryptionImprove encryption efficiencyDigital data protectionComputer hardwareEncryption
The invention discloses a file encryption method, a file decryption method, a file encryption device and equipment. The method comprises the following steps: obtaining a to-be-encrypted file; generating a secrete key, an offset value and a sampling value; determining the to-be-encrypted field in the to-be-encrypted file according to the offset value and the sampling value; and encrypting the to-be-encrypted field according to the secrete key. According to the invention, the file encryption efficiency can be improved.
Owner:BEIJING XIAOMI MOBILE SOFTWARE CO LTD
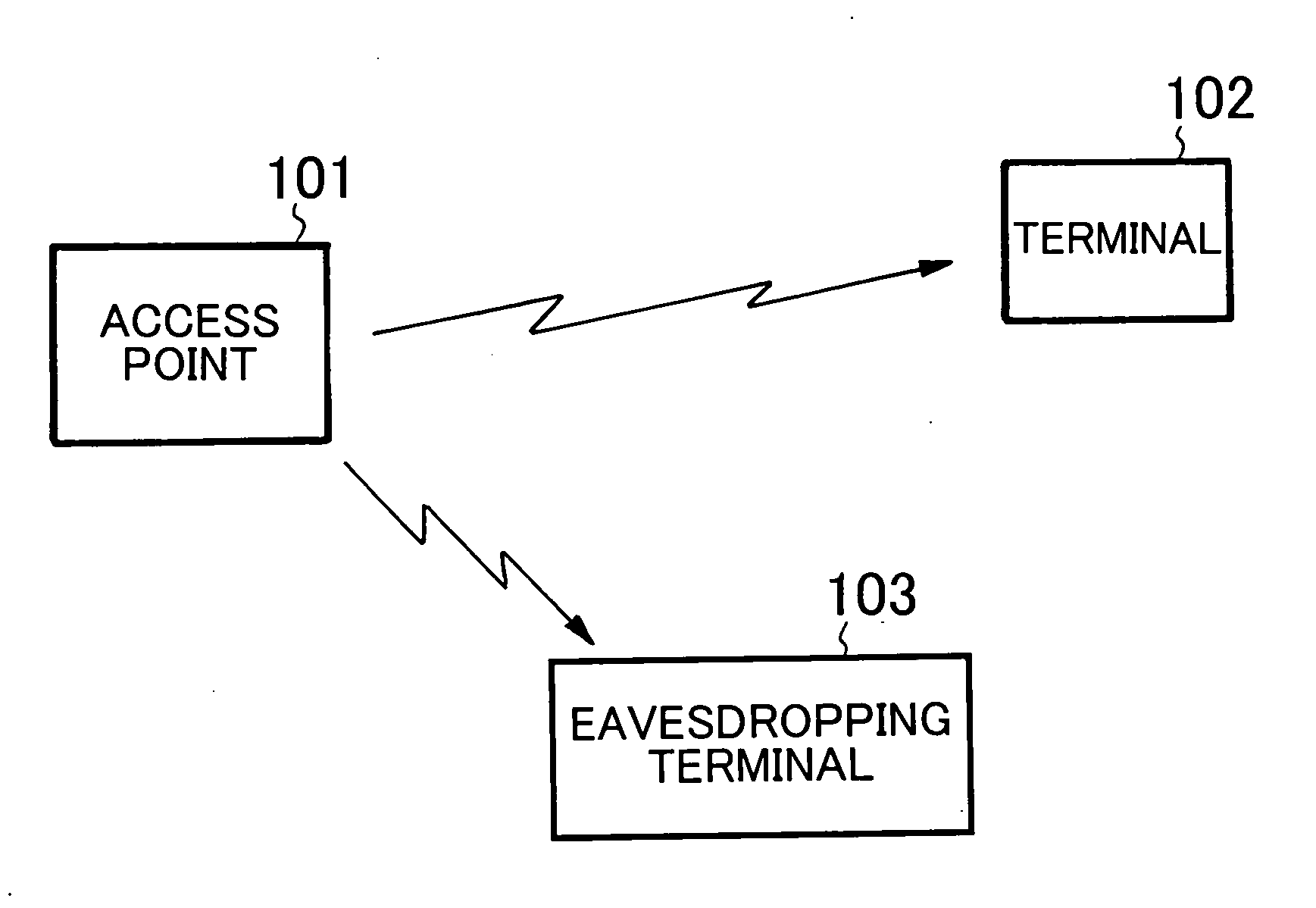
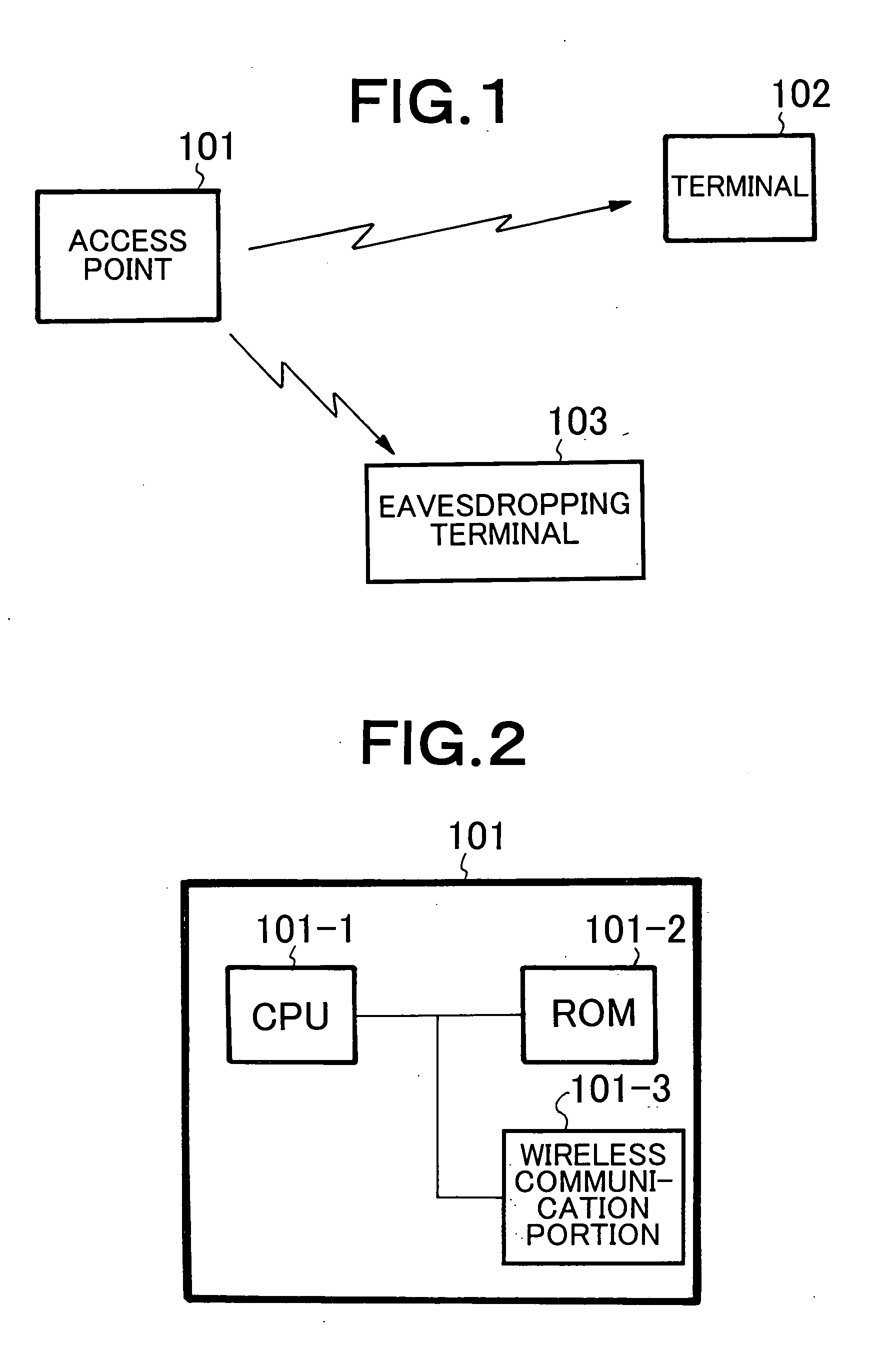
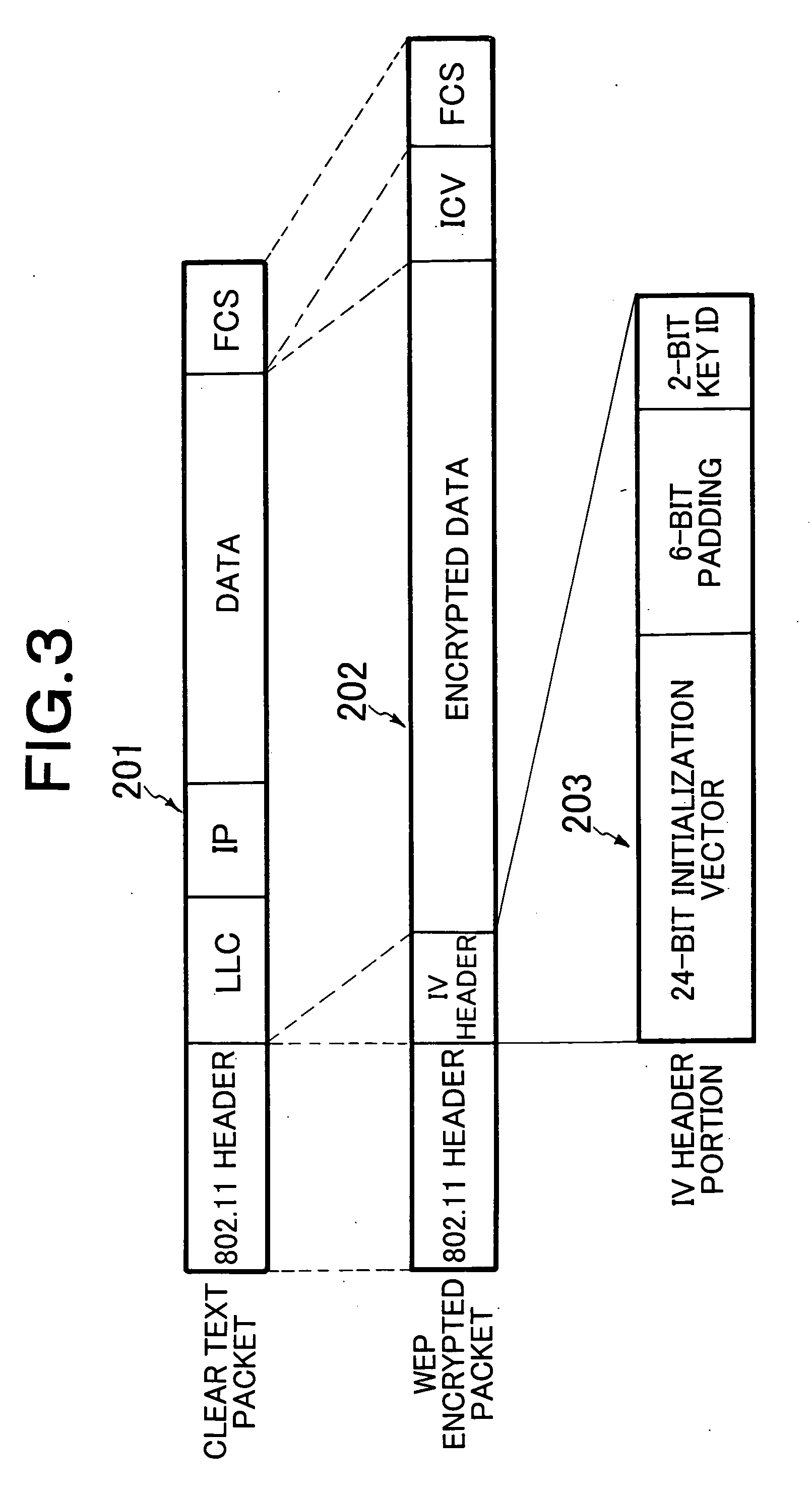
Method for preventing eavesdropping in wireless communication system
InactiveUS20060002559A1Avoid problemsAvoid decryptionNetwork topologiesSecret communicationCommunications systemWired Equivalent Privacy
A wireless communication system includes an access point 101 and a terminal 102 exchanging, with the access point 101, a packet encrypted with an encryption key that has been previously set on the basis of a Wired Equivalent Privacy (WEP). When receiving the packet, the access point 101 determines whether the received packet includes a Weak Initial Vector (Weak IV) having a specified bit pattern. When the packet includes the Weak IV, the access point 101 transmits a disturbing signal for preventing the packet from being eavesdropped.
Owner:NEC CORP
Method for hiding mass information by using remote sensing image
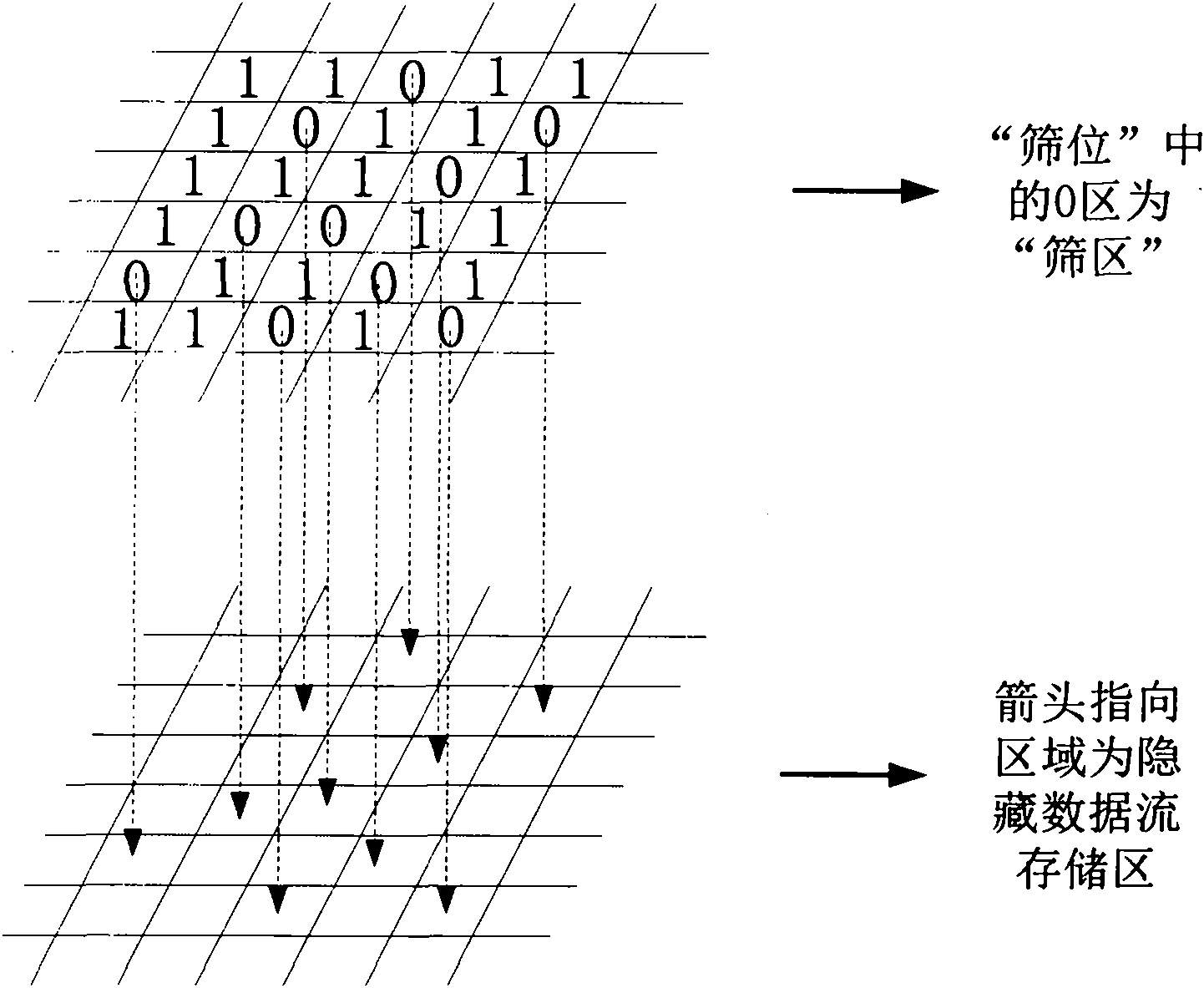
InactiveCN101840564AStrong concealmentAchieve hiddenWave based measurement systemsImage data processing detailsHidden dataComputer science
The invention relates to a method for hiding mass information by using a remote sensing image and belongs to the field of information hiding in pattern recognition and data encryption of information sciences. The method is characterized in that mass confidential files are stored in a remote sensing image file to have strong concealment; data is only stored in characteristic areas of the image file; and the hidden data is subjected to random encryption in advance and the encryption sites of an encrypted image still reserve the characteristics of an original image, so that the encrypted image has little appearance change to avoid being identified and decrypted and provide a security guarantee for the storage and transmission of private information. In addition, the invention also provides a method for extracting remote sensing image hidden information based on the method for hiding the mass information, which can effectively extract the hidden information and is simple and easy to implement.
Owner:NANJING UNIV
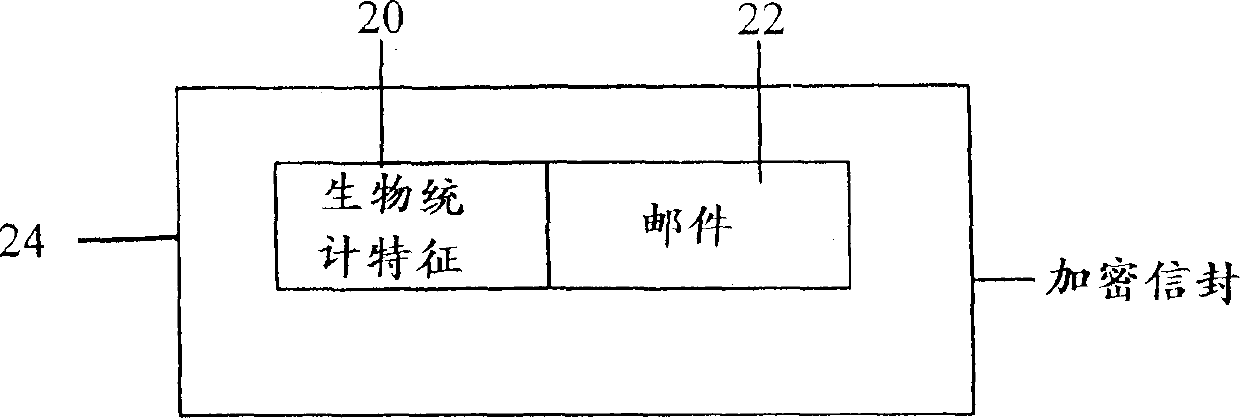
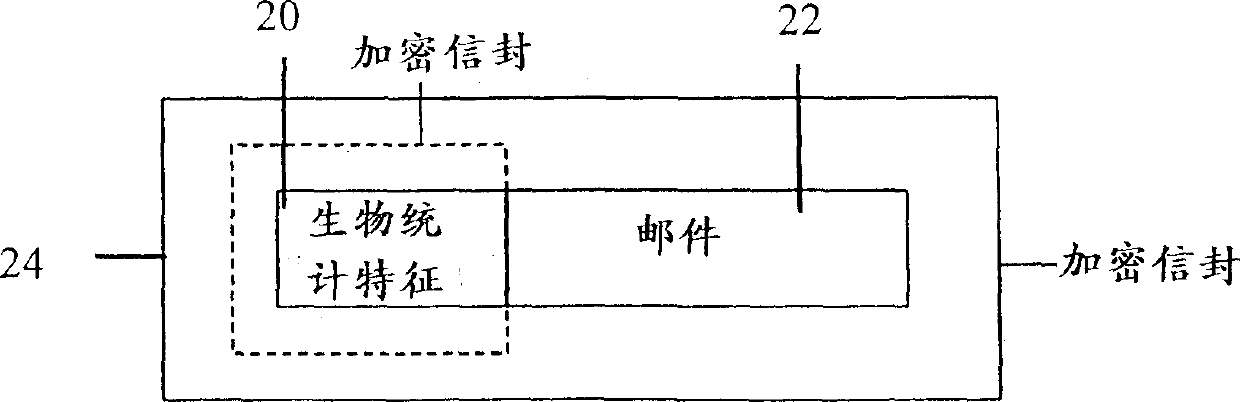
A system and method for authenticating electronic documents
InactiveCN1419664AAvoid decryptionDigital data processing detailsDigital data protectionElectronic documentNetwork packet
A method for securing an electronic document ( 22 ) comprising attaching a biometric characteristic ( 20 ) and the electronic document ( 22 ) to form a biometric characteristic-document combination and encrypting the biometric characteristic-document combination to form an encrypted data package ( 24 ).
Owner:XYGON COMP
Mobile Internet public opinion monitoring method and system based on URL
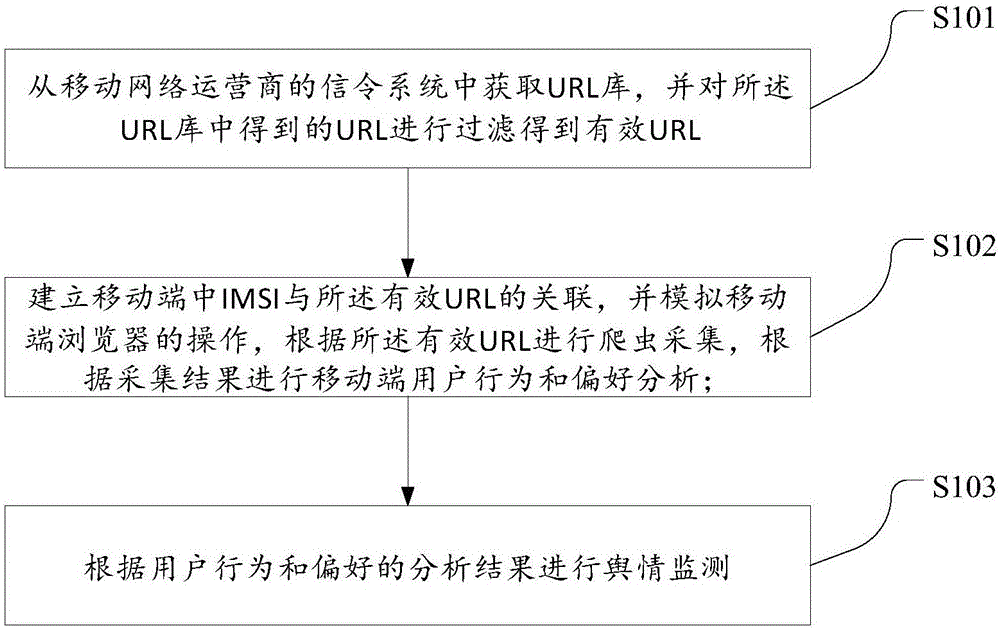
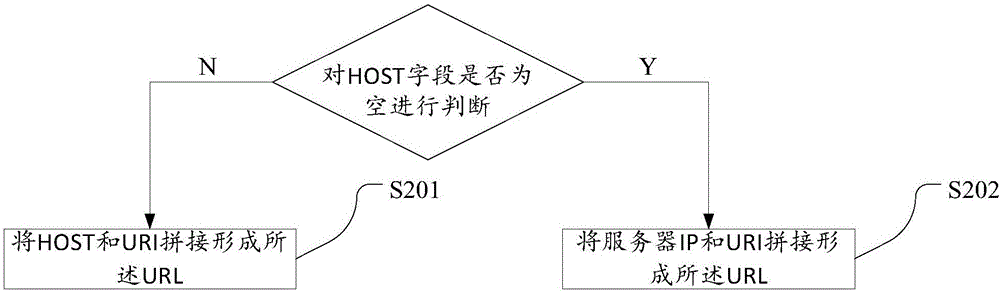
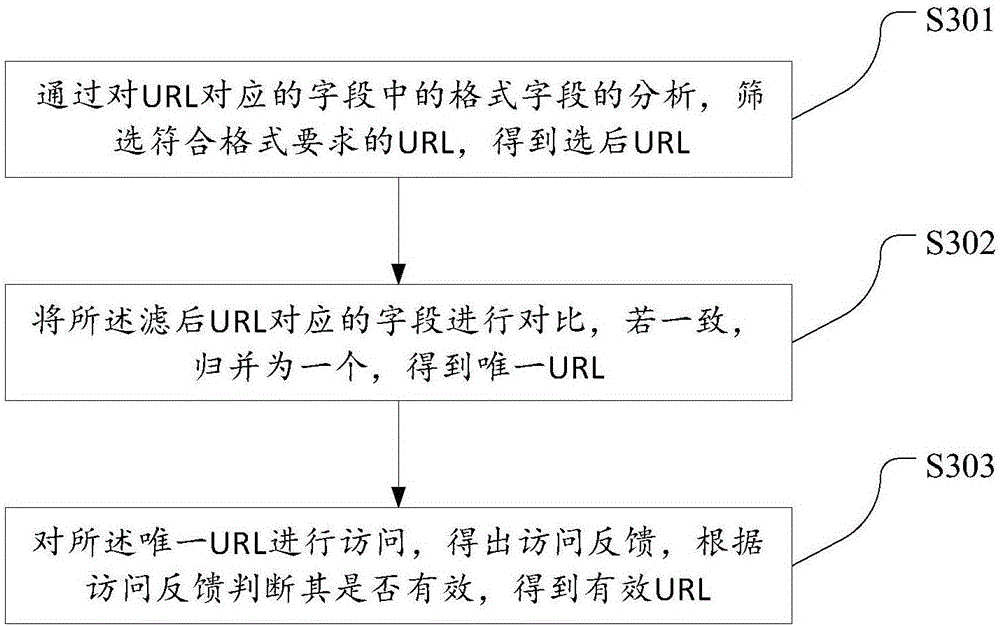
ActiveCN106230809AEfficient collectionAvoid decryptionTransmissionMobile endUniform resource locator
The invention discloses a mobile Internet public opinion monitoring method and system based on a URL. The method comprises following steps: obtaining a URL library from a signaling system of a mobile network service provider, and filtering URLs obtained from the URL library to obtain effective URLs; establishing association between an IMSI of a mobile terminal and the effective URLs, simulating operation of a mobile terminal browser, performing crawler acquisition according to the effective URLs, and performing user behavior and preference analysis of the mobile terminal according to an acquisition result; and performing public opinion monitoring according to a user behavior and preference analysis result. The beneficial effects of the method and system are that firstly, manual control and operation can be prevented; and users can use the method and system without professional knowledge, and the technical threshold is low; secondly, the number of the URLs in need of acquisition is greatly reduced so that the pressure of crawler acquisition is greatly relieved; and thirdly, web crawlers can effectively acquire content of the URLs in the mobile network.
Owner:快页信息技术有限公司
Image recording system and image recording apparatus
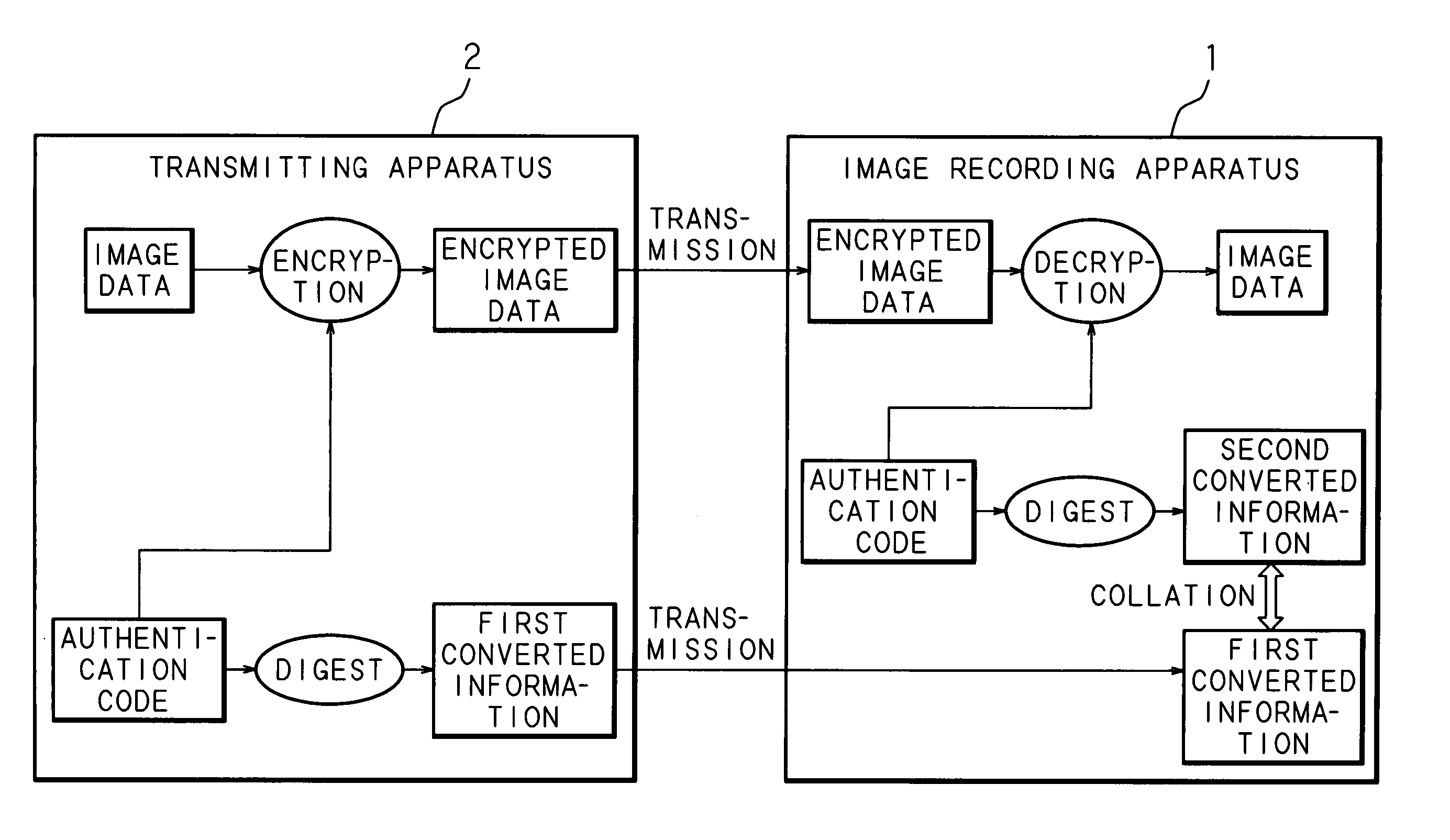
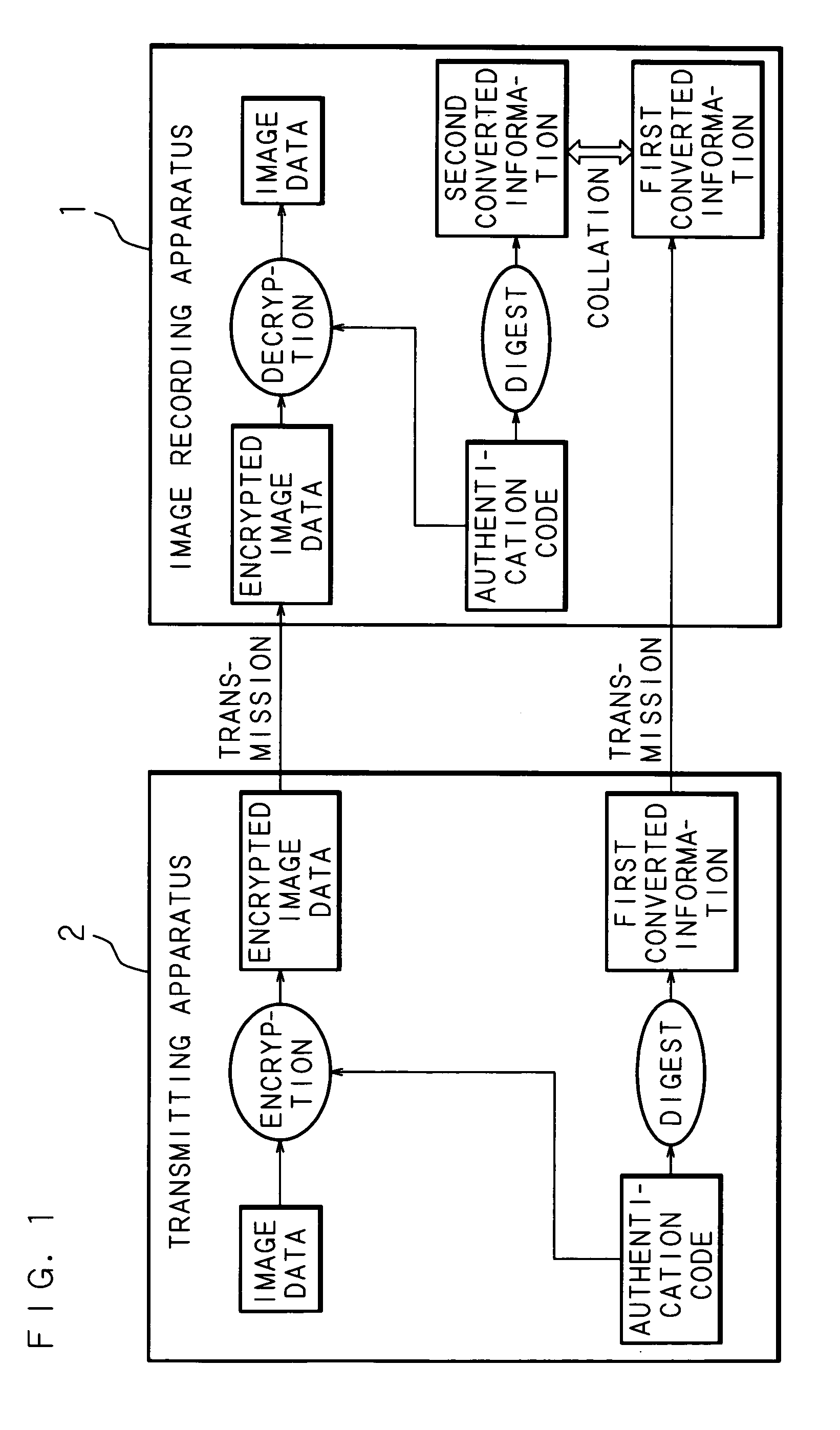
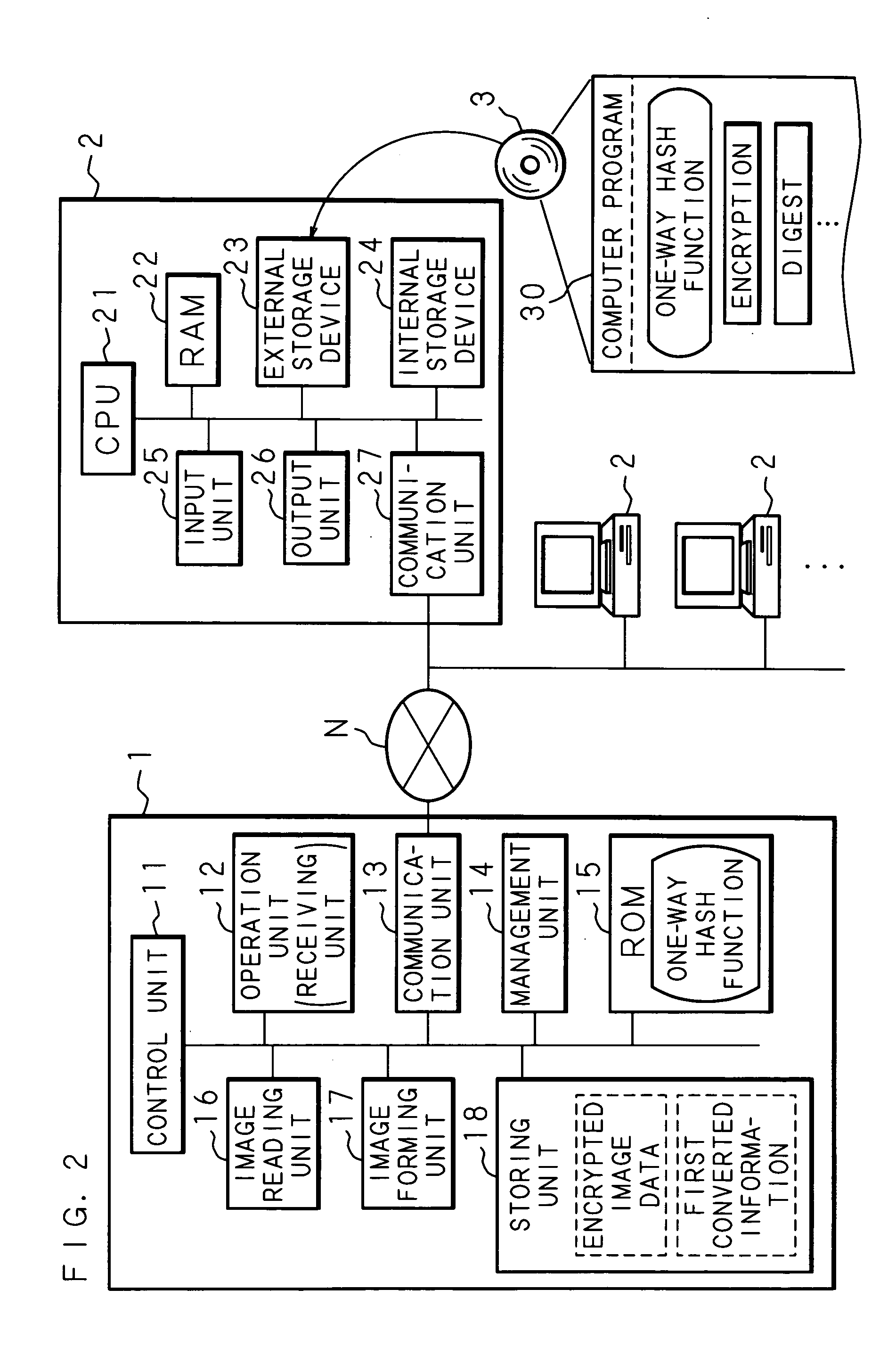
InactiveUS20060210244A1Avoid decryptionTelevision system detailsColor television signals processingComputer hardwareImage recording
A transmitting apparatus transmits encrypted image data created by encrypting image data by using an authentication code as an encryption key and the first converted information created by digesting the authentication code by using a one-way function to an image recording apparatus. The image recording apparatus creates the second converted information by digesting an authentication code received directly from the user by using a one-way function, decrypts the received encrypted image data into image data by using the received authentication code as a decryption key if the created second converted information and the received first converted information coincide, and creates and records an image based on the decrypted image data.
Owner:SHARP KK
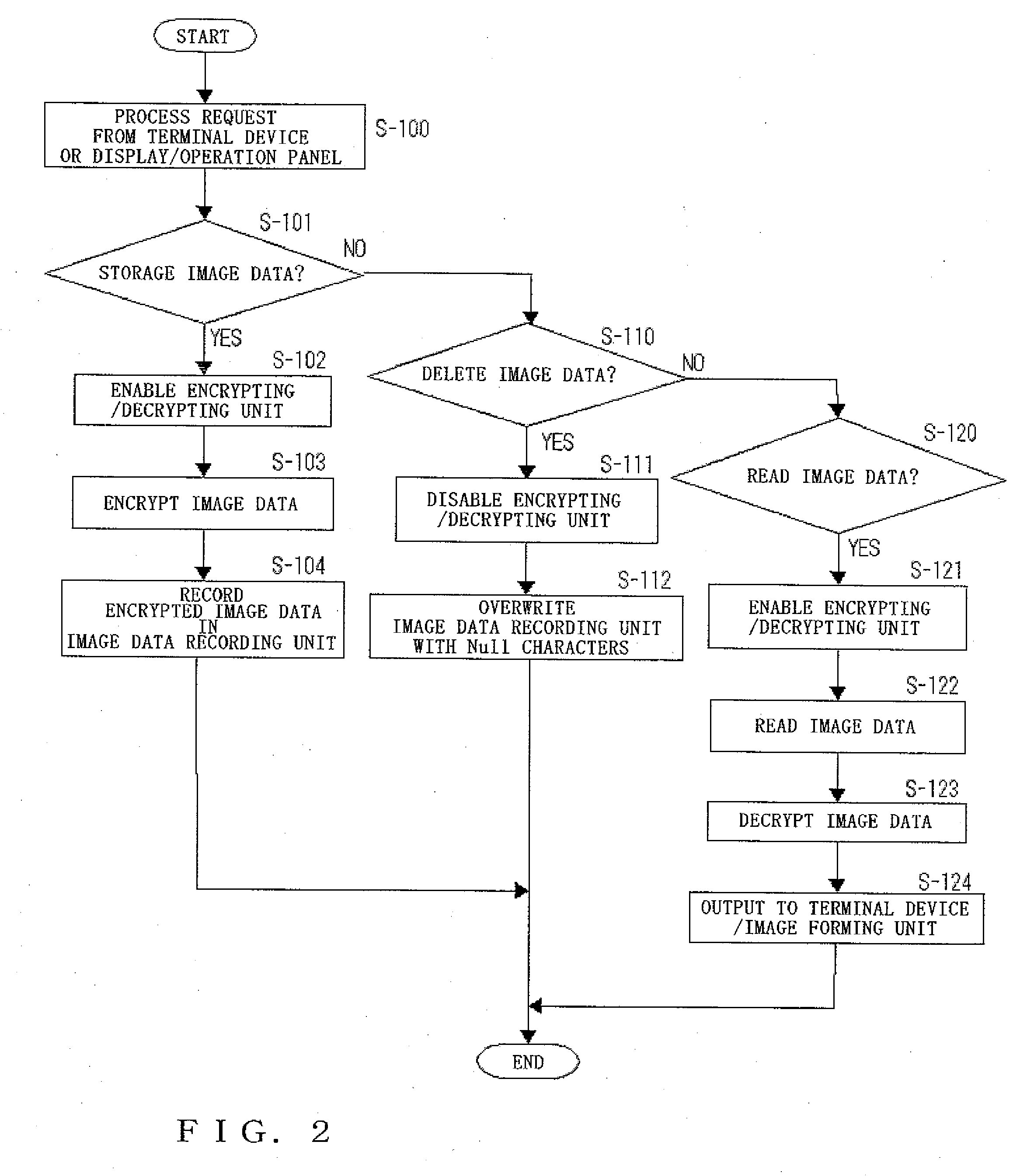
Image processing device, recording medium, and program
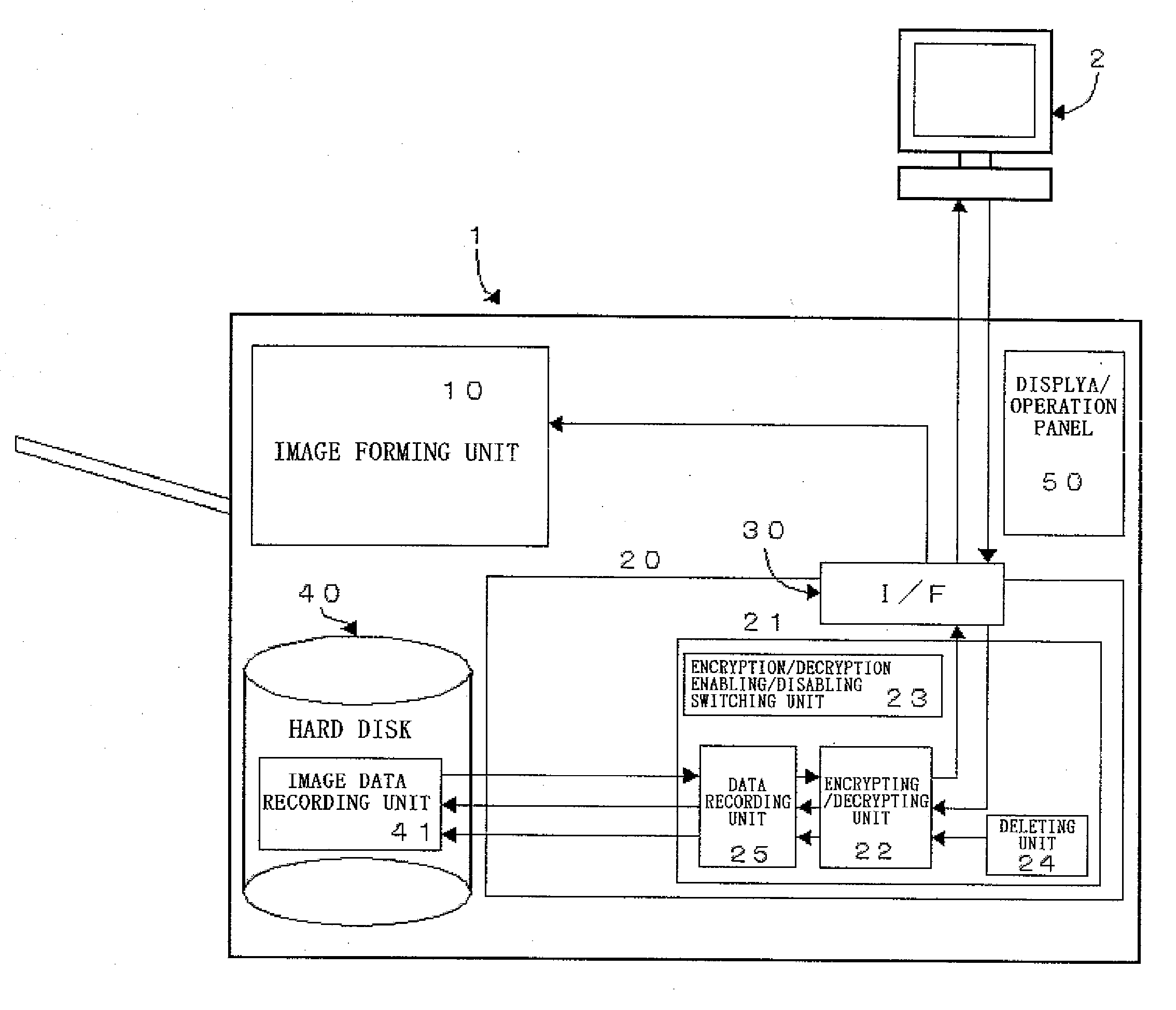
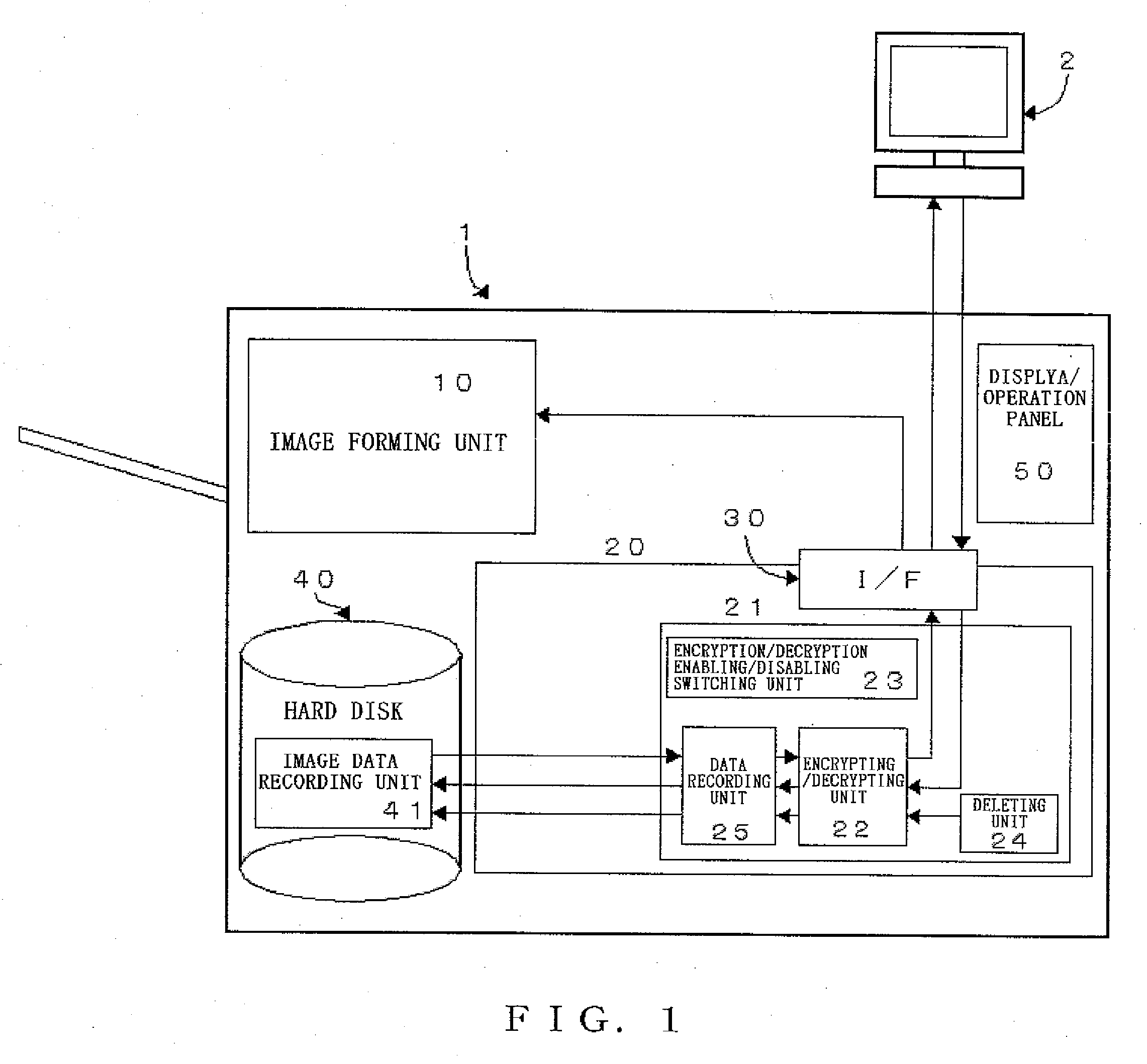
InactiveUS20070055895A1Easy transferPreventing encryptionUser identity/authority verificationUnauthorized memory use protectionComputer hardwareInformation processing
The present invention relates to an information processing device equipped with an encrypting / decrypting unit which encrypts or decrypts data as well as an encryption / decryption enabling / disabling switching unit, which enables the encrypting / decrypting unit to encrypt the file data upon recording such file data in a recording medium, and disables the encrypting / decrypting unit to prevent the deleting data used to overwrite and erase file data from being encrypted when such file data recorded in the recording medium is overwritten and deleted.
Owner:KYOCERA DOCUMENT SOLUTIONS INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com