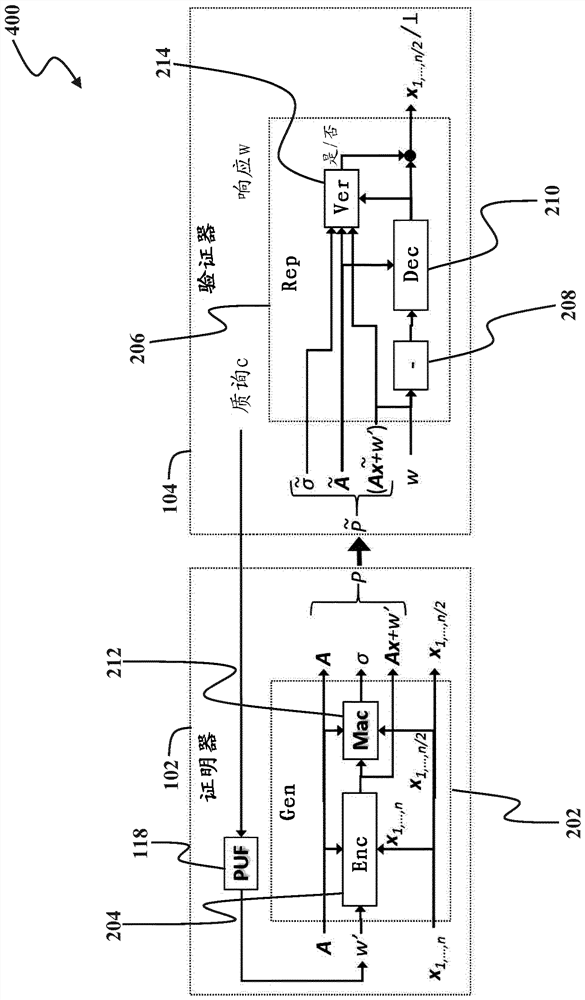
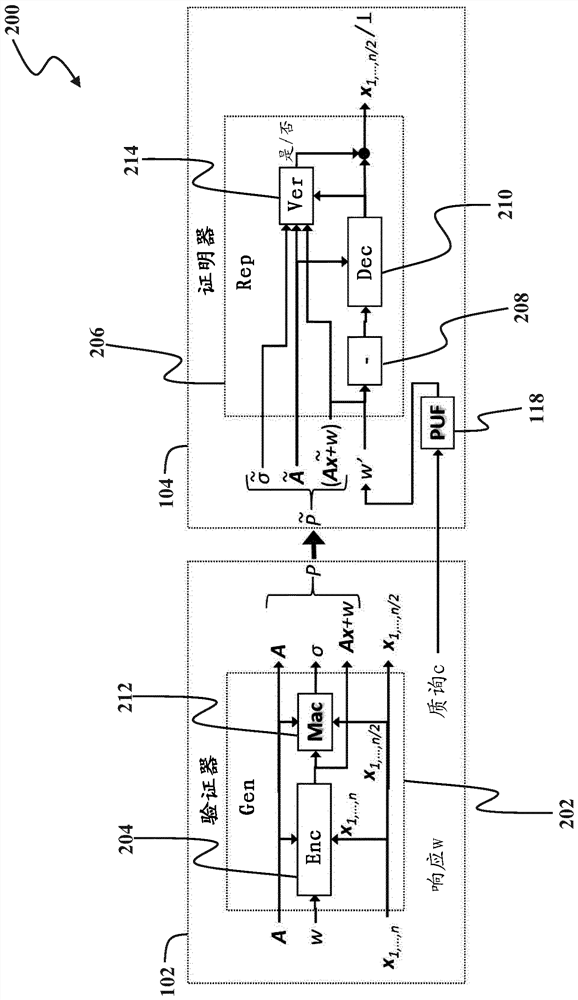
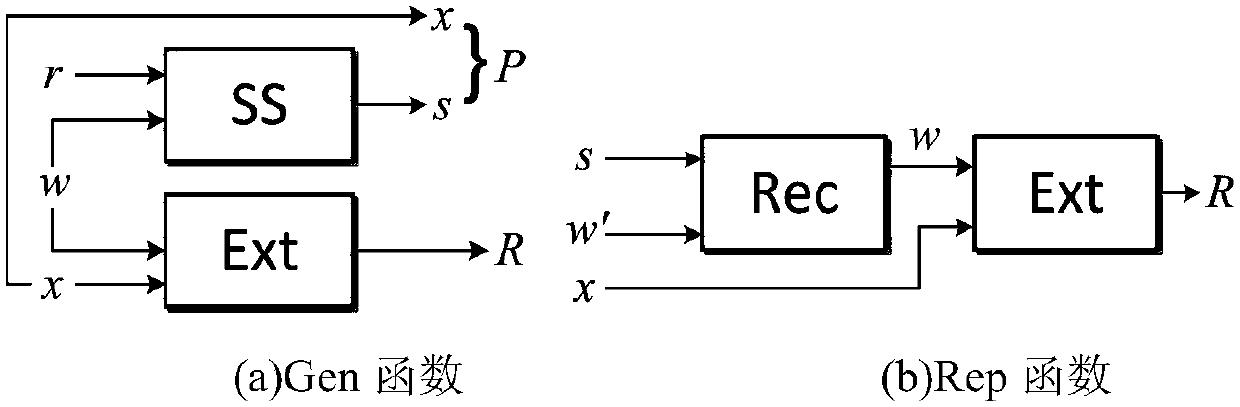
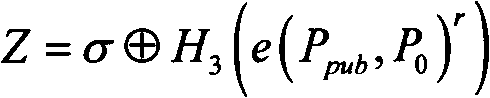Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
35 results about "Fuzzy extractor" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
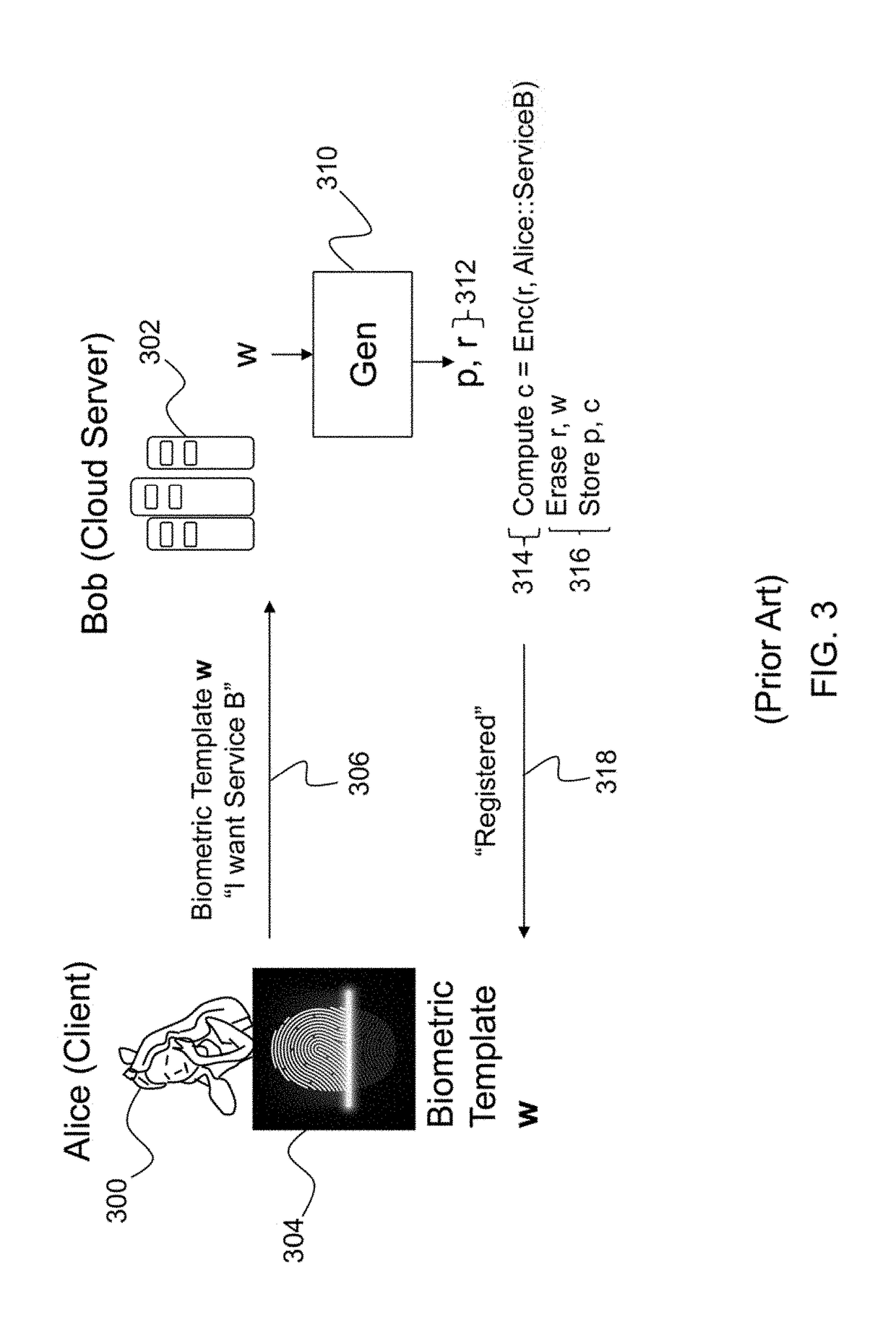
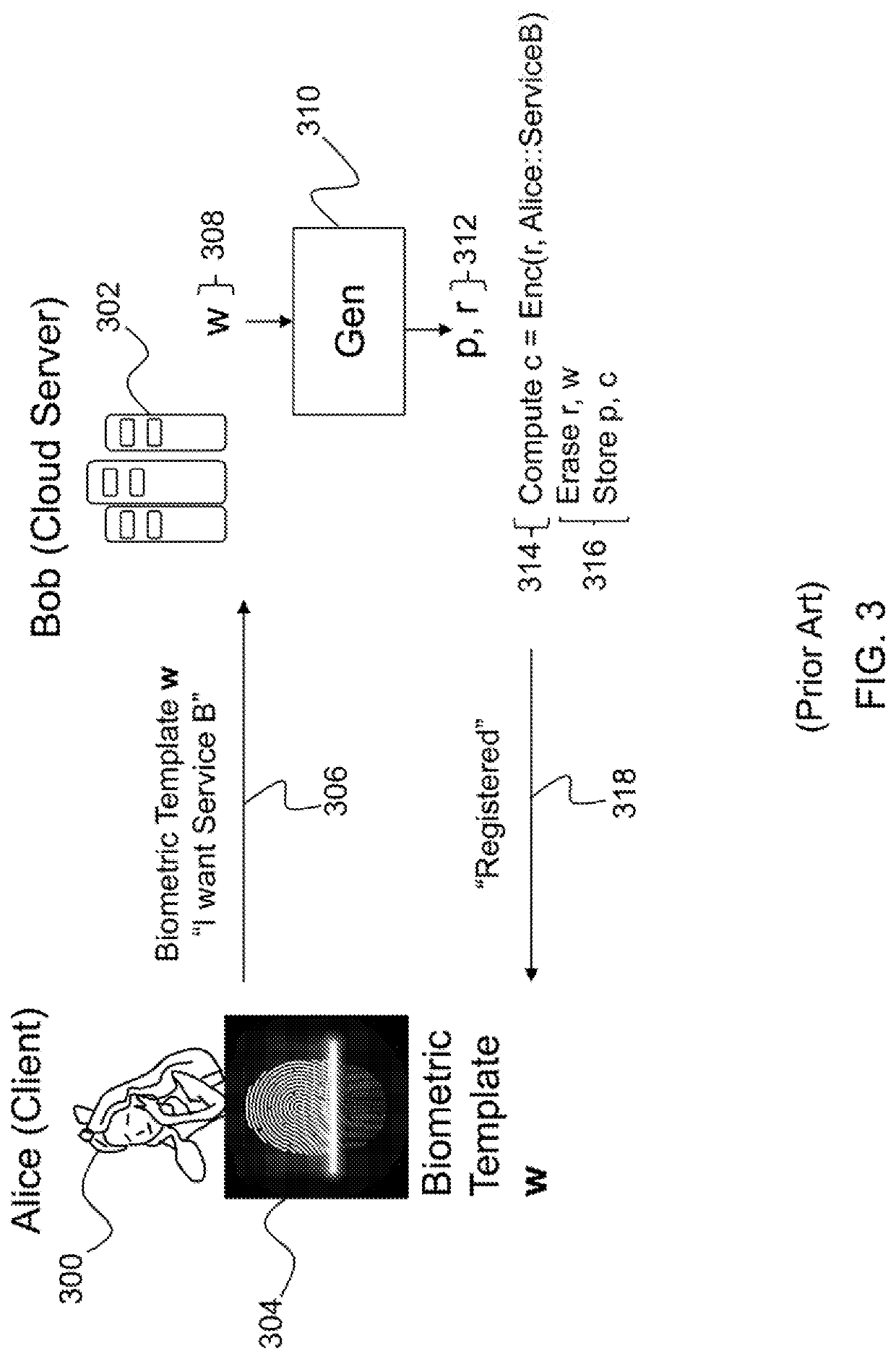
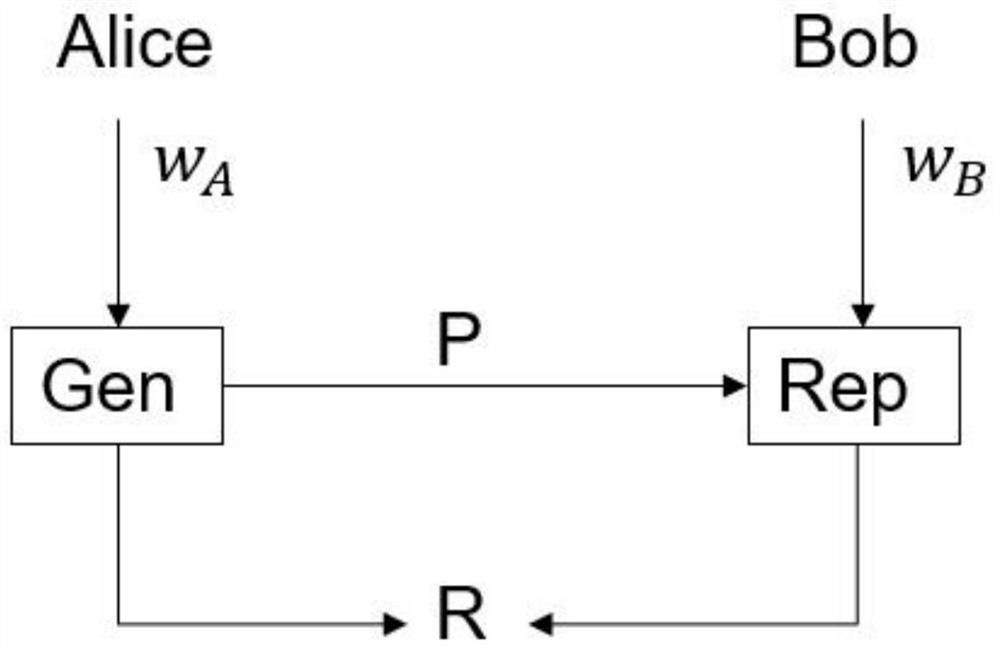
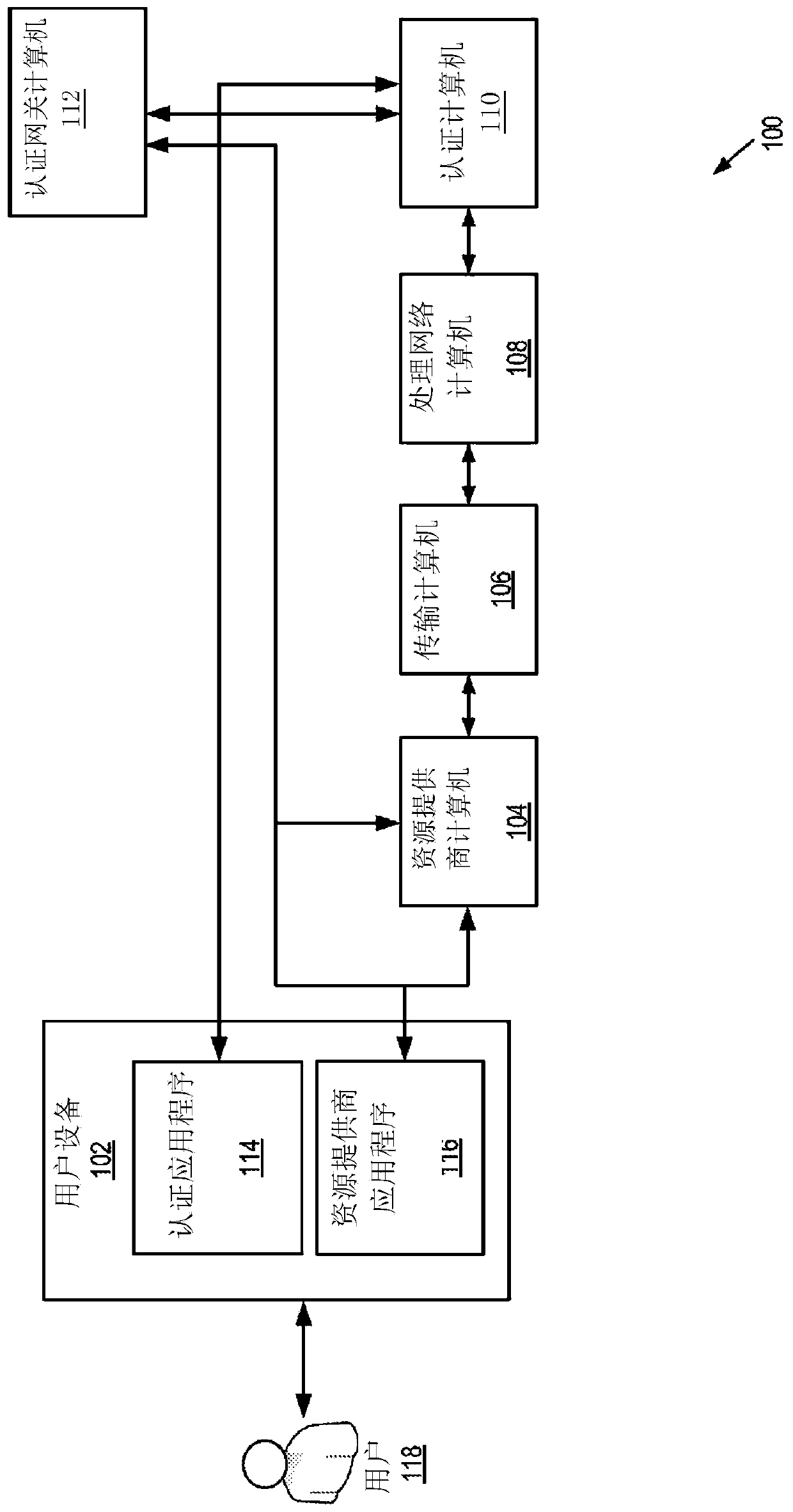
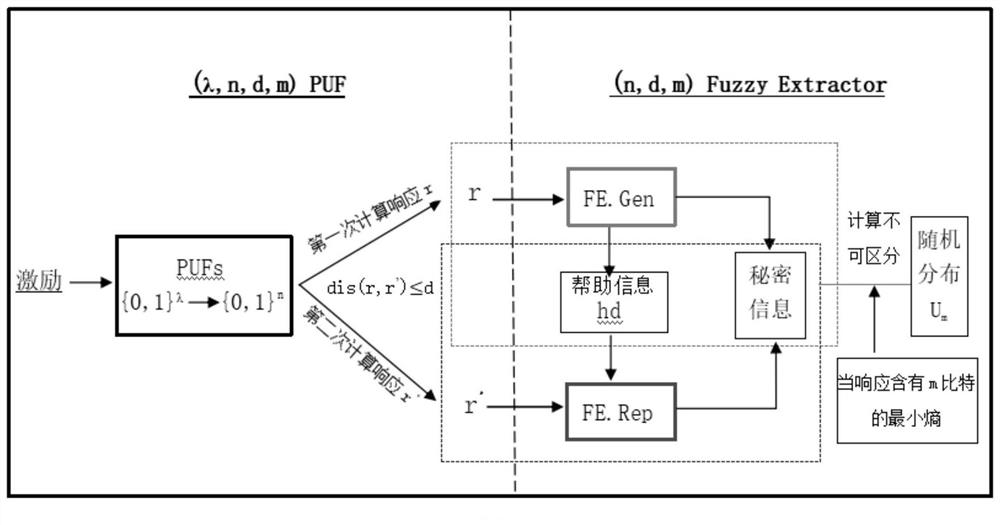
Fuzzy extractors are a method that allows biometric data to be used as inputs to standard cryptographic techniques for security. "Fuzzy", in this context, refers to the fact that the fixed values required for cryptography will be extracted from values close to but not identical to the original key, without compromising the security required. One application is to encrypt and authenticate users records, using the biometric inputs of the user as a key.
Geosecurity methods and devices using geotags derived from noisy location data from multiple sources
InactiveUS8315389B2Reduce rateImprove securityPosition fixationSecret communicationAlgorithmPosition dependent
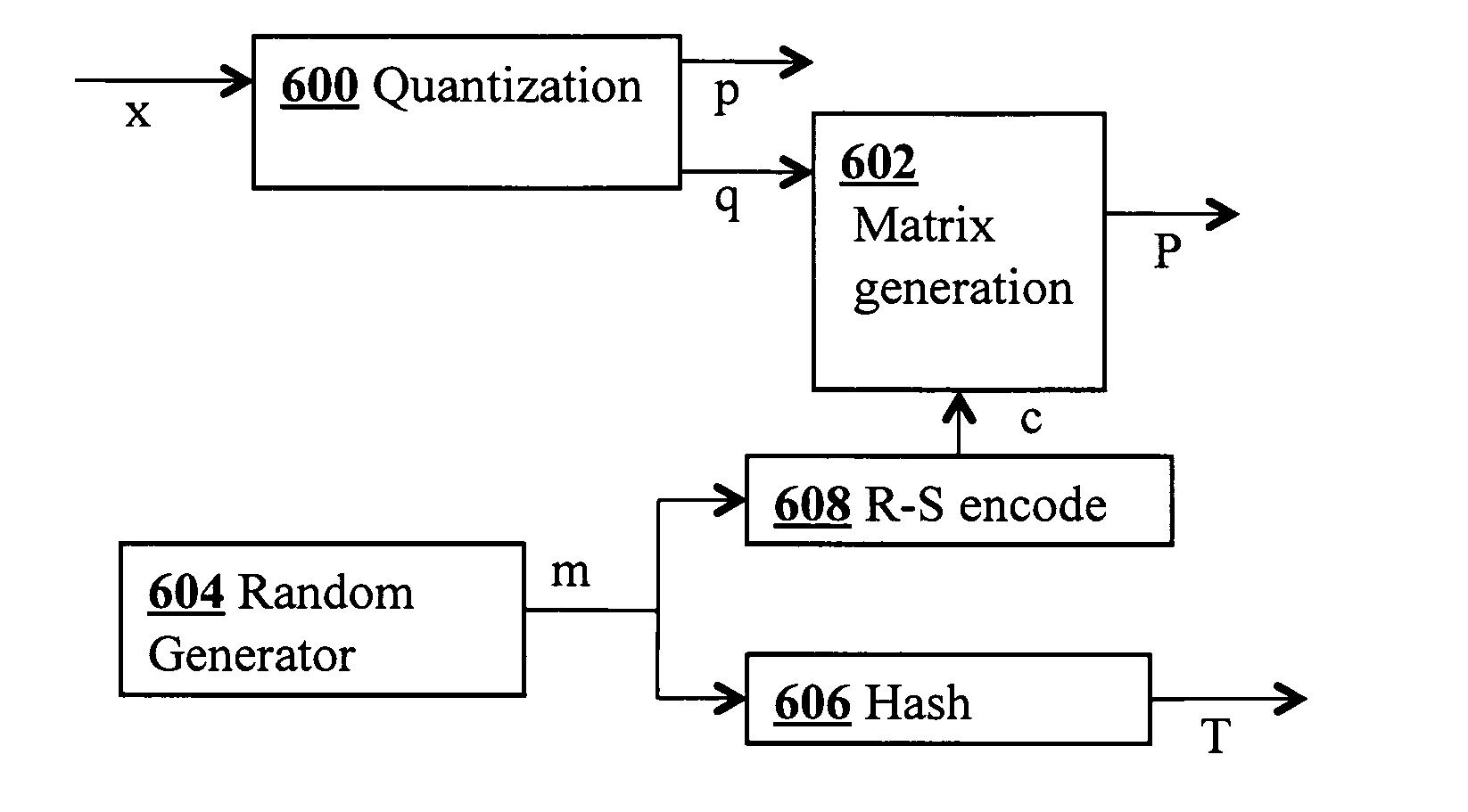
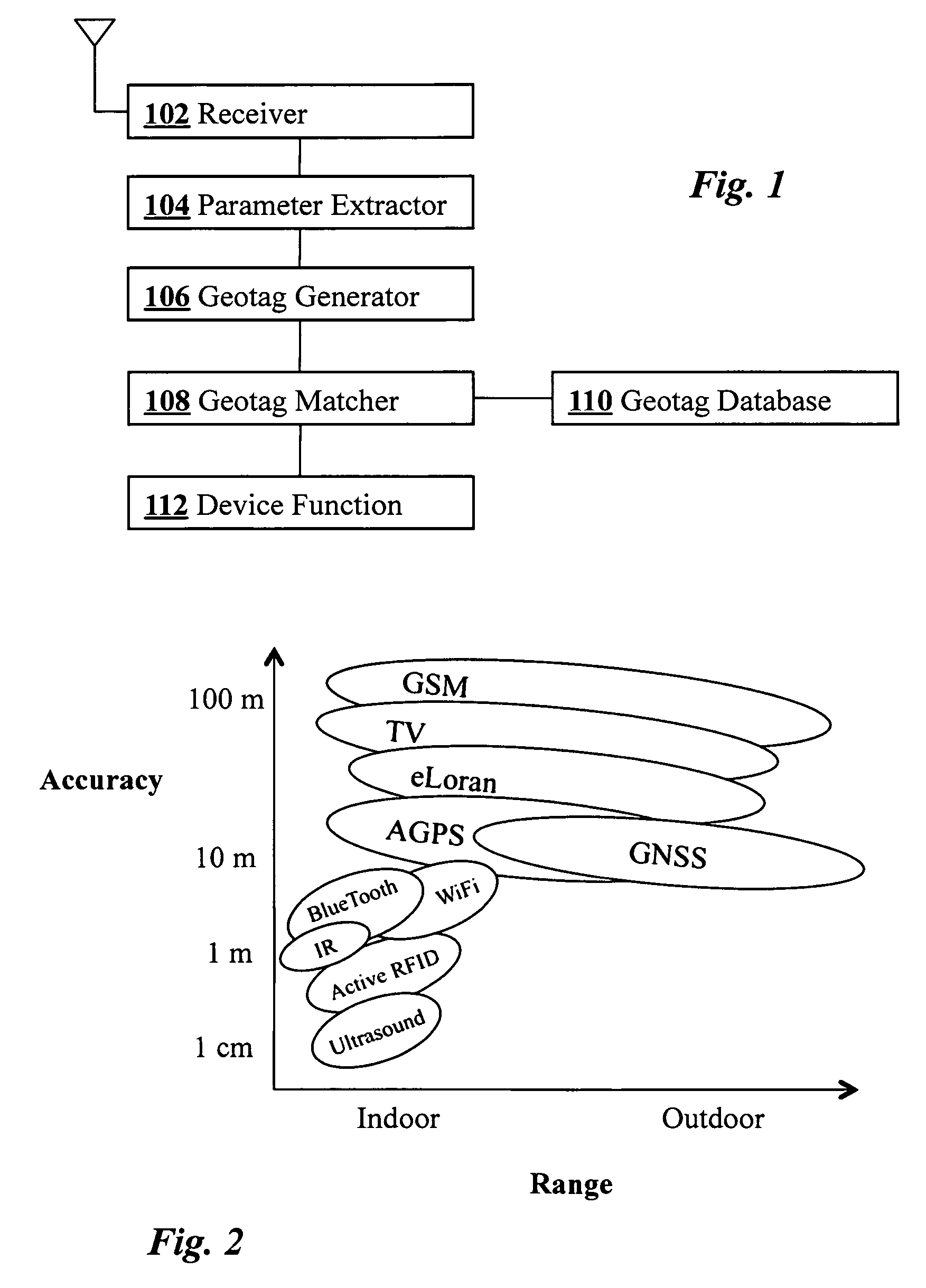
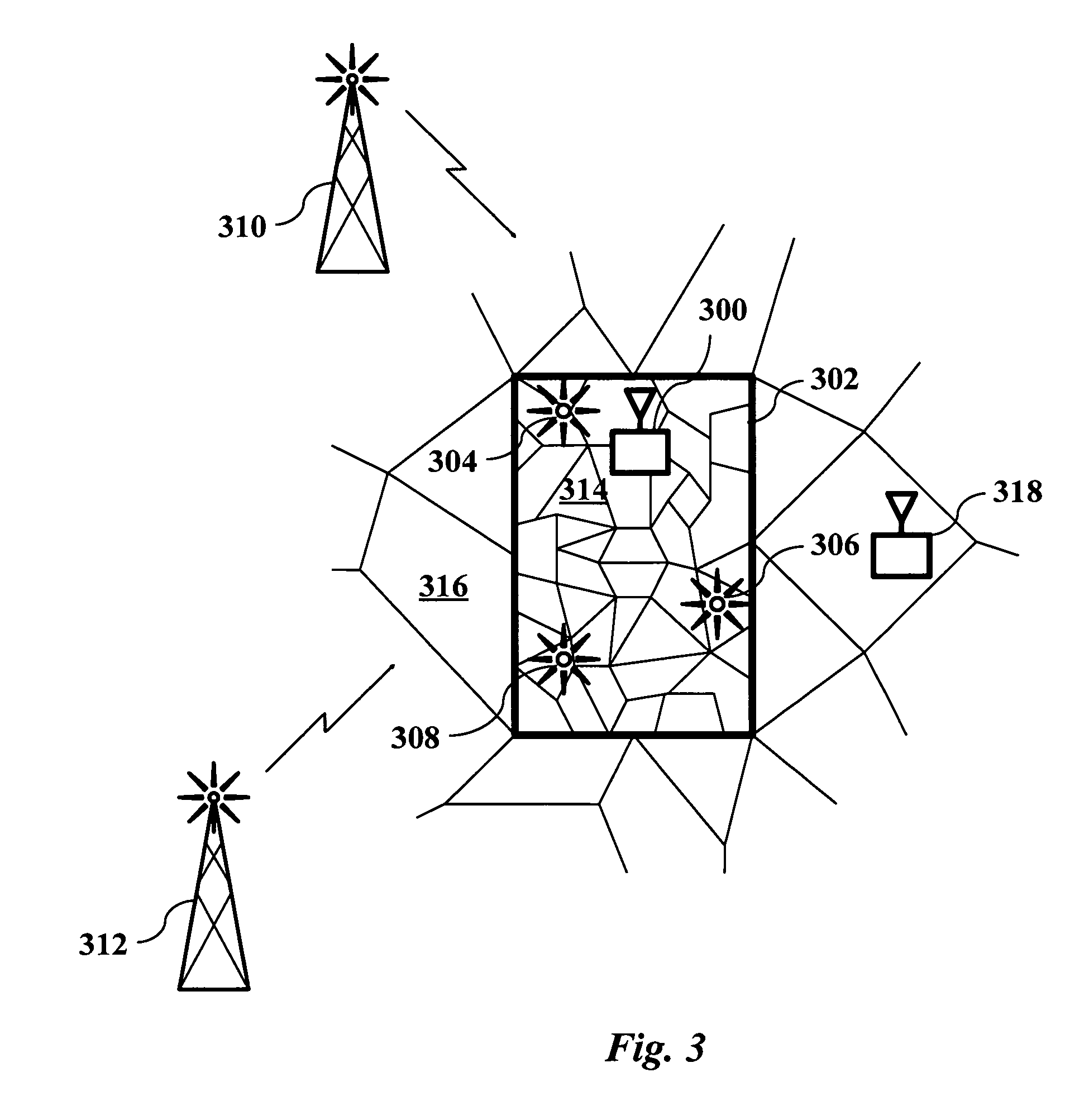
In a geo-security system, a device receives RF signals from multiple distinct classes of RF communication systems and extracts location-dependent signal parameters. A current geotag is computed from the parameters by fuzzy extractors involving quantization of the parameters and Reed-Solomon decoding to provide a reproducible unique geotag. The current geotag is compared with a stored geotag, and a geo-secured function of the device is executed based on the result of the comparison. The use of multiple signal sources of different types, combined with special fuzzy extractors provides a robust geotag that allows both lower false rejection rate and lower false acceptance rate.
Owner:THE BOARD OF TRUSTEES OF THE LELAND STANFORD JUNIOR UNIV
Signcryption method of biological features of a plurality of receivers
InactiveCN102710613AOvercome the problem of forgeryPrevent leakageTransmissionDigital signatureSigncryption
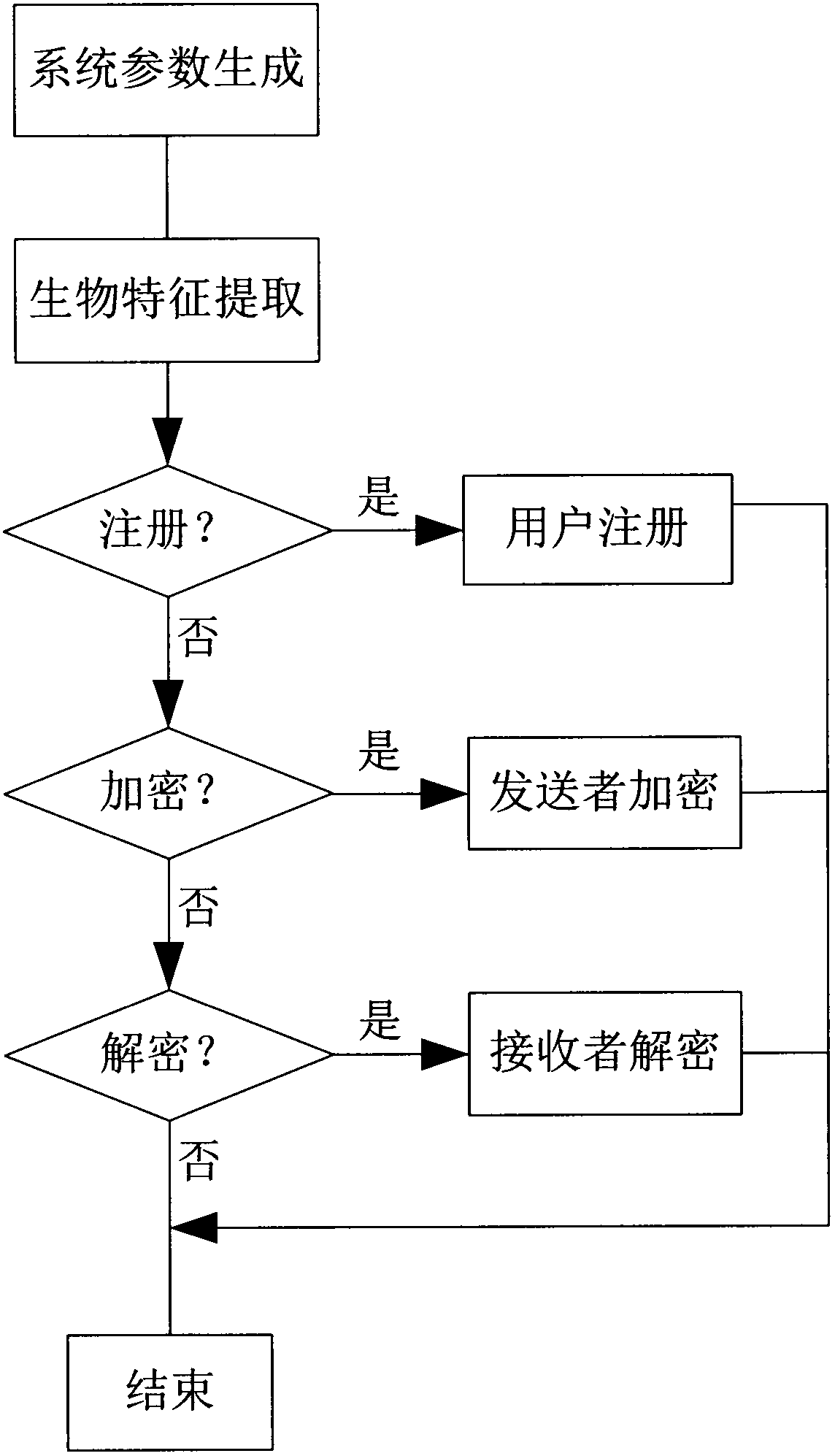
The invention discloses a signcryption method of biological features of a plurality of receivers, comprising generating system parameters; extracting features; performing user log-on; encrypting by a sender; and decrypting by receivers. The method employs fuzzy extractor technique to bind the biological features and user keys to protect keys, directly authenticates user identity through the biological features, solves the safety problems of key safety and key abuse in the conventional cryptography, adds digital signature of senders during encryption, verifies identity of senders through certification during decryption, and solves the problem of counterfeiting of senders. The method improves the safety and reliability of whole systems, has the advantages of high safety, high efficiency and no need for storing any secret information by users, and can be applied to the distributed network application field.
Owner:XIDIAN UNIV
Use of biometrics and privacy preserving methods to authenticate account holders online
PendingUS20200228340A1Secure performanceKey distribution for secure communicationUser identity/authority verificationBiometric dataEngineering
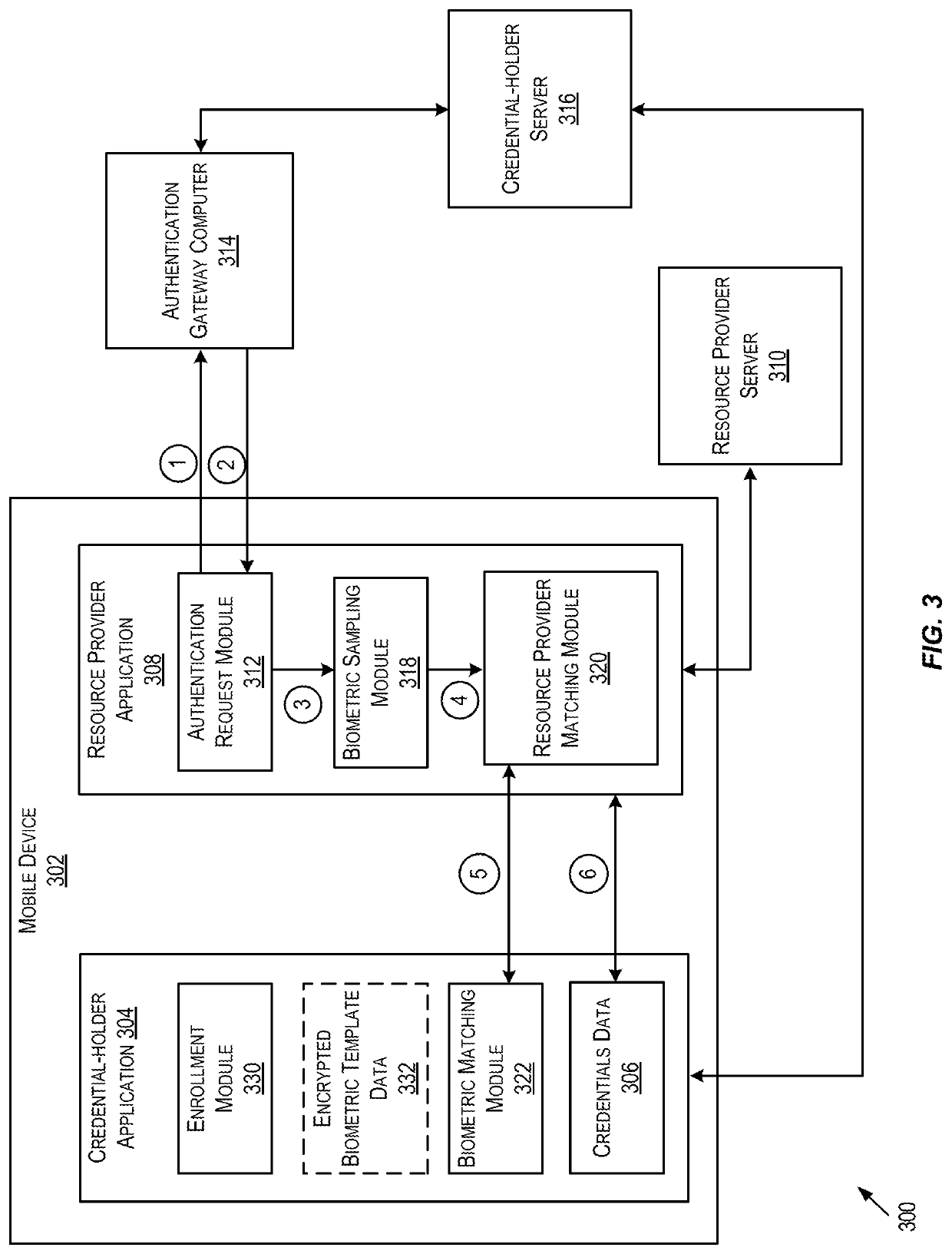
Embodiments are directed to a method for securely performing biometric authentication online. The method described can be used to securely perform biometric authentication on a mobile device. For protecting the privacy of the users biometric data, a cryptographic comparison protocol can be used to perform matching of encrypted templates. For example, the cryptographic comparison protocol may involve Fuzzy Extractors (FE), Homomorphic Encryption (HE), and / or Secure Multi-Party Computation (SMPC).
Owner:VISA INT SERVICE ASSOC
Novel fingerprint key generation method for digital signature
InactiveCN106059753AImprove securityAvoid safety hazardsKey distribution for secure communicationFeature extractionDigital signature
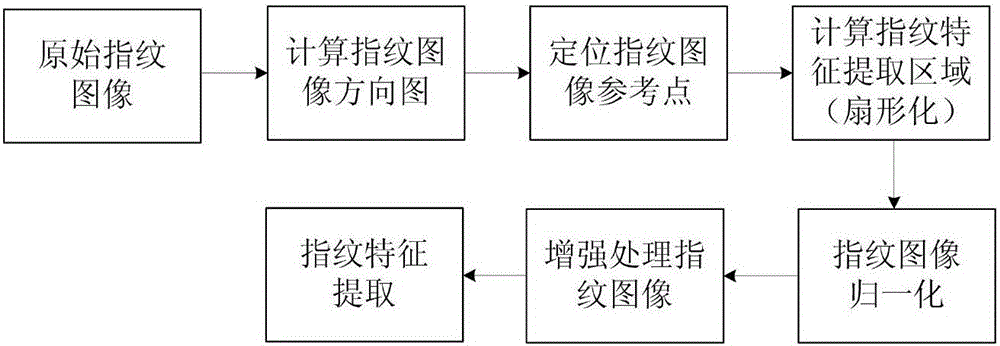
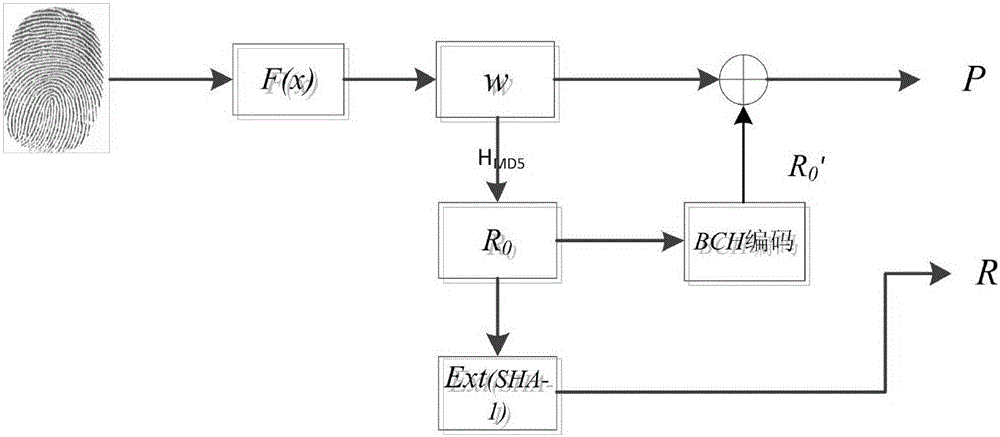
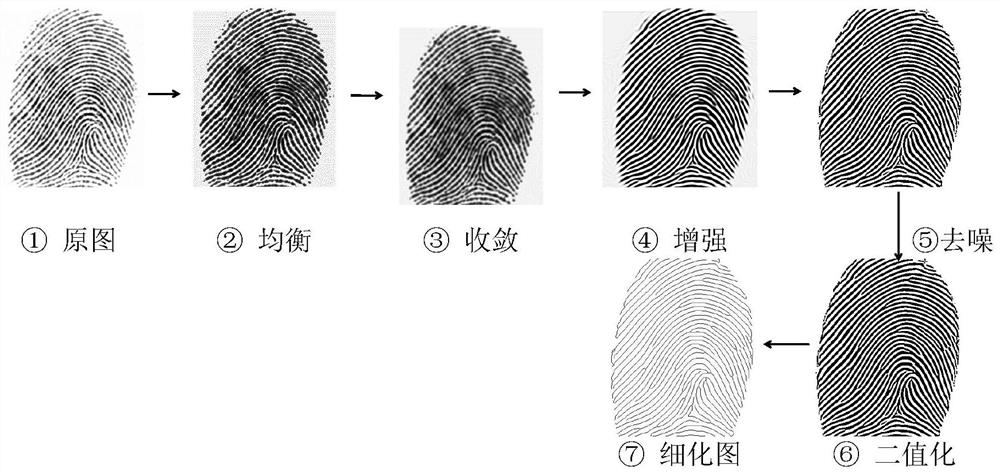
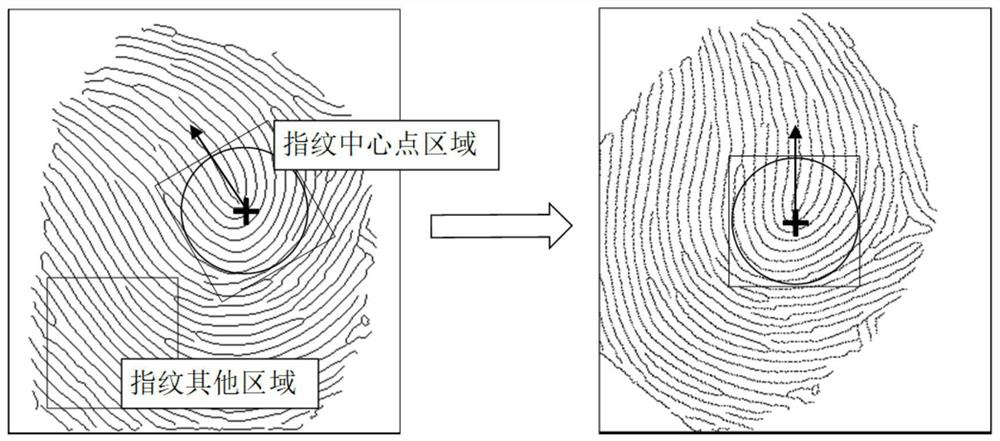
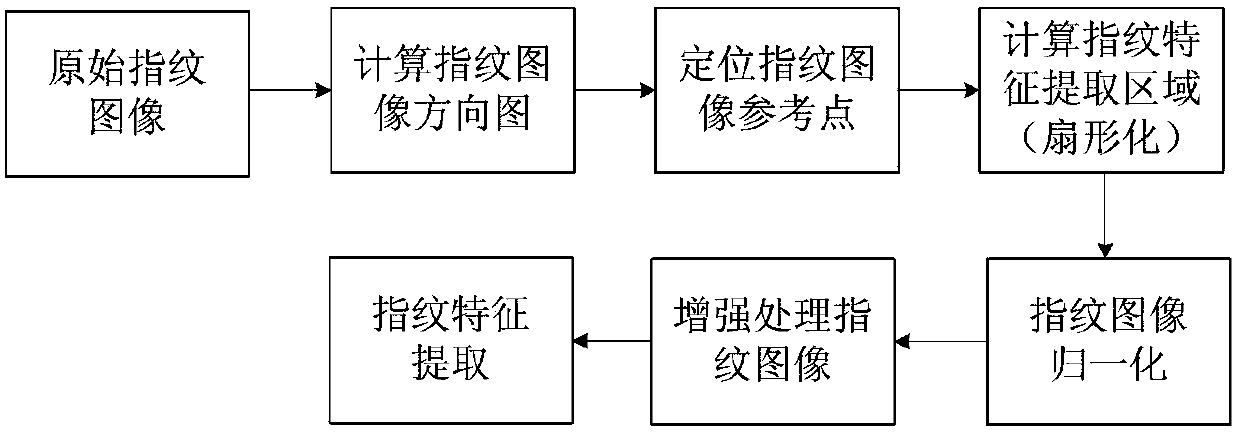
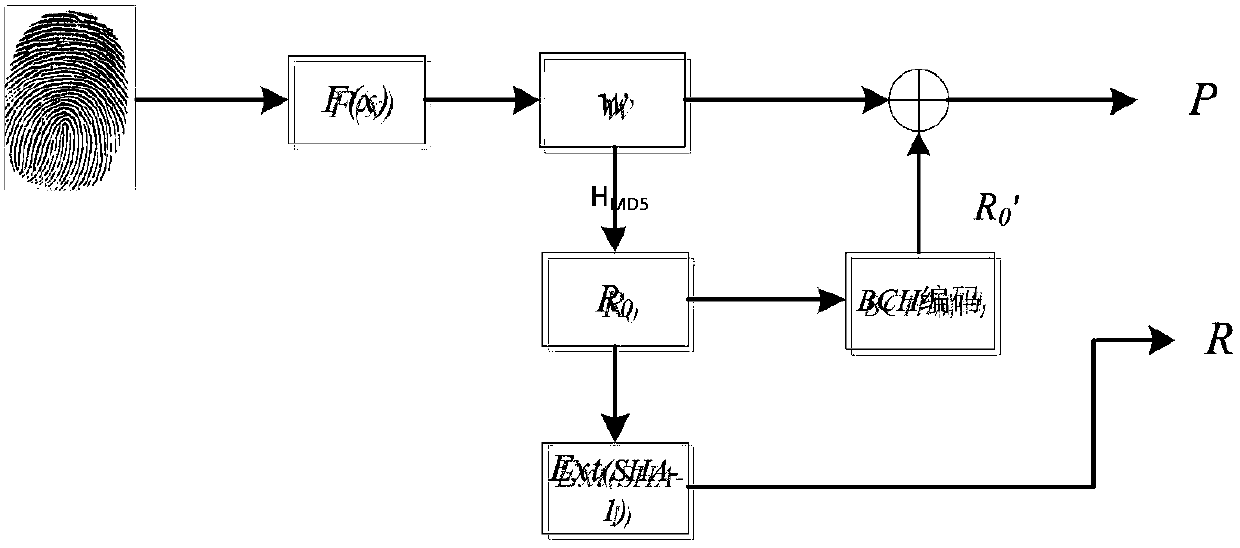
The invention relates to a novel fingerprint key generation method for a digital signature, which comprises two stages and is characterized in that the first stage is fingerprint feature extraction which comprises the steps of calculating a directional diagram of a fingerprint image, positioning a reference point of the fingerprint image, calculating a sector fingerprint feature extraction region, carrying out fingerprint image normalization, performing enhancement processing on the fingerprint image, and extracting fingerprint features; and the second stage refers to fuzzy extraction technology based fingerprint key generation which comprises the steps of constructing a security model based fuzzy extractor, constructing a Hamming distance based fuzzy extractor and generating a fingerprint key. The novel fingerprint key generation method has the advantages that the fingerprint key can be cancelled or updated for multiple times, the security is enabled to be higher, and potential safety hazards brought about by external information stealing can be avoided. Meanwhile, the novel fingerprint key generation method has important theoretical and practical values, and has wide application prospects.
Owner:XIJING UNIV
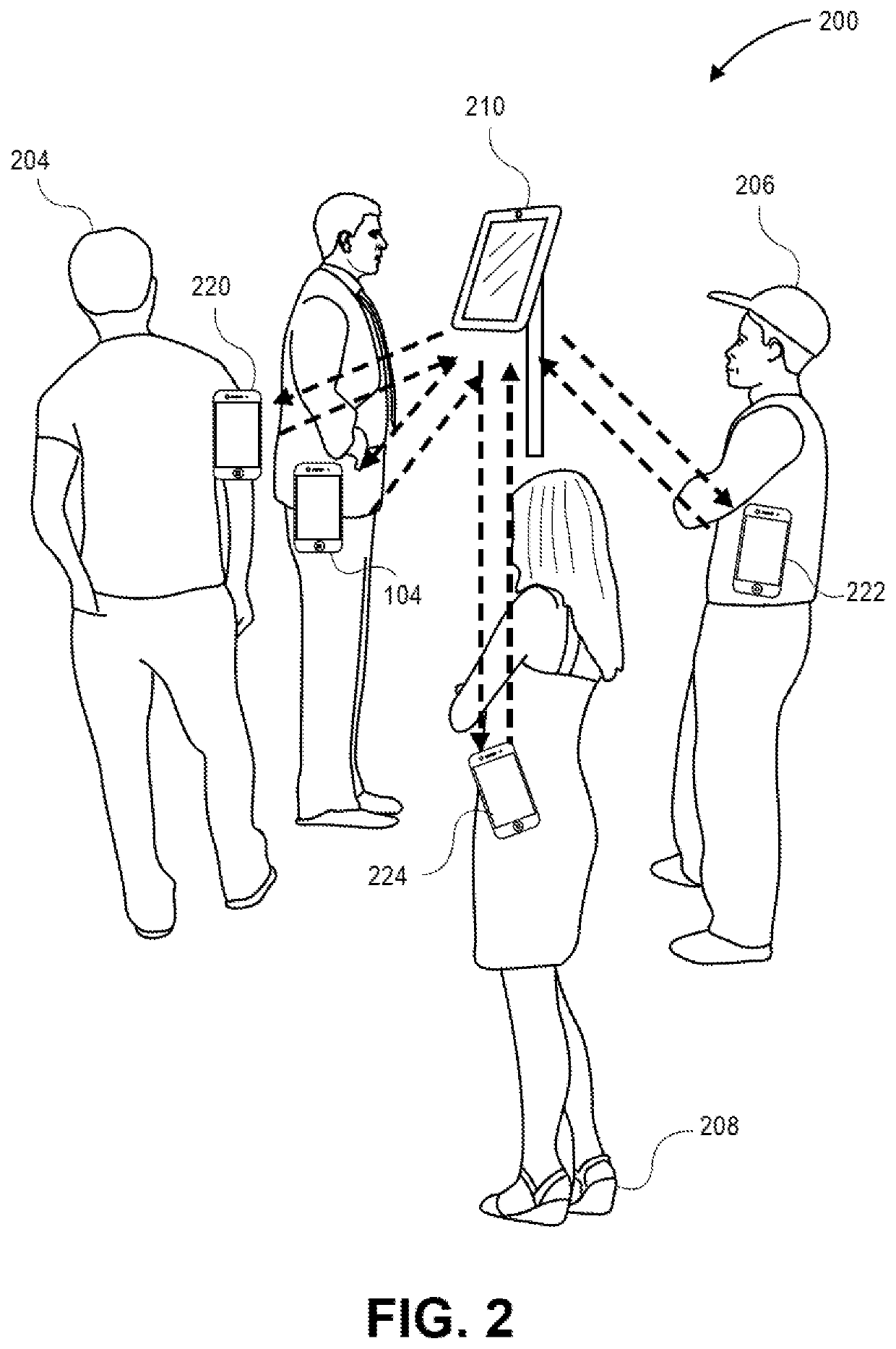
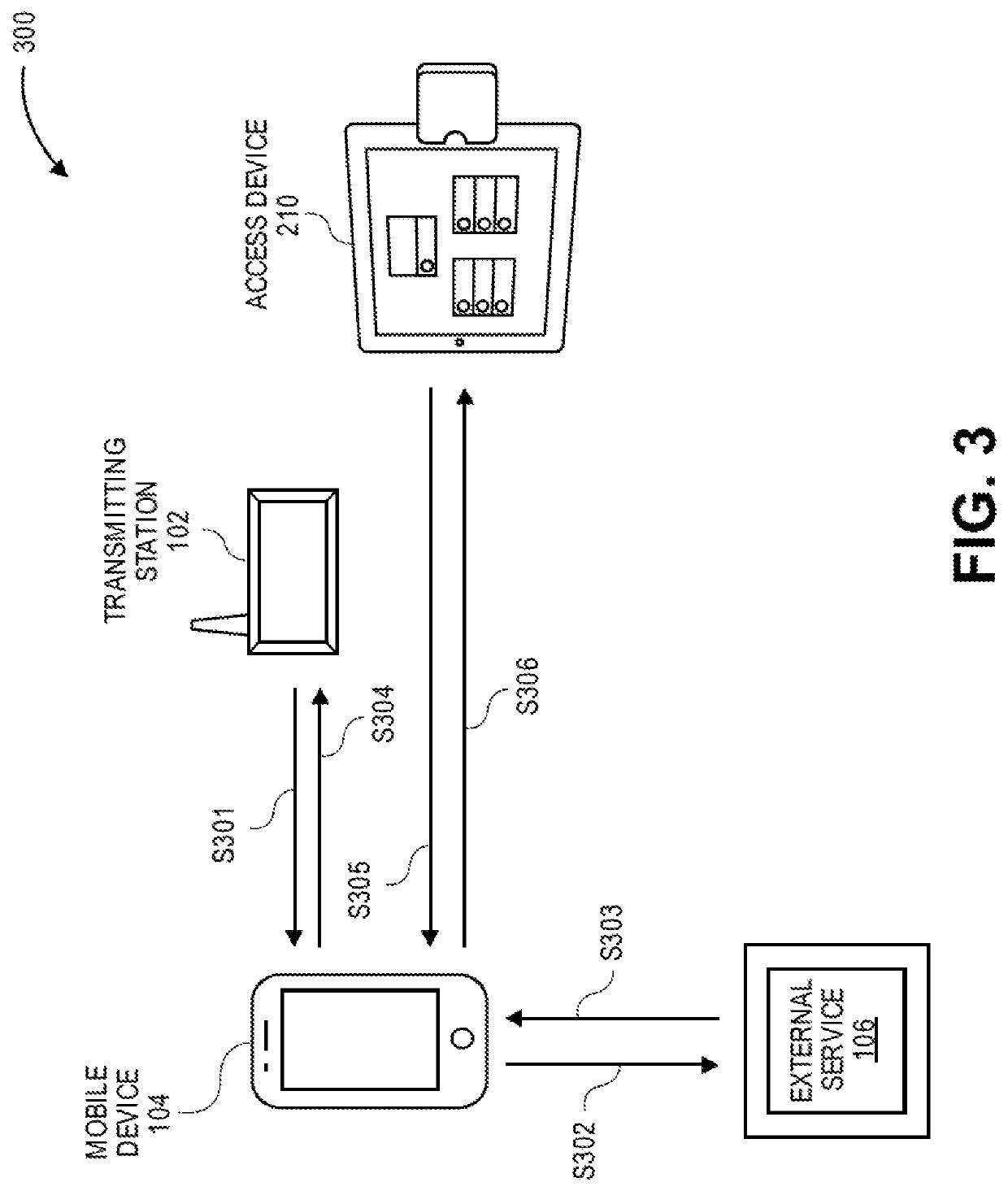
Wireless Biometric Authentication System and Method
ActiveUS20200279269A1Key distribution for secure communicationCryptography processingComputer networkEngineering
Embodiments of the invention involve using biometric templates to wirelessly authenticate individuals. In one embodiment, a mobile device may generate a first biometric template and a first public value from a first biometric sample of a user and generate a first cryptographic key by passing the first biometric template to a fuzzy extractors generate function. An access device may generate a second biometric template from a second biometric sample of the user, generate a second secret cryptographic key by passing the second biometric template and the first public value to the fuzzy extractors reproduce function, encrypt the second biometric template with the second secret cryptographic key, and broadcast the encrypted template to a plurality of nearby mobile devices including the mobile device. If the mobile device is able to decrypt the encrypted template with the first cryptographic key, the access device can associate the user with the mobile device.
Owner:VISA INT SERVICE ASSOC
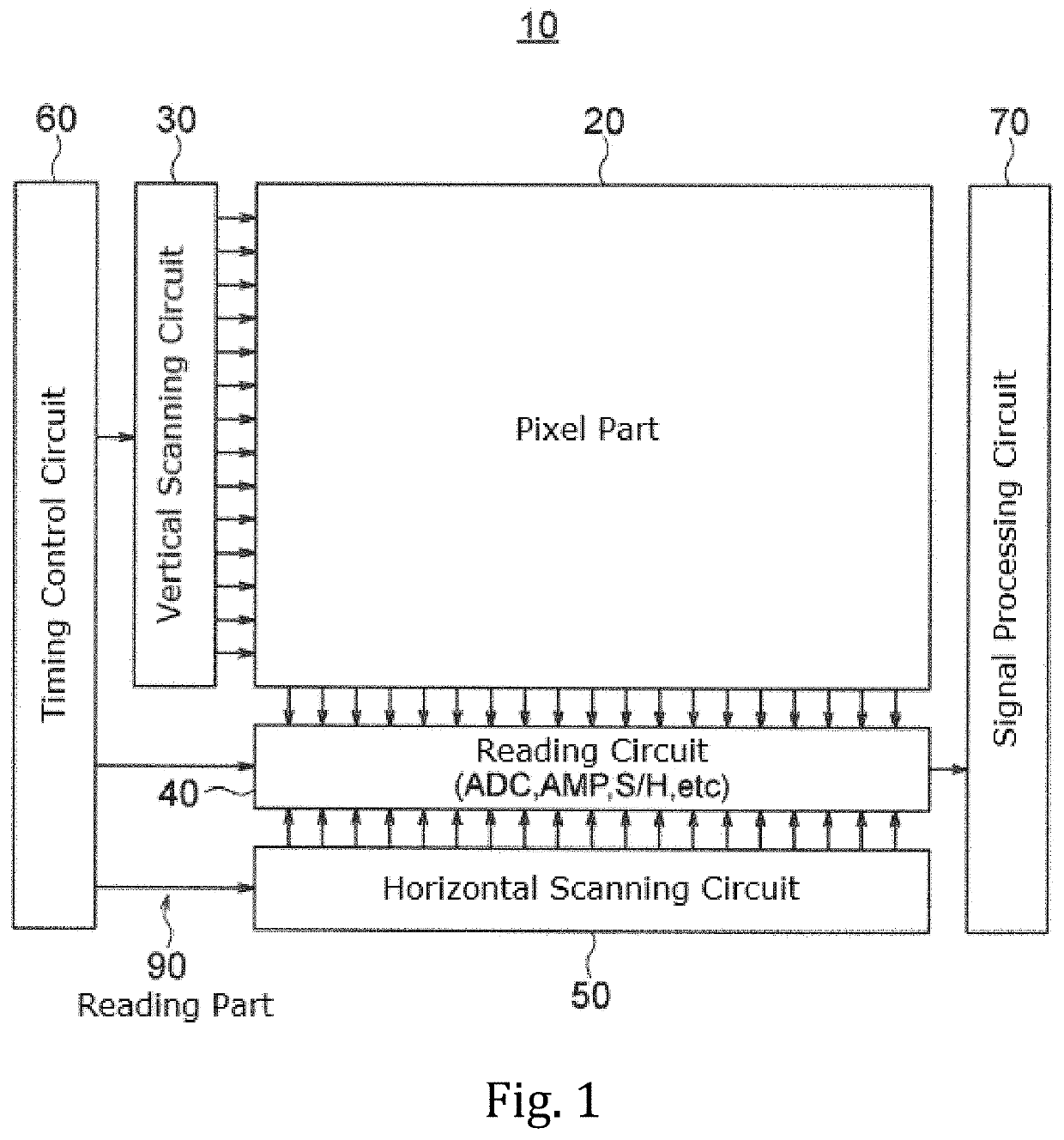
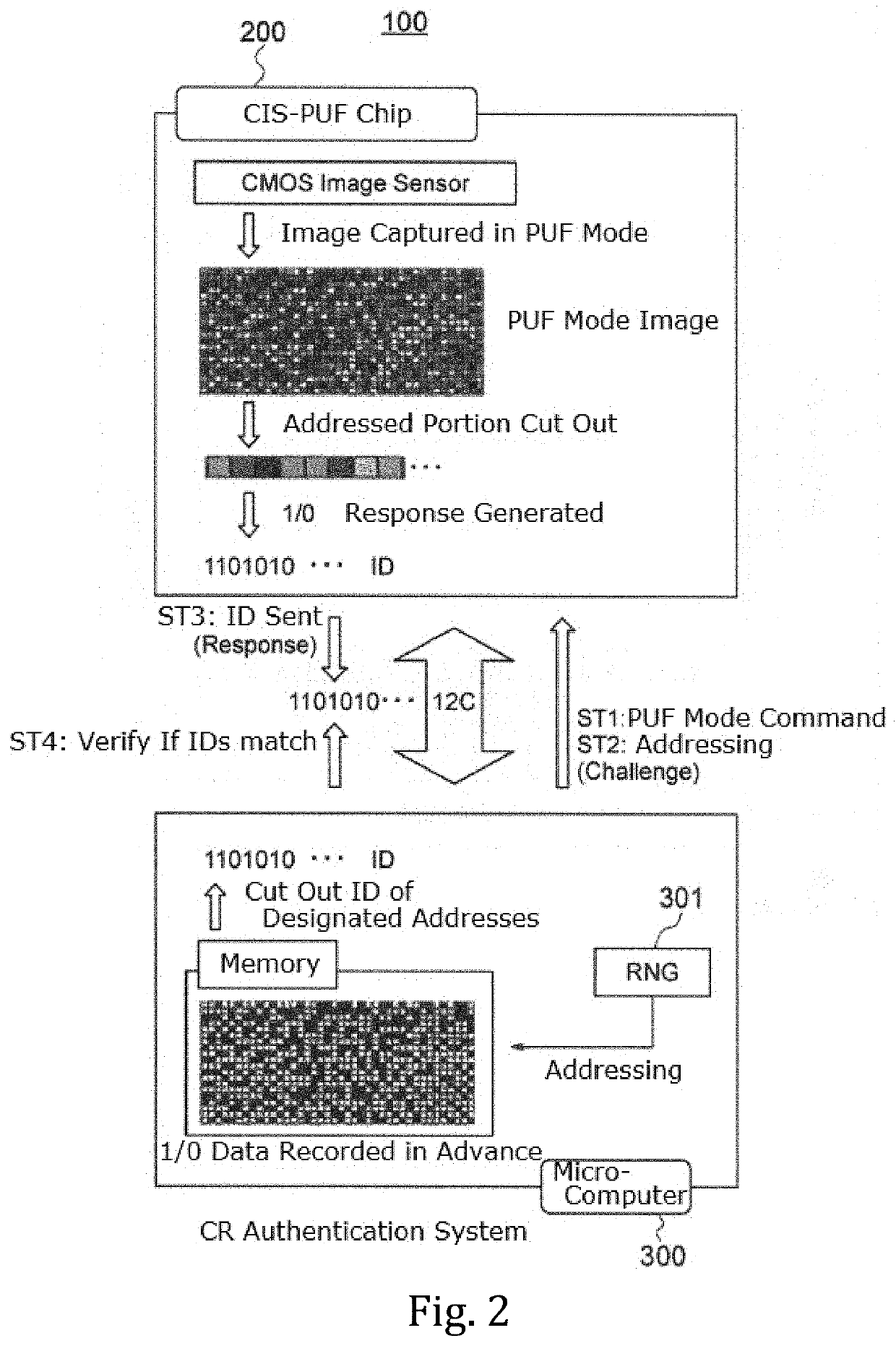
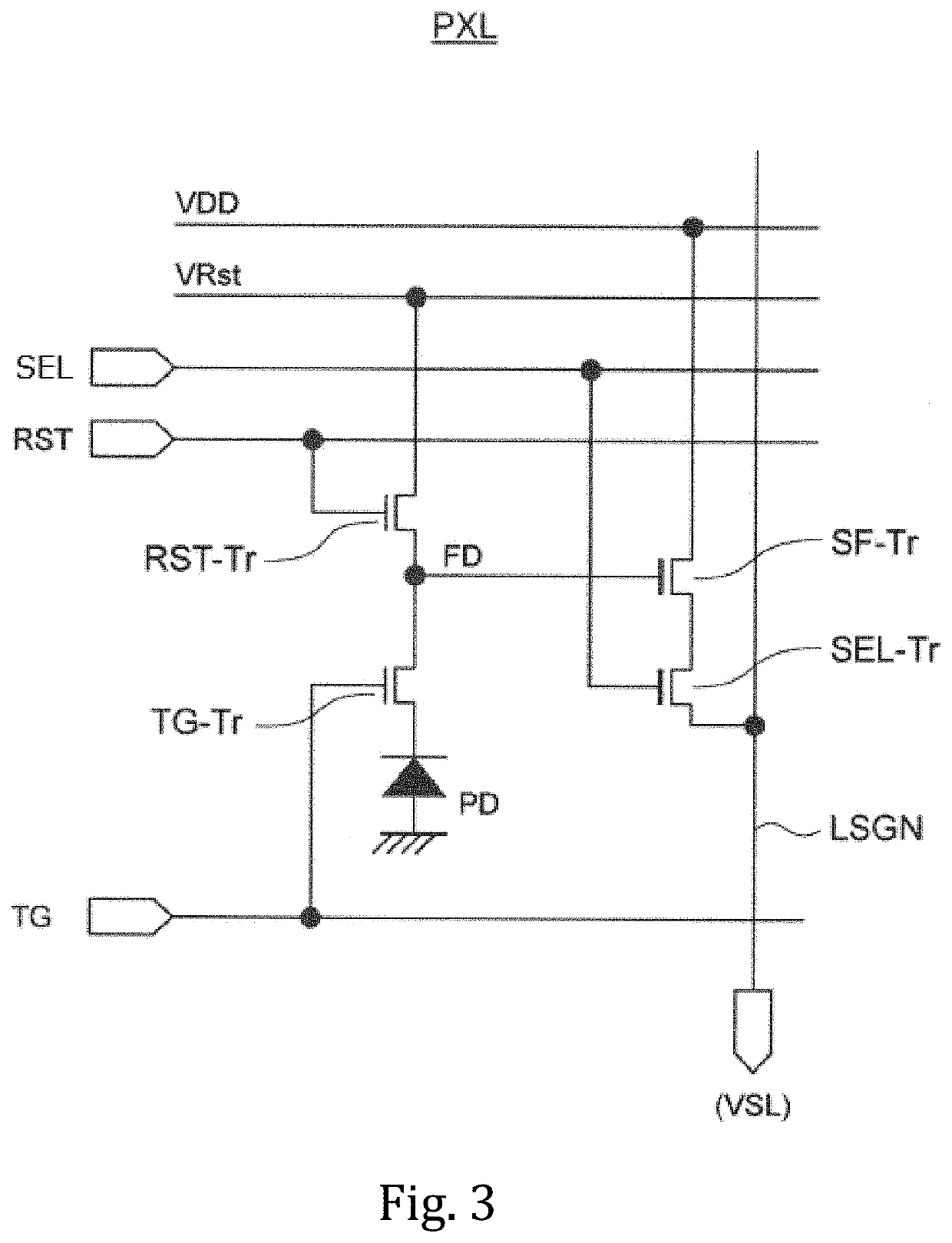
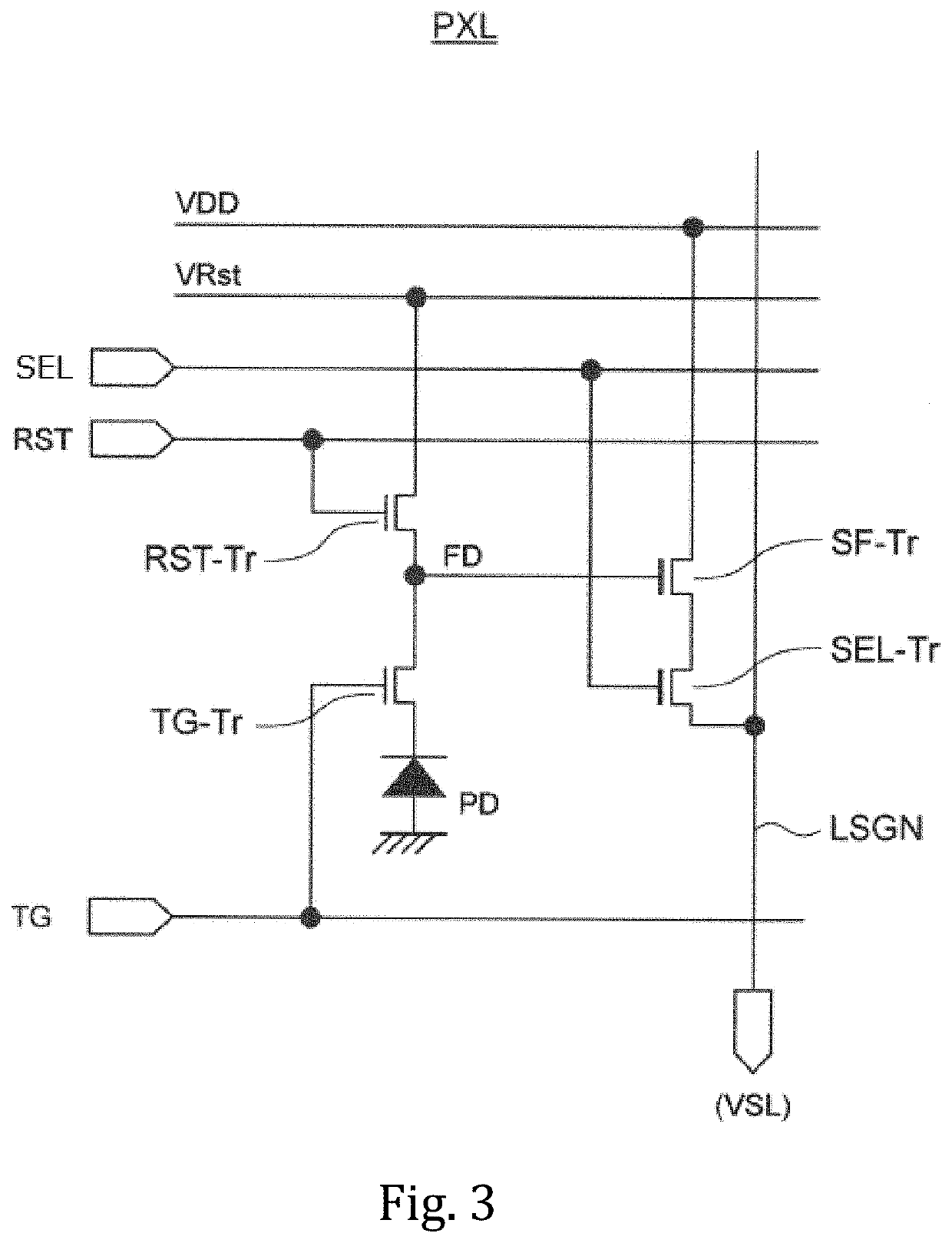
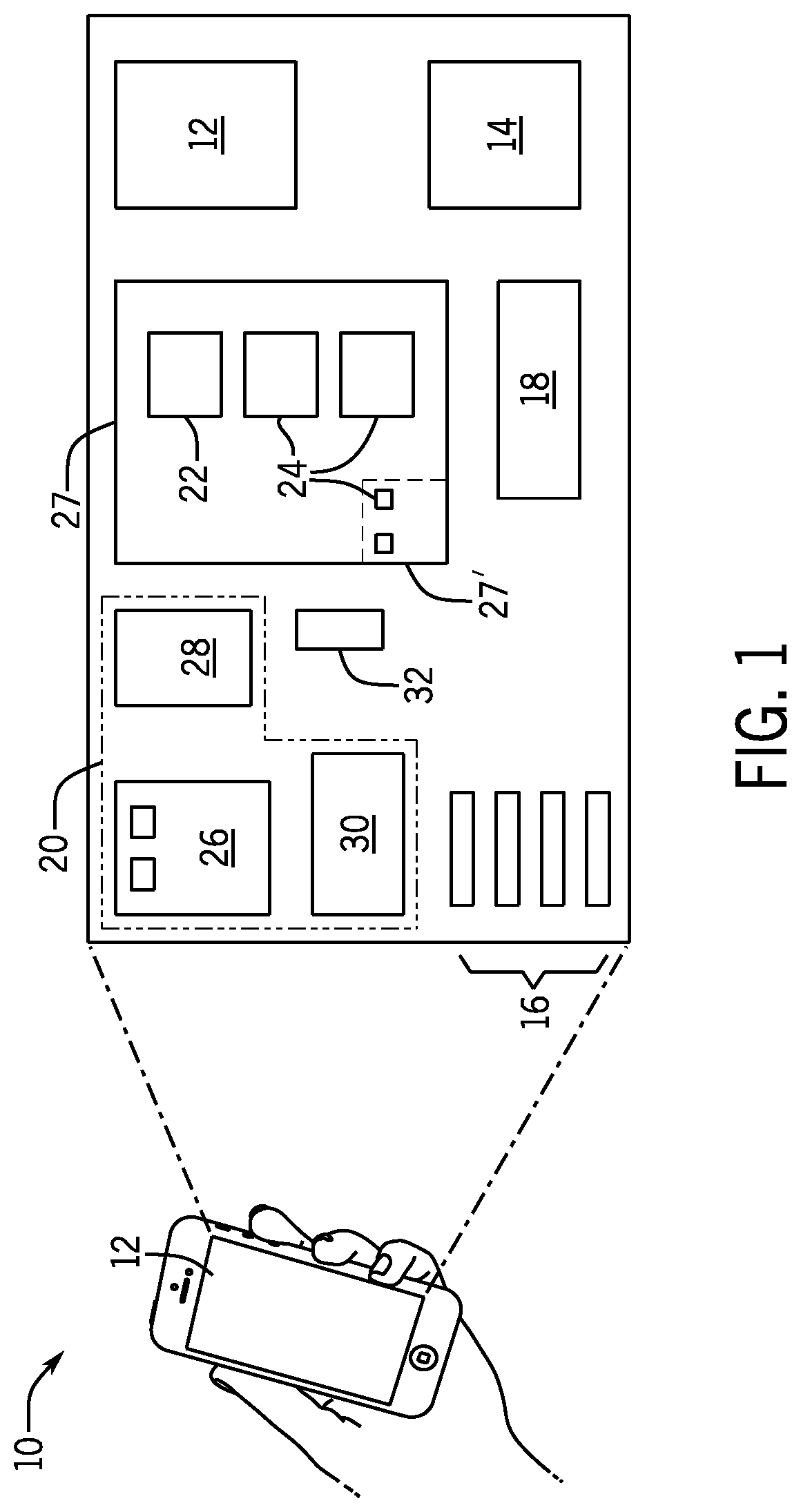
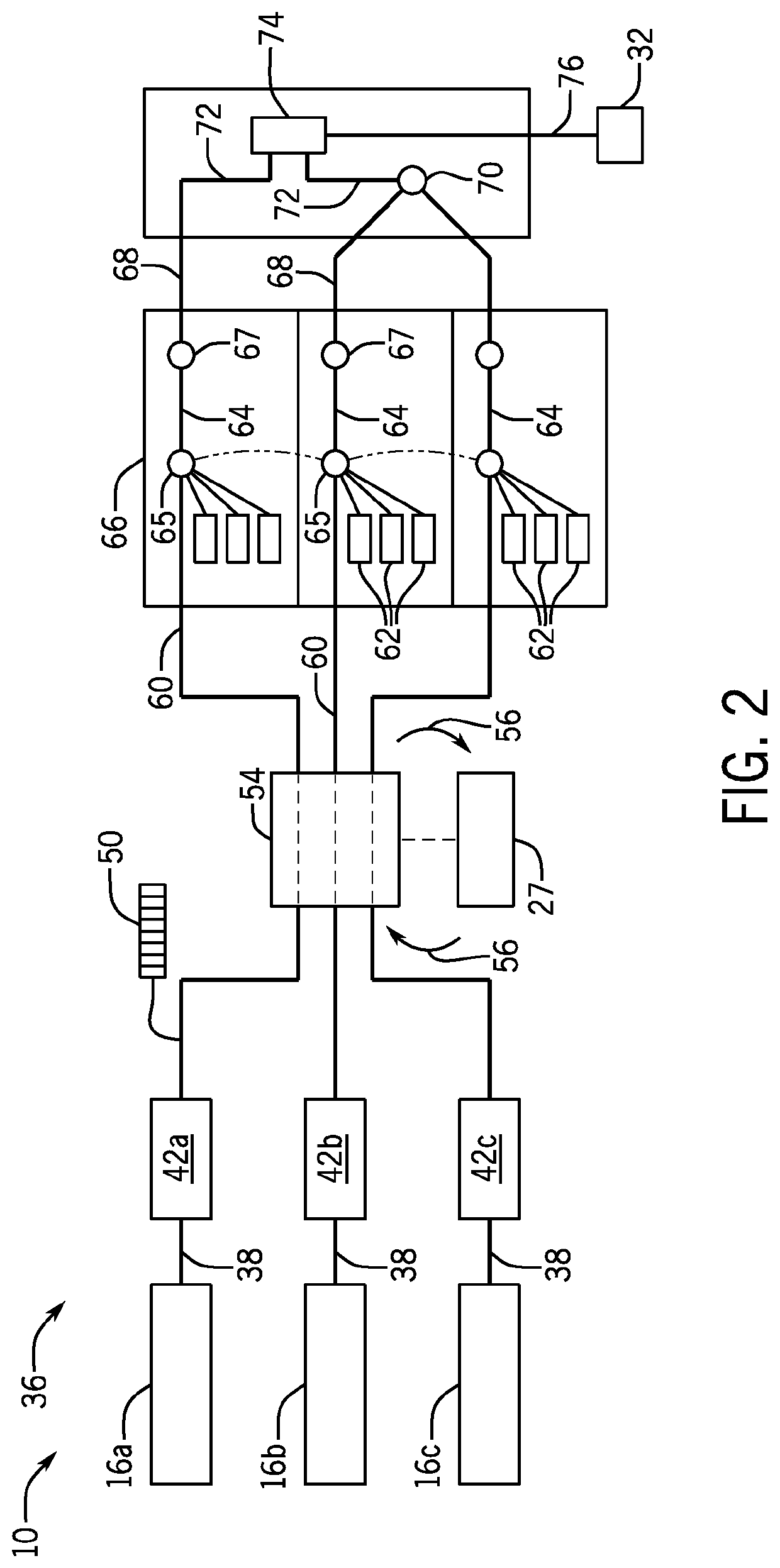
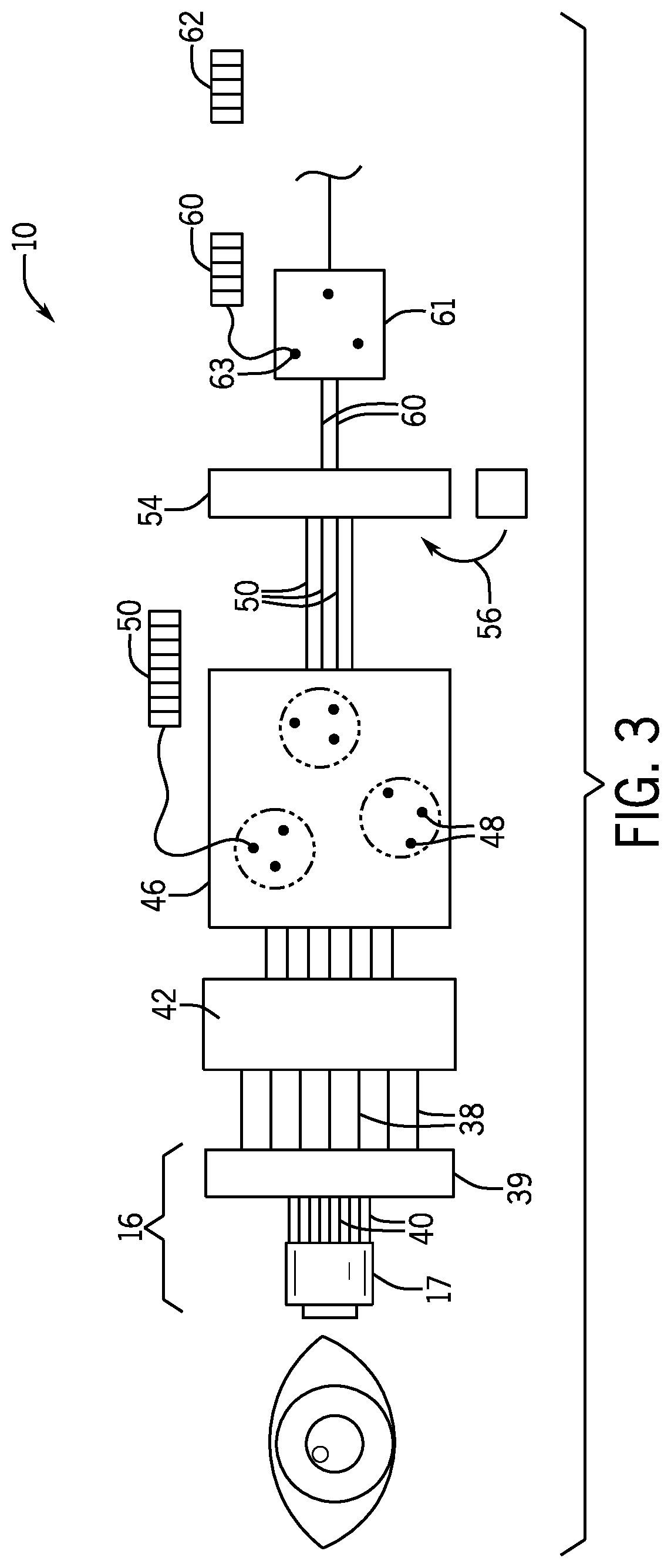
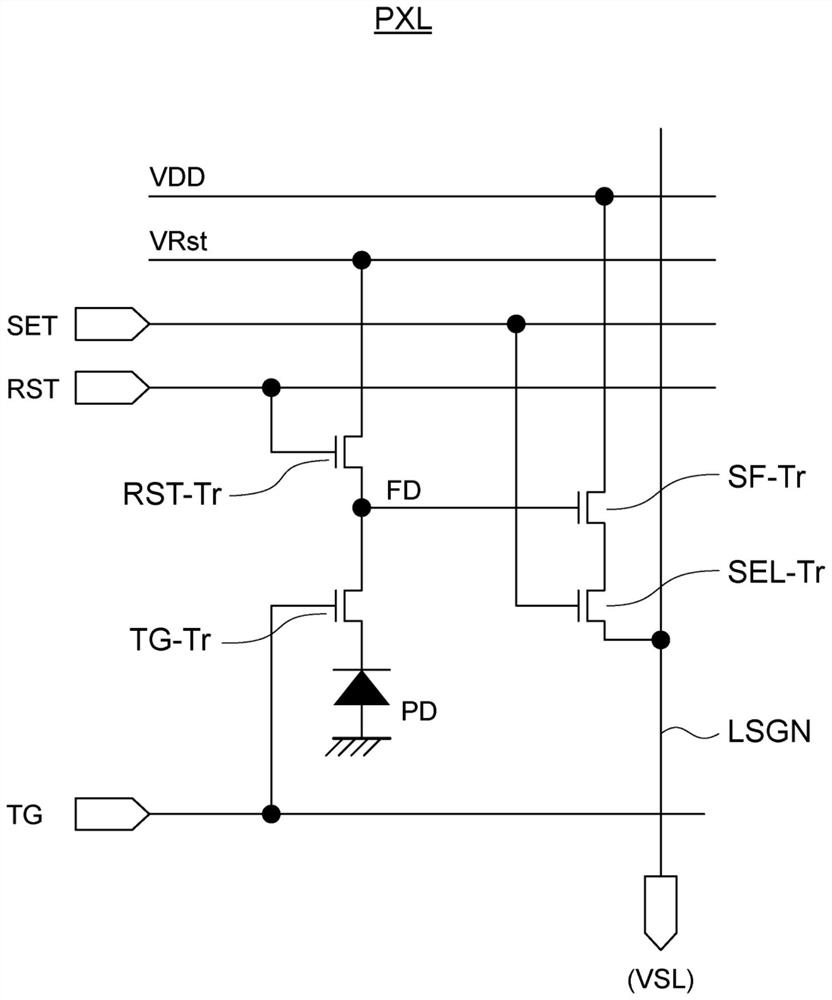
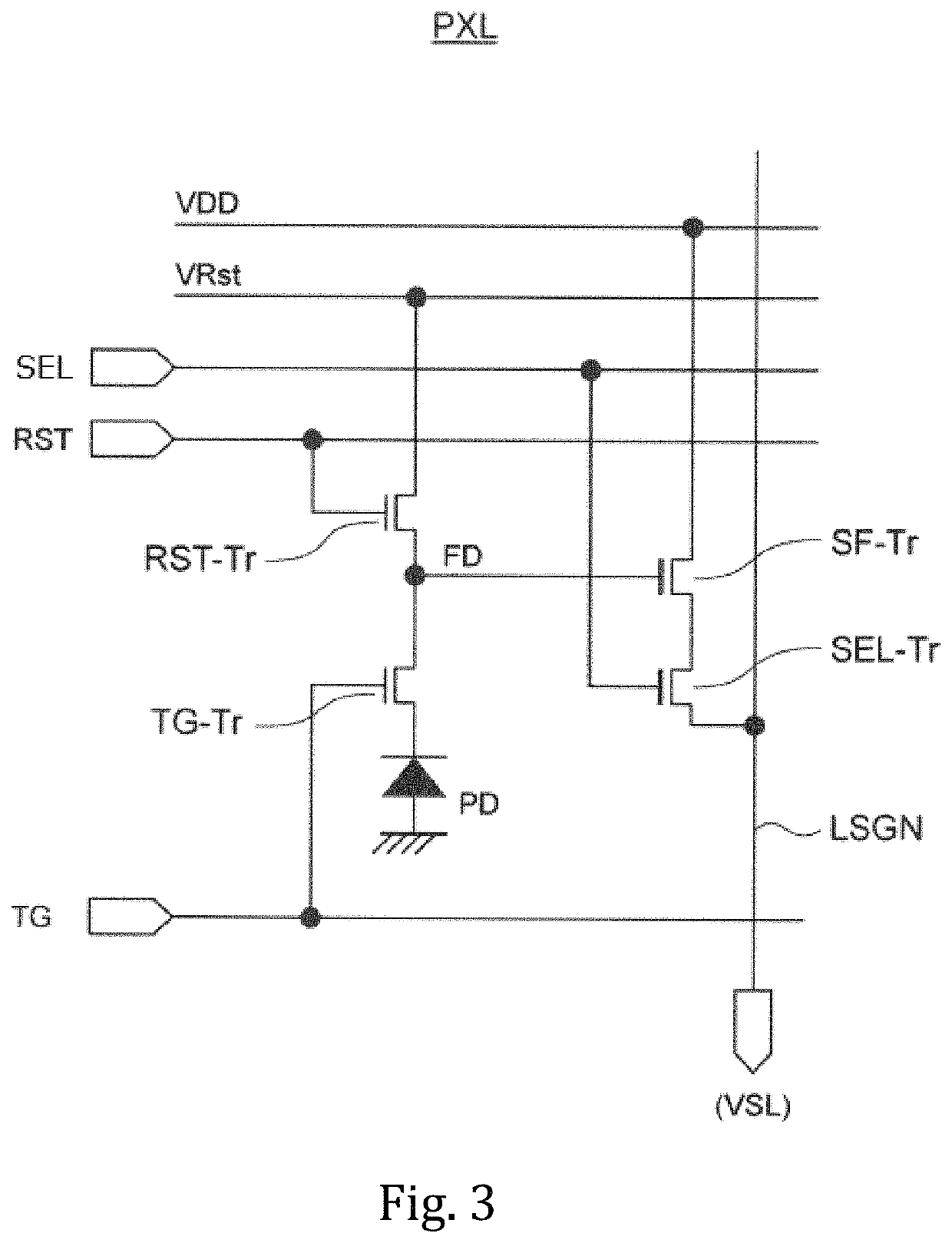
Solid-state imaging device, method for driving solid-state imaging device, and electronic apparatus
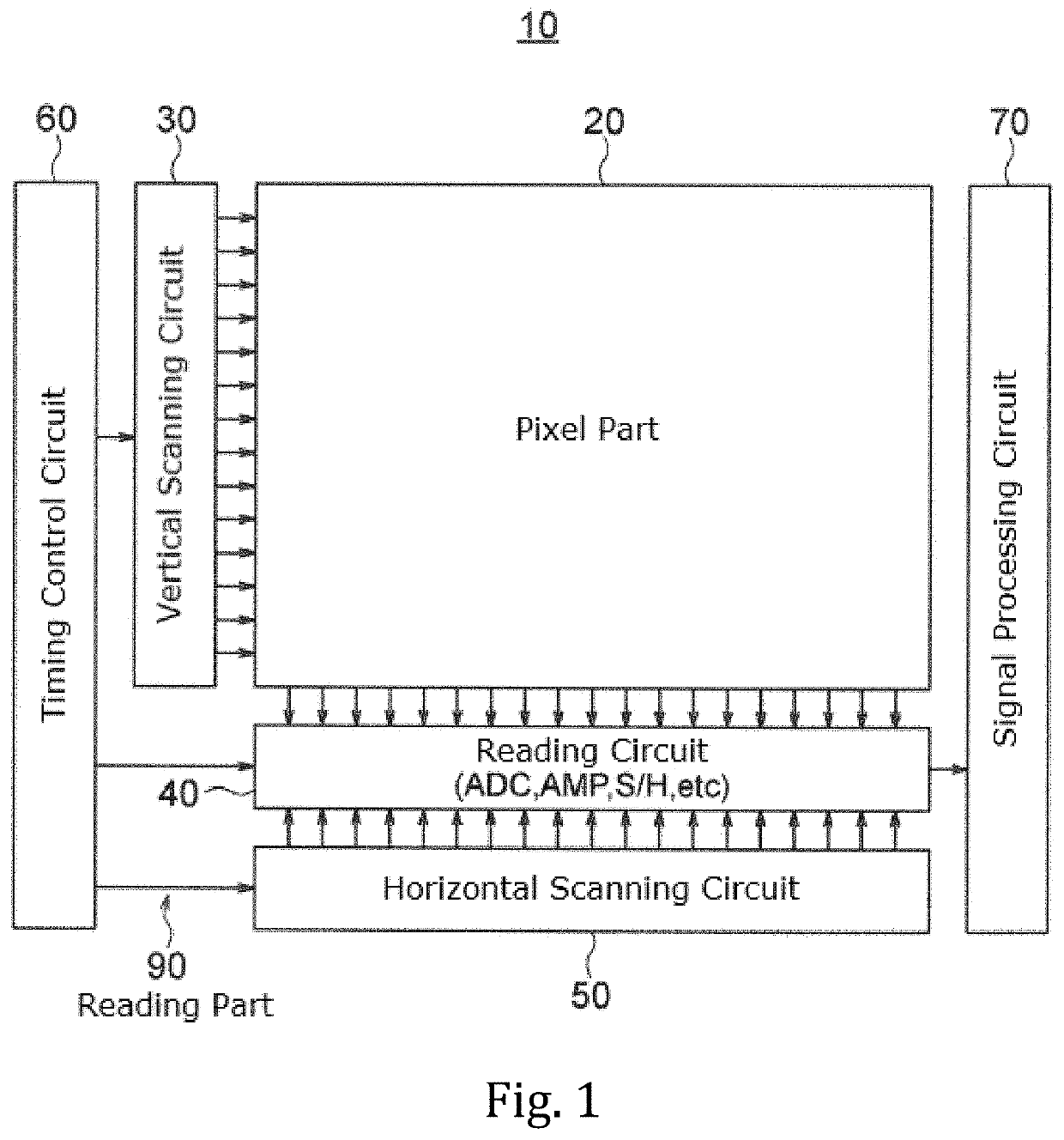
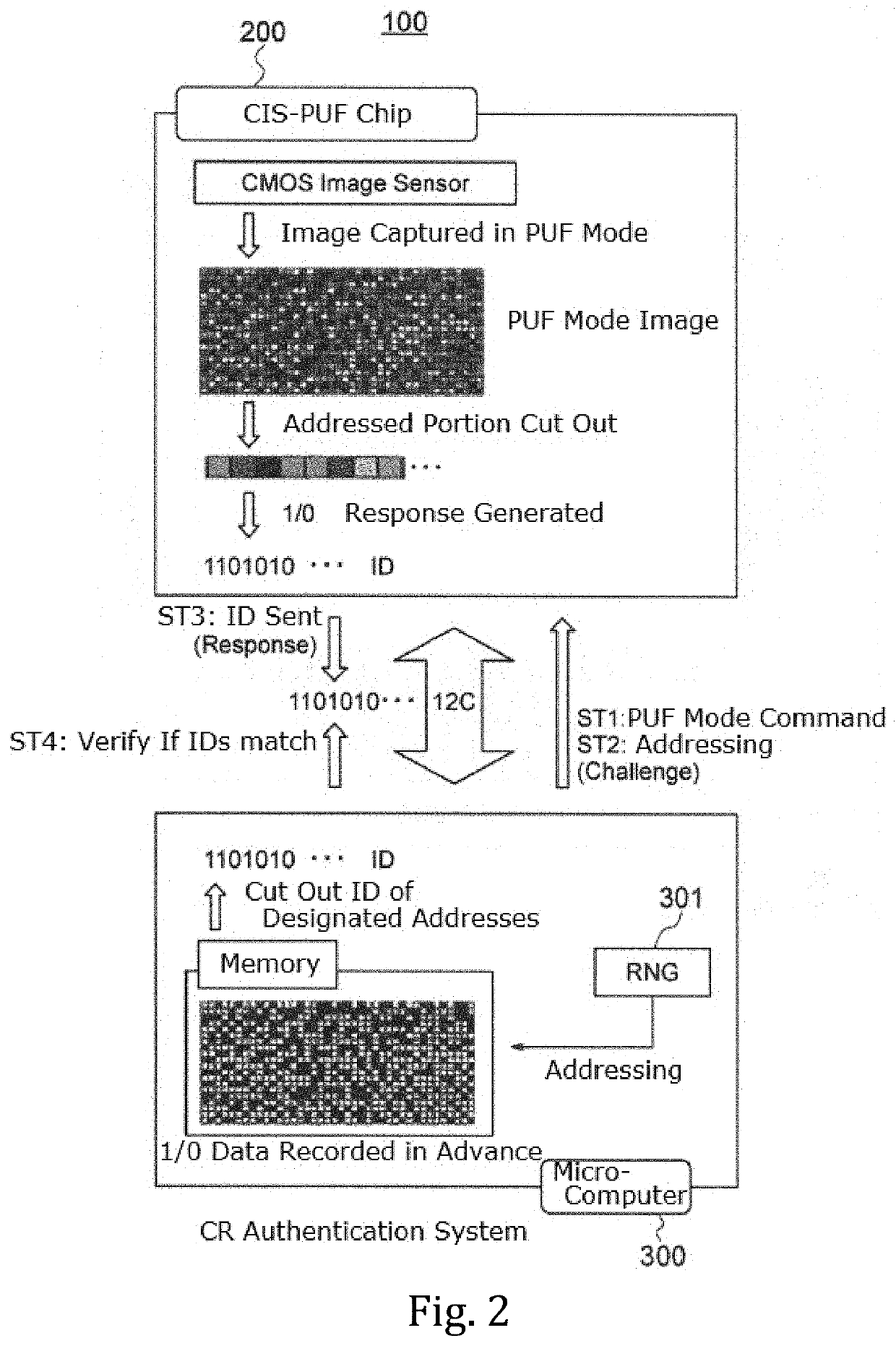
ActiveUS20200288078A1Increase randomnessLow costTelevision system detailsKey distribution for secure communicationFuzzy extractorNumber generator
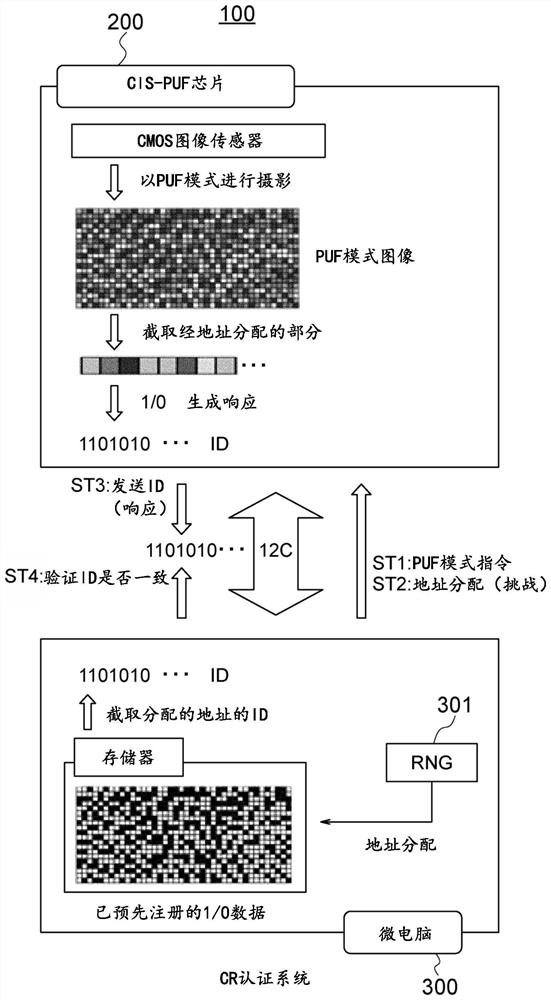
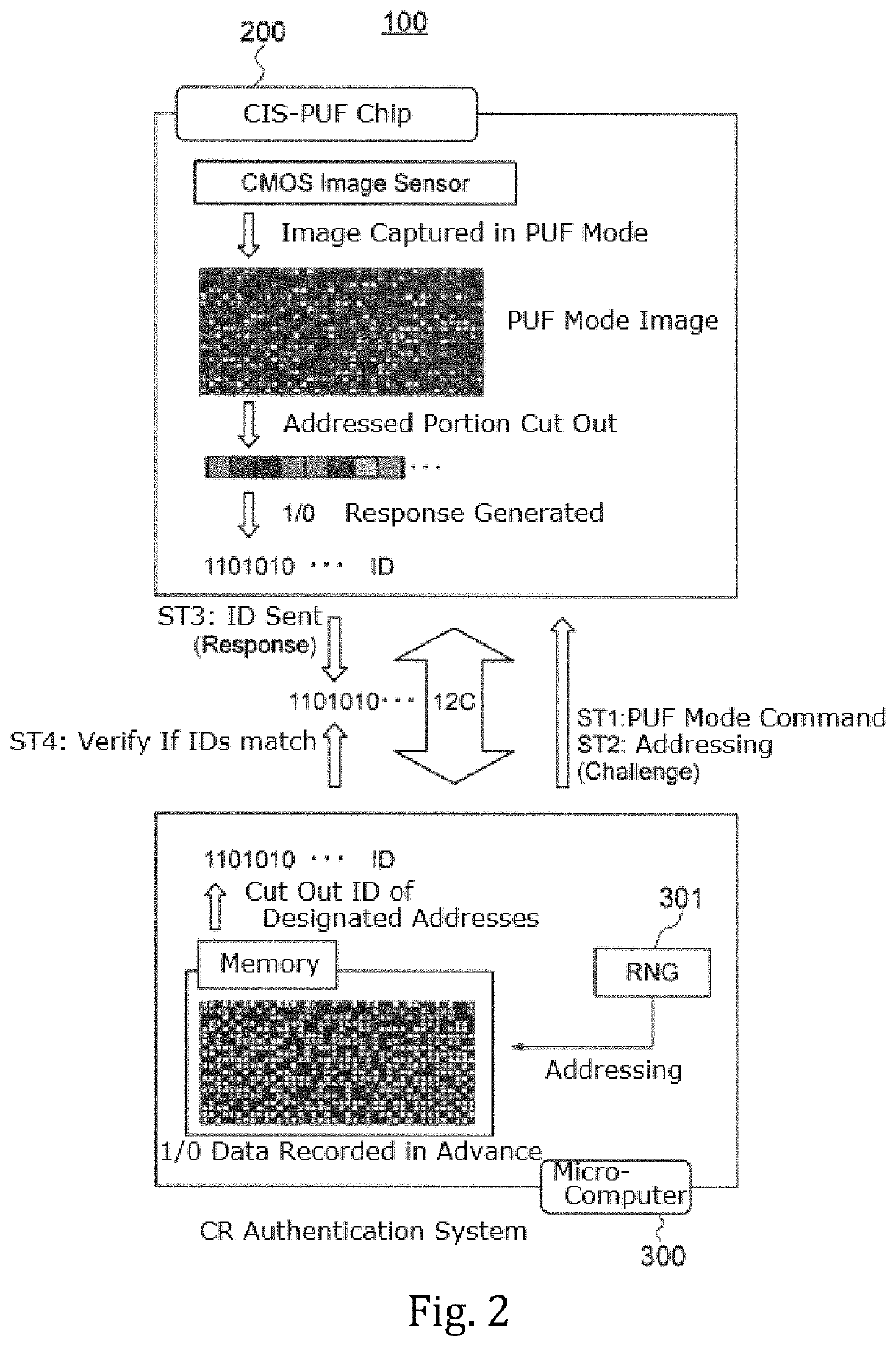
A fuzzy extractor includes an initial key generating part including a true random number generator, and a key regenerating part. The true random number generator generates a true random number using a read-out signal read from the reading part or a pixel signal read from the pixels of the pixel part in a true random number generation mode. The initial key generating part generates helper data and an initial key based on the true random number generated by the true random number generator and variation information acquired as a response when the initial key is generated. The key regenerating part generates, when a key is regenerated, a unique key based on helper data acquired when the initial key is generated and variation information acquired as a response including an error when the key is regenerated.
Owner:BRILLNICS JAPAN +1
Practical reusable fuzzy extractor based on the learning-with-error assumption and random oracle
ActiveUS20190020472A1Simple and efficient operationGuaranteed normal processingKey distribution for secure communicationEncryption apparatus with shift registers/memoriesComputer hardwareRandom oracle
Described is a system for biometric authentication. The system converts biometric data into a cryptographic key r′ using a reusable fuzzy extractor process having an underlying hash function modeling a random oracle model. The system allows access to secured services when a comparison of r′ to a previously computed cryptographic key r shows a match.
Owner:HRL LAB
Internet of Things security chip trusted mechanism
ActiveCN112152816AImprove securityAvoid the build processKey distribution for secure communicationEncryption apparatus with shift registers/memoriesComputer networkThe Internet
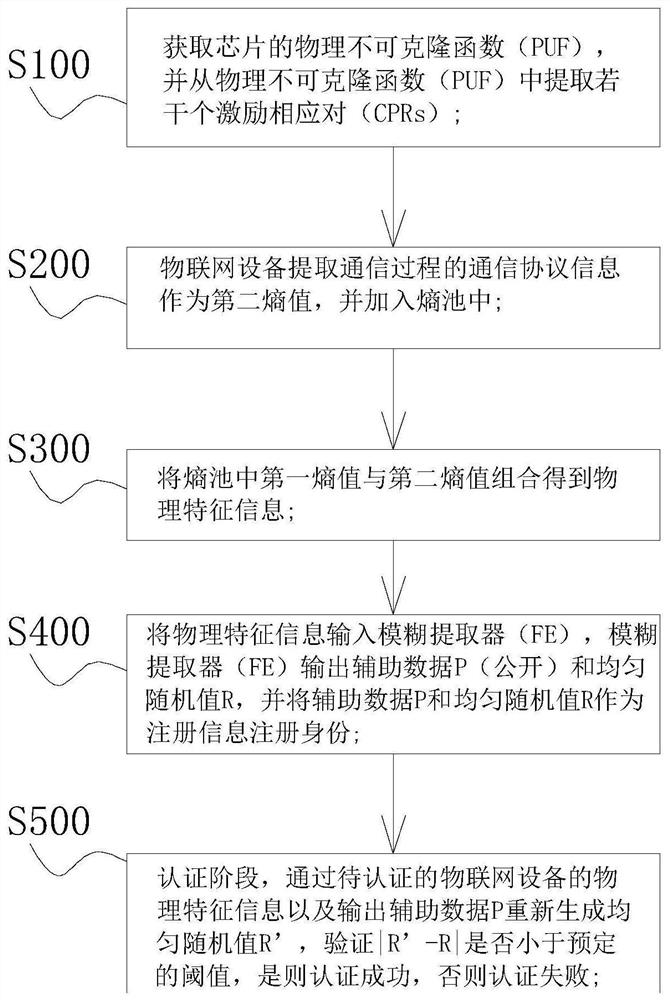
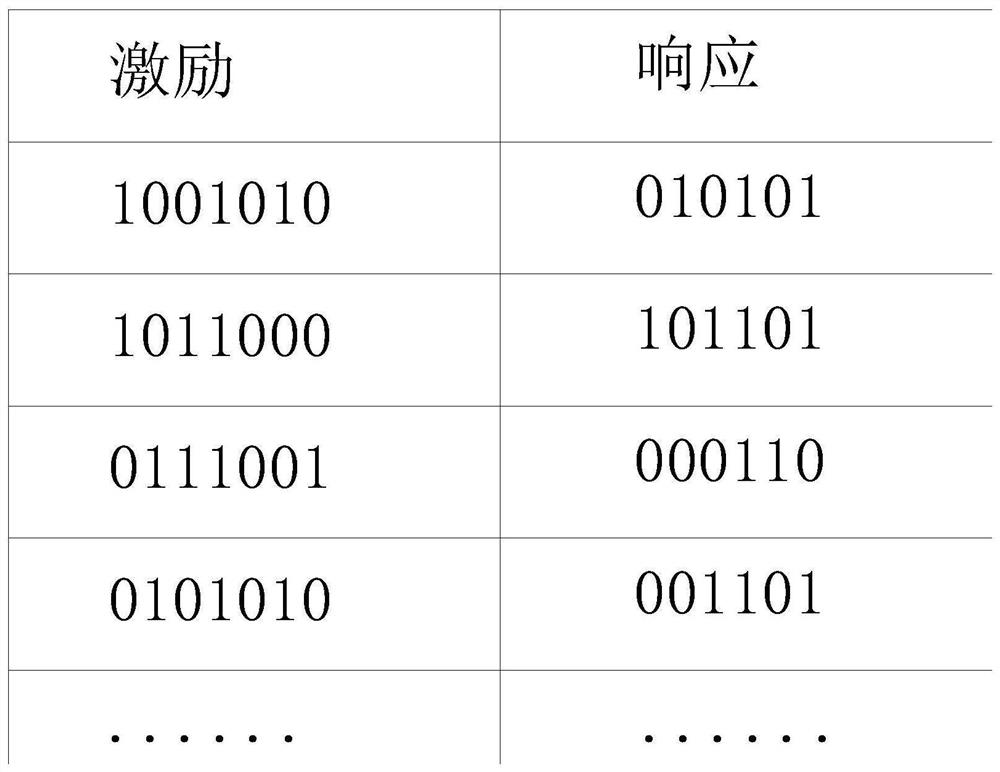
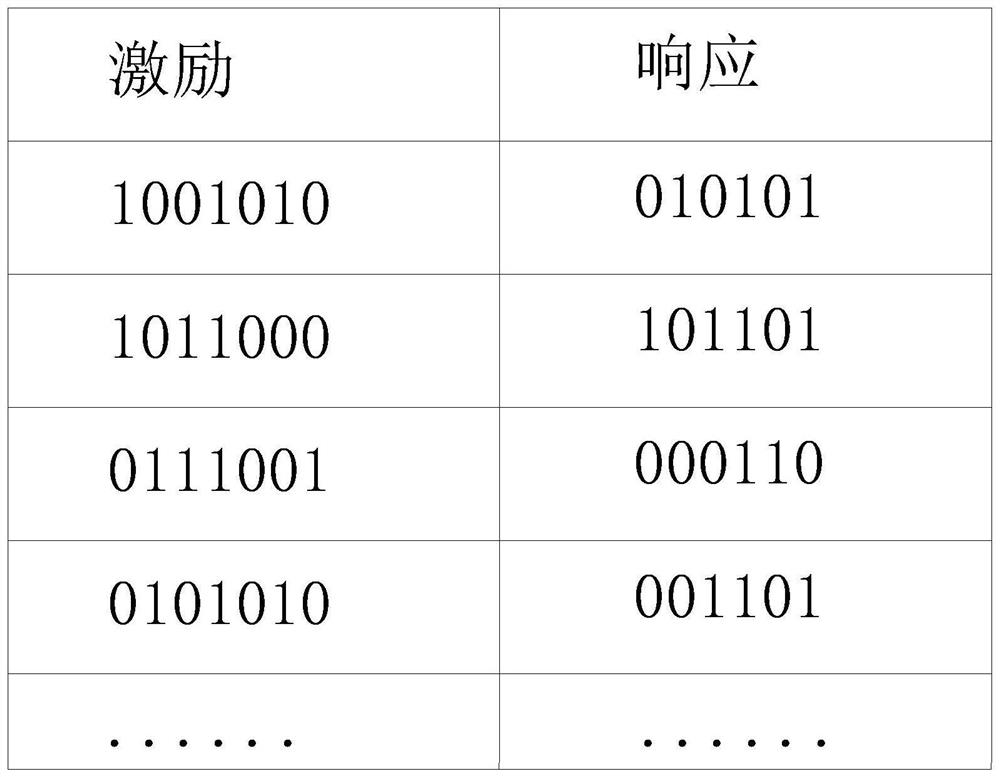
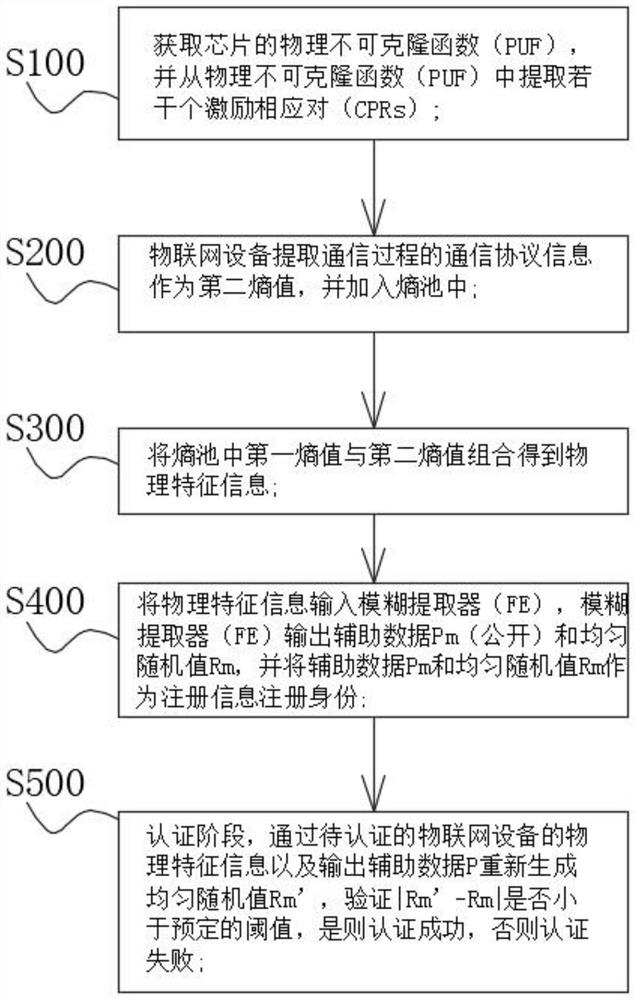
The invention discloses an Internet of Things security chip trusted mechanism, and relates to the technical field of Internet of Things security. The mechanism comprises the following steps: obtaininga physical unclonable function of a chip, and extracting a plurality of excitation corresponding pairs from the physical unclonable function; extracting a response part of the excitation corresponding pair as a first entropy value, and adding the first entropy value into an entropy pool; the Internet of Things equipment extracting communication protocol information in the communication process asa second entropy value and adding the second entropy value into an entropy pool; combining the first entropy value and the second entropy value in the entropy pool to obtain physical feature information; inputting the physical feature information into a fuzzy extractor, outputting auxiliary data P and a uniform random value R by the fuzzy extractor, and registering an identity by taking the auxiliary data P and the uniform random value R as registration information. The random feature physical fingerprint in the chip production and manufacturing process is used as identity registration information, the block chain is used as an identity generation and registration platform, and the safety is high.
Owner:南京航灵信息科技有限公司
Physical unclonable function circuit structure based on multiple bunching delay
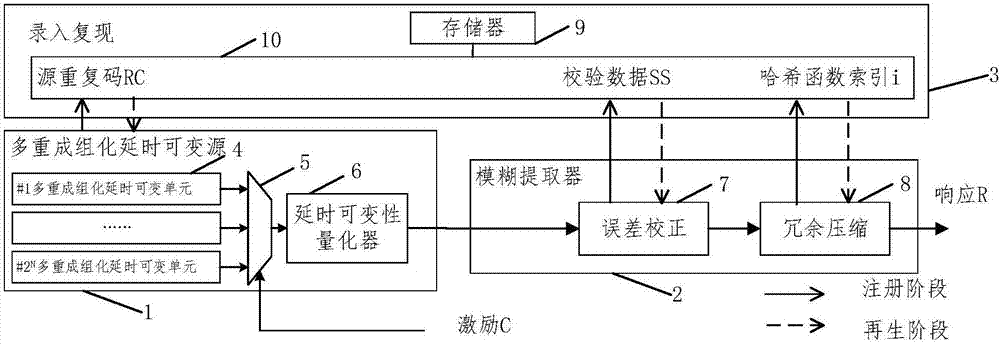
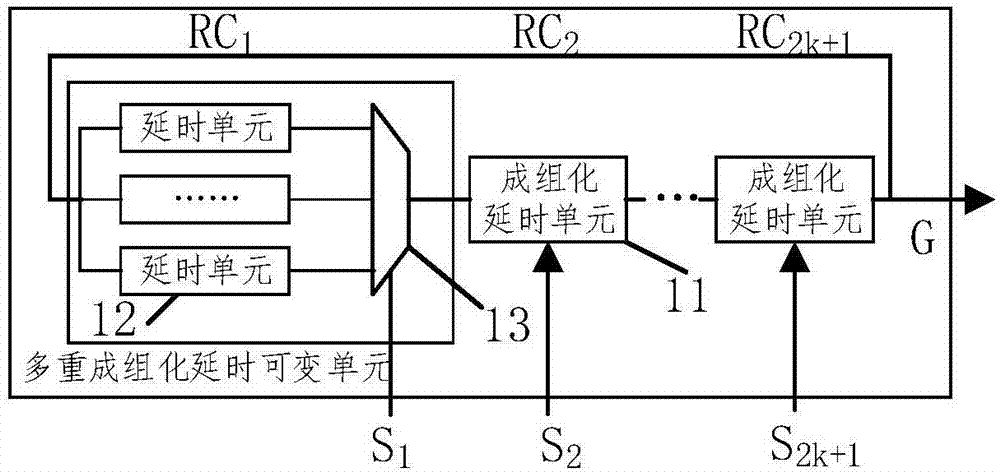
The invention discloses a physical unclonable function circuit structure based on multiple bunching delay. The physical unclonable function circuit structure includes a variable-source multiple bunching delay module, a fuzzy extractor module and a logging and recurrence module; a multiple bunching delay unit and a fuzzy extractor which is based on linear codes and a hash function family are adopted, and physical unclonable functions which are high in stability and uniqueness are achieved.
Owner:ZHEJIANG UNIV
Reusable fuzzy extractor based on the learning-with-error assumption secure against quantum attacks
ActiveUS20200145206A1Simple and efficient operationGuaranteed normal processingKey distribution for secure communicationUser identity/authority verificationGeneration processBiometric data
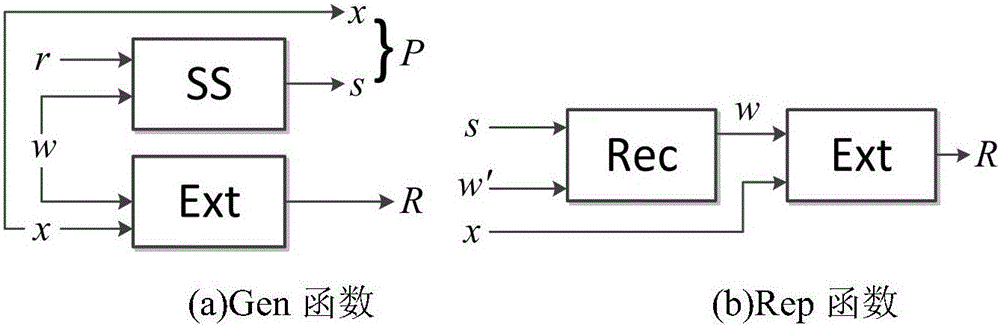
Described is a system for biometric based security. The system converts biometric data into a cryptographic key using a reusable fuzzy extractor process. The reusable fuzzy extractor process comprises a generation process and a reconstruction process. The generation process takes as input a public parameter and a first biometric input and outputs a public helper string and a first random string. The reconstruction process takes as input a public helper string and a second biometric input and outputs a second random string. The reusable fuzzy extractor process is reusable such that multiple public helper strings do not reveal any information about the first biometric input and the first random string. Secured data is unlocked by applying the cryptographic key for biometric security of access to secured data.
Owner:HRL LAB
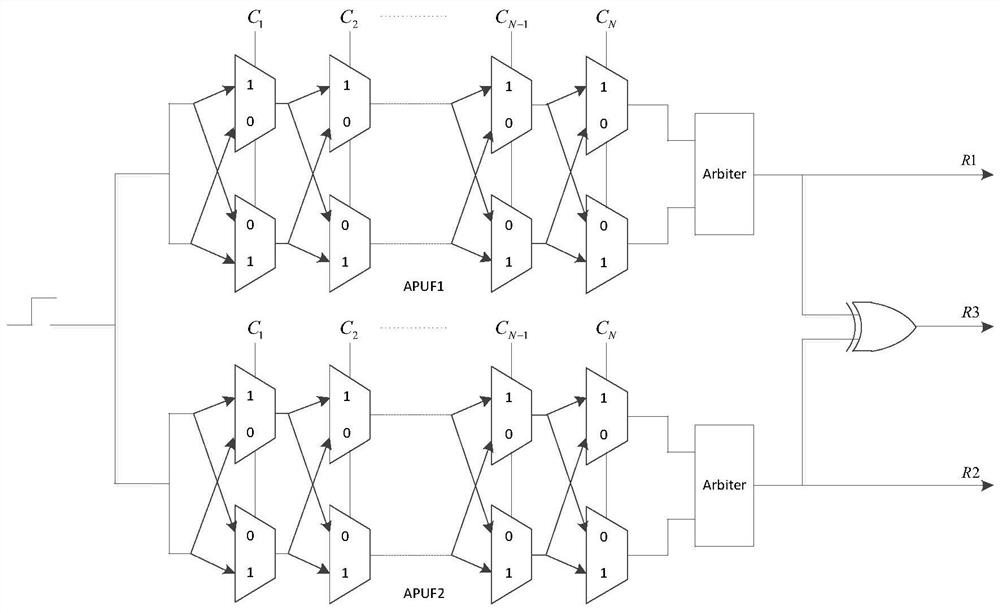
Lightweight security authentication method based on XOR-APUF
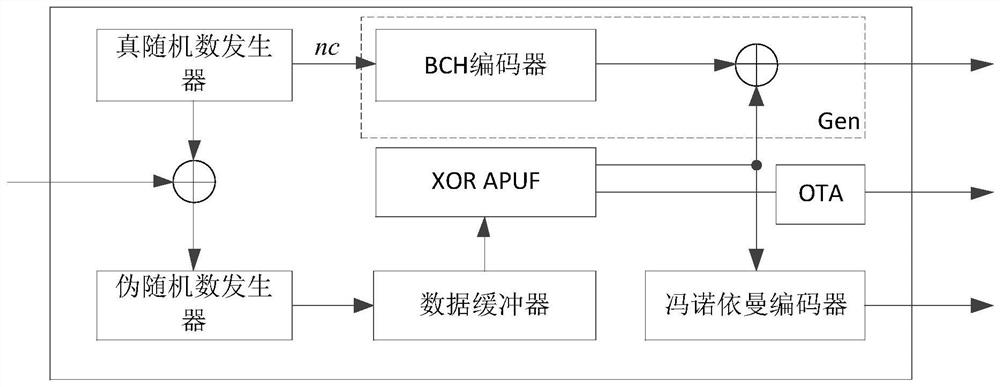
ActiveCN112019347AEnsure safetyGuaranteed lightweightKey distribution for secure communicationUser identity/authority verificationAlgorithmParallel computing
Owner:SOUTHEAST UNIV
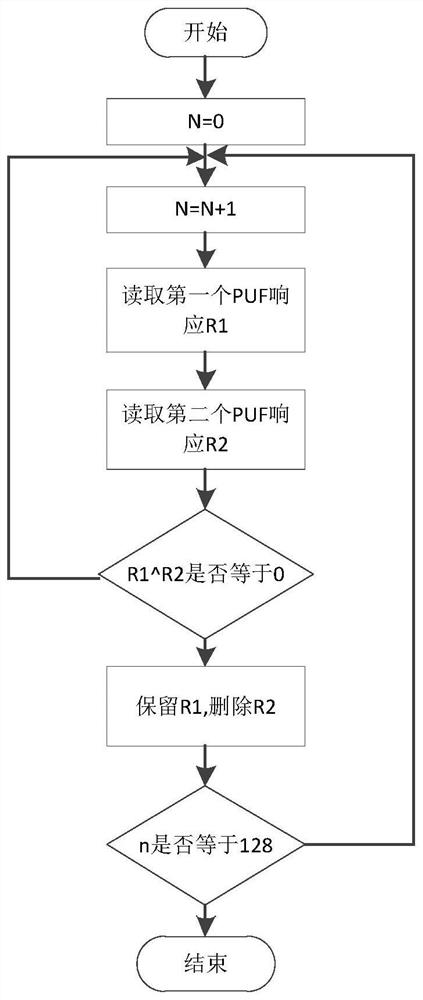
Random number generation, regeneration and tracking method based on non-uniform random source in group, and electronic device
Owner:INST OF INFORMATION ENG CAS +1
Fingerprint biometric key generation method based on deep neural network coding
PendingCN113128364AImprove securityIncrease flexibilityBiometric pattern recognitionNeural architecturesKey sizeEngineering
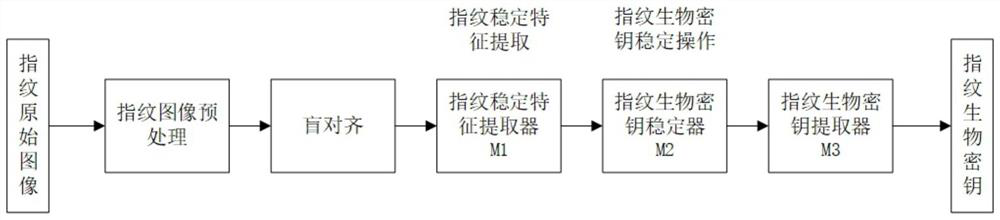
The invention discloses a fingerprint biological key generation method based on deep neural network coding. According to the method, a classic fingerprint image processing method and a deep neural network method are combined, a series of operations of blind alignment, stable feature extraction, feature sequence stabilization and the like of the fingerprint image are realized, stable feature components of different samples of the same fingerprint are extracted more accurately, and through layer-by-layer processing of the deep neural network, the method further stabilizes the fingerprint feature to the feature value, and finally realizes the high-intensity key sequence generation of the normal fingerprint image through a fingerprint key fuzzy extractor, and the length of the generated fingerprint biological key can be greater than 512 bits. According to the method, biological feature template information needing to be recorded does not exist, the risk of privacy disclosure is greatly reduced, meanwhile, a user can generate a high-safety secret key without high-intensity memory, the secret key can be used for existing public and private keys, symmetric encryption and other operations, and the safety and flexibility of fingerprint biological feature use are improved.
Owner:HANGZHOU DIANZI UNIV
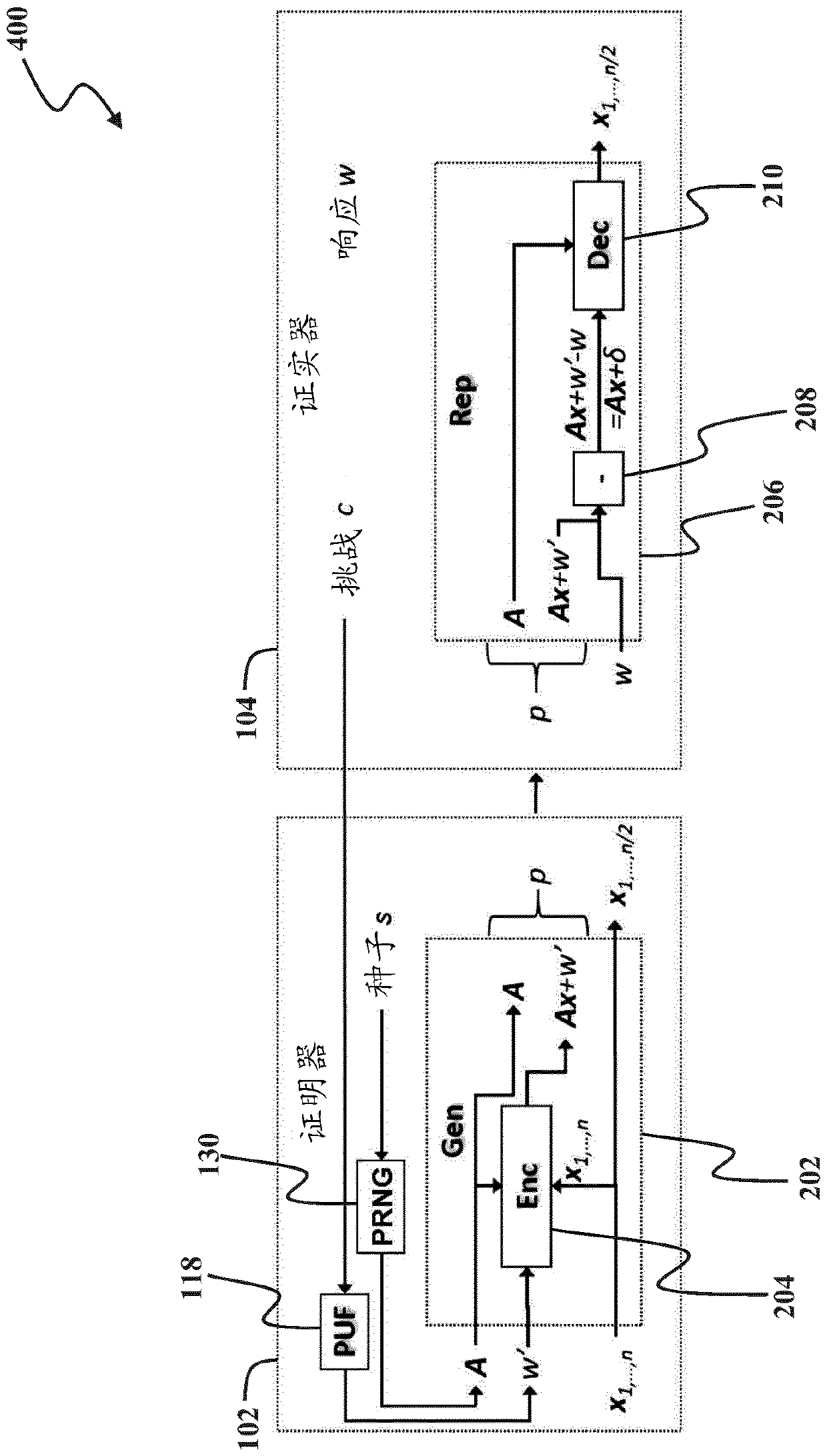
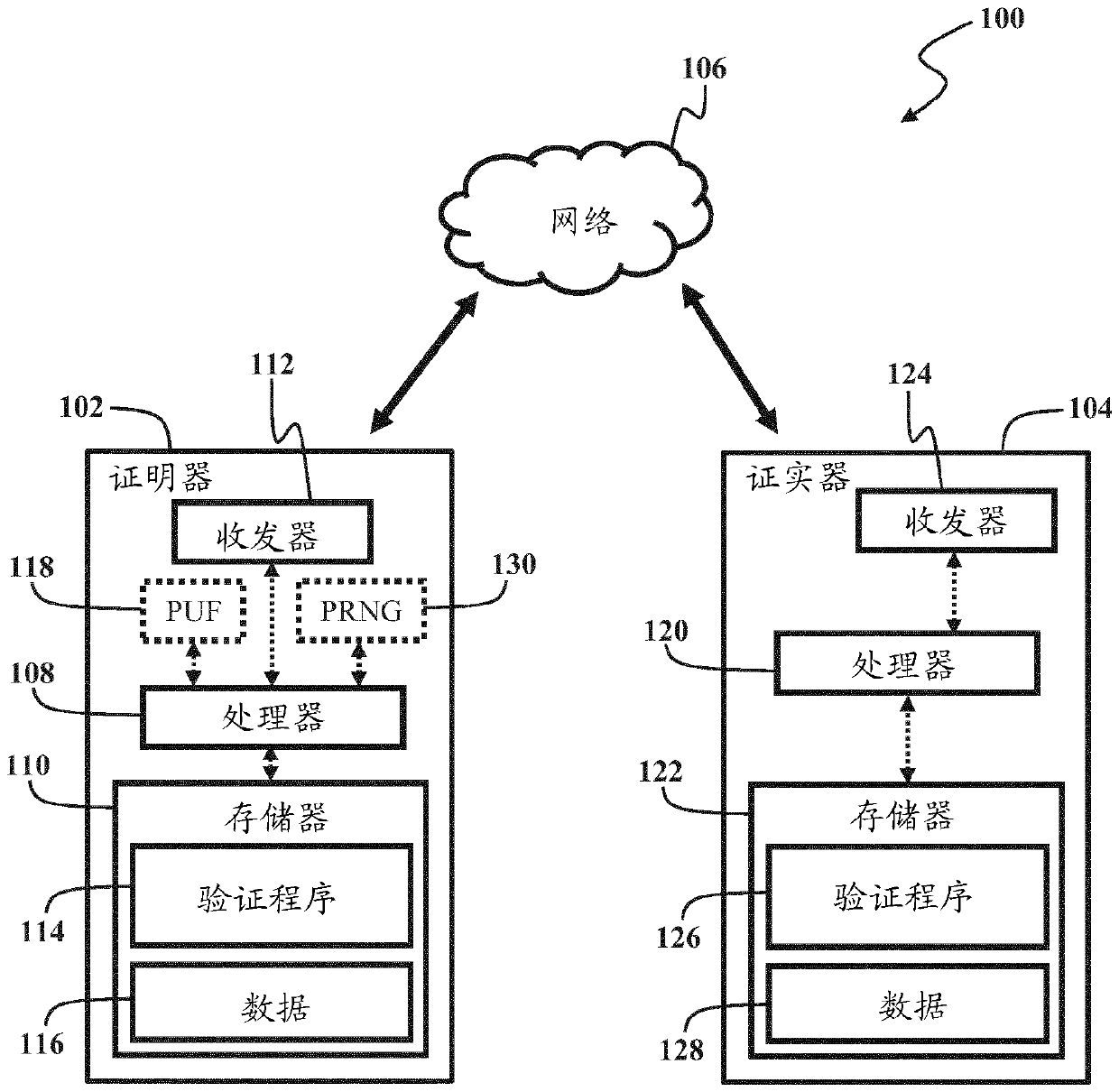
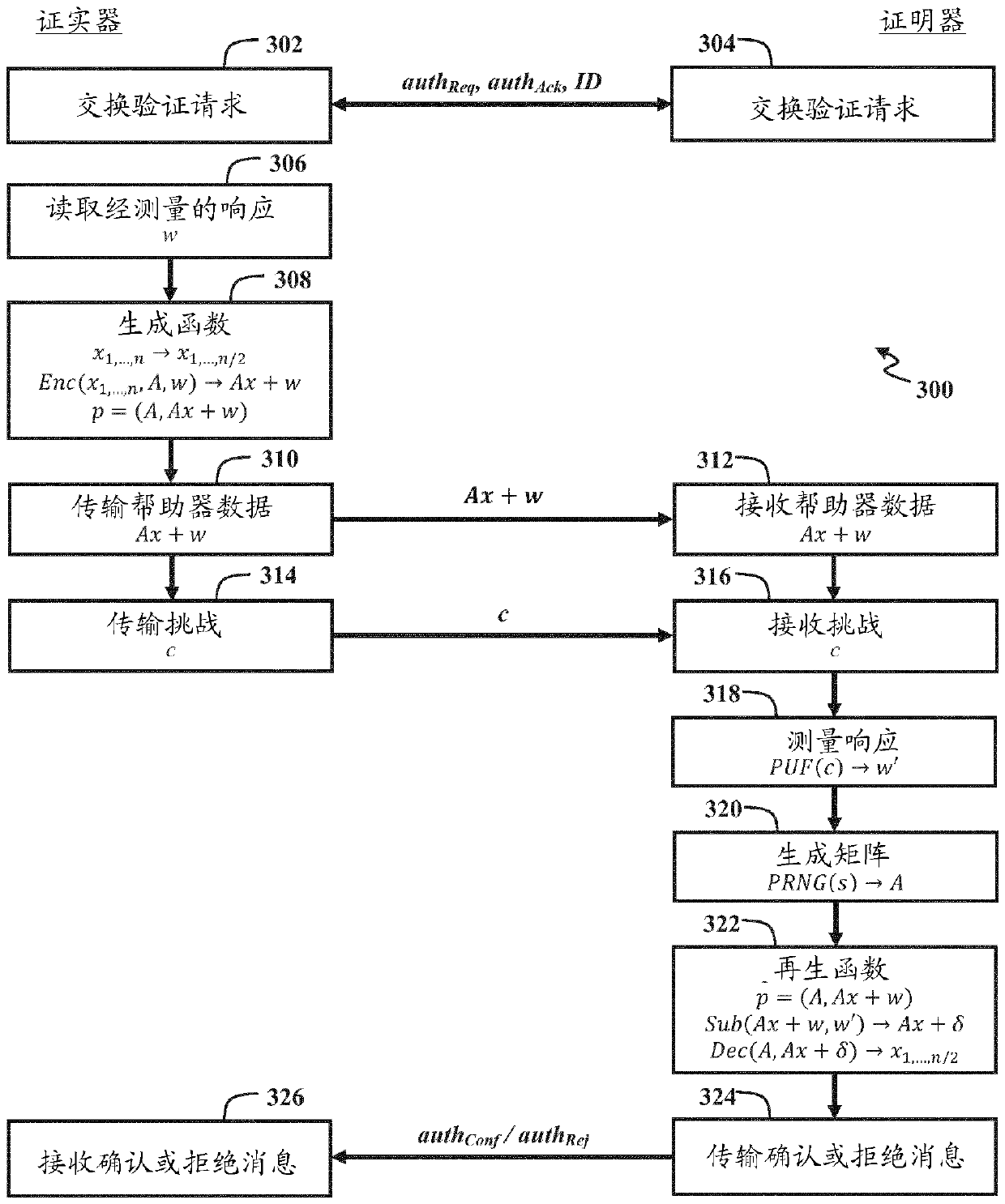
Pseudo-random generation of matrices for computational fuzzy extractor and method for authentication
ActiveCN110089075ADigital data processing detailsUser identity/authority verificationAlgorithmTheoretical computer science
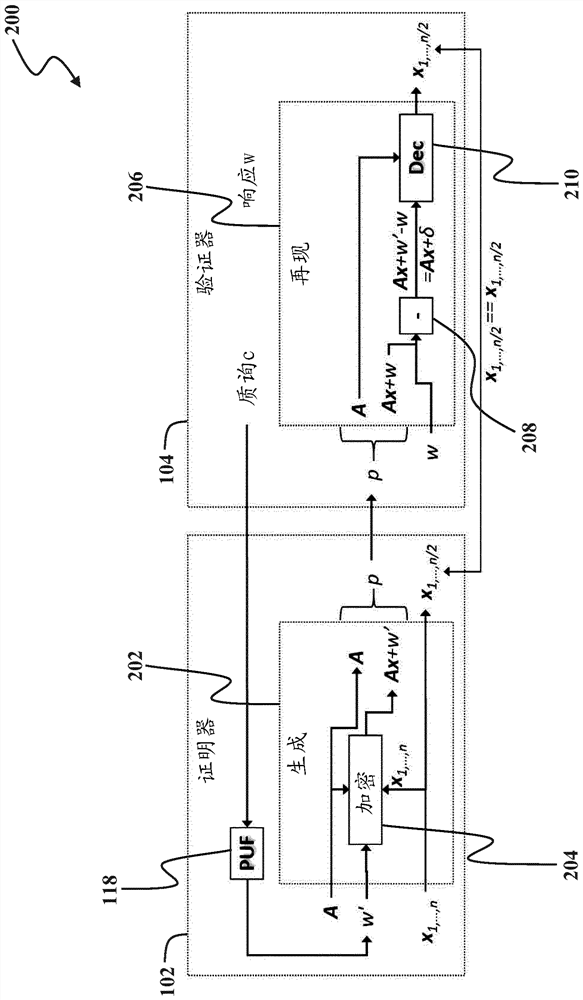
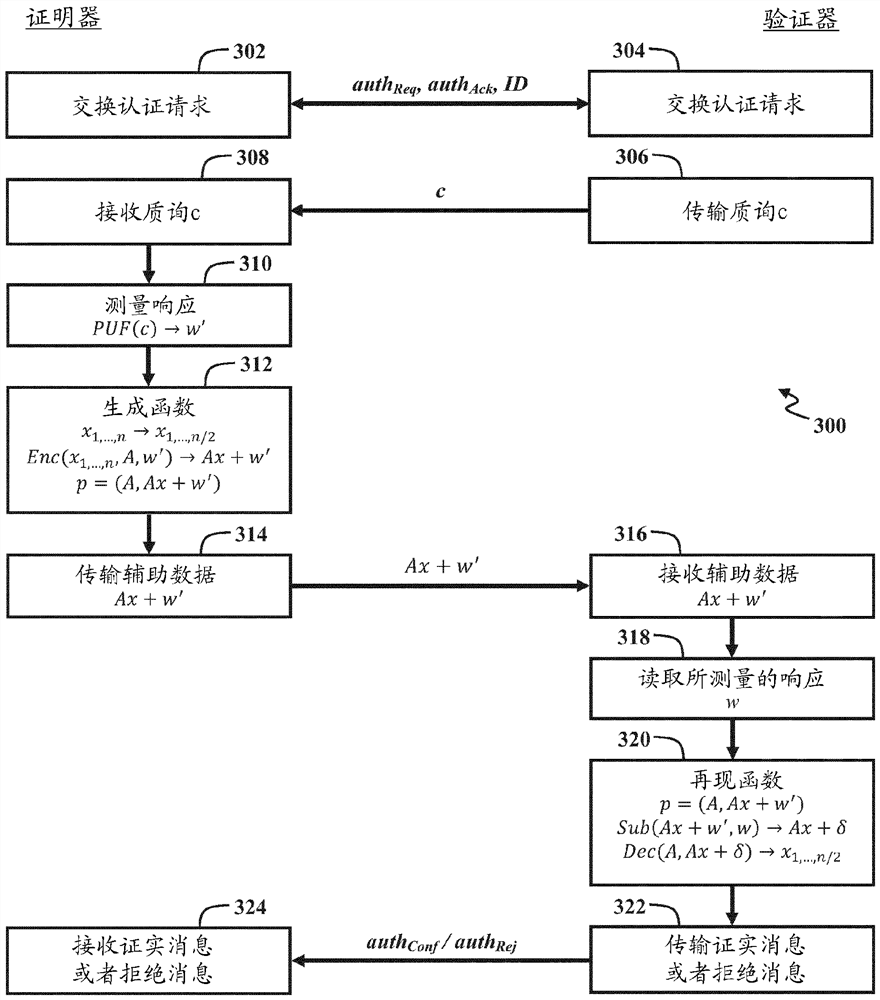
A method for authenticating a first device is disclosed. In one embodiment, the method includes the steps of: receiving a helper bit string from a second device that is remote from the first device; measuring a first response bit string of a physical unclonable function of the first device with respect to a challenge bit string; subtracting the first response bit string from the helper bit string;reconstructing a random matrix using a pseudo-random number generator initialized with a seed; and decoding a result of the subtraction using the random matrix, the shared secret bit string being provided from the decoding if the helper bit string was encoded using a previously measured second response bit string that is within a threshold level of similarity to the first response bit string, thedecoding outputting an error value otherwise.
Owner:ROBERT BOSCH GMBH
Solid-state imaging device, method for driving solid-state imaging device, and electronic apparatus
ActiveUS20210127080A1Reduce dataPrevent forgeryTelevision system detailsSolid-state devicesEngineeringComputer vision
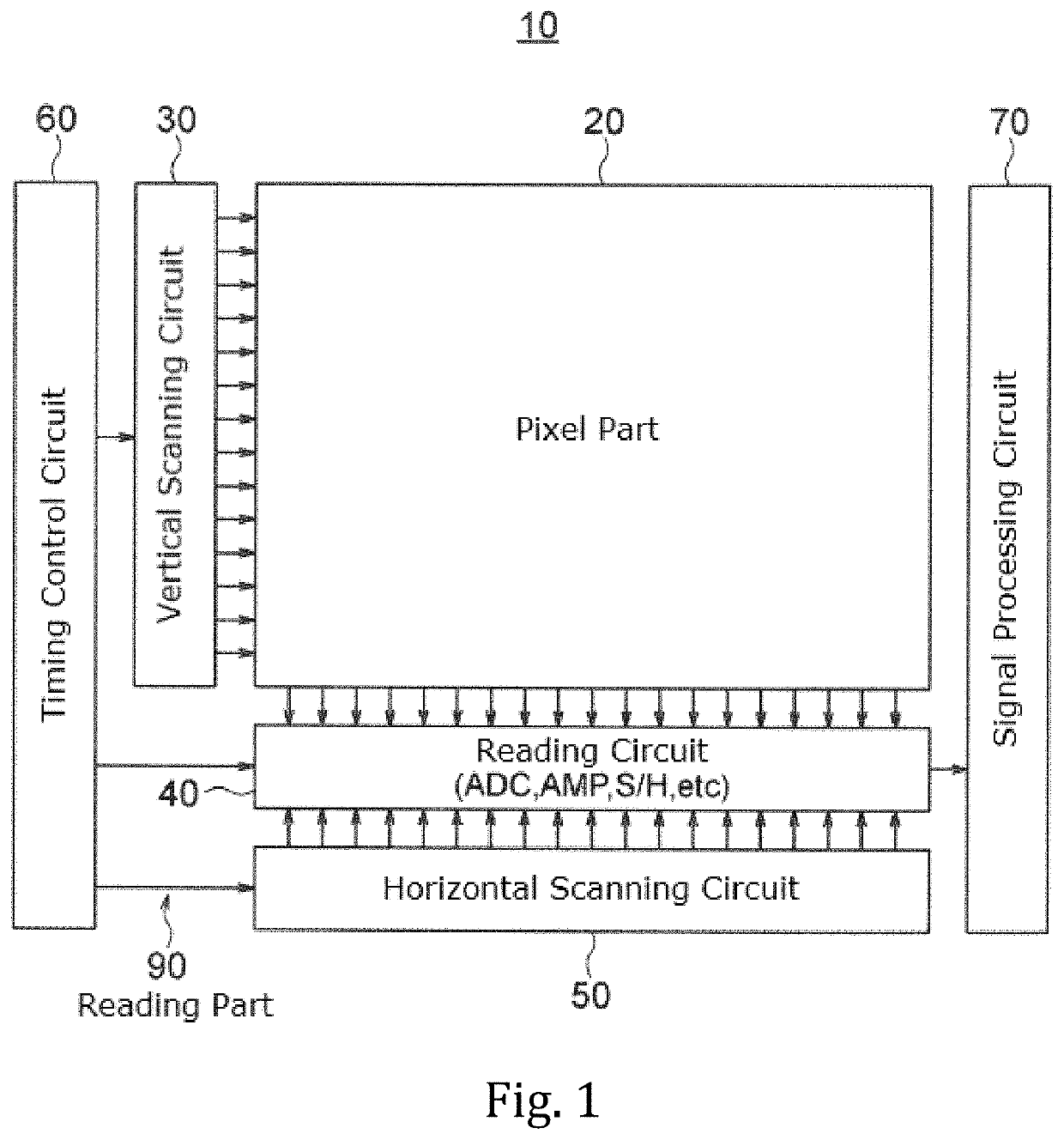
A solid-state imaging device includes a pixel part, a reading part for reading a pixel signal from the pixel part and a response data generating part including a fuzzy extractor. The response data generating part generates response data including a unique key in association with at least one selected from among variation information of pixels and variation information of the reading part. The response data generating part generates, when regenerating a key, a unique key using helper data acquired in generation of an initial key, variation information acquired in the regeneration of the key, and reliability information determined based on the variation information acquired in the regeneration of the key.
Owner:BRILLNICS JAPAN +1
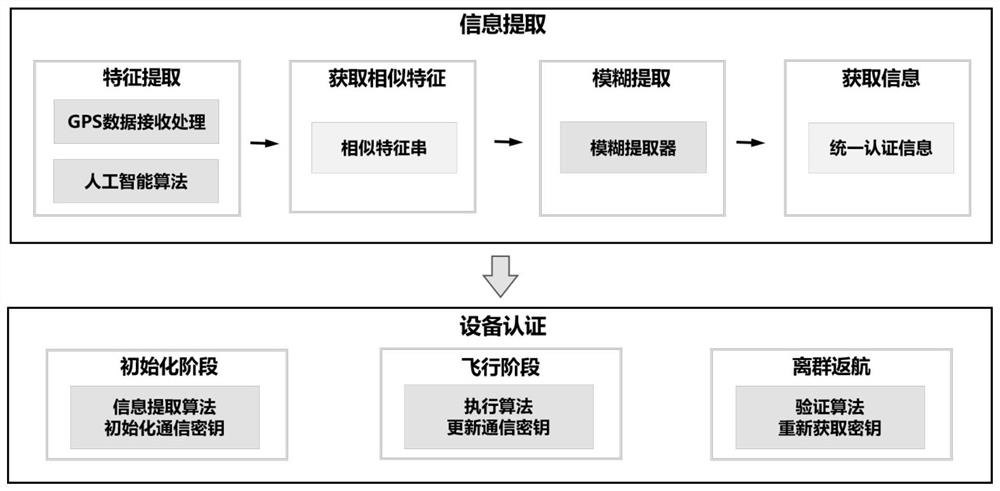
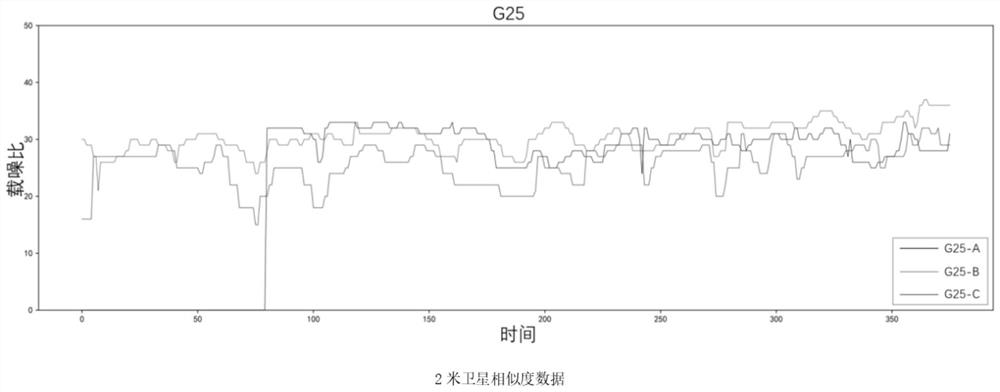
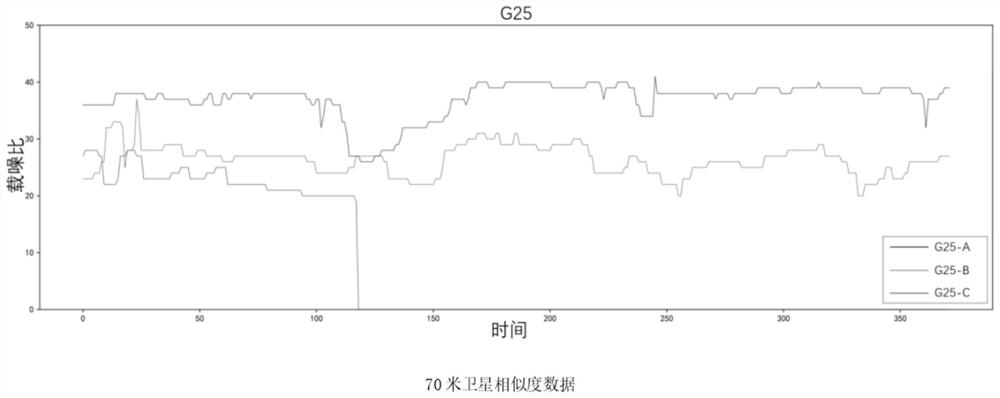
Unmanned aerial vehicle group key extraction and security authentication method based on GPS signal
PendingCN114153227AAvoid distributingEnough information entropyPosition/course control in three dimensionsCommunications securityInformation processing
The invention relates to an unmanned aerial vehicle group key extraction and security authentication method based on a GPS signal, and belongs to the technical field of data information processing. The method is mainly divided into an information extraction stage and an equipment authentication stage, and during initialization, each node in a cluster system generates similar sequence information by using an artificial intelligence technology according to a GPS signal acquired by the node; unified information is generated through a fuzzy extractor; and finally, generating a session key according to the unified information. In the flight process, interaction information is encrypted through session keys among the aircrafts so as to ensure communication safety, and in the flight process, the aircrafts extract the keys again according to the GPS signals at set intervals so as to realize key updating. According to the scheme, the generation of the initial keys on all the unmanned aerial vehicles in the fleet can be realized only through a public channel, and the problem of insufficient randomness of the keys can be well solved. In addition, the authentication mechanism based on the GPS signal in the scheme can also be applied to other unmanned equipment ad hoc network scenes, and has good expansibility and commercial value.
Owner:CHONGQING UNIV
Use of biometrics and privacy preserving methods to authenticate account holders online
ActiveCN110999212AUser identity/authority verificationCommunication with homomorphic encryptionBiometric dataInternet privacy
Embodiments are directed to a method for securely performing biometric authentication online. The method described can be used to securely perform biometric authentication on a mobile device. For protecting the privacy of the user biometric data, a cryptographic comparison protocol can be used to perform matching of encrypted templates. For example, the cryptographic comparison protocol may involve Fuzzy Extractors (FE), Homomorphic Encryption (HE), and / or Secure Multi-Party Computation (SMPC).
Owner:VISA INT SERVICE ASSOC
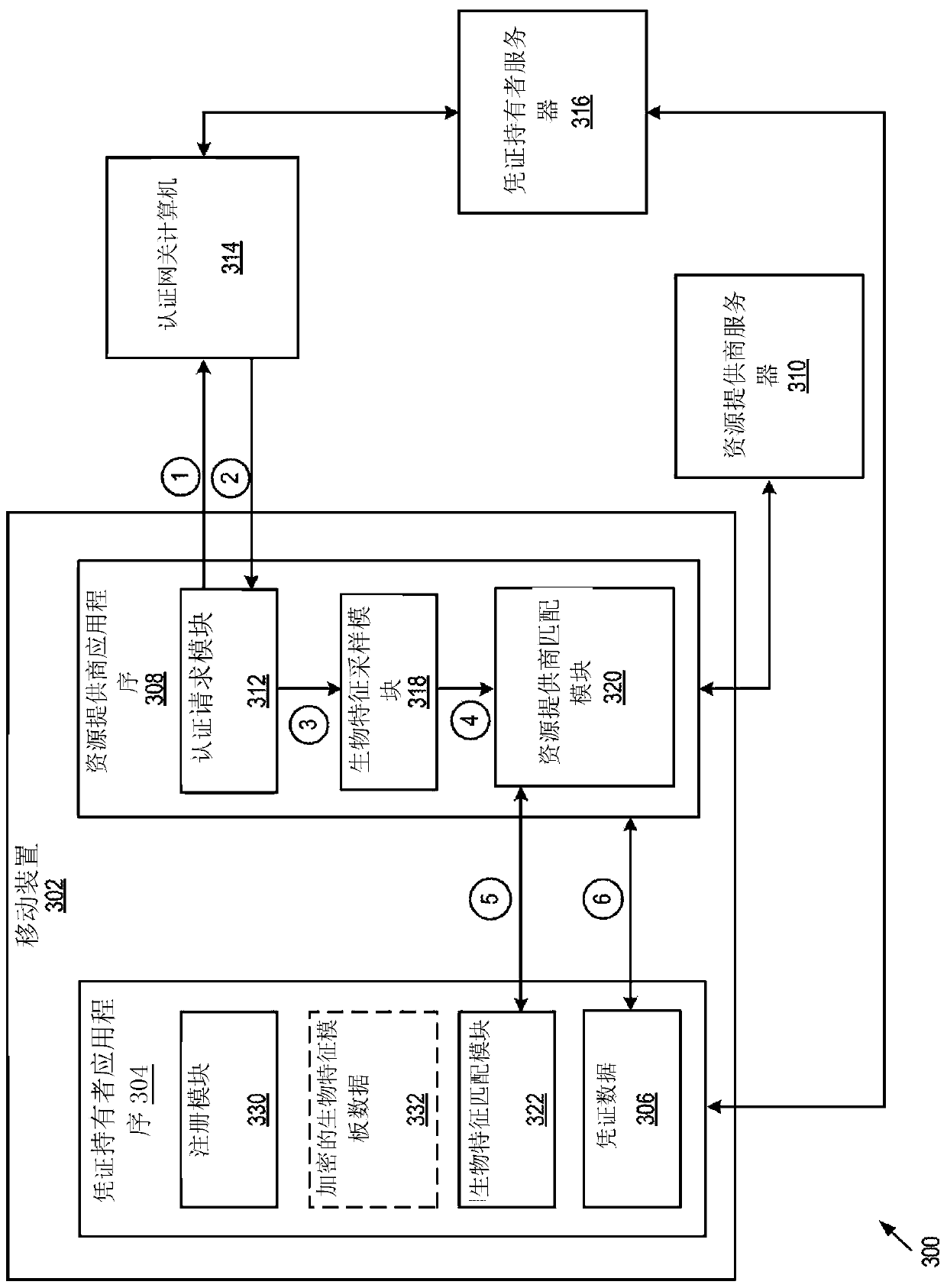
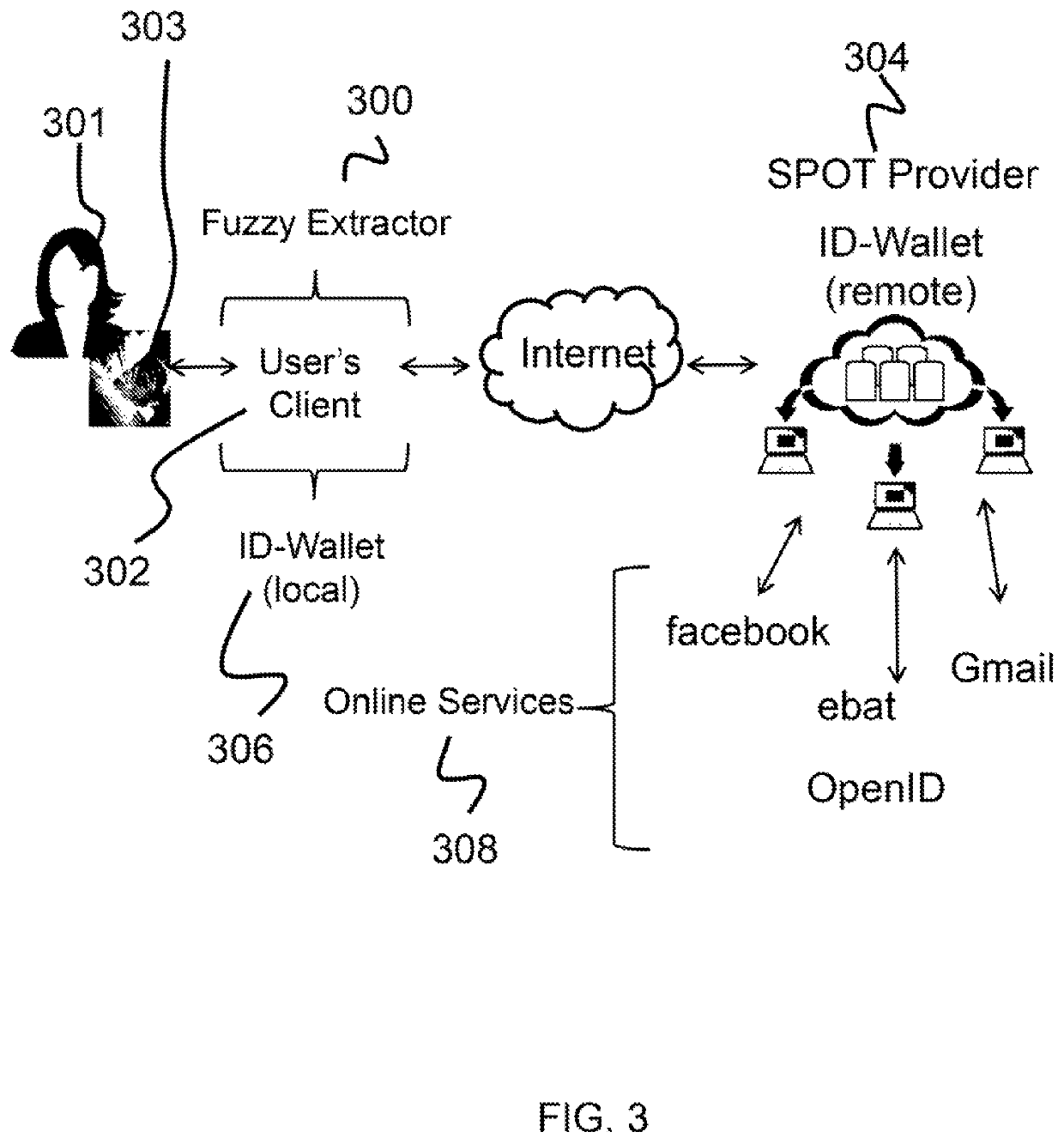
System and method to integrate secure and privacy-preserving biometrics with identification, authentication, and online credential systems
Described is a system for the implementation of biometric scanning in a user-privacy preserving fashion with respect to identification, authentication, and online credential systems. At enrollment, the user enrolls or initially registers at a physical location, where the user is provided a Fuzzy Extractor (FE) encrypted output (Enc(R)). The user is then registered with an online server, which creates an ID-Wallet for the user and stores the ID-Waller. During operation, the user sends an authentication request to the online server, which provides a corresponding authentication response. The user or user's client then extracts secret (R) for user authentication. The user can then be authenticated with the online server to retrieve credentials from the ID-Wallet, which can be used for a variety of online services.
Owner:HRL LAB
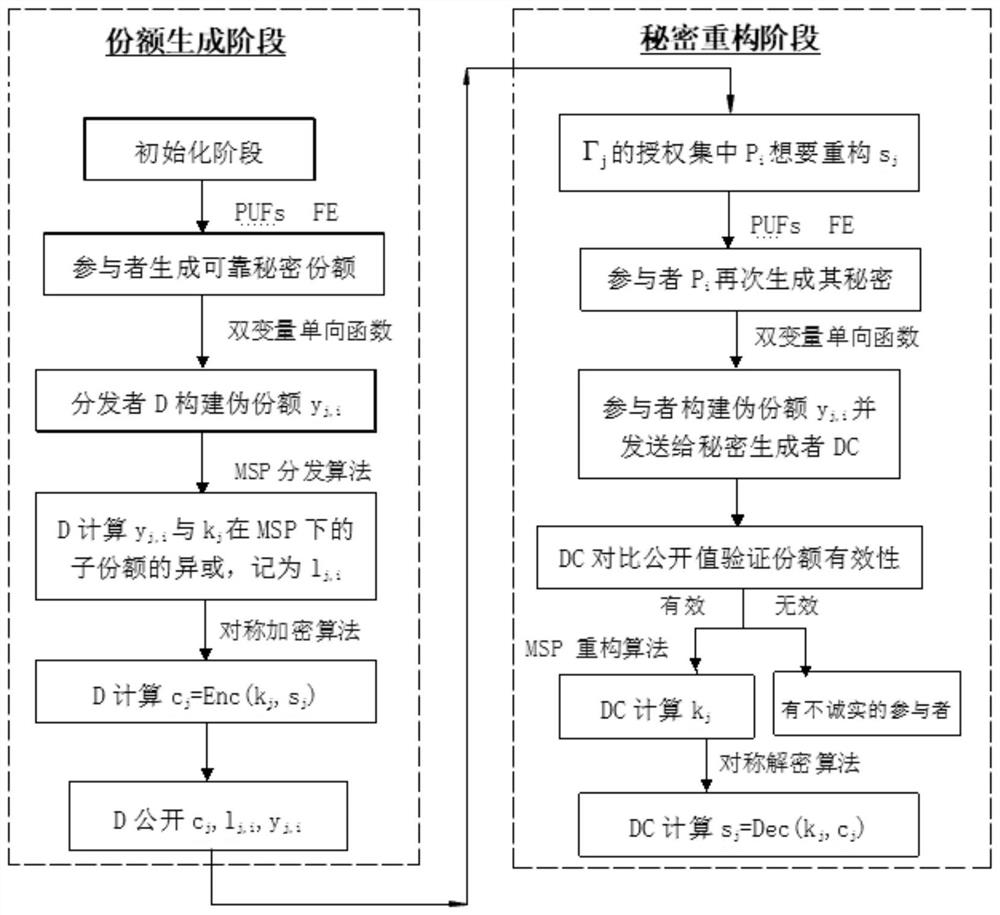
Multi-level secret sharing method for calculating safety under standard model and resisting memory leak
The invention discloses an anti-memory leak multi-level secret sharing method for calculating safety under a standard model, which relates to the technical field of computer information safety, and comprises the following steps of: extracting the same character string which is randomly and uniformly distributed by utilizing the combined action of a physical unclonable function and a fuzzy extractor, namely generating a reliable secret share; in this way, the secret sharing method can meet the safety requirement under the environment of memory leakage. Meanwhile, according to the secret sharing method, the secret share of each participant can be used for multiple times and is used for recovering multiple secrets. According to the technical scheme, a verifiable multi-level secret sharing method which is suitable for a common access structure and is capable of resisting memory leakage is constructed instead of the idea of storing a long-term secret share in a nonvolatile memory in the prior art.
Owner:SHAANXI NORMAL UNIV
Finger vein biological key generation method based on deep neural network coding
PendingCN112906527AImprove stabilityIncrease success rateBiometric pattern recognitionNeural architecturesPattern recognitionKey size
The invention discloses a finger vein biological key generation method based on deep neural network coding. By combining a classical finger vein image processing method and a deep neural network processing method of a finger vein original image, compared with an existing classical finger vein feature point extraction method, stable feature components of different samples of the same finger vein can be extracted more accurately, and through layer-by-layer processing of the deep neural network, features are kept to be feature values. finally, through a finger vein fuzzy extractor, high-intensity key sequence generation of a normal finger vein image is realized, and the length of the generated finger vein biological key can be greater than 256 bits. Biological feature template information needing to be recorded does not exist, the risk of privacy disclosure is greatly reduced, meanwhile, a user can generate a high-safety secret key without high-intensity memory, the secret key can be used for existing public and private keys, symmetric encryption and other operations, and the safety and flexibility of finger vein biological feature use are improved.
Owner:HANGZHOU DIANZI UNIV
A Trusted Mechanism for IoT Security Chips
ActiveCN112152816BImprove securityAvoid the build processKey distribution for secure communicationEncryption apparatus with shift registers/memoriesComputer networkEngineering
Owner:南京航灵信息科技有限公司
Backward Computational Fuzzy Extractor and Method for Authentication
ActiveCN110100412BUser identity/authority verificationParallel computingPhysical unclonable function
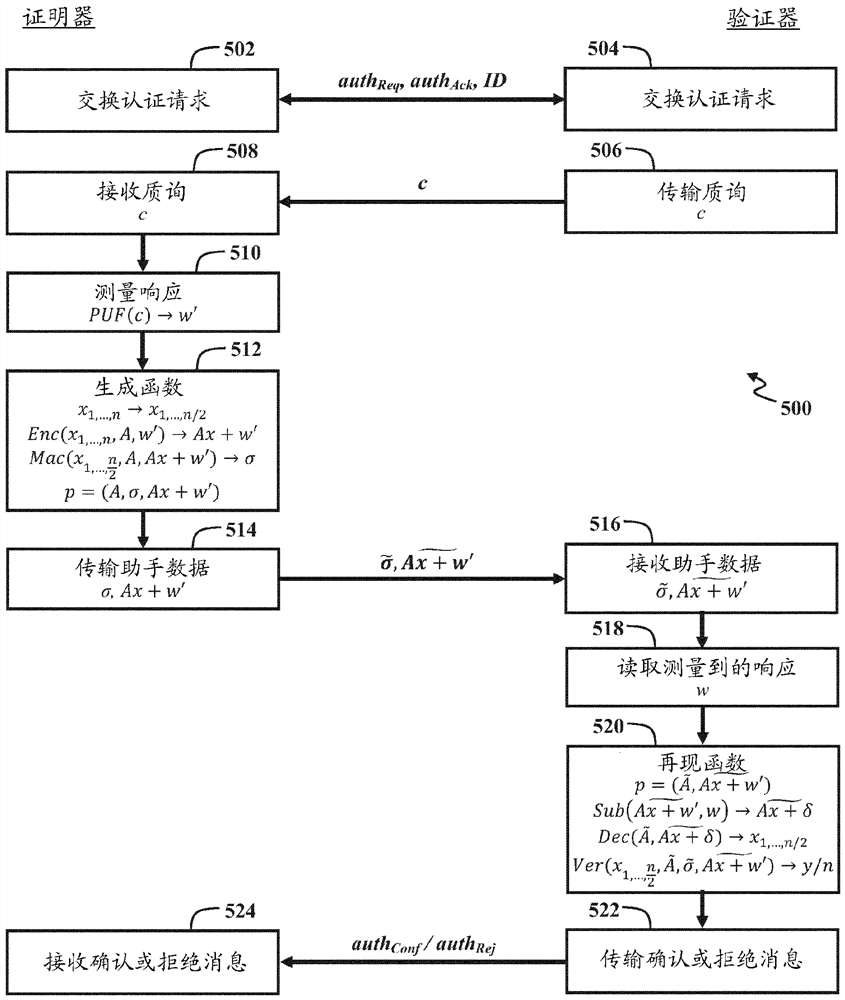
Methods and systems for authenticating a first device are disclosed. The method comprises the steps of measuring a first response bit string of a physical unclonable function of the first device with respect to a challenge bit string, the physical unclonable function being determined by a processor of the first device and a further physical component of the first device Provided by one of; derives a shared secret bitstring from a uniformly distributed random vector; encoded by multiplying a uniformly distributed random matrix with a uniformly distributed random vector and adding the first response bitstring to the result of the multiplication an auxiliary bit string; and transmitting the auxiliary bit string to a second device remote from the first device.
Owner:ROBERT BOSCH GMBH
Reverse computational fuzzy extractor and method for authentication
A method and system for authenticating a first device is disclosed. The method includes the steps of: measuring a first response bit string of a physical unclonable function of the first device with respect to a challenge bit string, the physical unclonable function being provided by one of the processor of the first device and a further physical component of the first device; deriving a shared secret bit string from a uniformly distributed random vector; encoding a helper bit string by multiplying a uniformly distributed random matrix with the uniformly distributed random vector and adding the first response bit string to a result of the multiplication; and transmitting the helper bit string to a second device that is remote from the first device.
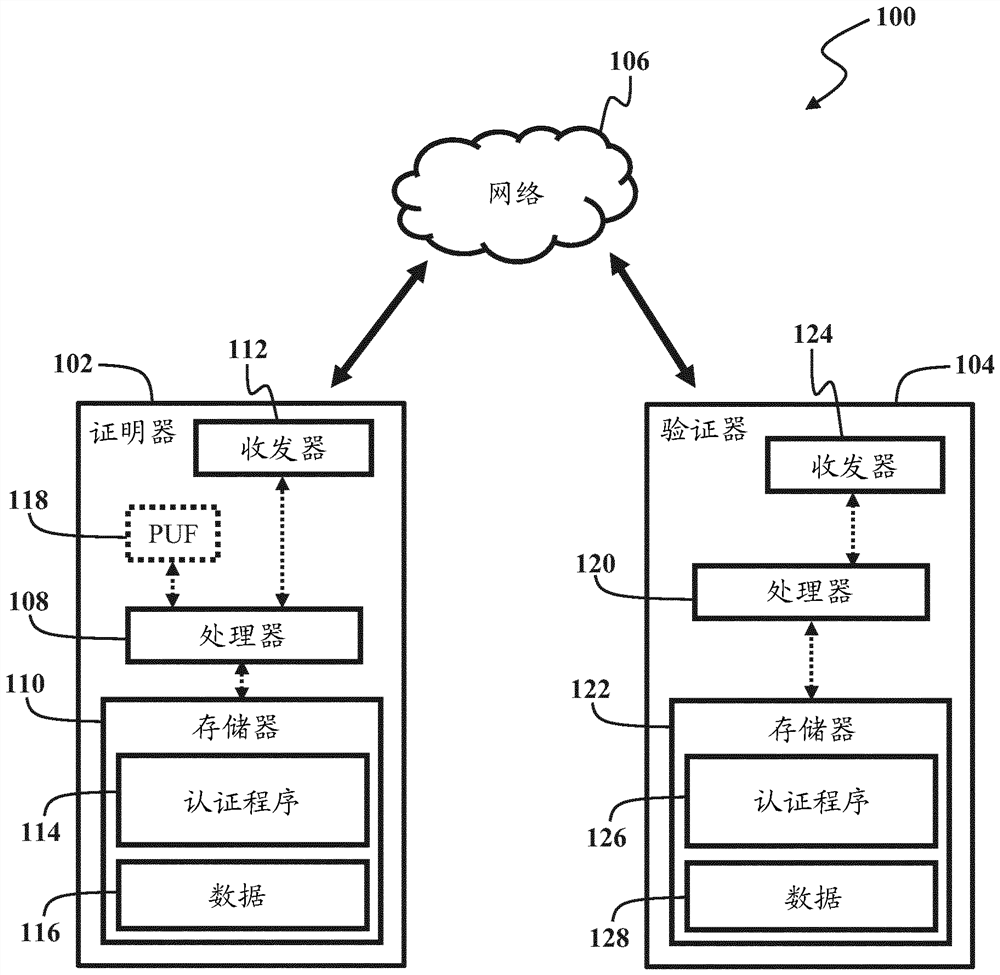
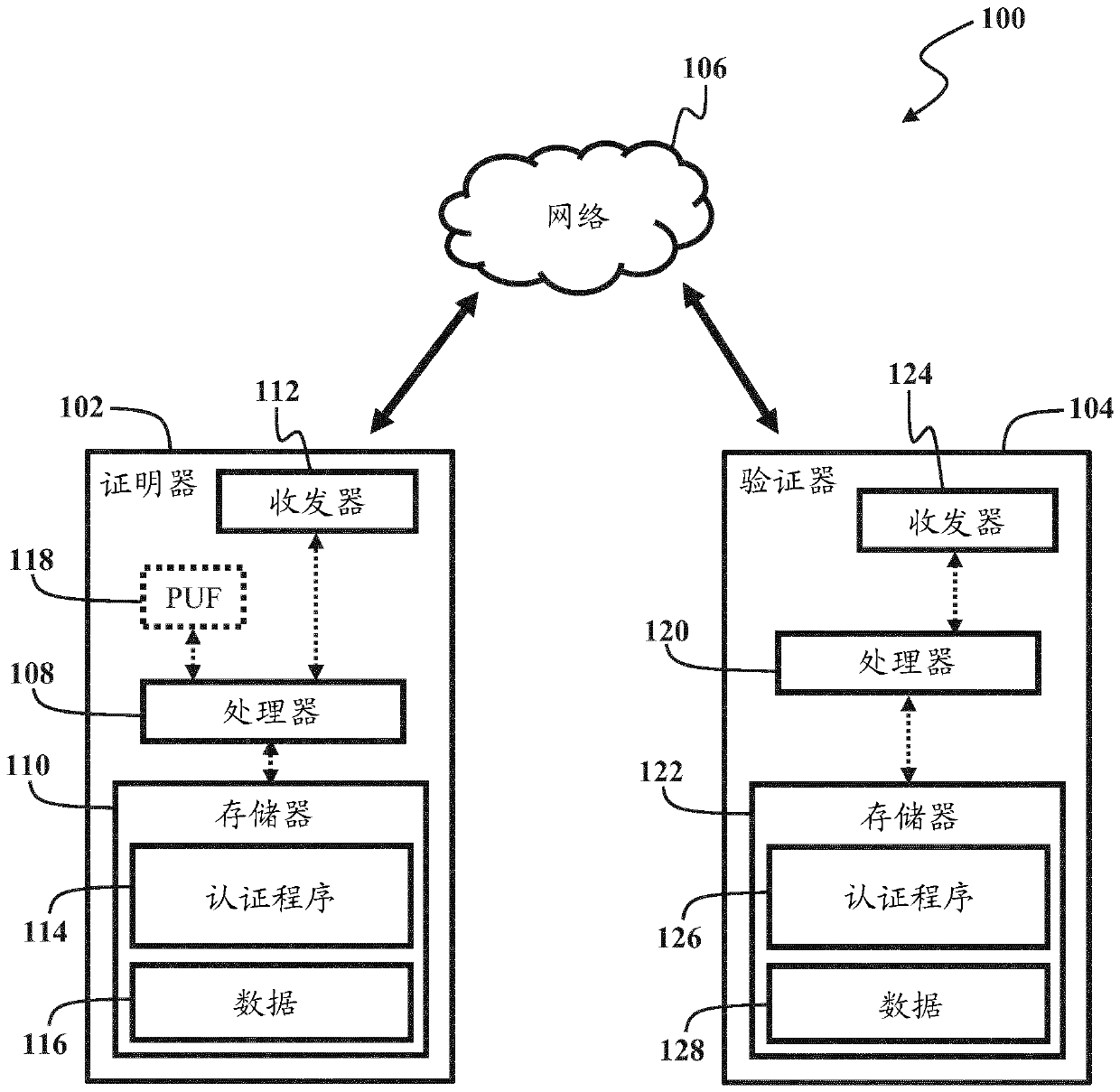
Owner:ROBERT BOSCH GMBH
Signcryption method of biological features of a plurality of receivers
InactiveCN102710613BOvercome the problem of forgeryPrevent leakageTransmissionDigital signatureSigncryption
The invention discloses a signcryption method of biological features of a plurality of receivers, comprising generating system parameters; extracting features; performing user log-on; encrypting by a sender; and decrypting by receivers. The method employs fuzzy extractor technique to bind the biological features and user keys to protect keys, directly authenticates user identity through the biological features, solves the safety problems of key safety and key abuse in the conventional cryptography, adds digital signature of senders during encryption, verifies identity of senders through certification during decryption, and solves the problem of counterfeiting of senders. The method improves the safety and reliability of whole systems, has the advantages of high safety, high efficiency and no need for storing any secret information by users, and can be applied to the distributed network application field.
Owner:XIDIAN UNIV
Robust computational fuzzy extractor and method for authentication
ActiveCN110100413BUser identity/authority verificationSecurity arrangementAlgorithmPhysical unclonable function
A method and system for authenticating a device is disclosed. The method includes the steps of: receiving a helper bit string and a first MAC; measuring a first response bit string of a physical unclonable function of the device with respect to a challenge bit string; subtracting the first response bit from the helper bit string string; decodes the result of the subtraction using a uniformly distributed random matrix, if the helper bit string is encoded using a previously measured second response bit string within a threshold level of similarity to the first response bit string , then providing the shared secret bit string from the decoding, otherwise the decoding outputs an error value; determining a second MAC based on the shared secret bit string, the uniformly distributed random matrix, and the helper bit string; and It is determined whether the second MAC matches the first MAC.
Owner:ROBERT BOSCH GMBH
A New Method of Fingerprint Key Generation for Digital Signature
InactiveCN106059753BImprove securityAvoid safety hazardsKey distribution for secure communicationFeature extractionDigital signature
The invention relates to a novel fingerprint key generation method for a digital signature, which comprises two stages and is characterized in that the first stage is fingerprint feature extraction which comprises the steps of calculating a directional diagram of a fingerprint image, positioning a reference point of the fingerprint image, calculating a sector fingerprint feature extraction region, carrying out fingerprint image normalization, performing enhancement processing on the fingerprint image, and extracting fingerprint features; and the second stage refers to fuzzy extraction technology based fingerprint key generation which comprises the steps of constructing a security model based fuzzy extractor, constructing a Hamming distance based fuzzy extractor and generating a fingerprint key. The novel fingerprint key generation method has the advantages that the fingerprint key can be cancelled or updated for multiple times, the security is enabled to be higher, and potential safety hazards brought about by external information stealing can be avoided. Meanwhile, the novel fingerprint key generation method has important theoretical and practical values, and has wide application prospects.
Owner:XIJING UNIV
Wireless biometric authentication system and method
ActiveUS11303435B2Key distribution for secure communicationCryptography processingComputer networkEngineering
Embodiments of the invention involve using biometric templates to wirelessly authenticate individuals. In one embodiment, a mobile device may generate a first biometric template and a first public value from a first biometric sample of a user and generate a first cryptographic key by passing the first biometric template to a fuzzy extractors generate function. An access device may generate a second biometric template from a second biometric sample of the user, generate a second secret cryptographic key by passing the second biometric template and the first public value to the fuzzy extractors reproduce function, encrypt the second biometric template with the second secret cryptographic key, and broadcast the encrypted template to a plurality of nearby mobile devices including the mobile device. If the mobile device is able to decrypt the encrypted template with the first cryptographic key, the access device can associate the user with the mobile device.
Owner:VISA INT SERVICE ASSOC
Method and Apparatus using Blended Biometric Data
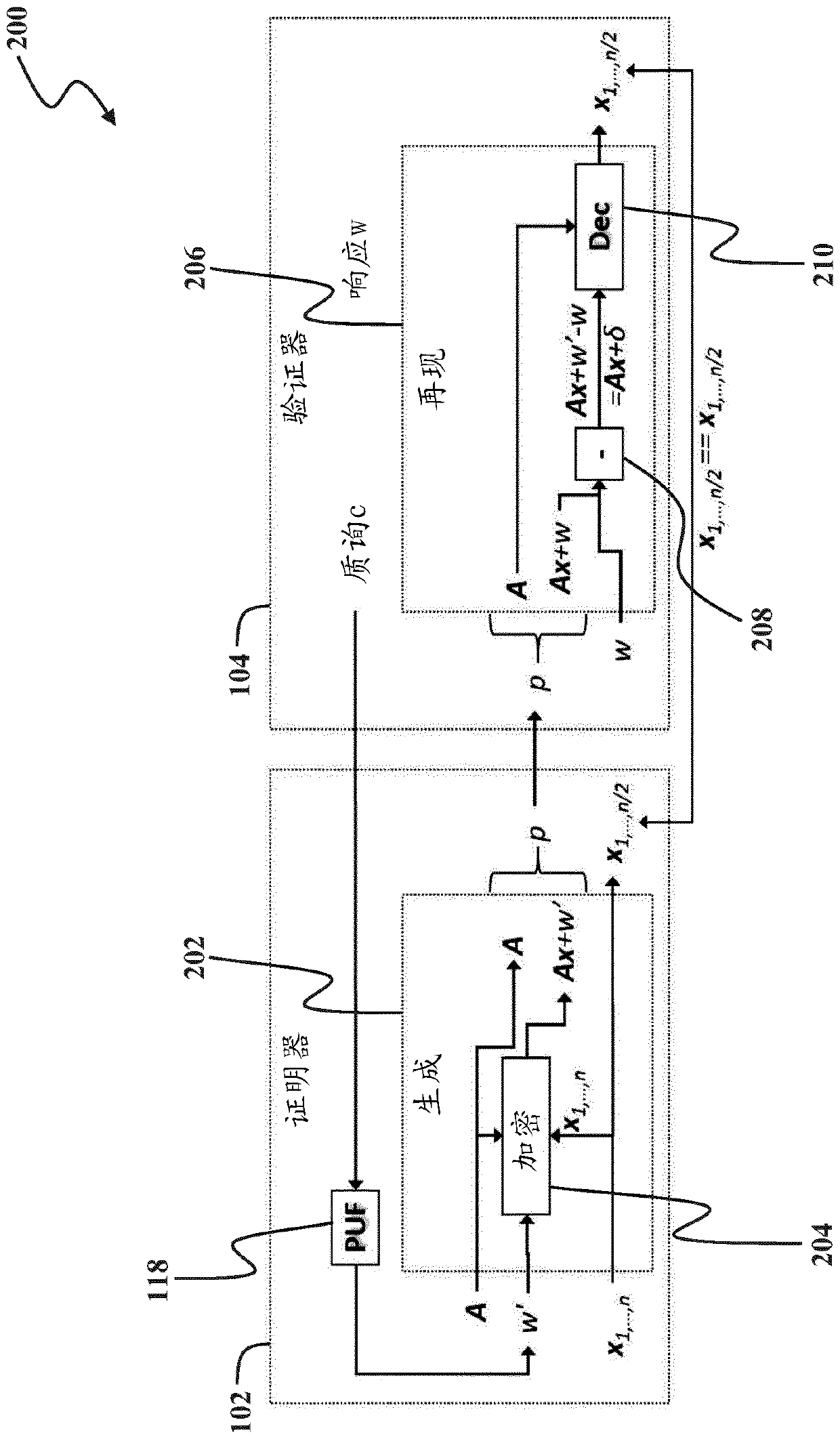
PendingUS20220261463A1Improve securityReduce interruptionsDigital data authenticationMachine learningBiometric dataEngineering
A biometric processing system for authentication combines multiple biometric signals using machine learning to map the different signals into a common argument space that may be processed by a similar fuzzy extractor. The different biometric signals may be given weight values related to their entropy allowing them to be blended to increase security and availability while minimizing intrusiveness.
Owner:WISCONSIN ALUMNI RES FOUND
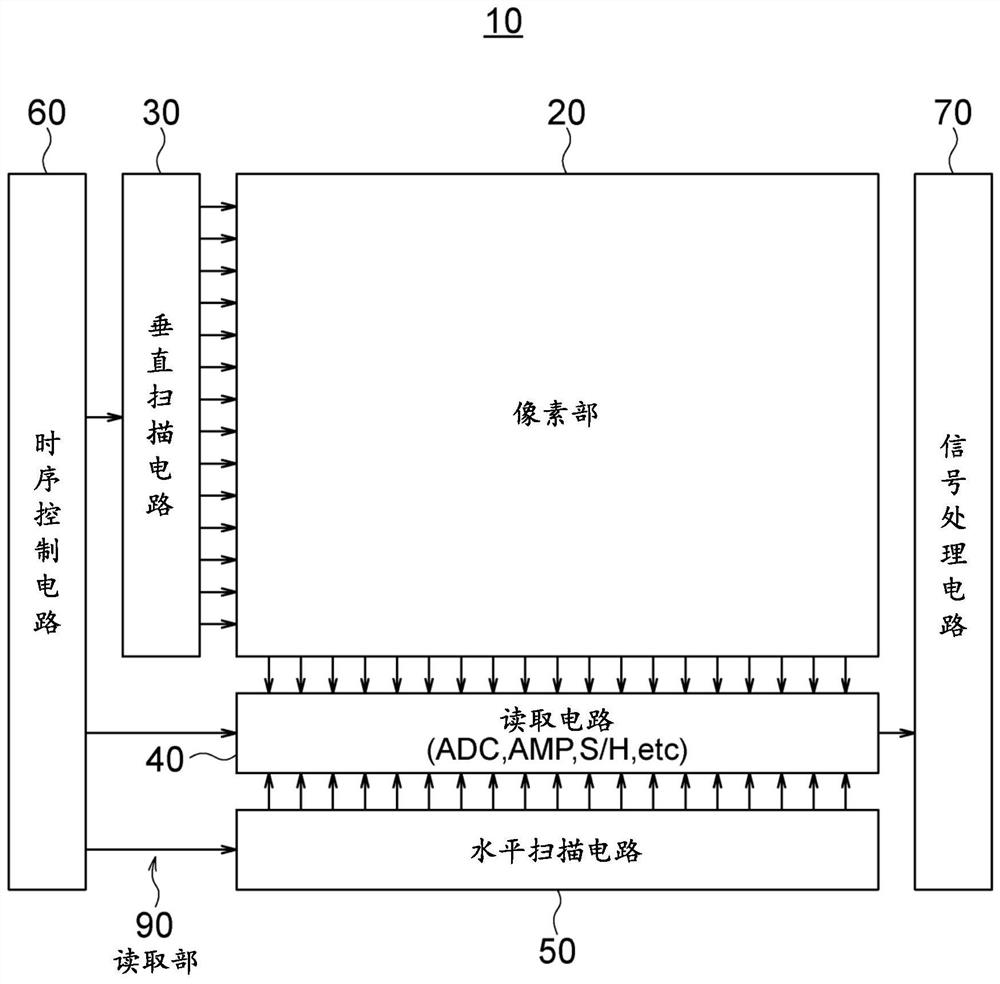
Solid-state image pickup device, solid-state image pickup device driving method, and electronic apparatus
ActiveCN111630845APrevent tamperingPrevent fabricationTelevision system detailsSolid-state devicesFuzzy extractorData storing
A solid-state image pickup device 10 comprises: a pixel unit 20; a read unit 90 that reads pixel signals from the pixel unit 20; and a response data generation unit 80 that includes a fuzzy extractorand that generates response-data containing a unique key associated with pixels and / or read unit variation-information. When regenerating a key, the response data generation unit 10 generates a uniquekey using: helper data obtained when initially generating the key; variation information obtained when regenerating the key; and reliability information predicted from the variation information whenregenerating the key. Due to this configuration: it is not necessary to perform multiple instances of counting a response for obtaining reliability information, nor is it necessary to impart reliability to helper data; it is possible to prevent an increase in the data stored in the fuzzy extractor when initially generating a key; and it is possible to generate unique response-data that has high confidentiality.
Owner:BRILLNICS JAPAN +1
Solid-state imaging device, method for driving solid-state imaging device, and electronic apparatus
ActiveUS11336857B2Reliably preventedIncrease randomnessTelevision system detailsKey distribution for secure communicationFuzzy extractorNumber generator
A fuzzy extractor includes an initial key generating part including a true random number generator, and a key regenerating part. The true random number generator generates a true random number using a read-out signal read from the reading part or a pixel signal read from the pixels of the pixel part in a true random number generation mode. The initial key generating part generates helper data and an initial key based on the true random number generated by the true random number generator and variation information acquired as a response when the initial key is generated. The key regenerating part generates, when a key is regenerated, a unique key based on helper data acquired when the initial key is generated and variation information acquired as a response including an error when the key is regenerated.
Owner:BRILLNICS JAPAN +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com