Use of biometrics and privacy preserving methods to authenticate account holders online
A biometric, user technology, applied in user identity/authority verification, digital transmission systems, secure communication devices, etc., can solve the problems of easy password theft and users' inability to change biometric identification information.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
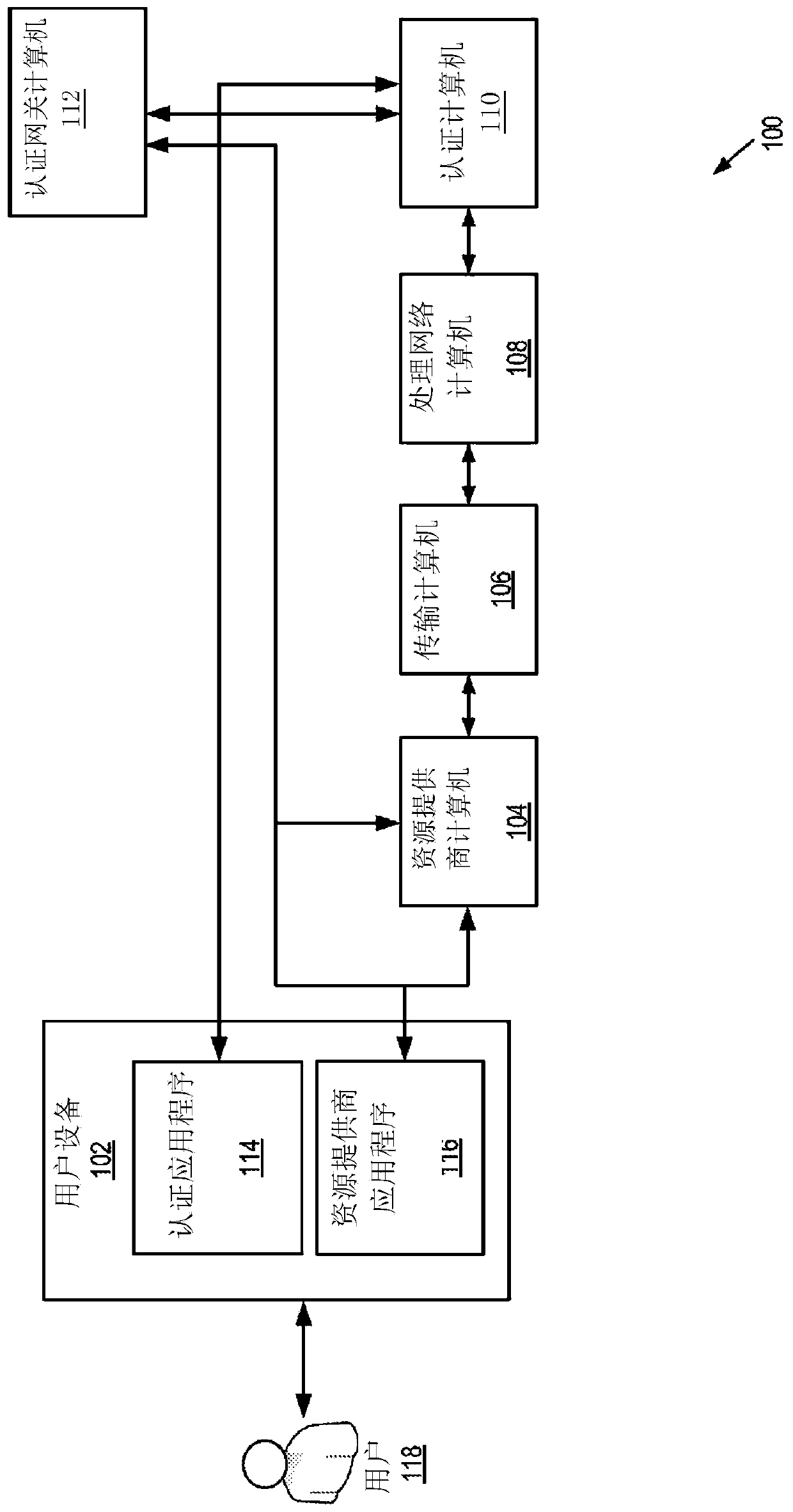
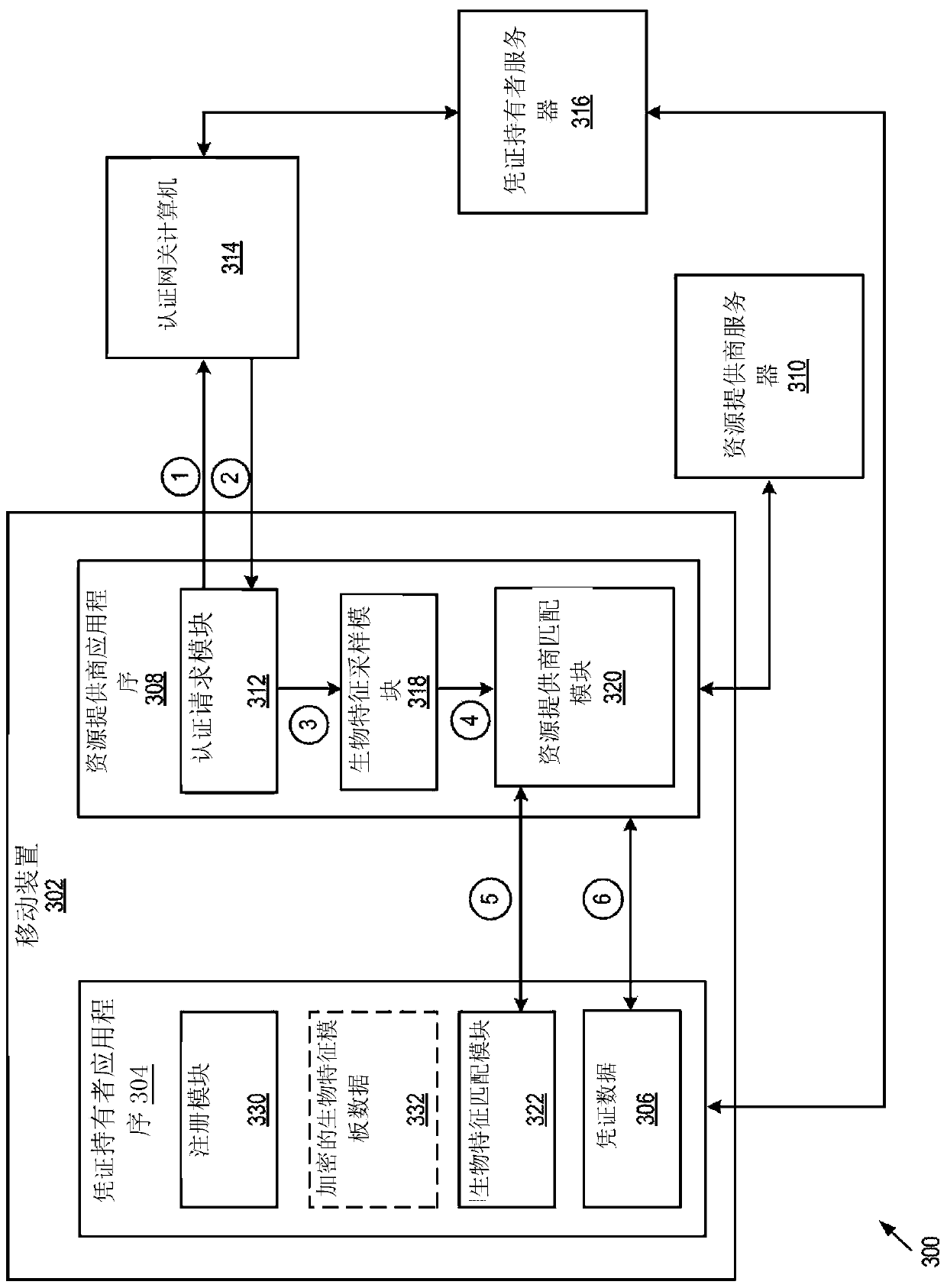
[0030] Embodiments relate to a method for securely performing biometric authentication online. The described method can be used to securely perform biometric authentication on a user's device (eg, a mobile device). To protect the privacy of the user's biometric data, a cryptographic comparison protocol may be used to perform matching of encrypted and / or unencrypted biometric templates. For example, the cryptographic comparison protocol may involve Fuzzy Extractor (FE), Homomorphic Encryption (HE), and / or Secure Multi-Party Computation (SMPC).
[0031] One use case may involve a user having one or more wallet applications on his or her mobile phone and being enrolled in a biometric authentication program. For example, an authentication program could be a service offered to conduct transactions using facial data (e.g., by using a front-facing camera to generate a selfie or “selfie”) or other biometric data (e.g., fingerprints, retinal scans, etc.). The user can then use a reso...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com