Robust computational fuzzy extractor and method for authentication
A technology for device authentication and message authentication code, applied in the field of cryptography, which can solve problems such as insufficient security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0013] For the purpose of promoting an understanding of the principles of the present disclosure, reference will now be made to the embodiments illustrated in the drawings and described in the following written specification. It should be understood that no limitation of the scope of the present disclosure is therefore intended. It is further to be understood that this disclosure includes any alterations and modifications to the illustrated embodiments and includes further applications of the principles of this disclosure, as will commonly occur to those skilled in the art to which this disclosure pertains.
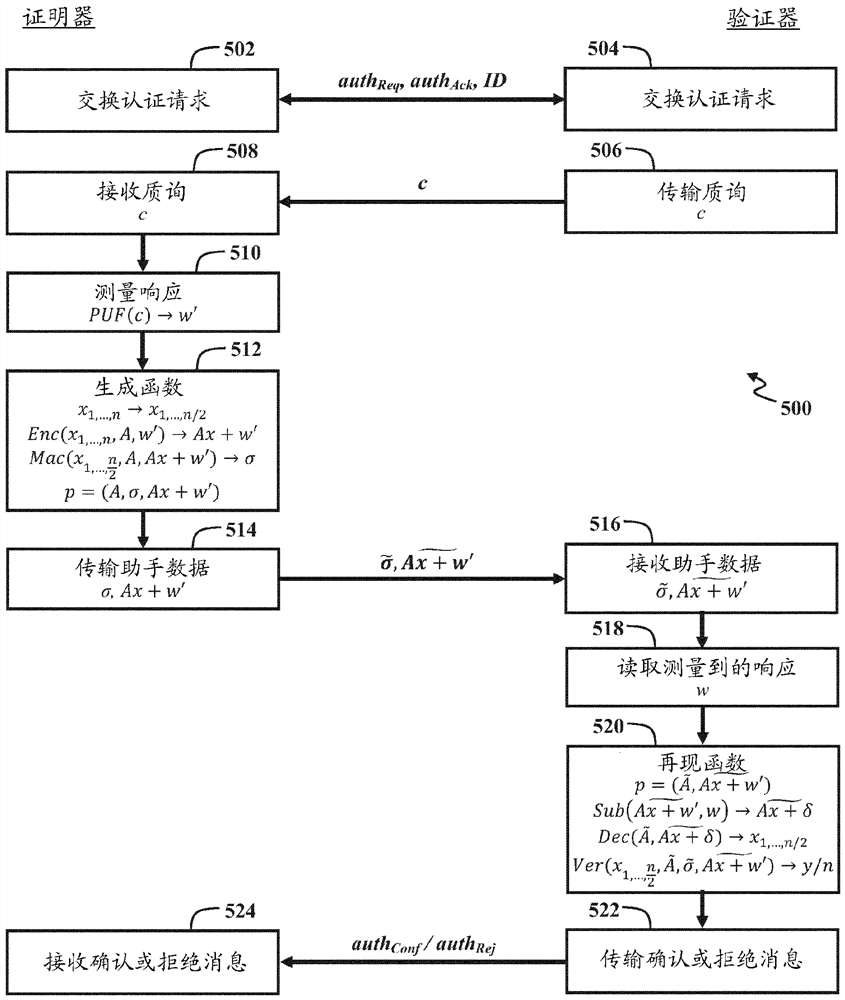
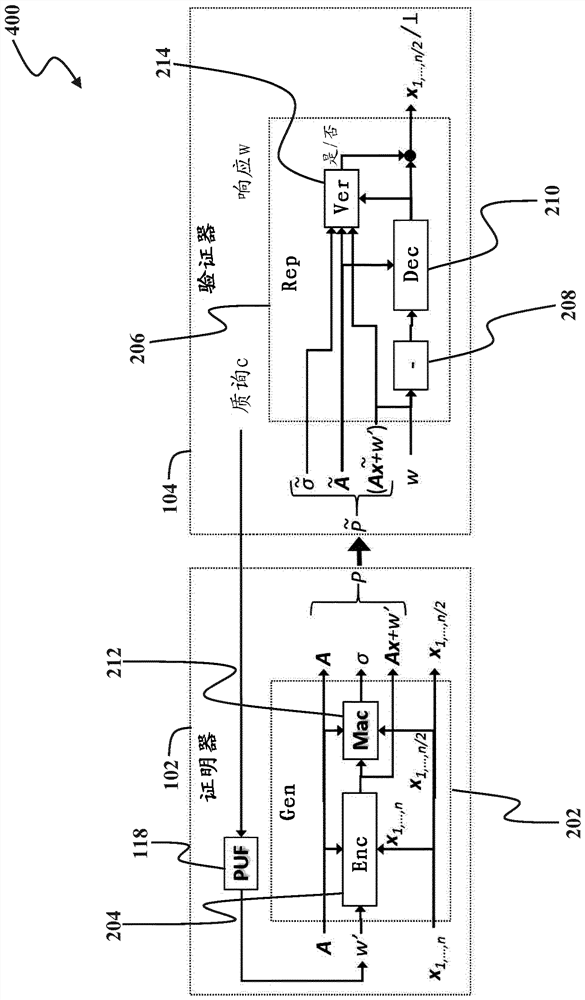
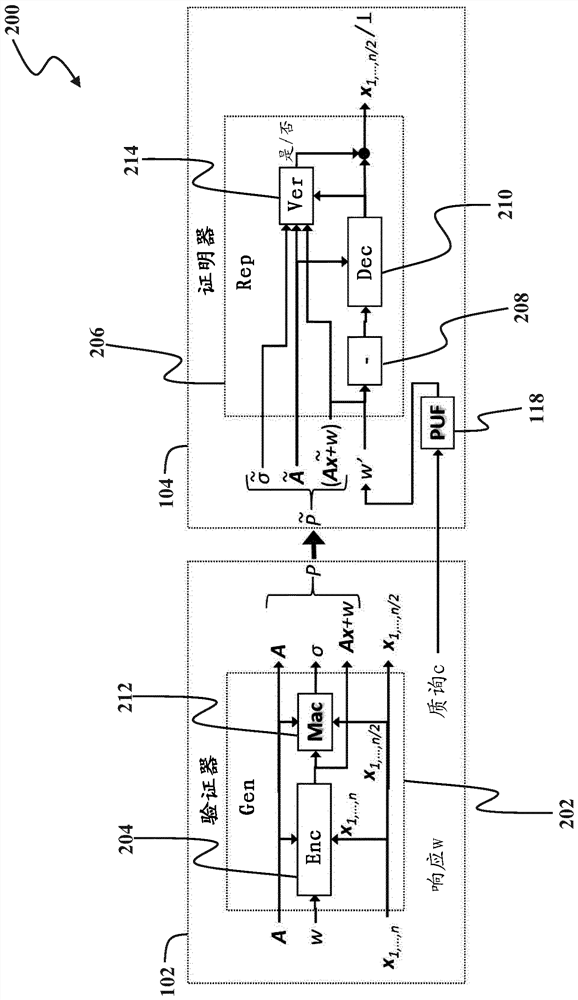
[0014] figure 1 A system 100 is shown that includes a proving device 102 (also referred to herein as a "certifier") and a verification device 104 (also referred to herein as a "verifier"). Attestation device 102 and verification device 104 via insecure communication channels such as network 106 (eg, the Internet, wireless local area network, or wireless mesh network) or ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com