Protecting secure software in a multi-security-CPU system
A computing system, secure boot technology, applied in the field of system security, can solve problems such as inaccessibility
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
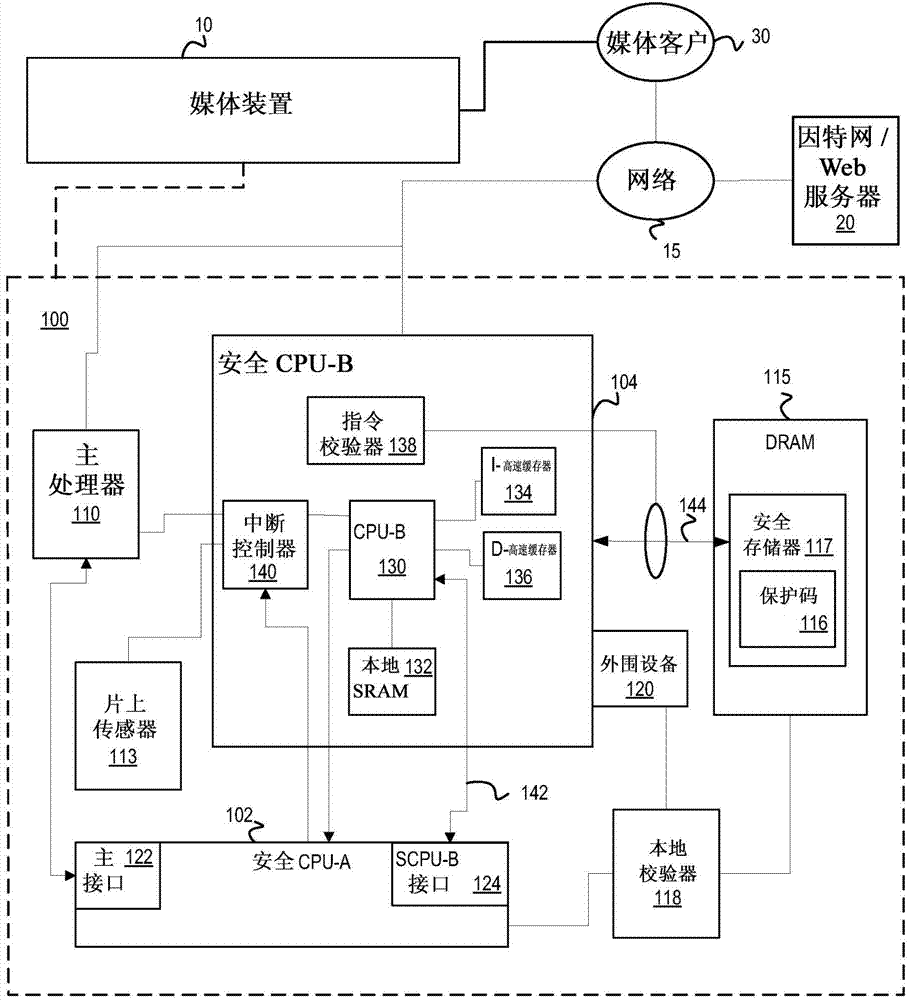
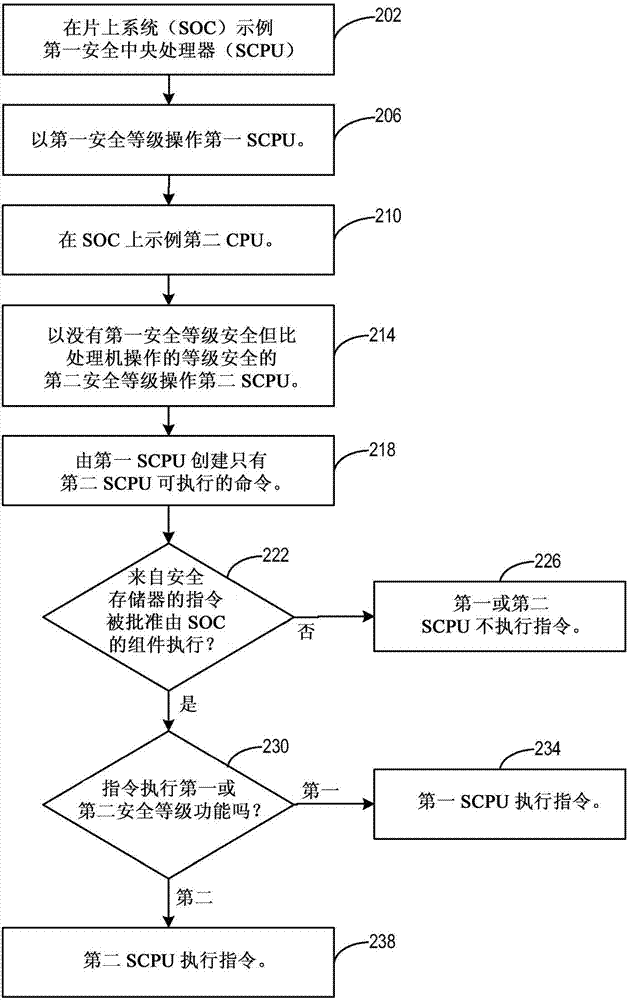
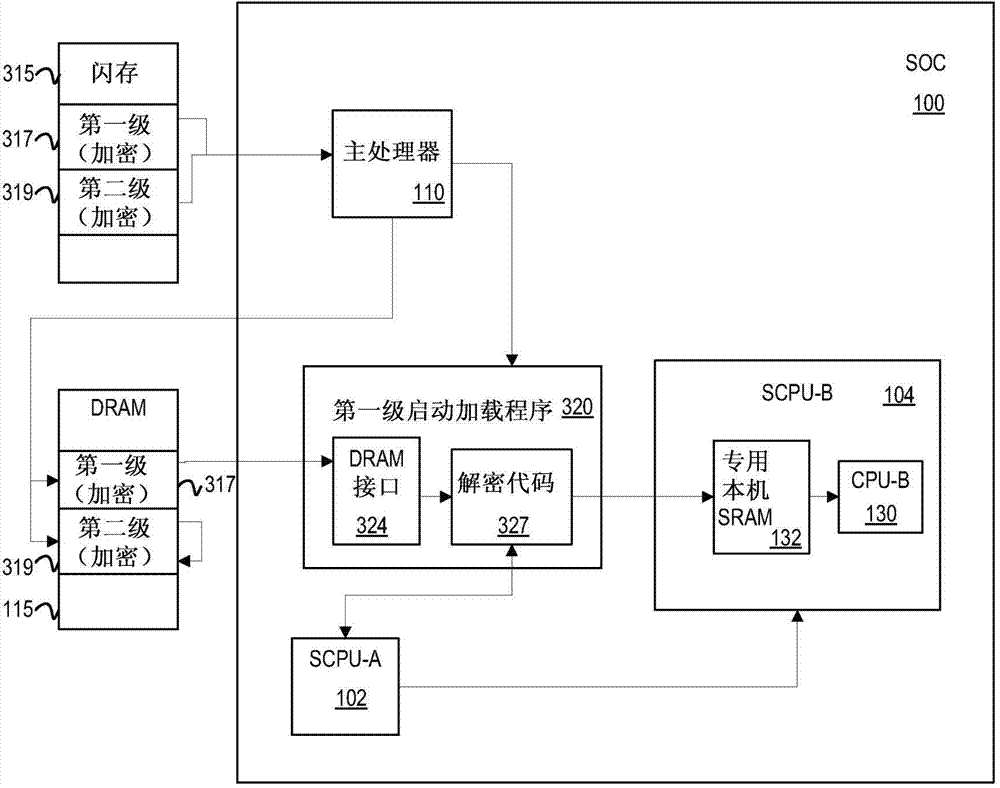
[0034]The following discussion relates to system security performed by a secure central processing unit (SCPU), and more specifically to security functions performed in a system by multiple SCPPUs operating at different security levels. For purposes of illustration, two SCPPUs are described, but more SCPPUs may be implemented. An SCPU such as may be used as an example on a system-on-chip (SOC), such as may be used to stream media into a consumer's set-top box (STB). Such media may include audio / video content viewable by consumers on media devices.
[0035] In a large system-on-chip with a single secure central processing unit (SCPU) performing security functions, the system trust level can be binary: operations are highly secure or completely untrusted. For operations requiring a moderate level of security, two options exist: (1) perform these operations in the SCPU; or (2) perform these operations in the host.
[0036] The first option may not be ideal since the SCPU can be...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com