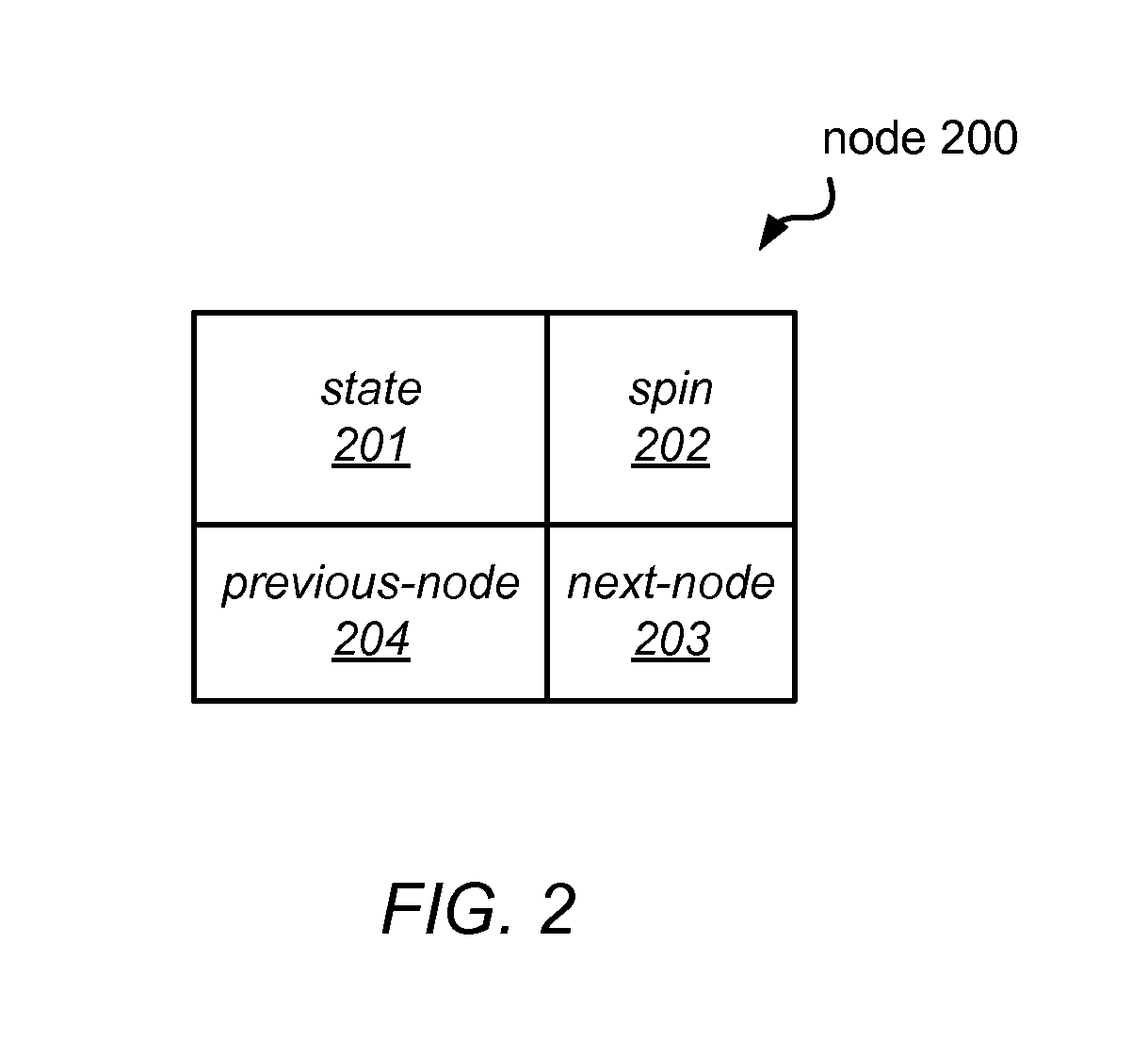
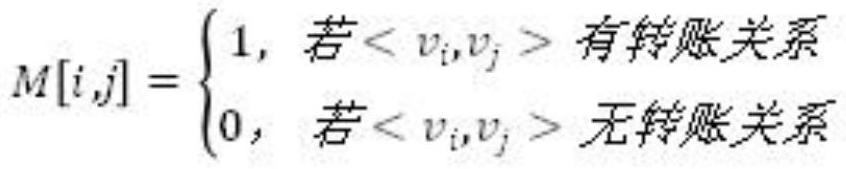Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
49 results about "Readers–writer lock" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
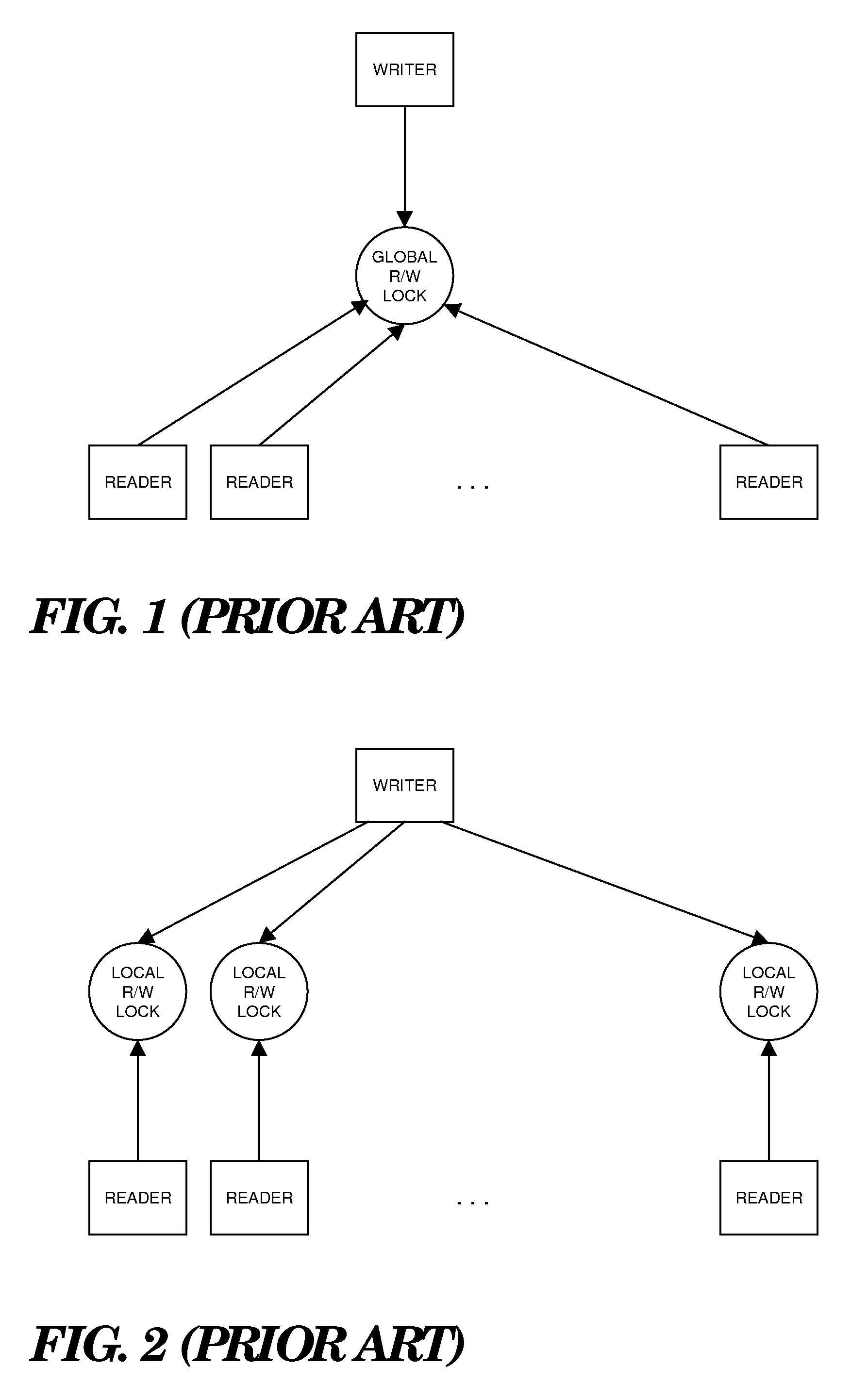
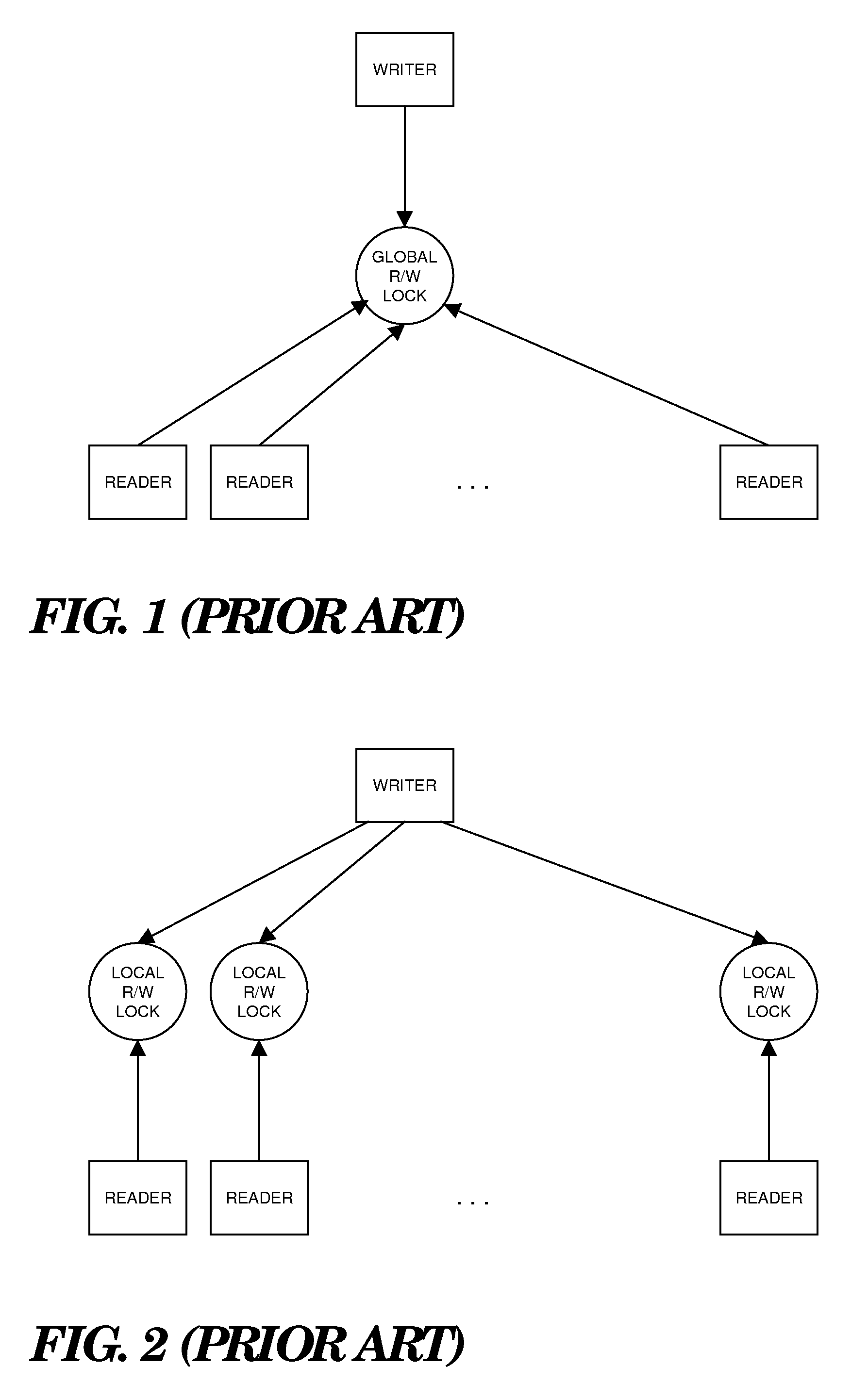
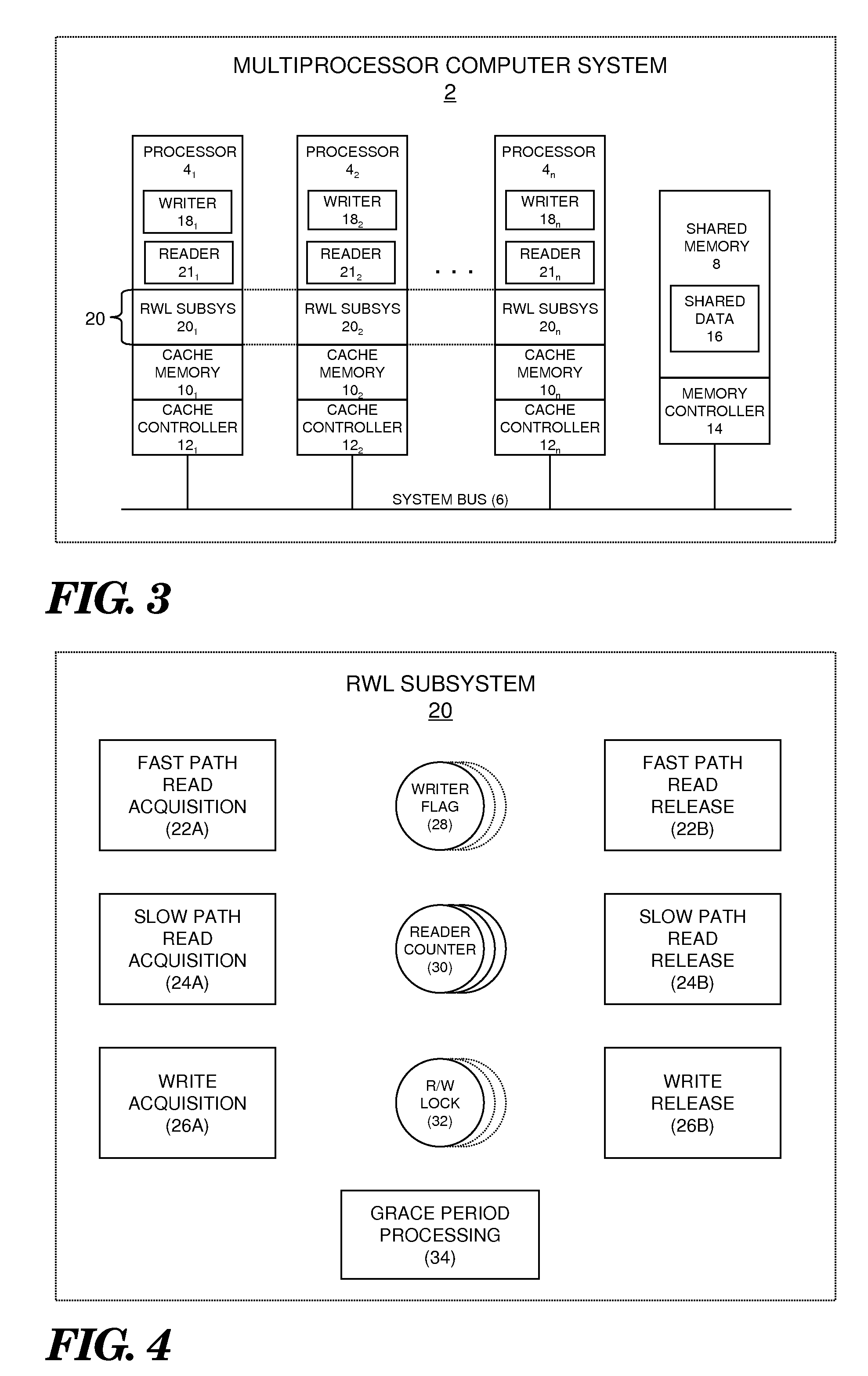
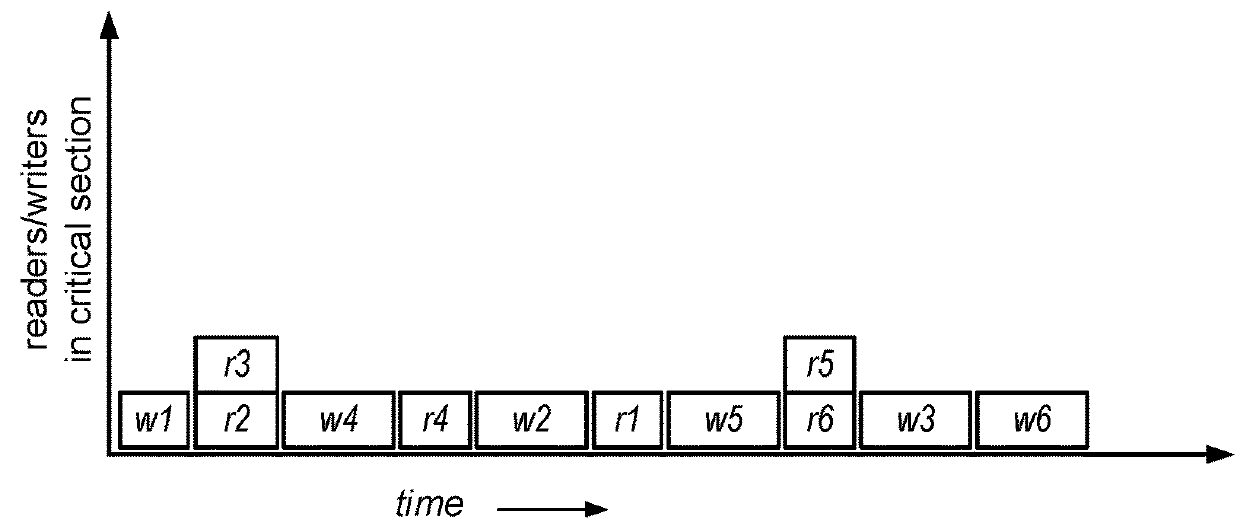
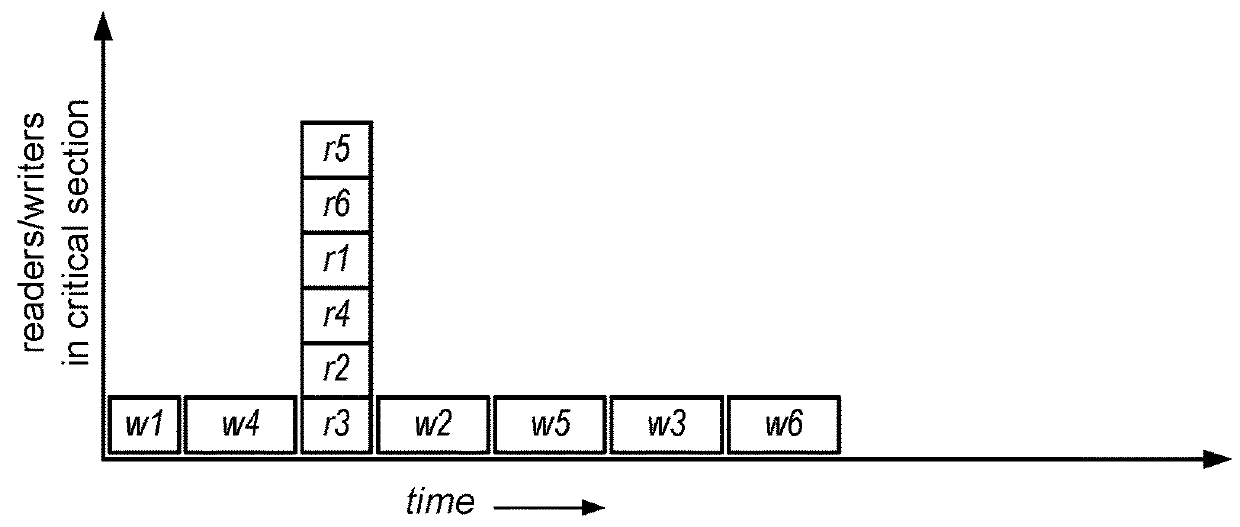
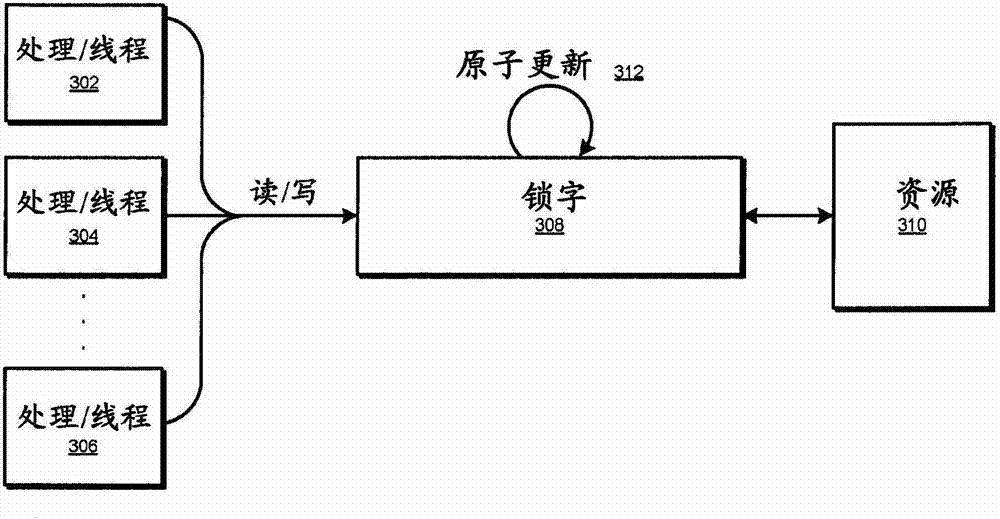
In computer science, a readers–writer (single-writer lock, a multi-reader lock, a push lock, or an MRSW lock) is a synchronization primitive that solves one of the readers–writers problems. An RW lock allows concurrent access for read-only operations, while write operations require exclusive access. This means that multiple threads can read the data in parallel but an exclusive lock is needed for writing or modifying data. When a writer is writing the data, all other writers or readers will be blocked until the writer is finished writing. A common use might be to control access to a data structure in memory that cannot be updated atomically and is invalid (and should not be read by another thread) until the update is complete.
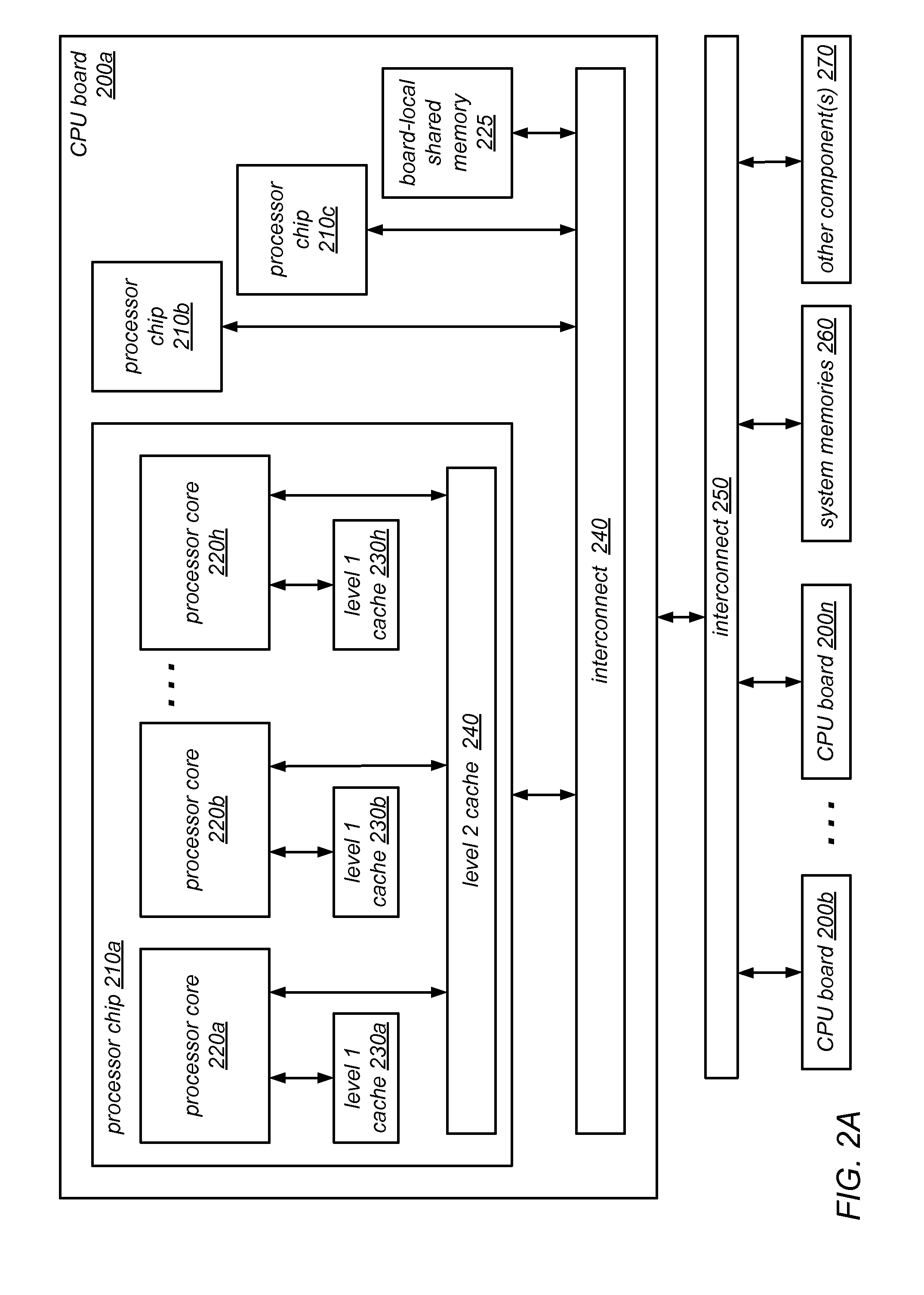
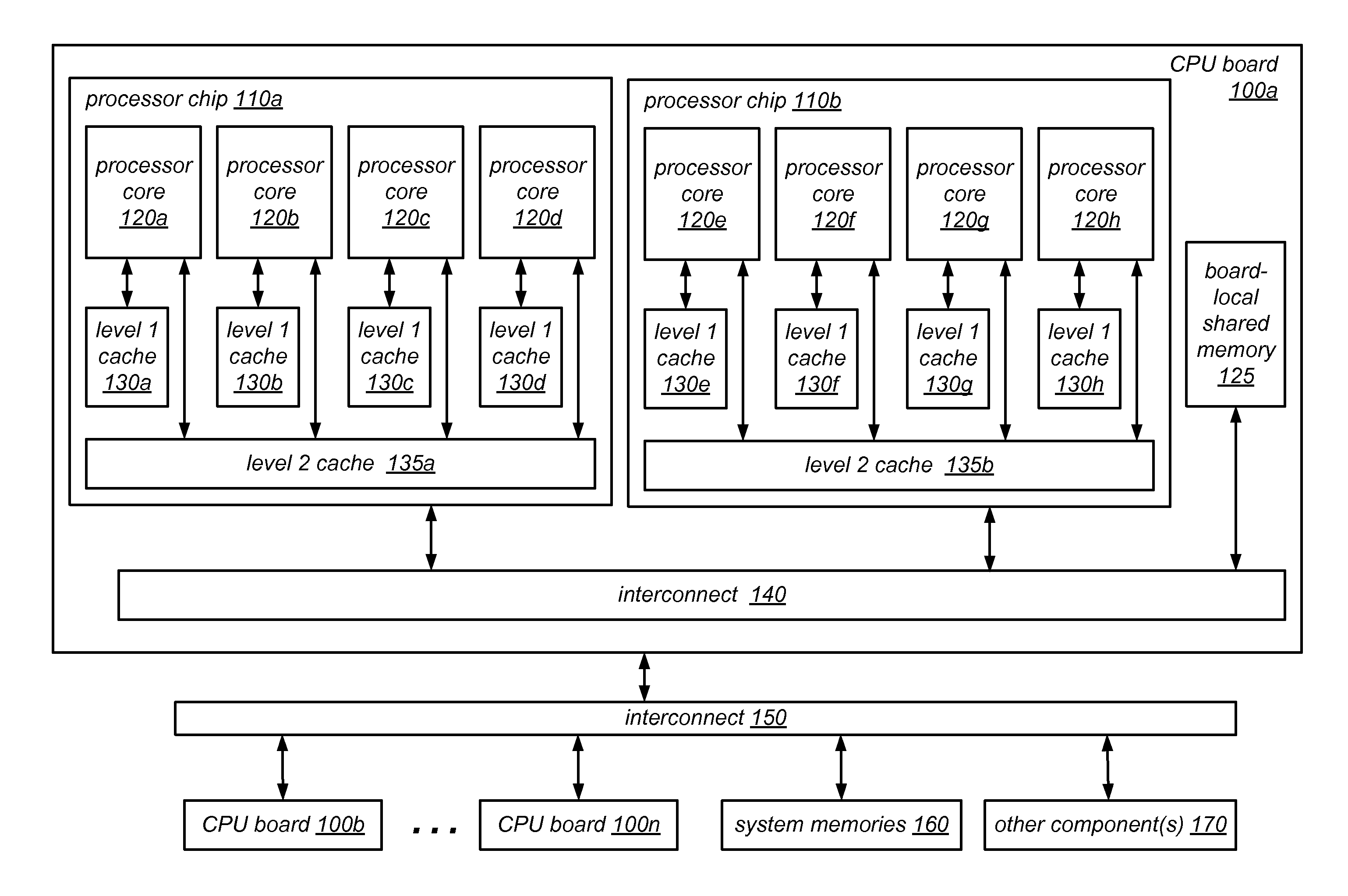
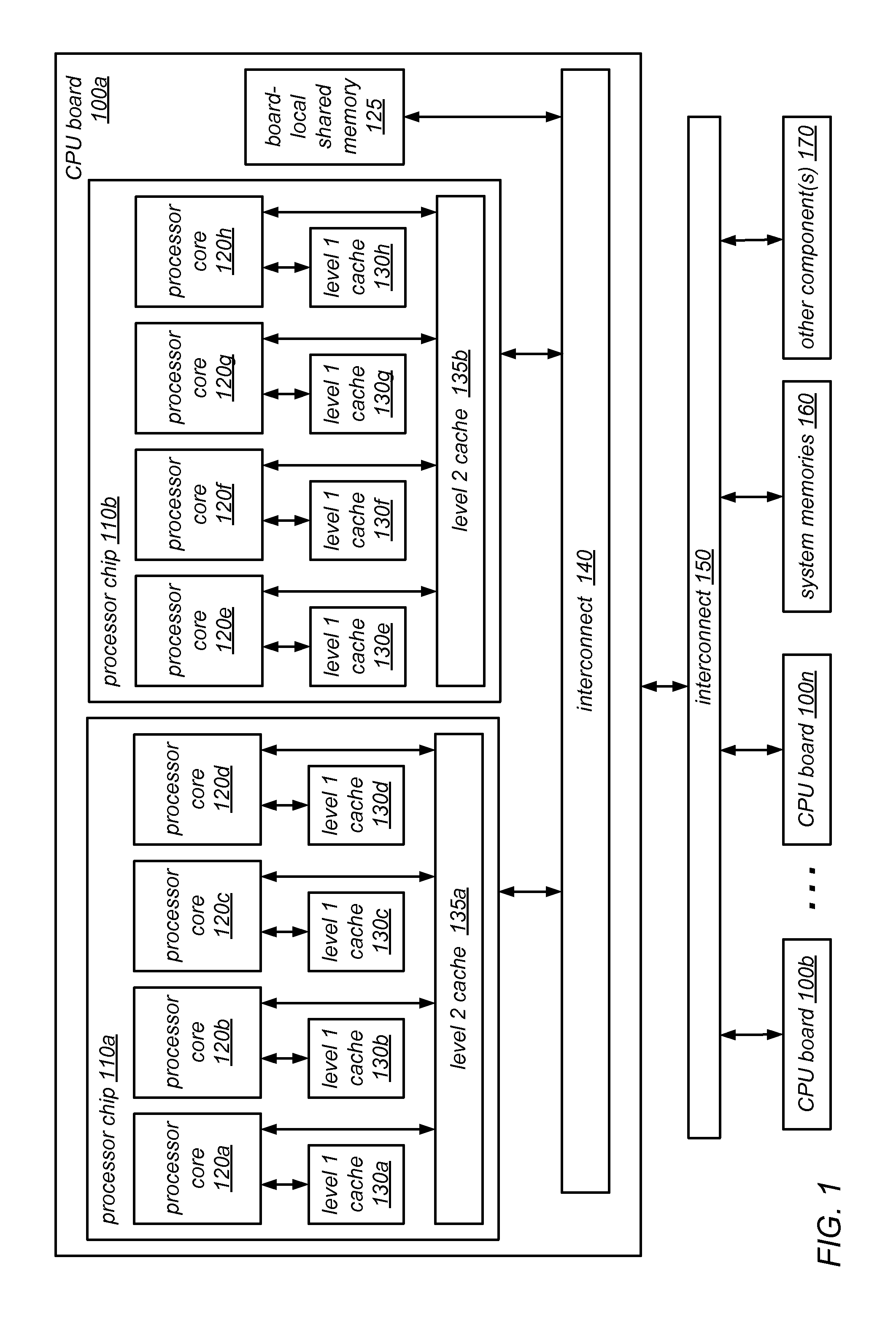
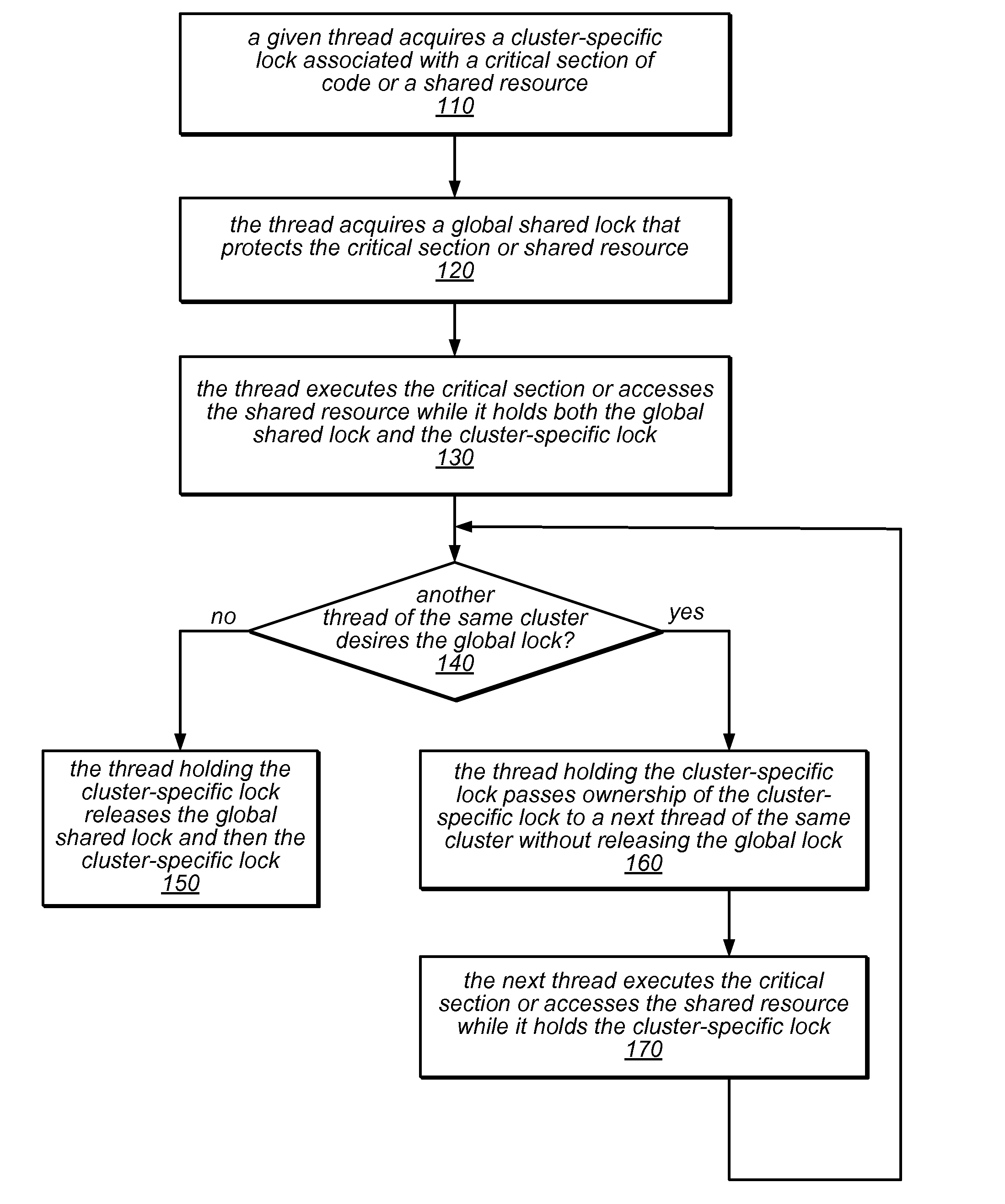
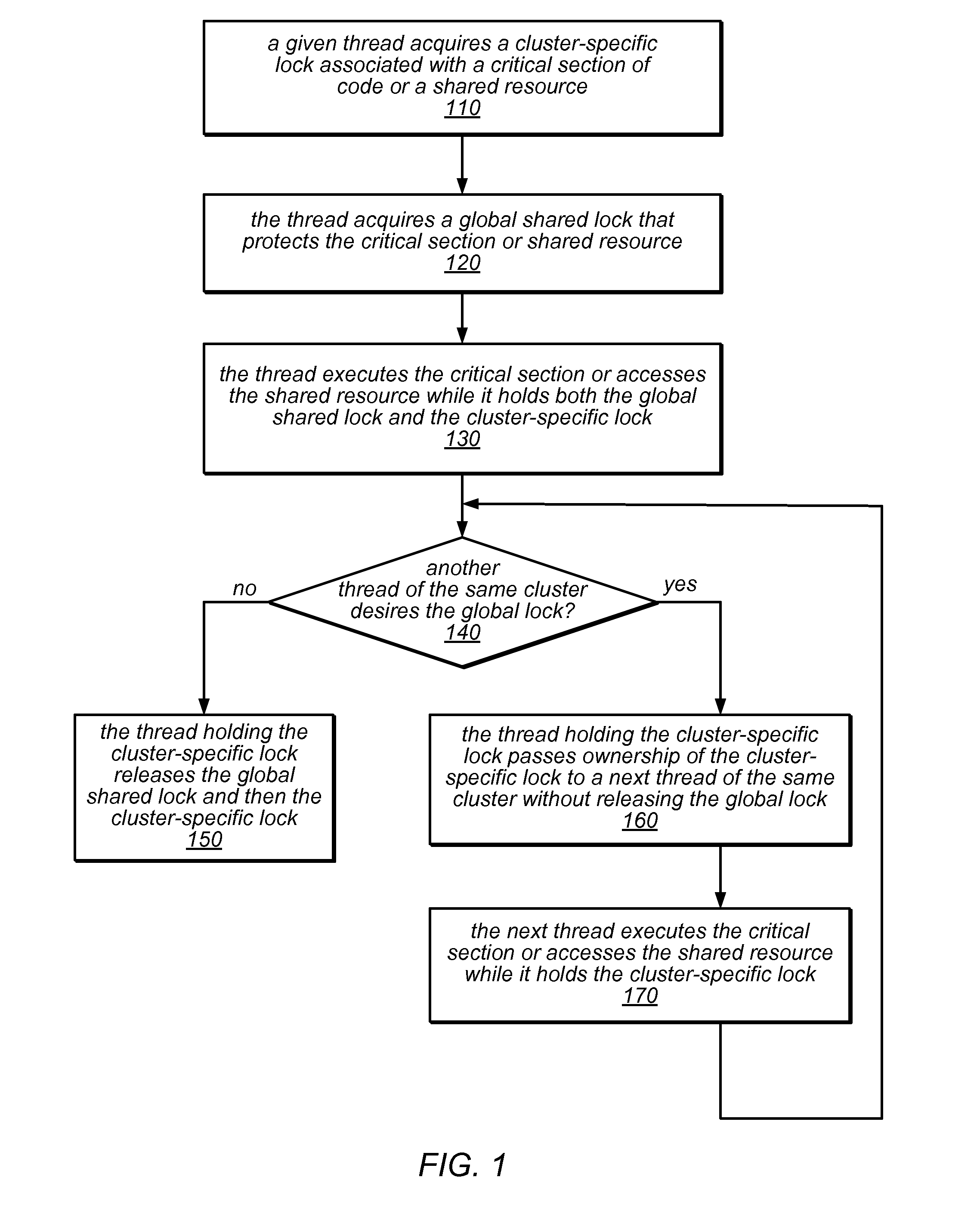
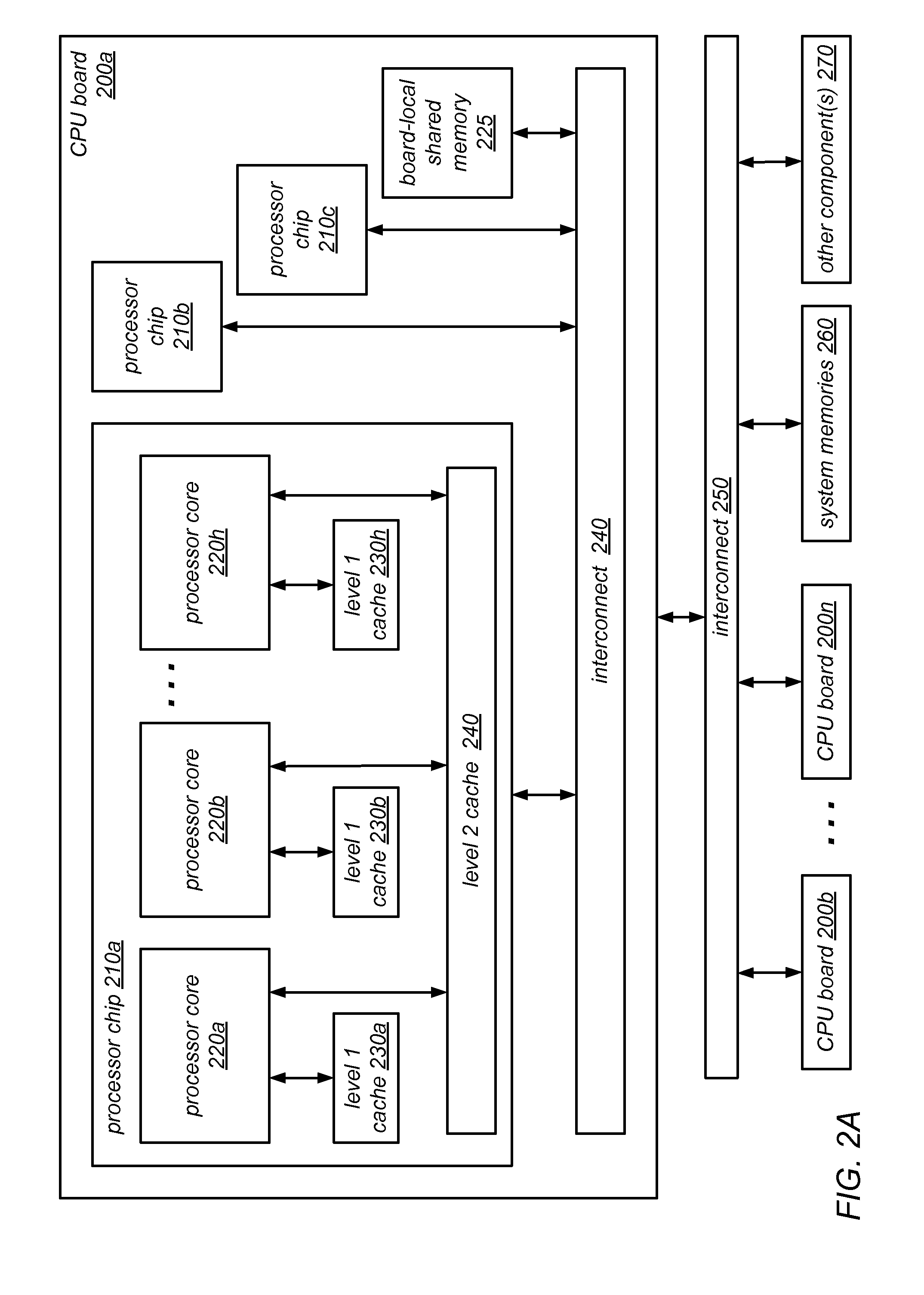
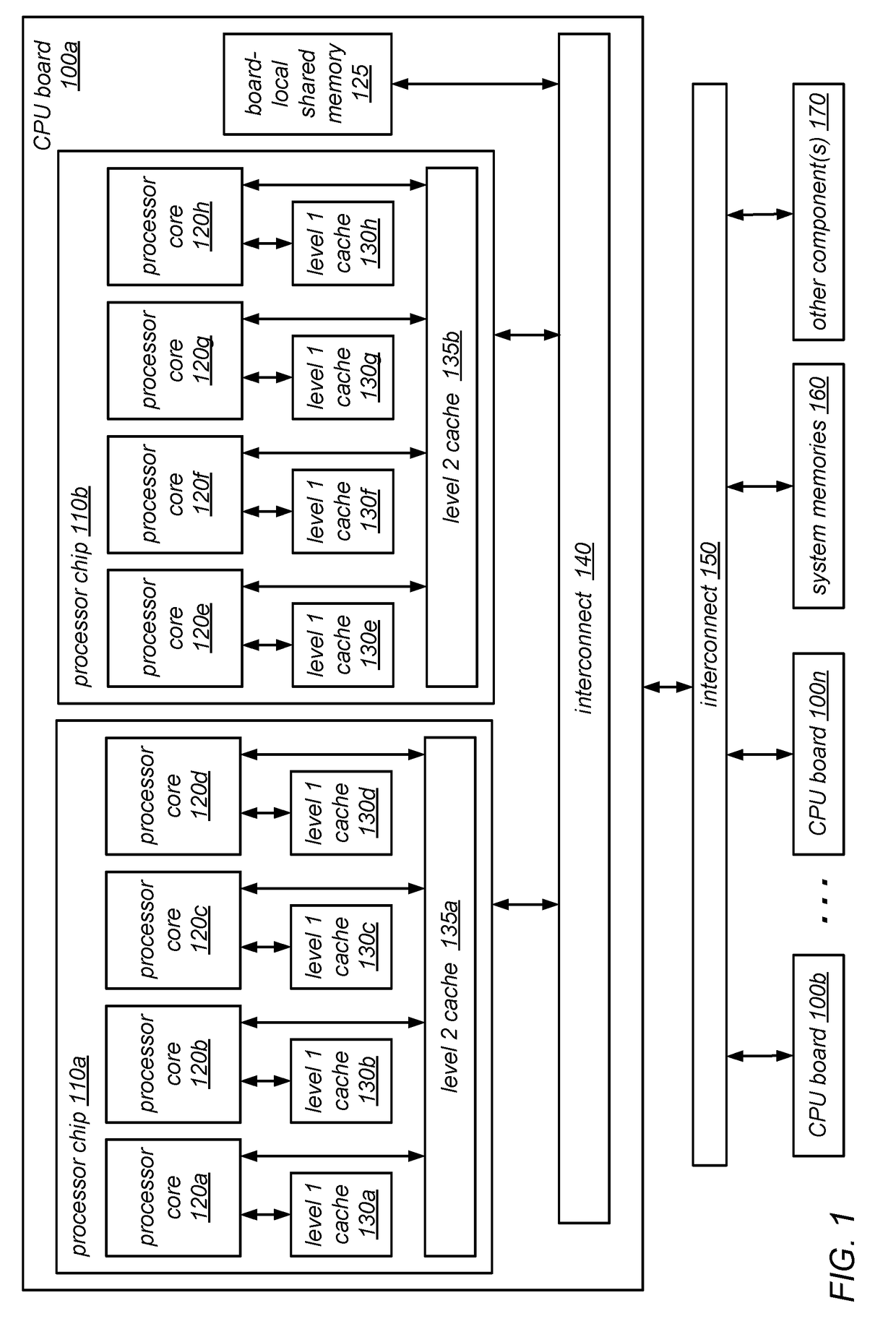
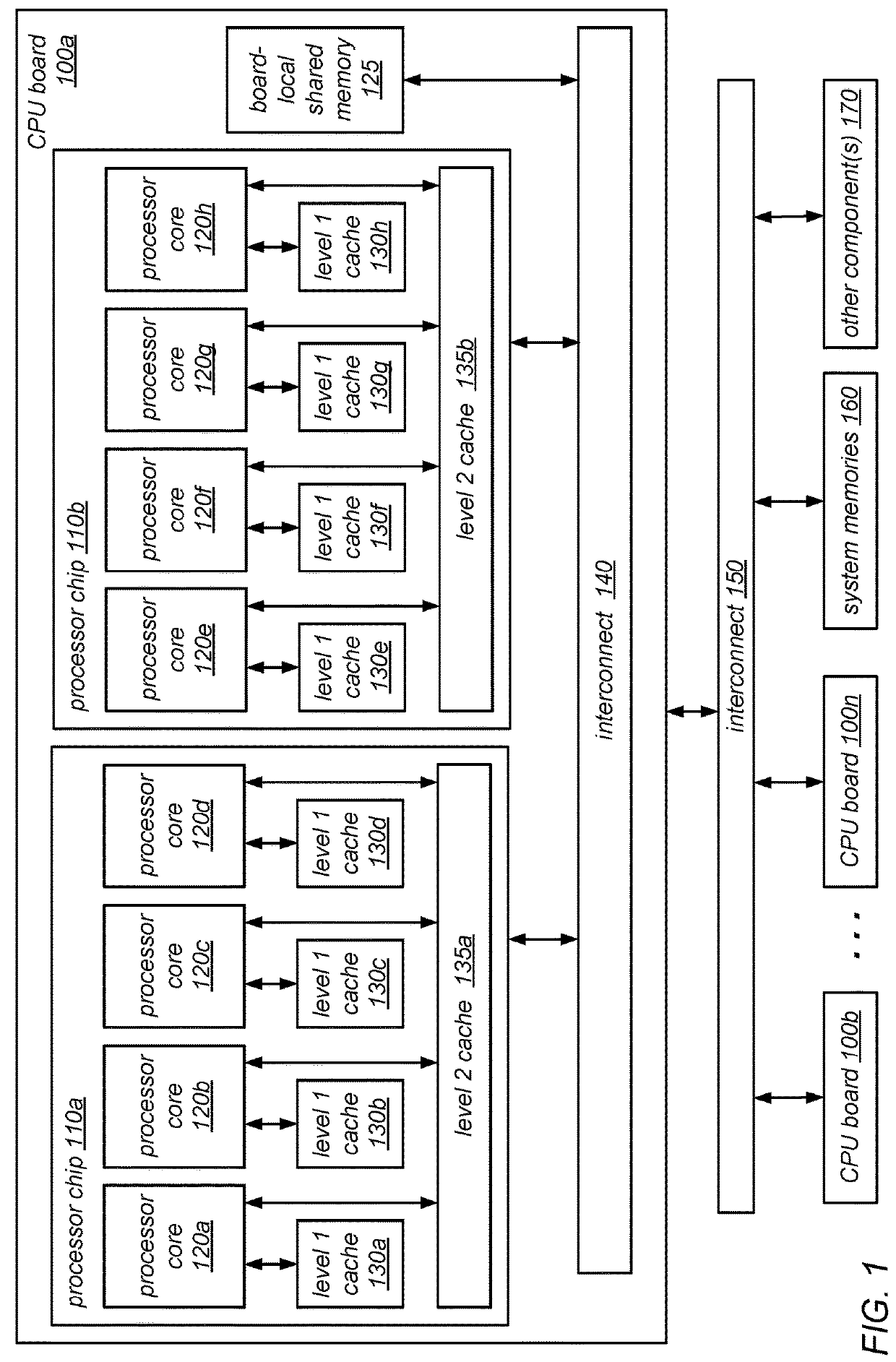
System and Method for Implementing NUMA-Aware Reader-Writer Locks
ActiveUS20130290967A1Reduce probabilityReduce traffic problemsMultiprogramming arrangementsMemory systemsCritical sectionParallel computing
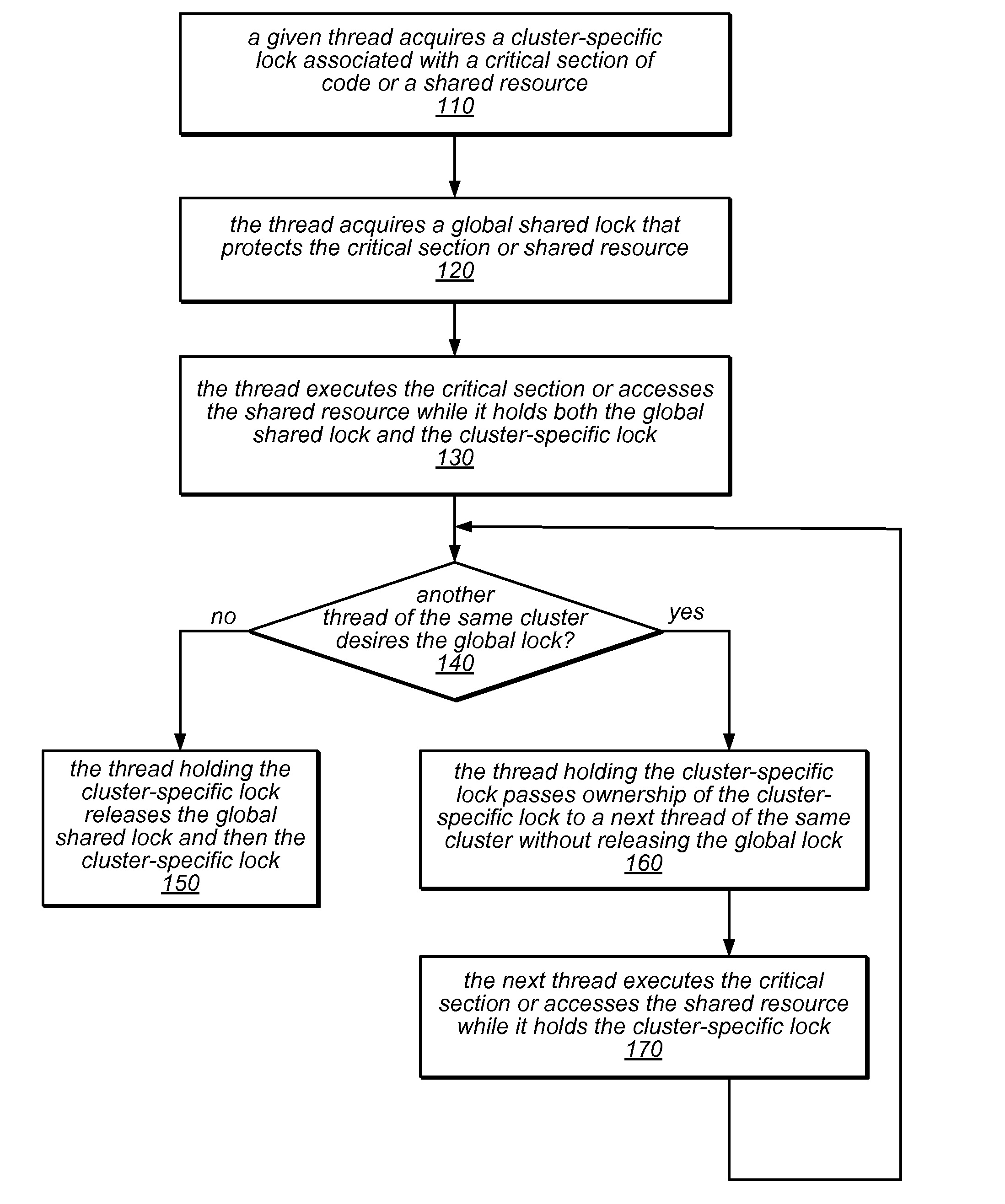
NUMA-aware reader-writer locks may leverage lock cohorting techniques to band together writer requests from a single NUMA node. The locks may relax the order in which the lock schedules the execution of critical sections of code by reader threads and writer threads, allowing lock ownership to remain resident on a single NUMA node for long periods, while also taking advantage of parallelism between reader threads. Threads may contend on node-level structures to get permission to acquire a globally shared reader-writer lock. Writer threads may follow a lock cohorting strategy of passing ownership of the lock in write mode from one thread to a cohort writer thread without releasing the shared lock, while reader threads from multiple NUMA nodes may simultaneously acquire the shared lock in read mode. The reader-writer lock may follow a writer-preference policy, a reader-preference policy or a hybrid policy.
Owner:ORACLE INT CORP
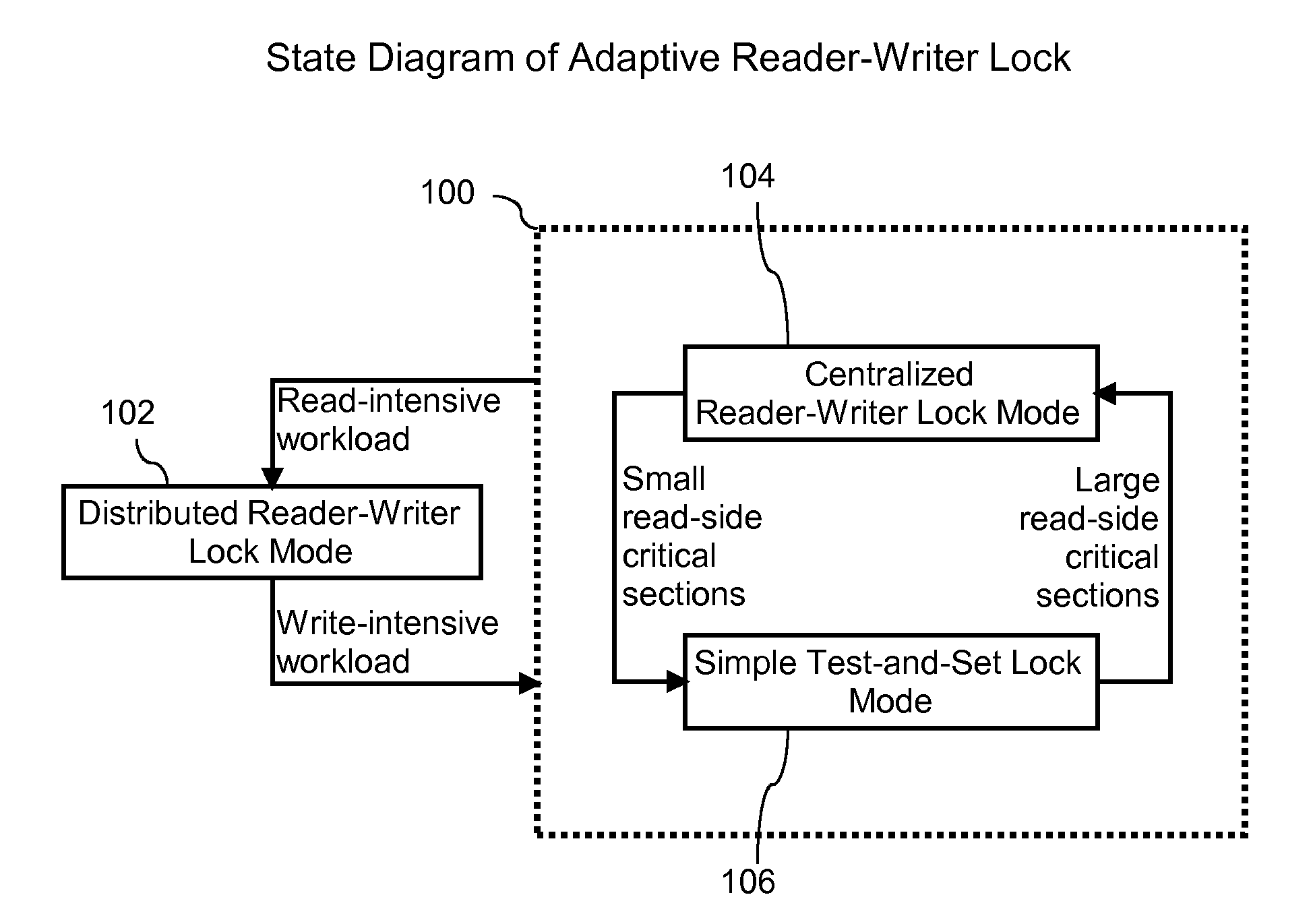
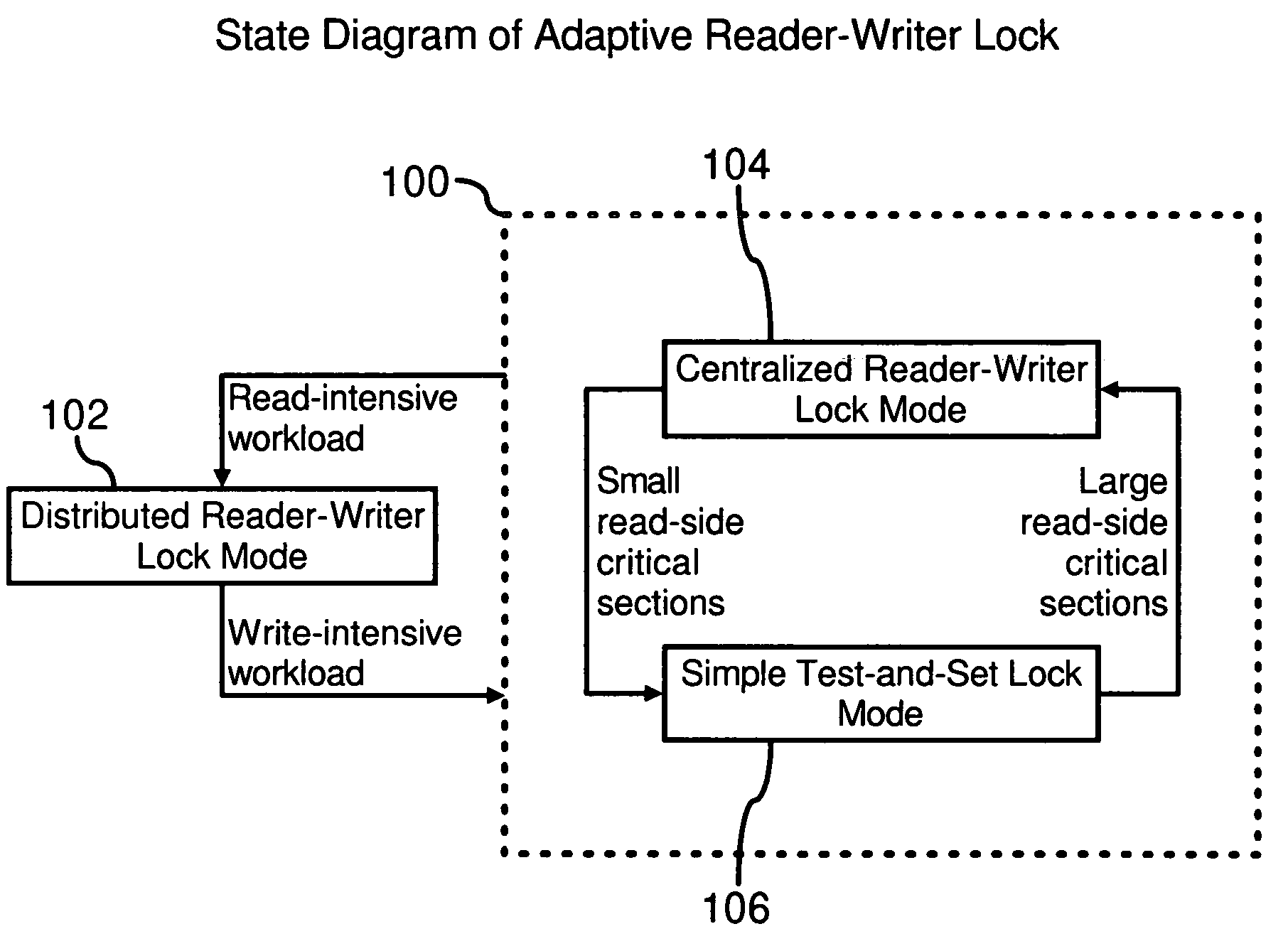
Adaptive reader-writer lock
InactiveUS7191272B2Efficient operating modeEasy to operateProgram synchronisationUnauthorized memory use protectionOperational systemMulti processor
A method and computer system for dynamically selecting an optimal lock mode in a multiprocessor environment. The method determines a quantity of read-side and write-side acquisitions, and evaluates the data to determine an optimal lock mode for efficiently operating the computer system while maintaining reduced overhead. The method incorporates data received from the individual units within a central processing system, the quantity of write-side acquisitions in the system, and data which has been subject to secondary measures, such as formatives of digital filters. The data subject to secondary measures includes, but is not limited to, a quantity of read-side acquisitions, a quantity of write-side acquisitions, and a quantity of read-hold durations. Based upon the individual unit data and the system-wide data, including the secondary measures, the operating system may select the most efficient mode of operation from among the locking modes available. Accordingly, efficiency of a computer system may be enhanced with the ability to selectively choose an optimal locking mode based upon selected and calculated parameters.
Owner:IBM CORP
System and Method for Implementing Scalable Adaptive Reader-Writer Locks
ActiveUS20150286586A1Memory architecture accessing/allocationProgram synchronisationSleep stateCritical section
NUMA-aware reader-writer locks may leverage lock cohorting techniques and may support reader re-entrancy. They may implement a delayed sleep mechanism by which a thread that fails to acquire a lock spins briefly, hoping the lock will be released soon, before blocking on the lock (sleeping). The maximum spin time may be based on the time needed to put a thread to sleep and wake it up. If a lock holder is not executing on a processor, an acquiring thread may go to sleep without first spinning. Threads put in a sleep state may be placed on a turnstile sleep queue associated with the lock. When a writer thread that holds the lock exits a critical section protected by the lock, it may wake all sleeping reader threads and one sleeping writer thread. Reader threads may increment and decrement node-local reader counters upon arrival and departure, respectively.
Owner:ORACLE INT CORP
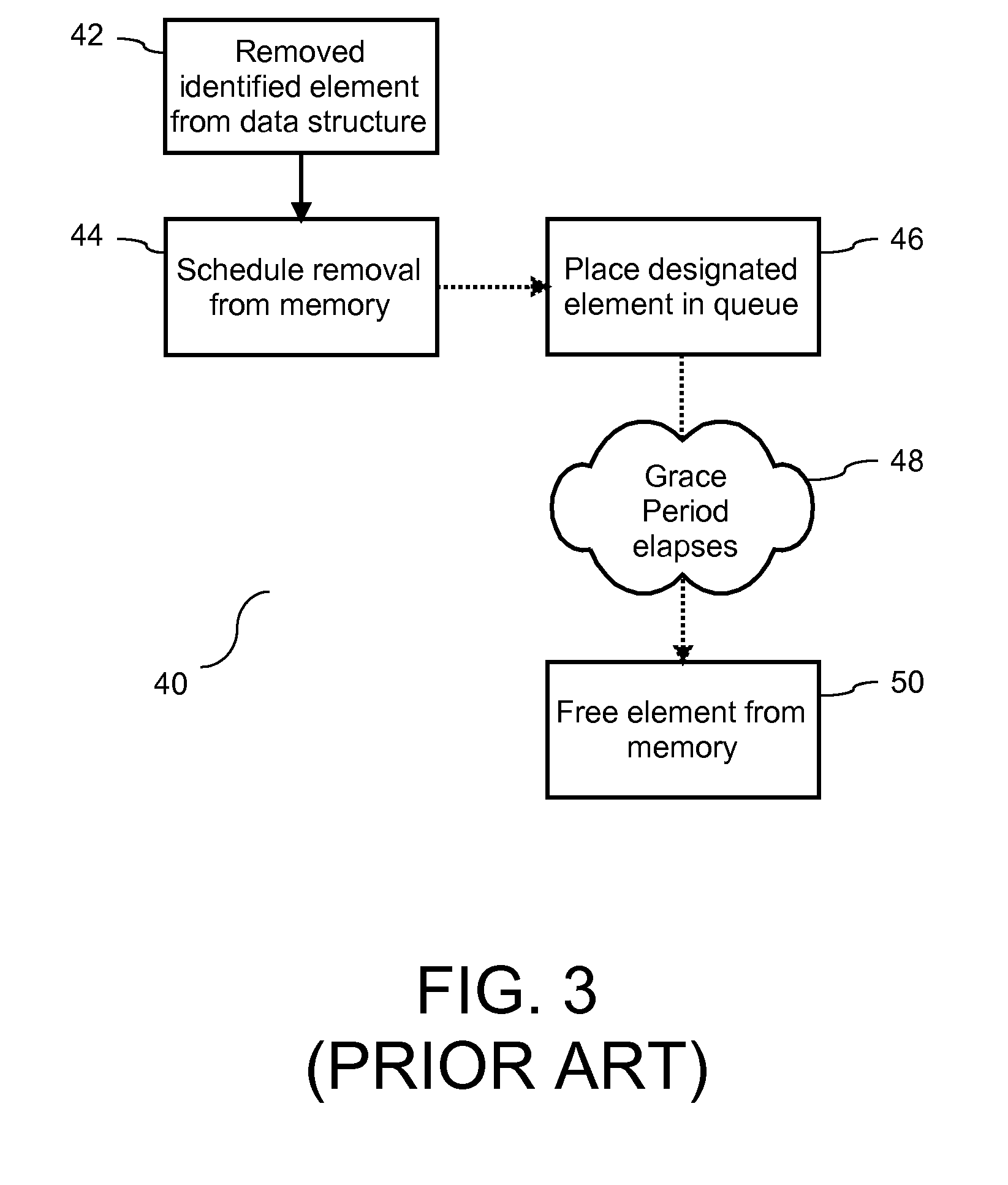
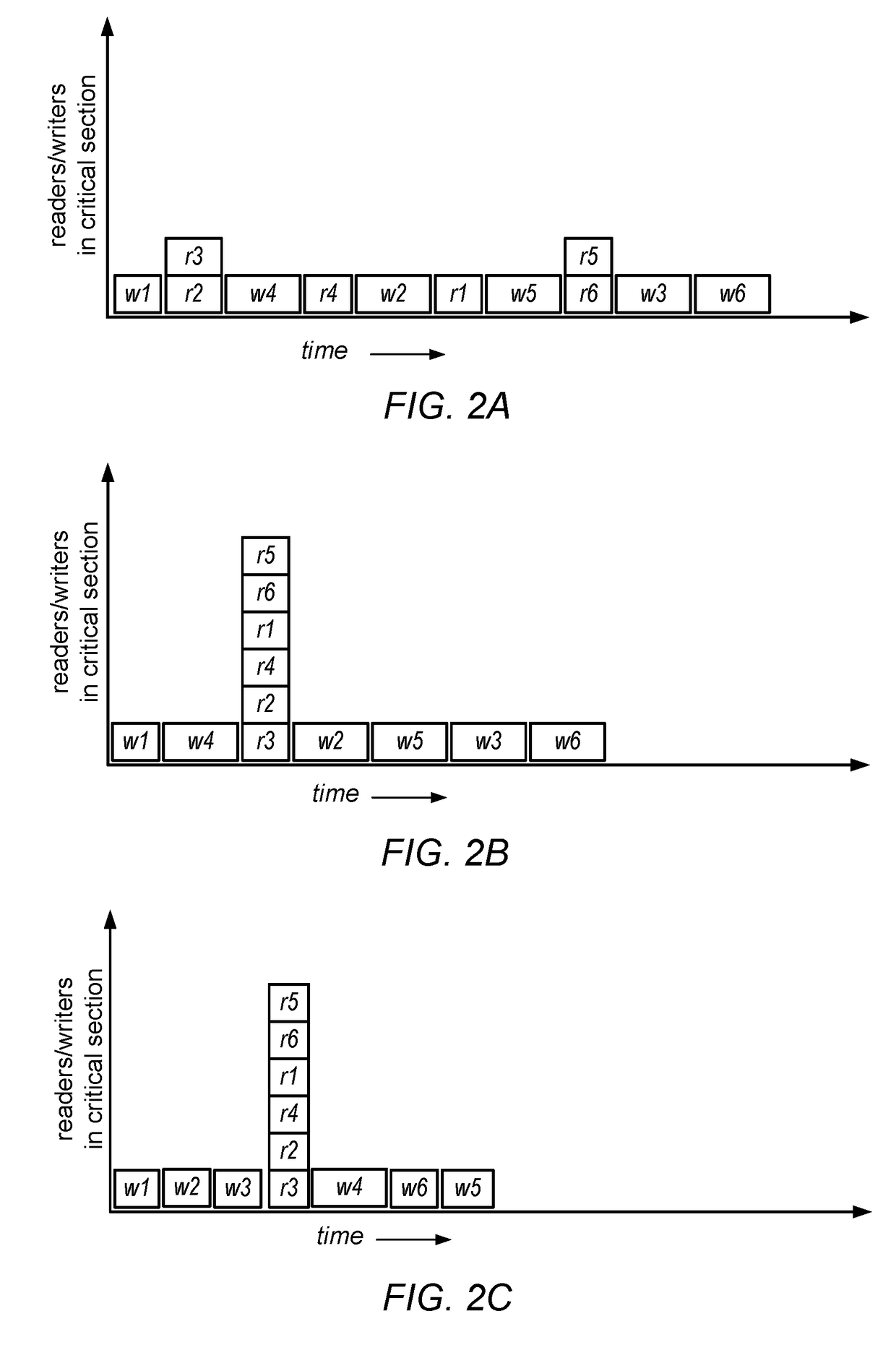
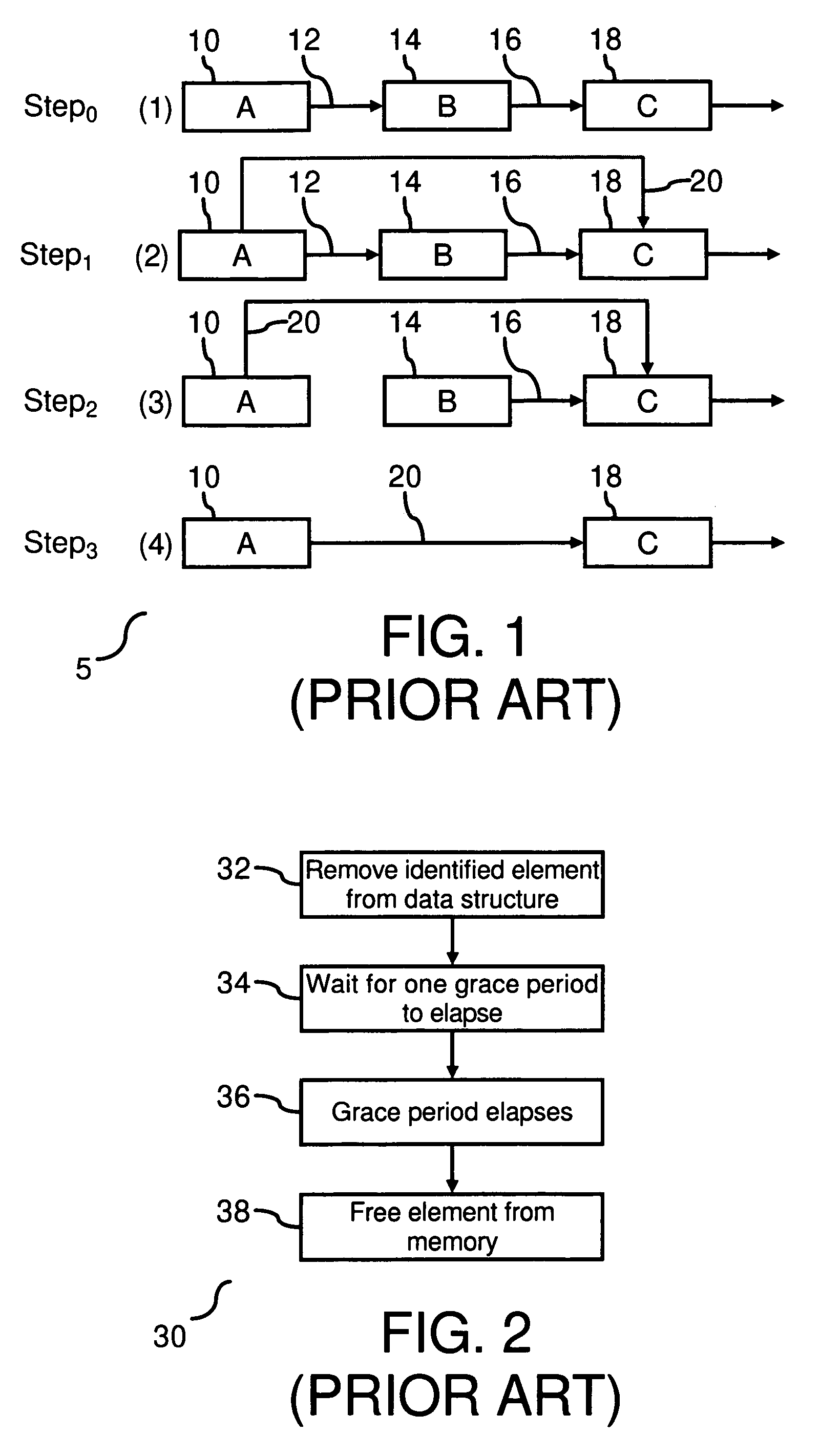
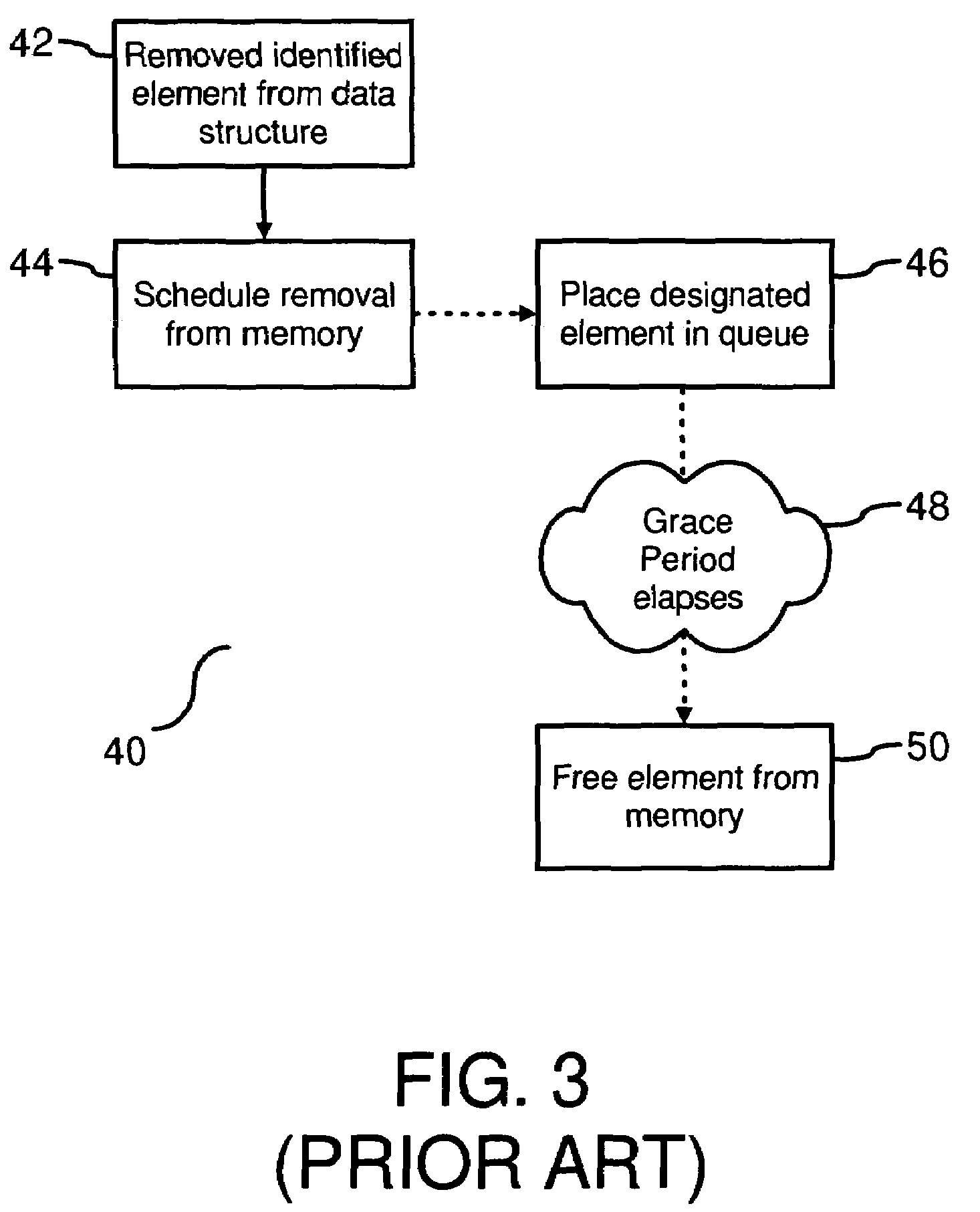
Read/write lock with reduced reader lock sampling overhead in absence of writer lock acquisition
ActiveUS20080320262A1Improved reader-writer lockingProgram synchronisationMemory systemsReader writerOperating system
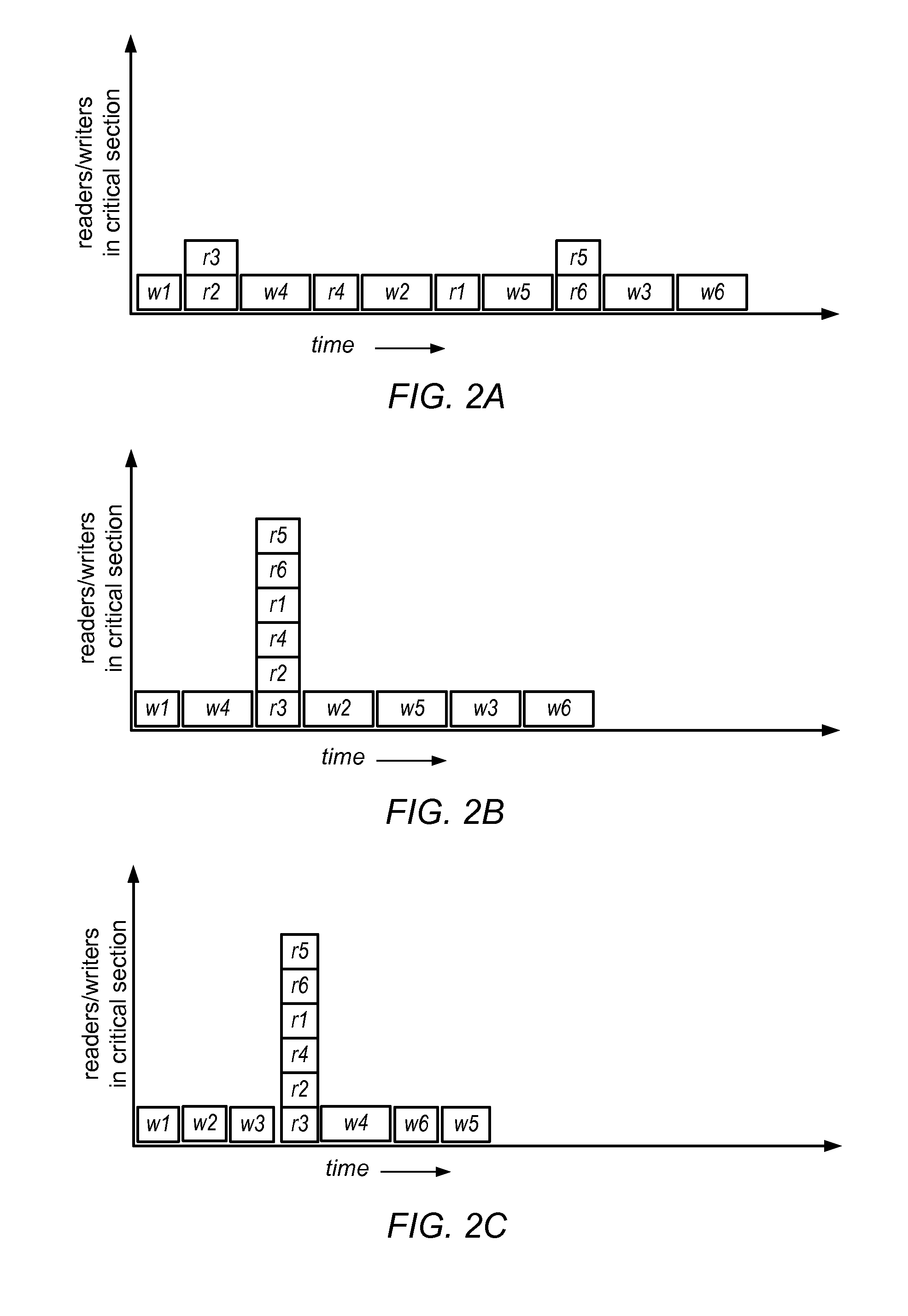
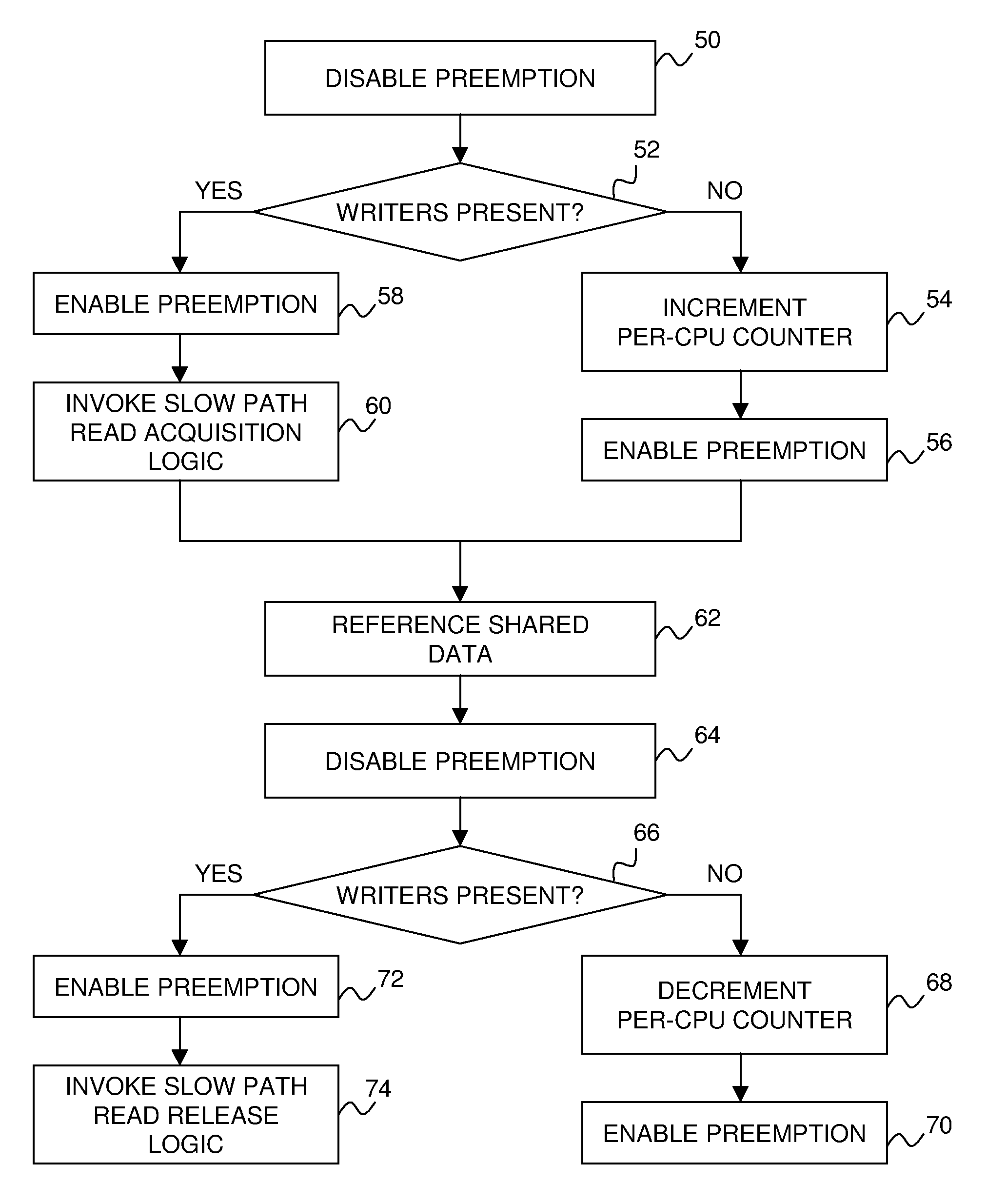
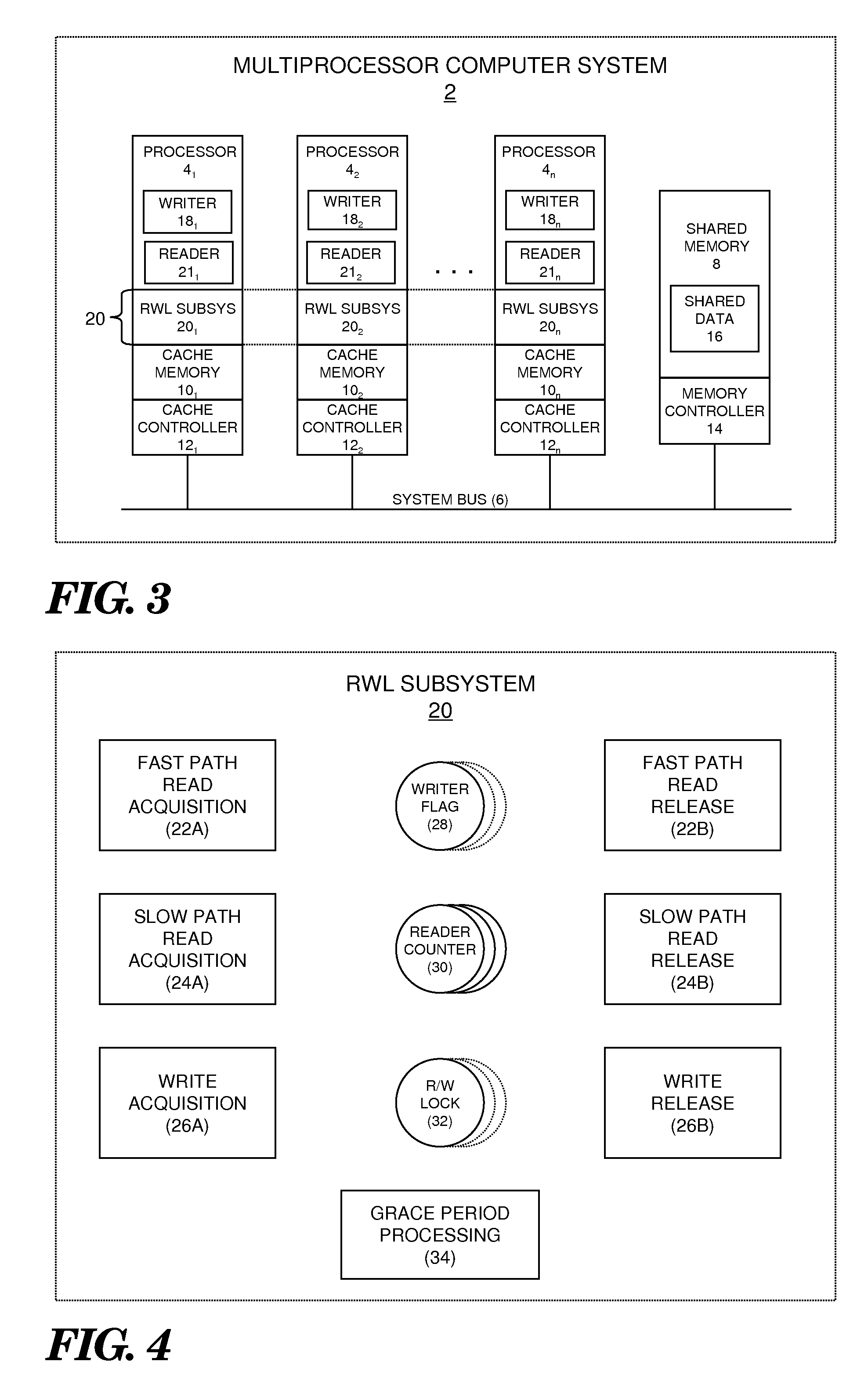
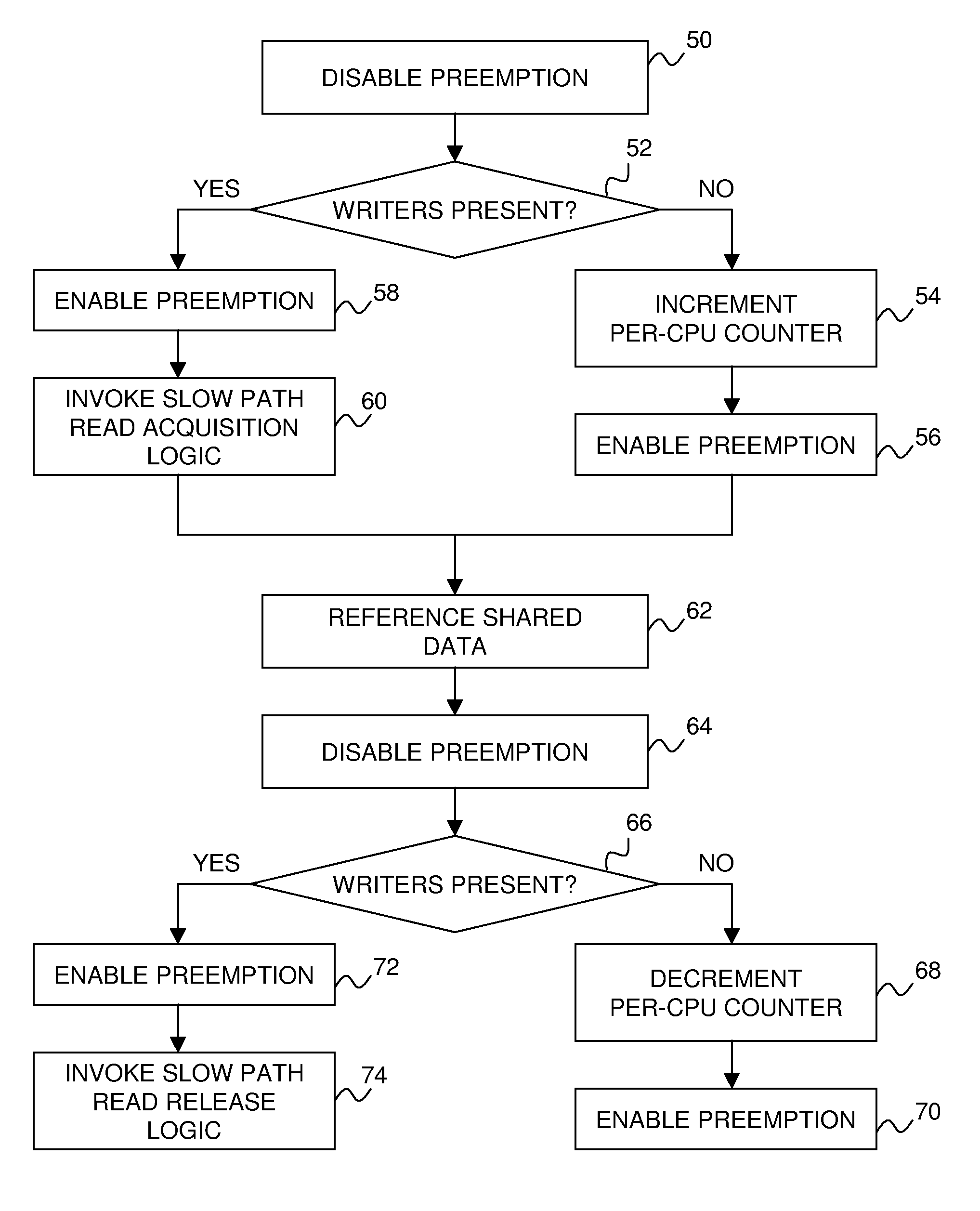
An improved reader-writer locking for synchronizing access to shared data. When writing the shared data, a writer flag is set and a lock is acquired on the shared data. The shared data may be accessed following the expiration of a grace period and a determination that there are no data readers accessing the shared data. When reading the shared data, the writer flag is tested that indicates whether a data writer is attempting to access the shared data. If the writer flag is not set, the shared data is accessed using a relatively fast read mechanism. If the writer flag is set, the shared data is accessed using a relatively slow read mechanism.
Owner:IBM CORP
Read/write lock with reduced reader lock sampling overhead in absence of writer lock acquisition
An improved reader-writer locking for synchronizing access to shared data. When writing the shared data, a writer flag is set and a lock is acquired on the shared data. The shared data may be accessed following the expiration of a grace period and a determination that there are no data readers accessing the shared data. When reading the shared data, the writer flag is tested that indicates whether a data writer is attempting to access the shared data. If the writer flag is not set, the shared data is accessed using a relatively fast read mechanism. If the writer flag is set, the shared data is accessed using a relatively slow read mechanism.
Owner:IBM CORP
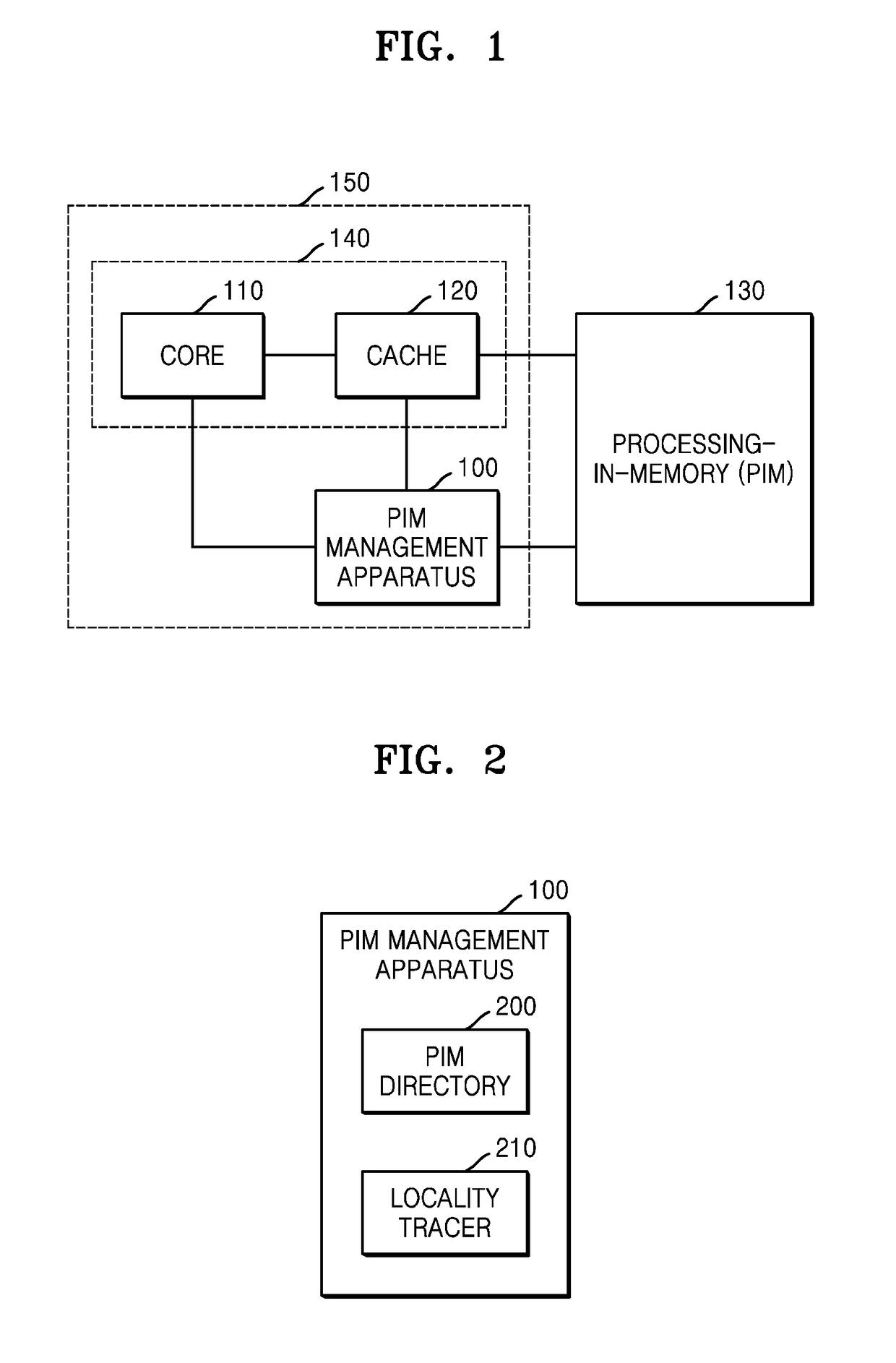
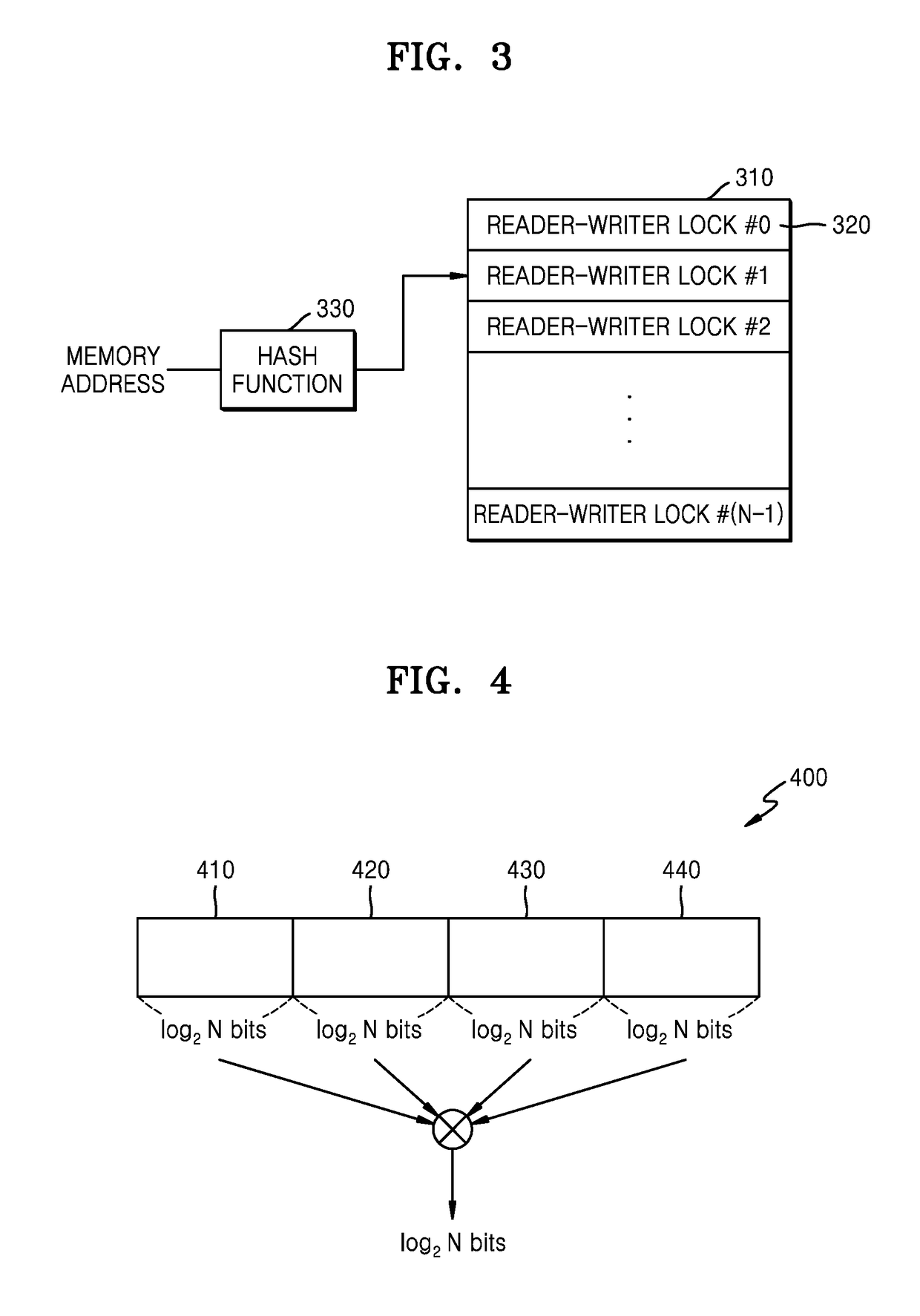
Method and apparatus for processing instructions using processing-in-memory
ActiveUS20180336035A1Control performanceIncreased memory bandwidthMemory architecture accessing/allocationProgram synchronisationMemory addressProcessing Instruction
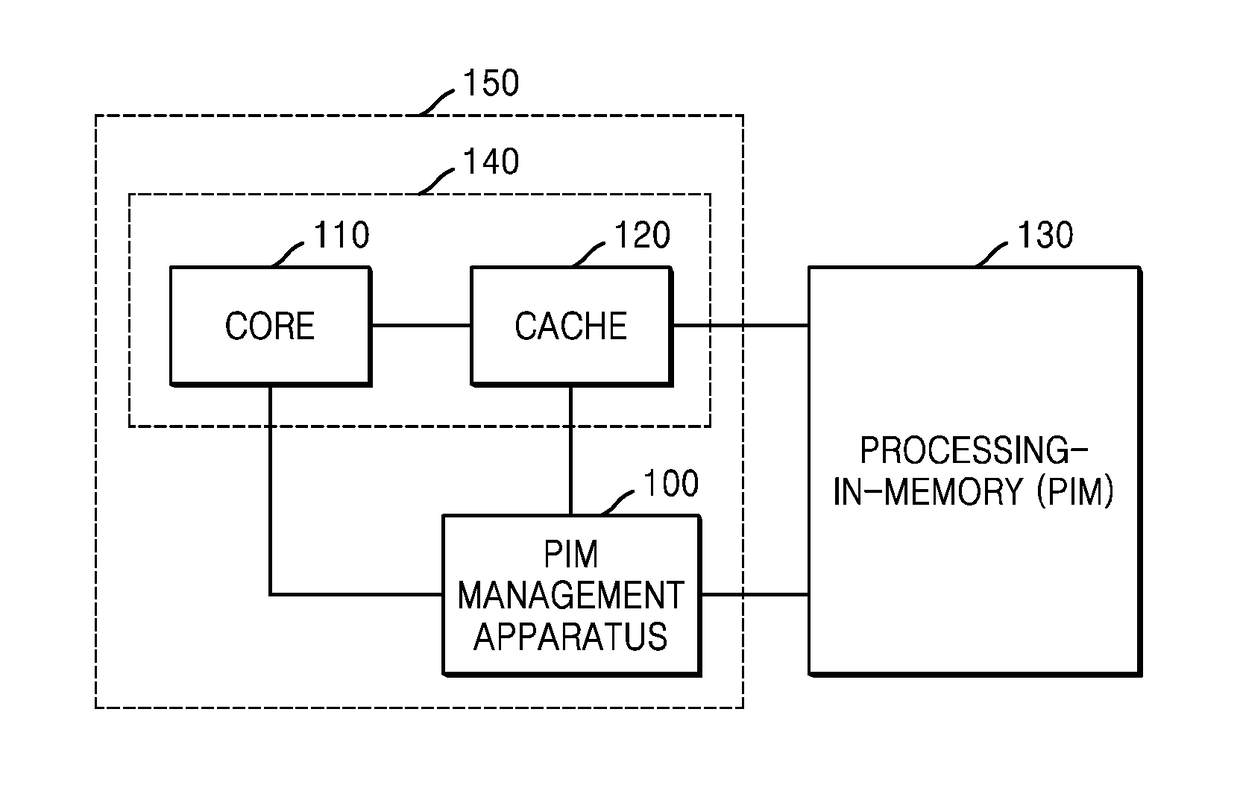
Provided is a method and apparatus for processing instructions using a processing-in-memory (PIM). A PIM management apparatus includes: a PIM directory comprising a reader-writer lock regarding a memory address that an instruction accesses; and a locality tracer configured to figure out locality regarding the memory address that the instruction accesses and determine whether or not an object that executes the instruction is a PIM.
Owner:SAMSUNG ELECTRONICS CO LTD
Adaptive Reader-Writer Lock
InactiveUS20080209433A1Efficient operating modeEasy to operateProgram synchronisationUnauthorized memory use protectionOperational systemMechanism based
A method and computer system for dynamically selecting an optimal synchronization mechanism for a data structure in a multiprocessor environment. The method determines a quantity of read-side and write-side acquisitions, and evaluates the data to determine an optimal mode for efficiently operating the computer system while maintaining reduced overhead. The method incorporates data received from the individual units within a central processing system, the quantity of write-side acquisitions in the system, and data which has been subject to secondary measures, such as formatives of digital filters. The data subject to secondary measures includes, but is not limited to, a quantity of read-side acquisitions, a quantity of write-side acquisitions, and a quantity of read-hold durations. Based upon the individual unit data and the system-wide data, including the secondary measures, the operating system may select the most efficient synchronization mechanism from among the mechanisms available. Accordingly, efficiency of a computer system may be enhanced with the ability to selectively choose an optimal synchronization mechanism based upon selected and calculated parameters.
Owner:IBM CORP
System and method for implementing NUMA-aware reader-writer locks
ActiveUS8966491B2Reduce probabilityReduce traffic problemsDigital data processing detailsDigital computer detailsCritical sectionParallel computing
Owner:ORACLE INT CORP
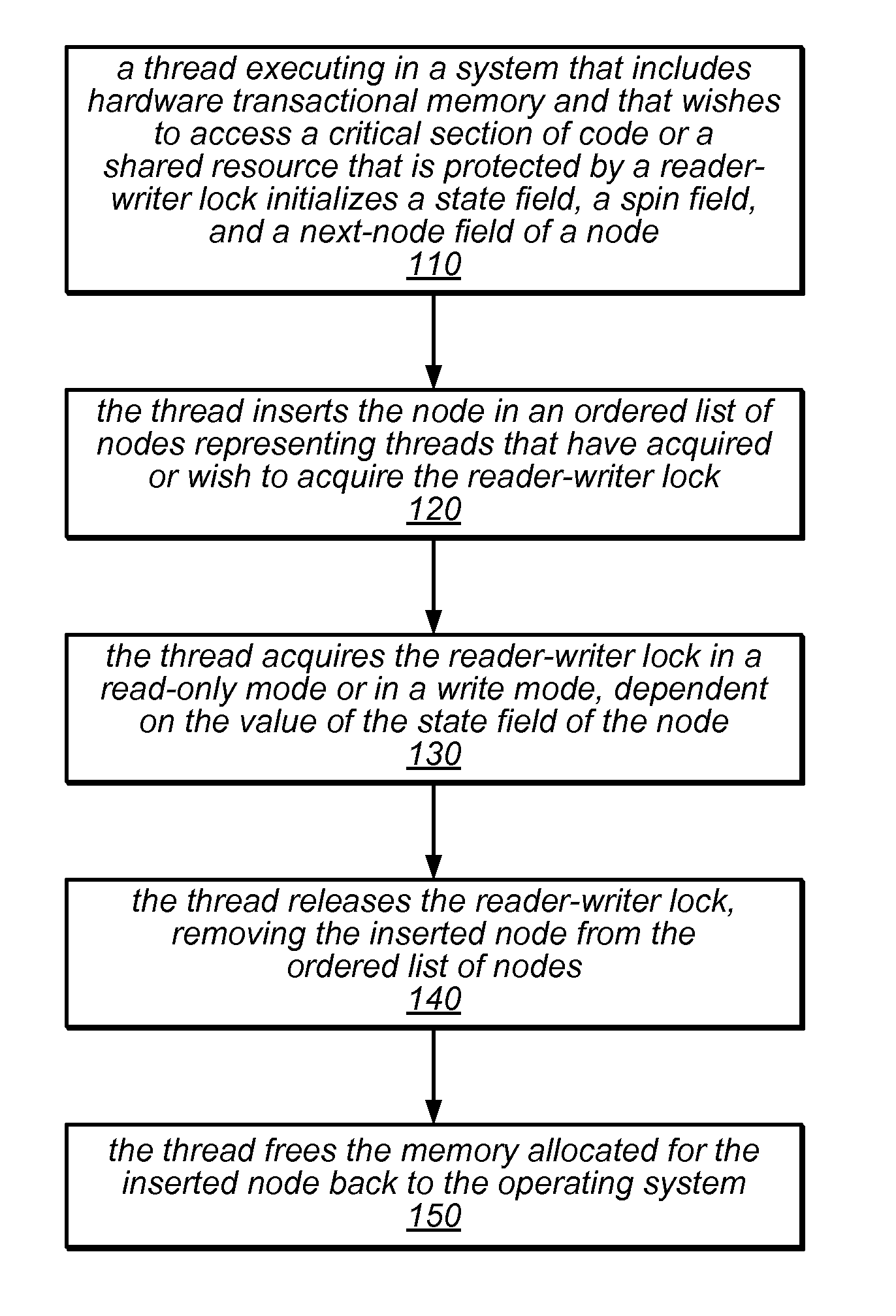
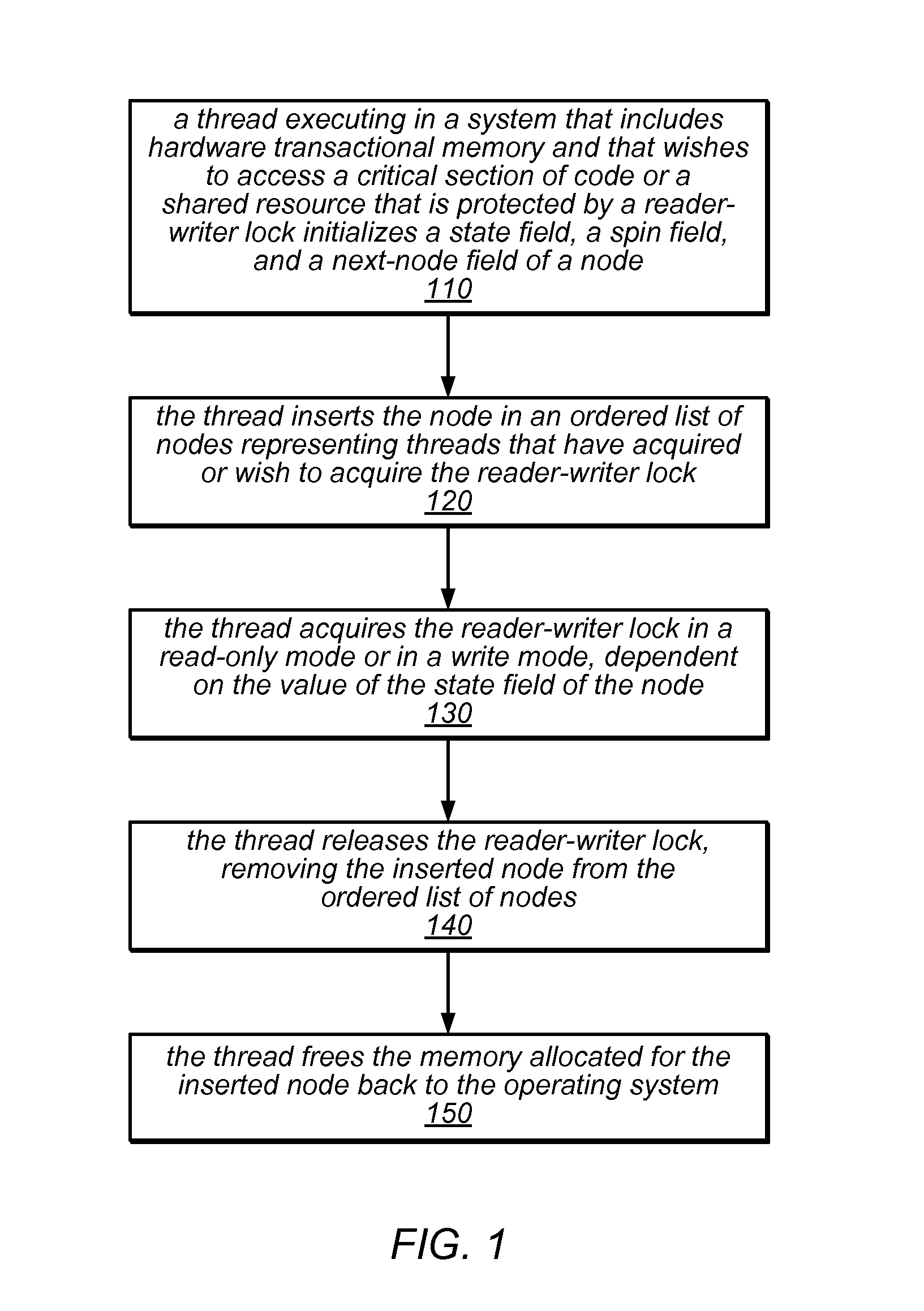
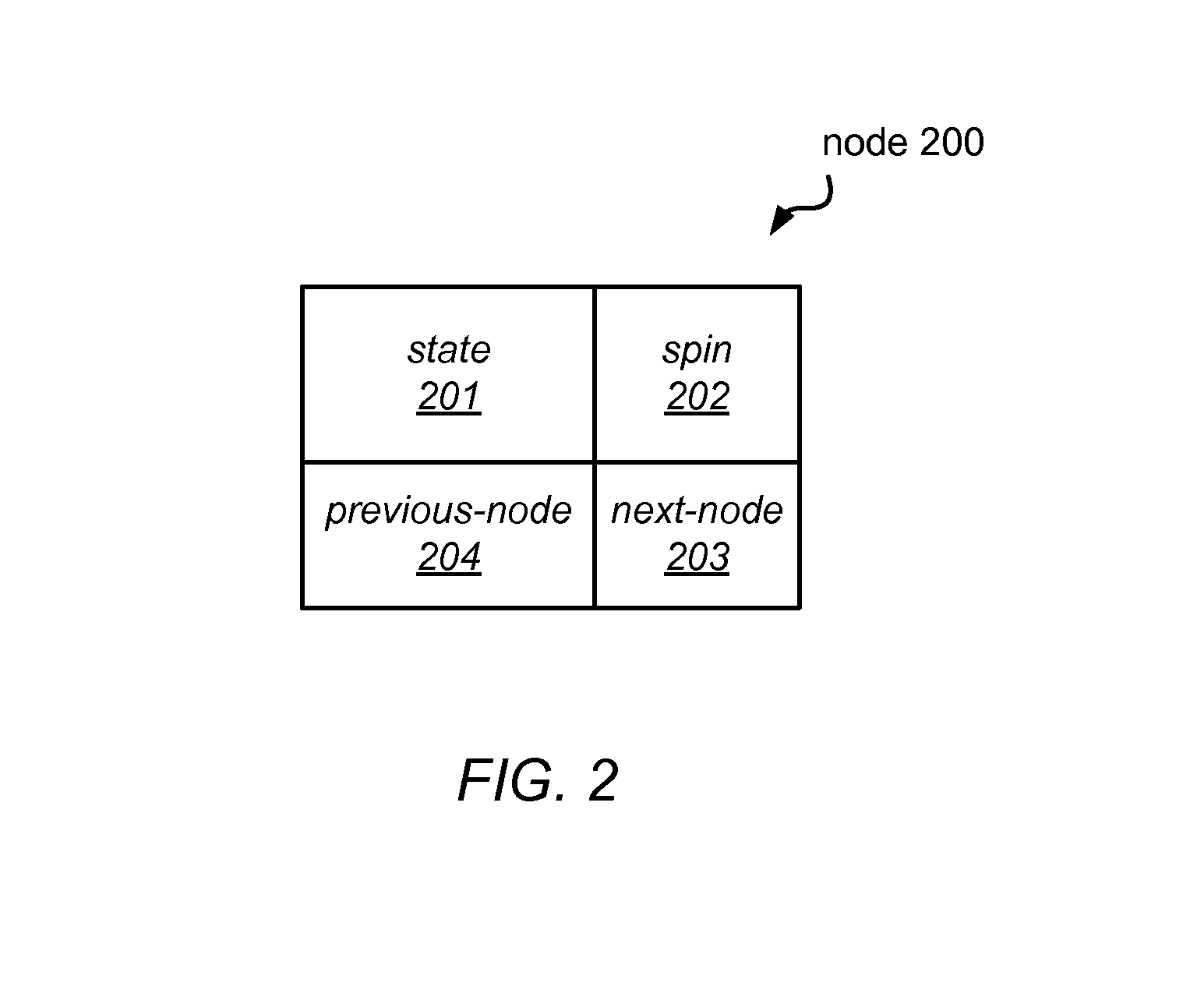
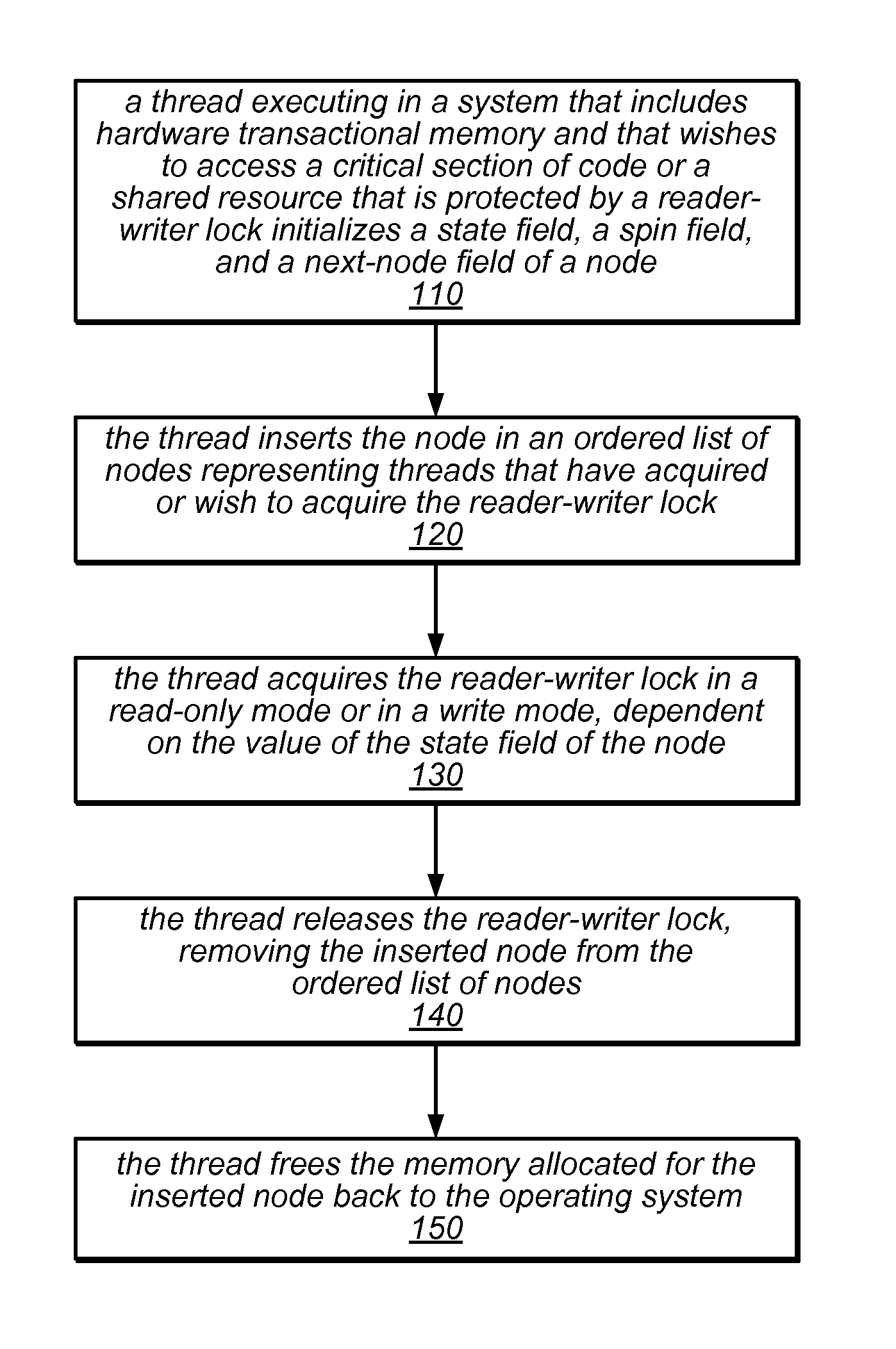
System and Method for Implementing Reader-Writer Locks Using Hardware Transactional Memory
ActiveUS20140258645A1Simple procedureEliminate requirementsUnauthorized memory use protectionTransaction processingCritical sectionReader writer
Transactional reader-writer locks may leverage available hardware transactional memory (HTM) to simplify the procedures of the reader-writer lock algorithm and to eliminate a requirement for type stable memory An HTM-based reader-writer lock may include an ordered list of client-provided nodes, each of which represents a thread that holds (or desires to acquire) the lock, and a tail pointer. The locking and unlocking procedures invoked by readers and writers may access the tail pointer or particular ones of the nodes in the list using various combinations of transactions and non-transactional accesses to insert nodes into the list or to remove nodes from the list. A reader or writer that owns a node at the head of the list (or a reader whose node is preceded in the list only by other readers' nodes) may access a critical section of code or shared resource.
Owner:ORACLE INT CORP
System and Method for Promoting Reader Groups for Lock Cohorting
ActiveUS20170220474A1Improve throughoutImprove performanceMemory architecture accessing/allocationSpecific access rightsCritical sectionReader writer
NUMA-aware reader-writer locks may leverage lock cohorting techniques that introduce a synthetic level into the lock hierarchy (e.g., one whose nodes do not correspond to the system topology). The synthetic level may include a global reader lock and a global writer lock. A writer thread may acquire a node-level writer lock, then the global writer lock, and then the top-level lock, after which it may access a critical section protected by the lock. The writer may release the lock (if an upper bound on consecutive writers has been met), or may pass the lock to another writer (on the same node or a different node, according to a fairness policy). A reader may acquire the global reader lock (whether or not node-level reader locks are present), and then the top-level lock. However, readers may only hold these locks long enough to increment reader counts associated with them.
Owner:ORACLE INT CORP
Adaptive reader-writer lock
InactiveUS7430627B2Easy to operateProgram synchronisationUnauthorized memory use protectionOperational systemMulti processor
A method and computer system for dynamically selecting an optimal synchronization mechanism for a data structure in a multiprocessor environment. The method determines a quantity of read-side and write-side acquisitions, and evaluates the data to determine an optimal mode for efficiently operating the computer system while maintaining reduced overhead. The method incorporates data received from the individual units within a central processing system, the quantity of write-side acquisitions in the system, and data which has been subject to secondary measures, such as formatives of digital filters. The data subject to secondary measures includes, but is not limited to, a quantity of read-side acquisitions, a quantity of write-side acquisitions, and a quantity of read-hold durations. Based upon the individual unit data and the system-wide data, including the secondary measures, the operating system may select the most efficient synchronization mechanism from among the mechanisms available. Accordingly, efficiency of a computer system may be enhanced with the ability to selectively choose an optimal synchronization mechanism based upon selected and calculated parameters.
Owner:IBM CORP
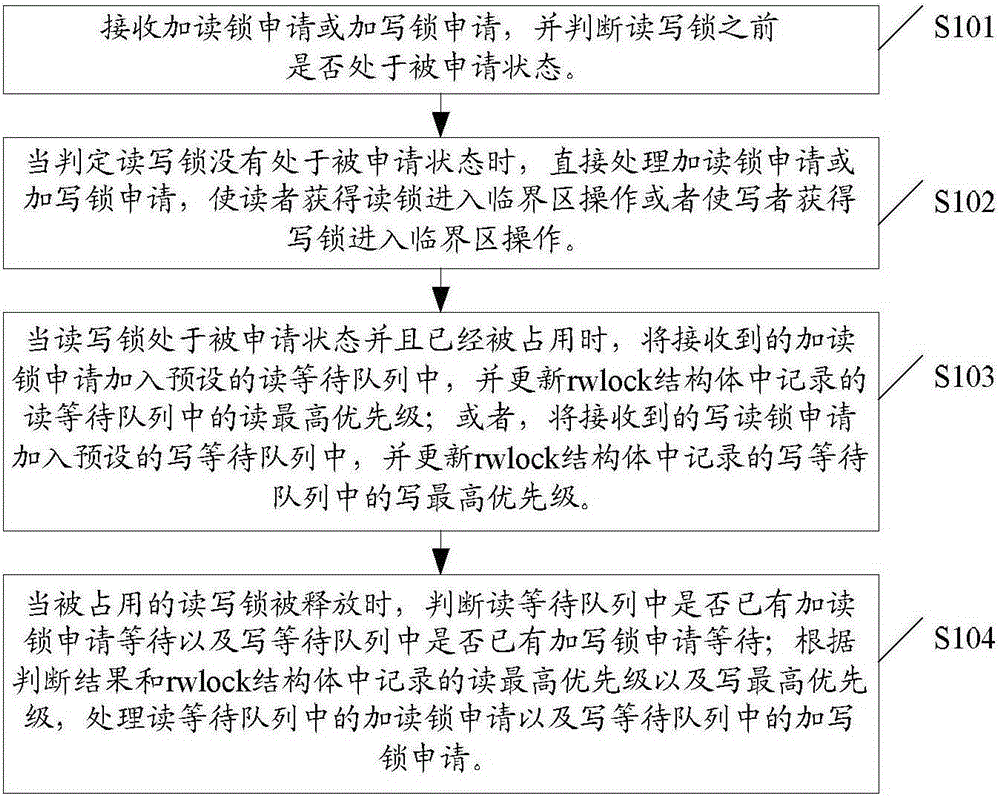
Method and system for optimizing reader-writer lock based on Linux
ActiveCN105224251AReduce starvationReduce or avoid starvationInput/output to record carriersResource utilizationGNU/Linux
The invention discloses a method and a system for optimizing reader-writer locks based on the Linux. The method comprises: receiving a reader lock adding application or a writer lock adding application, and determining whether reader-writer locks are in an applied state before; if the reader-writer locks are not in the applied state, directly processing the reader lock adding application or the writer lock adding application; if the reader-writer locks are in the applied state and are occupied, adding the reader lock adding application in a preset read-write waiting queue, and upgrading read highest priority-first or write highest priority-first recorded in a rwlock structural body; when the occupied reader-writer lock is released, determining whether reader-writer lock adding applications wait in the read-write waiting queue; according to a determination result, and the read highest priority-first and the write highest priority-first, processing the reader lock adding application in the read waiting queue and the writer lock adding application in the write waiting queue. Through the scheme, situation that a reader or a writer starves can be reduced or prevented, so as to improve resource utilization rate of the system and system parallel processing performance.
Owner:INSPUR BEIJING ELECTRONICS INFORMATION IND
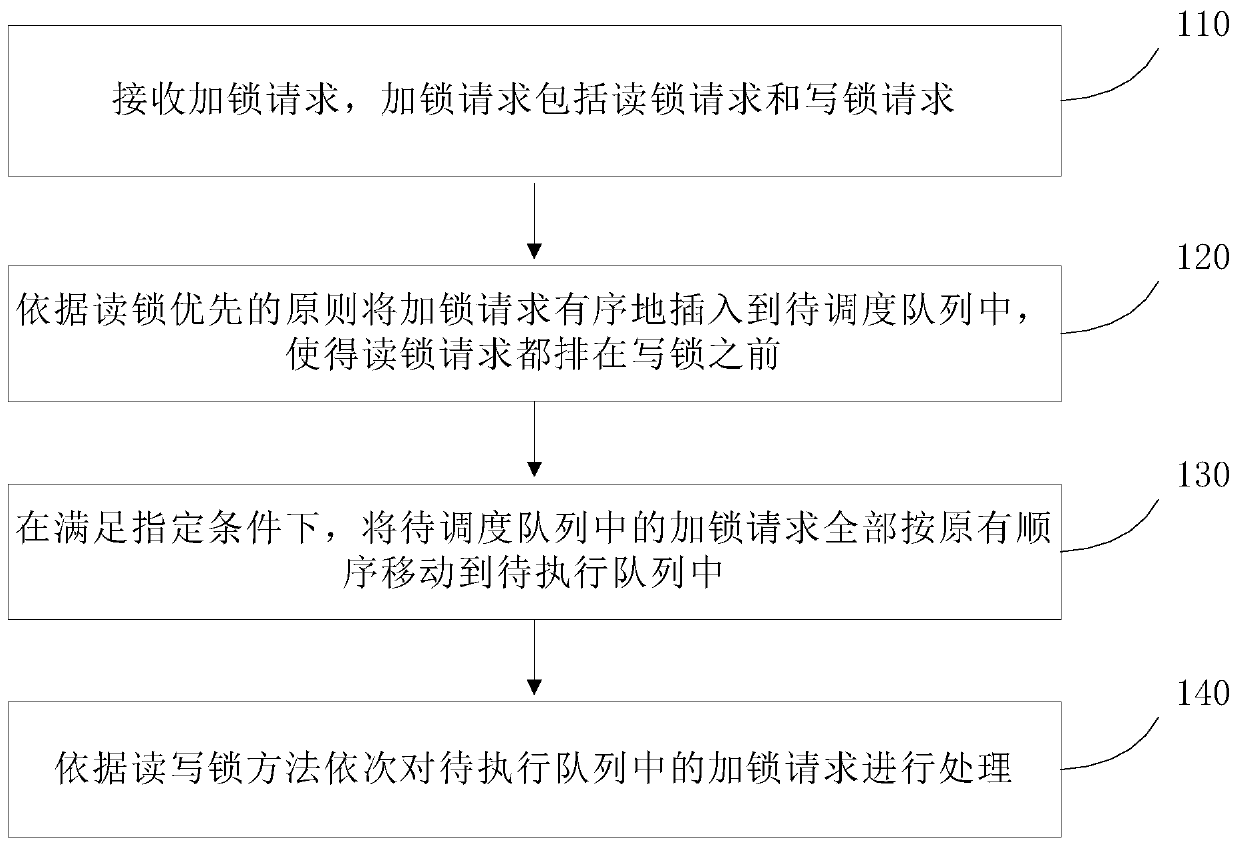
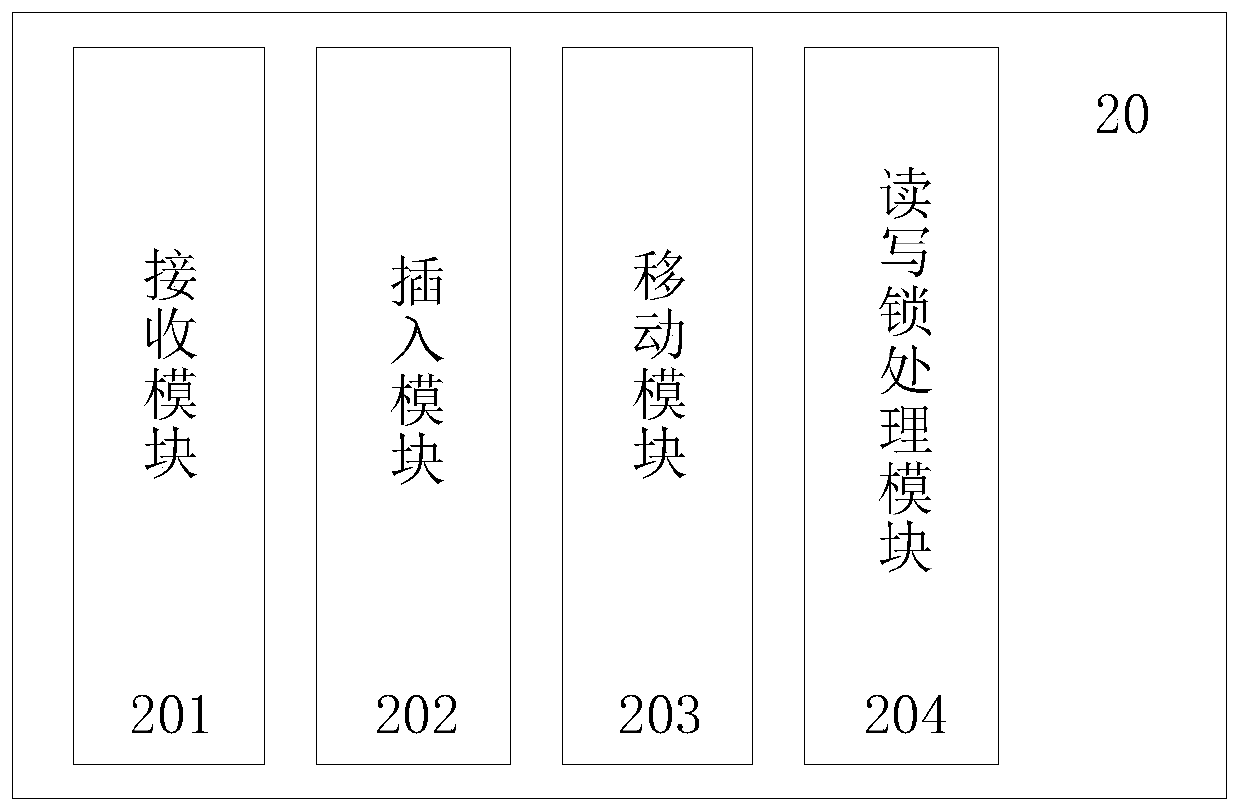
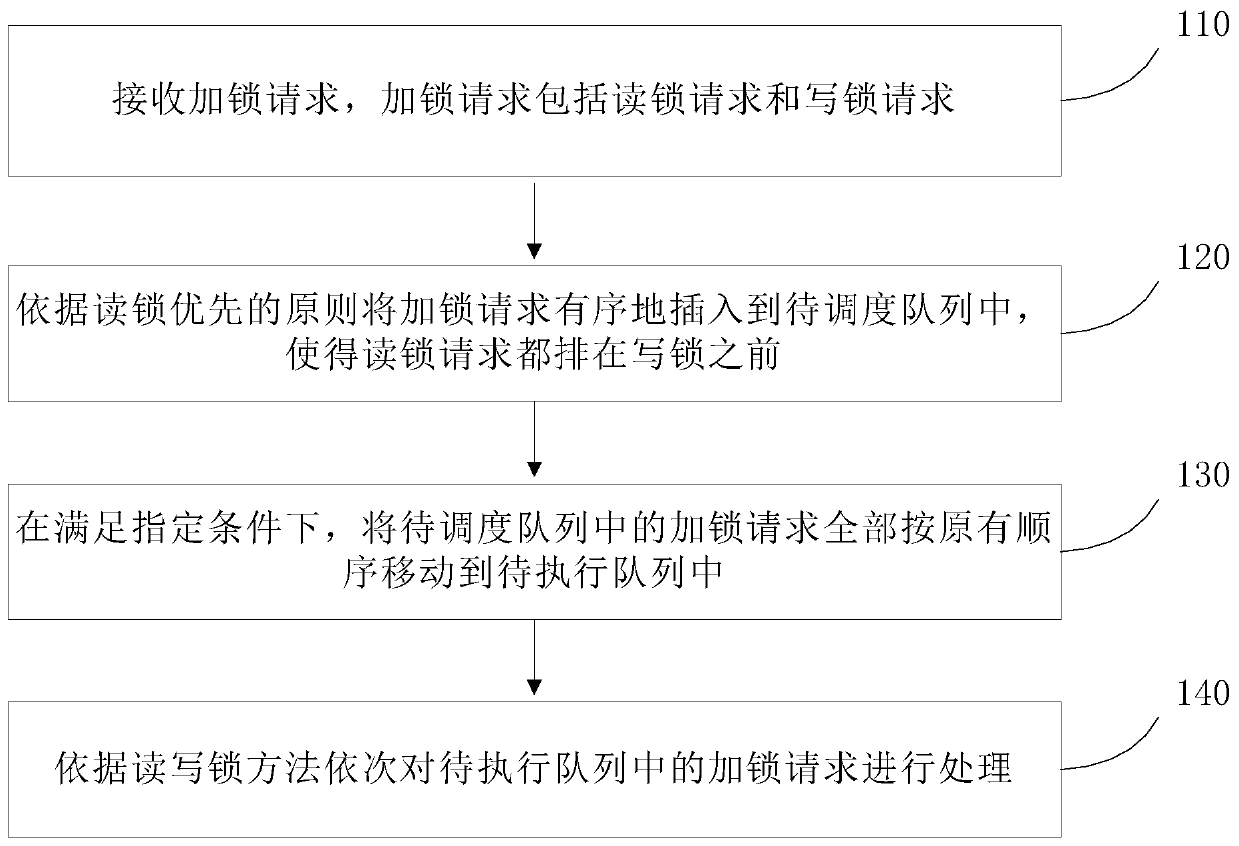
Read-write lock optimization method, device and system and storage medium
The invention discloses a read-write lock optimization method, device and system and a storage medium. The method comprises the following steps: firstly, receiving all locking requests by a to-be-scheduled queue, wherein the locking requests comprises a read lock request and a write lock request, and orderly inserting the locking request into the to-be-scheduled queue according to a read lock priority principle, so that the read lock request is ranked in front of the write lock request, the read lock can be ensured to be processed preferentially, and the characteristics and advantages of an original read-write lock method are ensured; then, under the condition of meeting the specified condition, moving all the locking requests in the to-be-scheduled queue to a to-be-executed queue according to an original sequence; and the locking requests in the to-be-executed queue are sequentially processed according to the read-write lock method, so that all the locking requests in the to-be-scheduled queue before can be processed, and the situation that the writing lock requests are blocked for a long time and cannot be processed is avoided.
Owner:LENOVO (BEIJING) LTD
System and method for implementing reader-writer locks using hardware transactional memory
ActiveUS9342380B2Simple procedureEliminate requirementsProgram synchronisationMemory systemsCritical sectionReader writer
Transactional reader-writer locks may leverage available hardware transactional memory (HTM) to simplify the procedures of the reader-writer lock algorithm and to eliminate a requirement for type stable memory An HTM-based reader-writer lock may include an ordered list of client-provided nodes, each of which represents a thread that holds (or desires to acquire) the lock, and a tail pointer. The locking and unlocking procedures invoked by readers and writers may access the tail pointer or particular ones of the nodes in the list using various combinations of transactions and non-transactional accesses to insert nodes into the list or to remove nodes from the list. A reader or writer that owns a node at the head of the list (or a reader whose node is preceded in the list only by other readers' nodes) may access a critical section of code or shared resource.
Owner:ORACLE INT CORP
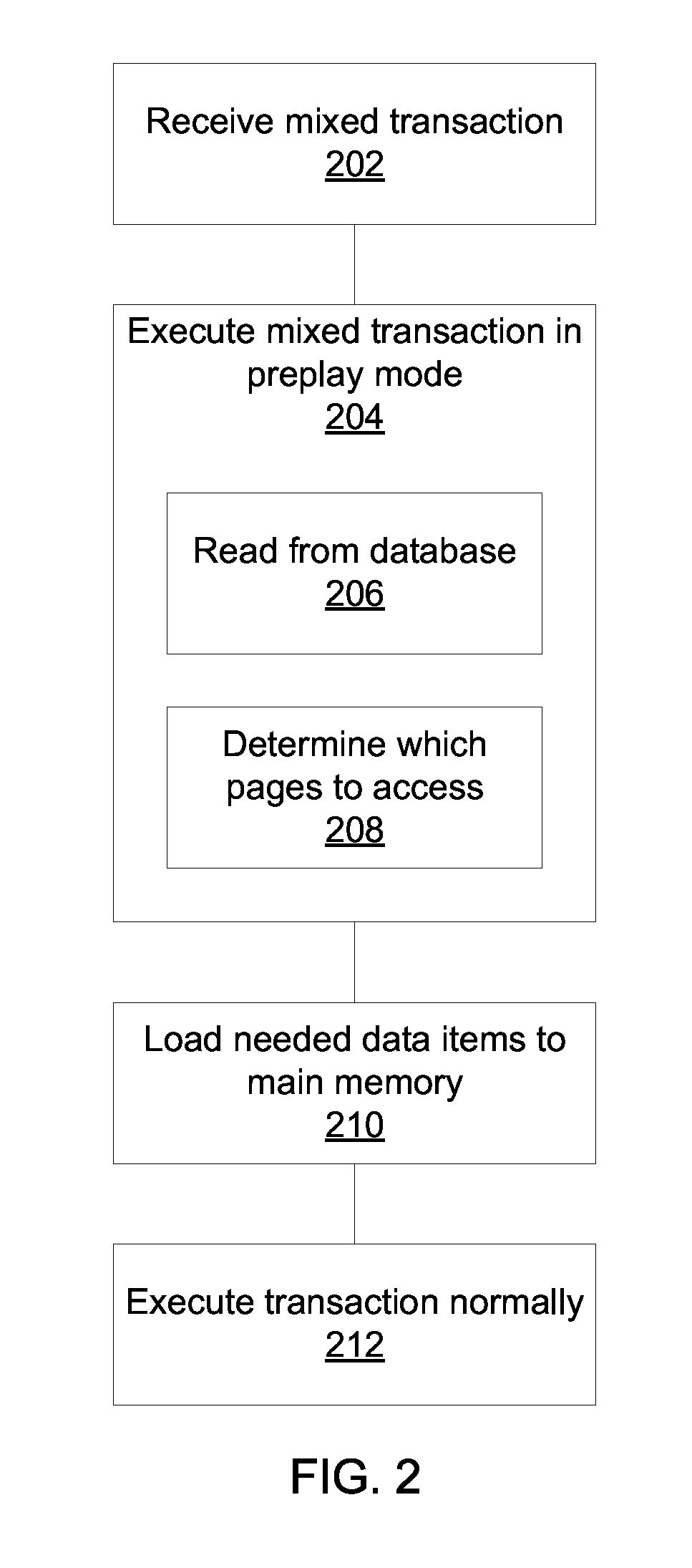
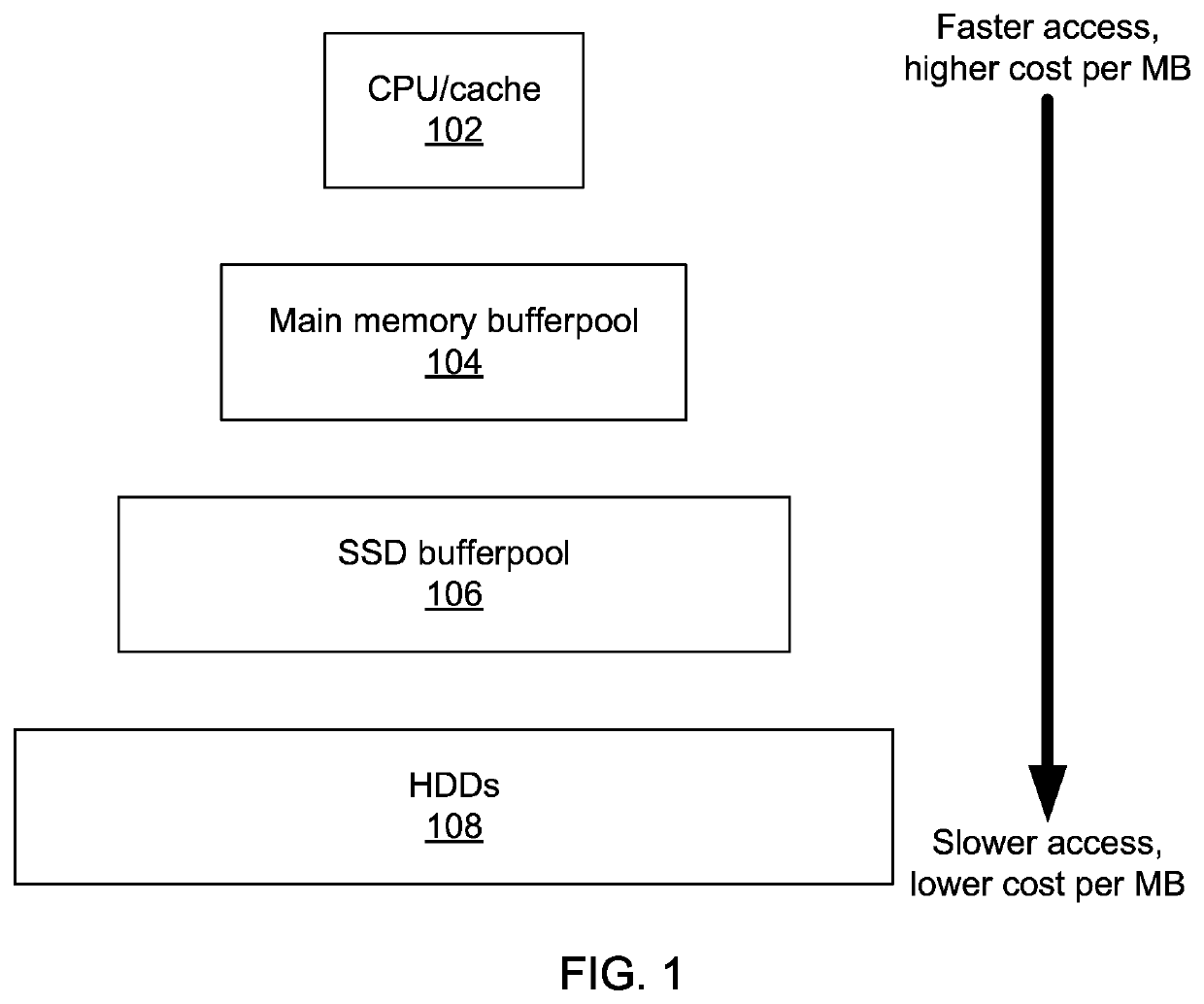
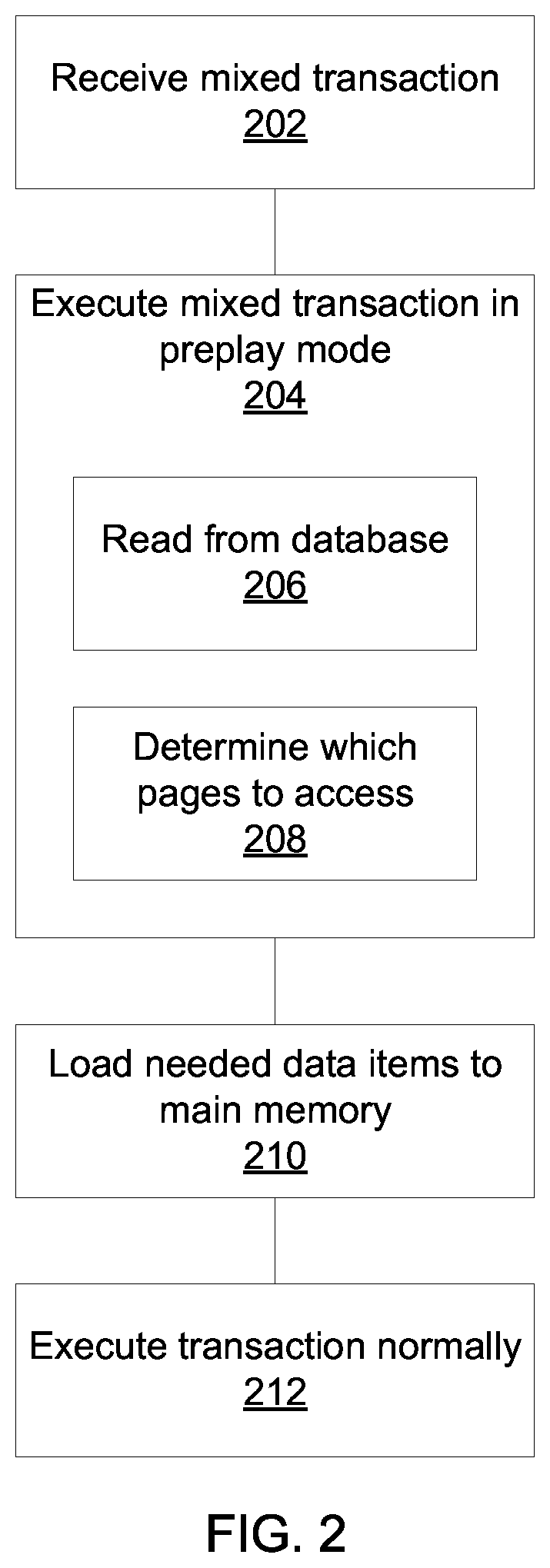
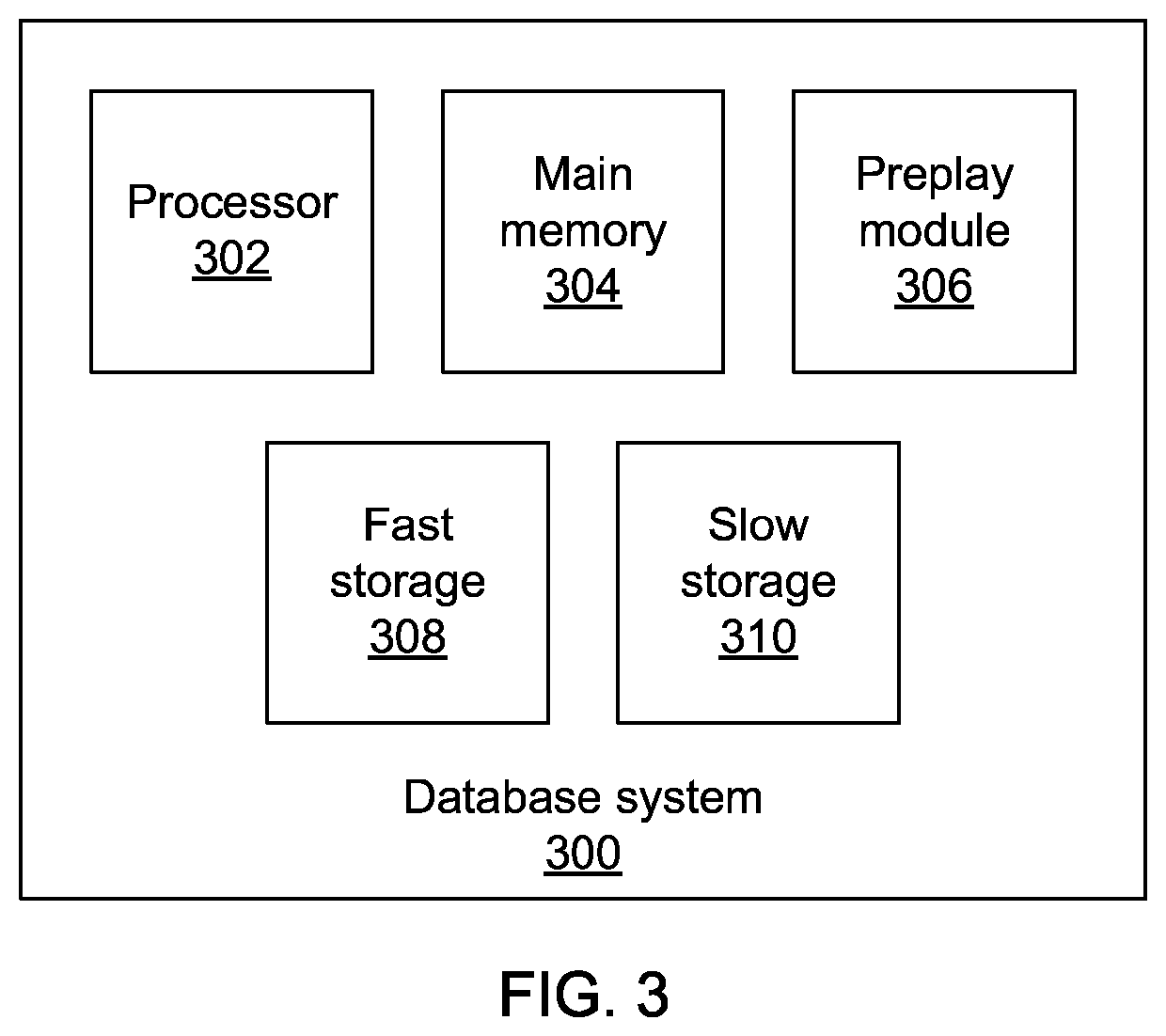
Preplaying transactions that mix hot and cold data
ActiveUS20150363455A1Memory architecture accessing/allocationDigital data information retrievalData bufferDatabase transaction
Methods and systems for performing database transactions include executing a first transaction request in a preplay mode that locks the requested data with a prefetch-lock and reads one or more requested data items from storage into a main memory buffer; locking the requested data items with a read / write lock after said data items are read into the main memory buffer; and performing the requested transaction on the data items in the main memory buffer using a processor.
Owner:IBM CORP
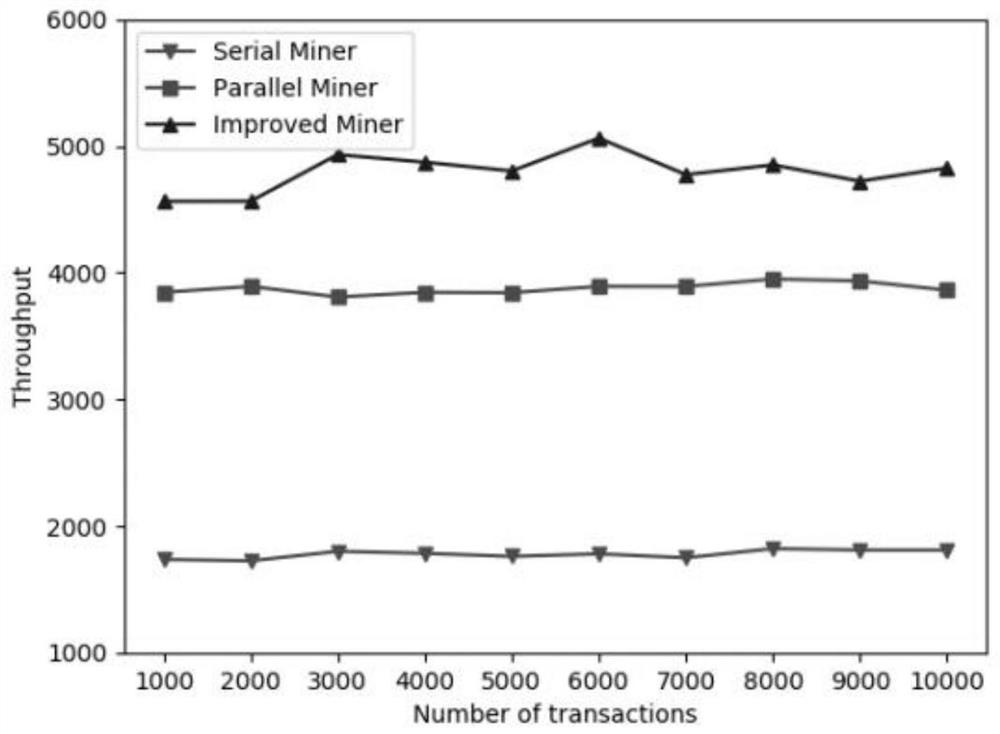
Intelligent contract execution optimization method based on multi-core architecture
PendingCN111724256ASolve the blockageSolve concurrency issuesFinanceForecastingComputer architectureMulticore architecture
The invention relates to an intelligent contract execution optimization method based on a multi-core architecture. The method comprises two stages: 1) a parallel mining stage; 2) parallel verificationstage. According to the invention, aiming at two stages of intelligent contract execution, parallel mining and parallel verification strategies are respectively designed and implemented. In the parallel mining stage, the problems of frequent context switching of threads and blockage of read-write locks are solved by introducing Spinlock and MVCC; meanwhile, in the parallel verification stage, conflict transactions are grouped, and parallelization of the transactions is achieved through a double-end queue; the intelligent contract parallelization strategy provided by the invention provides a new solution for execution of the intelligent contract, also explores the restorability of the task execution sequence in a multi-thread environment, and has certain theoretical value and research significance for effectively solving the concurrency problem.
Owner:TIANJIN UNIV
System and method for promoting reader groups for lock cohorting
ActiveUS10042679B2Improve performancePromote formationSpecific access rightsResource allocationCritical sectionReader writer
Owner:ORACLE INT CORP
Dual mode reader writer lock
InactiveCN102792273AProgram control using stored programsProgram synchronisationData processing systemDual mode
A method, system, and computer usable program product for a dual mode reader writer lock. A contention condition is determined in using an original lock. The original lock manages read and write access to a resource by several processes executing in the data processing system. The embodiment creates a set of expanded locks for use in conjunction with the original lock. The original lock and the set of expanded locks forming the dual mode reader writer lock, which operates to manage the read and write access to the resource. Using an index within the original lock, each expanded lock is indexed such that each expanded lock is locatable using the index. The contention condition is resolved by distributing requests for acquiring and releasing the read access and write access to the resource by the several processes across the original lock and the set of expanded locks.
Owner:IBM CORP
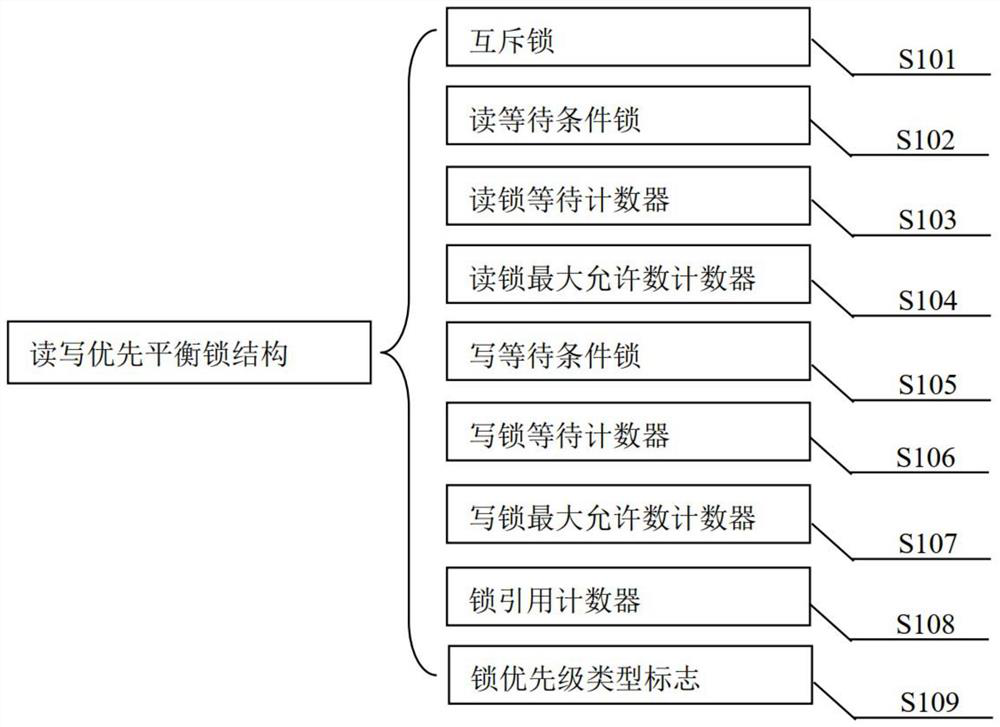
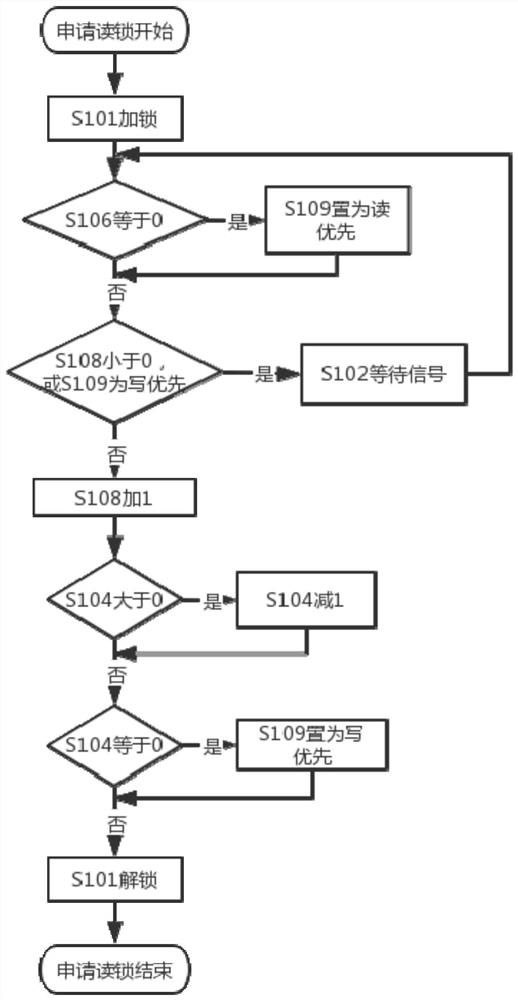
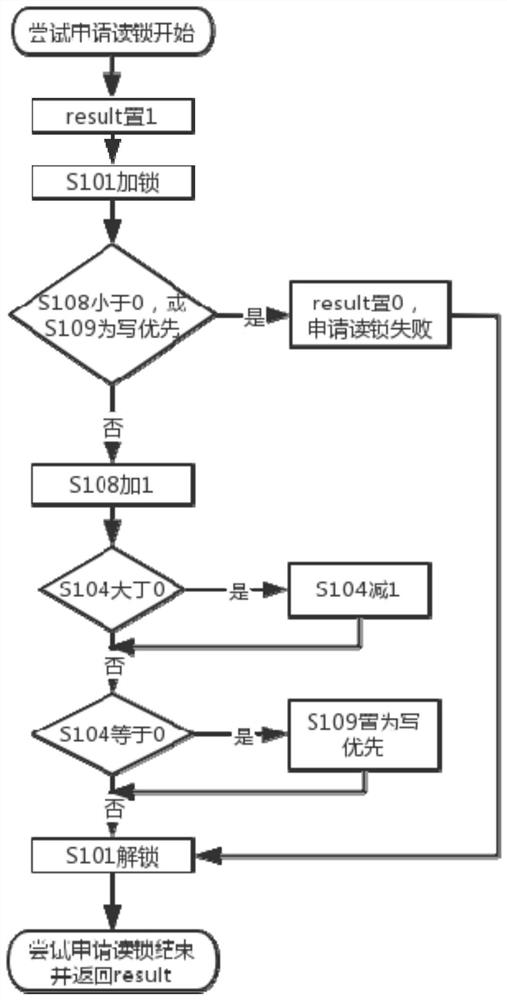
Data read-write priority balancing method, system and device and storage medium
PendingCN112416556ASolve the problem of deadlock easily caused by read and write starvationImprove read concurrency performanceProgram initiation/switchingProgram synchronisationEngineeringConcurrency
The invention discloses a data read-write priority balancing method, system and device and a storage medium. The method comprises the steps of: locking a data read-write request through a mutual exclusion lock; judging a read-write priority type mark of the current data according to a reference counter of the current data, wherein the read-write priority type mark comprises no read-write priority,read priority and write priority; judging read-write lock occupation conditions according to reference counters of variables corresponding to the read-write priority type marks, wherein the read-write lock occupation conditions include read lock occupation, write lock exclusive occupation and no lock occupation; obtaining a read-write priority type mark of the data according to the read-write lock occupation condition and the read-write lock maximum allowable number counter residual value; and unlocking the read-write operation of the request data through the mutual exclusion lock. Accordingto the method, the concurrency performance of data reading operation is improved, the system can run stably for a long time, the data high concurrency access performance is excellent, and a good economic effect is achieved in server software product application.
Owner:西安西热电站信息技术有限公司
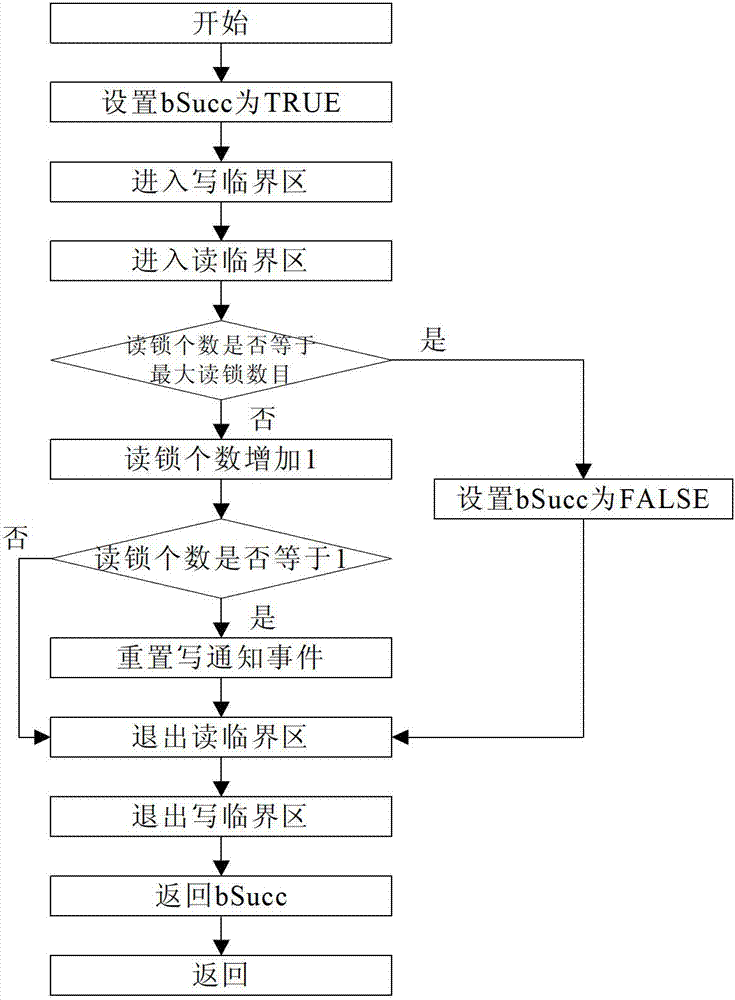
A method for implementing read-write lock
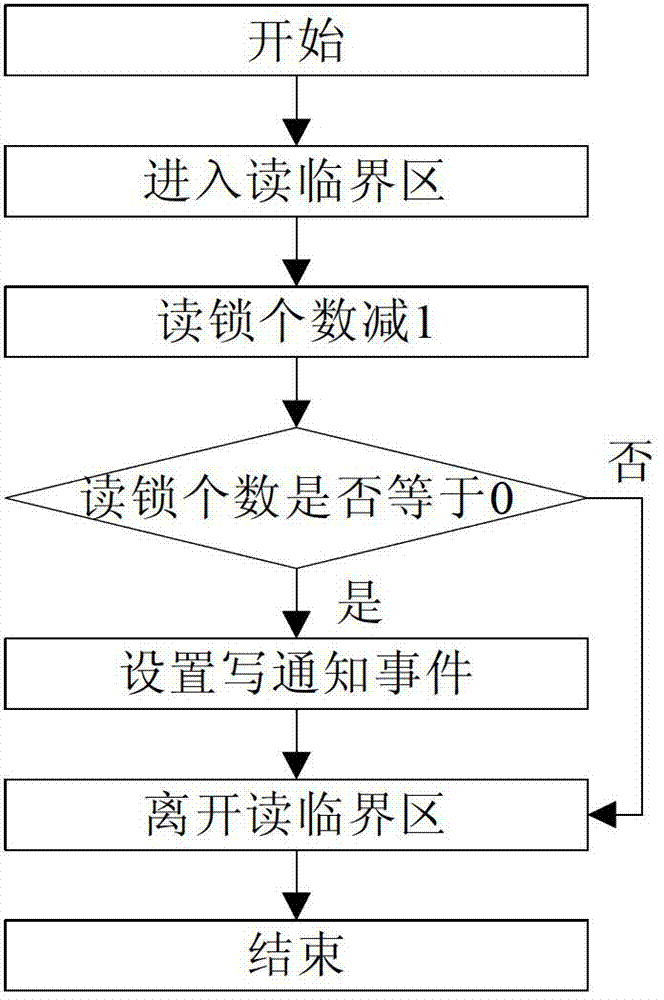
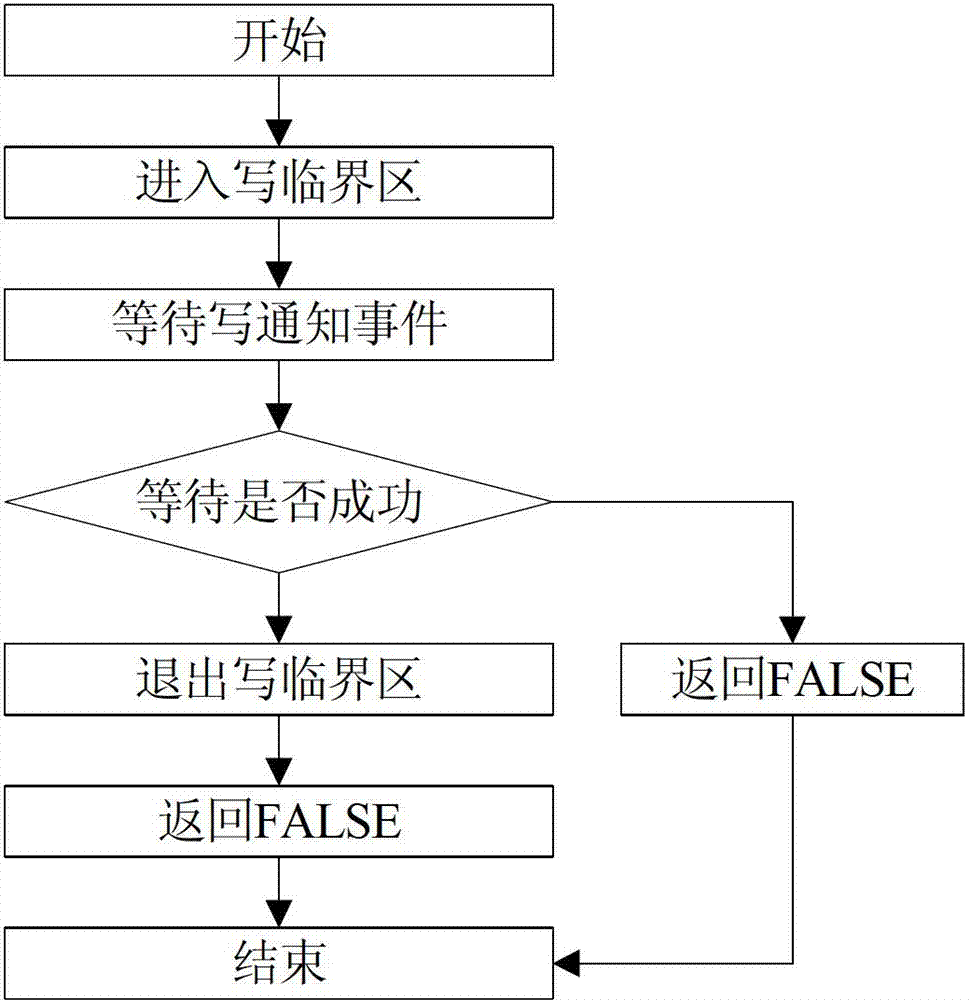
ActiveCN102999378BImprove performanceAvoid the overhead of frequent switchingMultiprogramming arrangementsCritical sectionCritical zone
The invention relates to a method for implementing synchronization among threads through a read-write lock. The method comprises the steps of: (1) initializing the read-write lock, initializing a read critical section and a write critical section to be at an enterable state and initializing a write notification event to be at a triggered state; (2) protecting critical codes in a shared resource according to the critical sections when a plurality of read threads and / or write threads concurrently access the shared resource, and setting the read-write lock; and (3) returning read-write lock information, and finishing the read-write lock setting to realize resource sharing. The method provided by the invention can implement the read-write lock by using the combination of the critical sections and the events, and has the advantages of being simple and easy to operate, light in load and high in speed. Meanwhile, the method can avoid the cost on frequently switching user states when a kernel mode object is used as the critical sections are taken as a main mutex tool; and the write threads do not need to wait infinitely and can access the shared resource after all of the read threads complete the operations when the lock write is applied, so as to prevent the condition that subsequent threads used for applying the read lock from occupies the shared resource, thereby greatly improving the performance of the read-write lock.
Owner:INST OF SOFTWARE - CHINESE ACAD OF SCI
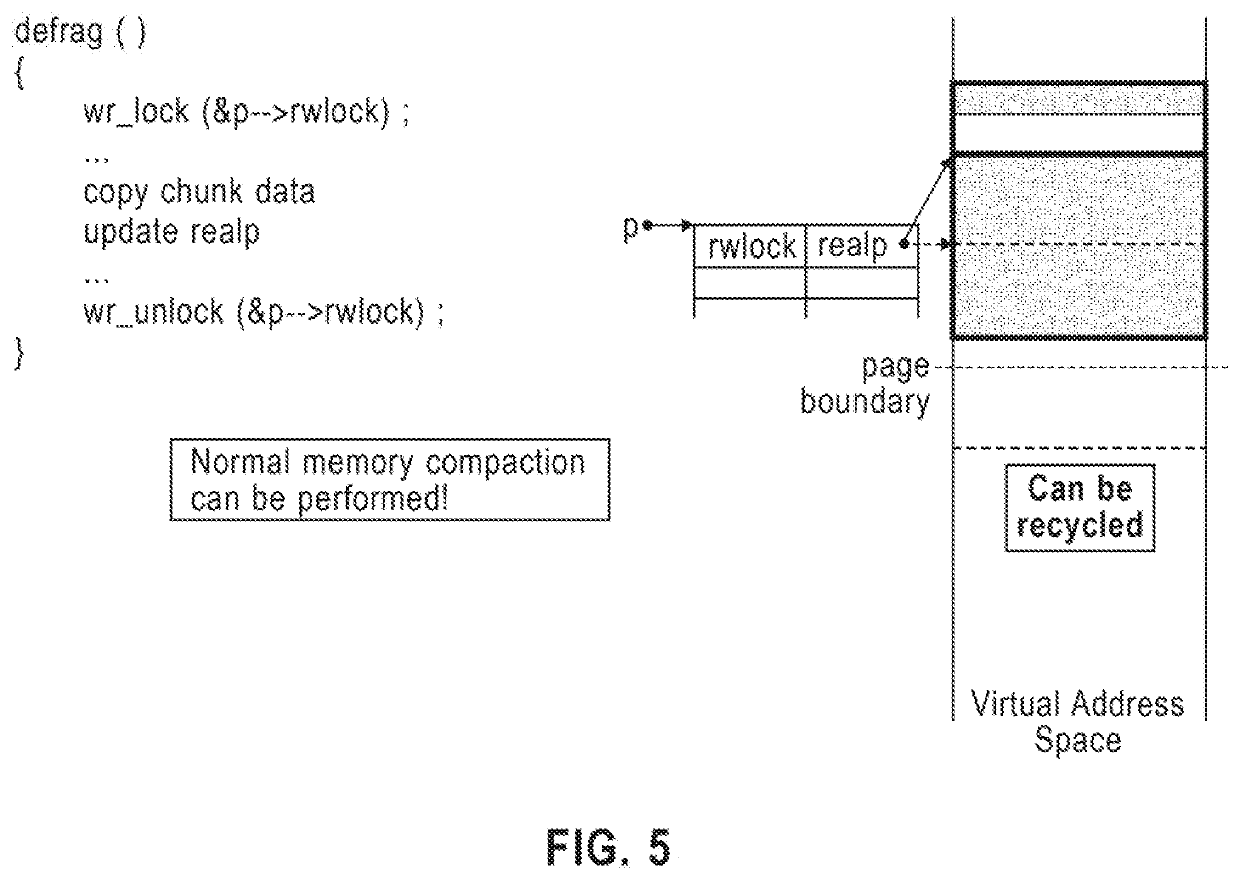
Reducing fragmentation of computer memory
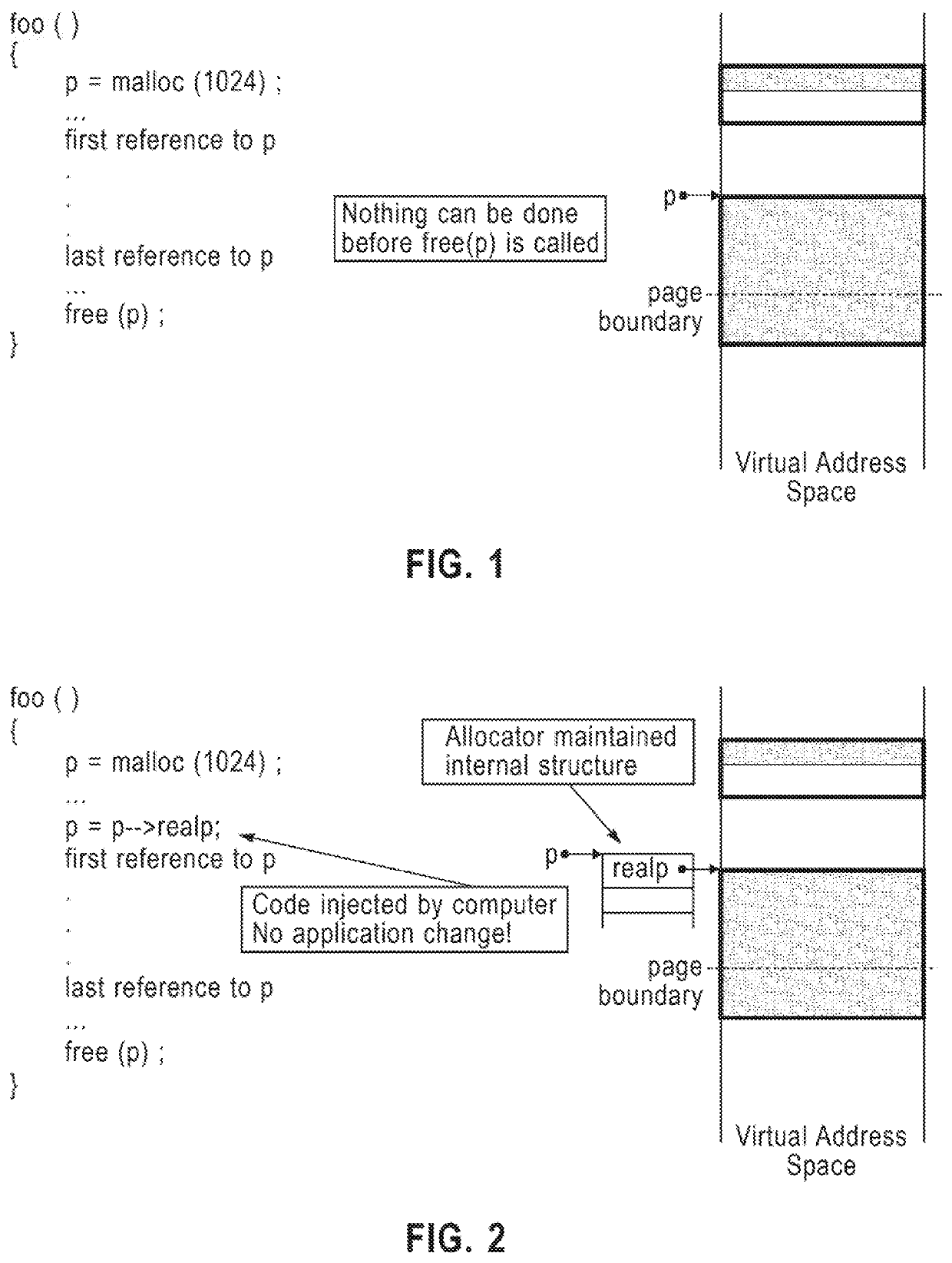
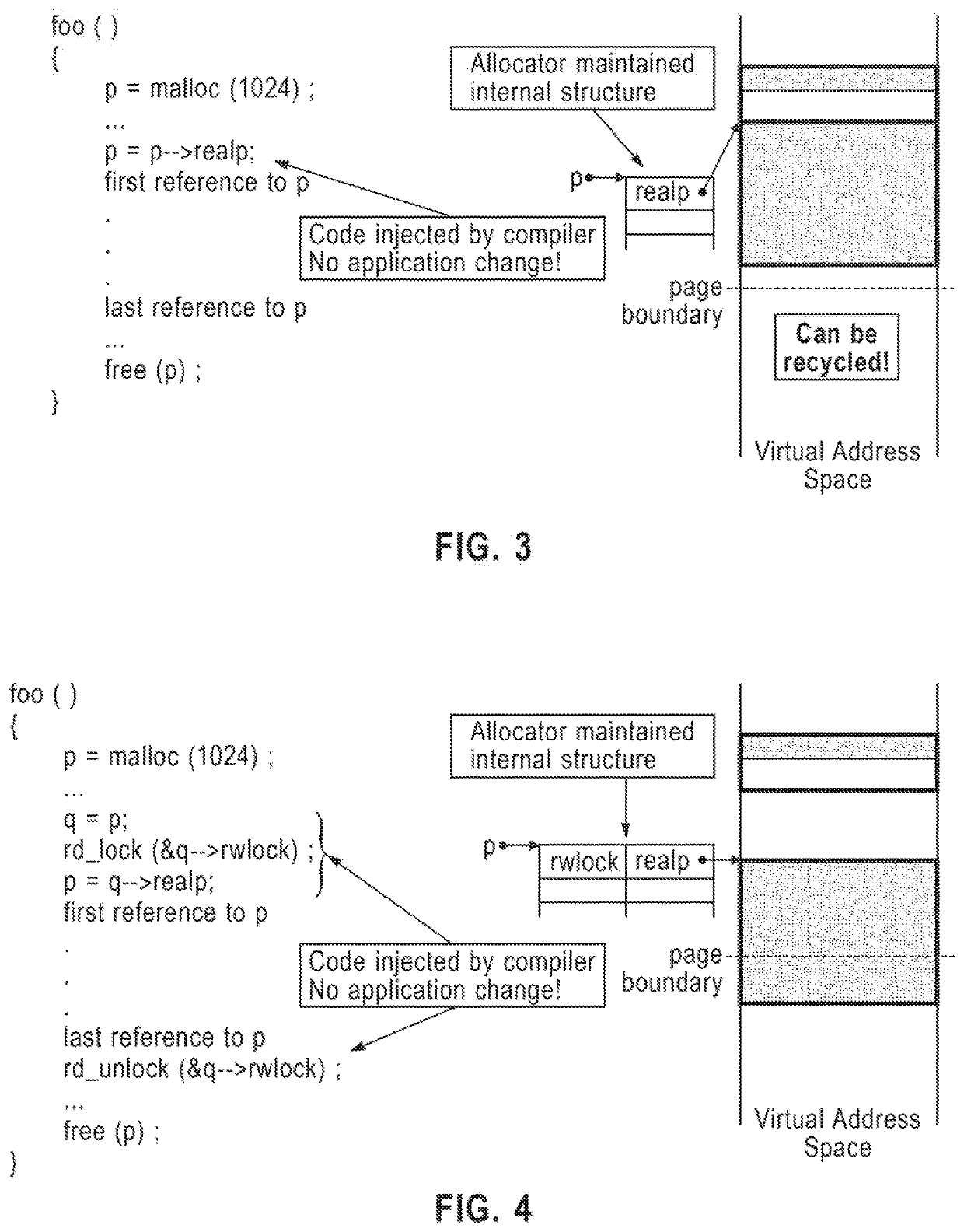
ActiveUS20200409833A1Reduce internal fragmentationReduce fragmentationMemory adressing/allocation/relocationCode compilationShardComputer architecture
A method for transparently moving a block of memory with respect to an application using the block of memory, includes inserting, by a compiler, in an application that includes a memory allocation call, instructions for transparently moving a block of memory with respect to an application using the block of memory. The instructions include obtaining a first pointer returned by a memory allocator, where the first pointer points to an internal data structure, the internal data structure includes a read-write lock and a second pointer, and the second pointer points to an actual memory block. The instructions further include acquiring a read lock on a read-write lock in the internal data structure, before the first pointer is used by the application, obtaining the second pointer to the actual memory block, and dereferencing the second pointer to access the actual memory block for the application data.
Owner:IBM CORP
Database transaction processing method and system based on optimistic lock, computing equipment and computer readable storage medium
ActiveCN114217978AReduce releaseAvoid the problem of endless redoDigital data information retrievalResource allocationParallel computingEngineering
The invention provides a database transaction processing method and system based on an optimistic lock, computing equipment and a computer readable storage medium. In the method, through a mode of combining an optimistic lock and a read-write lock, not only is the problem of data deadlock in a pessimistic lock avoided, but also when it is found that a lock needed after transaction redoing is changed, a minimum lock adjustment strategy is used for minimizing competition, under the condition that it is guaranteed that deadlock is not generated, the locks are released as few as possible, the probability of conflicts is reduced, and the method is suitable for popularization and application. Therefore, a series of problems caused by frequent transaction redoing are avoided.
Owner:在线途游(北京)科技有限公司 +1
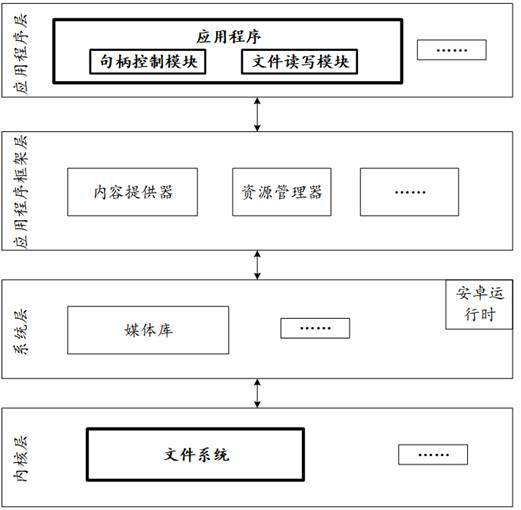
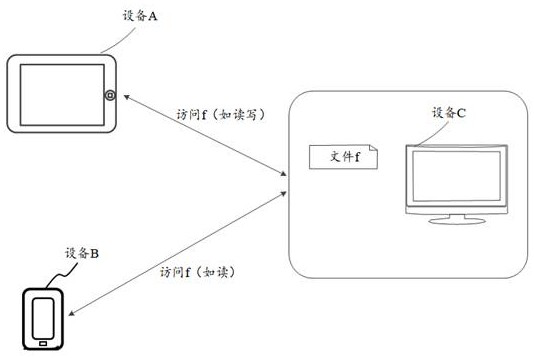
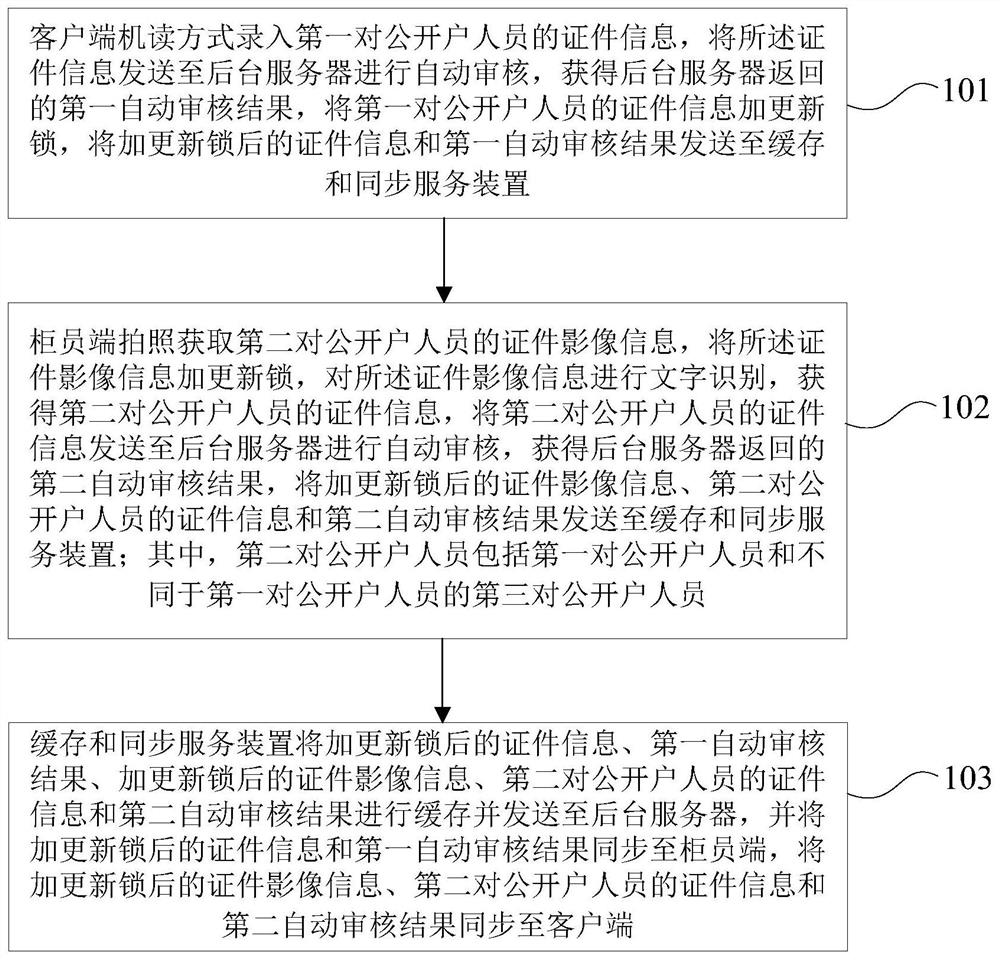
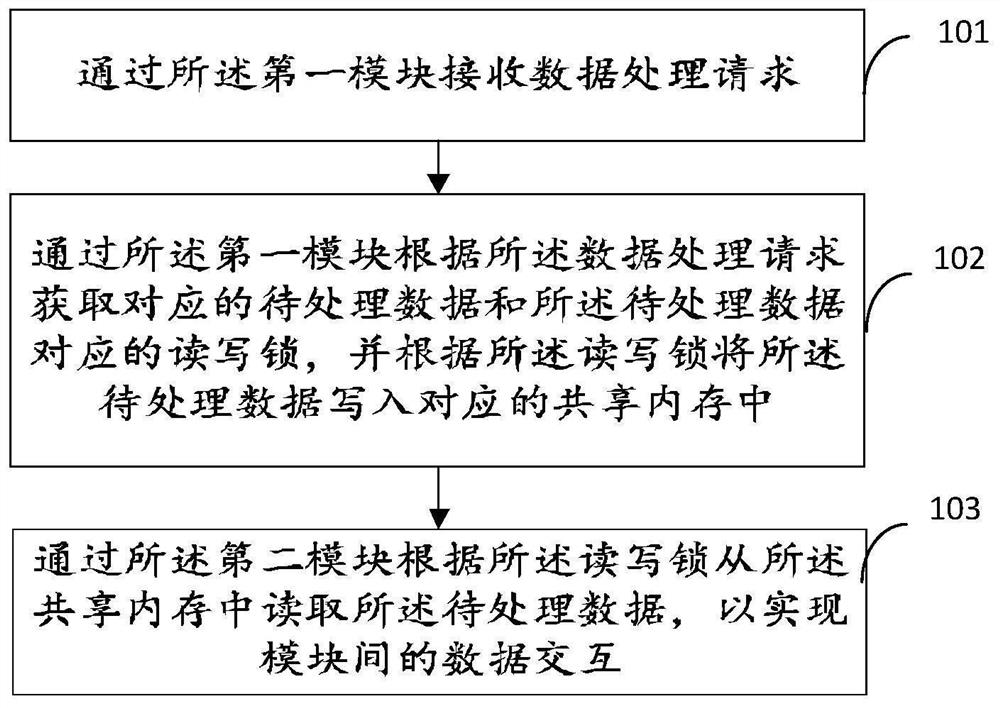
File access method, electronic equipment and readable storage medium
The invention discloses a file access method, electronic equipment and a readable storage medium, and belongs to the technical field of terminals. The method comprises the following steps: receiving a read-write operation of a second electronic device on a file based on a temporary modification file, wherein the temporary modification file comprises to-be-modified and / or modified contents in the file; receiving an access request of third electronic equipment to the file, wherein the access request carries indication information of the access mode and the first file piece information; Under the condition that the indication information indicates the read-only mode, if the temporary modification file comprises the first file piece indicated by the first file piece information and the first file piece is modified, reading the first file piece from the temporary modification file; and sending the read first file piece to the third electronic equipment. According to the method, access operations such as read-write and reading are carried out based on the temporarily modified file, a read-write lock mechanism does not need to be added, and access of multiple pieces of electronic equipment to the file at the same time is achieved.
Owner:HONOR DEVICE CO LTD
Preplaying transactions that mix hot and cold data
Methods and systems for performing database transactions include executing a first transaction request in a preplay mode that locks the requested data with a prefetch-lock and reads one or more requested data items from storage into a main memory buffer; locking the requested data items with a read / write lock after said data items are read into the main memory buffer; and performing the requested transaction on the data items in the main memory buffer using a processor.
Owner:INT BUSINESS MASCH CORP
R-tree index optimization method based on multi-granularity distributed read-write locks based on leaf nodes
ActiveCN109582678BSmall granularityReduce query efficiencyDatabase indexingComputational scienceTheoretical computer science
The invention provides an R-tree index optimization method based on multi-granularity distributed read-write locks of leaf nodes. After the leaf node is locked, the head element of the lock waiting queue acquires the lock, and when the update operation causes the R-tree index structure to change, other elements in the lock waiting queue cannot continue to acquire locks at the leaf node, and the nodes of these locks are temporarily Delete to make it execute the query operation again from the root node to ensure the correctness of the result. Read-write locks are established on leaf nodes, which reduces the granularity of locks, supports a higher degree of parallelism, and improves the execution efficiency of operations such as queries and updates.
Owner:NORTHEASTERN UNIV LIAONING
A method, device, equipment and storage medium for mixed reading and writing of ssd
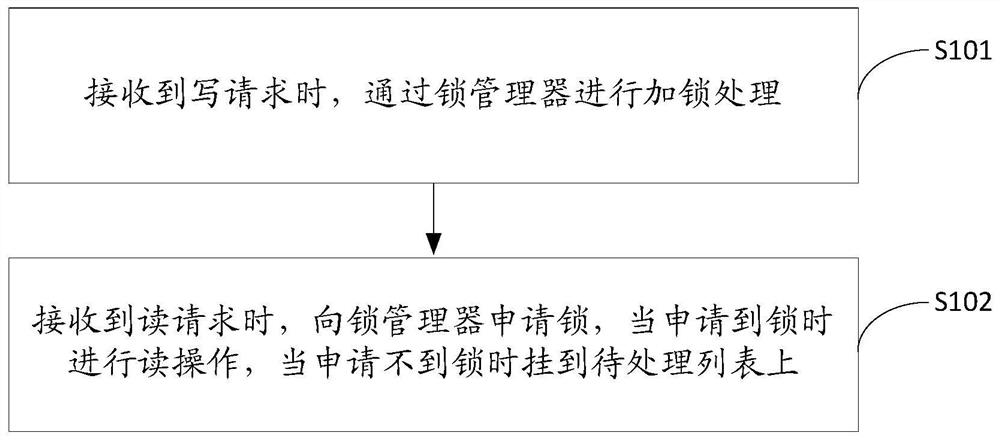
ActiveCN109739443BRealize reading, writing and unlockingGuaranteed atomicityInput/output to record carriersComputer hardwareLock manager
The present application discloses a method, device, device, and storage medium for mixed reading and writing of SSDs. The method includes: when a write request is received, lock processing is performed through a lock manager; when a read request is received, an application is made to the lock manager Lock, when the lock is applied for, the read operation is performed, and when the lock is not applied for, it is hung on the pending list. This application uses a special lock manager to manage read-write locks, which can realize read-write and unlock in the IO process, ensure the atomicity of writing in mixed reading and writing, and ensure the correctness of data during mixed reading and writing. In addition, due to the use of Managed by a dedicated lock manager, which can reduce IO latency.
Owner:ZHENGZHOU YUNHAI INFORMATION TECH CO LTD
Data interaction method and device of vehicle-mounted ATO and vehicle-mounted ATP
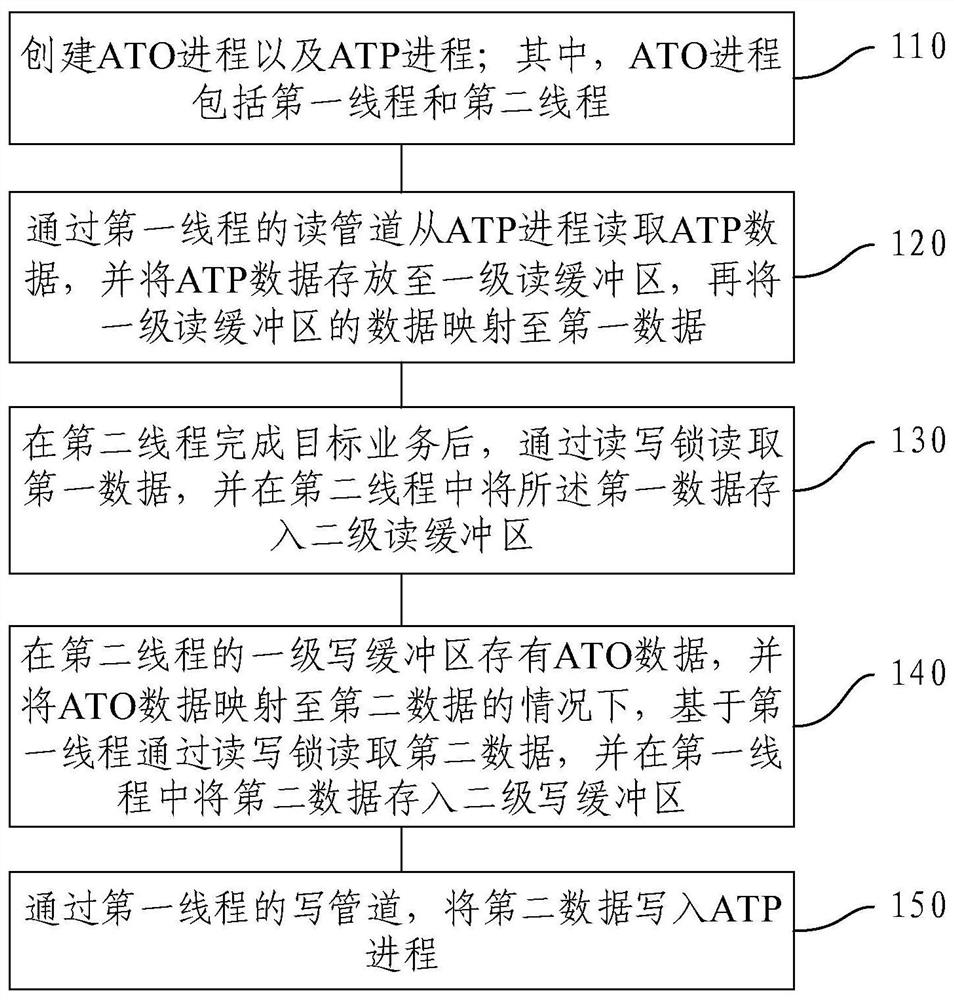
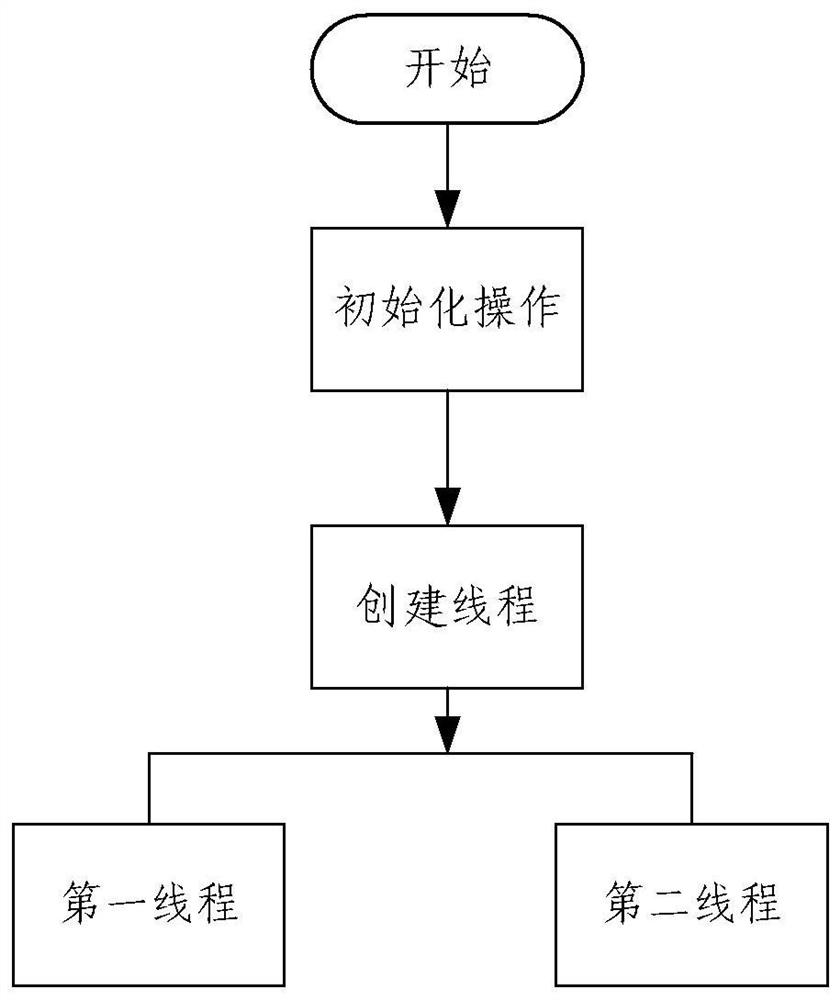
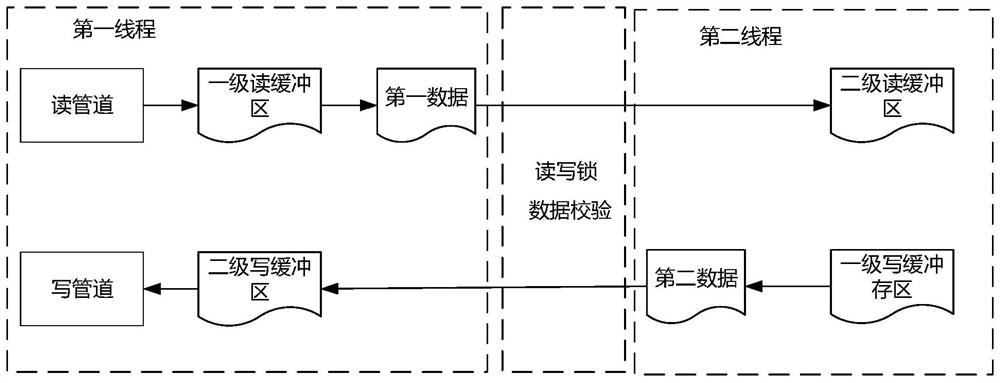
PendingCN113641306ASolve misalignmentAccurate speedInput/output to record carriersWrite bufferIn vehicle
The invention provides a data interaction method and device for a vehicle-mounted ATO and a vehicle-mounted ATP. The method comprises the steps of creating an ATO process and an ATP process, wherein the ATO process comprises a first thread and a second thread; reading ATP data through a reading pipeline, storing the ATP data in a first-level reading buffer area, and mapping the data in the first-level reading buffer area to first data; after the second thread completes the target service, reading the first data through the read-write lock, and storing the first data in a second-level read buffer area; reading second data through a read-write lock based on the first thread under the condition that ATO data is stored in a first-level write buffer area of a second thread and the ATO data is mapped to the second data, and storing the second data in a second-level write buffer area; and writing the second data into the ATP process through a writing pipeline of the first thread. According to the method, the train-mounted ATO can obtain accurate train speed information and position information in real time, and accurate control over the train is achieved.
Owner:通号城市轨道交通技术有限公司
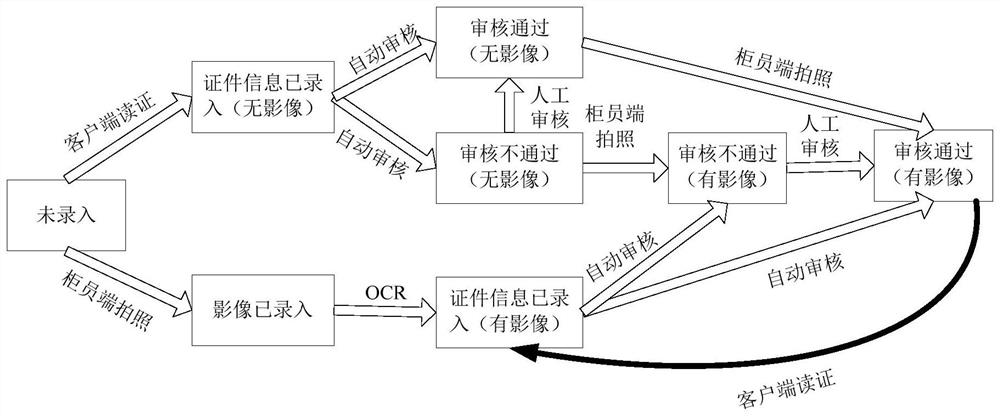
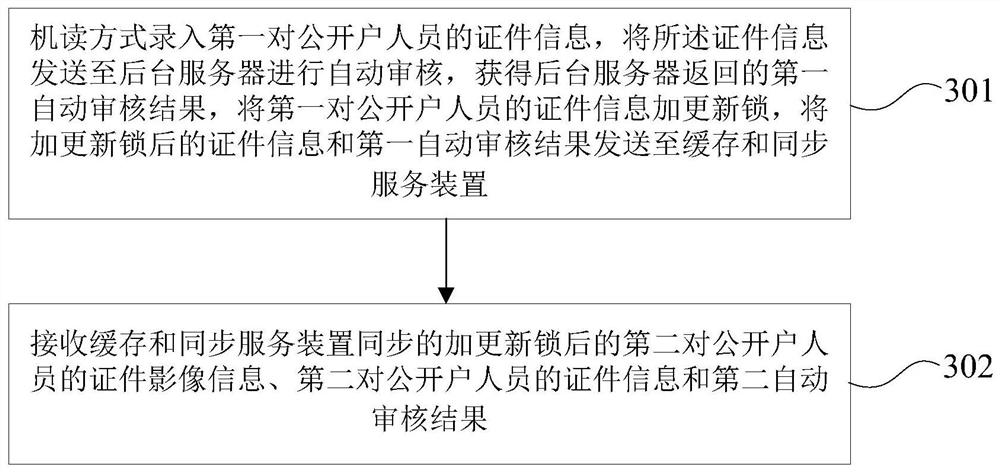
Certificate information parallel entry method, device and system based on read-write lock mechanism
PendingCN112037040AShorten the timeImprove input speedFinanceCharacter and pattern recognitionText recognitionLocking mechanism
The invention discloses a certificate information parallel input method, device and system based on a read-write lock mechanism, and the method comprises the steps: enabling a client to input the certificate information of a first pair of public persons in a mode of machine reading, transmitting the certificate information to a background server for automatic auditing, and returning a first automatic auditing result; after the certificate information is added with the updating lock, sending the certificate information and the first automatic auditing result to a cache and synchronization service device, and synchronizing thethe certificate information and the first automatic auditing result to a teller side by the cache and synchronization service device; enabling the teller terminal to take a picture to obtain certificate image information of a second pair of public users, send the certificate image information to the background server for automatic auditing, return a second automaticauditing result, and perform character recognition on the certificate image information to obtain certificate information; and sending the certificate image information with the updating lock, the certificate information of the second pair of public user personnel and a second automatic auditing result to a cache and synchronization service device, and synchronizing the certificate image information, the certificate information of the second pair of public user personnel and the second automatic auditing result to the client by the cache and synchronization service device. According to the invention, the time of the whole process of public users can be shortened.
Owner:BANK OF CHINA
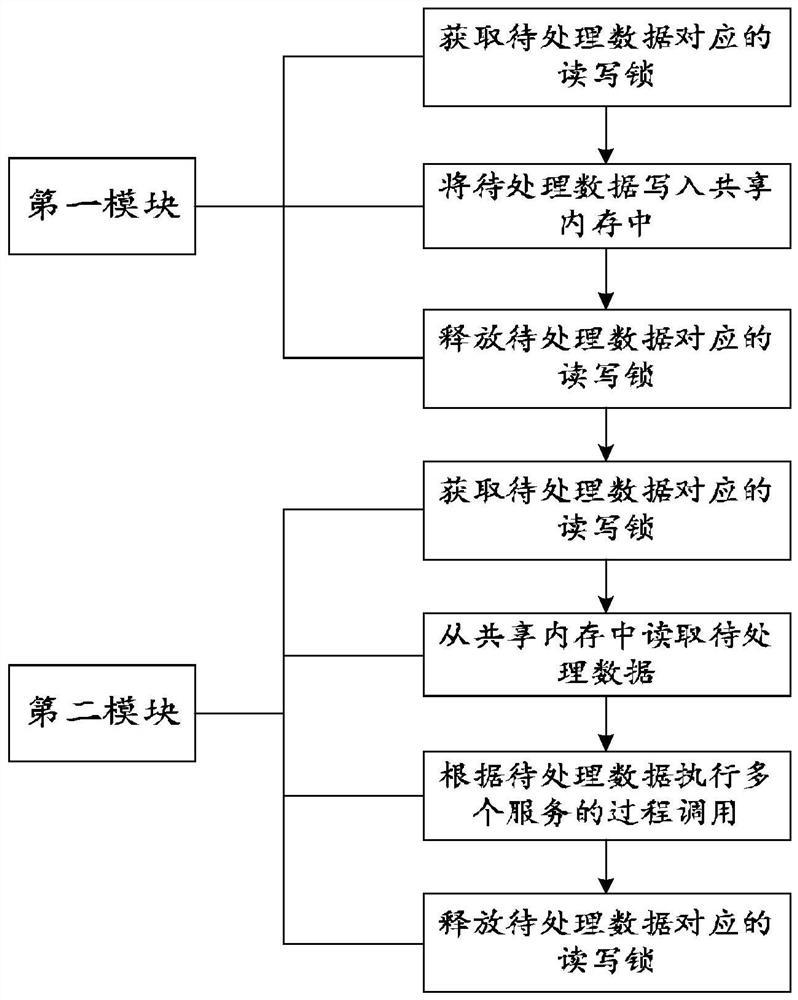
Module data interaction method of robot, electronic equipment and storage medium
ActiveCN113535437AGuaranteed reliabilityImprove interaction efficiencyInterprogram communicationEmbedded systemShared memory
The invention provides a module data interaction method of a robot, electronic equipment and a storage medium. The robot comprises a first module and a second module. The method comprises the following steps: receiving a data processing request through the first module; acquiring corresponding to-be-processed data and a read-write lock corresponding to the to-be-processed data through the first module according to the data processing request, and writing the to-be-processed data into a corresponding shared memory according to the read-write lock; and reading the to-be-processed data from the shared memory through the second module according to the read-write lock so as to realize data interaction between the modules. The read-write operation of the to-be-processed data is completed through the shared memory and the read-write lock, so that the data interaction among multiple modules of the robot is realized, the transmission delay in the data interaction process is reduced, and the real-time performance of the system is improved.
Owner:SHANGHAI JIEKA ROBOT TECH CO LTD
Time slot scanning anti-collision method based on collision precheck
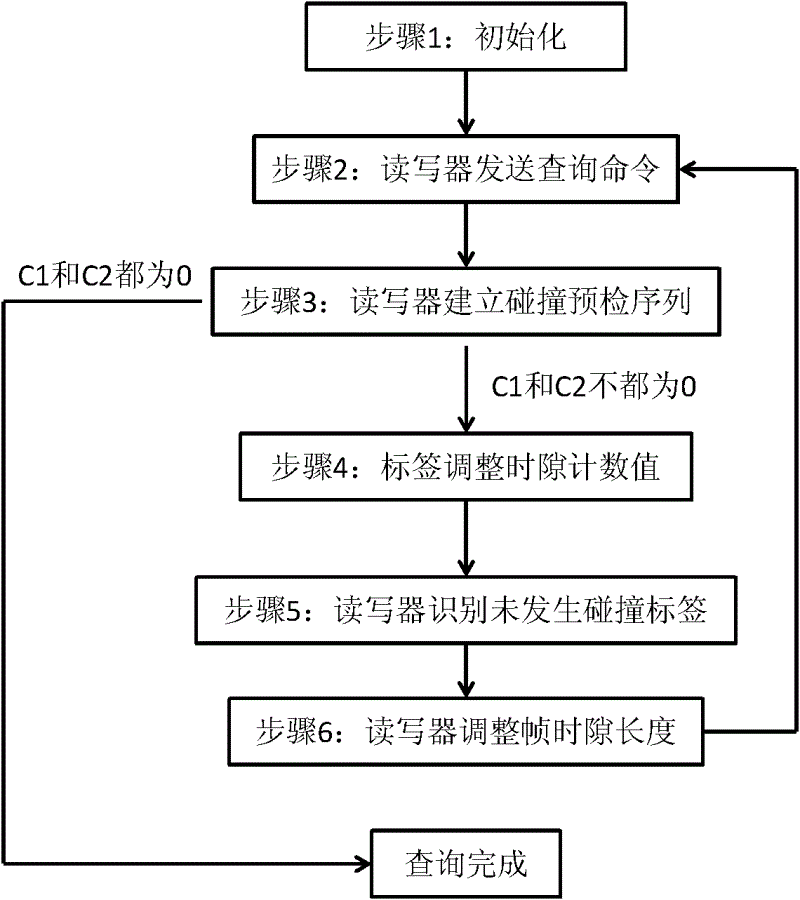
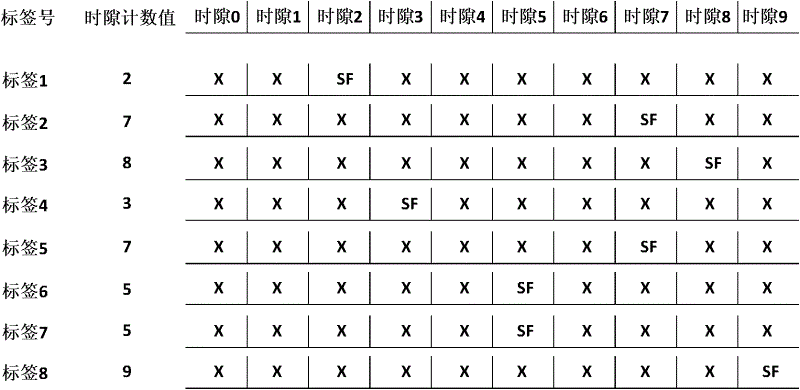
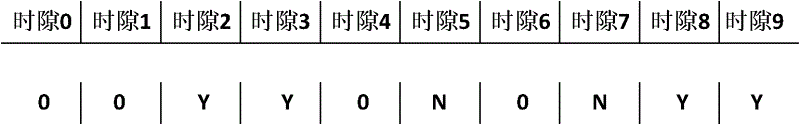
ActiveCN102004895BImprove communication efficiencyImprove efficiencyCo-operative working arrangementsSensing record carriersIdle timeCollision detection
The invention provides an anti-collision method used in a radio-frequency identification system for realizing the communication between a single reader writer and multiple tags. The technical scheme comprises the following six steps: 1, initialization is carried out; 2, the reader writer sends an inquiry command; 3, the reader writer establishes a collision precheck sequence; 4, the tags adjust the time slot count value; 5, the reader writer identifies tags not subjected to collision; and 6, the reader writer adjusts the frame time slot length. By combining the empty time slot scanning technology and the short-frame collision detection technology, the invention omits the check of the reader writer on idle time slots and time slots occupied by the multiple tags, thereby improving the multi-tag identification efficiency of the system.
Owner:NAT UNIV OF DEFENSE TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com