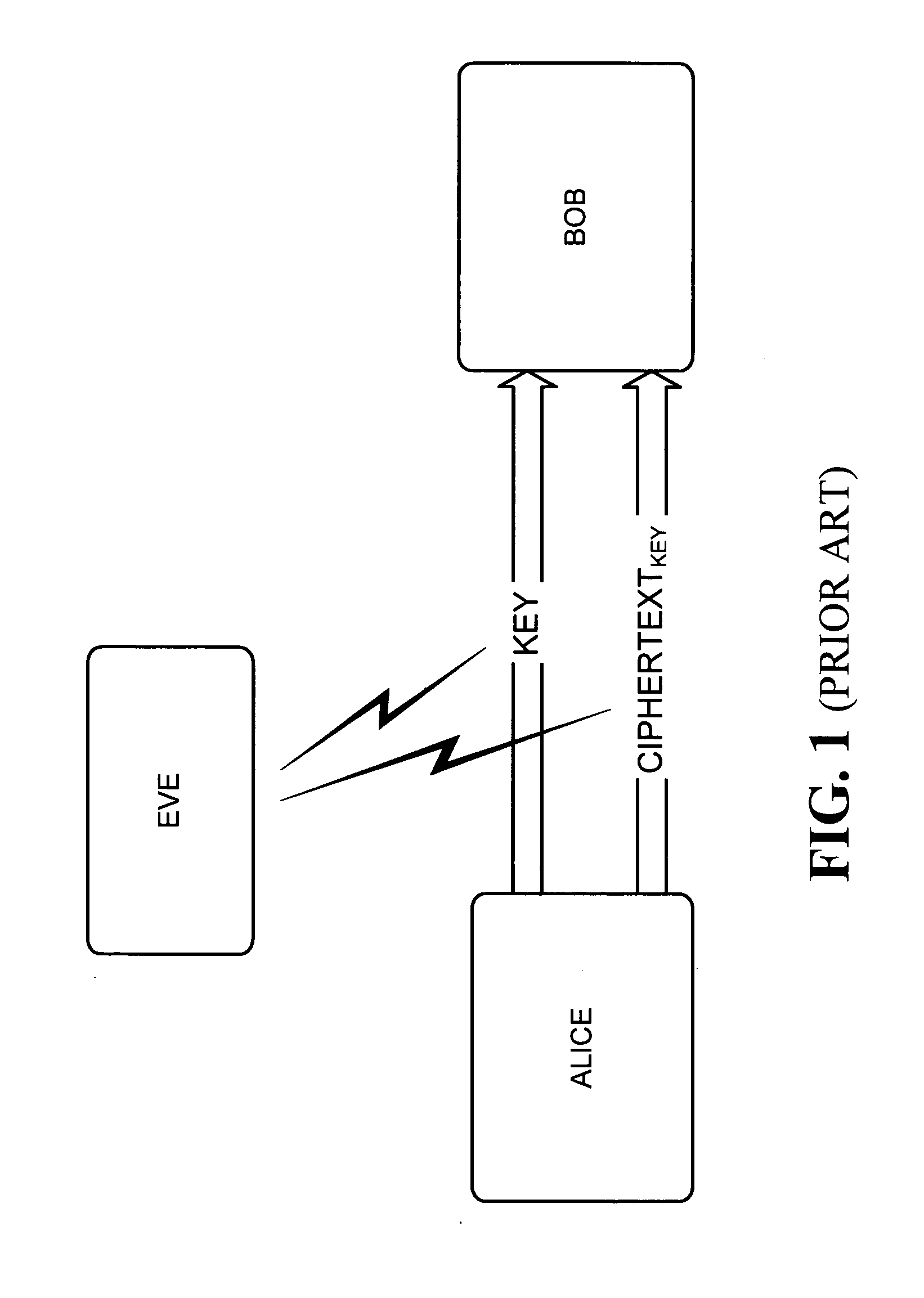
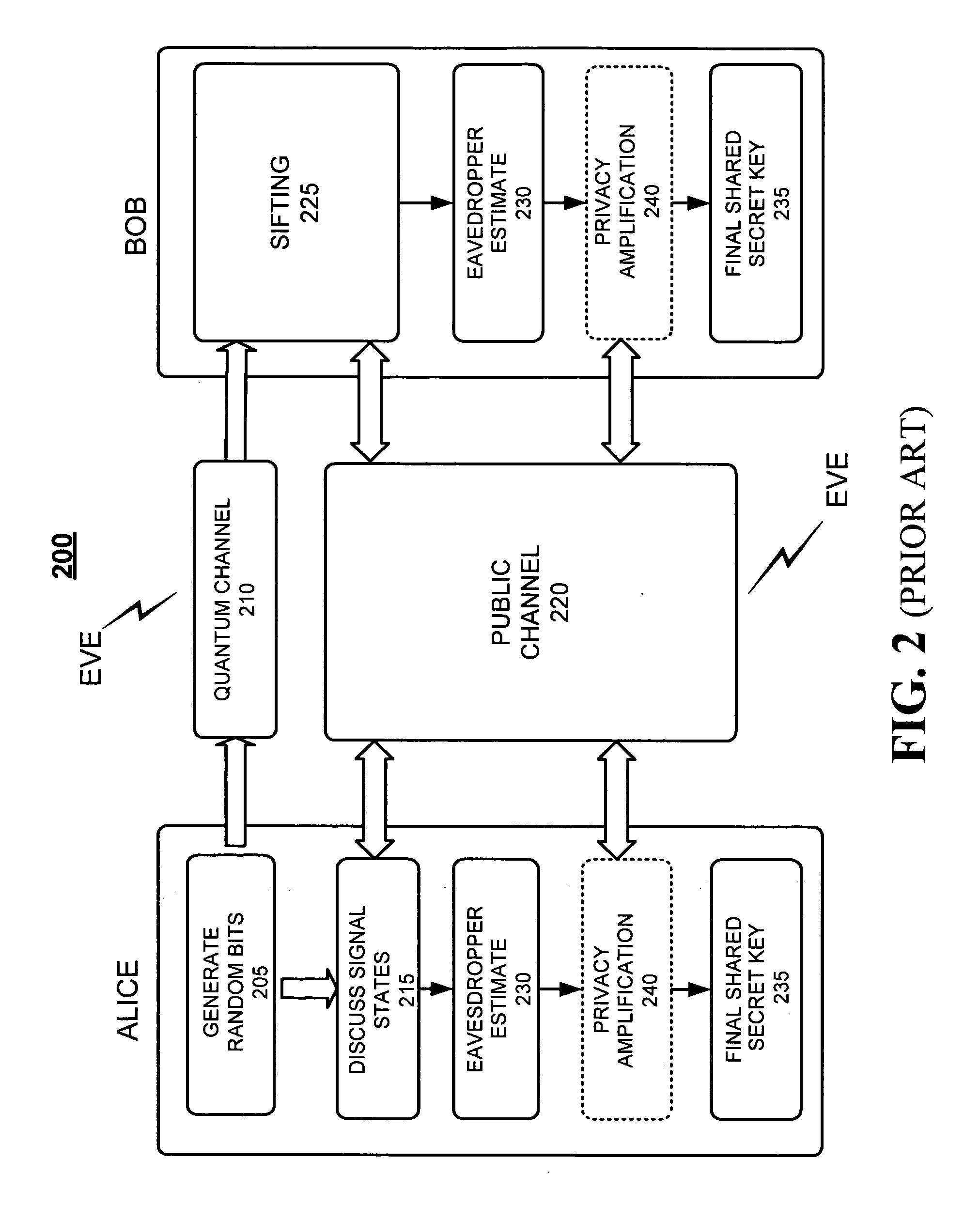
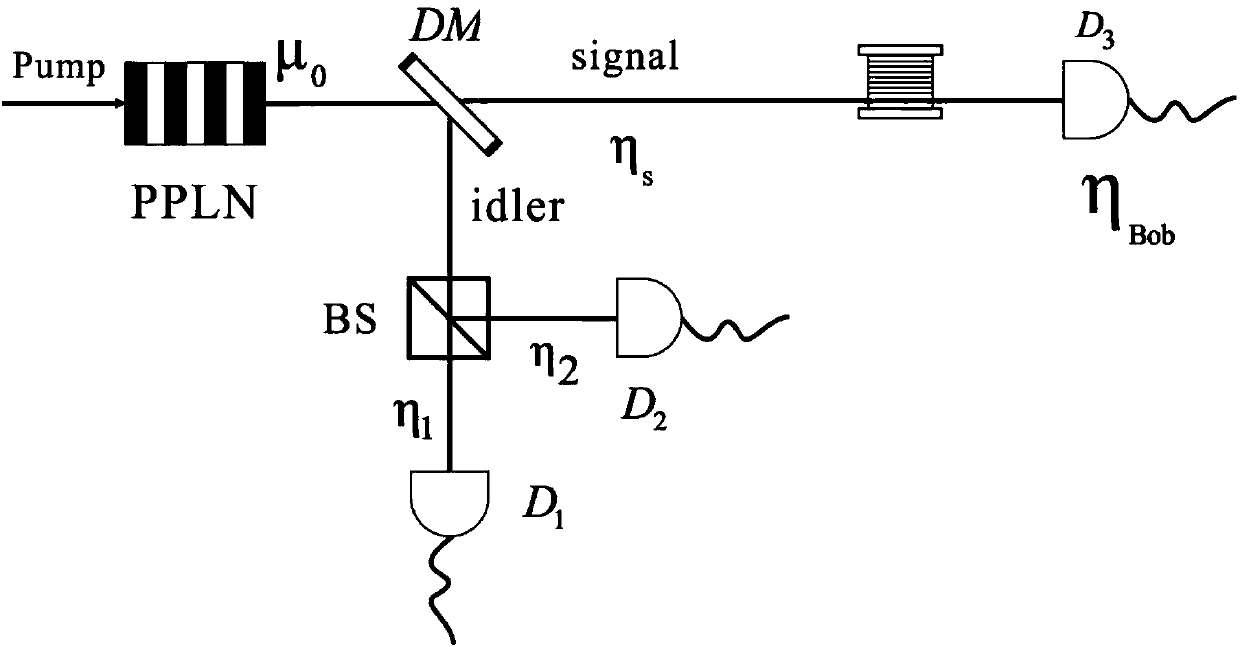
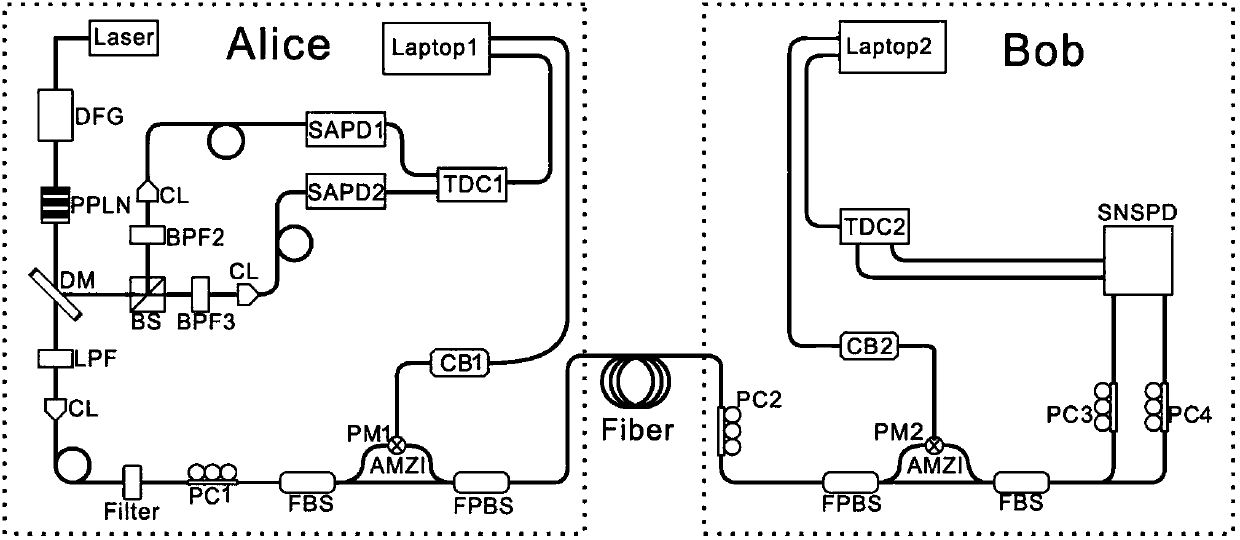
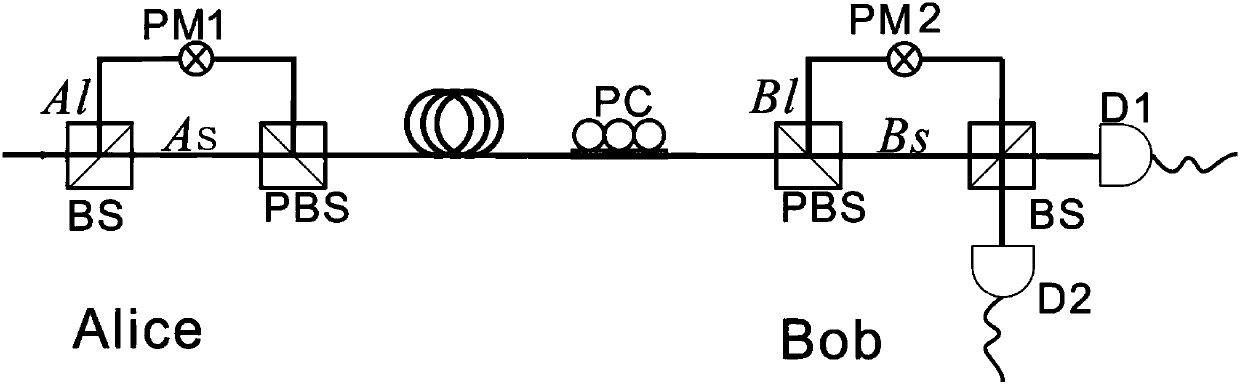
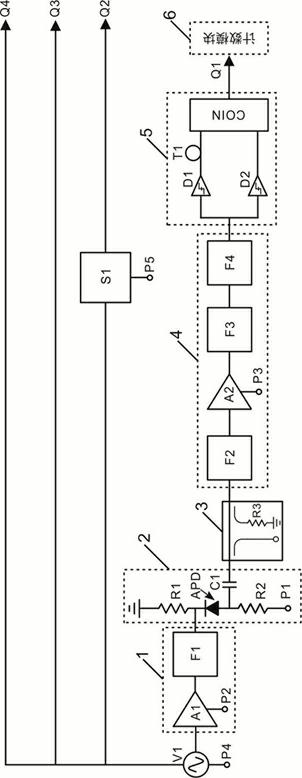
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
116 results about "Quantum codes" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
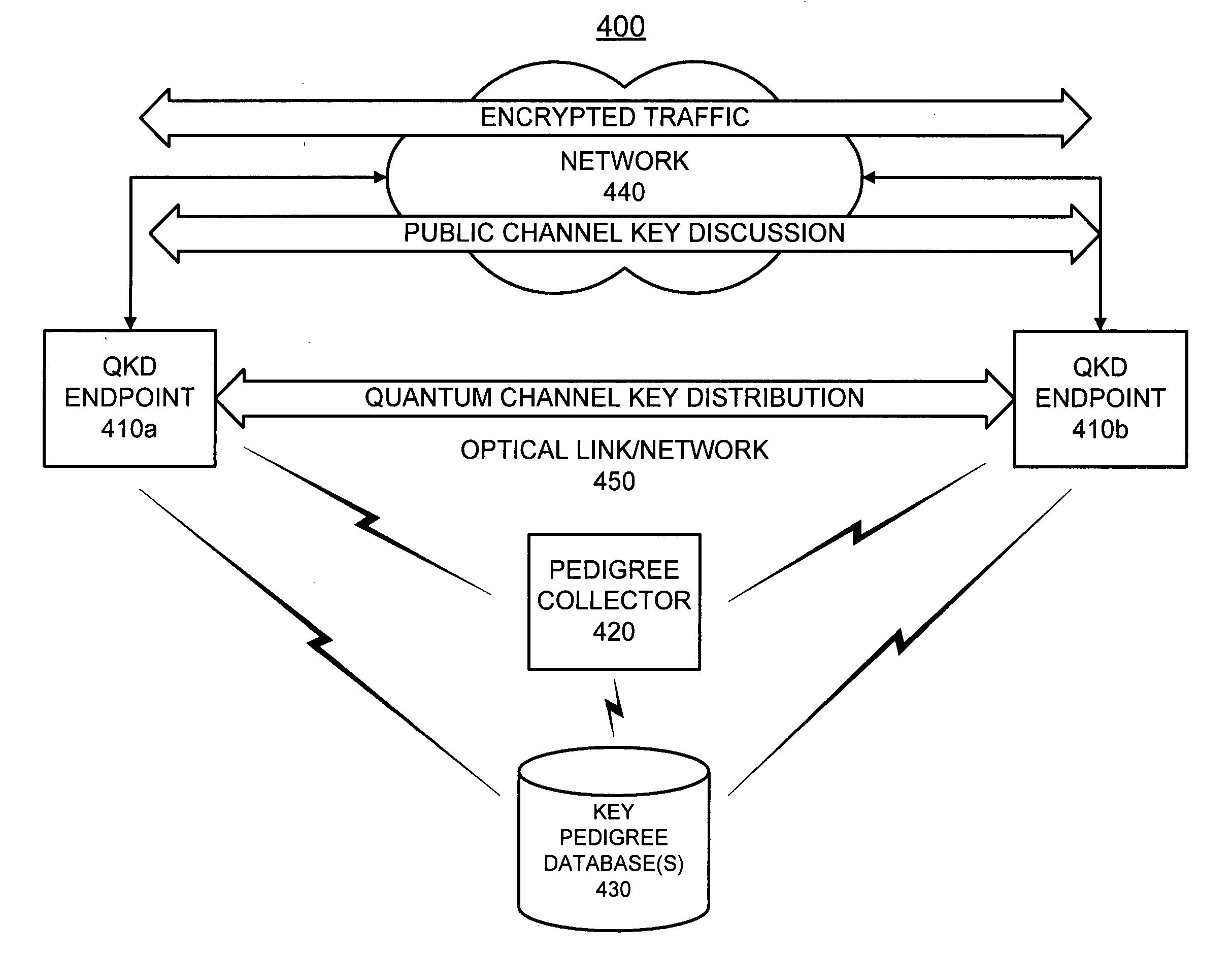
Pedigrees for quantum cryptography
ActiveUS20070192598A1Key distribution for secure communicationUser identity/authority verificationQuantumInformation system
A system stores pedigrees that include details of how and when each of multiple blocks of encryption key material were distributed between two endpoints using quantum cryptographic techniques. The system receives an indication of a possible quantum cryptographic security violation and accesses the stored pedigrees to identify one or more of the multiple blocks of encryption key material that may have been compromised.
Owner:RAYTHEON BBN TECH CORP
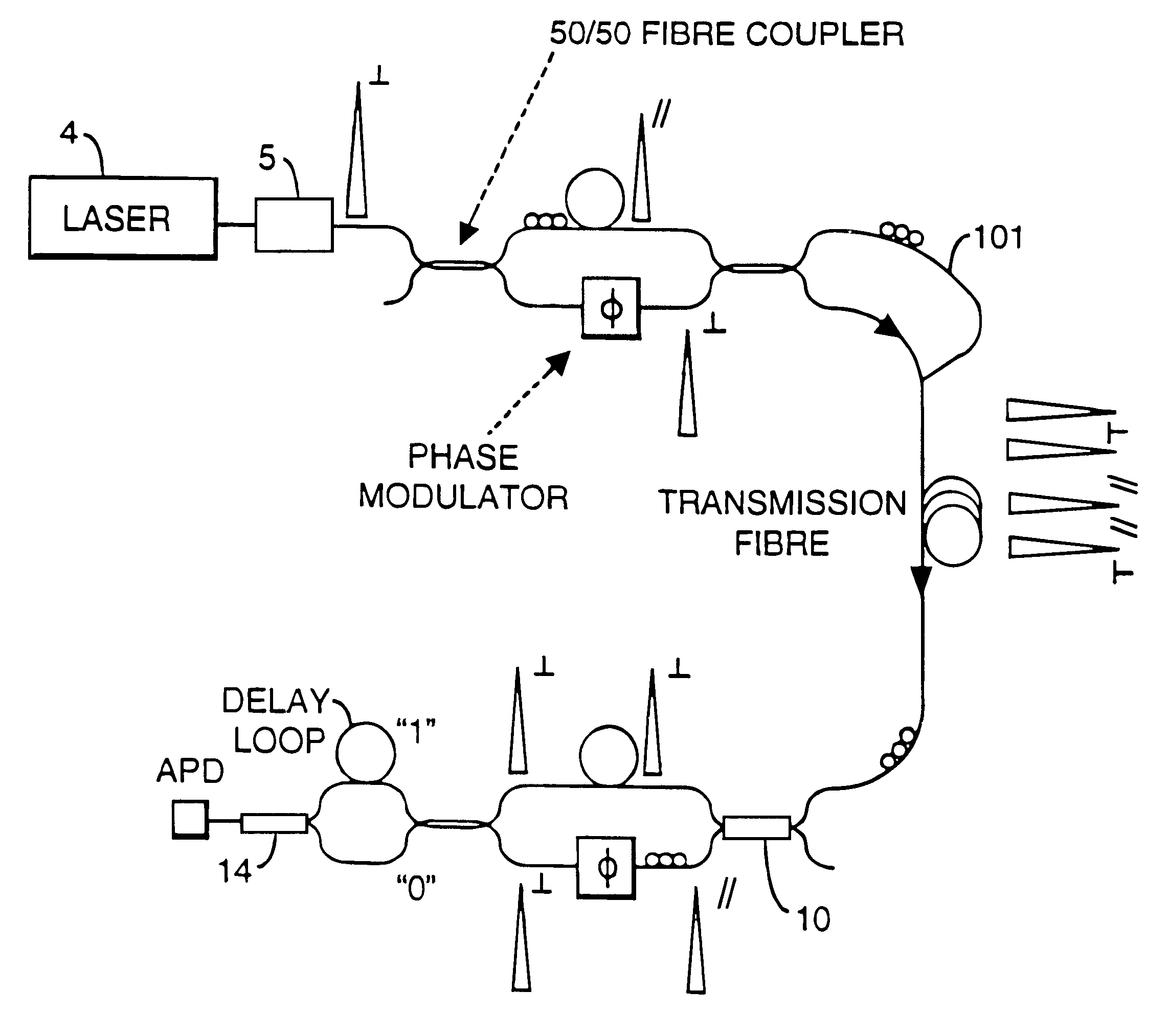
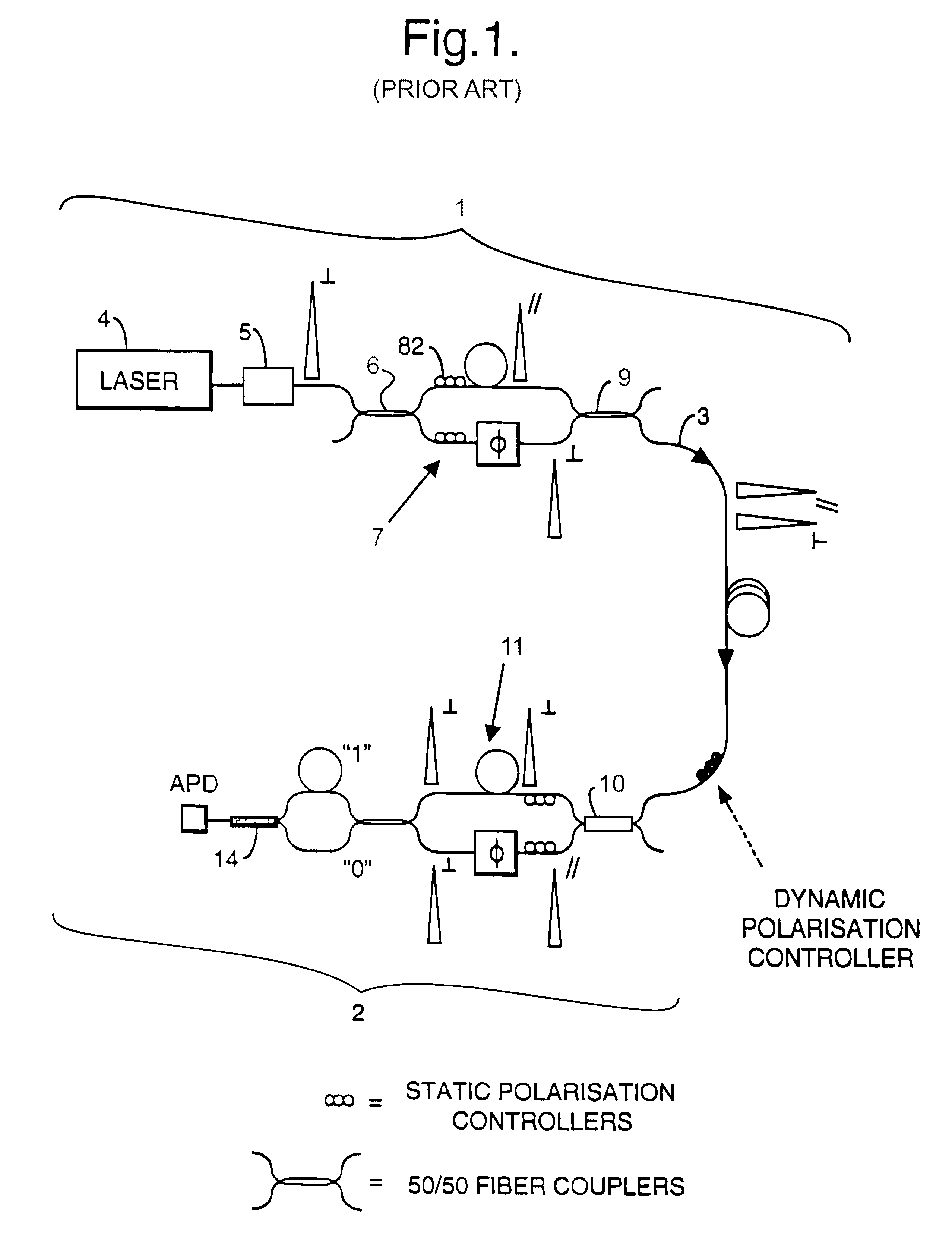
Method and apparatus for polarization-insensitive quantum cryptography
InactiveUS6529601B1Key distribution for secure communicationSynchronising transmission/receiving encryption devicesCommunications systemSingle polarization
A communication system uses quantum cryptography for the secure distribution of a key. A single-photon signal is phase-modulated and transmitted over a pair of time-multiplexed transmission paths. With each original single-photon signal in a given one of the transmission paths, a duplicate signal is transmitted. The duplicate is identically modulated and orthogonally polarized. At the receiver, the outputs of the two paths are combined interferometrically. A single polarization-insensitive measurement is derived from the combined contributions of the orthogonally polarized signals.
Owner:BRITISH TELECOMM PLC
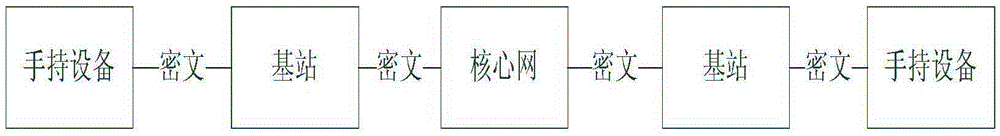
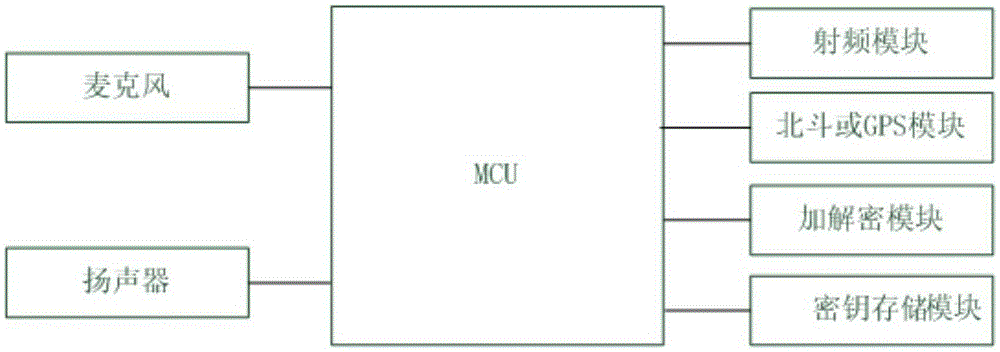
End-to-end hand-held device encryption method based on quantum cryptography and system
InactiveCN105337726AImprove securityIncrease independenceKey distribution for secure communicationHand heldHand held devices
The invention discloses an end-to-end hand-held device encryption method based on quantum cryptography and a system. The encryption method comprises following steps of storing quantum keys; initiating a call; synchronizing the quantum keys; performing synchronous confirmation; answering the call; and performing encryption communication. In the encryption communication, an MCU of a main calling end injects quantum communication keys Ksa into an encryption and decryption model; an MCU of a called end injects the quantum communication keys Ksa into the encryption and decryption model; the MCU of the called end using the quantum communication keys to encrypt the data; the encrypted data is sent out via a radio frequency module of the called end; a radio frequency module of the main calling end injects the received encrypted data into the encryption and decryption model for decryption; and after being decrypted, the data is played by a loudspeaker of the main calling end or displayed via a touch type display. The invention also discloses an end-to-end hand-held device encryption system based on quantum cryptography. The encryption method and system are highly safe, independent and easy, quick and simple to deploy.
Owner:ANHUI QASKY QUANTUM SCI & TECH CO LTD
Phase-differential quantum key allocation and allocating system
InactiveCN1897519AHighlight substantiveSignificant progressKey distribution for secure communicationDifferential phaseBeam splitting
The invention manages to provide a stable and fast differential quantum key distribution method and system thereof. At transmitting end, with a continuous laser source, the quantum codes are prepared using two approaches: 1) using the beam-splitting, polarization-independent and phase-stabilizing approach to prepare the stable quantum code; 2) using polarization approach to directly prepare stable quantum code. At receiving end,differential phase-Faraday-Micheal test approach is used to directly receive the quantum information.
Owner:SOUTH CHINA NORMAL UNIVERSITY
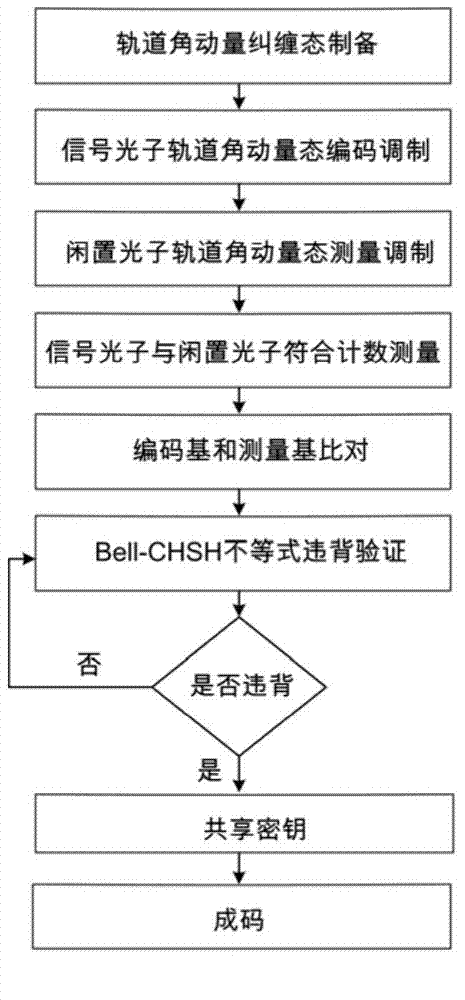
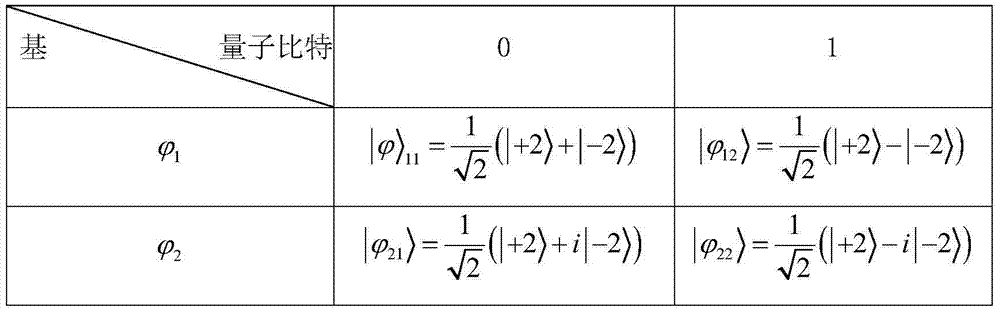
Quantum key distribution method and system based on orbital angular momentum encoding
ActiveCN104506309AEvenly distributedHigh bit rateKey distribution for secure communicationSpatial light modulatorQuantum codes
The invention provides a quantum key distribution method and system based on orbital angular momentum encoding. An orbital angular momentum entangled state is used as an information encoding carrier at a quantum key encoding transmitting terminal; orbital angular momentum is dynamically modulated through a spatial light modulator, and stable quantum codes are output; received quantum information can be stably and quickly measured at a receiving terminal through the spatial light modulator and a coincidence counting measurer, and by comparing encoding bases and measuring bases on a public channel, quantum bit code information is accurately decoded. The quantum key modulating and demodulating process is highly functionally integrated, information can be conveniently transmitted and received in real time, the system is efficient and stable, tapping behaviors of tappers can be judged in real time by violation verification of a Bell-CHSH inequation, and high-security quantum key distribution is guaranteed.
Owner:GUANGDONG INCUBATOR TECH DEV CO LTD
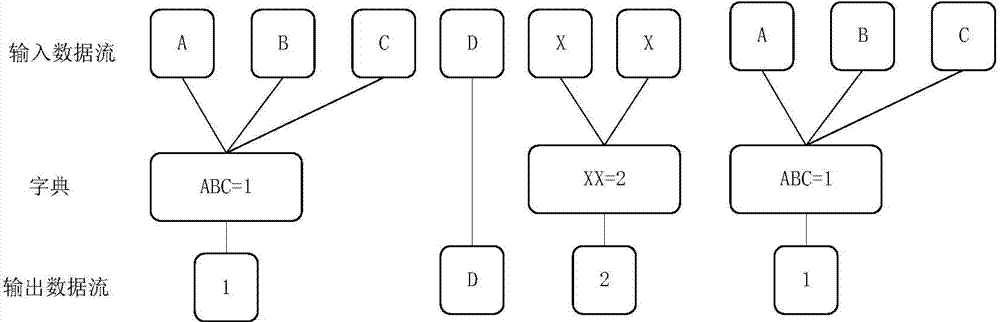
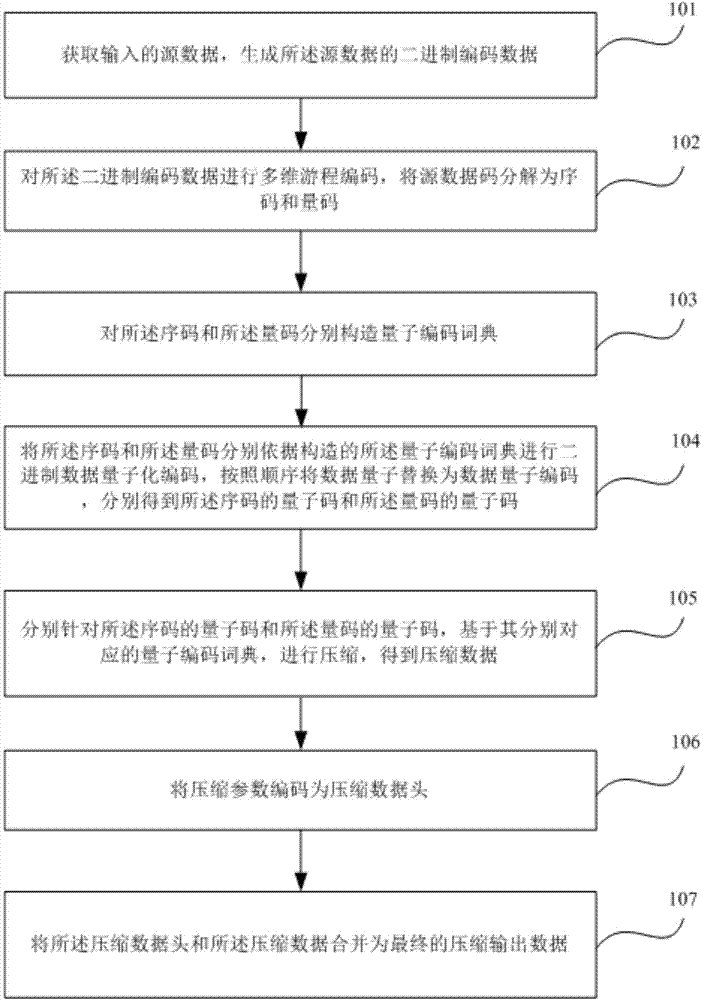
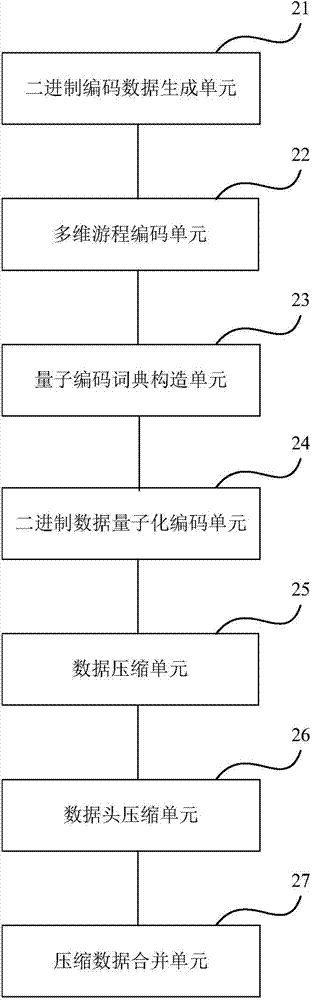
Multi-dimensional quantum data compressing and uncompressing method and apparatus
ActiveCN104125475AImprove compression efficiencyIncrease the compression ratioDigital video signal modificationQuantum codesMulti dimensional
The embodiment of the invention provides a multi-dimensional quantum data compressing and uncompressing method and apparatus. The multi-dimensional quantum data compressing method includes obtaining input source data to generate binary coded data of the source data; performing multi-dimensional run-length encoding on the binary encoded data and decomposing source data codes into program codes and quantum codes; building a quantum coding dictionary respectively for the program codes and the quantum codes; performing binary encoded data quantization coding on the program codes and the quantum codes according to the built quantum coding dictionaries, sequentially replacing data quantum with data quantum coding, and obtaining quantum codes of the program codes and the quantum codes respectively; compressing the quantum codes of the program codes and the quantum codes respectively to obtain compressed data; coding compression parameters into a compressed data header; combining the compressed data header with the compressed data to form ultimate compressed output data. The multi-dimensional quantum data compressing and uncompressing method is applicable to data of all types.
Owner:丁爱民
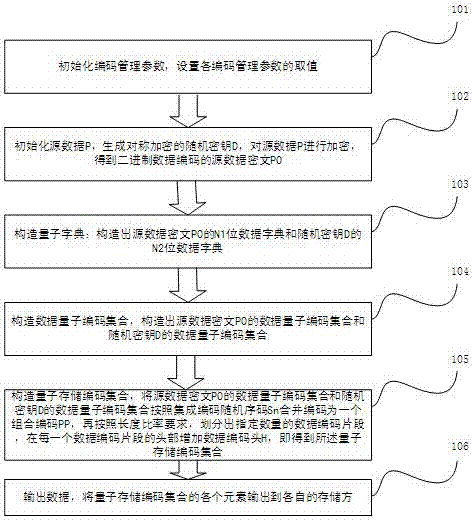
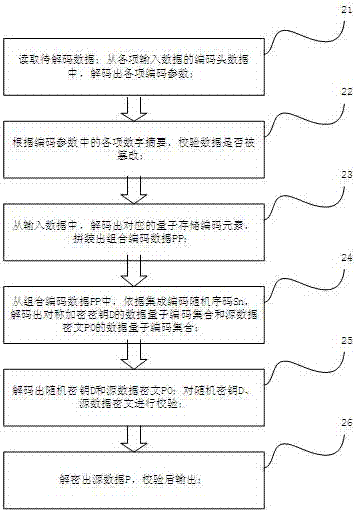
Quantum storage data encoding and decoding method, device and system
The embodiment of the invention provides a quantum storage data encoding and decoding method, a device and a system. According to the technical scheme of the invention, input data are encrypted by adopting a random number D to obtain a data ciphertext P0. The random number D and the data ciphertext P0 are respectively decomposed into data quantum code sets according to respective quantum dictionaries. According to an integrated coding random sequence code Sn, all data quantum codes of D and P0 are assembled to form coded data PP. The coded data PP are divided into n pieces of data fragments: PP1, PP2..., PPn. A coding head H and an envelope code HX are added to the head of each data fragment and then n data, namely P1, P2..., Pn, are constructed. The constructed data are outputted to the respective target positions. According to the embodiment of the invention, a secret segmentation method and a system are provided. The random features that, secret keys do not need to be stored in enciphered data and outputted data cannot be predicted and are different each time, are realized. Meanwhile, the invention provides a method for the compatibility of a binary quantum bit computer with a current silicon bit computer.
Owner:丁爱民
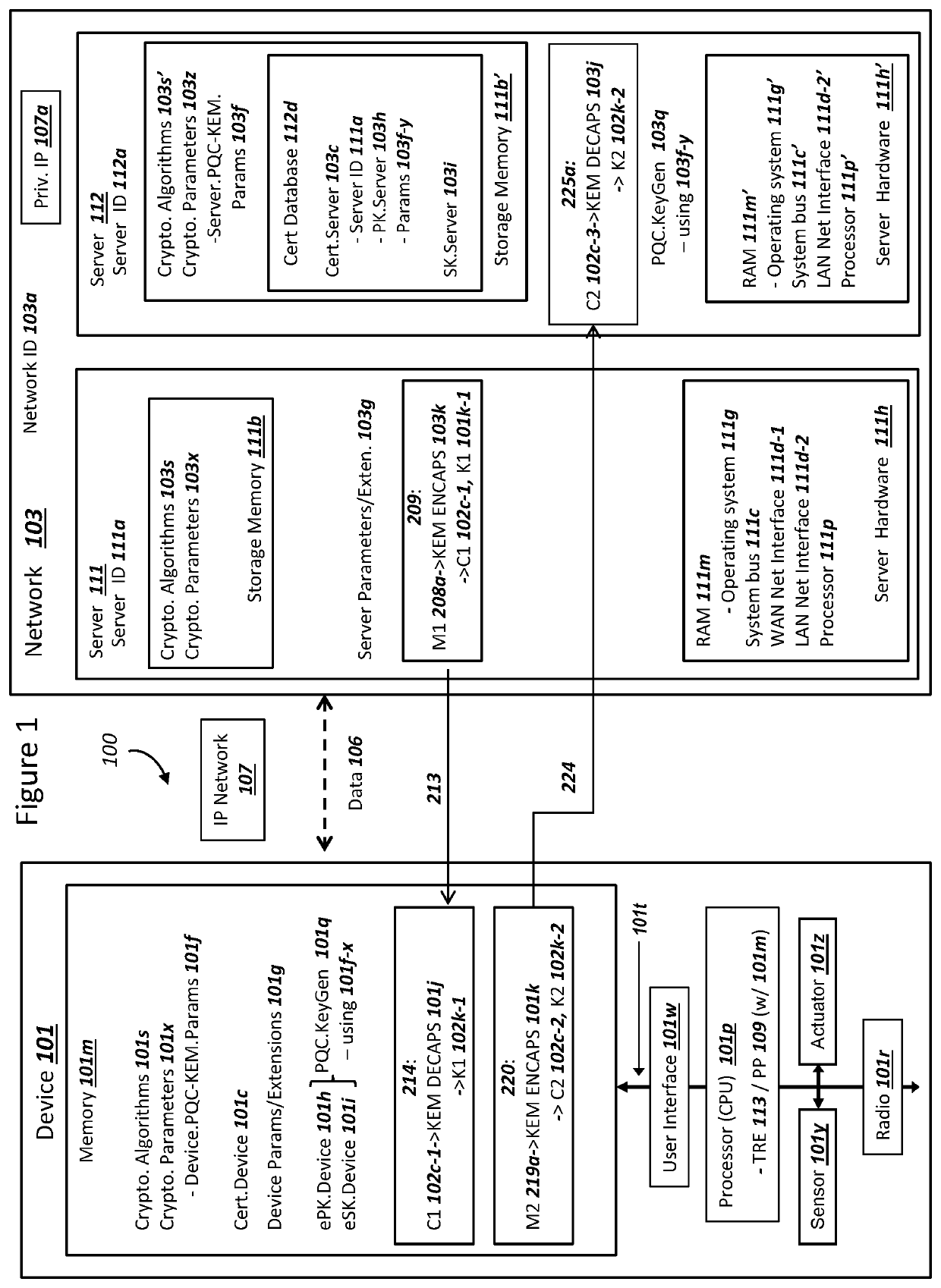
Network securing device data using two post-quantum cryptography key encapsulation mechanisms
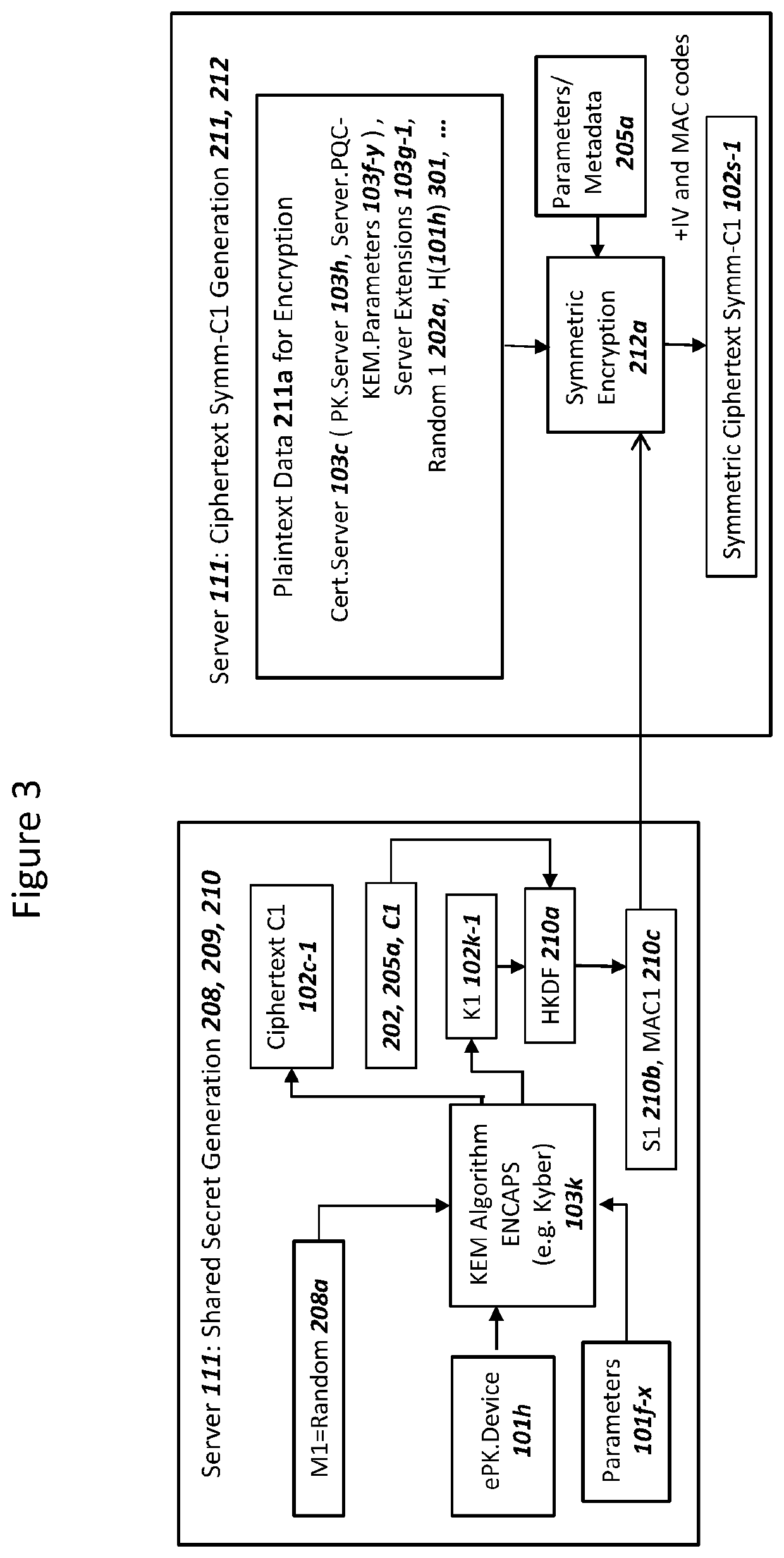
ActiveUS11153080B1Less-long-term and detailed studyGuaranteed long-term securityKey distribution for secure communicationPublic key for secure communicationKey (cryptography)Ciphertext
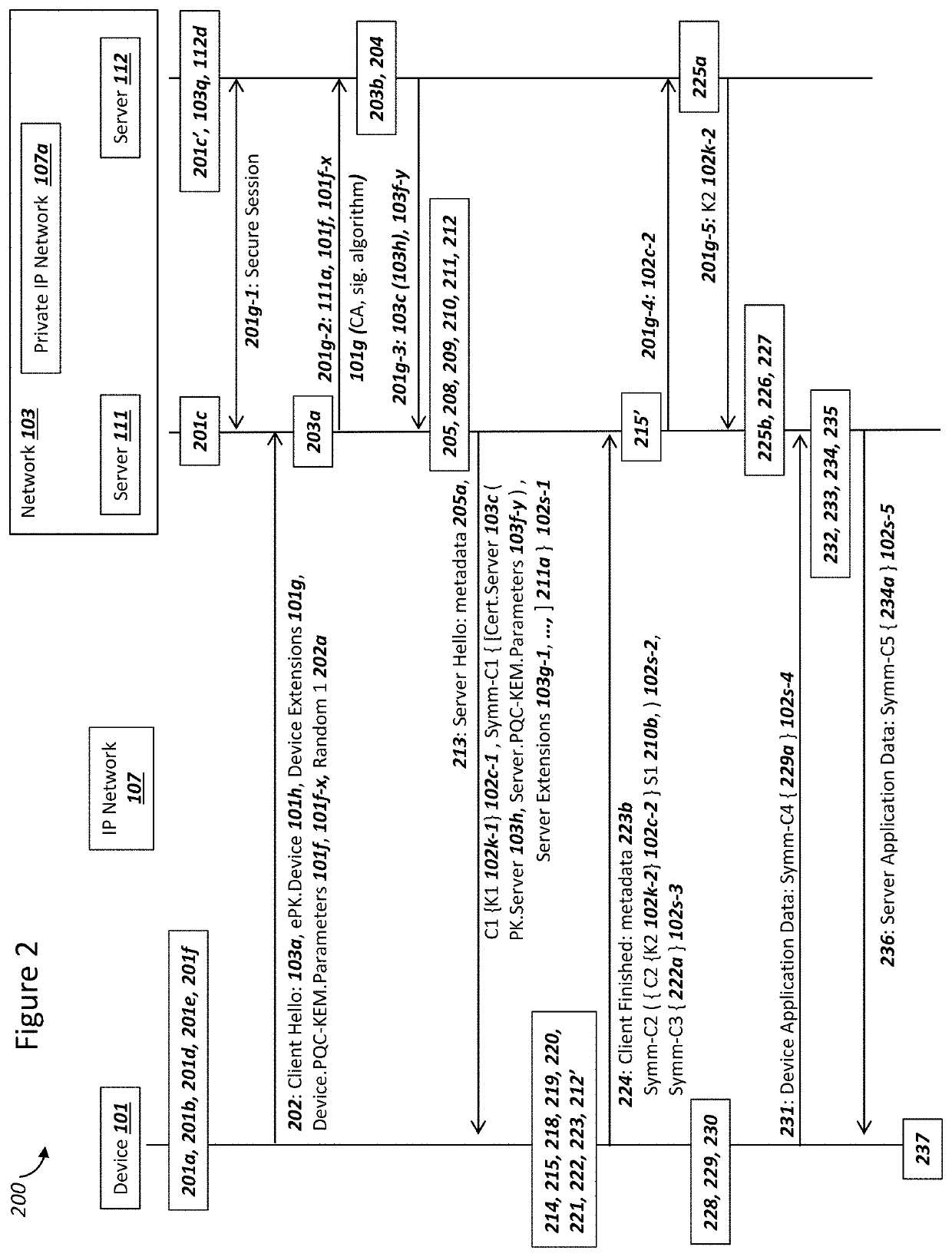
A network and a device can support secure sessions with both (i) a post-quantum cryptography (PQC) key encapsulation mechanism (KEM) and (ii) forward secrecy. The device can generate (i) an ephemeral public key (ePK.device) and private key (eSK.device) and (ii) send ePK.device with first KEM parameters to the network. The network can (i) conduct a first KEM with ePK.device to derive a first asymmetric ciphertext and first shared secret, and (ii) generate a first symmetric ciphertext for PK.server and second KEM parameters using the first shared secret. The network can send the first asymmetric ciphertext and the first symmetric ciphertext to the device. The network can receive (i) a second symmetric ciphertext comprising “double encrypted” second asymmetric ciphertext for a second KEM with SK.server, and (ii) a third symmetric ciphertext. The network can decrypt the third symmetric ciphertext using the second asymmetric ciphertext.
Owner:NIX JOHN A
Two non-orthogonal states quantum cryptography method and apparatus with inter-and inter-qubit interference for eavesdropper detection
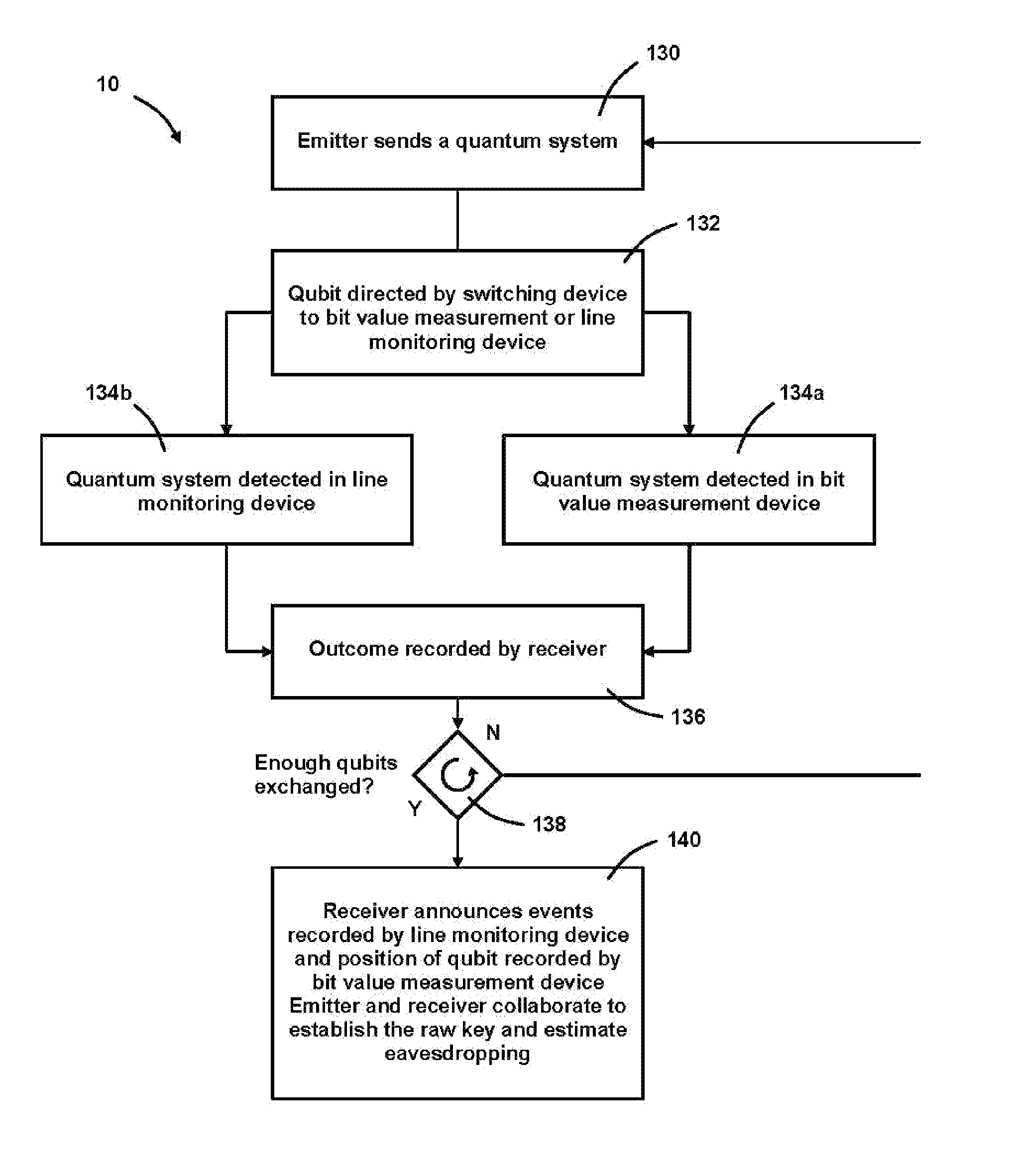
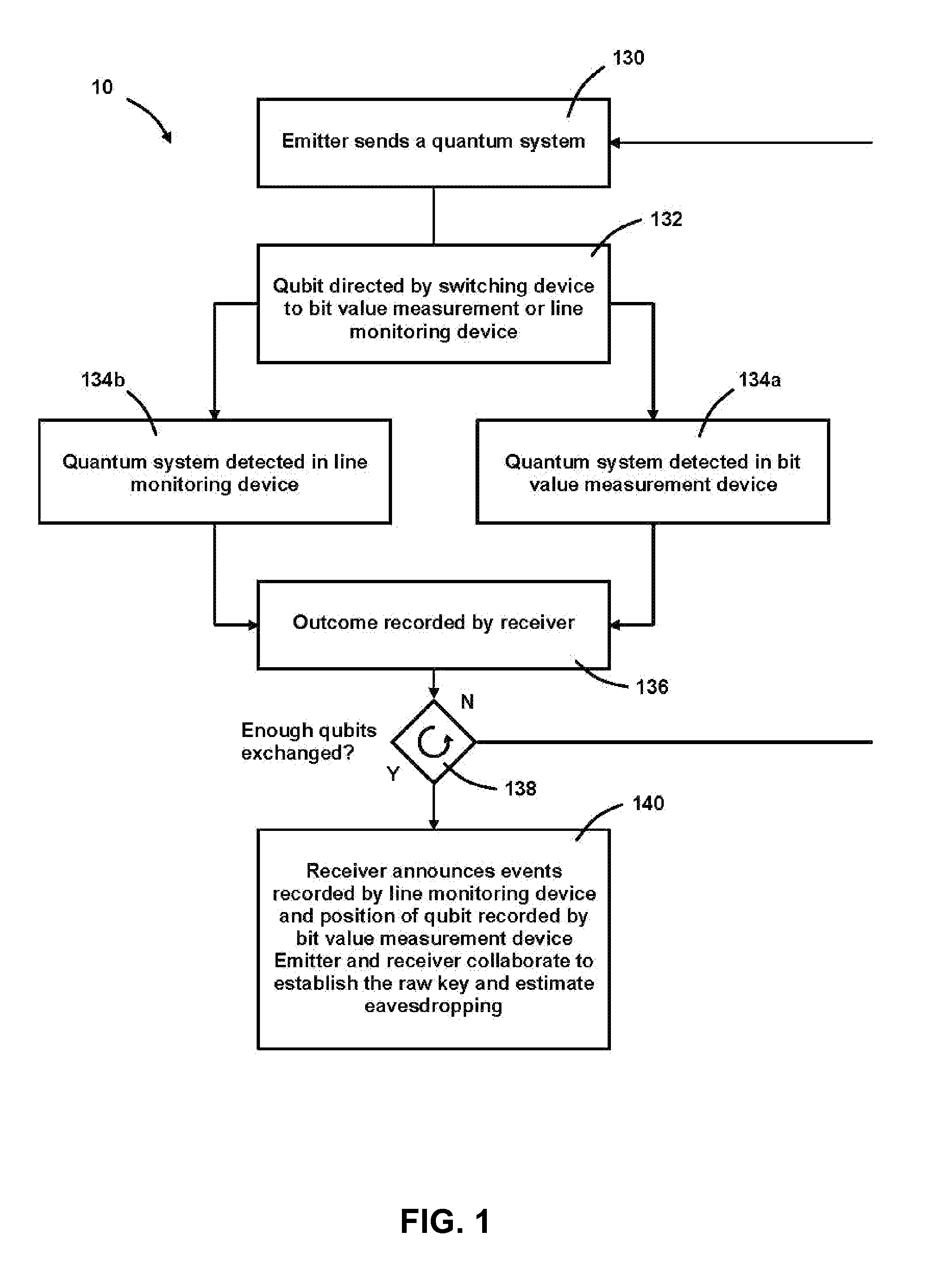
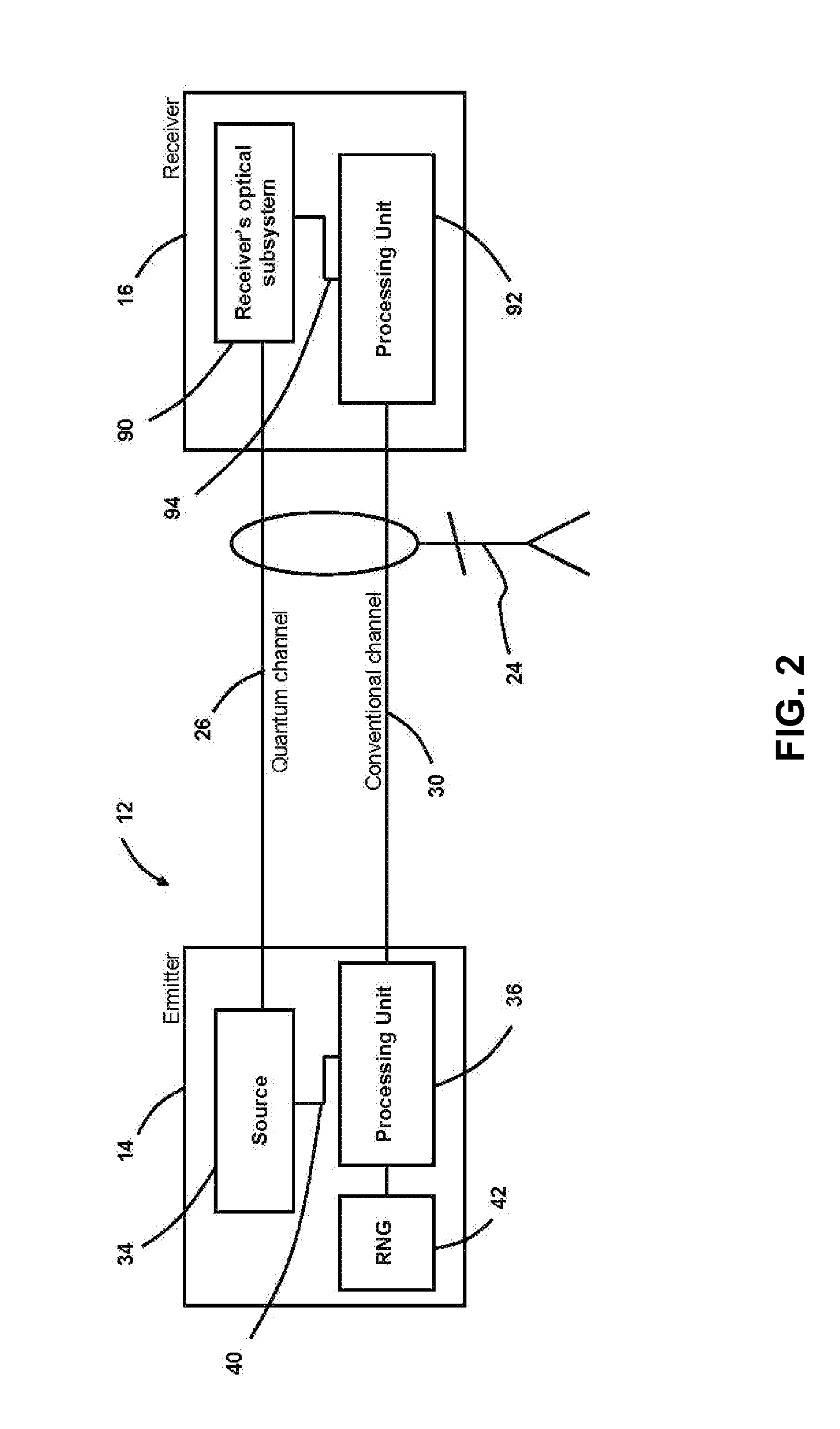
InactiveUS7929690B2Easy to implementRobust against environmental perturbationKey distribution for secure communicationSecret communicationQuantum codesParticle physics
An apparatus and method for implementing a secure quantum cryptography system using two non-orthogonal states. For each qubit, the to emitter station prepares a quantum system in one of two non-orthogonal quantum states in the time-basis to code bit values. Intra- and inter-qubit interference is then used to reveal eavesdropping attempts. Witness states are used to help reveal attacks performed across the quantum system separation.
Owner:ID QUANTIQUE SA
Quantum cryptography implementation method based on quantum light source
ActiveCN107659403AHigh key extraction ratePrevent leakageKey distribution for secure communicationPhotonic quantum communicationBeam splitterDecoy
The present invention discloses a quantum cryptography implementation method based on a quantum light source. The method comprises the following steps: generating a labeled single photon source through a PDC process, transmitting signal light to a receiving end, and allowing casual light to be used for local detection. The local detection of the transmitting end comprises a beam splitter (BS), a detector D1 and a detector D2. The casual light passes by the beam splitter to trigger the two detectors to generate four different response events. The four different response events are recorded andused for estimation and processing the signal received by the receiving end, so as to extract a secret key. Due to the usage of a novel passive decoy method, the single photon response rate and bit error rate can be estimated accurately. With a low-loss unequal-arm MZ interferometer used, the consumption of the system is greatly reduced. The single-mode standard commercial light enables the QKD system transmission distance to be over 200 km and based on a quantum light source, so that the final secret key extraction rate is two orders higher than that in the previous QKD system using the quantum light source.
Owner:NANJING UNIV OF POSTS & TELECOMM
Fully-integrated high-speed single photon detecting system and detecting method
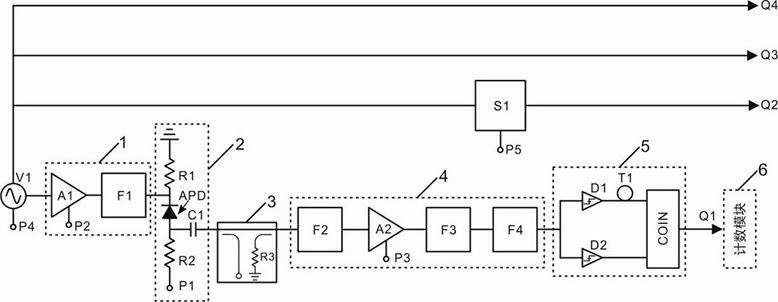
The invention relates to a fully-integrated high-speed single photon detecting system, comprising a precision clock source V1, wherein an output end of the precision clock source V1 is connected with an input end of an input filtering and amplifying module; an output end of the input filtering and amplifying module is connected with a temperature control module; an avalanche photodiode (APD) and a low noise direct current bias supply P1 are packaged in the temperature control module which is connected with an input end of an output filtering and amplifying module by a directional coupler; and an output end of the output filtering and amplifying module is connected with a counting module by a screening coincidence and dead time setting module. The invention also discloses a detecting method of the fully-integrated high-speed single photon detecting system. The fully-integrated high-speed single photon detecting system can strictly inhibit a back pulse effect, has a working frequency of 2 GHz and a counting rate of 100 MHz, is especially suitable for a quantum cryptographic system.
Owner:张军
Quantum key distribution method and system for authentication based on post-quantum cryptography algorithm
ActiveCN112152817AReduce complexityReduce workloadKey distribution for secure communicationUser identity/authority verificationKey (cryptography)Algorithm
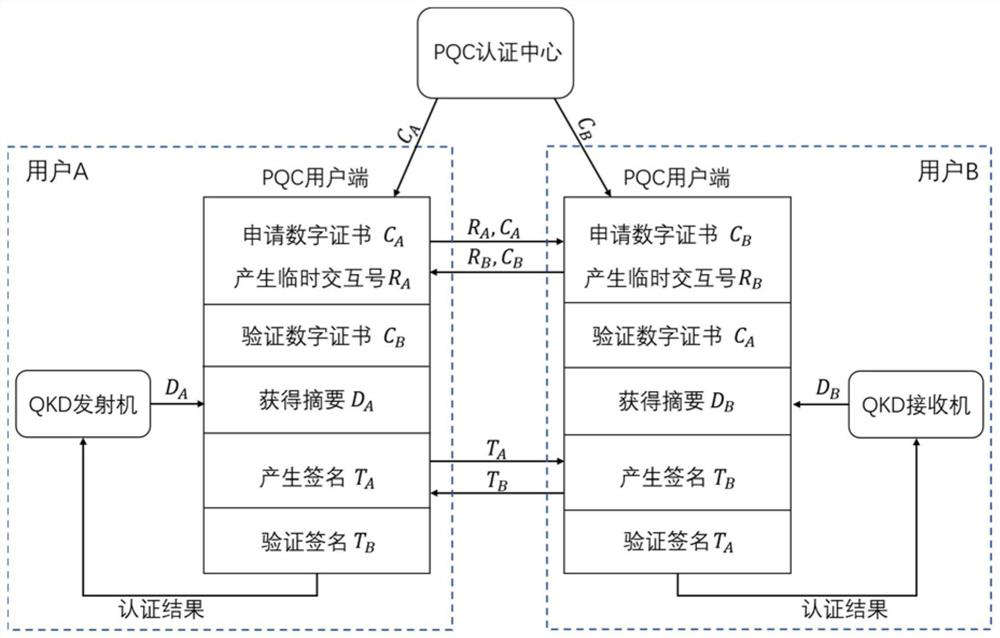
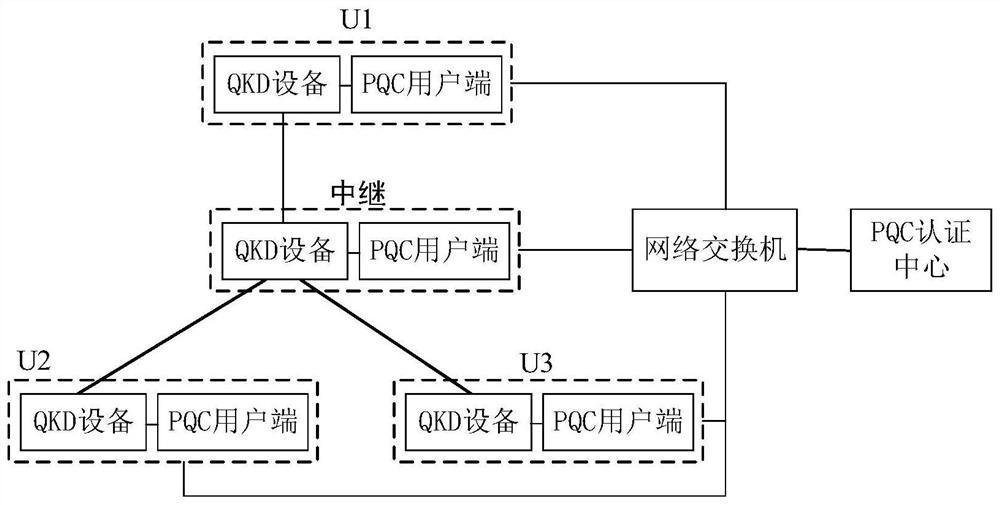
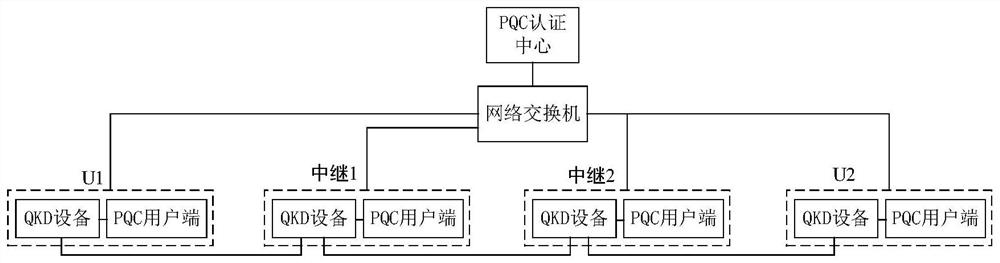
The invention provides a quantum key distribution method and system for authentication based on a post-quantum cryptography algorithm. The quantum key distribution system comprises a PQC authentication center, a PQC user side and QKD equipment. Communication in the quantum key distribution data post-processing process needs to be authenticated, a key presetting method is generally adopted at present, but the method is not suitable for a large-scale QKD network. According to the method and the system for authenticating the QKD by combining the PQC algorithm with the public key infrastructure, each user of the QKD network only needs to apply for one digital certificate from the authentication center, and the abstract of the authenticated information is signed and verified by using the PQC algorithm, so that the quantum-resistant computing security of the PQC algorithm in the authentication process can be ensured. And the operability and the flexibility of a large-scale QKD network are ensured.
Owner:CAS QUANTUM NETWORK CO LTD +3
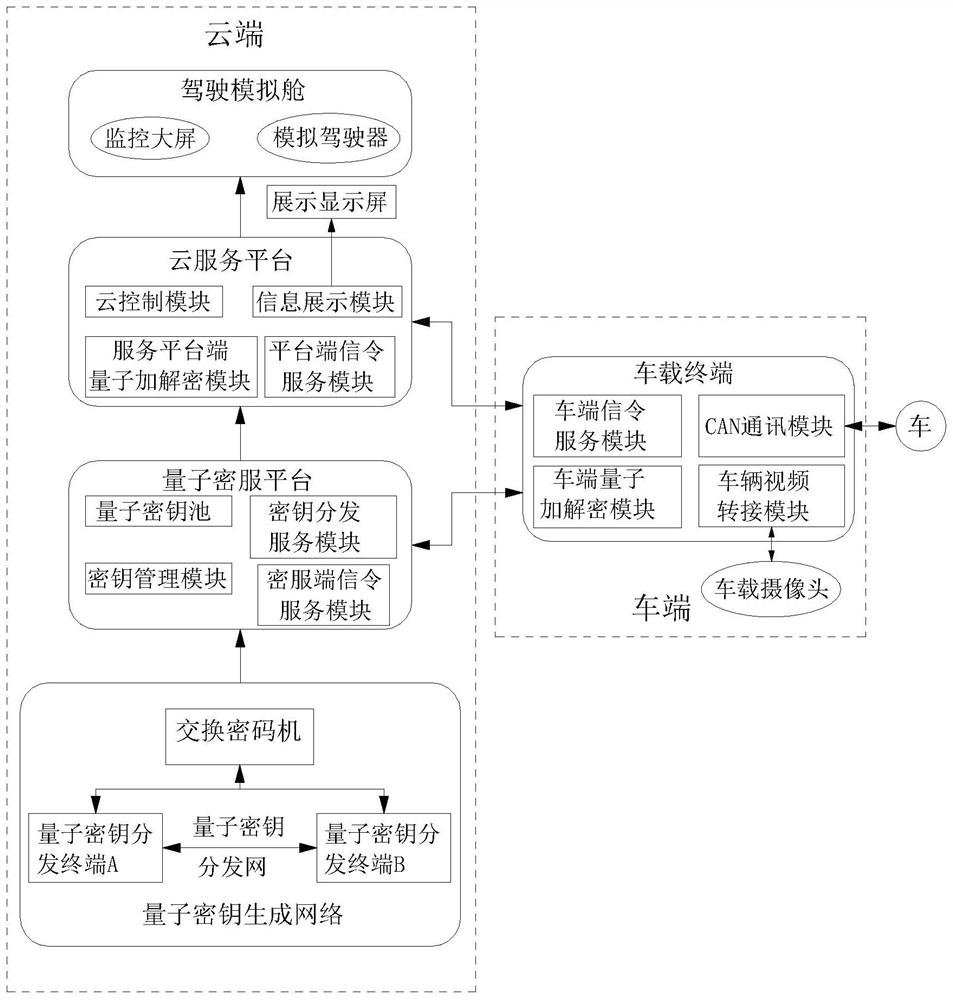
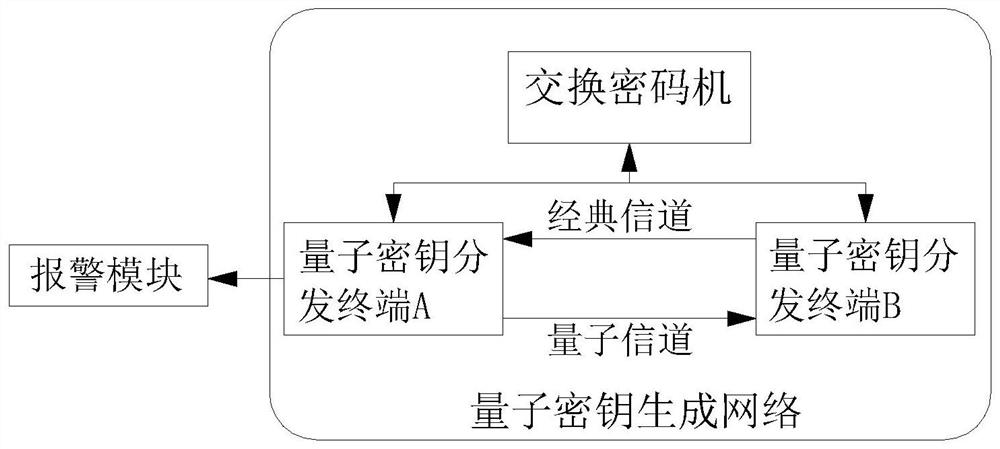
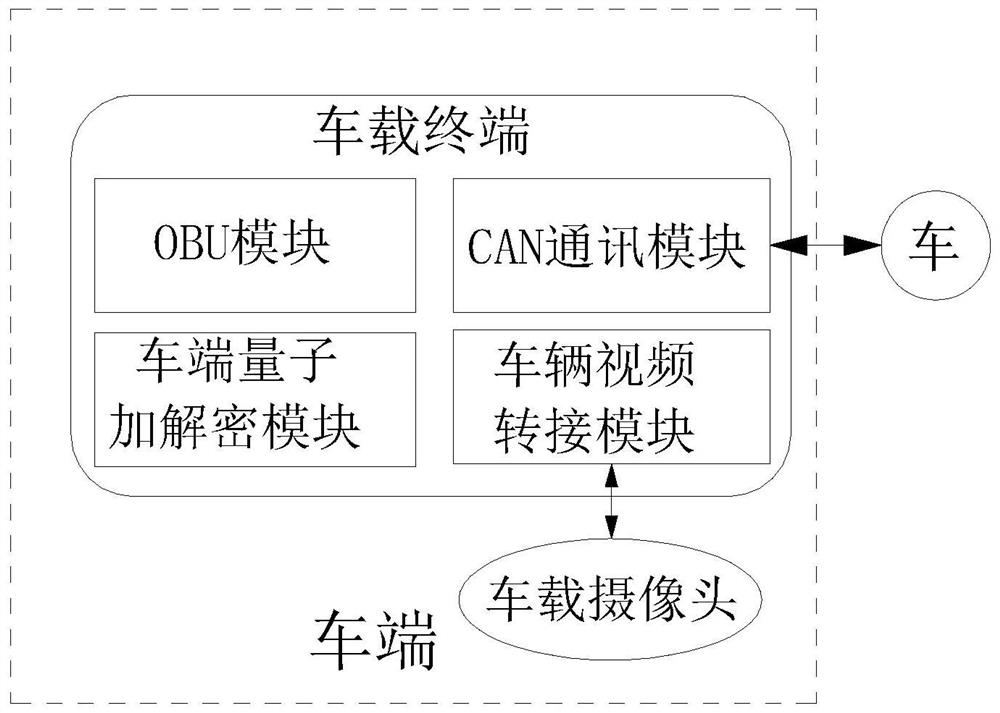
Vehicle and road cloud remote control system and method based on quantum encryption
ActiveCN114338003AGuaranteed confidentialityPrevent tamperingTelevision system detailsKey distribution for secure communicationCommunications securityIn vehicle
The invention discloses a vehicle and road cloud remote control system and method based on quantum encryption. The control system comprises a cloud service platform, a quantum password service platform, a quantum password generation network and a vehicle-mounted terminal. The cloud service platform comprises a service platform end quantum encryption and decryption module, an information display module and a cloud control module, and the quantum secret service platform comprises a quantum key pool, a quantum key distribution service module and a key management service module. The vehicle-mounted terminal comprises a vehicle end quantum encryption and decryption module, a vehicle video switching module, a CAN communication module, a vehicle end signaling service module and a network monitoring module. According to the method, a traditional quantum encryption mode is creatively improved, and the communication safety performance can be greatly improved; in the remote control process, the system can be automatically switched to the road end to perform short-distance communication with the road end, and the road end directly communicates with the cloud end, so that stable interaction with the cloud end is facilitated, and safe cloud driving is realized.
Owner:安徽冠盾科技有限公司
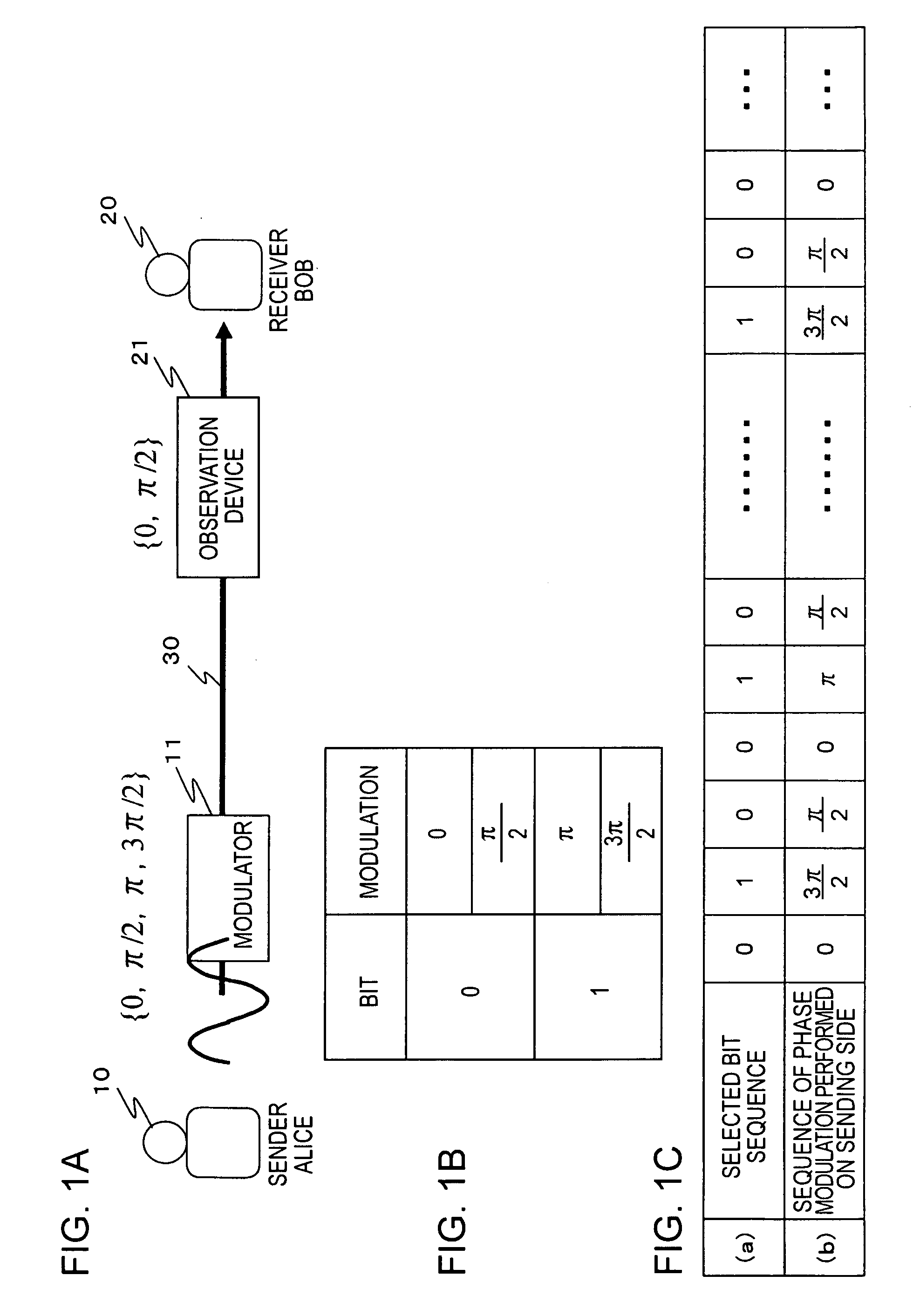
Method and apparatus for quantum cryptographic communication
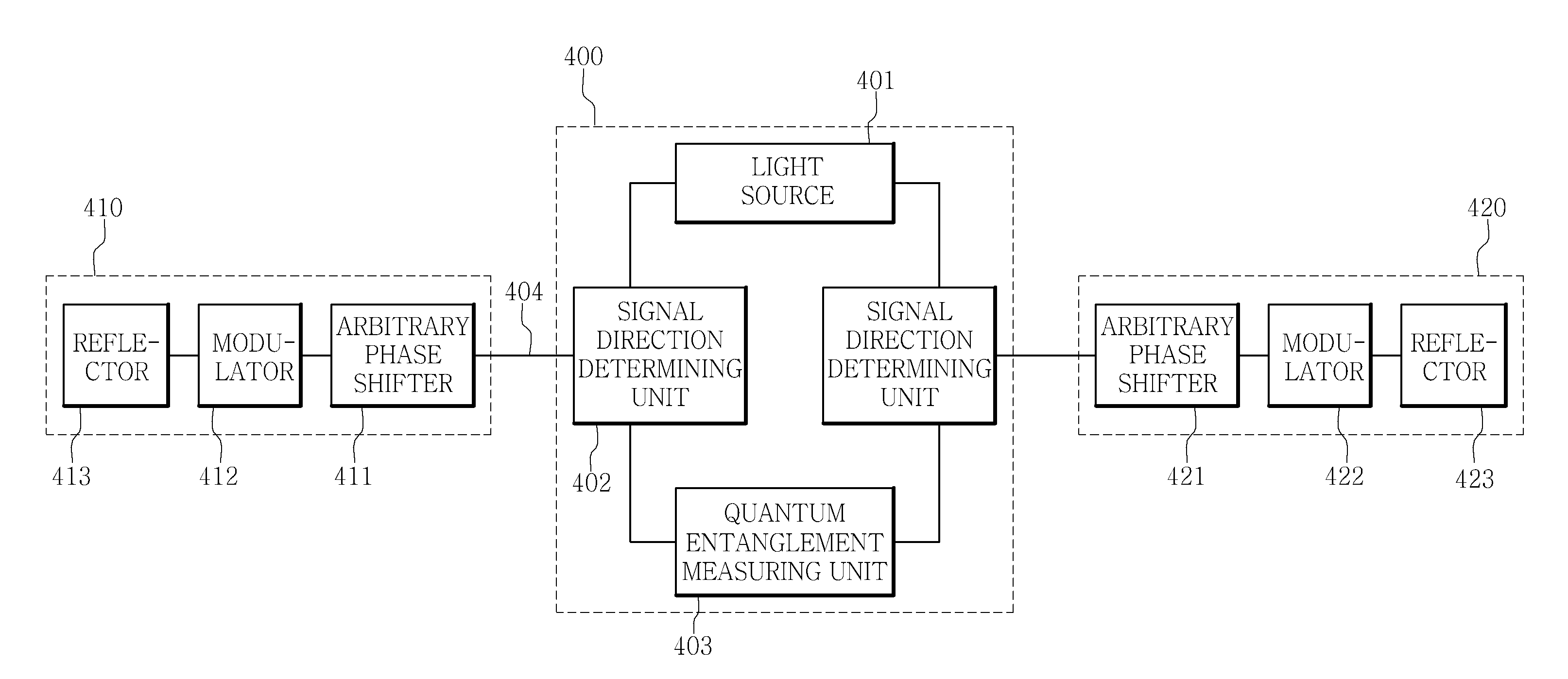
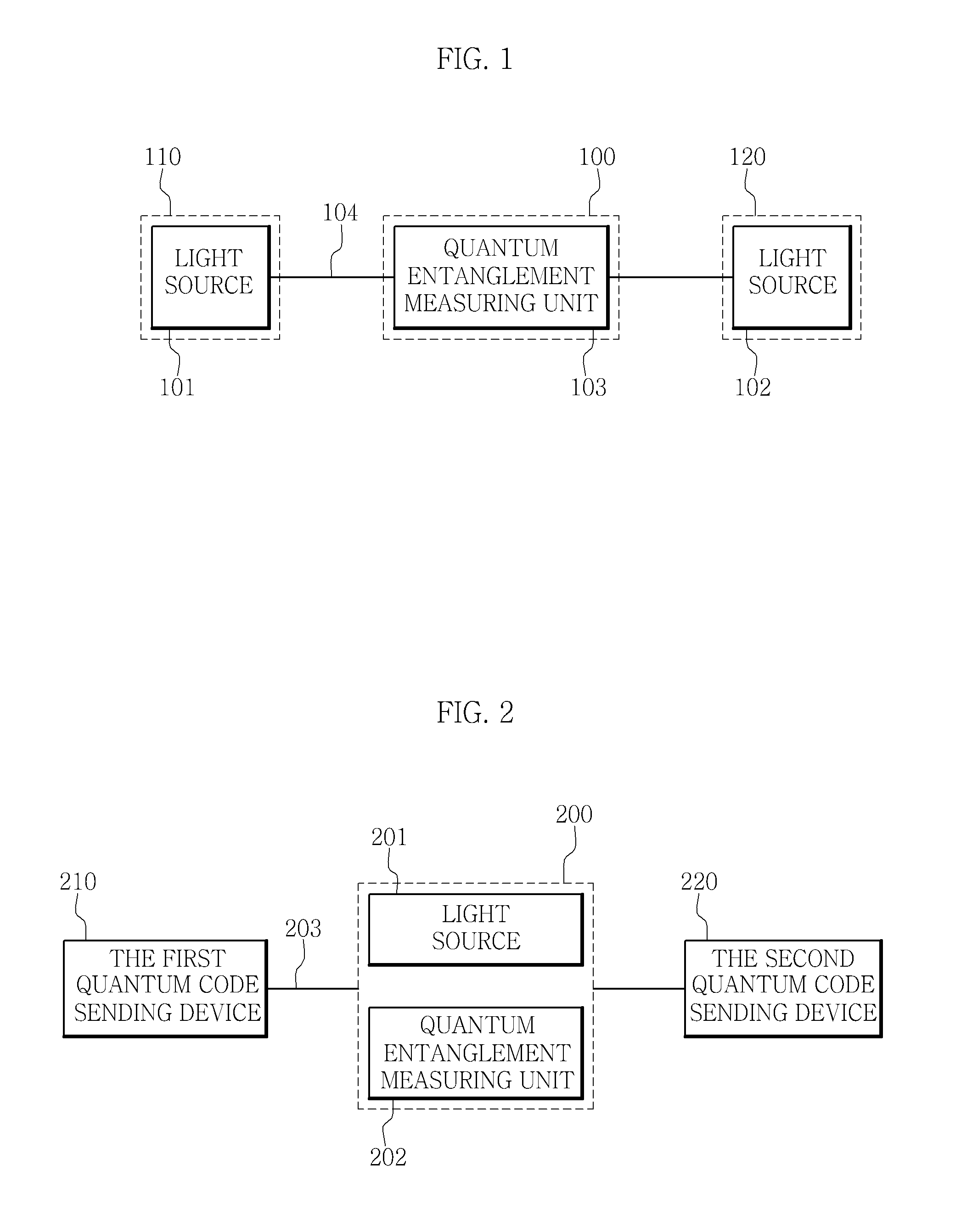
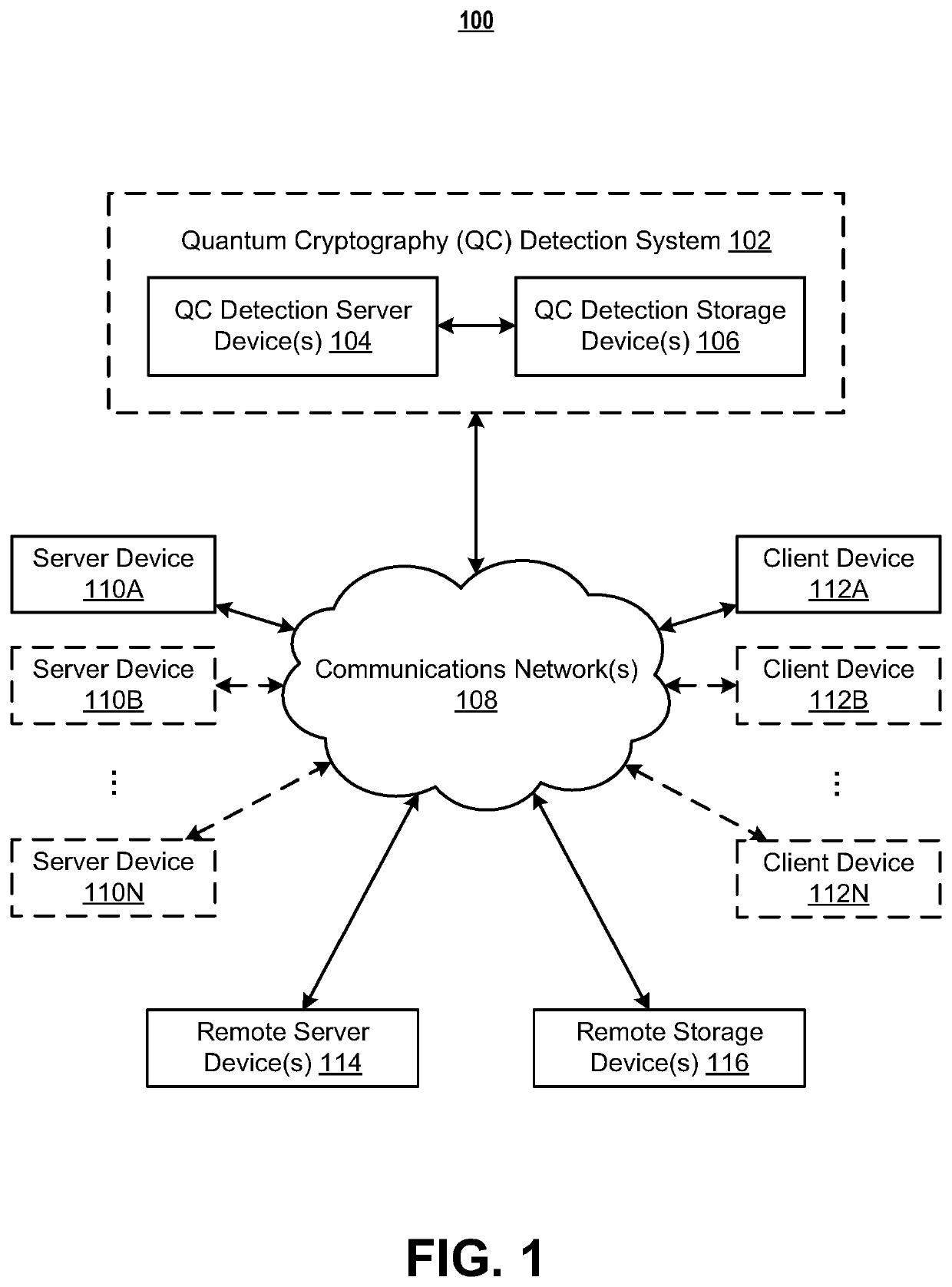
ActiveUS20160359624A1Improve practicalityKey distribution for secure communicationPhotonic quantum communicationQuantum entanglementDigital signal
An apparatus for quantum cryptographic communication includes a light source configured to generate an optical pulse which is transmitted to a plurality of quantum code sending devices, and a quantum entanglement measuring unit configured to receive the optical signal generated from each of the plurality of quantum code sending devices and measure a relation among quantum states of the optical signals received from the plurality of quantum code sending devices; the optical signal being generated by encoding a key to a quantum state of the optical pulse. The apparatus for quantum cryptographic communication may further include a signal direction determining unit, a reflector for reflecting the optical pulse or the optical signal, an arbitrary phase shifter, or a modulator for encoding a digital signal corresponding to the key to the optical pulse.
Owner:KOREA INST OF SCI & TECH
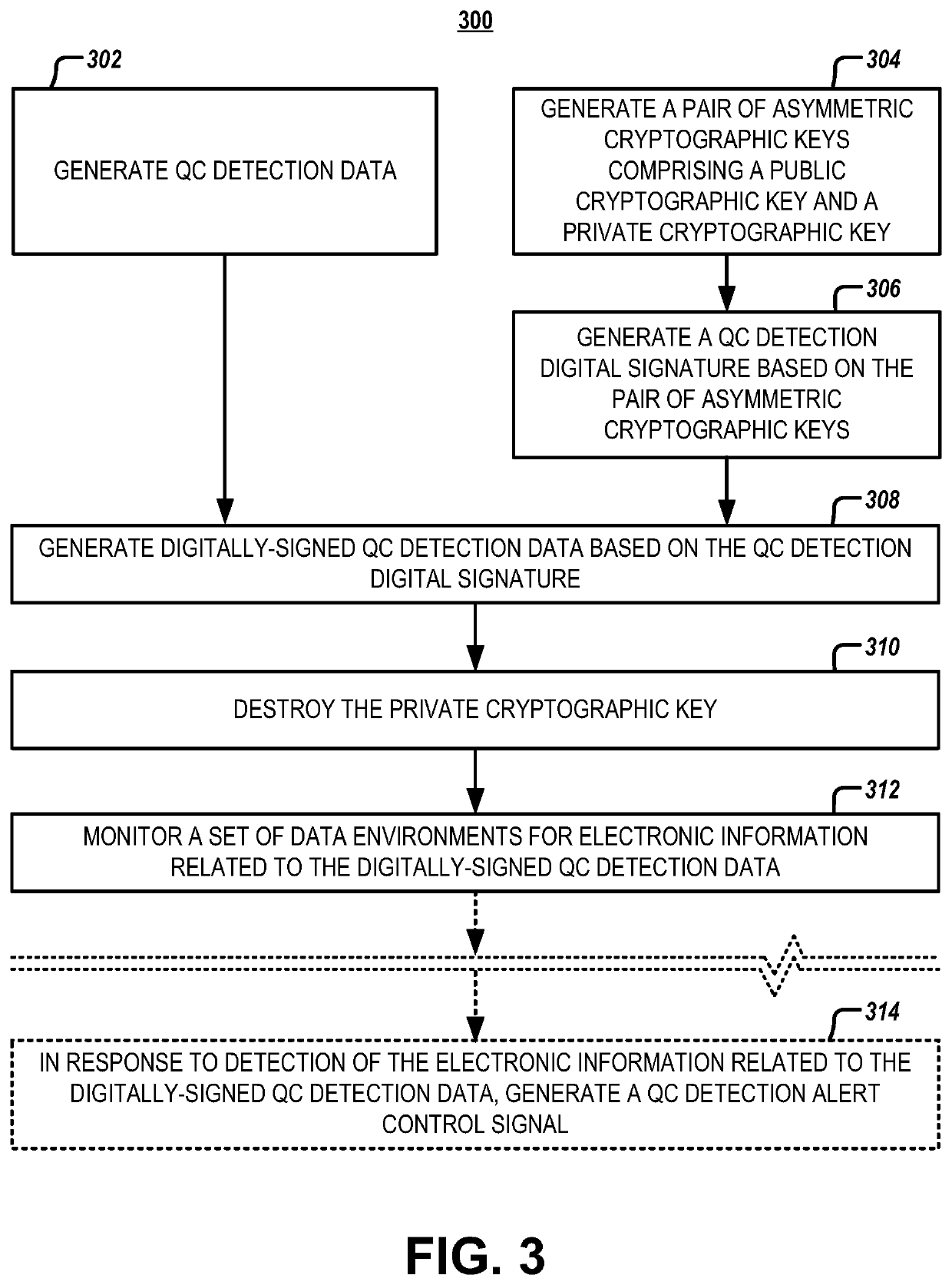
Systems and methods for layered quantum computing detection
ActiveUS11366897B1Reduce attack surfaceAvoid problemsQuantum computersKey distribution for secure communicationComputer networkQuantum codes
Systems, methods and computer program products are provided for layered quantum computing (QC) detection. An example system includes QC detection data generation circuitry that generates QC detection data via a first post-quantum cryptographic (PQC) technique. The system also includes cryptographic circuitry configured to generate a pair of asymmetric cryptographic keys including a public cryptographic key and a private cryptographic key via a second PQC technique, generate encrypted QC detection data based on the pair of asymmetric cryptographic keys, and destroy the private cryptographic key. The system further includes data monitoring circuitry configured to monitor a set of data environments for electronic information related to the encrypted QC detection data. In response to detection of the electronic information related to the encrypted QC detection data, the system may monitor a set of data environments for electronic information related to the QC detection data.
Owner:WELLS FARGO BANK NA
Quantum cryptography communication method, quantum cryptography communication apparatus, and quantum cryptography communication system
InactiveUS8175273B2Guaranteed normal transmissionData augmentationSecret communicationSecuring communicationCommunications systemSample sequence
In quantum cryptography communication, a sequence of signals in the form of quantum states randomly selected from a plurality of quantum states each having a different phase modulation angle is transmitted from a data transmitting apparatus. In a data receiving apparatus, if the sequence of samples is received, a plurality of bases corresponding to a plurality of different phase modulation angles are randomly selected, and a homodyne detection process is performed using the selected bases. Information indicating the bases used in the homodyne detection process is sent to the transmitting apparatus. In the data transmitting apparatus, depending on the bases used in the receiving apparatus, bit values are assigned to the plurality of different quantum states selected by the transmitting apparatus, and information indicating the assigned bit values is sent to the data receiving apparatus.
Owner:SONY CORP
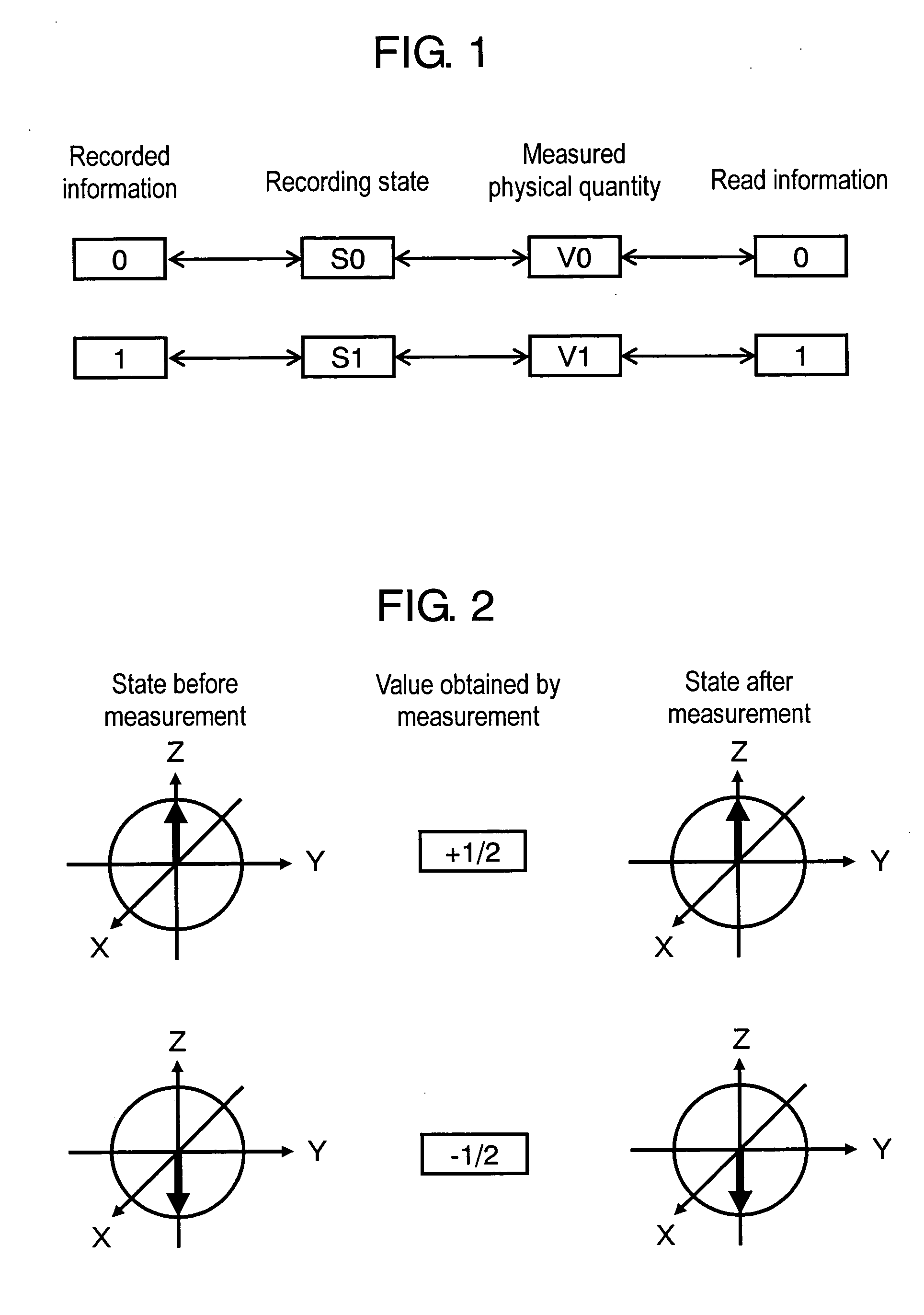
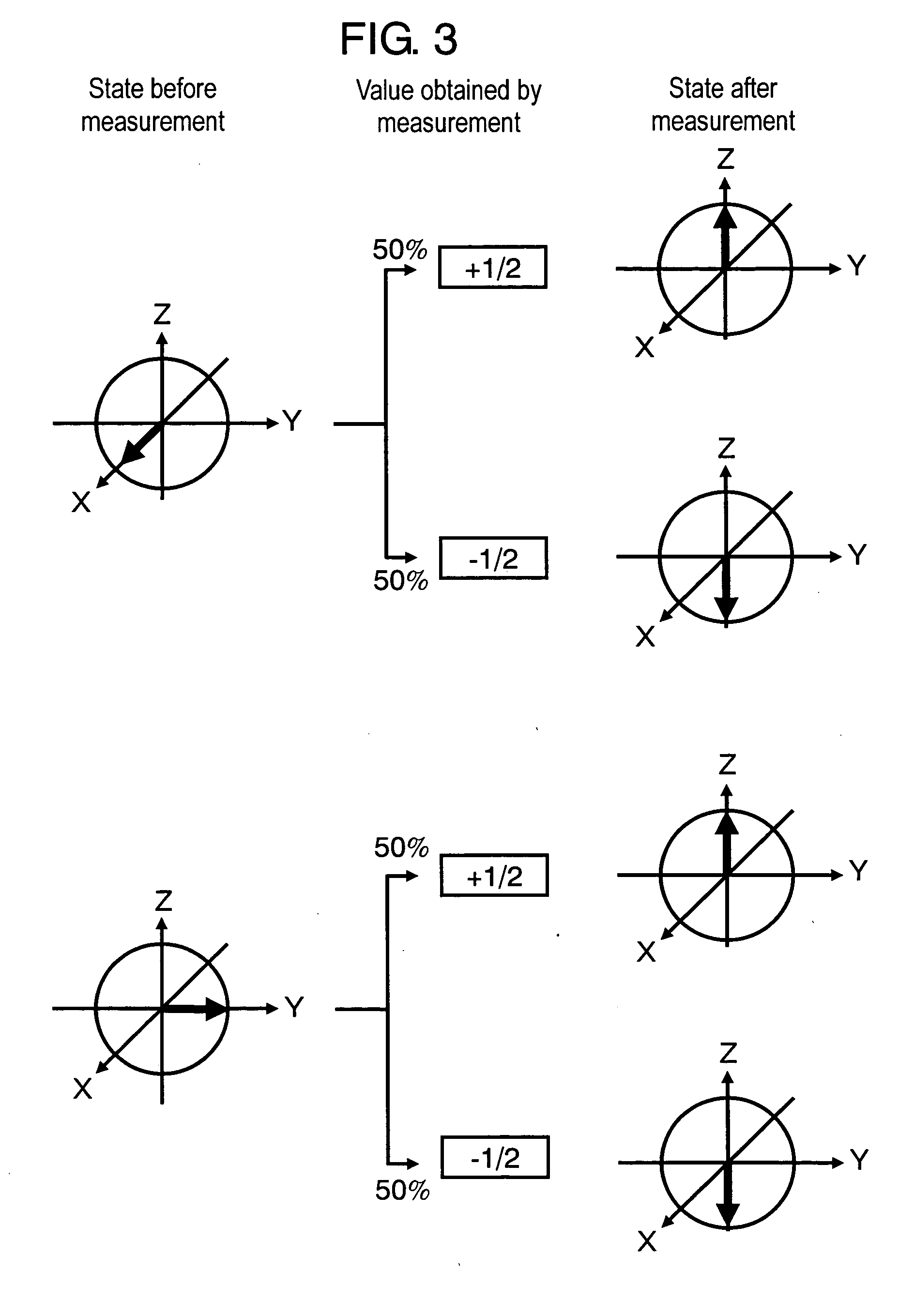
Quantum cipher recording method, and quantum cipher recording device
InactiveUS20070014214A1Reduce riskRisk of unauthorized decryption of the informationFilamentary/web record carriersUser identity/authority verificationComputer hardwareQuantum codes
An information recording / reproducing method comprises several steps. Information to be recorded, a reading key that allows a person knowing the key to specify a base used for recording each bit and inhibits a person unknowing it from specifying the base, and an algorithm for determining the base from the key are prepared. A state to be created for each bit from quantum states is selected so as to satisfy the conditions. A measured value corresponding to the information to be recorded is acquired when a reading procedure corresponding to each base is performed. The measured value is not acquired when unitary transformation corresponding to a different base is performed. The quantum state in the recording medium is created. The state is kept, and each base is determined according to the key and performing the reading procedure corresponding to the base. Safety of the recorded information can be sufficiently secured.
Owner:PANASONIC CORP
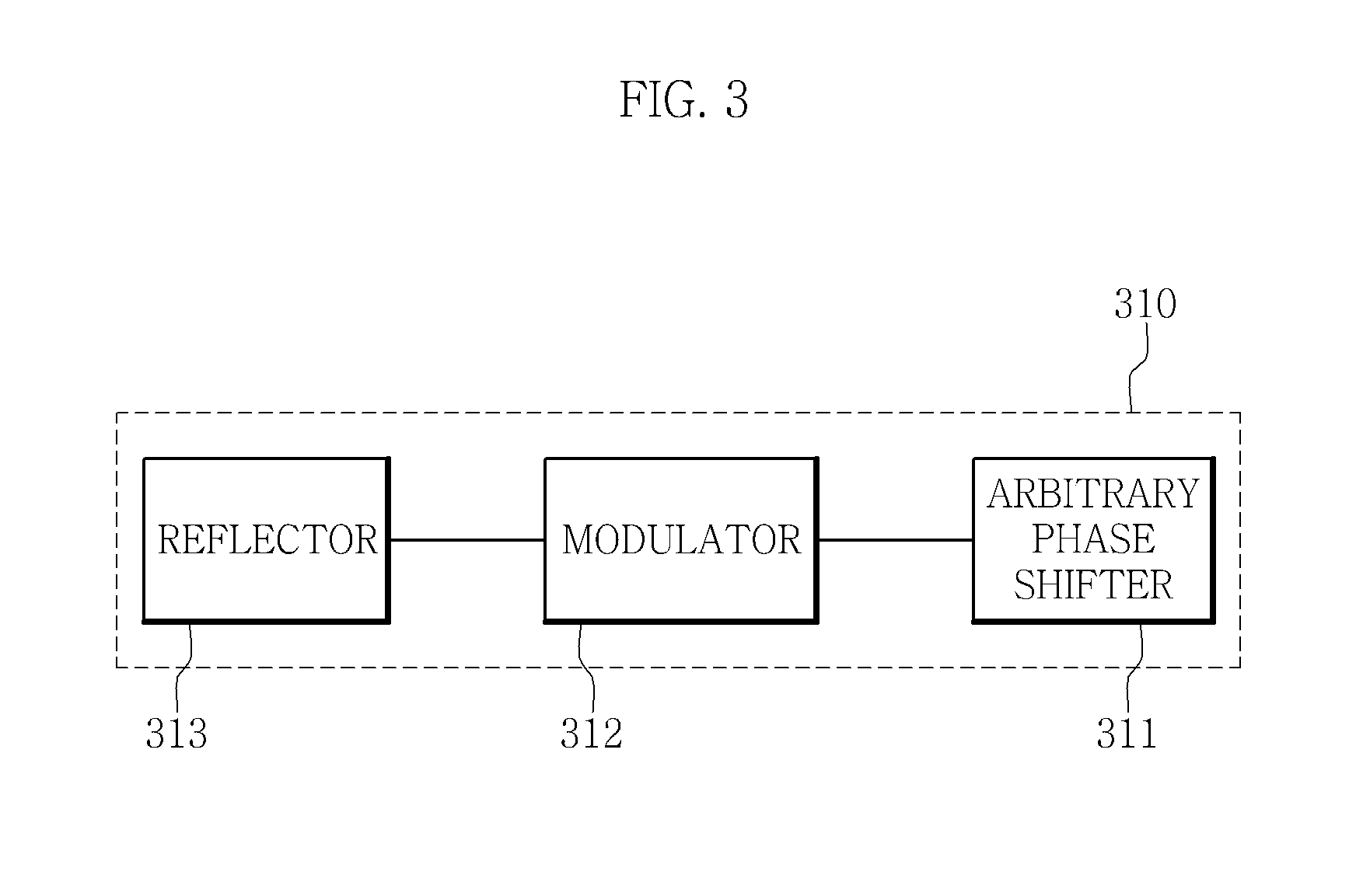
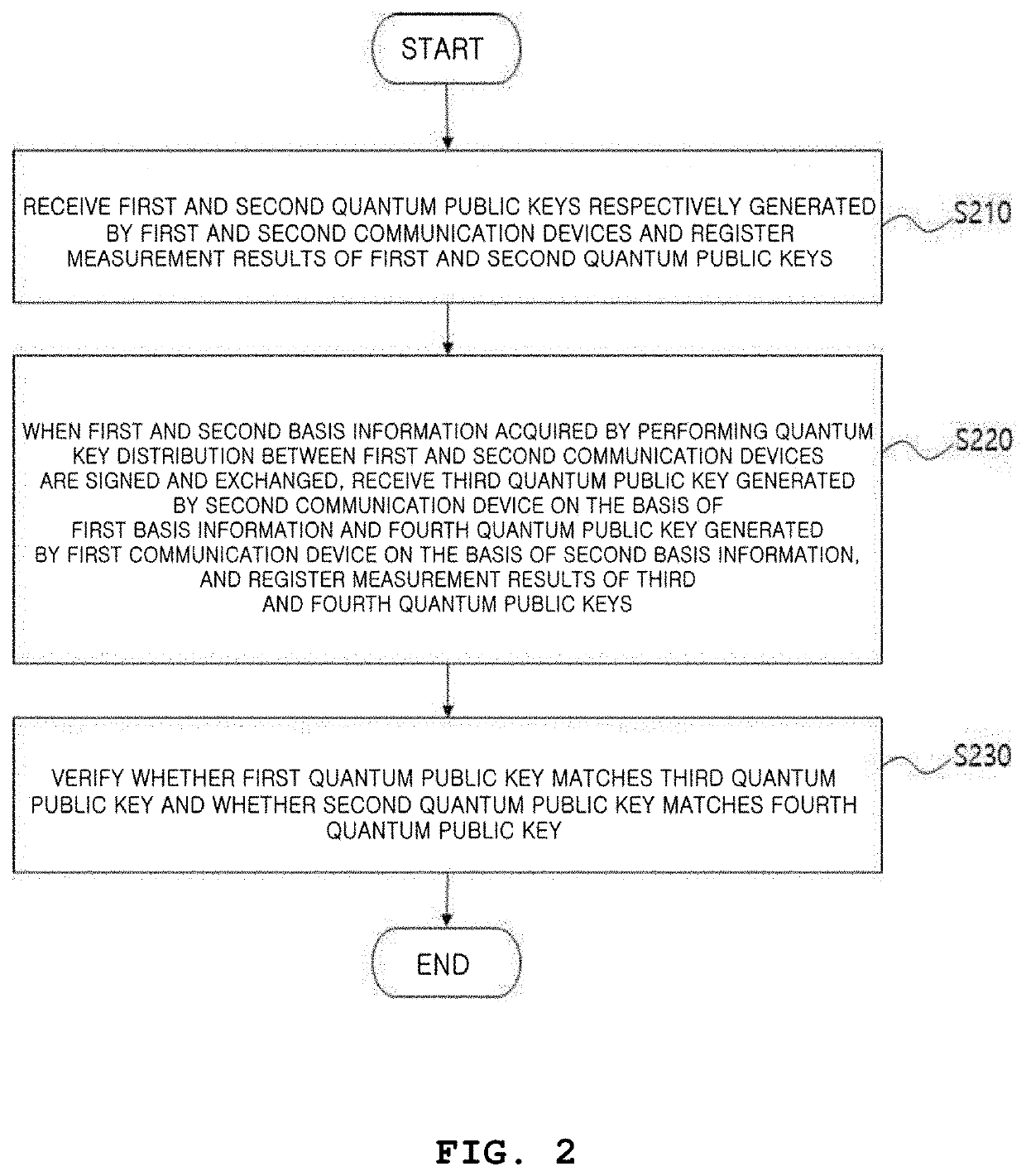
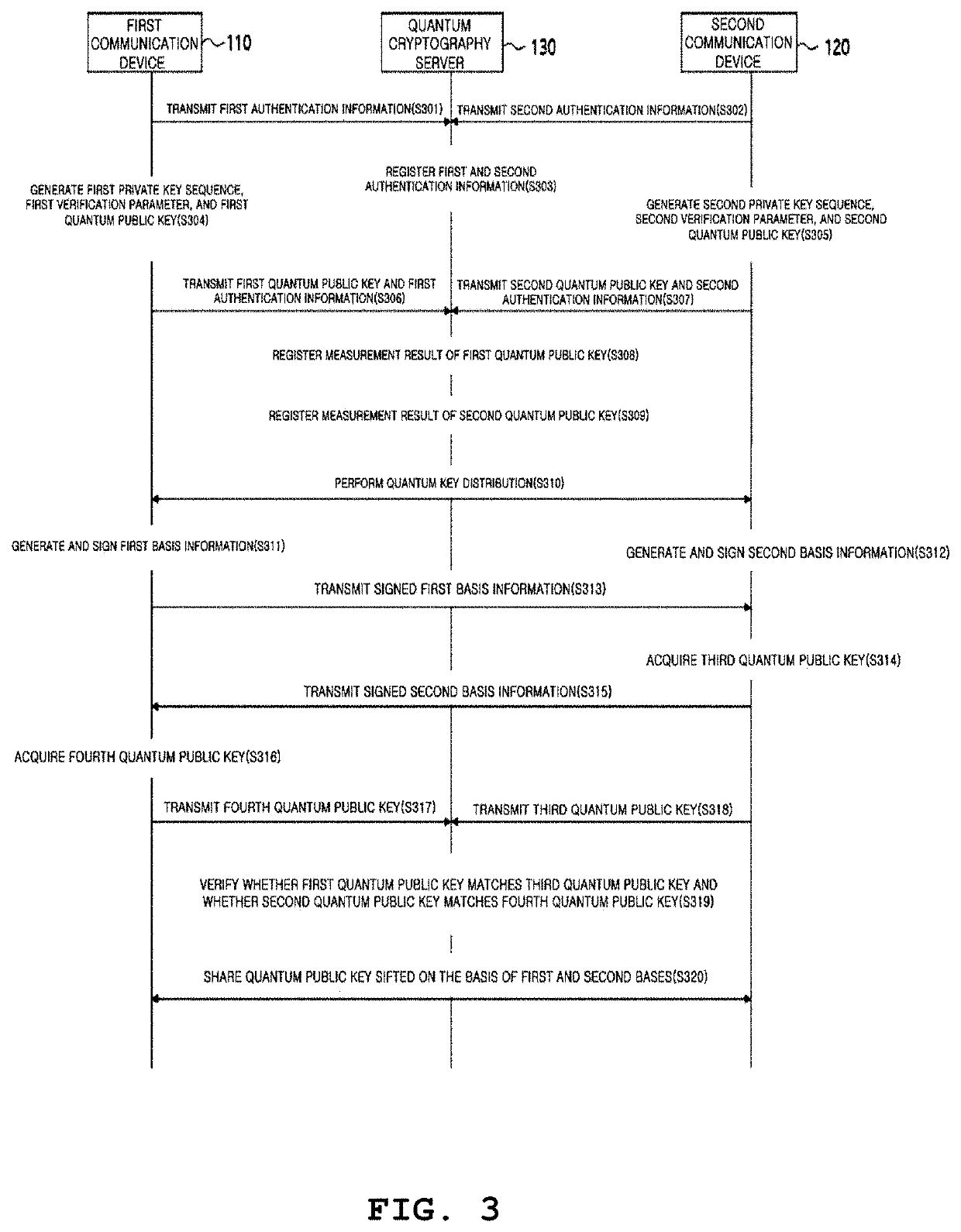
Certificated quantum cryptography system and method
ActiveUS20190379536A1Key distribution for secure communicationPublic key for secure communicationCommunication deviceQuantum key distribution
A certificated quantum cryptography method is provided. The method is performed by a quantum cryptography server connected to a first communication device and a second communication device which perform quantum key distribution. The method includes step of receiving a first quantum public key generated by the first communication device and a second quantum public key generated by the second communication device and registering measurement outcomes of the first and second quantum public keys. When first basis information and second basis information acquired by performing quantum key distribution between the first and second communication devices are signed and exchanged, the method includes the step of receiving a third quantum public key and a fourth quantum public key.
Owner:KOREA INST OF SCI & TECH
Quantum encoder whose polarization state is modulated by phase and decoder and its application
InactiveCN1477413ARealize quantum cryptography communicationLow modulation voltagePolarisation multiplex systemsSecret communicationCondensed matter physicsDistortion
The present invention relates to a quantum coder with phase modulated polarization state, decoder and polarization compensating method used in the quantum secret communication, four-state quantum coder and decoder are formed from a phase-polarization controller and a true random generator, and the six-state quantum coder and decoder are formed from two phase-polarization controllers and a synchronous trigger, in the quantum secret communication it utilizes the quantum coder and decoder to effectively compensate the polarization state distortion resulted in the course of signal transmission, so that its error code rate can be greatly reduced to 10 to the minus fifth, and its modulation speed can be up to several GHz from tens Hz.
Owner:SOUTH CHINA NORMAL UNIVERSITY
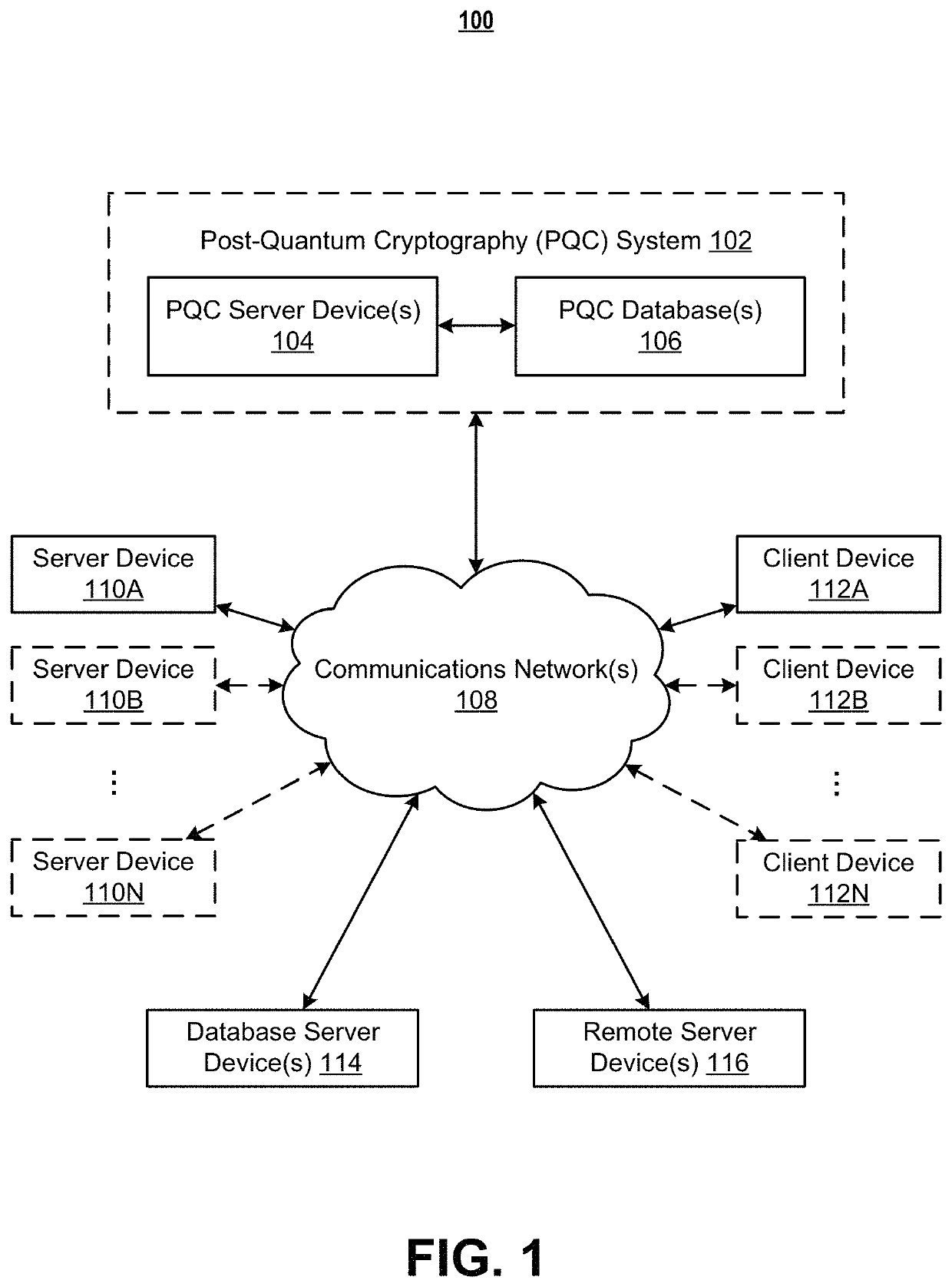
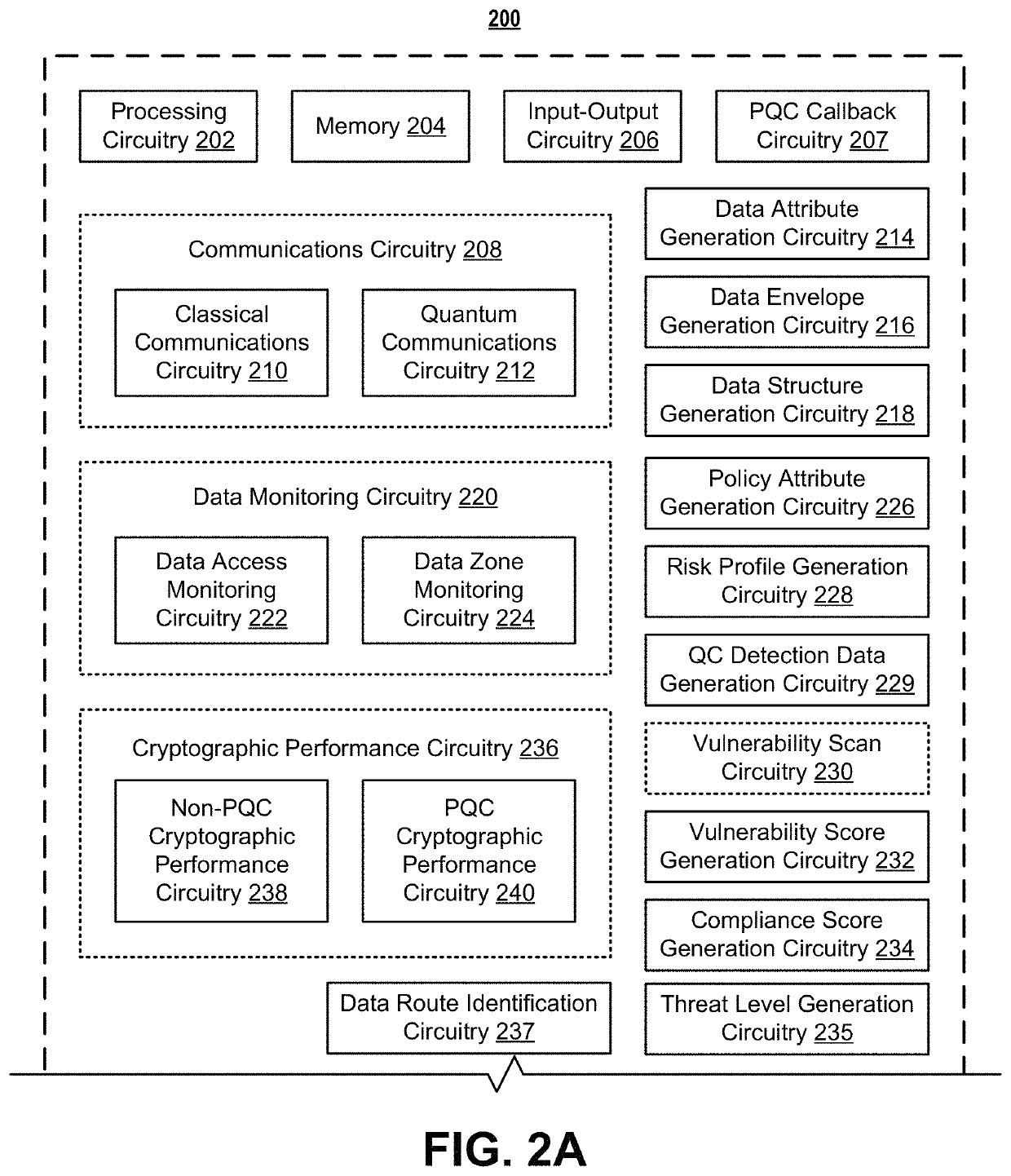
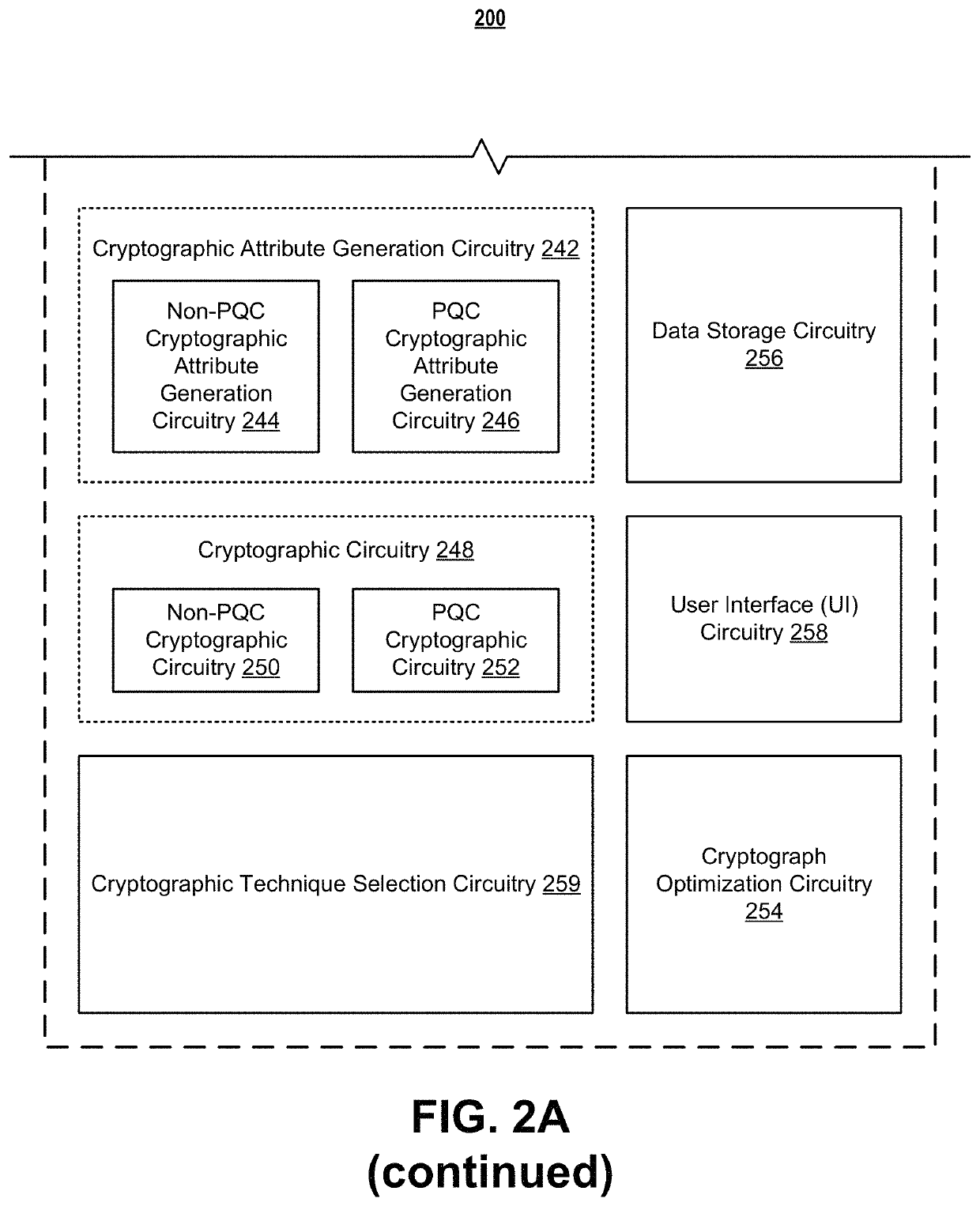
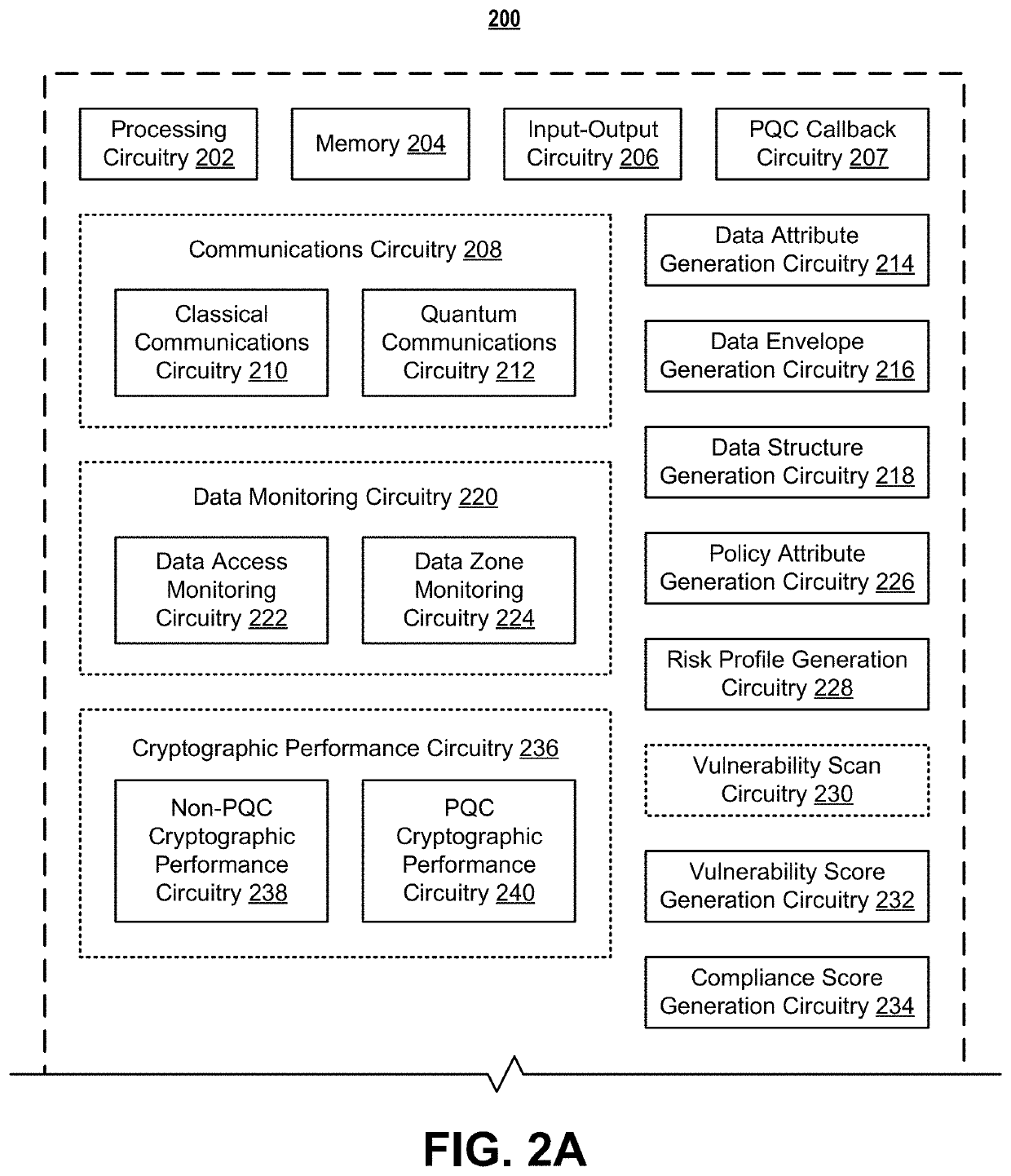
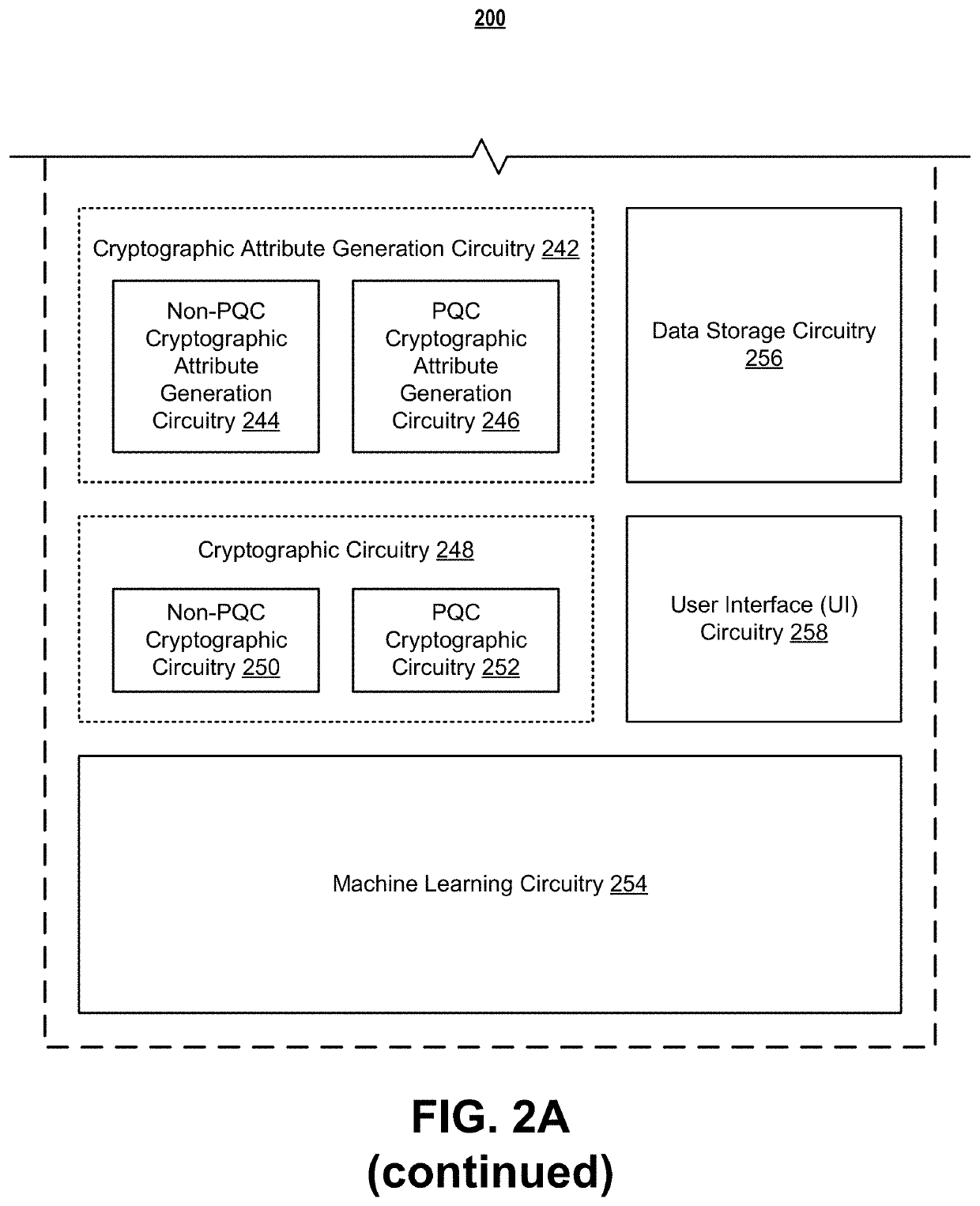
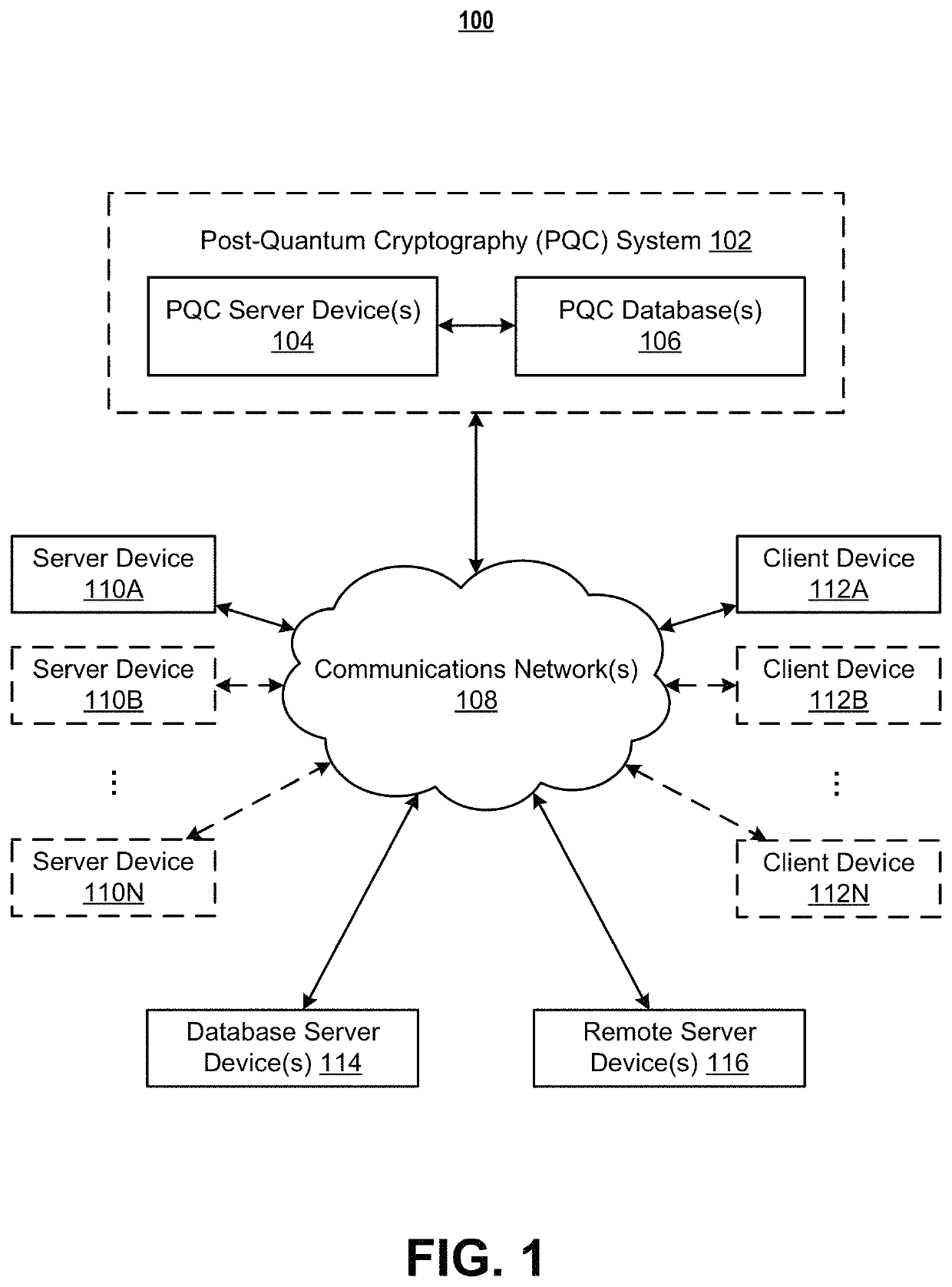
Systems and methods for post-quantum cryptography optimization
ActiveUS11449799B1Quantum computersKey distribution for secure communicationEngineeringQuantum codes
Systems, apparatuses, methods, and computer program products are disclosed for post-quantum cryptography (PQC). An example method includes receiving data. The example method further includes receiving a set of data attributes about the data. The set of data attributes comprises one or more sets of data environment data attributes that are each representative of a set of data environments associated with the data. The example method further includes receiving one or more sets of data environment threat data structures associated with one or more data environments in the one or more sets of data environments associated with the data. The example method further includes selecting one or more cryptographic techniques for encrypting the data for at least the one or more data environments based on the set of data attributes, the one or more sets of data environment threat data structures, and a cryptograph optimization machine learning model.
Owner:WELLS FARGO BANK NA
Systems and methods for post-quantum cryptography optimization
ActiveUS11343270B1Quantum computersKey distribution for secure communicationEngineeringQuantum codes
Systems, apparatuses, methods, and computer program products are disclosed for post-quantum cryptography (PQC). An example method includes receiving data. The example method further includes retrieving policy information associated with the data. The example method further includes generating a set of policy attributes about the data based on the data and the policy information. Subsequently, the example method includes generating a risk profile data structure based on the set of policy attributes. The risk profile data structure may be indicative of a vulnerability of the data in a PQC data environment.
Owner:WELLS FARGO BANK NA
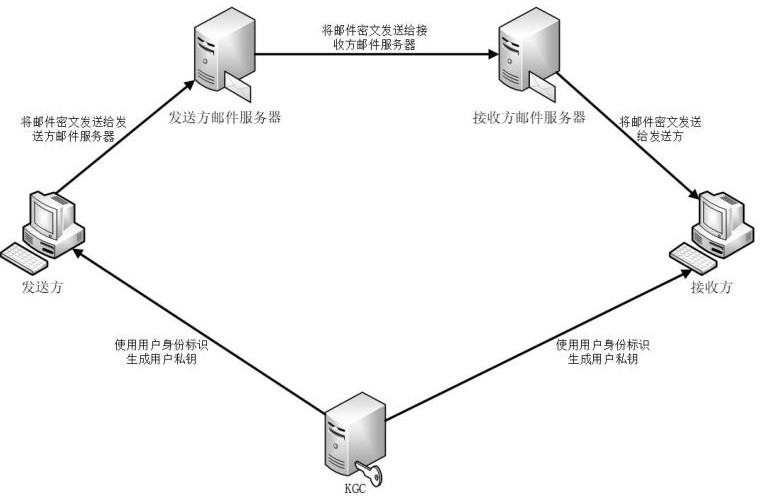
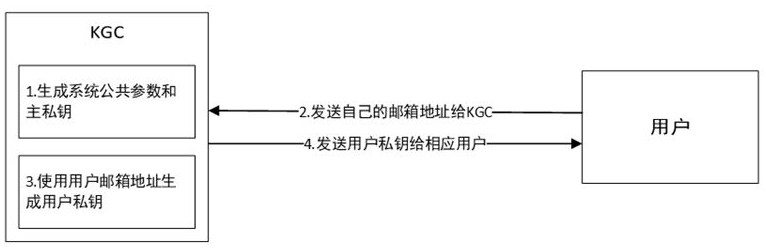
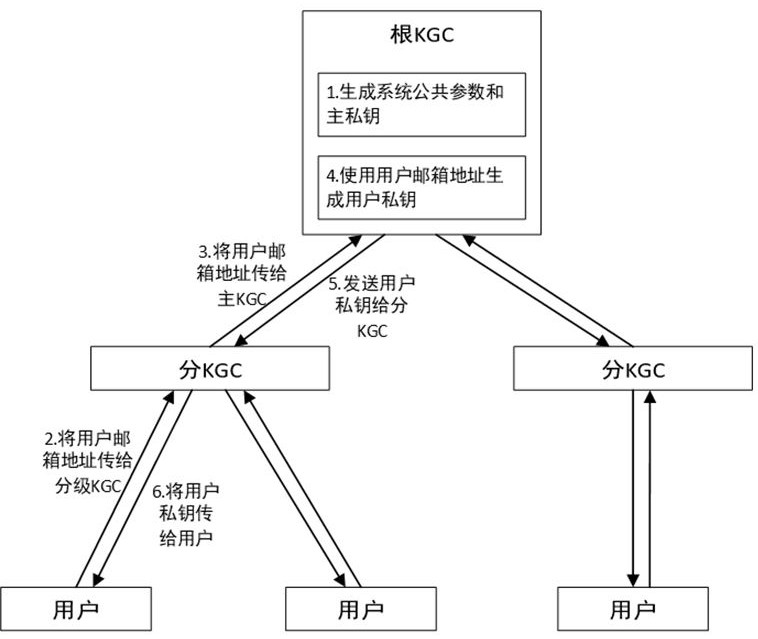
E-mail receiving and sending method and system based on post quantum and identity label
ActiveCN114024689AResistance to Computational AttacksAchieve securityKey distribution for secure communicationUser identity/authority verificationPlaintextCiphertext
The invention discloses an E-mail receiving and sending method and system based on post quantum and identity identification, and belongs to the technical field of secret communication. In the system, a KGC receives the identity identification sent by a user, generates a private key and returns the private key to the user; a sender sends an identity identifier to the KGC to obtain a sender private key, signs and encrypts a mail plaintext, and sends a mail ciphertext to a sender mail server; a sender mail server receives the mail ciphertext and delivers the mail ciphertext to a receiver mail server; a receiver mail server receives and stores the mail ciphertext; and a receiver sends the identity identifier to the KGC and obtains the private key of the receiver, receives the mail ciphertext from the mail server of the receiver and carries out decryption and signature verification on the mail ciphertext. According to the invention, based on the password system of the identity label, the defects of a complex public key acquisition mode and multiple authentication certificates are avoided; and meanwhile, a post-quantum cryptographic algorithm is combined, so that quantum computing attacks can be effectively resisted, and post-quantum secure communication is realized.
Owner:HUAZHONG UNIV OF SCI & TECH
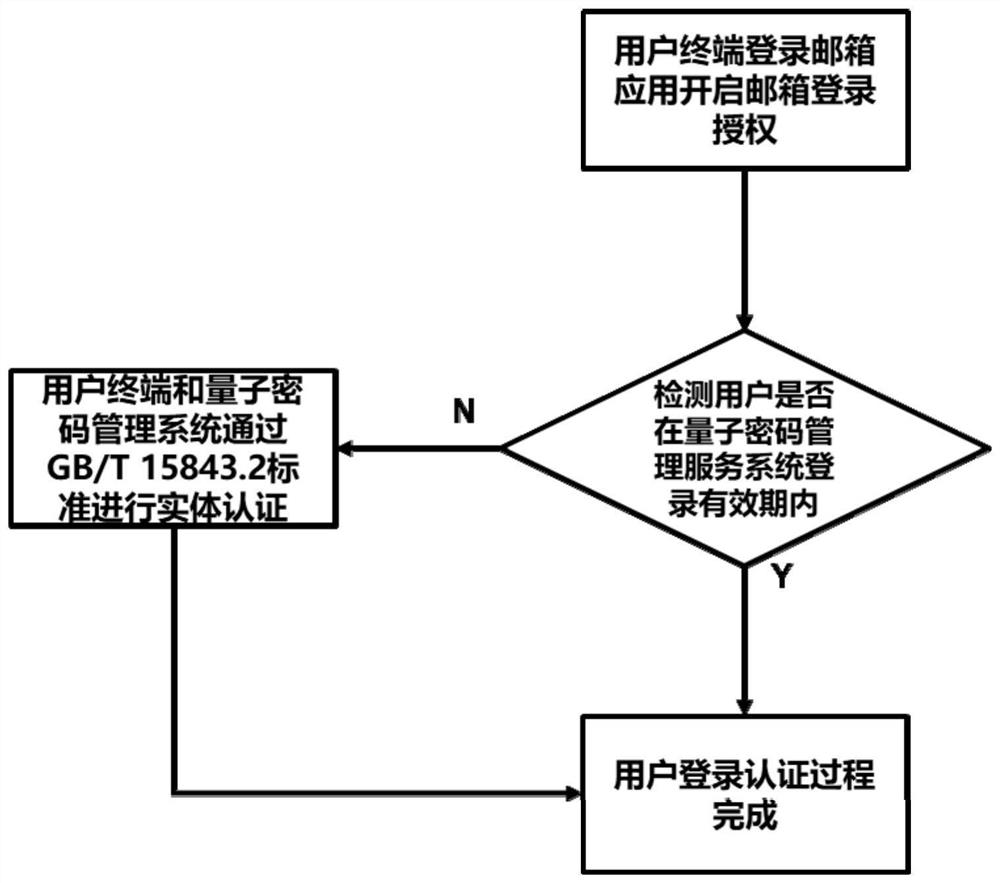
Sending mail encryption method based on quantum security key
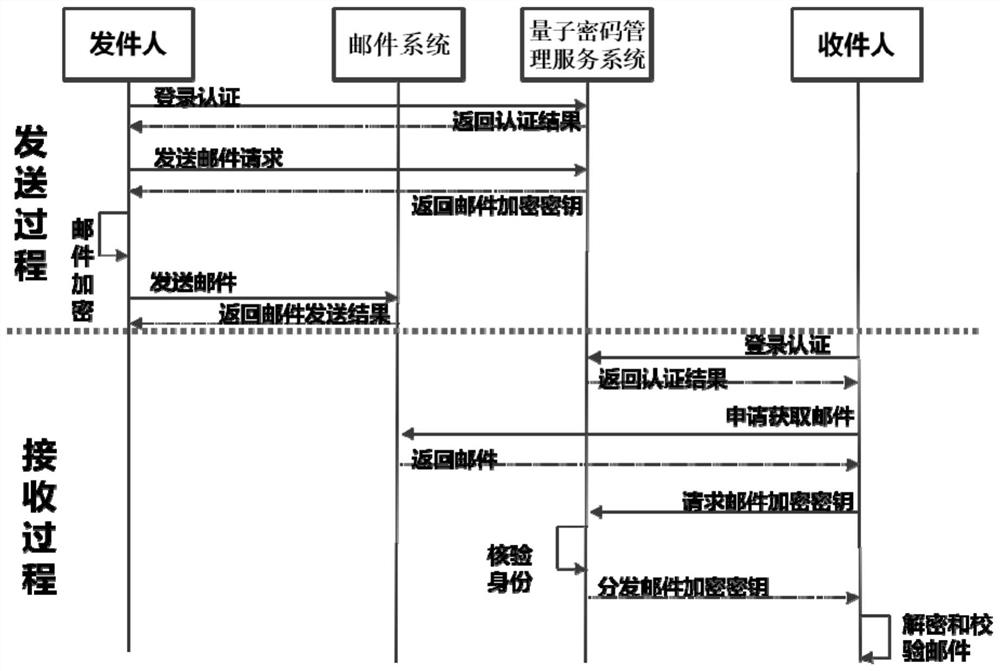
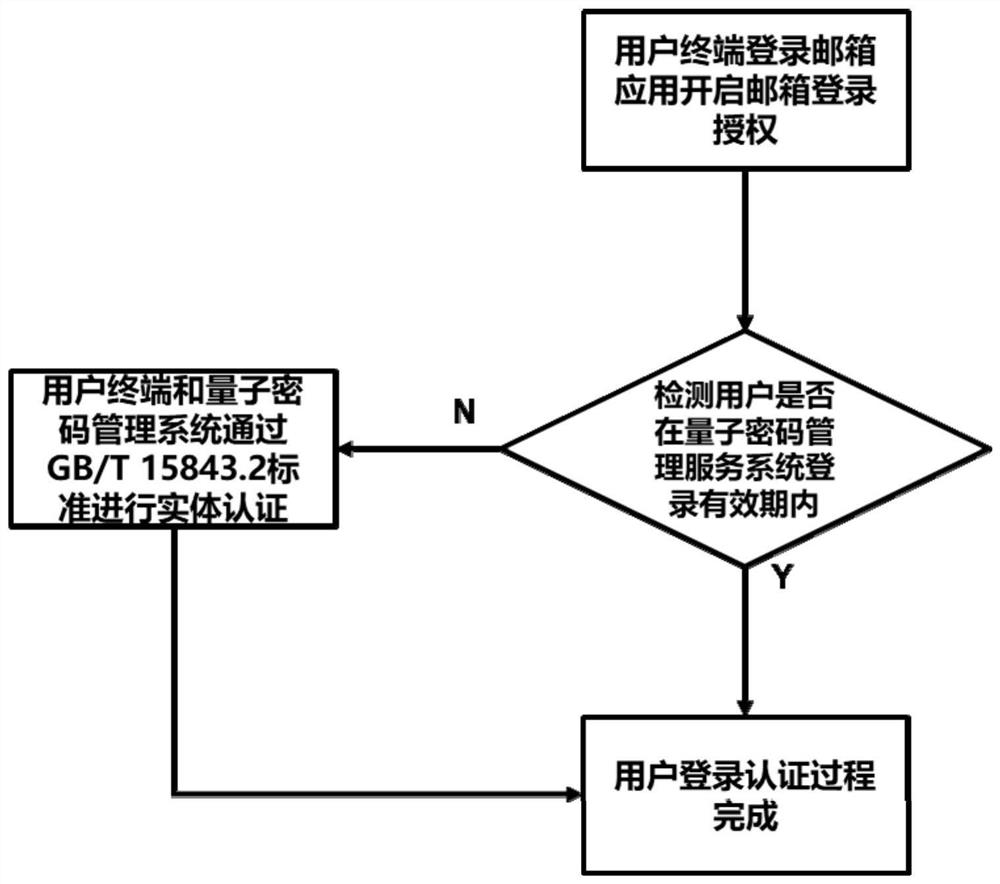
ActiveCN113452687AImprove securityReduce economic lossKey distribution for secure communicationUser identity/authority verificationInternet privacyQuantum algorithm
The invention provides a sending mail encryption method based on a quantum security key, which is applied to mail sending equipment. The method comprises the following steps that S1 ', before a mail is sent, mail sending equipment carries out identity verification through a quantum password management service system, the mail sending equipment reads a quantum security key preset in a built-in quantum security chip and carries out symmetric entity identity authentication with the quantum password management service system, and finally an authentication result is returned; S2 ', after the user completes login authentication in the step S1, when a mail needs to be sent, a sender needs to use a preset key in the quantum security chip to make an application for obtaining a mail encryption key to a quantum password management service system. By adopting the technical scheme, the threat of the environment with increasingly severe network attacks to the mailbox sending environment is solved, the security threat brought by a quantum computer and a quantum algorithm in the future is prevented, and the scheme is easy to implement.
Owner:中电信量子科技有限公司
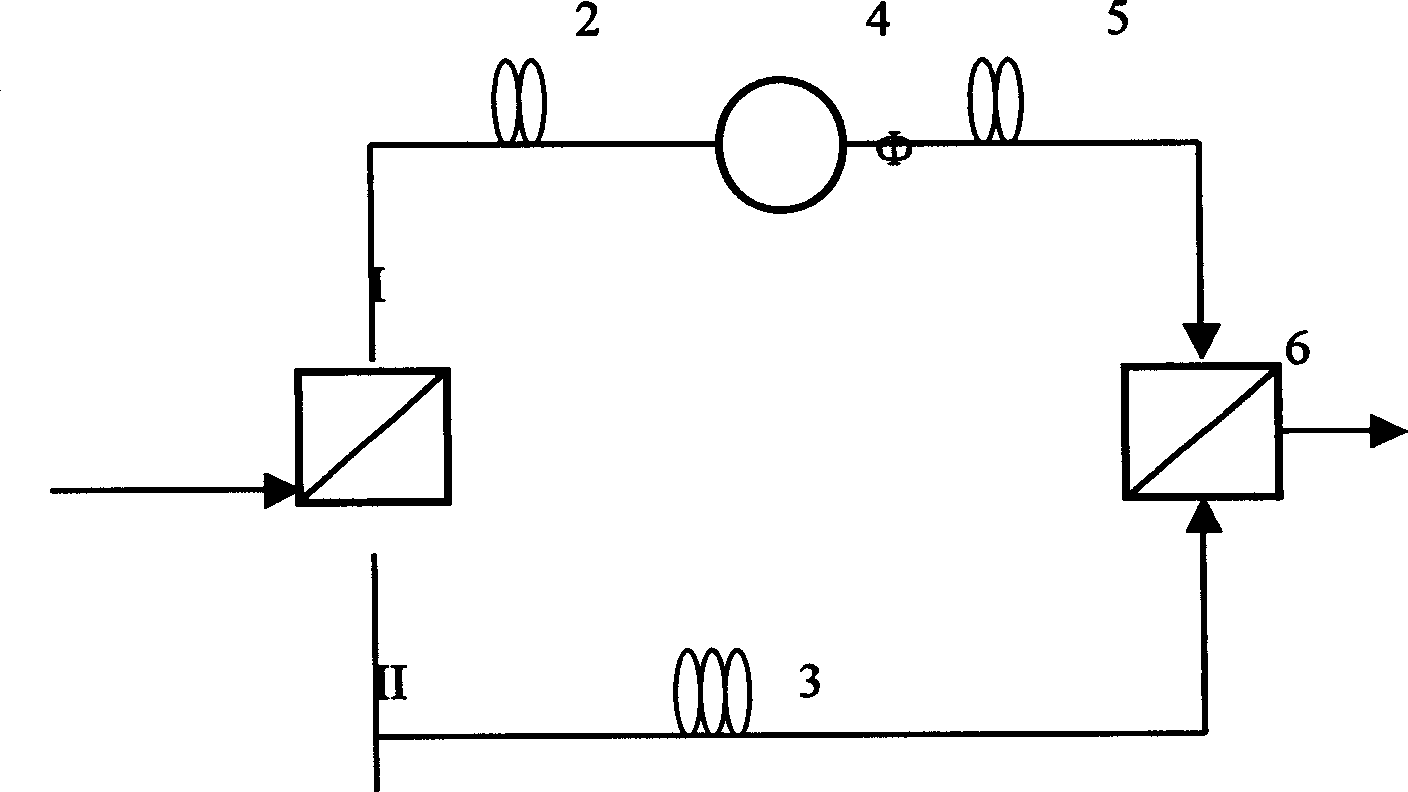
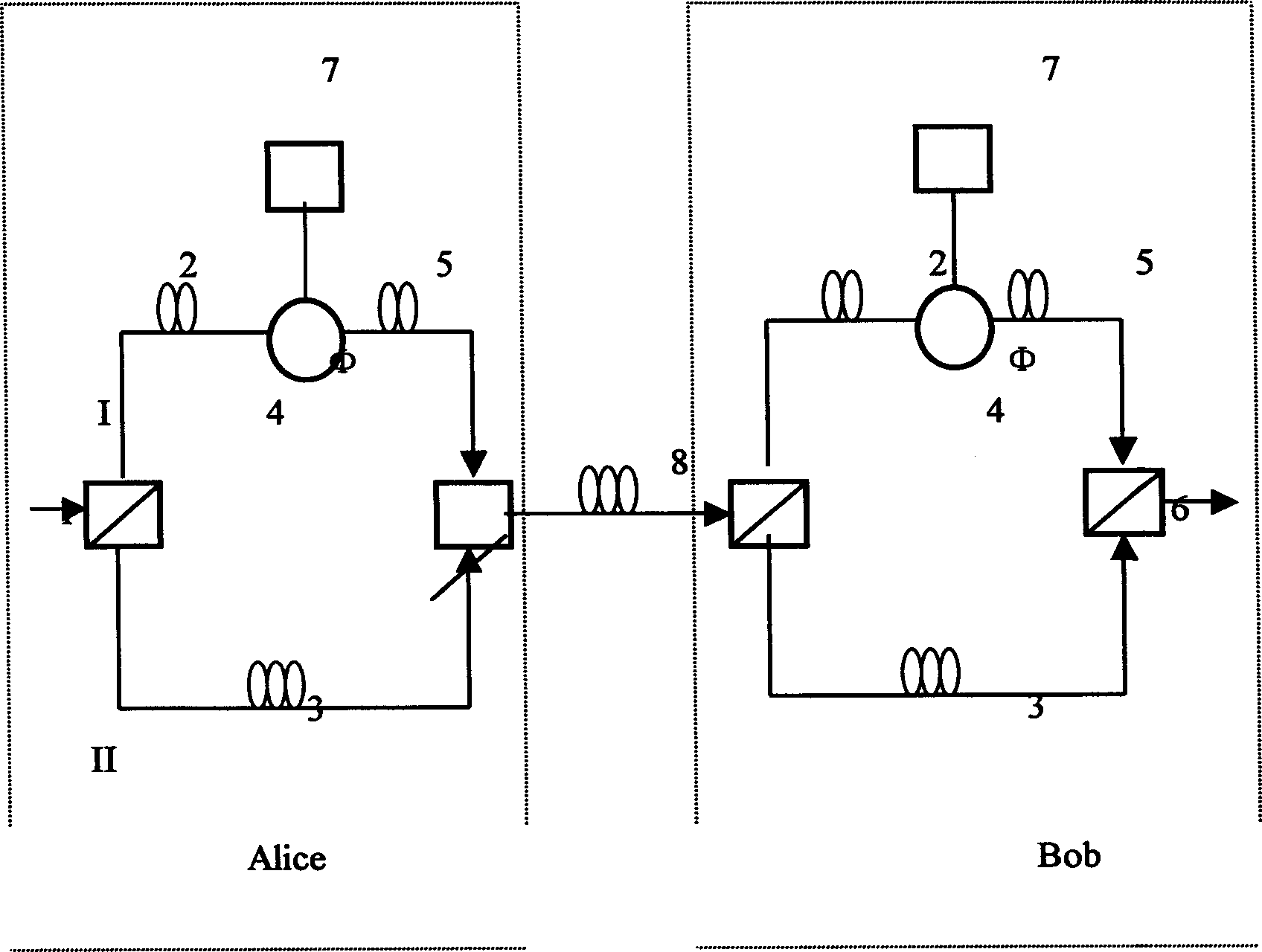
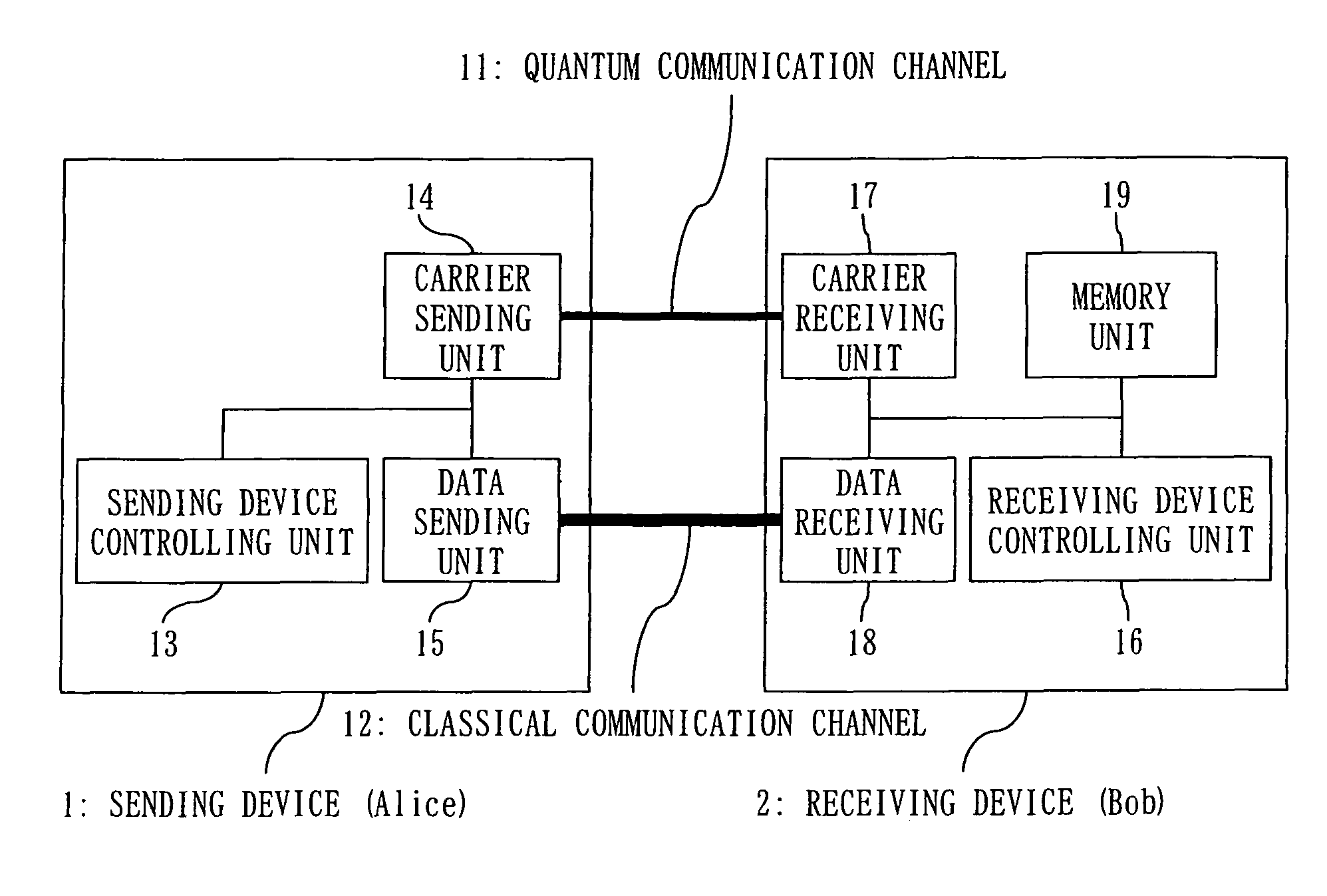
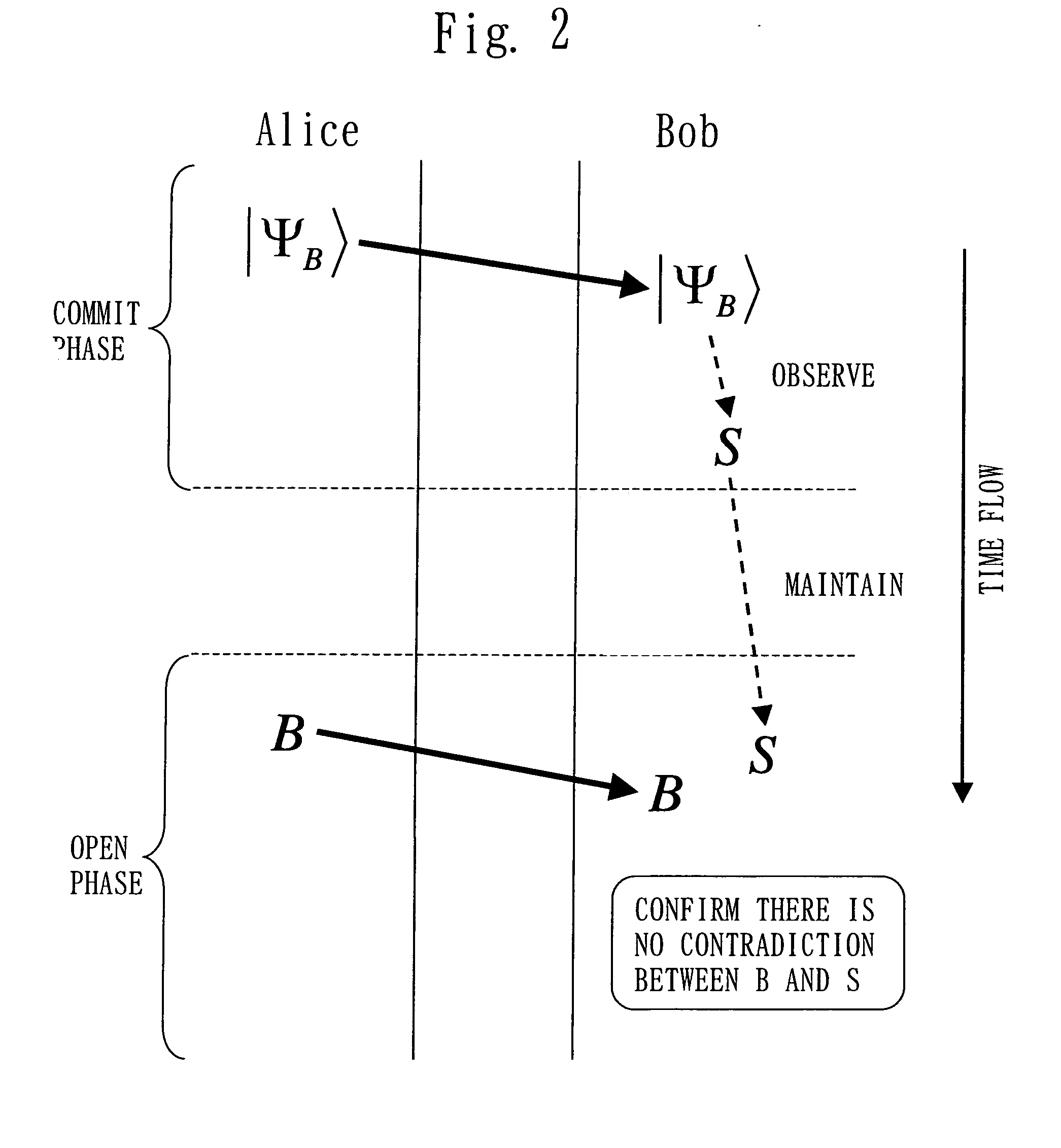
Quantum cryptography communication system
InactiveUS8155318B2Key distribution for secure communicationPhotonic quantum communicationCommunications systemCarrier signal
In a system carrying out cryptography communication using a quantum, it is aimed to correctly verify a quantum state received at the commit phase according to the quantum bit string commitment system, even if not maintaining the quantum state until the open phase but immediately observing the quantum state. According to the present invention, the quantum cryptography communication system includes a sending device 1 and a receiving device 2 connected by a quantum communication channel 11 and a classical communication channel 12. A carrier sending unit 14 of the sending device 1 sends a quantum to the quantum communication channel 11, a carrier receiving unit 17 of the receiving device 2 receives the quantum and observes its quantum state. A receiving device controlling unit 16 computes using the observation result and data sent from a data sending unit 15 of the sending device 1 to a data receiving unit 18 of the receiving device 2 through the classical communication channel 12, and outputs the result of cryptography communication derived from the computation.
Owner:MITSUBISHI ELECTRIC CORP
Post-quantum cryptographic communication protocol
ActiveUS10581604B2Key distribution for secure communicationMultiple keys/algorithms usageAlgorithmTheoretical computer science
Owner:COMSATS INST OF INFORMATION TECH
Apparatus and method for direct quantum cryptography system implementation over WDM telecommunication network
ActiveUS20200044835A1Accurate operationOvercome riskKey distribution for secure communicationPhotonic quantum communicationAutomatic controlTelecommunications network
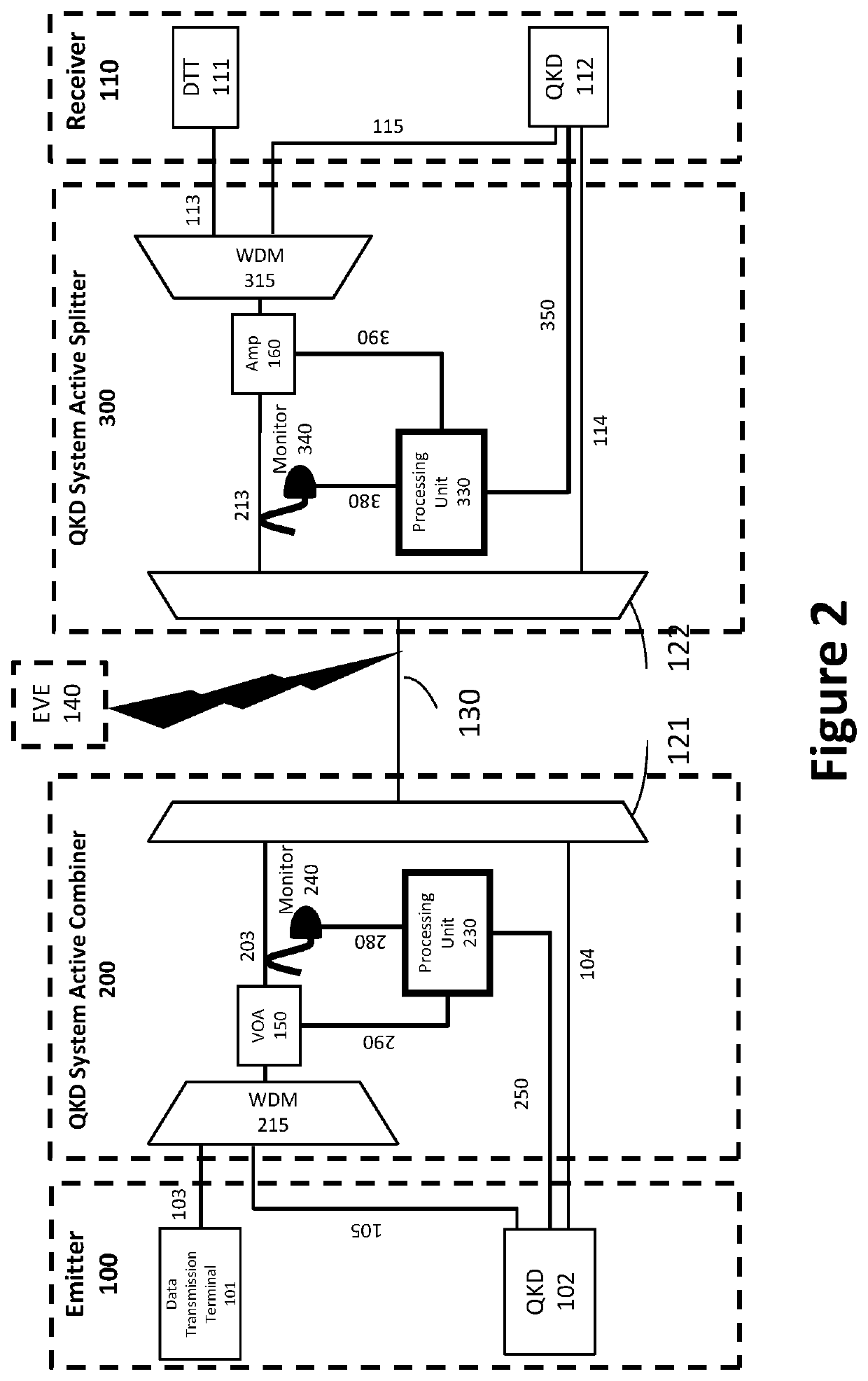
The invention relates to a QKD System Active combiner (200) adapted to be installed in a QKD apparatus, said QKD apparatus comprising an emitter (100), a receiver (110) and QKD systems (102 / 112), wherein the emitter (100) is adapted to send communication signals to the receiver (110) through the QKD System Active combiner (200), characterized in that the QKD System Active combiner (200) comprises an active attenuation system comprising a processing unit (230) adapted to automatically control at least one variable optical attenuator (150) through a control channel (290) in order to control an attenuation of a signal to be sent to the receiver, and a detector / monitor (240) adapted to monitor the intensity of the signal downstream the attenuation, and wherein the processing unit is adapted to control the variable optical attenuator (150) based on a QBER information or an intensity of a signal received by the receiver, sent by the QKD systems (112) through a classical channel (250).
Owner:ID QUANTIQUE SA
Device Securing Communications Using Two Post-Quantum Cryptography Key Encapsulation Mechanisms
ActiveUS20220038269A1Improve securityImprove security levelKey distribution for secure communicationPublic key for secure communicationKey (cryptography)Ciphertext
A network and a device can support secure sessions with both (i) a post-quantum cryptography (PQC) key encapsulation mechanism (KEM) and (ii) forward secrecy. The device can generate (i) an ephemeral public key (ePK.device) and private key (eSK.device) and (ii) send ePK.device with first KEM parameters to the network. The network can (i) conduct a first KEM with ePK.device to derive a first asymmetric ciphertext and first shared secret, and (ii) generate a first symmetric ciphertext for PK.server and second KEM parameters using the first shared secret. The network can send the first asymmetric ciphertext and the first symmetric ciphertext to the device. The network can receive (i) a second symmetric ciphertext comprising “double encrypted” second asymmetric ciphertext for a second KEM with SK.server, and (ii) a third symmetric ciphertext. The network can decrypt the third symmetric ciphertext using the second asymmetric ciphertext.
Owner:NIX JOHN A
Radio frequency identification authentication system and method based on quantum cryptography network
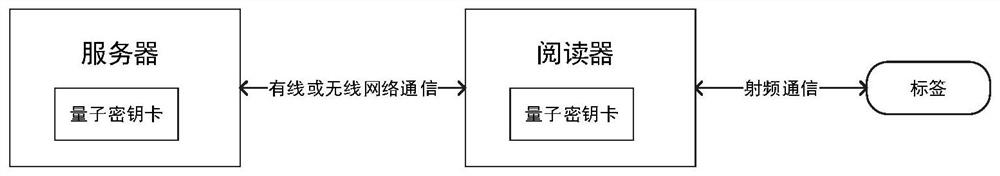
PendingCN114666040AImprove security strengthImplement updateKey distribution for secure communicationRf fieldKey (cryptography)
The invention belongs to the field of encryption communication of a quantum cryptography network, and provides a radio frequency identification authentication system and method based on the quantum cryptography network. The radio frequency identification authentication system based on the quantum cryptography network comprises a server, a reader, a quantum key card and a label, the ID of the reader and the corresponding authentication key thereof, and the ID of the tag and the corresponding authentication key thereof are stored in a database of the server; the server and the reader are respectively and correspondingly connected with the quantum key card, so that the server and the reader are subjected to identity bidirectional authentication through a quantum encryption channel; the reader and the tag communicate with each other through a radio frequency field, the server and the tag also adopt a bidirectional authentication mode to authenticate the identity, and when the bidirectional authentication of the identity between the reader and the server and the identity between the server and the tag succeeds, the radio frequency identification authentication succeeds.
Owner:QUANTUMCTEK +1
Systems and methods for post-quantum cryptography communications channels
ActiveUS11218301B1Key distribution for secure communicationEncryption apparatus with shift registers/memoriesKey (cryptography)Electronic communication
Systems, apparatuses, methods, and computer program products are disclosed for PQC. An example method includes transmitting a first portion of an electronic communication to a client device over a non-PQC communications channel. The example method further includes transmitting a quantum cryptographic key to the client device over a quantum communications channel and authenticating a session with the client device over the non-PQC communications channel based on the quantum cryptographic key. Subsequently, the example method includes, in response to authentication of the session with the client device, transmitting a second portion of the electronic communication to the client device over a PQC communications channel. In some instances, the first portion of the electronic communication may comprise overhead data, and the second portion of the electronic communication may comprise payload data.
Owner:WELLS FARGO BANK NA
Mail transmission system and transmission method based on quantum security key
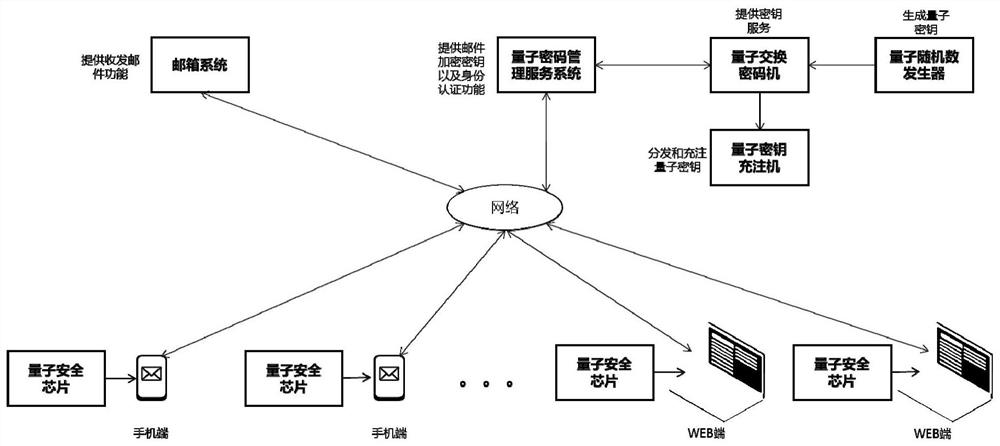
ActiveCN113285803AImprove securityAvoid threatsKey distribution for secure communicationUser identity/authority verificationTransceiverQuantum algorithm
The invention provides a mail transmission system and a mail transmission method based on a quantum security key. The mail transmission system comprises a mail box system; a quantum random number generator; a quantum exchange cipher machine in which a secret key is pre-stored; a quantum key charging machine which is connected with the output end of the quantum exchange cipher machine; a quantum password management service system which is used for providing a mail encryption key and an identity authentication function; quantum security chips which are used for storing quantum security keys, the keys stored in each quantum security chip and the keys pre-stored in the quantum exchange cipher machine are symmetric keys, and symmetric entity authentication is carried out on the security keys in the quantum security chips through a network and a quantum cipher management service system; and a mail transceiver which is internally or externally connected with a quantum security chip. By adopting the technical scheme, the threat of an environment with increasingly severe network attacks to a mailbox transceiving environment is solved, the security threat brought by a quantum computer and a quantum algorithm in the future is prevented, and the scheme is easy to implement.
Owner:中电信量子科技有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com