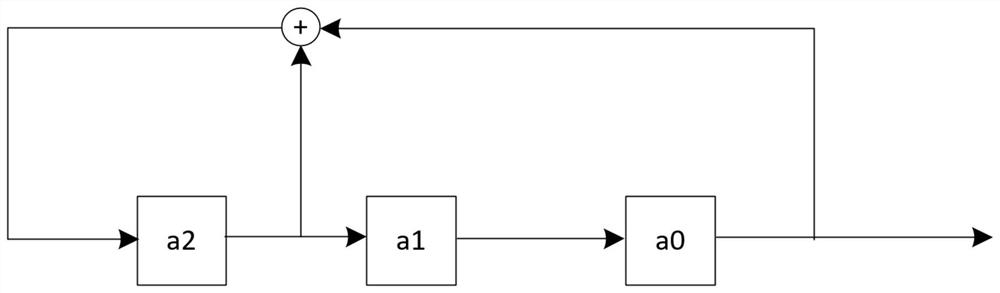
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
37 results about "Pseudo randomness" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
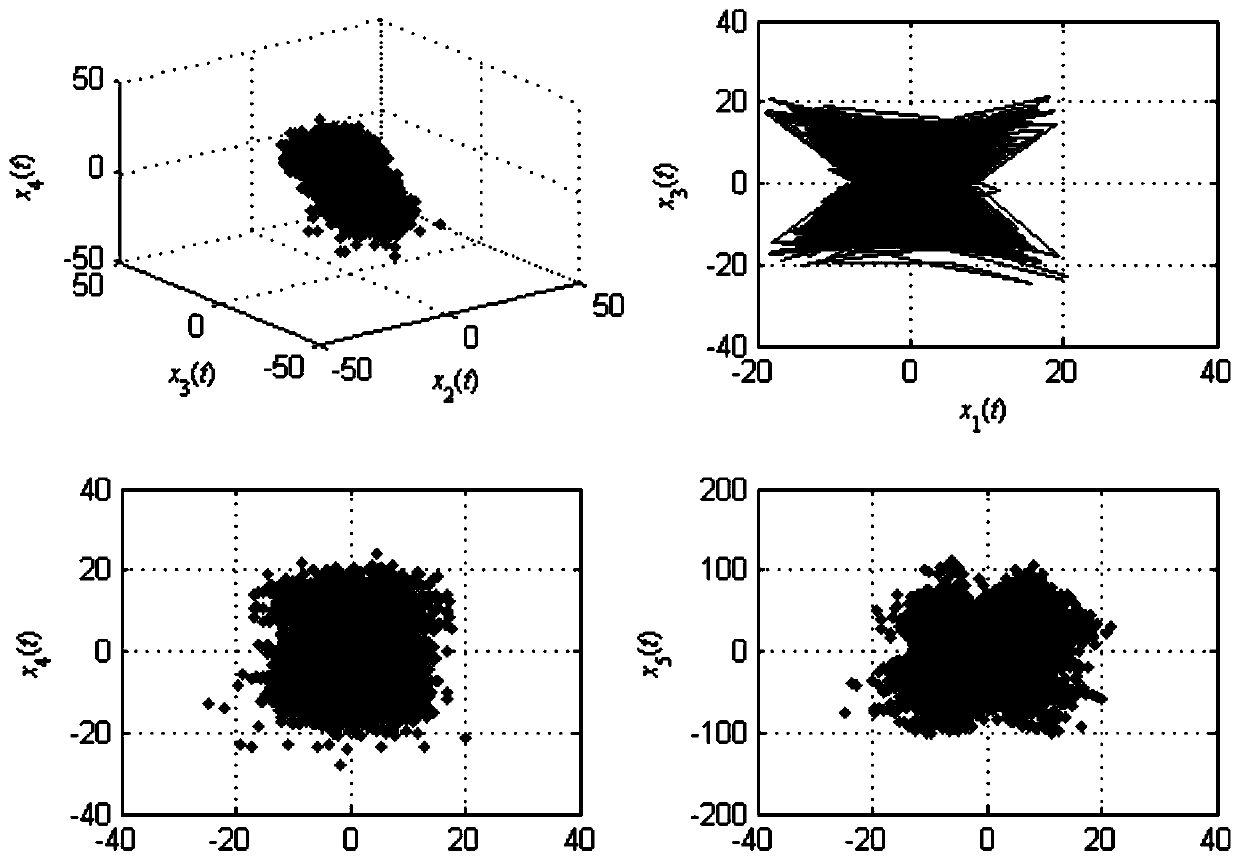
Pseudo-random numbers are essential to many computer applications, such as games and security. In computer security, pseudo-randomness is important in encryption algorithms, which create codes that must not be predicted or guessed. A pseudo-random number generator, or PRNG, is any program, or function, which uses math to simulate randomness.
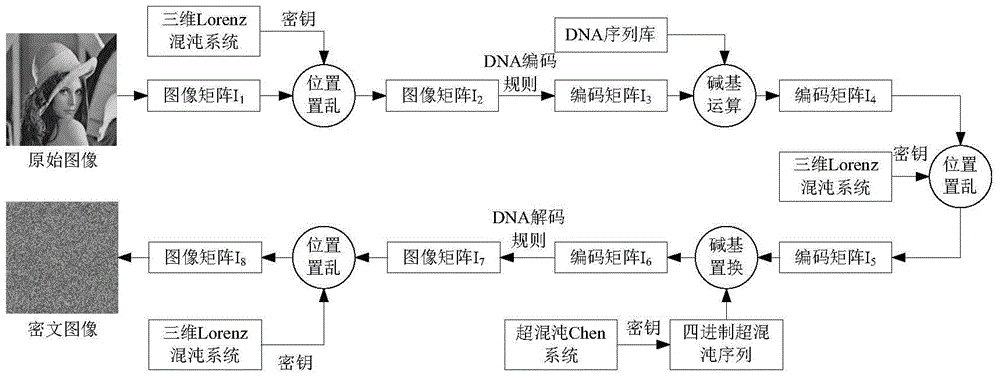
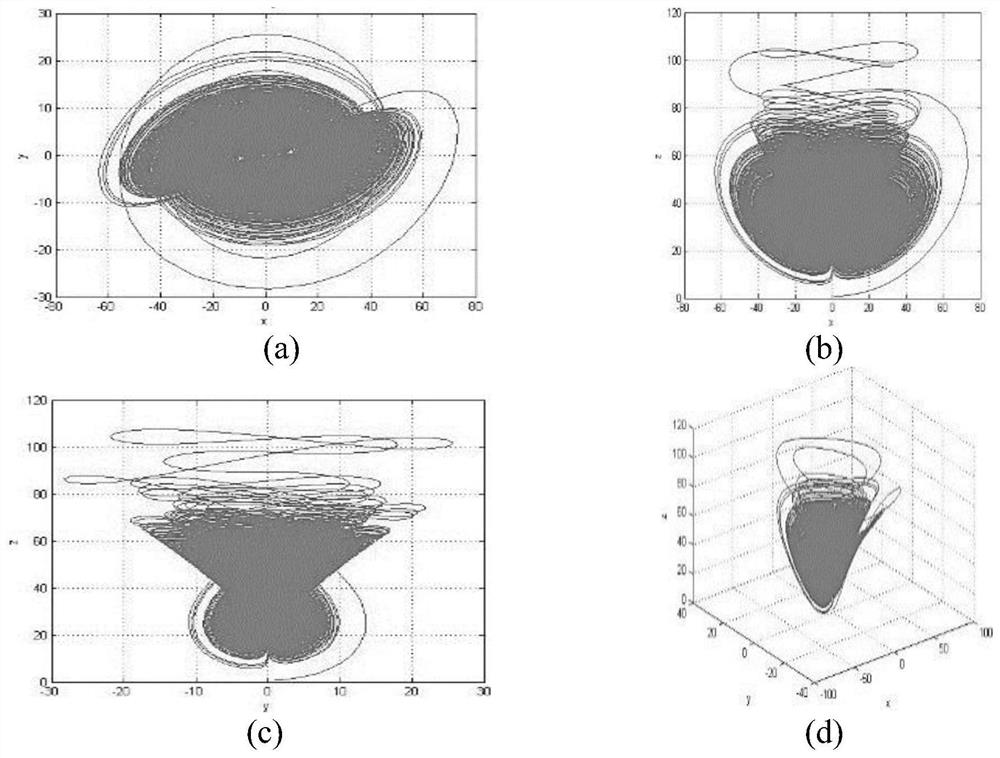
Digital image encryption method based on chaotic system and nucleotide sequence database
InactiveCN105046636AEnhanced confusionImprove featuresImage data processing detailsInformation processingSequence database
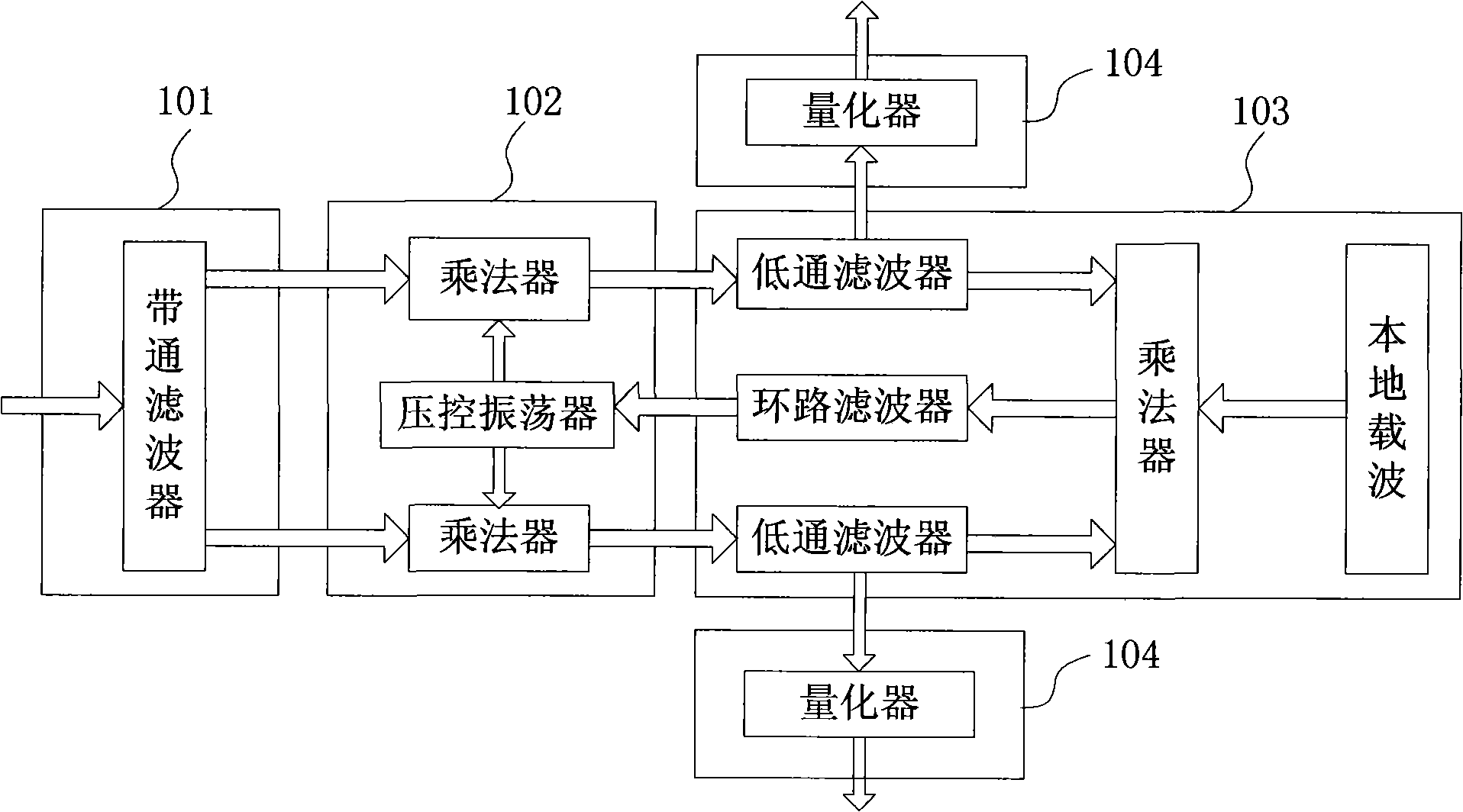
The invention provides a digital image encryption method based on a chaotic system and a nucleotide sequence database. The method comprises the following steps: image pixel positions are scrambled by chaotic mapping index sequence; an image pixel value undergoes DNA coding, and the DNA-coded image pixel value and a DNA sequence in a nucleotide sequence database undergo base operation; and the DNA-coded pixel undergoes base replacement according to a quanternary hyperchaos sequence generated by a hyperchaos Chen system, and confusion and diffusion properties are further enhanced by iteration of a ciphertext feedback and chaotic system. By means of sensibility and pseudo-randomness of chaotic mapping to initial conditions, by combining inherent spatial configuration and unique information processing capability of DNA molecules and through transformation and operation between two chaotic sequences, a DNA sequence database and pixel gray value, the purpose of confusion and diffusion is achieved so as to realize encryption of digital images. It shows through experimental results that the method has a large keyspace, has strong sensitivity to a secret key and can effectively defense attack operations such as statistical analysis, exhaustion analysis and the like.
Owner:ZHENGZHOU UNIVERSITY OF LIGHT INDUSTRY
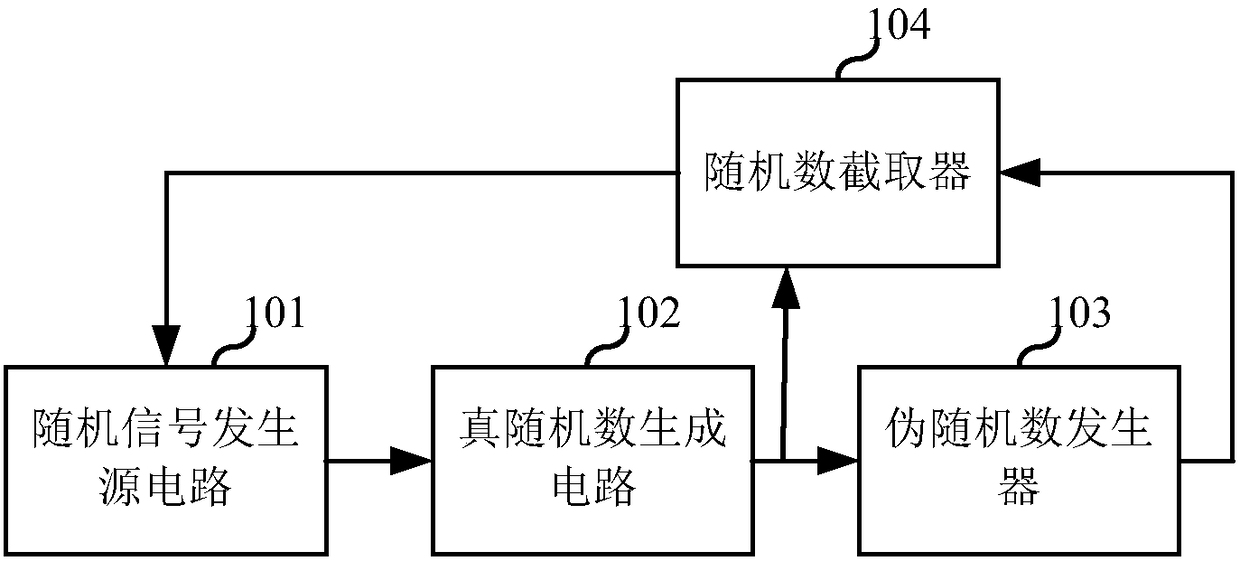
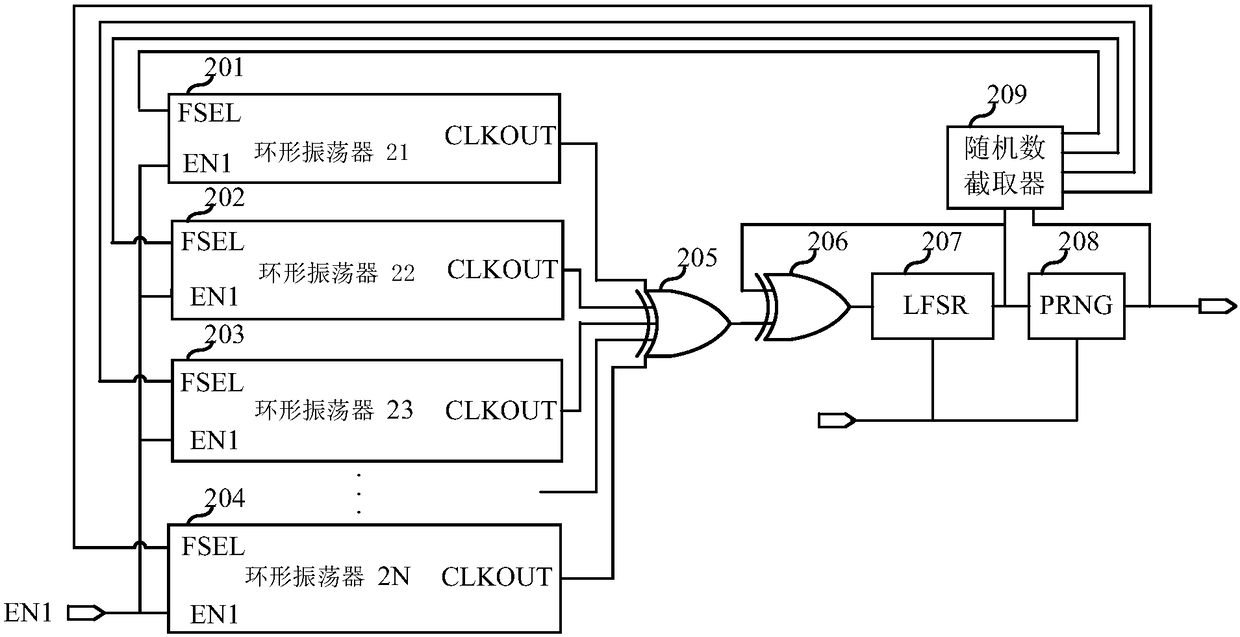
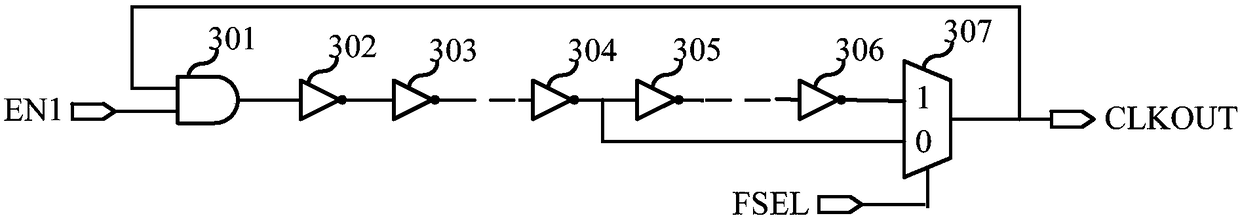
True random number generator
ActiveCN106293617AIncrease randomnessEliminate pseudo-randomnessRandom number generatorsReusabilityPseudo randomness
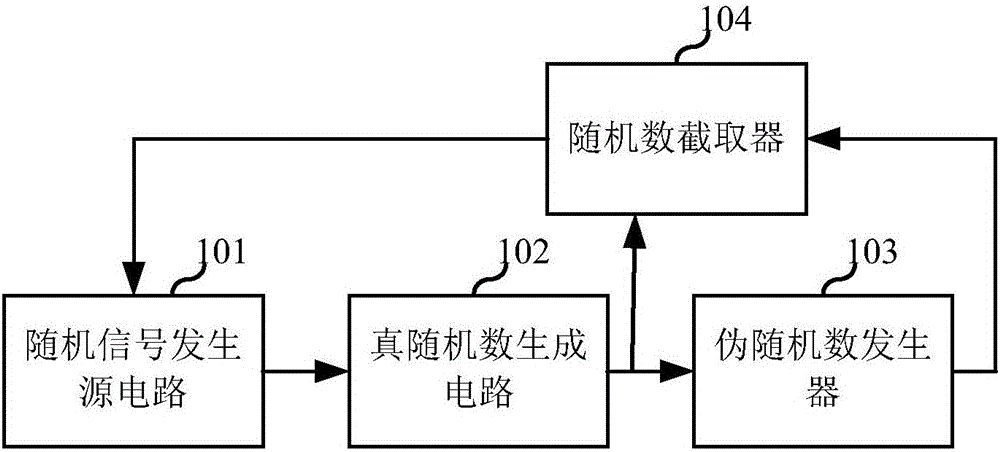
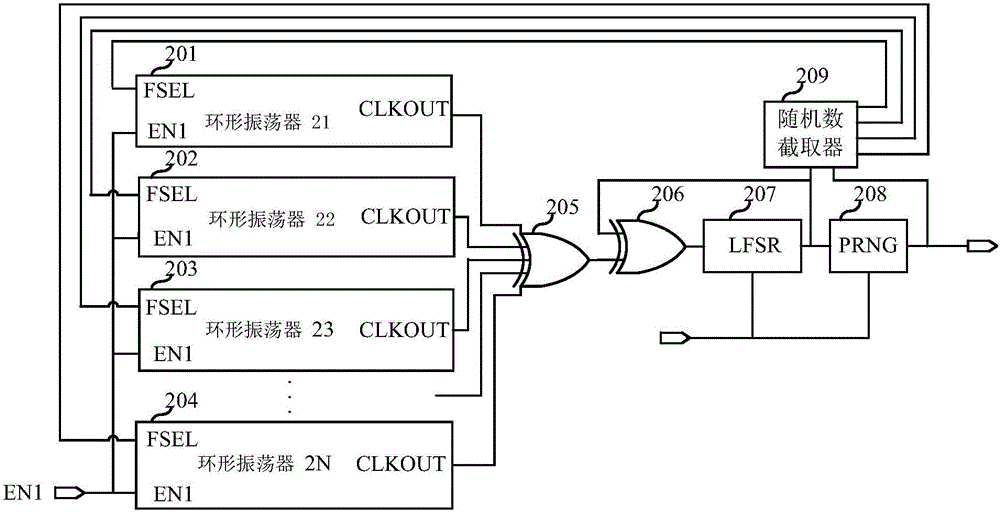
The invention relates to the technical field of circuits and discloses a true random number generator. The true random number generator comprises a random signal generation source circuit, a true random number generation circuit, a PRNG (pseudo random number generator) and a random number interceptor, wherein the random signal generation source circuit is used for generating random number generation source signals; the true random number generation circuit is used for sampling and diffusing the random number generation source signals and a true random number sequence is obtained; the PRNG is used for outputting the serial or parallel random number sequence according to the input true random number sequence; the random number interceptor is used for intercepting the random number sequence of the preset length from the random number sequence output from the PRNG according to the input true random number sequence and feeding back the intercepted random number sequence to the random signal generation source circuit; the random signal generation source circuit is used for adjusting the random number generation source signals according to the random number sequence fed back by the random number interceptor. The true random number generator can be realized through an ordinary logic device, the circuit structure is simple, the true random number generator is independent of the process and has good reusability, and a feedback mechanism is added, therefore, pseudo-randomness due to long-time working without feedback can be eliminated.
Owner:上海坚芯电子科技有限公司
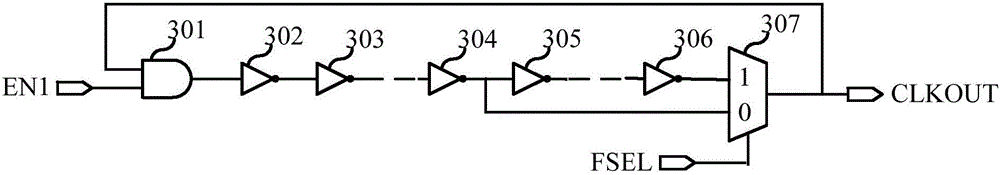
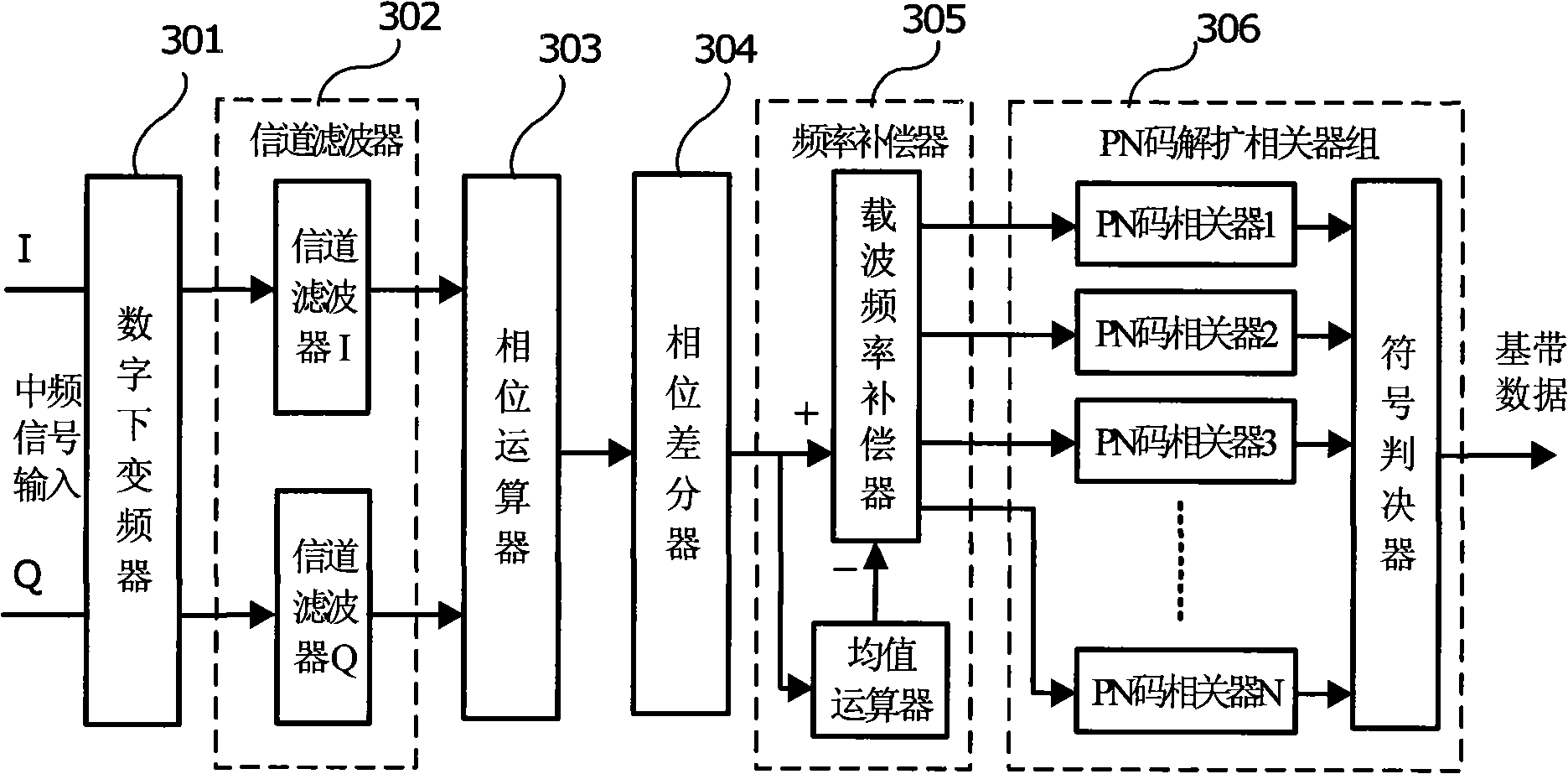
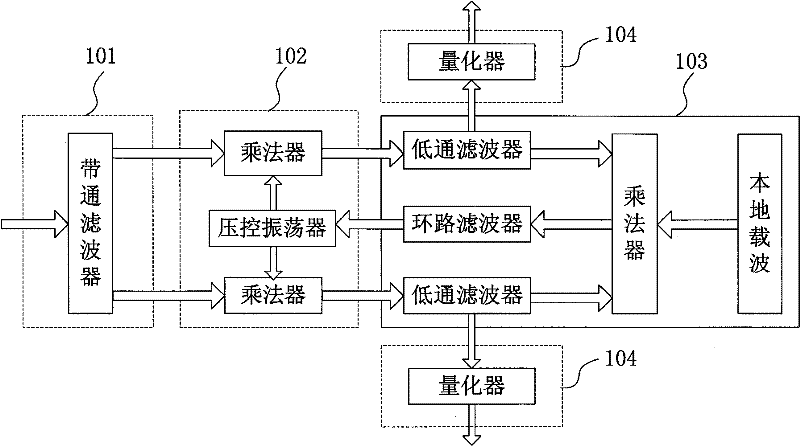
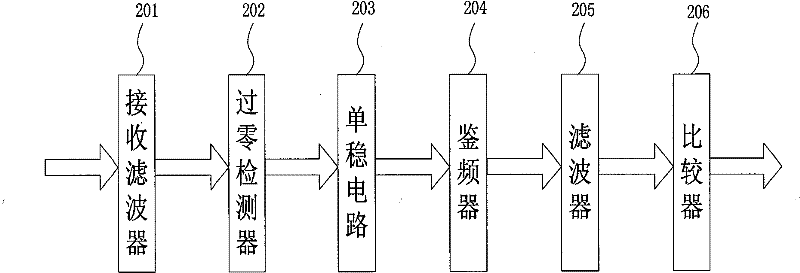
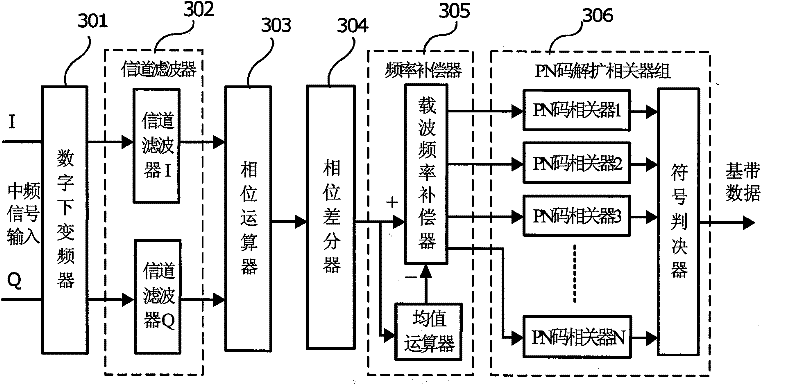
Non-coherent frequency compensation and modulation method and demodulating apparatus
InactiveCN101309253ASimpler than coherent demodulationReduce hardware requirementsMultiple carrier systemsShortest distanceTime signal
The invention proposes an incoherent frequency compensation and demodulation method and a demodulation device which have low power consumption, high performance and use the pseudo-randomness of the received signal phase and the PN code to realize the wireless digital communication data demodulation which has short distance, low power consumption and low packet loss rate through the carrier frequency error compensation and data recovery; the demodulation device is composed of a digital low-converter, a channel filter, a phase arithmetic unit, a phase differentiator, a frequency compensator and a PN code de-spreading correlator; the intermediate signal is converted into the plural baseband signals which are processed with channel outer band noise filtration so that the amplitude-time signal is converted into the phase-time signal; the phase differentiator is adopted to differentiate the phase-time signal; the frequency compensation circuit compensate the carrier frequency according to the phase difference signal and the phase average signal; the carrier frequency and the phase recovery circuit are avoided; the PN code correlator group processes the matching demodulation towards the semi-cosine shaping OQPSK and MSK signals of the DSSS directly to recover the baseband data; the incoherent frequency compensation and demodulation method and the demodulation device has the advantages of simple circuit, less quantity of hardware, easy low power consumption integration, good demodulation performance and being applicable to the wireless satellite navigation and the short-range wireless communication device with batteries as the power supply.
Owner:杭州中科微电子有限公司
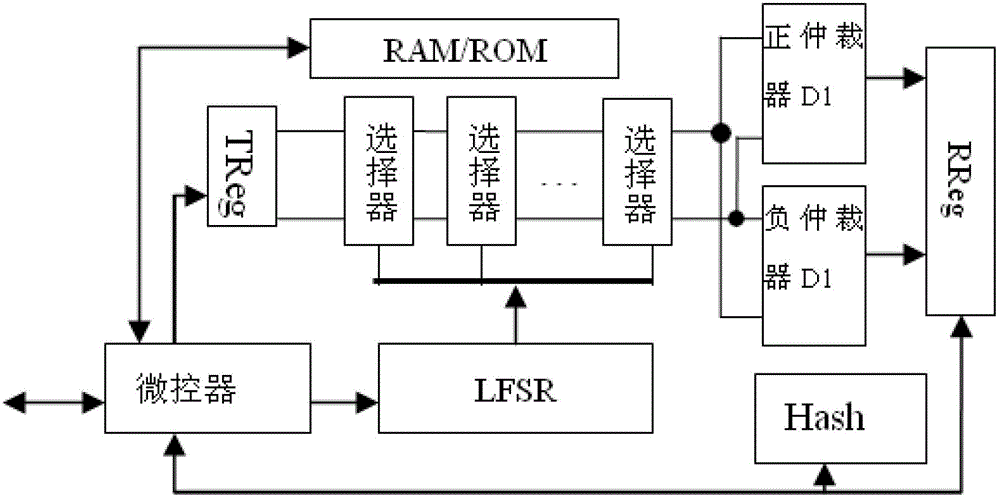
Secret key and true random number generator and method for generating secret key and true random number
InactiveCN103188075AReduce areaHigh speedKey distribution for secure communicationGeneration processMicrocontroller
The invention discloses a secret key and true random number generator and a method for generating a secret key and a true random number. The generator comprises a double-arbiter physically unclonable function (DAPUF), a trigger signal generation register (TReg), a response acquisition register (RReg), a microcontroller, a linear feedback shift register (LFSR), a Hash engine, a volatile memory and a nonvolatile memory. The invention also aims at providing a method for generating the secret key and the true random number. The method comprises the steps of: (1) initialization process of the secret key; (2) reconstruction process of the secret key; (3) initialization process of the true random number; and (4) the generation process of the true random number. The secret key and the true random number which are obtained by combining the response of the DAPUF with the steps in the method have the effects that (1) the error rate of the generated secret key is decided by the noise of the DAPUF and the election times of a majority of election methods, and the error rate of the generated secret key can be reduced unlimitedly; and (2) the LFSR is updated for a number of times, so that a random seed becomes an uncertain entropy source, and after the response which is generated by taking the uncertain entropy source as challenge is treated by the Hash, so that the output true random number meets the pseudo-randomness.
Owner:GUANGZHOU UNIVERSITY +5
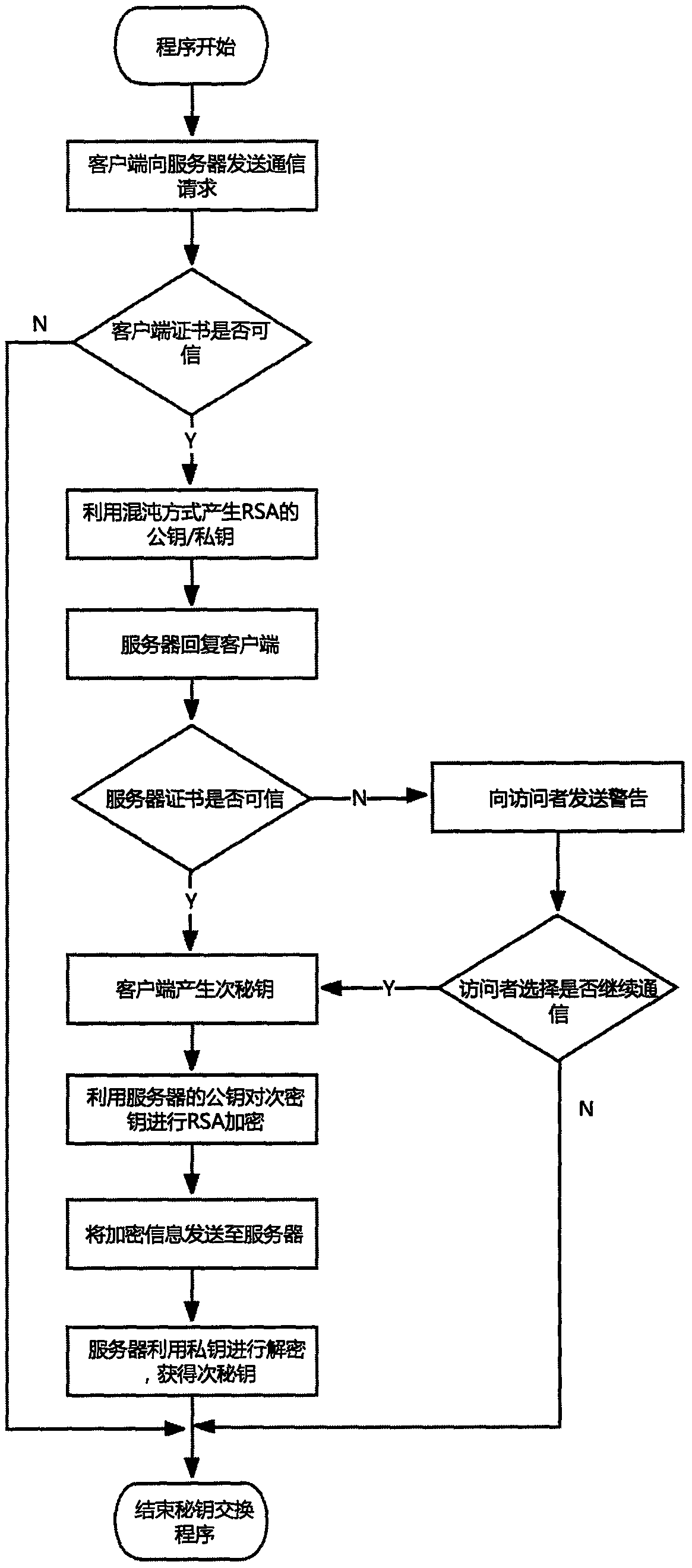
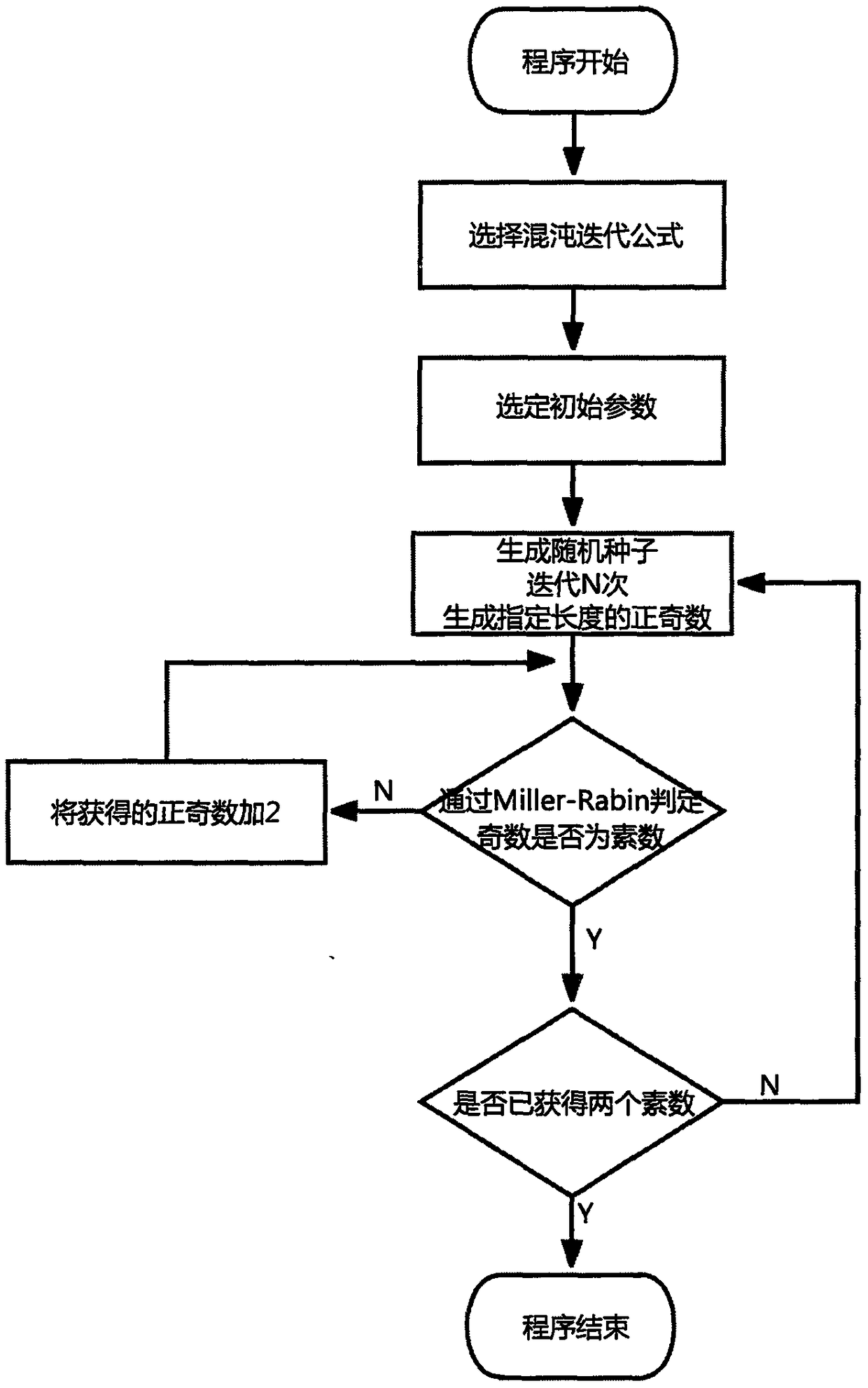
OPC UA (OPC Unified Architecture) key exchange method based on chaotic RSA encryption
InactiveCN108282327AReduce usageGood for encryptionPublic key for secure communicationUser identity/authority verificationKey exchangePseudo randomness
The invention provides an OPC UA (OPC Unified Architecture) key exchange method based on chaotic RSA encryption, and relates to industrial data communication and information security. The method is mainly used for securely exchanging key information between an OPC UA client and a server in order to complete a conversion process from asymmetric encryption to symmetric encryption. According to the method, a large prime number meeting requirement is generated according to the pseudo randomness of a chaotic sequence in order to replace a step of generating a prime number in traditional RSA. Through the establishment of a security channel between the OPC UA client and the server, a security mechanism of current communication is negotiated, and then key exchange is carried out. Through generation of the large prime number by the principle of chaos in the method, the encryption efficiency between OPC UA systems is increased. Moreover, the security of a key in an exchange process is ensured through design of a strict authentication and communication flow; symmetric encryption communication between OPC UA is realized; and the security and timeliness required in an industrial information exchange system are realized.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
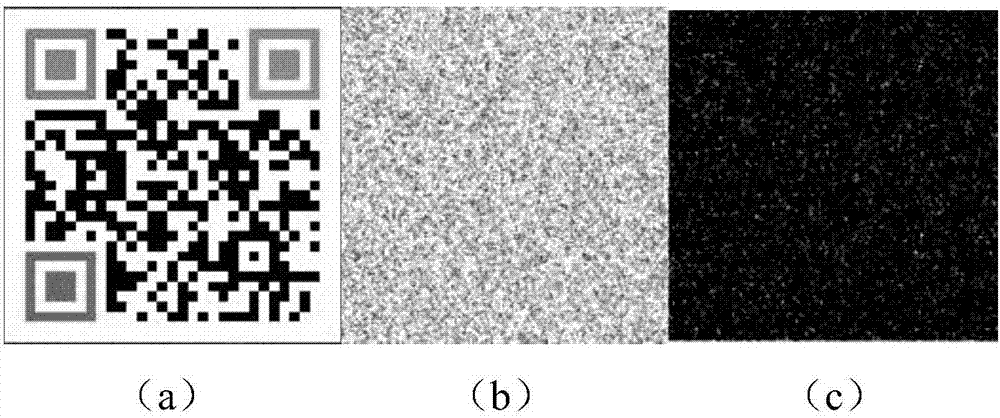
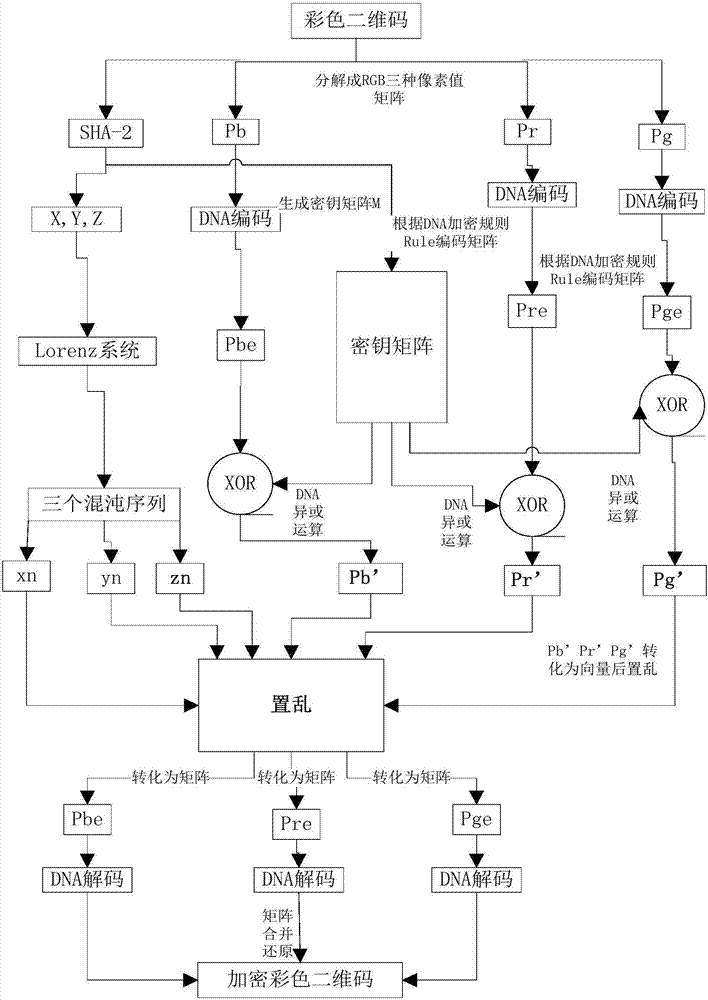
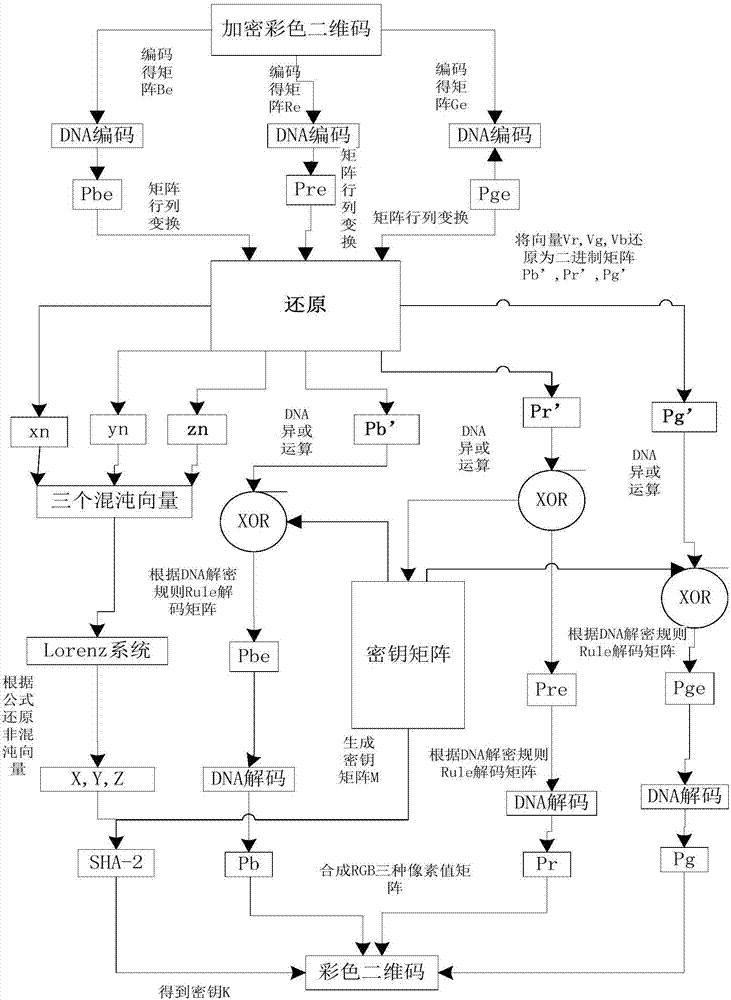
Color two-dimensional bar code encryption and decryption method in high-dimensional chaotic system
InactiveCN107086913AKey distribution for secure communicationEncryption apparatus with shift registers/memoriesComputer hardwarePseudo randomness
The invention provides a color two-dimensional bar code encryption and decryption method in a high-dimensional chaotic system. According to the method, application methods of a DNA sequence and an SHA-256 algorithm in the high-dimensional chaotic system are defined, and the DNA sequence and the SHA-256 algorithm are applied to encryption and decryption of a color two-dimensional bar code. An encryption method relates to steps such as generating a key and an initial value; carrying out coding through utilization of DNA; carrying out exclusive or operation on color two-dimensional bar code and key matrixes; carrying out color two-dimensional bar code matrix value substitution; carrying out decoding through utilization of the DNA; and synthesizing the encrypted color two-dimensional bar code. A decryption method is reverse operation for the encryption method. From a simulation experiment, it is observed that the method provided by the invention has relatively high pseudo-randomness, forgery prevention and attack resistance.
Owner:CIVIL AVIATION UNIV OF CHINA
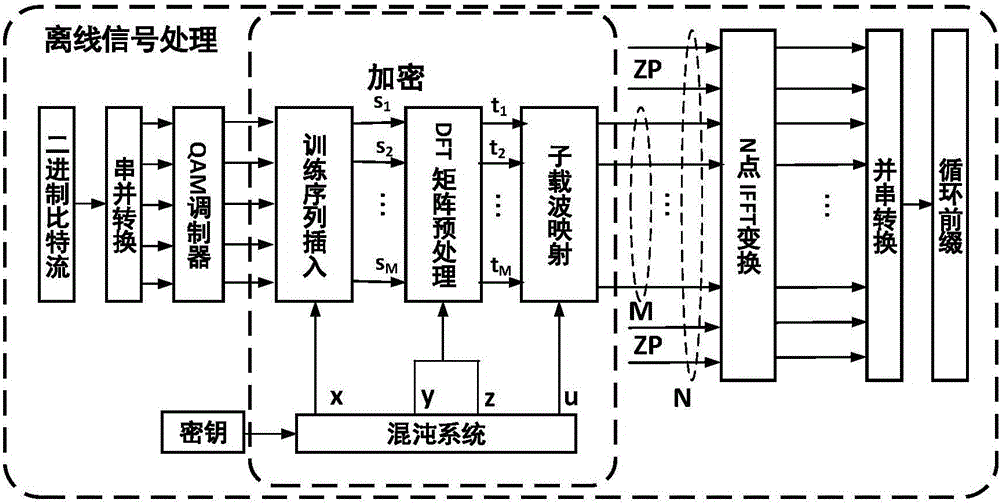
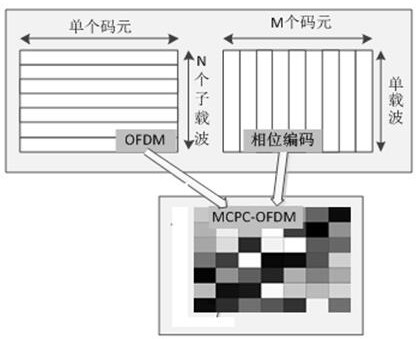
Light DFT-S-OFDM secure transmission system based on digital chaos
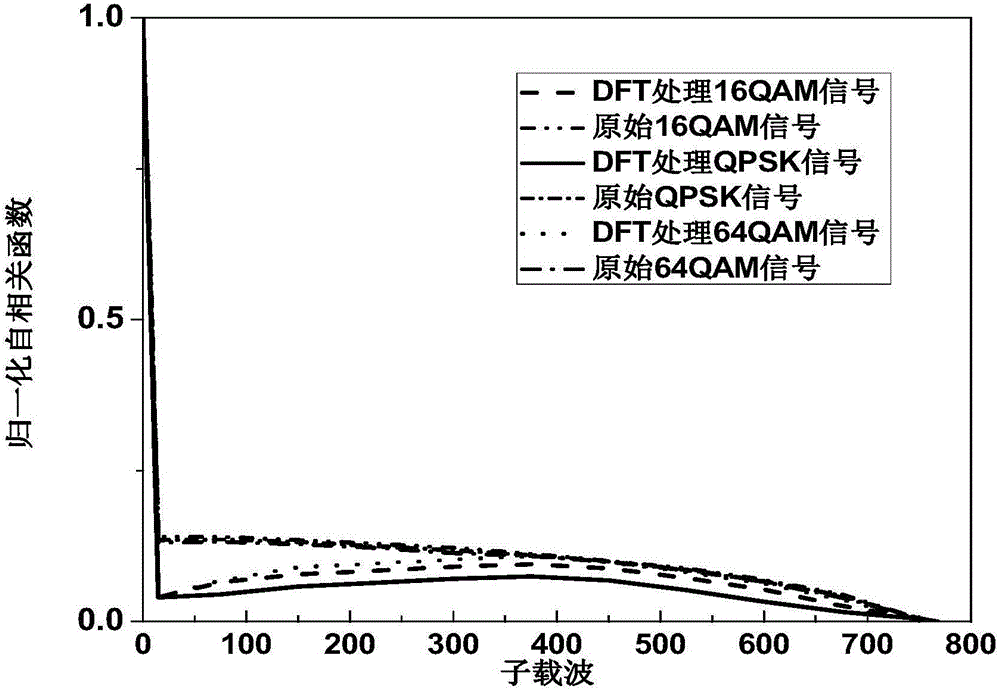
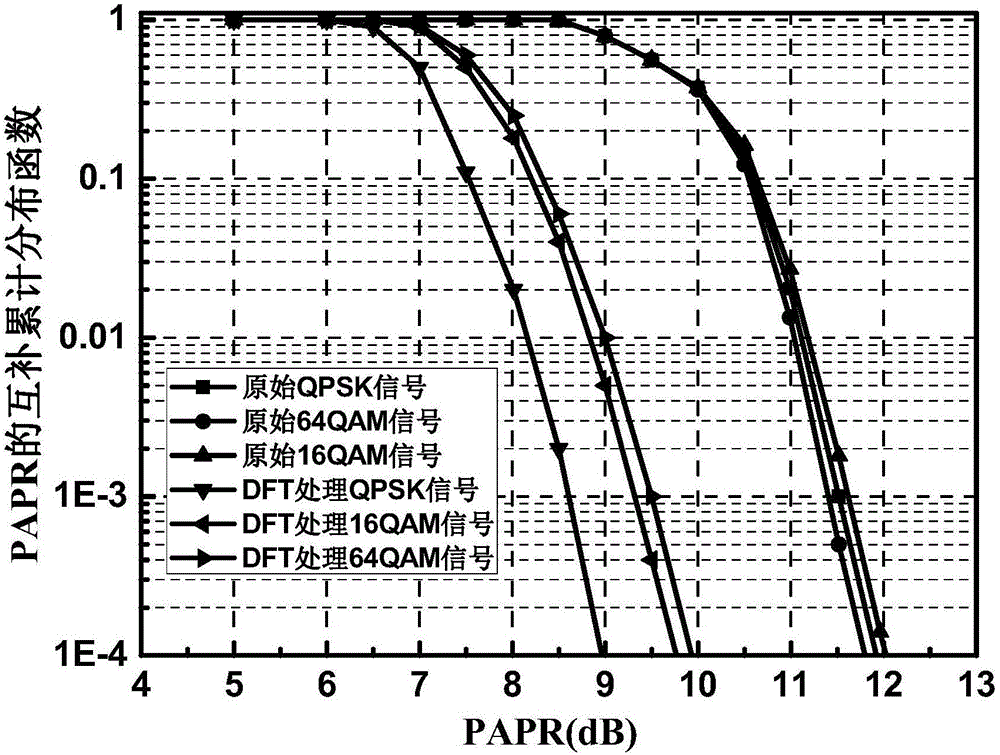
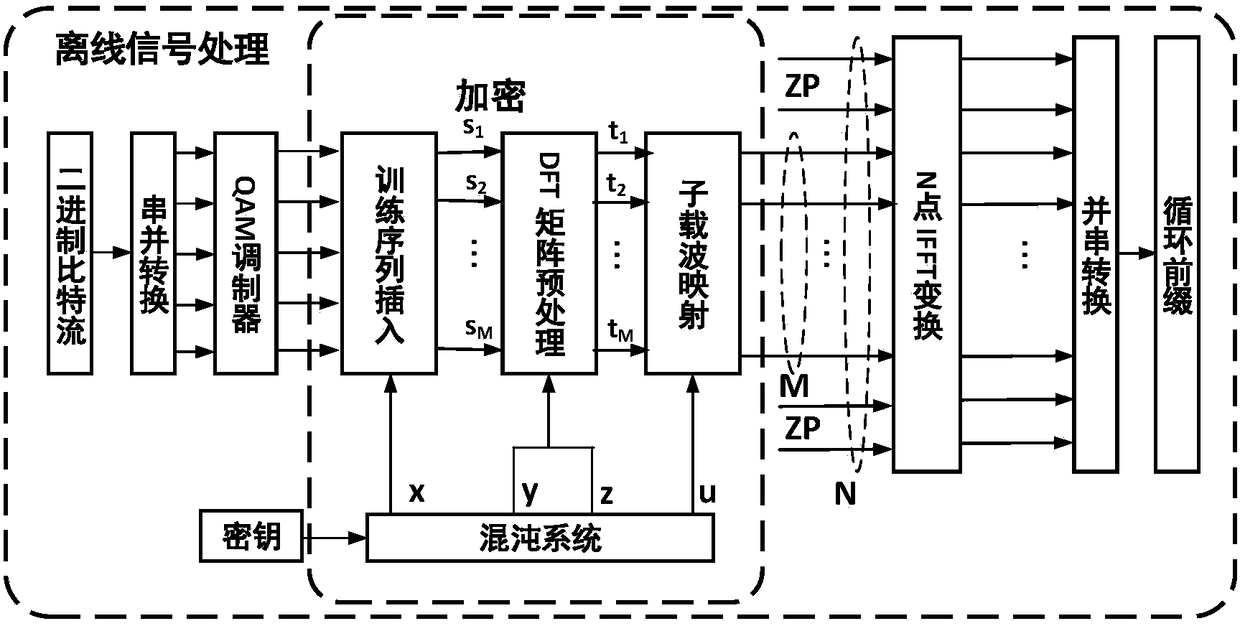
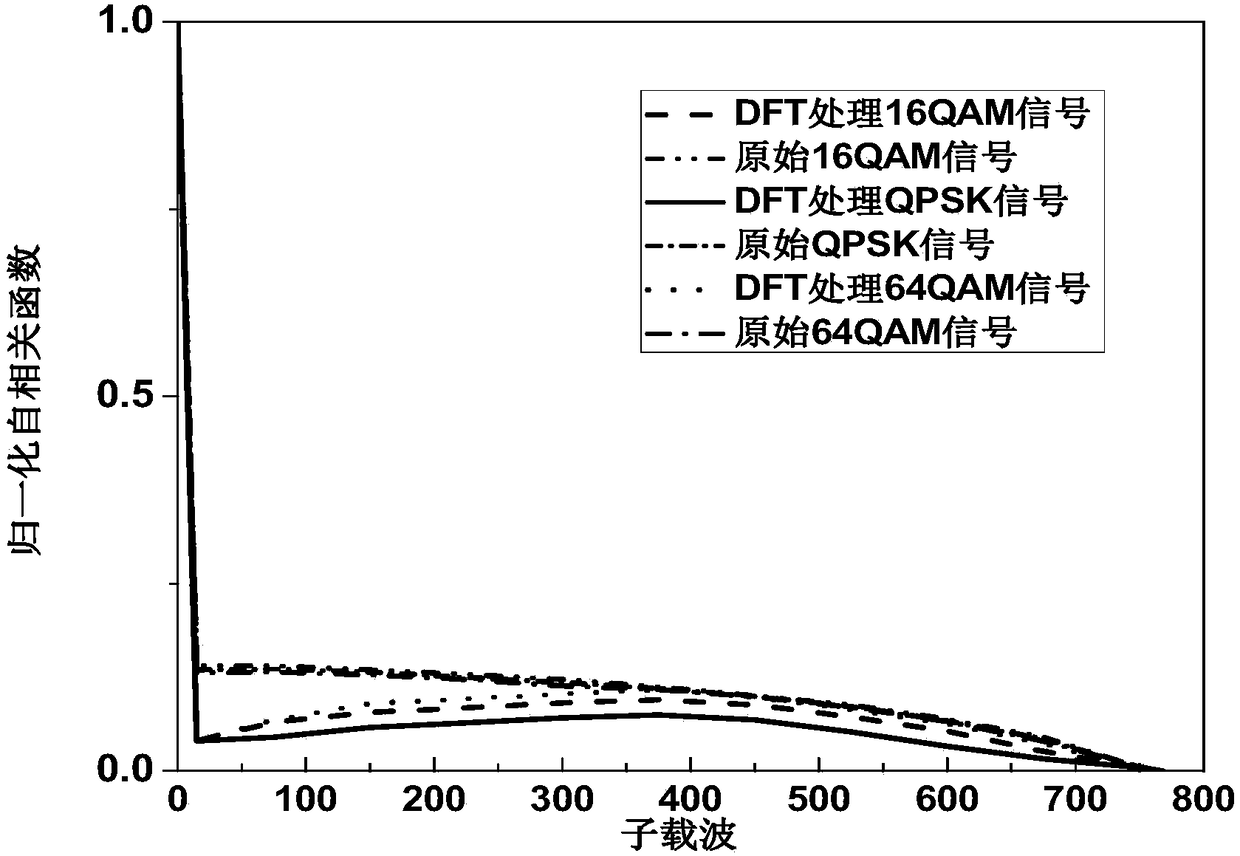
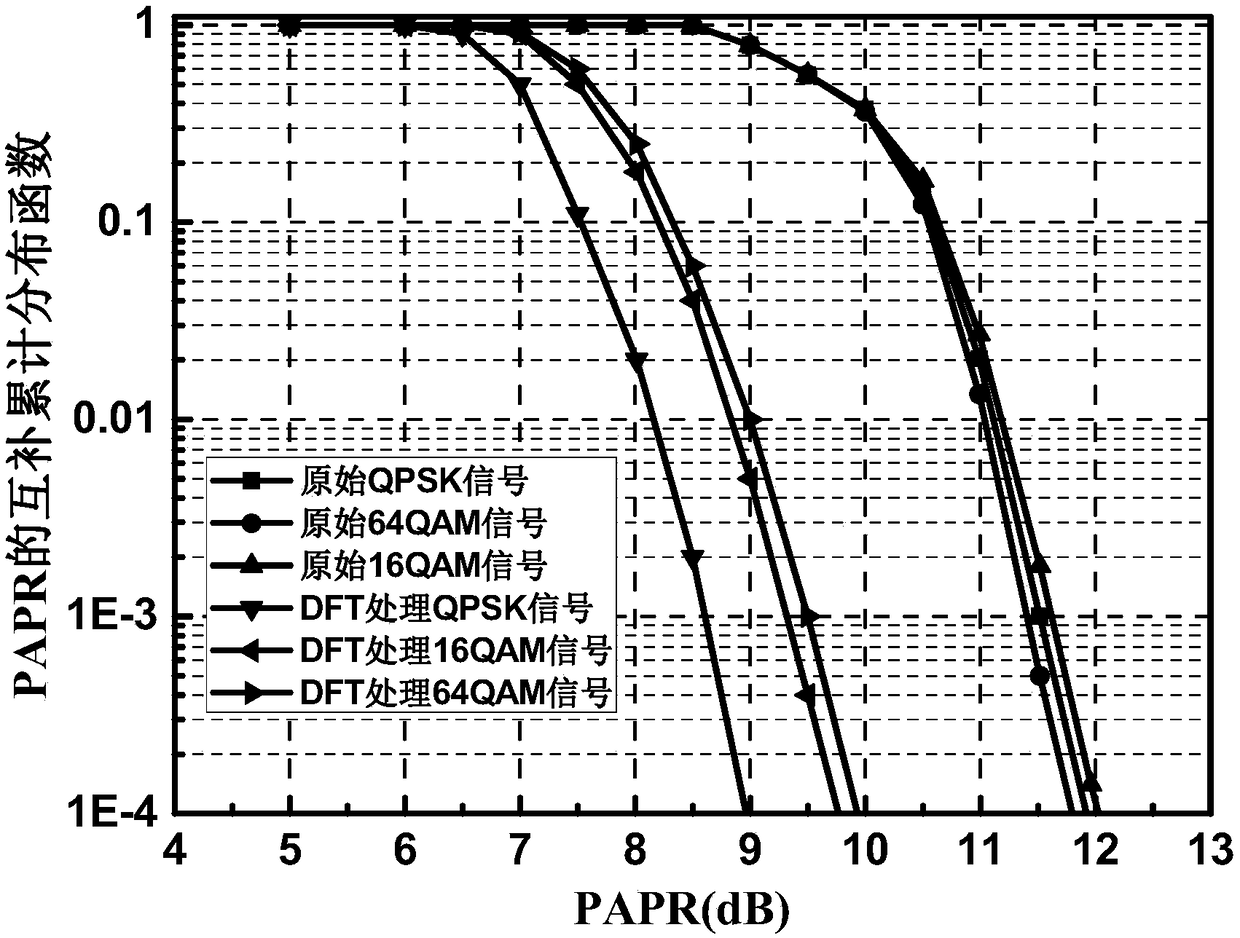
InactiveCN105933103AImprove transmission qualityImprove bit error rate performanceElectromagnetic transmission optical aspectsSecuring communication by chaotic signalsTransceiverDFT matrix
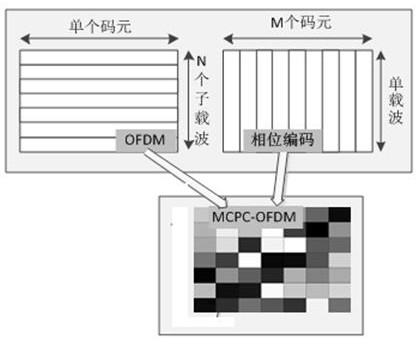
The invention discloses a light DFT-S-OFDM secure transmission system based on a digital chaos. The system comprises three encryption steps all together, i.e., insertion of an OFDM synchronous training sequence, DFT matrix signal preprocessing and subcarrier mapping, wherein an OFDM synchronous training sequence and a subcarrier mapping mode are both generated by a chaotic system, DFT matrix element parameters m and n are generated by the chaotic system, by use of initial value sensitivity and pseudo randomness of the digital chaos, encryption processing is performed on DFT-S-OFDM signals, and thus secret transmission is realized. On one hand, since a security system secret key space is huge, the security of high-speed information transmission can be effectively enhanced, and at the same time, since a DFT matrix can substantially reduce a peak average power ratio (PAPR) of OFDM signals, the performance of the transmission system is also improved; and on the other hand, since multiple iteration optimization and multiple discrete Fourier transformation operation are unnecessary in a DFT matrix signal processing system, the whole system has the following advantages: the system architecture is simple, the calculation amount is small, the transceiver cost is low, and transmission of sideband information is unnecessary.
Owner:SHANGHAI JIAO TONG UNIV
Image encryption method based on a five-dimensional hyper-chaotic system
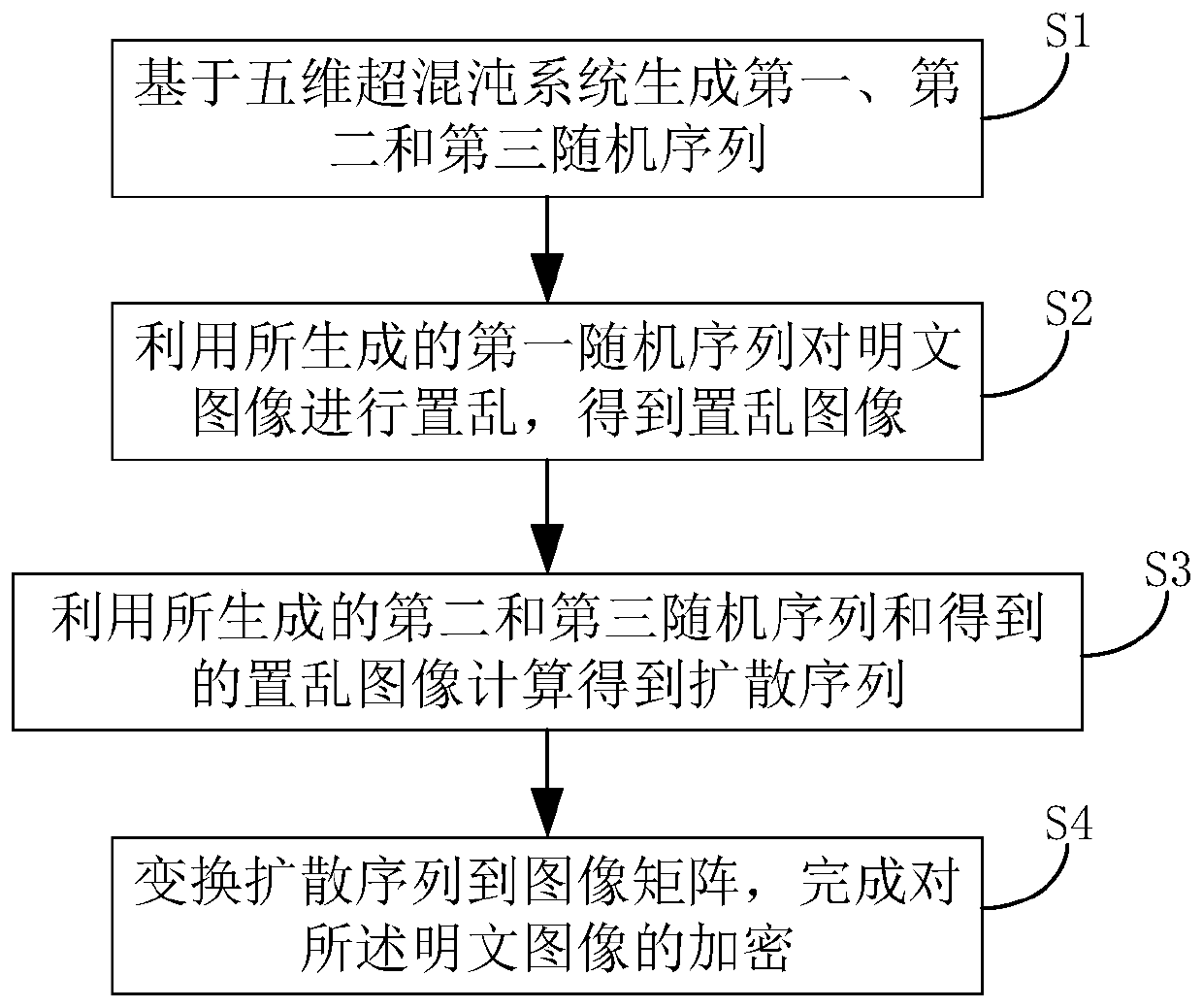
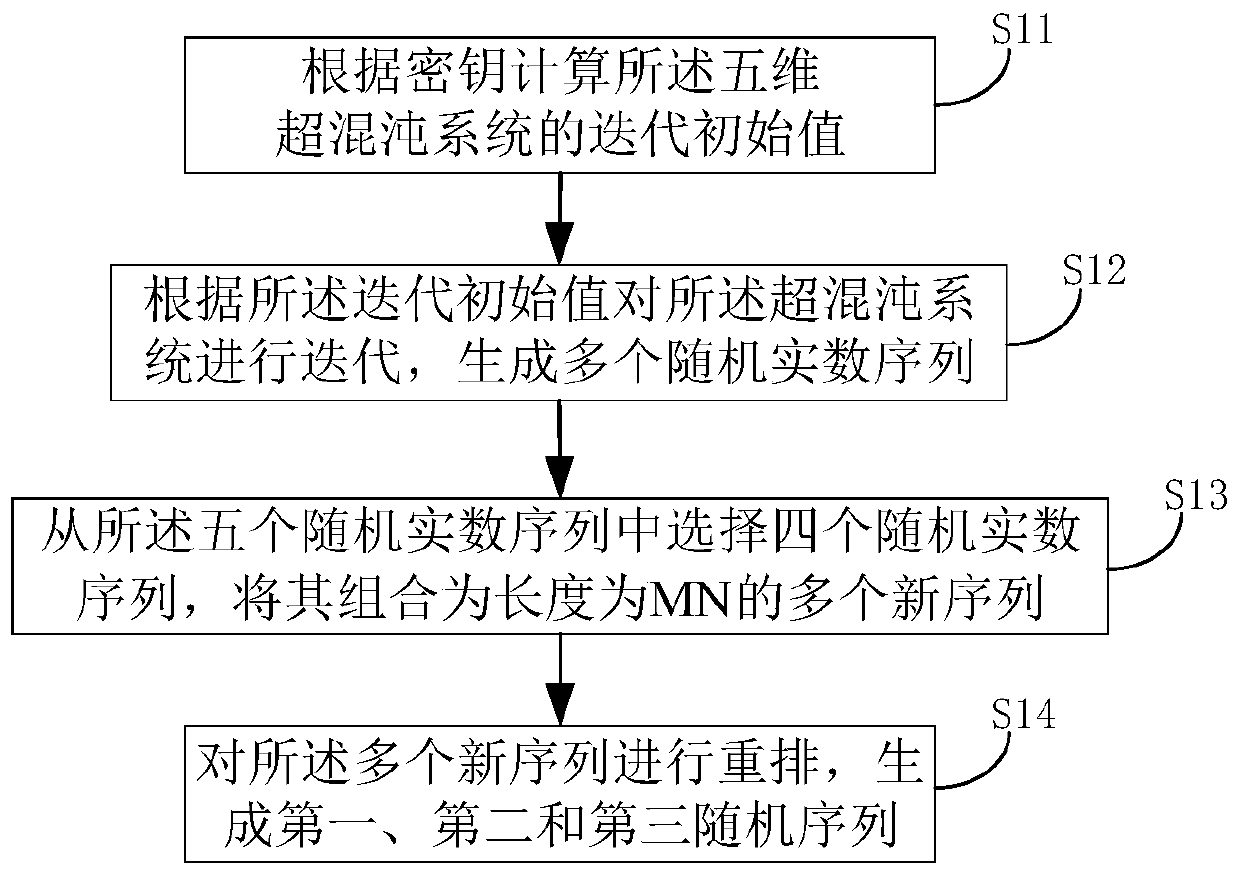
InactiveCN109803063AImprove encryption securityImprove pseudo-randomnessSecuring communicationPictoral communicationPlaintextPattern recognition
The invention relates to an image encryption method based on a five-dimensional hyper-chaotic system. The method comprises the steps of generating a first random sequence, a second random sequence anda third random sequence based on the five-dimensional hyper-chaotic system; Scrambling the plaintext image by using the generated first random sequence to obtain a scrambled image; Calculating to obtain a diffusion sequence by using the generated second and third random sequences and the obtained scrambled image; And transforming the diffusion sequence to an image matrix to complete encryption ofthe image. According to the embodiment of the invention, based on the five-dimensional hyper-chaotic system, the pseudo-randomness of the sequence and the scrambling effect of the image are improvedthrough the new chaotic sequence generation method and the new image scrambling method, so that the image has higher encryption security.
Owner:FUQING BRANCH OF FUJIAN NORMAL UNIV
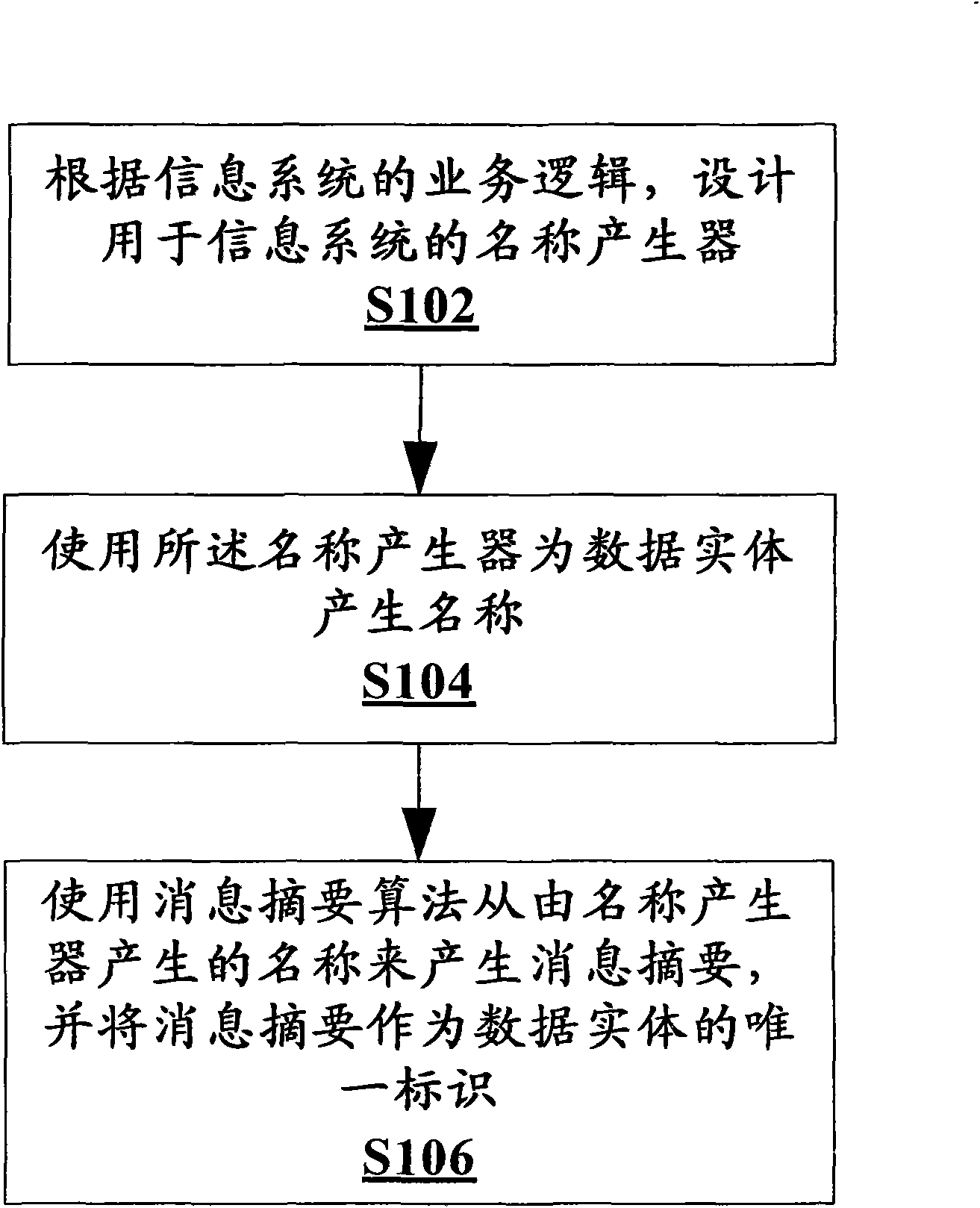
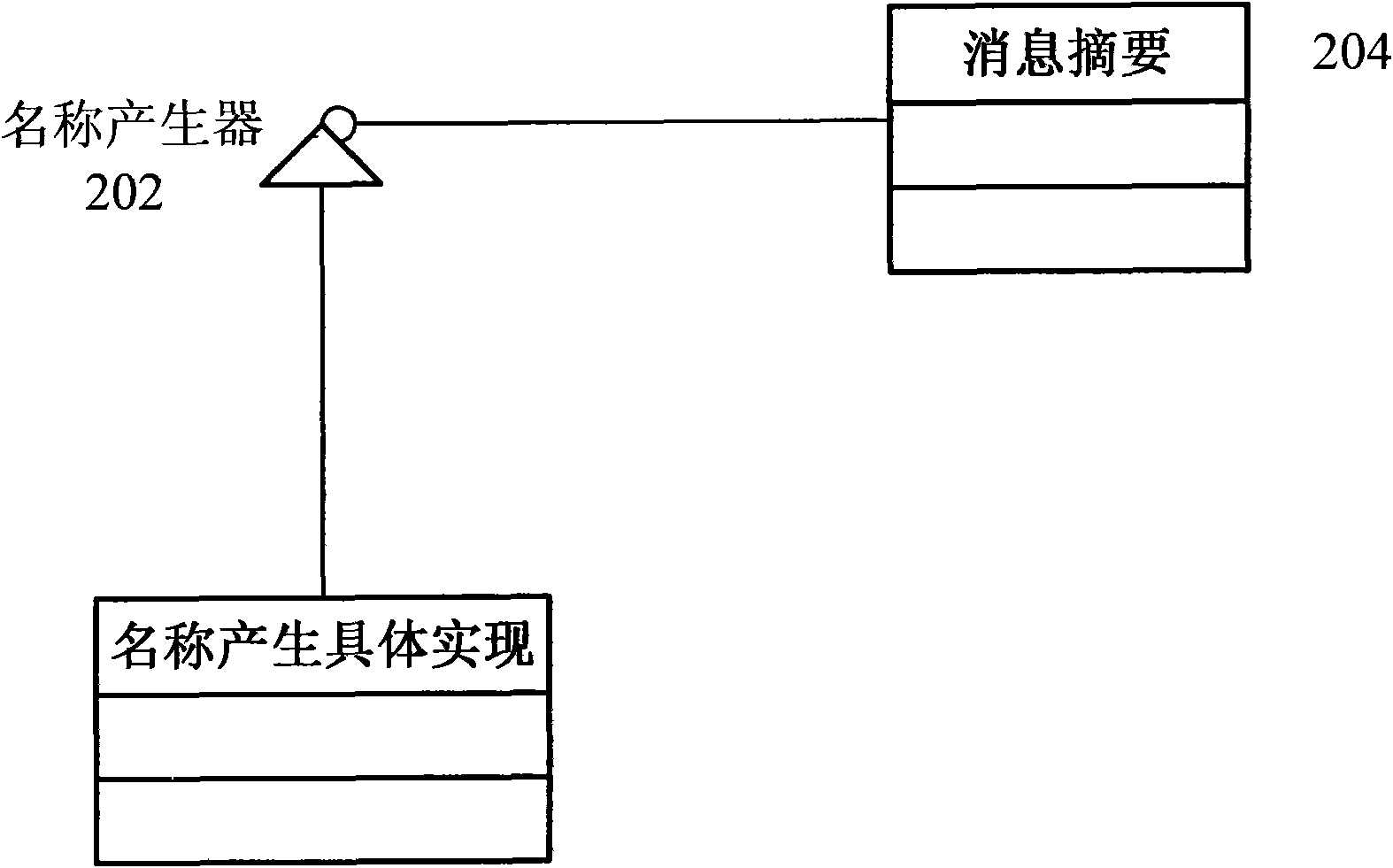
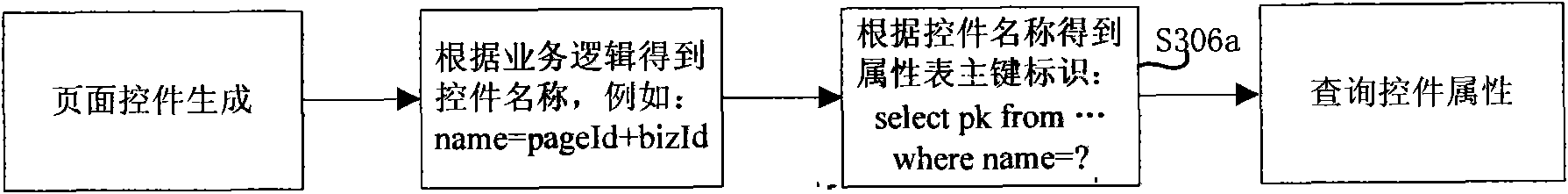
Mark generating method and device
The invention provides a mark generating method for generating a unique mark for a data entity according to the service logic of an information system, comprising the following steps of: designing a name generator used for the information system according to the service logic of the information system; using the name generator to generate a name for the data entity; and using an information digest algorithm to generate an information digest from names generated by the name generator, and using the information digest as the unique mark of the data entity. In addition, the invention also provides a mark generating device. The mark generating method and the mark generating device can solve the problems of the unpredictability and the pseudo-randomness of services of the traditional unique mark generation type and can also ensure the characteristics of the mark, such as the uniqueness, the length fixity, the information hiding and the like, based on business rules.
Owner:YONYOU NETWORK TECH
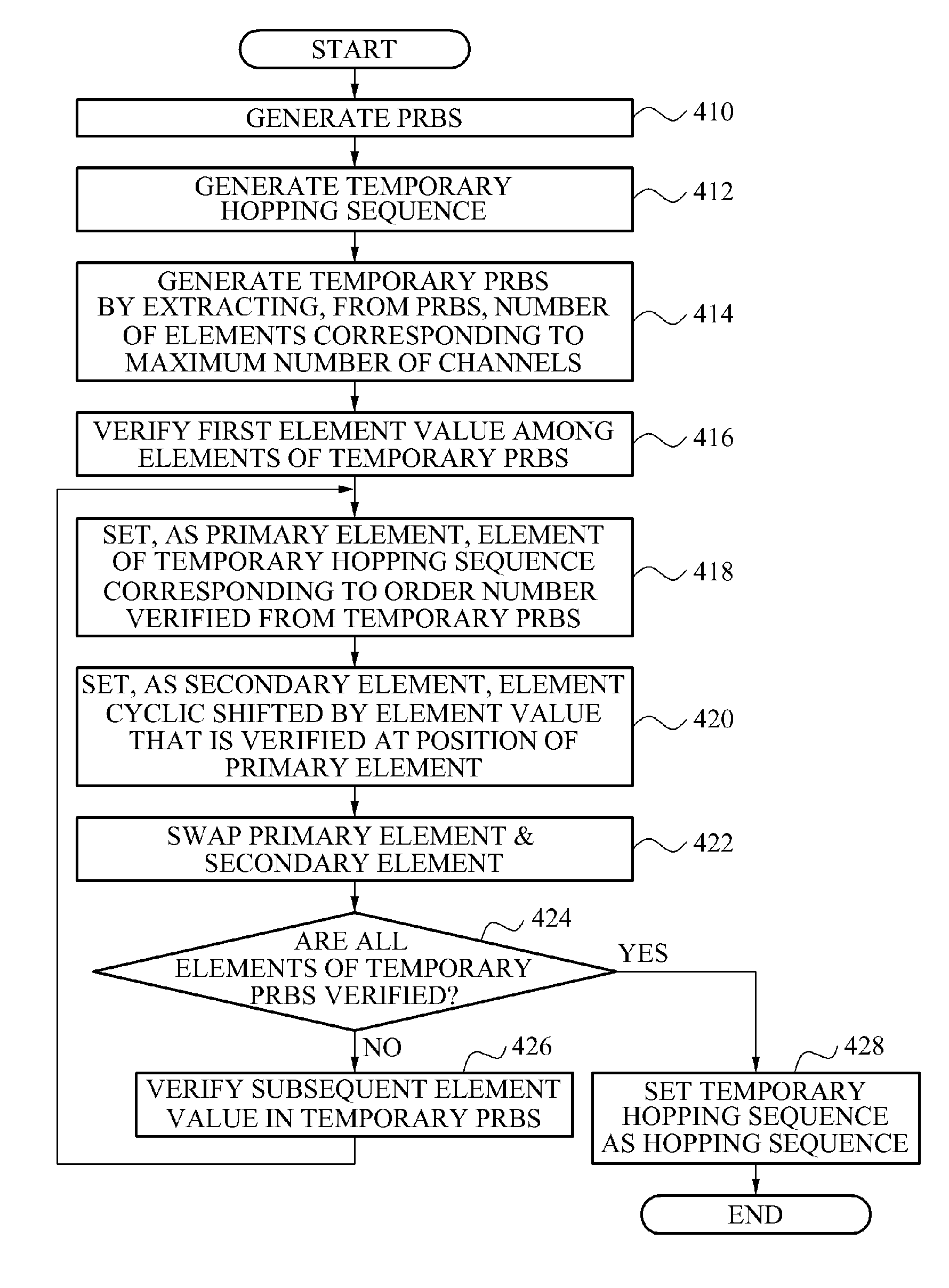
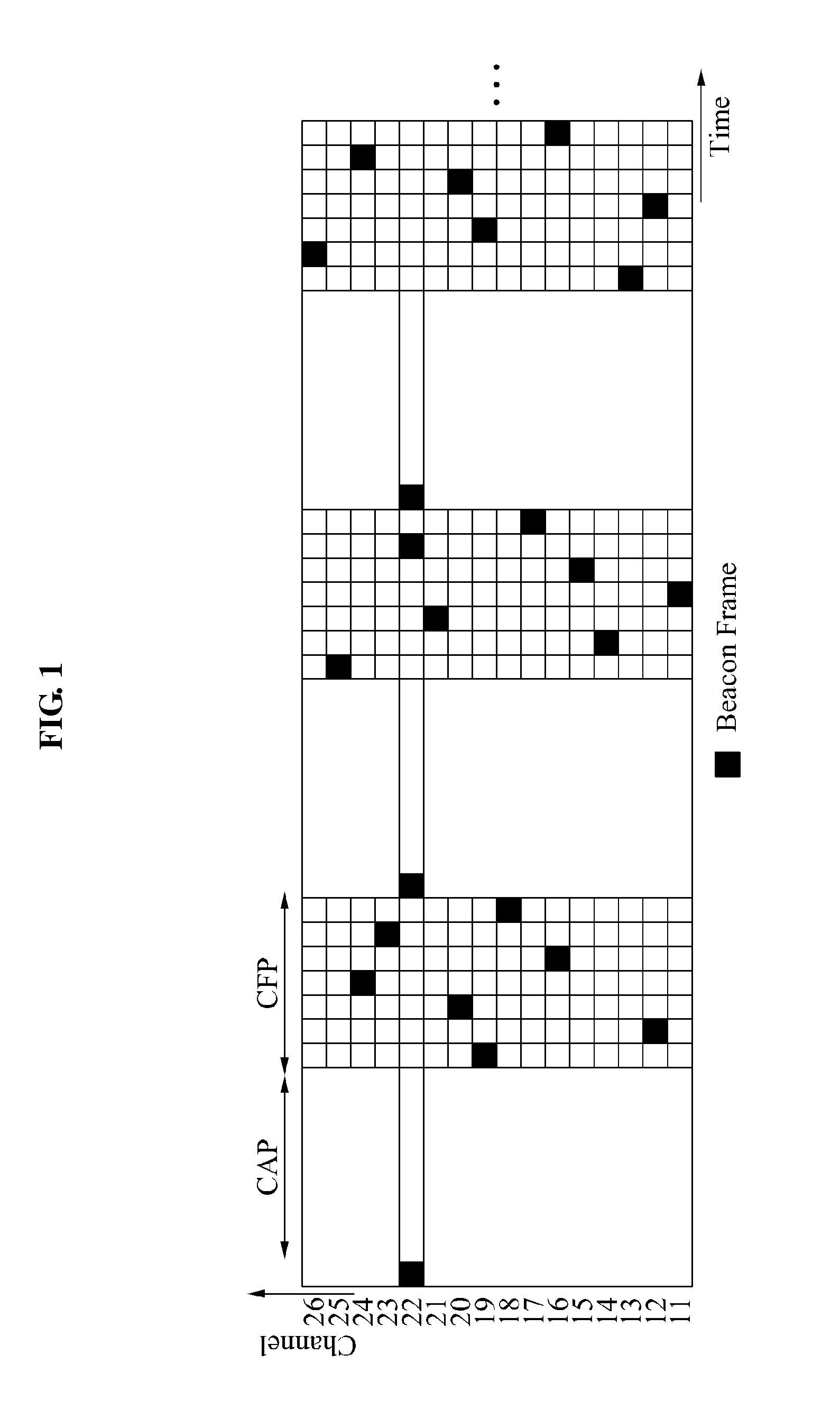
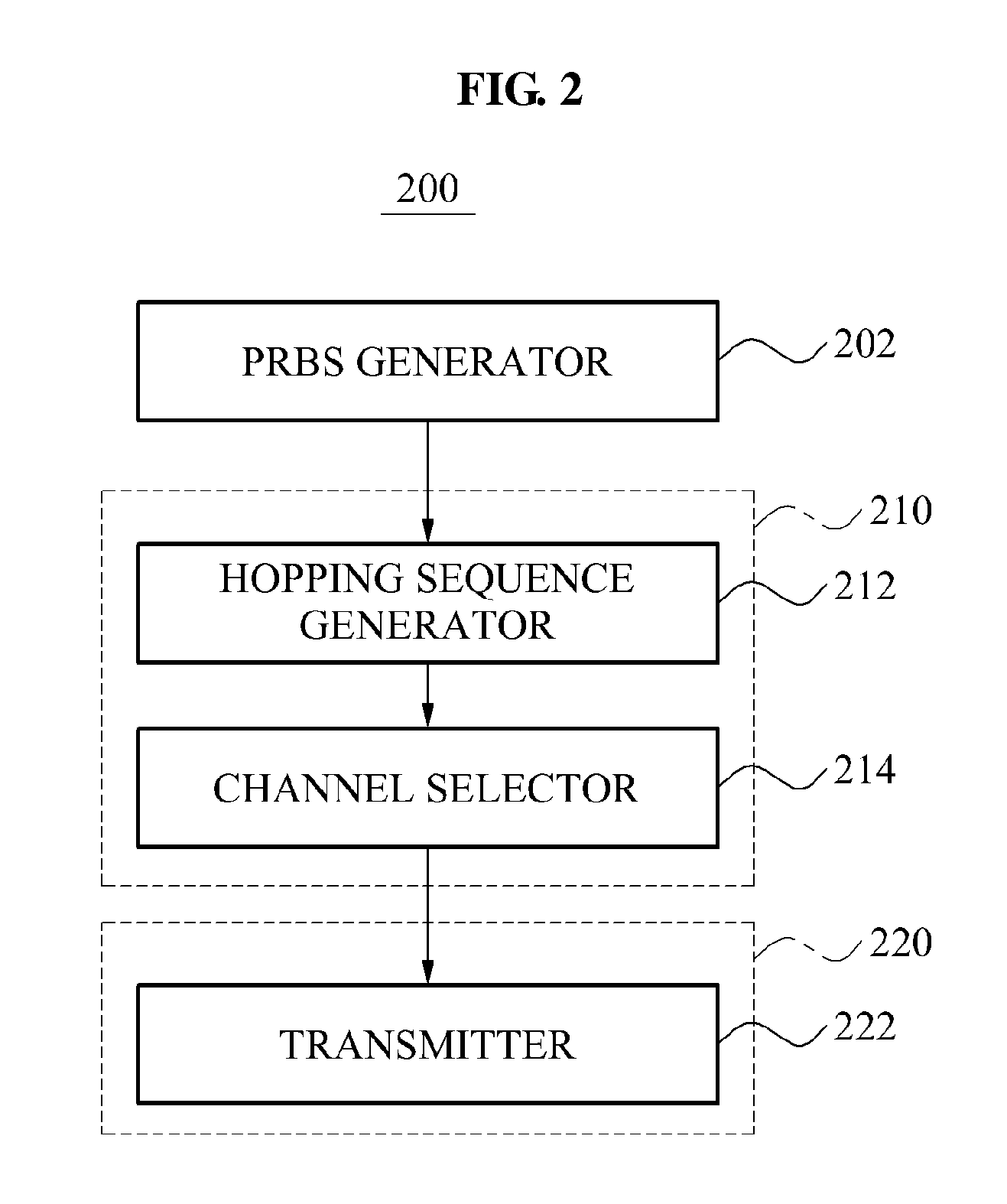
Apparatus and method for managing channel resource in beacon-enabled wireless personal area network (WPAN)
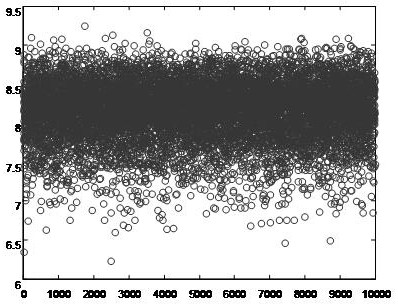
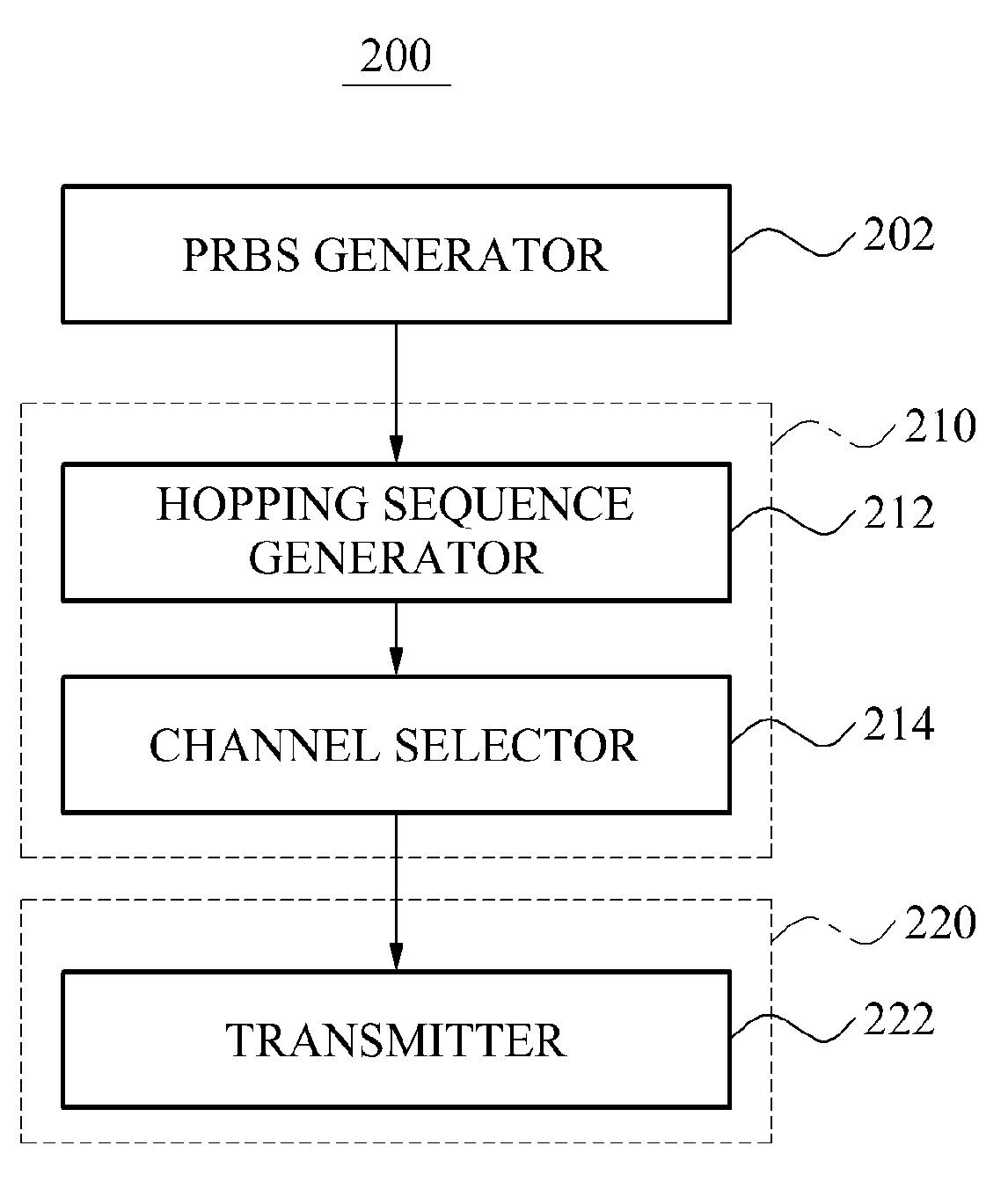
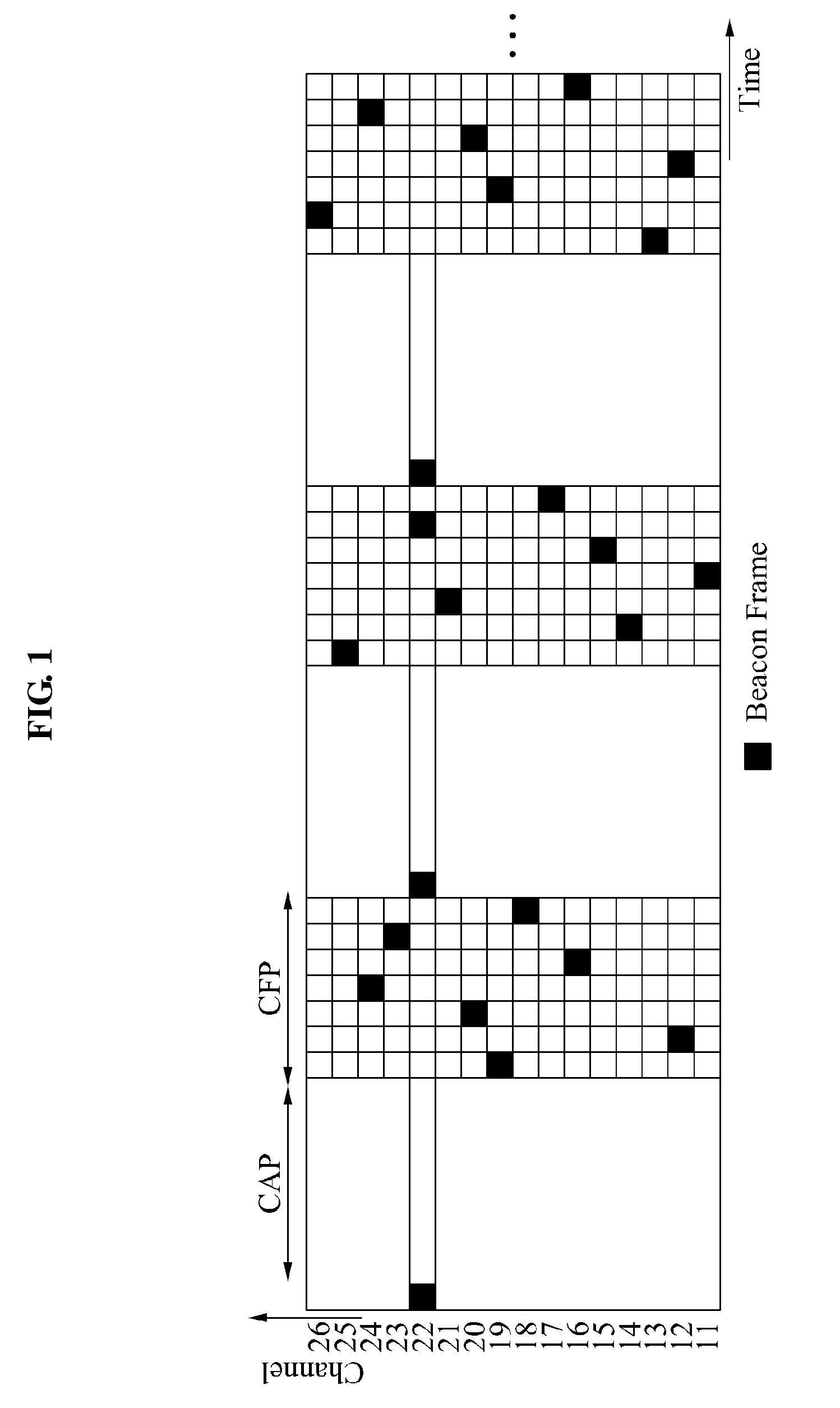
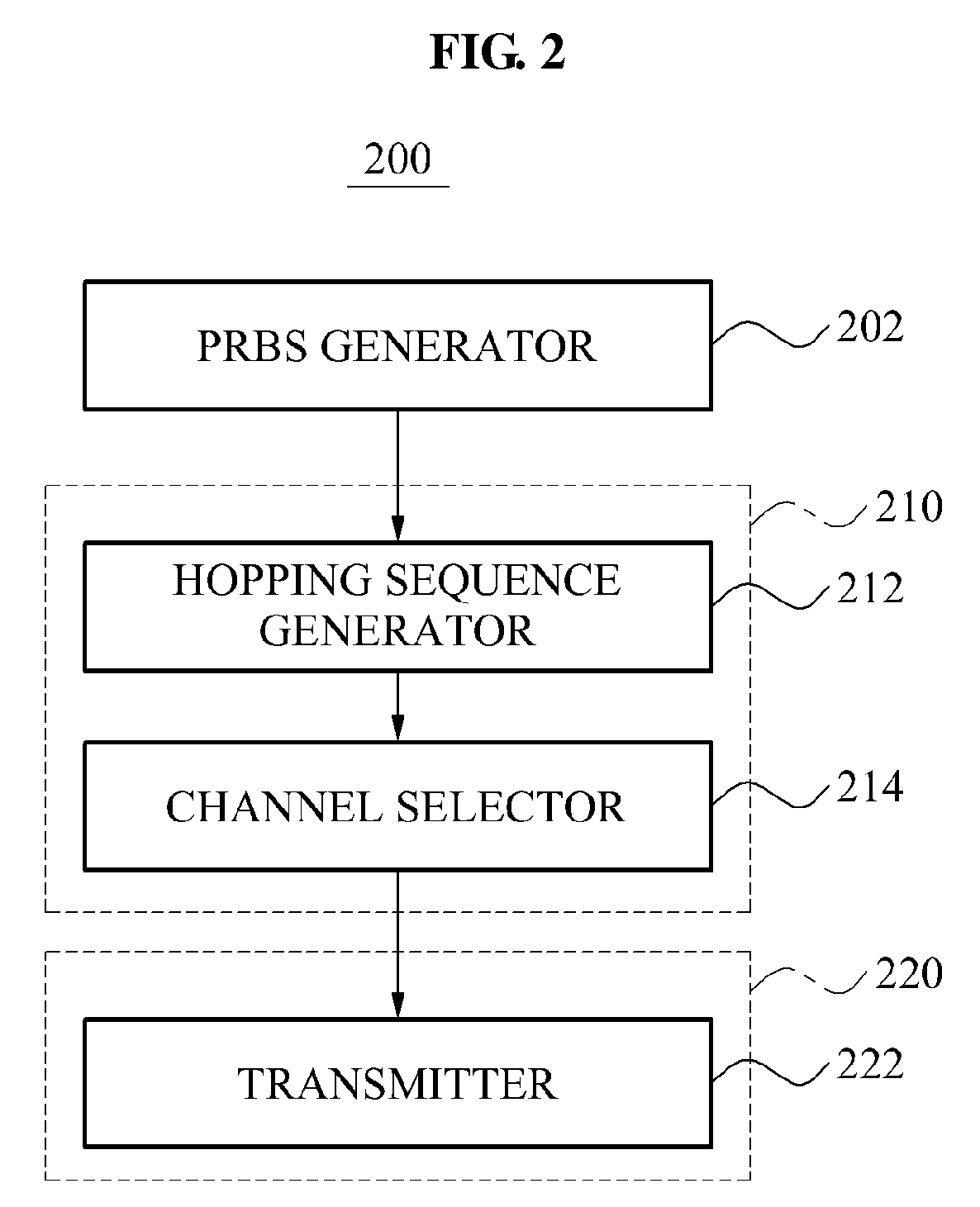
ActiveUS20120014414A1Reduce radio interferenceRemarkable effectNetwork traffic/resource managementAssess restrictionPseudo randomnessChannel use
Provided are a node device of a beacon-enabled Wireless Personal Area Network (WPAN) managing a channel resource and a method thereof. The node device may generate a pseudo random binary sequence (PRBS) and generate a hopping sequence based on a number of available channels using the PRBS, thereby generating a hopping sequence having a characteristic of pseudo randomness and selecting a channel to be hopped, using the hopping sequence.
Owner:ELECTRONICS & TELECOMM RES INST
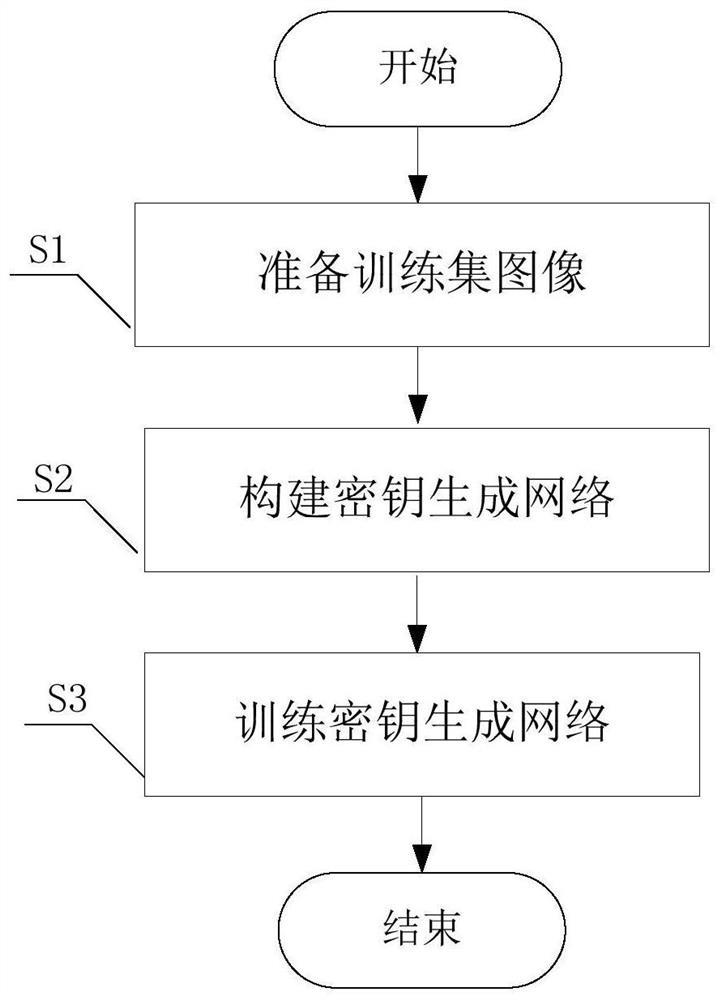
Key generation method based on deep learning generative adversarial network
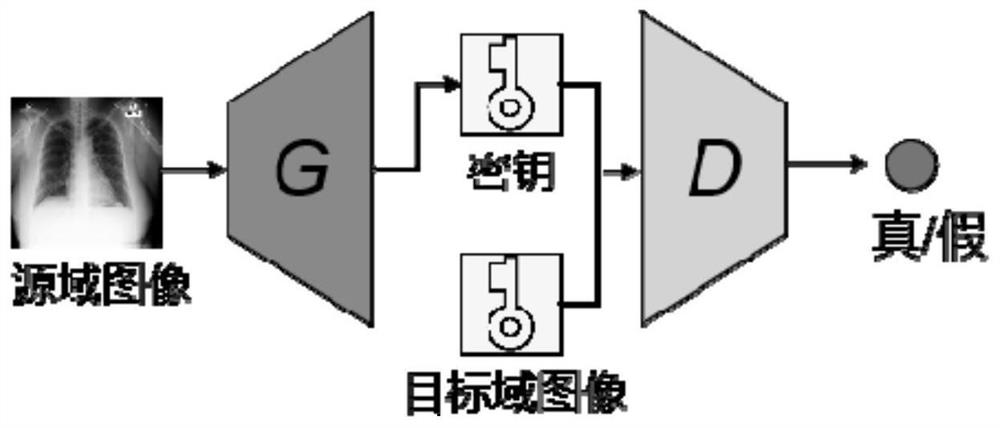
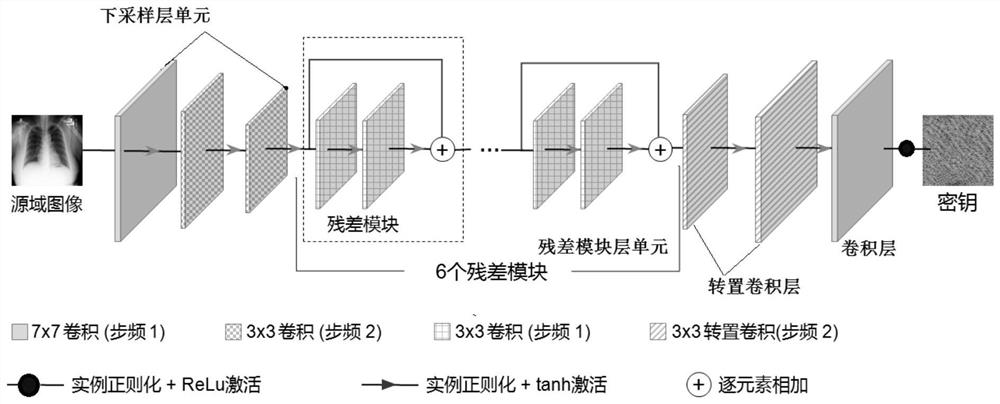
ActiveCN111654368ARealize generationRealize the discrimination functionKey distribution for secure communicationMedical imagesKey spaceGenerative adversarial network
The invention provides a secret key generation method based on a deep learning generative adversarial network, and the method comprises the steps: firstly preparing a training set image; constructinga key generation network: constructing the key generation network according to a generator network and a discriminator network, and inputting the training set image into the key generation network; and training a key generation network: training the key generation network by using a deep learning method to generate a key. The secret key generated by the method has the characteristics of large secret key space, pseudo randomness, one-time pad and sensitivity to an initial value. The method is one of the earliest researches of trying to adopt a deep learning method in the field of key generation, and the generated key is used for encrypting the plaintext medical image, so that relatively high security can be brought.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
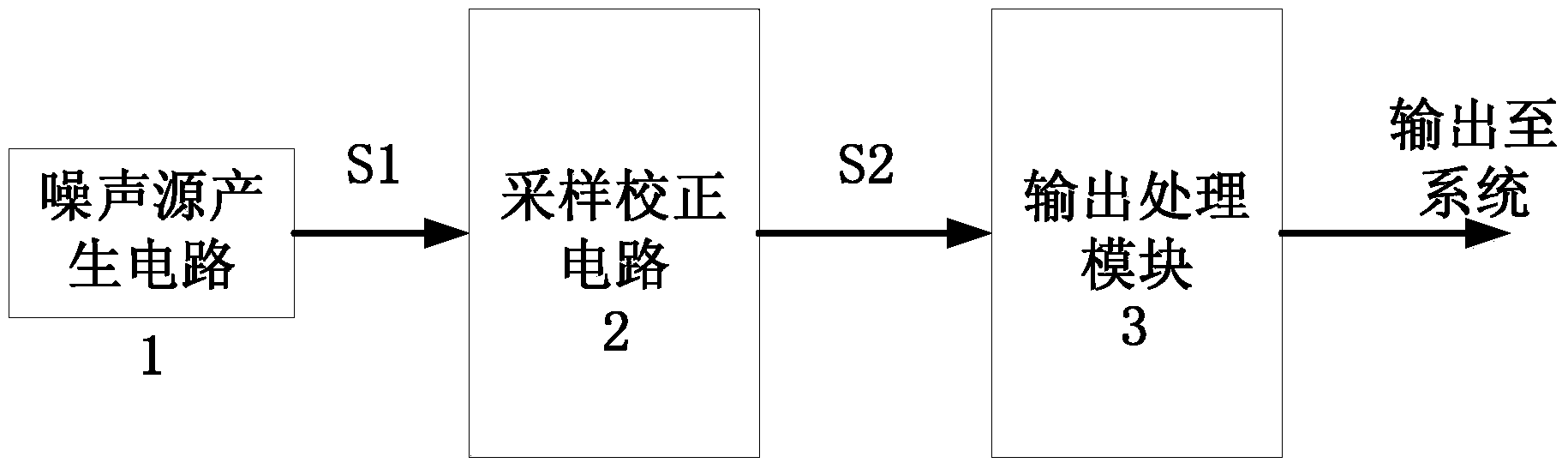
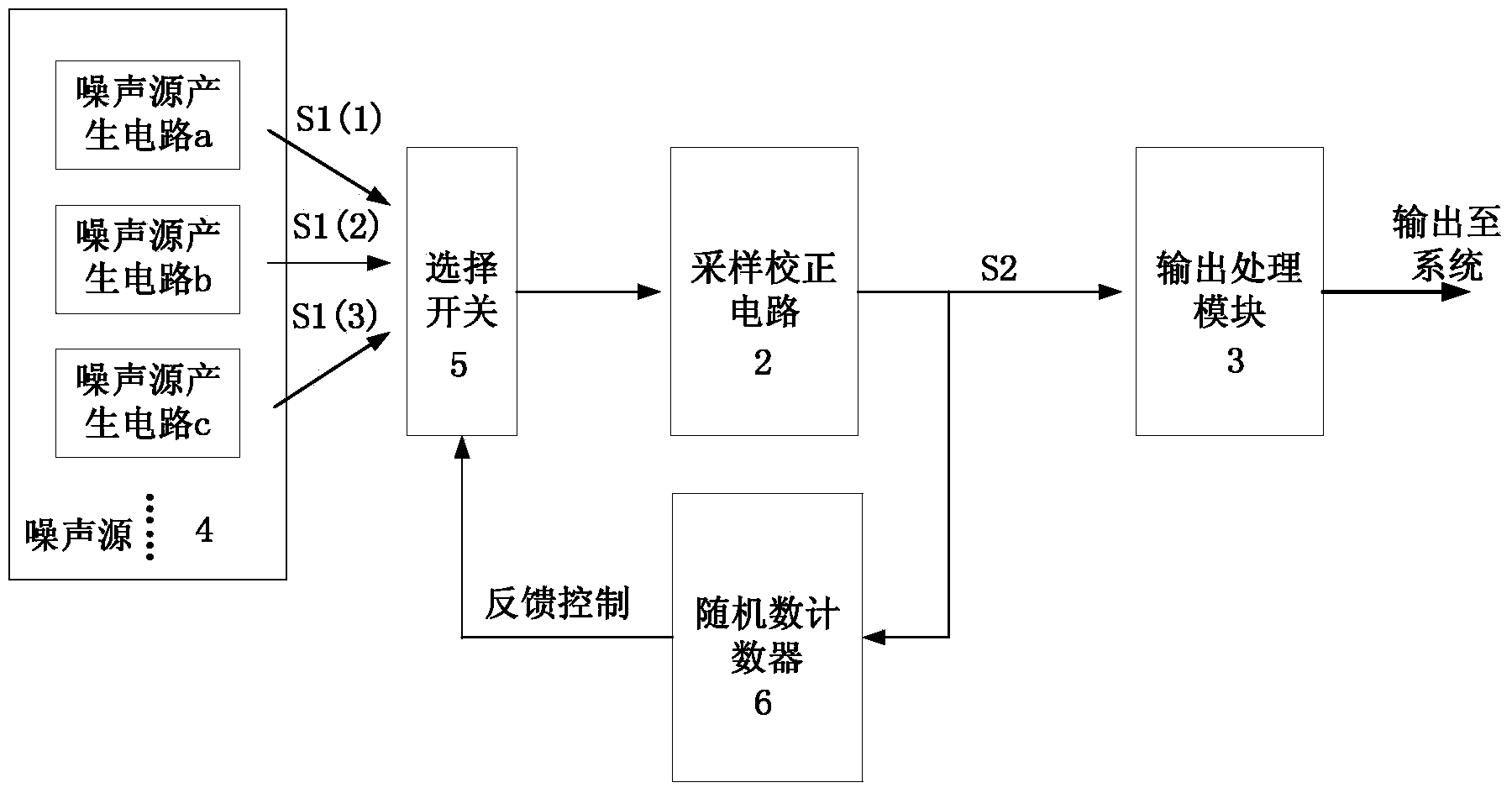
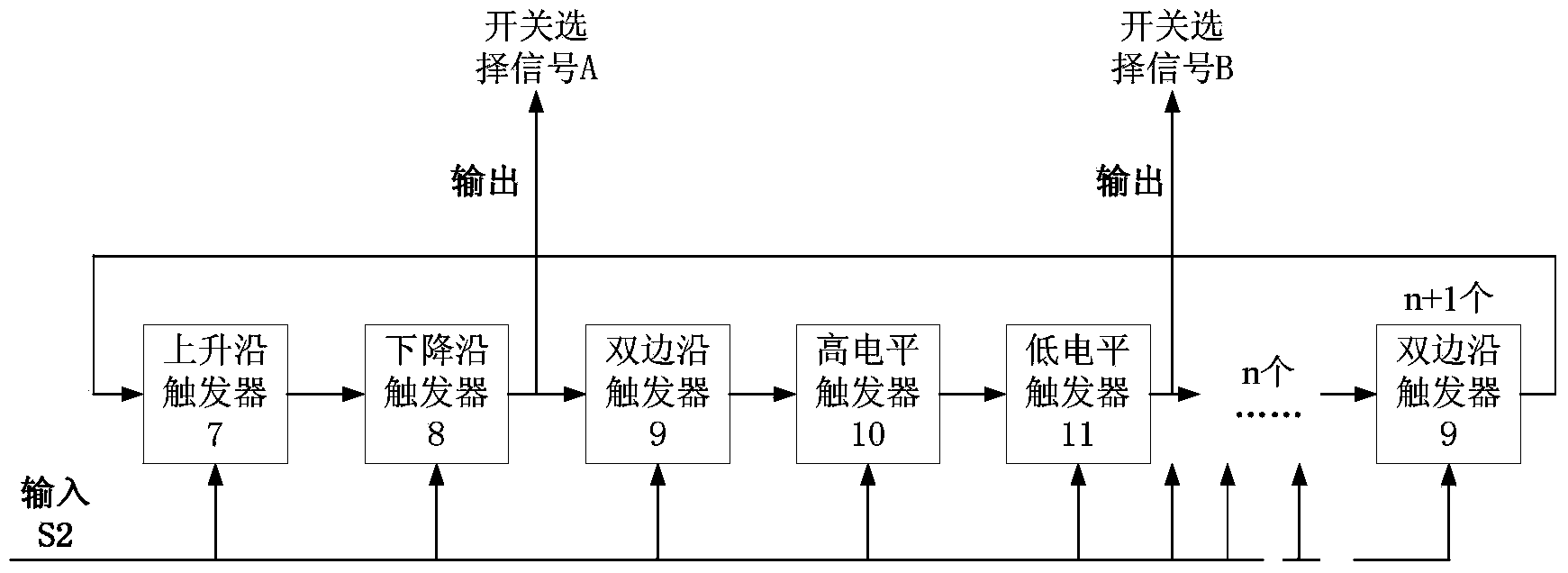
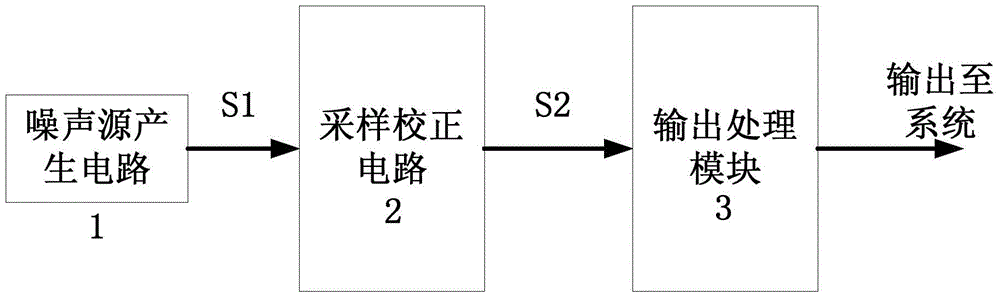
Multisource input true random number generator circuit structure
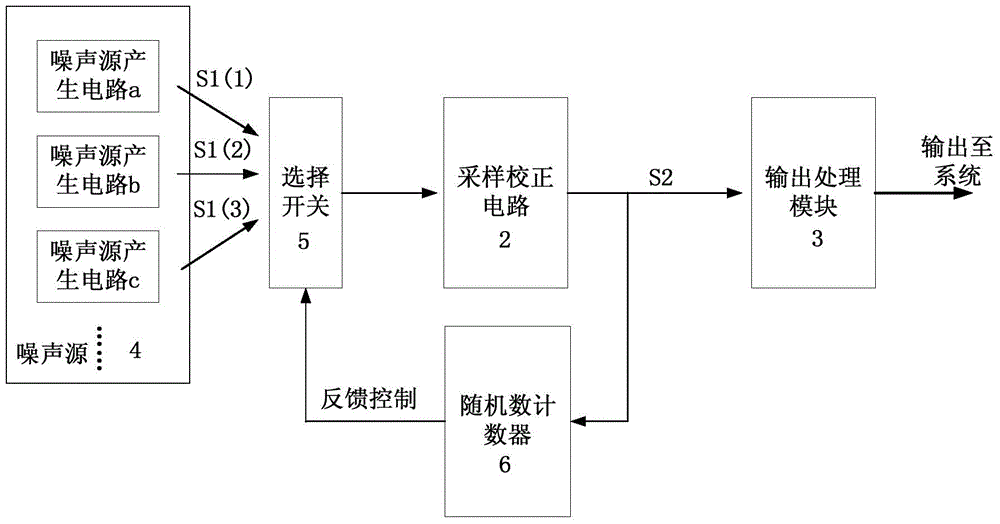
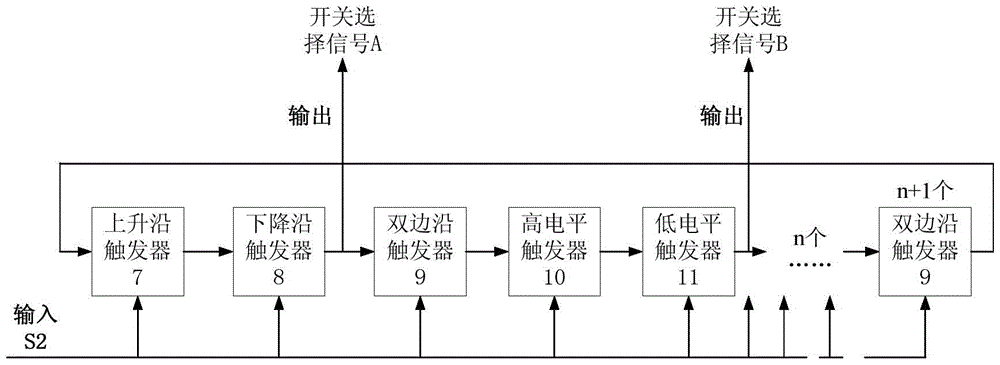
ActiveCN103955352AEliminate pseudo-randomnessImprove true randomnessRandom number generatorsInput selectionPseudo randomness
The invention discloses a multisource input true random number generator circuit structure. Multiple noise generating circuits of different types are used as noise sources; with input selection of an option switch, the noise is input into a sampling correcting circuit; on one hand, the input result enters into an output processing module, and on the other hand, the input result enters into a random number counter; the random number counter counts the generated random number, and feeds back the output result to the option switch; then the signals are randomly selected from the multiple noise generating circuits and then output. In the process, due to the randomness of selection from the multiple noise sources, the randomness of the sampling correcting output, and the randomness of application of the random number counter, the pseudo-randomness generated by the original single noise generating circuit due to long-time working can be eliminated wholly. Proved by the theory and experiments, the true random number generator utilizes multiple noise sources and the random number counter to realize feedback, so that the randomness of the long-range data is better than the original random number generator realized by the single noise source.
Owner:58TH RES INST OF CETC
Digital Image Encryption Method Based on Chaotic System and Nucleic Acid Sequence Library
InactiveCN105046636BImprove featuresIncreased sensitivityImage data processing detailsInformation processingSequence database
The invention provides a digital image encryption method based on a chaotic system and a nucleic acid sequence database. The chaotic map index sequence is used to scramble image pixel positions; Operation; base substitution is performed on the DNA-encoded pixels according to the quaternary hyperchaotic sequence generated by the hyperchaotic Chen system, and its confusion and diffusion properties are further enhanced through ciphertext feedback and chaotic system iteration. The invention relies on the sensitivity and pseudo-randomness of chaotic mapping to initial conditions, combined with the inherent spatial configuration and unique information processing capability of DNA molecules, by using the difference between two chaotic sequences, DNA sequence libraries and the gray value of its own pixel. The transformation and operation of the digital image achieve the purpose of confusion and diffusion, so as to realize the encryption of the digital image. Experimental results show that the invention has large key space and strong sensitivity to keys, and can effectively resist attack operations such as statistical analysis and exhaustive analysis.
Owner:ZHENGZHOU UNIVERSITY OF LIGHT INDUSTRY
Forming method and system of radio frequency stealth transmitting beam based on four-dimensional antenna array
ActiveCN110058218AGood radio frequency stealth performanceEffective regulationRadio wave reradiation/reflectionSequence designRadar
The invention provides a forming method of a radio frequency stealth transmitting beam based on a four-dimensional antenna array. Only simple timing sequence design is needed to achieve similar multiple input multiple output MIMO and phase controlled MIMO arrays and even better detection performance, a radar is different from a traditional radio frequency stealth radar, and good radio frequency stealth performance can be given to the radar due to pseudo-randomness of timing sequence. The invention further provides a forming system of the radio frequency stealth transmitting beam based on the four-dimensional antenna array based on the forming method. The forming system has the characteristics of being simple in structure, and easy to realize. According to the forming method and system of the radio frequency stealth transmitting beam based on the four-dimensional antenna array, the generation condition of four-dimensional antenna timing sequence is controlled, under the condition that aradiation signal with good radio frequency stealth performance is ensured, orthogonality among sub-arrays of transmitting antennas or different radio frequency switches is easily realized, a receiving end receives an echo and carries on the signal processing, and information of multiple targets can be simultaneously obtained.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
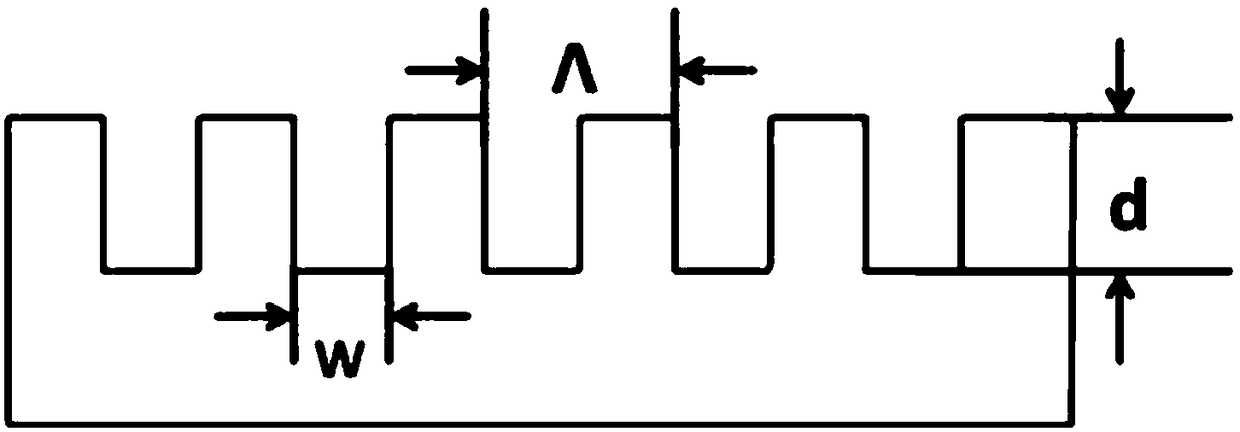
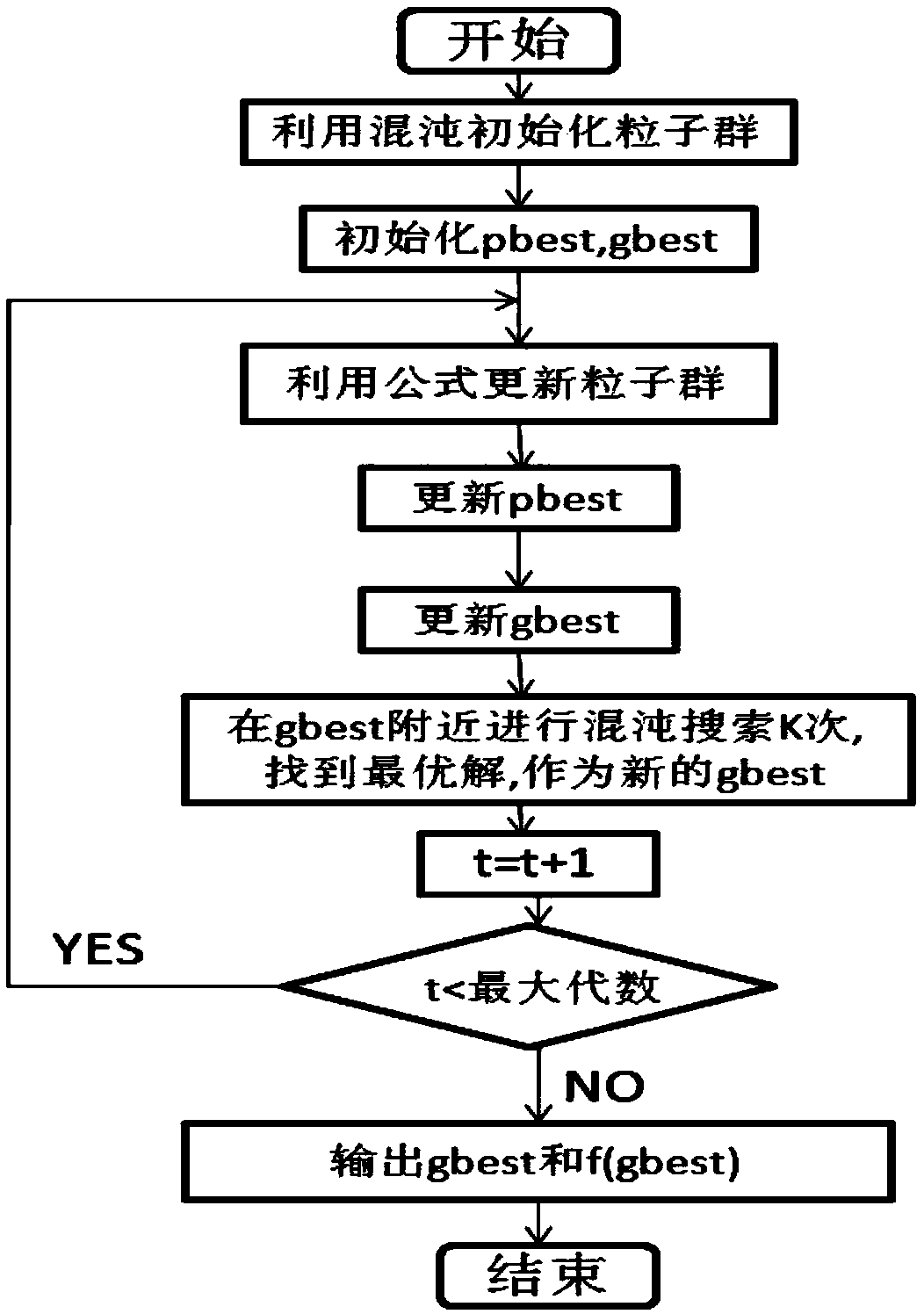
Method for designing fully randomized silicon-based waveguide optical grating on basis of chaotic particle swarm optimization algorithm
InactiveCN108227188AEasy to operateStrong autonomyOptical waveguide light guideSystems designGrating
The invention relates to a method for designing a fully randomized silicon-based waveguide optical grating on the basis of a chaotic particle swarm optimization algorithm. Uniform optical grating design parameters are made inhomogeneous, the overall variation of the optical grating is designed as the change of each periodic block, and a coupling efficiency value under the case of each parameter isan adaptation degree in the particle swarm optimization algorithm; when a particle swarm evolves to the next generation, each particle updates itself by tracking two optimal solutions including pbestand gbest; when a boundary position value is taken as a particle value, chaotic variable processing is conducted, and a global search function is achieved; an initial value is provided for a chaoticvariable, and a group of random sequences with ergodicity and pseudo-randomness are generated through iteration of a chaotic iterative equation; a coupling efficiency standard required for the opticalgrating is set, when a particle swarm optimization result reaches the required standard, the process stops automatically, and the particle value corresponding to the adaptation degree is the demandeddesign parameter value. Systematic design of the fully randomized optical grating is achieved, and design parameters and the coupling efficiency of the optical grating can be effectively and quicklyobtained.
Owner:SHANDONG UNIV
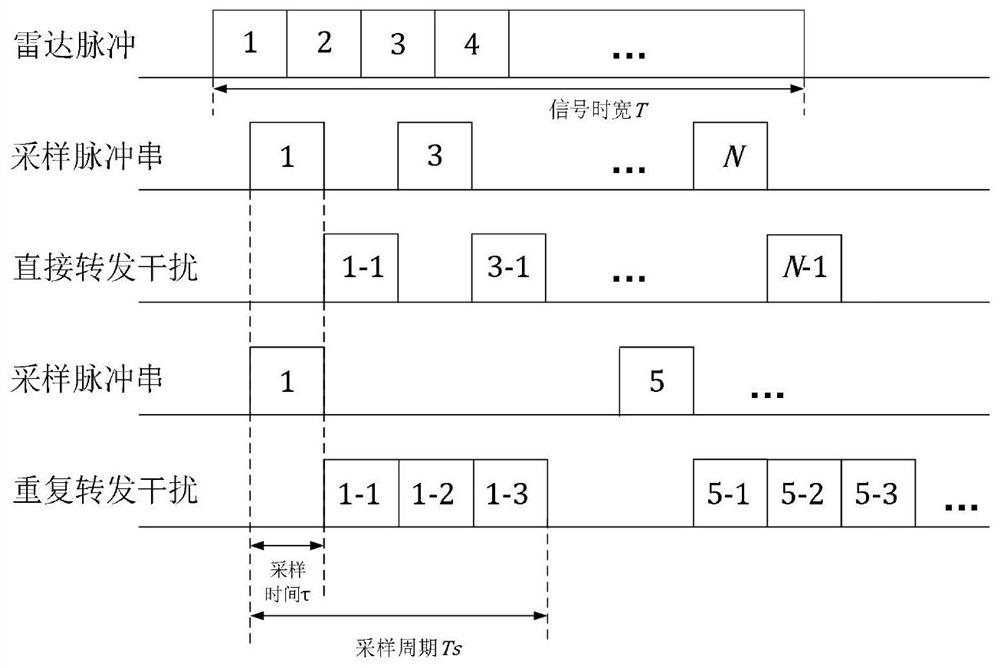
Radar signal design method capable of resisting intermittent sampling and forwarding interference
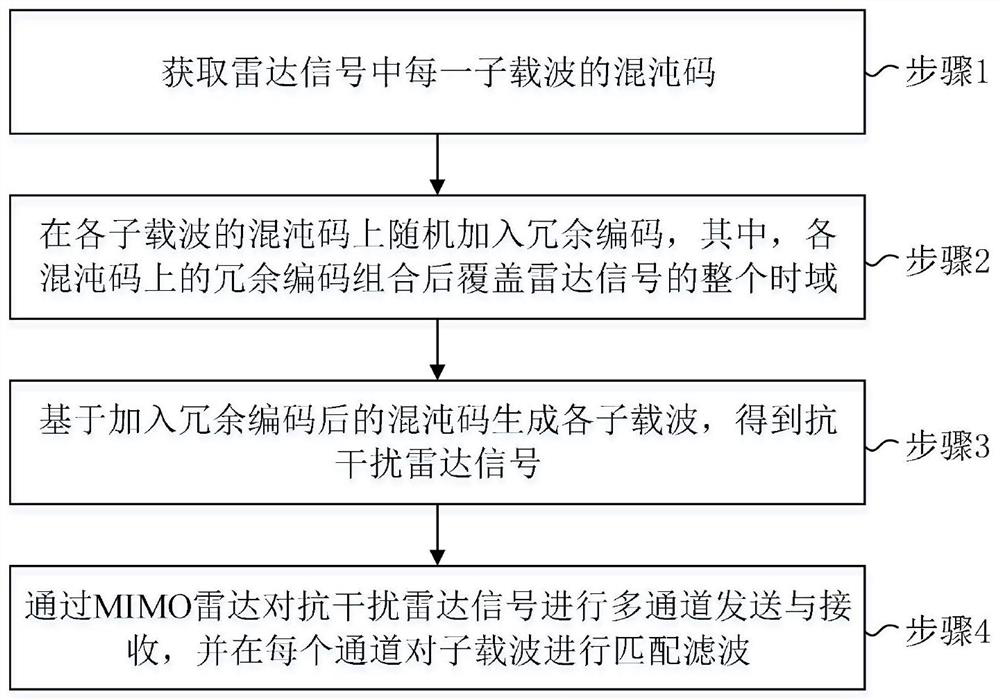
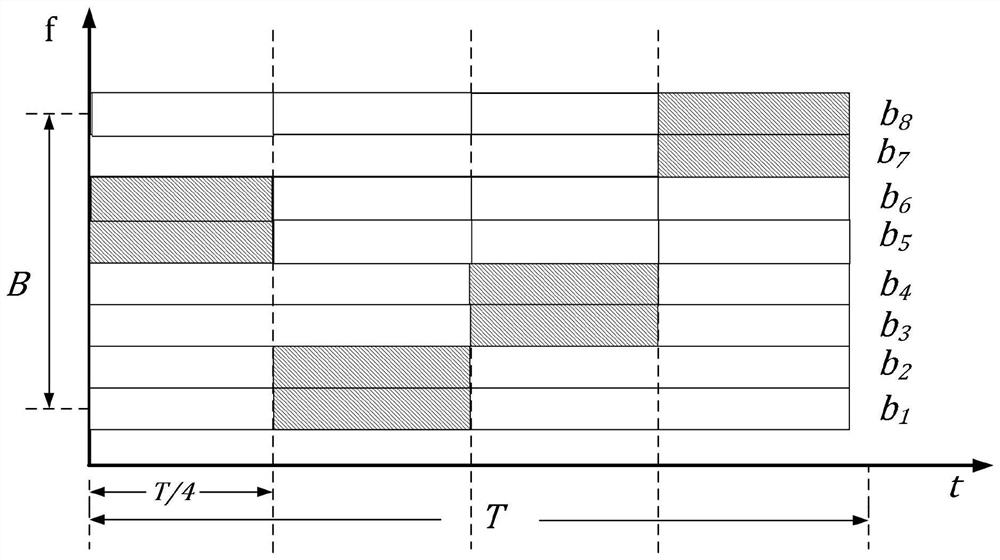
PendingCN113138370AReduced intravenous correlationIncreased pseudo-randomnessWave based measurement systemsTime domainRadar waveforms
The invention discloses a radar signal design method capable of resisting intermittent sampling and forwarding interference, which comprises the following steps of: starting from the angle of waveform design, coding each symbol in a time domain by adopting a chaos sequence with good pseudo-randomness, and adding a part of signal data in each path in the time domain into equivalent redundant codes according to random arrangement. The MIMO radar performs multi-channel sending and receiving and multi-channel matched filtering on the anti-interference radar signal, so that the pseudo-randomness of the radar waveform pulse is increased, the correlation between the radar echo and the intermittent sampling interference is reduced, and the intra-pulse correlation of the radar signal is reduced, and therefore, and the radar signal has the characteristic of resisting the intermittent sampling interference, therefore, the interference of ISRJ false targets can be effectively reduced and meanwhile, the method does not conflict with a common filter design method, and can be used in a superposed manner.
Owner:CHANGSHA UNIVERSITY OF SCIENCE AND TECHNOLOGY
Radar signal optimization method and device, computer equipment and storage medium
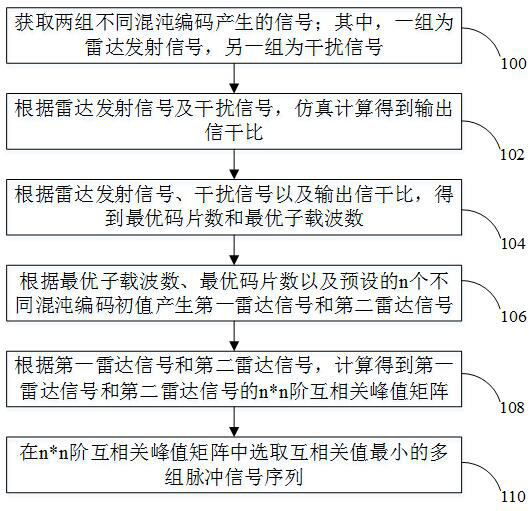
ActiveCN112394333AImprove anti-interference abilityLow anti-copy and forward interference performanceWave based measurement systemsInterference resistanceCarrier signal
The invention relates to a radar signal optimization method and device, computer equipment and a storage medium. The method comprises steps of carrying out the optimization design of signal waveform key parameters, the number of subcarriers, the number of chips and a chaotic initial value through employing the initial value sensitivity and pseudo-randomness of chaotic coding and reducing the correlation between adjacent pulse signals. According to the method, the correlation between adjacent pulses of the radar signal is low, even if an interference party identifies and copies the signal pulse, a certain time is needed in the identifying and copying process, the interference party cannot obtain matching gain with the subsequent pulses, and the interference party can not obtain the matchinggain with the subsequent pulses; therefore, the method has excellent copy-and-forward interference resistance. According to the method, a waveform optimization method is adopted to improve the anti-copy-and-forward-interference performance of the radar, extra calculation does not need to be carried out during signal processing, and the method is more suitable for engineering application.
Owner:CHANGSHA UNIVERSITY OF SCIENCE AND TECHNOLOGY
Apparatus and method for managing channel resource in beacon-enabled wireless personal area network (WPAN)
ActiveUS8594066B2Reduce radio interferenceNetwork traffic/resource managementAssess restrictionPseudo randomnessChannel use
Provided are a node device of a beacon-enabled Wireless Personal Area Network (WPAN) managing a channel resource and a method thereof. The node device may generate a pseudo random binary sequence (PRBS) and generate a hopping sequence based on a number of available channels using the PRBS, thereby generating a hopping sequence having a characteristic of pseudo randomness and selecting a channel to be hopped, using the hopping sequence.
Owner:ELECTRONICS & TELECOMM RES INST
An optical dft-s-ofdm secure transmission system based on digital chaos
InactiveCN105933103BImprove transmission qualityImprove bit error rate performanceSecuring communication by chaotic signalsElectromagnetic transmission optical aspectsTransceiverDFT matrix
The invention discloses a light DFT-S-OFDM secure transmission system based on a digital chaos. The system comprises three encryption steps all together, i.e., insertion of an OFDM synchronous training sequence, DFT matrix signal preprocessing and subcarrier mapping, wherein an OFDM synchronous training sequence and a subcarrier mapping mode are both generated by a chaotic system, DFT matrix element parameters m and n are generated by the chaotic system, by use of initial value sensitivity and pseudo randomness of the digital chaos, encryption processing is performed on DFT-S-OFDM signals, and thus secret transmission is realized. On one hand, since a security system secret key space is huge, the security of high-speed information transmission can be effectively enhanced, and at the same time, since a DFT matrix can substantially reduce a peak average power ratio (PAPR) of OFDM signals, the performance of the transmission system is also improved; and on the other hand, since multiple iteration optimization and multiple discrete Fourier transformation operation are unnecessary in a DFT matrix signal processing system, the whole system has the following advantages: the system architecture is simple, the calculation amount is small, the transceiver cost is low, and transmission of sideband information is unnecessary.
Owner:SHANGHAI JIAOTONG UNIV
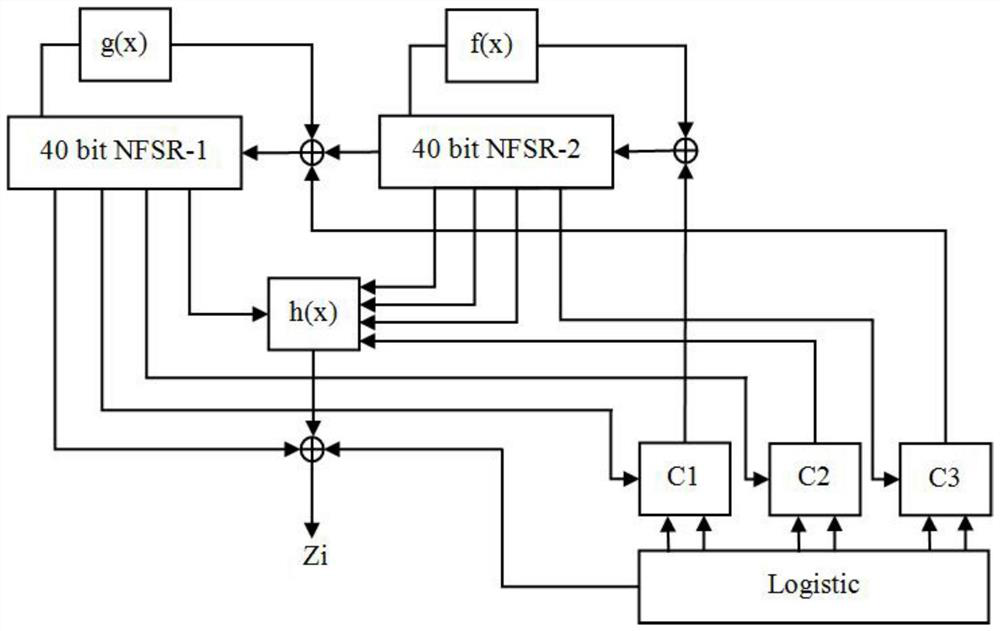
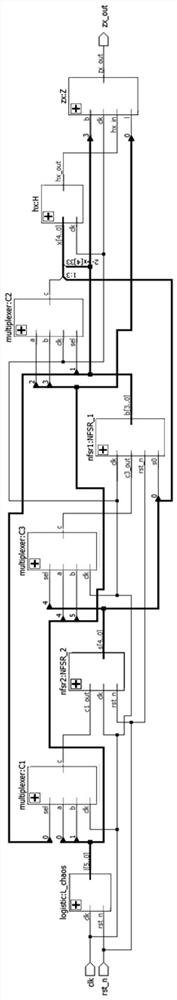
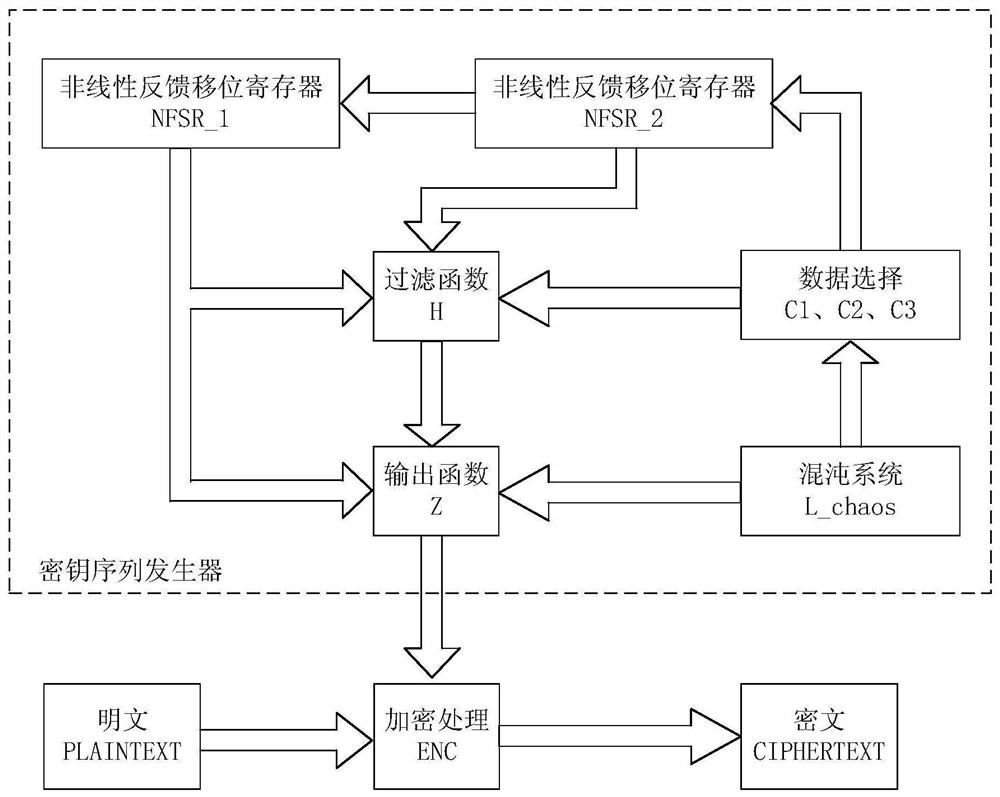
Lightweight key sequence generator based on chaotic system and FPGA
InactiveCN112260828AImprove bindingImprove securityKey distribution for secure communicationSecuring communication by chaotic signalsNonlinear feedback shift registerData selection
The invention provides a lightweight key sequence generator based on a chaotic system and an FPGA, and solves the problem that the precision of the chaotic system is limited by hardware resources. Thelightweight key sequence generator comprises a sequence generator module based on a Logistic chaotic system, two nonlinear shift registers, three data selection modules, a filter function H module and an output function Z module. According to the lightweight key sequence generator, a Logistic chaotic sequence is digitalized and is combined with a nonlinear feedback shift register through a certain algorithm; the chaotic system and the non-linear feedback shift register are well combined, and the FPGA-based hardware implementation ensures the pseudo-randomness of the sequence and the securityof the system, enables the code scale to be smaller, and occupies less hardware resources.
Owner:HEILONGJIANG UNIV
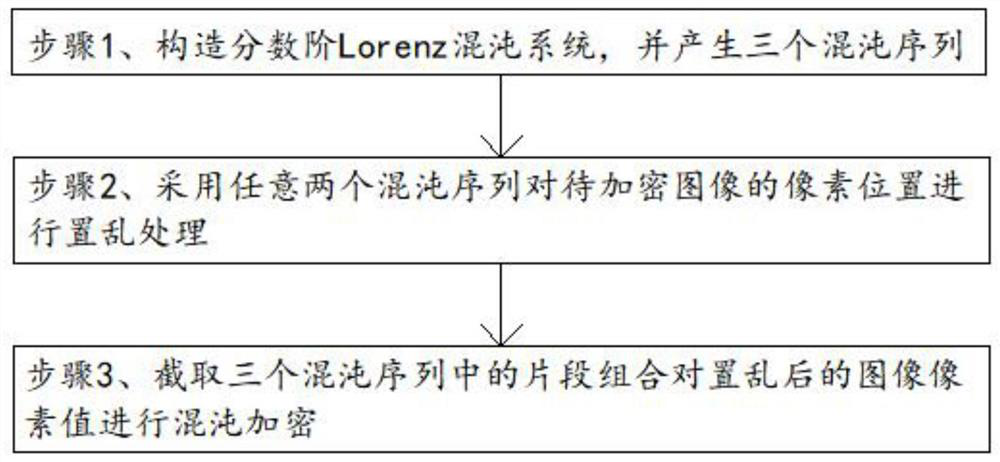
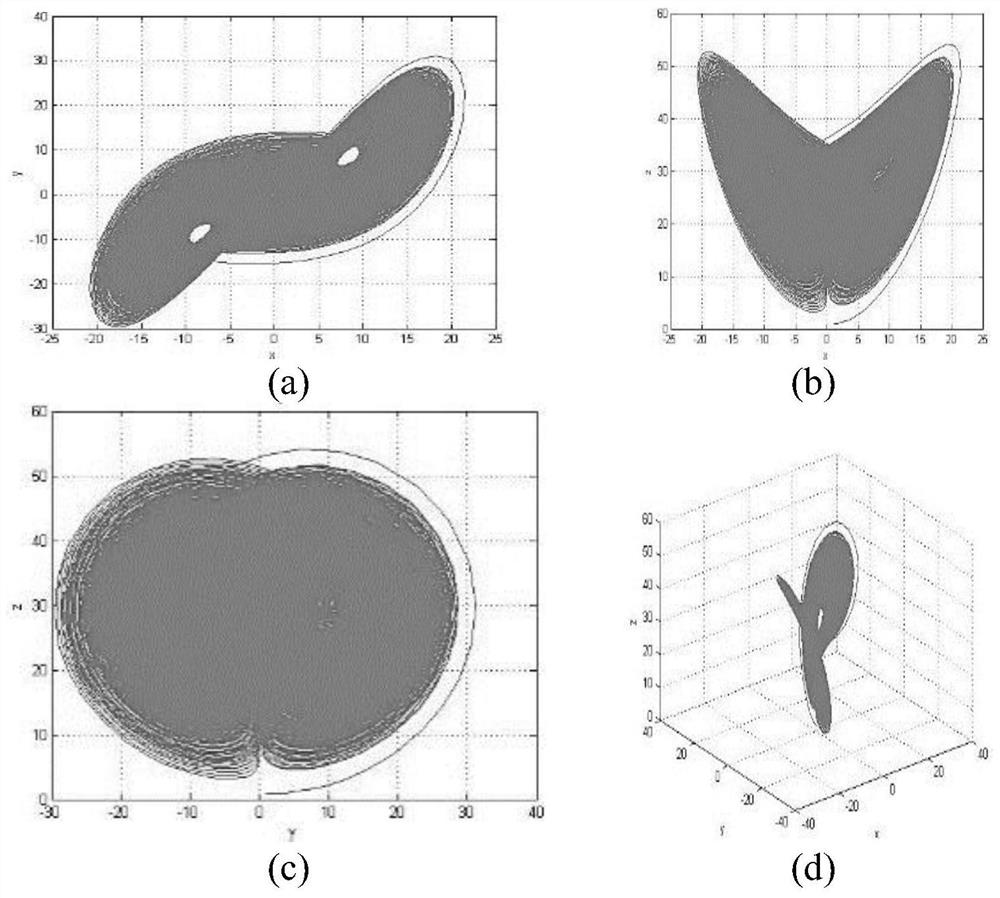
Image encryption method based on fractional order Lorenz chaotic system, and storage medium
PendingCN114022339AComplex dynamicsStrong pseudo-randomnessChaos modelsNon-linear system modelsImaging processingAlgorithm
The invention provides an image encryption method based on a fractional order Lorenz chaotic system, and a storage medium, belonging to the field of image processing. The method comprises the following steps: constructing the fractional order Lorenz chaotic system, and generating three chaotic sequences; scrambling the pixel position of a to-be-encrypted image P by using any two chaotic sequences; and performing chaotic encryption on a scrambled image pixel value by taking fragment combinations in the three chaotic sequences. According to the invention, the chaotic sequence generated by a new system is utilized to encrypt a gray level image, and an analysis result shows that a new fractional order system has more advantages in application in related fields such as image encryption and communication secrecy, and has more complex dynamic characteristics, stronger pseudo-randomness and unpredictability, strong attack resistance, larger parameter space and higher safety.
Owner:新疆理工学院
Non-coherent frequency compensation, demodulation method and demodulating apparatus
InactiveCN101309253BSimpler than coherent demodulationReduce hardware requirementsMultiple carrier systemsShortest distanceTime signal
The invention proposes an incoherent frequency compensation and demodulation method and a demodulation device which have low power consumption, high performance and use the pseudo-randomness of the received signal phase and the PN code to realize the wireless digital communication data demodulation which has short distance, low power consumption and low packet loss rate through the carrier frequency error compensation and data recovery; the demodulation device is composed of a digital low-converter, a channel filter, a phase arithmetic unit, a phase differentiator, a frequency compensator and a PN code de-spreading correlator; the intermediate signal is converted into the plural baseband signals which are processed with channel outer band noise filtration so that the amplitude-time signal is converted into the phase-time signal; the phase differentiator is adopted to differentiate the phase-time signal; the frequency compensation circuit compensate the carrier frequency according to the phase difference signal and the phase average signal; the carrier frequency and the phase recovery circuit are avoided; the PN code correlator group processes the matching demodulation towards the semi-cosine shaping 0QPSK and MSK signals of the DSSS directly to recover the baseband data; the incoherent frequency compensation and demodulation method and the demodulation device has the advantages of simple circuit, less quantity of hardware, easy low power consumption integration, good demodulation performance and being applicable to the wireless satellite navigation and the short-range wireless communication device with batteries as the power supply.
Owner:杭州中科微电子有限公司
Secure communication method based on end information extension sequence and m sequence
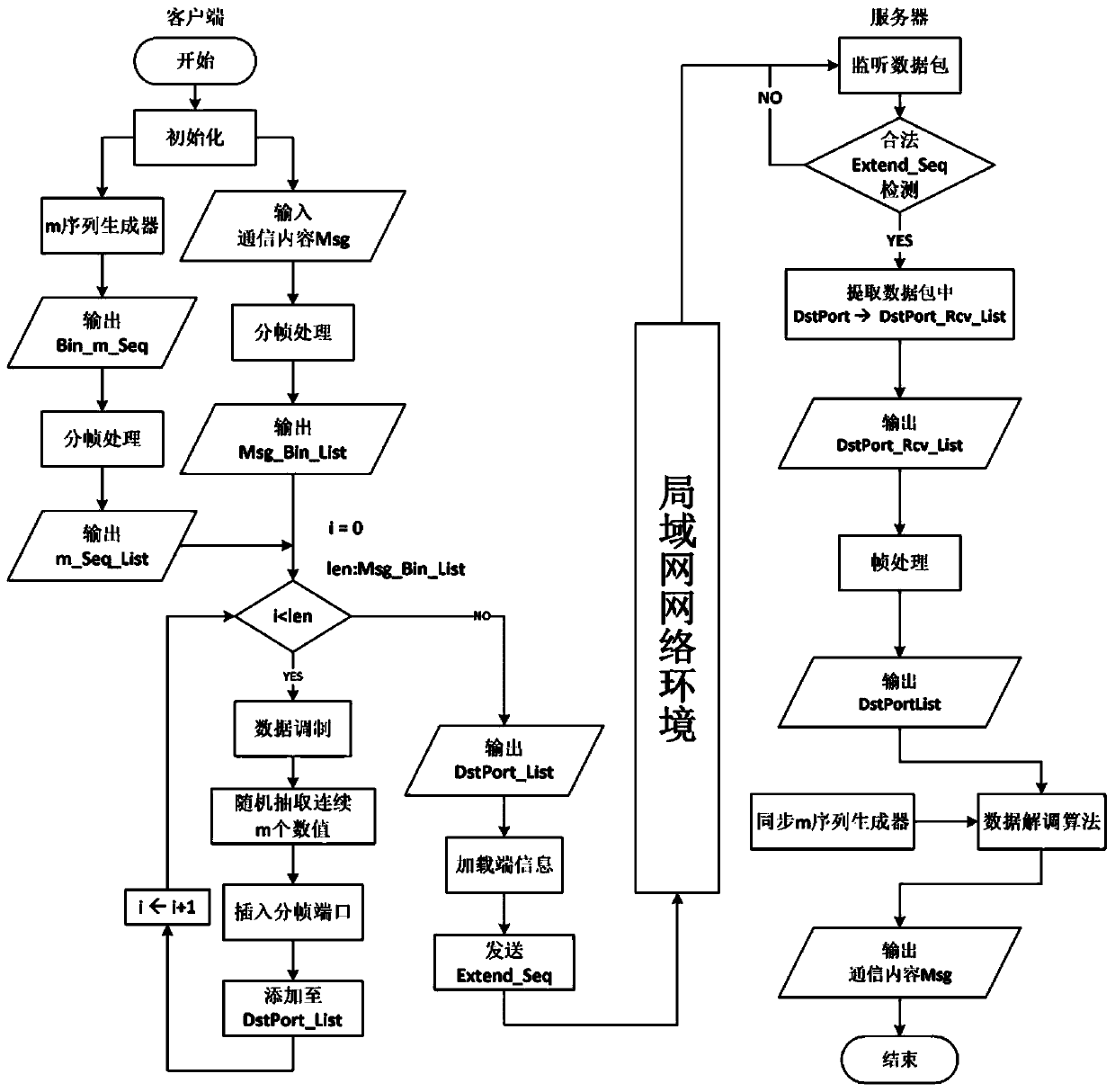
ActiveCN111525942AImprove terminal information utilizationImprove noise immunityTransmission format adaptationSecure communicationInterference (communication)
The invention relates to a secure communication method based on an end information extension sequence and an m sequence. According to the method, an m sequence is introduced in the process of loadingcommunication content Msg to an end information extension sequence by a client, and modulation of the m sequence by the communication content Msg is realized through a data modulation algorithm, so that the characteristic of poor pseudo-randomness of the existing end information extension sequence is improved, and the anti-analysis capability of the existing end information extension sequence is improved. The end information extension sequence is demodulated by using the m sequence generated synchronously at the server end so as to recover the communication content Msg of the client. In the modulation process, a data framing algorithm is used for preprocessing the communication content Msg, a server side uses a reverse algorithm of the data framing algorithm to analyze a side information extension sequence, and therefore high content accuracy can be obtained at the server side. According to the invention, the pseudo-randomness and anti-noise interference capability of the end information extension sequence can be effectively improved, so that the secure communication based on the end information extension sequence is better suitable for a complex network environment.
Owner:CHINA UNIV OF PETROLEUM (EAST CHINA)
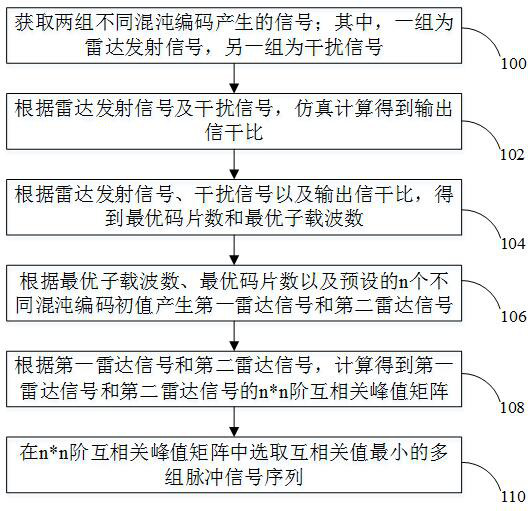
Radar signal optimization method, device, computer equipment and storage medium
ActiveCN112394333BImprove anti-interference abilityLow anti-copy and forward interference performanceWave based measurement systemsCarrier signalPseudo randomness
The application relates to a radar signal optimization method, device, computer equipment and storage medium. The method utilizes the initial value sensitivity and pseudo-randomness of chaotic coding, and optimizes the key parameters of the signal waveform by reducing the correlation between adjacent pulse signals. : The number of subcarriers, the number of chips, and the initial value of chaos, etc., and then obtain the radar pulse signal combination method with the best anti-replication and forwarding interference performance. And copied the signal pulse, but the process of identification and copying takes a certain amount of time, and the matching gain cannot be obtained with the subsequent pulse, so it has an excellent ability to resist copying and forwarding interference. This method adopts the waveform optimization method to improve the anti-replication and forwarding interference performance of the radar, does not require additional calculations during signal processing, and is more suitable for engineering applications.
Owner:CHANGSHA UNIVERSITY OF SCIENCE AND TECHNOLOGY
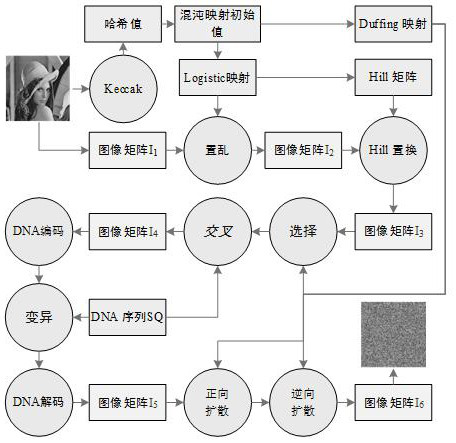
An Image Encryption Method Based on Duffing Mapping and Genetic Operation
ActiveCN109376540BIncreased sensitivityIncrease the difficulty of decipheringDigital data protectionTheoretical computer scienceGenetics algorithms
The invention provides an image encryption method based on Duffing mapping and genetic operation. The hash value of a plaintext image is calculated by using a Keccak algorithm as an initial value input key of a chaotic system; the sensitivity and pseudo-randomness of the chaotic map to the initial conditions are used, the pseudo-random sequence is obtained by iterating the Logistic map and the Hill encryption matrix is generated to scramble and replace the image matrix. Combined with Duffing map and DNA coding technology, pixel selection, crossover and mutation are realized by genetic operation to achieve pixel diffusion and scrambling, and bidirectional exclusive OR operation with chaotic sequence to enhance its confusion and diffusion characteristics. The invention utilizes the pseudo-randomness of Duffing mapping and Logistic mapping, ergodicity and the crossover mutation operation of genetic algorithm, has strong sensitivity to key, can effectively resist statistical attack and differential attack, etc., has good security and application potential, and the image encryption effect and performance are remarkably improved.
Owner:ZHENGZHOU UNIVERSITY OF LIGHT INDUSTRY
A Chaotic Encryption Method for Speech Information
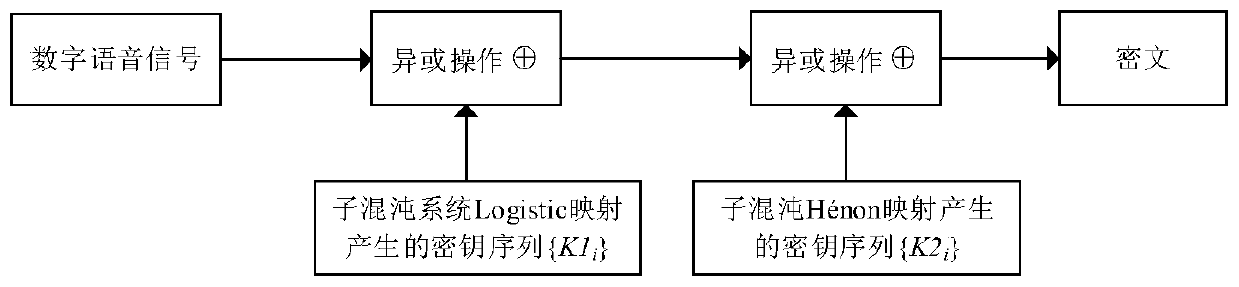
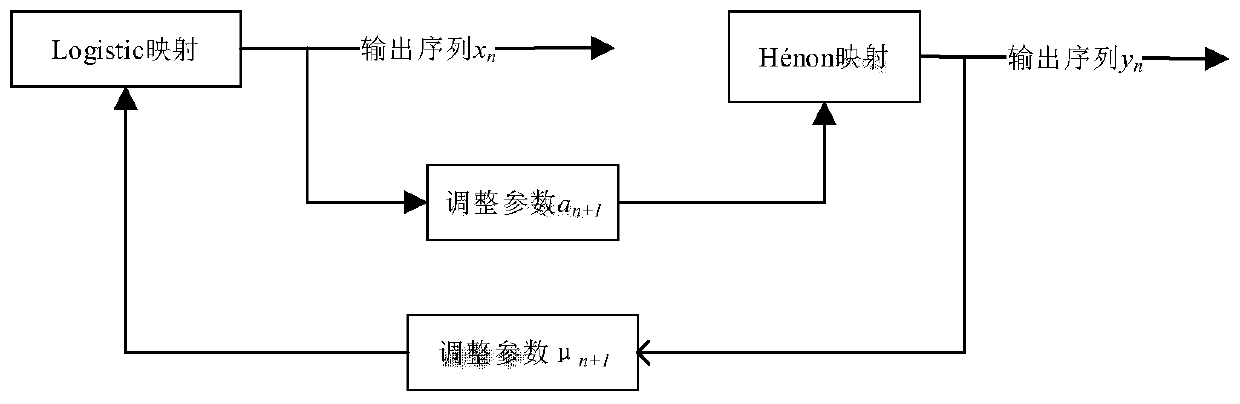
ActiveCN106375079BGood pseudorandomnessExtended cycleSecuring communication by chaotic signalsKey spaceAlgorithm
The invention discloses a chaotic encryption method for voice information. The method is characterized in comprising the steps of 1), establishing a dynamic variable parameter composite chaotic system and generating a real-value chaotic sequence of which length is the same to that of a plaintext voice sequence through utilization of the system; 2), carrying out binarization processing on the real-value chaotic sequence, thereby obtaining a chaotic key sequence of which length is the same to that of the plaintext voice sequence; and 3), through combination of the chaotic key sequence, carrying out bit-by-bit exclusive or operation on the plaintext voice sequence, thereby obtaining a ciphertext. According to the method, under limited calculation precision, the chaotic sequence with good pseudo-randomness can be generated, the valid precision effect is reduced, and a chaotic sequence cycle is prolonged; and through adoption of a chaotic system cascading mode, the encryption security is improved, a sufficient key space can be generated, and an exhaustive attack can be resisted effectively.
Owner:HUAQIAO UNIVERSITY
Multi-source Input True Random Number Generator Circuit Architecture
ActiveCN103955352BEliminate pseudo-randomnessImprove true randomnessRandom number generatorsInput selectionPseudo randomness
The invention discloses a multisource input true random number generator circuit structure. Multiple noise generating circuits of different types are used as noise sources; with input selection of an option switch, the noise is input into a sampling correcting circuit; on one hand, the input result enters into an output processing module, and on the other hand, the input result enters into a random number counter; the random number counter counts the generated random number, and feeds back the output result to the option switch; then the signals are randomly selected from the multiple noise generating circuits and then output. In the process, due to the randomness of selection from the multiple noise sources, the randomness of the sampling correcting output, and the randomness of application of the random number counter, the pseudo-randomness generated by the original single noise generating circuit due to long-time working can be eliminated wholly. Proved by the theory and experiments, the true random number generator utilizes multiple noise sources and the random number counter to realize feedback, so that the randomness of the long-range data is better than the original random number generator realized by the single noise source.
Owner:58TH RES INST OF CETC
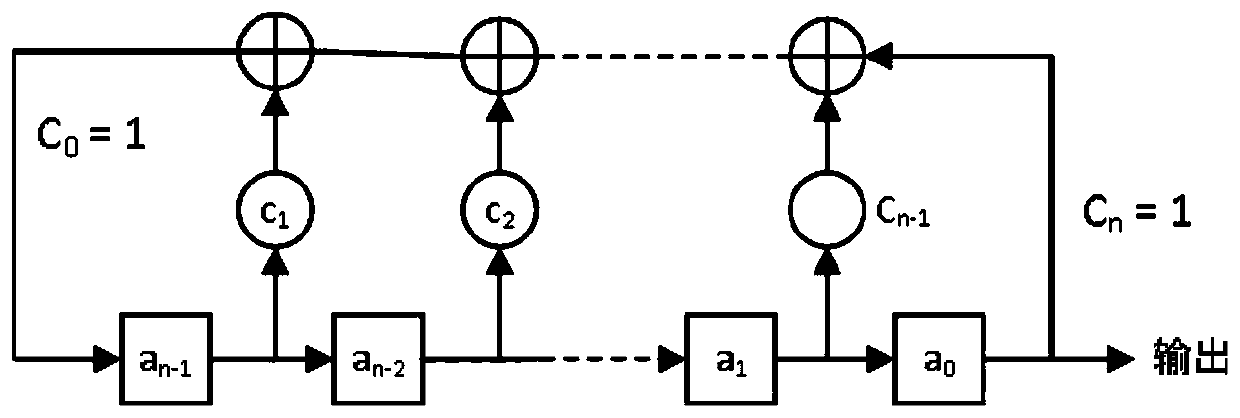
Interleaved Memory Pseudo-Random Mapping Method for Parallel Computing
ActiveCN113655966BReduce storage latencySimple designInput/output to record carriersRandom number generatorsConcurrent computationParallel computing
The invention discloses a cross-memory pseudo-random mapping method for parallel computing. The pseudo-random sequence generated by the maximum sequence code (m-sequence) is used to form an address mapping matrix, which can improve the performance of parallel access and parallel computing, and slow down Store latency in dynamic memory. The present invention adopts an H matrix adjustment method of address mapping, overcomes the weakness of the previous method, and ensures that the same H matrix can be used for forward mapping and reverse mapping. The address mapping matrix generated by the invention is combined with the XOR function to form an address mapping circuit, which is easy to design and simple in structure. For different address widths, the present invention uses an address division mapping method to optimize the pseudo-randomness of the mapping matrix to improve parallel storage performance.
Owner:HEXAFLAKE (NANJING) INFORMATION TECH CO LTD
true random number generator
ActiveCN106293617BIncrease randomnessEliminate pseudo-randomnessRandom number generatorsReusabilityPseudo randomness
The invention relates to the technical field of circuits and discloses a true random number generator. The true random number generator comprises a random signal generation source circuit, a true random number generation circuit, a PRNG (pseudo random number generator) and a random number interceptor, wherein the random signal generation source circuit is used for generating random number generation source signals; the true random number generation circuit is used for sampling and diffusing the random number generation source signals and a true random number sequence is obtained; the PRNG is used for outputting the serial or parallel random number sequence according to the input true random number sequence; the random number interceptor is used for intercepting the random number sequence of the preset length from the random number sequence output from the PRNG according to the input true random number sequence and feeding back the intercepted random number sequence to the random signal generation source circuit; the random signal generation source circuit is used for adjusting the random number generation source signals according to the random number sequence fed back by the random number interceptor. The true random number generator can be realized through an ordinary logic device, the circuit structure is simple, the true random number generator is independent of the process and has good reusability, and a feedback mechanism is added, therefore, pseudo-randomness due to long-time working without feedback can be eliminated.
Owner:上海坚芯电子科技有限公司
Encryption method for digital archive
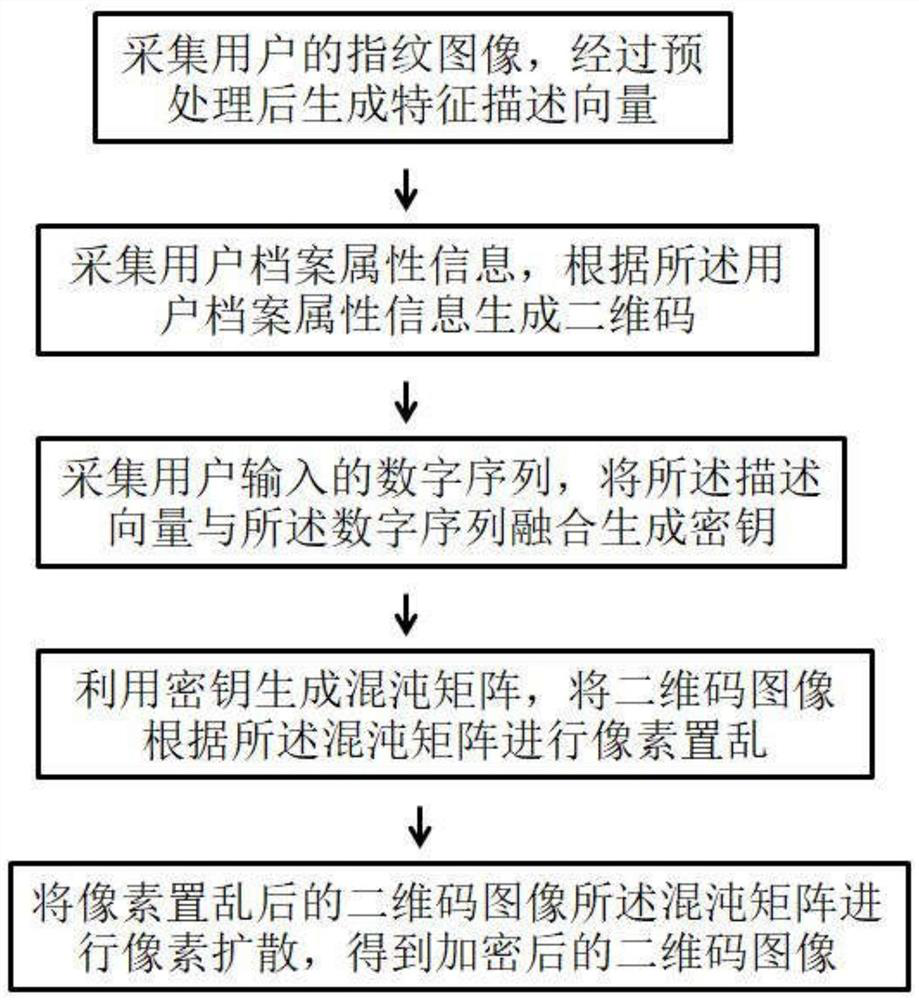
PendingCN113989091AUniqueness guaranteedReduce correlationImage data processing detailsPattern recognitionPseudo randomness
The invention discloses an encryption method for a digital archive. The encryption method comprises the following steps of: generating a chaotic matrix by taking a secret key fused with fingerprint information and a user input sequence as an initial state of a system, scrambling the positions of image pixel points through the pseudo-randomness of the chaotic matrix, and executing mod operation on the scrambled image and the chaotic matrix at a corresponding position. Therefore, encrypted pixels are changed, a pixel correlation is reduced, and original image information is protected. Meanwhile, the use of the fingerprint information also ensures the uniqueness of the secret key, and encryption security is improved.
Owner:北京市东成恒悦汽车科技有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com