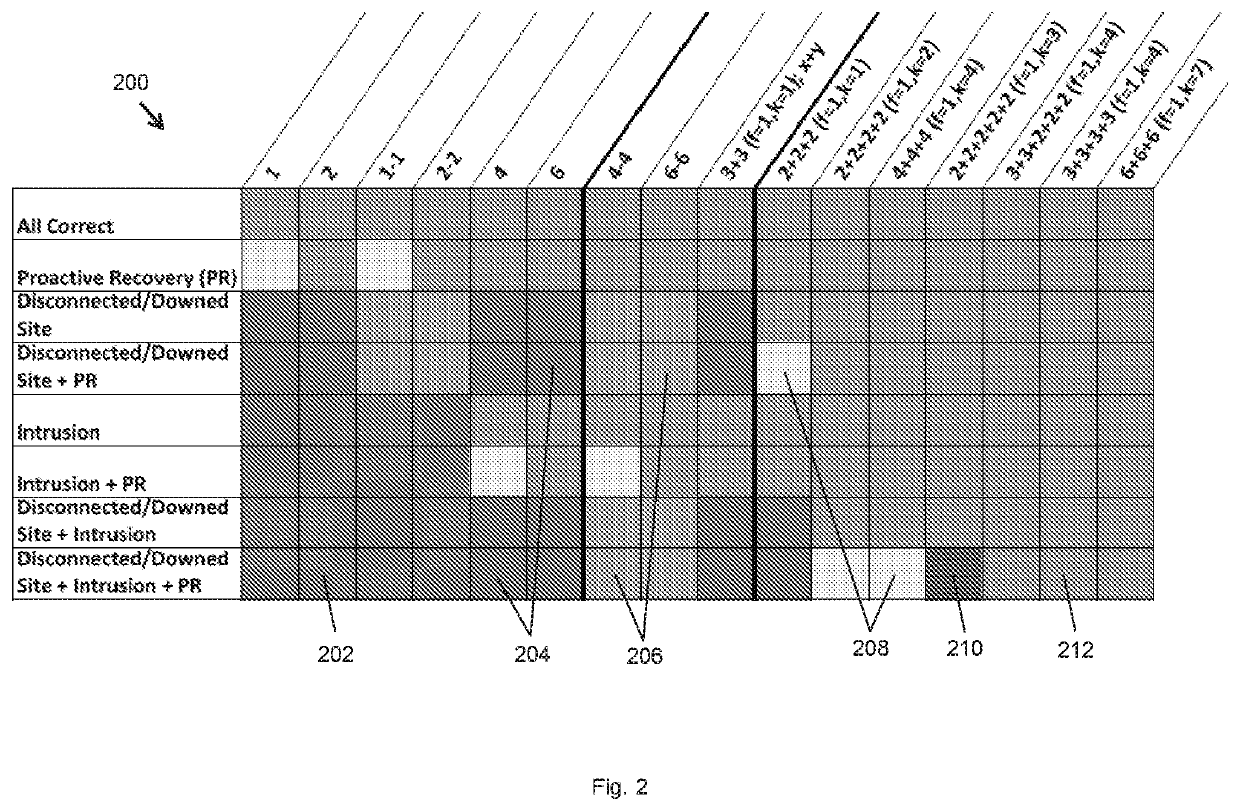
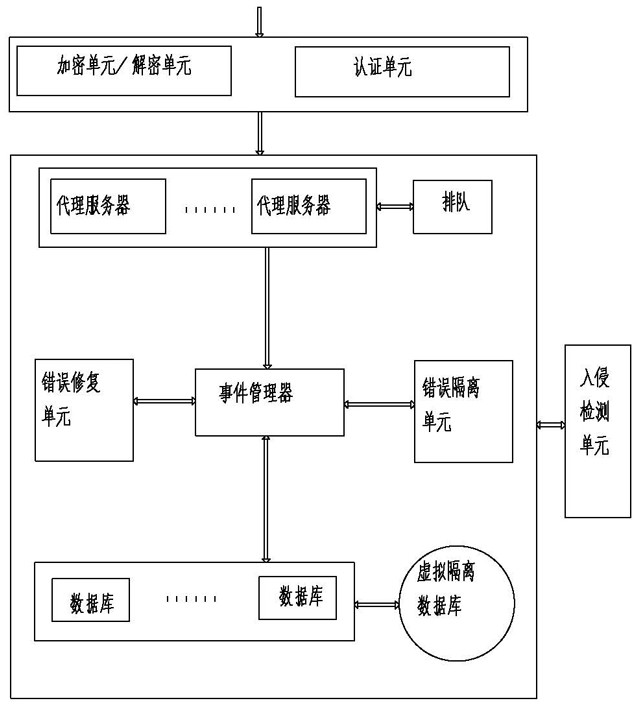
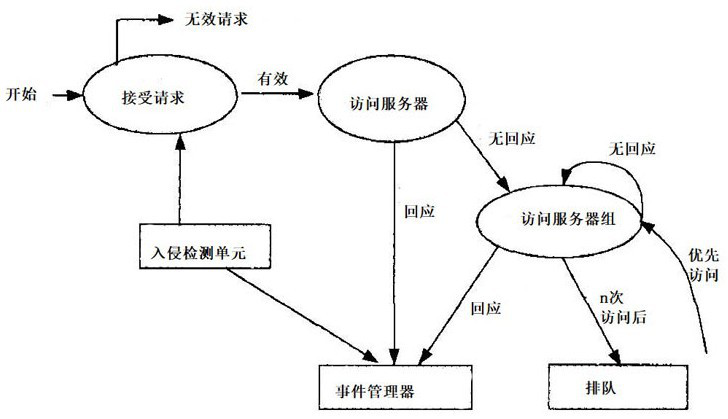
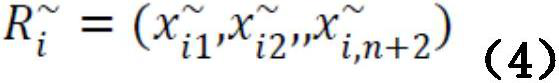Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
34 results about "Intrusion tolerance" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Intrusion tolerance is a fault-tolerant design approach to defending information systems against malicious attack. Abandoning the conventional aim of preventing all intrusions, intrusion tolerance instead calls for triggering mechanisms that prevent intrusions from leading to a system security failure.
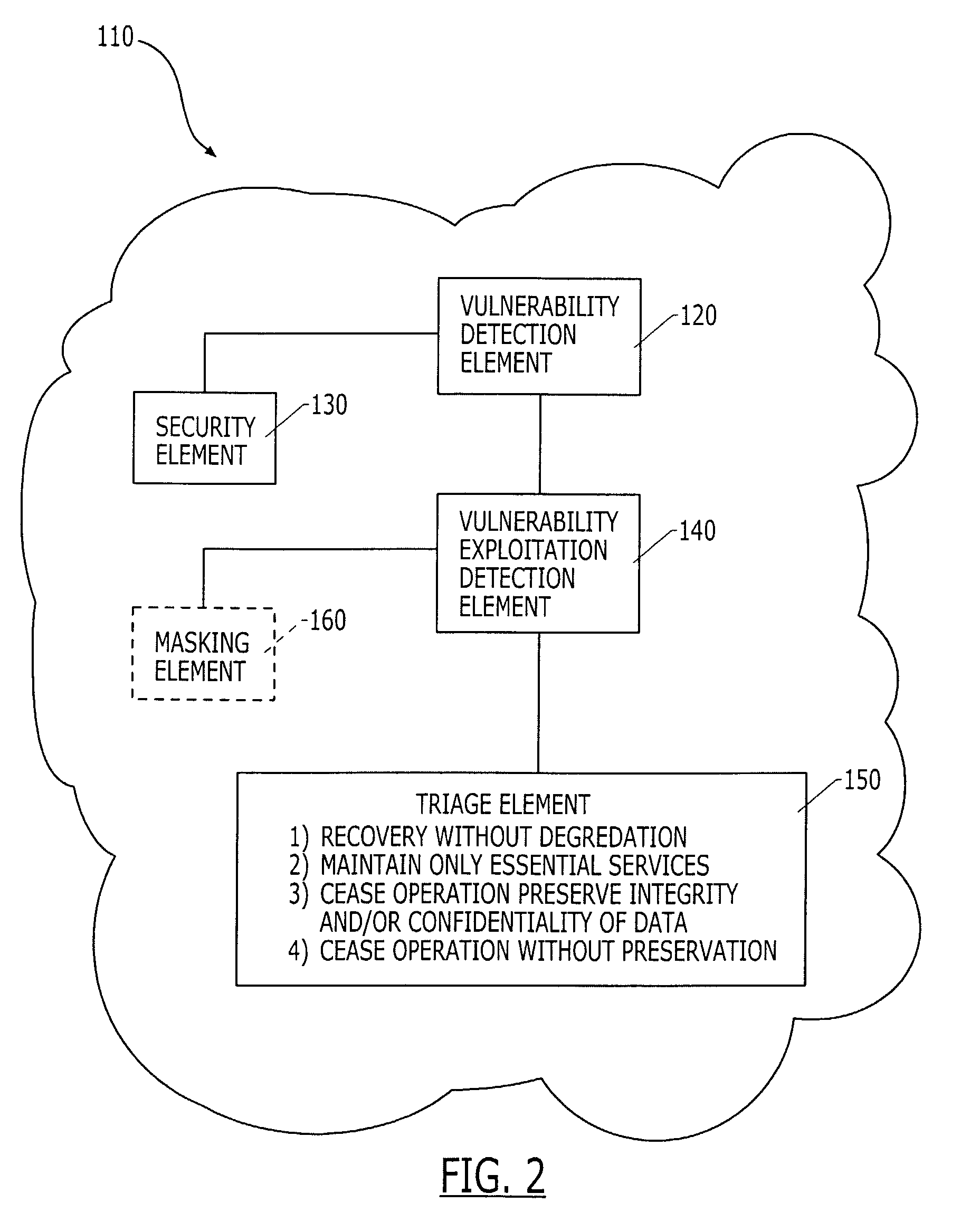
Intrusion tolerant server system
InactiveUS7076801B2Minimize impactDigital data processing detailsMultiple digital computer combinationsIntrusion toleranceClient-side
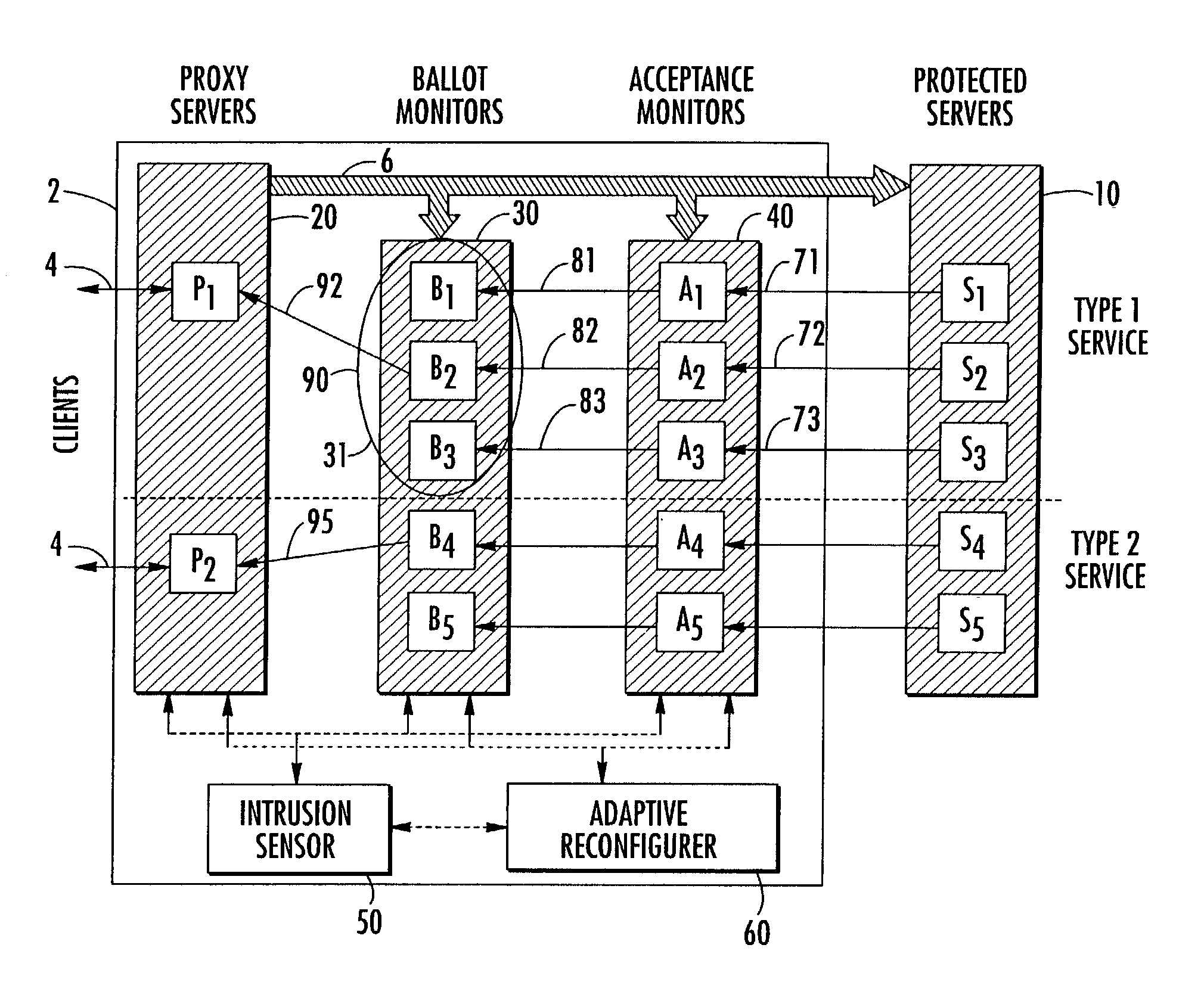
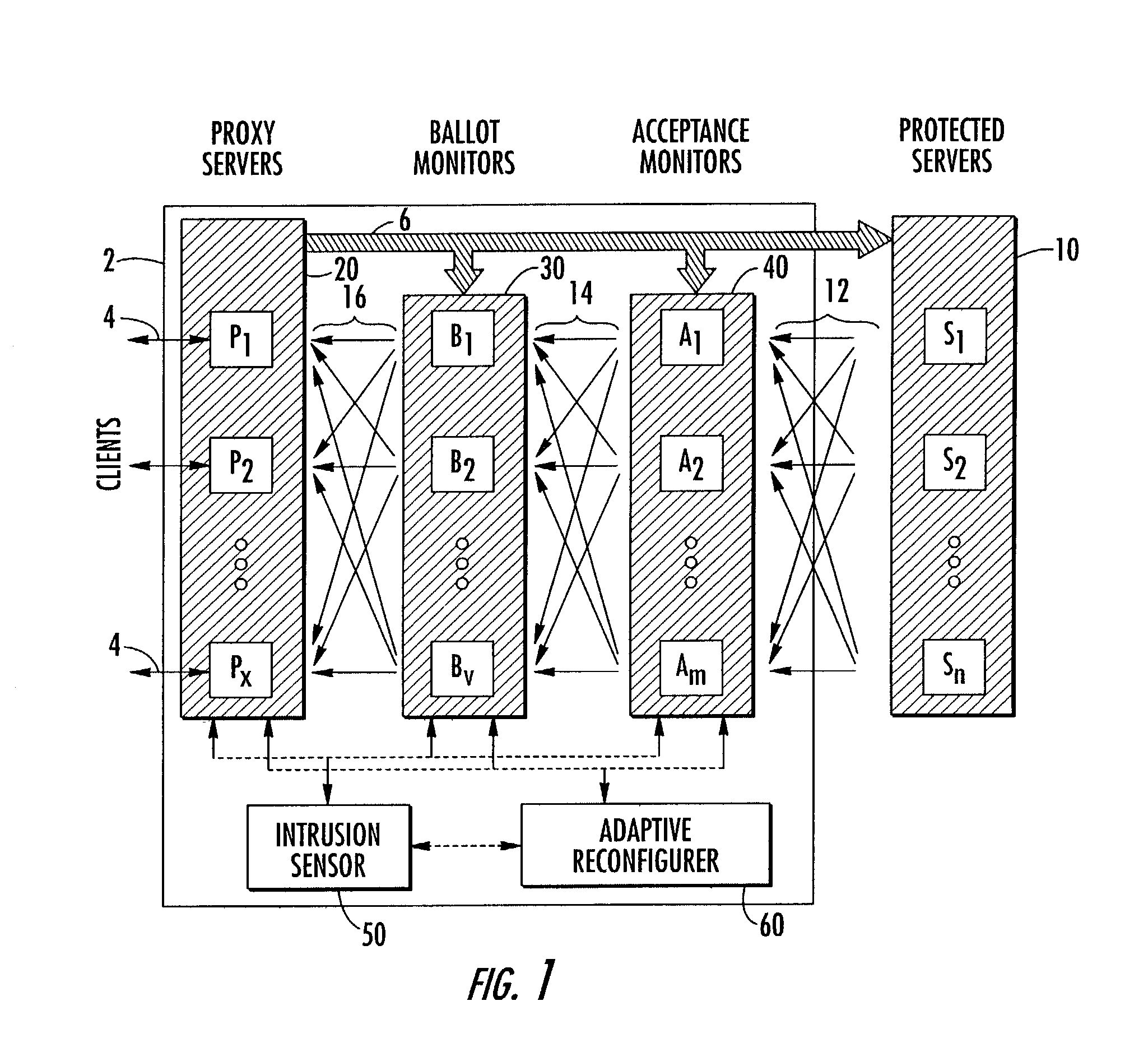
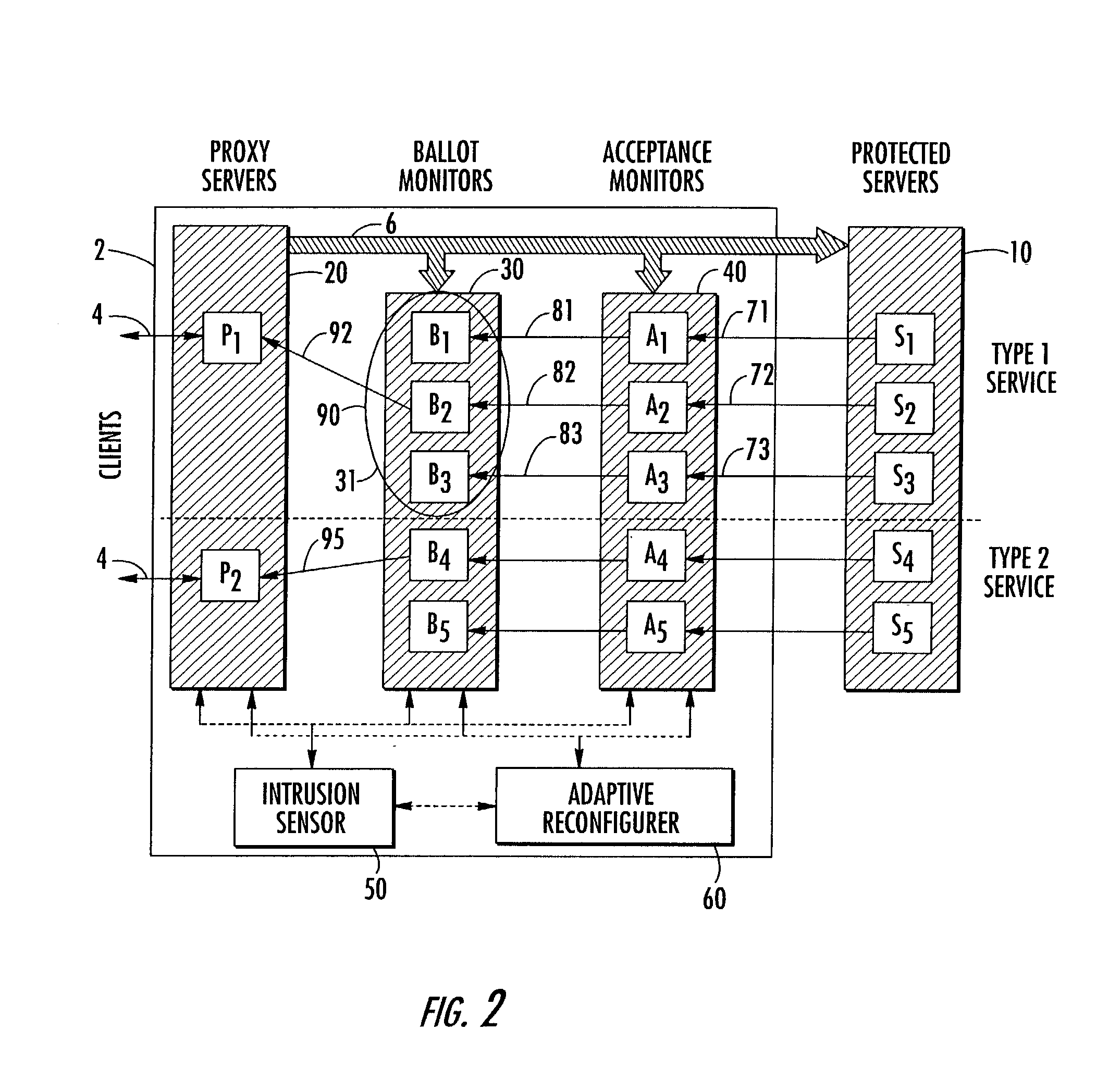
The invention relates to a reconfigurable scalable intrusion-tolerant network that is interposed between a service requesting client and a protected server to minimize the impact of intrusive events. The apparatus may include a proxy server for receiving the requests from a client and forwarding them to a protected server. Acceptance monitors receive the response from a protected server and apply one or more acceptance tests. A ballot monitor receives the result of the acceptance tests and determines a response to the client. The network may also include an intrusion sensor to detect threats to the network and a reconfigurer to alter the network forwarding scheme. Reconfiguration may include isolating network elements, creating parallel paths, implementing redundant operations, or assessing the validity of responses.
Owner:RES TRIANGLE INST
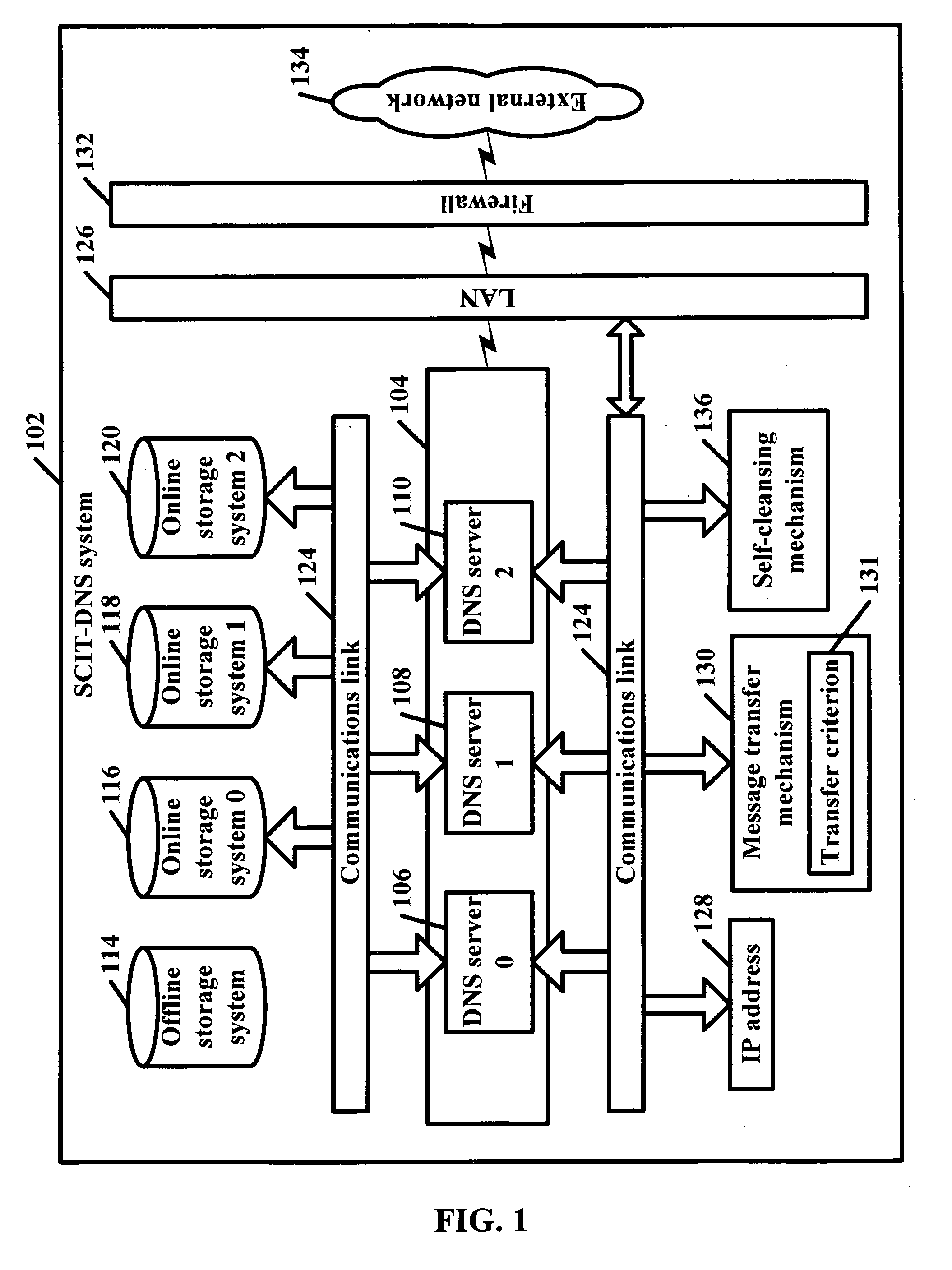
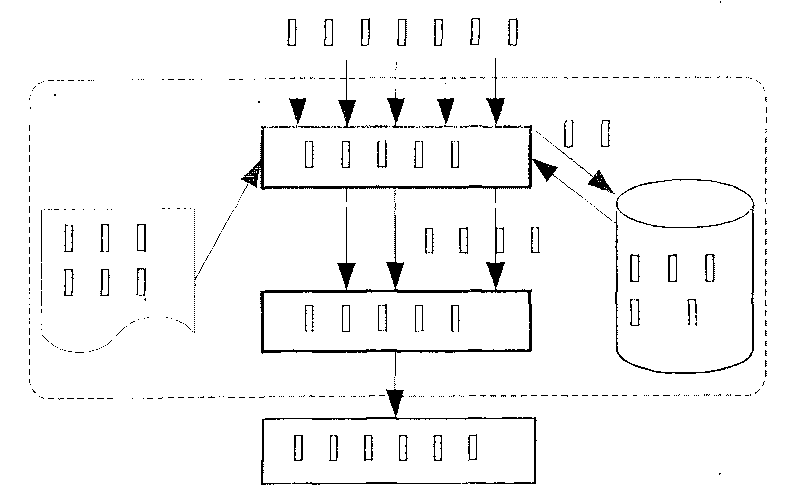
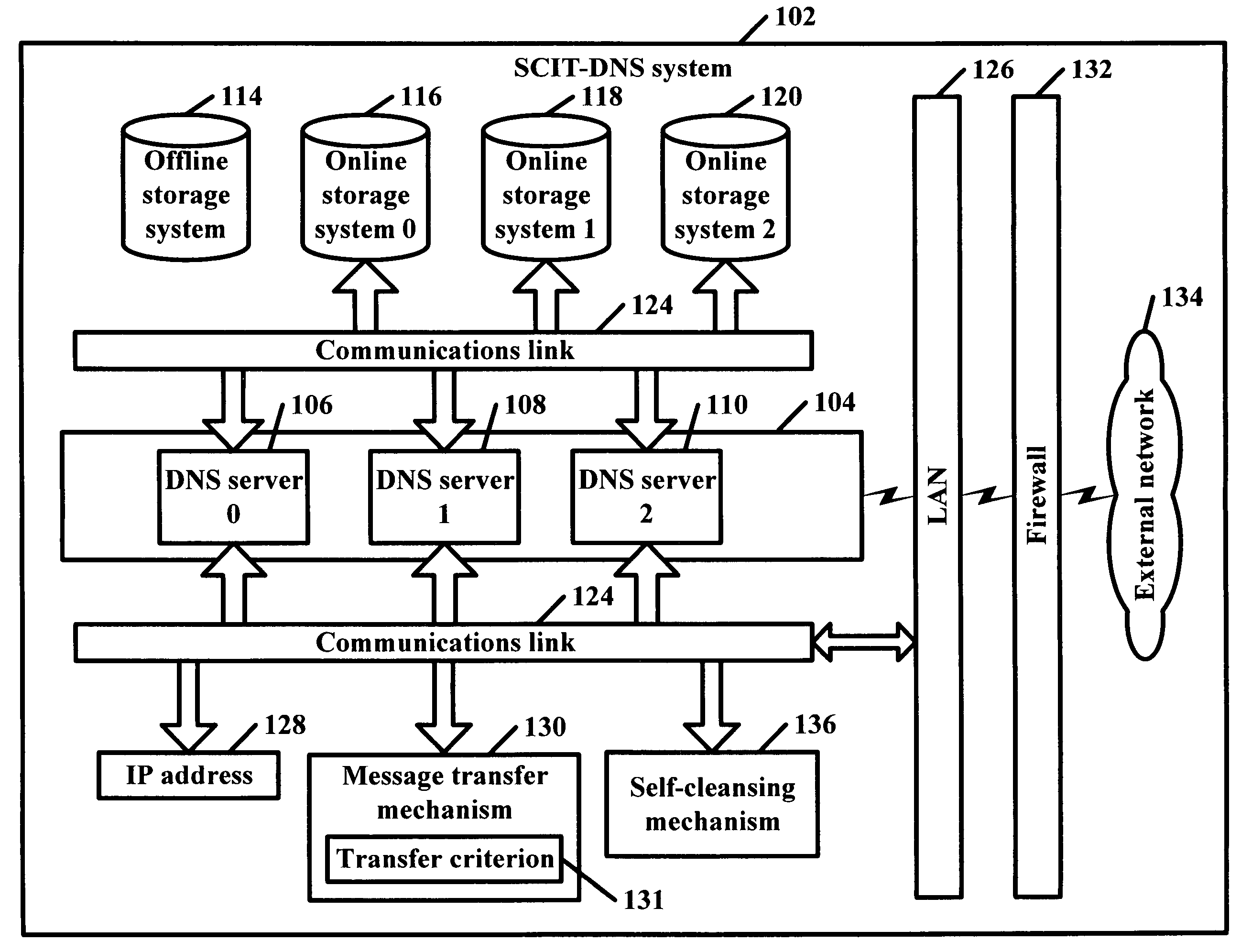
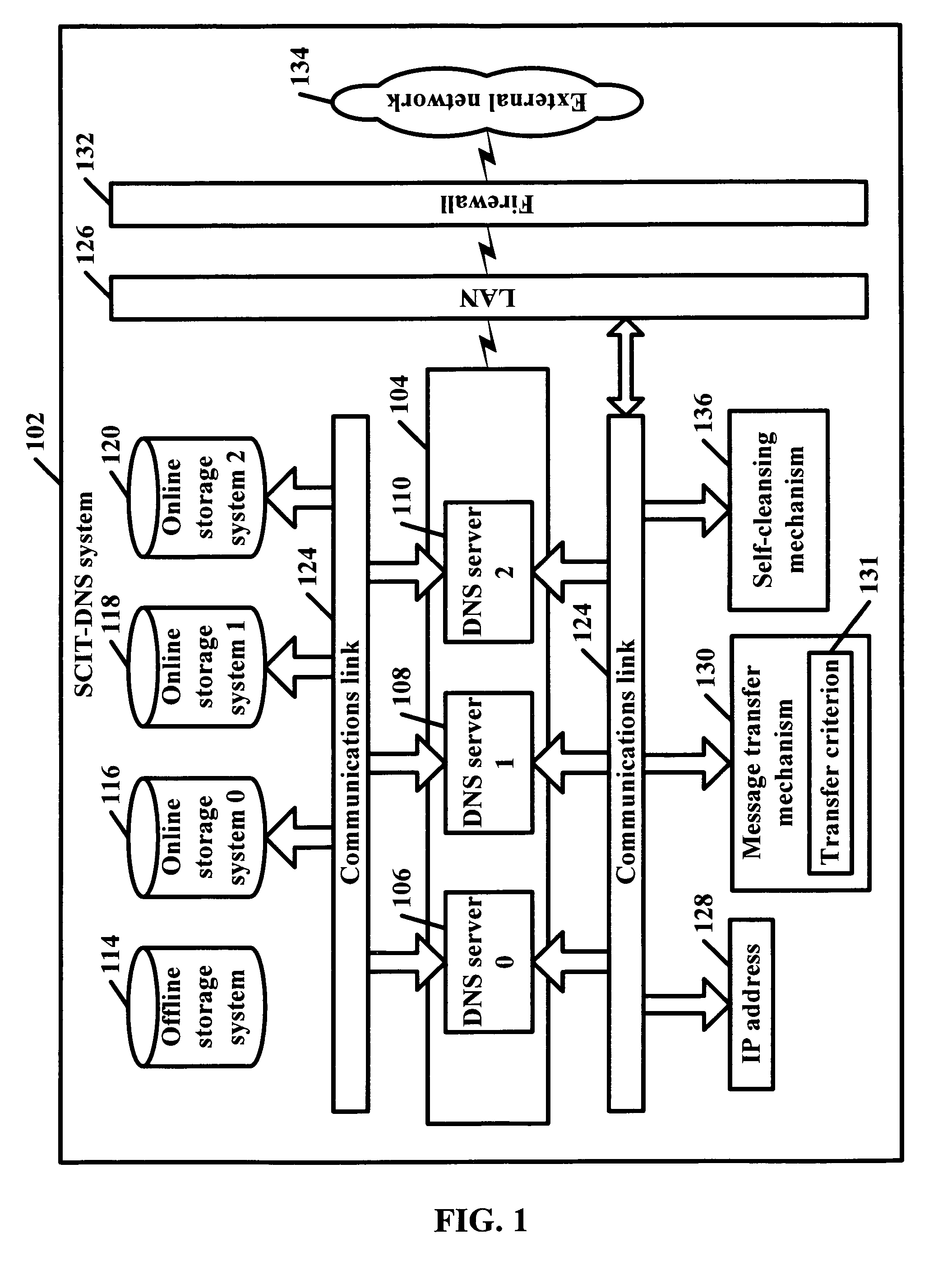
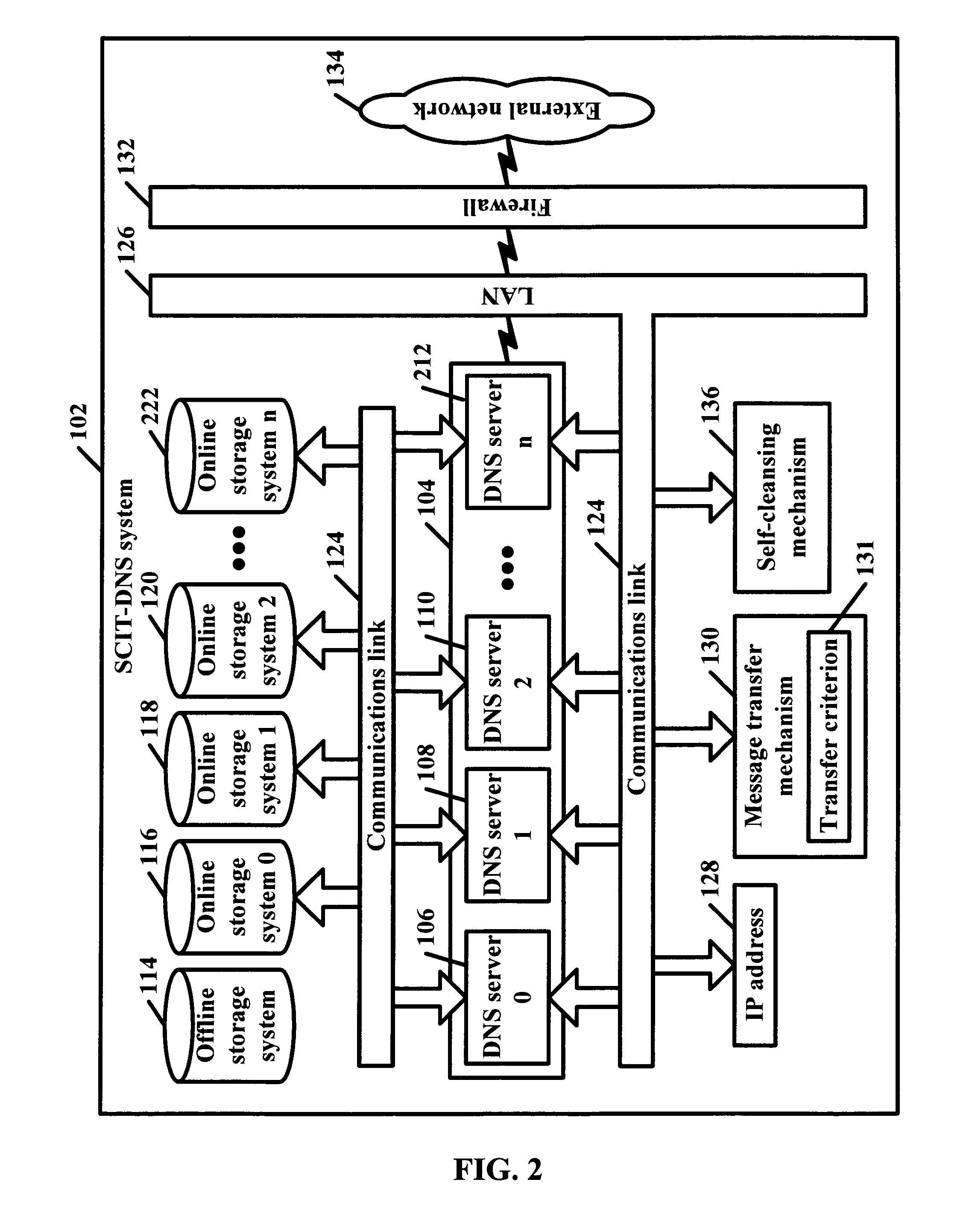
SCIT-DNS: critical infrastructure protection through secure DNS server dynamic updates
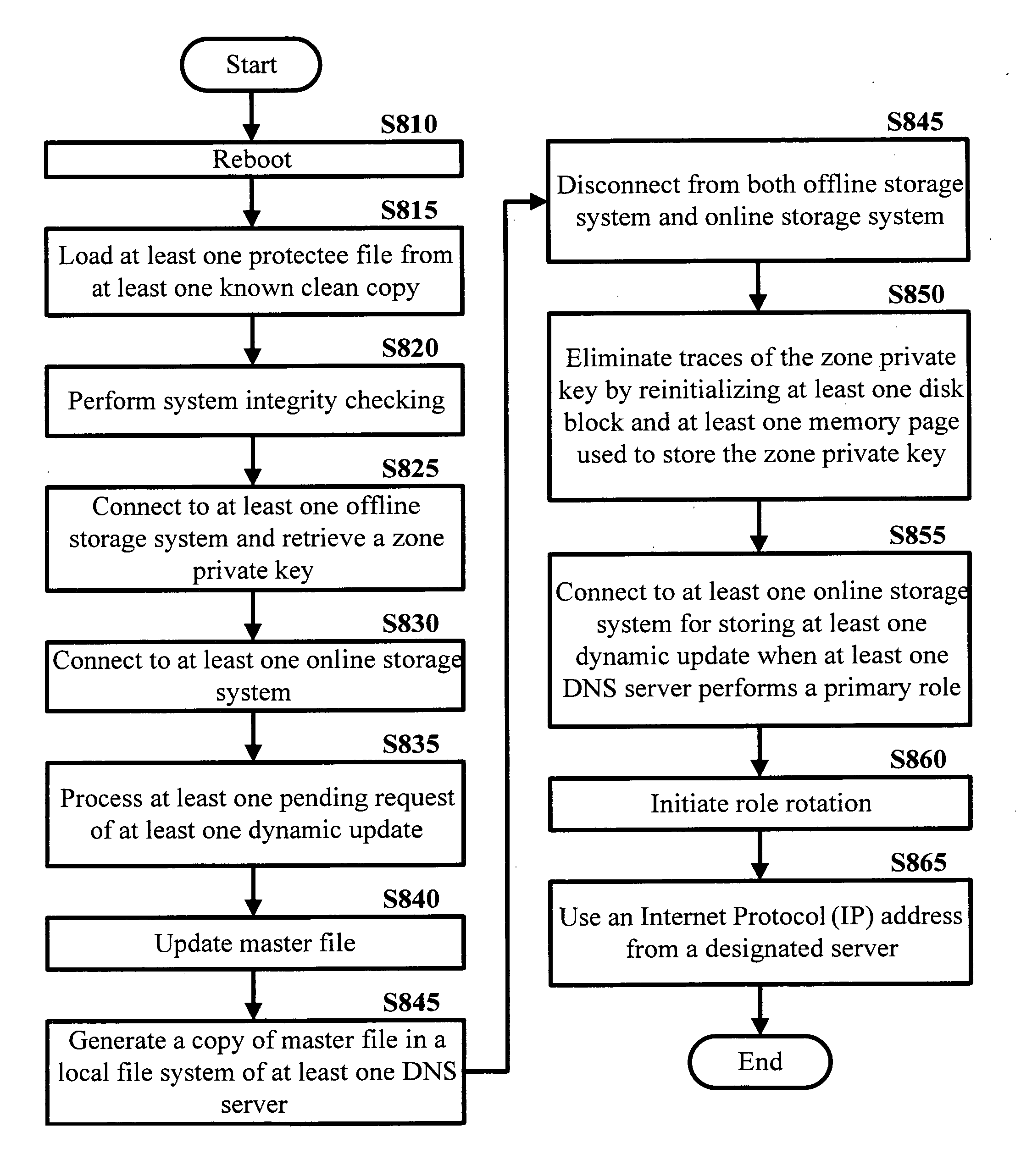
ActiveUS20060143711A1Protect resourcesEliminate tracesMemory loss protectionError detection/correctionDomain nameTelecommunications link
Disclosed is a self-cleansing intrusion tolerance-domain name systems system comprising at least three DNS servers, at least four storage systems accessible by the DNS servers, a communications link, a message transfer mechanism, and a self-cleansing mechanism. The storage systems include at least three online storage systems and at least one offline storage system. The communications link can connect the DNS servers with the storage systems, as well as connect the DNS servers with a local area network, which can connect the DNS servers with an external network. The message transfer mechanism can rotate the DNS servers into a plurality of roles, including a primary role, a secondary role, a designated role, and a self-cleansing role. The self-cleansing mechanism can be used to perform the self-cleansing role.
Owner:GEORGE MASON INTPROP INC
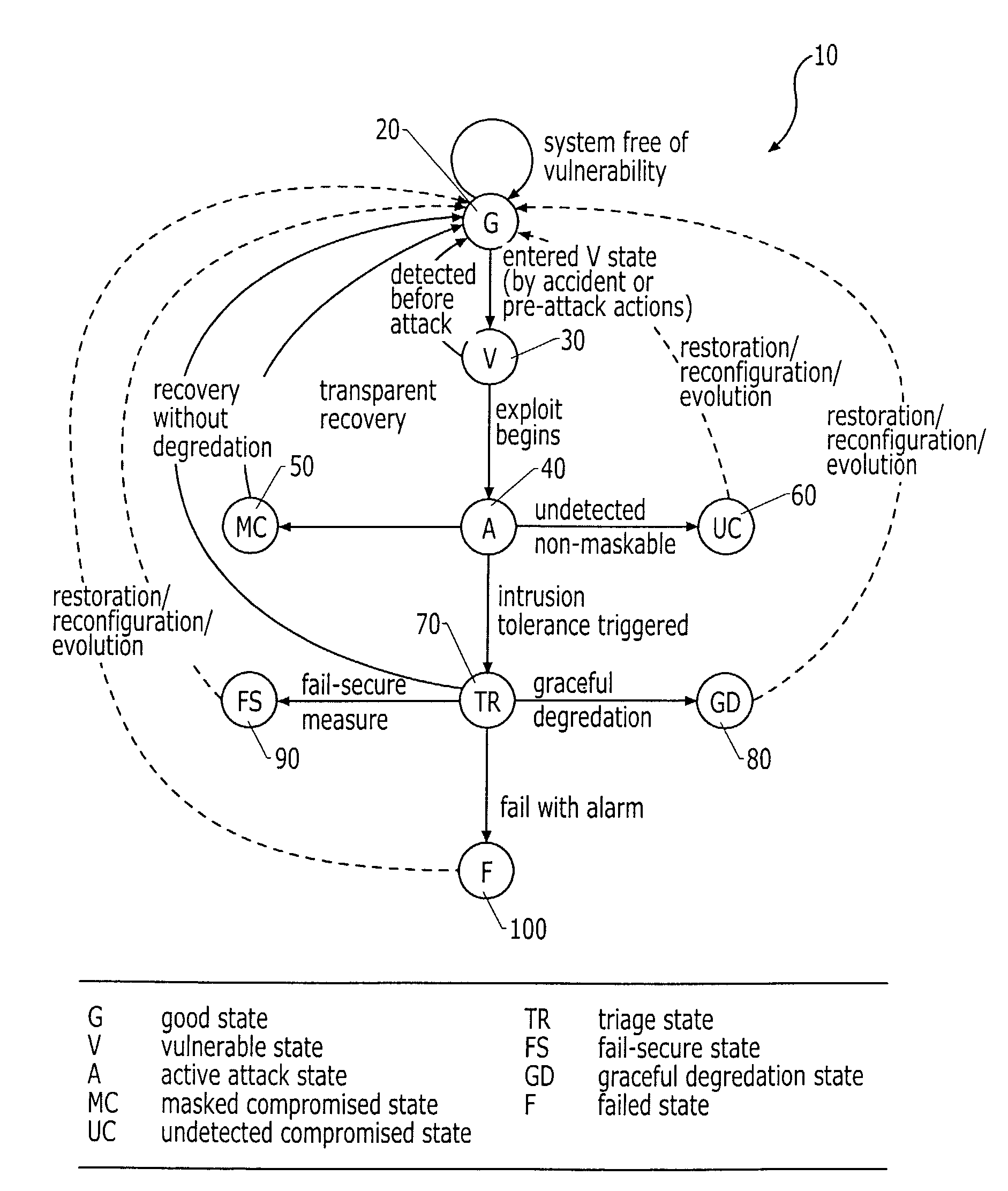
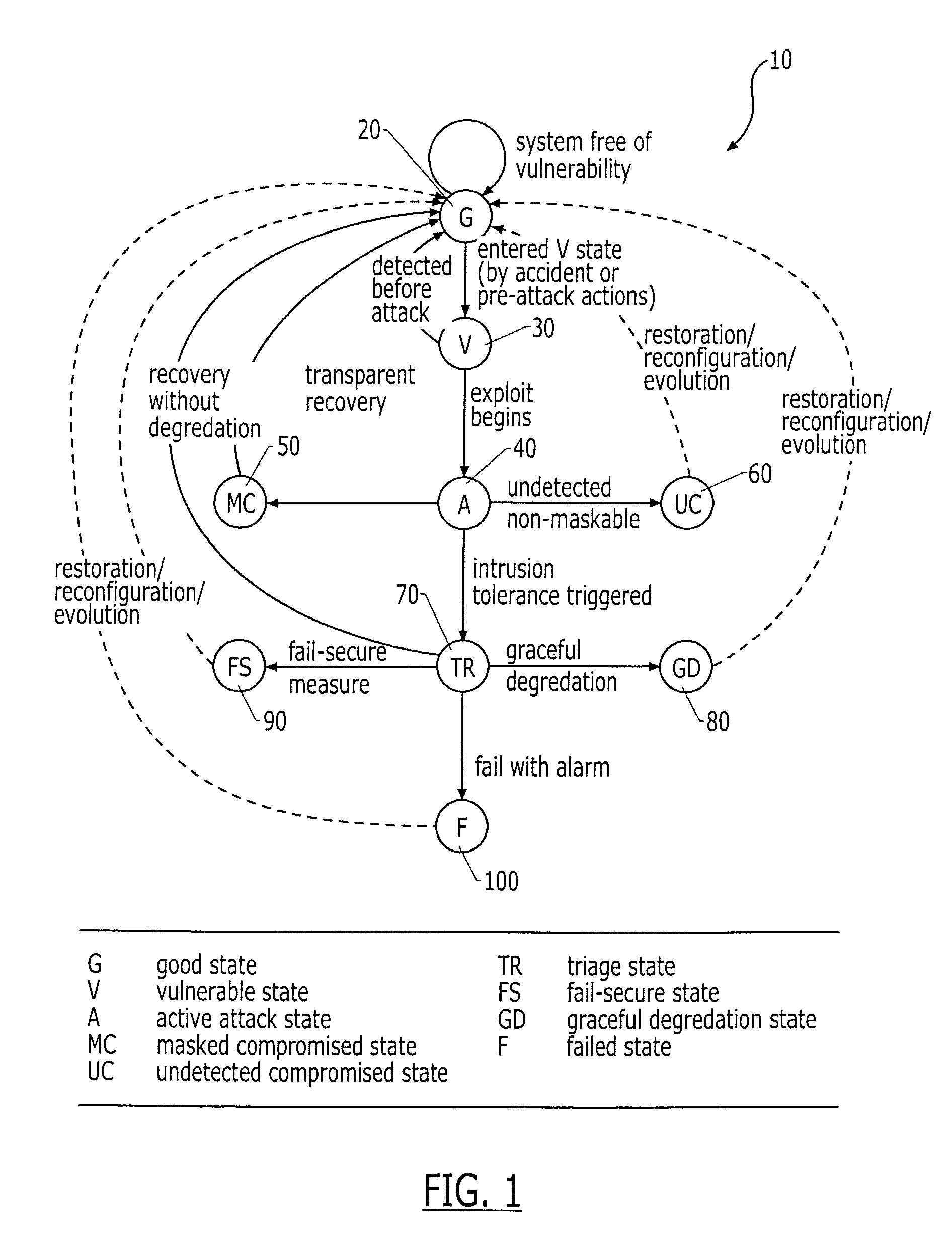
Intrusion tolerant communication networks and associated methods
InactiveUS7350234B2Memory loss protectionError detection/correctionIntrusion toleranceComputer security
An intrusion tolerant communication network and related methods is provided that places emphasis on continuity of operation and provides for an attack-survivable communication network whose network devices collectively accomplish the specified networking intent even under attack and despite active intrusions. The present invention defines methods for network intrusion tolerance in terms of the various state transitions that maximize the overall effectiveness of an intrusion tolerant communication network.
Owner:RES TRIANGLE INST
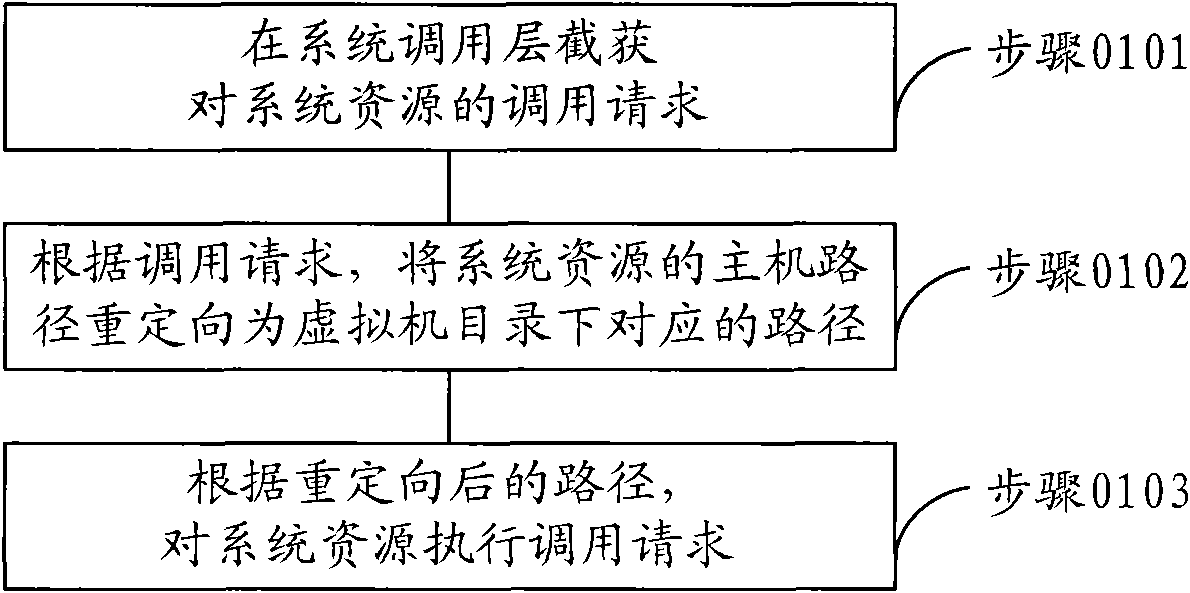
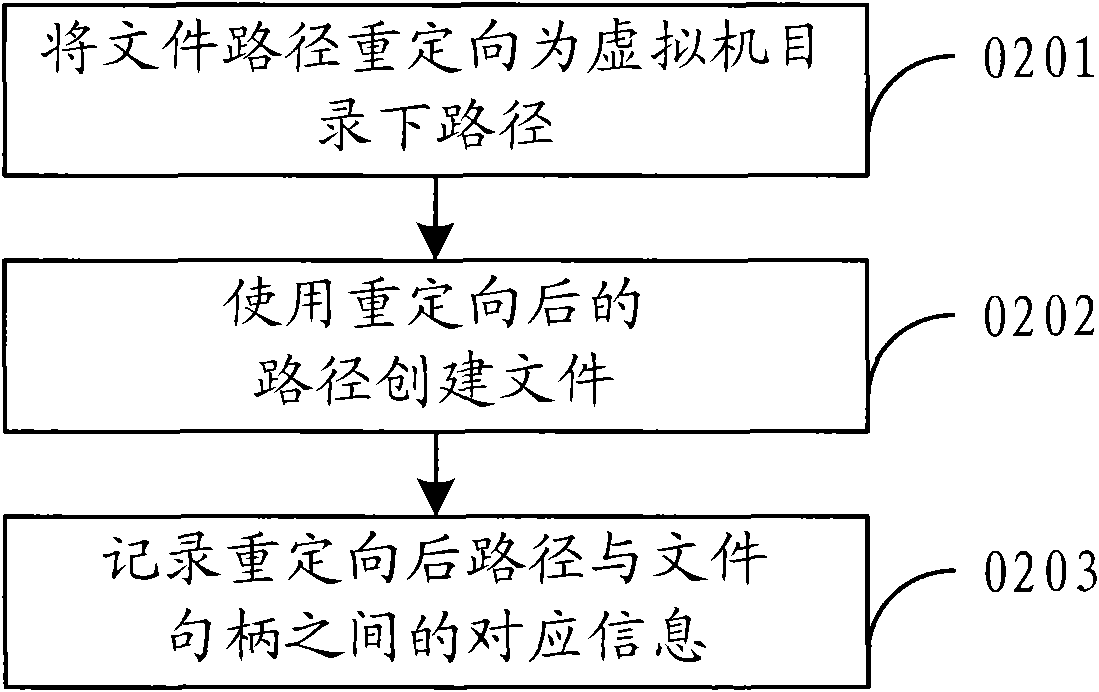
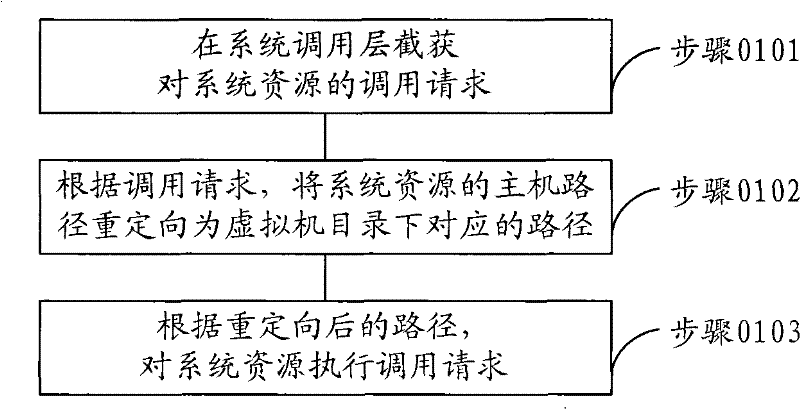
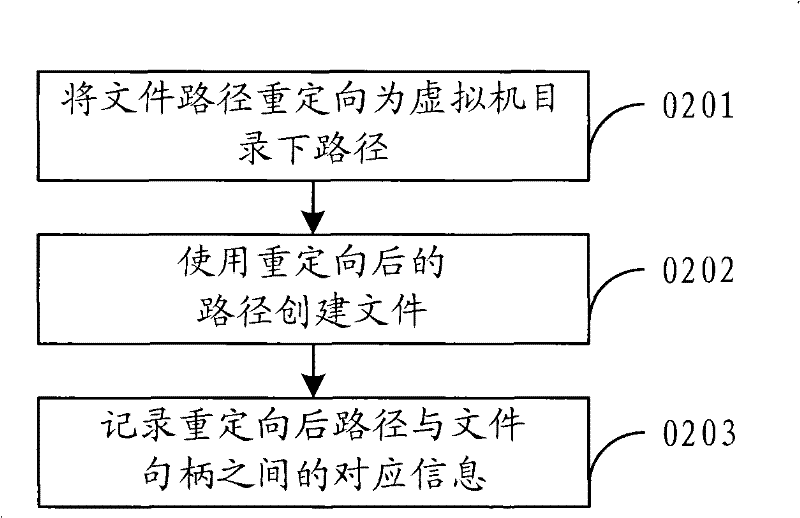
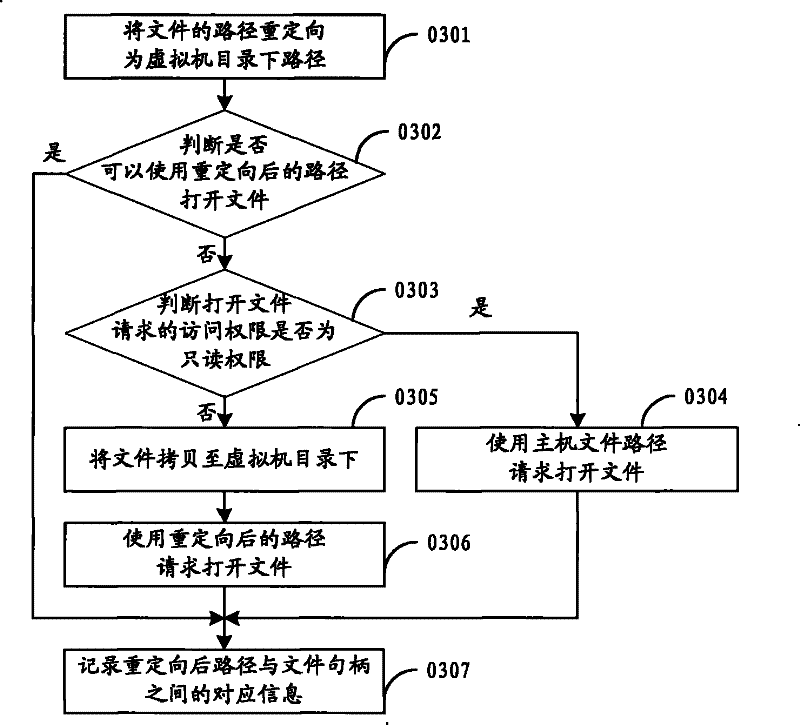
The virtual method and virtual device based on operating system layer
ActiveCN101551756ASave resourcesLess start-up delayProgram initiation/switchingSoftware simulation/interpretation/emulationVirtualizationOperational system
The embodiment of the present invention relates to a virtual method and virtual device based on operating system layer. Through intercepting the invoking request of system resource at system invocation layer, the host path of the system resource is redirected to the corresponding path under the directory of virtual machine; the virtualization based on operating system layer may be realized. As no support of hardware abstract layer is needed, it can meet the demand of failure tolerance and intrusion tolerance system and is characterized by small occupation of system resource, high flexibility and short startup delay.
Owner:CHENGDU HUAWEI TECH
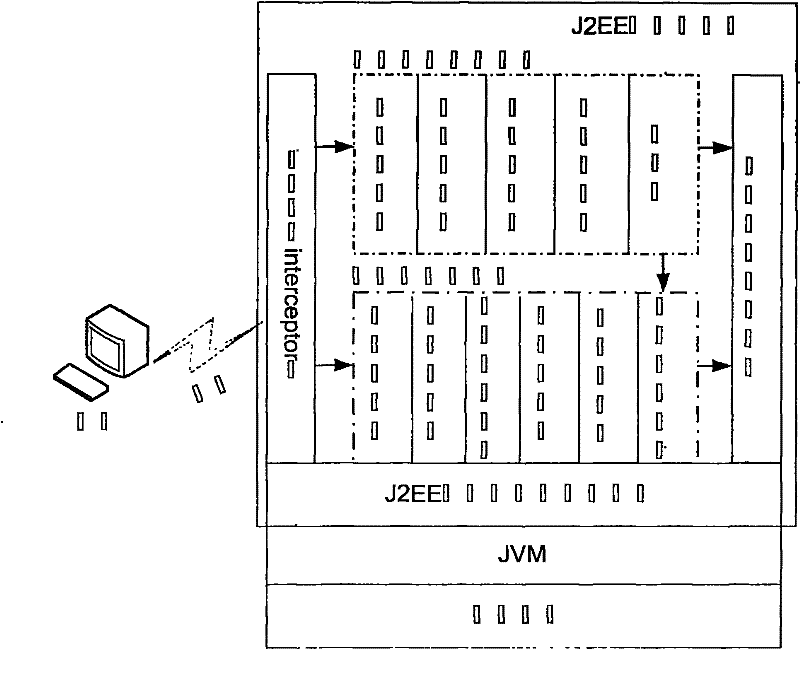
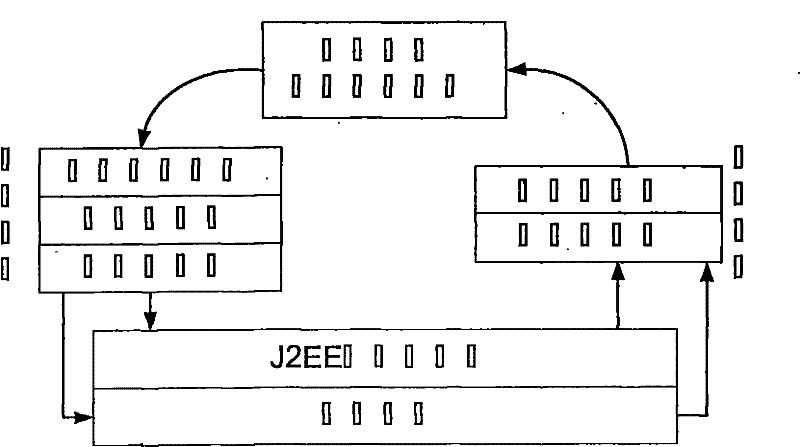
Self-curing J2EE application server for intrusion tolerance and self-curing method thereof
InactiveCN101741619AImprove reliabilityImprove securityData switching networksGroup communication systemsSurvivability
The invention discloses a self-curing J2EE application server for intrusion tolerance and a self-curing method thereof. The application server comprises an intrusion tolerance functional unit, a self-curing functional unit, a secure group communication system and a base platform for the J2EE application server, wherein the self-curing functional unit is used for receiving output results of the intrusion tolerance functional unit and the secure group communication system to carry out self-curing treatment, provides self-curing function support for the base platform for the J2EE application server and comprises a detection component, a management component and an execution component; the detection component detects intrusion and failure and submits results to the management component; the management component analyzes the detection results and gives and sends a curing scheme to the execution component; and the execution component cures the application server according to the curing scheme. On the basis of the intrusion tolerance method, the self-curing method is additionally provided with reactive recovery and periodic recovery, further improves the reliability and the survivability of the J2EE application server and can be applied to the field of network security.
Owner:THE PLA INFORMATION ENG UNIV
Method for implementing IP credible route based on fault-tolerance and invade-tolerance
InactiveCN101355495AFast convergenceAvoid harmError prevention/detection by using return channelData switching networksFault toleranceRouting table
The invention discloses a method for realizing an IP credible route based on fault tolerance and intrusion tolerance, comprising the following steps: (1) when a data packet is transmitted to a node, the node is taken as a transmitting node which selects a receiving node to deliver the data packet, and then the receiving node carries out detection through trust detection and a trust extension route table; if the detection fails, the data packet delivery fails and step (2) is carried out; if the detection succeeds, the receiving node receives the data packet and a route is established successfully; and (2) routing recovery for the data packet which can not be delivered successfully is carried out. The realization process of the IP route is safe and credible; when a network encounters vicious attacks or breaks down, communication can be recovered quickly on the premise of minimum resource consumption; moreover, the method can eliminate damages to a network route caused by decrial attacks, two-faced behavior attacks, intermittent attacks and node failures, and has better fault-tolerant and intrusion-tolerant capability.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
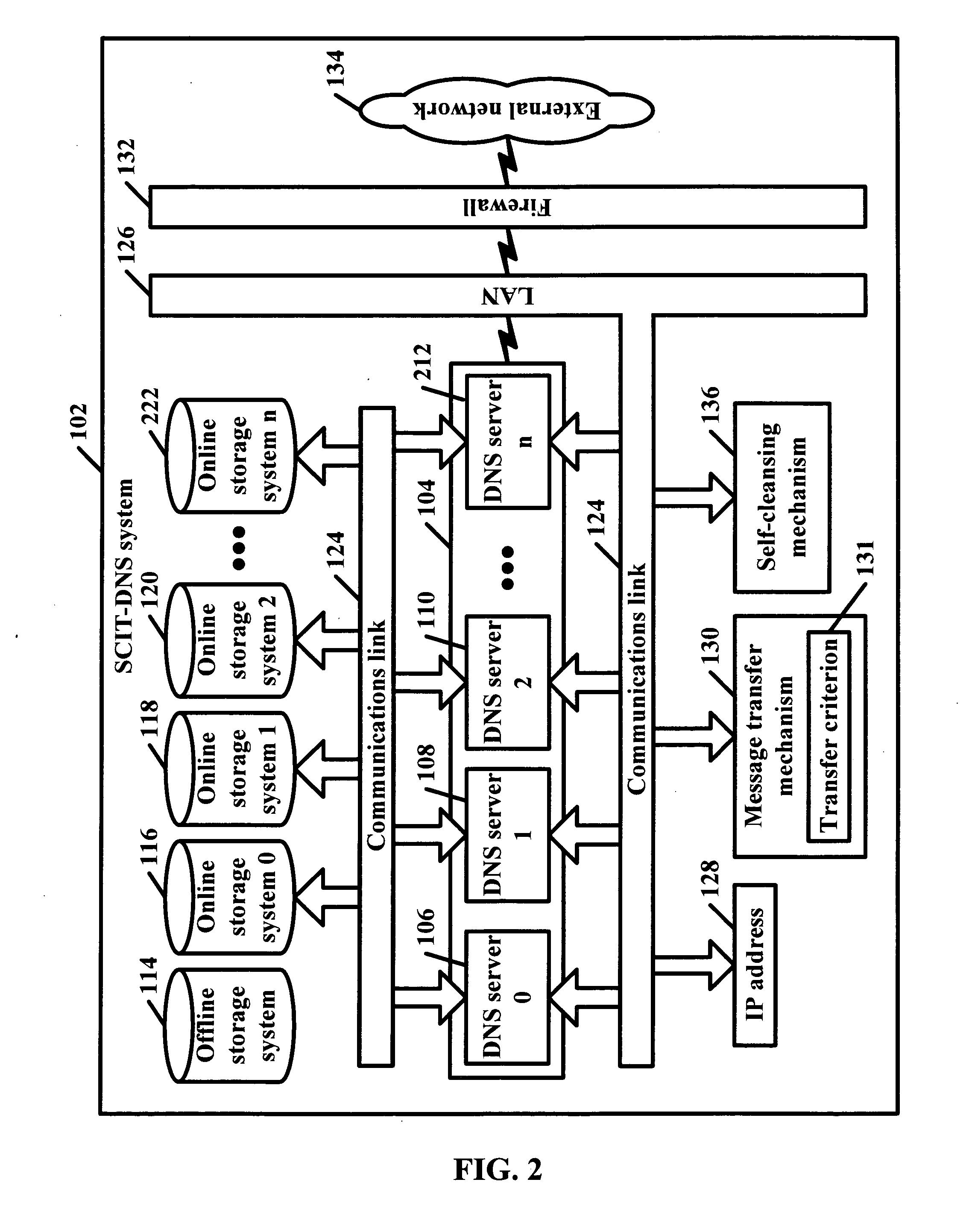
SCIT-DNS: critical infrastructure protection through secure DNS server dynamic updates
ActiveUS7680955B2Eliminate tracesMemory loss protectionError detection/correctionDomain nameTelecommunications link
Disclosed is a self-cleansing intrusion tolerance-domain name systems system comprising at least three DNS servers, at least four storage systems accessible by the DNS servers, a communications link, a message transfer mechanism, and a self-cleansing mechanism. The storage systems include at least three online storage systems and at least one offline storage system. The communications link can connect the DNS servers with the storage systems, as well as connect the DNS servers with a local area network, which can connect the DNS servers with an external network. The message transfer mechanism can rotate the DNS servers into a plurality of roles, including a primary role, a secondary role, a designated role, and a self-cleansing role. The self-cleansing mechanism can be used to perform the self-cleansing role.
Owner:GEORGE MASON INTPROP INC
IP network two-stage fault-tolerance intrusion-tolerance routing mechanism based on faith
InactiveCN101296181AUniversally applicableHave diversityError prevention/detection by using return channelData switching networksFault toleranceIntrusion tolerance
The invention discloses a two-stage fault tolerant and intrusion tolerant routing mechanism for an IP network based on trust. The mechanism is divided into two stages: the first stage is routing discovery, namely, a plurality of credible paths are discovered; the second stage is optimal path selection, namely, the optimal path for routing is selected from the discovered paths. In the first stage, the mechanism utilizes a trust relationship appraisal method of blending multiplication and addition and effectively improves the fault tolerant and intrusion tolerant performance of an IP network router. In the second stage, users always use the optimal router for communication by a path grading strategy, thus effectively avoiding various attacks to the paths. In addition, the invention also describes a definition, measurement, updating and an obtaining method of a trust value with fault tolerant and intrusion tolerant performance in detail.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
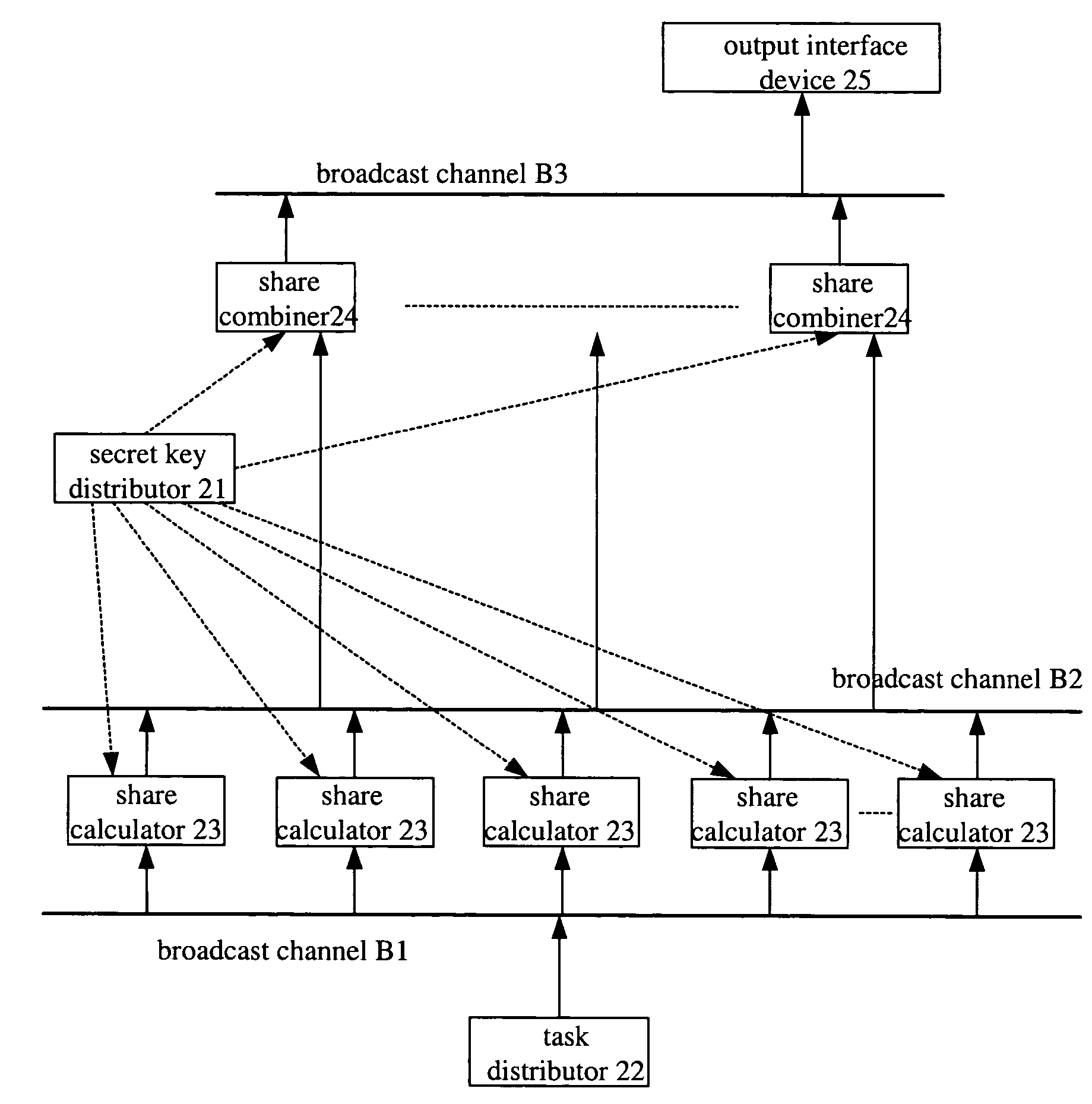
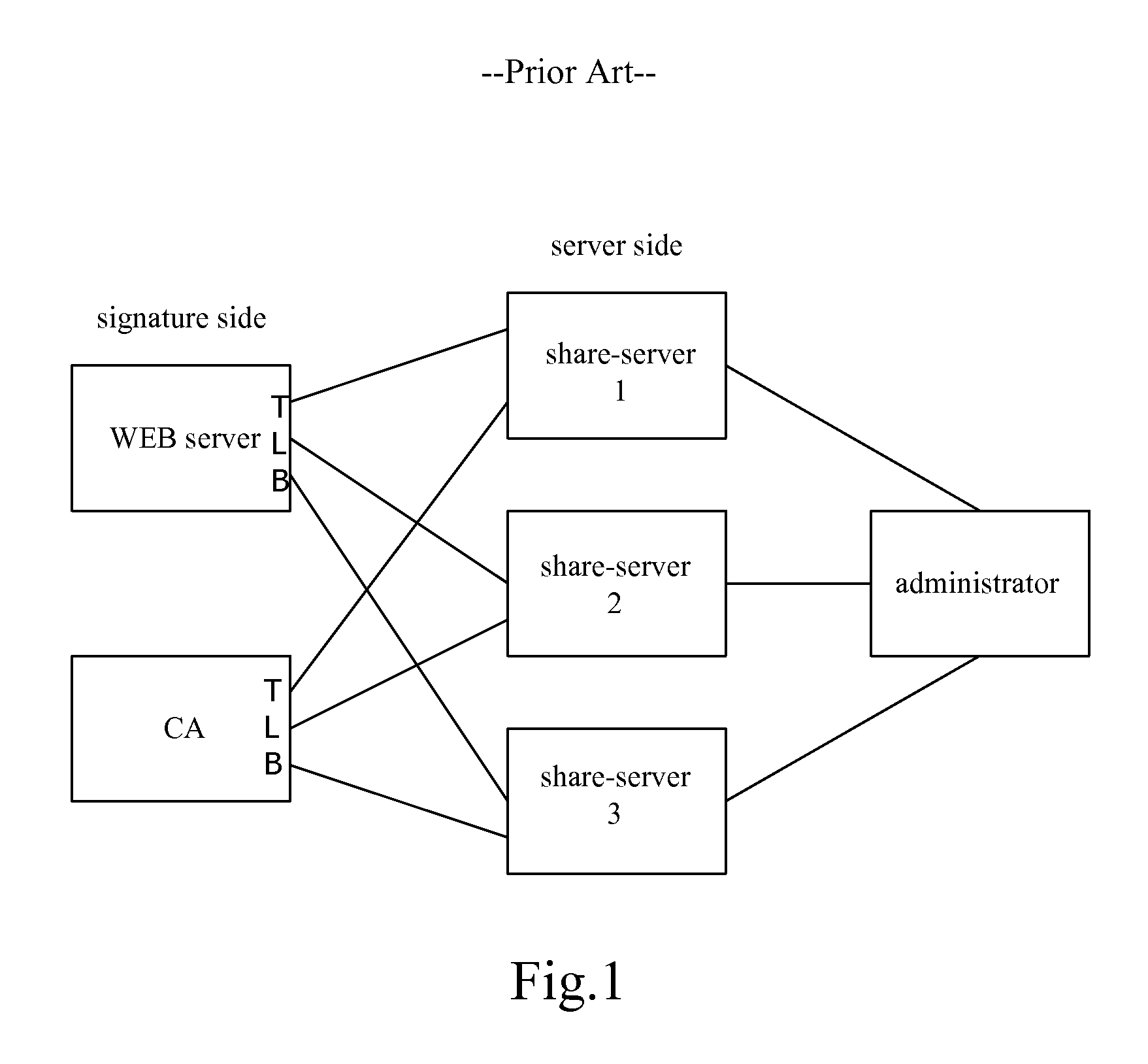
Tolerant digital certificate distribute system and distribute method
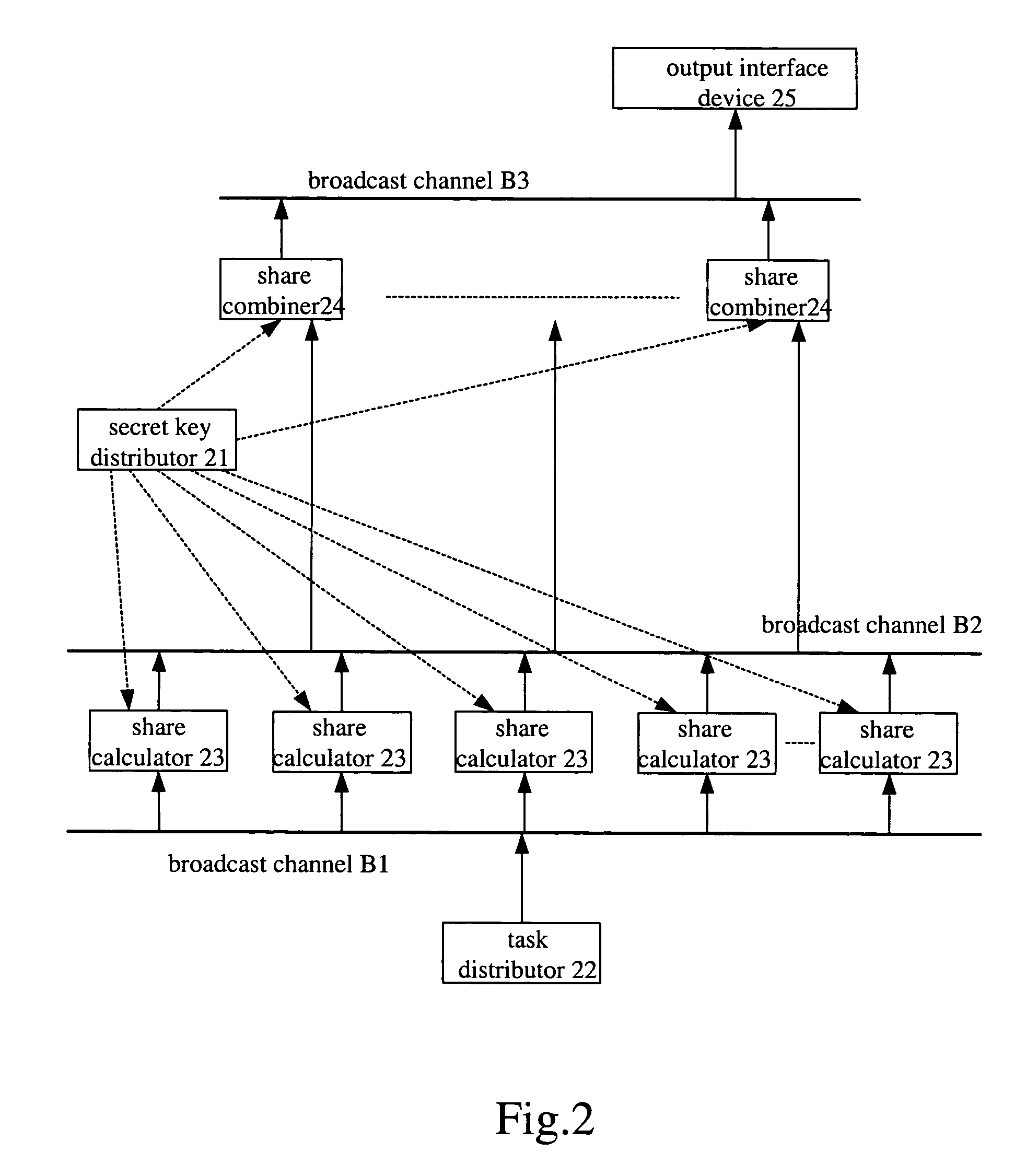
InactiveUS7386131B2Solve the real problemSatisfies requirementKey distribution for secure communicationUser identity/authority verificationSecret shareIntrusion tolerance
A digital certificate issuing system with intrusion tolerance ability and the issuing method thereof are disclosed. The system comprises an offline secret key distributor, at least one online task distributor, k online secret share calculators and m online secret share combiners. And the method includes: splitting a private key into multiple first sub-secret-keys and multiple second sub-secret-keys, wherein the multiple first sub-secret-keys are divided into k groups, and the private key is constructed by one second sub-secret-key and t first sub-secret-keys, the second sub-secret-key corresponds to the t first sub-secret-keys according to an equation combination representation including t items of j and i, j is sequence number of the group which has the first sub-secret-key, and i is number of the first sub-secret-key in the jth group, each of j in one equation combination representation is different, j, i, k, and t are positive integers, and t is less than k; calculating t first calculation results according to a certificate to be signed and the t first sub-secret-keys in the multiple first sub-secret-keys upon receiving the certificate to be signed; obtaining the second sub-secret-key corresponding to the t first sub-secret-keys according to the equation combination representation; calculating a second calculation result according to the second sub-secret-key obtained and the certificate to be signed; generating a digital signature according to the t first calculation results and the second calculation result; generating a digital certificate according to the digital signature and contents of the certificate to be signed.
Owner:INST OF INFORMATION ENG CAS
WSN (Wireless Sensor Network)-oriented lightweight intrusion detection method on basis of artificial immunization and mobile agent
InactiveCN102448066AImprove securityEffective intrusion detectionNetwork topologiesSecurity arrangementIntrusion toleranceRenewable resource
The invention relates to a WSN (Wireless Sensor Network)-oriented lightweight intrusion detection method on the basis of the artificial immunization and a mobile agent, which comprises the following steps of: 1, establishing a lightweight intrusion detection model which is combined with the mobile agent, sharing information by cooperation of various role agents and completing replacement by adopting a mode of evoluting the agent by self-learning; 2, adopting an intrusion detection process of the immunity cooperation of T cells and B cells on the basis of the life cycle; and 3, realizing the self-updating capacity of an intrusion tolerance topological network of a WSN by gradually increasing novel nodes serving as renewable resources. The invention provides the WSN-oriented lightweight intrusion detection method on the basis of the artificial immunization and the mobile agent, which can be used for effectively preventing network information of the WSN from being maliciously tampered or preventing effective information from being lost due to intrusion.
Owner:ZHEJIANG UNIV OF TECH
Information asset protection method based on intrusion tolerance
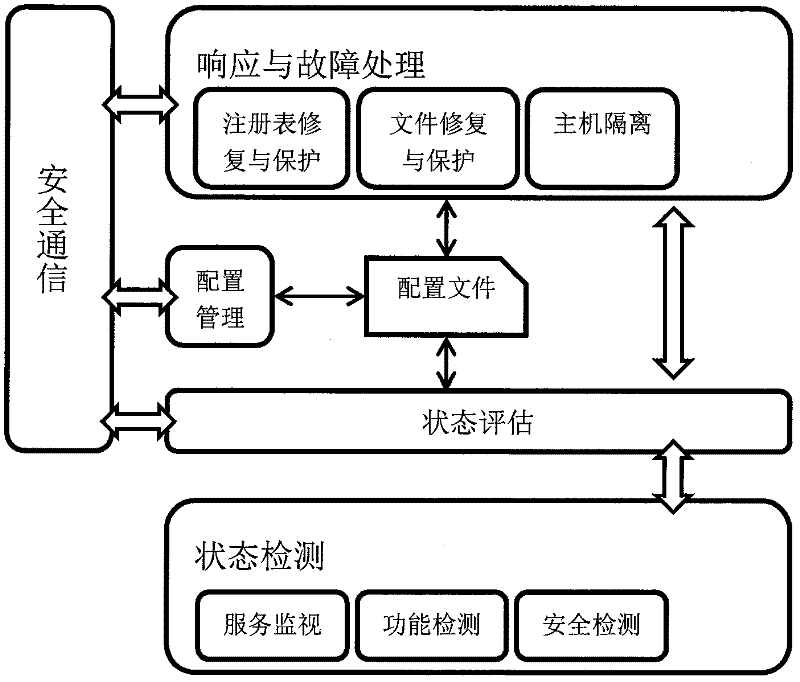
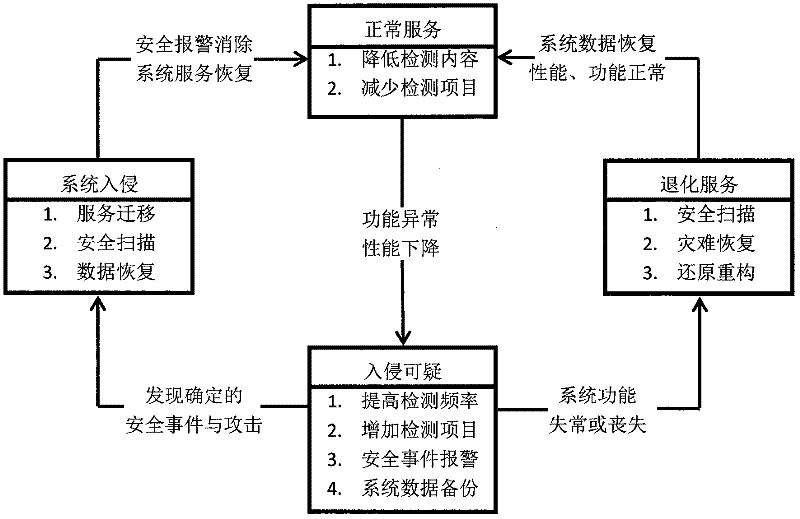
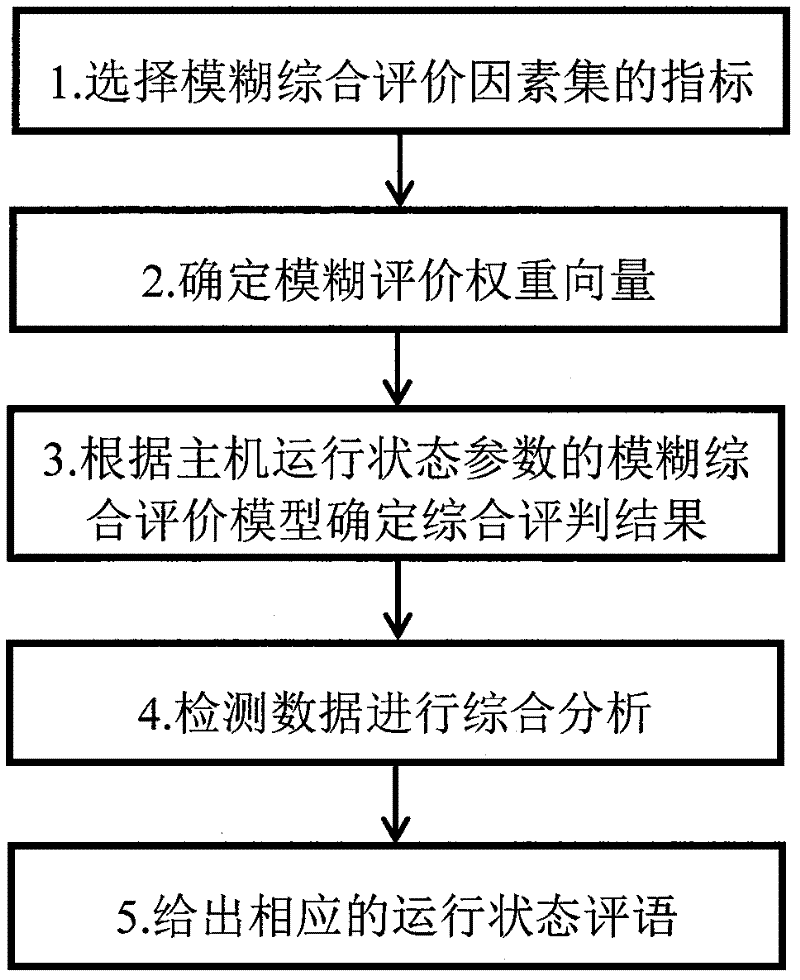
InactiveCN102307184AImprove reliabilityGuaranteed confidentialityTransmissionEvaluation resultSystem recovery
The invention discloses an information asset protection method based on intrusion tolerance. The information asset protection method comprises the following steps: firstly detecting and monitoring core data and service states; by virtue of an evaluation model carried by a state evaluation module and a threshold value which is preset in a configuration file by a user, performing objective evaluation on the system state and uploading the objective evaluation result to a response and fault handling module of a system in the form of events by using the state evaluation module; and then according to the system state evaluation result, starting local fault isolation and system recovery reconstruction mechanisms so as to guarantee the confidentiality of core information assets. The information asset protection method has the beneficial effects that the intrusion tolerance is introduced into an individual host so as to provide basic functions such as auto-diagnosis, fault isolation, recovery reconstruction and safety communication for each system in a resource constraint environment.
Owner:北京峰盛博远科技股份有限公司
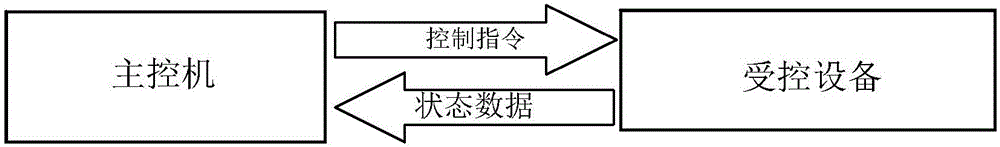
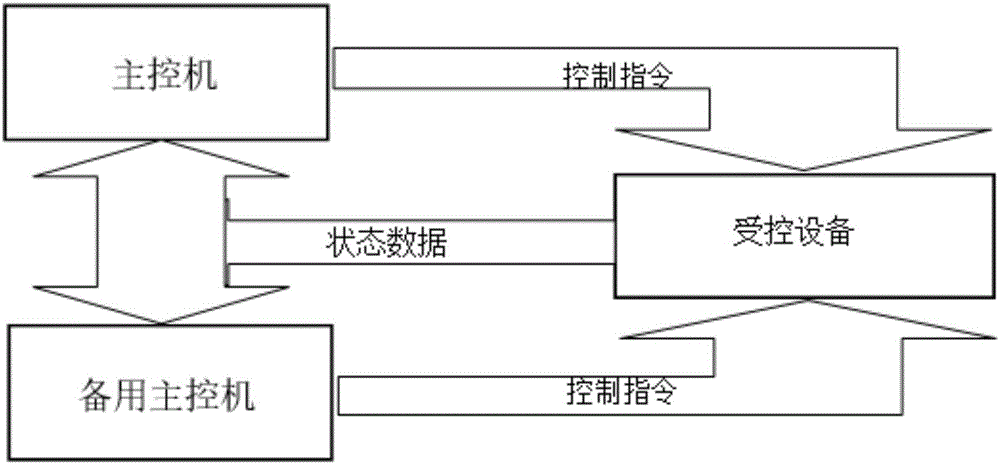
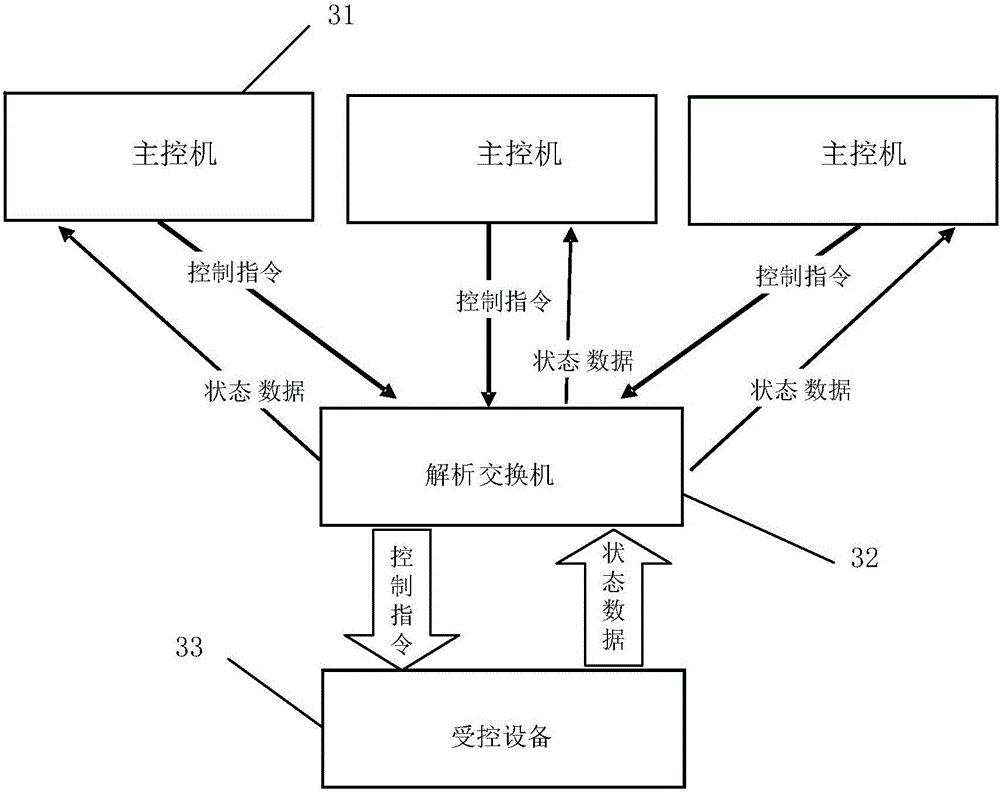
Industrial control system with intrusion tolerance and security protection method
The invention provides an industrial control system with intrusion tolerance and a security protection method. The method comprises N main control computers, a parsing switch and at least one controlled device. The main control computers are used for sending control instructions to the parsing switch; the parsing switch is used for sending the control instructions to the controlled device after receiving at least [(N-1) / 2] identical control instructions; and the controlled device is used for sending status data to the main control computers via the parsing switch, wherein N is an integer greater than or equal to 3, and [(N-1) / 2] is the integer part of (N-1) / 2. According to the embodiments of the invention, the parsing switch compares the control instructions received from the multiple main control computers, and only when the parsing switch receives at least [(N-1) / 2] identical control instructions, the parsing switch sends the control instructions to the controlled device. Thus, malicious control instructions cannot be sent to the controlled device even if the main control computers are intruded, and the network security of the industrial control system is improved.
Owner:BEIJING KUANGEN NETWORK TECH
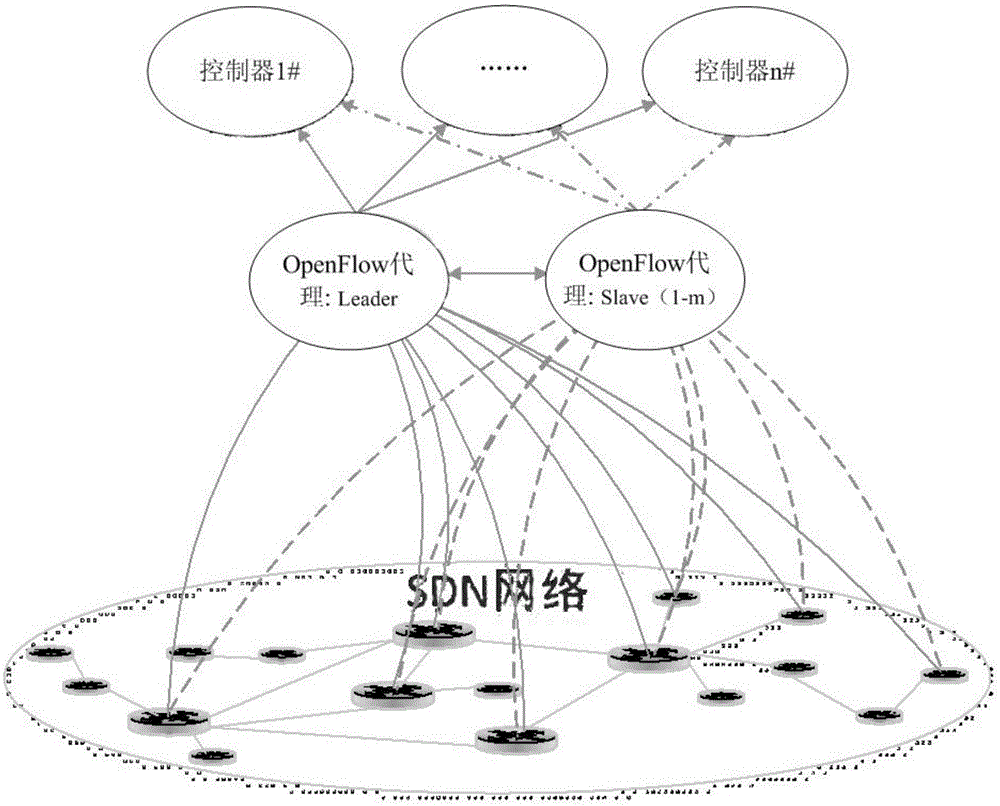
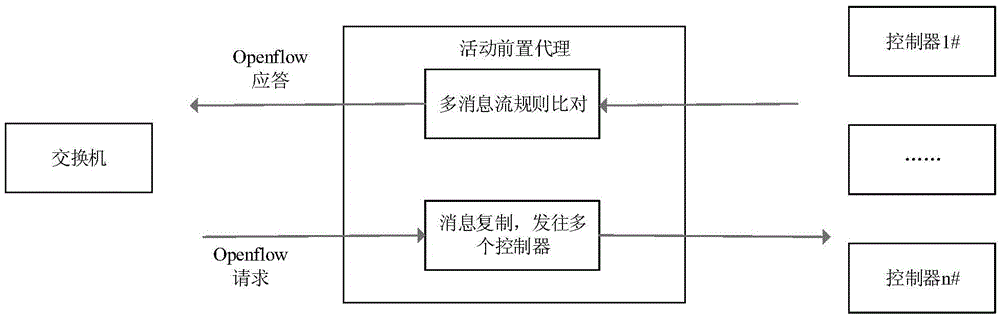
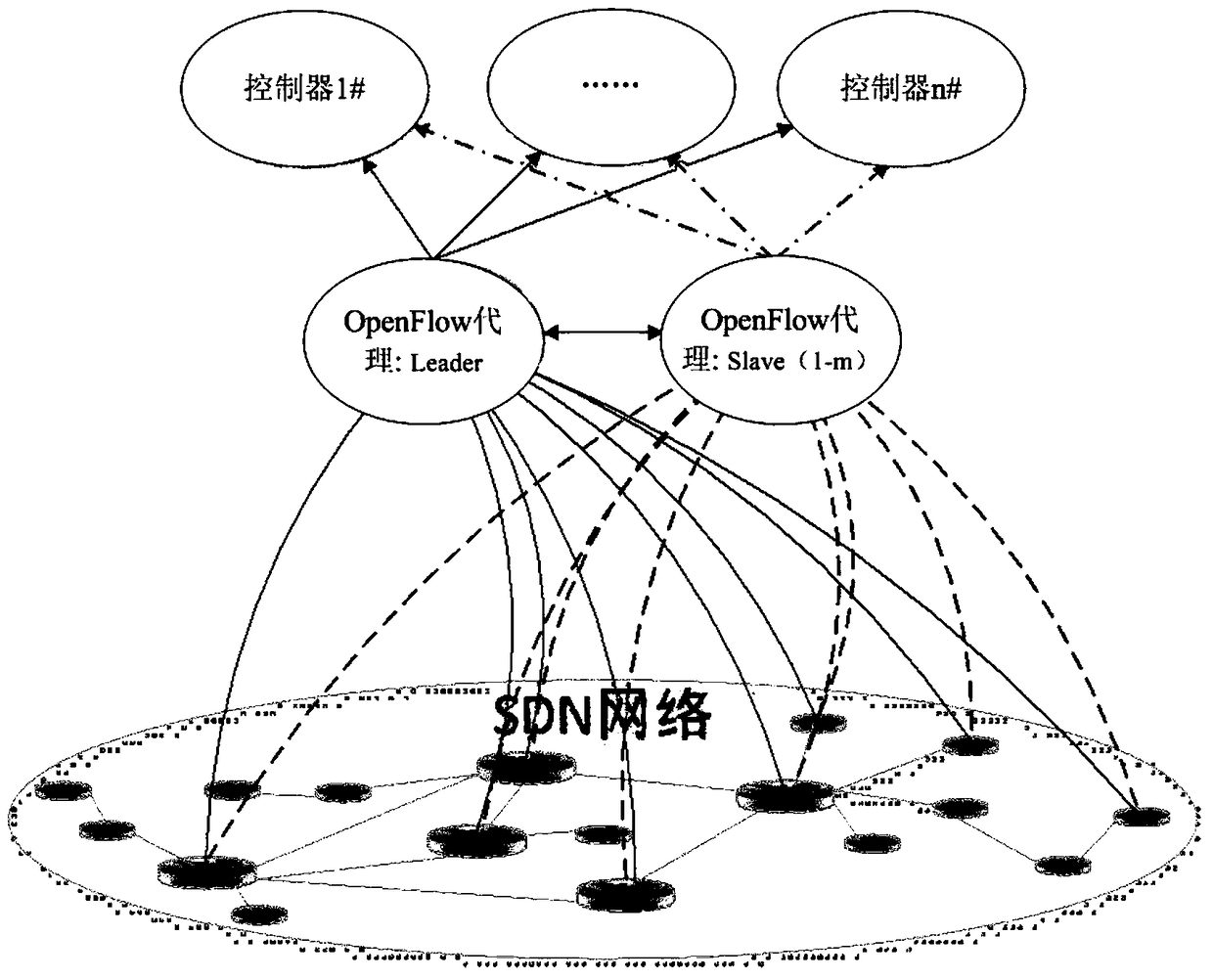
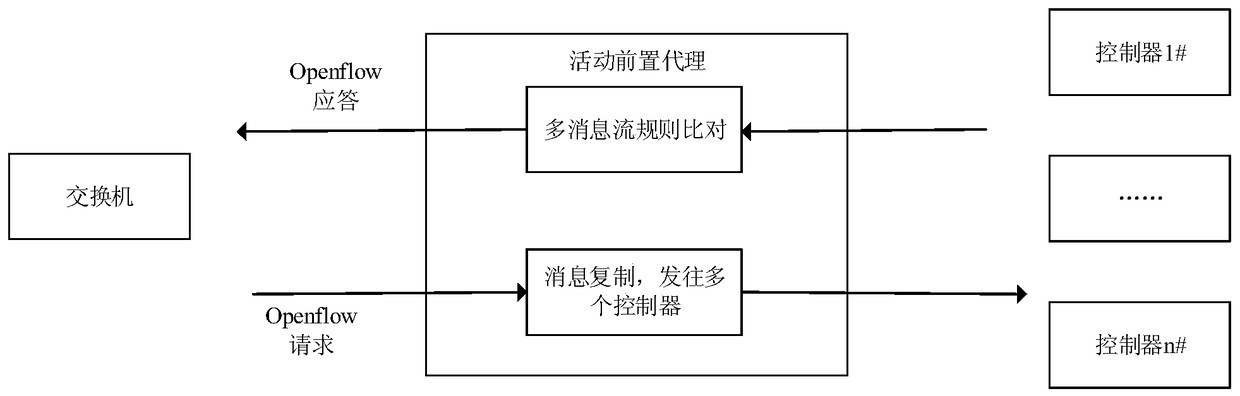
SDN controller end system based on intrusion tolerance and safety communication method
ActiveCN105072101ASDN Control Implementation of ToleranceEasy to controlTransmissionSecure communicationEnd system
The present invention relates to an SDN controller end system based on an intrusion tolerance and a safety communication method. The system comprises an SDN controller group, a switch and at least one pre-proxy between the SDN controller group and the switch. The pre-proxy is responsible for sending the Openflow request message emitted by the switch to multiple SDN controllers in the SDN controller group, extracting the flow rule in the Openflow reply message emitted by each SDN controller, comparing the extracted flow rule, and forwarding a correct Openflow reply message to the switch if a comparison result satisfies a preset intrusion tolerance policy. According to the SDN controller end system and the safety communication method, the availability and reliability of the SDN controllers can be improved, and a security guarantee is provided for an SDN network.
Owner:INST OF INFORMATION ENG CAS
Wireless sensor network intrusion tolerance method and system based on tree topology
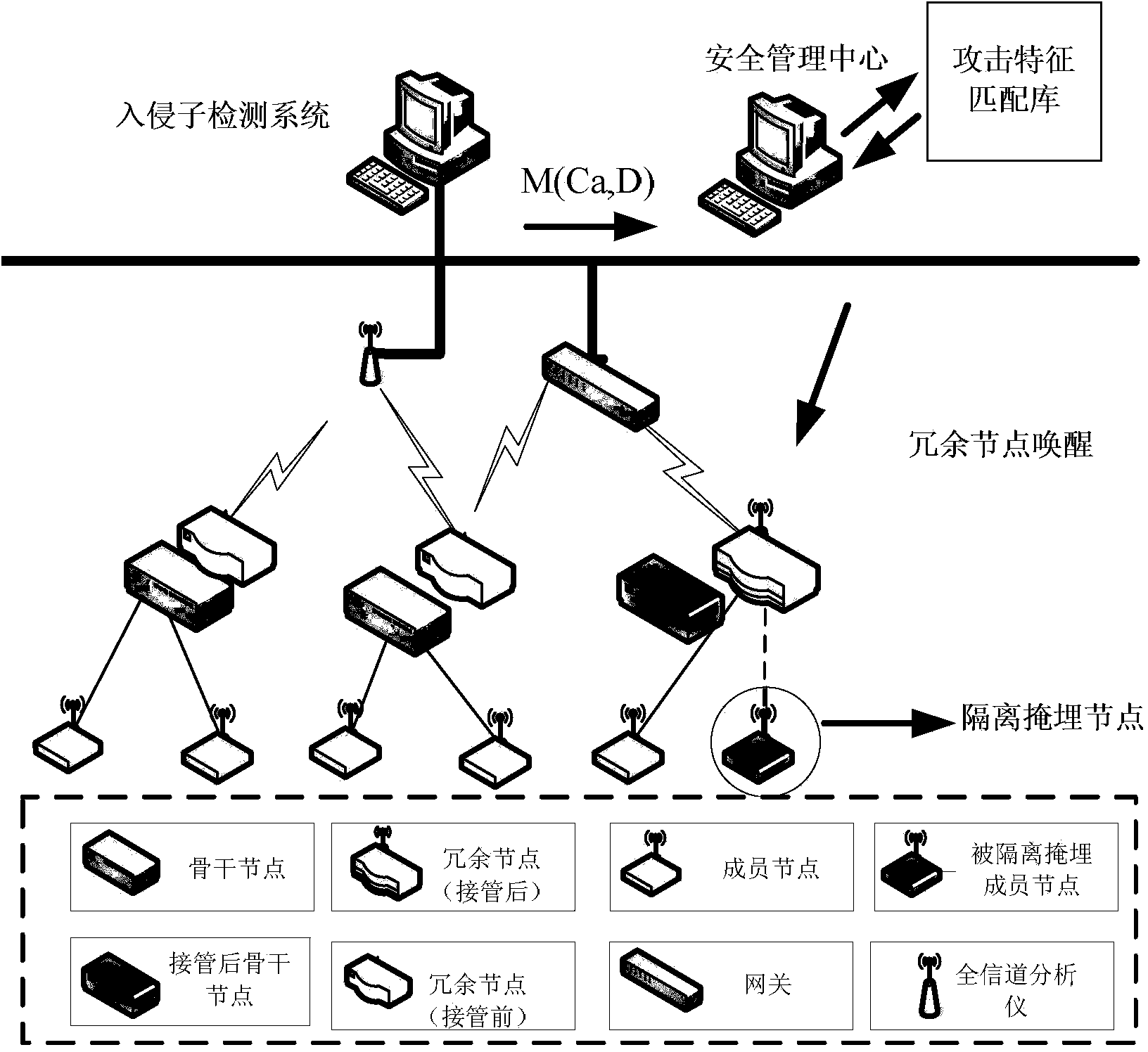
ActiveCN103686737AEffective protectionProlong lifeNetwork topologiesSecurity arrangementPower analysisTraffic capacity
The invention provides a wireless sensor network tolerance system based on tree topology. The system comprises an intrusion detecting subsystem, a safety management center and an attacking feature matching bank. The intrusion detecting subsystem can judge a network abnormal situation through node flow and energy analysis, and by arranging threshold value warning, results are uploaded to the safety management center at the same time. For the wireless sensor network abnormal situation, attack matching can be carried out through the attacking feature matching bank, meanwhile, corresponding processing is carried out according to attack types, and network lifetime is prolonged. For attacked backbone nodes in a network, a redundant node rousing strategy is used, redundant nodes are roused to take over current attacked nodes, and network normal operation is kept. For attacked member nodes in the network, an isolation burying strategy is used, node ID is recorded, and using by attacking nodes is avoided.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
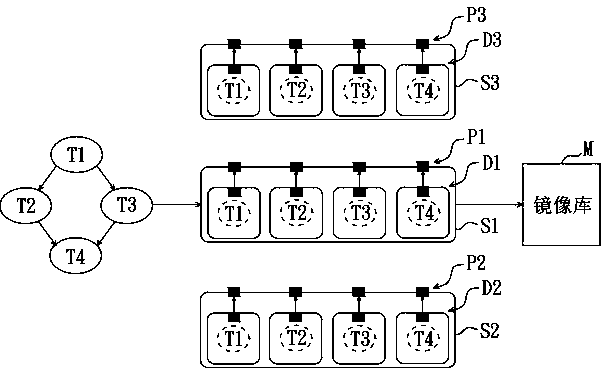
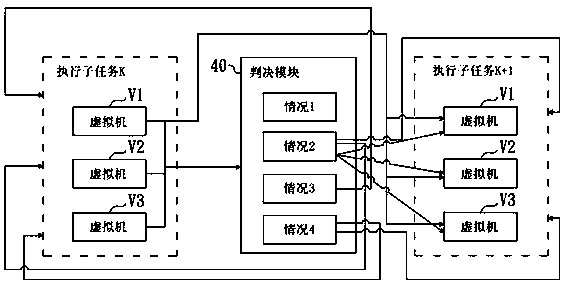
Intrusion-tolerant cloud workflow implementation method and system
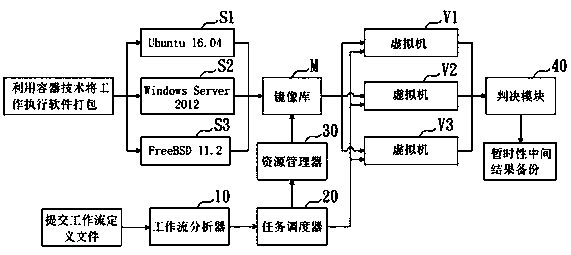
InactiveCN110110520AGuaranteed pureImprove intrusion tolerancePlatform integrity maintainanceSoftware simulation/interpretation/emulationOperational systemIntrusion tolerance
According to the cloud workflow implementation method with intrusion tolerance, the executive programs corresponding to the tasks in the workflow are deployed in the containers respectively, and thenthe containers are transplanted to the virtual machines with the different operating systems, so that the cloud system intrusion tolerance capability can be effectively improved. Furthermore, the subtask results executed by the plurality of virtual machines are judged; calculating the confidence coefficient of the sub-task result generated within the preset time; therefore, the reliability and credibility of the execution of the current subtask are determined, whether the selection result is submitted to the next subtask or the execution subtask of the virtual machine is reset is determined, the reliability and credibility of the output result are ensured through the mutual judgment and verification of the generation results of the plurality of virtual machines, and the invasion toleranceof the cloud system can be truly improved. In addition, the invention provides a system applying the cloud workflow implementation method with intrusion tolerance, and the purpose and the effect of the implementation method are achieved.
Owner:ZHUHAI GAOLING INFORMATION TECH COLTD +1
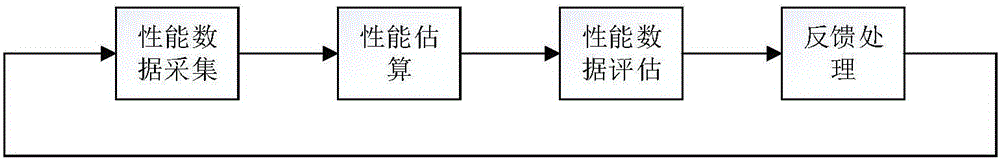
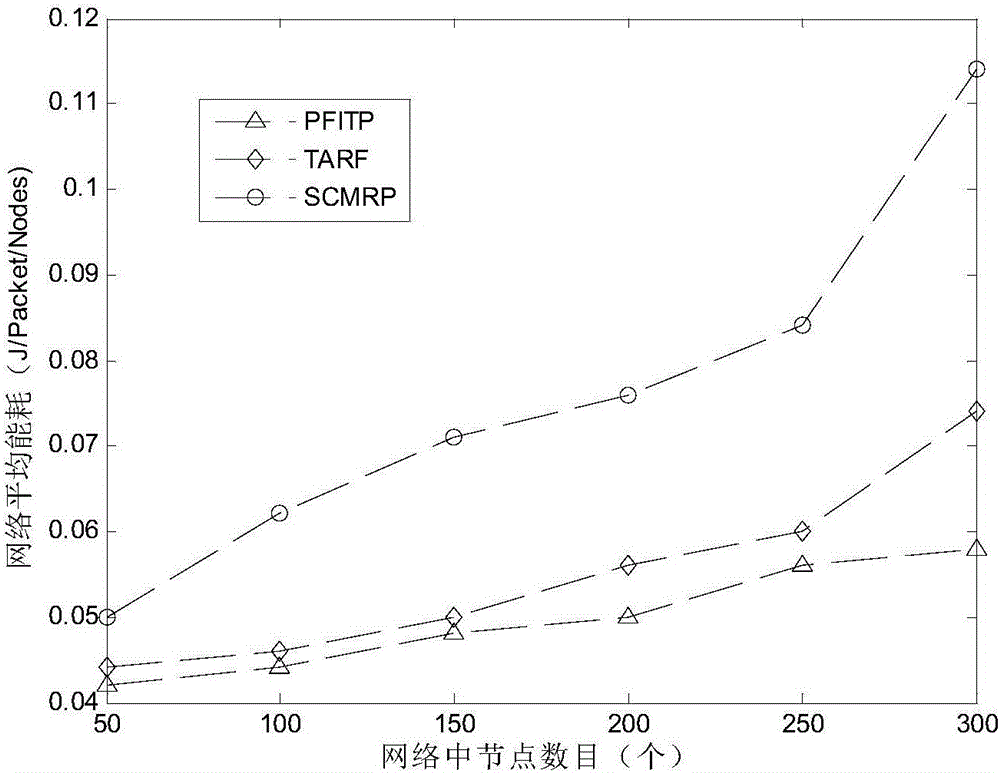
Performance feedback intrusion tolerance protocol
ActiveCN106412888AImprove communication efficiencyExclude influencePower managementTransmissionMobile wireless sensor networkWireless mesh network
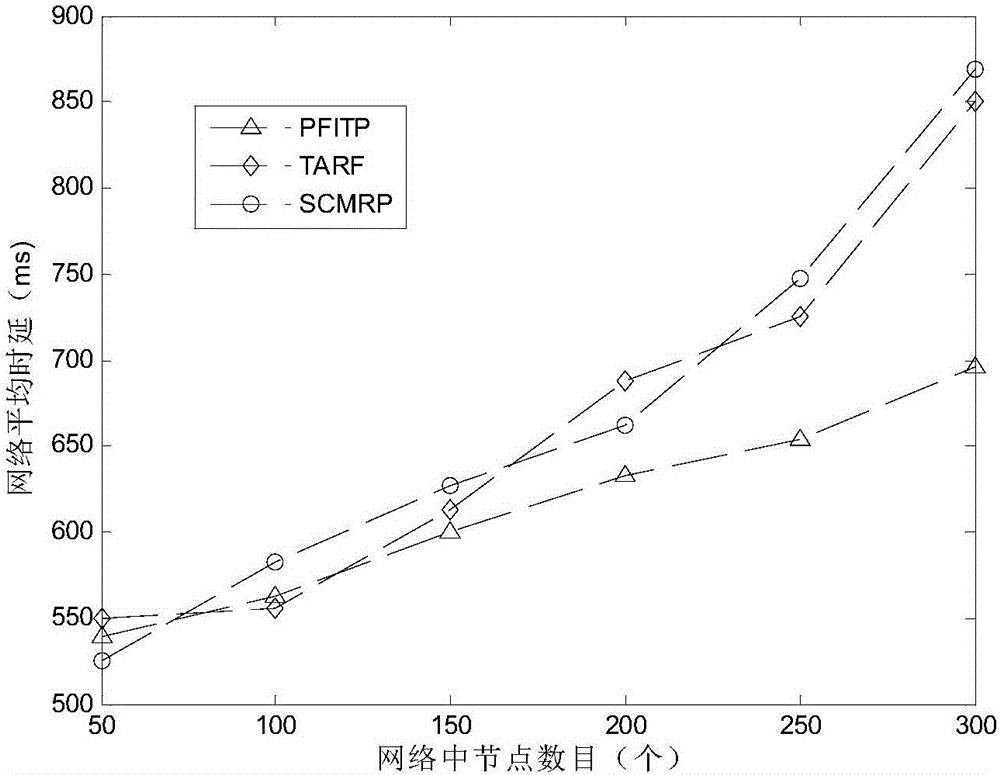
The present invention discloses a performance feedback intrusion tolerance protocol (PFITP). The protocol is suitable for a wireless sensor network, and mainly comprises a performance feedback mechanism, a network performance estimation, abnormal node marking, cluster-head reselection, and node authentication. The protocol can estimate the network QoS performance, mark the abnormal nodes, select reliable nodes as the cluster head, ensure that the wireless sensor network can resist to common hostile attack and provide a good network performance.
Owner:SOUTHEAST UNIV
Multi-path safety topology control method with intrusion tolerance capacity
ActiveCN108882328AExtend the life cycleGuaranteed normal transmissionData switching networksWireless communicationIntrusion toleranceDirect communication
The invention relates to a multi-path safety topology control method with intrusion tolerance capacity, which comprises the steps of: cluster head selection, i.e., determining an optimal cluster number according to an initialization parameter, calculating cluster head election probabilities and cluster head competition radii, and determining cluster head nodes; clustering, i.e., selecting to add non-cluster-head nodes into an optimal cluster according to residual energy and node distance information of a cluster head which sends out an invitation; routing establishment, i.e., enabling a sourcenode to establish a single hop of single path by adopting direct communication or establish multiple hops of paths by adopting an indirect communication mode according to different transmission distances with target nodes, and storing routing information; and data transmission, i.e., enabling the source node to carry out patch transmission on data to the target nodes according to the establishedpath by combining (k, n) threshold secret sharing scheme. According to the invention, in a case that a malicious node exists in a network and a data transmission path is damaged, normal transmission of the data can be ensured so as to achieve effects of balancing energy consumption and prolonging the life cycle of the network.
Owner:ZHEJIANG SCI-TECH UNIV
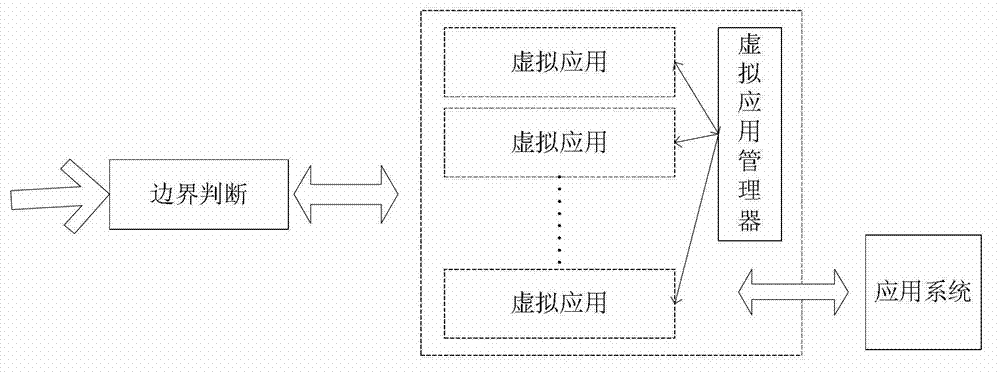
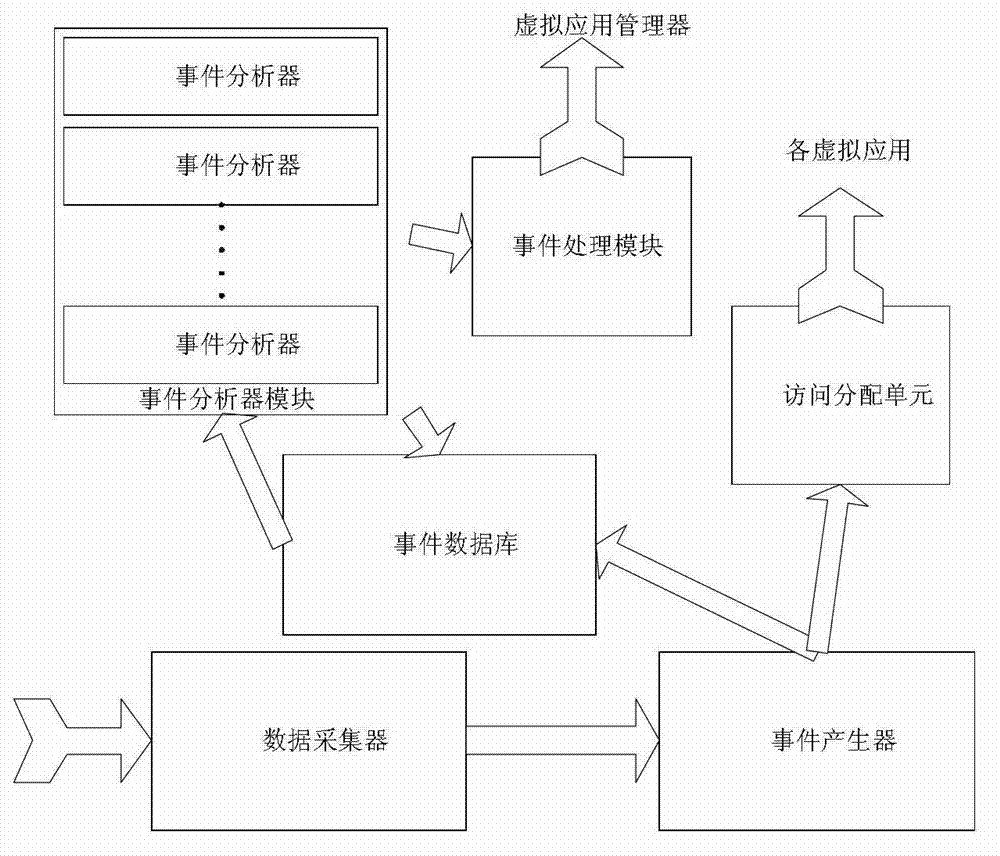
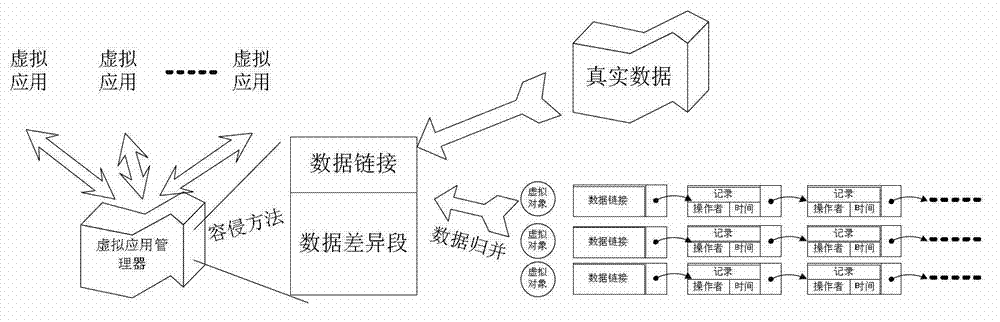
Application level intrusion tolerance system and method
ActiveCN103118021AGuaranteed to be isolated from each otherRealize the mergerTransmissionIntrusion toleranceComputer science
The invention provides application level intrusion tolerance system and method. The application level intrusion tolerance system comprises a boundary judging unit, an application unit and an application system module which are sequentially connected. The application level intrusion tolerance method includes steps of (1) access distribution and analysis; (2) application system virtualization; and (3) convergence and backspacing of application behaviors. By virtualizing the application into multiple virtual applications, and by means of the intrusion tolerance method, the problem about how to guarantee availability of application system software when network intrusion occurs is solved.
Owner:CHINA ELECTRIC POWER RES INST +2
Network-attack-resilient intrusion-tolerant scada architecture
The present invention generally relates to network-attack-resilient intrusion-tolerant Supervisory Control and Data Acquisition (SCADA) systems. Some implementations utilize redundant, proactively-recovery-configured servers at multiple centers communally executing a replication protocol. Some implementations, in addition to control centers, include data centers, which participate in the replication protocol, except that they may not be capable of controlling remote units such as Remote Terminal Units (RTUs).
Owner:THE JOHN HOPKINS UNIV SCHOOL OF MEDICINE
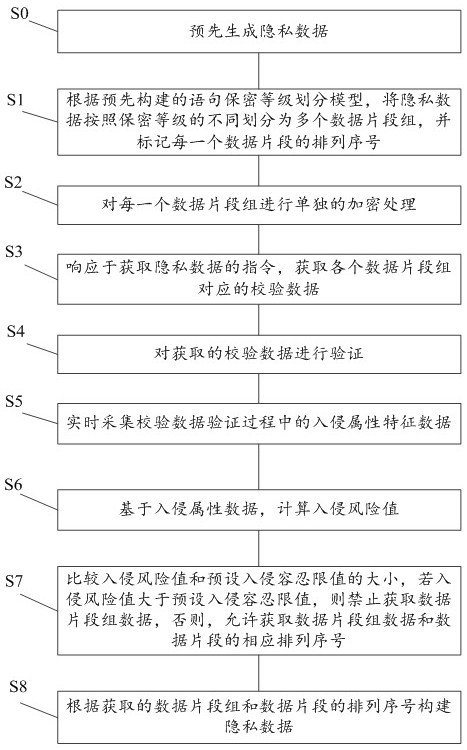
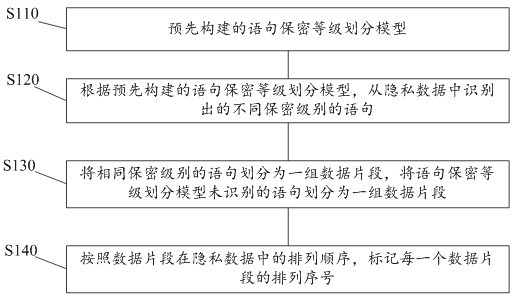
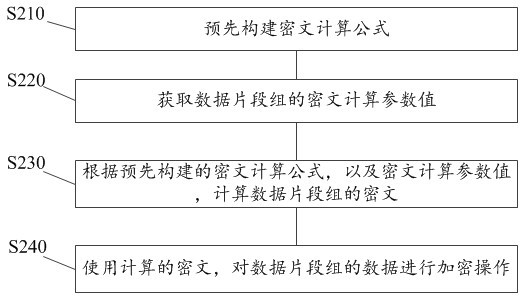
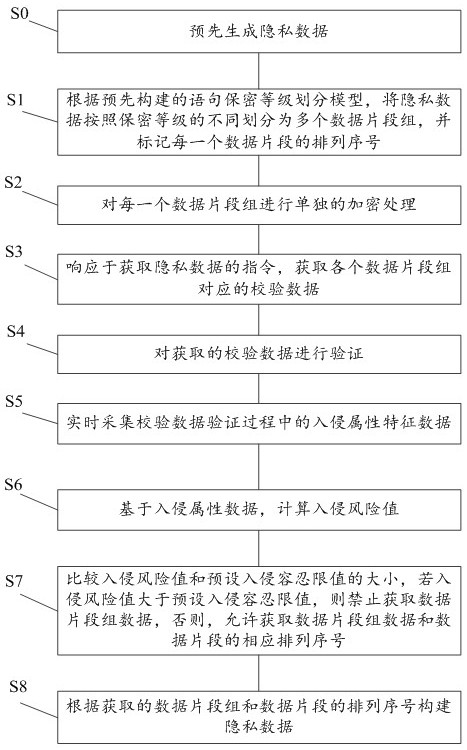
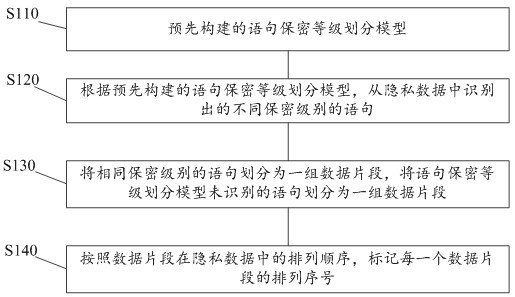
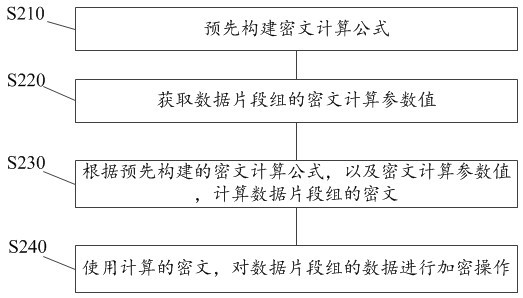
Threshold-based homomorphic encryption privacy protection device and method
The invention provides a threshold-based homomorphic encryption privacy protection device and method, and the method comprises the following steps: dividing privacy data into a plurality of data segment groups according to different secrecy levels according to a pre-constructed statement secrecy level division model; performing independent encryption processing on each data segment group; in response to an instruction for acquiring the private data, acquiring verification data corresponding to each data segment group; verifying the obtained verification data; acquiring intrusion attribute characteristic data in a verification process of the verification data in real time; calculating an intrusion risk value based on the intrusion attribute data; and comparing the intrusion risk value with a preset intrusion tolerance limit value, if the intrusion risk value is greater than the preset intrusion tolerance limit value, forbidding to acquire the data of the data segment group, otherwise, allowing to acquire the data of the data segment group. According to the method, the security of the privacy data is improved, and the privacy data is prevented from being stolen by an intruder.
Owner:BEIJING ZHONGKE JINCAI TECH
A security control method for a networked motion control system with quantization
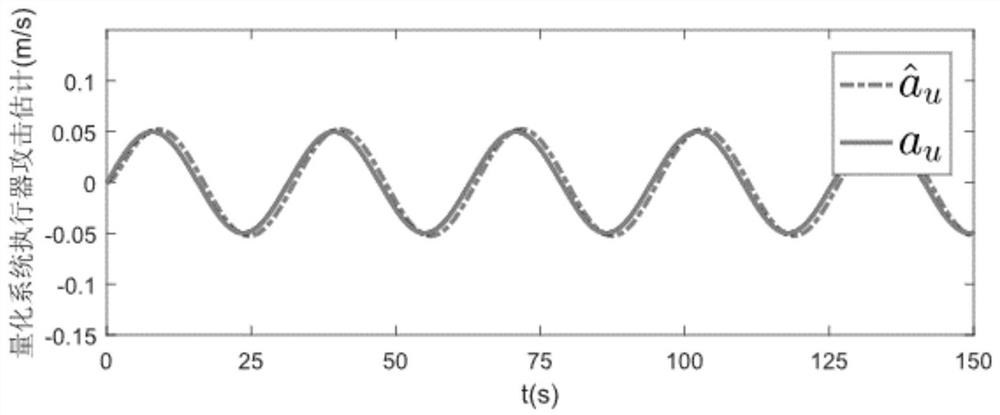
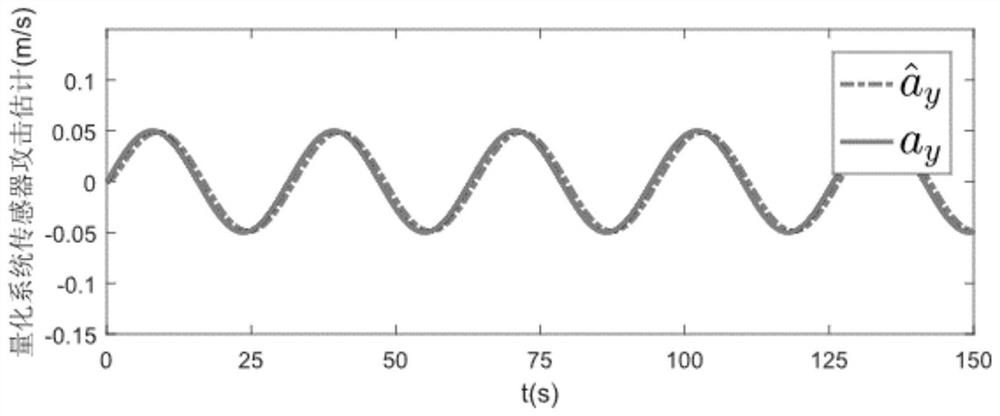
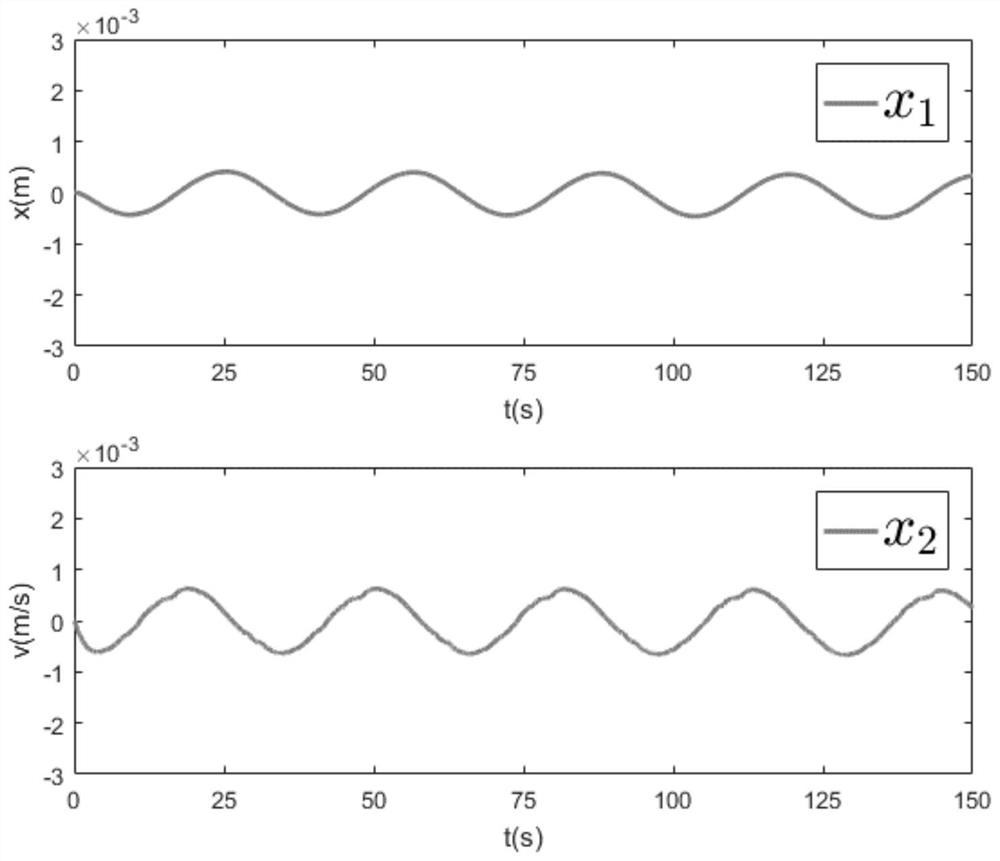
ActiveCN110794811BAvoid additional performance indicatorsProgramme controlElectric testing/monitoringLinear matrixDesign control
A safety control method for a networked motion control system under the influence of quantification, comprising the following steps: modeling the networked control system, establishing a state equation and an output equation; expanding the dimension of the state equation of the networked control system; designing an intermediate Observer; design a linear matrix inequality to solve the estimated gain matrix L and design a controller. The invention can detect the attack of the actuator and the sensor at the same time, suppress the quantitative effect by adjusting specific parameters, and design an intrusion-tolerant controller according to the estimated value, so that the state of the closed-loop system is consistent and finally bounded, and the safe operation of the system is guaranteed.
Owner:ZHEJIANG UNIV OF TECH
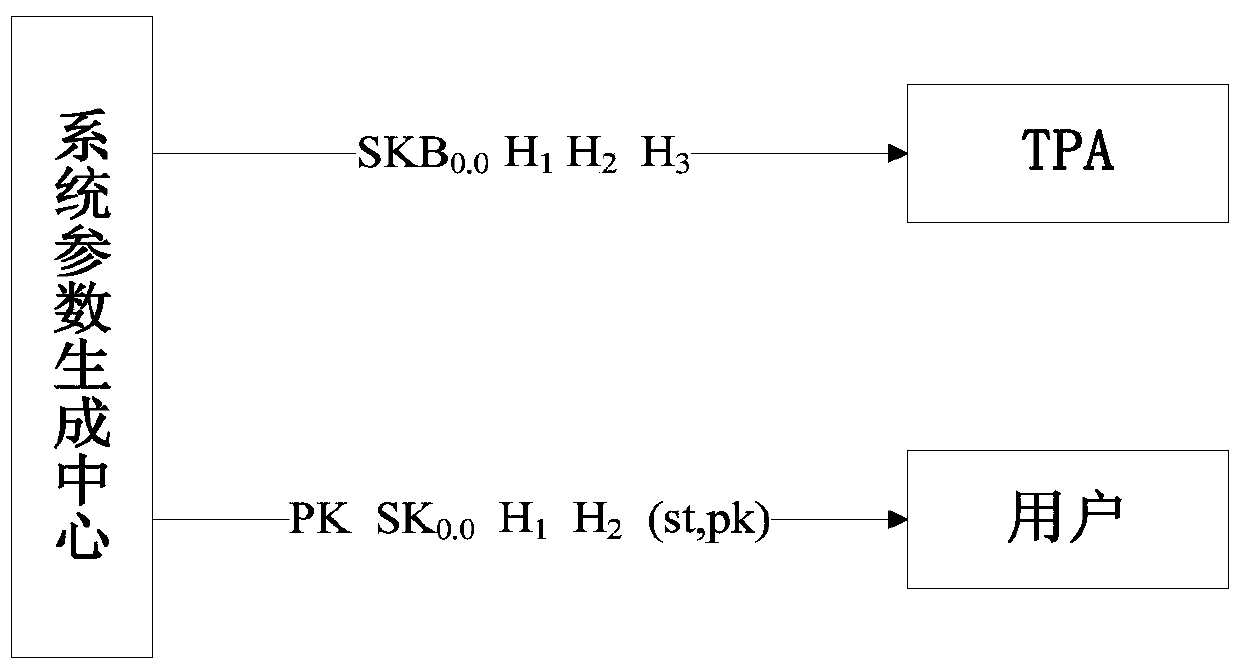
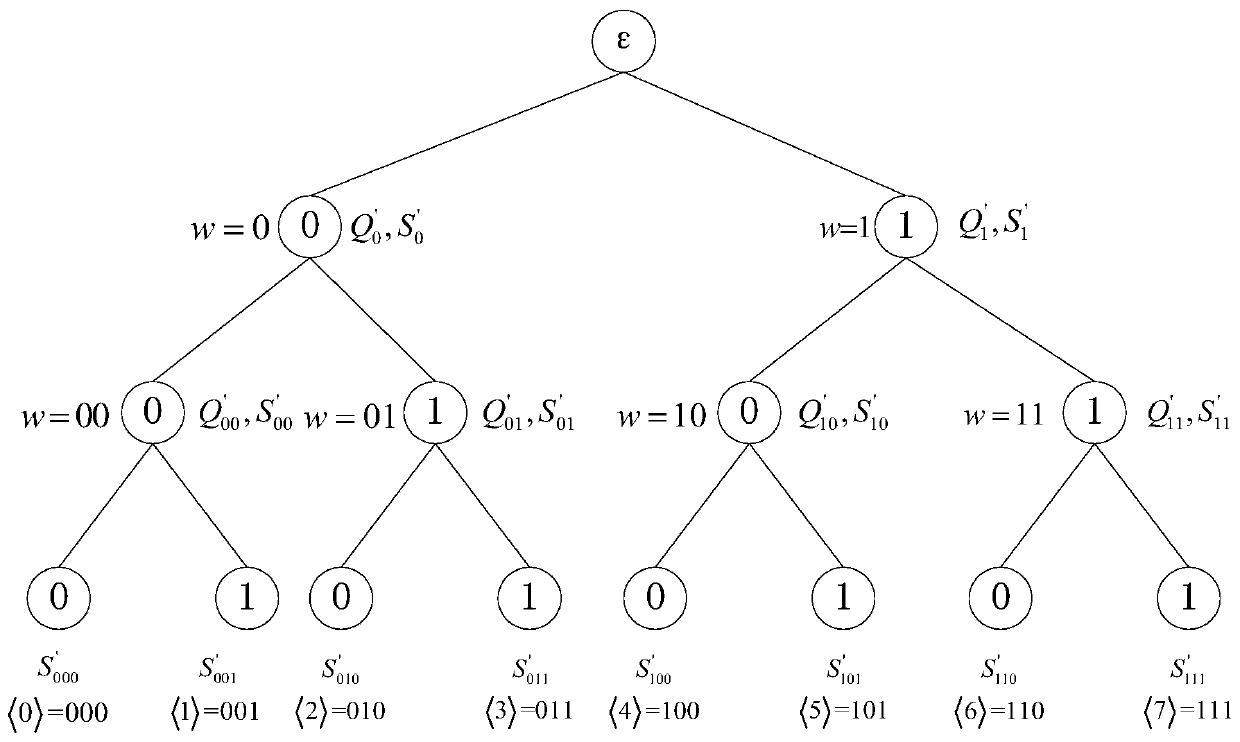
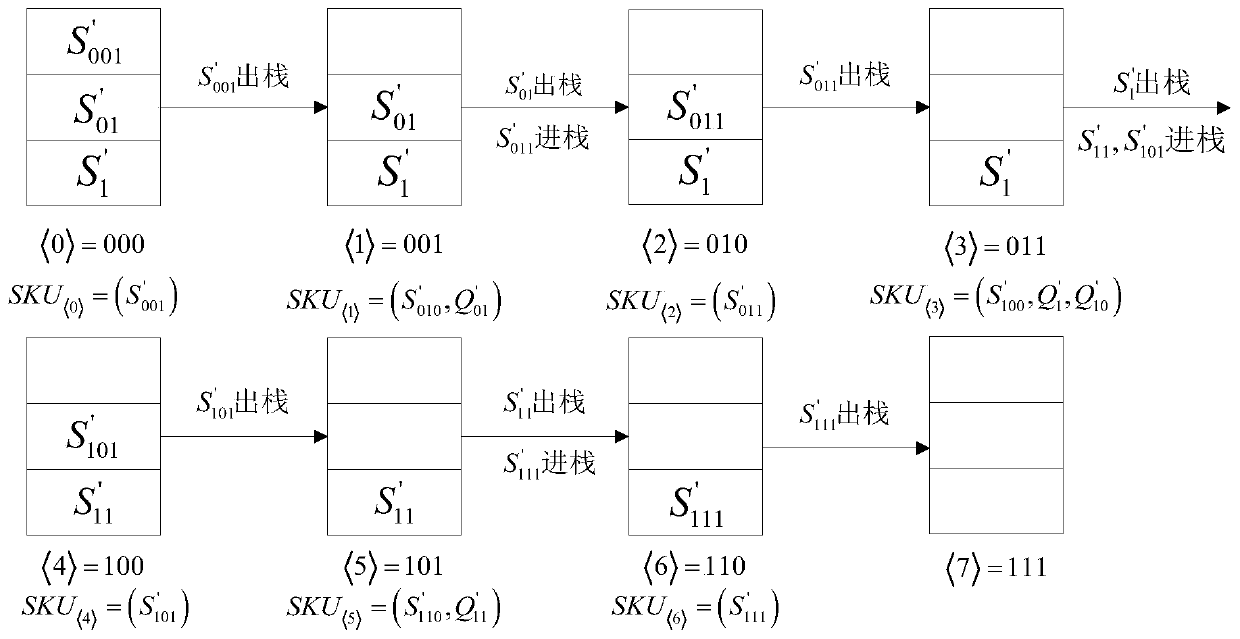
Intrusion-tolerant cloud storage data auditing method
ActiveCN107046465BDoes not affect audit efficiencyImprove audit efficiencyKey distribution for secure communicationUser identity/authority verificationThird partyIntrusion tolerance
The invention discloses an intrusion-tolerant cloud storage data audit method and a data audit system. The method includes: a system parameter generation step in which various system parameters are generated by a system parameter generation center; TPA assists users in periodically updating audit keys Key update step; TPA assists the user to refresh the audit key in each cycle; after the user generates a verification tag for the file, upload the file and the verification tag to the cloud server, and TPA audits the file for verification Whether the file is complete and stored on the cloud server is the data upload and audit steps. In this method, a third-party audit (TPA) is introduced to perform audit operations, and at the same time, it assists users in performing periodic key update and key refresh operations in each time period. Even if the keys on the user and the TPA are leaked multiple times, except for the few cycles where the user's key is leaked, data auditing in any other cycle is still safe.
Owner:ANHUI UNIVERSITY
Virtual method and virtual device based on operating system layer
ActiveCN101551756BSave resourcesLess start-up delayProgram initiation/switchingSoftware simulation/interpretation/emulationVirtualizationFault tolerance
Owner:CHENGDU HUAWEI TECH
Self-curing J2EE application server for intrusion tolerance and self-curing method thereof
InactiveCN101741619BImprove reliabilityImprove securityData switching networksGroup communication systemsApplication server
The invention discloses a self-curing J2EE application server for intrusion tolerance and a self-curing method thereof. The application server comprises an intrusion tolerance functional unit, a self-curing functional unit, a secure group communication system and a base platform for the J2EE application server, wherein the self-curing functional unit is used for receiving output results of the intrusion tolerance functional unit and the secure group communication system to carry out self-curing treatment, provides self-curing function support for the base platform for the J2EE application server and comprises a detection component, a management component and an execution component; the detection component detects intrusion and failure and submits results to the management component; the management component analyzes the detection results and gives and sends a curing scheme to the execution component; and the execution component cures the application server according to the curing scheme. On the basis of the intrusion tolerance method, the self-curing method is additionally provided with reactive recovery and periodic recovery, further improves the reliability and the survivabilityof the J2EE application server and can be applied to the field of network security.
Owner:THE PLA INFORMATION ENG UNIV
A threshold-based homomorphic encryption privacy protection device and method
Owner:BEIJING ZHONGKE JINCAI TECH
SDN controller-side system and secure communication method based on intrusion tolerance
ActiveCN105072101BSDN Control Implementation of ToleranceEasy to controlTransmissionSecure communicationIntrusion tolerance
The present invention relates to an SDN controller end system based on an intrusion tolerance and a safety communication method. The system comprises an SDN controller group, a switch and at least one pre-proxy between the SDN controller group and the switch. The pre-proxy is responsible for sending the Openflow request message emitted by the switch to multiple SDN controllers in the SDN controller group, extracting the flow rule in the Openflow reply message emitted by each SDN controller, comparing the extracted flow rule, and forwarding a correct Openflow reply message to the switch if a comparison result satisfies a preset intrusion tolerance policy. According to the SDN controller end system and the safety communication method, the availability and reliability of the SDN controllers can be improved, and a security guarantee is provided for an SDN network.
Owner:INST OF INFORMATION ENG CHINESE ACAD OF SCI
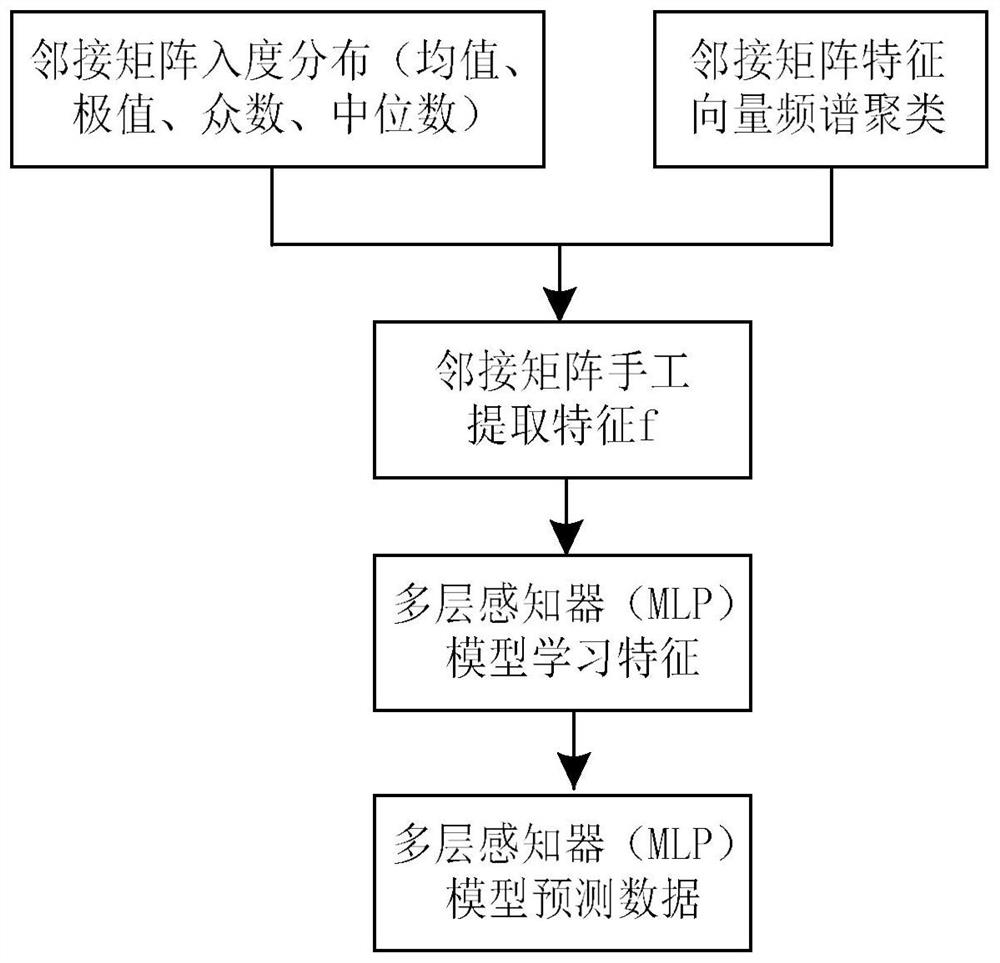
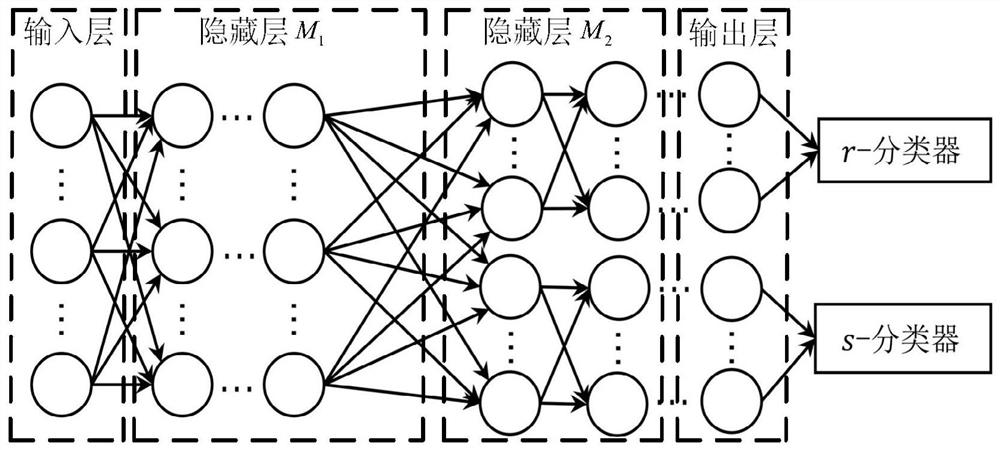
Multi-Agent System Network Intrusion Tolerance Evaluation Method Based on Multilayer Perceptron
Owner:HANGZHOU DIANZI UNIV
Network-attack-resilient intrusion-tolerant SCADA architecture
The present invention generally relates to network-attack-resilient intrusion-tolerant Supervisory Control and Data Acquisition (SCADA) systems. Some implementations utilize redundant, proactively-recovery-configured servers at multiple centers communally executing a replication protocol. Some implementations, in addition to control centers, include data centers, which participate in the replication protocol, except that they may not be capable of controlling remote units such as Remote Terminal Units (RTUs).
Owner:THE JOHN HOPKINS UNIV SCHOOL OF MEDICINE
Data security processing method
PendingCN112347497AAchieving External Level Intrusion ToleranceIntegrity guaranteedDigital data protectionConfidentialityIntrusion tolerance
The invention relates to the technical field of data processing methods, in particular to a data security processing method, which processes data through an encryption authentication module and an internal tolerance module. Data security processing is realized through the encryption authentication module and the internal tolerance module, and an encryption authentication function is realized through the encryption unit, the decryption unit and the authentication unit of the encryption authentication module, so that the integrity, confidentiality and security of data are ensured, and the validity and authenticity of a data source are ensured at the same time; in addition, errors in the data transmission process are tolerated through the internal tolerance module, and external intrusion tolerance of a database is achieved.
Owner:国网新疆电力有限公司信息通信公司 +1
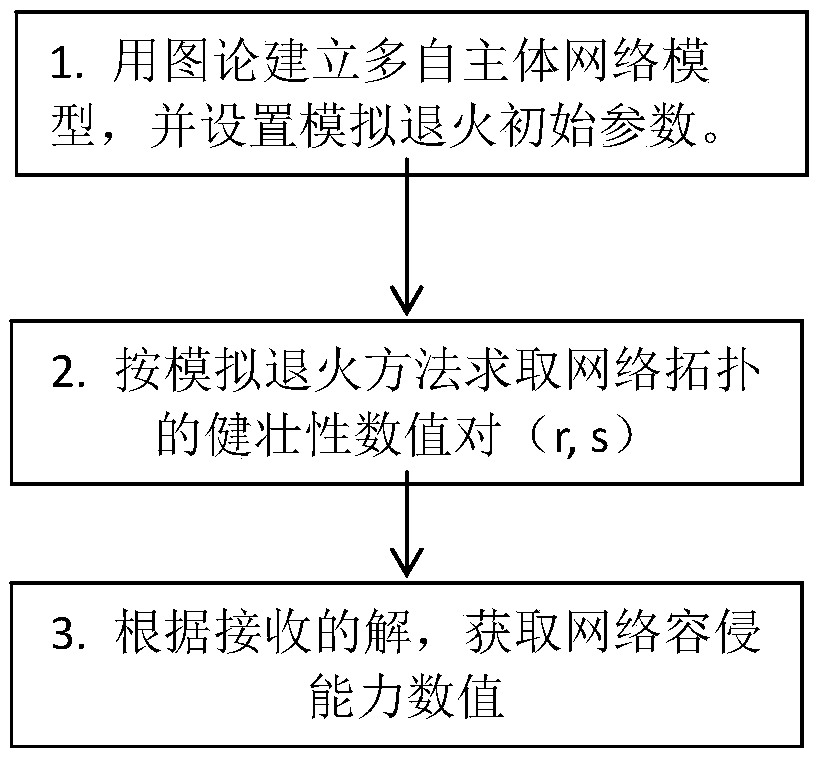
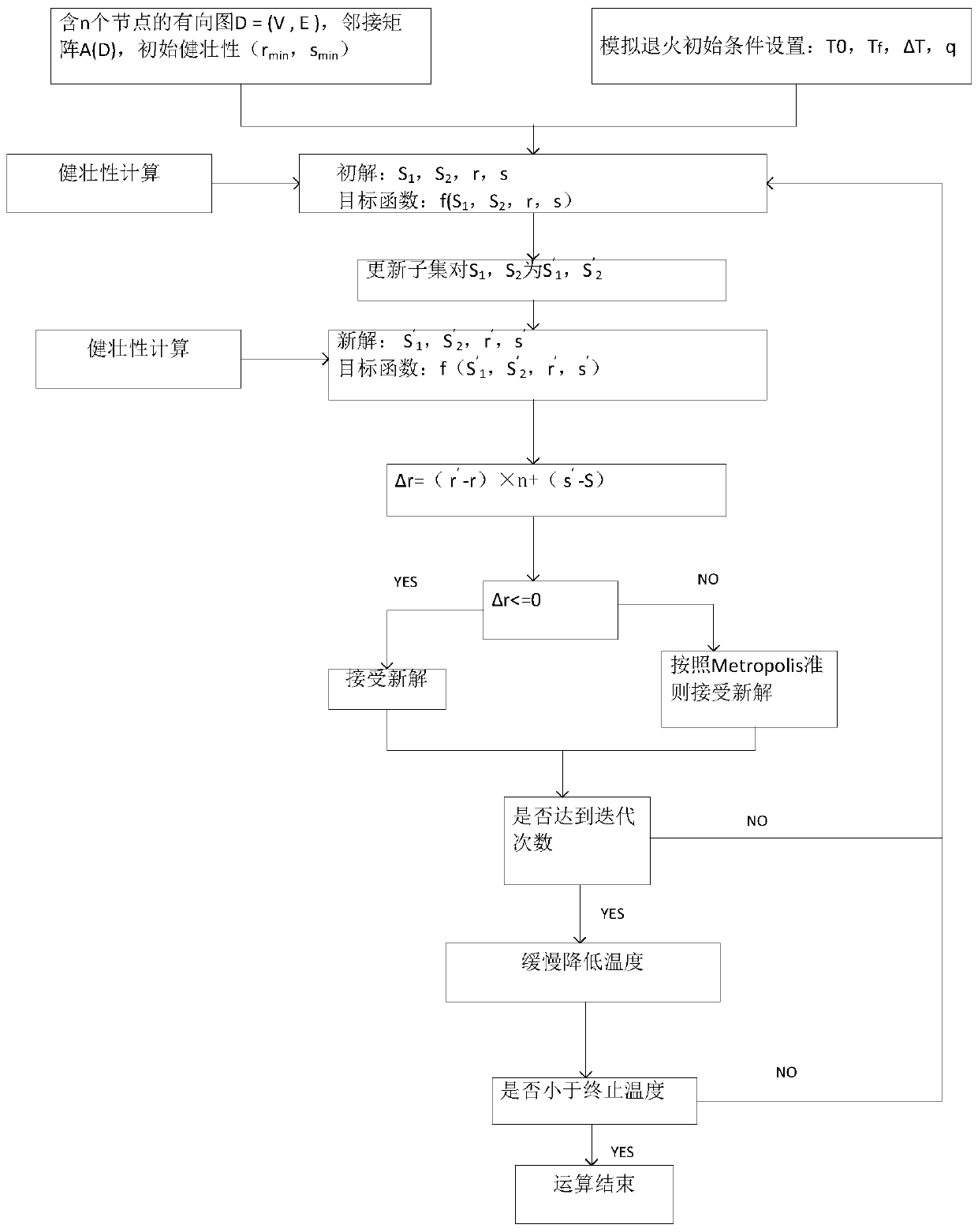
Multi-agent network intrusion tolerance capability assessment method based on simulated annealing algorithm
The invention discloses a multi-agent network intrusion tolerance capability assessment method based on simulated annealing algorithm. The simulated annealing technology is applied to the field of network intrusion tolerance capability assessment, and meanwhile, three alternative states are introduced when a network robustness calculation subset pair is updated on the basis of a traditional simulated annealing method, so that the subset pair has higher sampling randomness. The method has the advantage that the problem that large-scale multi-agent network intrusion tolerance capability assessment cannot be solved due to NP difficulty is solved.
Owner:HANGZHOU DIANZI UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com