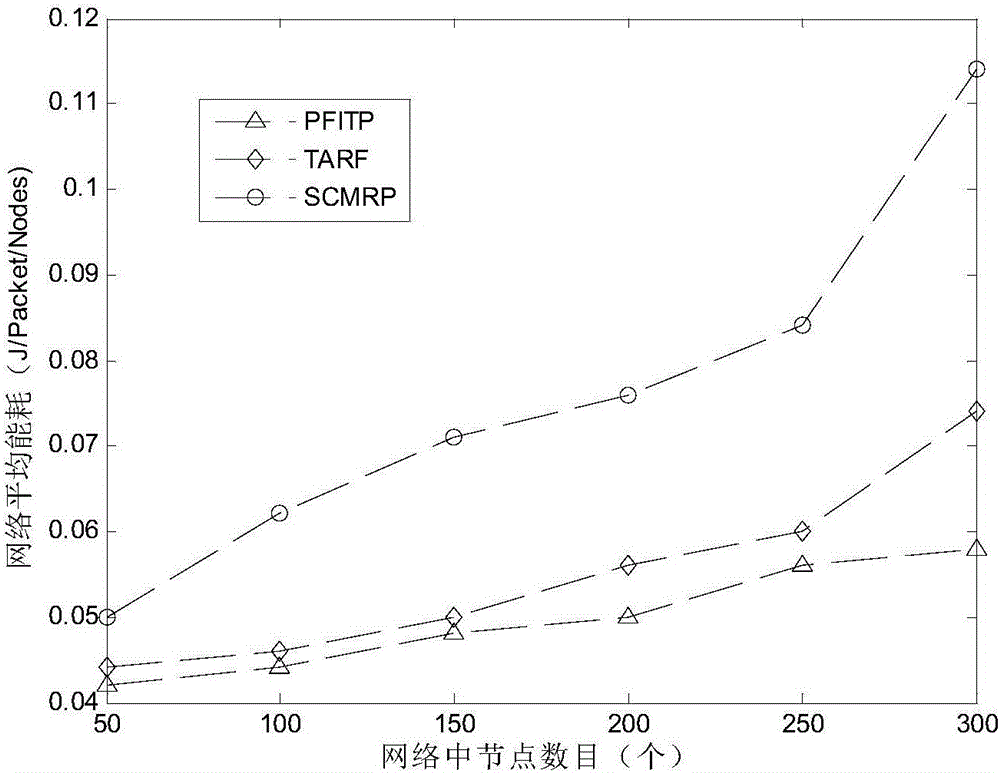
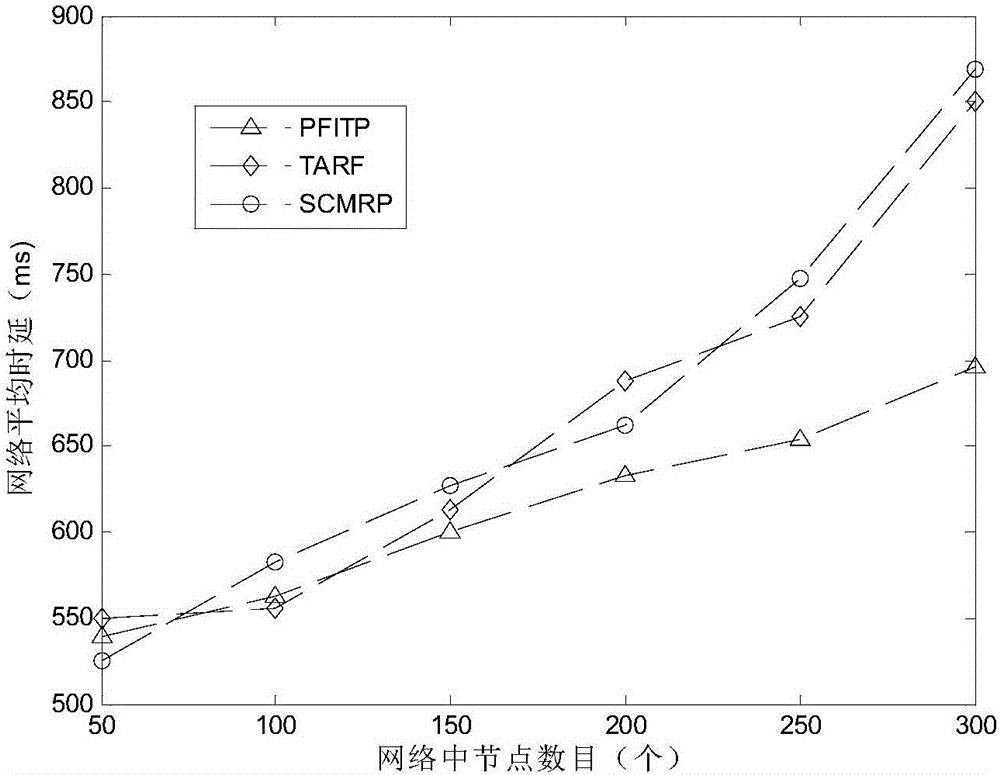
Performance feedback intrusion tolerance protocol
A routing protocol and performance technology, applied in the field of routing protocols, can solve problems such as security and less consideration of network QoS performance, and achieve the effect of improving network communication efficiency and reducing energy consumption
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
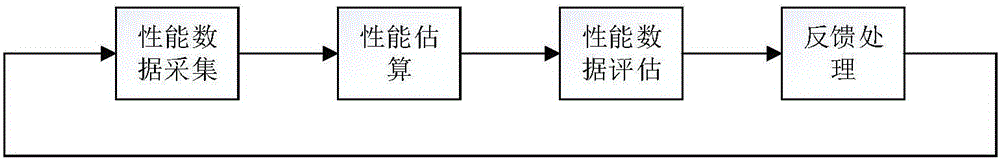
[0043] This embodiment discloses an intrusion-tolerant routing protocol PFITP based on performance feedback. The premise of the protocol is: firstly, routes should be clustered within a safe time, and the specific route clustering process is as follows:
[0044] (1) During the safe time, the base station will broadcast once: BS→*:Broad||ID BS , Broad indicates that the packet type is a broadcast packet, ID BS Indicates that the broadcast packet is from the base station. The node returns a response packet after receiving the broadcast packet: *→BS:RPT||RSSI||ID BS ||ID RPT , PRT indicates that the packet type is a response packet of broadcast data, ID RPT Indicates the node number that responds to the broadcast signal, and RSSI indicates the strength of the base station signal received by the responding node. The base station records the nodes that give response data packets, these nodes can be regarded as candidate cluster head nodes, and 10% of them can be taken as cluste...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com