A threshold-based homomorphic encryption privacy protection device and method
A technology of homomorphic encryption and privacy protection, applied in the field of threshold-based homomorphic encryption privacy protection devices, to achieve the effect of improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
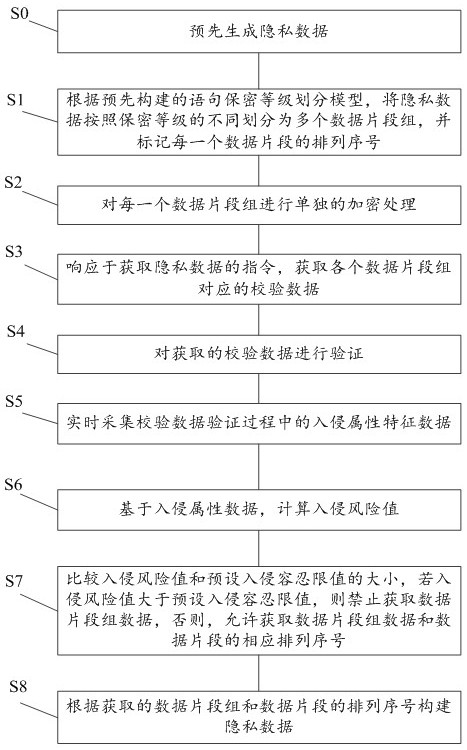
[0029] Such as figure 1 As shown, the present application provides a threshold-based homomorphic encryption privacy protection method, which includes the following steps:
[0030] Step S0, generating private data in advance.
[0031] The user terminal generates the user's private data, and indicates the date of generation of the private data.
[0032] Step S1, according to the pre-built classification model of sentence secrecy level, divide the private data into multiple data fragment groups according to different secrecy levels, and mark the sequence number of each data fragment.
[0033] Wherein, the data fragment group includes a plurality of data fragments with the same confidentiality level, and the sequence numbers of the data fragments indicate the position order of the data fragments in the private data, and the private data can be recovered by sorting the disordered multiple data fragments by the sequence numbers.
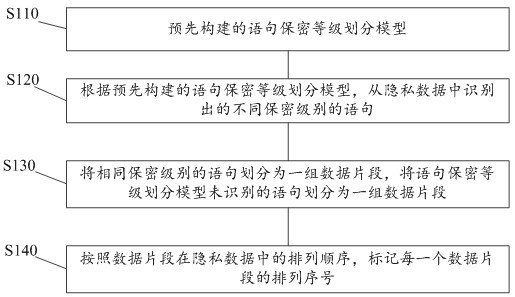
[0034] Such as figure 2 As shown, step S1 includ...
Embodiment 2
[0091] Such as Figure 6 As shown, the present application provides a threshold-based homomorphic encryption privacy protection device 100, which device includes:
[0092] The data segment division unit 10 is used to divide the private data into a plurality of data segment groups according to the different confidentiality levels according to the pre-built sentence secrecy level division model;
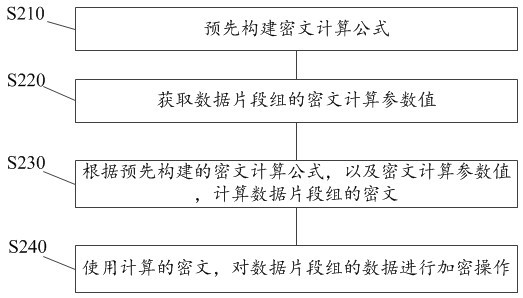
[0093] An encryption processor 20, configured to perform separate encryption processing on each data segment group;
[0094] A verification data acquisition unit 30, configured to acquire verification data corresponding to each data segment group in response to an instruction to acquire private data;
[0095] A verification processor 40, configured to verify the acquired verification data;
[0096] The collection module 50 is used to collect intrusion attribute characteristic data in the verification data verification process in real time;
[0097] A data processor 60, configured to...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com