Application level intrusion tolerance system and method
An application system and level-capacity technology, applied in the field of information security, can solve problems such as huge data structure, inability to cover attack modes and attack methods, illegal use, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
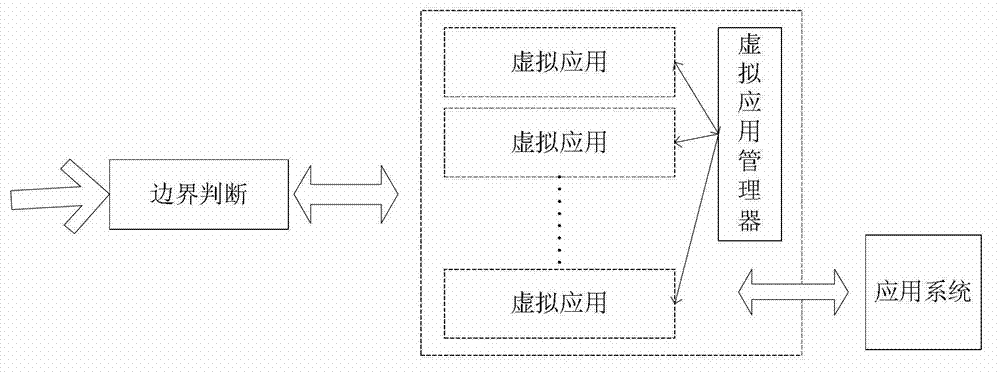
[0038] like figure 1 As shown, an application-level intrusion-tolerant system includes: a boundary judgment unit, an application unit, and an application system module connected in sequence.
[0039] The boundary judging unit is used for analyzing and allocating external access and responding to intrusion events.
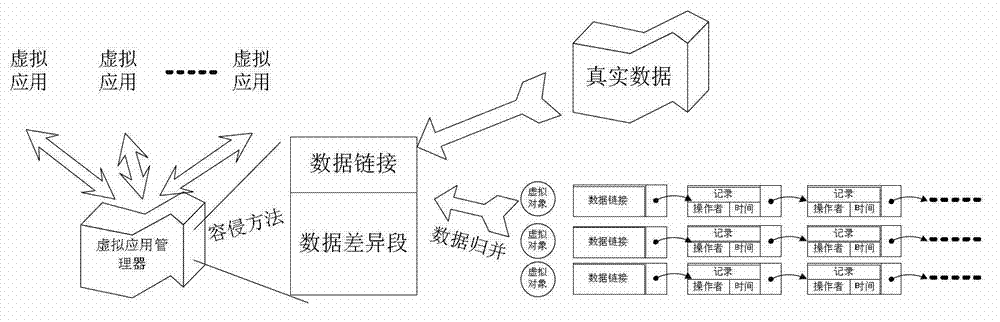
[0040] The application unit includes: a virtual application module, and a virtual application manager that performs data interaction with each virtual application module.
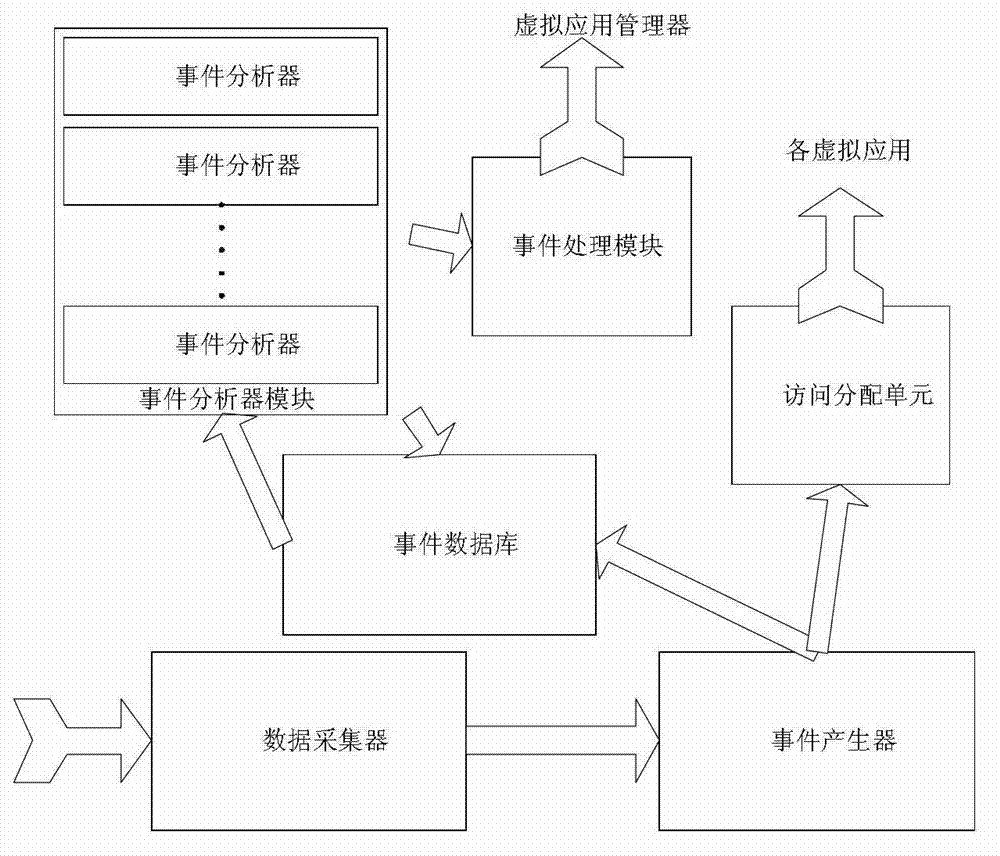
[0041] The boundary judging unit includes: a data collector, an event generator, an event database, an access distribution module, an event analyzer module and an event processing unit; the data collector, the event generator, the event database and the The event processing unit communicates in turn; the event generator sends data to the access allocation module.
[0042] The data collector collects data of the external access process, the collected data includes network data packets, access ad...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com