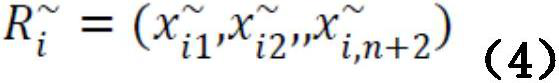Data security processing method
A processing method and data security technology, applied in the field of data processing, to achieve the effect of ensuring integrity, realizing intrusion tolerance, and ensuring legality and authenticity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
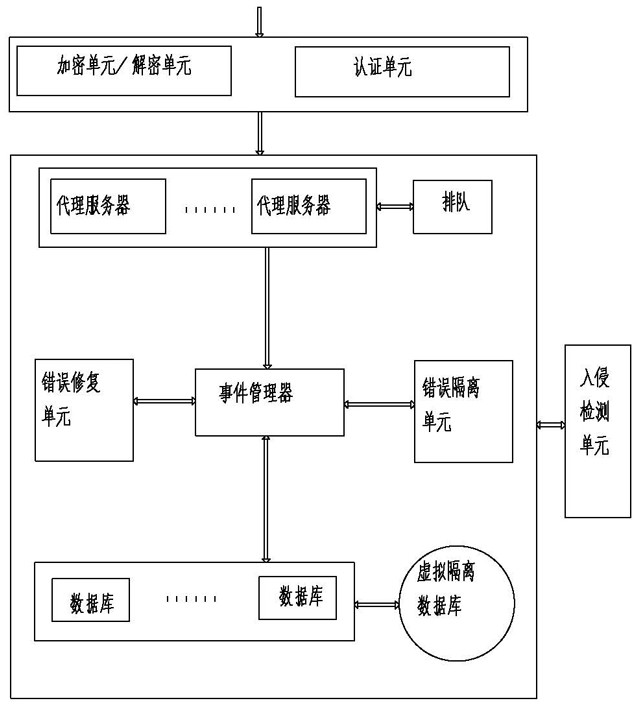
[0041] Embodiment 1: as figure 1 As shown, the data security processing method processes data through an encryption authentication module and an internal tolerance module, and the encryption authentication module includes an encryption unit, a decryption unit and an authentication unit;
[0042] The data is authenticated by the authentication unit to determine that each field of the i records has not been modified, and to determine the integrity and legality of the data. The authentication unit includes:
[0043] Construct X i value:
[0044] In formula (1),
[0045] satisfy
[0046] j=1,2,...,n+2;
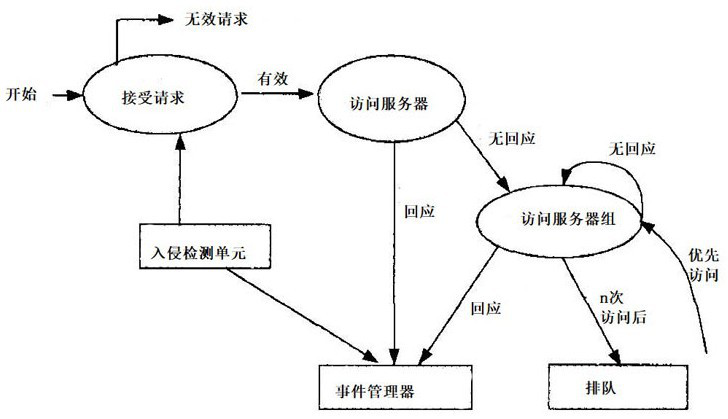
[0047] The data is encrypted by the encryption unit, such as figure 2 As shown, the encryption unit includes:
[0048] Define the i-th record of a table in the database as (x i1 , x i2 , x i3 ,...,x in ),
[0049] Choose n modulus values (m 1 m 2 … m n ), where X i ∈[0,M],
[0050] x i Expressed as:
[0051] In formula (2), M=m 1 m 2 … m n ,
[005...
Embodiment 2
[0067] Embodiment 2: As the optimization of the above-mentioned embodiment, the internal tolerance module includes an agent service unit, an error repair unit, an error isolation unit, an event management unit and an intrusion detection unit, an agent service unit, an error repair unit, an error isolation unit and an intrusion detection unit Communicatively connect with the event management unit respectively.
Embodiment 3
[0068] Embodiment 3: As an optimization of the above embodiment, the proxy service unit includes more than one heterogeneous proxy server.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com