Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
43 results about "Image forensics" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Method for image forensics of motor vehicle plate covering and staining behaviors
ActiveCN102682608ALiberation timeRestrain illegal behaviorTelevision system detailsRoad vehicles traffic controlEngineeringRoad surface
The invention relates to an image forensic method for the traffic management industry, in particularly to a method for the image forensics of motor vehicle plate covering and staining behaviors, wherein an induction coil or video detection is utilized to detect vehicles, and when a passing vehicle is detected, a signal is sent to a control host; the control host receives the signal, a wireless network is utilized, and simultaneously, a plurality of high-definition cameras are enabled to shoot; the cameras shoot from multiple angles, the shot pictures of the cameras from the adjacent angles can clearly capture the common part of the vehicle, and condition that the pictures are a group of pictures of the same vehicle from different angles is proved; the road surface has an obvious mark when the vehicle is shot, the mark can be identified from the shot picture, so the group of pictures are further proved to be taken on the same vehicle from multiple angles at the same place; through global positioning system (GPS) timing, all the cameras are synchronized, times and places are added onto the pictures after the cameras take the pictures, so the group of pictures are further proved to be taken on the same vehicle from multiple angles at the same place; according to steps 3 to 5, an complete chain of evidence is formed; and a plate identification system is utilized to compare a head picture with a tail picture of the vehicle to find out the plate covering or staining condition.
Owner:JIANGSU UTIS NEW TECH
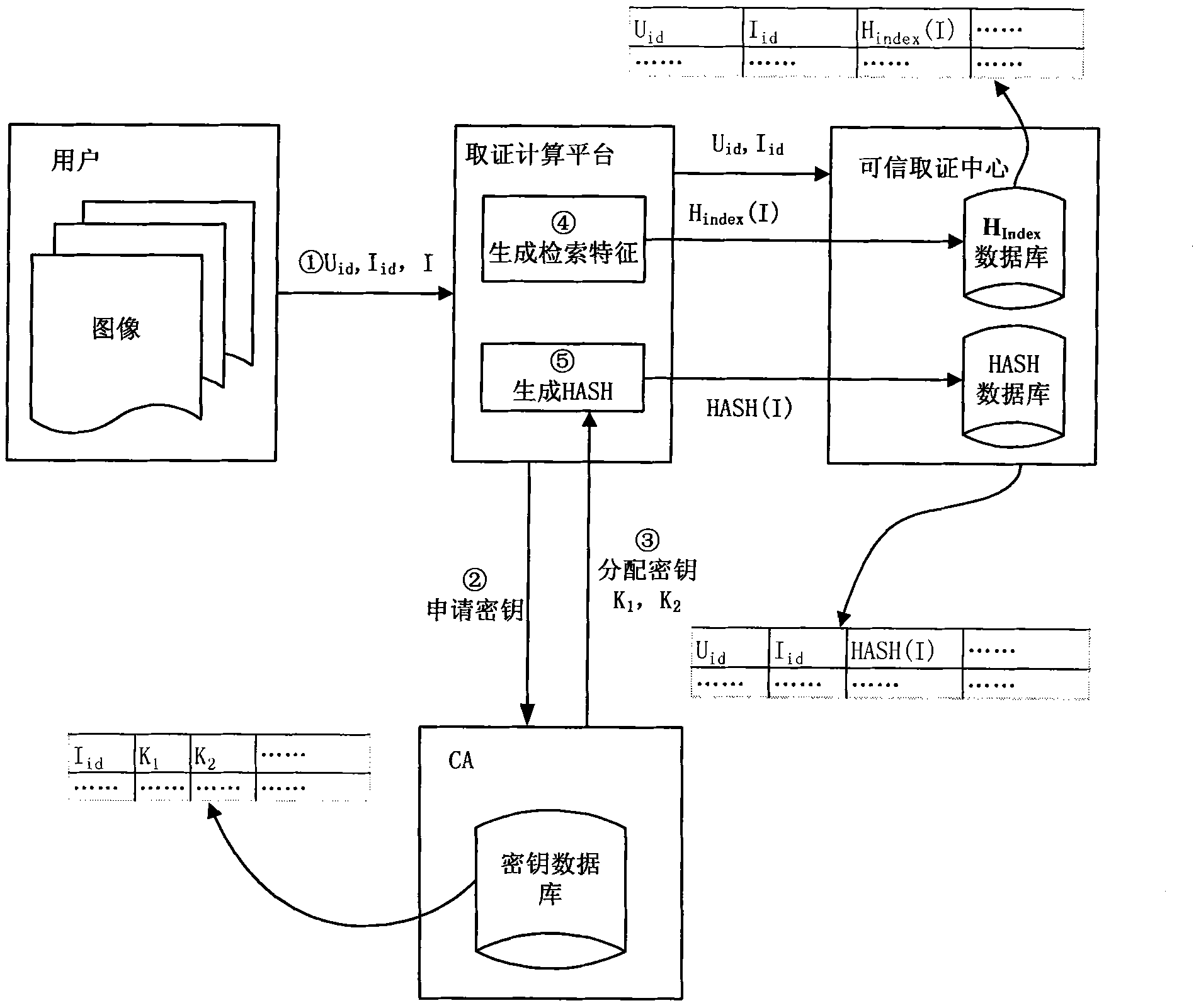
Perceptual hashing-based practical and safe image forensic system and forensic method
ActiveCN101964041AReliable evidence collectionPrecise positioningDigital data authenticationImage data processing detailsUser needsImage retrieval
The invention discloses a perceptual hashing-based practical and safe image forensic system and a perceptual hashing-based practical and safe image forensic method. The system comprises a certificate authority (CA), forensics computing platform (FCP) and a forensic center (FC). The method comprises the following steps that: the CA provides a certificate for a user, the FCP and the FC and distributes and manages a control key of a hash function for the FCP and the FC; the FCP calculates a characteristic value and generates a hash value of an image at a registration or forensics stage; the FC manages an image hash value from the FCP and provides retrieval and forensics services; the user submits the image to the FCP, extracts an image retrieval characteristic by using the FCP, calculates the hash value of an image segment by using a key distributed by the CA and submits the hash value to an FC database; and when the user needs an authentication image, the image is also submitted to the FCP, the retrieval characteristic is extracted to retrieve the most coincident original image from the FC, the image is segmented and the hash value is calculated by using the same key and the difference between the image and the hash value is compared so as to determine a position on which content tampering occurs. The system achieves high balanced performance in the aspects of safety, robustness, sensibility, rapid retrieval and the like.
Owner:ANHUI TELECOMM ENG
Sobel edge detection and image block brightness feature-based blind image tampering forensic method
InactiveCN107067389AImprove forensics efficiencyImprove efficiencyImage enhancementImage analysisSobel edge detectionLightness
The invention discloses a Sobel edge detection and image block brightness feature-based blind image tampering forensic method. The method is characterized by comprising the following steps of: converting a to-be-detected suspicious image into a grayscale image; carrying out convolution processing on the grayscale image I (i, j); obtaining a gradient image G (i, j) of the image; carrying out threshold value segmentation on the G (i, j) to obtain the gradient image G (i, j); carrying out binary processing on the gradient image G (i, j) to obtain a binary image W (i, j); carrying 1 pixelation on the binary image; and judging the similarity of two sub-image sets. According to the method, blocking processing is carried out on image sets; through brightness mean value sorting, the forensic algorithm efficiency can be effectively improved; and through comparing the similar brightness values of image blocks, the correctness is further improved and the image forensic efficiency is further improved. According to the method, the problem that the tampered images cannot be correctly detected due to cloning and tampering behaviors of large-scale zooming is solved; and through normalized image block brightness values, the detection result of cloned images with different brightness values is further improved.
Owner:FOSHAN UNIVERSITY
Bank transaction image forensic acquiring method based on face recognition
InactiveCN101751562ASimple methodImprove recognition efficiencyCharacter and pattern recognitionSerial codeRecognition system
A bank transaction image forensic acquiring method based on face recognition includes the procedures that: 1) the discrimination value is firstly initialized for preparing image acquisition: a camera on a bank client equipment starts to operate and corresponds to a serial number; 2) with the serial number, the camera snaps a group of face photos of the user; 3) the photo with the most complete face image is selected from the photos with the serial number to be stored; 3.1) the snapped photos without faces are removed; 3.2) the photo with proper size and face image in the center is selected as the optimum photo; 3.3) the optimum is stored for face recognition and corresponds to the serial number. Compared with prior art, the bank transaction image forensic acquiring method based on face recognition is simple and feasible, is used as the precondition method of the face recognition method, improves the recognition efficiency and accuracy and can be independently programmed into a function for being called by other programs.
Owner:ZHENJIANG QIDIAN SOFTWARE
Image forensics method for natural image and compressed and tampered image based on DWT
InactiveCN103903271AGet rid of the gameFeature extraction is simpleImage analysisSupport vector machineHough transform
The invention provides an image forensics method for a natural image and a compressed and tampered image based on DWT. According to the method, the natural image and the compressed image based on the DWT can be effectively distinguished, meanwhile, good distinguishability is achieved on certain specific image tampering carrying out compression trace elimination on the compressed image, the joint probability histogram of a wavelet transform coefficient of the natural image and the tampered image is calculated through the method, the histogram is normalized, then Hough transform is carried out, the mean value, variance value, skewness value and kurtosis value of a Hough transform coefficient matrix are extracted as characteristic values of a support vector machine, and a training set is formed by the characteristic values. A classification model is generated by the support vector machine through the training set in a training mode, unknown characteristic value samples are classified through the model, and whether compression or anti-compression forensics processing is carried out on an image or not is judged. The method is stable in performance, easy and convenient to implement, efficient, high in accuracy and suitable for forensics detection of the natural image and the tampered image in other aspects.
Owner:BEIHANG UNIV
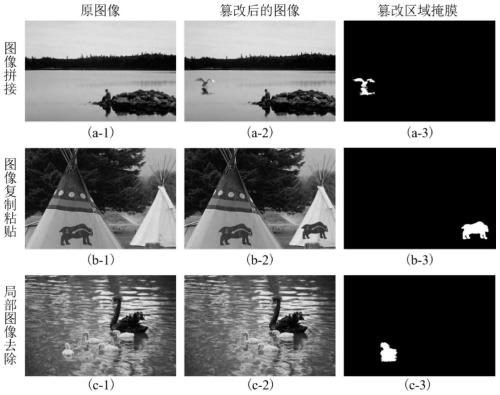
Image authenticity identification method and application thereof in certificate identification
ActiveCN111445454AEffective segmentationVerify validityImage enhancementImage analysisData setEngineering
The invention discloses an image authenticity identification method and application thereof in certificate identification, and belongs to the field of digital image processing. With the development and application of digital image editing software, lawbreakers can edit images such as identity cards, business licenses and business licenses illegally, and a adulterate effect is achieved. Therefore,the demand of image evidence obtaining becomes increasingly urgent, and most of existing models can only detect whether images are tampered or not and cannot well segment tampered areas. The inventionprovides an image tampering detection method based on a convolutional neural network, which can effectively segment a tampered area in an image by fusing multiple features of the tampered image. Experiments are carried out on a plurality of data sets, and experiment results further show that our work is effective.
Owner:JIANGNAN UNIV
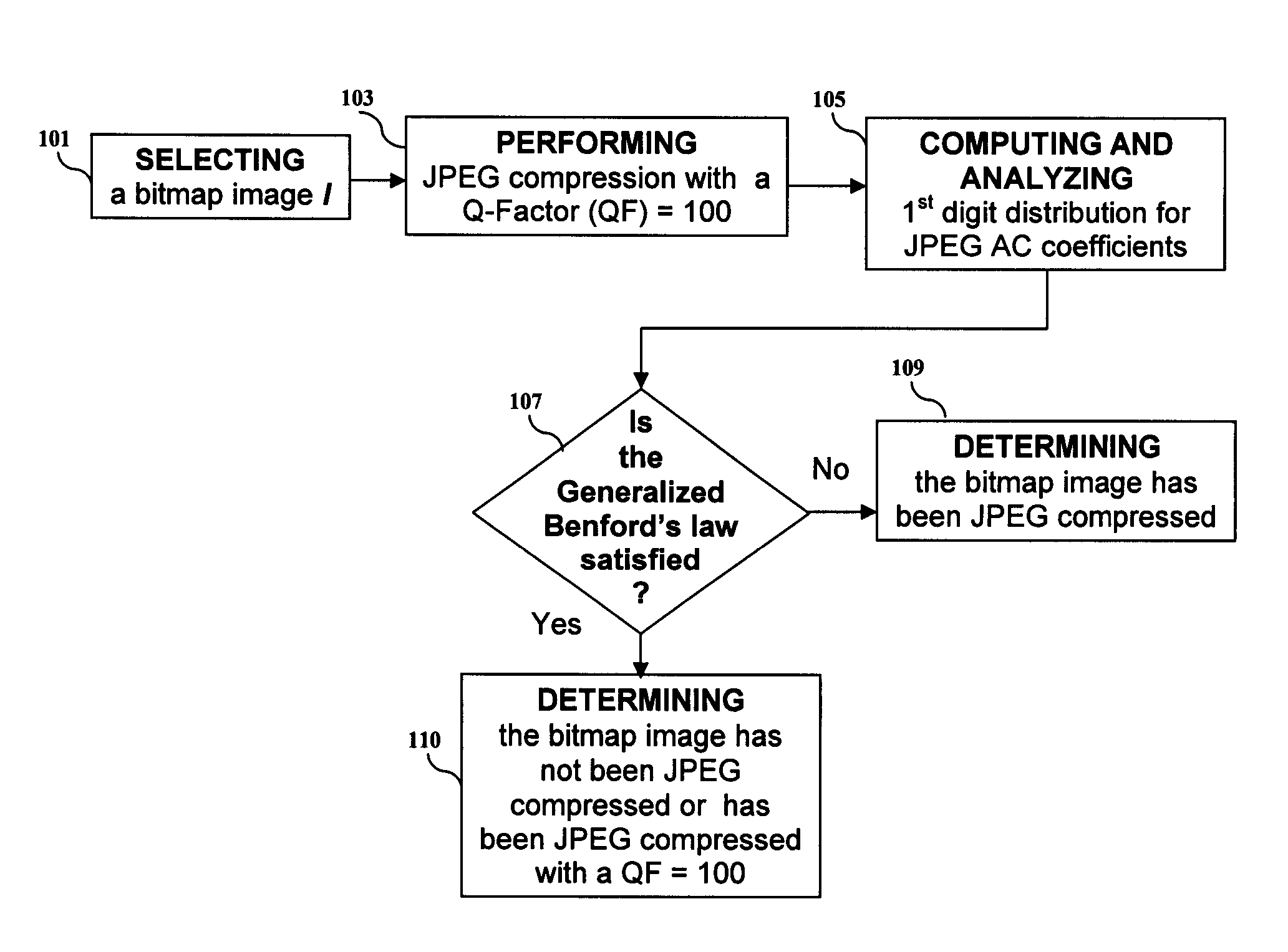
Apparatus and method for a generalized benford's law analysis of DCT and JPEG coefficients
ActiveUS7940989B2Character and pattern recognitionDigital video signal modificationJPEGLaws of thermodynamics
A method and apparatus for a novel statistical model based on Benford's law for the probability distributions of the first digits of the block-DCT and quantized JPEG coefficients. A parametric logarithmic law, the generalized Benford's law, is formulated. Furthermore, some potential applications of this model in image forensics, which include the detection of JPEG compression for images in bitmap format, the estimation of JPEG compression Q-factor for JPEG compressed bitmap image, and the detection of double compressed JPEG image. Experimental results demonstrate the effectiveness of the statistical model used in embodiments of the invention.
Owner:NEW JERSEY INSTITUTE OF TECHNOLOGY
Synthetic face image evidence obtaining method based on local binary pattern and deep learning
InactiveCN111222434AReduce feature dimensionReduce training complexityCharacter and pattern recognitionNeural architecturesSample imageTest set
The invention discloses a synthetic face image evidence obtaining method based on a local binary pattern and deep learning, and the method comprises the steps: collecting and marking a real face imageand a synthetic face image, creating a face image evidence obtaining sample image library, and dividing the image library into three parts: a training set, a verification set and a test set; determining an LBP operator mode and a sampling radius according to the extracted local binary pattern LBP features of the face image; constructing a face forensic convolutional neural network model, settinga convolutional neural network training hyper-parameter, obtaining an evaluation score according to logistic regression in a classification module, and updating a network parameter in the feature extraction module according to a loss function, a data label and the evaluation score; and training a neural network through the training set and the test set to obtain a training model, wherein the training model detects whether the input face image is a real natural face or a synthetic face. According to the invention, the common synthetic face image at the present stage can be rapidly and efficiently detected.
Owner:SHENZHEN AIXIESHENG TECH CO LTD
Method for shooting and taking evidence through handheld camera
InactiveCN103077523AReduce complexityThe importance is self-evidentImage analysisComputer visionImage forensics
The invention relates to an image evidence-taking technology. The invention aims at adopting the bevel angle of a blanking line, which is obtained by computing, to perform the certification of camera shooting modes, and adopts the technical scheme that the method for shooting and taking evidence through a handheld camera comprises the following steps of: firstly, extracting linear information of an original image, secondly, positioning a corresponding blanking point according to the extracted linear information, thirdly, computing the rotation angle of a camera, and fourthly, performing the certification of shooting modes according to the rotation angle. The method is mainly applied to image forensics.
Owner:TIANJIN UNIV
Image blind detection method based on secondary seam clipping features
ActiveCN104599279AReduce feature dimensionReduce computational complexityImage analysisCharacter and pattern recognitionComputation complexityFeature Dimension
The invention provides an image blind detection method based on secondary seam clipping features and belongs to the field of blind image forensics image processing. The method includes: (1) conducting additional seam clipping operation on an image to obtain an additional seam clipping image; (2) conducting feature extraction which includes calculating the similarity feature, the energy ratio feature and the stitch distance difference feature between the image and the corresponding additional seam clipping image; (3) detecting seam clipping through a training support vector machine by utilizing the similarity feature, the energy ratio feature and the stitch distance difference feature which are extracted. The method is low in feature dimension, has lower calculation complexity and meanwhile has higher detection rate.
Owner:TIANJIN POLYTECHNIC UNIV
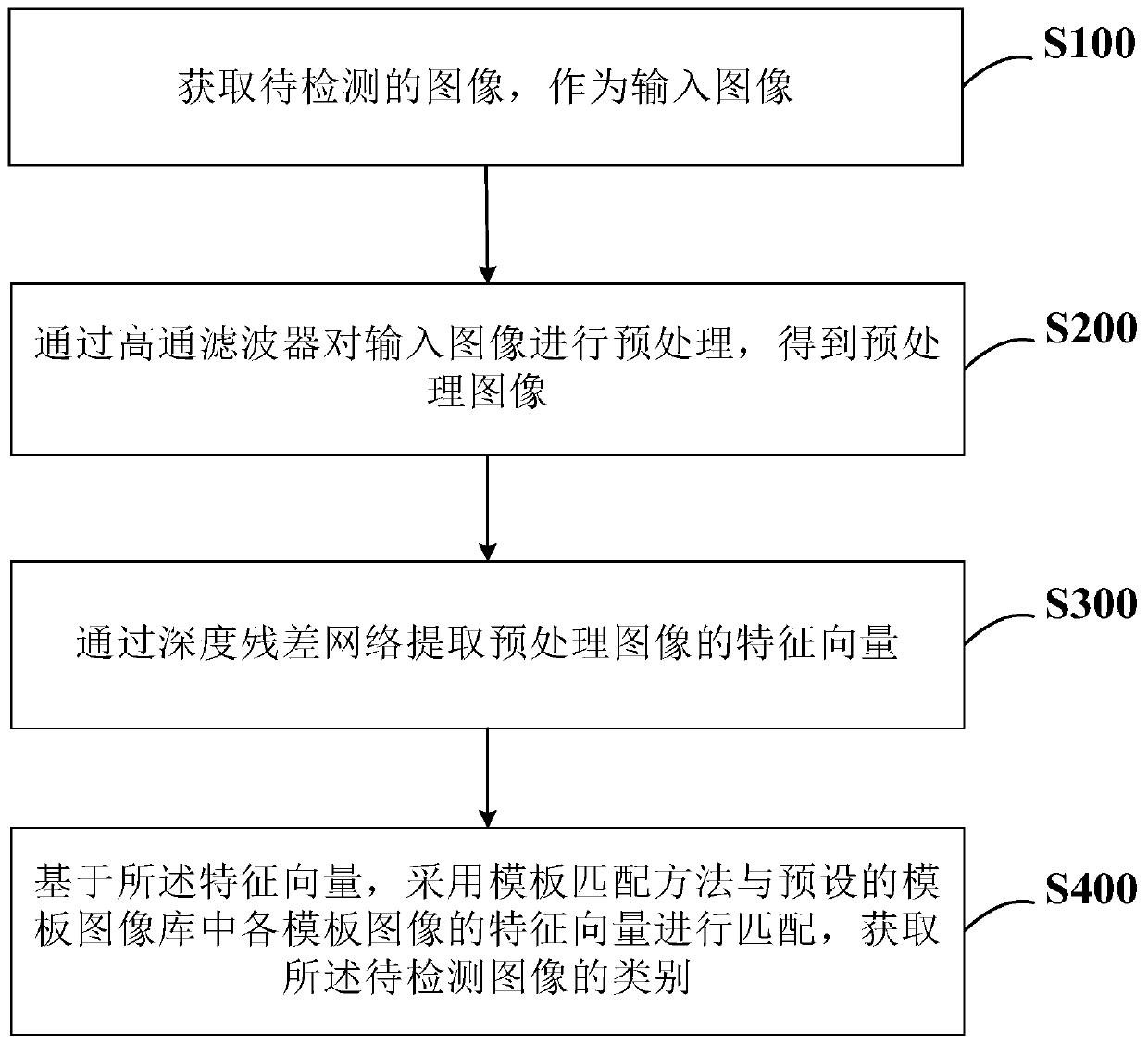
Method, system and device for detecting multi-type deep network generated images
PendingCN110942034AImprove detection accuracyImprove scalabilityCharacter and pattern recognitionNeural architecturesTemplate matchingFeature vector
The invention belongs to the field of deep network generated image, computer vision and image forensics, particularly relates to a method, a system and a device for detecting multiple types of deep network generated images, and aims to solve the problem of low detection rate of the existing deep network generated image detection method for different types of deep network generated images and new types of deep network generated images. The method comprises the following steps: acquiring a to-be-detected image as an input image; preprocessing the input image through a high-pass filter to obtaina preprocessed image; extracting a feature vector of the preprocessed image through a deep residual network; and based on the feature vector, matching the feature vector with the feature vector of each template image in a preset template image library by adopting a template matching method to obtain the category of the to-be-detected image. According to the invention, the detection accuracy of images generated by different types and new types of deep networks is improved.
Owner:INST OF AUTOMATION CHINESE ACAD OF SCI
Deep multi-scale network-based secondary JPEG compressed image forensics method
ActiveCN108537762AEliminate less defectsFeature distinctionImage enhancementImage analysisJPEGDct coefficient
The invention provides a deep multi-scale network-based secondary JPEG compressed image forensics method. The invention aims to improve the accuracy of image forensics. The implementation process of the method include the following steps that: N DCT coefficient histogram features of a JPEG image to be subjected to forensics are extracted; four deep neural networks are trained; the preliminary tampering detection result of the corresponding data block of one DCT coefficient histogram feature in the JPEG image to be subjected to forensics is obtained; the final tampering detection result of thecorresponding data block of the one DCT coefficient histogram feature in the JPEG image to be subjected to forensics is obtained; the final tampering detection results of the corresponding data blocksof the other N-1 DCT coefficient histogram features in the JPEG image to be subjected to forensics are obtained; and the forensics result image of the JPEG image to be subjected to forensics is obtained. The method of the invention can be used for fields such as news photography authentication, judicial authentication, insurance authentication and bank electronic bill authentication.
Owner:XIDIAN UNIV
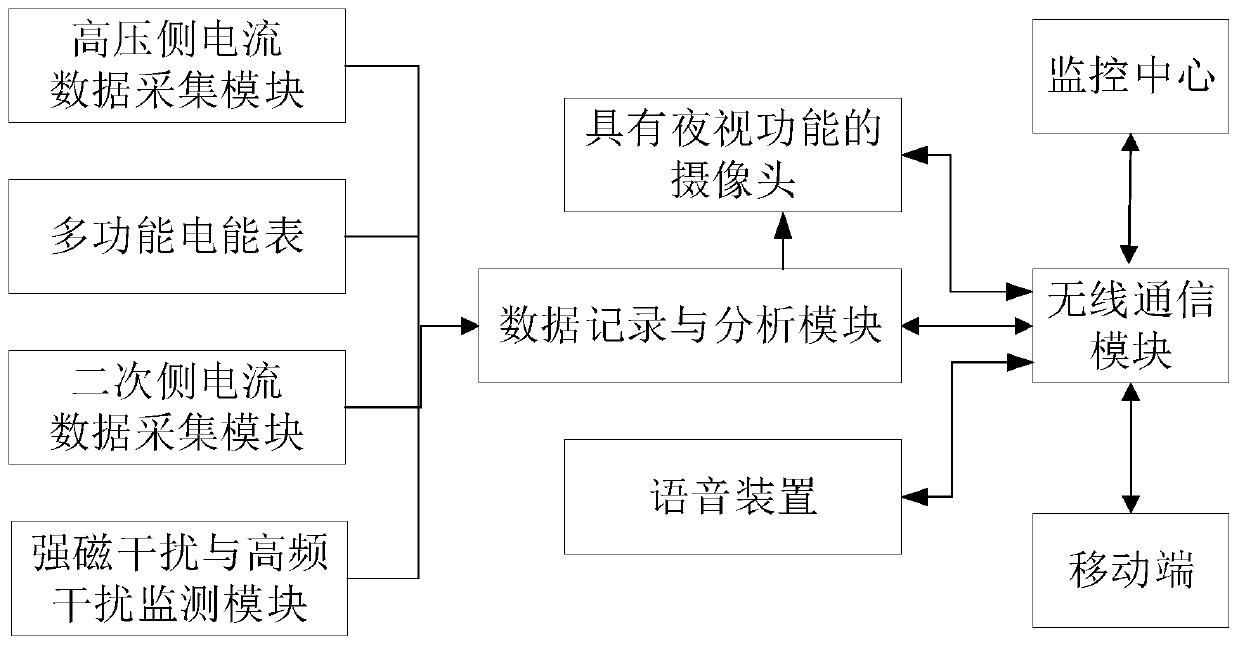
Electricity stealing prevention video evidence collecting and real-time warning device
InactiveCN110728814AStealing electricityRealize anti-stealing video image forensicsElectrical measurementsBurglar alarmInterference (communication)Low voltage
The invention relates to an electricity stealing prevention video evidence collecting and real-time warning device, and belongs to the field of electricity stealing prevention. The electricity stealing prevention video evidence collecting and real-time warning device comprises a high voltage side current data acquisition module, a secondary side current data acquisition module, a strong magnetic interference and high frequency interference detection module, a data recording and analysis module, a wireless communication module, a mobile terminal, a camera device, and an audio device, wherein the high voltage side current data acquisition module, the secondary side current data acquisition module, the strong magnetic interference and high frequency interference detection module, the camera device, and a multifunctional electric energy meter are respectively connected with the data recording and analysis module; and the camera device, the data recording and analysis module, and the audiodevice are all connected with the wireless communication module. The electricity stealing prevention video evidence collecting and real-time warning device compares high voltage current information with low voltage current information to determine an electricity stealing behavior; meanwhile, by integration of an advanced measurement system, current data of a user side is compared with the currentstealing criteria for analysis to determine the electricity stealing more accurately; moreover, the electricity stealing prevention video evidence collecting and real-time warning device can adjust the electricity stealing criteria on line to improve the accuracy, and can also realize electricity stealing prevention video image evidence collection and real-time warning.
Owner:JINZHONG POWER SUPPLY COMPANY OF STATE GRID SHANXI ELECTRIC POWER +1
Copy-paste fake image evidence obtaining method based on end-to-end deep neural network
The invention discloses a copy-paste forged image evidence obtaining method based on an end-to-end deep neural network, and the method is characterized in that the method comprises the steps: 1, constructing an end-to-end Dense-InceptionNet neural network model which comprises a Dense-InceptionNet pyramid feature extraction module, a feature correlation matching module, a hierarchical post-processing module and a step 2, and training the end-to-end Dense-InceptionNet neural network model. Compared with the prior art, the model provided by the invention mainly takes feature correlation as a learning object, searches a suspected counterfeit area through a feature matching clue, and can accurately position the counterfeit area at a pixel level.
Owner:GUANGDONG MECHANICAL & ELECTRICAL COLLEGE
Image forensic adversarial attack defense method based on class feature restoration fusion
PendingCN112215780AAchieve filteringImprove applicabilityImage enhancementImage analysisImaging qualityEngineering
The invention discloses an image forensic adversarial attack defense method based on class feature restoration fusion, and the method comprises the steps of inputting an original image containing adversarial disturbance into a classification model constructed based on a convolutional neural network, carrying out the class feature visualization of an extracted feature map, obtaining a reconstruction region based on a visualization result, and obtaining an adversarial disturbance model; performing feature restoration on the reconstructed area to obtain a restored image; and denoising the original image to obtain a denoised image, fusing the restored image and the denoised image to obtain a fused image, selecting a plurality of classification areas with high image quality according to the pixel distribution characteristics of the fused image, inputting the classification areas into the classification model, and taking the highest classification probability output by the classification model as a defended class label. The method can improve the robustness of the deep learning model and accurately restore the evidence obtaining information.
Owner:ZHEJIANG UNIV OF TECH
Fine-grained image splicing area detection method
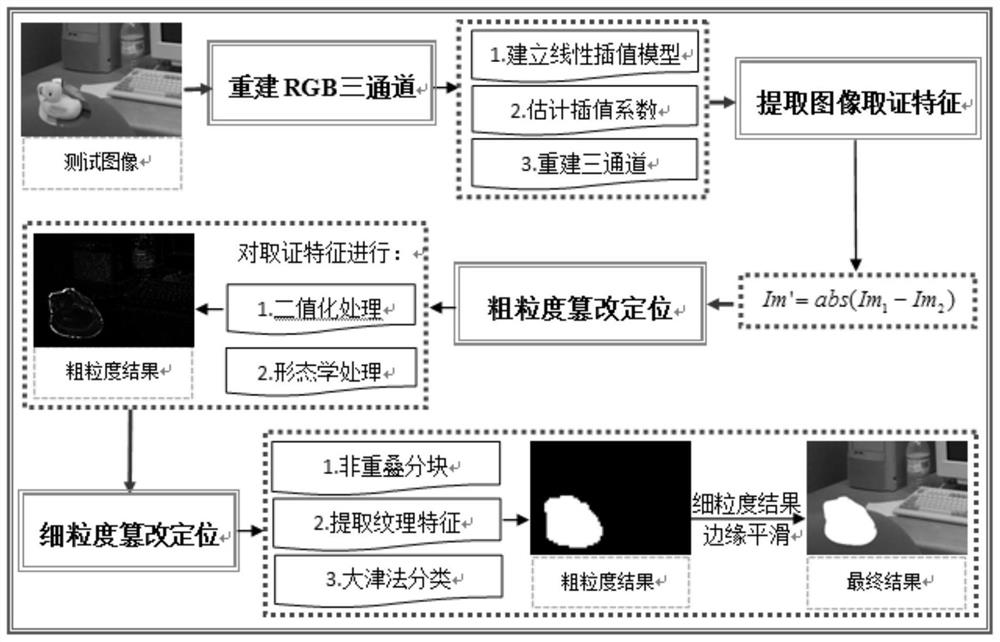
PendingCN112435226ATroubleshoot detection failuresAvoid dependencyImage enhancementImage analysisSuperpixel segmentationRegion detection
The invention discloses a fine-grained image splicing region detection method, which comprises the following steps of: firstly, extracting RGB (Red, Green and Blue) color channels of an image, establishing a linear interpolation model, and respectively estimating interpolation coefficients of the three channels through a covariance matrix so as to reconstruct the three channels; and then, constructing an image forensic feature by using a Laplace operator, performing binarization processing and morphological operation on the forensic feature, performing non-overlapping blocking on a coarse-grained detection result, extracting texture strength features of coarse-grained blocks, and then performing classification and false detection removal to obtain a detection result of a fine-grained splicing region; and finally, smoothing the edge of the detection result of the fine-grained splicing region through a super-pixel segmentation algorithm to obtain a final detection result of the image splicing region. According to the method, the problem that a common CFA-based image stitching detection method is not robust to JPEG compression is solved.
Owner:XIAN UNIV OF TECH
Customs anti-smuggling execution system and method
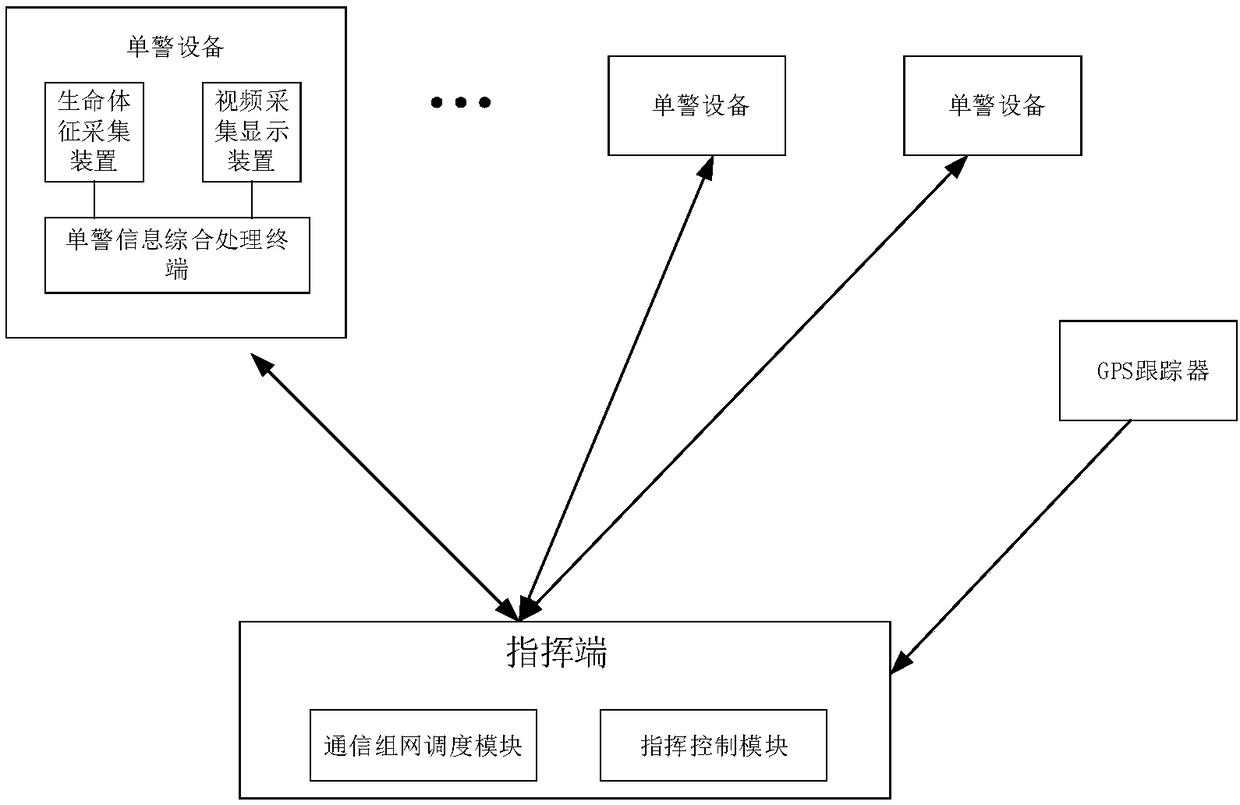
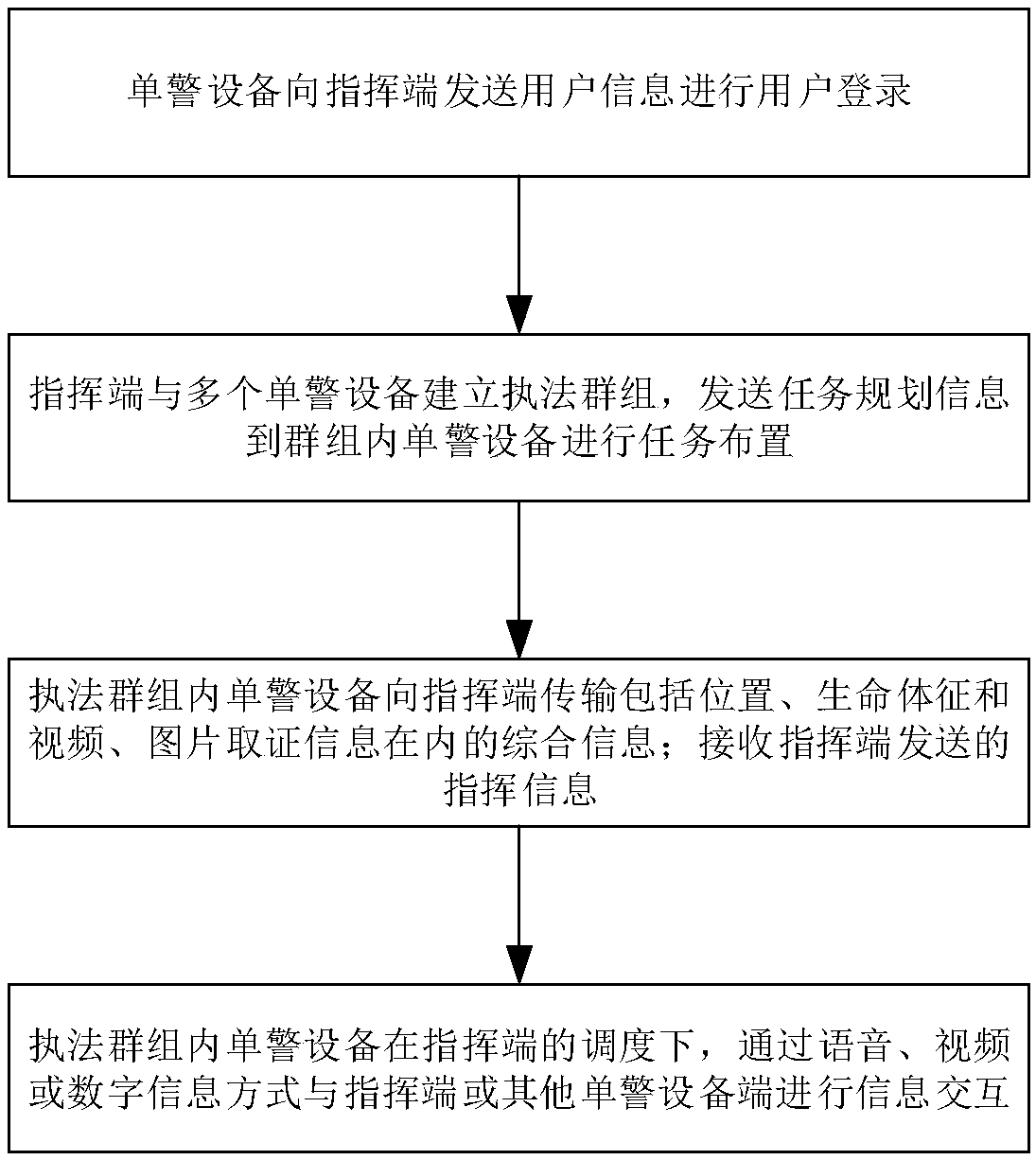
InactiveCN109120891ARealize a reasonable distributionReliable interactionTelevision system detailsTransmission systemsVital signsComputer science
The invention relates to a customs anti-smuggling execution system and method. The customs anti-smuggling execution system includes a command end and a plurality of single police devices, wherein thecommand end is used for establishing a law enforcement group including the command end and the plurality of single police devices, receiving integrated information including single police position, vital sign information, and video and image forensics information, sent by each single police device, sending command information to the single police device, performing scheduling between the command end and the single police devices, and between the single police devices in the group, and implementing information interaction, including voice, video and digital information. The customs anti-smuggling execution system fully considers the specific characteristics of the customs anti-smuggling work, establishes a variety of information interaction modes, ensures real-time and reliable interactionof multiple types of integrated information, enables a commander to fully grasp the situation of the law enforcement staff and the law enforcement site so as to achieve accurate command, can liberatethe hands of the law enforcement staff, and realizes visual and intelligent law enforcement, thus improving the law enforcement effect of law enforcement staff.
Owner:CSSC ELECTRONICS TECH
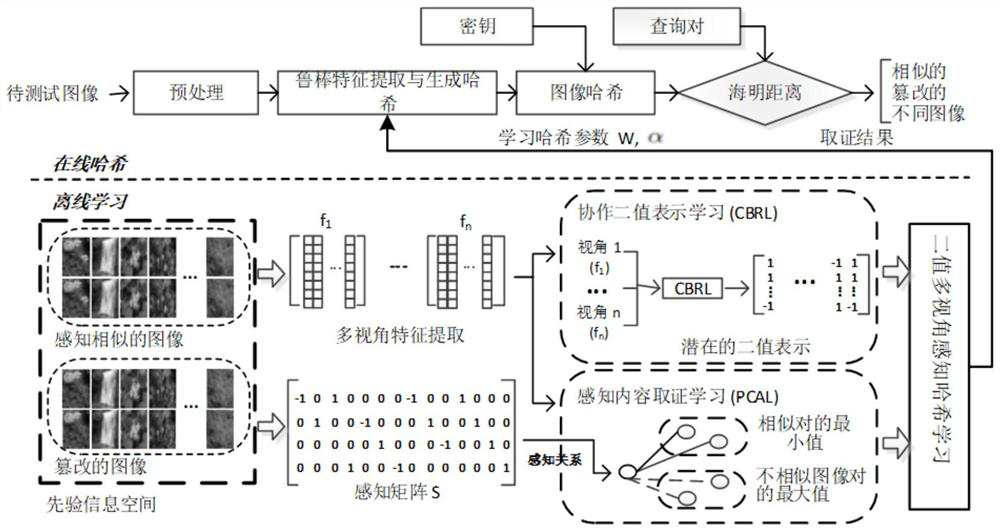
Image evidence obtaining method and system based on multi-view features
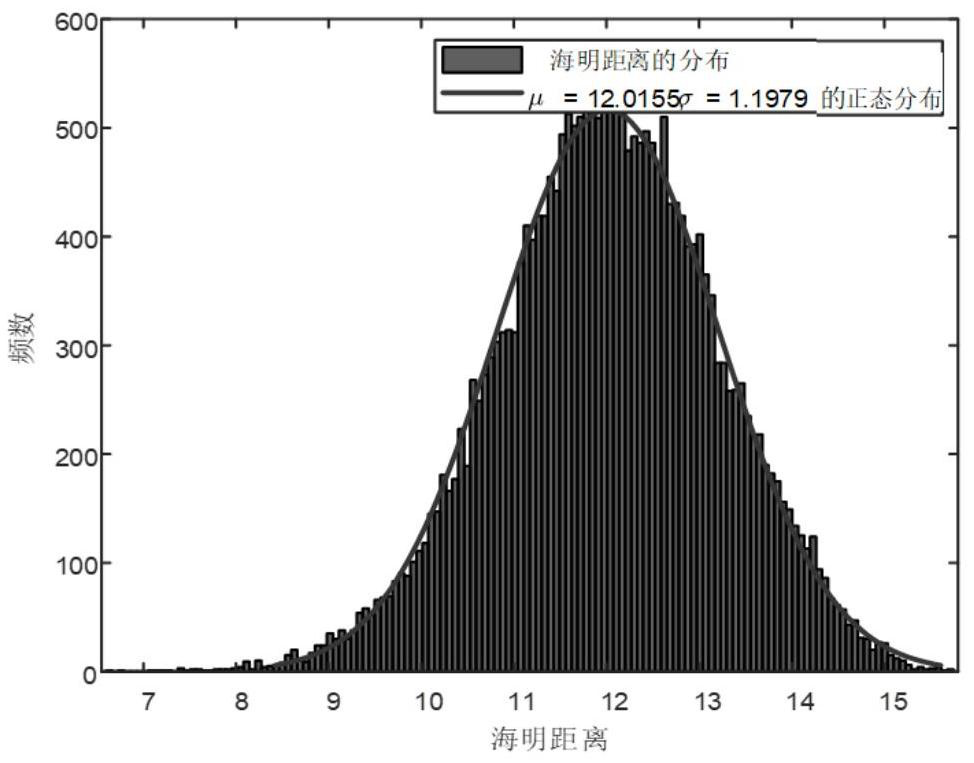
ActiveCN113191380AHigh expressionImprove accuracyCharacter and pattern recognitionPattern recognitionImage detection
The invention provides an image evidence obtaining method and system based on multi-view features, and belongs to the field of image detection. The method comprises the following steps: step 1, respectively obtaining image features of an original image and a to-be-tested image; 2, respectively calculating the hash value of the original image and the hash value of the to-be-tested image; 3, calculating to obtain a Hamming distance by using the hash value of the original image and the hash value of the to-be-tested image; and step 4, obtaining an evidence obtaining result by using the Hamming distance. According to the invention, the bottleneck of calculation and storage is solved, so that the Hash coding result has better expression ability and accuracy; according to the invention, a potential binary representation multi-view function is effectively utilized, and the method is more comprehensive compared with a single view; data with multiple view angles can be fused, so that the framework has better flexibility and wider application scenes; according to the invention, the operation robustness of the image content can be kept, and meanwhile, the method has good distinguishing performance on malicious tampering operation.
Owner:TIANJIN POLYTECHNIC UNIV
Vehicle illegal parking detection method convenient to adjust
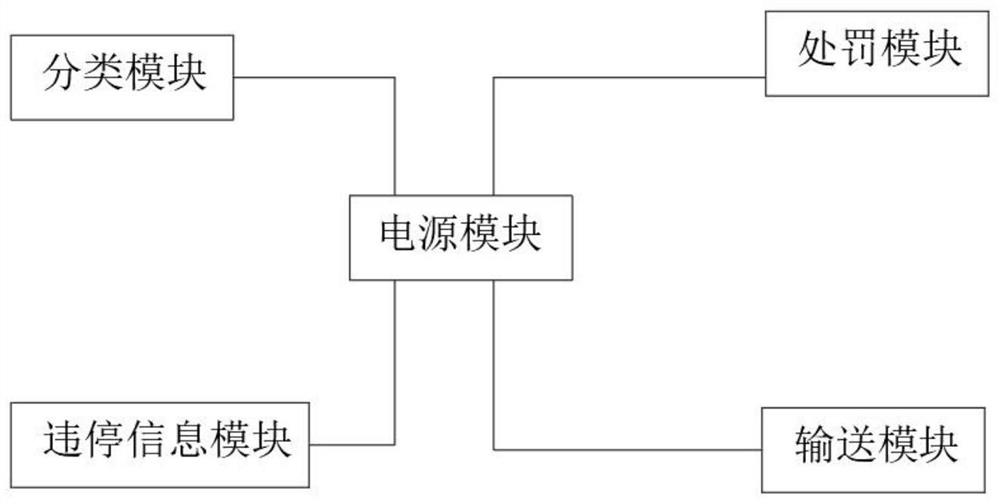
PendingCN112507971AAvoid warningAvoid misjudgmentData processing applicationsRoad vehicles traffic controlData transmissionReliability engineering
The invention discloses a vehicle illegal parking detection method convenient to adjust. The vehicle illegal parking detection method comprises the following steps that S1, image evidence obtaining iscarried out by shooting an image of a motor vehicle; s2, the image is transmitted to a snapshot system through data transmission, and data comparison is carried out; s3, after the data comparison iscompleted, the information is determined; and S4, the owner of the illegally-parked vehicle is notified. The method is scientific and reasonable in structure and safe and convenient to use, evidencesare obtained by shooting images of the motor vehicle and system comparison is conducted, then the data are intervened better and more accurately; therefore, some official vehicles are processed independently, unnecessary warning and misjudgment of the vehicles under special conditions are avoided, and the safety of the official vehicles is improved; meanwhile, punishment is performed through the punishment module according to the information of the classification module in combination with a local traffic management part, so that the system is more humanized and reasonable and is suitable forbetter popularization and application.
Owner:中科视拓(南京)科技有限公司
Information evidence collection method for Internet of things
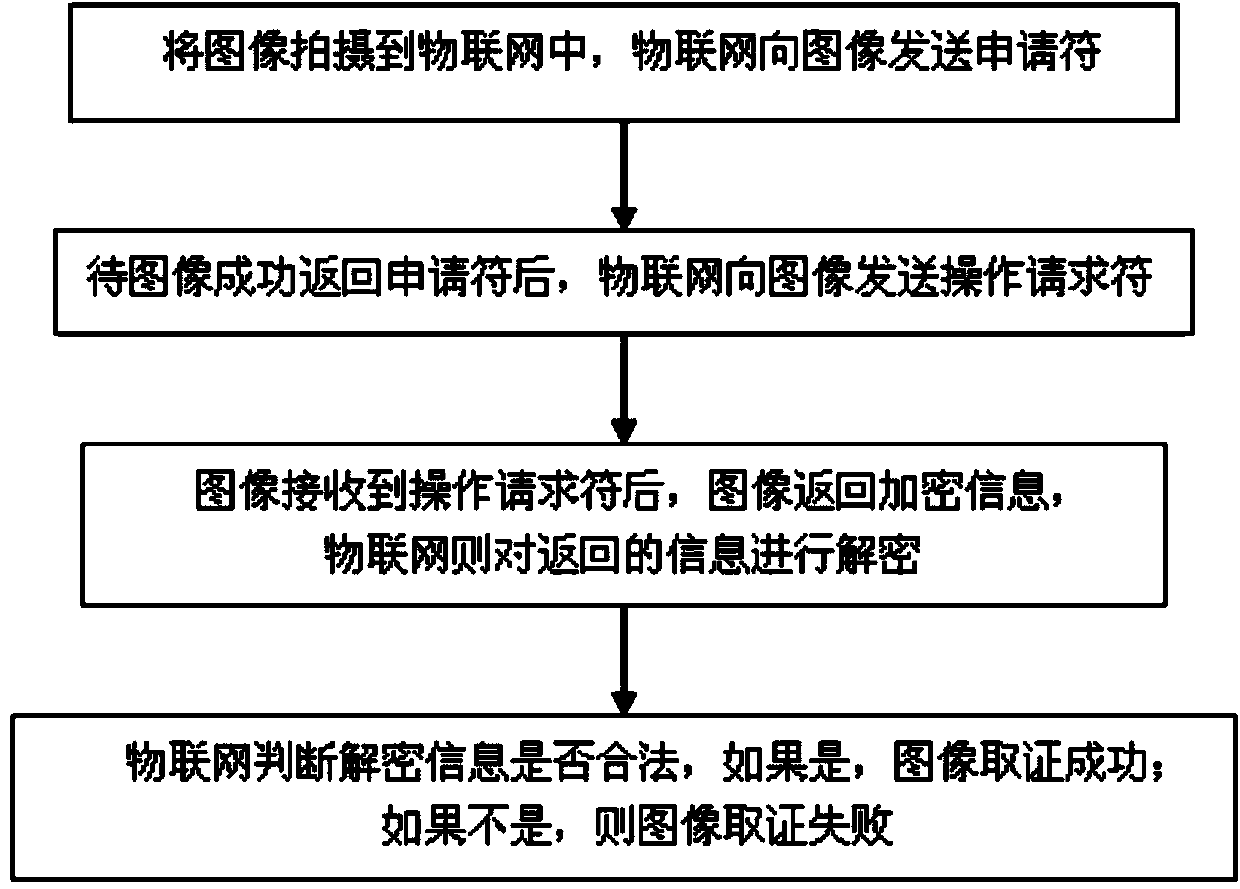
InactiveCN103810410ASecurity and confidentialityTelevision system detailsColor television detailsInternet of ThingsImage pattern
The invention discloses an information evidence collection method for Internet of things. The method comprises the following steps that 1, an evidence collection starting mode of the Internet of things is selected; 2, after the starting mode in the step 1 is set, any person needs to pass identity evidence collection before using the Internet of things, wherein the identity evidence collection comprises image evidence collection and head pattern evidence collection; 3, the evidence collection of the Internet of things is started successfully, and the Internet of things enters a work mode. A system comprises a processor module, an information evidence collection module and an internal memory connected with the processor module, wherein the information evidence collection module comprises a head pattern evidence collection module and an image evidence collection module; both the head pattern evidence collection module and the image pattern are connected with the processor module. According to the information evidence collection method for the Internet of things, an evidence collection step is added in the starting process, so that the use of the Internet of things is more secure.
Owner:UNIV OF SCI & TECH LIAONING
Recolored image evidence obtaining method based on spatial correlation
PendingCN114202592AAccurate detectionImage analysisCharacter and pattern recognitionFeature learningImage detection
The invention discloses a recoloring image evidence obtaining method based on spatial correlation. The method comprises the following steps: 1, constructing a training set and a test set by using images processed by multiple recoloring algorithms and corresponding natural images; 2, extracting spatial correlation characteristics, and calculating co-occurrence matrixes of each color channel of the image in four directions; 3, constructing a feature learning network; 4, training the designed model by using the constructed training set and the corresponding label set; and 5, predicting the images of the test set by using the stored optimal model weight, and distinguishing natural images from re-colored images. According to the invention, the preset network model is trained to obtain the re-colored image detection model after training, whether one picture is subjected to re-coloring tampering or not is accurately detected by using the re-colored image detection model, and the method plays an important role in various practical application occasions related to image security.
Owner:NANJING UNIV OF AERONAUTICS & ASTRONAUTICS
Air quality detecting device based on unmanned aerial vehicle
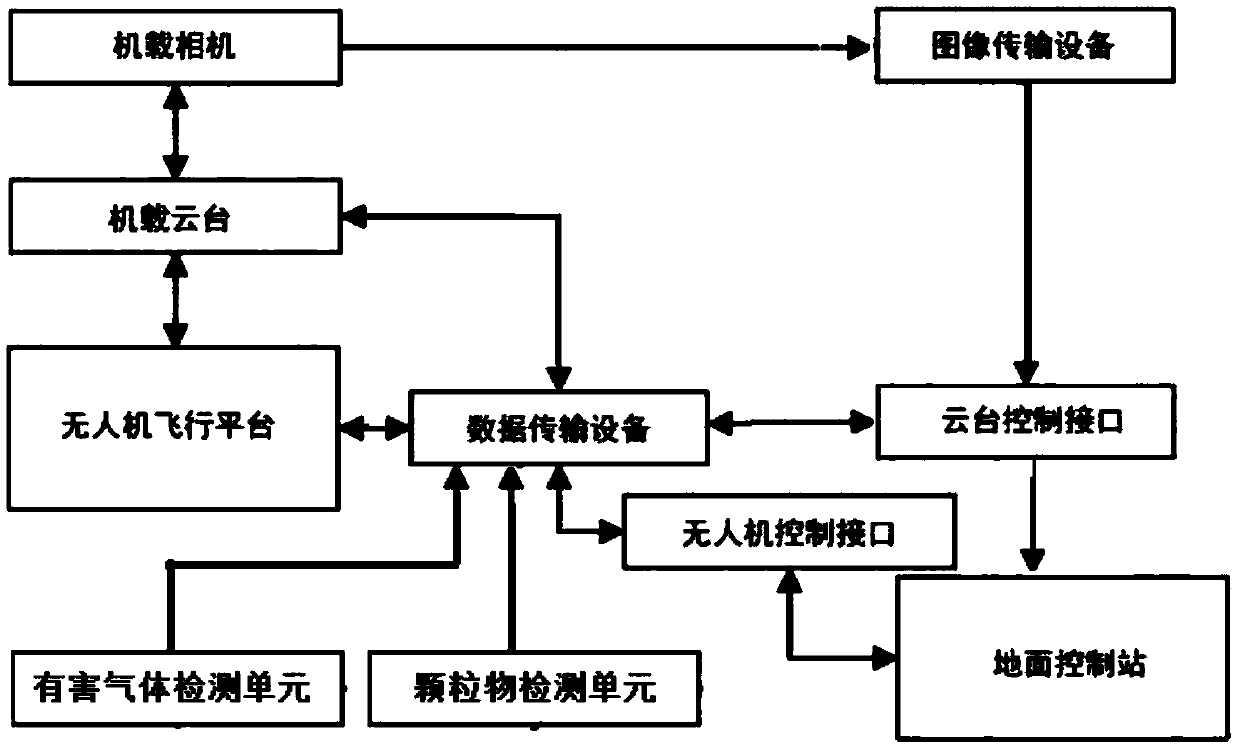
InactiveCN109725108ARapid determinationAccurate measurementParticle suspension analysisParticulatesControl signal
The invention provides an air quality detecting device based on an unmanned aerial vehicle. The device comprises the unmanned aerial vehicle and a ground control station. An unmanned aerial vehicle flight platform is equipped with a harmful gas detecting unit, a particulate matter detecting unit, an unmanned aerial vehicle end of a data transmission unit, an onboard pan-tilt, and an unmanned aerial vehicle end of an image transmission unit. The onboard pan-tilt is equipped with an onboard camera. The ground control station comprises an unmanned aerial vehicle control interface and a pan-tilt control interface. The harmful gas detecting unit, the particulate matter detecting unit, the onboard pan-tilt and the unmanned aerial vehicle flight platform transmit harmful gas detection data, particulate matter detection data and the state data of the onboard pan-tilt to the ground control station through the data transmission unit respectively. The unmanned aerial vehicle end of the data transmission unit transmits a control signal sent by the ground control station to the unmanned aerial vehicle flight platform and the onboard pan-tilt. The device provided by the invention can quickly andaccurately measure the air quality in a wide range, transmits an air quality measurement result to the ground control station in real time, and at the same time carries out image forensics on an abnormal air quality area.
Owner:NANJING KAITIANYAN UAV TECH CO LTD
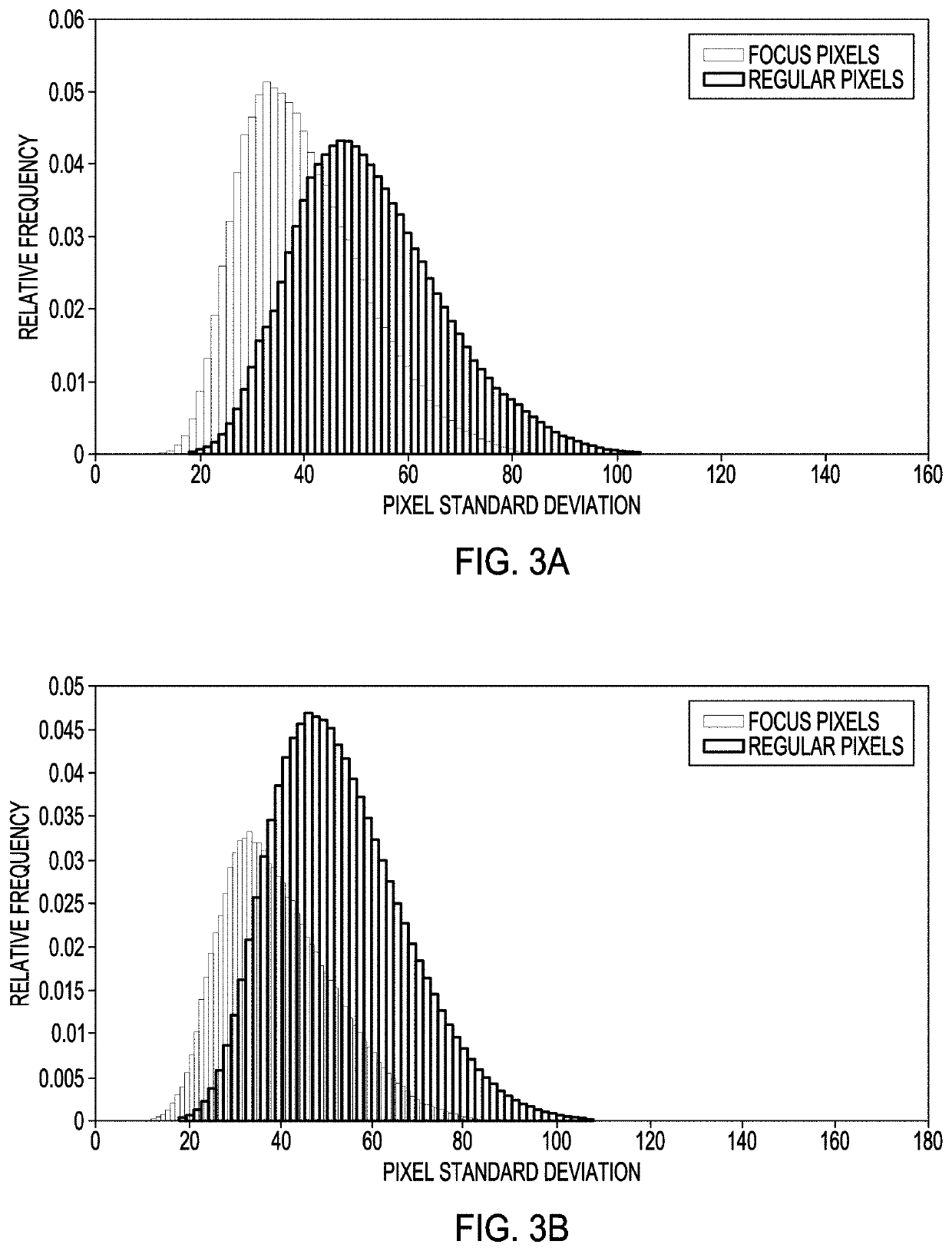
Image forensics using non-standard pixels
ActiveUS11288537B2Eliminate shiftingCharacter and pattern recognitionNeural learning methodsPattern recognitionComputer graphics (images)
A system and process to determine whether a digital image has been manipulated involves determining expected locations of non-standard pixels in the digital image, and determining a feature for evaluating the non-standard pixels. The feature in pixels of the digital image that are located at the expected locations of non-standard pixels is then measured, and a statistical measure of the feature of pixels in the digital image that are located at the expected locations of non-standard pixels is evaluated. The digital image is assessed to determine a probability that the digital image includes a manipulated portion, based on the statistical measure. The system and process can also determine a make and model of an image sensing device via an examination of the non-standard pixels.
Owner:SERVICES HONEYWELL SLW PATENT
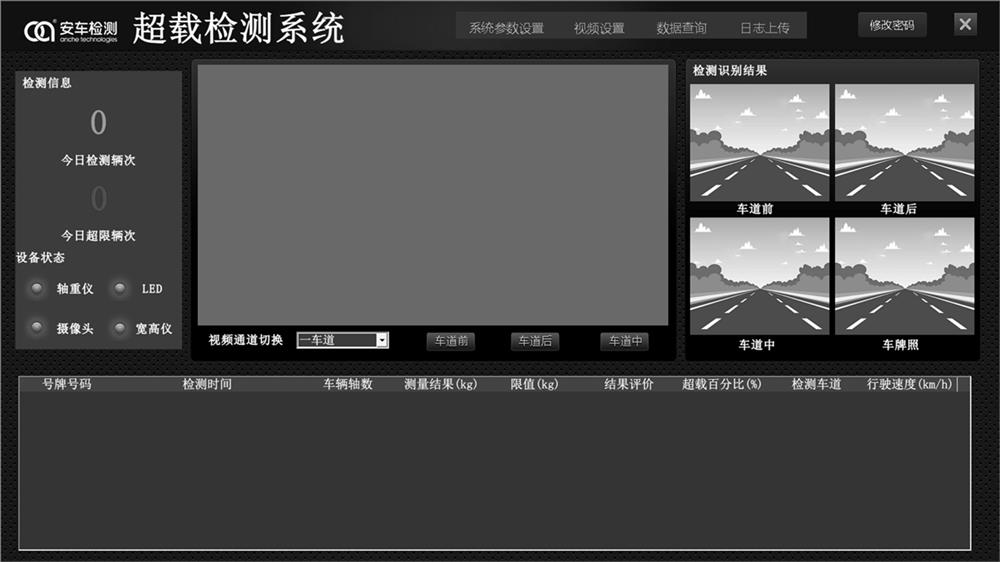
Overload and overlimit width and height measurement system and method for highway governance
PendingCN113744534ADetection of traffic movementClosed circuit television systemsVideo monitoringData processing system
The invention discloses an overload and overlimit width and height measurement system and method for highway governance, and the system comprises a dynamic weighing subsystem which is used for generating vehicle data information when a vehicle passes through a detection region; an image evidence obtaining subsystem used for completing vehicle snapshot and license plate recognition and uploading; a video monitoring subsystem used for monitoring the detection region; and a measurement point location data processing system used for carrying out integration processing and uploading on the data of each subsystem.
Owner:SHENZHEN ANCHE TECH
Face changing forgery detection method, system and equipment based on three-dimensional shape of human face
The invention belongs to the field of face exchange images, computer vision and image evidence obtaining, particularly relates to a face exchange forgery detection method, system and equipment based on a face three-dimensional shape, and aims to solve the problems that the prior art is easily attacked by post-processing operation and a non-homologous face forgery method, and the robustness and generalization of a model are not high, so that the face forgery detection accuracy is low and even the face forgery cannot be detected. The method comprises: extracting a figure face appearance to determine a figure identity; acquiring a facial three-dimensional shape feature template of the corresponding character from the registration reference set; extracting facial three-dimensional shape features of the image to be detected through 3DMM; calculating the mahalanobis distance between the two images, and if the mahalanobis distance is smaller than a true and false judgment threshold, determining that the image is a real face image and otherwise, faking the image for face changing. The forged sample can be detected from the real face image, and meanwhile, the anti-interference capability of the detection model on various post-processing operations and the generalization capability of a forging method which is not homologous with training data are effectively improved.
Owner:INST OF AUTOMATION CHINESE ACAD OF SCI
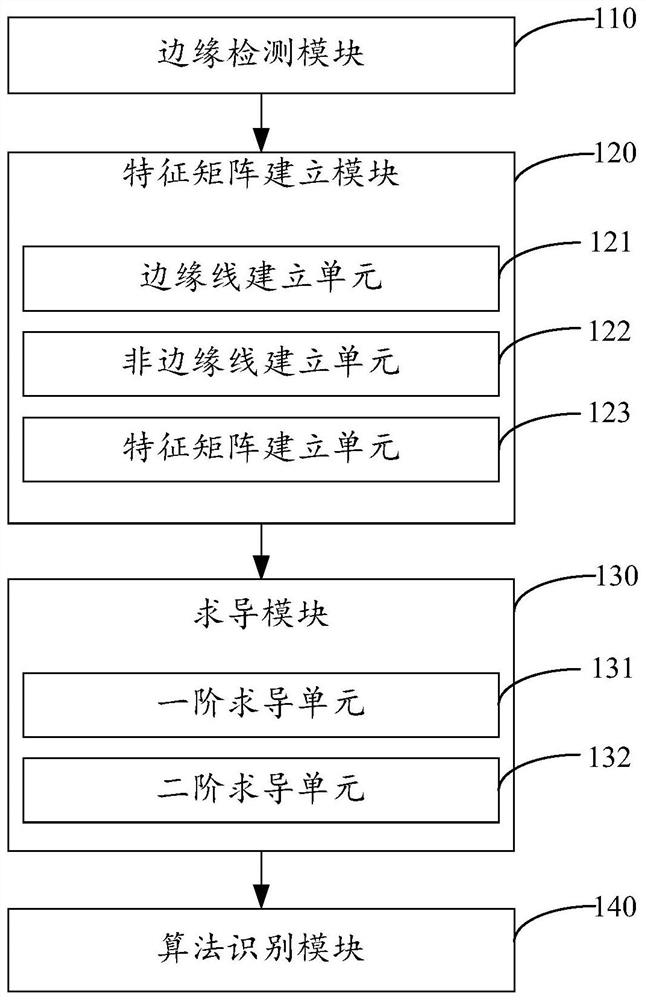
Image smoothing detection method and device
ActiveCN110874845BSmoothing detection worksImprove accuracyImage enhancementImage analysisPattern recognitionImaging processing
The present invention is applicable to the technical field of image processing, and provides an image smoothing detection method and device. The method includes: performing edge detection on an image, determining edge points, extracting pixels of the edge points, and establishing a feature matrix, and calculating the Deriving the feature matrix to obtain the feature derivative matrix, classifying and identifying the feature derivative matrix through a classification algorithm, determining the smoothing algorithm used for the image, realizing effective detection of image smoothing, and improving image smoothing The accuracy of automated detection further improves the effectiveness of image forensics.
Owner:SHENZHEN INST OF ADVANCED TECH CHINESE ACAD OF SCI
Remote intelligent evidence obtaining system and method based on mobile internet
InactiveCN111064856AEnsure safetyGuaranteed confidentialityData processing applicationsPictoral communicationComputer networkConfidentiality
The invention belongs to the technical field of mutual inductors, and particularly relates to a remote intelligent evidence obtaining system and method based on the mobile Internet, and the system comprises an evidence obtaining end, a transmission end, and a cloud storage end. The evidence obtaining end is used for obtaining evidences of images and voices to obtain evidence obtaining informationand transmitting the evidence obtaining information to the transmission end; the transmission end is used for encrypting the evidence obtaining information and sending the encrypted evidence obtaininginformation to the cloud storage end; the cloud storage end is used for storing the received encrypted evidence obtaining information; the evidence obtaining end comprises an image evidence obtainingunit, a voice evidence obtaining unit, a display and a processor; the processor is in signal connection with the image evidence obtaining unit, the display and the voice evidence obtaining unit. Theremote intelligent evidence obtaining system and method have the advantages of high safety, good confidentiality and good evidence obtaining integrity.
Owner:欣诚信息技术有限公司
Method, system and equipment for face-changing forgery detection based on three-dimensional shape of human face
Owner:INST OF AUTOMATION CHINESE ACAD OF SCI
A Blind Image Detection Method Based on Secondary Seam Cropping Feature
ActiveCN104599279BReduce feature dimensionReduce computational complexityImage analysisCharacter and pattern recognitionComputation complexityImaging processing
The invention provides an image blind detection method based on secondary seam clipping features and belongs to the field of blind image forensics image processing. The method includes: (1) conducting additional seam clipping operation on an image to obtain an additional seam clipping image; (2) conducting feature extraction which includes calculating the similarity feature, the energy ratio feature and the stitch distance difference feature between the image and the corresponding additional seam clipping image; (3) detecting seam clipping through a training support vector machine by utilizing the similarity feature, the energy ratio feature and the stitch distance difference feature which are extracted. The method is low in feature dimension, has lower calculation complexity and meanwhile has higher detection rate.
Owner:TIANJIN POLYTECHNIC UNIV
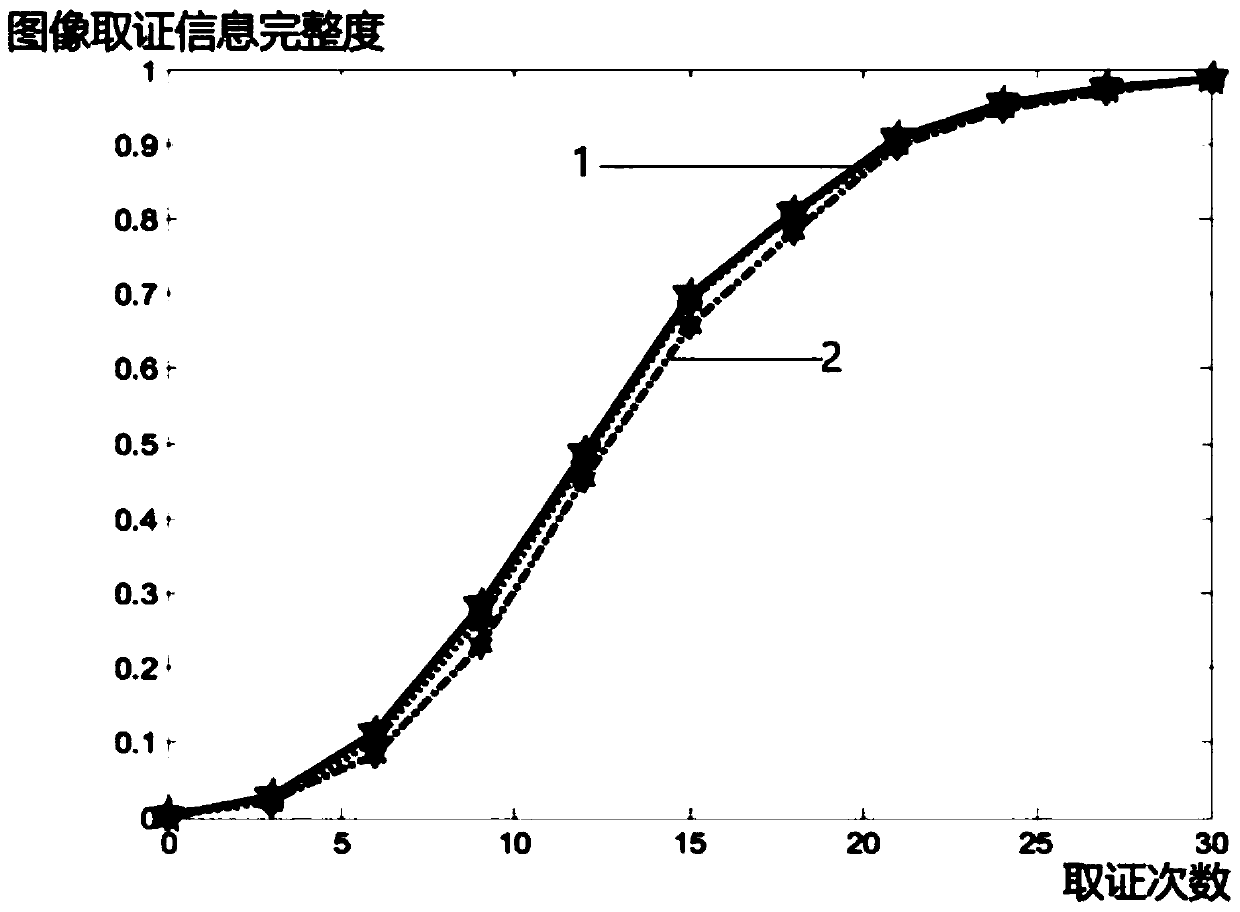
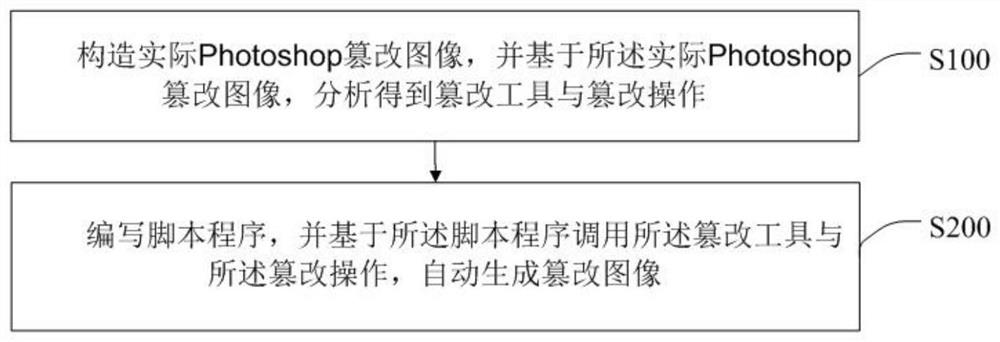
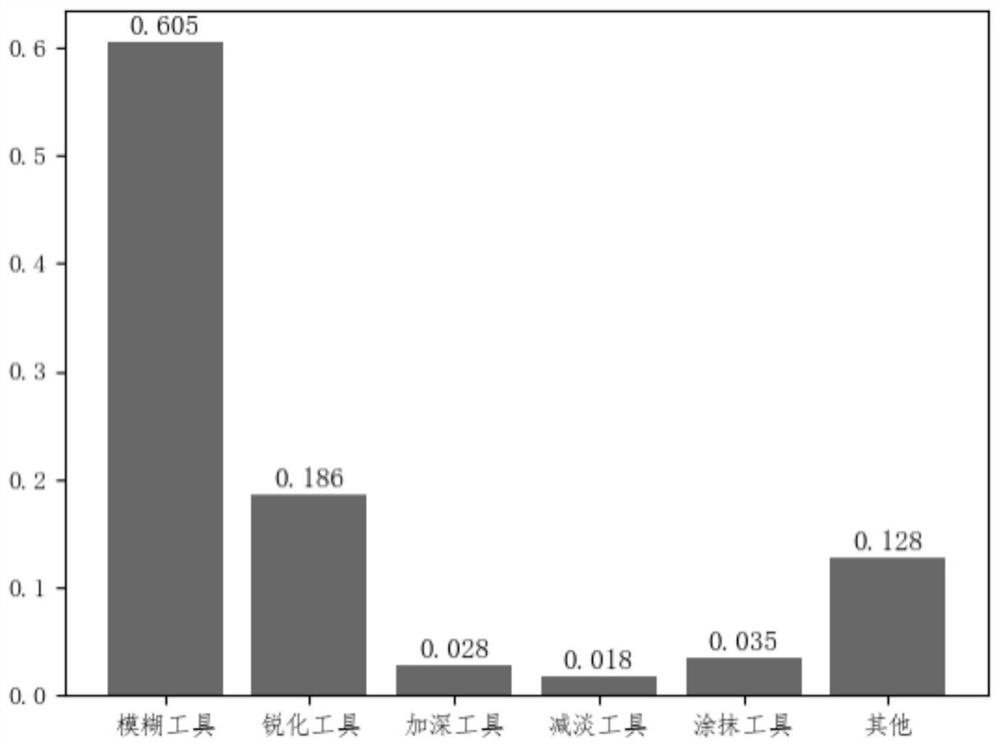
Photoshop tampered image generation method and Photoshop tampered image generation system
PendingCN111915574ASave labor costSave time and costImage enhancementImage analysisComputer graphics (images)Engineering
The invention discloses a Photoshop tampered image generation method and system, and the method comprises the steps: constructing an actual Photoshop tampered image, and obtaining a tampering tool anda tampering operation through analysis based on the actual Photoshop tampered image; writing a script program, calling the tampering tool and the tampering operation based on the script program, andautomatically generating a tampered image. According to the method, a large amount of manpower and time cost for generating the tampered image can be saved, and the method can play an important role in an image evidence obtaining method based on deep learning.
Owner:SHENZHEN UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com