Image authenticity identification method and application thereof in certificate identification
An image, authenticity technology, applied in image enhancement, image analysis, image data processing, etc., can solve problems such as deformation, falsified area boundary feature destruction, etc., and achieve the effect of improving accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
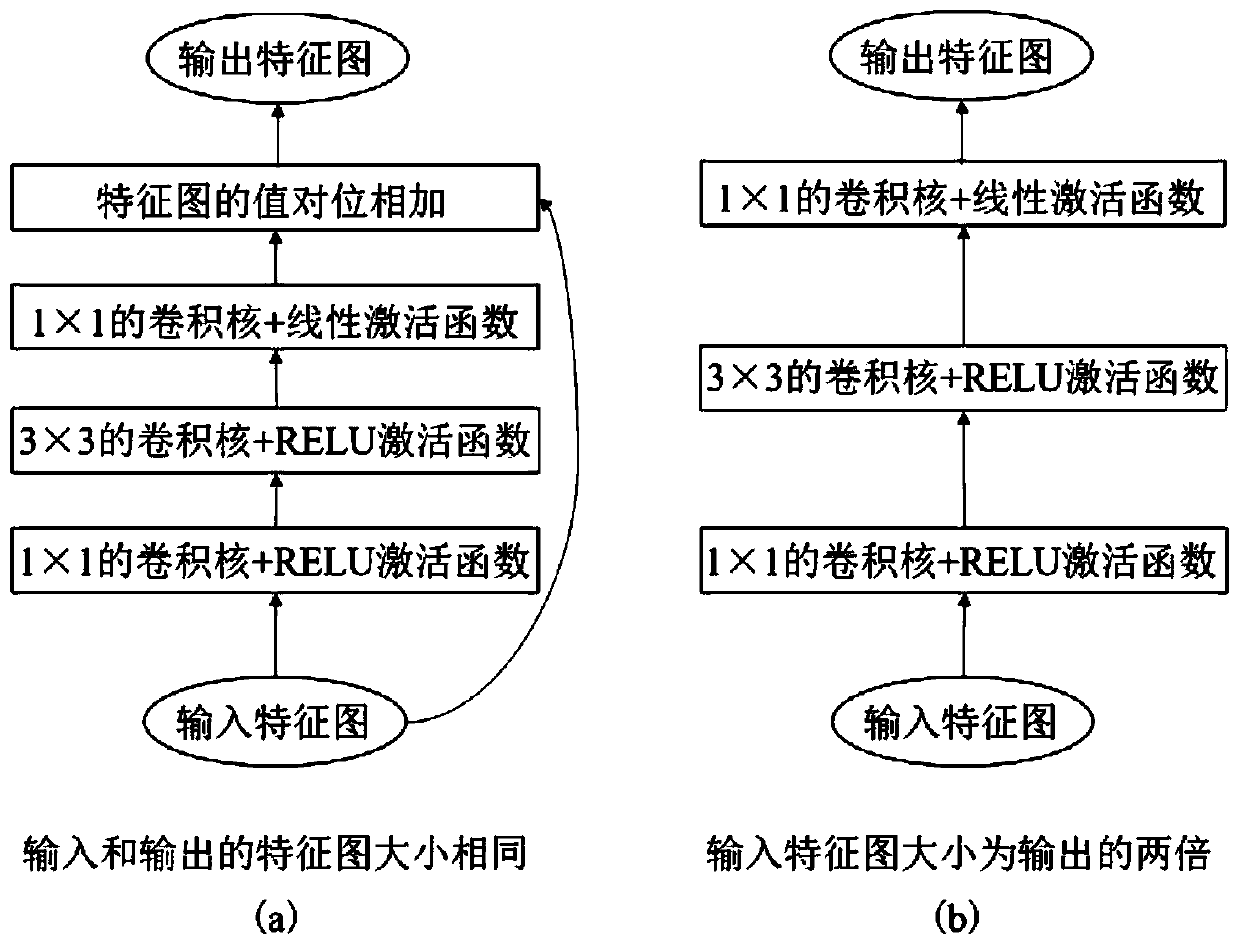
Method used
Image
Examples
Embodiment 1
[0084] The following will introduce our model training process. First, we will introduce the processing process of the data set CASIAv2.0 used for model training, and then introduce the hyperparameters and specific steps we use in the training process.
[0085] Processing of datasets
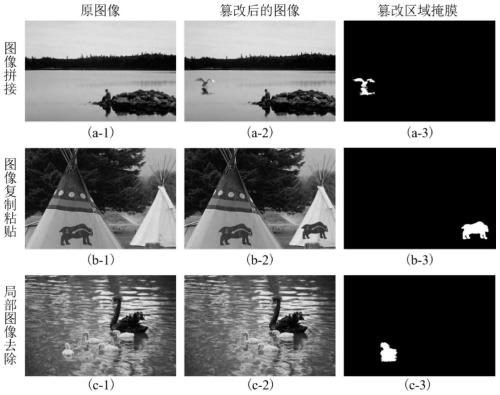
[0086] The application of deep learning in the field of image forensics is not very extensive. In the field of image forensics, there is no data set containing millions of pictures like ImageNet. The largest data set in the field of image forensics is CASIA v2.0[Dong J, Wang W, Tan T.Casia image tampering detection evaluation database[C] / / 2013IEEE China Summit and International Conference on Signal and Information Processing.IEEE,2013:422 -426.], this data set consists of 7491 original pictures and 5123 tampered pictures. The pictures in the data set have various shooting scenes and rich types of objects. The tampered pictures in CASIA v2.0 are all synthesized by Adobe Photoshop CS3 software. T...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com