Information evidence collection method for Internet of things
An Internet of Things and headprint technology, applied in the field of information security, can solve the problems of misappropriation of intellectual property rights, Internet of Things deception, and difficulty in collecting effective evidence, and achieve the effect of ensuring security and confidentiality.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0035] The present invention will be further described in detail below in conjunction with the embodiments and the accompanying drawings, but the embodiments of the present invention are not limited thereto.
[0036] like figure 1 , figure 2 , image 3 shown, including the following steps:
[0037] Step 1. Enter the forensics start mode of the Internet of Things;
[0038] Step 2. When the start mode of step 1 is set, anyone must pass identity verification before using the Internet of Things, and the identity verification includes image verification and headprint verification;
[0039] Step 21, image forensics mode:
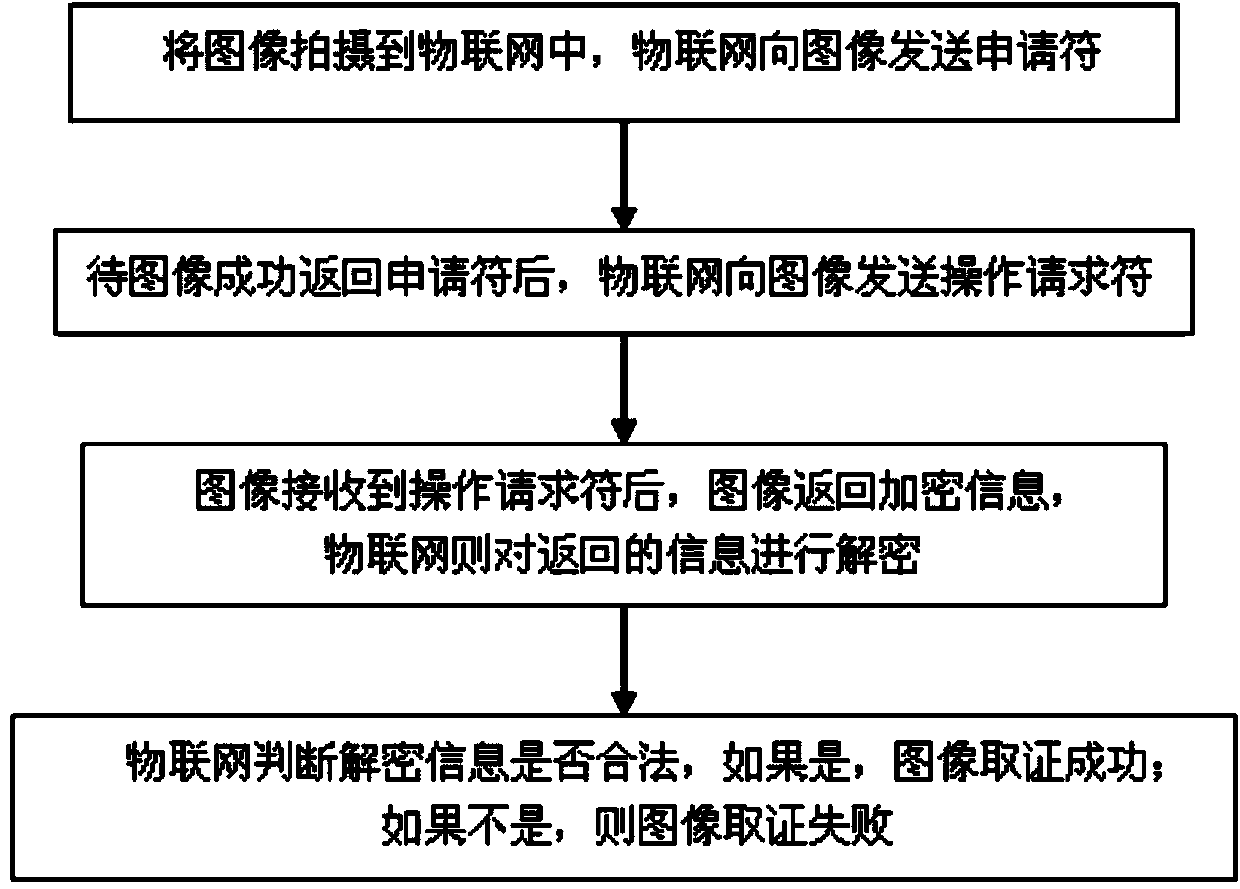
[0040] After successfully setting up this forensic mode, when entering the identity forensics interface, the user needs to take an image to start the IOT smoothly; otherwise, the IOT will stay in the forensics stage and cannot perform any operations;
[0041] Step 22. Forensics mode of forehead tattoo
[0042] After successfully setting this forensic mode, ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com