Cloud data encryption method
An encryption method and cloud data technology, applied in the field of cloud data security management, can solve problems such as public key cryptographic data leakage, and achieve the effects of ensuring security, increasing difficulty, and being easy to distinguish.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0027] The following will clearly and completely describe the technical solutions in the embodiments of the present invention with reference to the accompanying drawings in the embodiments of the present invention. Obviously, the described embodiments are only some, not all, embodiments of the present invention. Based on the embodiments of the present invention, all other embodiments obtained by persons of ordinary skill in the art without creative efforts fall within the protection scope of the present invention.
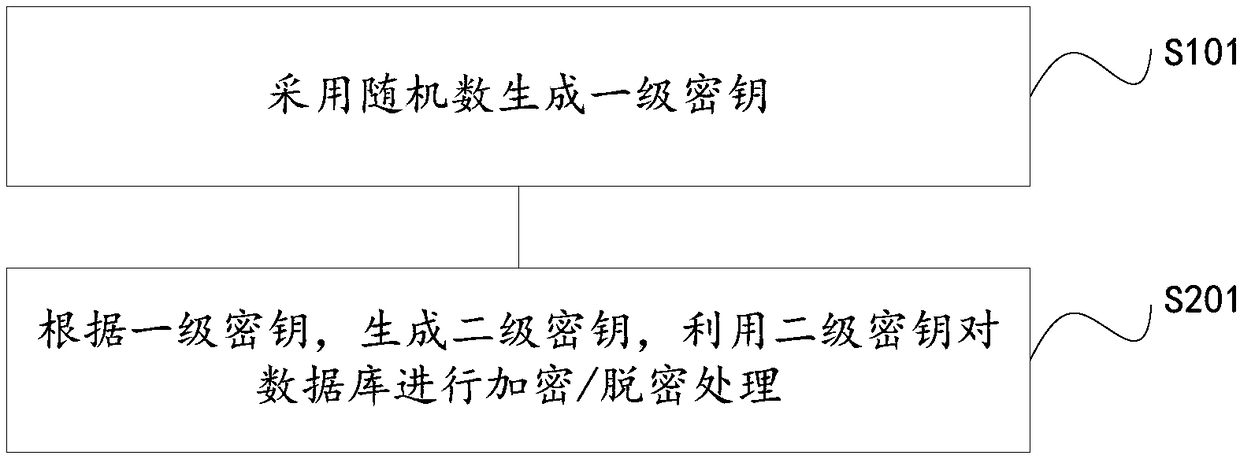
[0028] Such as figure 1 As shown, the cloud data encryption method includes the following steps:
[0029] S101: Generate a first-level key by using a random number;
[0030] S201: Generate a secondary key according to the primary key, and use the secondary key to encrypt / decrypt the database.
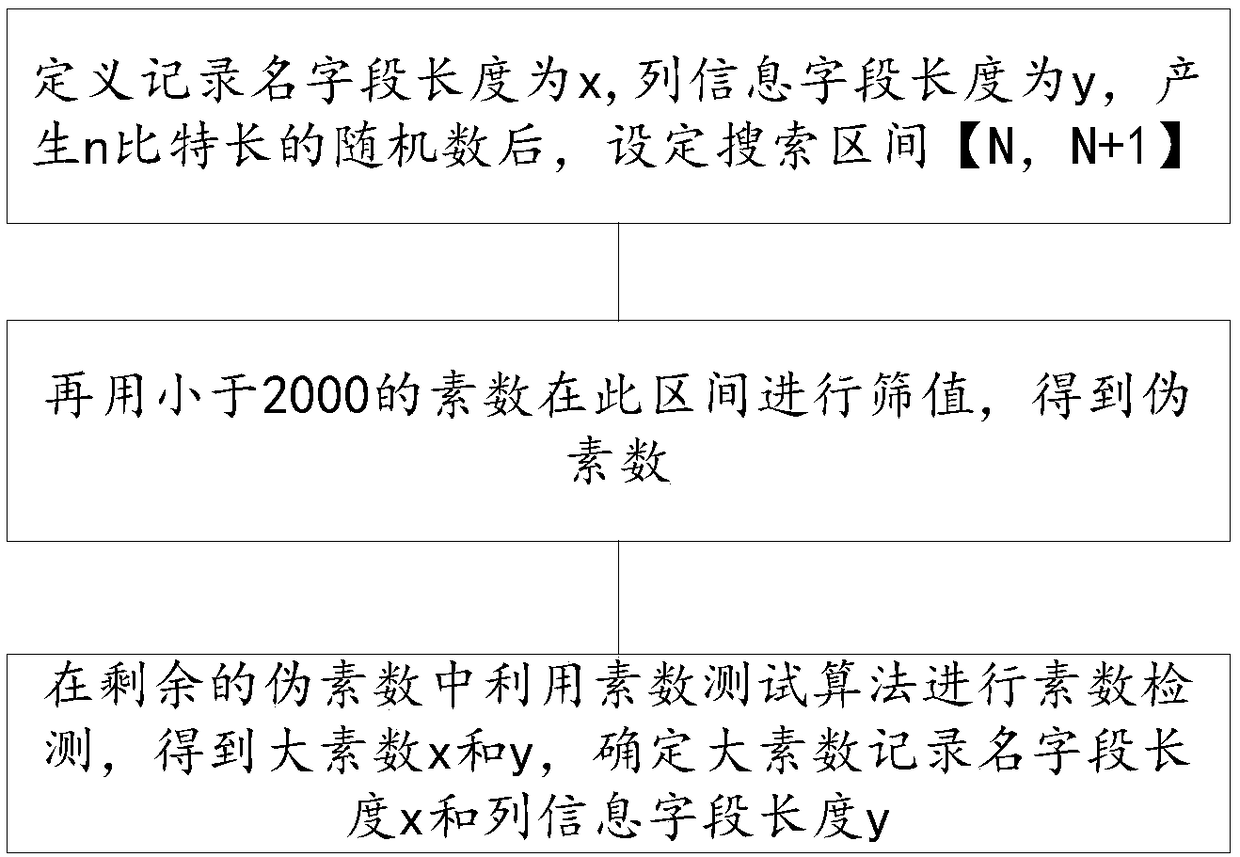
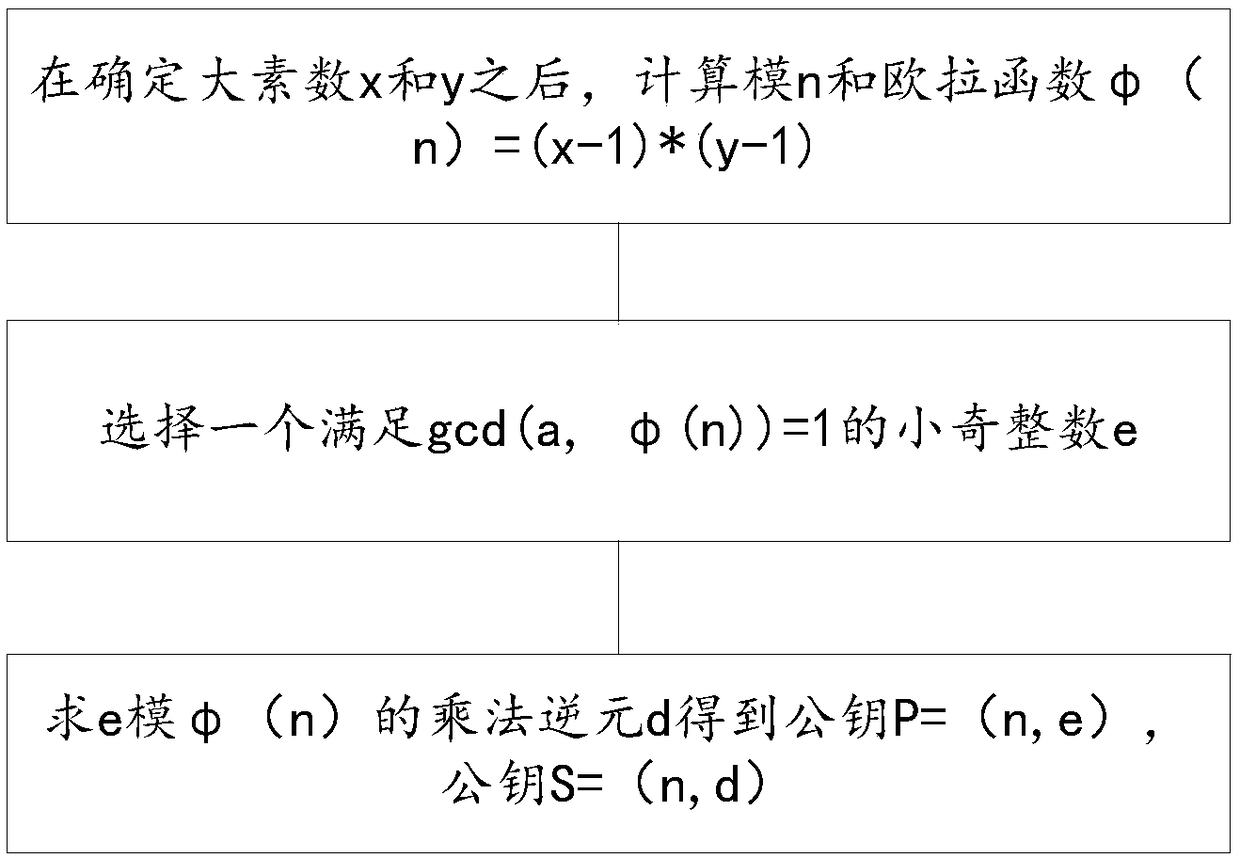
[0031] The secondary key includes a number of record name fields that need to be checked and stored in the database table and column information fields that are temporaril...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com