Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
79 results about "Data access object" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
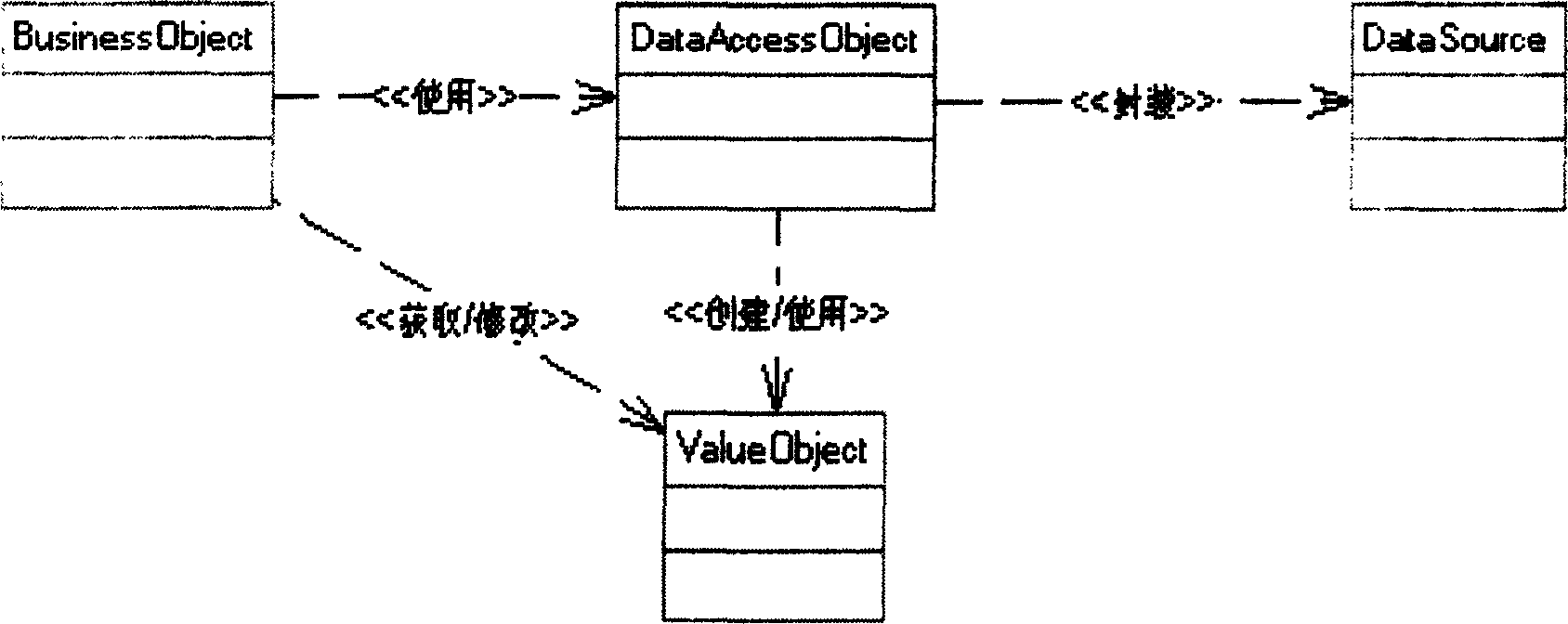
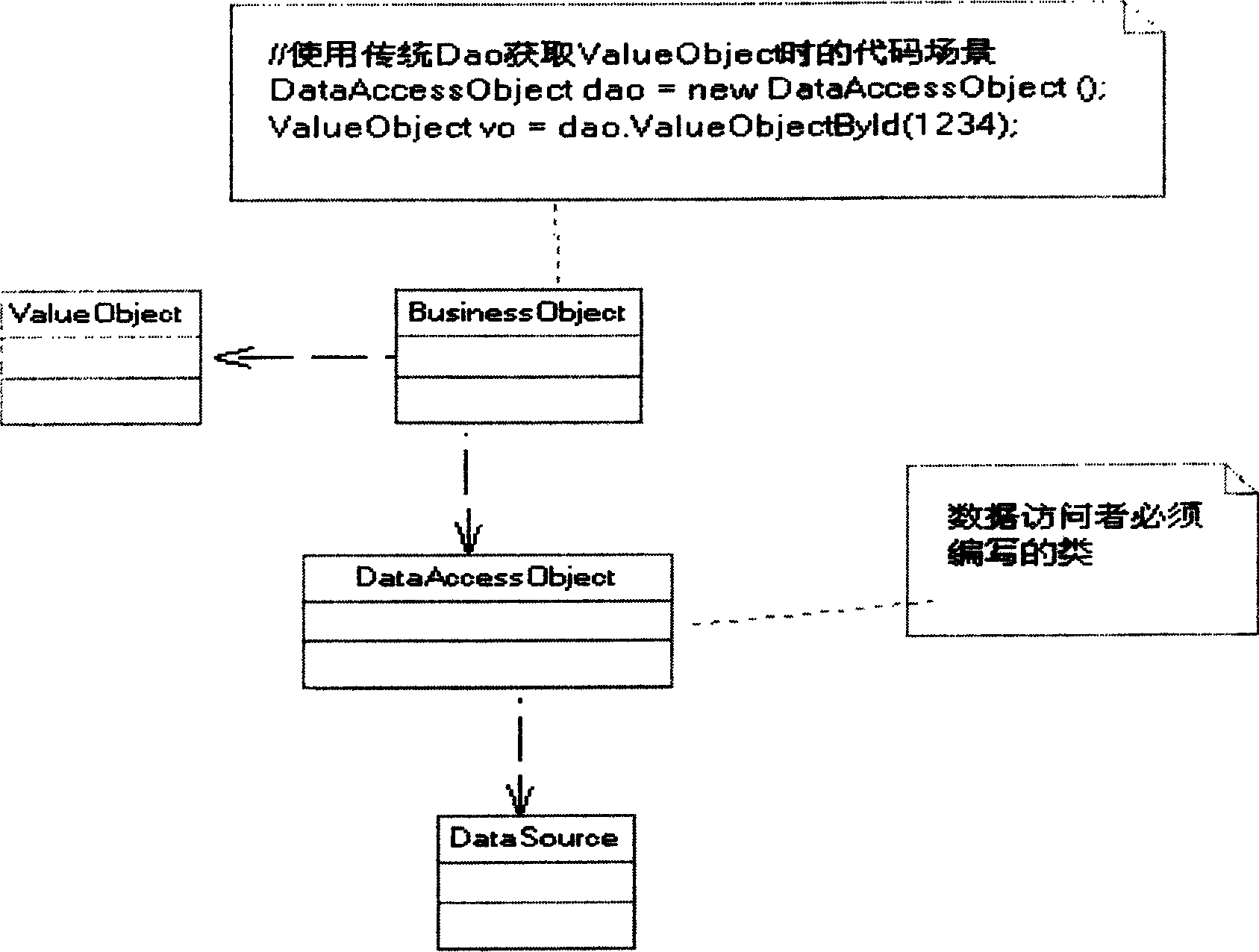
In computer software, a data access object (DAO) is an object that provides an abstract interface to some type of database or other persistence mechanism. By mapping application calls to the persistence layer, the DAO provides some specific data operations without exposing details of the database. This isolation supports the single responsibility principle. It separates what data access the application needs, in terms of domain-specific objects and data types (the public interface of the DAO), from how these needs can be satisfied with a specific DBMS, database schema, etc. (the implementation of the DAO).
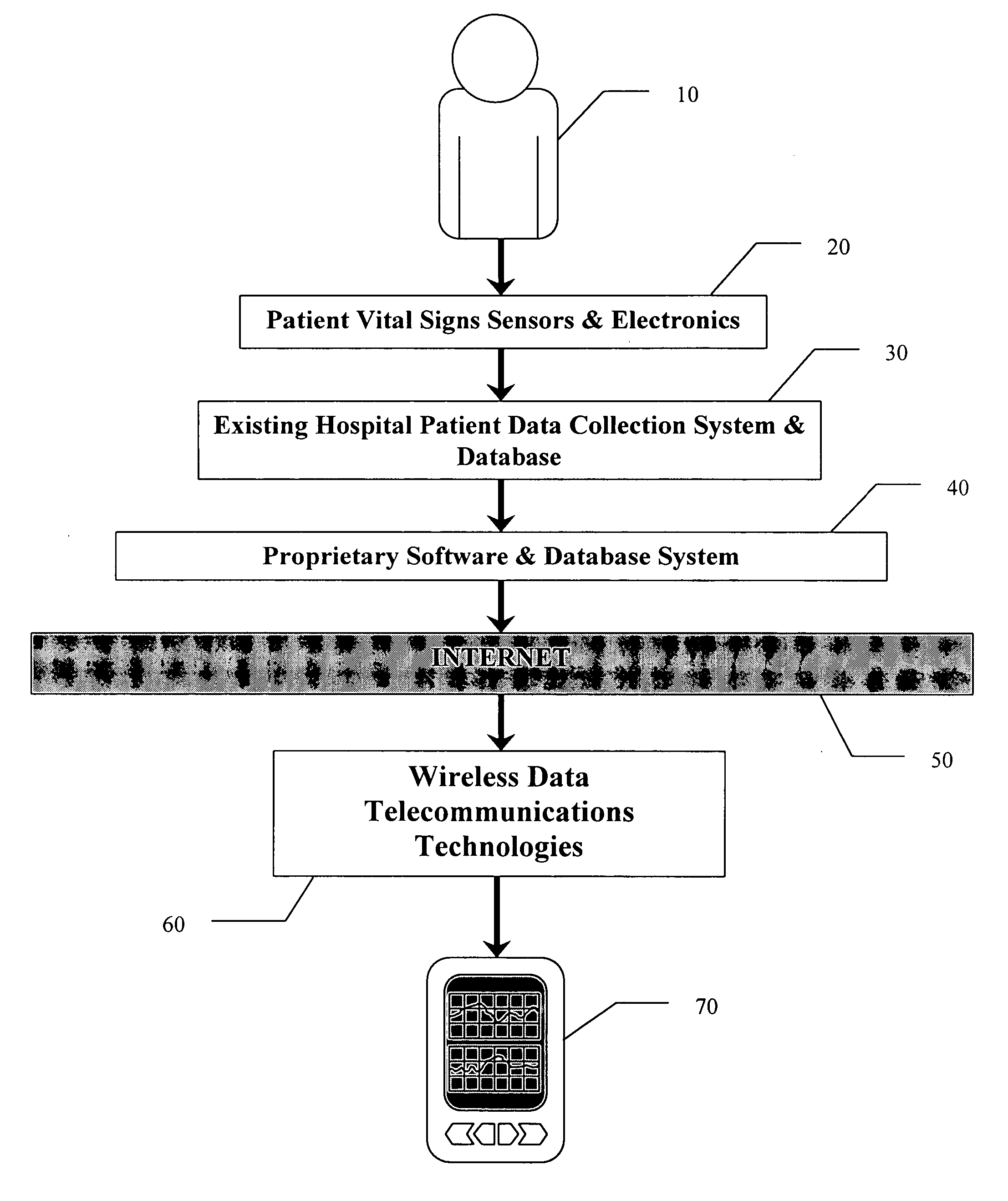
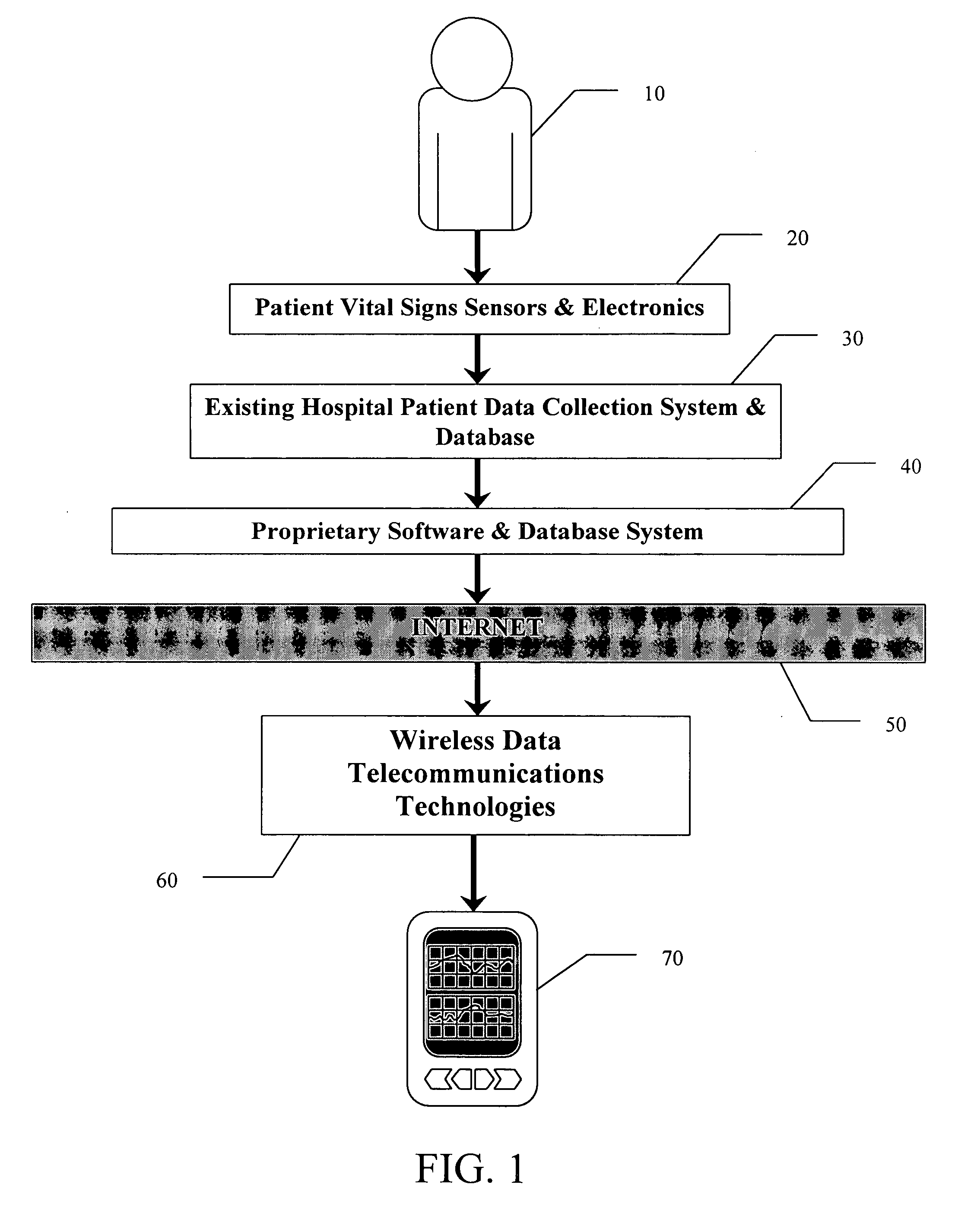
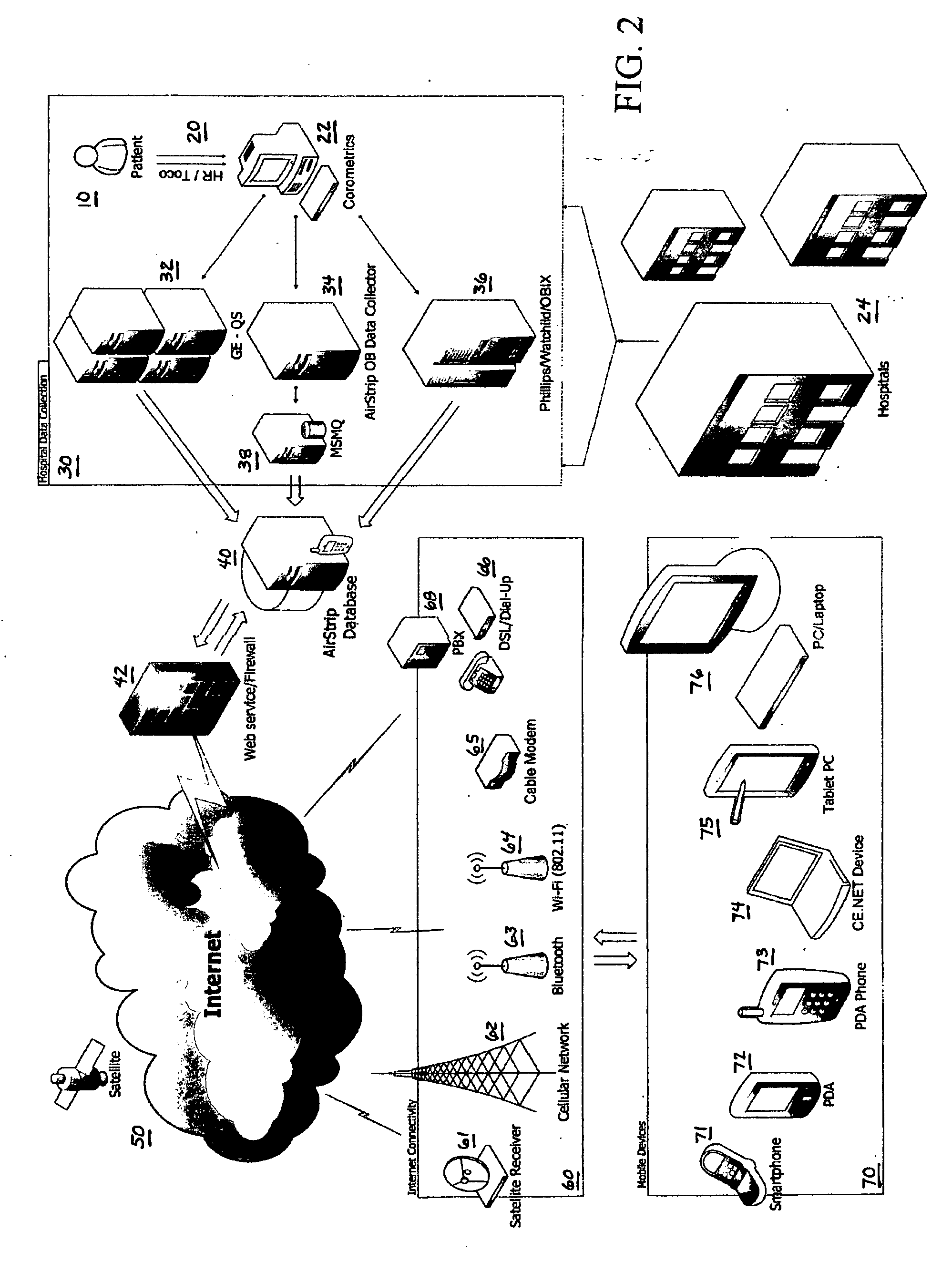
System and method for real time viewing of critical patient data on mobile devices
ActiveUS20060149597A1Improve performanceImprove usabilityMeasurement devicesLocal control/monitoringData accessPatient data
A data processing tool for the viewing of real-time, critical patient data on remote and / or mobile devices. The tool efficiently renders graphical data on the screen of the remote device in a manner that makes it practical for the health care provider to accurately and timely review the data for the purpose of making an informed decision about the condition of the patient. Charting control is established and implemented using the latest GDI+, GAPI and PDA drawing techniques. The charting components provide landscape support, an ability to overlay patient data and patient images, zoom in / zoom out, custom variable speed scrolling, split screen support, and formatting control. The methodology operates as an asynchronous application, without sacrificing crucial processing time in the mobile / handheld device. The methodology allows the critical patient data to be streamed in real-time to the handheld device while conserving enough CPU power to simultaneously allow the end user to interact at will with the responsive display application. The methodology is structured using object oriented concepts and design patterns. Each logical tier of the methodology, from the data access objects and the charting control objects, to the user interface objects, is structured with precise interfaces. Finally, the methodology implements an IT management console that allows system managers to monitor the exchange of data between hospital systems and the primary database, including all patient data packets, notifications and alerts, connected remote devices, etc.
Owner:AIRSTRIP IP HLDG LLC
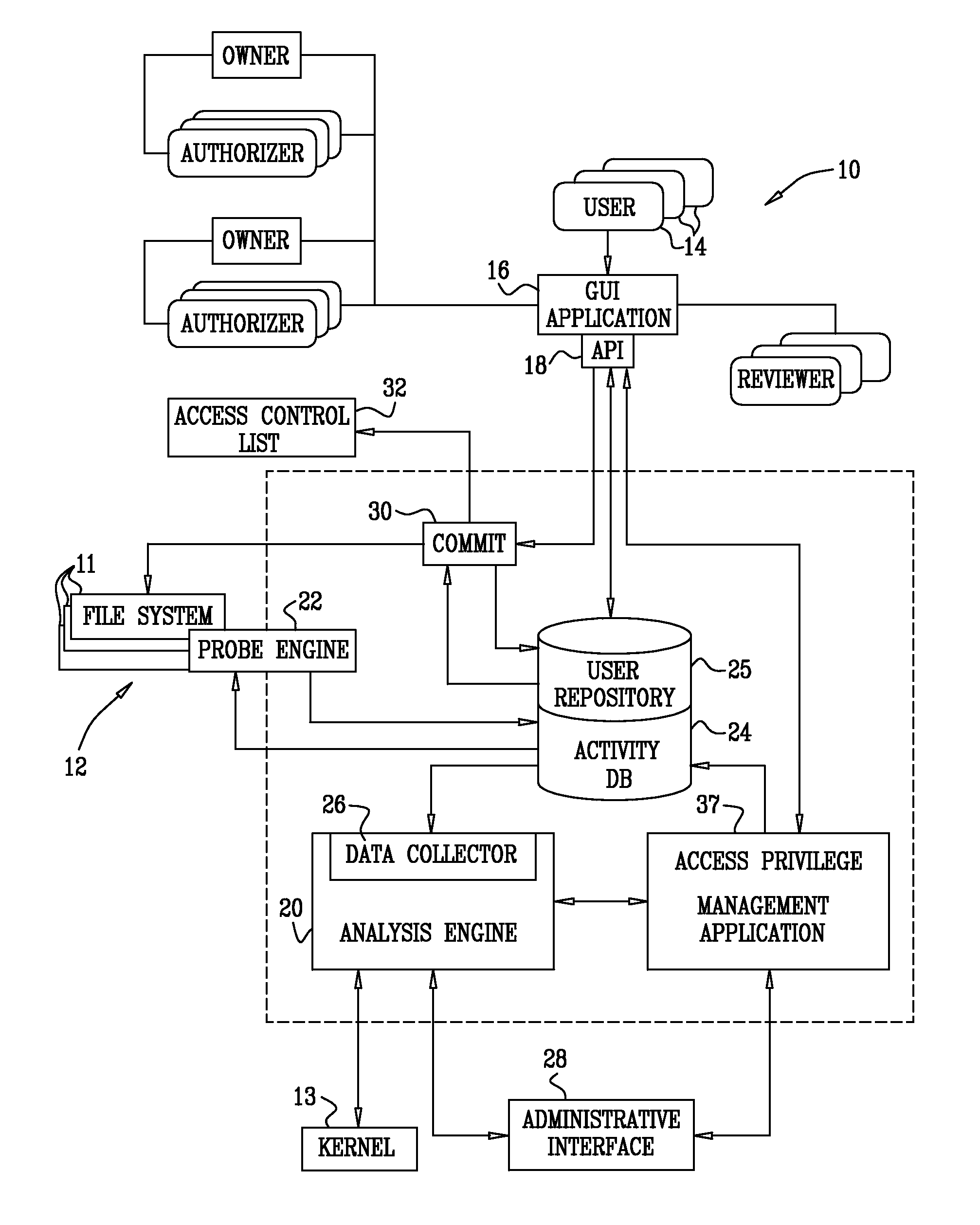
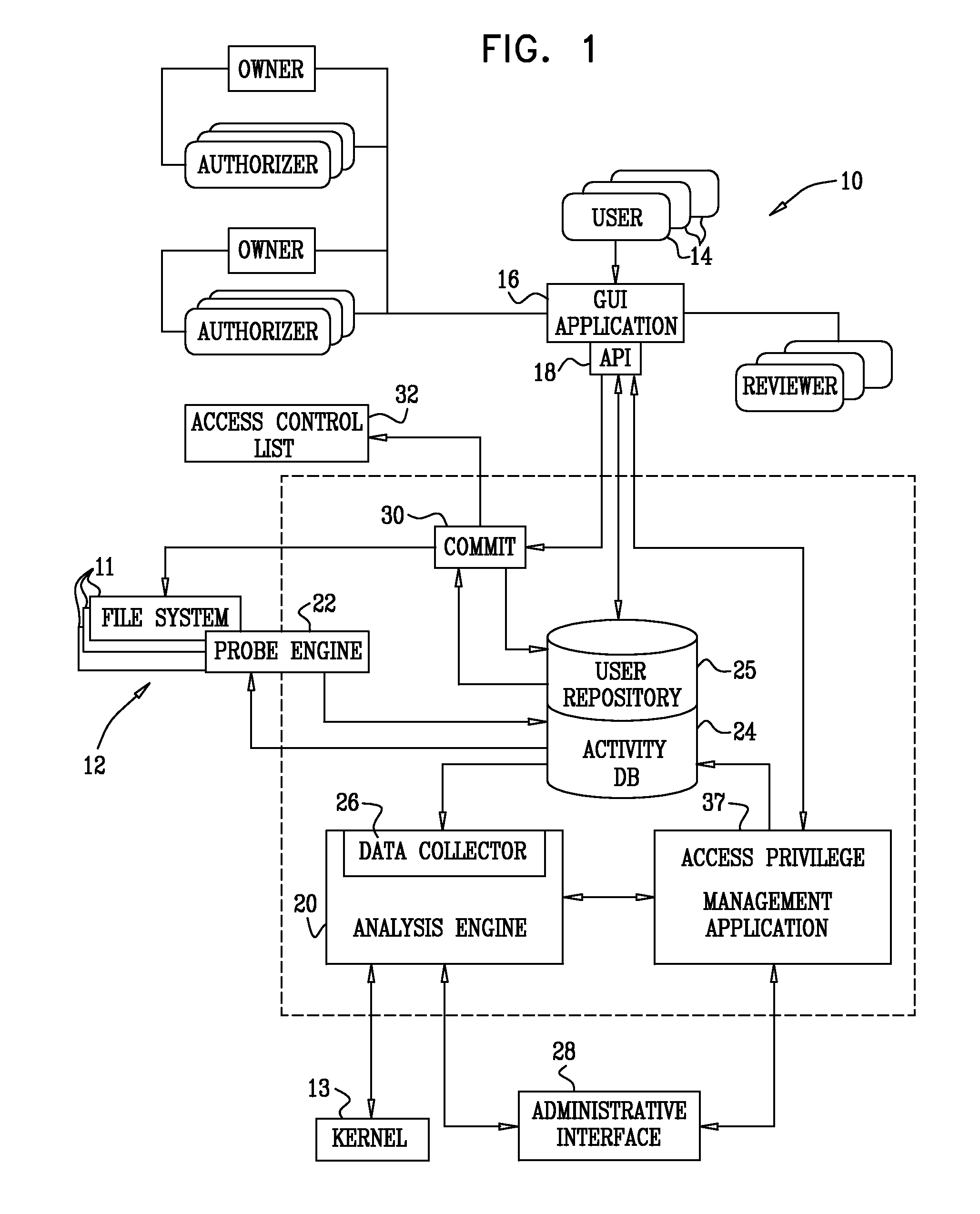
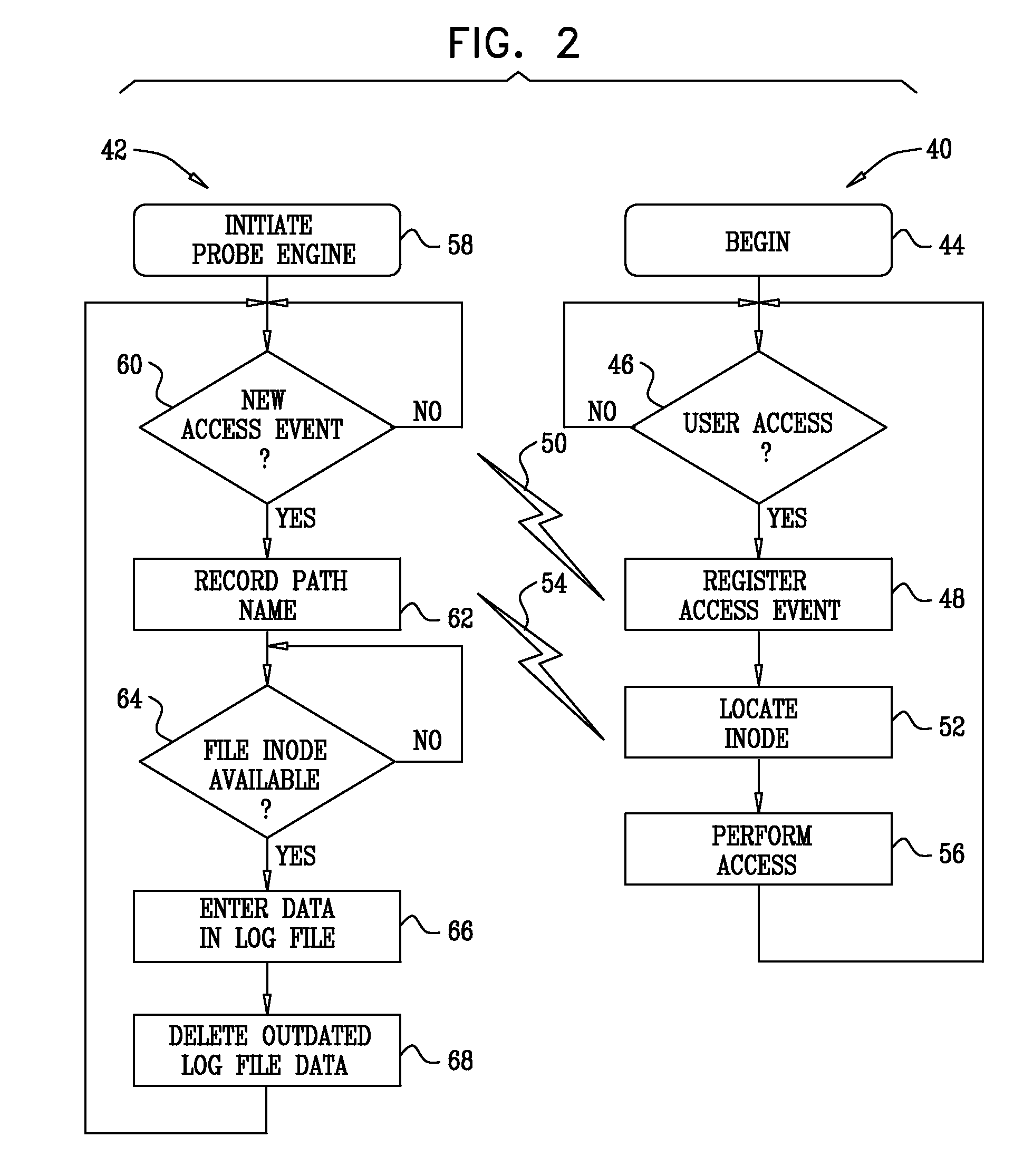
Access event collection
InactiveUS20090265780A1Improve data securityPrevent fraudMemory loss protectionError detection/correctionFile systemData access
On-line and computationally efficient methods and systems are provided for back resolving path names of files from inode numbers during data access request processing. As a result, a near real-time recording of data access events is achieved, including identification of the user who performed the access, and the full path name of the data object that was accessed. In a typical application, access events are collected for use in access control of storage elements in complex organizational file systems.
Owner:VARONIS SYSTEMS
Systems and methods of accessing and updating recorded data via an inter-object proxy
ActiveUS20070156690A1Data processing applicationsDigital data information retrievalData accessData access object
Some embodiments provide a system including a database, two or more data access objects, and a proxy object. In some such embodiments, each data access object has exclusive access privileges to a subset of data within the database. Further each object includes one or more of a read method that provides access to data and a write method that causes data to be stored. In such embodiments, the proxy object accesses data via data access object methods and includes a valuate method, the execution of which causes data to be passed from a data access object to the proxy object.
Owner:SAP AG
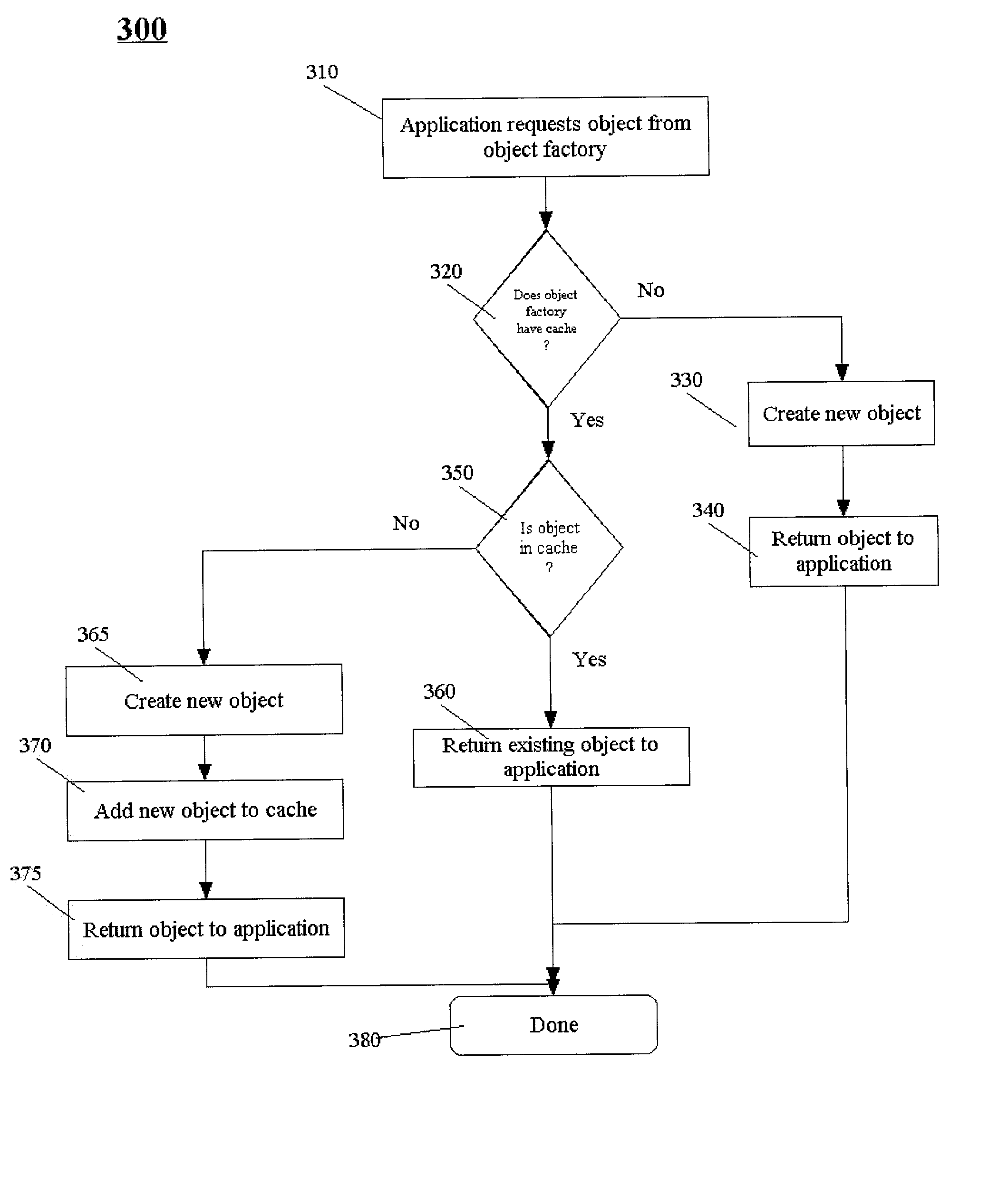
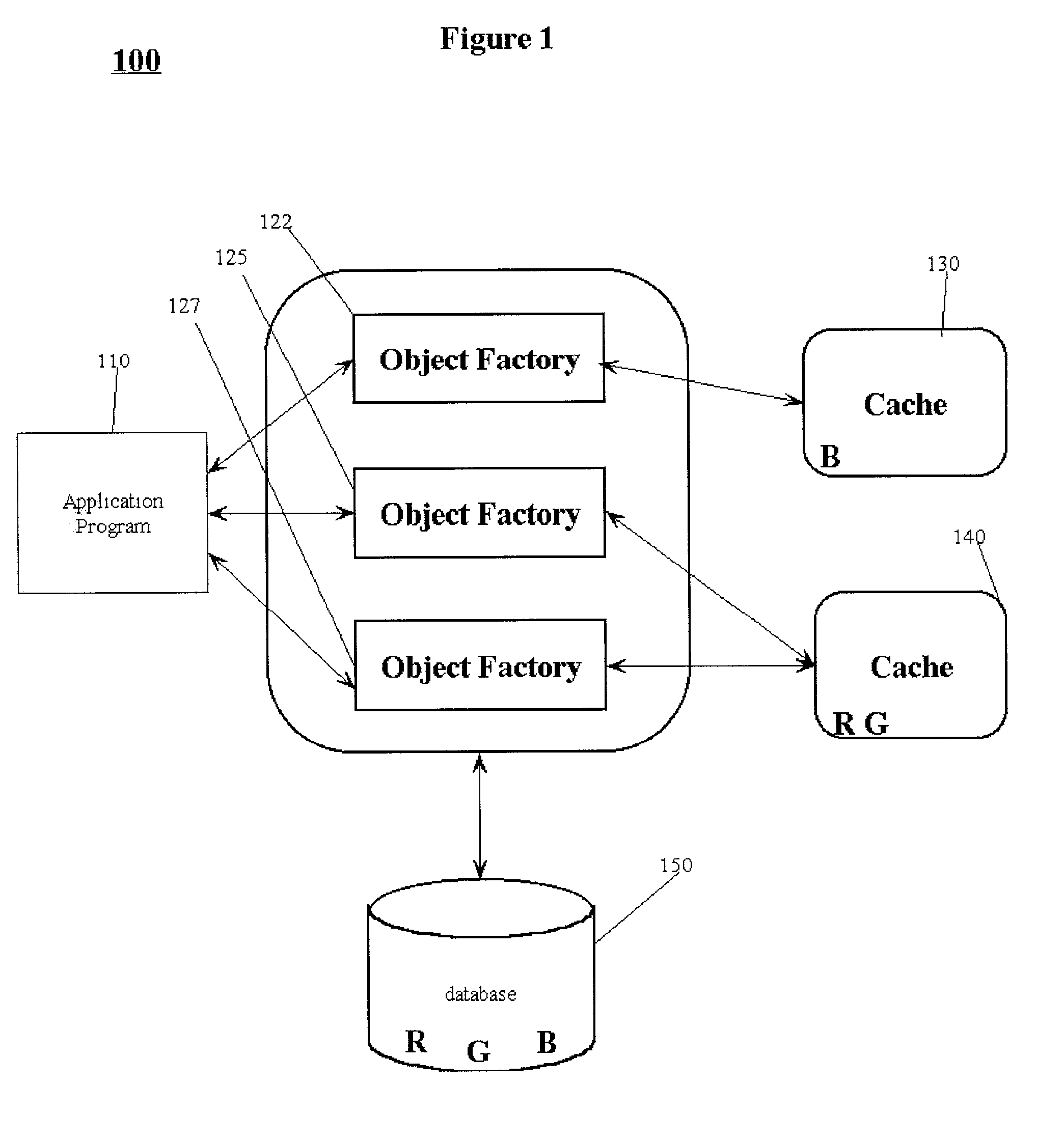
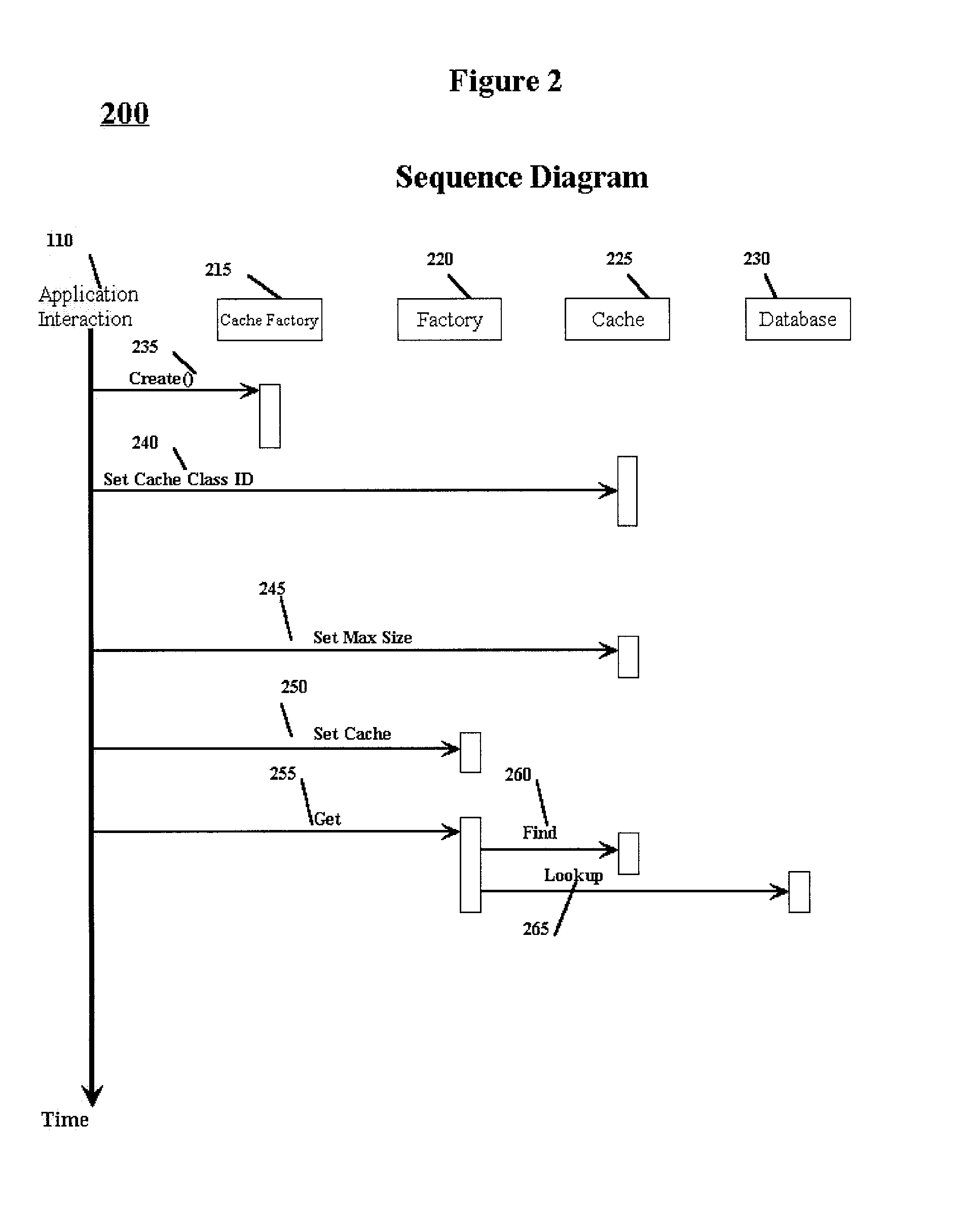
Runtime configurable caching for component factories
InactiveUS20020184612A1Memory adressing/allocation/relocationSpecific program execution arrangementsGeneral purposeParallel computing
A method and structure for allowing object-oriented applications to create and configure caches for the objects used is disclosed. The method and structure use a general purpose cache integrated with object factories that provide the objects used by the application. The object factory can store objects in cache so that application requests for objects are returned in a fast and transparent manner to the calling application. A particular cache may support one or more object factories. The object factory that provides access to a cache is a specialized type of object factory, called a cacheable factory. The cacheable factory contains methods for adding, removing, and accessing objects in the cache associated with the cacheable factory object.
Owner:HEWLETT PACKARD DEV CO LP
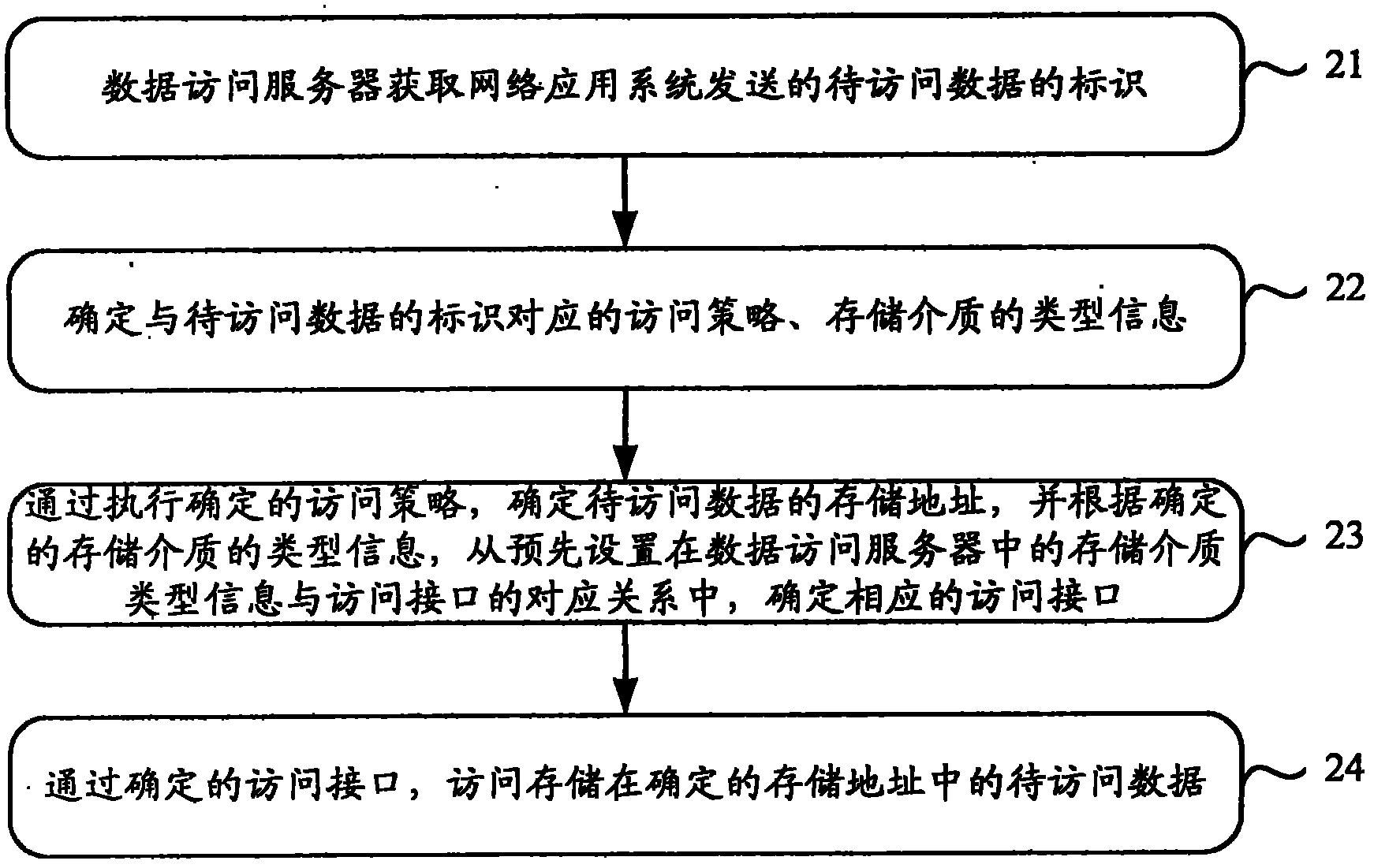
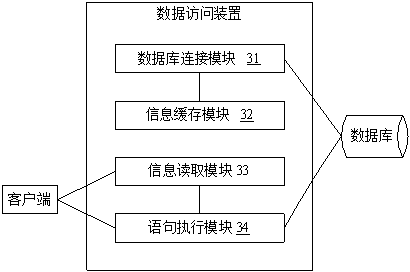
Data access method and device
ActiveCN101958838ASave processing resourcesAchieve accessData switching networksData access objectData information
The invention discloses data access method and device which are used for solving the problem that many processing resources of network application systems are consumed because the data access scheme provided by the prior art requires all the network application systems to set respective DAOs (Data Access Objects). The method comprises the following steps of: acquiring the identifier of data to be accessed sent by at least one network application system by a data access server; determining the type information of an access policy and a storage medium corresponding to the identifier of the data to be accessed according to the correspondence preset in the server between data information and the type information of access policies and storage media; determining the storage access of the data to be accessed through executing the determined access policy, and determining the corresponding access interface from the correspondence preset in the server between the type information of the storage media and the access interface according to the determined type information of the storage medium; and accessing the data to be accessed stored in the determined storage access through the determined access interface.
Owner:UNION MOBILE PAY
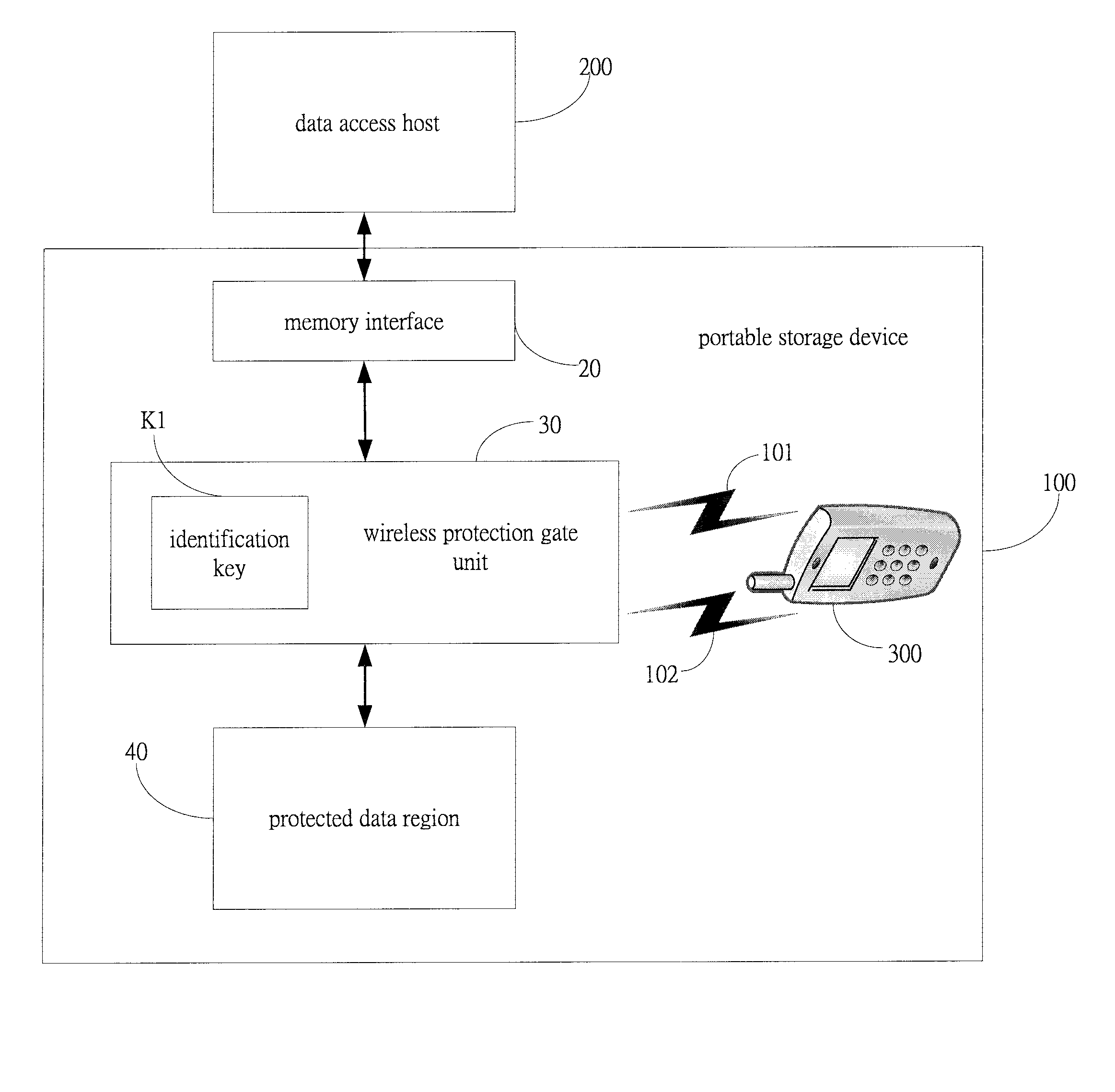
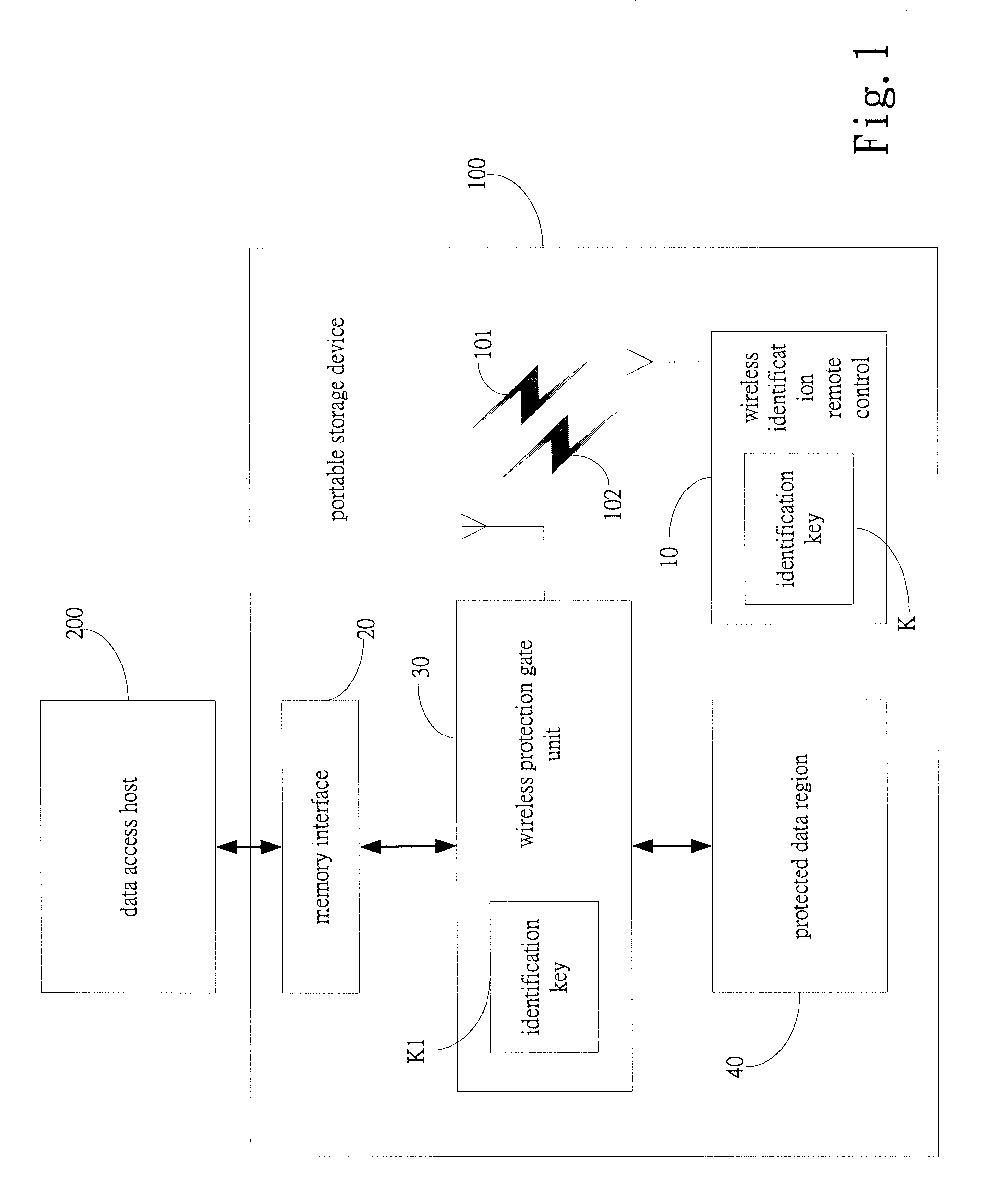
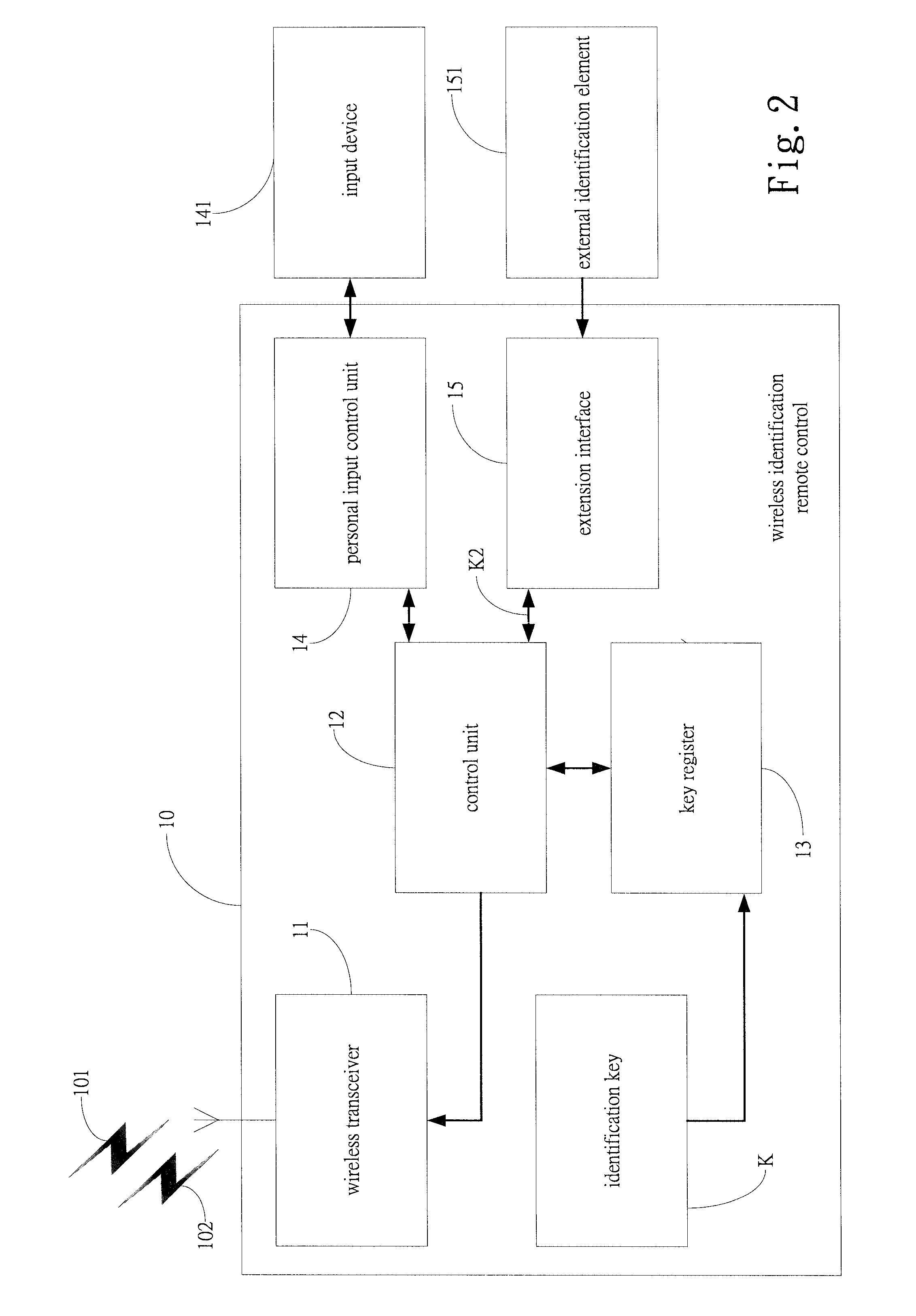
Portable storage device with wireless encryption protection
InactiveUS20080069358A1Accurate and effective mechanismEliminate useUser identity/authority verificationInternal/peripheral component protectionWireless transmissionControl signal
A portable storage device with wireless encryption protection is provided, including wireless identification remote control, for transmitting identification signal and information or lock control signal through wireless transmission, a memory interface connected to a data access host, for inputting decryption information from the data access host and for outputting to data access host, a wireless protection gate unit connected to the memory interface for receiving the identification signal and information or lock control signal issued by the wireless identification remote control, and enabling or disabling the data transmission to the memory interface according to the identification result, and at least a protected data region connected to the wireless protection gate unit, for the protected data region to output data to data access host when the wireless protection gate unit being enabled, so that the portable storage device can achieve the objects of accurate and permanently effective wireless encryption.
Owner:GENESYS LOGIC INC
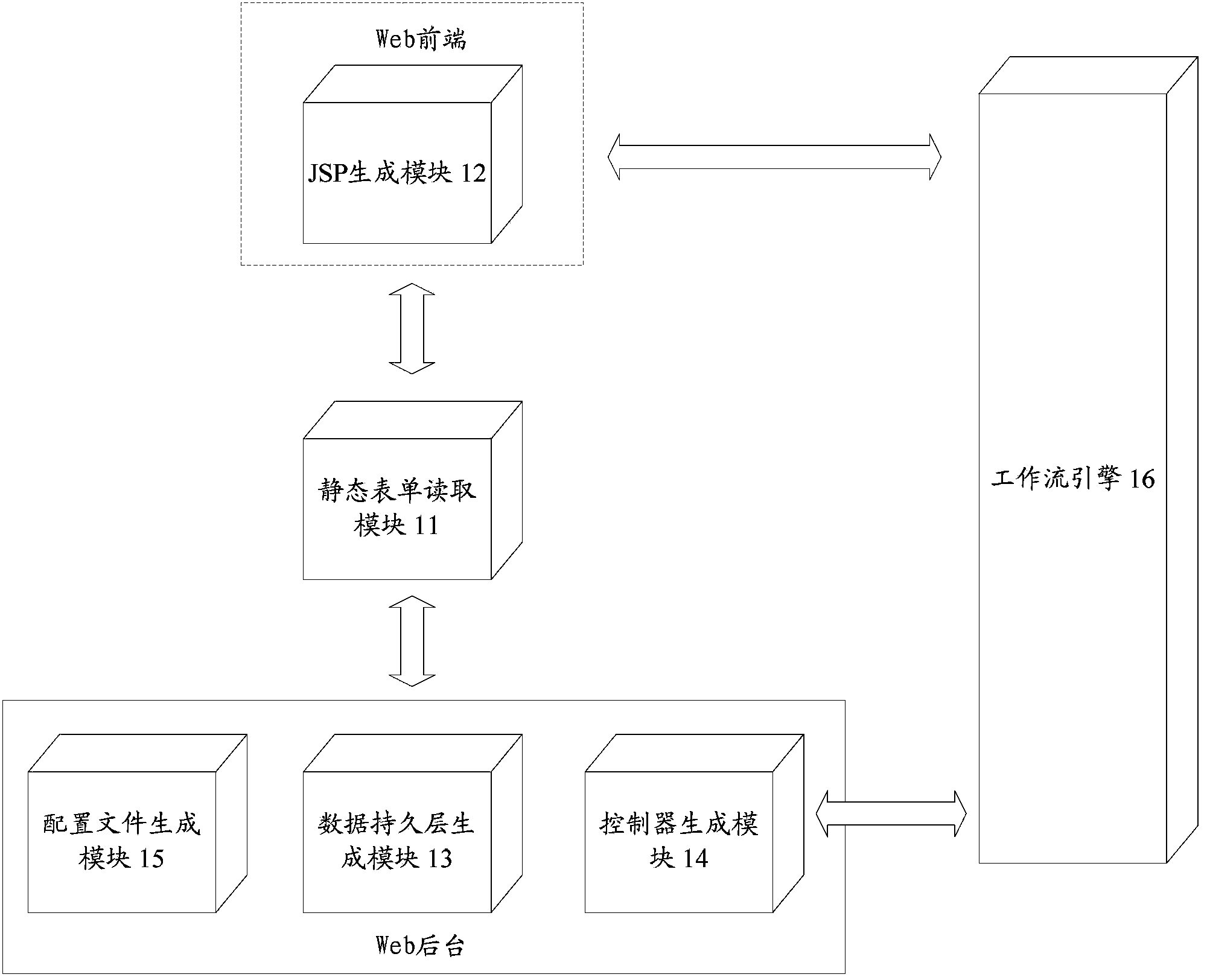
Code generation method and system
ActiveCN103383645AQuality improvementImprove efficiencySpecific program execution arrangementsItem generationJava class file
The invention discloses a code generation method and system. The code generation system comprises a static state sheet reading module, a Java server page (JSP) generation module, a data persistence layer generation module, a controller generation module and a configuration file generation module. The JSP generation module generates view JSP files, the data persistence layer generation module generates simple JAVA object (POJO) type files and data access object (DAO) type files, the controller generation module generates controller Java type files, and the configuration file generation file generates extensible markup language (XML) configuration files. By adopting the code generation method and system, service codes can be generated efficiently according to specific frameworks of different software to be developed, and development cost can be reduced.
Owner:BEIJING UNIV OF POSTS & TELECOMM
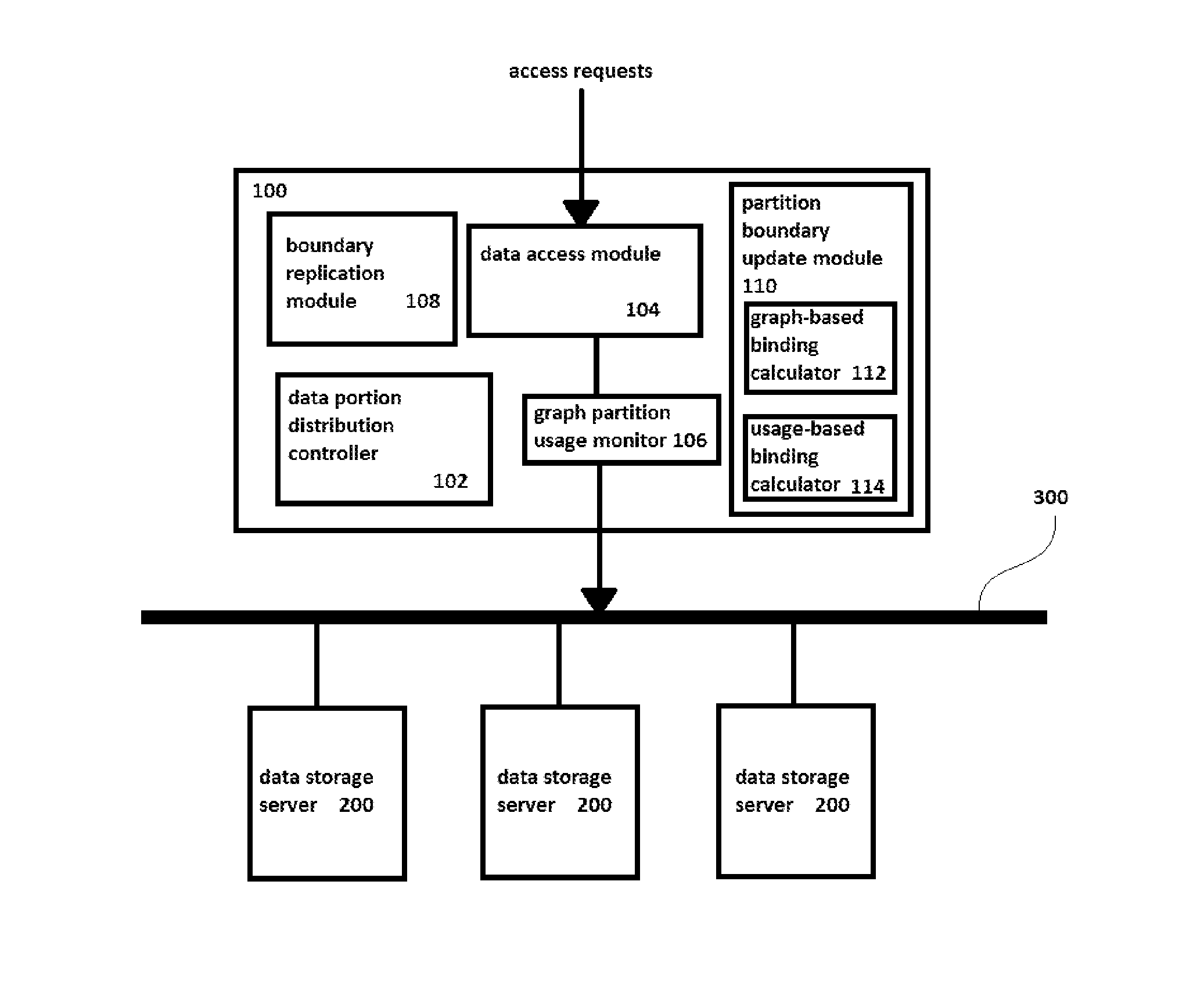
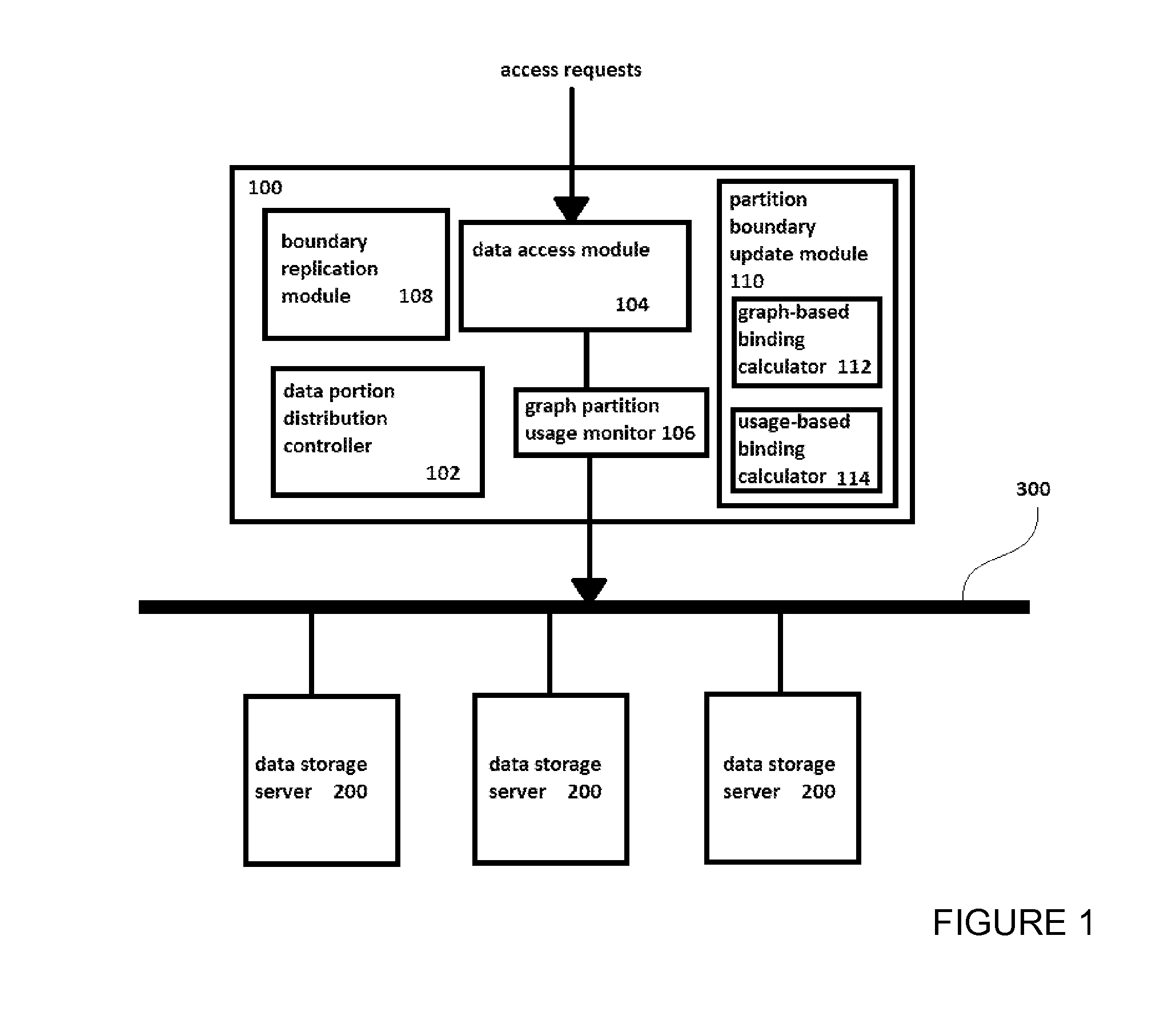
Method and system for storing distributed graph data
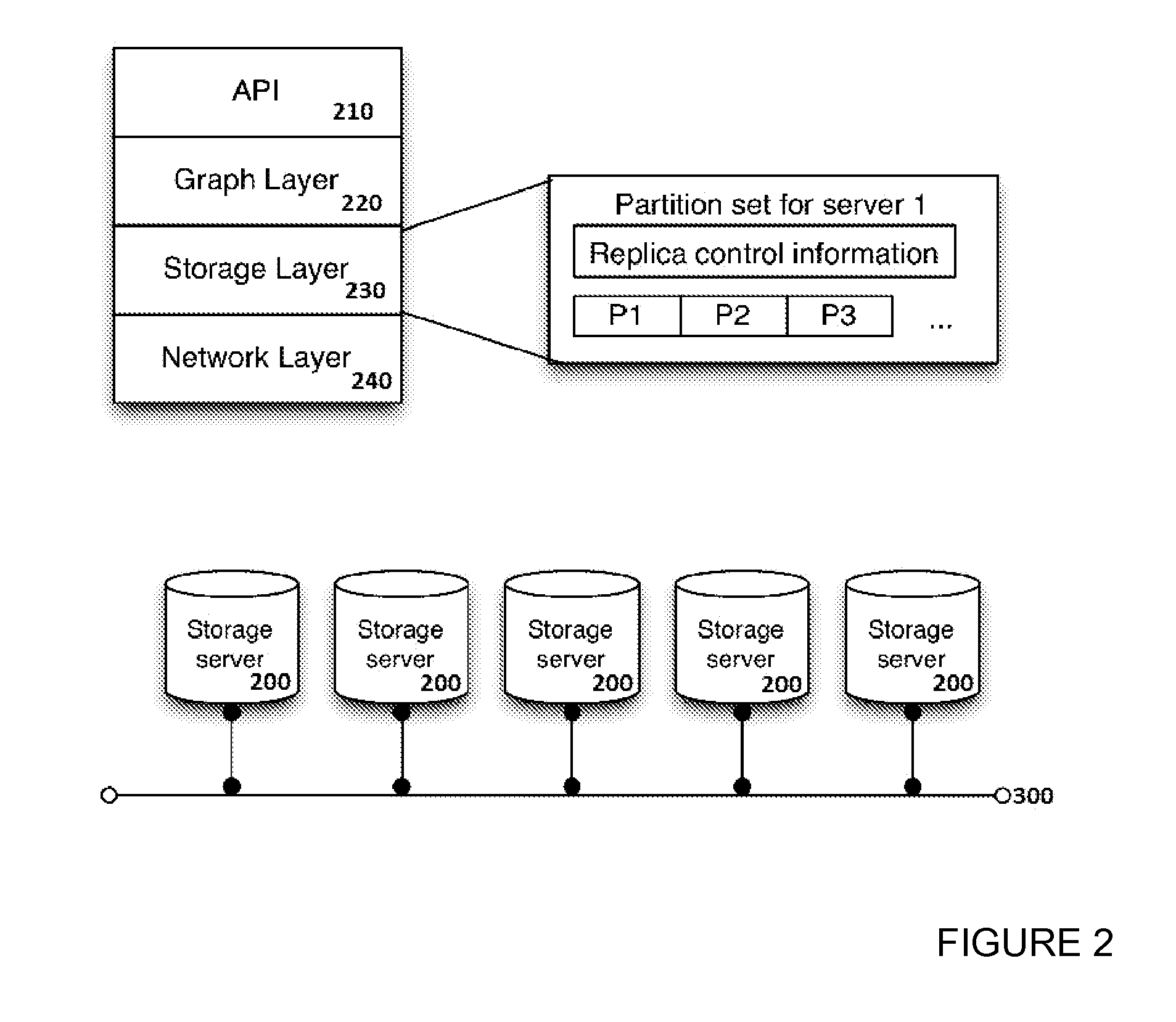
InactiveUS20150350324A1Save spaceAvoid bottlenecksDigital data information retrievalHardware monitoringGraphicsDistribution control
A distributed data graph storage system, to store a data graph representing information as vertices interconnected by edges denoting relationships between connected vertices, the data graph being a plurality of graph partitions. The data graph storage system includes data storage servers to store data portions, each portion encodes a graph partition; a data portion distribution controller, when the data portions each encode a same graph partition, to allocate the portions to different data storage servers; a data access module to receive access requests for the data graph and to distribute the access requests among the servers; a graph partition usage monitor to record statistics representing the distribution of data access events caused by the access requests; where the data portion distribution controller is configured to increase or decrease the number of portions in dependence upon the recorded statistics.
Owner:FUJITSU LTD
Identity authentication based virtual terminal safety environment protection method and system
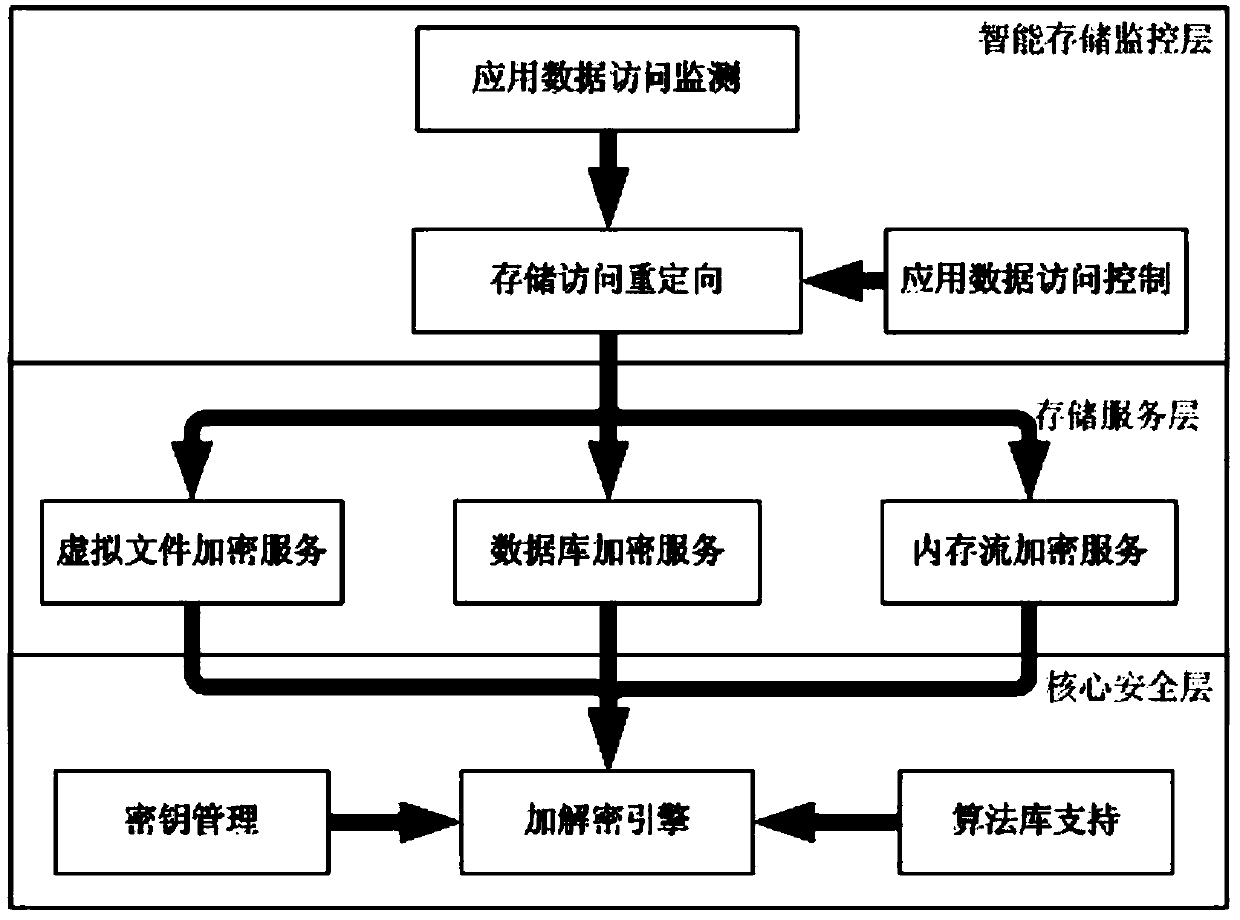
ActiveCN103778384APrevent Data LeakageOperating habits have no effectDigital data protectionInternal/peripheral component protectionVirtual terminalData access
The invention discloses an identity authentication based virtual terminal safety environment protection method and system. The system comprises an intelligent storage monitoring layer, a storage serving layer, and a core safety layer, wherein the intelligent storage monitoring layer comprises a storage access redirecting module, is in charge of monitoring and analyzing data access acts of application programs, and performs actions according to configuration rules, the storage access redirecting module transfers input / output access according to access control rules, the storage serving layer is in charge of encrypting and decrypting files or data and recording file mapping relations, and the core safety layer is the basis of the whole framework, provides a key management function, provides encryption and decryption support for the storage serving layer, and dispatches different algorithms as desired. By means of the identity authentication based virtual terminal safety environment protection method and system, safety of core application data can be protected, data leakage is prevented, and data inside and outside the environment are isolated without influence and do not influence user operation habits.
Owner:北京明朝万达科技股份有限公司
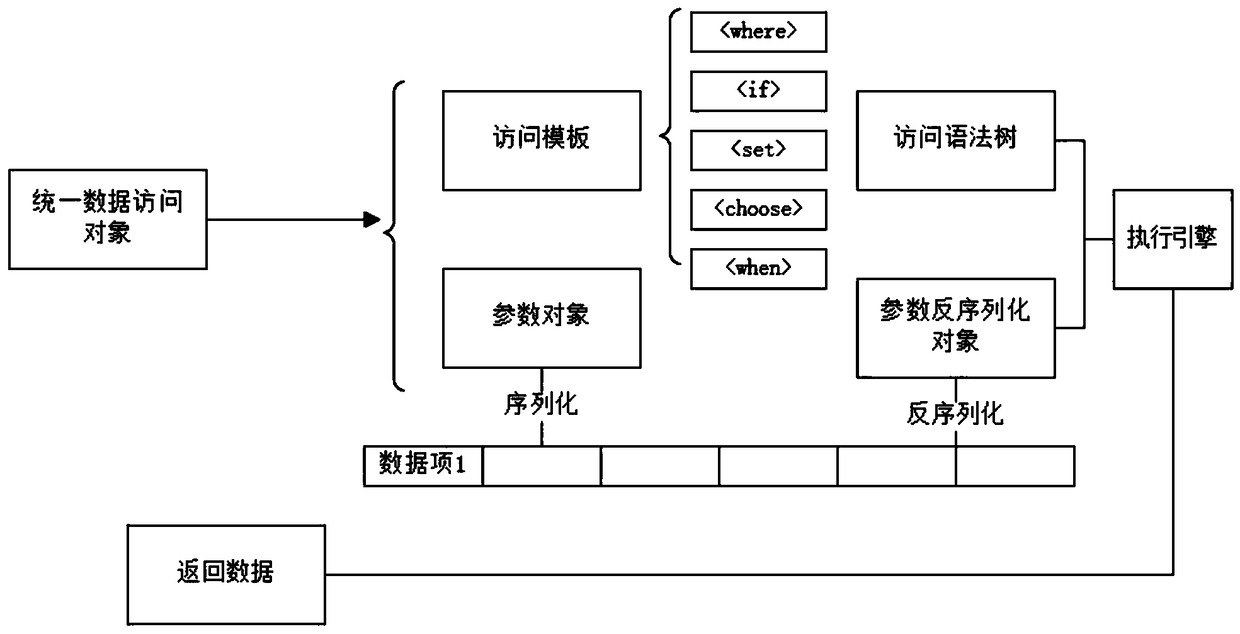
View-based data access system and method
ActiveCN102254029ASmall amount of workShorten the development cycleSpecial data processing applicationsDatabase interfaceView based
The invention discloses a view-based data access system and method. An interface element is connected with a data access layer, an object creating element of the data access layer creates a data access element, the data access element comprises a complex view element and a simple view element; the data access element generates an SQL (Structured Query Language) operation statement, the data access element is connected with a database interface, the database interface transmits the SQL operation statement to a relational database through a relational database connecting module, the relational database executes the SQL operation statement and obtains an inquiry statement defined by a data attribute from a data access element object as well as transmits the inquiry statement to the relational database, the relational database executes the inquiry statement; the relational database connecting module transmits data returned by the inquiry statement to the data access element; and the data access element transmits an obtained data source to the interface element for displaying. According to the invention, work amount of developers is effectively reduced and whole development cycle can be shortened.
Owner:HUNAN CRRC TIMES SIGNAL & COMM CO LTD
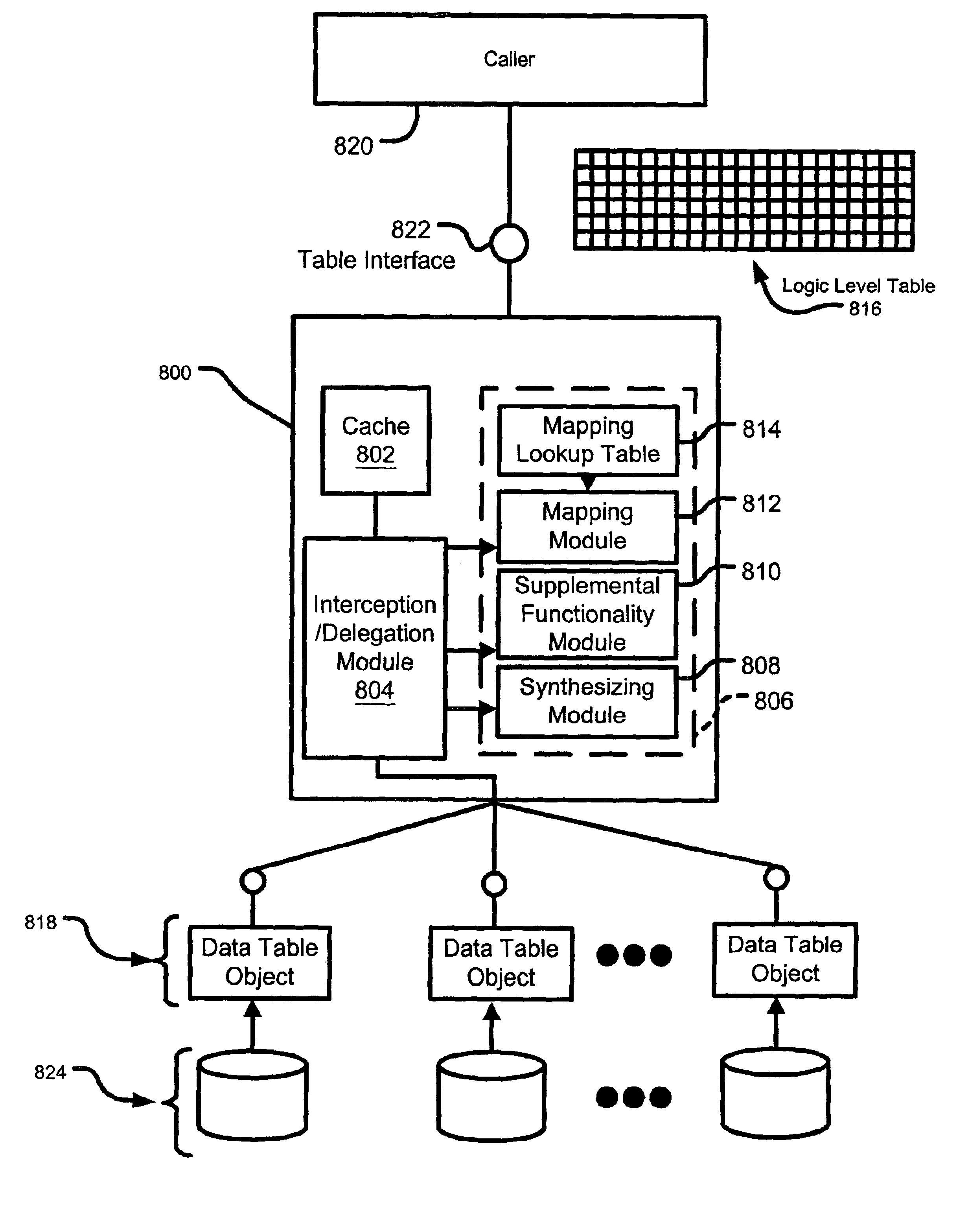
Catalog management system architecture having data table objects and logic table objects
InactiveUS6917933B2Data processing applicationsSpecial data processing applicationsAbstraction layerEncapsulated data
An abstraction layer in a catalog management system for accessing system configuration information. The catalog management system presents the configuration information that is stored in a datastore to a computer process by storing the information in cache memory so that the datastore is encapsulated from the caller. The request for the configuration information may be both location independent and type independent.
Owner:MICROSOFT TECH LICENSING LLC
Multi-core processor and data access method
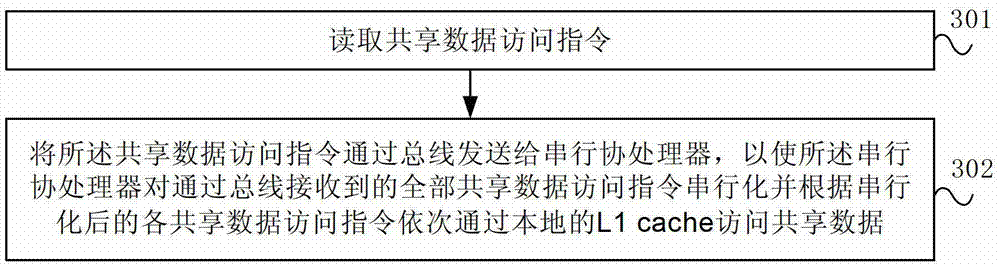
ActiveCN103092788ASolve conflictsGuaranteed to be relatively fixedDigital computer detailsElectric digital data processingData access objectMulti-core processor
The invention provides a multi-core processor and a data access method. The multi-core processor comprises at least two processing cores and serial coprocessors which are connected with the at least two processing cores through a bus. Each processing core is used for reading sharing date access orders, and sending the sharing data access orders to each coprocessor through the bus. The serial coprocessor is used for carrying out serialization to all sharing data access orders received through the bus, and sequentially accessing sharing data through a local L1 buffer according to each serialized sharing data access order. When a plurality of processing cores are in cooperation, namely the plurality of processing cores simultaneously access the same sharing data, due to the facts that the sharing data respectively points to each serial coprocessor, and the serial coprocessors can serialize all the received sharing data access orders through the bus, conflict problems are solved, and then relative fixation of cooperative time is ensured.
Owner:浙江杭海新城控股集团有限公司
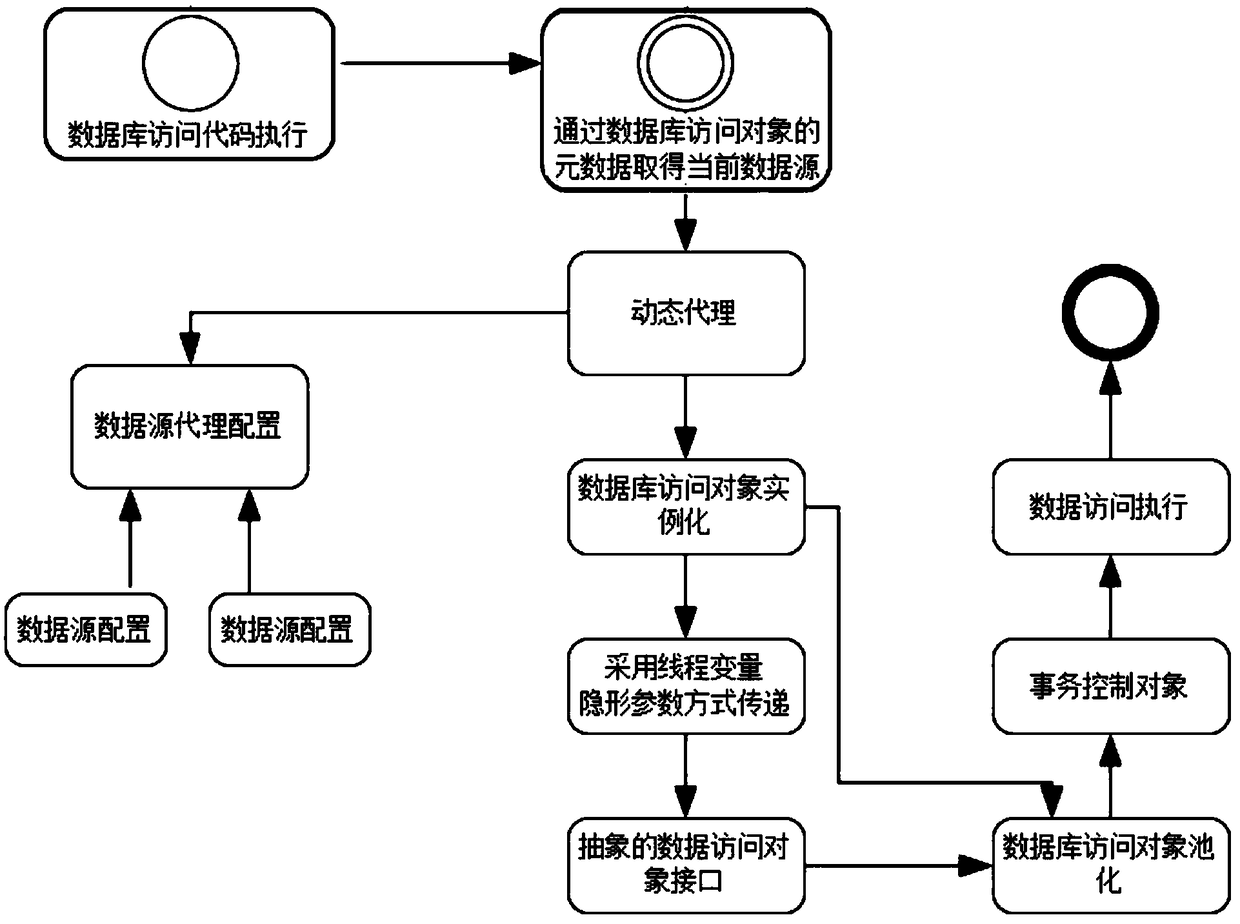
Implement method of data access object mode based on dynamic proxy
InactiveCN1869991ASpecial data processing applicationsSpecific program execution arrangementsOpen sourceData access object
A method for realizing data access object mode based on dynamic agent includes applying open source object mapping tool Hibernate to realize DAO, utilizing DAO layer to carry out API interaction of Hibernate to let the other portion of program be separated form direct operation on Hibernate and applying some other scheme to replace off Hibernate for realizing DAO if it is necessary.
Owner:LINKAGE SYST INTEGRATION
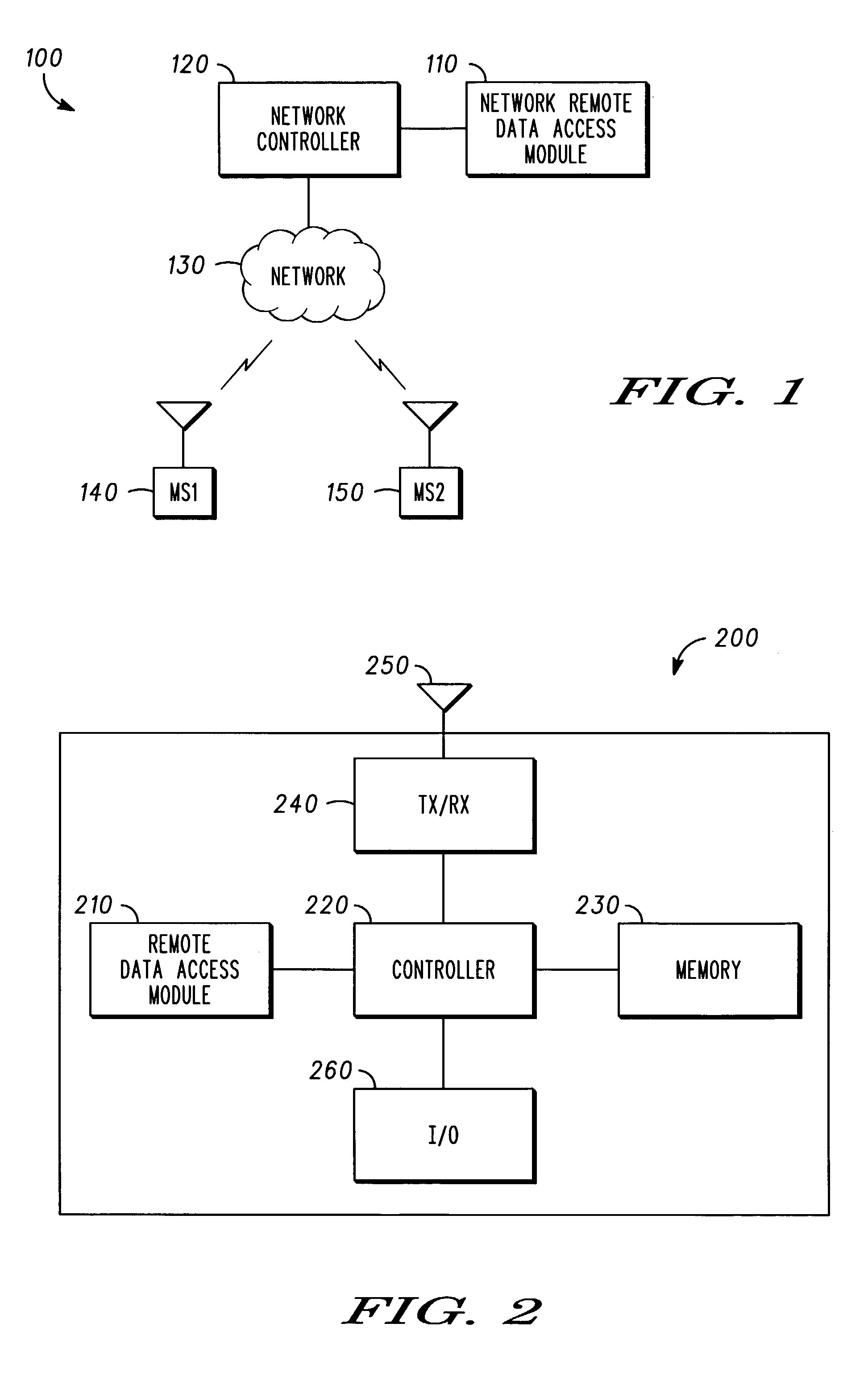
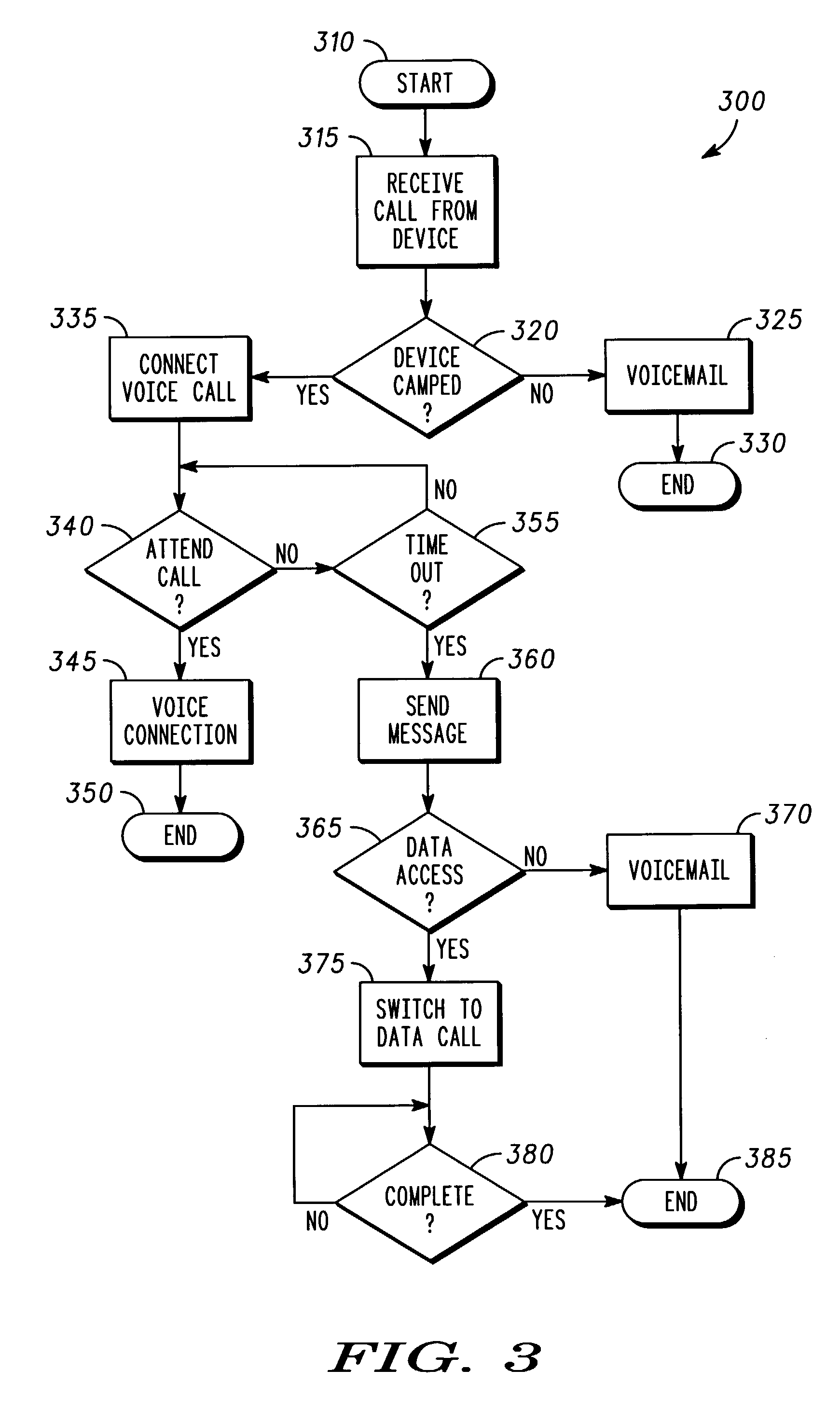
Method and apparatus for remote data access in a mobile communication device
ActiveUS7653383B2Unauthorised/fraudulent call preventionEavesdropping prevention circuitsTelecommunicationsData access
A method and apparatus for remote data access in a mobile communication device. A voice call can be initiated between a first voice and data wireless device and a second voice and data wireless device. A data access request can be communicated between the first voice and data wireless device and the second voice and data wireless device. The voice call can be switched to a data call to establish a data access connection. Data can then be transferred between the first voice and data wireless device and the second voice and data wireless device.
Owner:GOOGLE TECH HLDG LLC
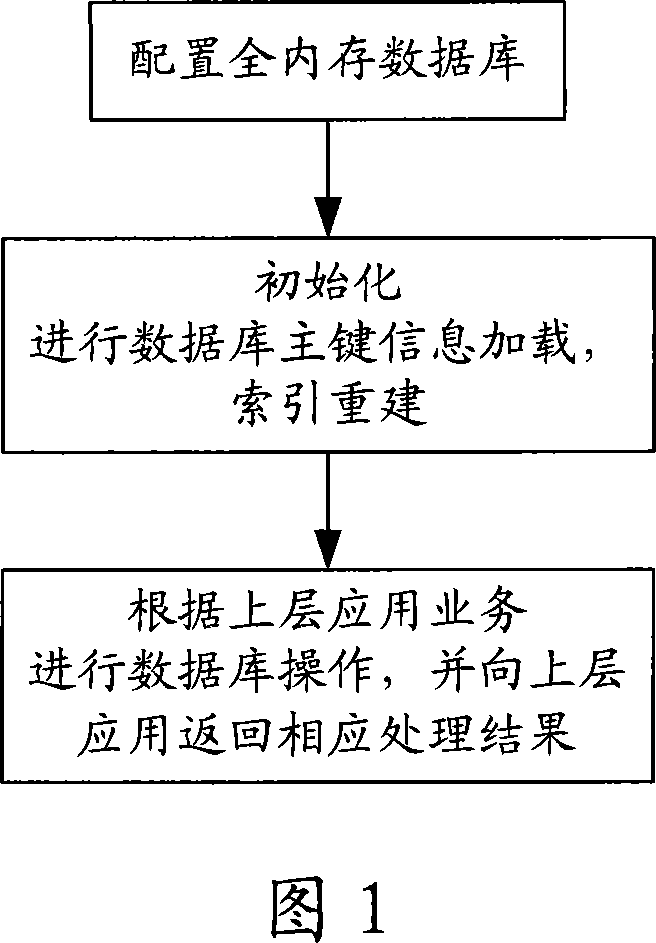
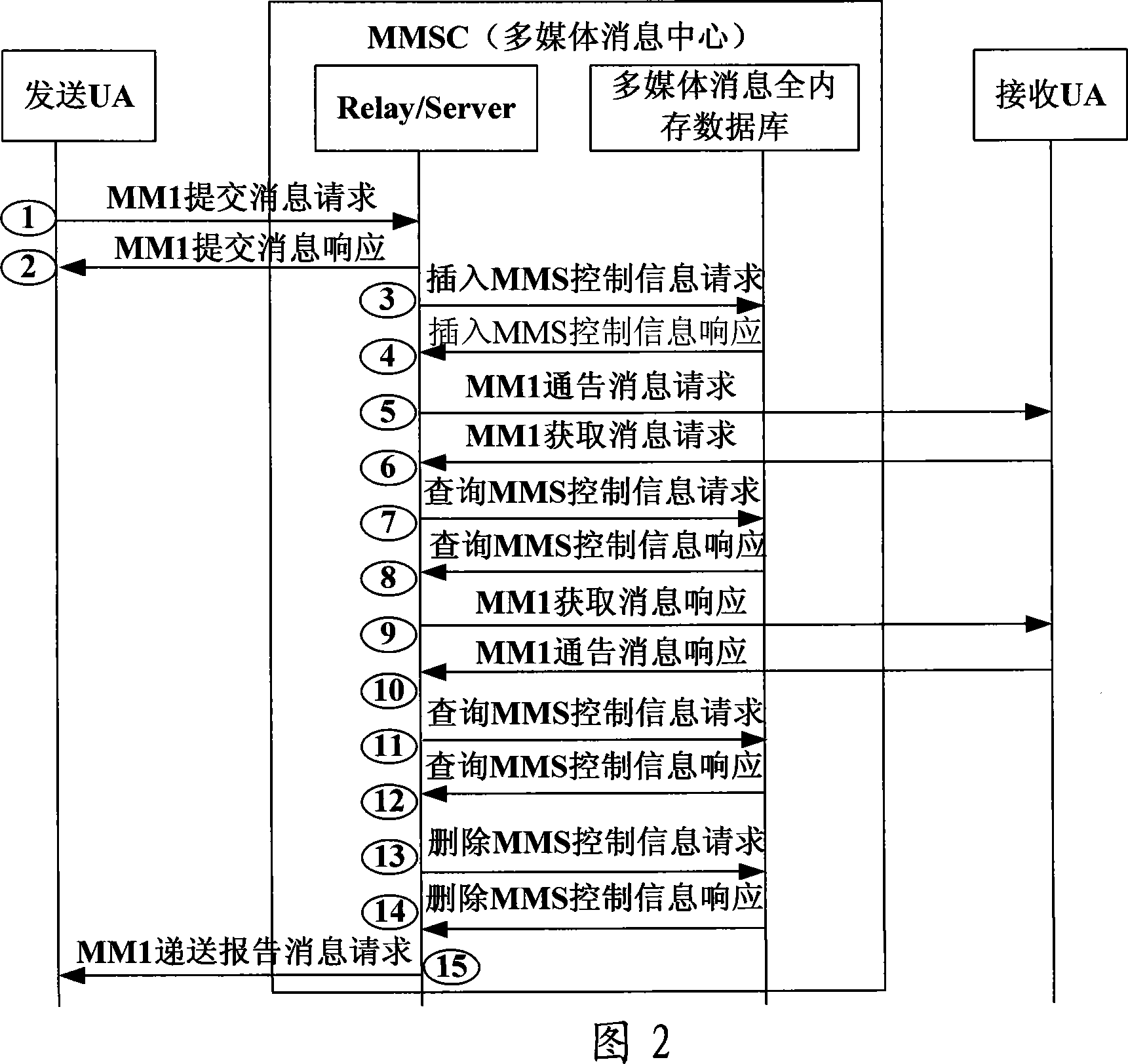
Data access method for all-memory database
InactiveCN101055591AAvoid running speed impactPrevents reduction in processing capacityStore-and-forward switching systemsSpecial data processing applicationsIn-memory databaseAccess method
A data access method of whole memory database, belongs to a data access method. In the method, a whole memory database information is arranged firstly, and is initialized then, a corresponding operation of database is carried out according to a upper application professional operation at last,and a corresponding operated result is returned towards the upper application. The invention is especially suitable for a system in which the requirement for the data access effect is high and the lifecycle of database is in a certain range, accordingly the operated speed of system is improved, and the operated ability of system is enlarged, the cost of syatem and the maintenance of system are reduced.
Owner:NANJING ZHONGXING XIN SOFTWARE CO LTD
Method and system for generating database access objects
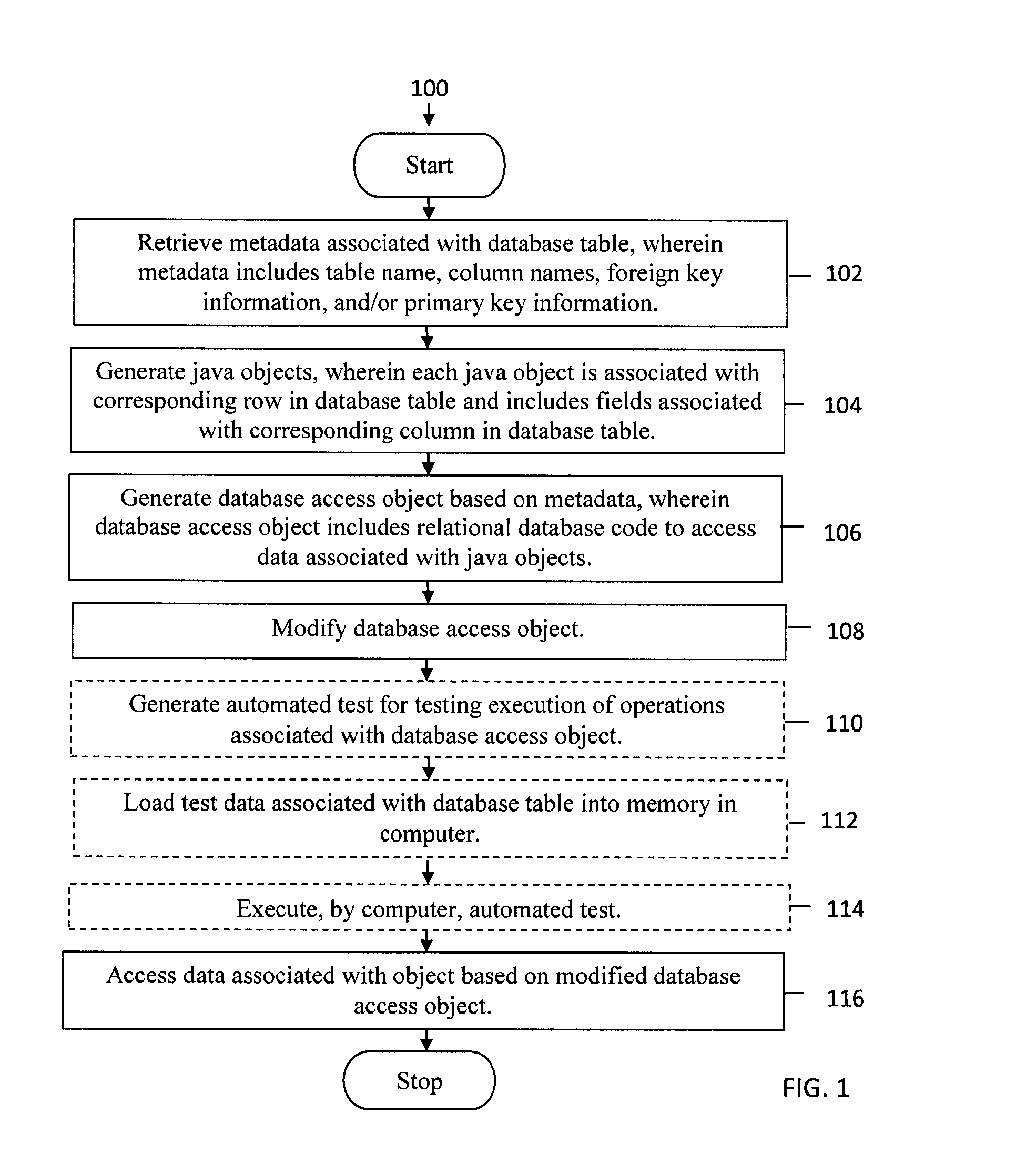
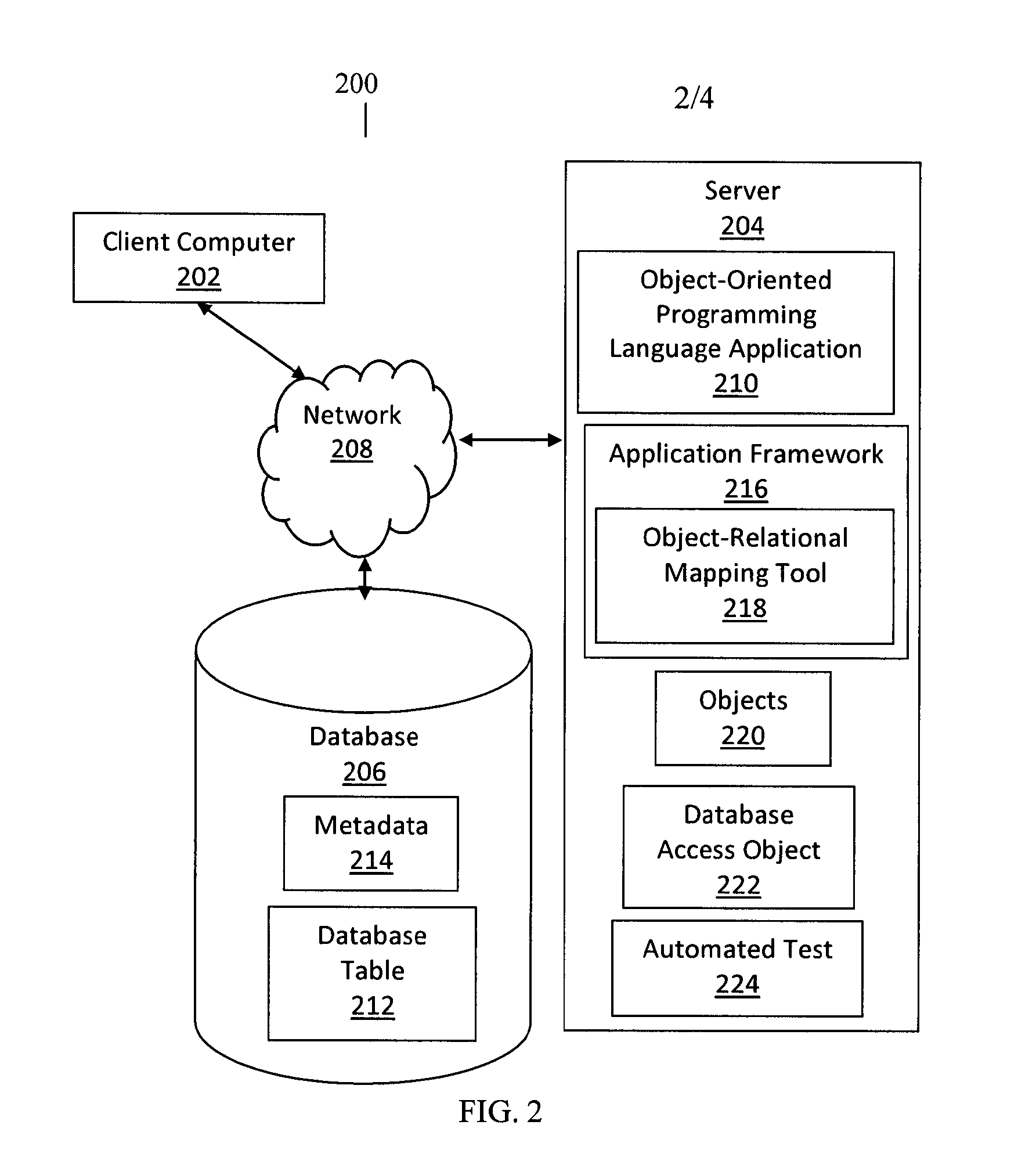
ActiveUS20130297654A1Efficient access to dataData efficientDigital data processing detailsDigital data protectionObject systemData access object
Systems and methods are provided for generating database access objects. Metadata associated with a database table is retrieved. The metadata includes a table name, column names, foreign key information, and / or primary key information. Objects are generated. Each object is associated with a corresponding row in the database table and includes fields associated with a corresponding column in the database table. A database access object is generated based on the metadata. The database access object includes relational database code to access data associated with the objects. The database access object is modified. Data associated with an object is accessed based on the modified database access object.
Owner:SALESFORCE COM INC
Interactive electronic technical manual browsing system
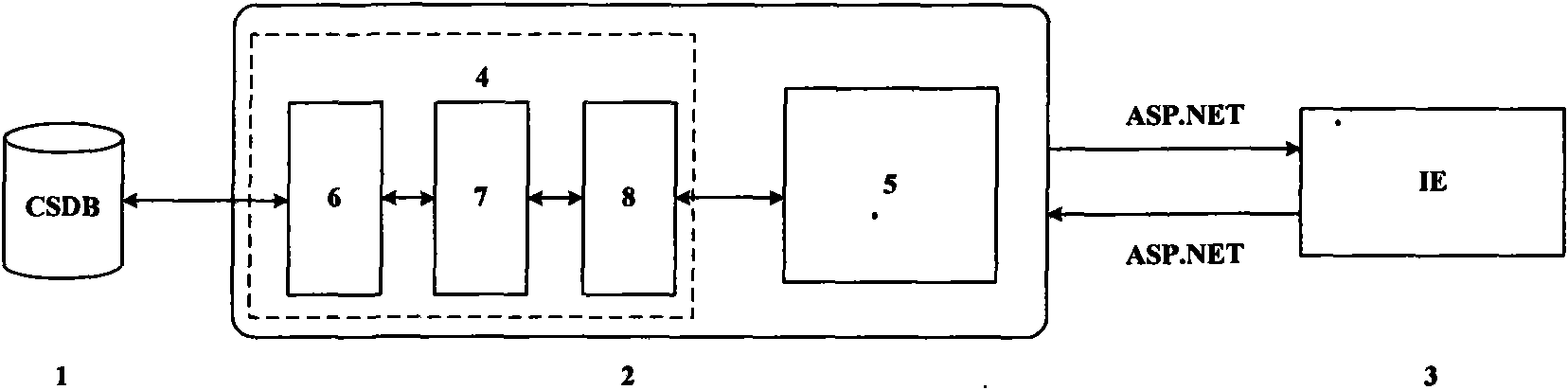
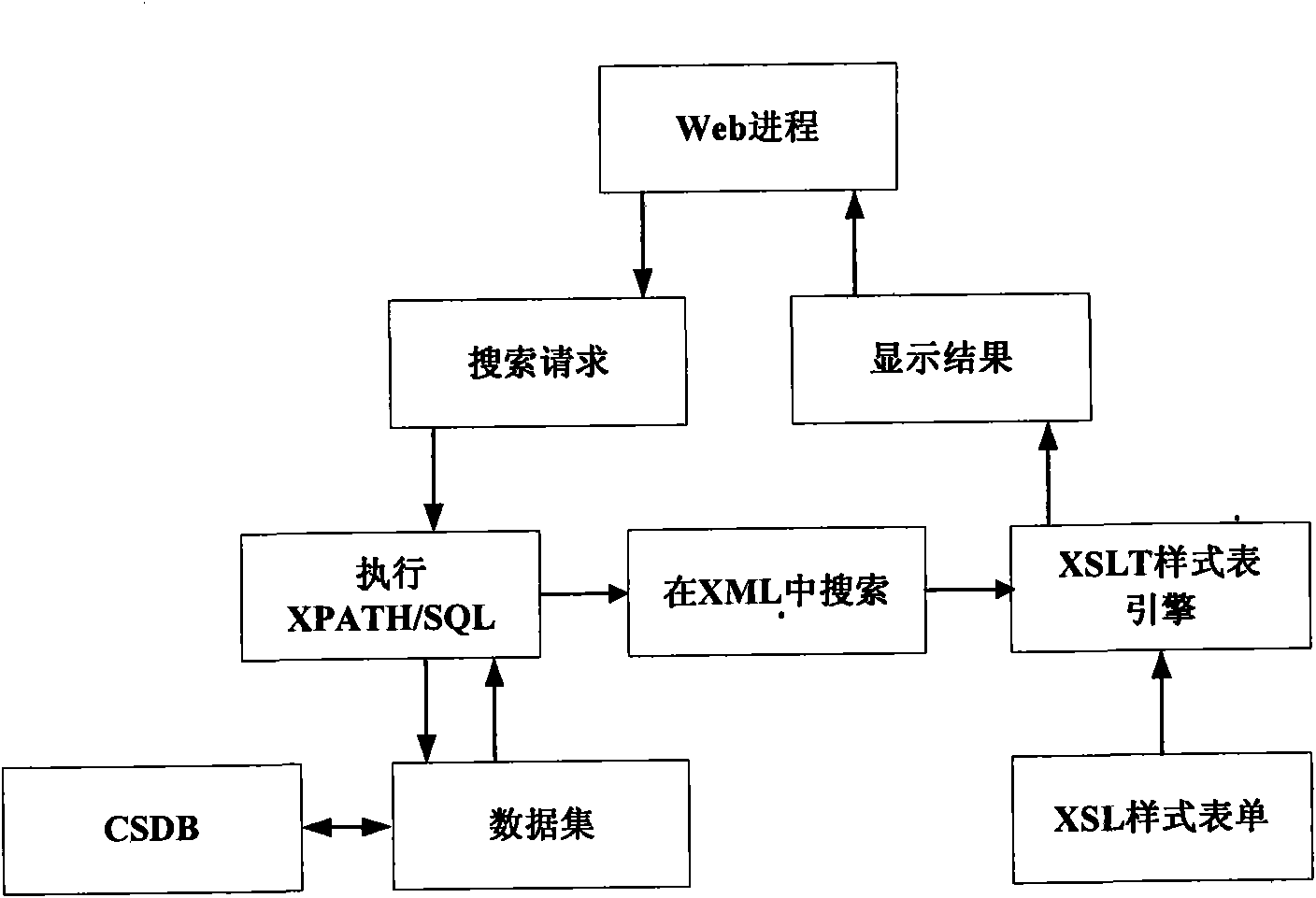
InactiveCN101661493AAddress information sharingSolve information interactionSpecial data processing applicationsWeb serviceNetwork connection
The invention discloses an interactive electronic technical manual browsing system, which is characterized by being a three-layer running mode based on network connection, that is a data layer (1), anintermediate layer (2) and an express layer (3), wherein the data layer (1) is a Common Source Data Base(CSDB); the intermediate layer (2) comprises a data ADO.NET data access model (4) and a Web server ASP.NET (5); the data access model (4) extracts and saves data from the data layer (1); the Web server ASP.NET (5) processes, maintains and guarantees service logic and service rule which are related with technical data; the express layer (3) is a client browser; the system can directly use the technical data of XML format; information elements can be used by a plurality of systems, such as anIETM, CBT(based on the training of a computer), a WBT(based on the training of network) and the like, for many times and are easy to update; and the interactive electronic technical manual browsing system can realize convenient and quick information search of a plurality of channels, can be integrated with an expert system and the CBT to enhance fault positioning, realizes real-time training, andhas simple and convenient operation and friendly interface.
Owner:NAVAL AERONAUTICAL & ASTRONAUTICAL UNIV PLA
Database access method and device
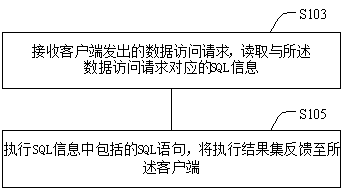
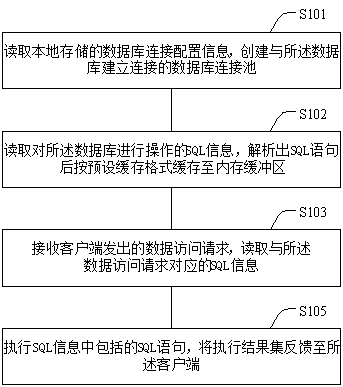
InactiveCN108228597AImprove securityImprove efficiencyDatabase management systemsPlatform integrity maintainanceData accessData access object
The invention provides a database access method and device. An execution main body of the method is a server; and SQL information for operating a database is stored in the server according to a presetformat. The method comprises the following steps of: receiving a database access request sent by a client and reading SQL information corresponding to the database access request; and executing an SQL statement included in the SQL information and feeding back an execution result to the client. Through the method and device, dependency on browsers and other server containers can be dispensed, so that the problem that data access codes are easy to expose in the prior art is effectively solved, and the data access safety and efficiency are improved.
Owner:深圳市优朋普乐传媒发展有限公司
Database persistent layer device and database operation method
ActiveCN103049251ARealize automatic generationSimplify the design processSpecific program execution arrangementsSpecial data processing applicationsData operationsApplication software
An embodiment of the invention provides a database persistent layer device and a database operation method. The database persistent layer device comprises a pixel domain module, a pixel code mapping and code generating domain module and a database domain module, wherein the pixel domain module is used for providing a pixel editing environment, receiving design instructions on data objects represented in pixel form and input into the pixel editing environment by users and editing the data objects designed by the users to generate corresponding pixel describe files; the pixel code mapping and code generating domain module is used for analyzing the pixel describe files generated by the pixel domain module to generate corresponding plain old java object (POJO) and data access object (DAO); and the database domain module is used for mapping the generated POJO into a database table in the database and performing operation on the database table in the database and data members of the database table according to the generated DAO. By means of the embodiment of the data persistent layer device and the database operation method, automatic generation of data of the POJO and the DAO in a persistence layer can be achieved in the application program design, so that work amount of the persistence layer in the application program database is greatly reducd, and development efficiency is improved.
Owner:CHINA MOBILE COMM GRP CO LTD
Method and device for data compression for page access object
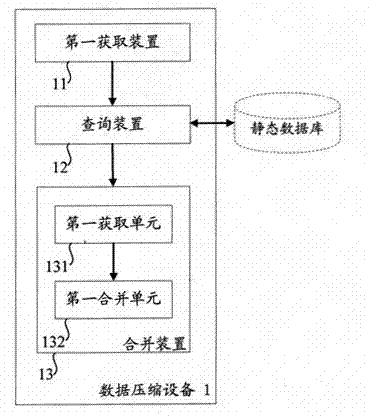
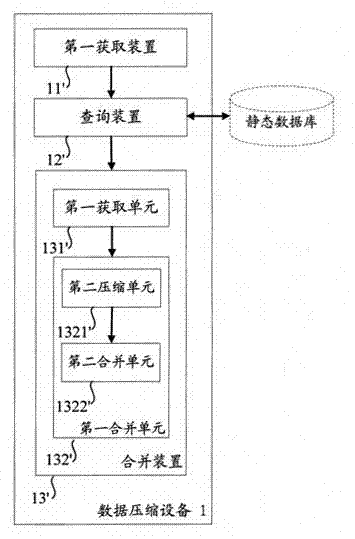
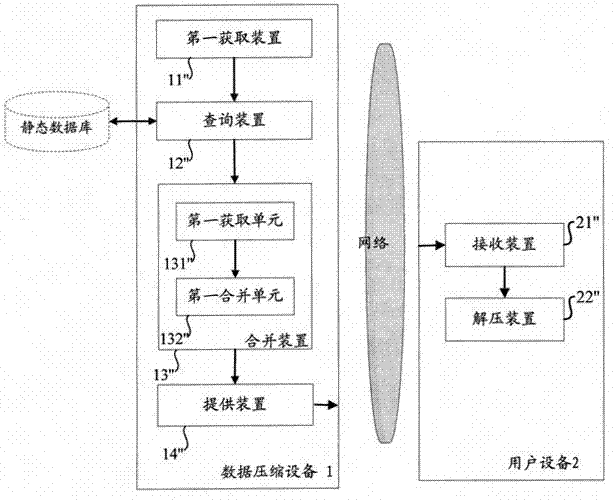
InactiveCN102375884AReduce loadReduce data volumeCode conversionSpecial data processing applicationsData compressionWeb service
The invention aims at providing a method and device for data compression for a page access object. The method comprises the following steps of: acquiring the page access object to be compressed; executing matching query in a static database according to the page access object obtain a static data compressed package corresponding to the page access object; obtaining the dynamic data corresponding to the page access object while obtaining the static data compressed package; and merging the dynamic data with the static data compressed package to obtain a page access object compressed package corresponding to the page access object. In comparison with the prior art, the static data in the data to be compressed is compressed in advance to generate the static data compressed package, and the dynamic data is merged with the static data compressed package to generate a result compressed package, thus, the data volume which needs to be compressed immediately is reduced, and the compression effect almost same as that in the prior art is realized while reducing the load on a Web server.
Owner:BEIJING BAIDU NETCOM SCI & TECH CO LTD
Remote monitoring system for chlorine dioxide generation device based on cloud platform
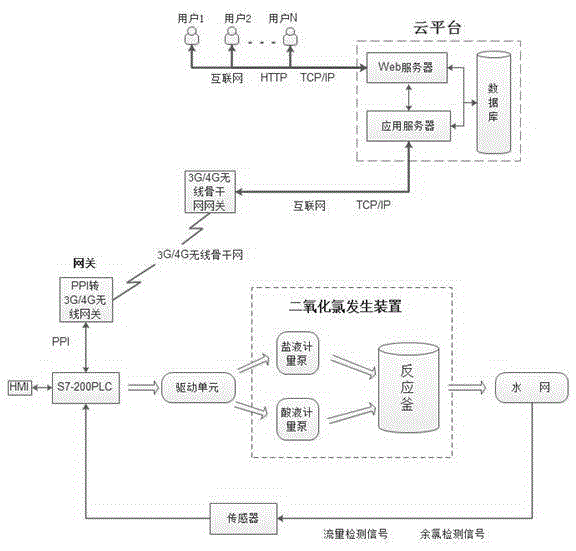
ActiveCN105652787AHigh control precisionImprove anti-interference abilityProgramme control in sequence/logic controllersChlorine dioxideApplication server
The invention relates to a remote monitoring system for a chlorine dioxide generation device based on a cloud platform. The remote monitoring system comprises the chlorine dioxide generation device, a sensor, a PLC, an HMI, a driving unit and the cloud platform, wherein the PLC is connected with the cloud platform through a wireless network; the cloud platform comprises an application server, a web server and a database system; the application server acquires data in the PLC, and transmits and confirms a control instruction for the chlorine dioxide generation device to the PLC; the web server is used for realizing access of a user; and the data of the application server and the data of the web server are stored into a database, and the user can access the database through the web server. The monitoring system intensively monitors and manages a plurality of devices through a public wireless network and an internet technology; the cloud platform supports multi-user accessing; and by the adoption of a public data accessing object technology, the problem of contention of a PLC port during the same access to the same generation device is solved, the expandability of the monitoring system can be greatly improved, and great convenience is brought to expansion of the user and after-sale service of a manufacturer.
Owner:南京基撰自动化科技有限公司
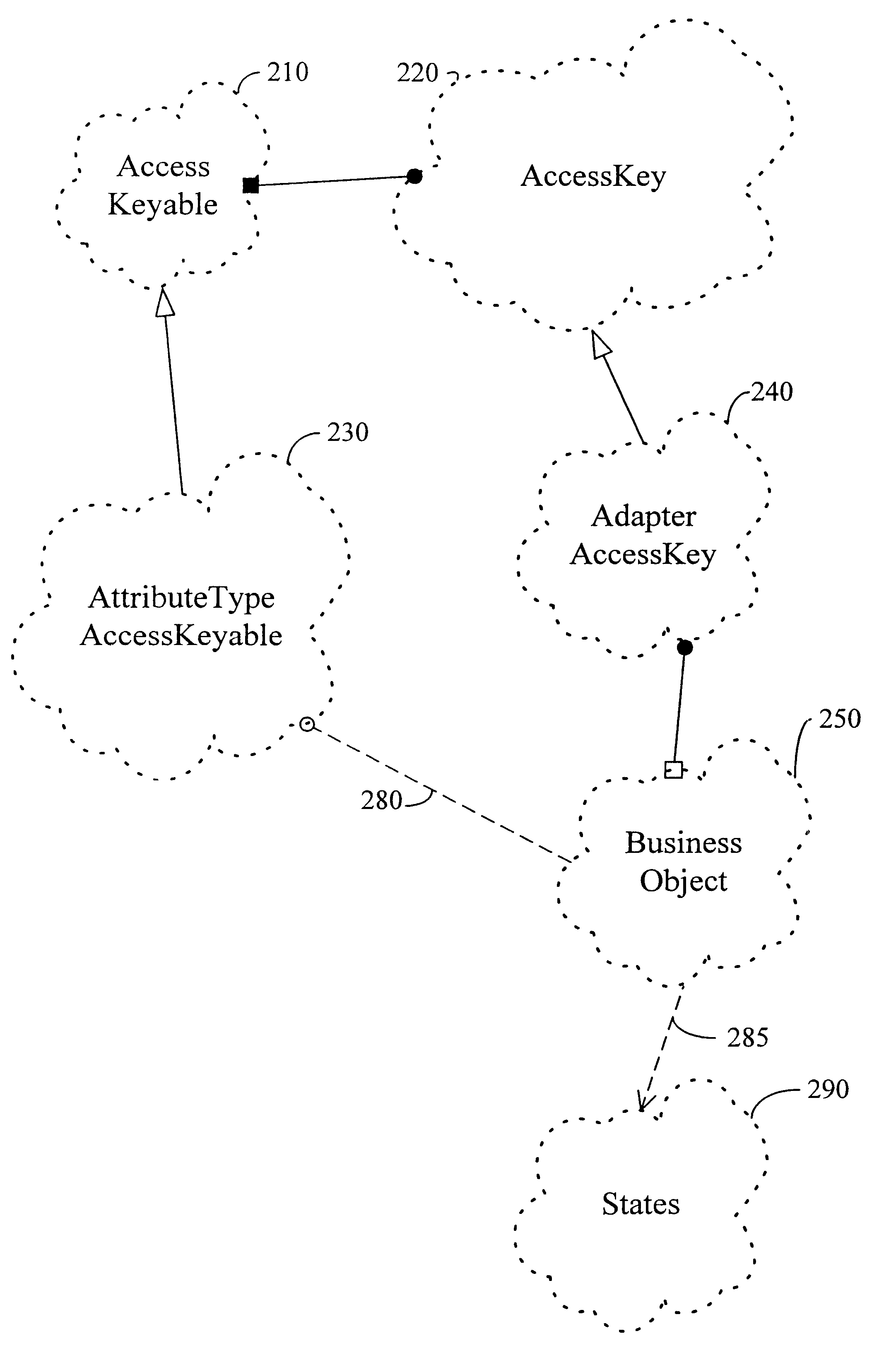
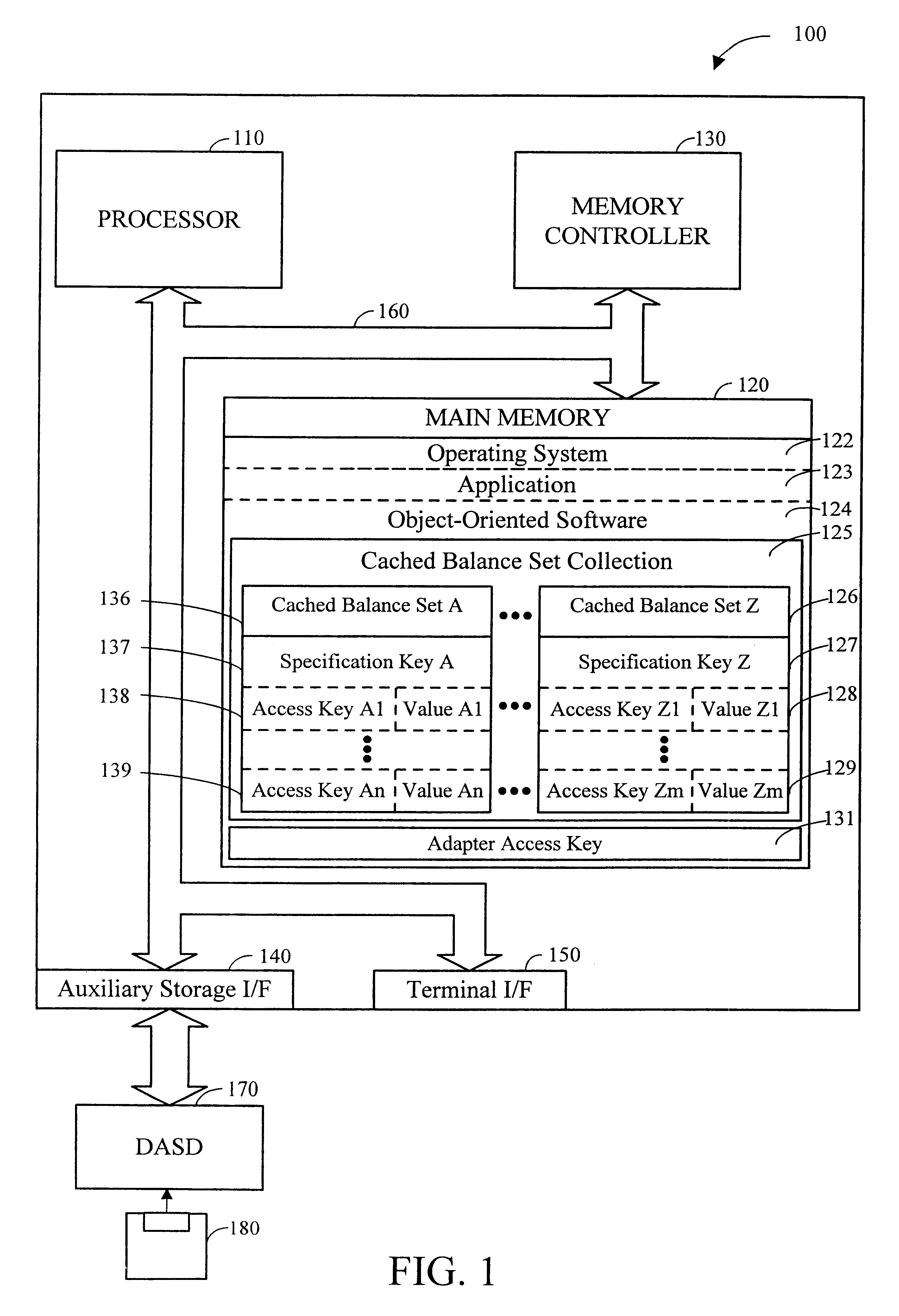
Use of adapter key to increase performance when updating a value referenced by a data access object
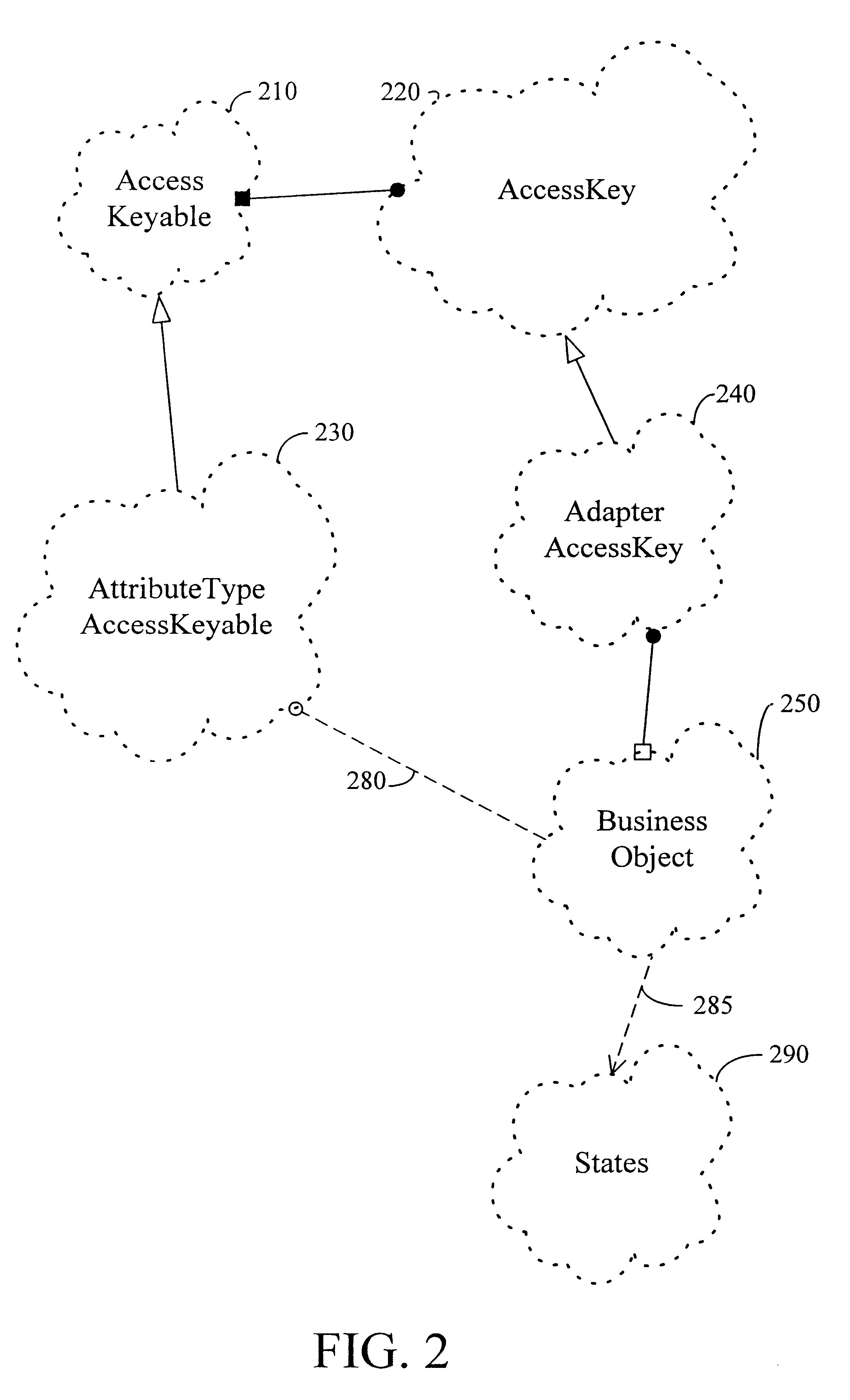
InactiveUS6526412B1Reduce the amount requiredEasy resetData processing applicationsObject oriented databasesObject pointData access object
A method and apparatus for dynamically loading criteria from an object to reduce the amount of total criteria necessary to update a referenced value is disclosed. The value can be "inside" a database or an object in an object-oriented framework. When updating a value that is referenced by a data access object (such as an access key) that depends on other objects (such as access keyables) for criteria necessary to reference the value, a special data access object (called an adapter access key) is used instead of using the data access object. Instead of creating and populating all of the access keyables prior to an update of the value, the adapter access key holds onto the source of the criteria (such as a business object) needed to fill the access keyables and to access the value. The adapter access key dynamically determines criteria from the business object only for those keyables that are important in updating the value. This reduces the comparison time that used to occur when the criteria in the access key was compared to criteria that determined if the value was "within" a database or an object in an object-oriented framework, or if the data access object pointed to the value. Preferably, there is a facsimile (such as with a boolean array) of keyables that is marked in such a way that the adapter access key can be easily reset and used for multiple updates. This eliminates copying of the original key and minimizes comparison time.
Owner:IBM CORP
Portable non-volatile memory device and data security method of same
InactiveUS20050015629A1Improve reliabilityLow costDigital data processing detailsUser identity/authority verificationDigital dataPassword
A portable non-volatile memory device includes a housing, a data access connector, a non-volatile memory, a password-entering interface and a password-verifying device. The data access connector is mounted to the housing and attachable to and detachable from a digital data processor. The non-volatile memory is disposed in the housing and selectively accessible by the digital data processor when the data access connector is attached to the digital data processor. The password-entering interface is disposed in the housing and has a portion exposed from the housing for allowing a user to enter a password. The password-verifying device verifies the password entered via the password-entering device according to a preset pattern, and allows the digital data processor to access to the non-volatile memory when the password complies with the preset pattern.
Owner:IADEA CORP
Code generation method and device based on integration of frameworks Spring and MyBatis
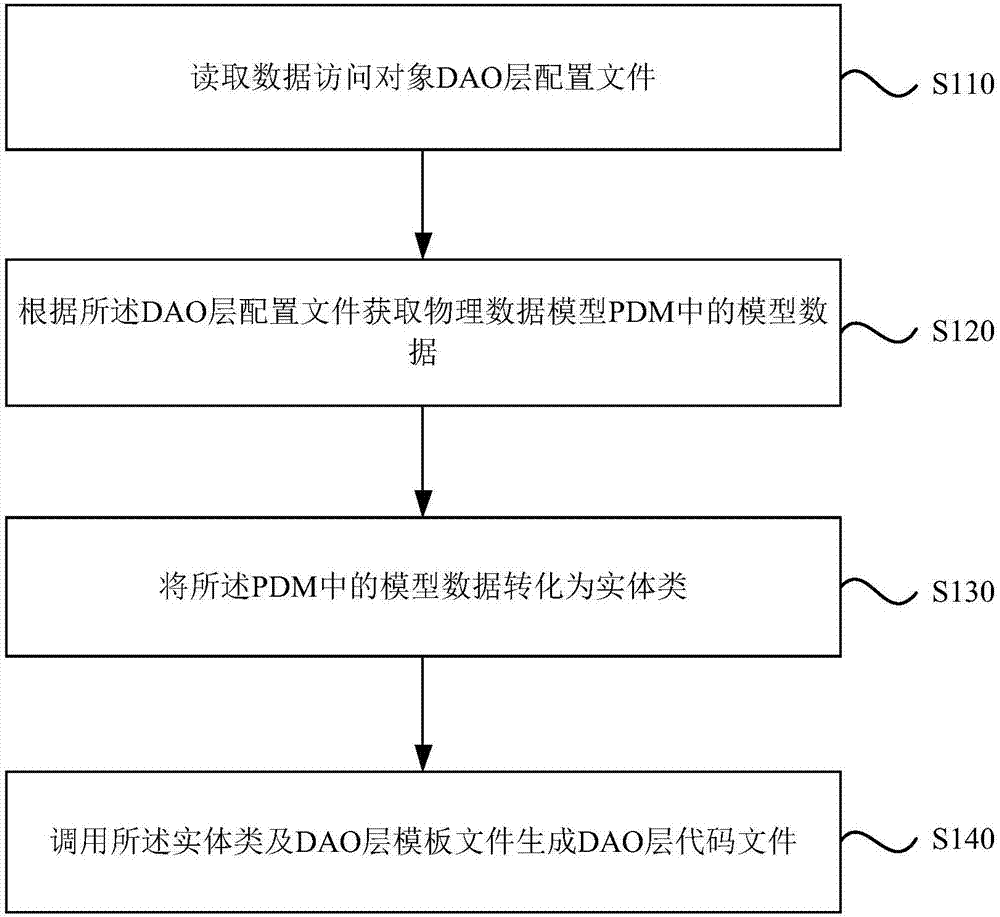
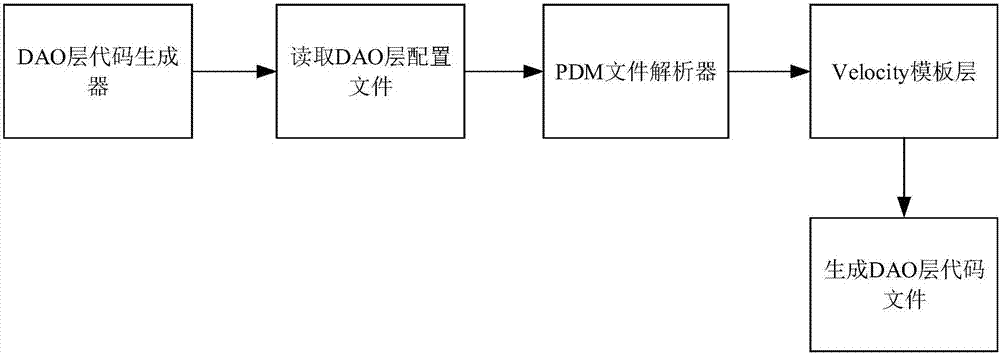
The invention discloses a code generation method and device based on the integration of frameworks Spring and MyBatis. The method comprises the steps that a data access object DAO layer configuration file is read; according to the DAO layer configuration file, model data in a physical data model (PDM) is obtained; the model data in the PDM is converted into an entity class; the entity class and a DAO layer template file are called to generate a DAO layer code file. The problems that in the prior art, codes can be generated by integrating different database drives for different databases and a large amount of repeated work exists in application development based on the frameworks Spring and MyBatis are solved, and the effects of improving the code reuse rate and enhancing a code generating function are achieved.
Owner:SHENZHEN LEXIN SOFTWARE TECH CO LTD
Method for coordinating schema and data access objects
InactiveUS20060218174A1Eliminate pointShorten the timeDigital data processing detailsObject oriented databasesDatabase interfaceBatch processing
Two techniques are commonly used when developing database applications. First, script files containing batched database commands are frequently used to establish the schema of database tables. Second, the software design pattern “Data Access Objects” are sometimes used to contain programmatic database requests while providing an application programmer a more abstract, easier to use interface to the database. Both of these techniques require essentially the same information: an understanding of the organization of particular database tables. The present invention reduces the labor associated with maintaining synchronicity between these two components by a method that allows both the schema and the format of the Data Access Object to be determined by evaluating the properties of an object to be stored in the database.
Owner:COMBRIO
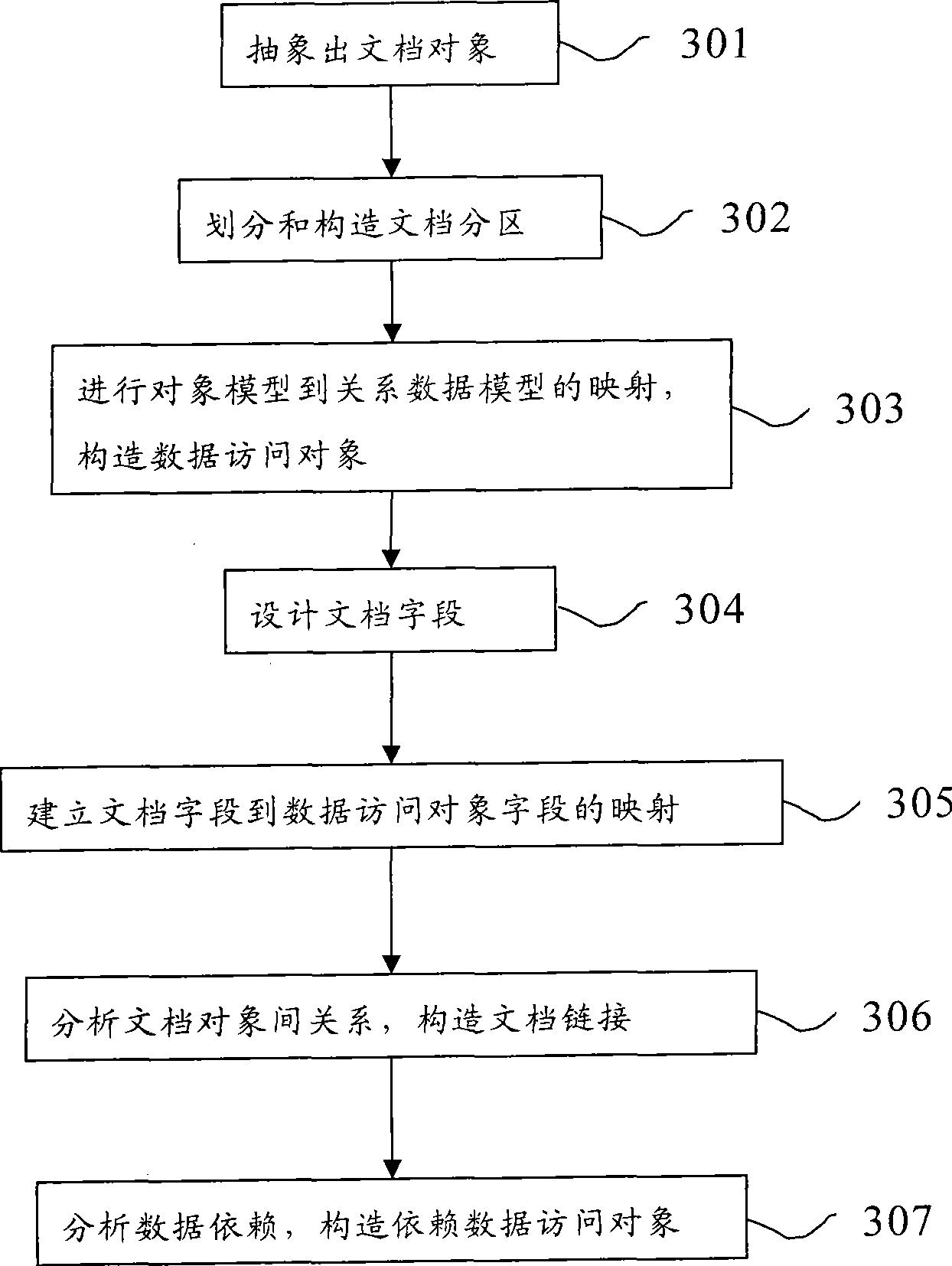
Business logic object modeling method and device thereof
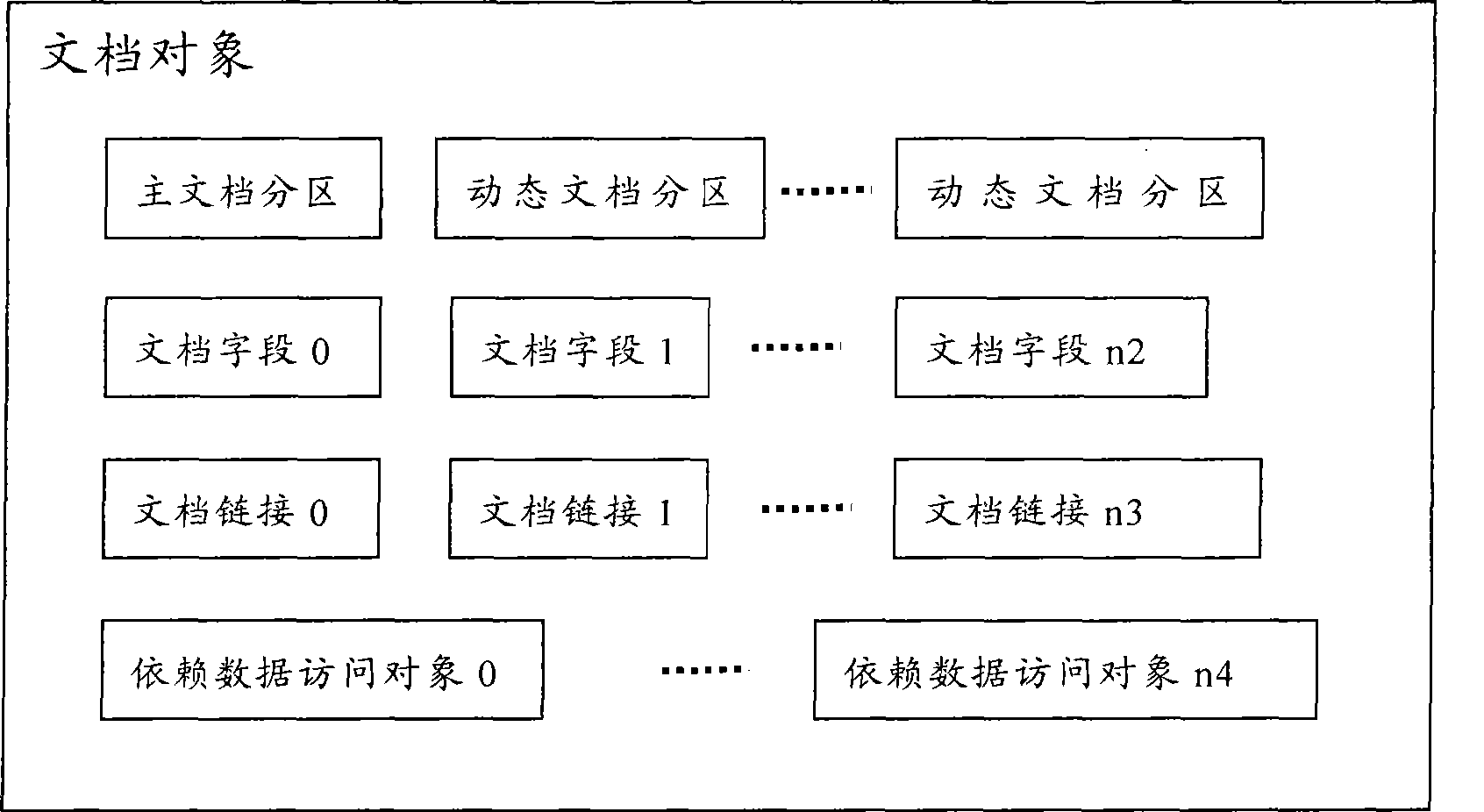
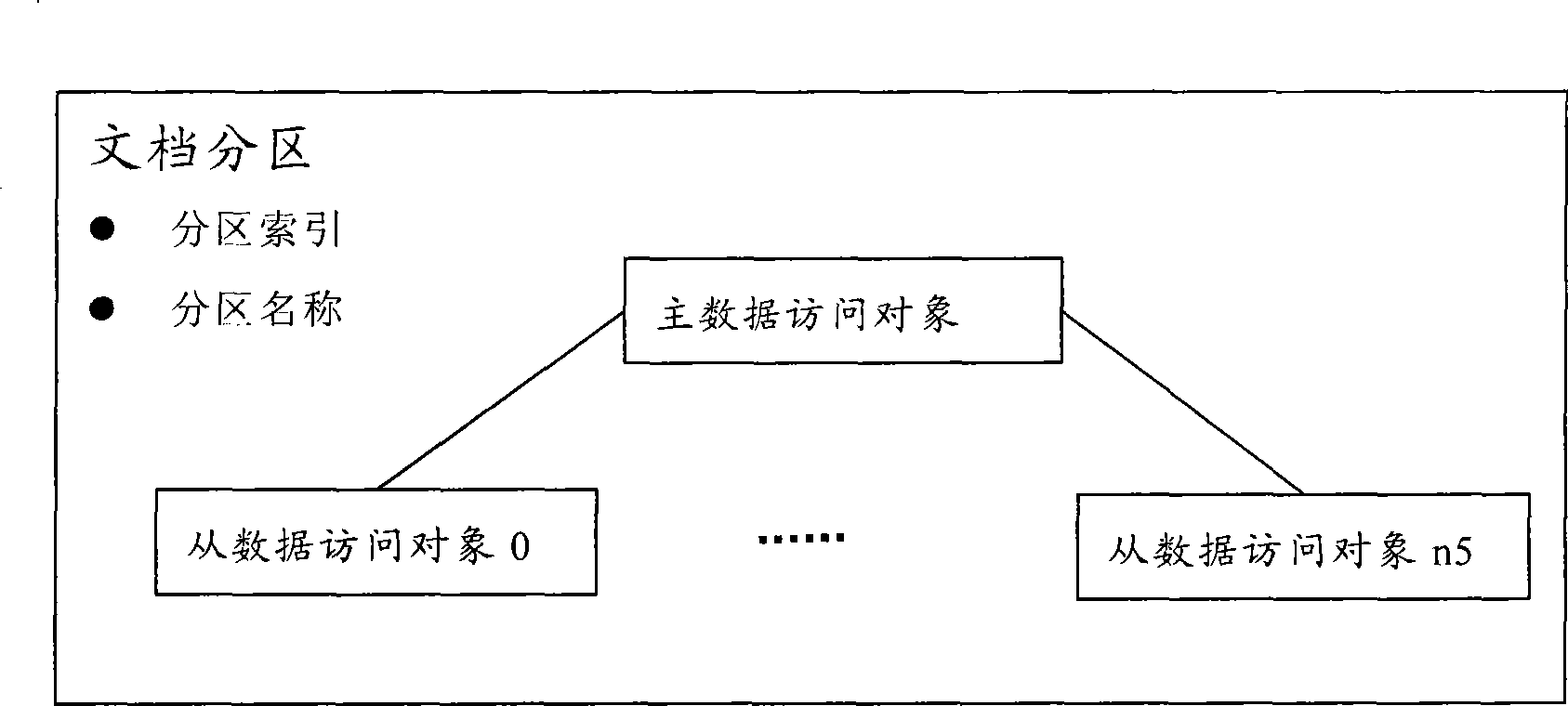
The invention discloses a business logic object modeling method which establishes a business logic object into a document object, wherein the document object comprises a plurality of document subareas which include one read / write main document subarea, a plurality of read-only dynamic document subareas, and no or a plurality of data visiting objects. The data visiting objects include a plurality of document fields, and every document field can be relevant to data fields in the data visiting objects. The document objects include a plurality of document linkages, and every document linkage records the information linked to the other document objects. The document objects include a plurality of dependent data visiting objects which record the data of the prior state of dependent document objects. The invention conveniently develops novel properties or functions to all business logic objects, and only one aspect is required to be added. The structures of the business logic objects are unified to enable the dynamic configuration of the business logic objects to be possible, and the encoding work amount is greatly reduced.
Owner:武汉刻度信息科技股份有限公司
Cross-database access method and abstract data access method based on dynamic proxy
The invention provides a cross-database access method and an abstract data access method based on a dynamic proxy. The cross-database access method based on the dynamic proxy includes: defining and configuring a plurality of data sources to form an abstract data source, and configuring the plurality of data sources through the abstract data source proxy; in the service that needs to access the database, annotating the alias of the database that the service needs to access before the service class name by the service annotation; when executing data access, the dynamic proxy intercepting the service method of accessing the database, obtaining the database alias injected into the object in the service annotation mode, and obtaining the database connection parameter from the configuration information according to the database alias; generating an instance of a database access object corresponding to the data source; obtaining the database access connection and passing the connection to a subsequent invocation method. In the method of the invention, the program does not need hard-coded database connection, and the parameters of the service component are connected with the database and decoupled by the recessive transmission parameter.
Owner:南京汇银迅信息技术有限公司
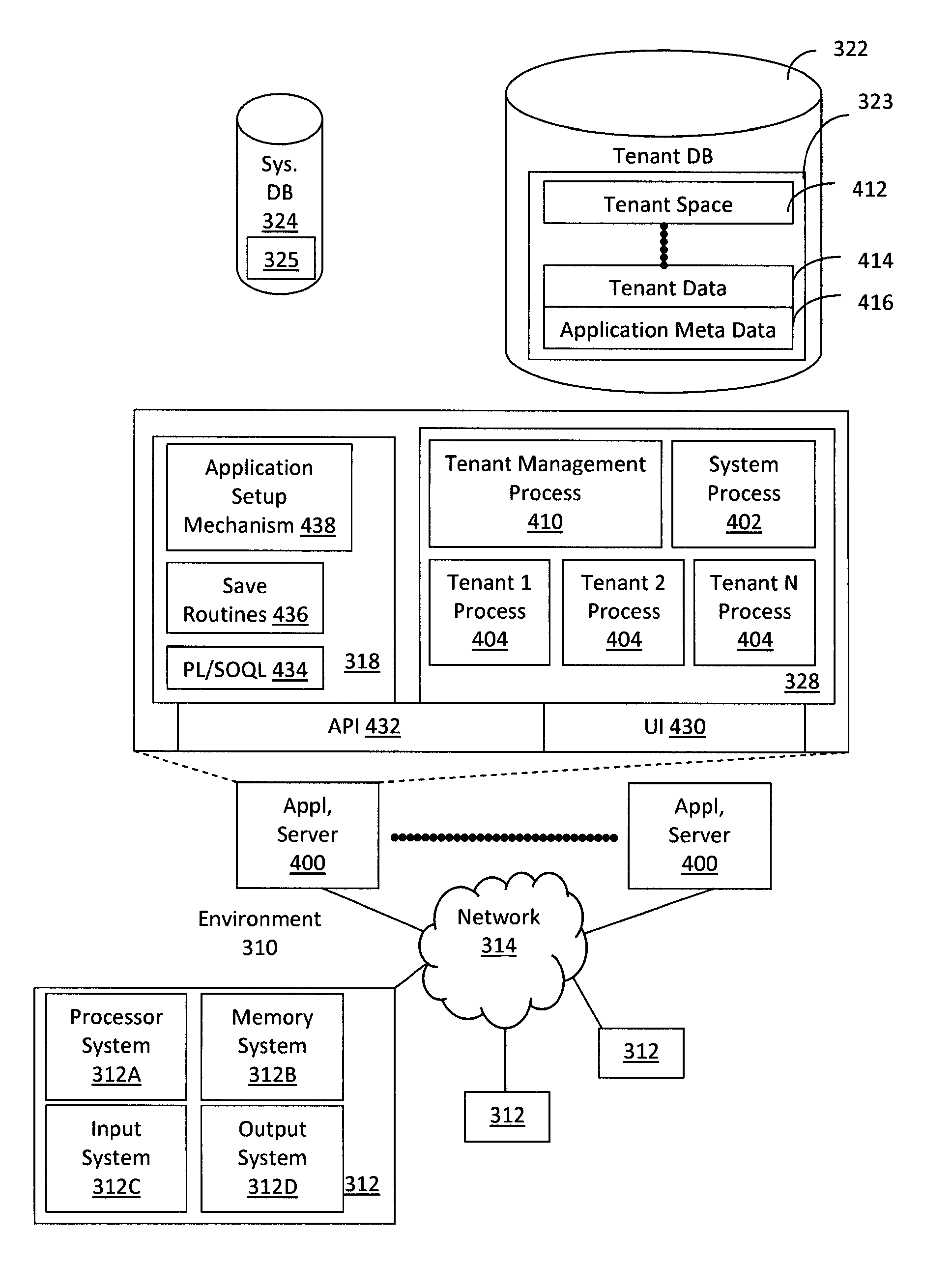
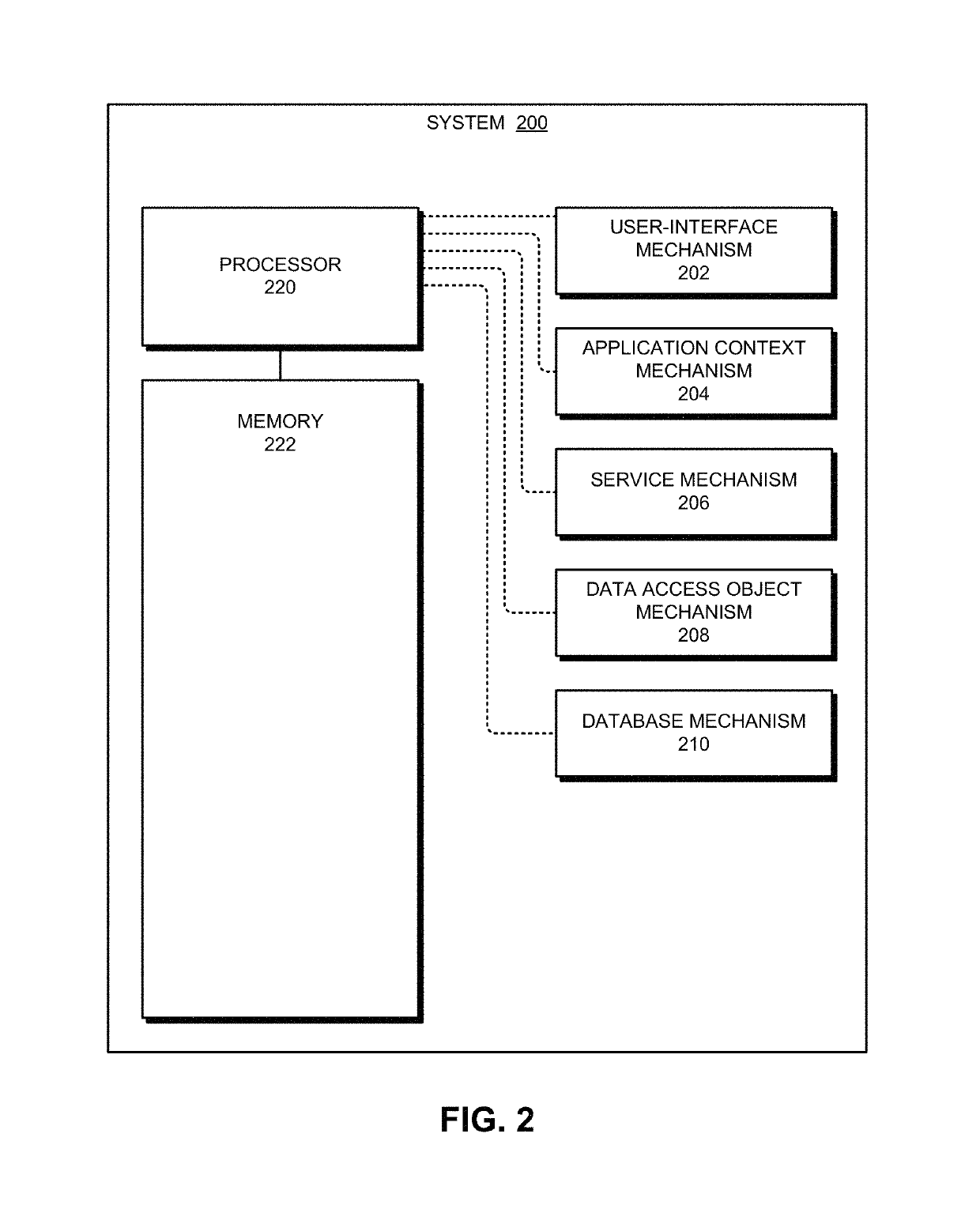
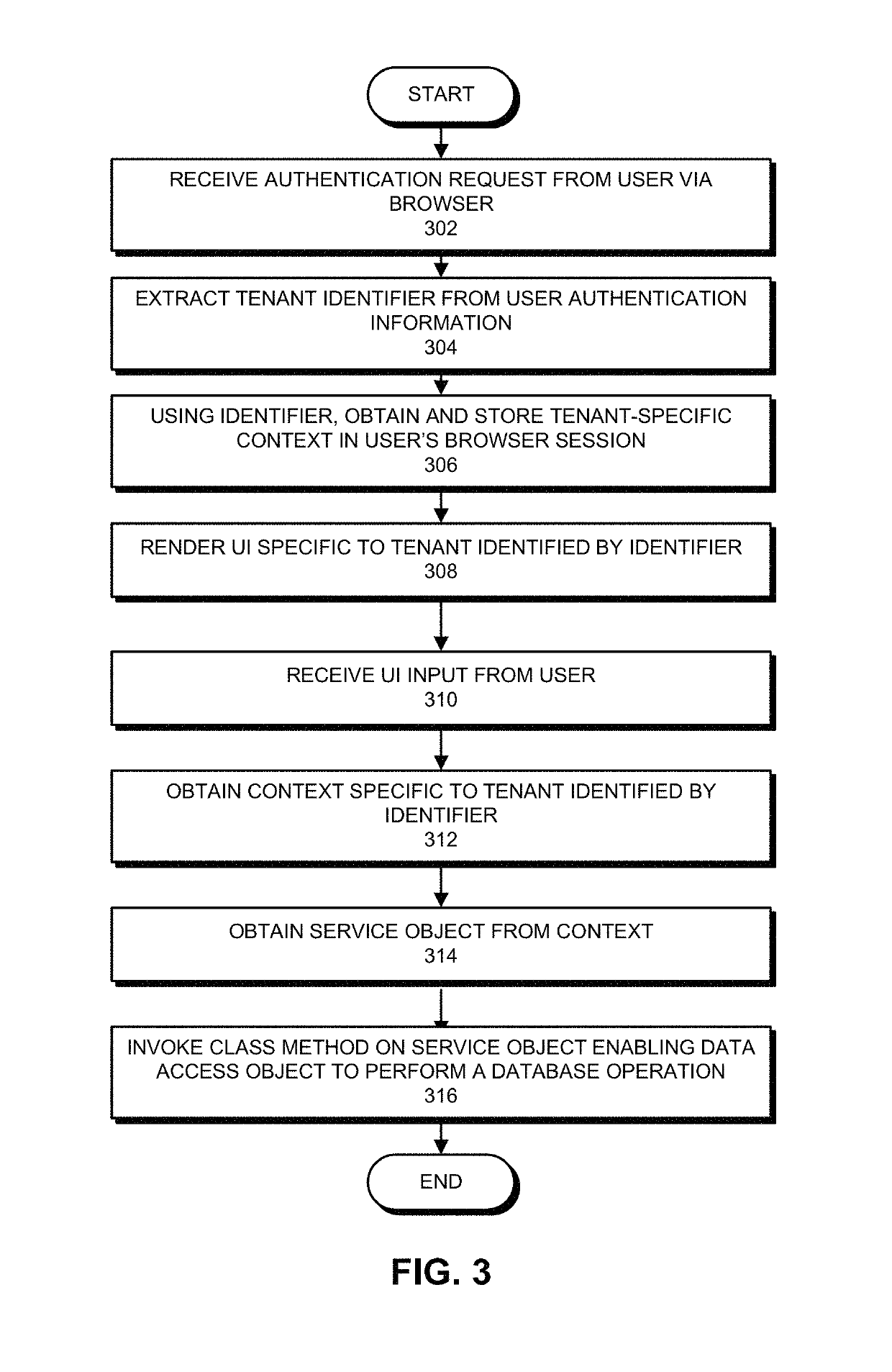
System for supporting a multi-tenant data architecture
ActiveUS10250453B1Input/output for user-computer interactionComputer security arrangementsData access objectApplication software
One embodiment of the present invention relates to a system that enables a single software application instance to support multiple tenants, wherein each tenant is associated with a separate database. First, the software application instance receives an input, wherein the input requires an operation to be performed on a database of one of the supported tenants. Next, the software application instance identifies the tenant with which the input is associated. The software application instance then obtains a context associated with the tenant. From the context, the software application instance obtains a service object. Finally, the software application invokes a method provided by the service object's class. This enables a data access object, which is encapsulated within the service object, to perform the operation on the database.
Owner:INTUIT INC
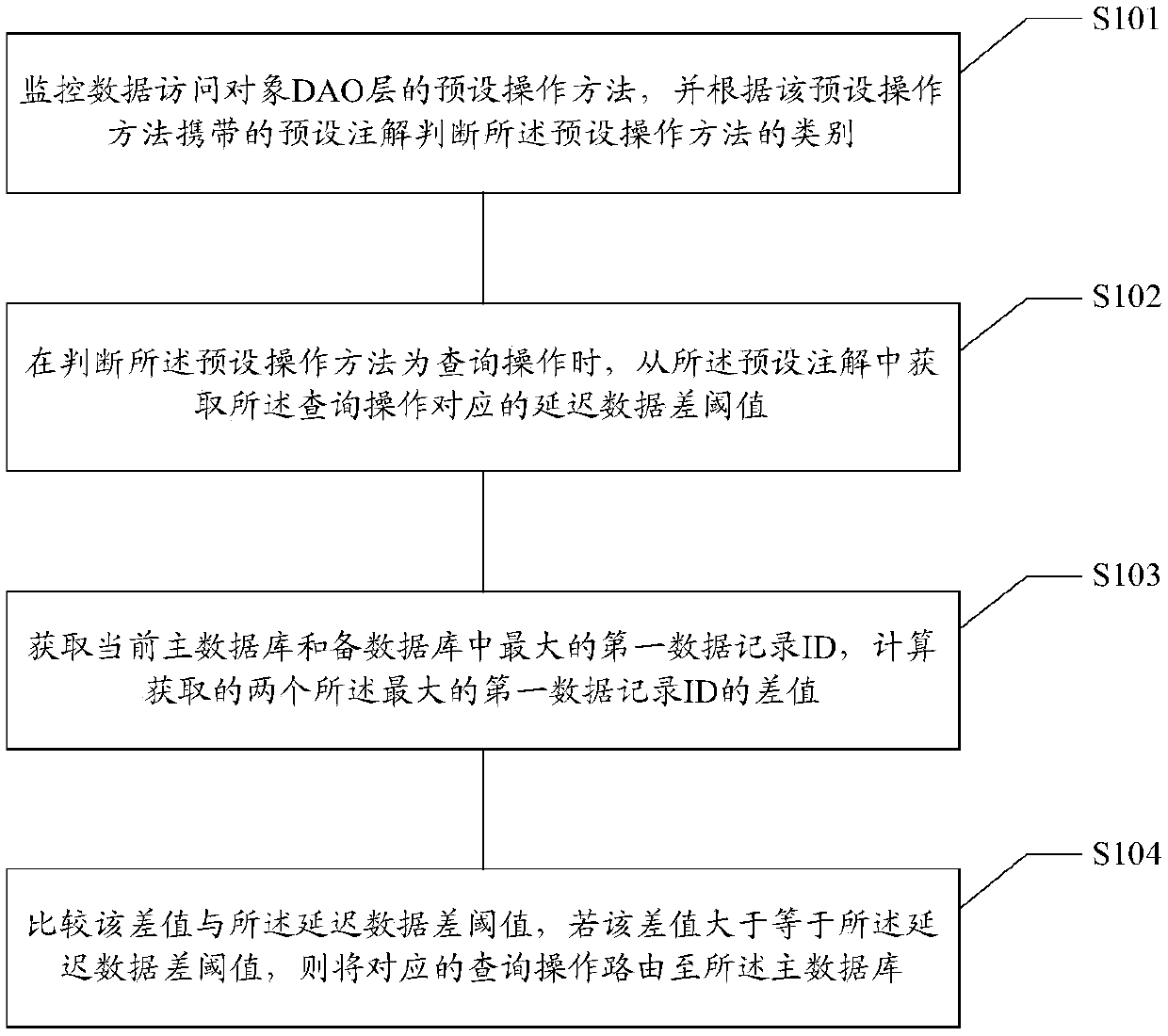
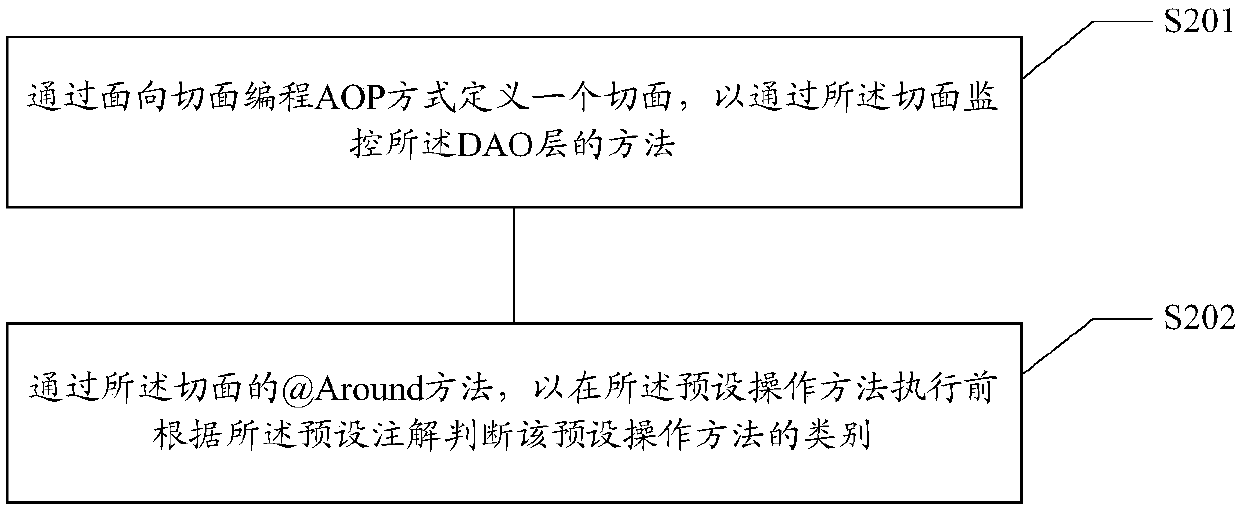
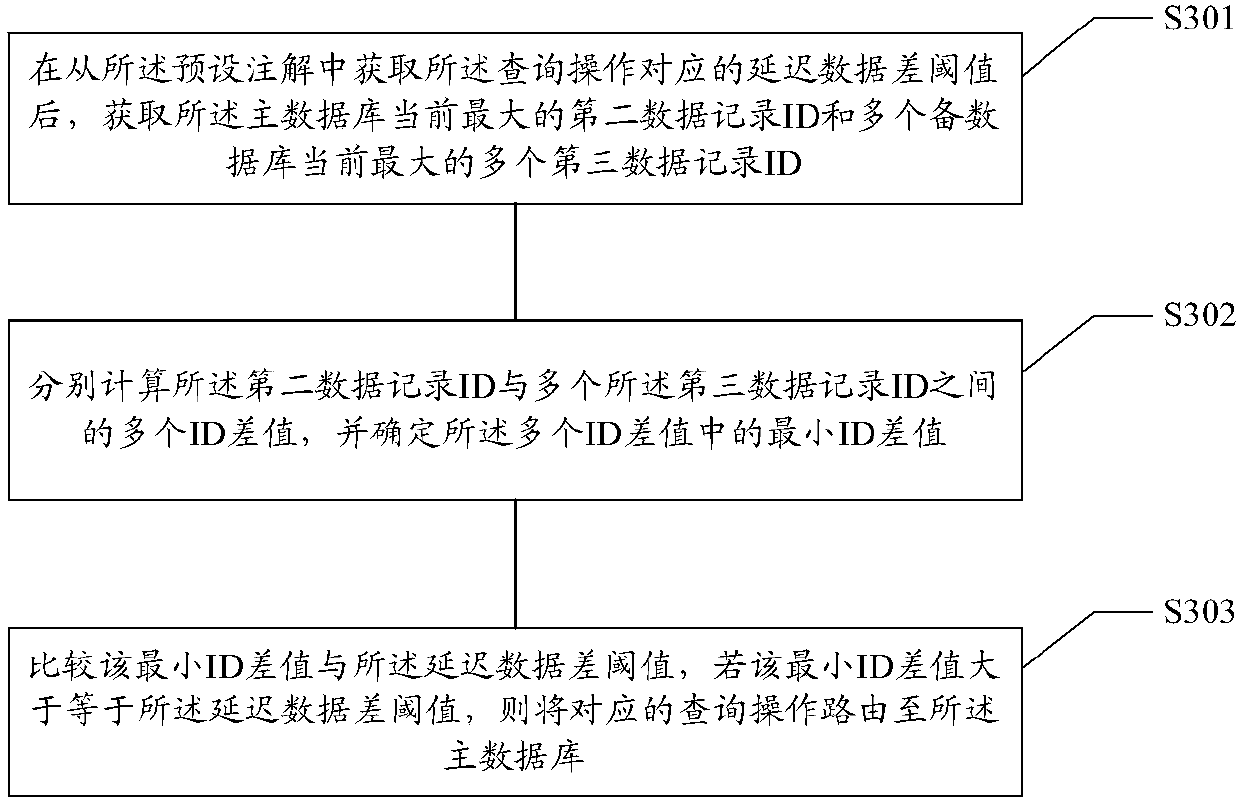
Main and standby database delay time processing method and device, medium and electronic equipment
InactiveCN110019257AImprove developmentSave manpower and material costsDatabase updatingDatabase distribution/replicationDelayed timeMaterial resources
The invention relates to a main and standby database delay time processing method and device, a storage medium and electronic equipment. The method comprises the following steps: monitoring a preset operation method of a data access object DAO layer, and judging the category of the preset operation method according to a preset annotation carried by the preset operation method; when it is judged that the preset operation method is a query operation, obtaining a delay data difference threshold value corresponding to the query operation from a preset annotation, wherein the delay data differencethreshold value is in direct proportion to the read-write delay time; obtaining the maximum first data record ID in the current main database and the standby database, and calculating the difference between the two obtained maximum first data record IDs; and comparing the difference value with a delay data difference threshold, and if the difference value is greater than or equal to the delay datadifference threshold, routing the corresponding query operation to the main database. According to the invention, different read-write delay times can be set for different service scenes, the application range is wide, the scheme development is simple and convenient, and the manpower and material resource cost is saved.
Owner:BEIJING JINGDONG SHANGKE INFORMATION TECH CO LTD +1
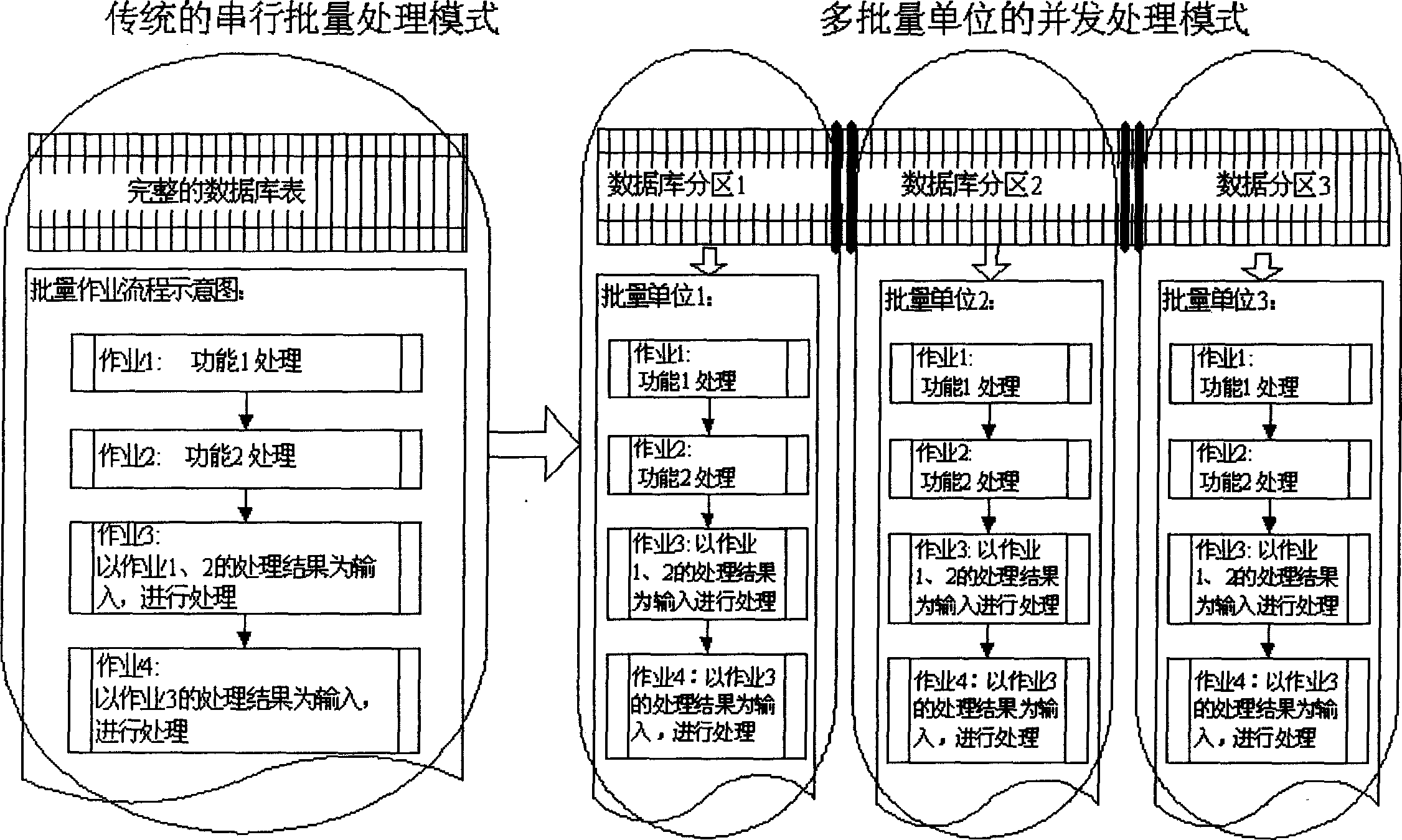
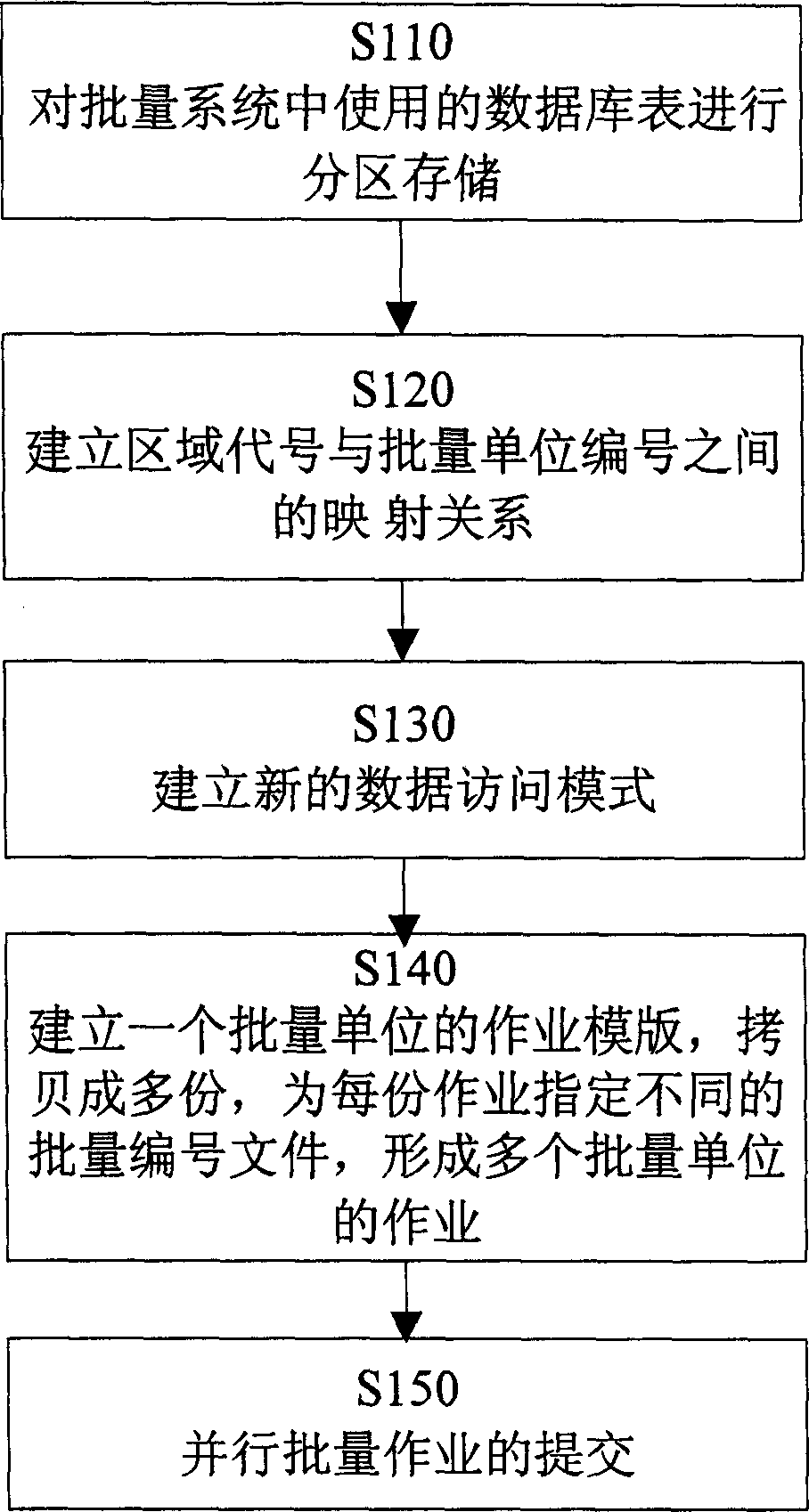
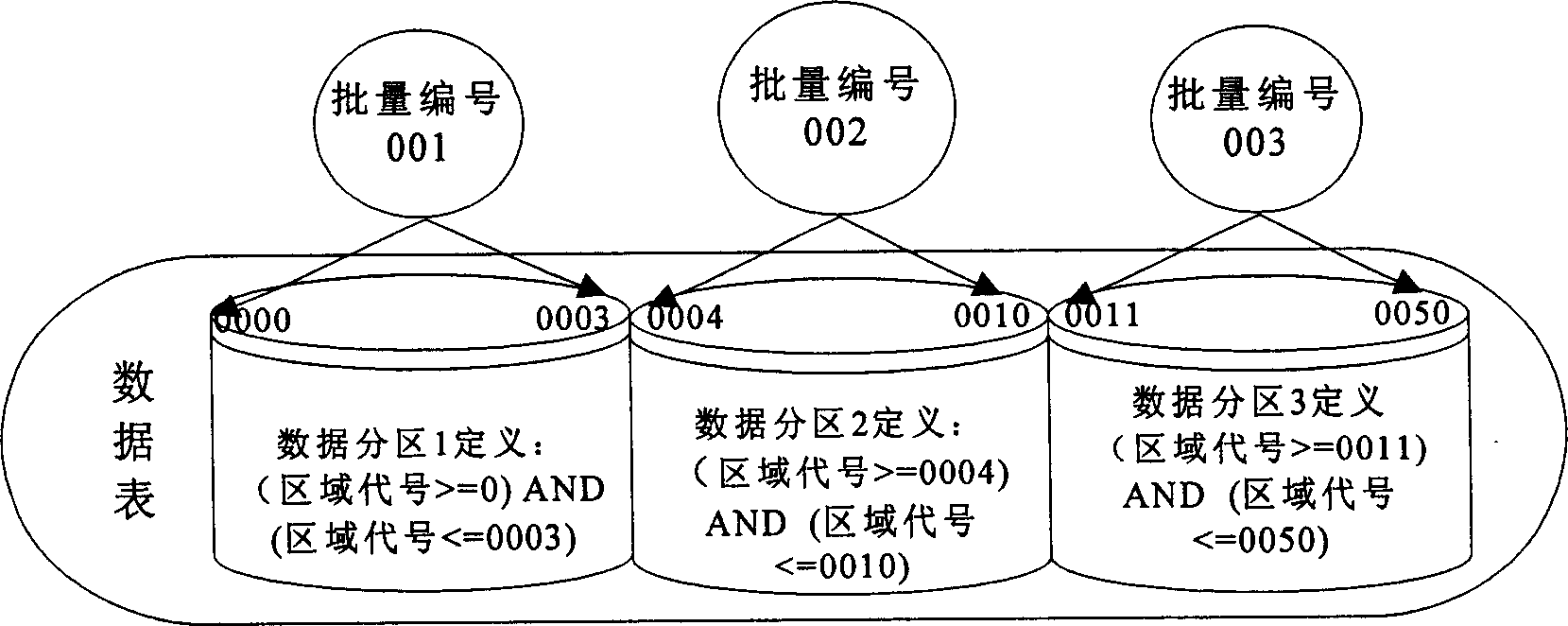
Parallel batch processing method
InactiveCN1794285AReduce running timeImprove processing efficiencyFinanceSpecial data processing applicationsBatch processingData access
This invention discloses a parallel batch process method, in which, said batch unit includes at least one operation being carried out and the method includes: dividing a database table into multiple sub-areas physically and storing the data corresponding to a pre-designed region with a code name of the region in it, setting up an image list between the code names and numbers of the batch units, setting up a data access mode to limit the data sphere of the operation access of the batch units in the sphere imaged by the region code names and numbers of the units, copying the operation in the pre-designed batch unit to multiple ones to form multiple batch units and presenting said multiple batch units in parallel.
Owner:INDUSTRIAL AND COMMERCIAL BANK OF CHINA
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com