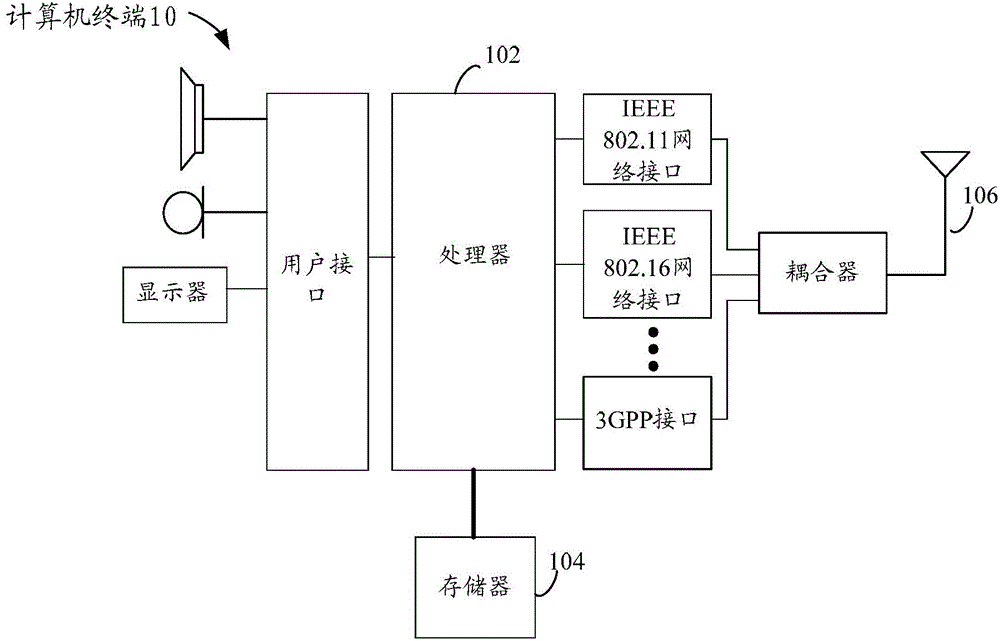
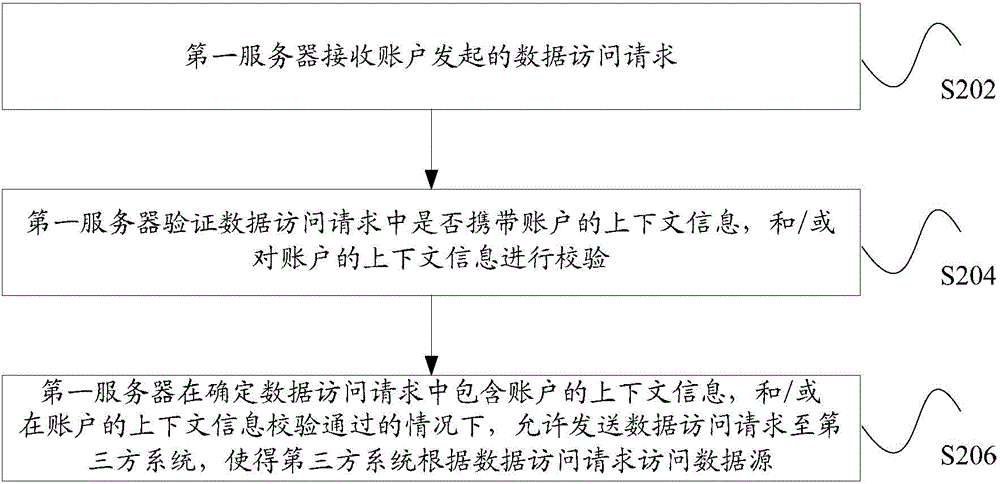
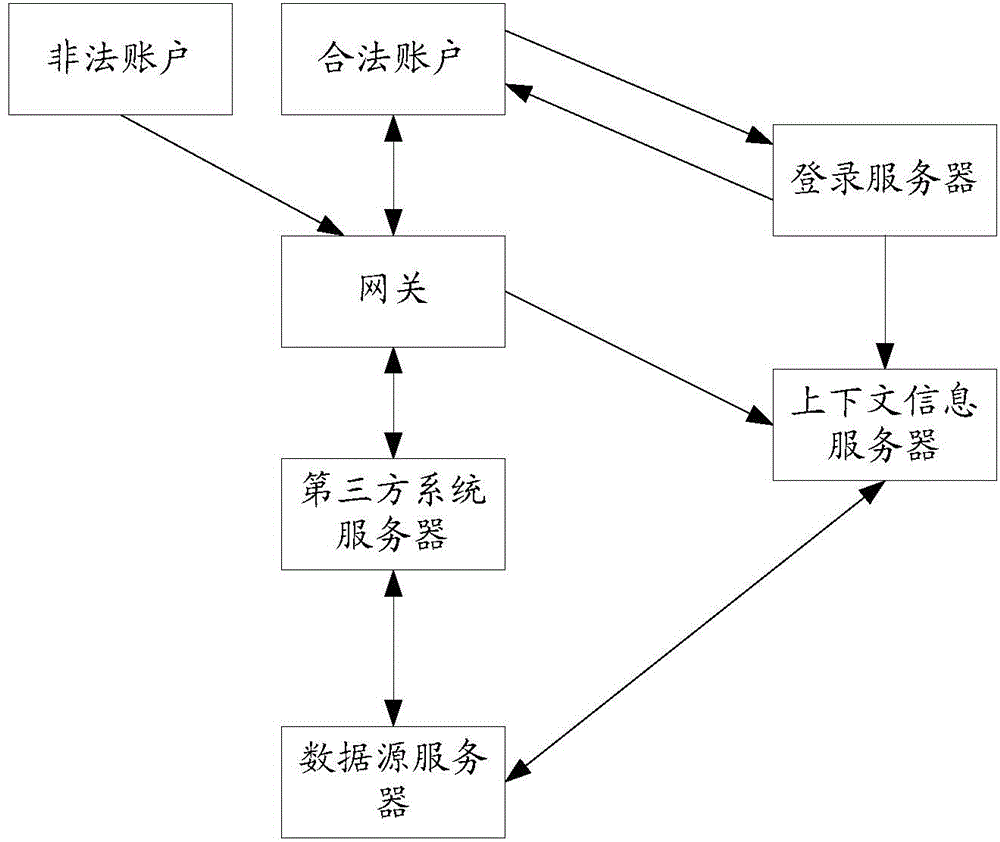
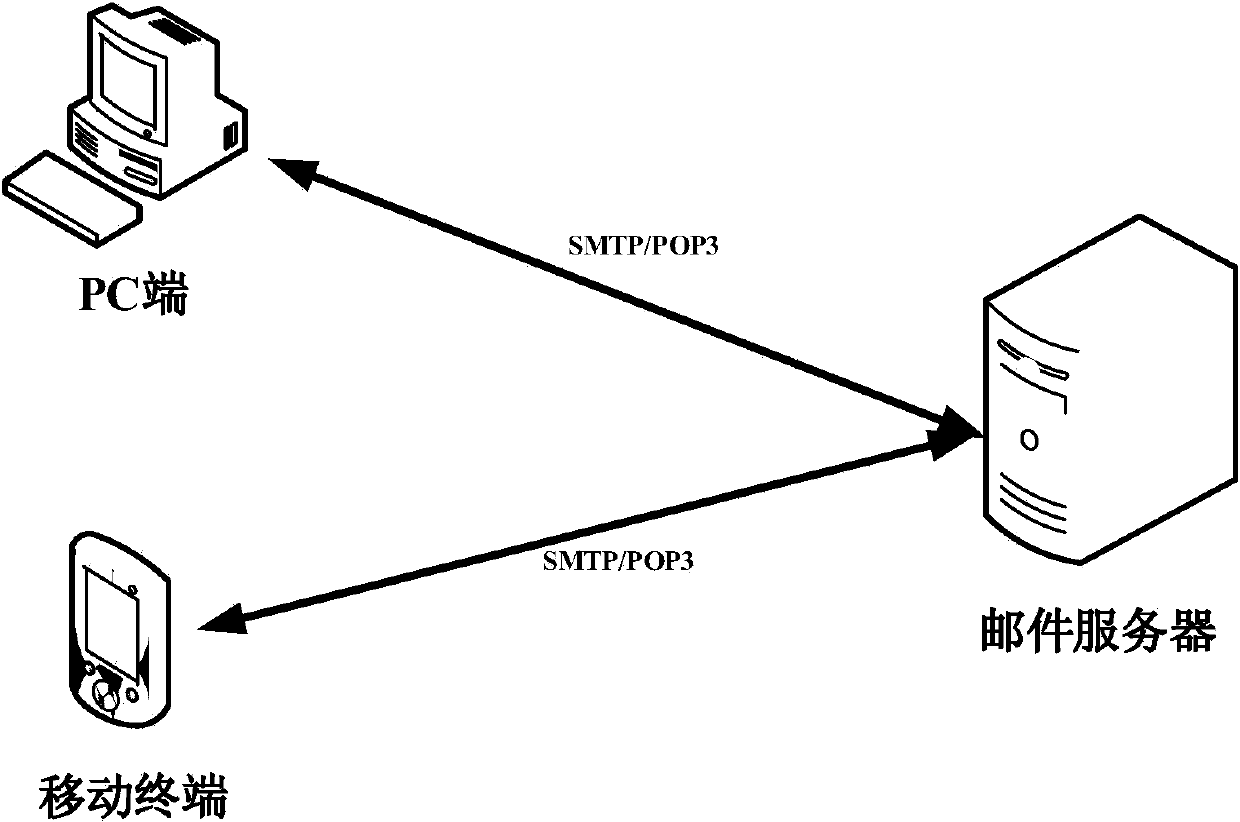
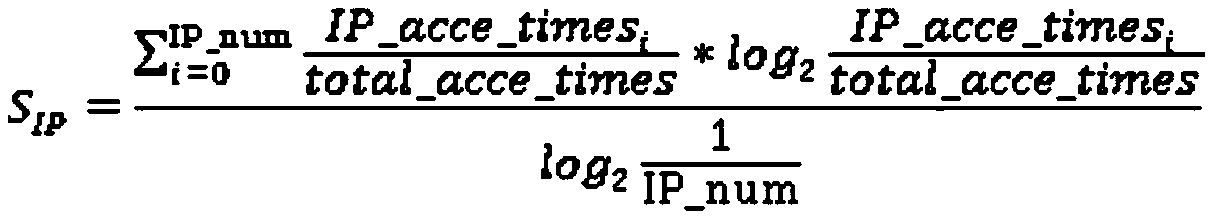Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
78results about How to "Prevent Data Leakage" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
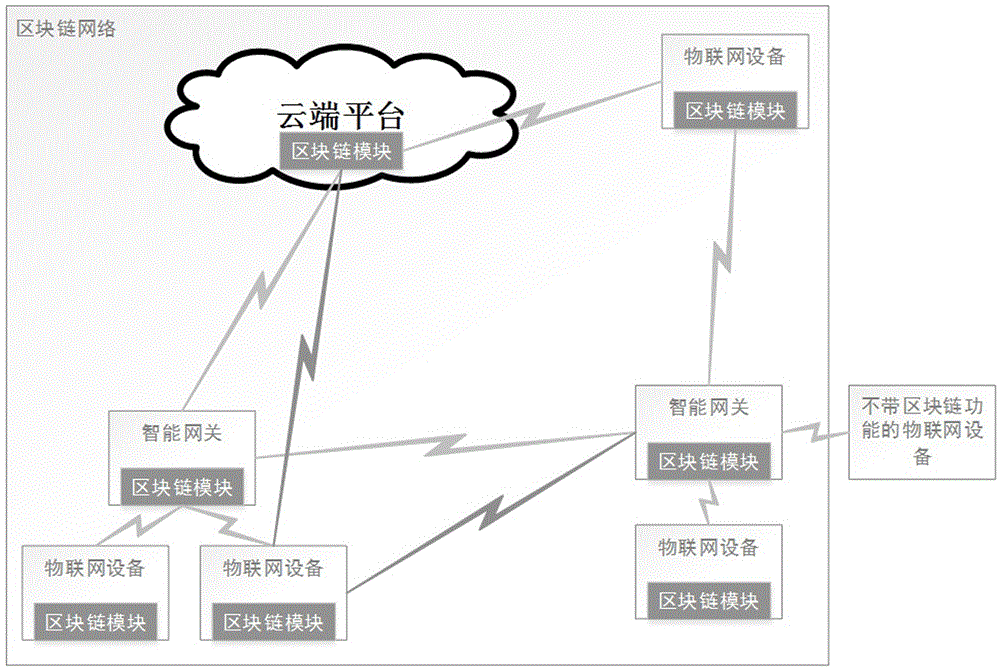
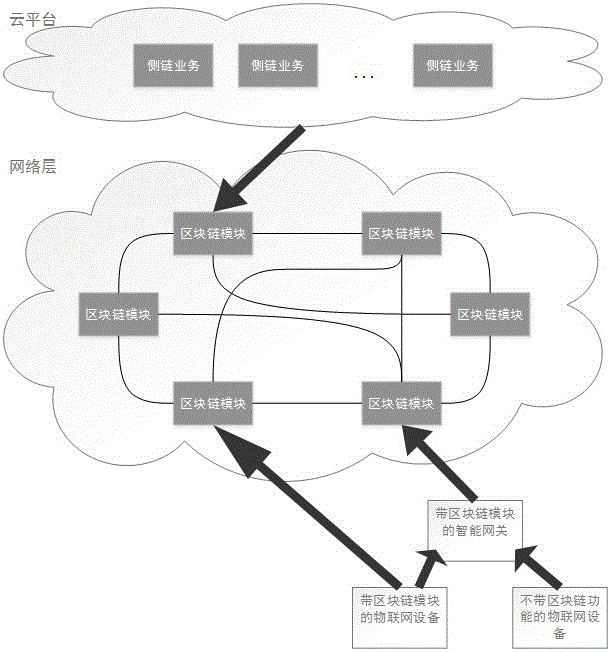
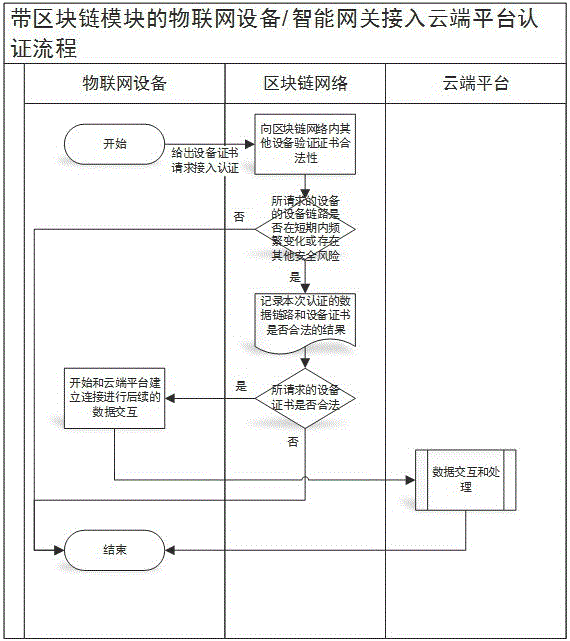
Access authentication method of internet-of-things fog device at cloud platform based on blockchain
The present invention relates to an access authentication method of an internet-of-things fog device at a cloud platform based on a blockchain. An internet-of-things device initiates an agent request of accessing a cloud platform to an intelligent gateway with a blockchain module through the means of device authentication; the blockchain module of the intelligent gateway accesses a blockchain network and gives out device certificate of the internet-of-things device and the device certificate of the intelligent gateway to the blockchain network for requiring authentication, wherein the blockchain network determines whether the request link of the intelligent gateway is frequently changed in a short period or has safety risk or not, and then verifies the legality of the intelligent gateway certificate; the same mode is employed to verify the legality of the device certificate of the internet-of-things device; and if the internet-of-things device with the blockchain module also can initiate the agent request of accessing the cloud platform, the authentication access mode is the same as the authentication mode of the intelligent gateway. The dependence on the cloud platform and the usage frequency are reduced, and the risks of the cloud platform being sniffered and injected at the aspect of the device access are reduced.
Owner:FUJIAN SHIDA COMP EQUIP
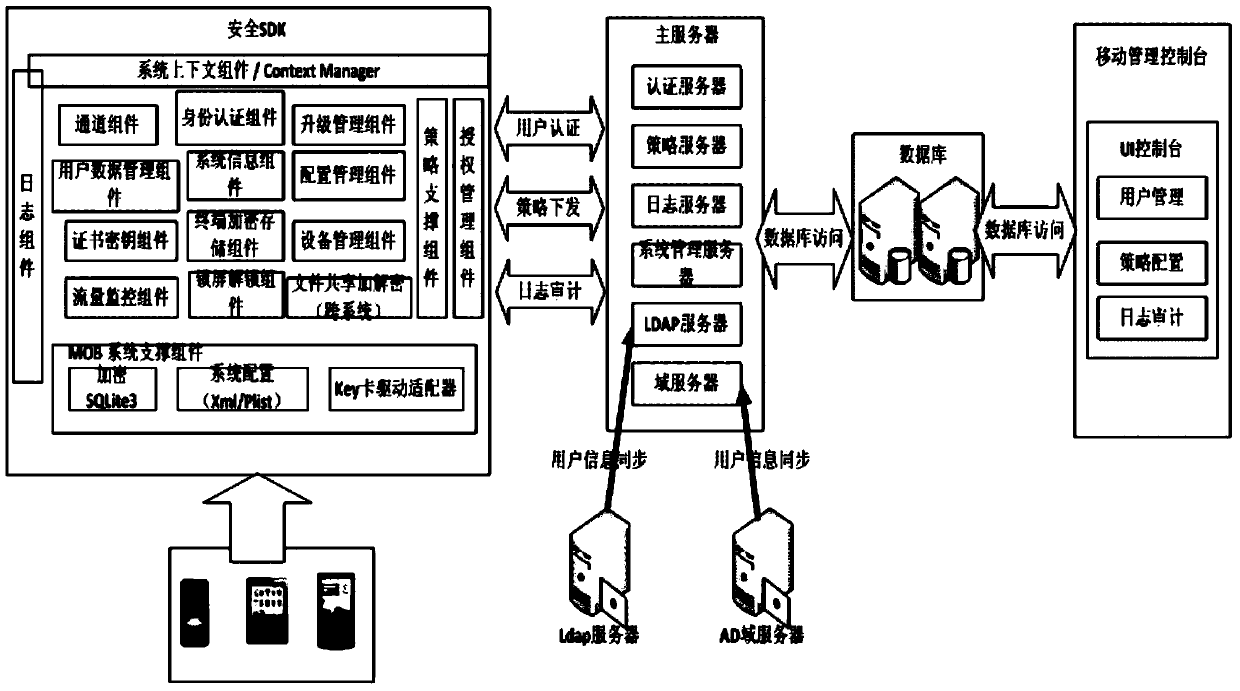
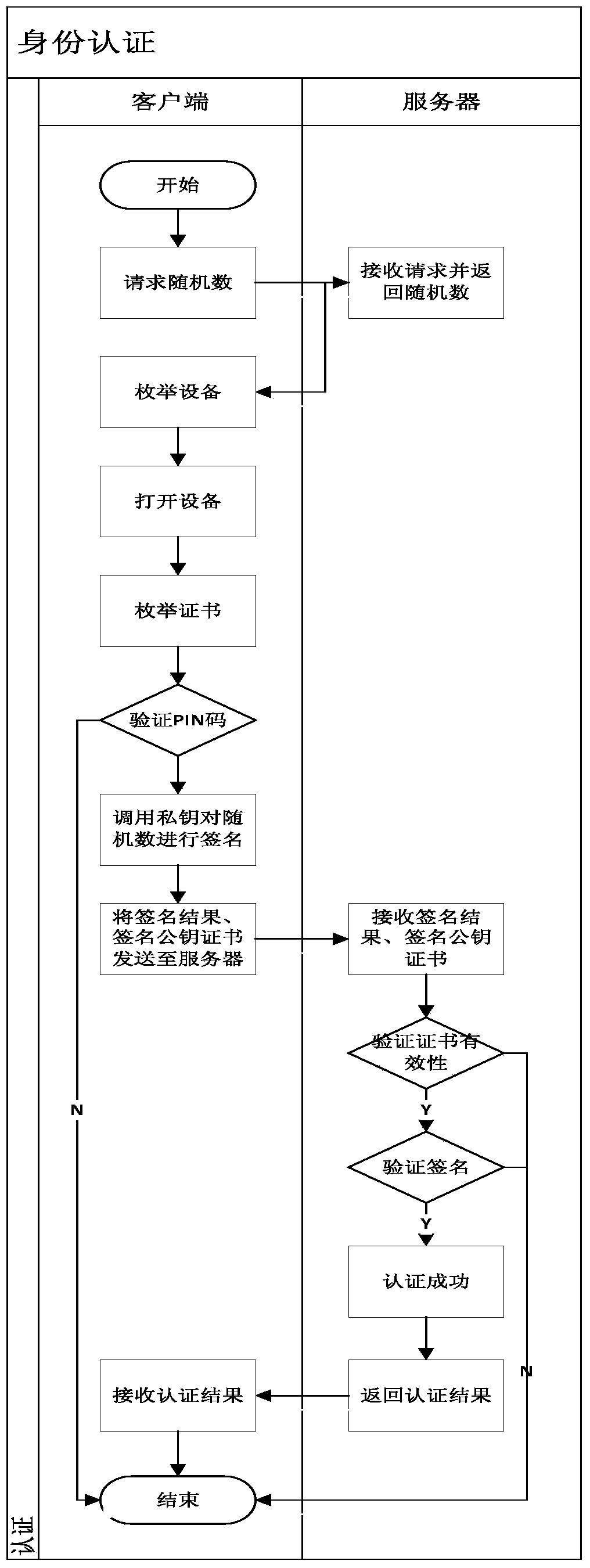
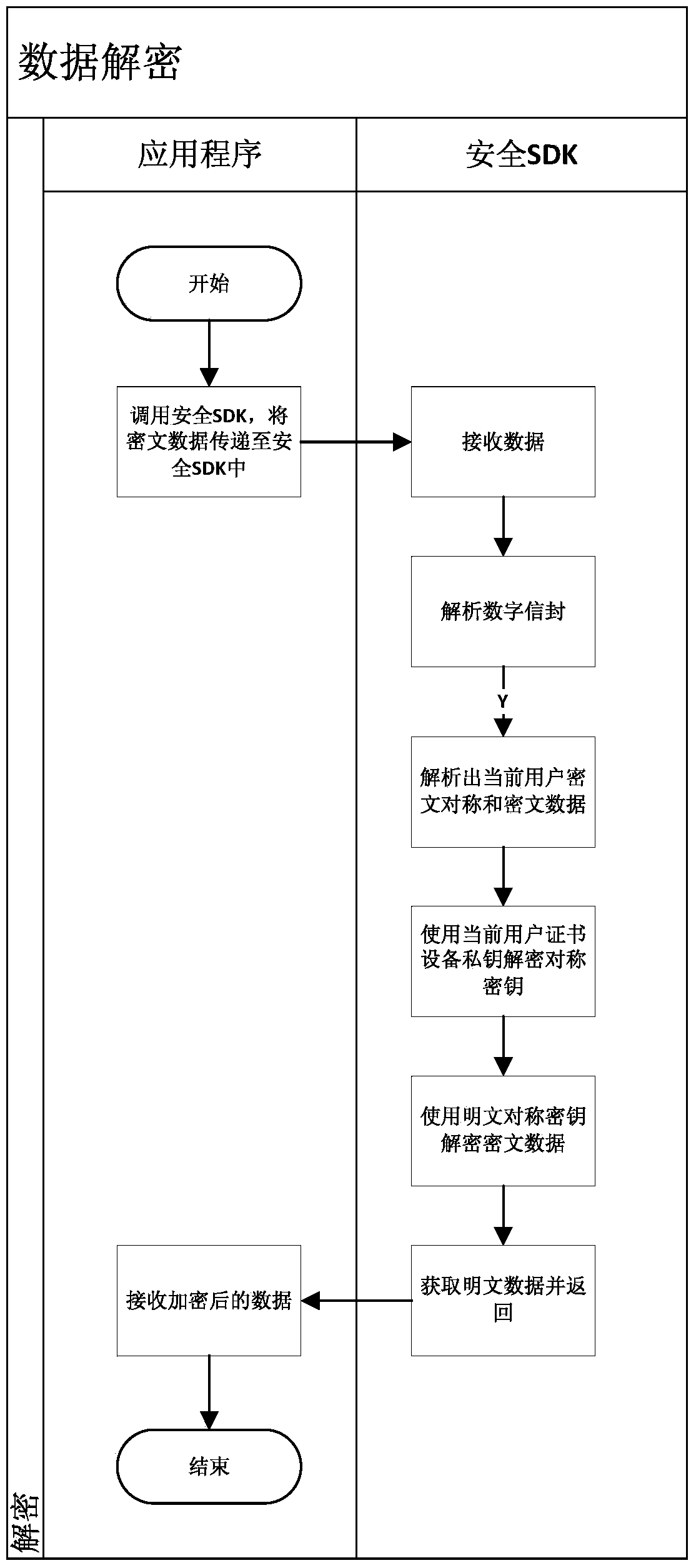
Development method and system based on mobile terminal application program security application
ActiveCN103812871AAvoid security issuesAvoid authenticationPublic key for secure communicationUser identity/authority verificationData informationCiphertext
The invention discloses a development method and system based on mobile terminal application program security application. The system comprises a sending terminal, a safe software development kit (SDK), a server and a receiving terminal. The method includes that the sending terminal requests a random number from the server, after the requested random number is received, a private key of the sending terminal is called to perform signing on the random number, and a signing result and a signing public key certificate are sent to the server; after the success of identity authentication, the safe SDK is called, received data information is encrypted through symmetric keys, the symmetric keys are encrypted by a public key of the receiving terminal, and encrypted symmetric keys and data information are sent to the receiving terminal; the receiving terminal calls the safe SDK to decrypt encrypted data. By means of the development method and system based on mobile terminal application program security application, related problems such as identity authentication, data breach and equipment controlling of data information safety are avoided.
Owner:北京明朝万达科技股份有限公司
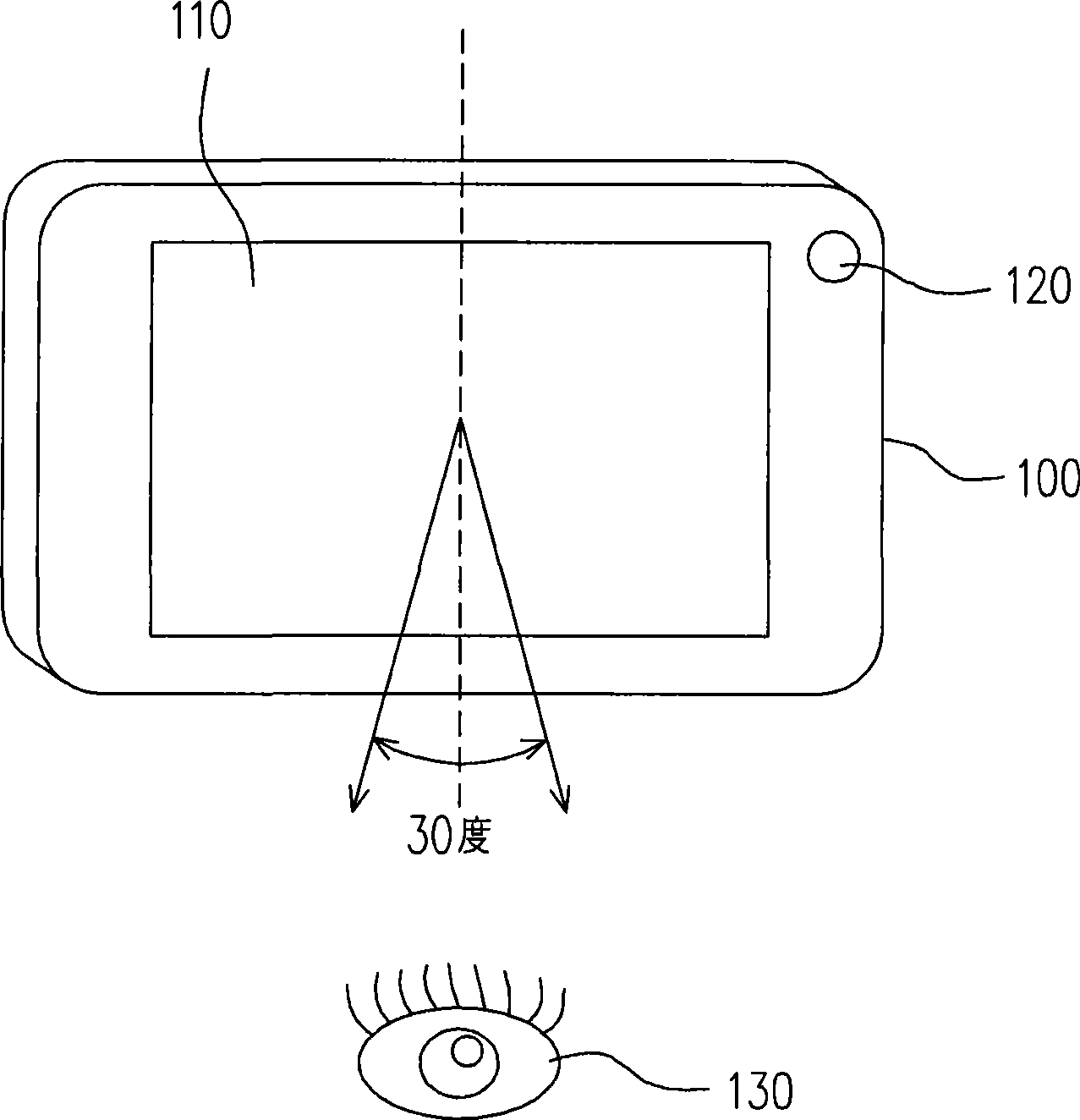
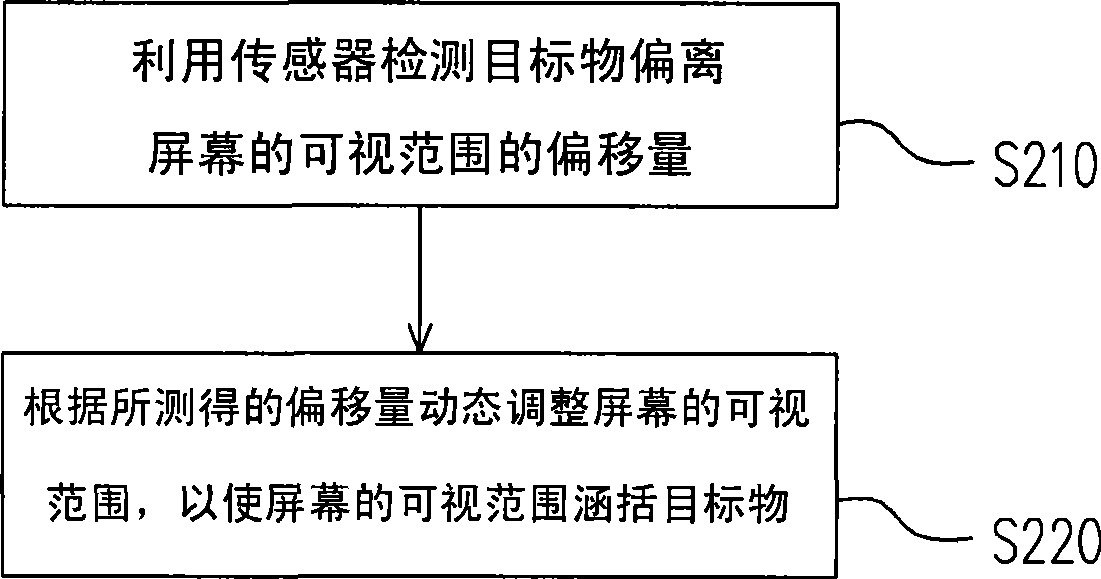
Method and apparatus for dynamically regulating visual angle of screen
ActiveCN101488326APrevent Data LeakageImprove convenienceCathode-ray tube indicatorsInstrumental componentsVisual rangeScreen viewing
The invention discloses a method for adjusting screen viewing angle dynamically and a device thereof. The method is applicable to adjust the screen visual range of a hand-hold electronic device dynamically; wherein the screen has adjustable viewing angles. The method comprises the following steps: detecting the offset of a target object deviating from the screen visual range, and then adjusting the screen visual range dynamically according to the offset so as to cause the target objects included in the screen visual range. Hereby, the method can prevent the contents of screen pictures from being peeped by others and is convenient for users to watch screen pictures.
Owner:HTC CORP
Identity authentication based virtual terminal safety environment protection method and system
ActiveCN103778384APrevent Data LeakageOperating habits have no effectDigital data protectionInternal/peripheral component protectionVirtual terminalData access
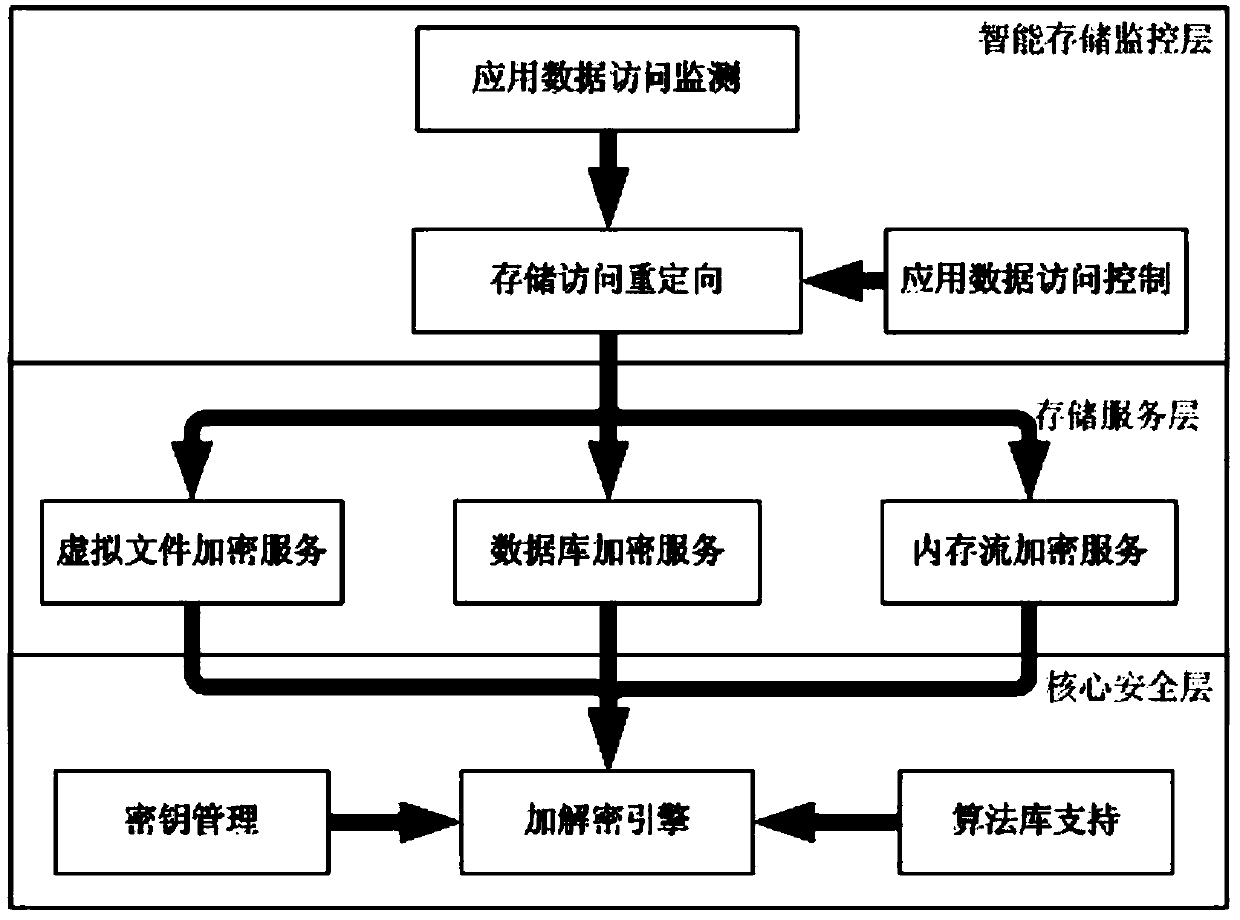
The invention discloses an identity authentication based virtual terminal safety environment protection method and system. The system comprises an intelligent storage monitoring layer, a storage serving layer, and a core safety layer, wherein the intelligent storage monitoring layer comprises a storage access redirecting module, is in charge of monitoring and analyzing data access acts of application programs, and performs actions according to configuration rules, the storage access redirecting module transfers input / output access according to access control rules, the storage serving layer is in charge of encrypting and decrypting files or data and recording file mapping relations, and the core safety layer is the basis of the whole framework, provides a key management function, provides encryption and decryption support for the storage serving layer, and dispatches different algorithms as desired. By means of the identity authentication based virtual terminal safety environment protection method and system, safety of core application data can be protected, data leakage is prevented, and data inside and outside the environment are isolated without influence and do not influence user operation habits.
Owner:北京明朝万达科技股份有限公司
Data protection method of USB storage device based on magnetic disc virtual technology
ActiveCN102567233ARealize data protection functionPrevent Data LeakageUnauthorized memory use protectionUser verificationComputer module
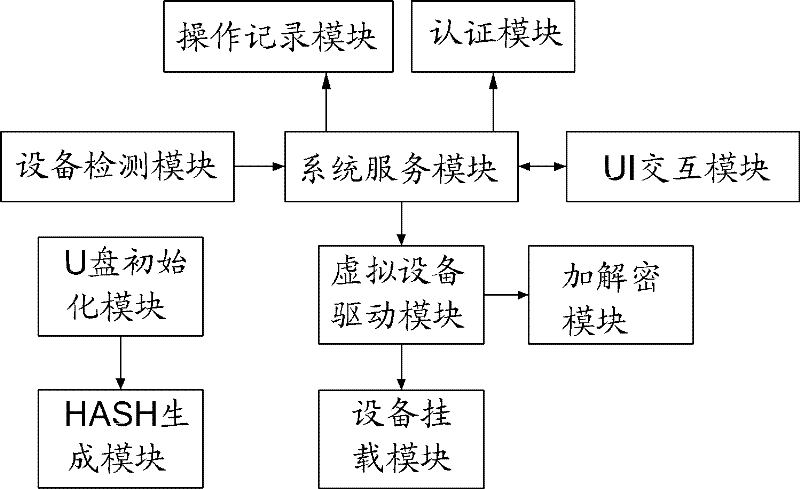
The invention provides a data protection method of a USB (Universal Serial Bus) storage device based on a magnetic disc virtual technology. The data protection method comprises the following steps: 10) generating a U-disc verification key, a user verification key and an encryption and decryption key through a U-disc initialization module, dividing a U disc into an ordinary partition, an encryption partition and a log partition, and hiding the encryption partition and the log partition; 20) enabling the encryption and decryption key to disappear after performing strategy encryption on the U disc and saving the U-disc verification key and the user verification key; 30) calculating a user key through an authentication module by utilizing an access key, further calculating the encryption and decryption key by the user key and the user verification key and verifying a strategy and the U-disc verification key; 40) enabling authentication to succeed, accessing the encryption partition by a user, and operating a recording module to record an operation action of the encryption partition into the log partition; and 50) terminating access and relieving the carrying between a virtual device and a window roll through a device carrying module. According to the data protection method disclosed by the invention, the data protection function of the USB storage device can be realized in a software layer.
Owner:FUJIAN CENTM INFORMATION
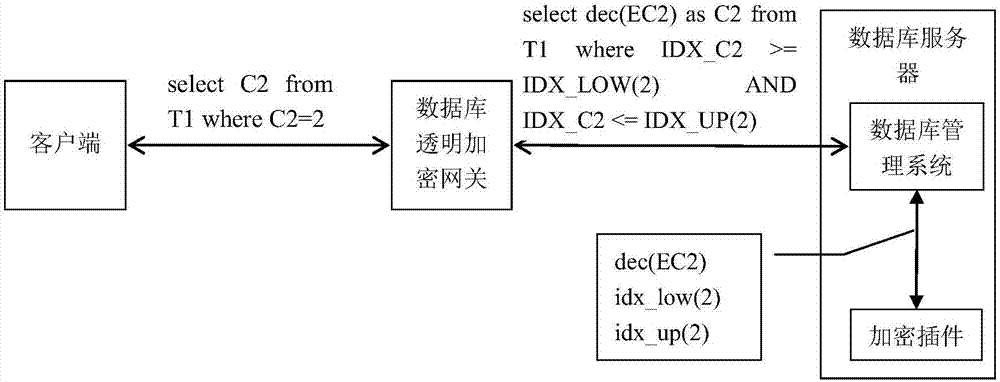
General database transparent encryption system
ActiveCN106934298APrevent Data LeakageImprove versatilityEncryption apparatus with shift registers/memoriesDigital data protectionDatabase encryptionUser-defined function
The invention relates to a general database transparent encryption system and belongs to the fields of information security and database encryption technologies. According to the system, first, an existing data table is subjected to encryption transformation, the table where an encrypted field P1 exists is recorded as T1, and a ciphertext index field I1 is established based on the encrypted field P1; and then, the content of a to-be-encrypted field is mapped to a Hash value based on an order-preserving Hash function, and the Hash value is used as an index value to be interposed into the field I1. The system comprises an SQL gateway module and an encryption plug-in module, wherein the SQL gateway module is used for receiving and rewriting an SQL statement sent by a client, sending the SQL statement to a database server and forwarding a result returned by the database server to the client; and the encryption plug-in module is located in a database, mainly comprises a series of user-defined functions (UDFs) and achieves encryption, decryption and ciphertext indexing functions according to the SQL statement obtained after rewriting. Compared with the prior art, the truly-general database encryption system is realized.
Owner:戴林
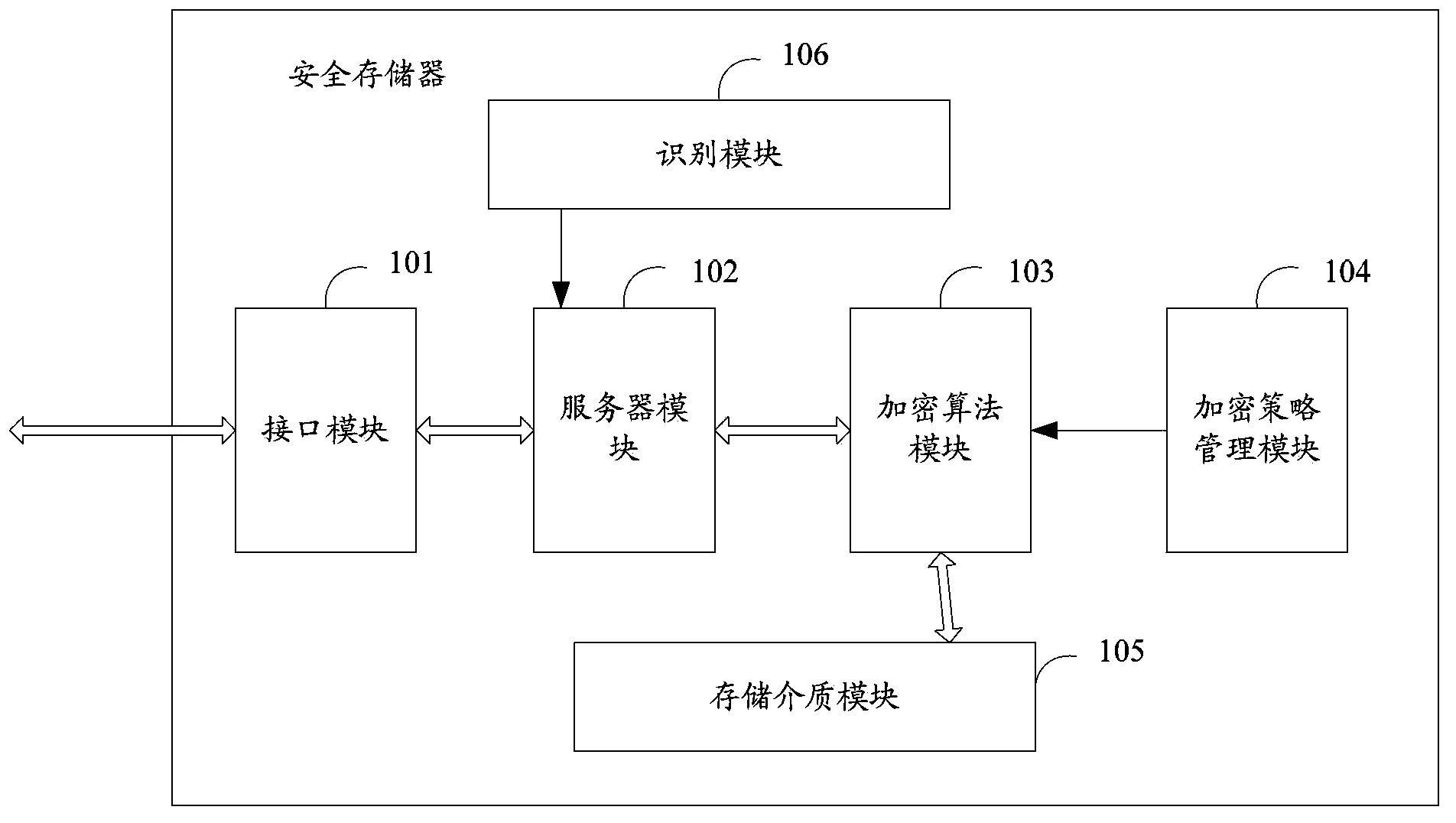
Secure storage device
ActiveCN104239820AAchieve securityPrevent Data LeakageInternal/peripheral component protectionLocal machineComputer hardware
The invention discloses a secure storage device which comprises an interface module, a server module, an encryption algorithm module, an encryption strategy management module, a recognition module and a storage medium module. The server module is used for providing an operating system and file processing programs of the storage device, receiving file access requests from a local computer of a user, converting operation results into images, and transmitting the images to the local computer of the user through the interface module. The encryption algorithm module is used for extracting an encryption strategy from the encryption strategy management module, adopting the encryption strategy to carry out encryption on files according to random seeds formed by the recognition module and file characteristic information and then storing the files in the storage medium module and is also used for adopting the encryption strategy to carry out decryption on the files stored in the storage medium module according to encryption seeds formed by the recognition module and the file characteristic information. The recognition module is used for receiving information input by the user to generate the random seeds which are used as initial indexes of other secret keys.
Owner:POTEVIO INFORMATION TECH
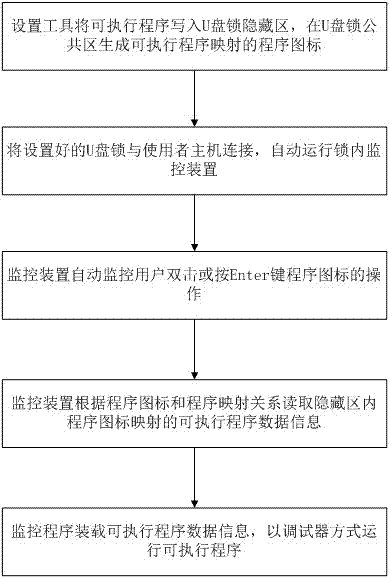
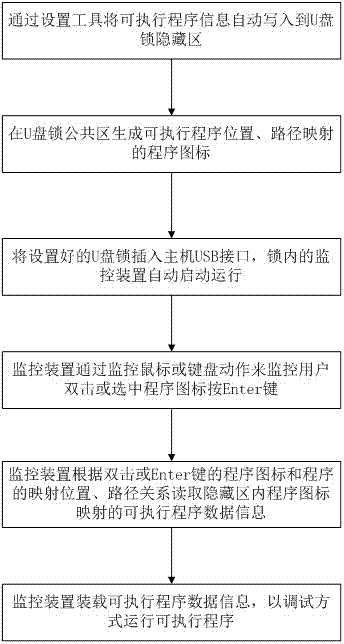
Protection method and device for executable programs
ActiveCN103488919APrevent memory dumpsPrevent Data LeakageProgram/content distribution protectionData informationExecutable
The invention relates to a protection method and device for executable programs. The method comprises writing information of the executable programs in hidden areas of storage devices, generating mapped icons corresponding to the information of the executable programs; starting monitoring apparatuses automatically when the storage devices and hosts are connected, wherein the monitoring apparatuses monitor double click of icons in common areas or Enter key operations; reading program data information corresponding to the icons form the hidden areas according to mapping relations; executing executable files in a debugger mode. By the aid of the method, data leakage caused by program copying can be prevented, debugging and cracking difficulties are increased, and the security is improved.
Owner:BEIJING SENSESHIELD TECH
Blockchain foundation-based three-dimensional (3D) printer for internet of things
InactiveCN106776431AMeet the needs of print jobsImprove securityAdditive manufacturing apparatusDigital data protectionCode moduleThe Internet
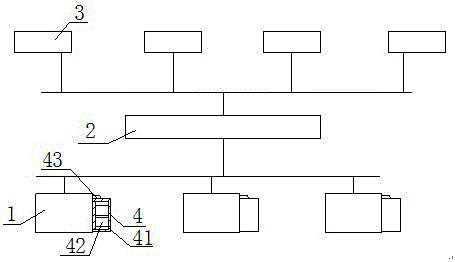
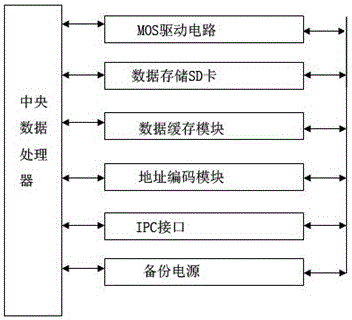
The invention relates to a blockchain foundation-based three-dimensional (3D) printer for internet of things. The 3D printer comprises printers, a communication network and control computers, wherein the plurality of printers are respectively connected with the control computers by the communication network, and all the printers are connected in parallel; the plurality of control computers respectively form at least one control local area network by means of the communication network; the printers are respectively provided with a blockchain control device; the blockchain control devices are respectively connected with the printers and the communication network; each blockchain control device comprises a bearing shell, a backup power, a central data processor, a metal oxide semiconductor (MOS) drive circuit, a data storage secure digital (SD) card, a data caching module, an address coding module and an inter-process communication (IPC) interface. The blockchain foundation-based 3D printer for the internet of things is simple in structure and flexible and convenient to use, can effectively meet the need of carrying out file printing operation from a long distance through the network on one hand, and can effectively improve the safety and reliability of file transfer and response during file printing on the other hand so as to prevent the phenomenon of data leakage.
Owner:CHENGDU YUYA TECH
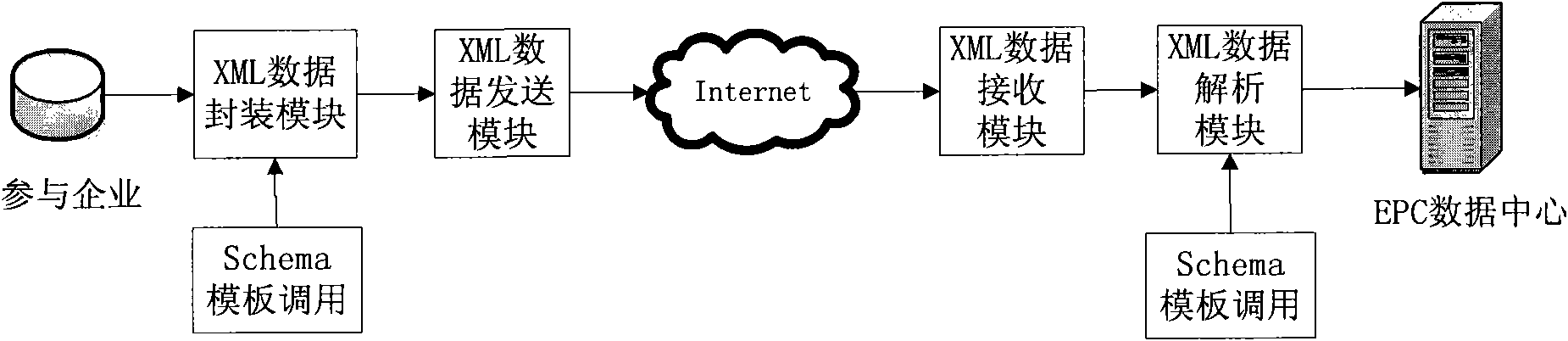
EPC engineering data processing system and method in complex network environment
InactiveCN101799894AShorten the timeCut costsSpecial data processing applicationsData processing systemData center
The invention provides an EPC engineering data processing system and method in complex network environment. The data processing system comprises an EPC data centre, an output Schema template calling module, an XML data file sending module, a network connecting a data transmitting terminal and a data receiving terminal, an XML data file receiving module and an input Schema template calling module, wherein the EPC data centre is used to accumulate data of all users; the output Schema template calling module is used to call an exported Schema module, establish an output Schema module and then generate an XML data file; the XML data file sending module is used to send the XML data file to a recipient through a network; the XML data file receiving module is used to receive the XML data file; and the input Schema template calling module is used to call an input Schema module, establish an input Schema module and then generate an XML data file. By using the system of the invention, good data safeguard is provided for the business integration among enterprises without changing the business process within the enterprises.
Owner:BERIS ENG & RES CORP
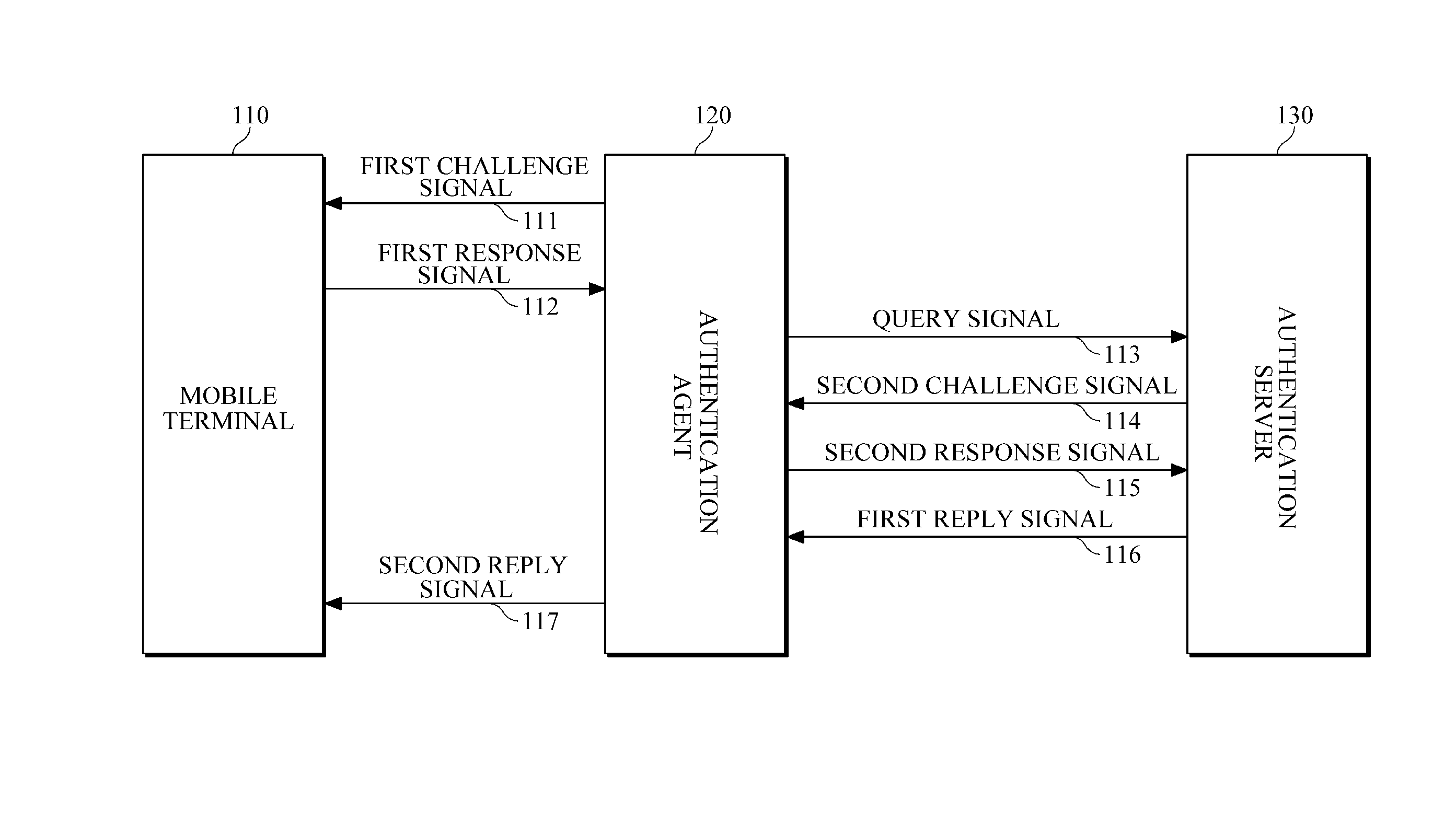
Mutual authentication system and method for mobile terminals
InactiveUS20120166801A1Avoid data breachesEfficient updateDigital data processing detailsUser identity/authority verificationAuthentication systemMutual authentication
Provided is a technique for mutual authentication between different kinds of objects (devices, apparatuses, users, etc.) by expanding the kinds of objects that are subject to authentication, such as authentication between users, authentication between users and an apparatuses (devices, equipment, terminals, etc.), and authentication between apparatuses (devices, equipment, terminals, etc.).
Owner:ELECTRONICS & TELECOMM RES INST
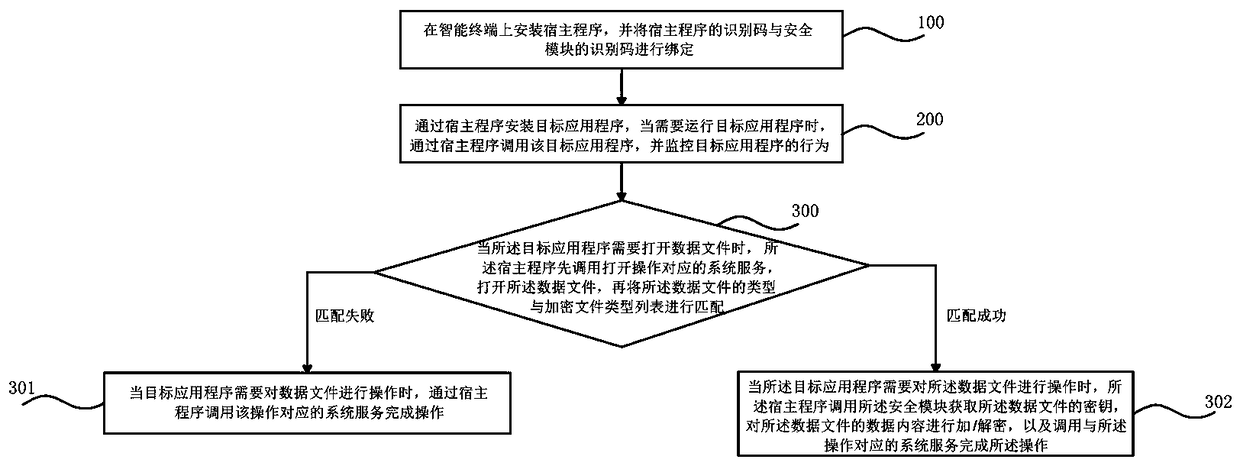
Application data leakage preventing method and apparatus
ActiveCN108509802AHighlight substantiveSignificant progressKey distribution for secure communicationMultiple keys/algorithms usageComputer moduleData file
The invention discloses an application data leakage preventing method and apparatus. A host program and a use security module are installed in an intelligent terminal; system services are interceptedand agented through the host program; installation, calling, monitoring and management of a target application are realized; hardware encryption is realized through a security module; different keys are allocated for data files of the target application, and encryption and decryption of the keys are finished; and transparent encryption and decryption of data are realized by using particular keys for the data files needed to be encrypted. The target application accesses the data files only through the host program bound with the security module, so that the target application is enabled to runin a tight secret running space, and the data of the target application only can be used in the secret running space. According to the technical scheme, application data leakage is prevented more effectively, so that the application data has higher security.
Owner:ZHENGZHOU XINDA JIEAN INFORMATION TECH
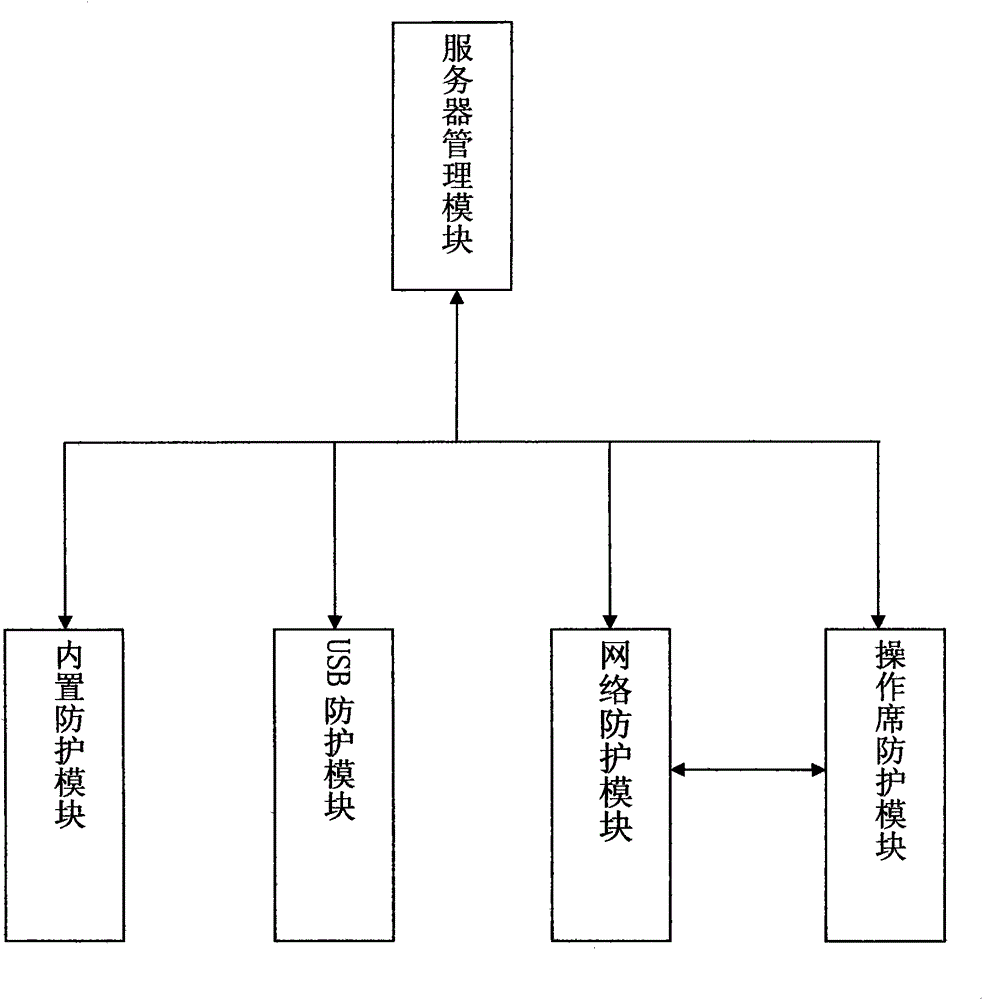
Information security protection system and method for video monitoring system
ActiveCN104581008ARestrict recording operationsRealize security protectionClosed circuit television systemsTransmissionVideo monitoringOperational system
The invention provides an information security protection system and method for a video monitoring system. The information security protection system comprises a server management module, a built-in protection module, a USB protection module, a network protection module and an operating seat protection module, performs security protection in four aspects, namely, a video monitoring center, a user terminal, a USB storage interface and networking of the video monitoring system, respectively, timely encrypts video files downloaded and exported from the video monitoring system as well as picture files produced by screenshot tools, performs security control on screenshots and screen records of operating systems during operations of the video monitoring center and the user terminal, and performs real-time monitoring on the network of the video monitoring system and the USB storage interface. The system and the method can provide data security protection for the video monitoring system and are complete in protection, high in extendibility, high in security, low in system resource occupation rate and good in user experience in terms of operation behavior.
Owner:慧盾信息安全科技(苏州)股份有限公司
User data access control method, device and system
ActiveCN106302332APrevent Data LeakageDigital data protectionSecuring communicationThird partyInternet privacy
Owner:ALIBABA GRP HLDG LTD
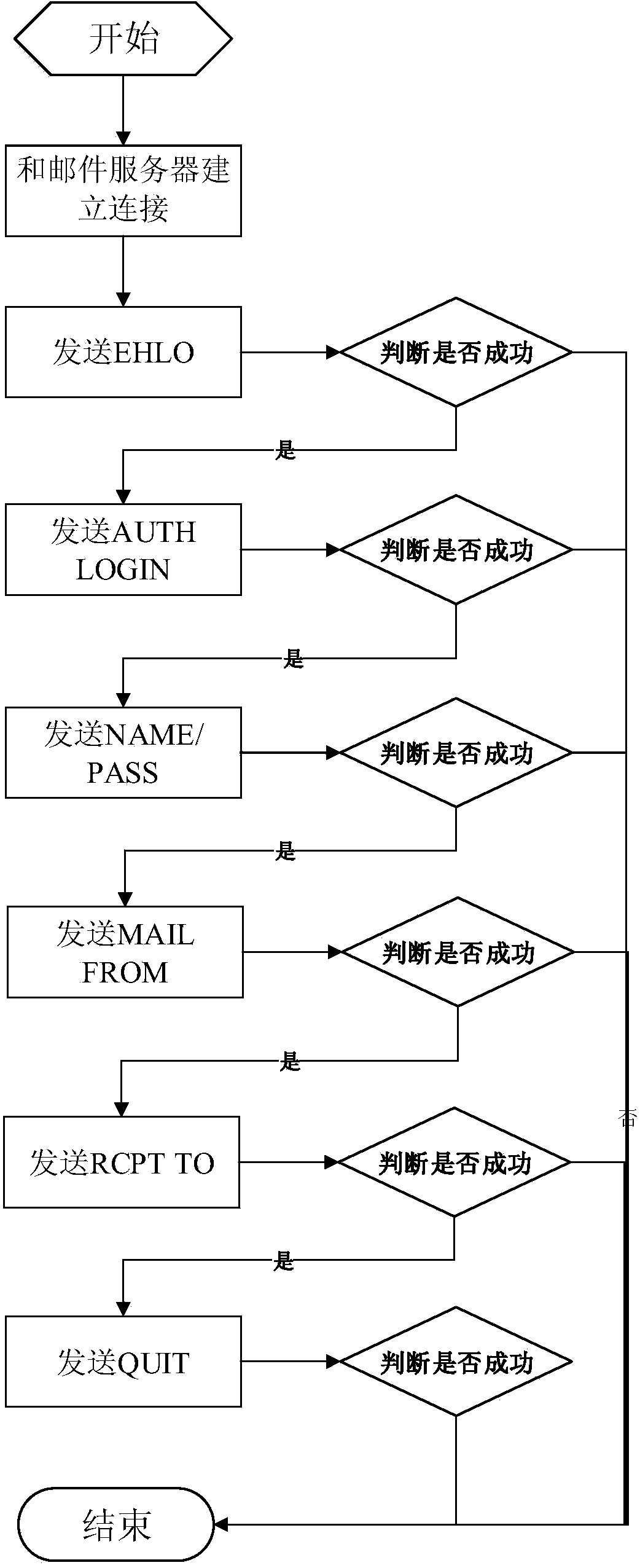
Method and system for safely receiving and sending mails
ActiveCN103428077AEnsure safetyImplement encryptionUser identity/authority verificationData switching networksSecure transmissionClient-side
The invention discloses a method and a system for safely receiving and sending mails. Mail receiving and sending safety authentication and safety transmission of the mails are realized. The method includes the steps: connecting a mail client with a login platform to perform identity authentication; returning a token message to the mail client after authentication success; accessing a first address in the token message by the mail client; receiving a first message including a second address by the mail client; calling an interface of a safety management platform and transmitting the first message to the safety management platform by the mail client; generating a second message and transmitting the second message to the mail client and a mail gateway by the safety management platform; acquiring a user policy message from the safety management platform through the second message by the mail client; carrying the second message by the mail client and authenticating the second message at the mail gateway; connecting the mail gateway with a mail server and starting receiving and sending the mails after passing authentication.
Owner:北京明朝万达科技股份有限公司
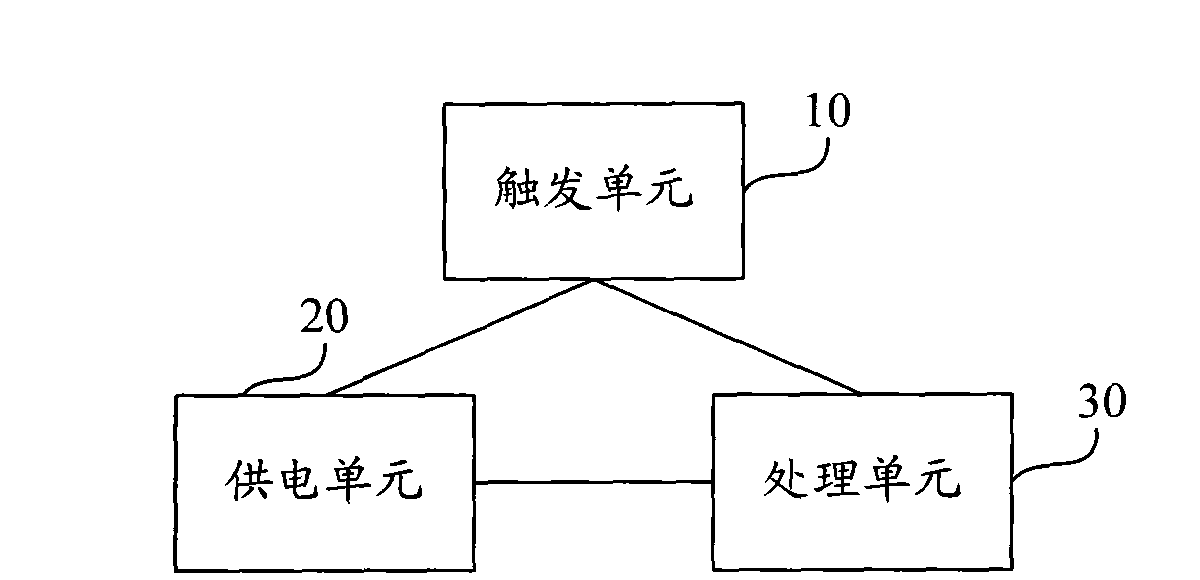
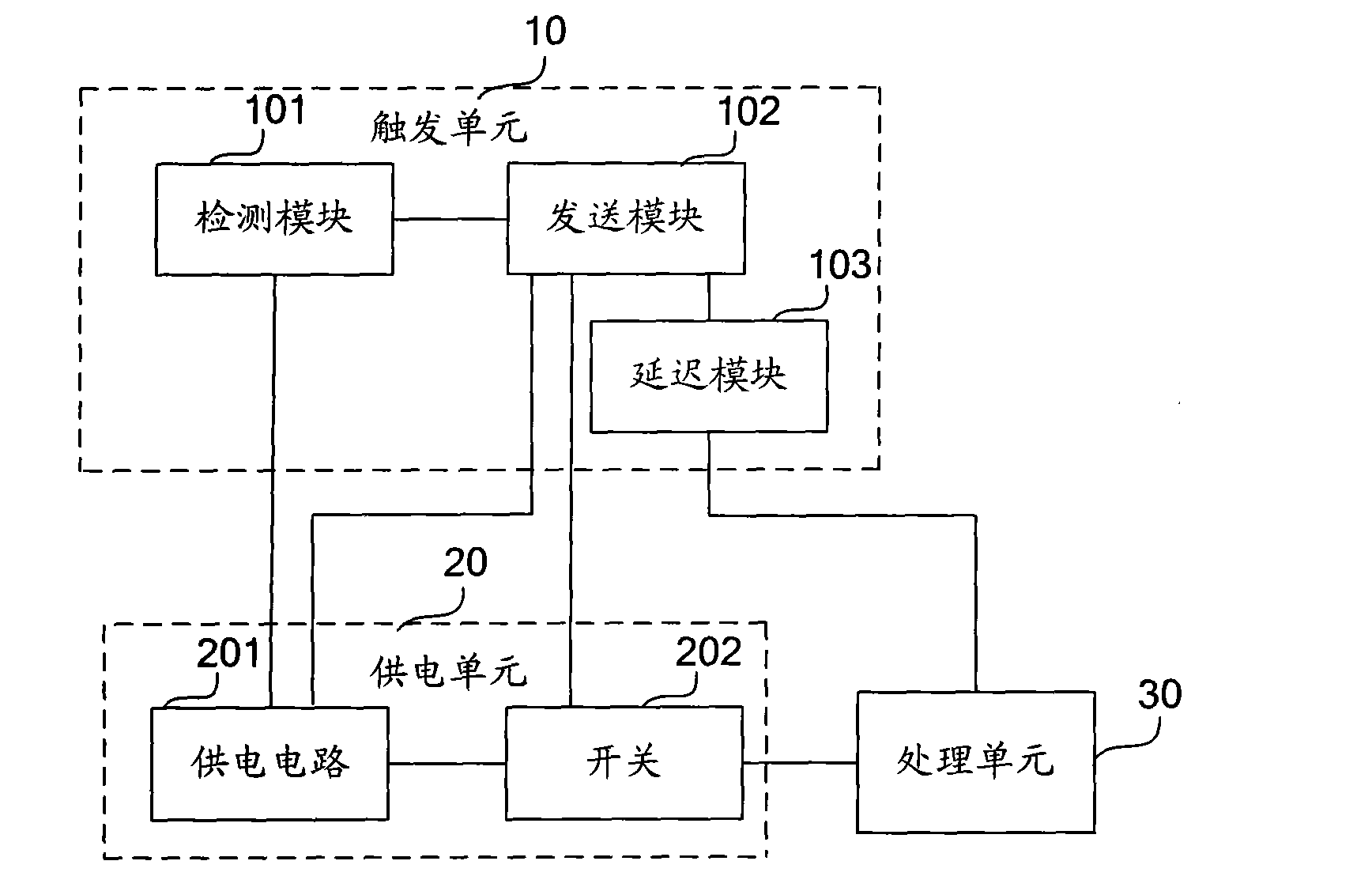
Data protection method and data protection device of movable storage equipment and movable storage equipment
InactiveCN101634972APrevent Data LeakageEnsure safetyUnauthorized memory use protectionStorage cellEngineering
The embodiment of the invention provides a data protection method and a data protection device of movable storage equipment and the movable storage equipment. The data protection device comprises a triggering unit, a power supply unit and a processing unit, wherein the triggering unit is used for emitting a power supply request signal and an elimination request signal when the movable storage equipment meets a preset data protection triggering condition; the power supply unit is used for receiving the power supply request signal emitted by the triggering unit and supplying power to the processing unit and a storage unit of the movable storage equipment; and the processing unit is used for receiving the elimination request signal emitted by the triggering unit and eliminating data stored in the storage unit. In the embodiment, a certain triggering condition is preset in the movable storage equipment; if the condition is met, the power is supplied to the movable storage equipment and the data stored in the movable storage equipment are eliminated, therefore, the problem of leaking the data after the movable storage equipment is filched is avoided and the safety of information stored in the movable storage equipment is ensured.
Owner:HUAWEI DIGITAL TECH (CHENGDU) CO LTD
Automatic goods selling device control system and method based on blockchain foundation
InactiveCN106781008AEffective Encoding ProtectionImprove data confidentialityCoin-freed apparatus detailsTransmissionNetwork communicationElectrical bonding
The invention relates to an automatic goods selling device control system and method based on a blockchain foundation. The automatic goods selling device control system comprises a backup power, a central data processor, an MOS driving circuit, a data storage SD card, a coding module, a crystal oscillator, a clock frequency dividing circuit, a data caching module, an address coding module, a data communication interface, a network communication module and a relay control circuit based on a single chip microcomputer, wherein the central processing unit is electrically connected with the backup power, the MOS driving circuit, the data storage SD card, the data caching module, the address coding module and the network communication module; the MOS driving circuit is connected with the backup power, the data storage SD card, the clock frequency dividing circuit, the data caching module, the data communication interface and the relay control circuit based on the single chip microcomputer. On one hand, the requirements that product sales and sales information monitoring feedback work are remotely carried out through a network can be effectively met, and on the other hand, data security and safety in a data communication process is improved.
Owner:CHENGDU YUYA TECH
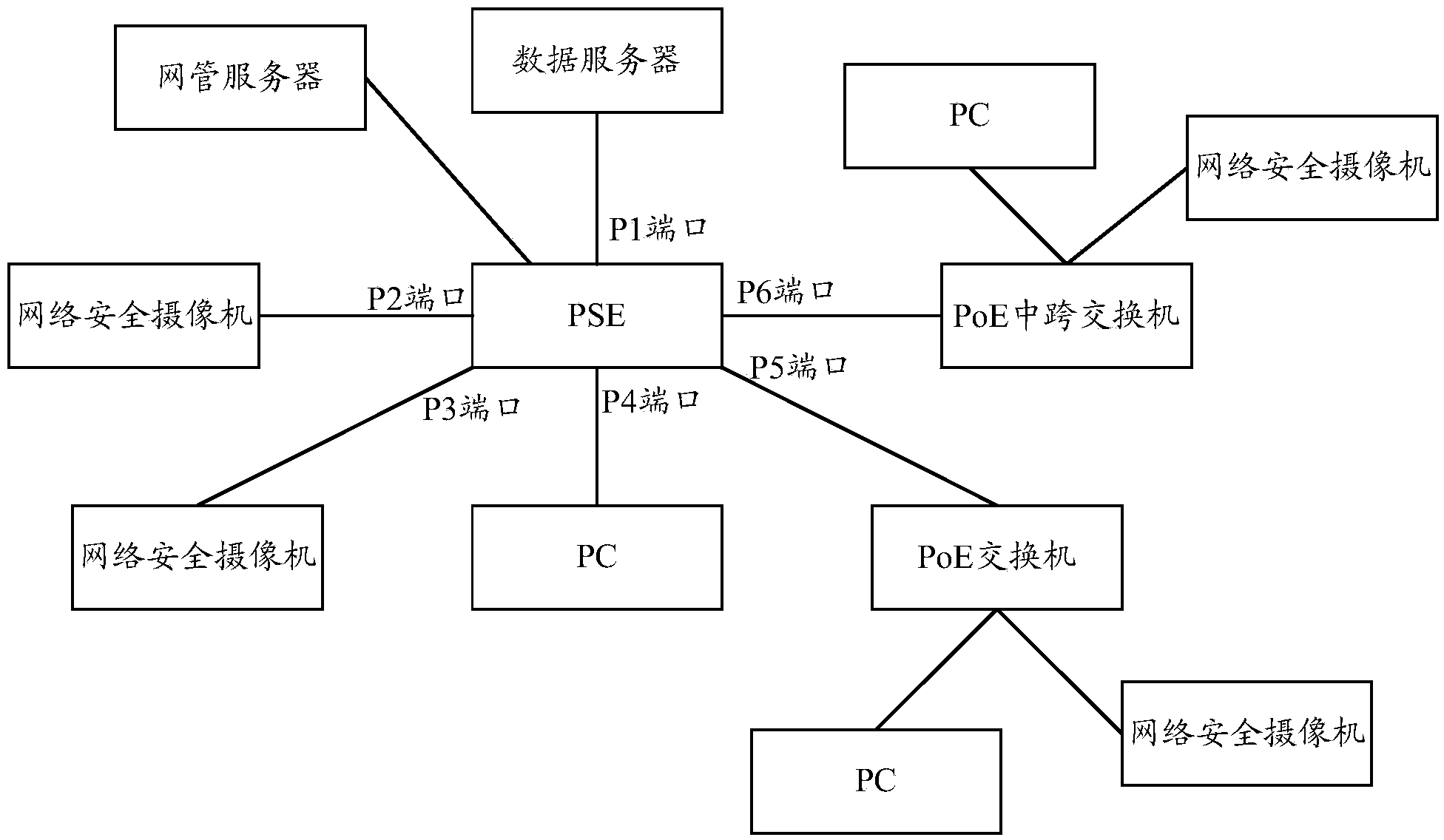
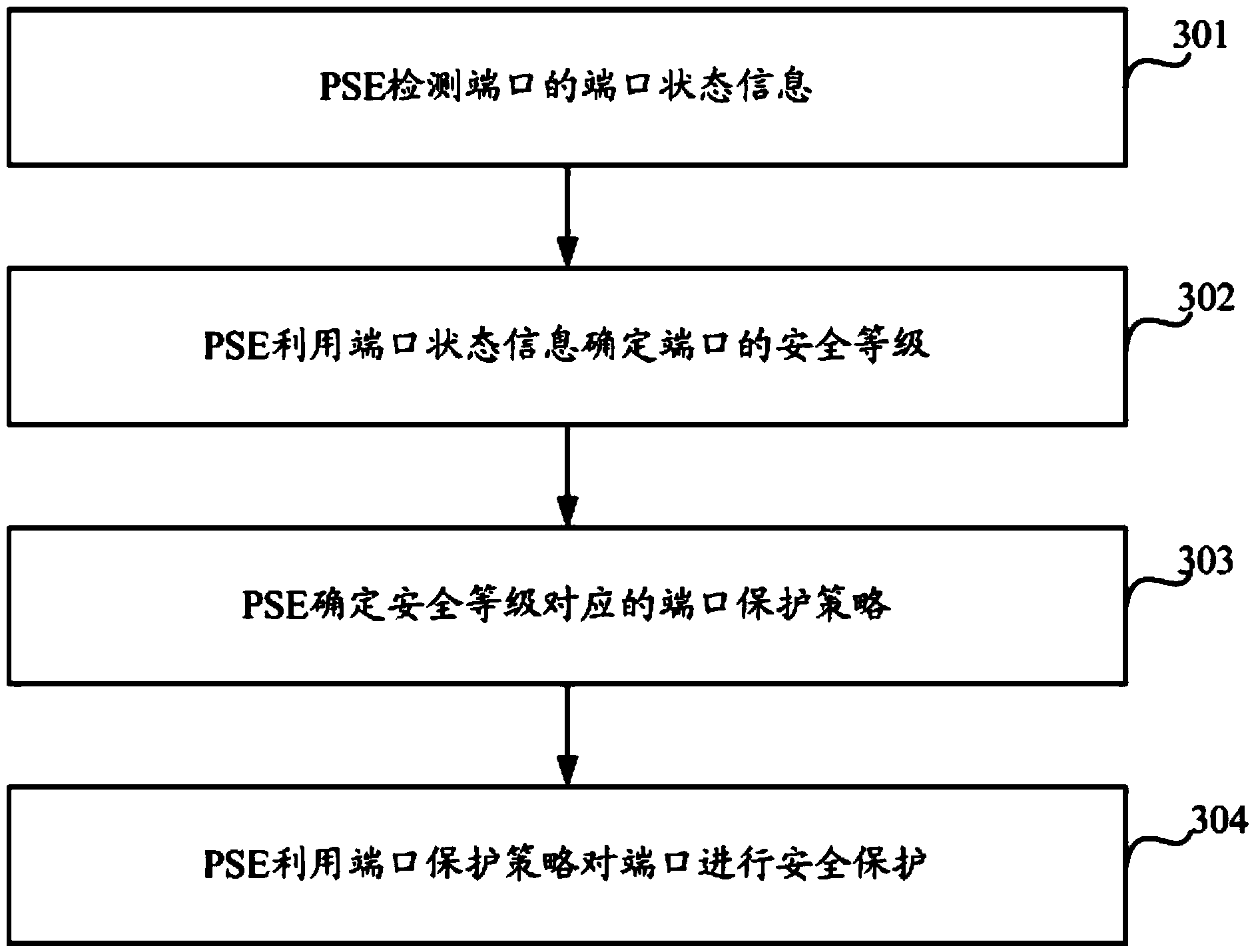
Port protection method of PSE and PSE
ActiveCN104168121AImprove securityEffective protectionData switching current supplyEngineeringSecurity level
The invention discloses a port protection method of power sourcing equipment (PSE) and a PSE. The method comprises: the PSE detects port state information of a port; the PSE uses the port state information to determine a security level of the port; the PSE determines a port protection strategy corresponding to the security level; and the PSE uses the port protection strategy to carry out security protection on the port. According to the embodiment of the invention, the port data can be effectively protected; the port security is enhanced; and a phenomenon that an illegal user obtains legal powered device (PD) data can be prevented.
Owner:NEW H3C TECH CO LTD
Commodity anti-counterfeiting traceability method based on block chain technology
InactiveCN112184252APrevent Data LeakageProtect business privacy data protectionDigital data protectionTransmissionBlockchainAccess frequency
The invention discloses a commodity anti-counterfeiting traceability method based on a block chain technology. The method at least comprises the following steps of information acquisition, informationmarking, authentication ID generation, data storage, access instruction receiving and access frequency comparison. According to the method, commodity anti-counterfeiting traceability is innovativelycompleted through a block chain technology, so that a user using the method can store the content of data in situ, and hash values in one-to-one correspondence with the data, identity identification information of the user and basic attribute data of target file data are associated and stored in a trusted block chain; therefore, the original creation and attribution of the data can be proved whilethe data leakage is avoided, and meanwhile, the corresponding certificate storage certificate is generated, and therefore a way for proving and verifying the certificate is provided for other people.More importantly, decentralization is realized by using a block chain technology, so that the data is real, credible and tamper-resistant, the commercial privacy data protection is protected, and theauthority and credibility of the platform and the enterprise participation enthusiasm are guaranteed.
Owner:雲禾(浙江)科技集团有限公司
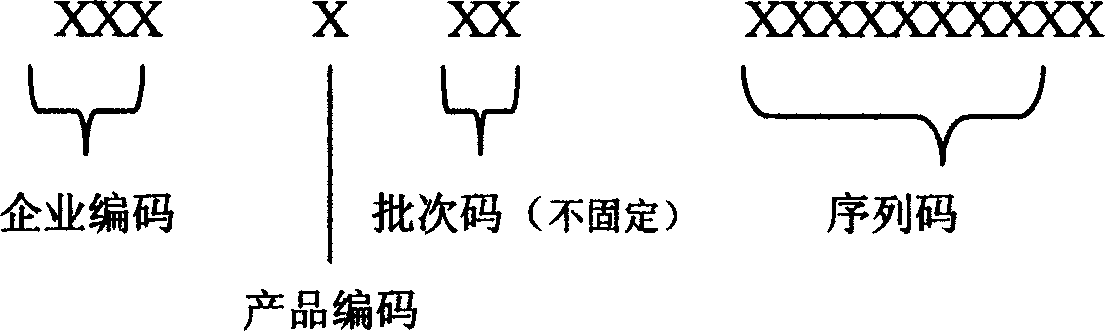
Encoding method for condition code of false proof code
InactiveCN1632818APrevent leakageImprove work efficiencyVerifying markings correctnessThe InternetTheoretical computer science
It is a false proof character coding method, which comprises the following steps: first to code each product with clear code on batch; to turn the irregular false proof data though coding; the characteristic code generate a set of code according to the above code with sequence zero, which are the characteristic coded of the false proof codes; to turn these set o f codes into irregular codes; to store these coded in the computer database; to decode the characteristic codes into clear codes; the batch of false codes can be used in searching when this batch of codes are stored in the database.
Owner:BEIJING ZHONGLIAN ZHAOXIN NETWORK INFORMATION TECH
Method and system for controlling data output
InactiveUS20070039059A1Avoid data breachesAvoid dataDigital data processing detailsUser identity/authority verificationOperational systemControl data
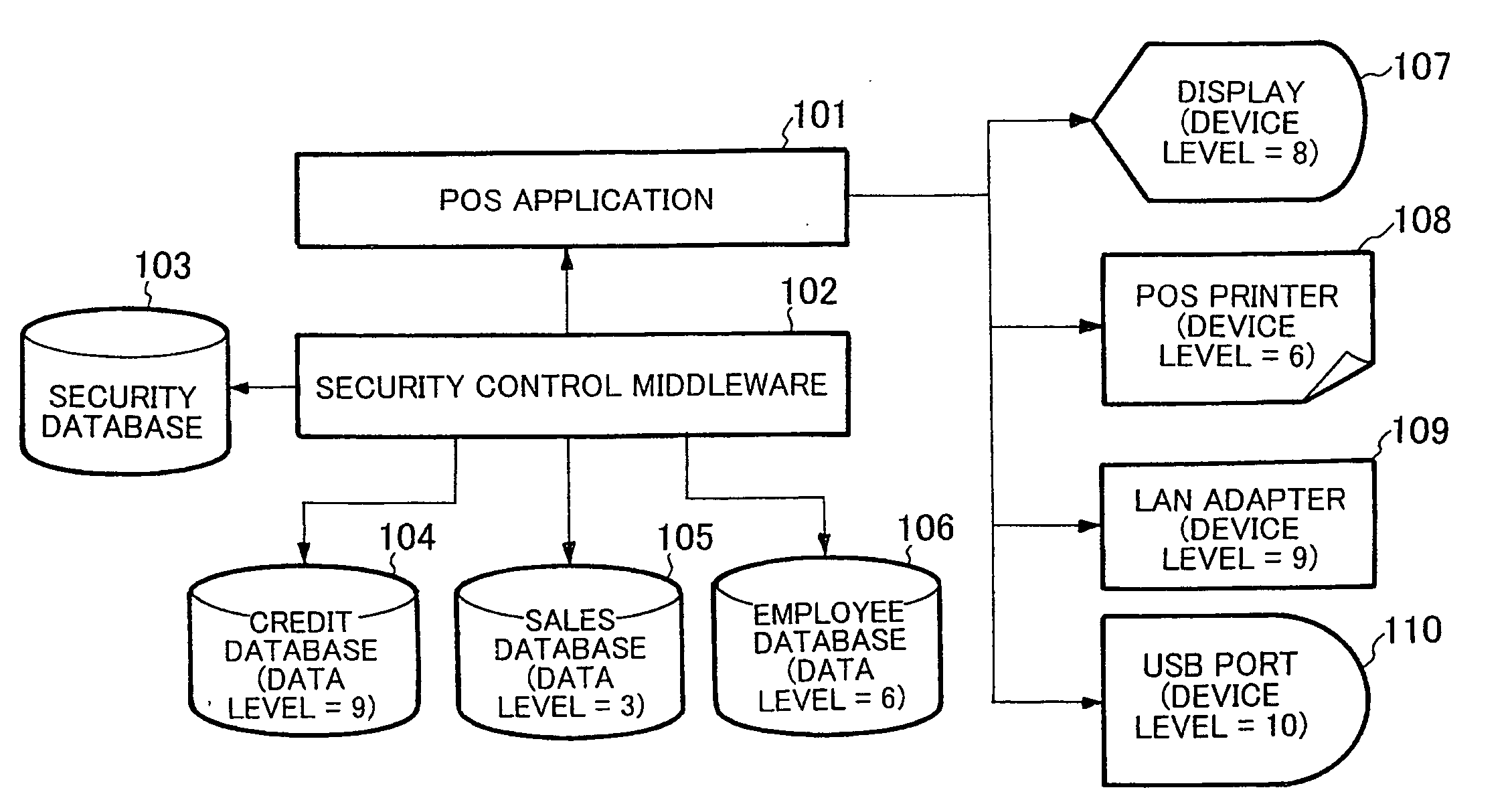
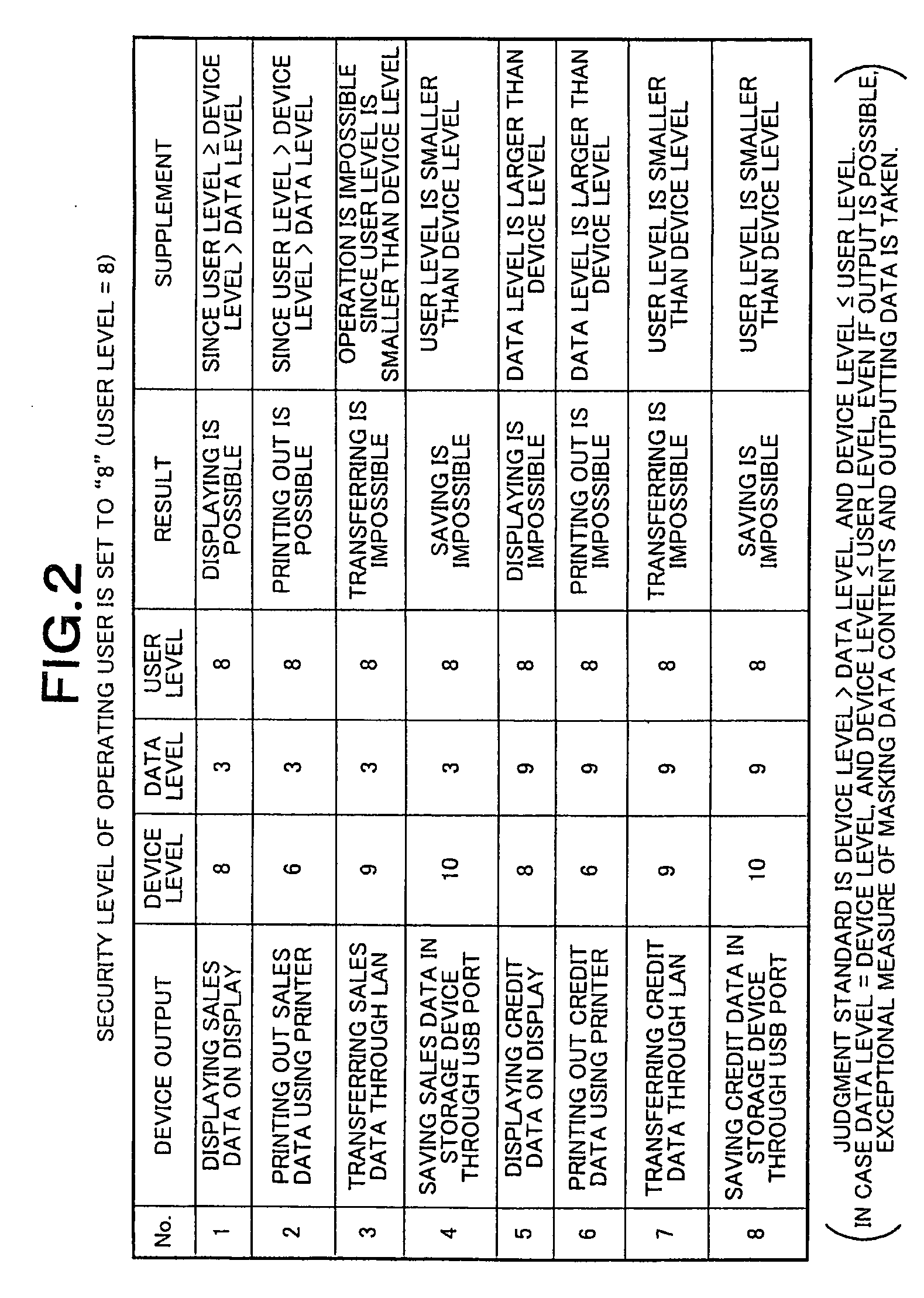
The present invention provides a method and system for controlling data output which can surely prevent data leakage from data output devices, and can also prevent data browsing by the remote operation which strikes weakness of a system. Security levels are set up for respective data output devices which output data, for respective data which is to be dealt with in a system, and for respective users who operate the system. In case the security level of a data output device is set to a device level, the security level of data to be dealt with in the system is set to a data level, the security level of a user is set to a user level, data output from the data output device is allowed when such conditions are satisfied that the device level is larger than the data level and that the device level is equal to or smaller than the user level.
Owner:NEC INFRONTIA CORP
Media treatment device
InactiveCN101156198AEasy to handlePrevent Data LeakageUnauthorized memory use protectionRecord information storageComputer hardwarePrinting press
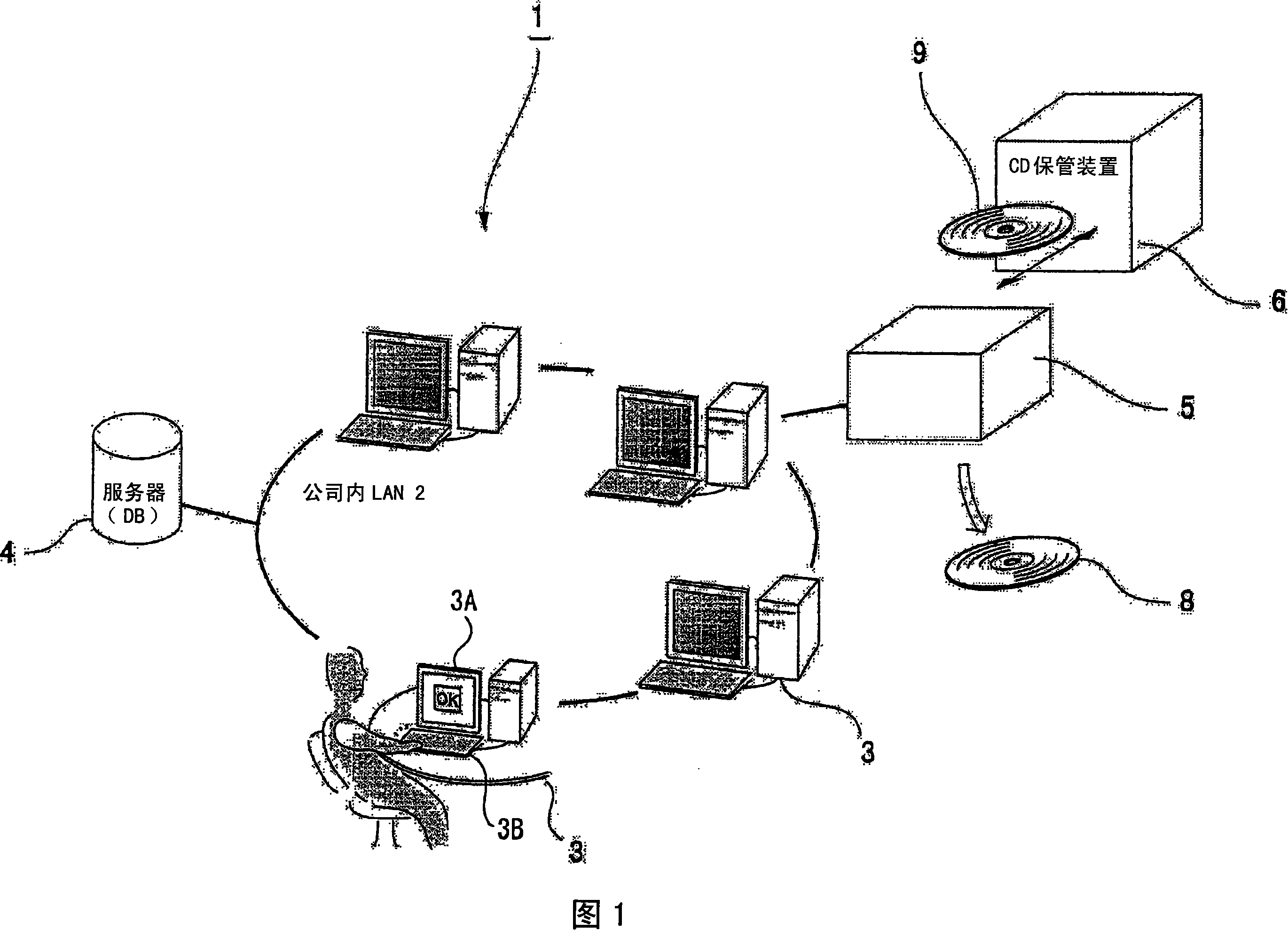
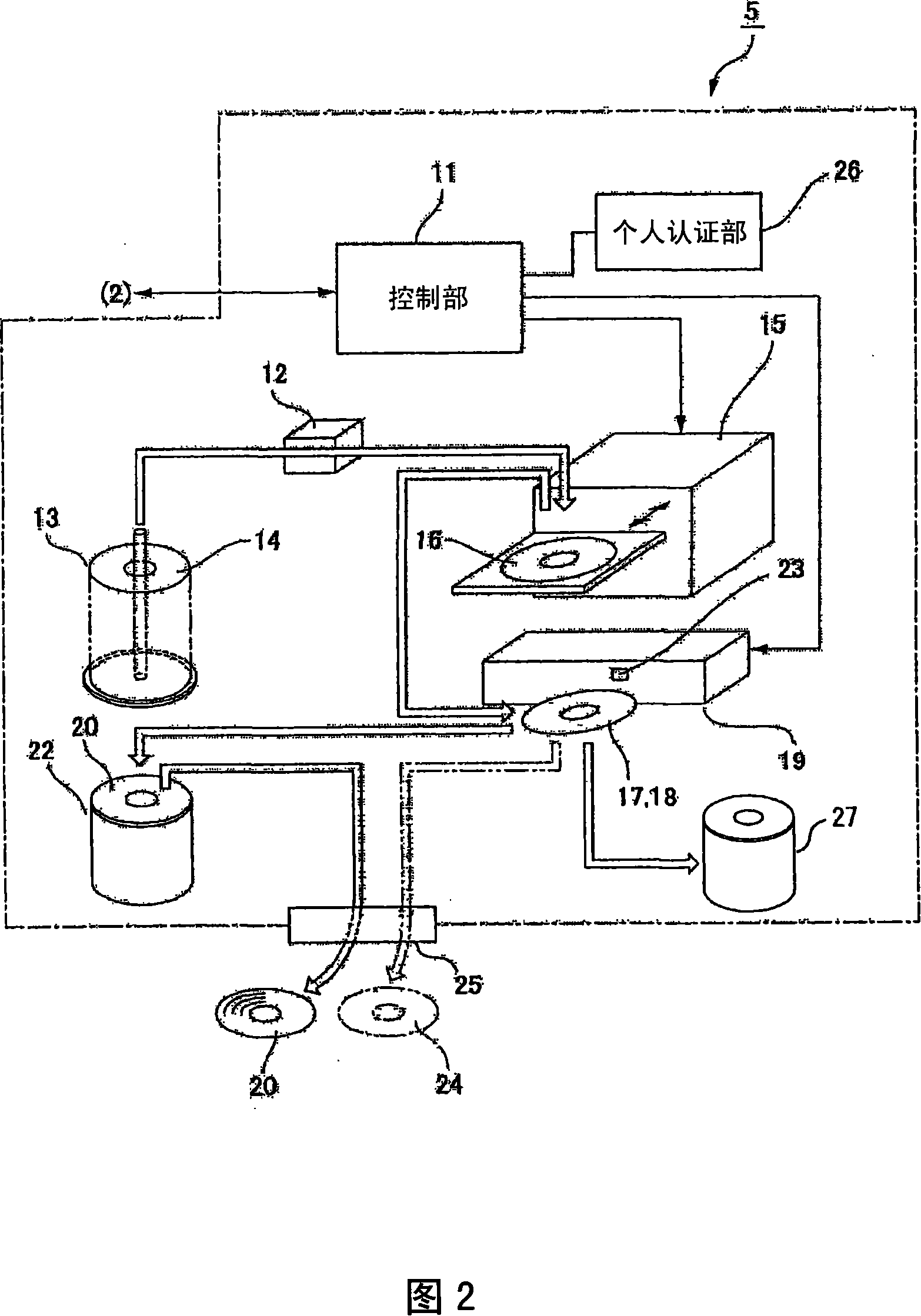
A media treatment device for an optical disc publisher, capable of efficiently disposing media such as defective CDs without using manpower. To produce a medium by an optical disc publisher (5), a blank medium (14) received in a feeding side stacker (13) is taken out by a media conveyance mechanism (12) and conveyed to a media drive (15), and predetermined data are written on the medium. A printing surface of the medium where the data are normally written is subjected to printing by a label printer (19). The medium after the production is stored in a storage side stacker (22). The recording surface of a defective medium having a write failure is mechanically destroyed by a media disposal mechanism (23) while the medium is moved on a medium tray (71) of the printer (19), thereby the data are not readable. The medium after the above process is discharged from a media discharge opening (25).
Owner:SEIKO EPSON CORP
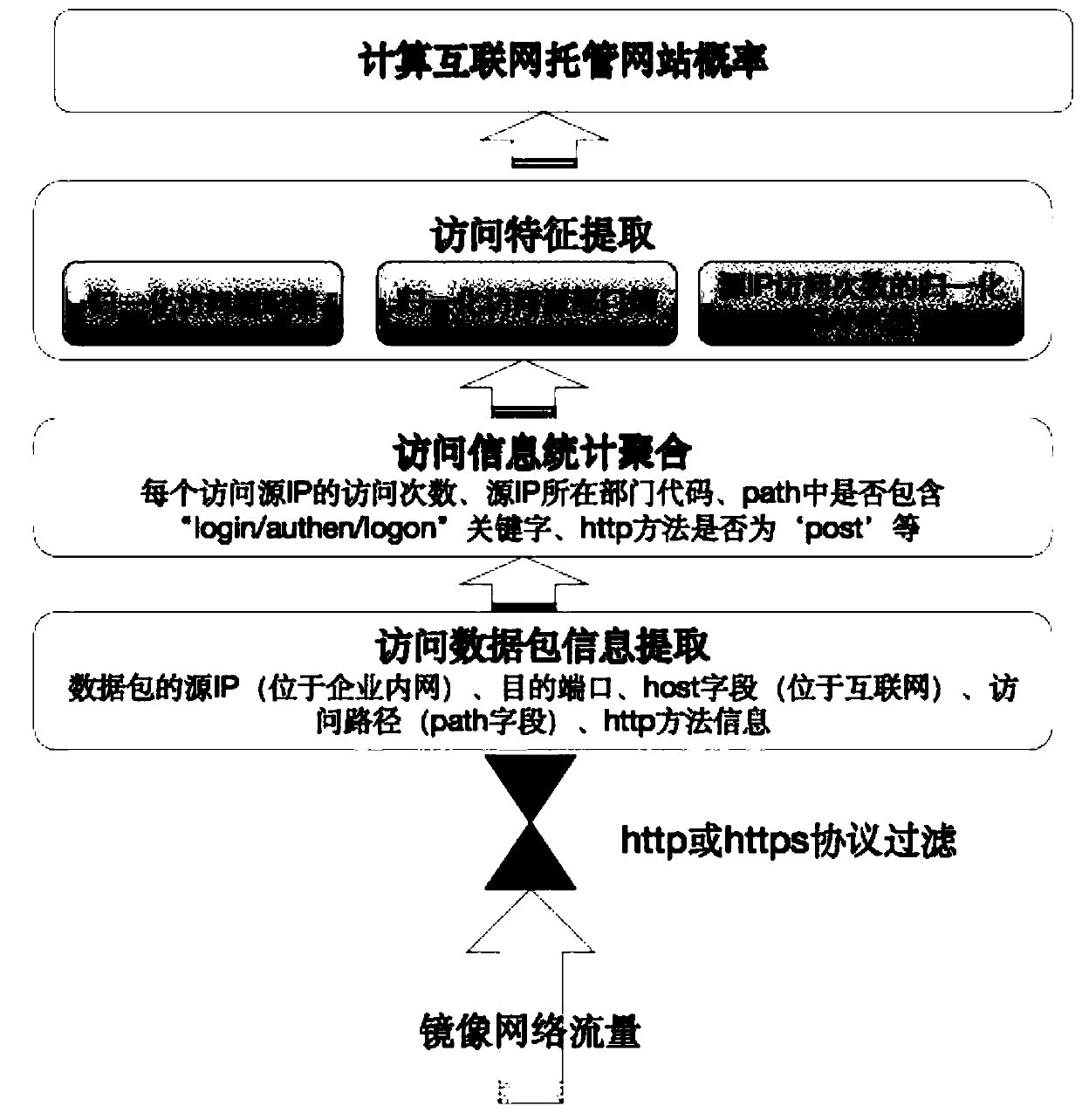
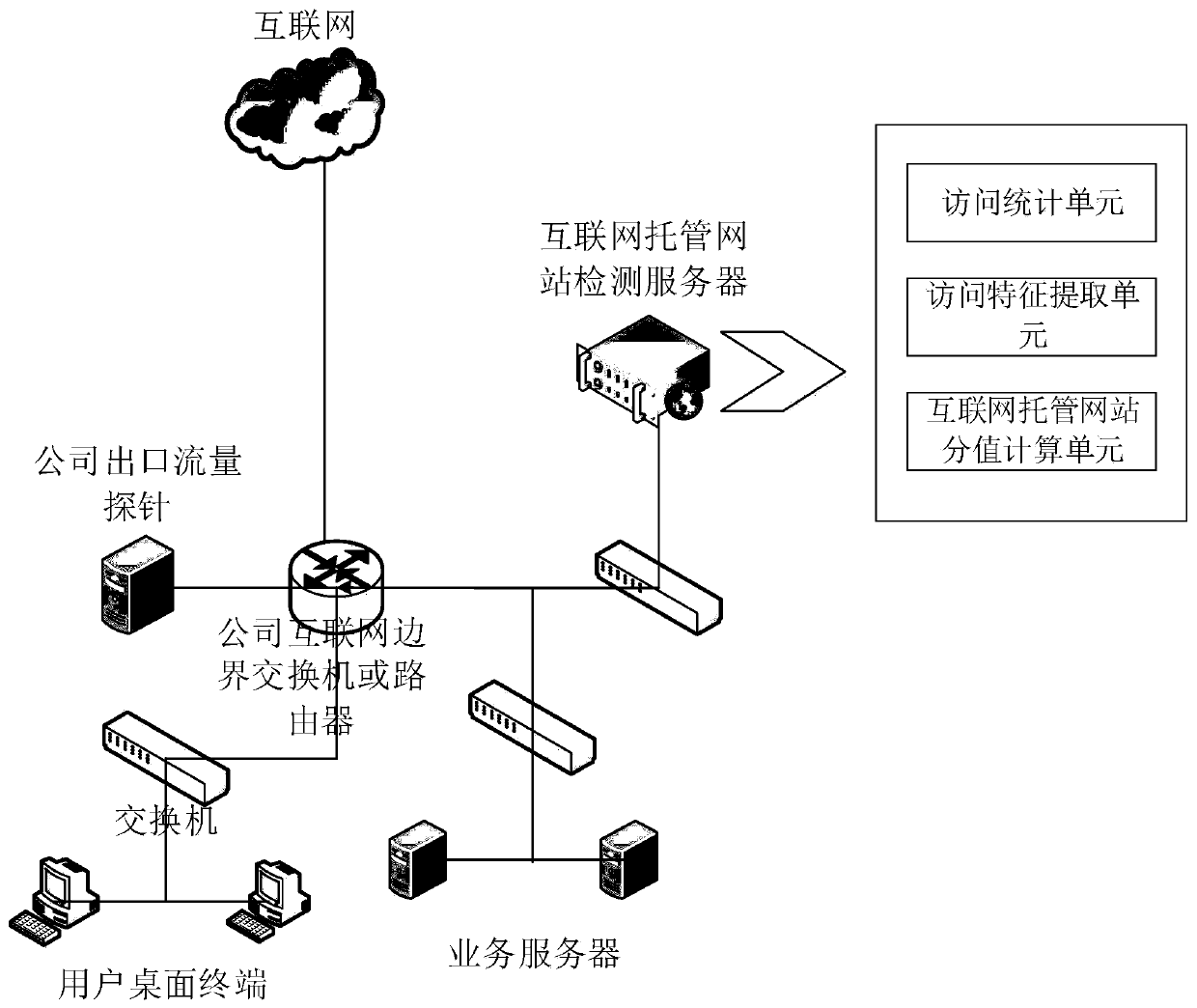
Internet hosting website detection method and system based on network access behavior analysis and readable storage medium
ActiveCN110572402APrevent Data LeakageImprove computing efficiencyTransmissionTraffic volumeInternet Website
The invention discloses an Internet hosting website detection method and system based on network access behavior analysis and a readable storage medium. According to the method, Internet access behavior characteristics in network traffic are extracted regularly, the probability that each accessed Internet website is an enterprise trusteeship website is calculated by utilizing the extracted characteristics, and website trusteeship detection is realized so as to assist enterprise security technicians in judgment. According to the scheme, the general network topology characteristics of enterprises are deeply combined, the access behavior characteristics of the Internet hosting website are analyzed based on the network traffic, the method does not depend on an enterprise keyword library, keyword matching does not need to be carried out on the load of the network traffic packet, and the operation efficiency and accuracy are high.
Owner:STATE GRID HUNAN ELECTRIC POWER +2
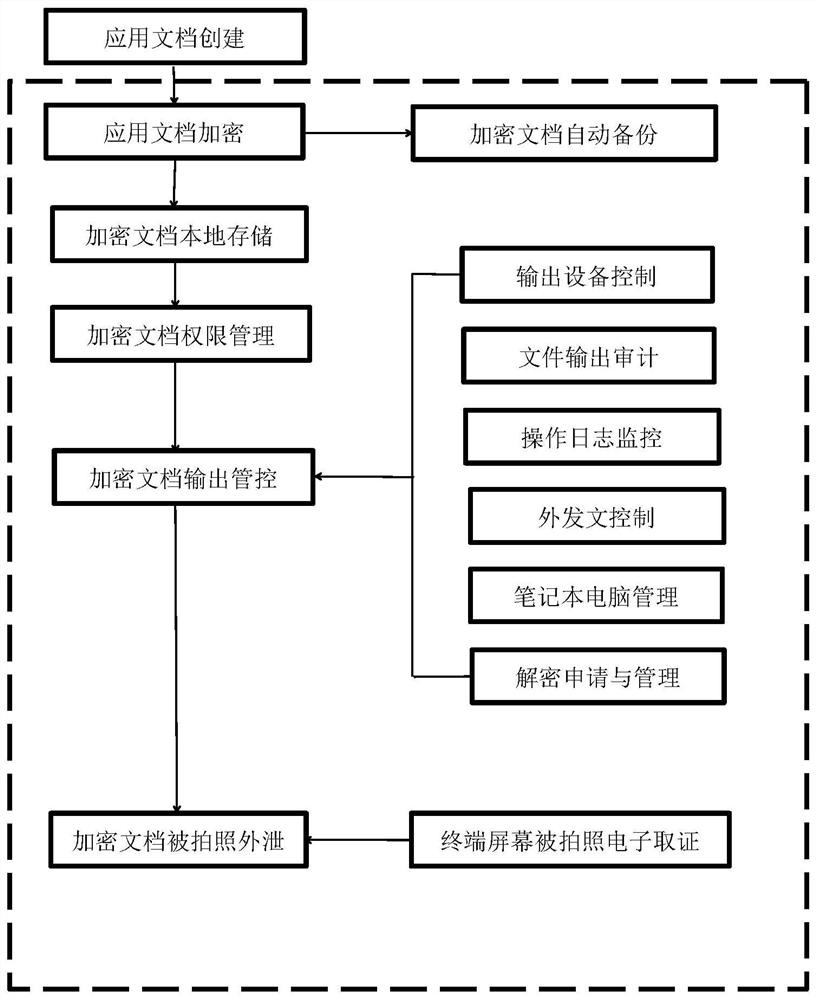
Electronic document security management method and system based on big data
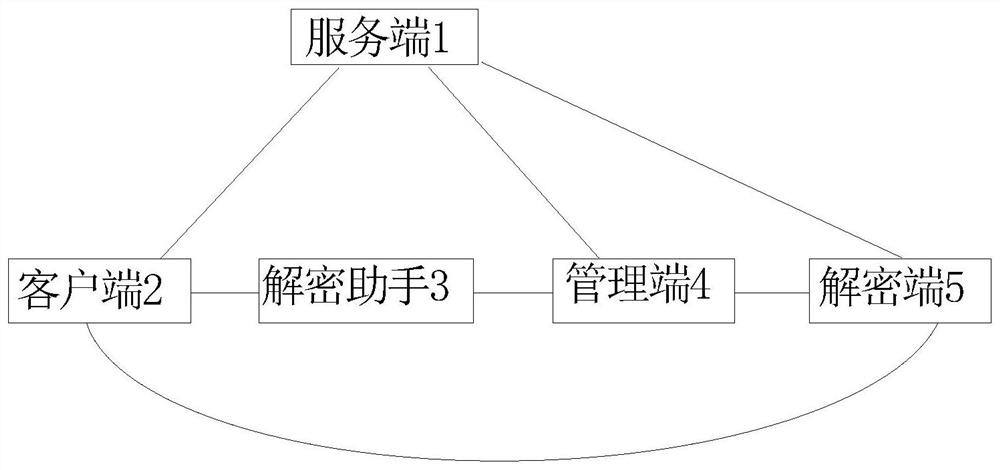
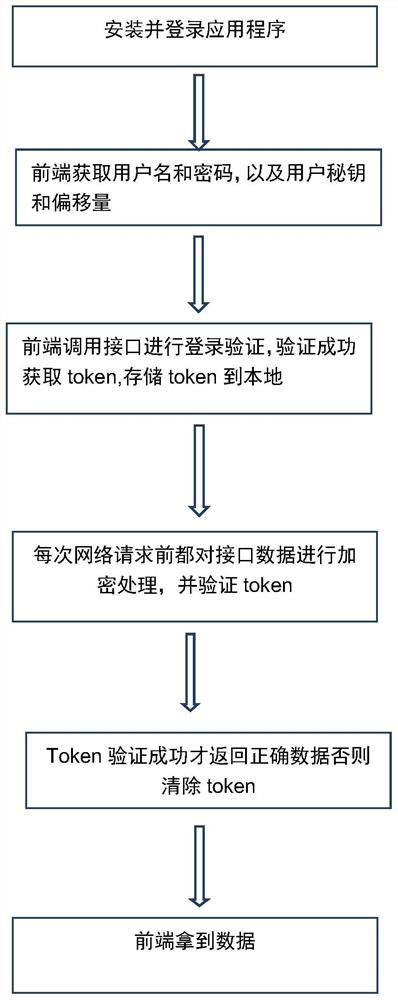
PendingCN112948870ASolve confidentiality issuesSolve needsDigital data protectionDigital data authenticationConfidentialityEngineering
The invention relates to an electronic document security management method based on big data. The method comprises the following steps of encryption protection of a document, local storage of the encrypted document, authority management of the encrypted document, output management and control of the encrypted document, automatic backup of the encrypted document and electronic evidence collection after a terminal screen is photographed. The encrypted document output control comprises output equipment control, file output auditing, operation log monitoring, outgoing document control, notebook computer management and decryption application and management. Besides, the invention further discloses a management system of the system. The system comprises a server side, a client side, a decryption side, a management side and a decryption assistant, the server side is installed on a server, and the client side, the decryption side, the management side and the decryption assistant are all installed on terminal computers of corresponding users. The confidentiality and safety management requirements of internal data assets of a company can be perfectly met, and various secret divulging channels are blocked.
Owner:北京国联易安信息技术有限公司
Security and secrecy method applied to financial transaction front-end projects
InactiveCN112580076AProtect interestsEnsure data transmission securityFinanceDigital data protectionPasswordEngineering
The invention provides a security and secrecy method applied to financial transaction front-end projects, and belongs to the technical field of language programming. The method comprises the followingsteps: acquiring a secret key and data offset defined at a native end through js interaction between the native end and a webpage end, logging in the native end, and acquiring a user name and a password by using a jsbridge method at the webpage end; enabling the webpage end to use a uniformly packaged network request method, employing an AES256 encryption algorithm for encrypting parameters, andverifying an interface by using a token, thereby achieving the transmission purpose that data cannot be decoded by using several measures at the same time.
Owner:天元大数据信用管理有限公司
Graphene secure and smart phone
InactiveCN106993071AAvoid damagePrevent Data LeakageTelephone set constructionsCooling/ventilation/heating modificationsTouchscreenCooling capacity
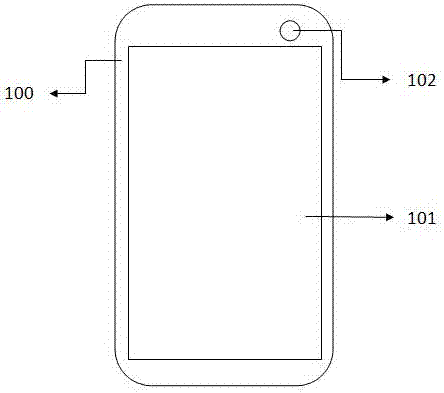
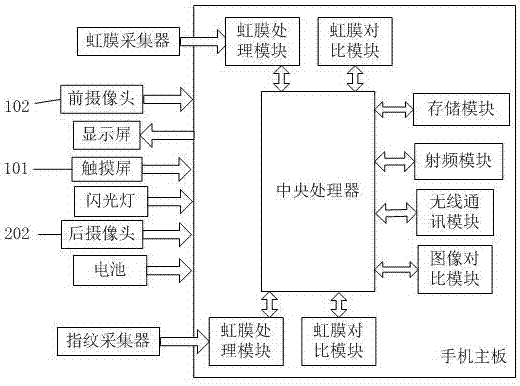
The present invention proposes a graphene safe smart phone, which solves the problems of insecure data and uneven heat dissipation in existing smart phones. There is a front camera, and an iris collector is arranged under the front camera; a graphene heat dissipation layer is arranged on the rear case, a rear camera and a fingerprint collector are arranged on the upper part of the rear case, and a flash light is arranged on the circumference of the fingerprint collector; A mobile phone main board and a battery are arranged, and a central processing unit, a memory module, a wireless communication module and a radio frequency module are arranged on the mobile phone main board. The present invention increases the heat conduction and heat dissipation capacity of the rear case by setting a graphene heat dissipation layer on the rear case of the mobile phone, preventing the heat source temperature in the mobile phone from being too high and damaging the mobile phone; using the comparison between the iris collector and the fingerprint collector to determine the identity of the user, Thereby ensuring that it is a legitimate user, preventing data leakage in the mobile phone, and ensuring the user's data security.
Owner:河南省创酷通信技术有限公司
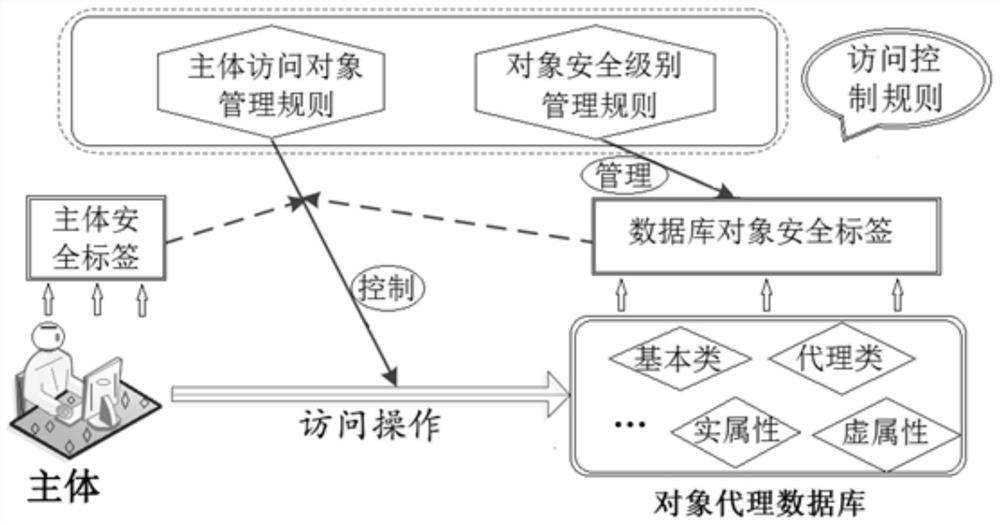
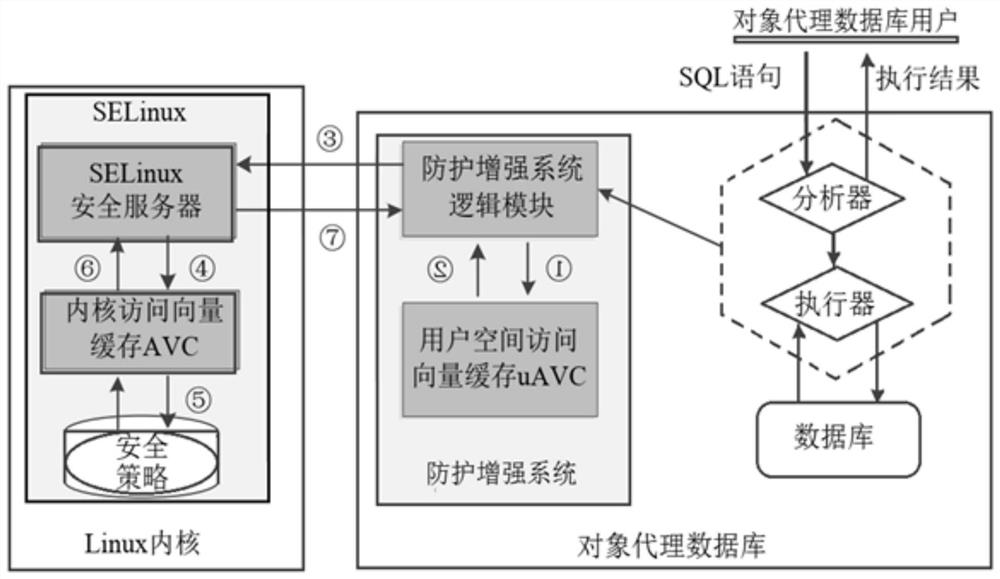
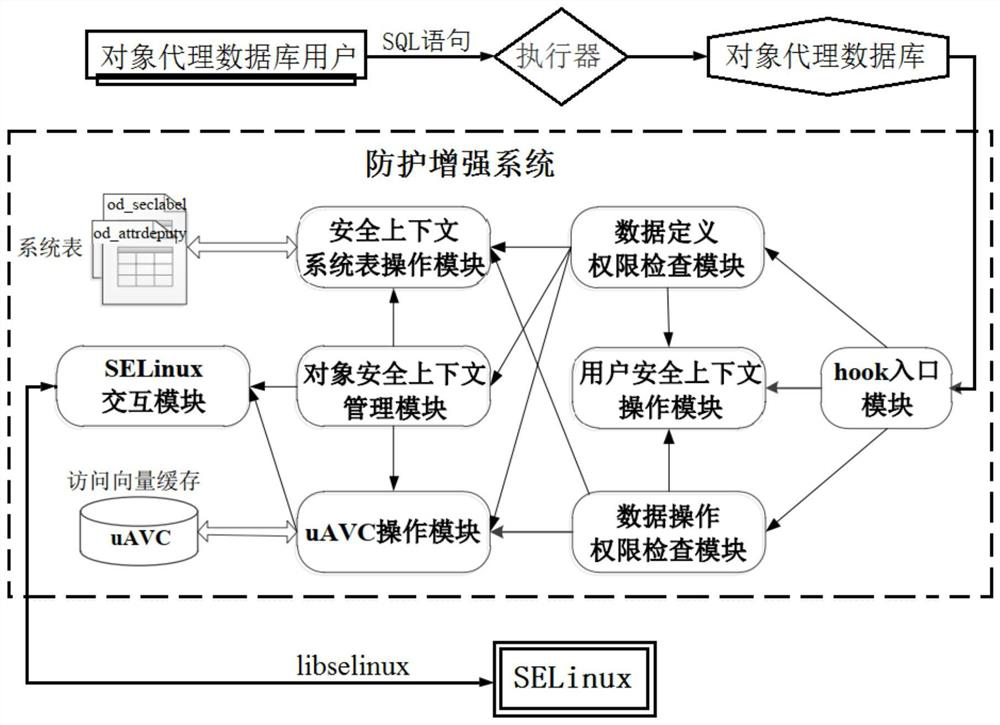
MAC protection enhancement system forobject agent feature database
PendingCN112231733AImprove securitySecure and flexible access controlDigital data protectionDatabase objectEngineering
According to the MAC protection enhancement system for the object agent feature database provided by the invention, a database MAC model based on object agent features is designed, and a set of strictdatabase object access control rules and database object security level limiting rules are designed on the basis of the model; a security level management model of the database object is designed, and a strategy and a method for performing fusion unified management on the security level of the database object are provided; a method for subdividing virtual attribute security levels based on data sources is provided, and a fine-grained access control method of multi-data-source agent classes is designed; a protection enhancement system for providing an MAC function in an object proxy database is designed. The result shows that the method has a good effect in the object proxy database, safer and more flexible access control is provided for the objects in the object proxy database, and the safety performance of the object proxy is improved.
Owner:刘秀萍
Mobile remote power monitoring system and monitoring method based on 4G network
ActiveCN106385104BPrevent Data LeakageMaintain securityCircuit arrangementsImaging processingMonitoring system
The invention relates to a mobile remote power monitoring system based on 4G network. The system comprises a mobile remote power monitor, a high-definition camera, an authorization management device and an image processing device; the image processing device is connected with the high-definition camera and used to carry out face feature detection on a high-definition face image output by the high-definition camera; and the authorization management device is connected with the image processing device and the mobile remote power monitor, and used to start or close mobile remote power monitor based on output of the image processing device automatically. The invention relates to a mobile remote power monitoring method based on the 4G network. According to the invention, it can be ensured that a user can access the mobile remote power monitor legally.
Owner:烟台宝骏软件技术有限公司
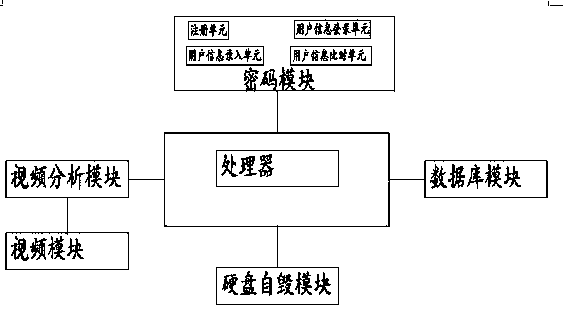
Security protection system of a computer information network
InactiveCN109756486APrevent Data LeakageEnsure safetyDigital data protectionClosed circuit television systemsAnalysis dataInformation networks
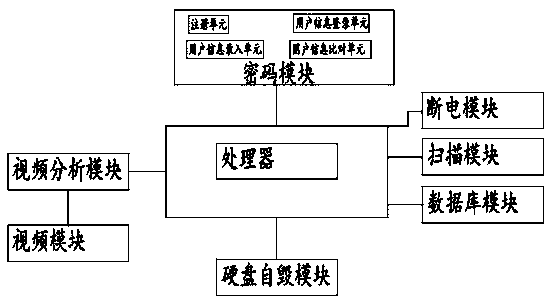
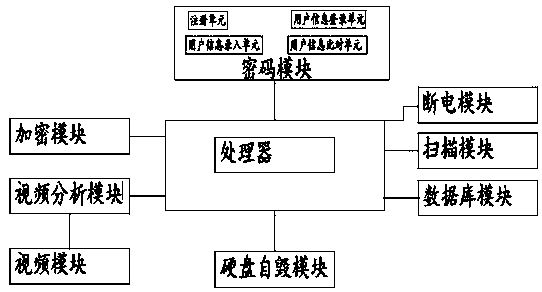
The invention discloses a security protection system of a computer information network, and relates to the technical field of information security. The system comprises a video module, a video analysis module, a database module, a hard disk self-destruction module and a processor, the video module is connected with the video analysis module, and the video analysis module, a password module, the hard disk self-destruction module and the database module are all connected with the processor; The video module is used for recording a video of a database module area and transmitting video data to the video analysis module in a recording manner; The video analysis module is used for analyzing the video data transmitted by the video module, the analysis result is that suspicious persons move in the area of the database module or no suspicious persons exist in the area of the data module, and the database module is in a safe state; The analysis data is sent to the processor; The system preventsa person from removing the hard disk in the database to prevent data leakage.
Owner:广州破折号信息科技有限公司
Distributed cloud security storage method and system and storage medium
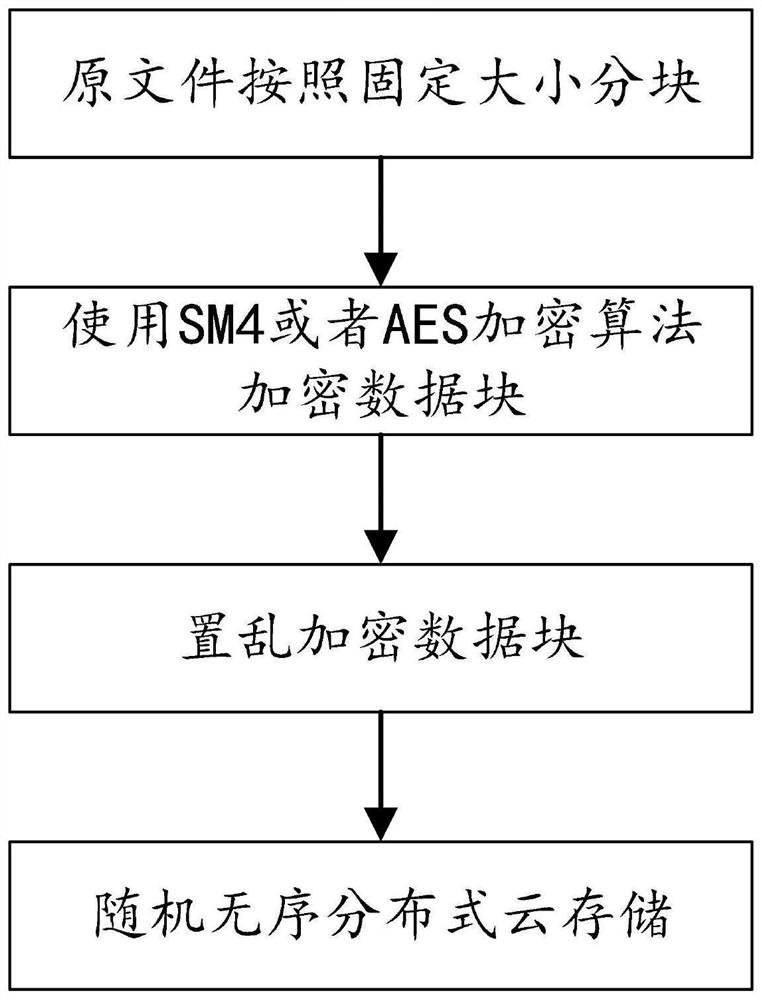
PendingCN113641648APrevent Data LeakagePrevent leakageDigital data protectionFile access structuresEngineeringDistributed computing
The invention discloses a distributed cloud security storage method and system and a storage medium, and the method comprises the steps: segmenting a target file into a plurality of data blocks, carrying out the block encryption of the data blocks through an SM4 or AES encryption algorithm, and obtaining encrypted data blocks; randomly scrambling the encrypted data block by using a preset scrambling algorithm; uploading the scrambled encrypted data blocks to different cloud hosts for distributed storage, and establishing a storage index in a local host; and according to the storage index, downloading the encrypted data block corresponding to the target file from the cloud host, performing inverse scrambling according to the scrambling key, performing decryption according to the encryption key, and recombining the target file. Block encryption and random scrambling of the target file are supported, distributed storage of a plurality of different cloud hosts at the cloud end is transmitted, an authorized user can open a system and download encrypted data blocks corresponding to the target file from the cloud hosts, the user is supported to browse and use the file without barriers, and the data leakage in the transmission process can be effectively avoided.
Owner:SHANDONG COMP SCI CENTNAT SUPERCOMP CENT IN JINAN
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com