MAC protection enhancement system forobject agent feature database
A technology of object proxy and enhancement system, applied in the direction of digital data protection, electrical digital data processing, instruments, etc., to achieve the effect of improving security performance and secure and flexible access control
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0064] The technical solution of the MAC protection enhancement system for the object proxy feature database provided by the present invention will be further described below in conjunction with the accompanying drawings, so that those skilled in the art can better understand the present invention and implement it.
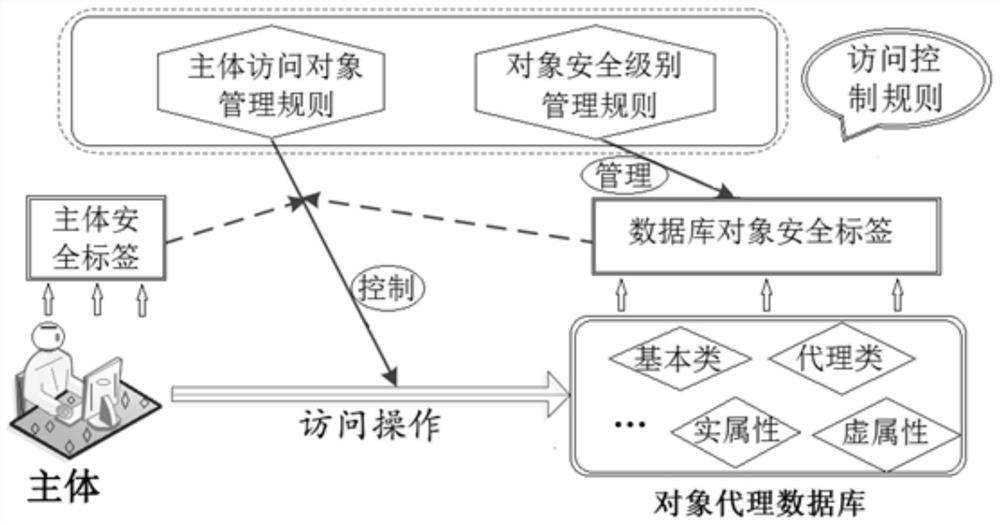
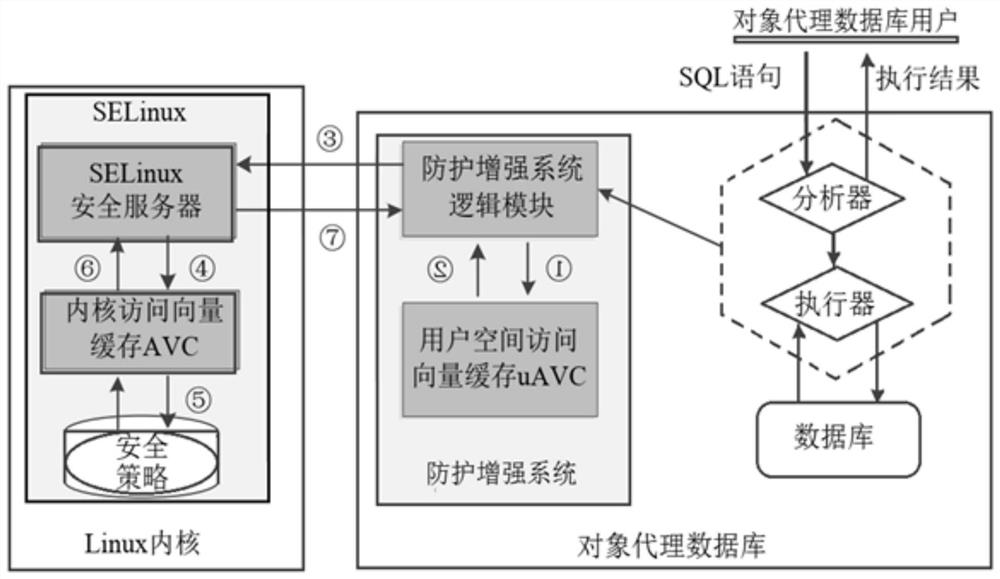
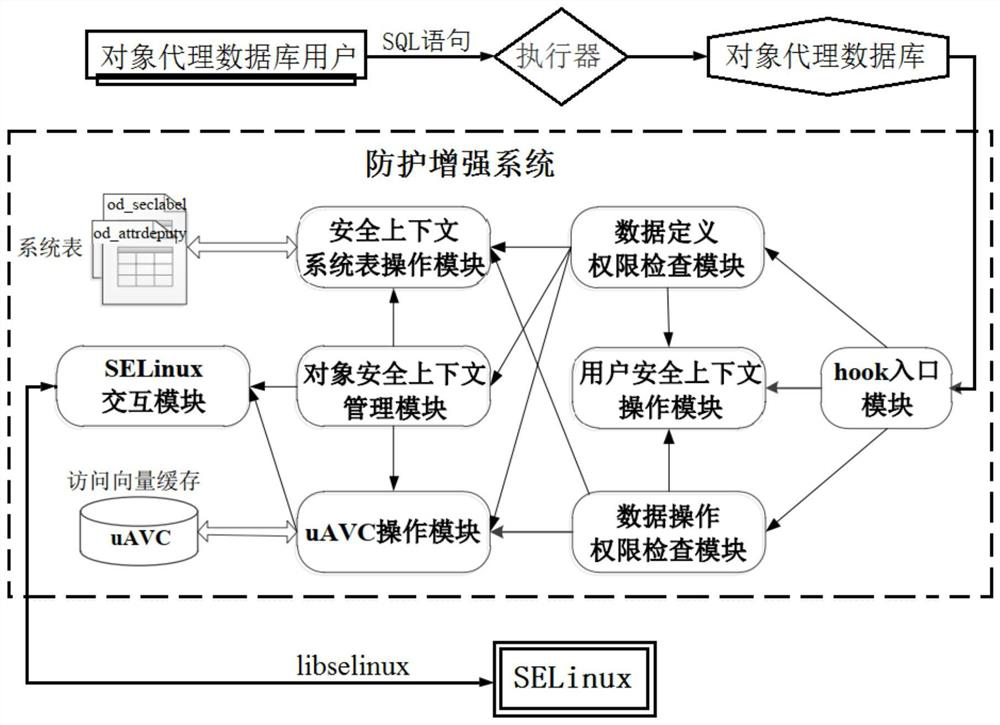
[0065] Aiming at the security problems existing in the access control module of the object proxy database in the prior art and the limitations of the application of the MAC model to the object proxy, the present invention proposes a MAC model suitable for the object proxy database based on the characteristics of the object proxy, and designs on the basis of this model Subject’s access control rules to database objects and agent relationship database object security level restriction rules; at the same time, to provide integrated and unified security level management for database objects, the present invention proposes a database object security level management mode...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com