Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
92results about How to "Solve security issues" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
APP (Application) safety protection system and method under IOS (Iphone Operating System)
ActiveCN108595989AAvoid security issuesSecurity question validKey distribution for secure communicationEncryption apparatus with shift registers/memoriesProtective systemMobile app
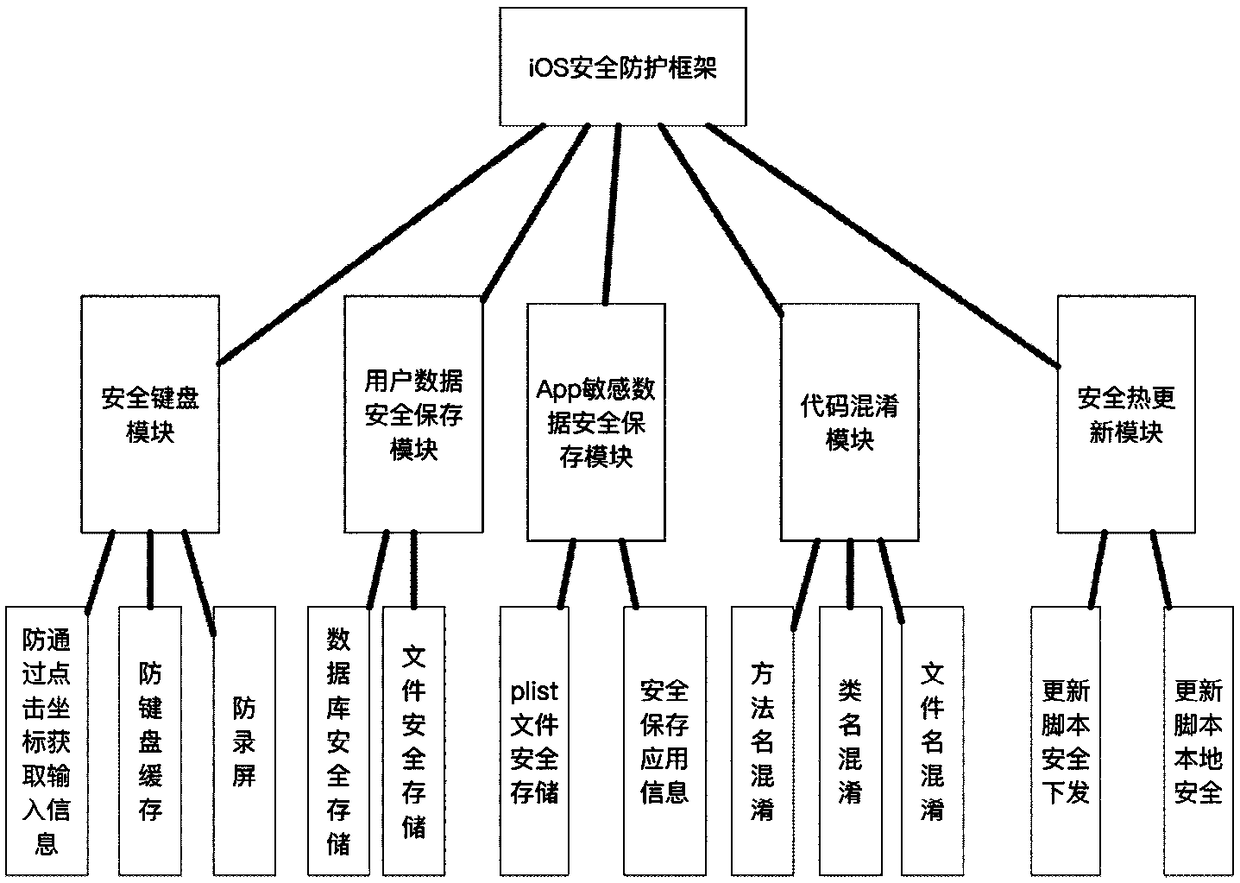
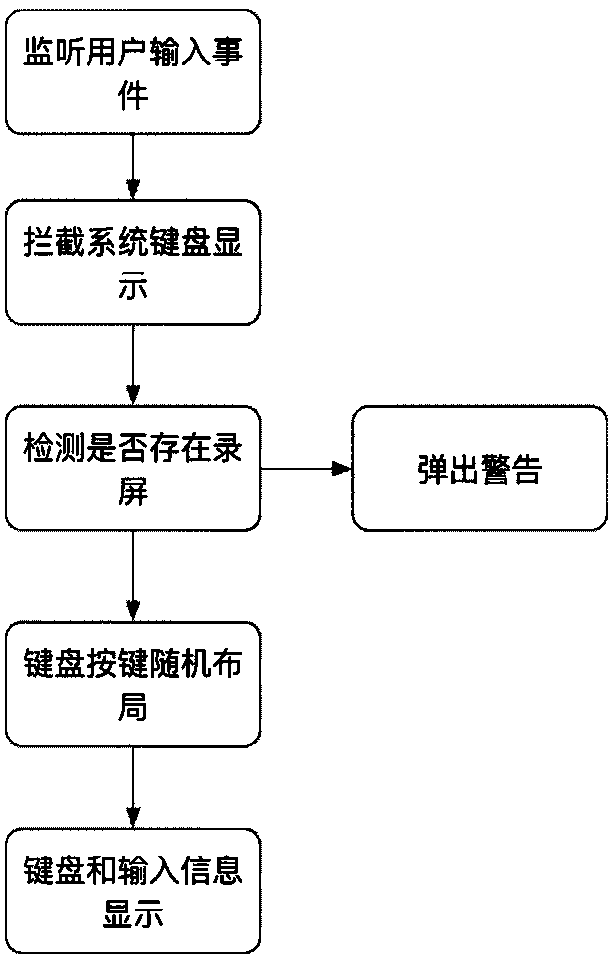
The invention discloses an APP (Application) safety protection system and method under an IOS (Iphone Operating System). The system comprise a safety keyboard module, a user data safety storage module, an App sensitive information storage module, a source code protection module and a safety hot update module, wherein the five safety protection modules are used for carrying out safety protection ona situation that an existing IOS mobile APP has defects and problems. By use of the system, solutions for five safety problems which are usually met in an existing iOS-App development process are integrated into a safety protection frame method, a developer only needs to apply the safety protection method to the App, effective safety protection can be carried out on the App through correct deployment, a developer can conveniently solve an App safety problem, development time is shortened, and the safety of the App is improved.
Owner:HANGZHOU DIANZI UNIV
Swivel and closure construction method for large-span continuous beam crossing existing station
ActiveCN105421248AThe method steps are simpleReasonable designBridge erection/assemblyBridge materialsButtressReinforced concrete
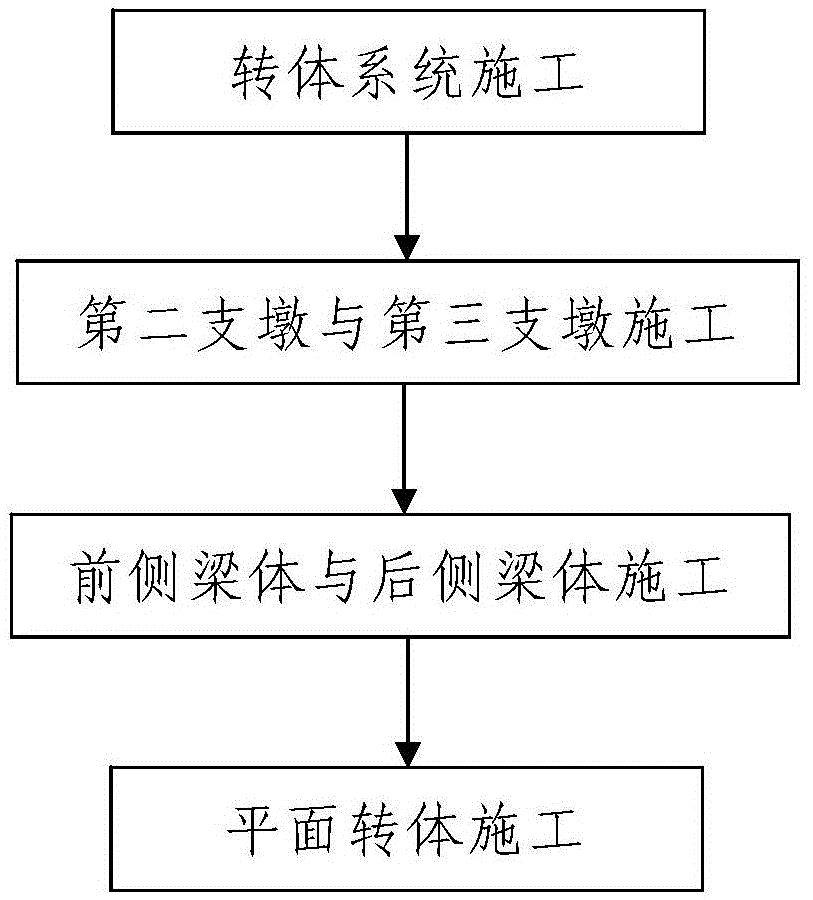
The invention discloses a swivel and closure construction method for a large-span continuous beam crossing an existing station. A constructed large-span continuous beam adopts a reinforced concrete box beam crossing the existing station and the front end and the rear end of a span are supported on a second buttress and a third buttress respectively; the swivel and closure construction process comprises steps as follows: step one, swivel system construction: a swivel system is constructed at the bottom of each of the second buttress and the third buttress and comprises a lower support disc, an upper rotating disc, a bridge swivel spherical hinge and a swivel traction system, multiple support legs are arranged at the bottom of the upper rotating disc, and an annular slide way allowing the support legs to slide is formed on a lower bearing platform; step two, construction of the second buttress and the third buttress; step three, construction of a front side beam body and a rear side beam body; step four, plane swivel construction; step five, side span closure construction; step six, mid-span closure construction. According to the method, the steps are simple, the design is reasonable, the construction is simple and convenient, the use effect is good, the swivel and closure construction process of the large-span continuous beam crossing the existing station can be completed simply, conveniently and rapidly, and the construction process is safe.
Owner:NO 1 ENG LIMITED OF CR20G
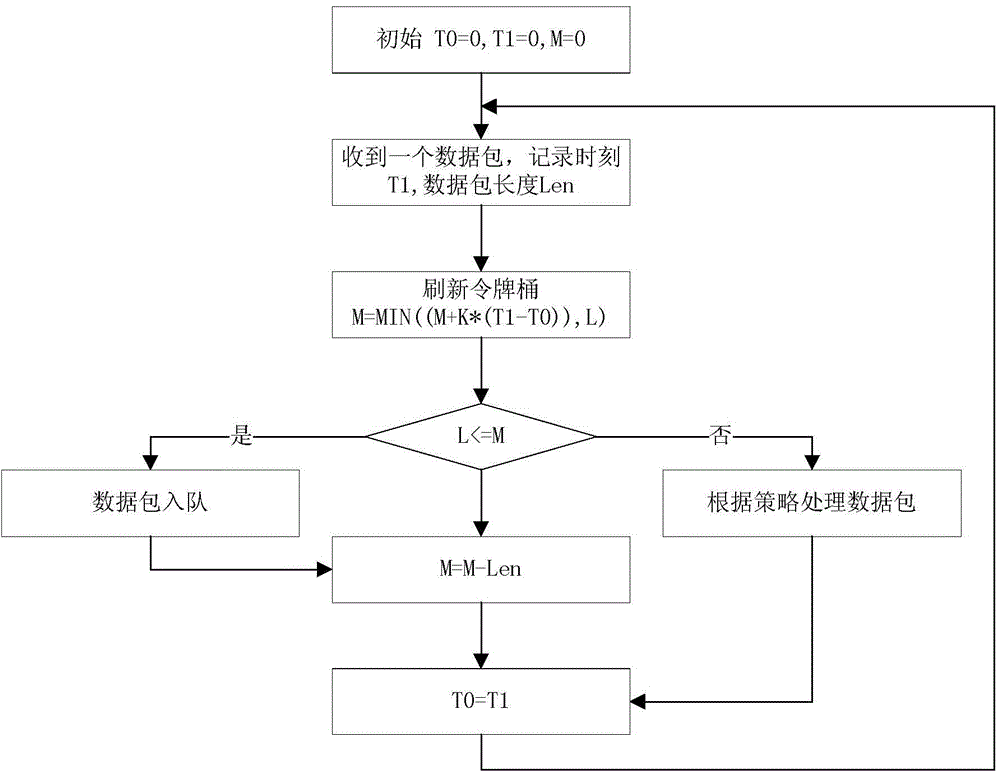
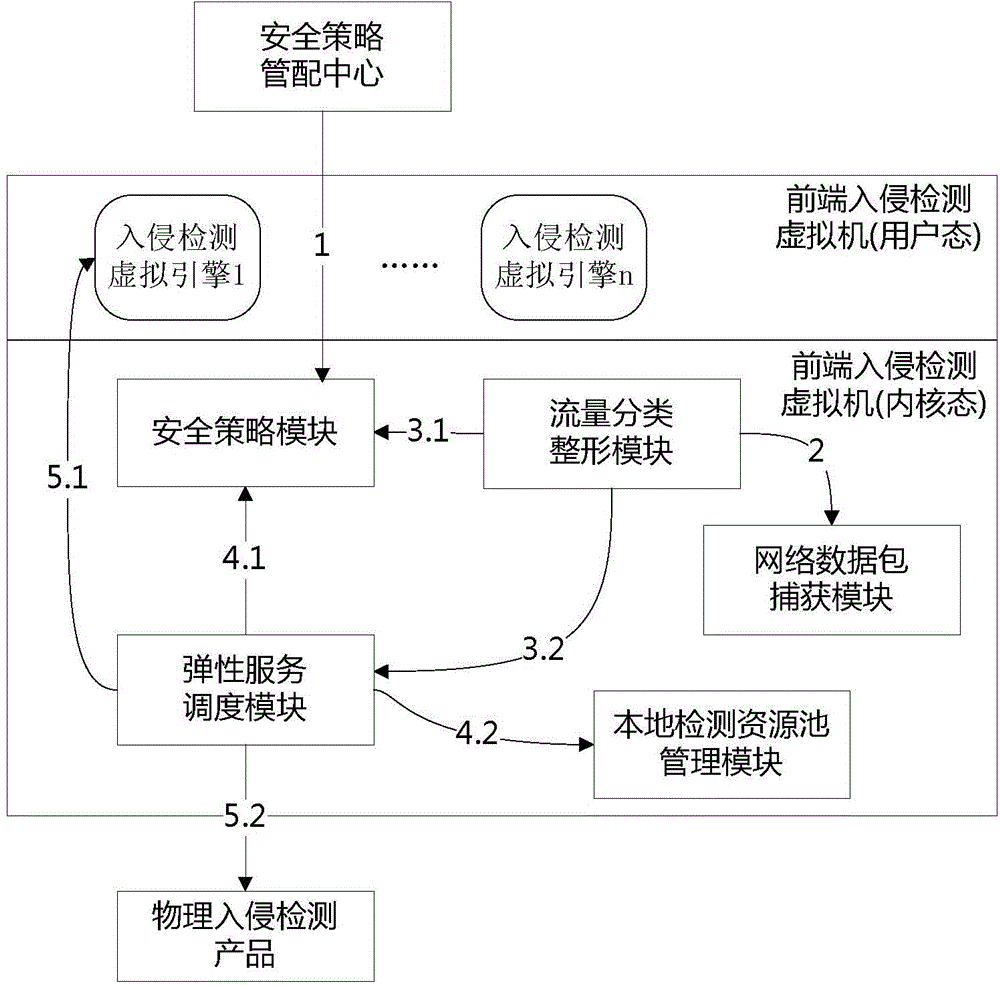
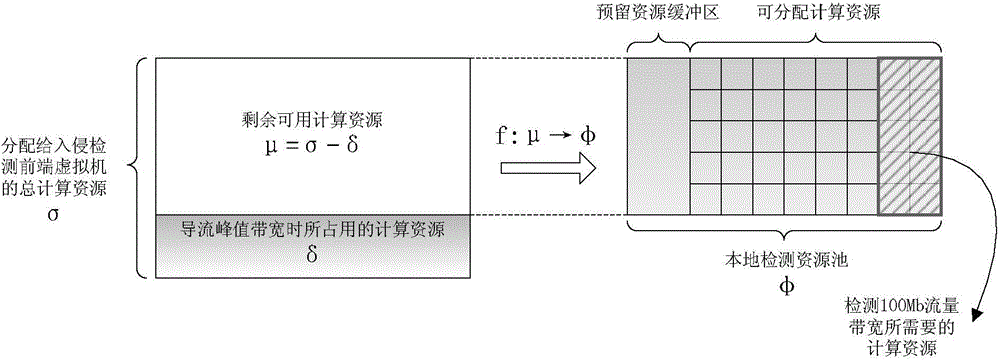
On-demand-service virtualization network intrusion detection method and device
InactiveCN104580120ASolve security issuesIncrease flexibilityTransmissionResource poolVirtualization
The invention discloses an on-demand-service virtualization network intrusion detection method and device, and relates to the technical field of information security. The virtualization network intrusion detection device comprises an elastic service scheduling module, and a local detection resource pool management module, wherein the elastic service scheduling module is used for evaluating whether the residual resource in a local detection resource pool can provide a local detection service or not, sending a local detection resource regulation command to the local detection resource pool management module if the residual resource can provide the local detection service, and exporting flow to be detected to an external hardware network intrusion detection product if the residual resource cannot provide the local detection service; the local detection resource pool management module allocates corresponding resources to the local detection resource from the residual resource of the local detection resource pool when receiving the local detection resource regulation command. The invention further discloses an on-demand-service virtualization network intrusion detection method. According to the technical scheme provided by the invention, the safety protection problem of a server virtualization application scene under a virtualization network environment is effectively solved.
Owner:BEIJING VENUS INFORMATION TECH +1
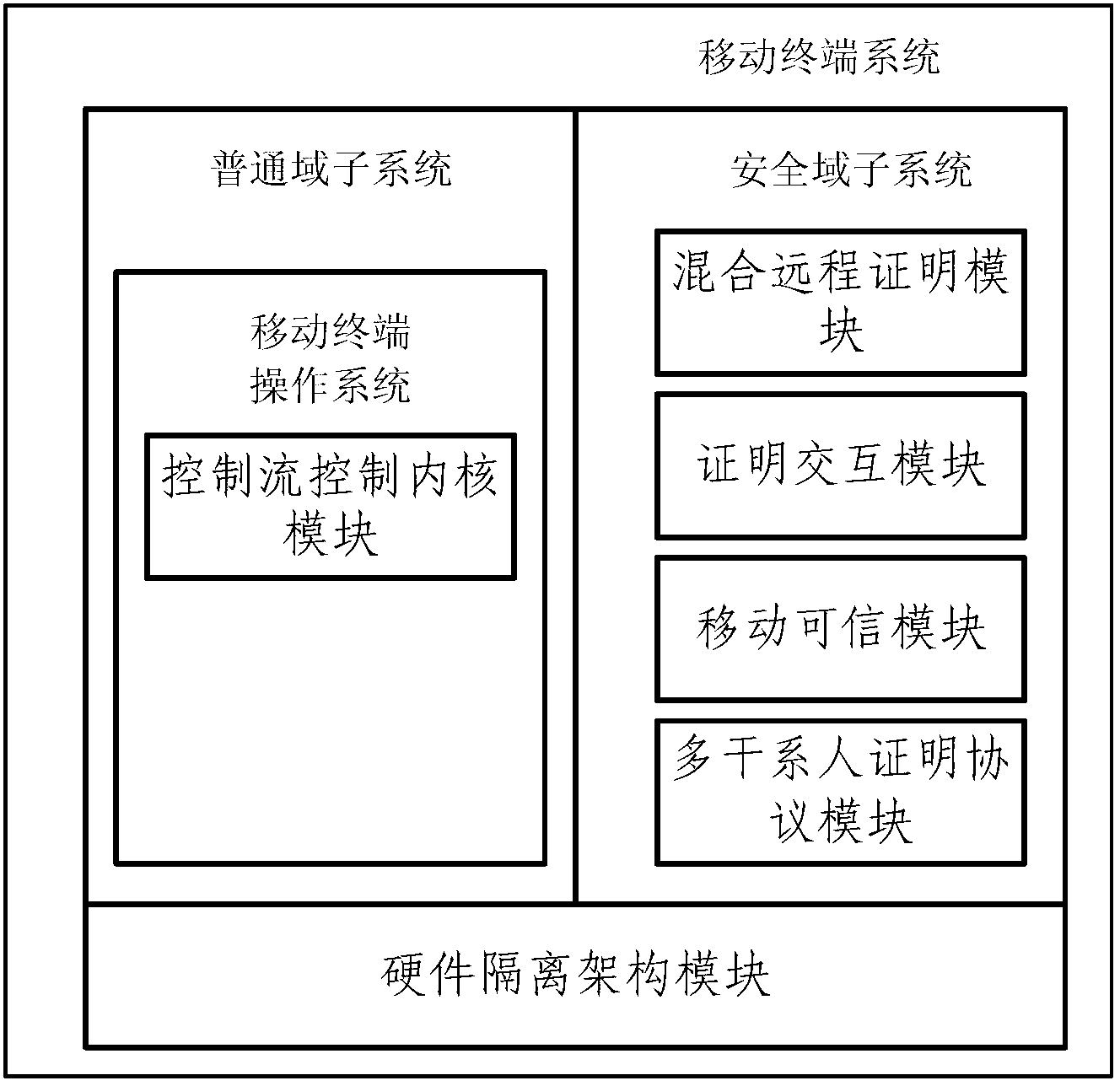
Mobile terminal system supporting dynamic remote attestation
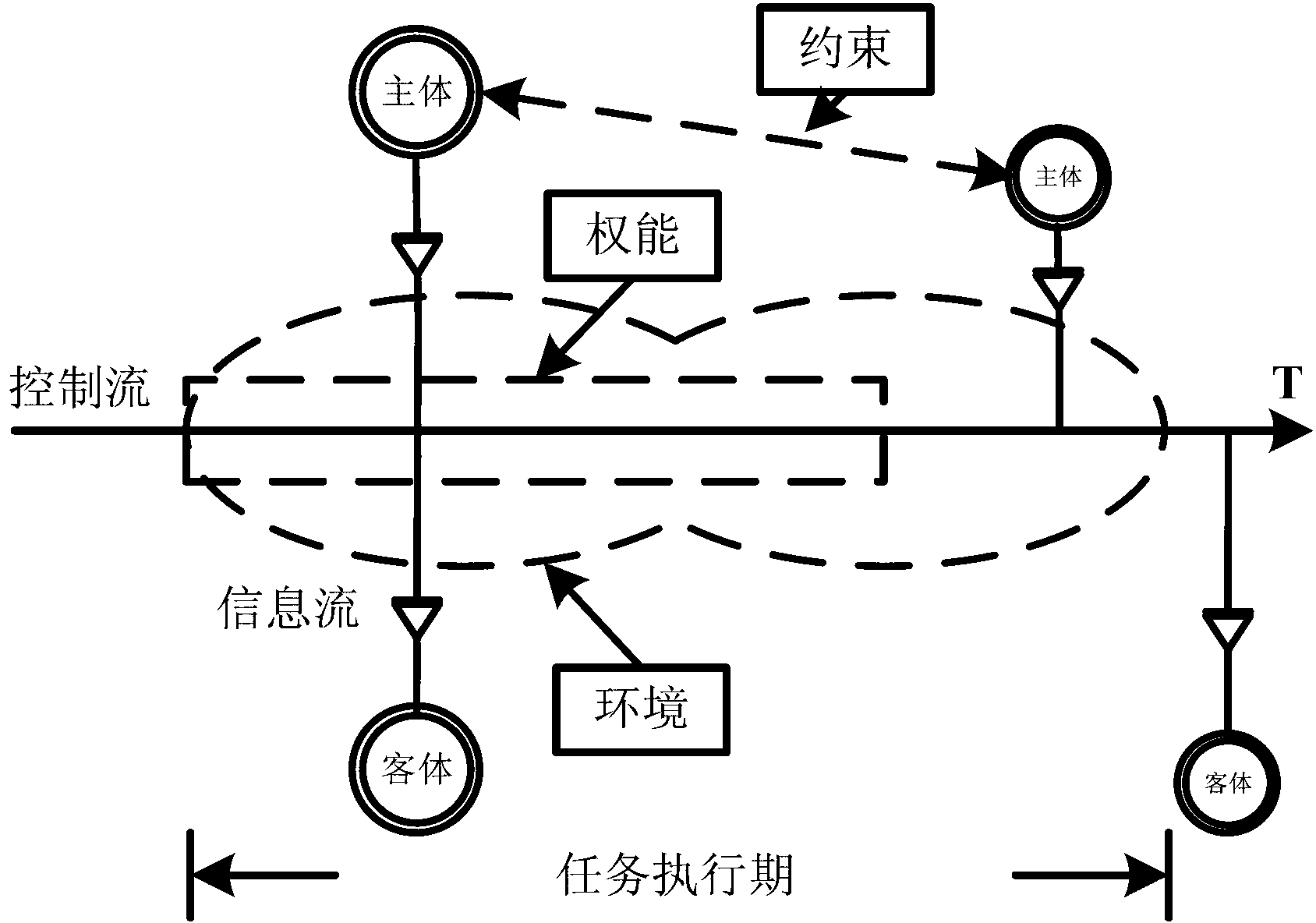
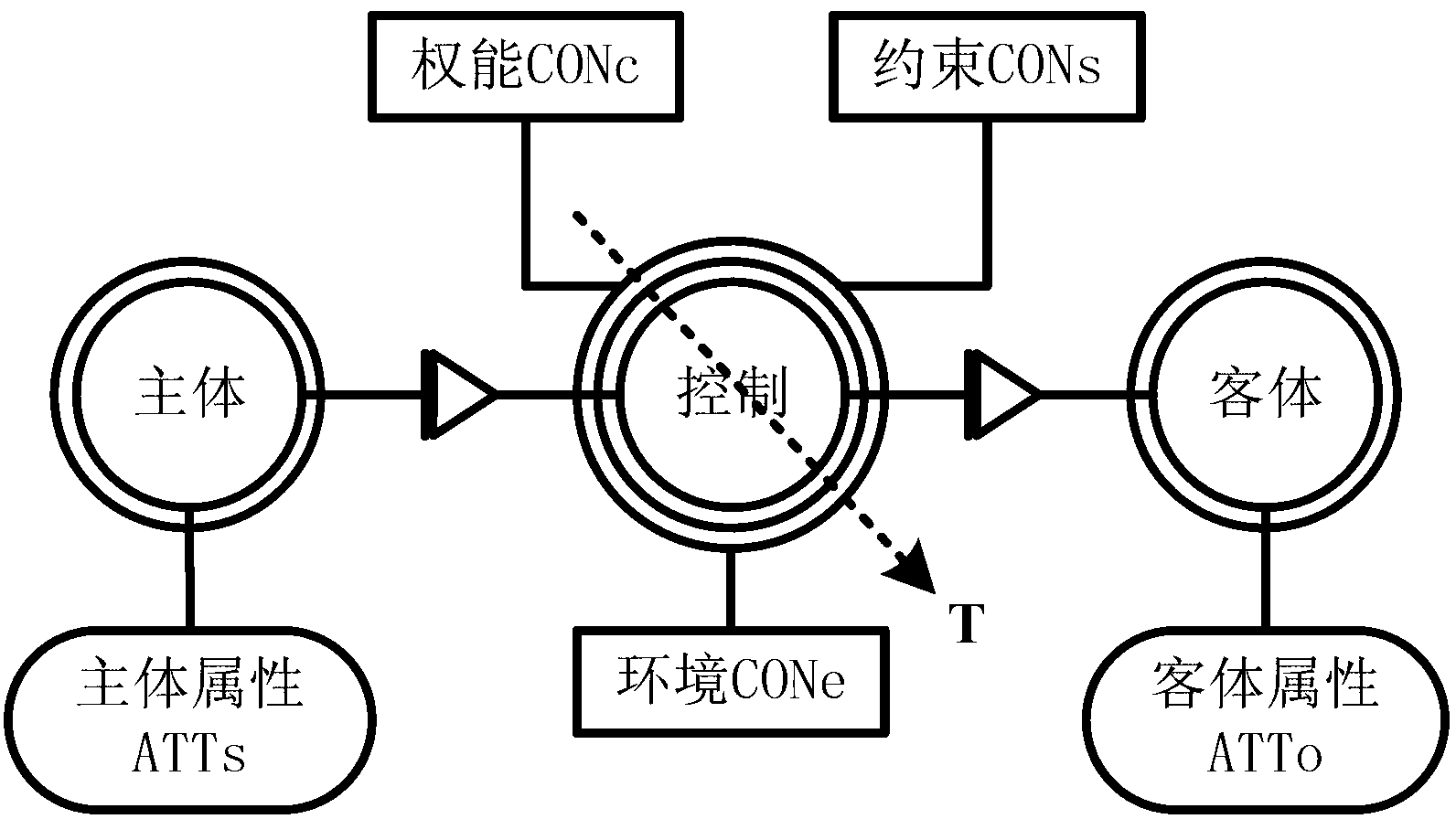
ActiveCN103220300AIncrease credibilitySolve security issuesUser identity/authority verificationControl flowOperational system
The invention relates to a mobile terminal system supporting dynamic remote attestation. The mobile terminal system comprises a control flow control kernel module, a hybrid remote attestation module and an attestation interaction module, wherein the control flow control kernel module is used for realizing a control flow model on an operating system of a mobile terminal and controlling the subject attribute, object attribute, capability conditions, constraint conditions and environment conditions in the mobile terminal system based on the control flow model and a security policy; the hybrid remote attestation module simultaneously supports a model-behavior-based remote attestation method and a multiple-measurement-based remote attestation method, and is used for carrying out remote authentication on the subject attribute, object attribute, capability conditions, constraint conditions and environment conditions in the system; and the attestation interaction module is used for transmitting attestation information acquired by the hybrid remote attestation module to a server for authentication and receiving authentication result information from the server. According to the mobile terminal system supporting the dynamic remote attestation, disclosed by the invention, the model-behavior-based remote attestation method and the multiple-measurement-based remote attestation method can be simultaneously applied to the mobile terminal system, so that the credibility and security of the mobile terminal system are enhanced.
Owner:TSINGHUA UNIV
Swivel construction method for large span continuous beam which spans existing station
ActiveCN105648926AThe method steps are simpleReasonable designBridge erection/assemblyButtressReinforced concrete
The invention discloses a swivel construction method for a large span continuous beam which spans an existing station. The constructed large span continuous beam is a reinforced concrete box beam which spans the existing station and the two ends of a middle span of the constructed large span continuous beam are supported on a second buttress and a third buttress correspondingly. A swivel construction process includes the steps that (1) swivel system construction is performed, specifically, swivel systems are constructed at the bottom of the second buttress and the bottom of the third buttress correspondingly, each swivel system comprises a lower supporting disc, an upper rotary disc, bridge swivel spherical hinges and a swivel hauling system, multiple supporting feet are disposed at the bottom of the upper rotary disc, and a lower bearing platform is provided with an annular sliding way where the supporting feet slide; (2) construction of the second buttress and the third buttress is performed; (3) construction of a front side beam body and a rear side beam body is conducted; and (4) plane swivel construction is carried out, specifically, the plane swivel construction is performed through the two swivel systems and the two swivel hauling systems. The swivel construction method for the large span continuous beam which spans the existing station is simple in steps, reasonable in design, easy and convenient to construct, good in using effect, capable of easily, conveniently and rapidly finishing the swivel construction process for the large span continuous beam spanning the existing station and safe in construction process.
Owner:CHINA RAILWAY 20 BUREAU GRP
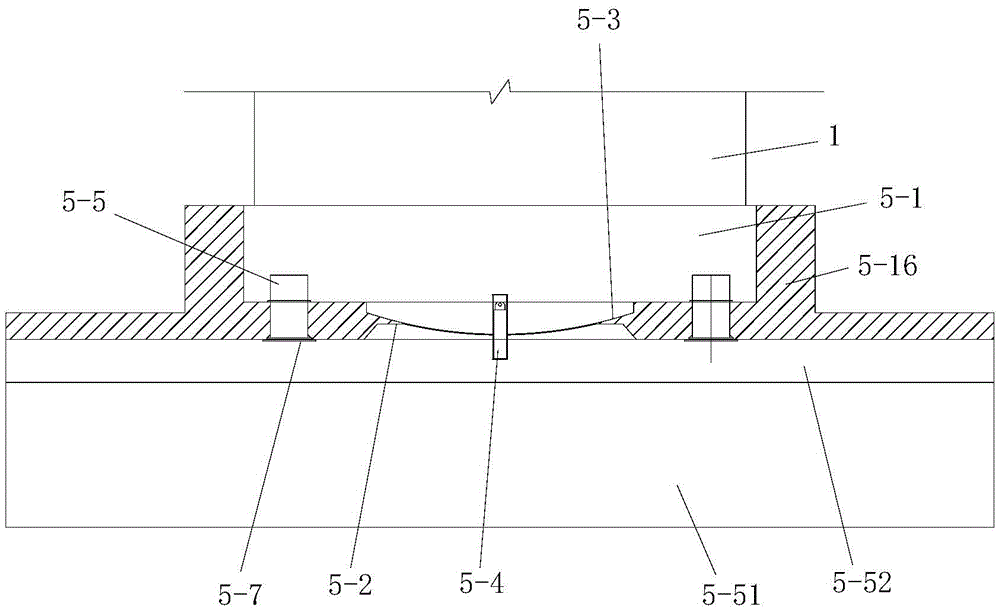
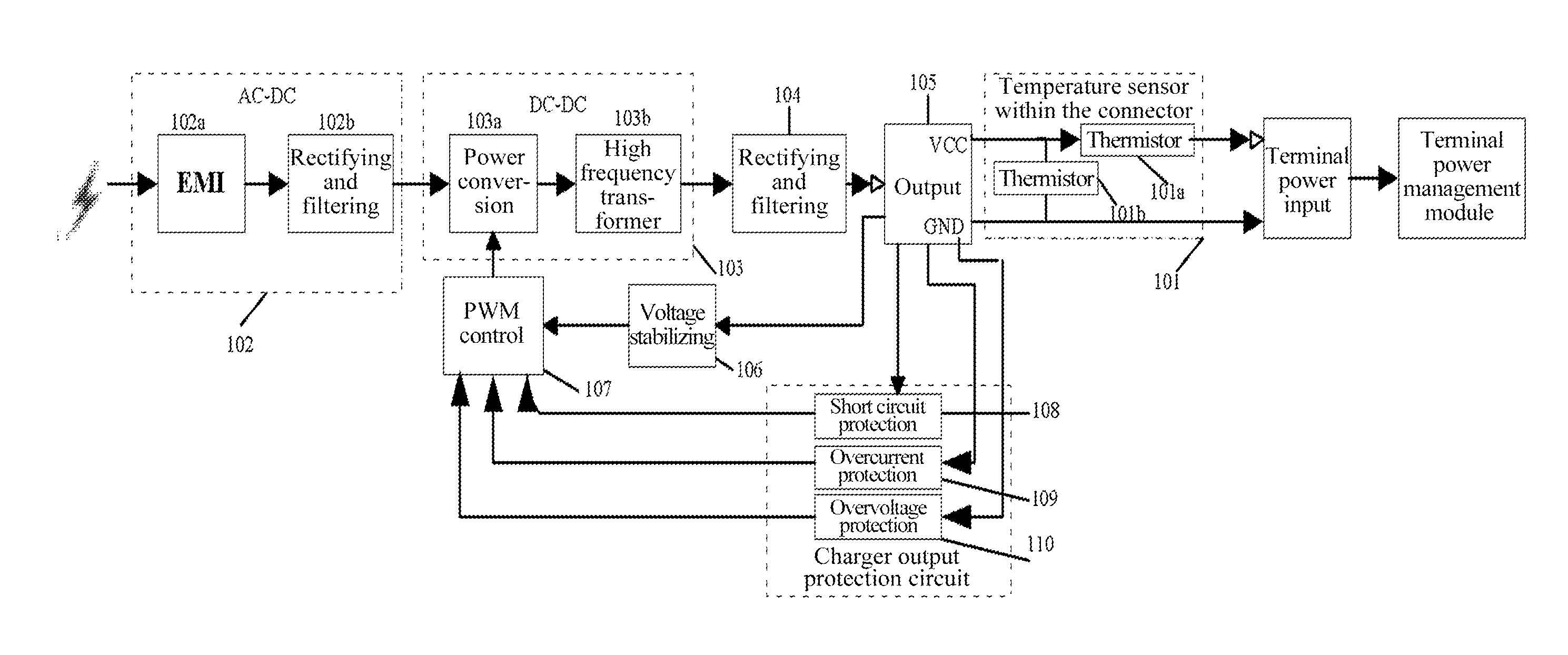
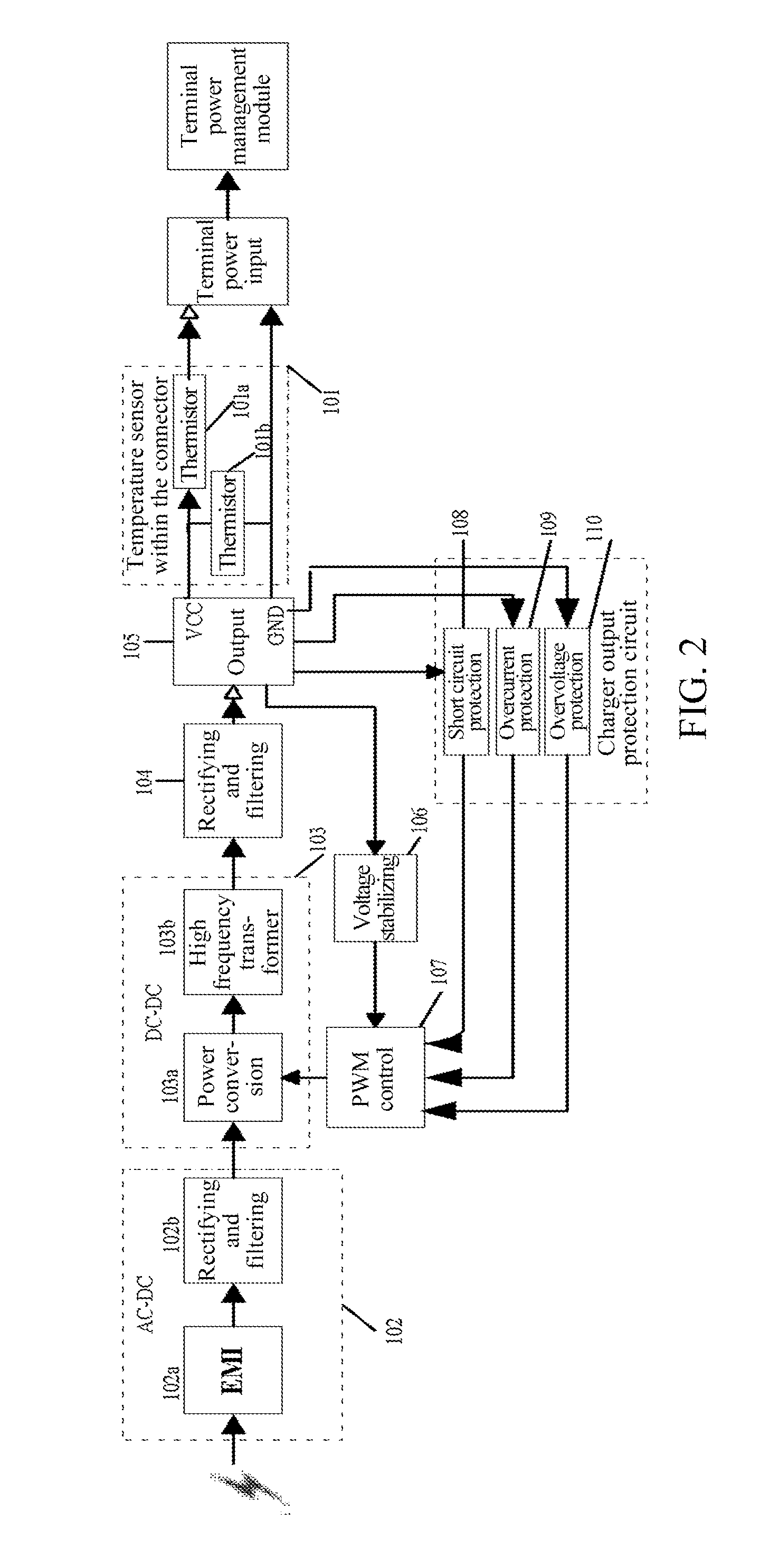
Mobile Terminal Charger
ActiveUS20160197500A1Safety can be solvedSolve security issuesElectric powerBattery overcurrent protectionElectrical batteryThermistor
A mobile terminal charger relates to the field of mobile terminals such as cell phone and data card with battery charging. The mobile terminal charger comprises: a thermistor and a charger output protection circuit, wherein the thermistor mounted on a head of a connector accesses a charger circuit via a charger direct current (DC) cable, constitutes a charger loop resistor with the resistor in the charger; and the charger output protection circuit cuts off or reduces the output power of the charger when the resistance of the charger loop resistor is less than the overcurrent protection threshold value.
Owner:XIAN ZHONGXING NEW SOFTWARE
Battery assembly
ActiveUS7670718B2Solve security issuesAvoid dangerLi-accumulatorsCell component detailsElectric powerLithium battery
Owner:BIXIANG ELECTRIC ENERGY HIGH SCI & TECHCO
Mobile wireless monitoring and alarming fence system
ActiveCN102419884ASolve security issuesGuarantee the safety of lifeEnergy efficient ICTBurglar alarmMobile wirelessEngineering
The invention discloses a mobile wireless monitoring and alarming fence system, which comprises multiple mobile wireless monitoring and alarming fences and a monitor center, wherein the multiple mobile wireless monitoring and alarming fences are used for field security protection and are vertically arranged at certain interval; the monitor center is used for remote monitoring of the multiple mobile wireless monitoring and alarming fences; the monitor center is in wireless communication connection with the multiple mobile wireless monitoring and alarming fences; and two adjacent mobile wireless monitoring and alarming fences are in signal correlation connection through signal sending and signal receiving. The mobile wireless monitoring and alarming fence system disclosed by the invention can overcome the defects of high cost, high risk, low reliability, large electric power consumption, small application range and the like in the prior art, and has the advantages of simpleness in installation, convenience for moving, no need for commercial power, low cost, good safety, high reliability, strong interference resistance, good stability, energy saving and environmental friendliness andlarge application range.
Owner:WUHAN POWER TECH
ID authentication method based on representation of barcode
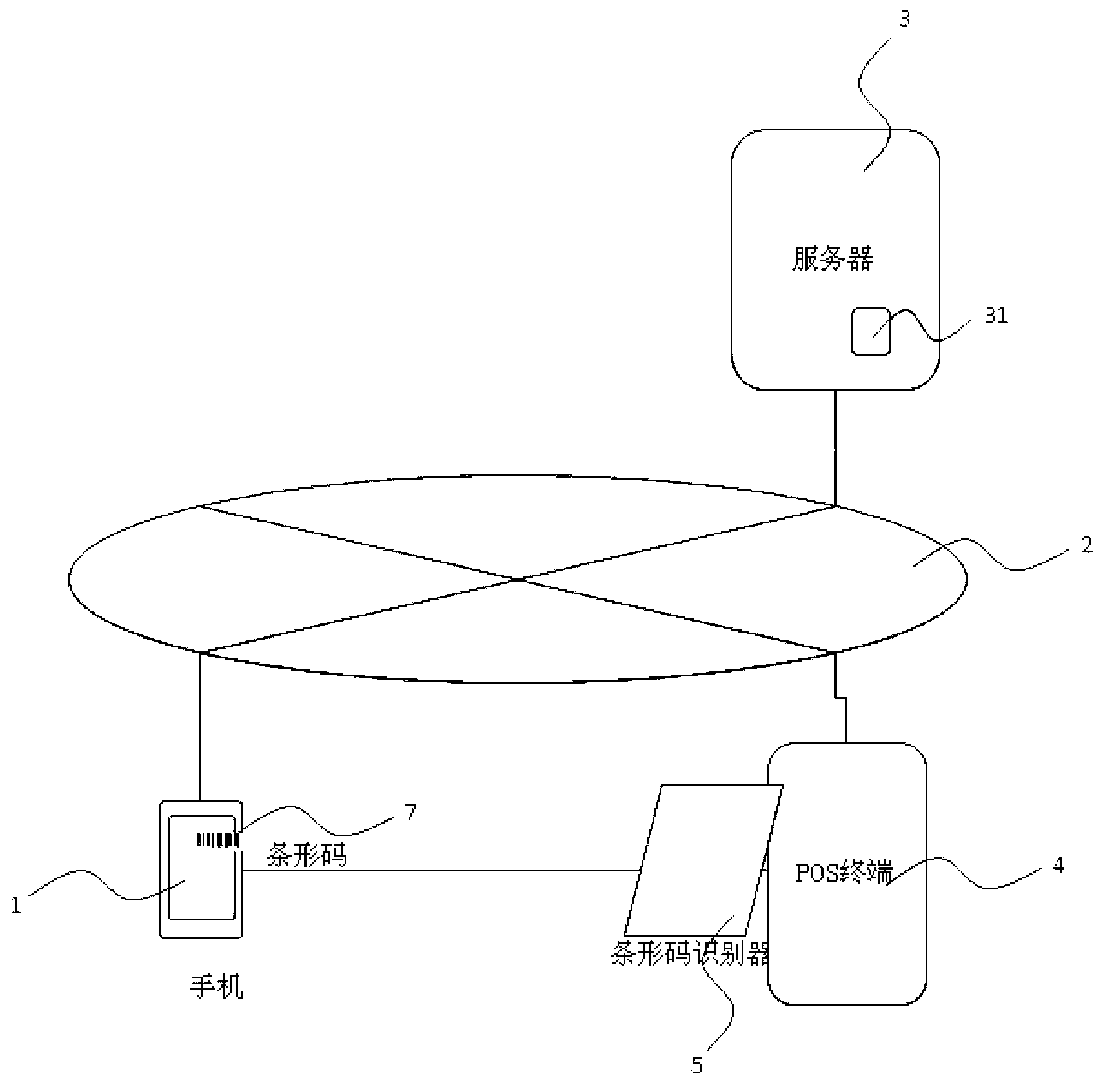
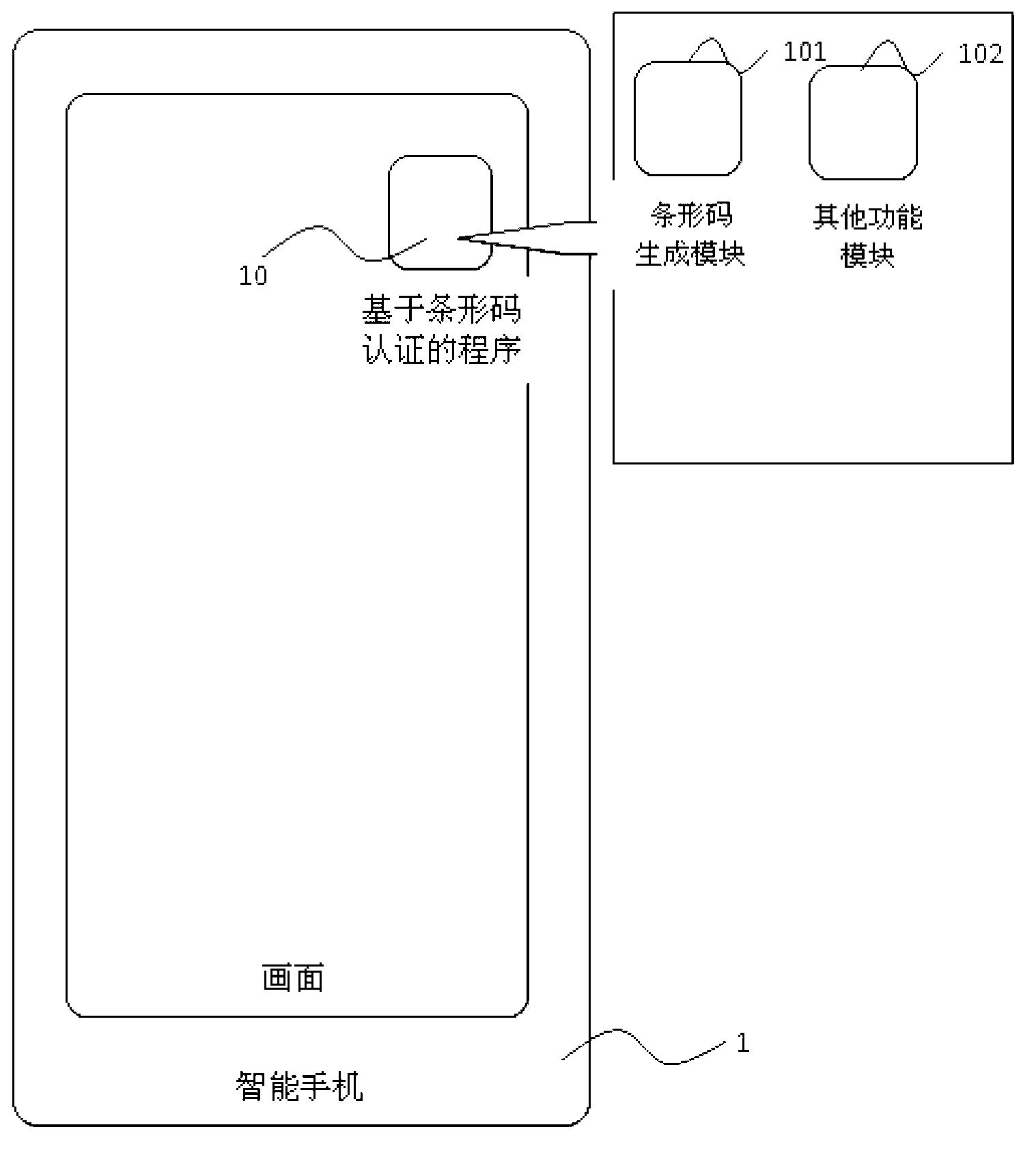
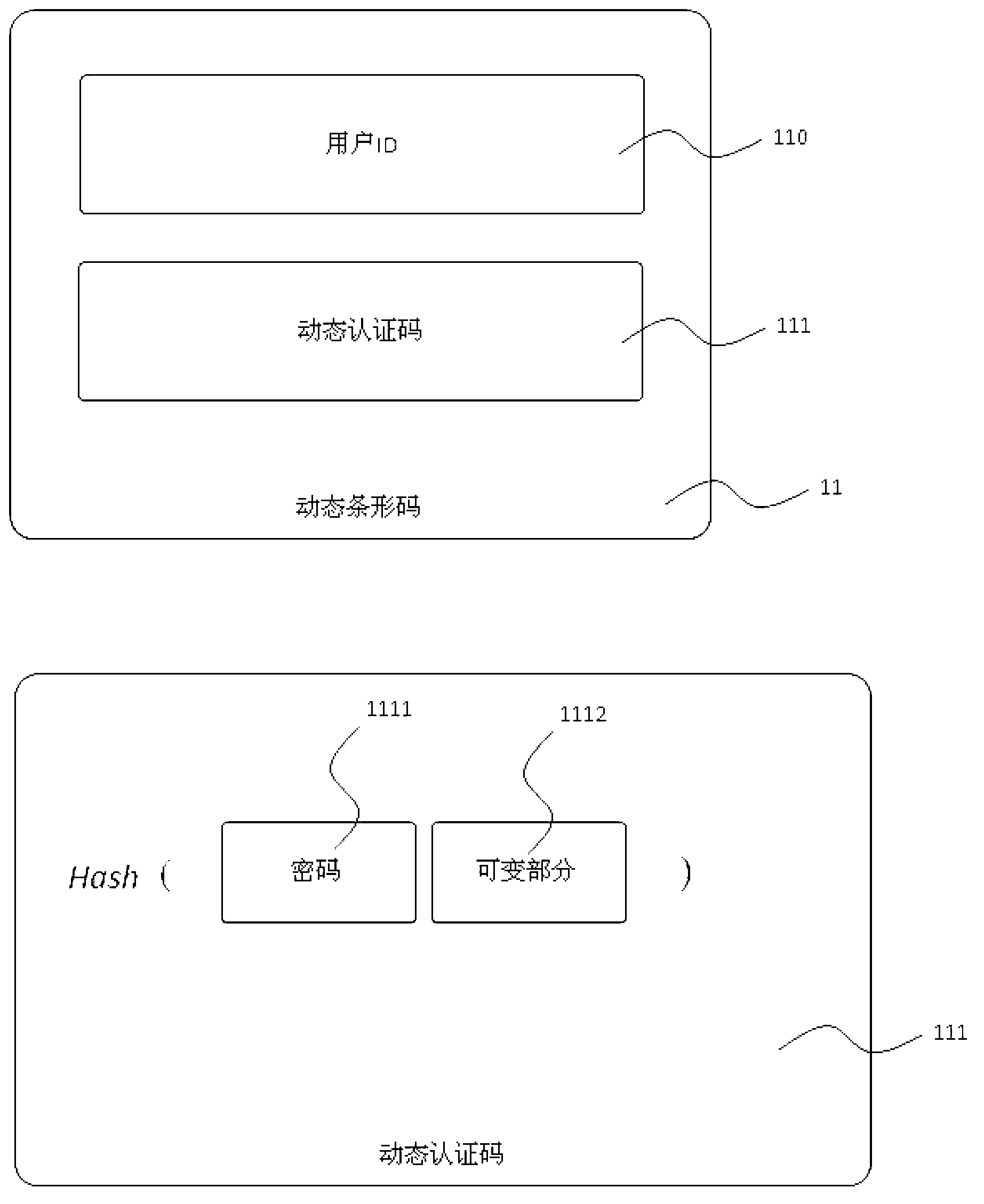
ActiveCN103258265ASolve security issuesPoint-of-sale network systemsProtocol authorisationComputer hardwareAuthentication information
A barcode which is generated by a mobile phone or represents an ID of a user is used. Various treatment which needs ID authentication such as electronic payment in electronic commerce is finished through the ID represented by the barcode. Due to the fact that the barcode needs to be represented through a picture, a secure channel cannot be set up just like NFC or other communication methods. In order to prevent the ID from being masked, a usual method comprises the step that the user inputs a PIN to further carry out confirmation. In the ID authentication method based on the representation of the barcode, the authentication of the PIN is replaced by the method using a dynamic authentication code. The dynamic authentication code is guaranteed to be effective only in a certain time range. The user just needs to prevent the own barcode from being stolen in the certain time, and then safety of the ID authentication can be guaranteed, so that authentication procedures are simplified and the needed time is shortened, and the above equal safety is guaranteed. An irreversible Hash value is adopted in the process of transmission of the dynamic authentication code, and the phenomenon that authentication information contained in an authentication code cannot be copied is guaranteed.
Owner:郁晓东
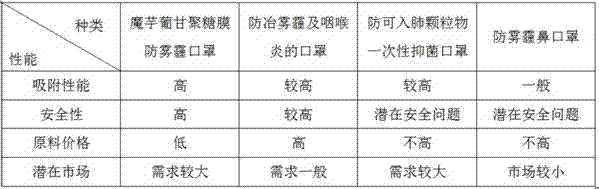
Konjac glucomannan membrane haze-prevention mask
ActiveCN105962481AGood material performanceSolve security issuesGarment special featuresProtective garmentAdditive ingredientElectric field
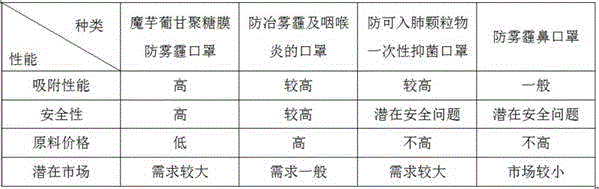
The invention relates to a konjac glucomannan membrane haze-prevention mask. A mask body of the konjac glucomannan membrane haze-prevention mask is composed of four layers which specifically include the first layer, namely, the outmost layer, made of non-woven fabric, the second layer made of a konjac glucomannan porous membrane, the third layer made of a konjac glucomannan nanometer porous membrane, and the fourth layer, namely, the layer in contact with the face, made of non-woven fabric. With natural polymer polysaccharide, namely, konjac glucomannan, serving as the main ingredient, the konjac glucomannan membrane haze-prevention mask has various characteristics of hydrophilia, the thickening characteristic, stability and the like. In recent years, natural polymer compounds are widely applied to the material field, and many problem emerging on material safety are solved. The technology of preparing high-quality nanometer porous membranes with plant polysaccharide serving as the raw materials become a hot point in recent years; according to the method, the special gel property of konjac glucomannan is utilized, and the konjac glucomannan nanometer porous membrane is obtained through application of the electric field technology, and has great application potential in the material field. The konjac glucomannan membrane haze-prevention mask has higher indexes such adsorption performance, safety, raw material price and potential markets than those of other masks on the market, and can be selected by mass consumers as high-quality haze-prevention masks.
Owner:上海盈兹无纺布有限公司
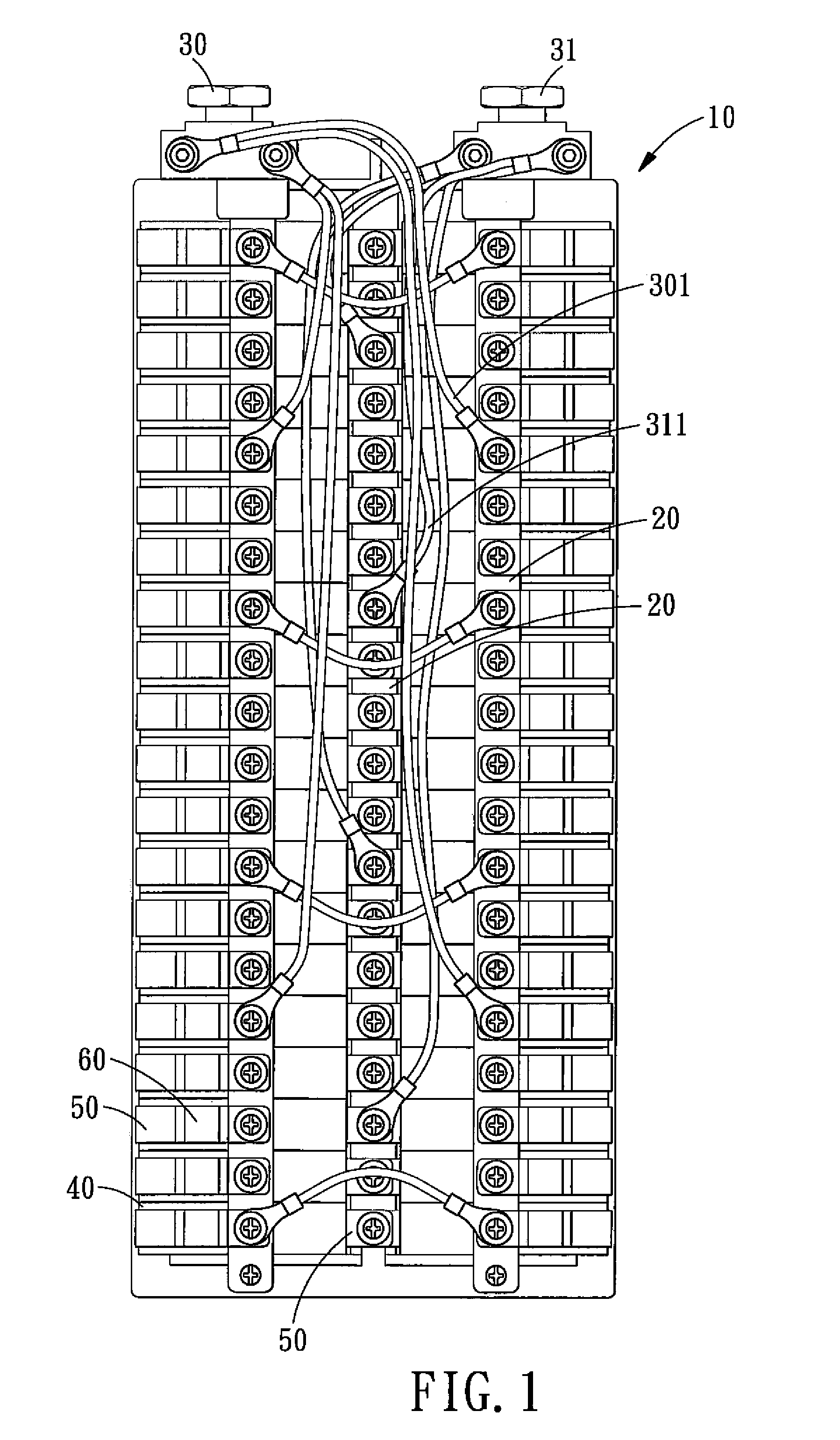
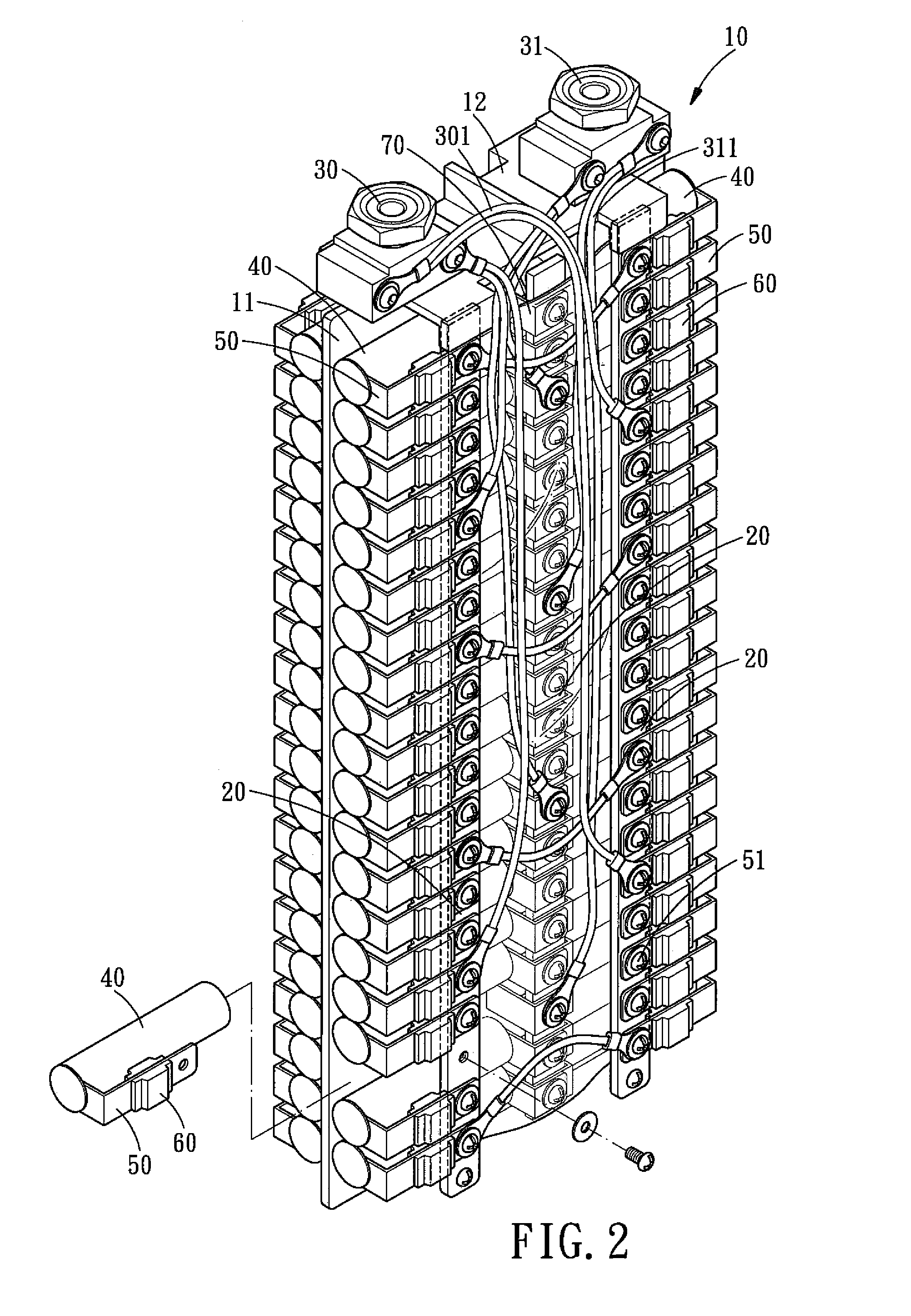
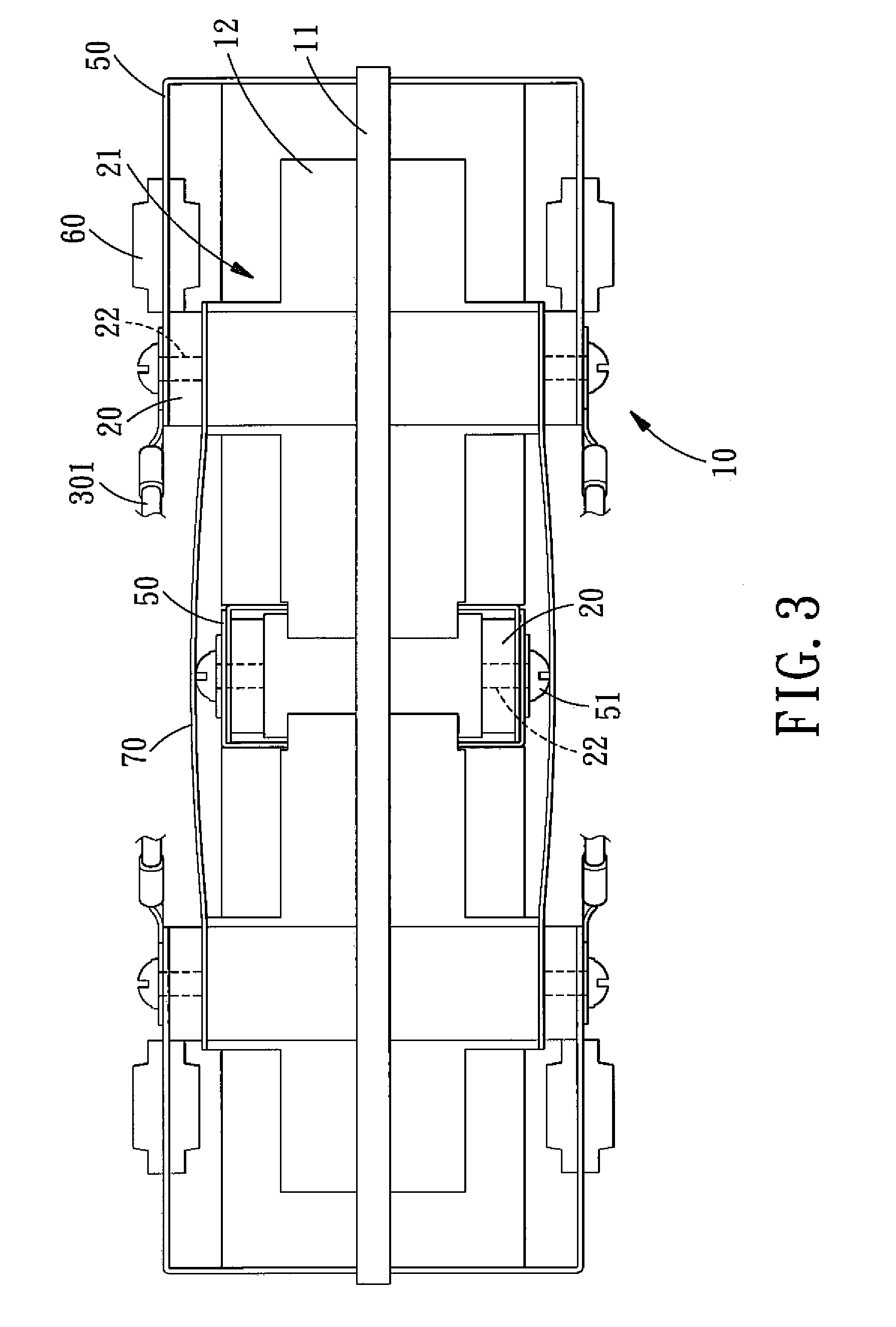
Independent Separating Type Power Battery Assembly
ActiveUS20090061298A1Solve security issuesAvoid dangerPrimary cell to battery groupingLi-accumulatorsPower batteryEngineering
An independent separating type power battery assembly comprises a rack assembly, a plurality of guiding strips, two polar heads, a plurality of lithium batteries and safety units. The guiding strips are connected to the polar heads and are disposed on the rack assembly, respectively. The rack assembly has a containing space for accommodating the lithium batteries, and each lithium battery is connected to the guiding strip by a guiding piece via one safety unit, such that the lithium batteries are connected in parallel, thus providing enough power with a small size. In addition, each safety unit can cut off the broken lithium battery separately, so as to avoid the immediate shut-off of the electric power.
Owner:BIXIANG ELECTRIC ENERGY HIGH SCI & TECHCO
Apparatus and method for managing customized application
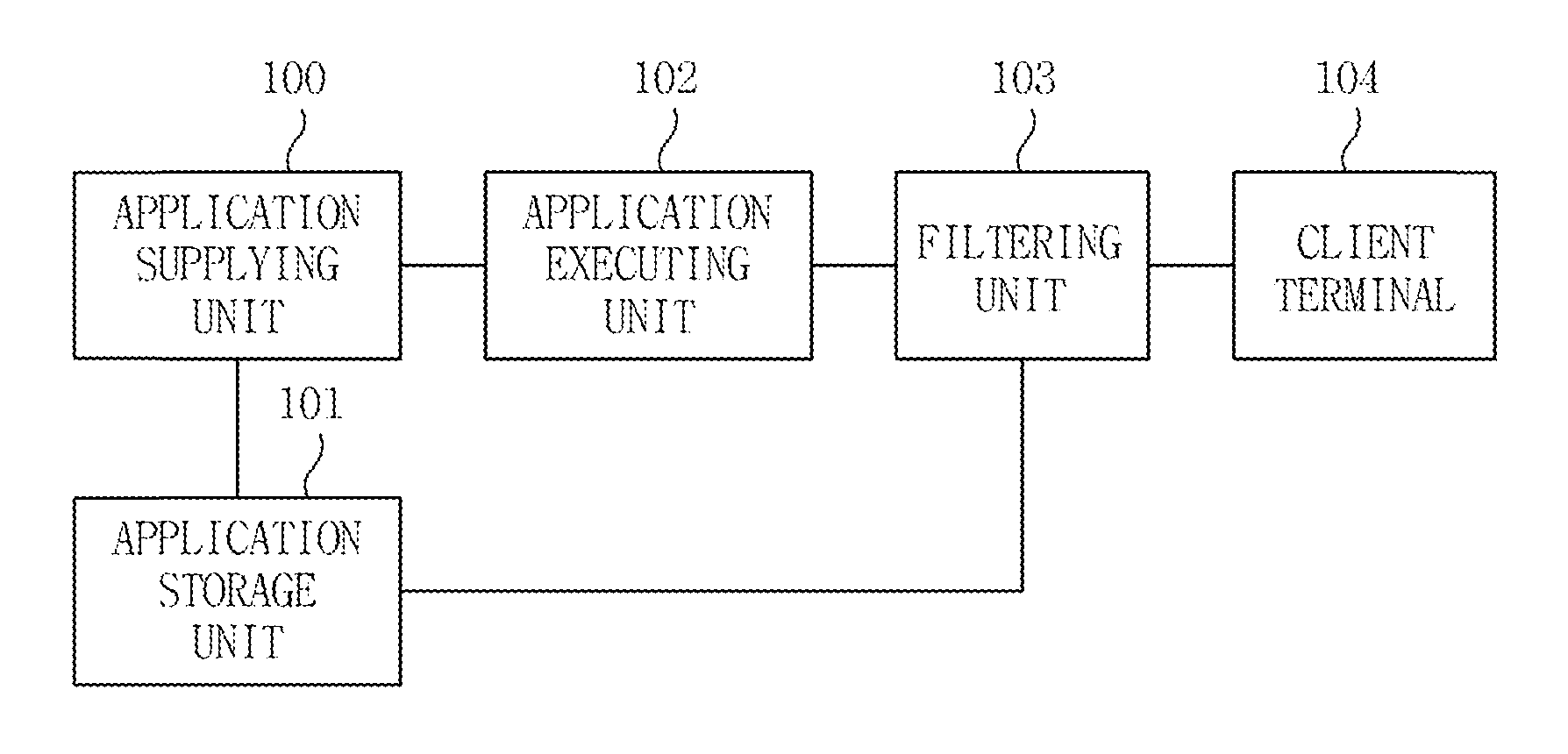
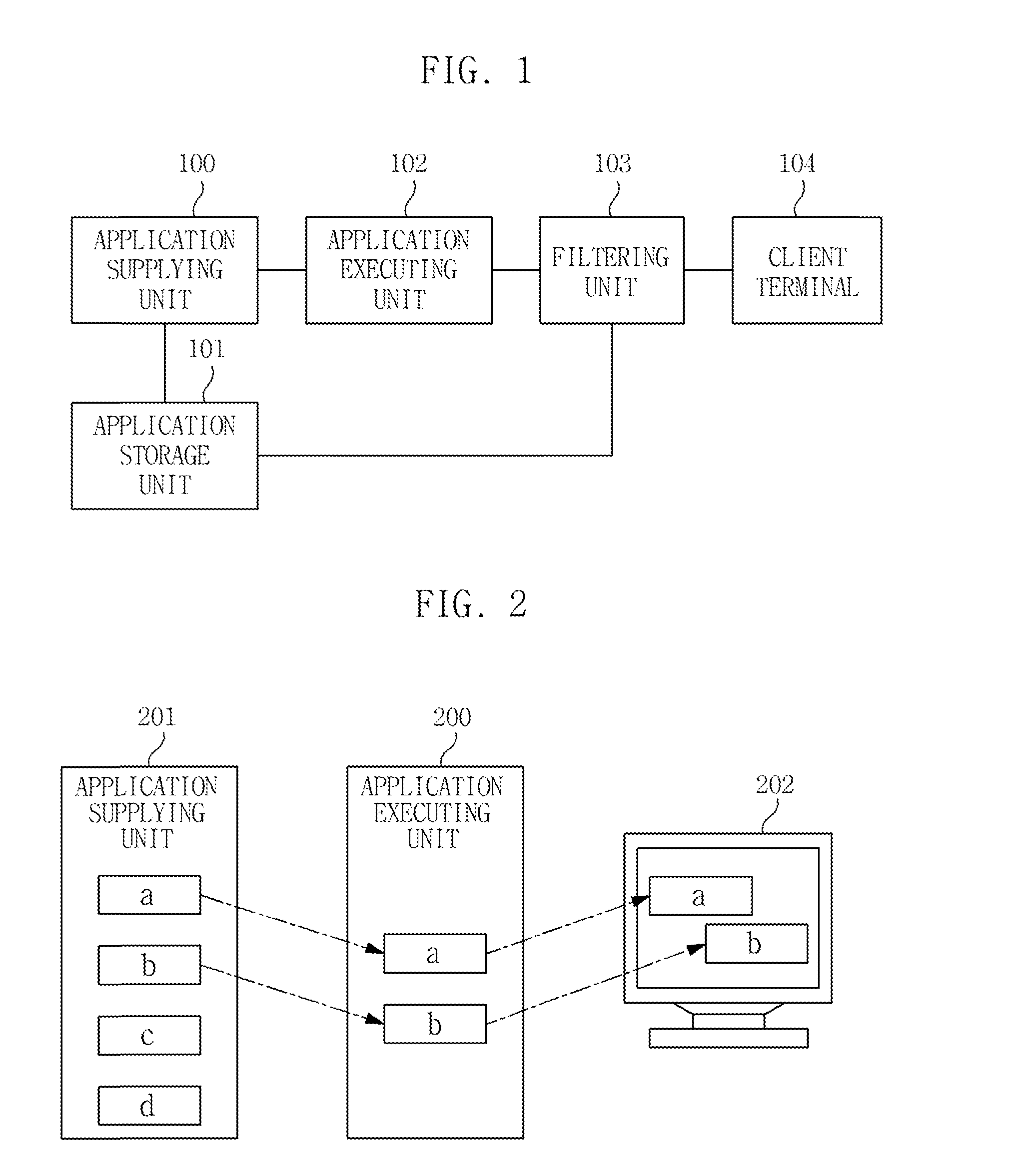
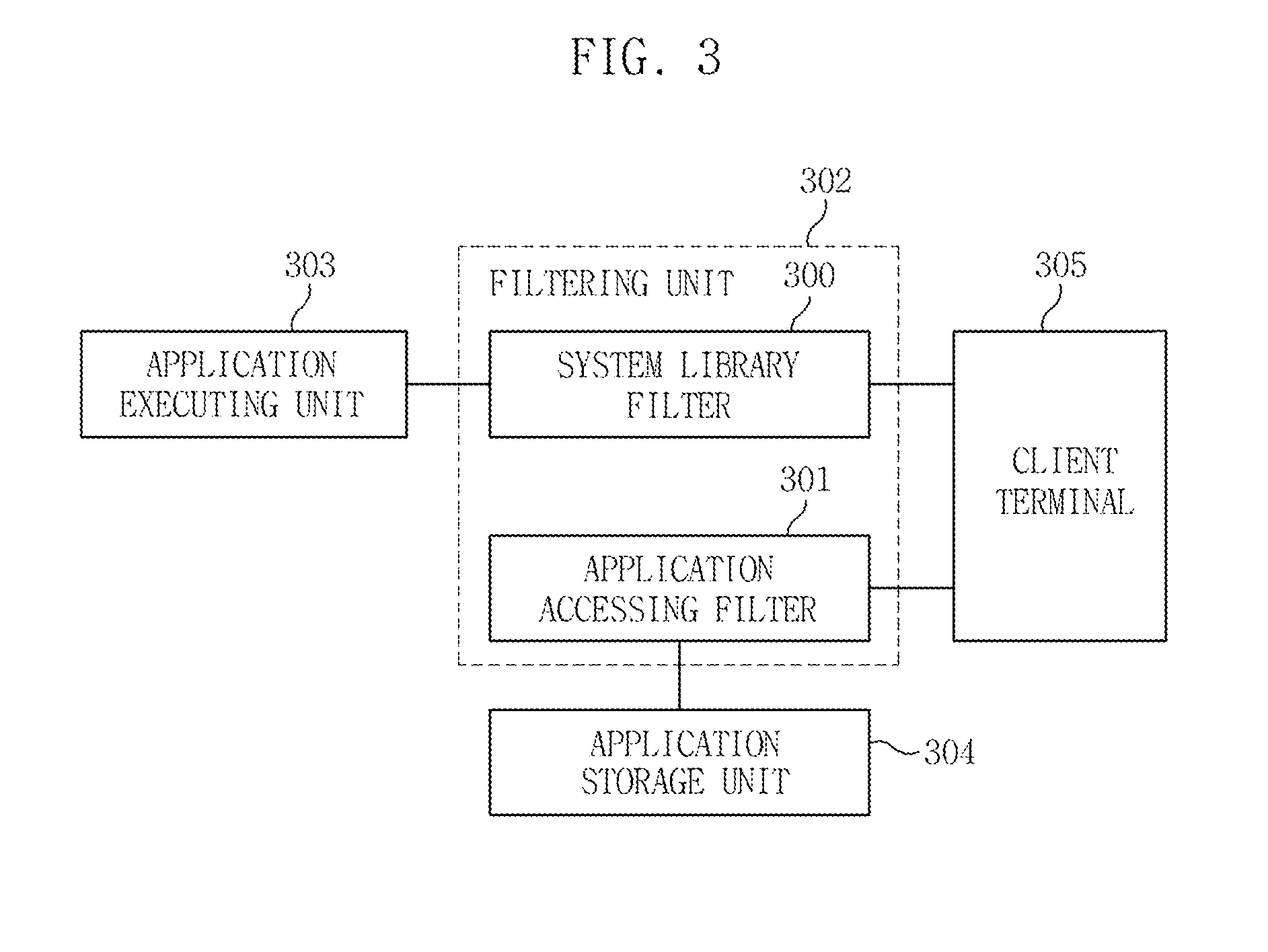
InactiveUS20110154374A1Easy to disassembleImprove stabilityMultiprogramming arrangementsInformation controlApplication software
Provided is a technology capable of efficiently managing various customized applications according to clients and providing security and efficiency in executing and editing the customized applications. An apparatus for managing customized applications according to an exemplary embodiment of the present invention, comprising: an application supplying unit generating the customized applications by combining a plurality of pre-stored application data according to client information; an application executing unit generatin a virtual executing environment to allow the customized applications to be executed in a server or virtual server on a client terminal and supplies the virtual executing environment to the client terminal; and a filtering unit controlling whether it permits one or more of the execution and edition of the customized applications according to the client information.
Owner:ELECTRONICS & TELECOMM RES INST
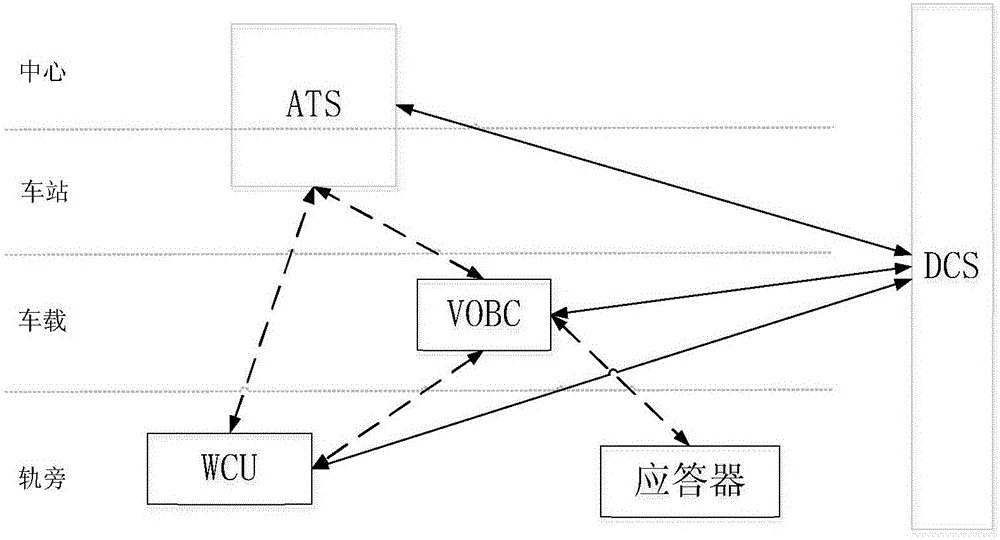
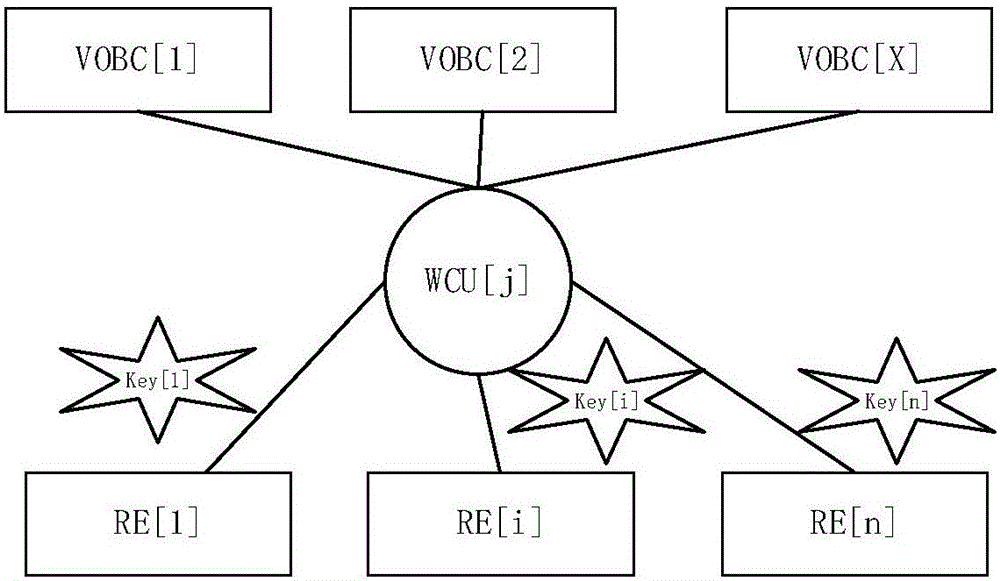
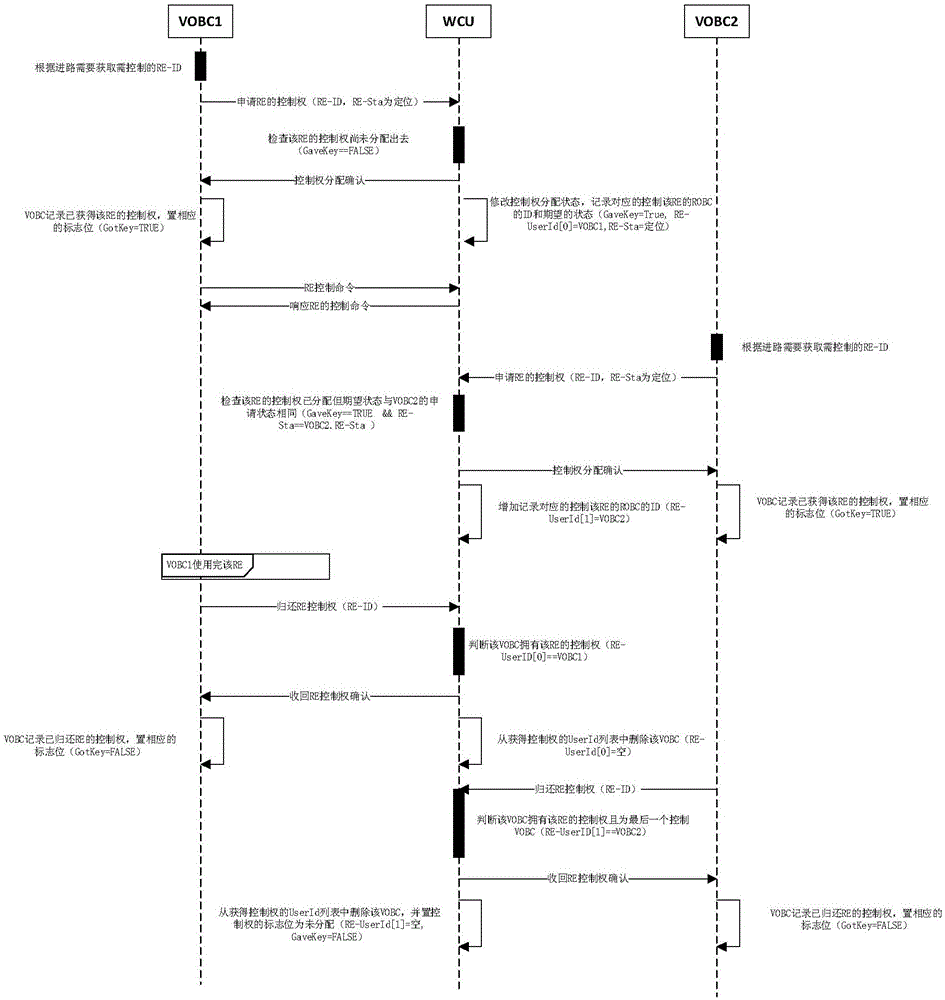
Method for safety control trackside device of vehicle-mounted controller
The invention provides a method for a safety control trackside device of a vehicle-mounted controller. The method comprises the following steps: after a train enters into an access road, acquiring a trackside controller corresponding to the access road by the vehicle-mounted controller according to an access table; sending a request for applying for a control right of the trackside device in the access road by the trackside controller; returning the control right of the trackside device to the vehicle-mounted controller by the trackside controller; operating the trackside device in the access road by the vehicle-mounted controller through the trackside controller; after completing the operation, returning the control right of the trackside device to the trackside controller by the vehicle-mounted controller. According to the invention, a control right mechanism is designed for realizing the cooperative control of the vehicle-mounted controller and the trackside controller; the safety in controlling the trackside device by the vehicle-mounted controller is guaranteed; the trackside device can be used when the expected states of a plurality of vehicle-mounted controllers for the trackside device are consistent to each other; the system efficiency is increased.
Owner:BEIJING JIAOTONG UNIV
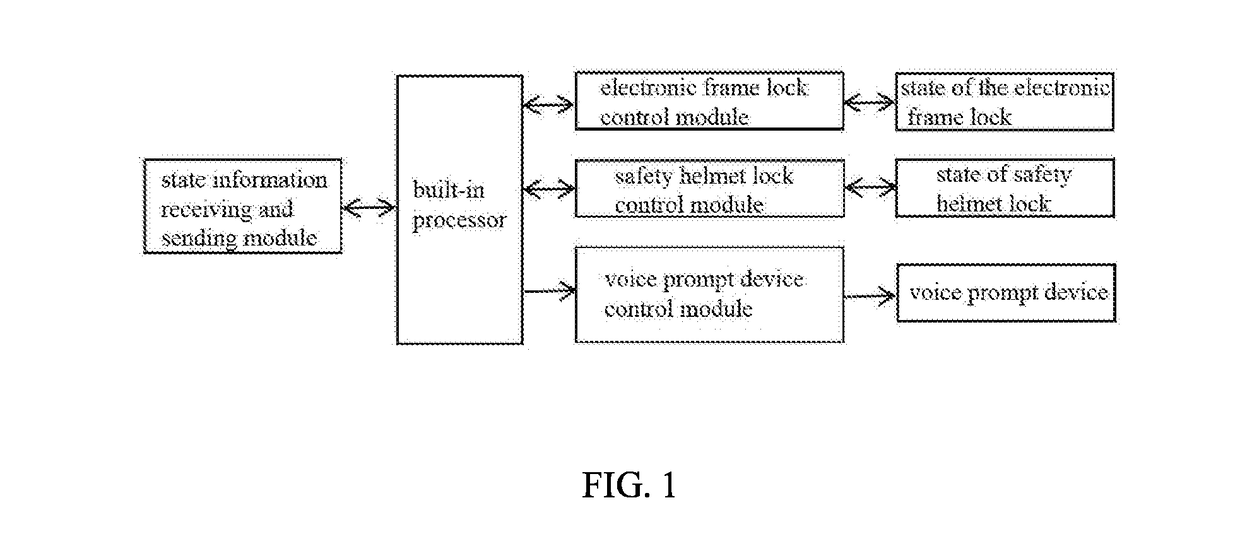
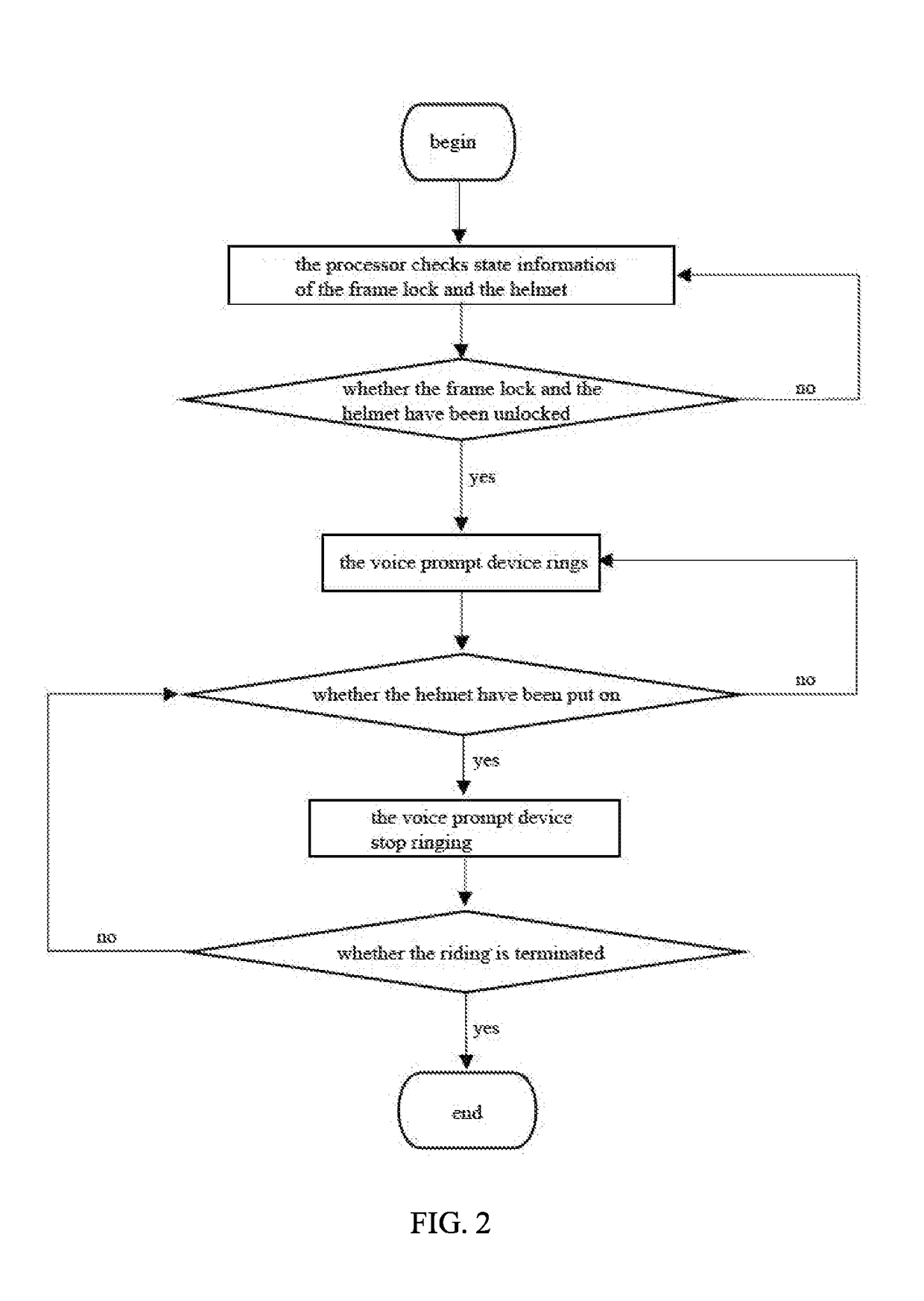
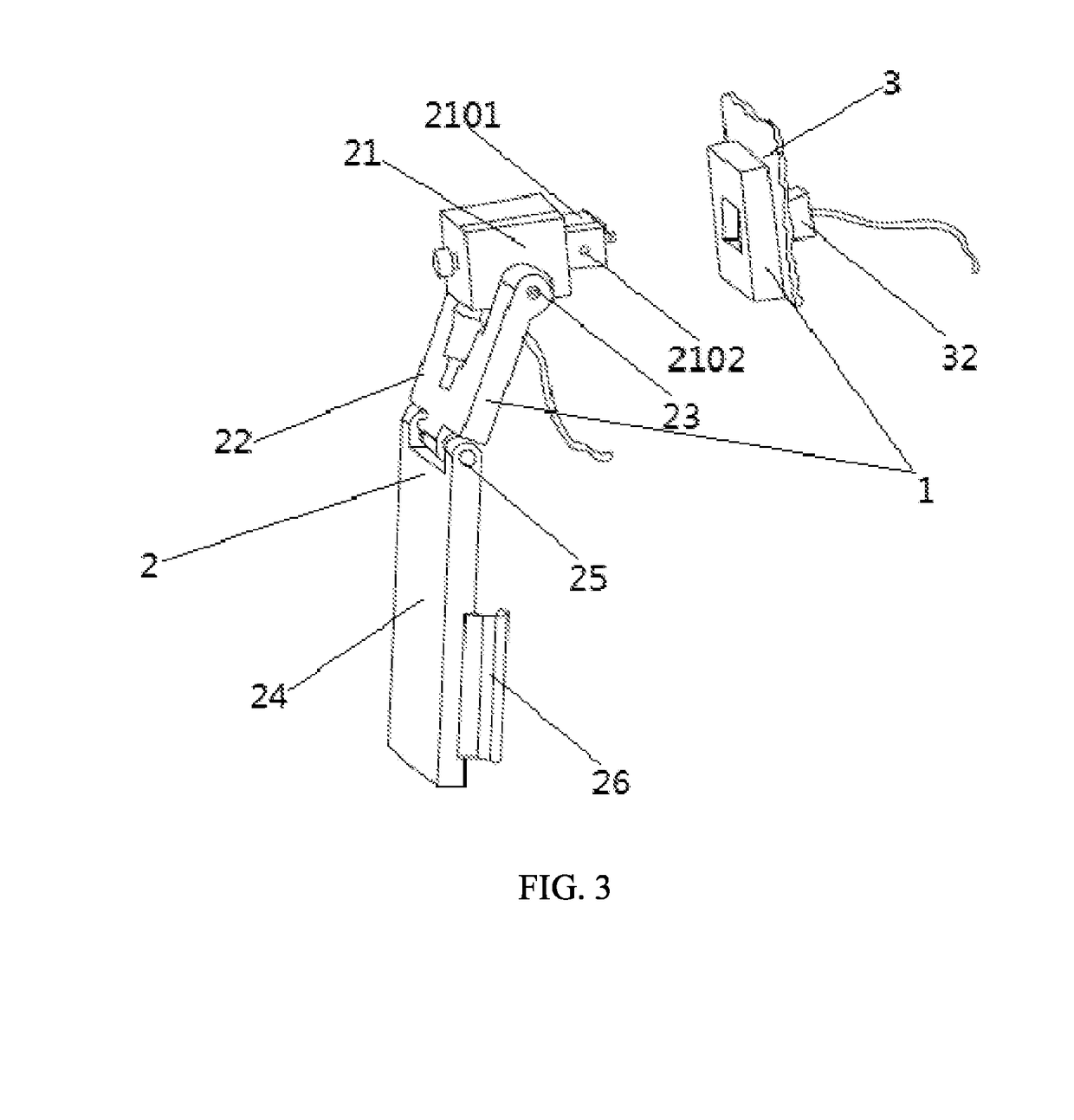
Interlocking method and interlocking device for shared bicycle and intelligent safety helmet
ActiveUS20190082764A1Conveniently obtainEnsure safetyTicket-issuing apparatusAnti-theft cycle devicesEngineering
The present invention discloses a method for interlocking a shared bicycle and an intelligent safety helmet, and the method comprises the following steps: (1) providing an electronic frame lock and an intelligent safety helmet for using cooperatively on a shared bicycle respectively, interlocking both of them when the shared bicycle is parked; (2) checking the current state information of an electric lock and a safety helmet lock simultaneously when a user uses the mobile intelligent terminal to scan the shared bicycle; (3) unlocking of the electric lock and the safety helmet lock when the verification is passed; (4) wearing an intelligent safety helmet before using the bicycle; (5) beginning to record the trip information by the intelligent helmet after the user puts on the intelligent safety helmet; (6) stopping the voice broadcast function and terminating the recording of the trip information when the state information of the electronic frame lock and the safety helmet lock which is checked shows that the electronic frame lock and the safety helmet lock are locked, after the user terminates the using of the bike. The invention also discloses an interlocking device for a shared bicycle and an intelligent safety helmet implementing the above-mentioned method, which makes that the bicycle and the intelligent safety helmet are always in a state that they are used in cooperation with each other.
Owner:DONGGUAN UNIV OF TECH
Train operation safety protection system without secondary train occupation detection equipment
ActiveCN112406963ASolve security issuesSolve the problem of safe runningRailway traffic control systemsSignaling systemOperation safety
The invention discloses a train operation safety protection system without secondary train occupation detection equipment, and the system comprises an initial train position marking module which enables a dispatcher to mark the section occupation information corresponding to the initial train positions of all trains manually through ATS before the system is powered on, a train tracking initialization list module which is used for initializing a train tracking list by the ATS according to the marked section occupation information and sending the train tracking initialization list to the trackside ZC; and a running train position tracking module which is used for tracking the positions of all trains by the trackside ZC in the running process of the trains. According to the invention, the train operation safety protection can be realized when no secondary train occupies the detection equipment, and the safety protection problem of the signal system when no secondary train occupies the detection equipment for auxiliary protection is effectively solved.
Owner:浙江众合科技股份有限公司
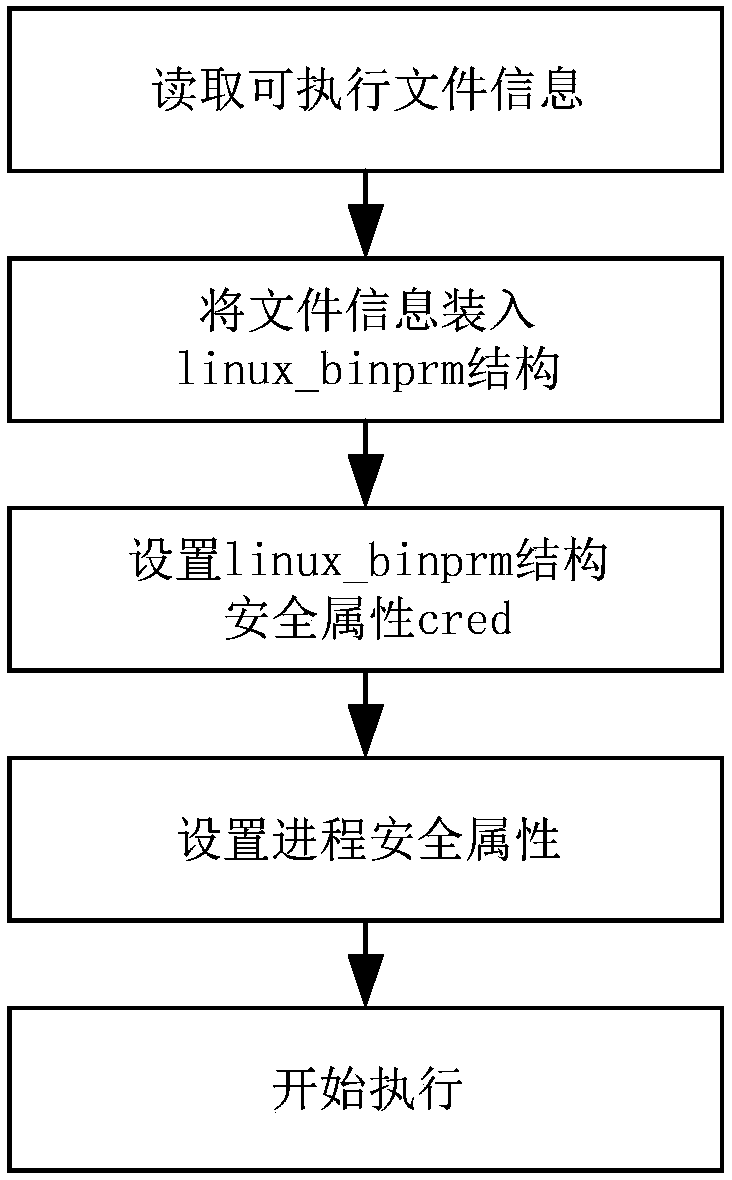
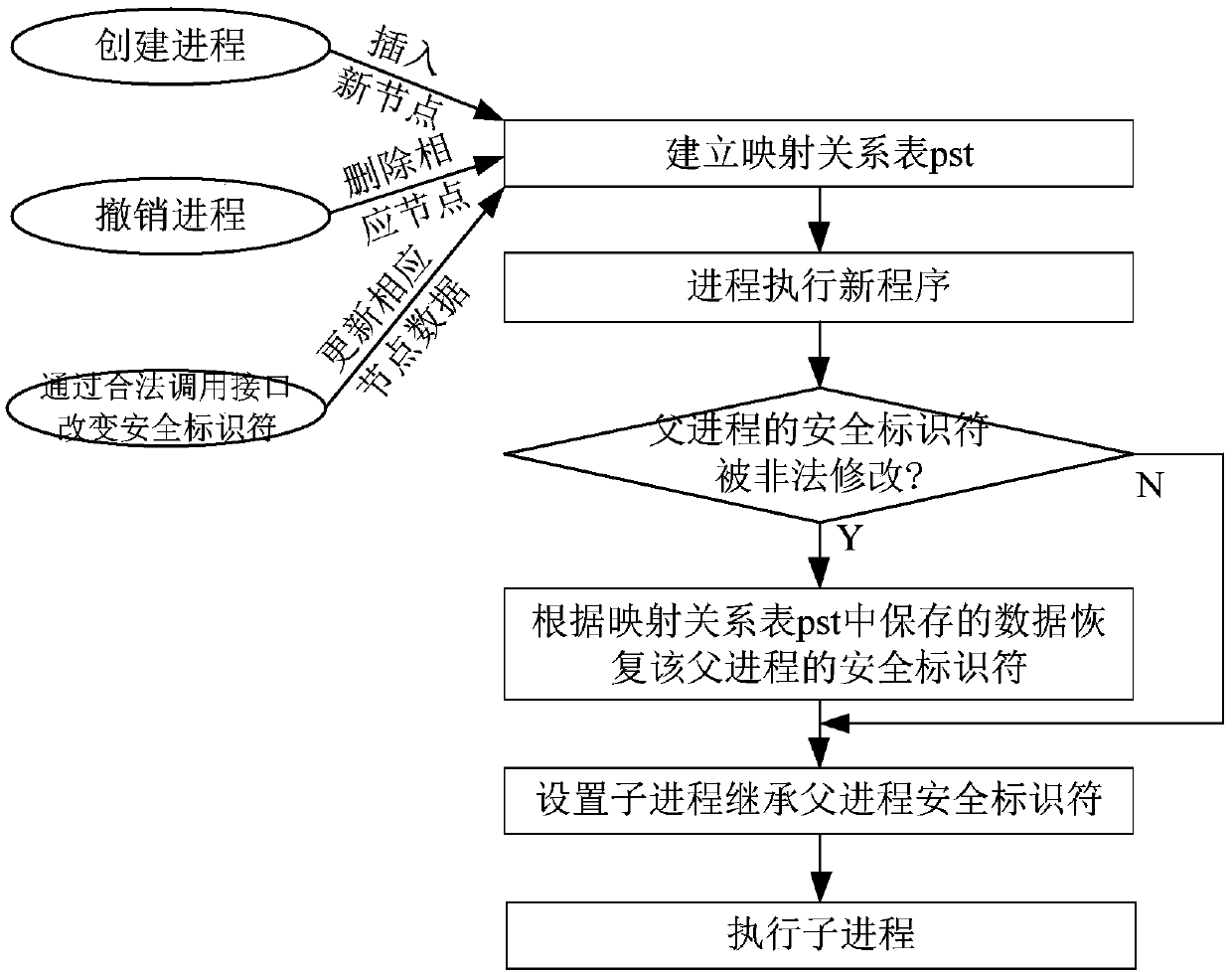
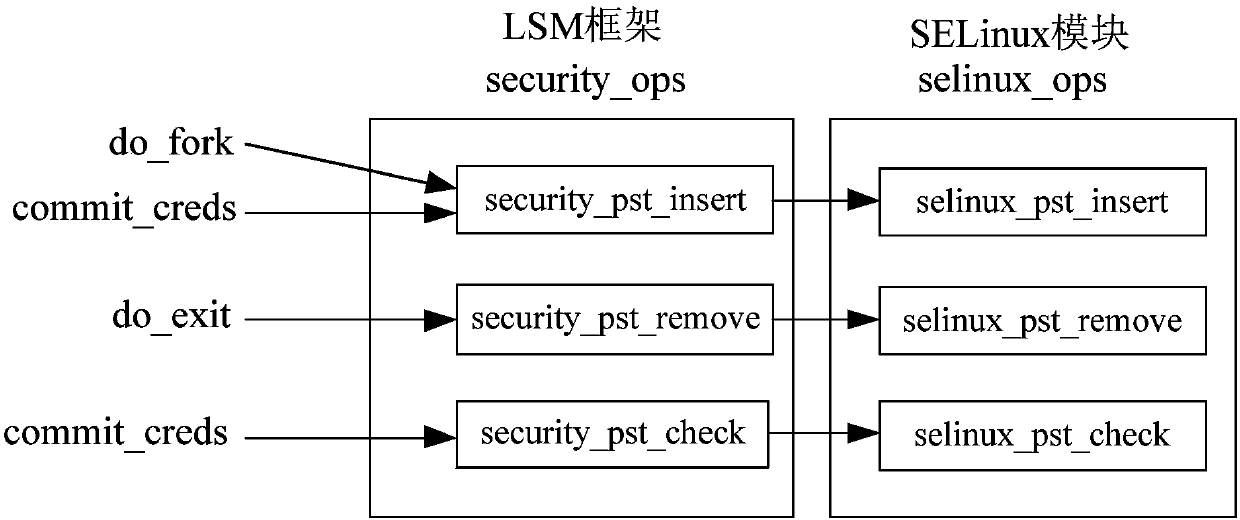
SELinux security identifier anti-tamper detection method and system
ActiveCN107908958ASolve security issuesDigital data protectionPlatform integrity maintainanceUser identifierRelational table
The invention discloses a SELinux security identifier anti-tamper detection method and system. The method comprises the implementation steps of: establishing a mapping relational table of processes and security identifiers thereof, when a process is created, taking the process and the security identifier thereof as new nodes to be inserted into the mapping relational table, when the process is removed, deleting the nodes, and updating the nodes when change is generated through a legal calling interface; and, when the process executes a new program, performing legality detection on a security identifier of a parent process, if the security identifier of the parent process is not same as the security identifier in the mapping relational table, recovering the security identifier of the parentprocess according to the mapping relational table, and starting to execute by setting the security identifier of the parent process as the default security identifier of a sub-process. By means of the SELinux security identifier anti-tamper detection method and system disclosed by the invention, illegal tampering on the security identifier of the process by an attacker using a kernel root attackmeans can be detected; furthermore, the security identifier of the process is recovered to the security identifier before illegal tampering; and the attacker can be prevented from breaking through security protection on the system by SELinux through the kernel root attack means.
Owner:NAT UNIV OF DEFENSE TECH
Glass container
InactiveCN103964042ATransportation safetyReduce volumeRigid containersConveyor partsEngineeringSquare Window
A glass container provided by the invention is characterized in that front, back, right, and left fixing support frames are installed on an a corner folding connecting part and a corner connecting part, so that front and back support bodies and left and right side support bodies which are in a square window frame shape and composed of a horizontal support part and vertical support parts and the lower support frame and the right side support body composed of an V-shaped reinforcing frame are provided with hinges on the above fixing support frames through the hinges in a folding manner. Upper gear support frames are provided between the above support frames. Left and right side gear support frames are arranged on the horizontal support frames; and lower gear support frames are attached to the lower support frames. A plurality of glasses are inserted among the gears of the above gear support frames so as to support load. Protruded caps having protrusion cover upper ends of corners of an upper part so as to form connection and fixation.
Owner:GONG GAN CHANNEL +1
Method, device and system for protecting safety of computer
The invention discloses a method, a device and a system for protecting the safety of a computer. The method for protecting the safety of the computer comprises that: a first server receives the message digest 5 (MD5) value of the original information from a client side, wherein the original information is the start point information which is obtained through scanning a start point of the computer by the client side; the first server searches the start point state which corresponds to the MD5 value from a first database to obtain a first matching result, wherein the corresponding start point states of different MD5 values can be stored in the first database; and the first server sends the first matching result to the client side, so that the client side process the start point according to the operation command corresponding to the first matching result. The method is utilized to solve the problem that the method for protecting the safety of the computer in the prior art cannot protect the safety of the computer when the computer is started by virus by utilizing null files, and furthermore, an effect of protecting the safety of the computer is well realized.
Owner:ZHUHAI BAOQU TECH CO LTD
Automatic irrigation system based on Internet-of-Things security
InactiveCN110338040ASolve security issuesNo need to worry about being hijackedMeasurement devicesWatering devicesControl signalTerminal equipment
The invention discloses an automatic irrigation system based on Internet-of-Things security. The system ensures the security of Internet-of-Things data through two-way encryption and verification andcomprises a server, a database, a client side and an execution side; the server is used for instruction transceiving, checking and feedback and data calculation and collection; the database is used for storing registration, verification and user information and storing data collected by the server; the client side is used for providing convenience for a user to input a request in the whole system,obtaining data and sending data to the server; the execution side is used for making corresponding action according to instructions sent from the server and only executes the instructions sent from the server. The automatic irrigation system solves the security protection problems in the aspects of terminal device connection, remote data transmission and control signal triggering so that a largequantity of devices can be deployed quickly without worrying about that signals are hijacked, and an effective security protection measure is provided for an Internet-of-Things system.
Owner:GSY GROUP
Transformer substation insulator hot-line work robot system and method
ActiveCN110883764ASolve positioningSolving the Alignment DilemmaProgramme-controlled manipulatorGripping headsRobotic systemsTransformer
The invention discloses a transformer substation insulator hot-line work robot system and method. The system comprises a robot body, a control module arranged in the robot body and an insulating lifting mechanism arranged on the robot body. The tail end of the insulating lifting mechanism is connected with a live-line work tool through a quick connecting part; the live-line work tool comprises a live-line cleaning device or an RTV spraying device. The invention has the beneficial effects that the system can be quickly switched to the RTV spraying device after an insulator sweeping operation iscompleted, so the continuous operation of sweeping-spraying of the insulators of a transformer substation can be achieved.
Owner:STATE GRID INTELLIGENCE TECH CO LTD
Ship capable of achieving charging during movement
InactiveCN106275346ASolve security issuesEasy to movePropulsion power plantsPropulsive elementsReduction driveReducer
The invention provides a ship capable of achieving charging during movement. The ship comprises a weighting block, a movable groove, a hydraulic lifting device, a first telescopic rod, a second telescopic rod, a first fixator, a second fixator, a speed reducer, a servo motor, an ejection rod, an electrical socket, a sealing cover and a fixing rod. The movable groove is machined in the right portion of the weighting block. The hydraulic lifting device is mounted at the lower end of the weighting block. The first telescopic rod is assembled on the movable groove. The second telescopic rod is arranged at the right end of the first telescopic rod. The first fixator is assembled on the right portion of the upper end of the second telescopic rod. The second fixator is assembled on the right portion of the upper end of the first telescopic rod. The lower end of the servo motor penetrates through the speed reducer and the weighting block and is connected with the left portion of the first telescopic rod. The left side of the sealing cover is provided with the electrical socket. The left end of the electrical socket is fixed to the fixing rod. The electrical socket and the sealing cover are mounted in the ejection rod. The ship is convenient to use and operate, charging of ships of different specifications is achieved, the front side and the rear side can be connected for charging, the using range is enlarged, the protection effect is improved, the stability is good, and the reliability is high.
Owner:安徽浙科智创系统服务有限公司
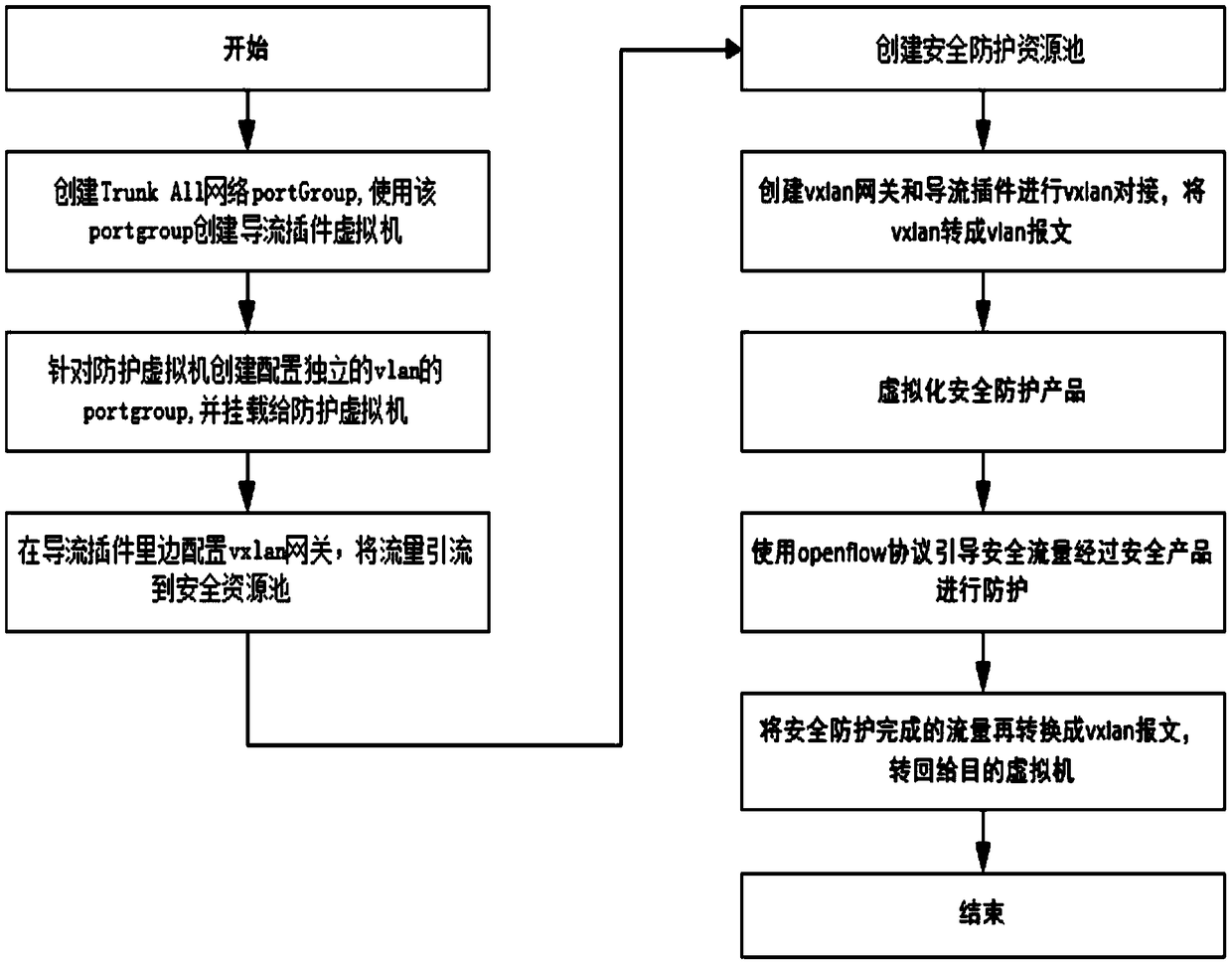
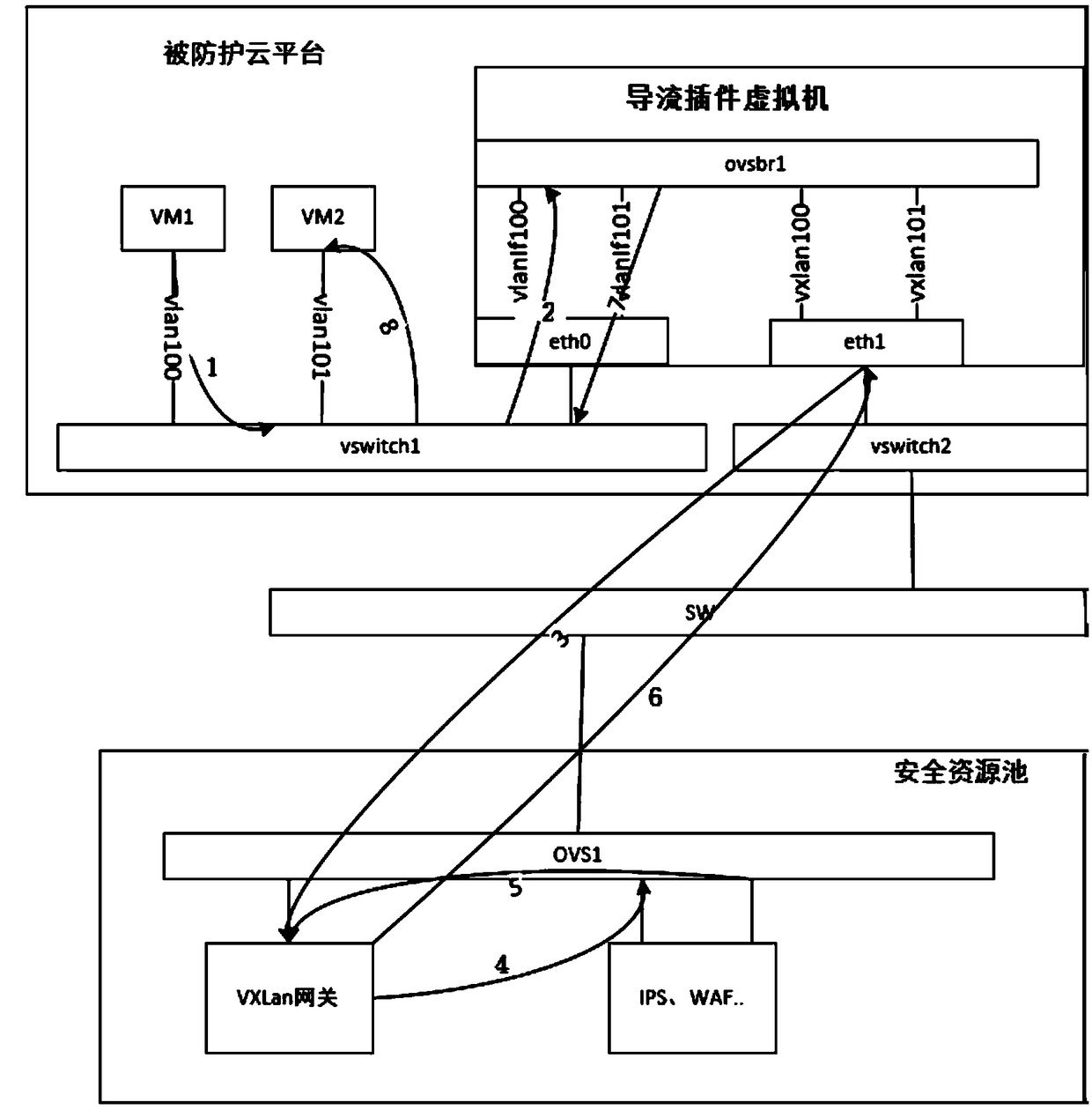
Virtualization platform east-west direction flow isolation protection method
InactiveCN109194640ASolve out of controlSolve security issuesNetworks interconnectionVirtualizationStreamflow
The present invention provides a virtualization platform east-west direction flow isolation protection method. In order to guarantee the flow safety between virtual machines in a cloud platform, the method employs SDN and VXLAN technologies to guide the flow of the cloud platform virtual machines requiring being protected to the outer portion of a server, the flow passes through safety protectionproducts such as FW, IPS and IDS to perform flow protection and then be returned to the other cloud platform virtual machine in the cloud platform so as to achieve isolation protection of the east-west direction flow. A stream guidance plug-in virtual machine and an independent vxlan tunnel are led to solve the problem that the east-west direction flow between the virtual machines in a traditionalcloud environment cannot be controlled and the problem of the safety protection, and therefore the virtualization platform east-west direction flow isolation protection method can be applied to a current mainstream cloud platform.
Owner:北京安数云信息技术有限公司
Method for monitoring local area wind field based multiple wind measurement devices
PendingCN113687447AStrong promotion and application prospectsSolve security issuesDesign optimisation/simulationElectromagnetic wave reradiationControl equationAtmospheric sciences
A method for constructing a wind field model based on CFD and monitoring a local area wind field of multiple wind measurement devices comprises the steps of 1) constructing a business guarantee area geographic information model: according to business guarantee area requirements, properly extending to determine business guarantee area boundary conditions, utilizing precise terrain information obtained by GIS, combining with business guarantee area landform characteristics, and constructing a business guarantee area geographic information model containing elevation, roughness and other information; 2) constructing a computational fluid dynamics (CFD) wind field simulation model: solving a discrete solution of a fluid dynamics control equation through a numerical method, and performing CFD numerical simulation according to a geographic model of a service guarantee area to obtain CFD wind field simulation results with different directions, different wind speeds and different gust characteristics, wherein the selection of the size of the grid of the service guarantee area needs to be determined in combination with the landform condition so as to achieve the minimum calculation amount and the optimal simulation result; 3) analyzing sensitivity of observation points; and 4) establishing a regional wind field monitoring system.
Owner:NAT UNIV OF DEFENSE TECH
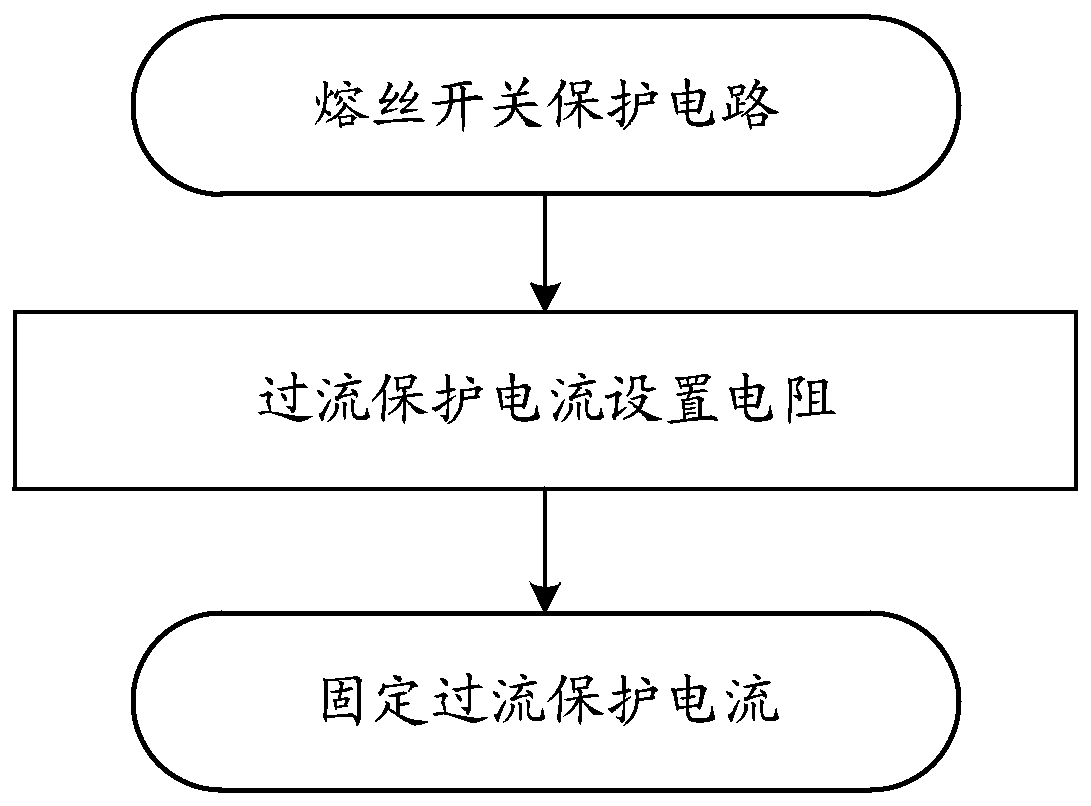
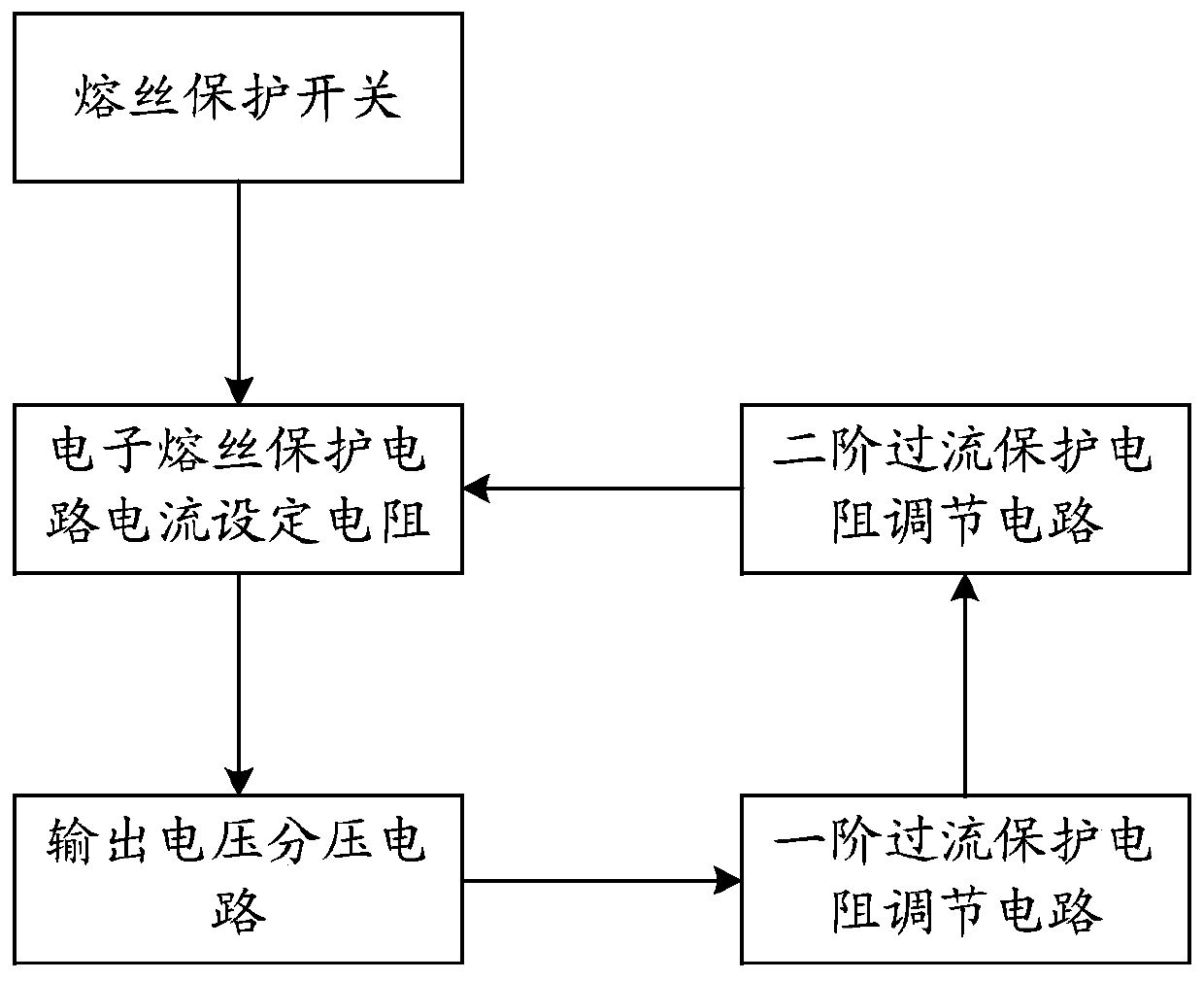
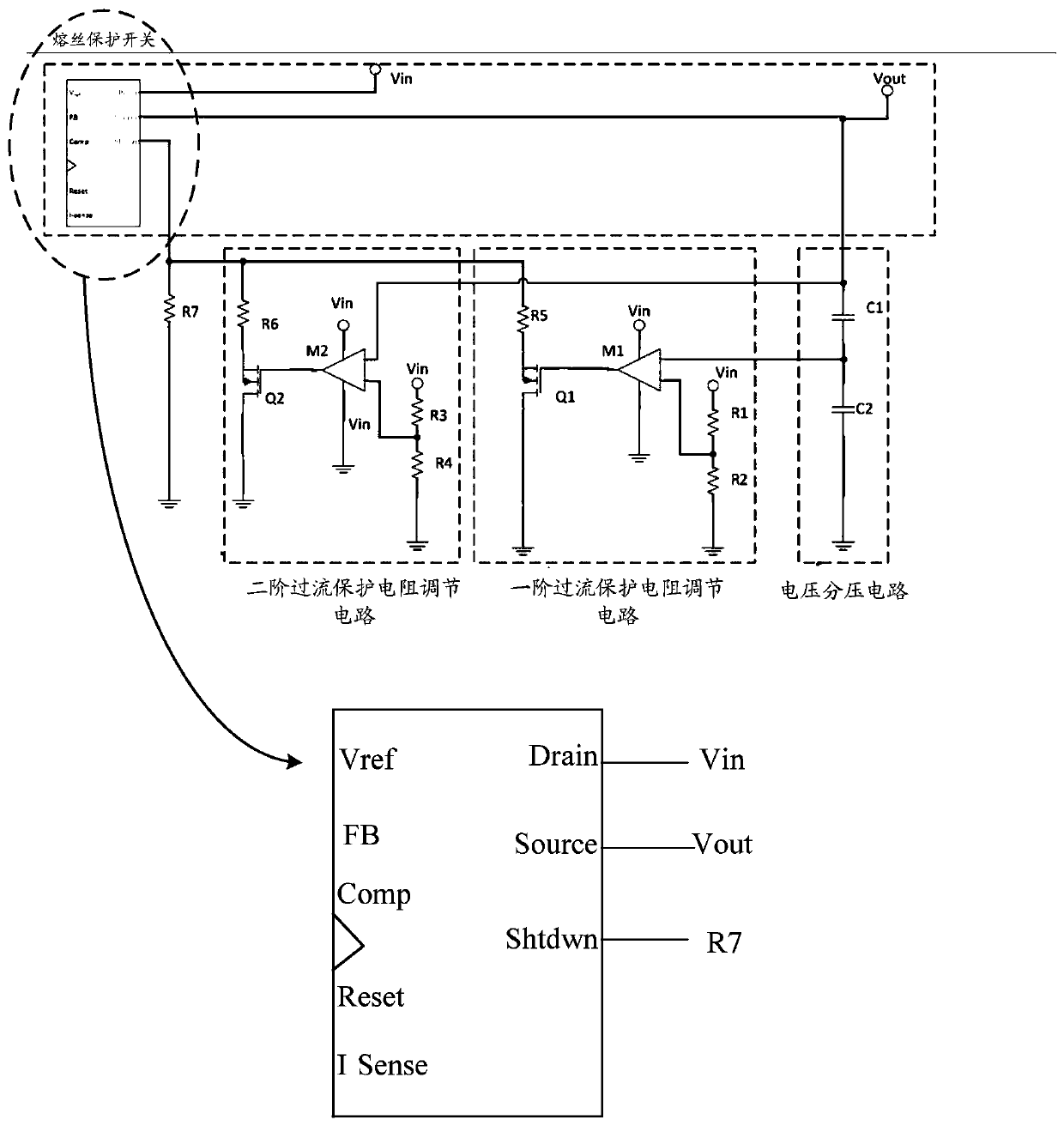
Circuit overcurrent protection device and method
ActiveCN109728564ASolve security issuesArrangements responsive to excess currentElectrical resistance and conductanceOvercurrent
The invention discloses a circuit overcurrent protection device and method, relates to circuit fuse protection technology, and solves the problem that a fixed fusing current value causes a potential safety hazard. The device comprises an electronic fuse protection circuit current setting resistor, a voltage dividing circuit, a first-order overcurrent protection resistor adjusting circuit and a second-order overcurrent protection resistor adjusting circuit. The technical solution provided by the invention is suitable for circuit protection of electronic devices, and realizes a fuse protection scheme adapted to a voltage variation scenario.
Owner:ZHENGZHOU YUNHAI INFORMATION TECH CO LTD
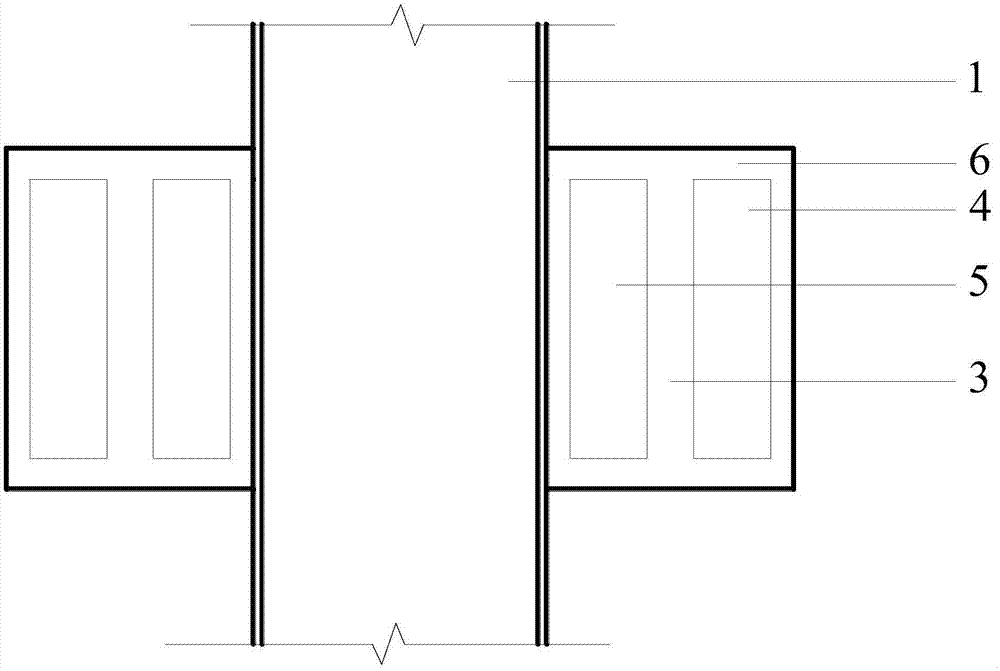
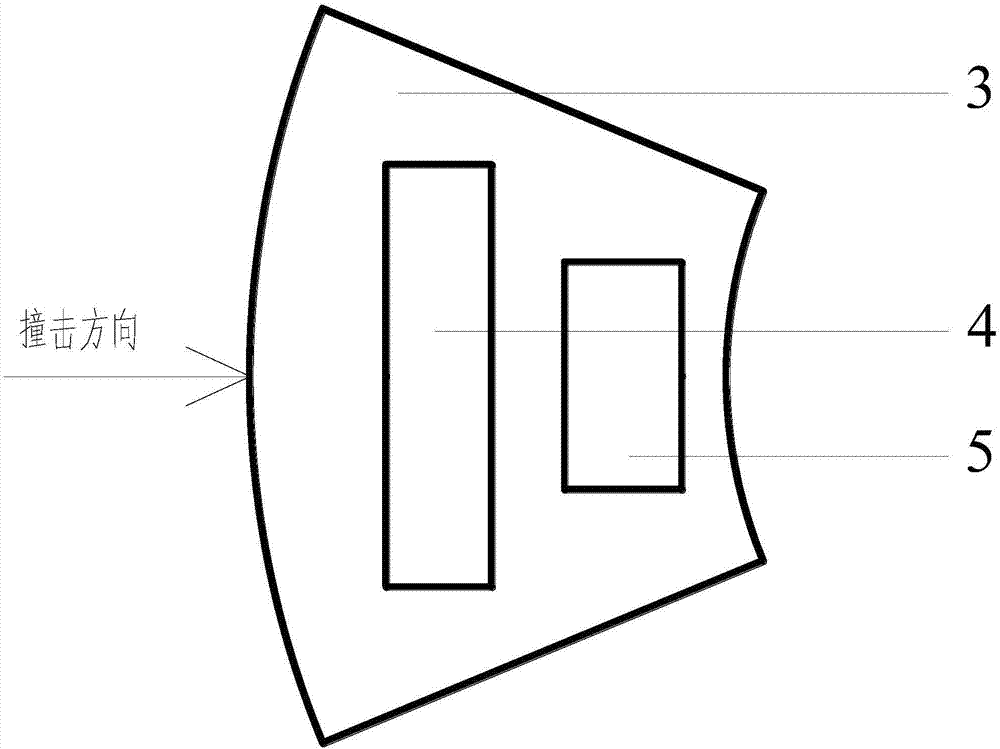
FRP (Fiber Reinforce Plastic) and steel board combined type offshore collision preventing device
ActiveCN107119634ASolve security issuesGood for long term protectionClimate change adaptationShipping equipmentFiberEngineering
The invention belongs to the field of structure safety protection of marine engineering, in particular relates to an FRP (Fiber Reinforce Plastic) and steel board combined type offshore collision preventing device, and aims at solving the problem of safety protection of an offshore structure. The device is formed by assembling a plurality of basic collision preventing units around the protected structure, wherein each basic collision preventing unit is in a shape of a sector cylinder and comprises an FRP housing, a corrugated steel plate corrosion preventing structure, an S-shaped steel plate collision preventing structure and a propping cover; the corrugated steel plate collision preventing structure and the S-shaped steel plate collision preventing structure are embedded into the FRP housing; the FRP housing is manufactured through FRP material, and the inside of the FRP housing is hollowed out and divided into an outer side and an inner side which do not communicate; the corrugated steel plate collision preventing structure can be embedded into the outer side, and the S-shaped steel plate collision preventing structure can be embedded into the inner side. With the adoption of the device, the problem of safety protection of the offshore structure can be solved; the corrosion resistance is high while the energy absorbing effect is good, so that the later maintenance cost can be decreased, and the offshore structure can be protected for a long term, and as a result, the offshore work and the assembling and replacing can be conveniently carried out.
Owner:HARBIN ENG UNIV
Safety protection method for treatment of high-narrow large-scale karst cave cavity
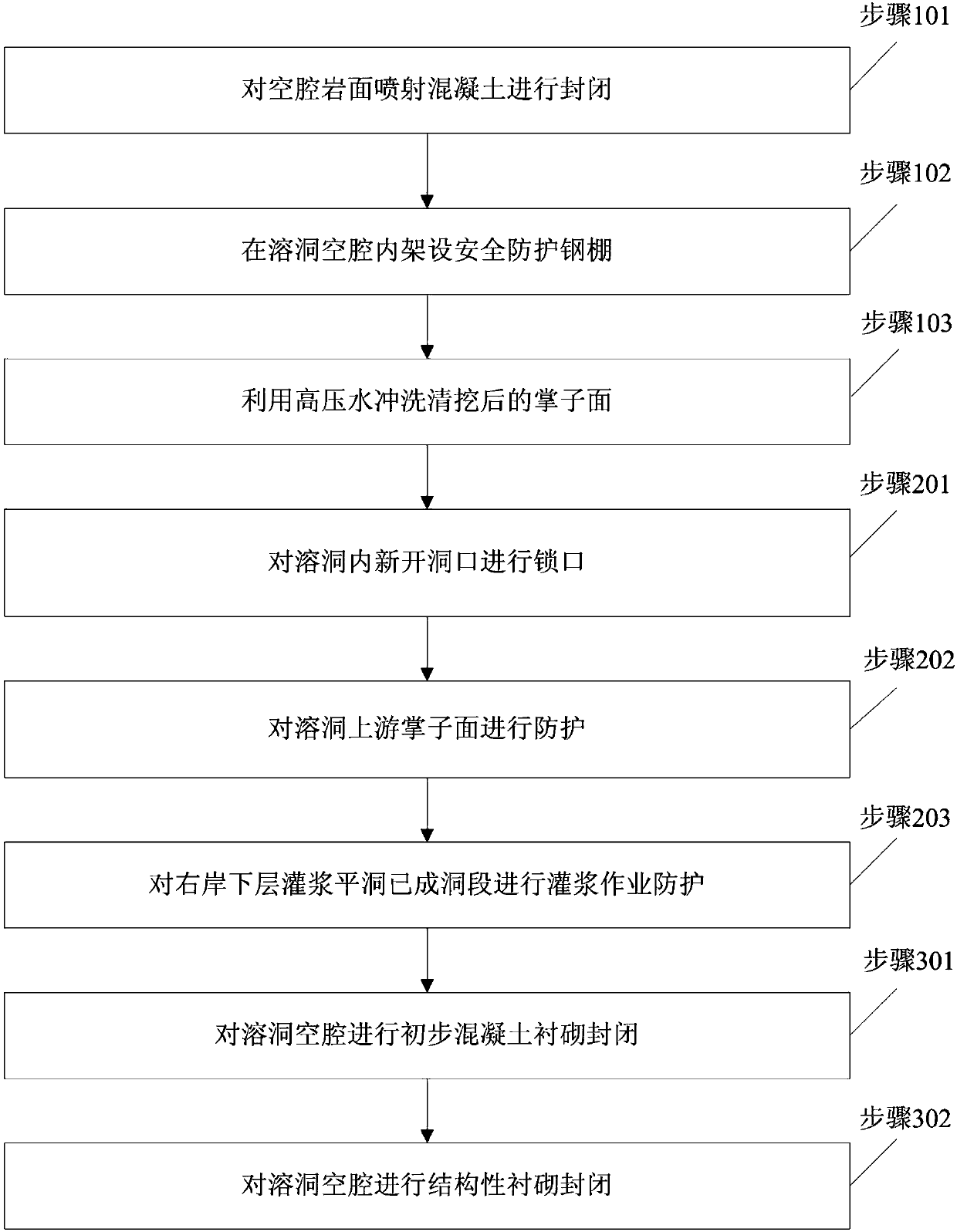
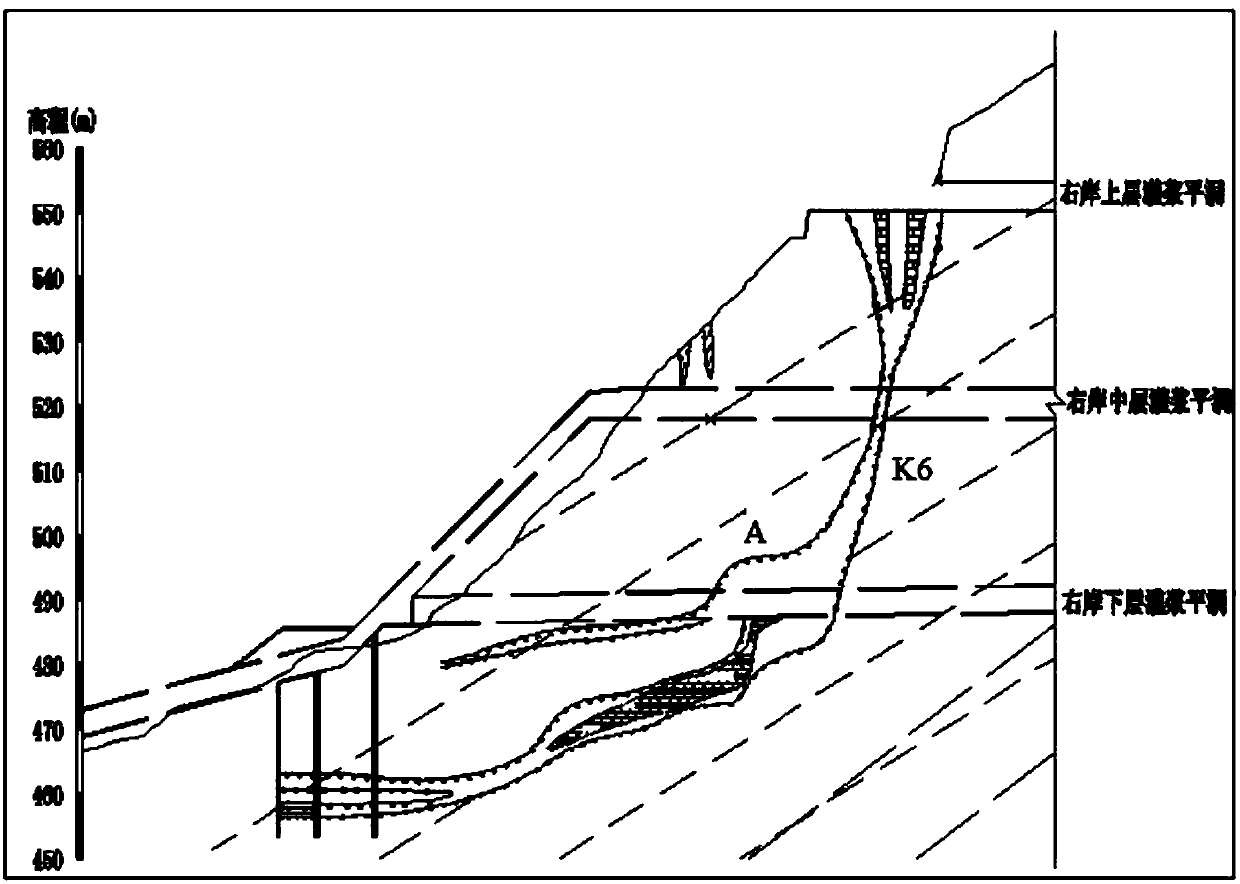
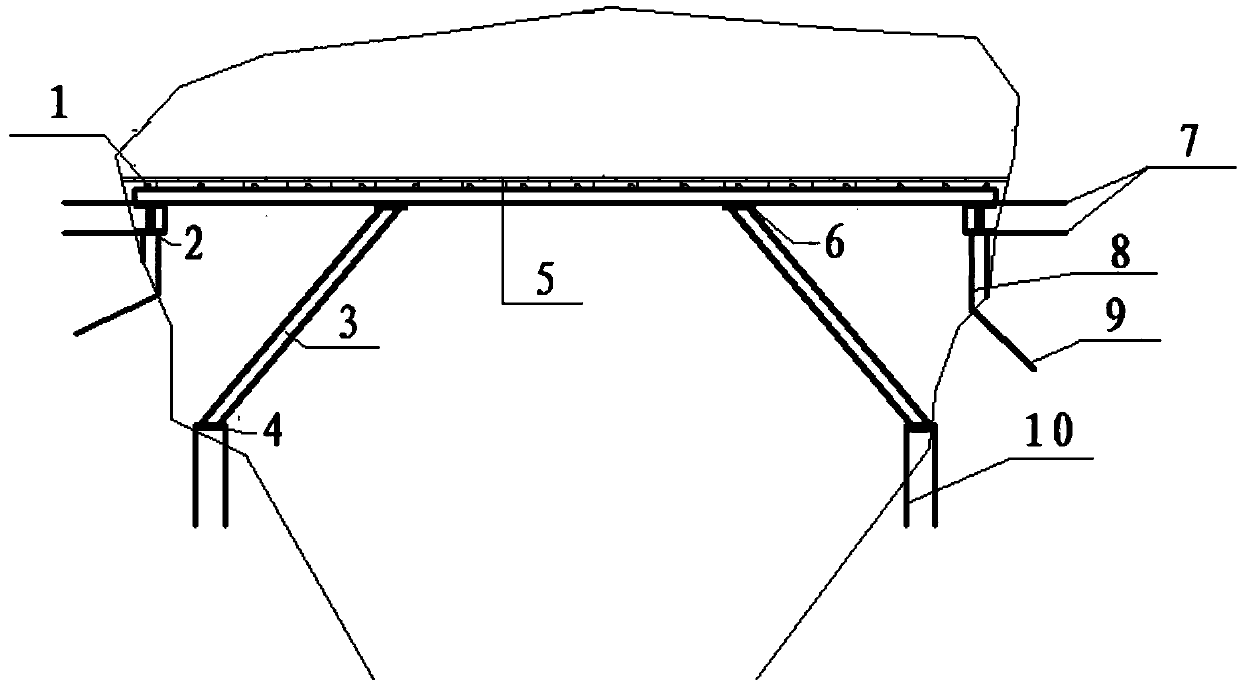
ActiveCN107869351AEnsure safe operationAvoid safety accidentsUnderground chambersTunnel liningShotcreteKarst
The invention discloses a safety protection method for treatment of a high-narrow large-scale karst cave cavity. The method comprises the steps that at the stage of cleaning and digging the karst cavecavity, concrete is sprayed on the rock surface of the cavity to seal the cavity, and a safety protection steel shed is erected in the karst cave cavity; high-pressure water is used for flushing a cleaned and dug tunnel face; at the stage of running through a newly formed cave opening at a grouting flat cave of the lower layer of a right bank, the newly formed cave opening in the karst cave is subjected to opening locking; an upstreaming tunnel face of the karst cave is protected; a cave-forming segment of the grouting flat cave of the lower layer of the right bank is subjected to grouting operation protection; at the lining stage of the grouting flat cave of the lower layer of the right bank and the karst cave cavity, the karst cave cavity is subjected to primary concrete lining sealing;the cave cavity is subjected to structural lining sealing. According to the safety protection method for treatment of the high-narrow large-scale karst cave cavity, effective safety protection measures are adopted at different stages, the safety accident in the treatment period of the karst cave cavity can be effectively prevented, and the operation safety of construction personnel is guaranteed.
Owner:SINOHYDRO BUREAU 11 CO LTD
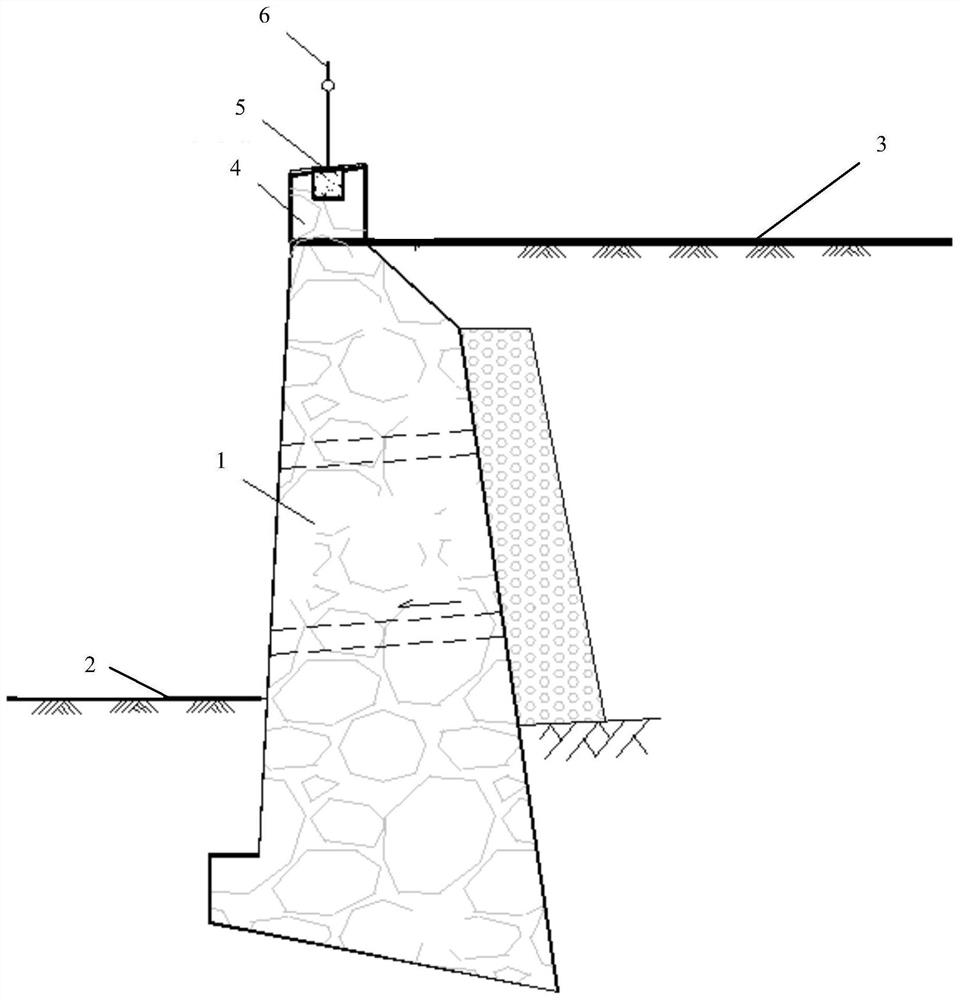
Road shoulder type retaining wall top safety protection structure and construction method
PendingCN112663670ASolve security issuesGuaranteed normal passageArtificial islandsUnderwater structuresArchitectural engineeringStructural engineering
The invention discloses a road shoulder type retaining wall top safety protection structure and a construction method, and relates to the field of road safety protection. The road shoulder type retaining wall top safety protection structure comprises a road shoulder retaining wall body, wherein the lower portion of the road shoulder retaining wall body is a ground horizontal line, and the upper portion of the road shoulder retaining wall body is a passing area for pedestrians to pass through; and a plurality of protective piers are uniformly distributed along the top of the road shoulder retaining wall body, embedded parts are arranged on the two sides of each protective pier, the bottoms of steel railings are inserted into the embedded parts and are welded and fixed, and the steel railings and the protective piers form a guardrail type protective structure. The road shoulder type retaining wall top safety protection structure has the beneficial effects that the safety protection problem of areas where vehicles pass through and maintainers pass through on a road square at the top of the road shoulder type retaining wall is solved, the safe passing of the vehicles can be guaranteed, a certain protection effect can be achieved on the maintainers, and meanwhile, certain attractiveness is achieved.
Owner:日昌升建筑新材料设计研究院有限公司
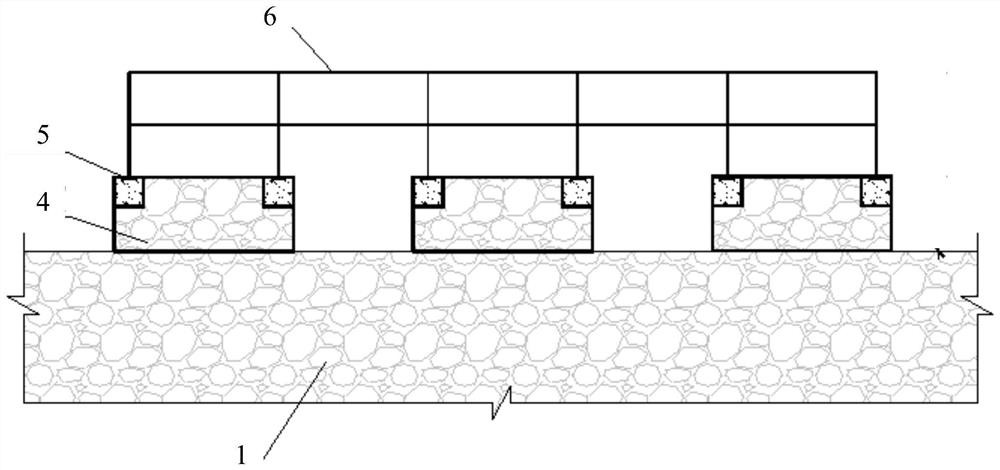
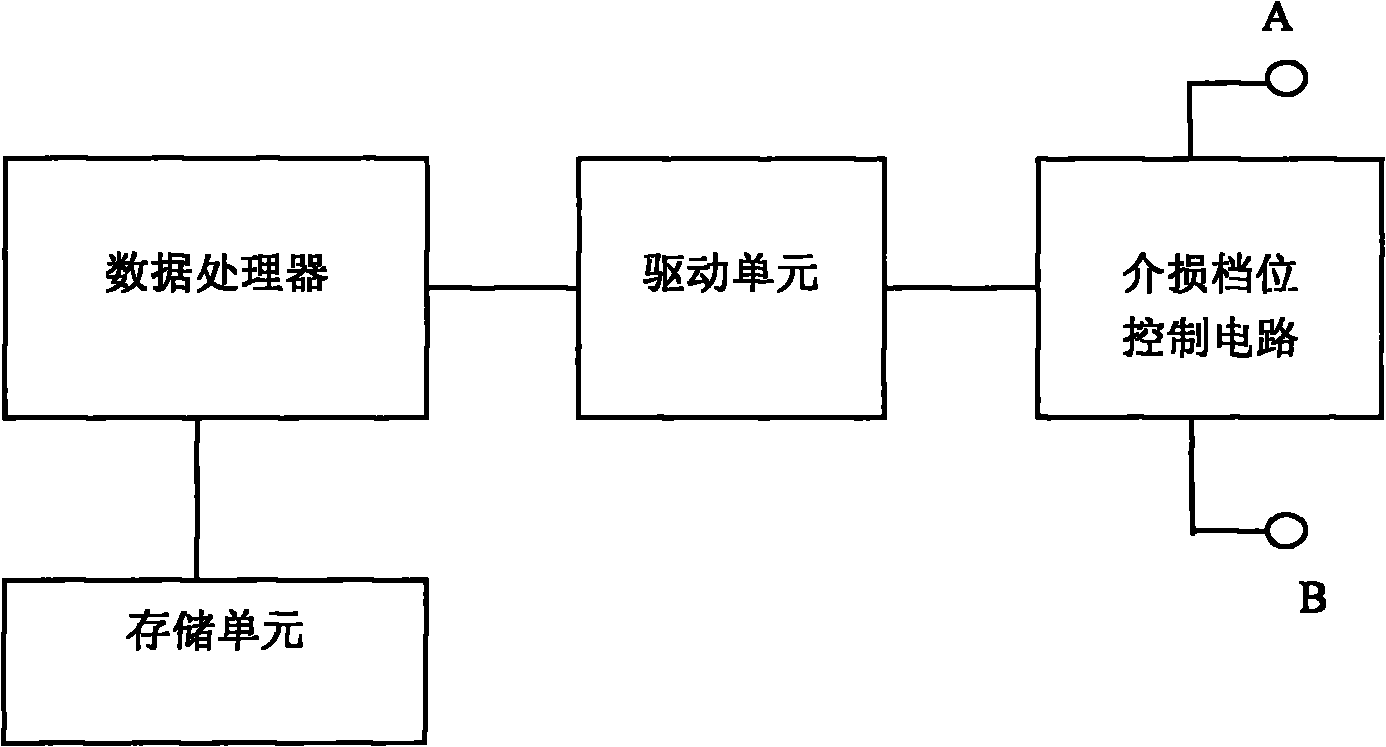
Calibrating device for fully automated high-voltage dielectric loss tester
ActiveCN102313876ASolve security issuesAccurate detectionResistance/reactance/impedenceDielectric lossStorage cell
The invention relates to a calibrating device for a fully automated high-voltage dielectric loss tester, which comprises a data processor, a storage unit, a drive unit and a dielectric loss gear control circuit. The storage unit is connected with the storage port of the data processor, the control signal output end of the data processor is connected with the signal input end of the drive unit, the signal output end of the drive unit is connected with the control end of the dielectric loss gear control circuit, the high-voltage signal input end of the dielectric loss gear control circuit is connected with the high-voltage signal output end of the high-voltage dielectric loss tester to be tested, and the measurement result output end of the dielectric loss gear control circuit is connected with the low-voltage sampling input end of the high-voltage dielectric loss tester to be tested.
Owner:STATE GRID HENAN ELECTRIC POWER ELECTRIC POWER SCI RES INST +1
A kind of anti-smog mask with konjac glucomannan film
ActiveCN105962481BImprove material performanceSolve security issuesGarment special featuresProtective garmentAdditive ingredientElectric field
The invention relates to a konjac glucomannan membrane haze-prevention mask. A mask body of the konjac glucomannan membrane haze-prevention mask is composed of four layers which specifically include the first layer, namely, the outmost layer, made of non-woven fabric, the second layer made of a konjac glucomannan porous membrane, the third layer made of a konjac glucomannan nanometer porous membrane, and the fourth layer, namely, the layer in contact with the face, made of non-woven fabric. With natural polymer polysaccharide, namely, konjac glucomannan, serving as the main ingredient, the konjac glucomannan membrane haze-prevention mask has various characteristics of hydrophilia, the thickening characteristic, stability and the like. In recent years, natural polymer compounds are widely applied to the material field, and many problem emerging on material safety are solved. The technology of preparing high-quality nanometer porous membranes with plant polysaccharide serving as the raw materials become a hot point in recent years; according to the method, the special gel property of konjac glucomannan is utilized, and the konjac glucomannan nanometer porous membrane is obtained through application of the electric field technology, and has great application potential in the material field. The konjac glucomannan membrane haze-prevention mask has higher indexes such adsorption performance, safety, raw material price and potential markets than those of other masks on the market, and can be selected by mass consumers as high-quality haze-prevention masks.
Owner:上海盈兹无纺布有限公司
Wireless monitoring type high-pressure testing protection wall device
InactiveCN104634651ARealize full trackingSolve security issuesStrength propertiesElectricityAccess network
A wireless monitoring type high-pressure testing protection wall device comprises a pressure testing wall, wherein the pressure testing wall comprises a base and a pressure testing protection wall mounted on the base; an electric interface box is mounted on the base; a plurality of cameras are mounted at the upper part of the pressure testing protection wall; the cameras are connected with the electric interface box through a composite cable and are connected with a wireless monitoring control system in the electric interface box respectively; and the wireless monitoring control system is connected with a remote monitor through a local access network and a remote access network respectively, and is used for converting all electric signals into wireless signals through the local access network and the remote access network to realize remote control of the cameras and remote transmission of monitoring data. Through the wireless monitoring type high-pressure testing protection wall device, a pressure curve of pressure equipment for pressure testing can be recorded and traced, and remote video data of the pressure in a pressure testing process can be collected so as to greatly improve the reliability and safety of a field test environment.
Owner:CHINA NAT OFFSHORE OIL CORP +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com