SELinux security identifier anti-tamper detection method and system
A security identifier and tamper detection technology, applied in the field of Linux system security, can solve problems such as access control mechanism bypass, SELinux security identifier illegal tampering, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
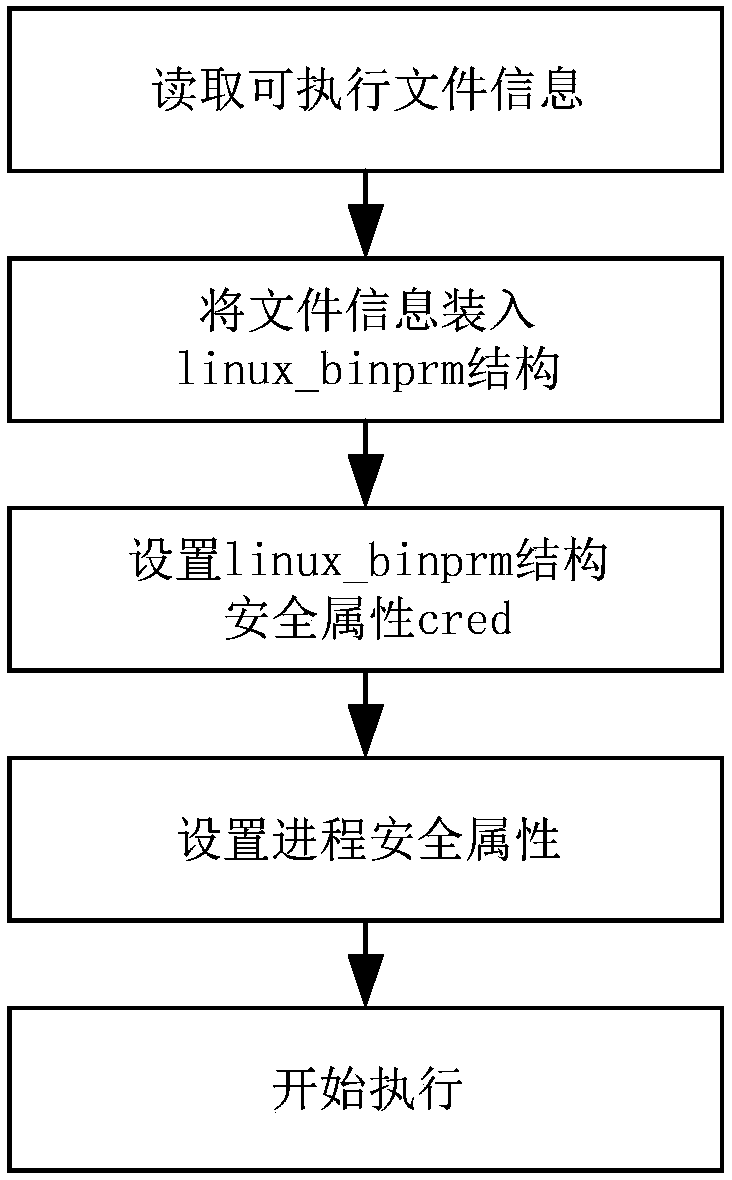
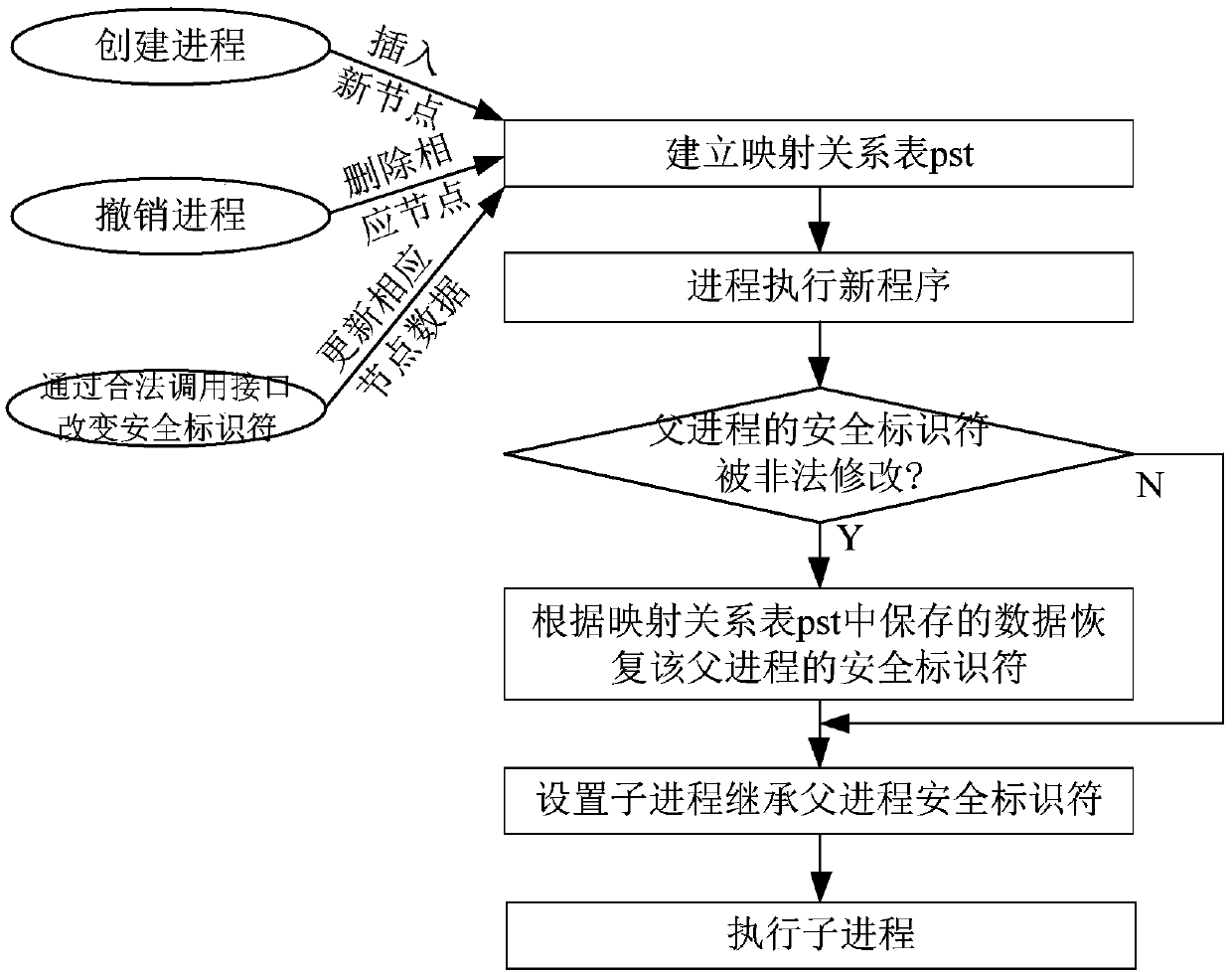
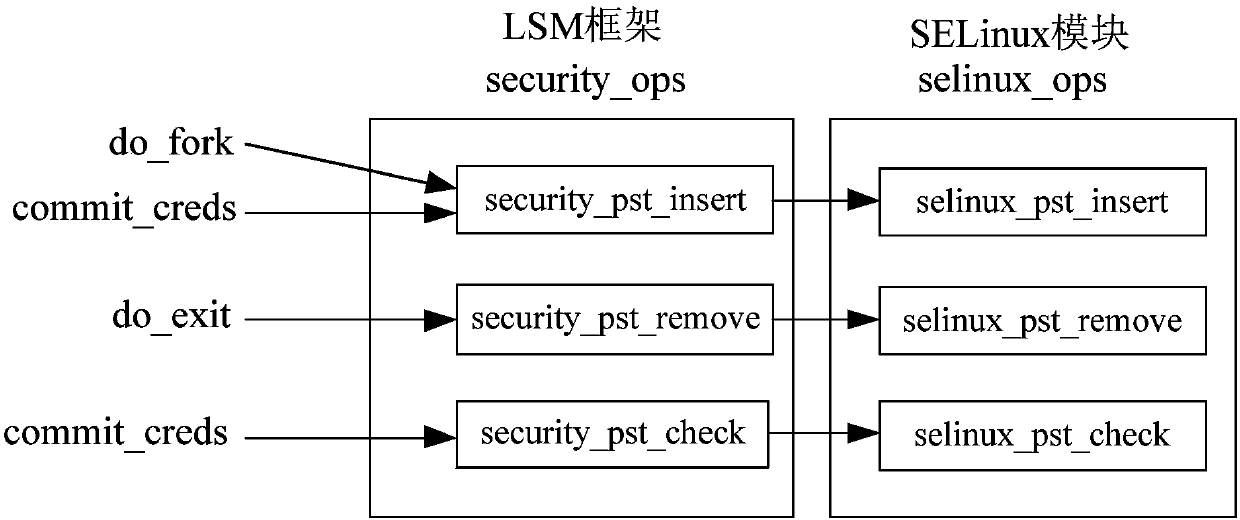
[0026] Such as figure 2 As shown, the implementation steps of the SELinux security identifier anti-tampering detection method of this embodiment include:
[0027] 1) Establish a mapping relationship table pst of a process ID and its security identifier SID, and when the system creates a process, use the process ID as an index, and insert the process ID and its security identifier SID as a new node into the mapping relationship table pst ; When the process is withdrawn, delete the node indexed by the process ID from the mapping relationship table pst; when the system changes the security identifier SID of the process through the legal call interface, then update the process ID and its security identifier SID in the mapping relationship table pst , so that the mapping relationship between the process ID and its security identifier SID in the mapping relationship table pst is always kept up-to-date;
[0028] 2) When a process executes a new program, first detect whether the sec...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com