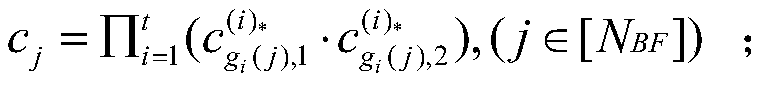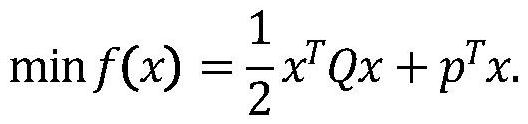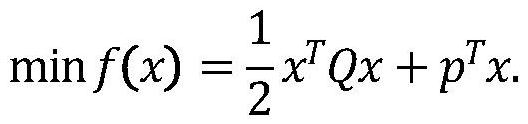Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
48results about How to "Prevent Malicious Behavior" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
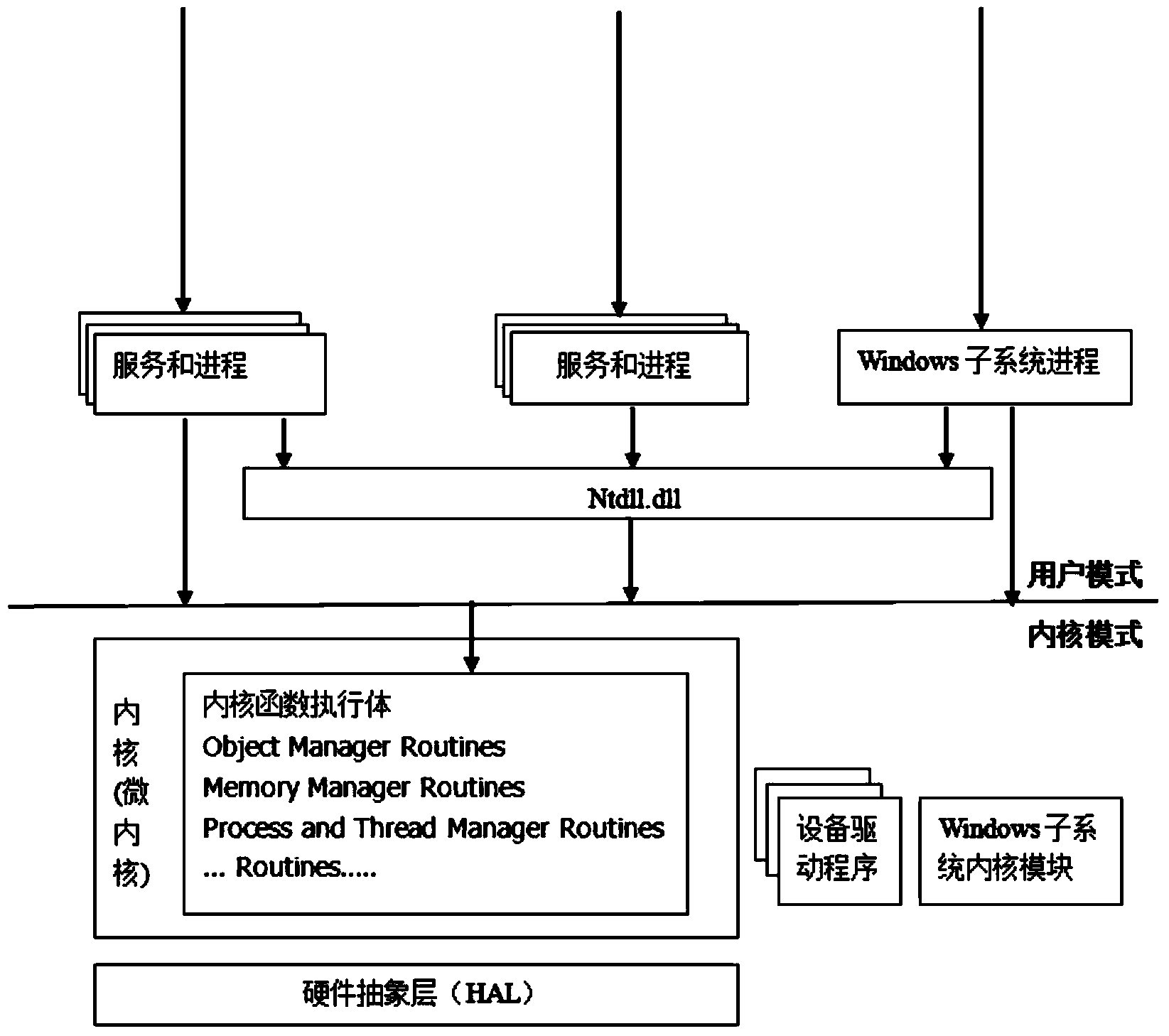
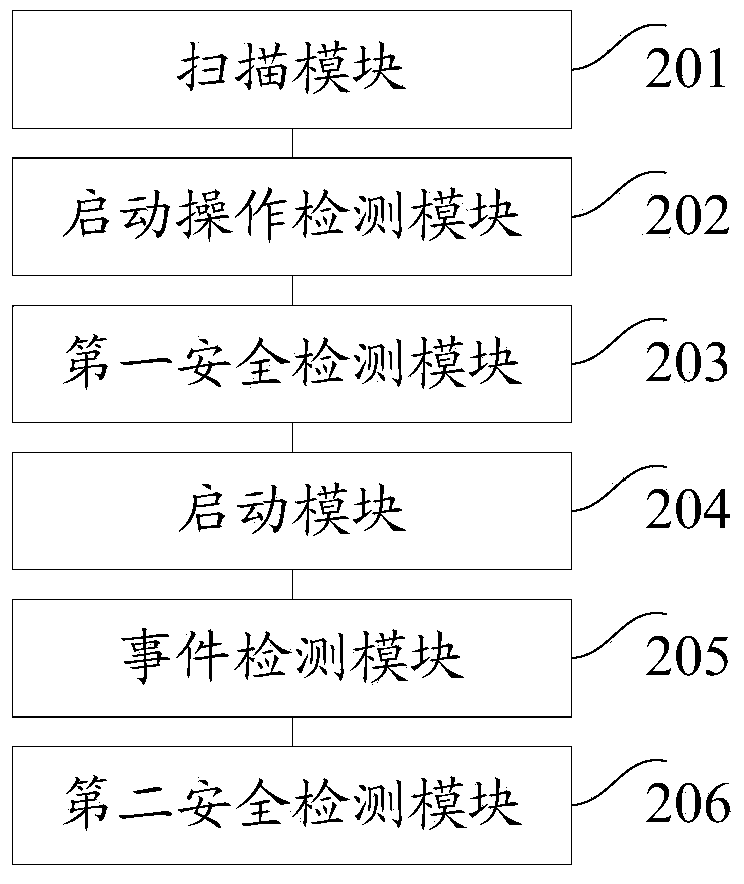
Application running device and terminal device
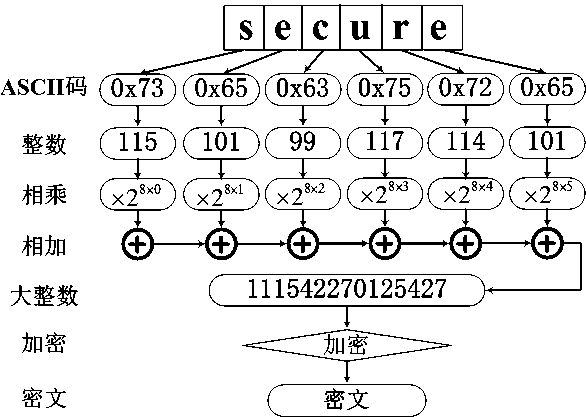
ActiveCN104267994ASecure bootGuaranteed uptimeProgram loading/initiatingOperational systemSoftware engineering
An embodiment of the invention provides an application running device and a terminal device. The application running device comprises a scanning module, a starting operation detection module, a first safety detection module, a starting module, an event detection module and a second safety detection module; the scanning module is used for scanning a specified type of application in the current operation system; the starting operation detection module is used for detecting the starting operation of the specified type of application; the first safety detection module is used for performing the first safety detection on the running environment of the application before the application is started; the starting module is used for starting the application after a result of the first safety detection indicates that the running environment is safe; the event detection module is used for detecting a preset event in the running process of the application; the second safety detection module is used for triggering the second safety detection on the preset event in the application. According to the application running device and the terminal device, the safety of the running environment when the application is started is effectively ensured and the safety of the application in the running process is effectively ensured.
Owner:BEIJING QIHOO TECH CO LTD
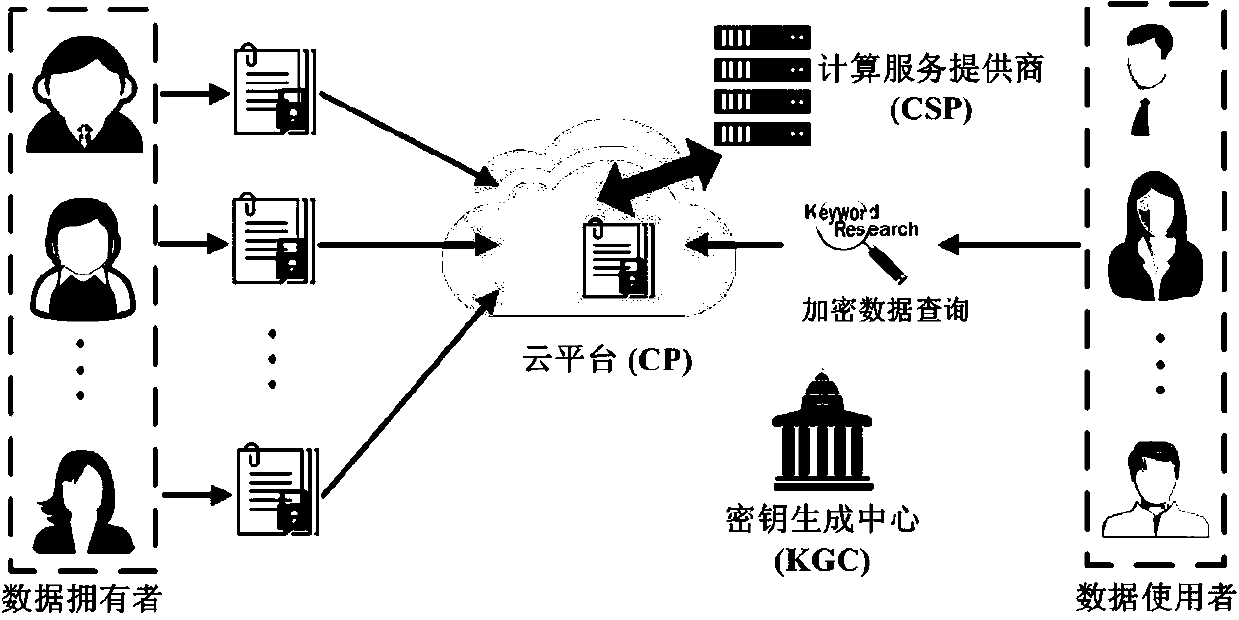
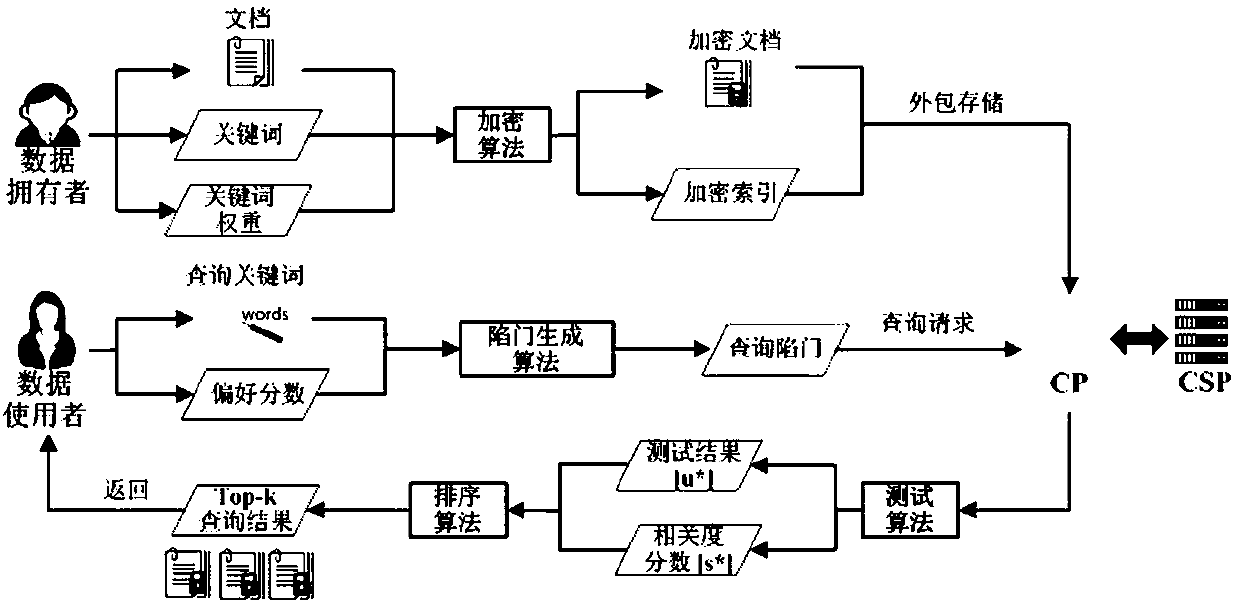
Retrieval system of encrypted data in secure cloud storage
PendingCN107734054APrevent Malicious BehaviorOffline KG attack preventionKey distribution for secure communicationDatabase queryingCloud storageDocumentation
The invention relates to a retrieval system of encrypted data in secure cloud storage. The retrieval system comprises a key generation center used for managing and distributing a public key / private key generated in the system; a cloud platform used for providing a data storage service to a data owner and responding to a search request of a user, that is, a data owner encrypts the data by utilizingthe public key and sends the encrypted data to the cloud platform for storage; and the user generates a query trap door and sends the query door to the cloud platform so as to search the encrypted data; and a calculation service provider for providing an online calculation service and interacting with the cloud platform to carry out calculation. The retrieval system of encrypted data in secure cloud storage supports multiple search and query modes; the system allows the user to search the encrypted documents from multiple data owners by utilizing one query trap door and supports flexible userauthorization and revocation mechanisms; and the system prevents offline keyword guessing attacks.
Owner:FUZHOU UNIV
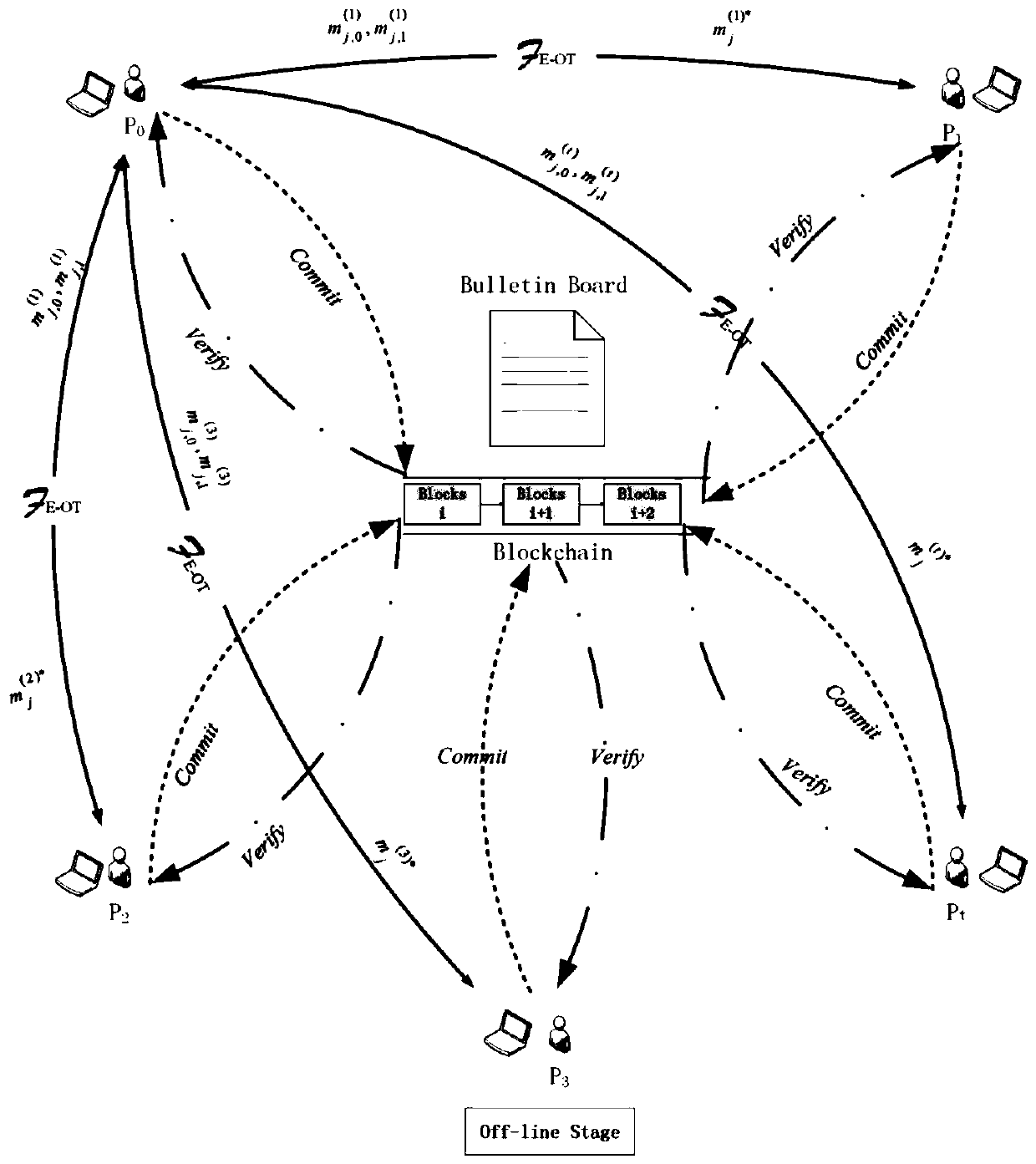
Multi-party privacy set intersection method for resisting malicious enemies
ActiveCN110719159AProtection of rights and interestsConvenient verificationKey distribution for secure communicationEncryption apparatus with shift registers/memoriesInternet privacyEngineering
The invention relates to a multi-party privacy set intersection method for resisting malicious enemies. The method comprises an offline stage and an online stage. In the offline stage, appointment commitment, careless transmission and the like are carried out, and operation is carried out in the online stage; a threshold homomorphic encryption scheme, a non-interactive zero knowledge proof, an improved Bloom filter and the like are mainly used for constructing a protocol. Even if malicious enemies can obtain the Bloom filters and the operation results of all honest parties, the malicious enemies and the operation results cannot leak extra information of all honest participants except the intersection under the condition of aiming at multiple parties. The bulletin board function is achieved, the commitment values of all participants are disclosed together while all the participants send corresponding information to the bulletin board so that the published information can be convenientlyverified in the later period, and malicious behaviors of part of the participants are prevented.
Owner:HENAN NORMAL UNIV
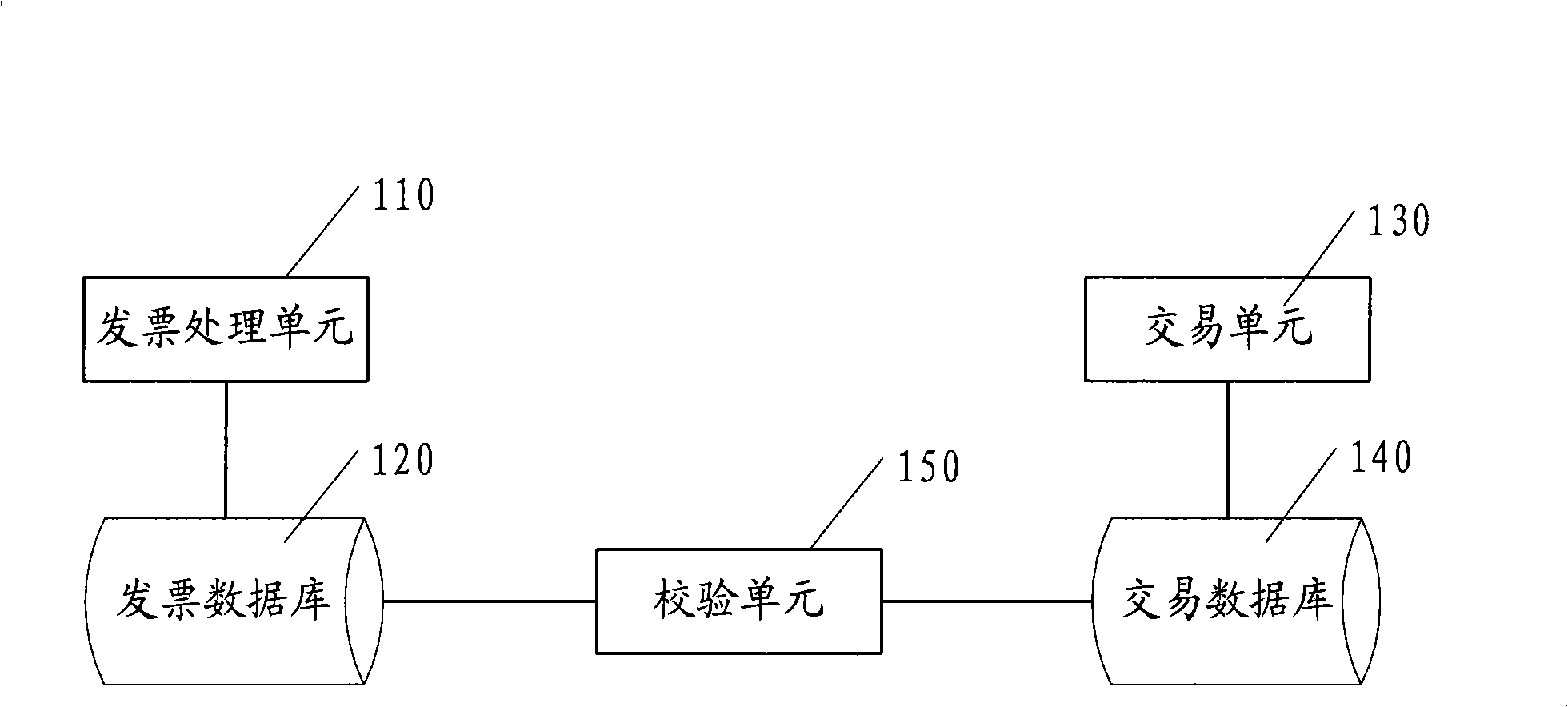
Receipt processing system and method based on internet trade
The invention discloses an invoice processing system based on Internet transaction, and a method; the system comprises a transaction information acquiring unit used for acquiring the transaction information, an invoice database used for storing invoice records, and an invoice processing unit used for generating invoice records according to the transaction information acquired by the transaction information acquiring unit; the invoice records are stored in the invoice database; as the check does not need to be carried out to the content of the generated invoice records additionally, resources of the system are saved greatly; besides, as the invoice records are generated directly by the invoice processing unit, the generation of garbage data caused by the input error of users in the prior art is avoided.
Owner:ALIBABA GRP HLDG LTD
Application running method
ActiveCN104268476ASecure bootGuaranteed uptimePlatform integrity maintainanceOperational systemSoftware engineering
An embodiment of the invention provides an application running method. The application running method comprises scanning a specified type of application in the current operation system; detecting the starting operation of the specified type of application; performing the first safety detection on the running environment of the application before the application is started; starting the application after a result of the first safety detection indicates that the running environment is safe; detecting a preset event in the running process of the application and triggering the second safety detection on the preset event in the application. According to the application running method, the safety of the running environment when the application is started is effectively ensured, the safety of the application in the running process is effectively ensured, the comprehensive safety protection is provided for the application, and the safe starting and running of the application can be achieved.
Owner:360 TECH GRP CO LTD
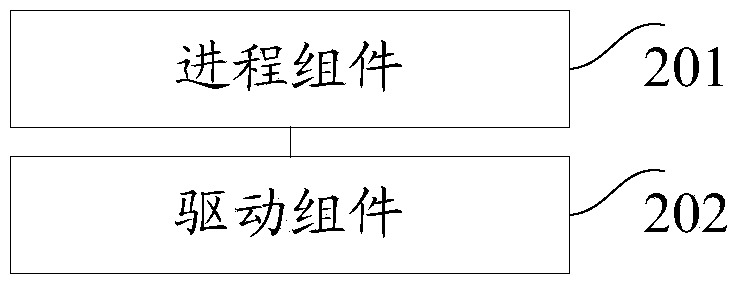
Application running system
ActiveCN104268475ASecure bootGuaranteed uptimePlatform integrity maintainanceOperational systemSoftware engineering
An embodiment of the invention provides an application running system. The application running system comprises a driving assembly and a process assembly; the process assembly is used for scanning a specified type of application in the current operation system; the driving assembly and or the process assembly are or is used for detecting the starting operation of the specified type of application; the driving assembly and the process assembly are used for performing the first safety detection on the running environment of the application before the application is started; the driving assembly is used for starting the application after a result of the first safety detection indicates that the running environment is safe; the driving assembly is used for detecting a preset event in the running process of the application; the driving assembly and the process assembly are used for triggering the second safety detection on the preset event in the application. According to the application running system, the comprehensive safety protection is provided for the application and the safe starting and running of the application can be achieved.
Owner:BEIJING QIHOO TECH CO LTD
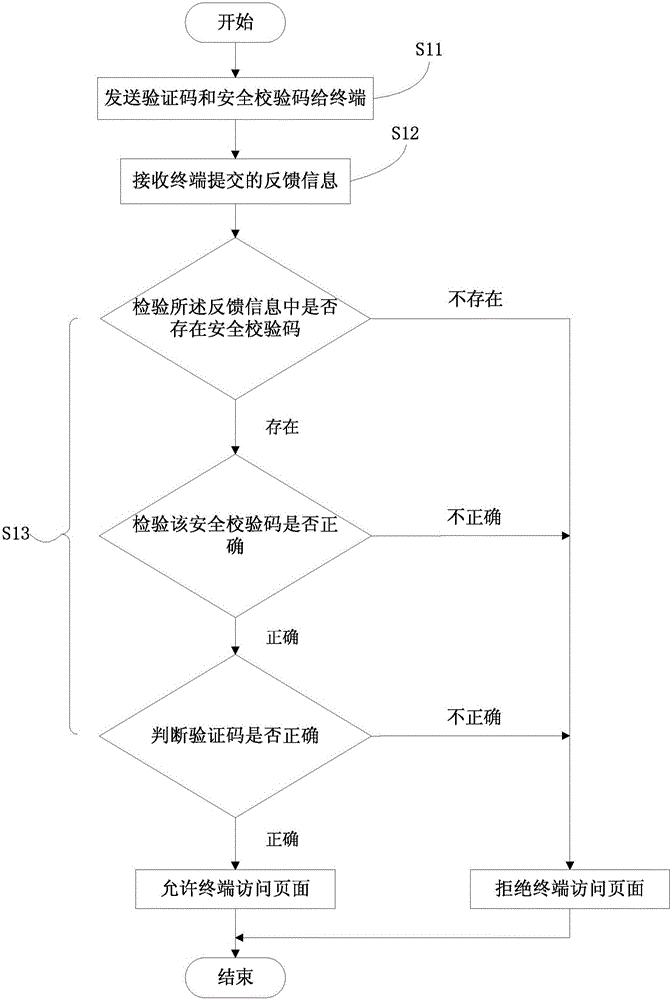
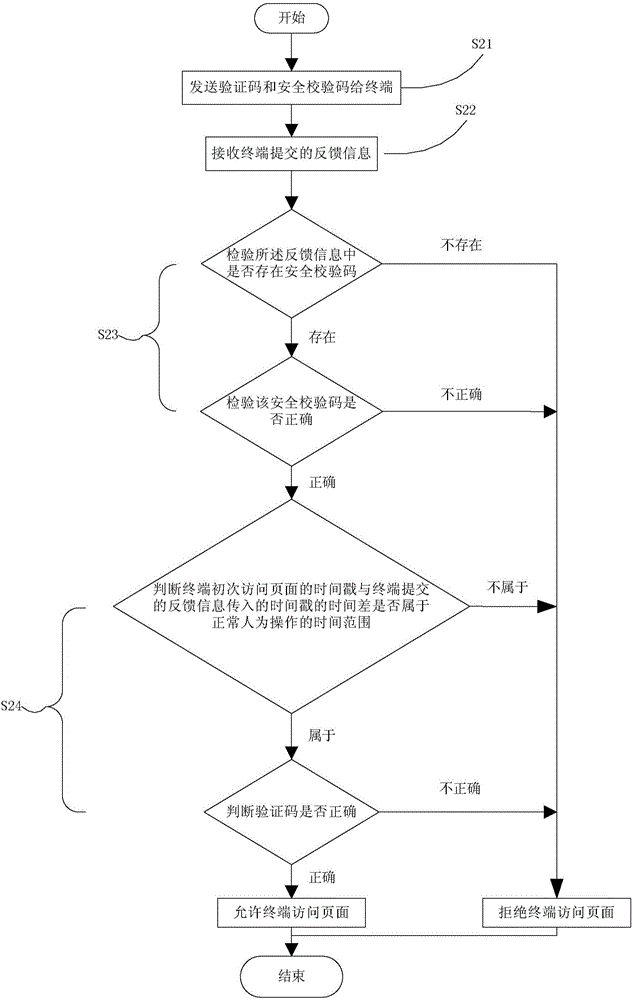
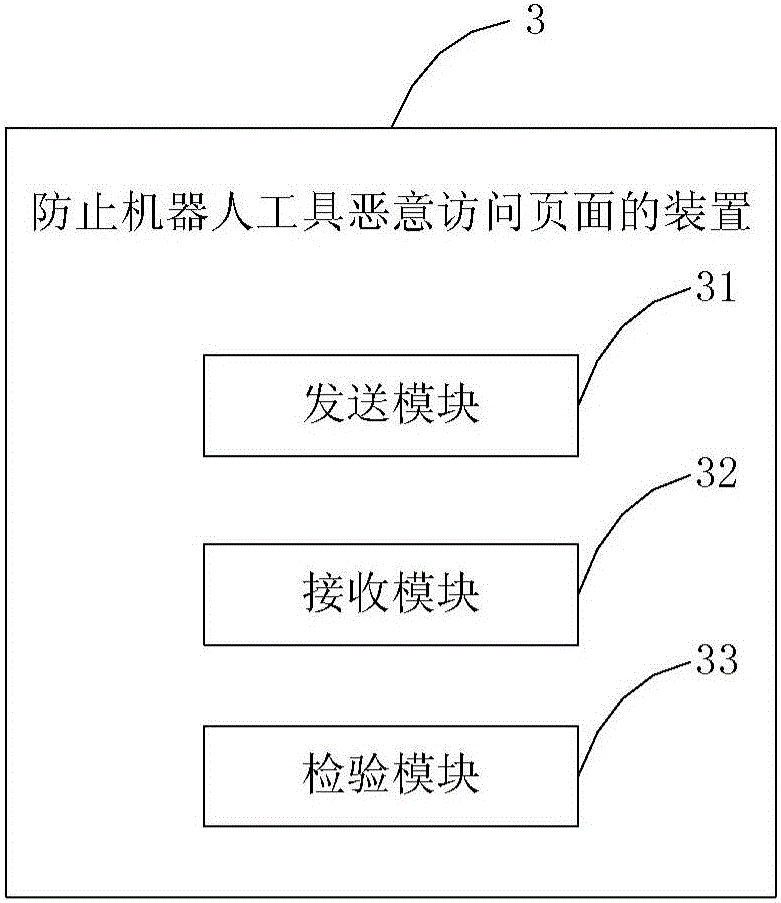
Method and device for preventing robot tool from maliciously accessing page
InactiveCN106257480APrevent Malicious BehaviorLower success rateDigital data authenticationComputer scienceServer-side
The invention provides a method for preventing a robot tool from maliciously accessing a page. The method comprises the steps that a verification code and a safety check code are sent to a terminal; feedback information submitted by the terminal is received; whether the safety check code exists in the feedback information or not is inspected, if yes, whether the safety check code is correct or not is inspected, and if not, the terminal is not allowed to access the page; whether the verification code in the feedback information is correct or not is judged on the condition that the safety check code is correct; if yes, the terminal is allowed to access the page, and if not, the terminal is allowed to access the page. According to the method, the safety check code is implanted into the code of the page or a cookie or a server side cache, and therefore the malicious behavior that the robot tool skips the premise step of coupon getting to directly get coupons is effectively prevented; meanwhile, the condition that the robot tool frequently and quickly gets the coupons is effectively prevented, and the success rate that the robot tool maliciously gets the coupons is decreased.
Owner:BEIJING JINGDONG SHANGKE INFORMATION TECH CO LTD +1
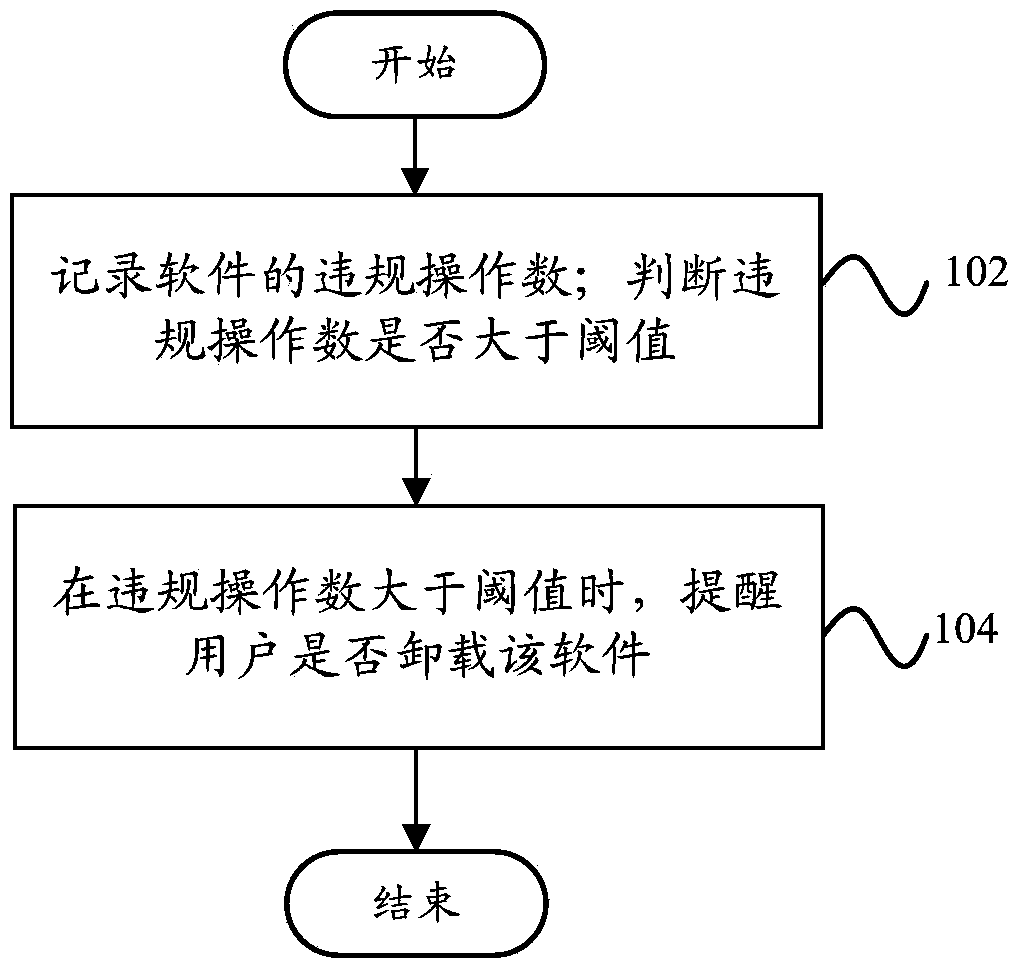
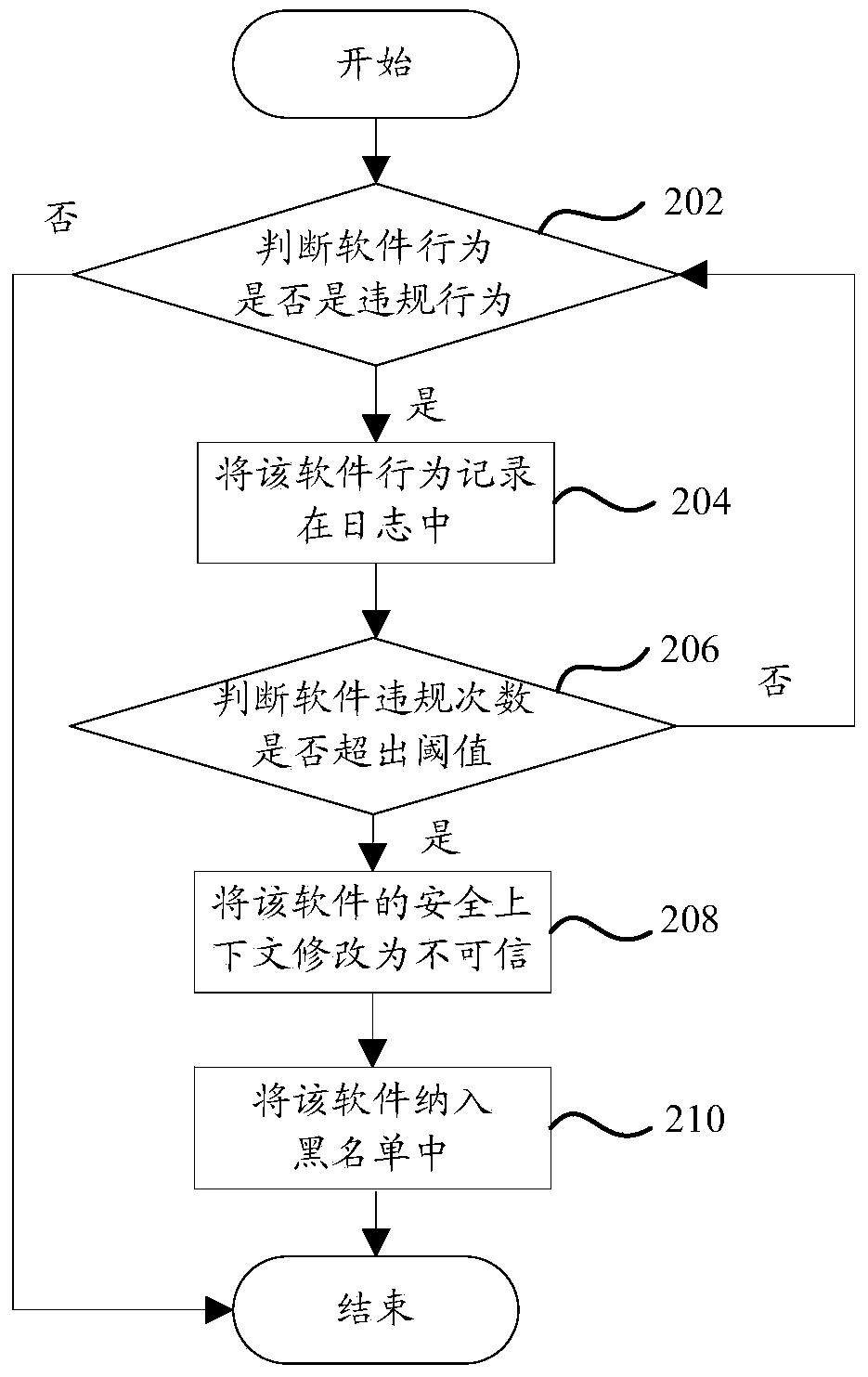
Software behavior monitoring method and terminal
InactiveCN103679028APrevent Malicious BehaviorImprove securityPlatform integrity maintainanceGNU/LinuxSoftware engineering
The invention provides a software behavior monitoring method and a terminal. The software behavior monitoring method includes the steps of recording the number of violation operations of software, judging whether the number of the violation operations is larger than a threshold value, and reminding a user to uninstall the software when the number of the violation operations is larger than the threshold value. A security-enhanced Linux subsystem is transplanted on the terminal so as to monitor violation operation behaviors of the software according to a set authority strategy, when the number of the violation operations is larger than the threshold value, the user is reminded of software behaviors, pre-warning and collection of rogue software are achieved, and safety performance of the terminal is improved.
Owner:SHENZHEN COOLPAD SOFTWARE TECH +1
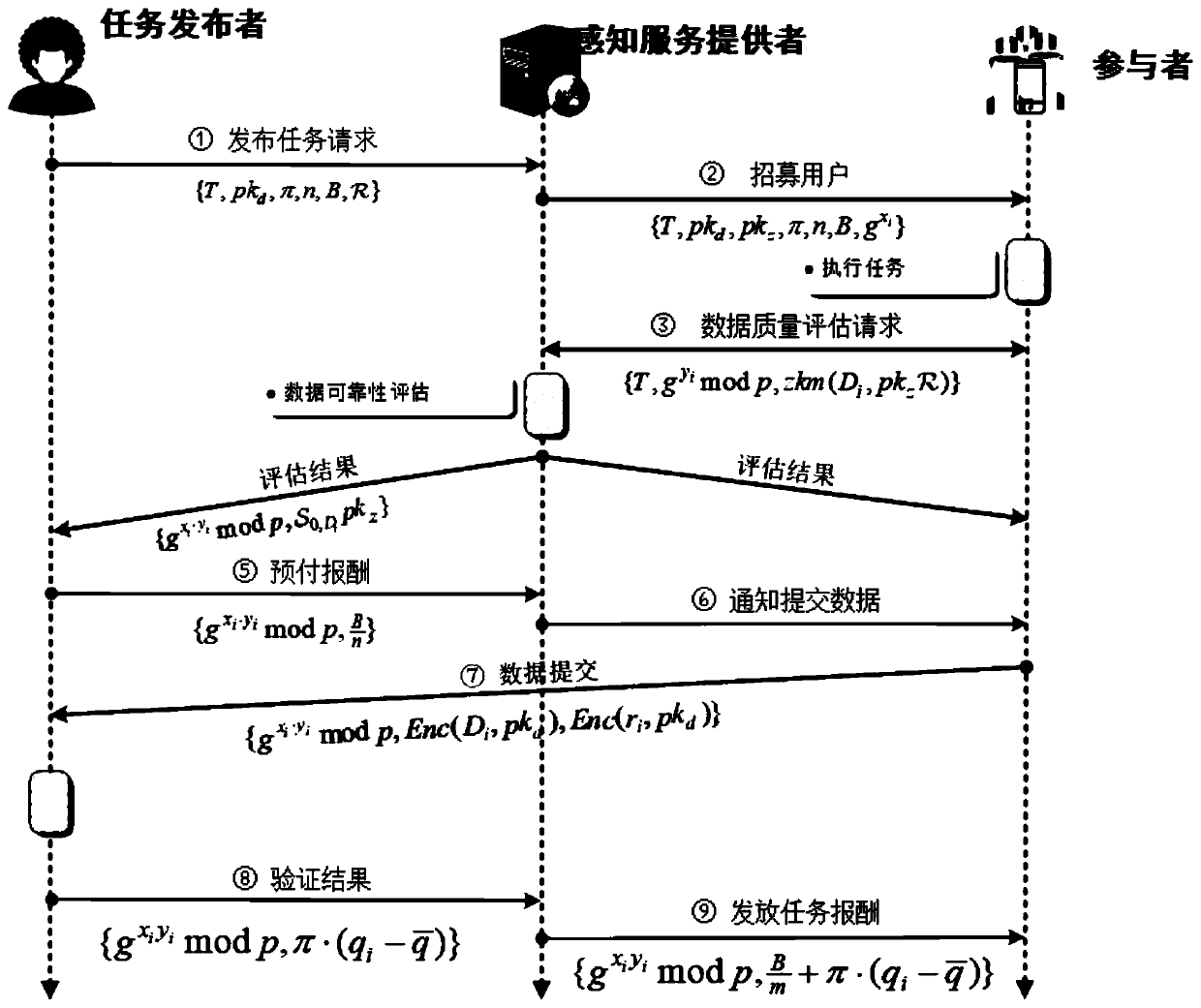
Data quality perception excitation method for privacy protection in group perception
ActiveCN111246468AIdentify scope constraintsWon't leakUser identity/authority verificationSecurity arrangementHidden dataMedicine
The invention discloses a data quality perception excitation method for privacy protection in group perception. According to the method, data quality evaluation of privacy protection and excitation based on data quality are realized on the basis of a zero knowledge proof principle and an anonymity technology. A task publisher publishes a collection value range, task participants are recruited by perception service providers, the participants hide data in the constructed commitment to participate in the evaluation of the perception service providers, the task publisher verifies the reliabilityof data submitted by the task participants, the perception service providers provide an anonymous technology for the participants to protect the identity privacy of the participants, and data qualityexcitation under privacy protection is achieved under task budget constraints through measurement of two-stage data quality and an excitation mechanism based on the data quality. According to the method, the identity privacy of the user is protected, and the reliability of the data of the participants is evaluated in a privacy protection manner.
Owner:SOUTH CHINA UNIV OF TECH
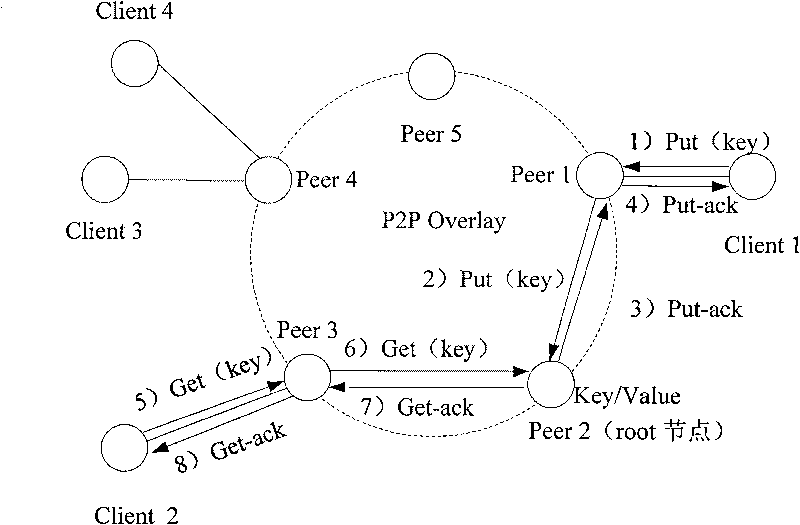
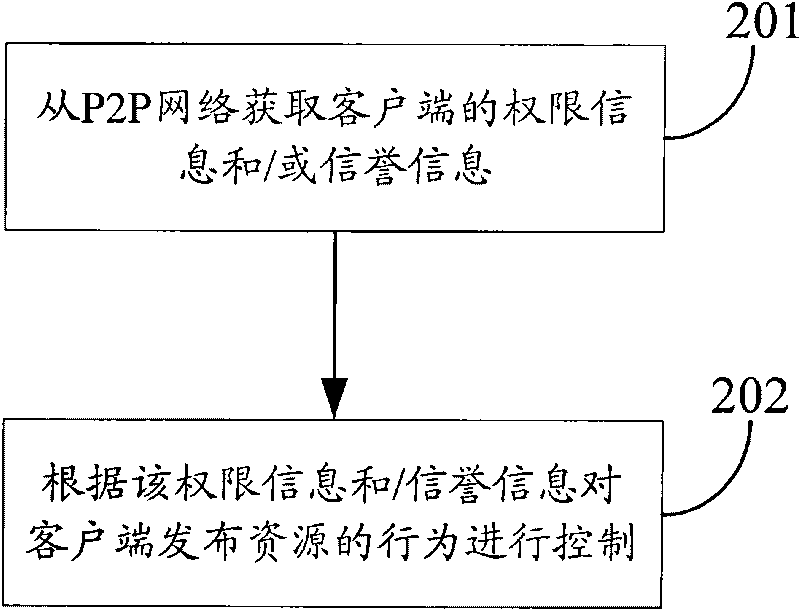
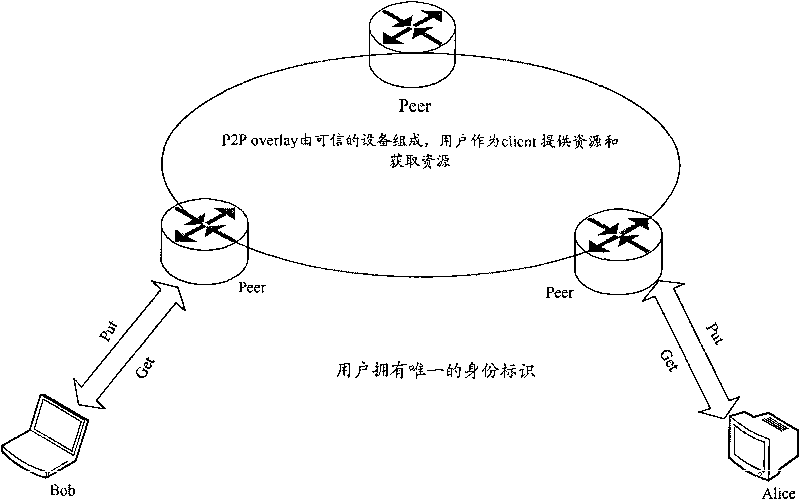
Method, system and device for controlling resource release in P2P
The embodiment of the invention discloses a method for controlling resource release in a P2P network. The P2P network is formed by believable nodes. The method is that the authority information and / or reputation information of a client are obtained from the P2P network; and the behavior of the client releasing resources is controlled according to the authority information and / or reputation information. In the embodiment of the invention, since the resources released by the client are inspected at an accessed Peer node, the malicious behaviors of the client are prevented. Moreover, the Peer releases the relevant client information on an Overlay. When a client node is shifted to the Peer, a newly accessed Peer node obtains the authority information of the client from the Overlay and inspects and controls the accessed client releasing and obtaining resources.
Owner:HUAWEI TECH CO LTD
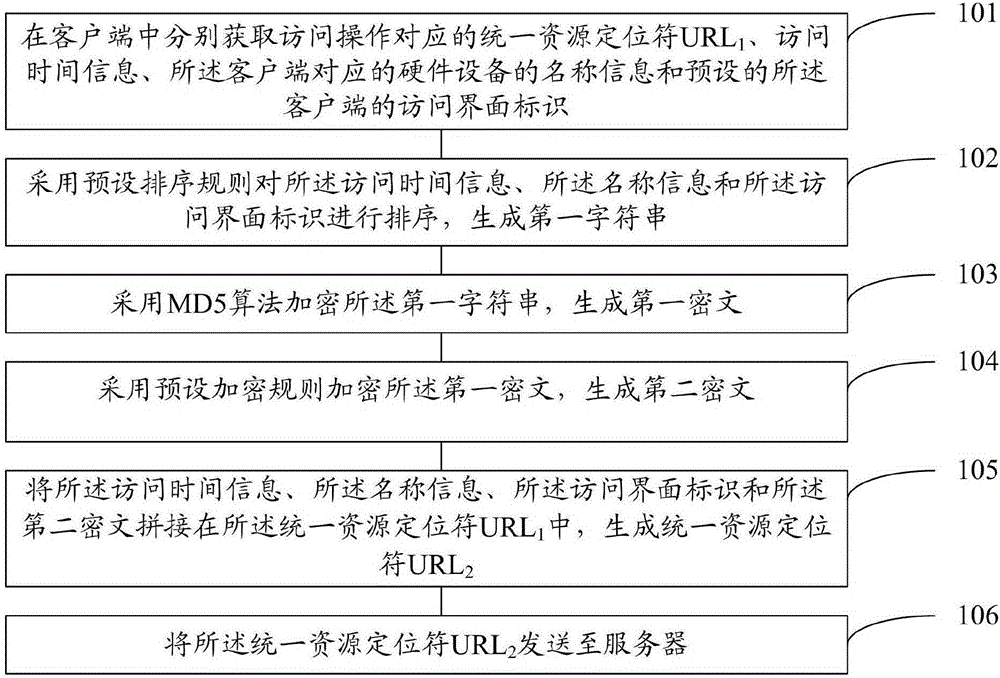
Communication encryption method, device and system
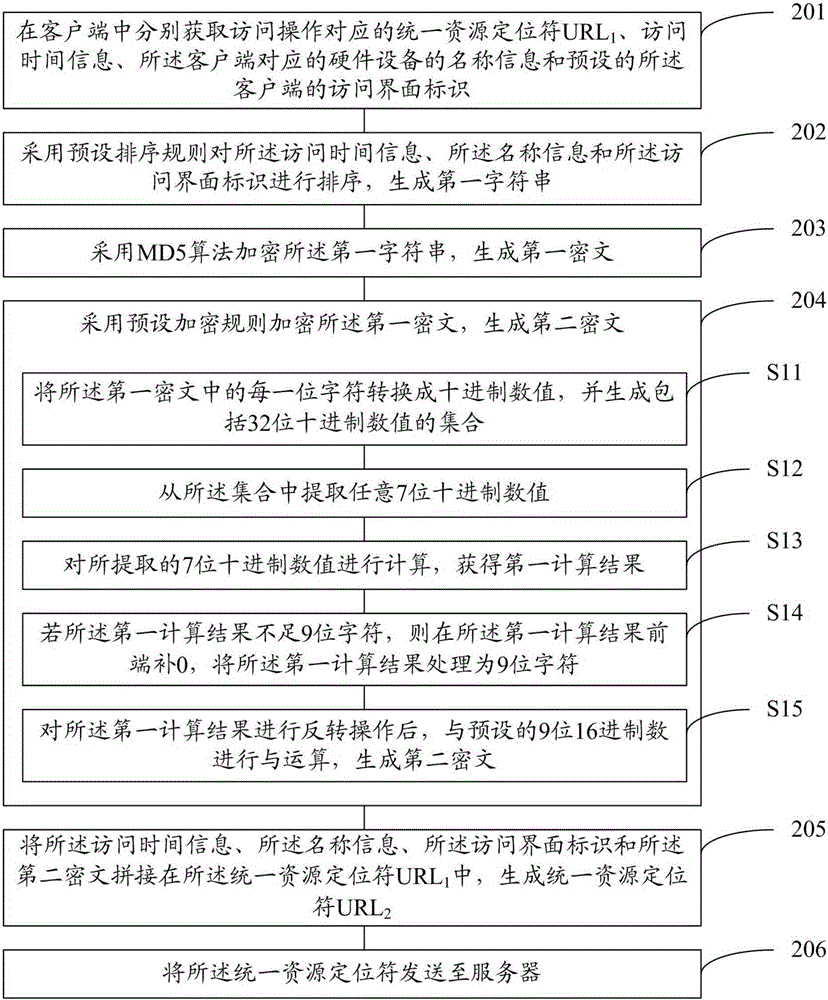
Embodiments of the present invention provide a communication encryption method, a device and a system. The method comprises the steps of respectively acquiring a uniform resource locator (URL1) corresponding to an access operation, the access time information, the name information of hardware equipment corresponding to a client, and the identifier of the preset access interface of the client; according to a preset sorting rule, sorting the access time information, the name information and the identifier of the access interface to generate a first character string; encrypting the first character string based on the MD5 algorithm to generate a first cipher text; encrypting the first cipher text by using a preset encryption rule to generate a second cipher text; splicing up the access time information, the name information, the identifier of the access interface and the second cipher text in the uniform resource locator (URL1) to generate a uniform resource locator (URL2); and sending the uniform resource locator (URL2) to a server. Embodiments of the present invention show that, the communication encryption method is higher in safety, and is capable of effectively preventing the malicious behavior of disturbing the generation of a ranking list.
Owner:VIVO MOBILE COMM CO LTD
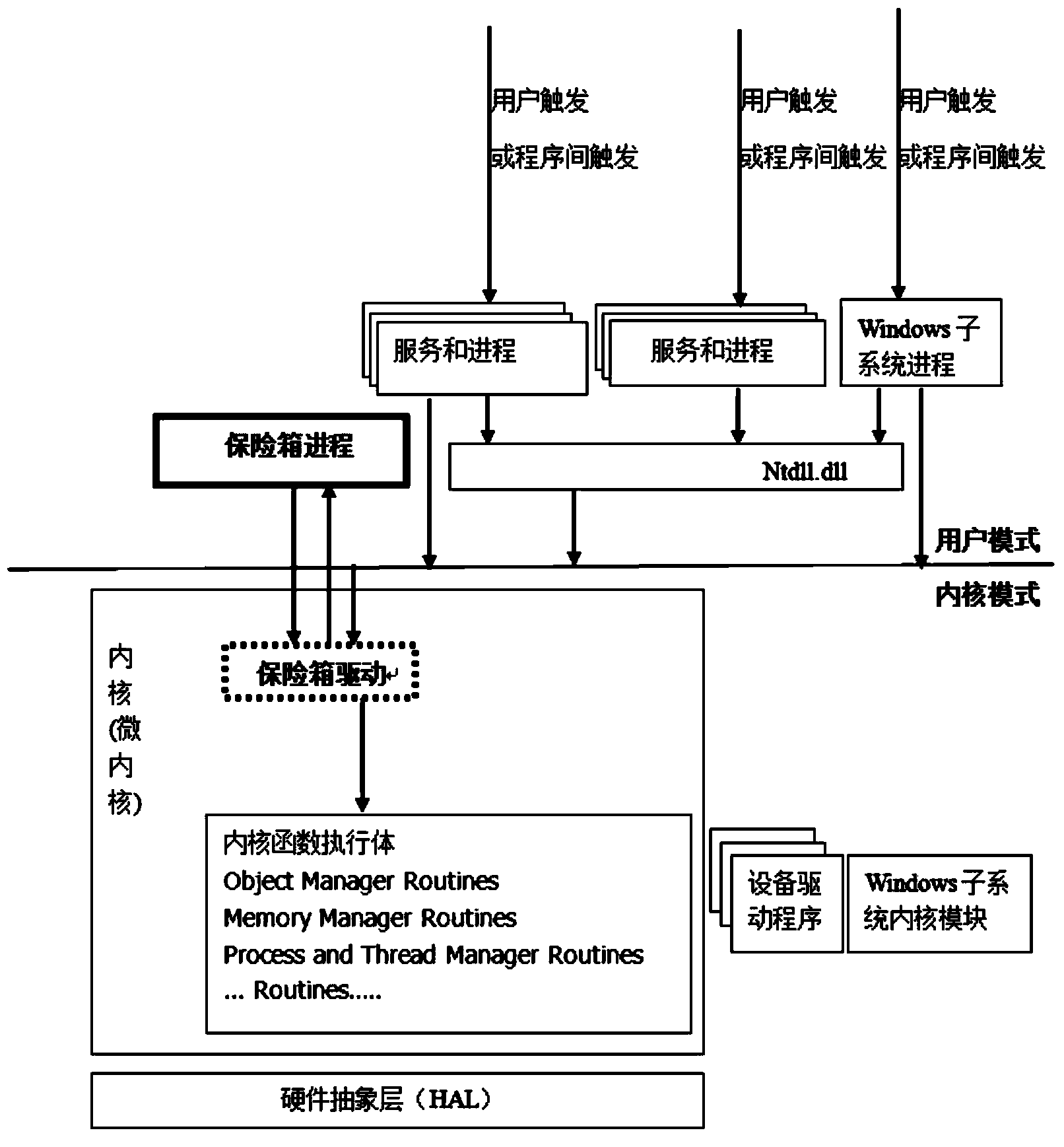
Process protection method, device and terminal
InactiveCN106203093AImprove defenseImprove protectionPlatform integrity maintainanceData informationComputer science
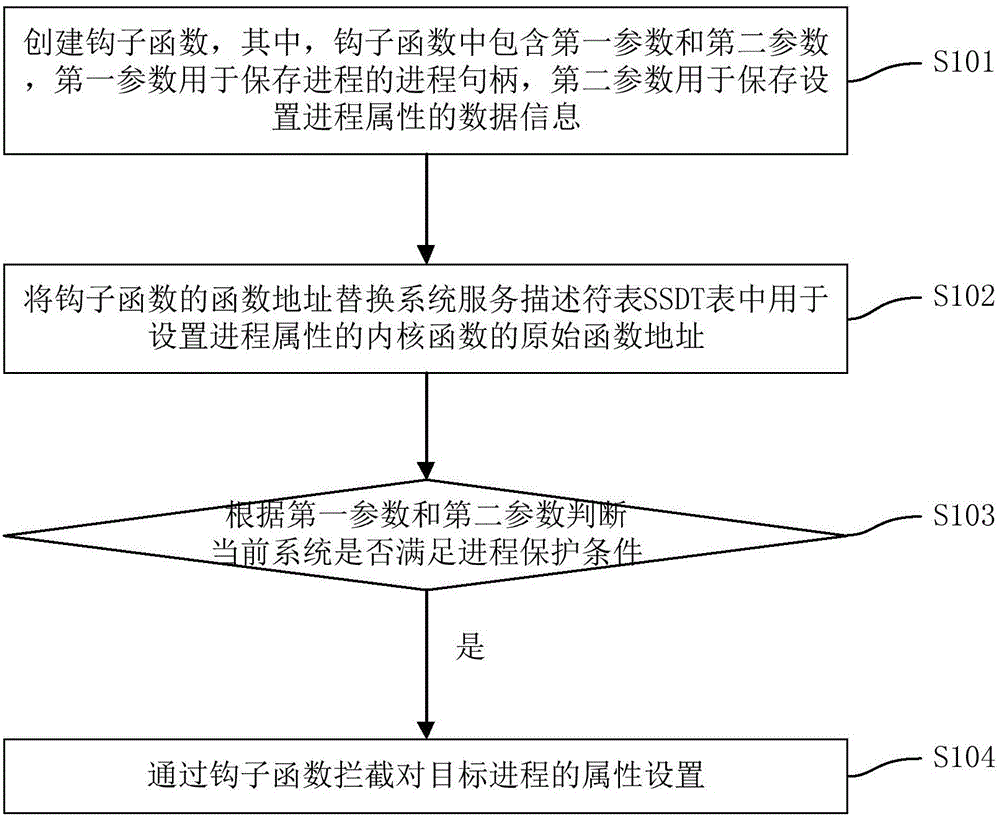
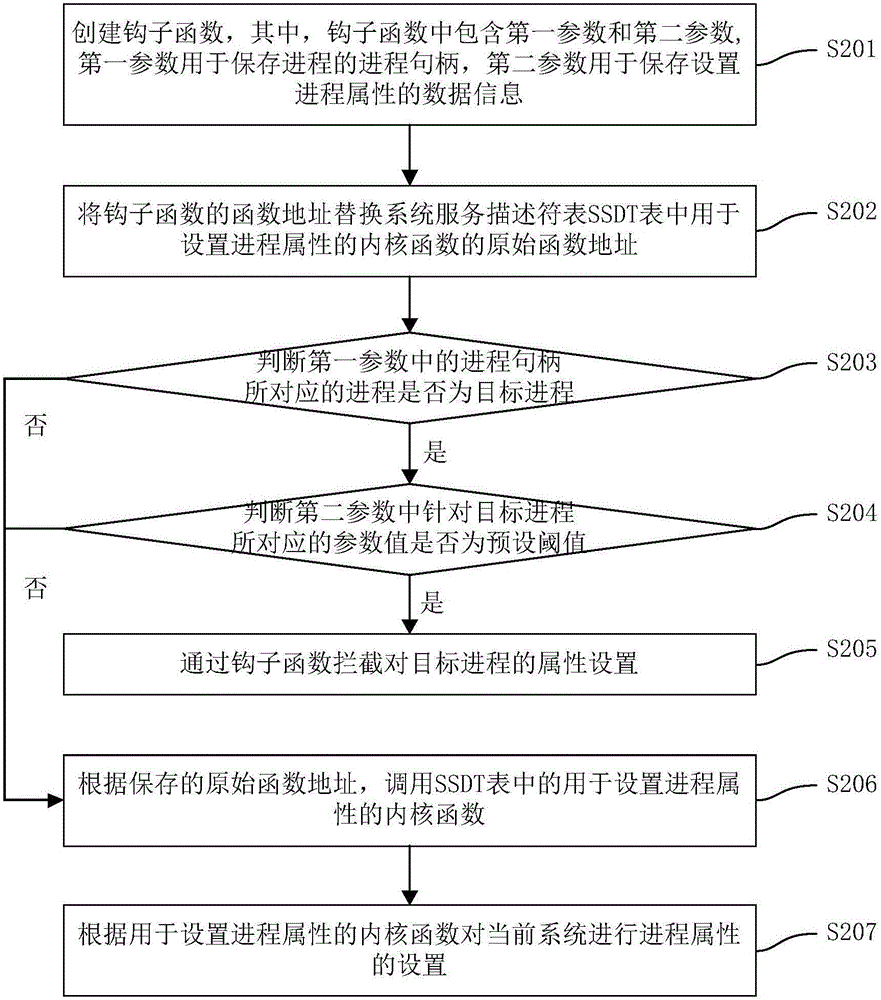
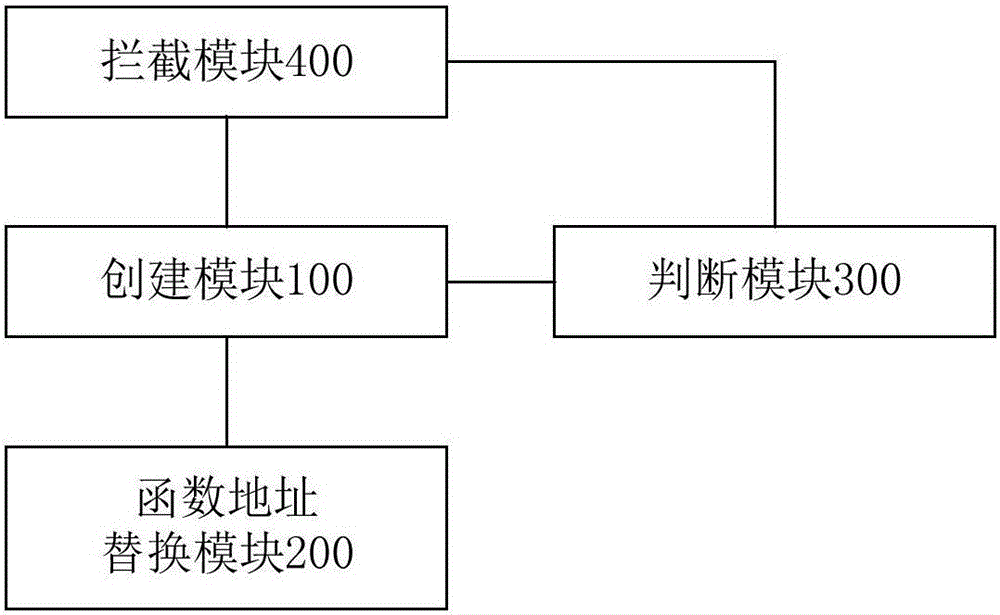
The invention discloses a process protection method, device and terminal, wherein the method comprises the following steps of: creating a hook function, wherein the hook function includes a first parameter and a second parameter; the first parameter is used for storing a process handle of a process; and the second parameter is used for storing data information for setting process attribute; replacing a function address of the hook function by an original function address used for setting a kernel function of the process attribute in a system service descriptor table SSDT; judging whether the current system satisfies a process protection condition or not according to the first parameter and the second parameter; and, if the current system satisfies the process protection condition, intercepting attribute setting of a target process through the hook function. The purpose of protecting the process by intercept a process attribute setting function is achieved; therefore, the target process, such as a process of a safety element in a terminal system, is protected easily; the defence capability of the target process is improved; and safety protection to a user terminal and the system can be carried out easily.
Owner:ZHUHAI BAOQU TECH CO LTD
Method for sensing abnormal behavior of passenger by wireless technology
InactiveCN108737968APersonal protectionGuarantee property securityAlarmsTransmissionMaterial resourcesSpanning tree
The invention discloses a method for sensing an abnormal behavior of a passenger by a wireless technology. The method comprises the following steps: a single carriage AP (Access Point) collects STA (Spanning Tree Algorithm) data; the data is summarized and stored in a control center; analyze the data and match a processing model; predefine a normal / abnormal model matched with a predefined normal / abnormal model; and alarm about the abnormal user. The method provided by the invention is based on the vehicle-mounted internet to identify and predict the theft in advance, is low in cost and high intimeliness, and saves plenty of costs of manpower and material resources.
Owner:成都天佑飞天科技有限公司
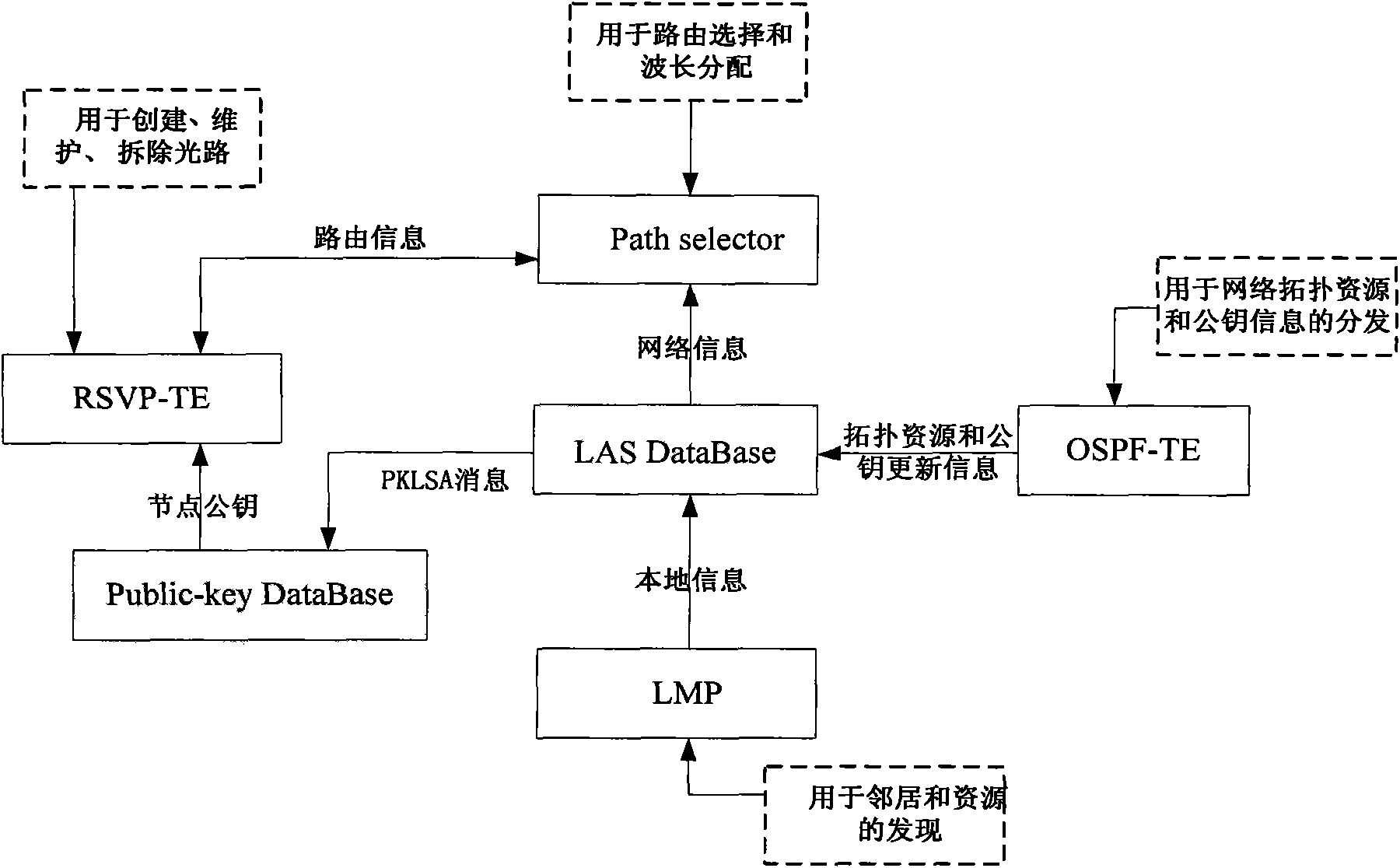
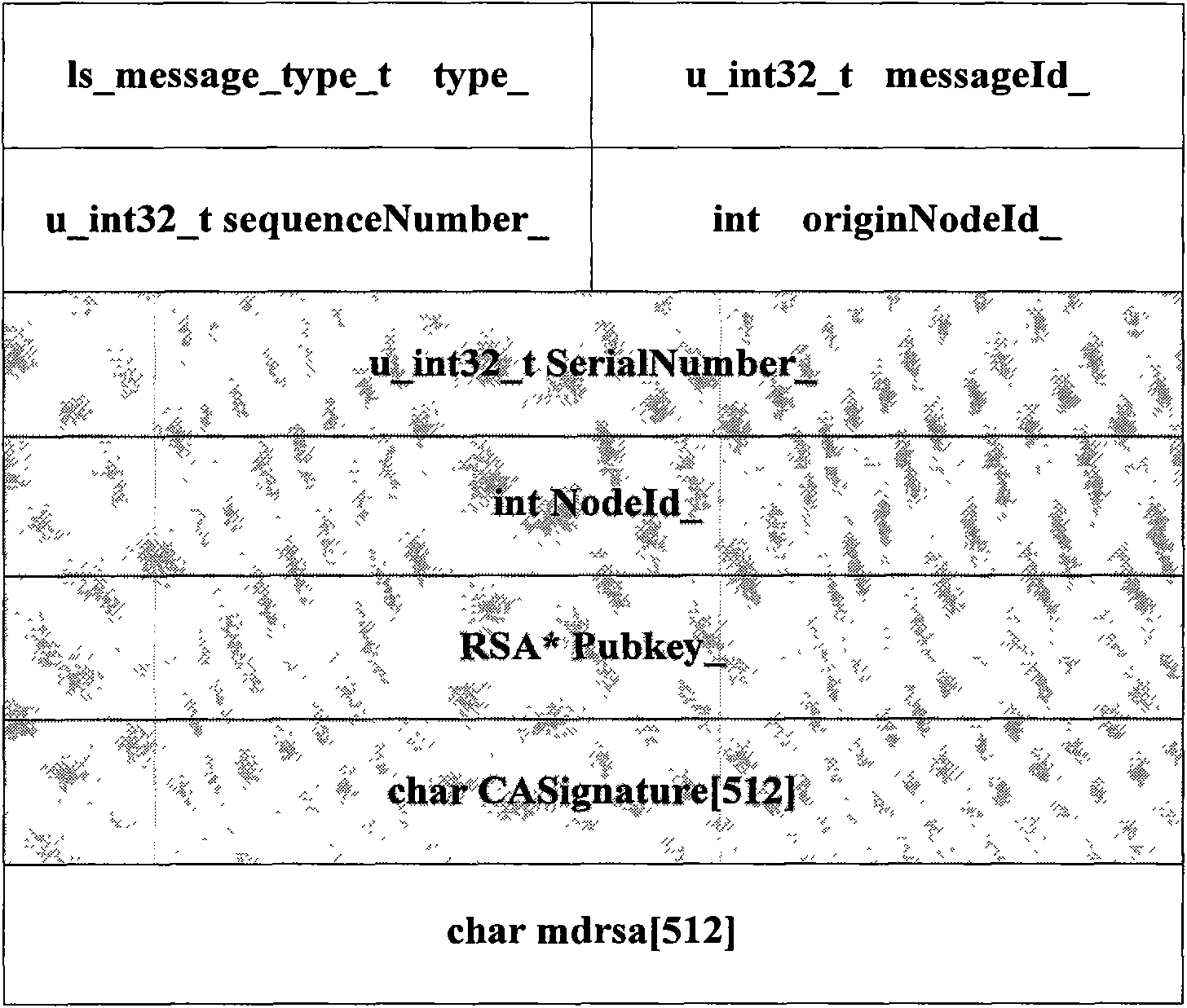
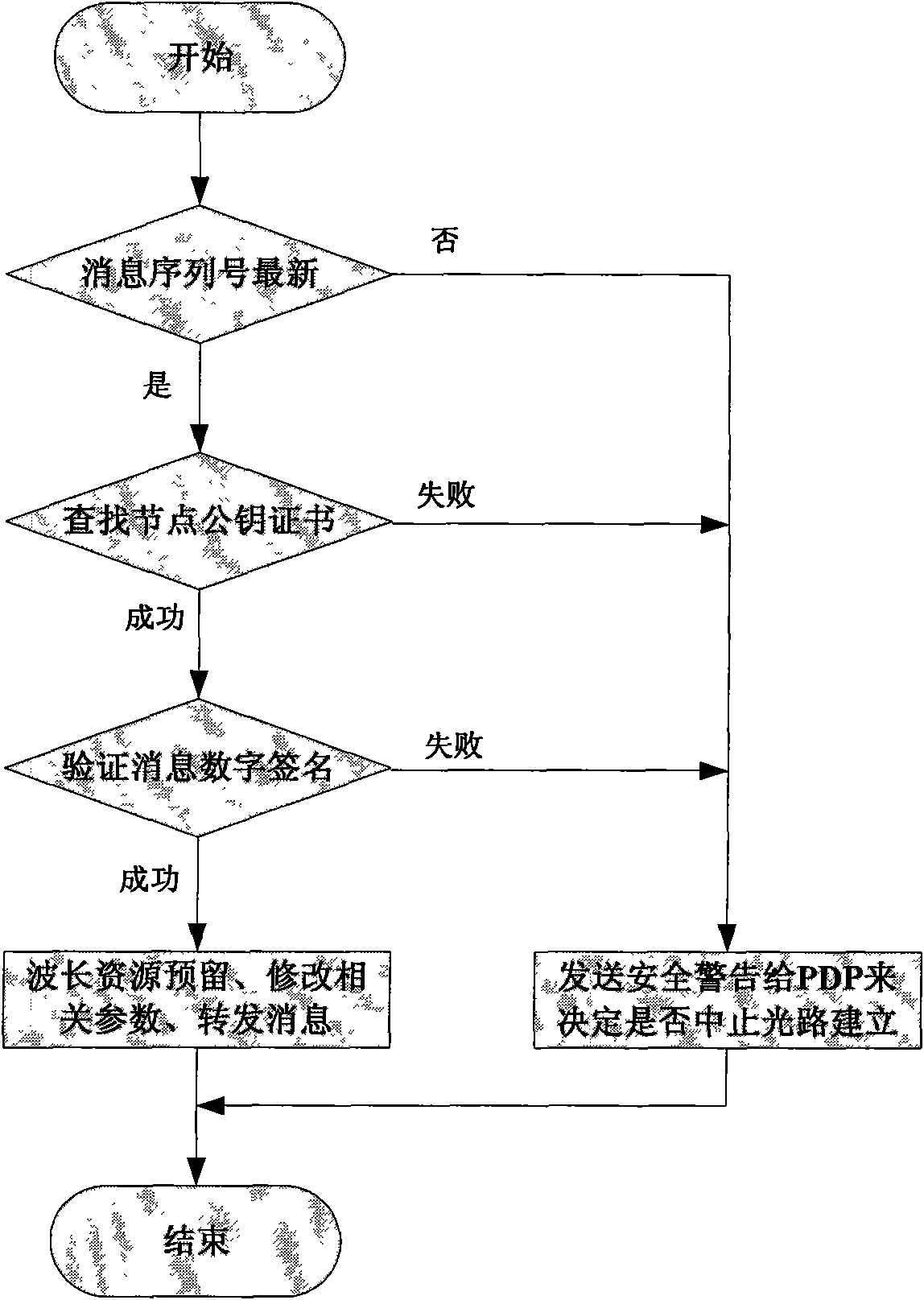
Secure lightpath establishment method based on automatically switching optical network (ASON)
InactiveCN101616340APrevent Malicious BehaviorPrevent malicious tamperingMultiplex system selection arrangementsFibre transmissionOptical pathComputer security
The invention provides a secure lightpath establishment method based on an automatically switching optical network (ASON), relating to the establishment of lightpaths or light connection in a control plane of the ASON. The method can prevent malevolence or selfishness of internal nodes by employing the comprehensive wavelength reservation strategy to carry out integrity protection on the important objects in the GMPLS RSVP-TE message through the security mechanisms such as digital signature and message feedback. In addition, the method designs a corresponding key management mechanism according to the characteristic of close coupling between a routing module and a signaling module in the ASON and distributes a node public key certificate needed in the process of establishing the lightpath by adopting the PKLSA message of OSPF-TE. The method has the characteristics of fast lightpath establishment, short attack detection and low message load while ensuring secure establishment of the lightpaths, and is especially suitable for secure establishment of light connection in the control plane in the ASON.
Owner:UNIV OF SCI & TECH BEIJING
Method and system for merchants to perform user data drainage
PendingCN111612551AUninterrupted Financial DistributionHuge orderDiscounts/incentivesBuying/selling/leasing transactionsThird partyEngineering
The invention discloses a method for a merchant to perform user data drainage. The method comprises the steps that S1 an online merchant and an offline merchant on a third-party management platform upload commodity information and participated promotion activity information to a background terminal through a merchant client to complete merchant parking; S2 a consumer operates the consumer client through any one of a applet or an APP or a PC; the consumer uses the marketing management platform for the first time and registers the marketing management platform as a platform member, and the management platform server continuously records consumption information of the consumer and expands the consumer into a merchant of the platform member by the merchant for the first time to serve as an affiliated merchant of the corresponding consumer; and S3 starting from the affiliated merchant, other settled merchants perform discount consumption on the consumer of the registered platform member according to the promotion activity information participated by the merchant and display the discount consumption through the consumer client.
Owner:陈包容
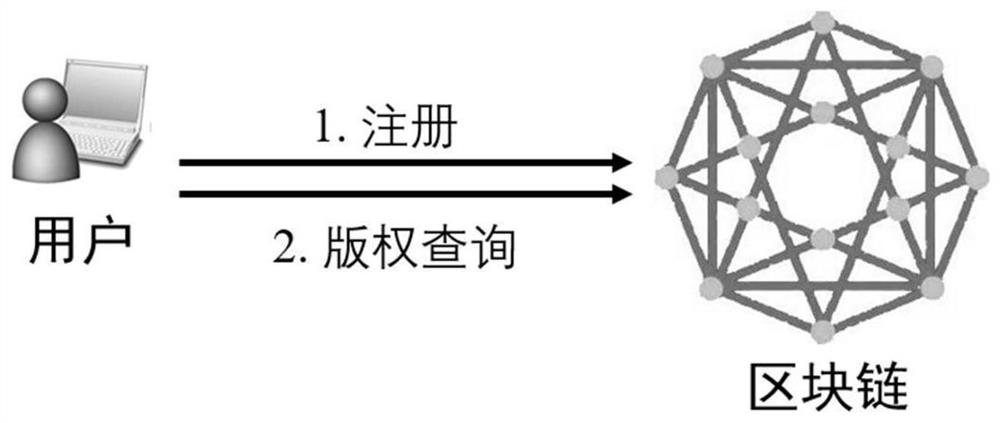
Digital copyright protection method based on block chain
PendingCN113706344AAchieve traceabilityGuaranteed fair exchangeData processing applicationsDigital data protectionFinancial transactionSmart contract
The invention aims to provide a digital copyright protection scheme based on a block chain, copyright services of the whole process are designed in combination with a block chain technology and a digital watermarking technology, and five functional requirements of copyright registration, copyright query, copyright transaction, copyright transfer and copyright protection are met. In addition, an OptiFairSwap protocol is realized through a smart contract to complete effective delivery proof and prevent malicious behaviors of both transaction parties, and a pirate tracking function is realized in combination with a digital fingerprint technology. Once the works are confirmed on the block chain, subsequent transactions can be recorded in real time, so that the works are traceable and traceable in the whole life cycle of creation, circulation and use, and powerful technical guarantee and conclusion evidence are provided for judicial evidence collection. Meanwhile, in the copyright transaction and copyright transfer process, a copyright owner can directly participate in the copyright management of own works, the transaction process is open and transparent, and the royalty is settled in a transparent manner.
Owner:WUHAN UNIV
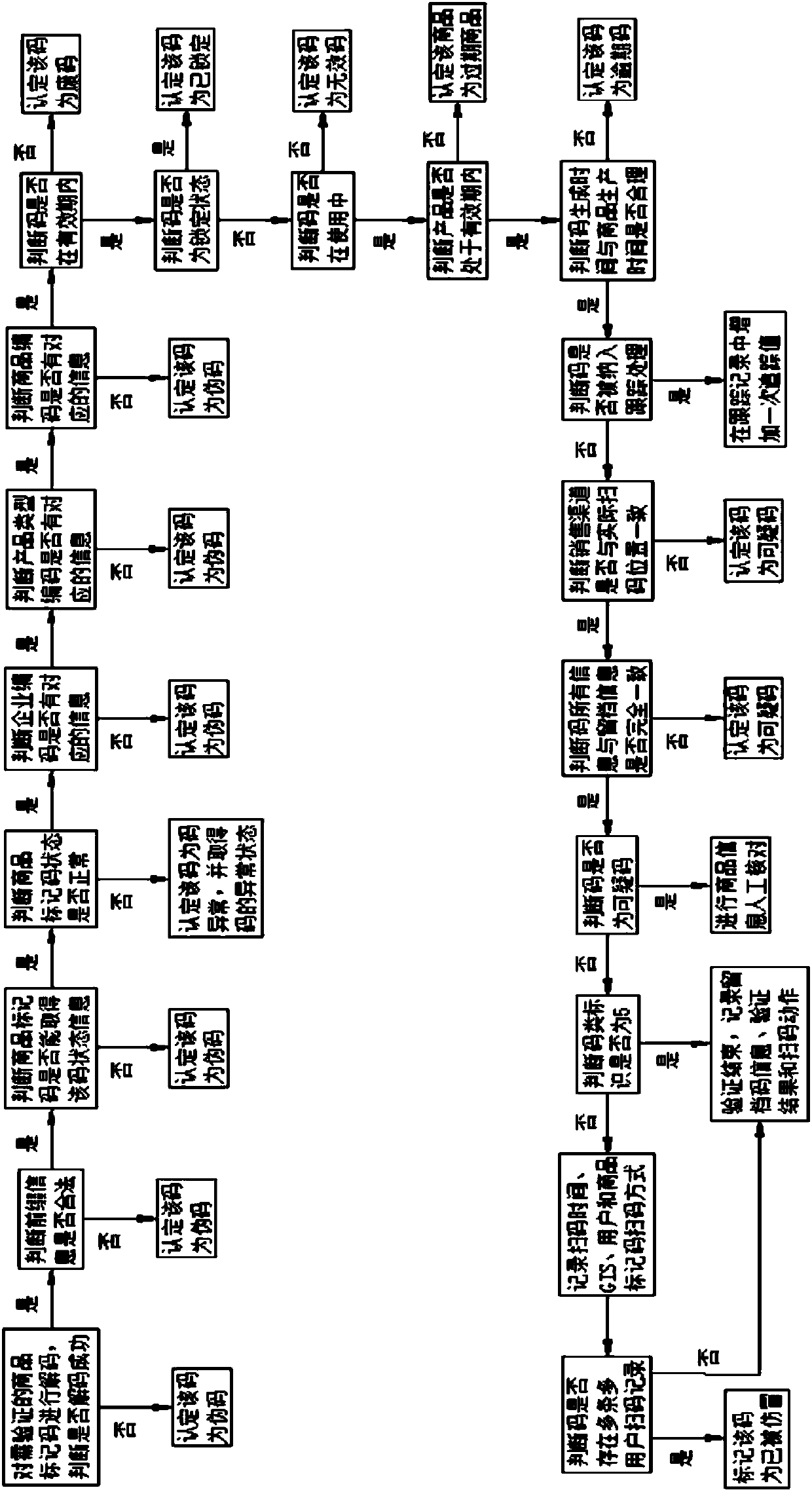
Combined verification method of product labels with two-dimensional codes and feature codes in bottle caps
InactiveCN105761086AImprove consumer experiencePrevent Malicious BehaviorCommerceRecord carriers used with machinesValidation methodsSoftware engineering
The present invention discloses a combined verification method of product labels with two-dimensional codes and feature codes in bottle caps. The method comprises the following steps: a, a uniquely identified two-dimensional code is arranged at the right side of a product label, and a feature code is arranged in a bottle cap; b, the two-dimensional code on the product label and the feature code in the bottle cap are identified on a packing line in the process of product package through adoption of the visual identification technology, and the incidence relation therebetween is formed and is stored in the APP background database; c, a consumer buys a product and uses a hand-held terminal to scan the two-dimensional at the right side of the product label to enter an APP interface; d, the bottle cap is opened, the feature code is inputted in the hand-held terminal according to the notice of the APP interface; and e, the feature code is compared with pre-storing data at package at the APP background, and the verification passes if the comparison is successful. The combined verification method of product labels with two-dimensional codes and feature codes in bottle caps is able to improve the consumer's consumption experience of reading two-dimensional codes when the consumer is buying products, and avoid the malicious behavior that a consumer only scans two-dimensional codes and does not really buy the products.
Owner:上海凌脉网络科技股份有限公司
Anti-channel conflict method for electronic business
InactiveCN108229977APrevent cross-sellingConvenient and quick automatic identificationProgramme controlComputer controlOrder formBlack list
The invention discloses an anti-channel conflict method for electronic business. The anti-channel conflict method comprises the following steps: S1, ordering by customers and obtaining order information by background; S2, comparing keywords in the order information with a blacklist in a database; S3, if no keywords exist in the blacklist in the comparison in the S2, extracting address characters;S4, combining the characters in the S3 to obtain combined words, and then comparing the combined characters with addresses in an address base; S5, comparing the keywords in the S4 to obtain one part;determining whether suspicion indexes need to be manually reviewed or not when whether the compared part belongs to the sales scope of dealers cannot be determined; S6, if the suspicion indexes in theS5 are not up to standard, packing and delivering by adopting packing containers. By use of the method disclosed by the invention, the channel conflict risk in an electronic business system can be quickly and automatically identified; even if the dealers maliciously change the addresses of recipients, a system can recognize the address change by similarity matching, so that the malicious channelconflict behavior of the dealers can be effectively inhibited.
Owner:脉度(上海)电子商务有限公司 +1
Crowd sensing method based on block chain
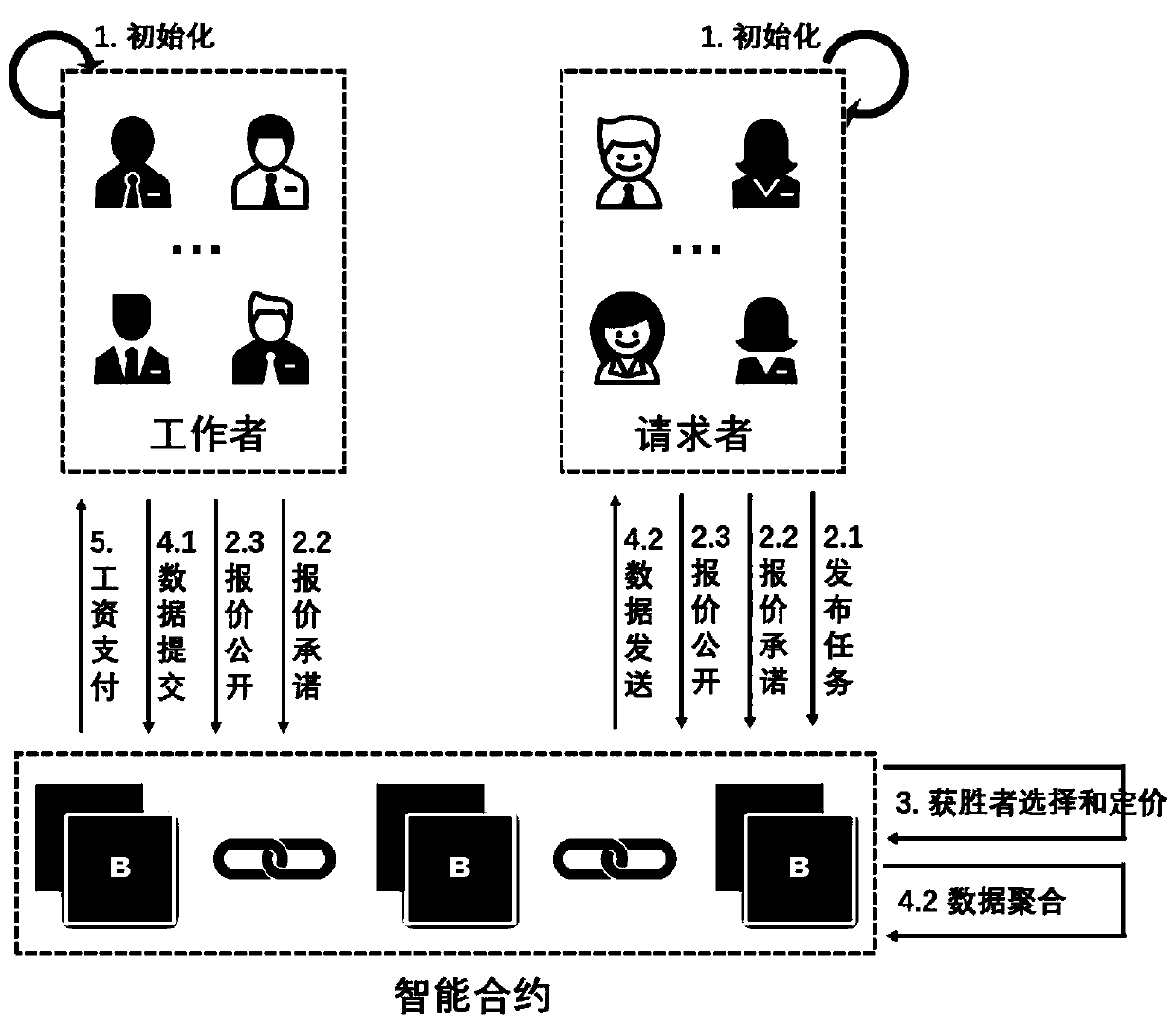
InactiveCN111262708AEnhanced anonymityProtect privacy and securityFinancePublic key for secure communicationPaymentFinancial transaction
The invention discloses a crowd sensing method based on a block chain, which is applied to a network environment composed of n crowd sensing workers, m crowd sensing requesters and the block chain, and comprises the steps of S1 an initialization stage; S2 a quotation stage; S3 a winner selection and pricing stage; S4 a data submitting and aggregating stage; and S5 a payment stage. According to themethod, the problem that fairness and privacy are not considered in a current crowd sensing incentive mechanism can be solved, so that it is guaranteed that workers and requesters can execute transactions under the condition that fairness is guaranteed; meanwhile, anonymity of the workers is protected; contact between user information and position information is cut off; and personal privacy safety is protected.
Owner:ANHUI UNIVERSITY +1
System and method for providing privacy and security protection in blockchain-based private transactions
ActiveCN111164935AImprove securityImprove protectionUser identity/authority verificationPayment architectureEngineeringFinancial transaction
Methods, systems, and apparatus, including computer programs encoded on computer storage media, for implementing blockchain-based private transactions are provided. One of the methods is performed bya first blockchain node to a private transaction, the method including: determining one or more second blockchain nodes to the private transaction according to a blockchain contract in a public blockchain; transmitting transaction information to the one or more second blockchain nodes, the transaction information comprising one or more senders of the private transaction, one or more recipients ofthe private transaction, and one or more transaction amounts of the private transaction; obtaining a signature from each of a number of the one or more second blockchain nodes certifying receipt of the transaction information; and in response to obtaining the number of the signatures over a threshold, storing at least a representation of the private transaction and the signatures in the public blockchain.
Owner:ADVANCED NEW TECH CO LTD
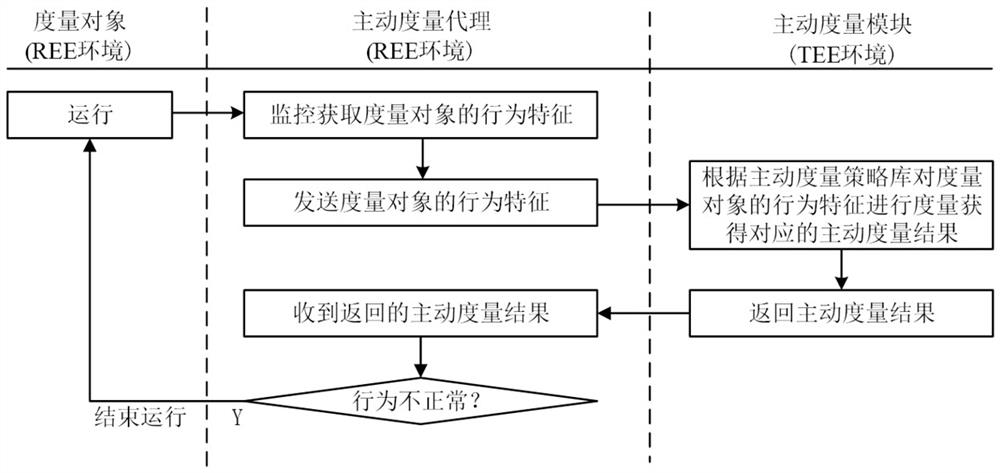
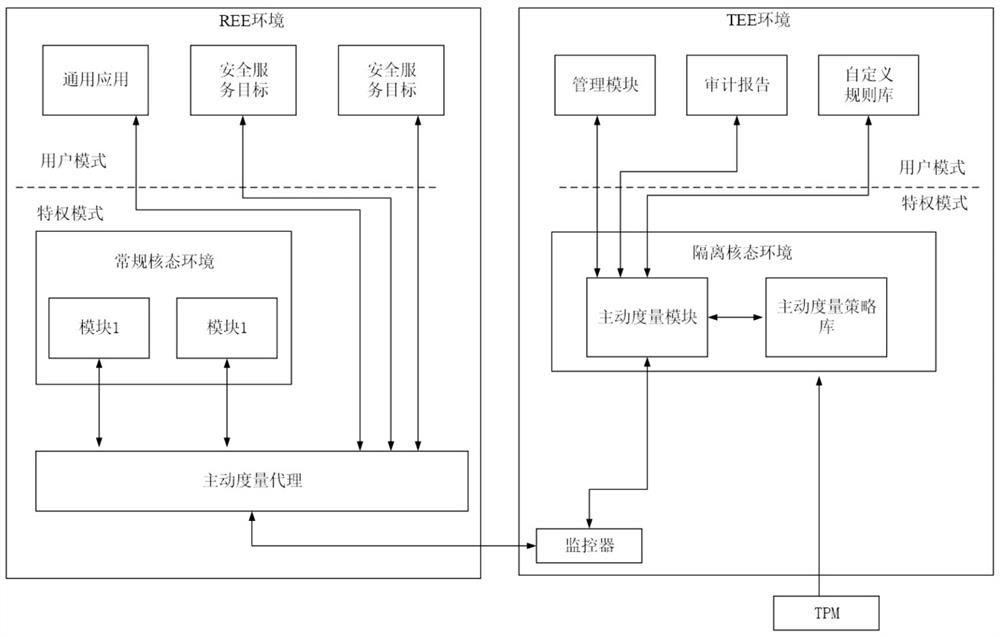
TEE-based software behavior active measurement method and system
ActiveCN111859394AStrong Behavioral MetricsImprove operational efficiencyProgram initiation/switchingResource allocationSimulationActive measurement
The invention discloses a TEE-based software behavior active measurement method and system. The method comprises the following steps executed in the operation process of a measurement object in an REEenvironment: an active measurement agent in the REE environment monitors and acquires behavior characteristics of the measurement object, and sends the behavior characteristics of the measurement object to an active measurement module in a TEE environment; the active measurement module in the TEE environment measures the behavior characteristics of the measurement object according to the active measurement strategy library to obtain a corresponding active measurement result, and returns the active measurement result to the active measurement agent in the REE environment; and the active measurement agent in the REE environment receives the returned active measurement result. Compared with a traditional measurement method, the method has higher software behavior measurement capability, better operation efficiency and better security strength, can guarantee credible operation of the software, supports initiative measurement of real-time operation behaviors of the software, and has highermeasurement capability compared with an existing method.
Owner:NAT UNIV OF DEFENSE TECH
Digital security encoding method with universality and high-strength characteristics
ActiveCN107563768AImprove accuracyImprove retrieval efficiencyCo-operative working arrangementsCommerceTime markValidation methods
The invention discloses a digital security encoding method with universality and high-strength characteristics, which includes a marking code encoding method developed to adapt to various sales scenarios and product shapes, a digital pairing algorithm constructed to enhance the efficiency of the marking code marking process and provide real-time marking ability, and a mathematical validation method based on overall verification and branch verification constructed to achieve accurate authenticity identification and to ensure the accuracy of verification. Digital encoding is used as the core ofthe method. The two-dimensional code is used as a demonstration body, and digital encoding serves as an assistant. Multiple levels of security are provided. The method can adapt to various anti-counterfeiting application scenarios, and is of low cost and high adaptability. Moreover, the method is of very high safety, accuracy, security and usability, and is very inexpensive.
Owner:贺强宏
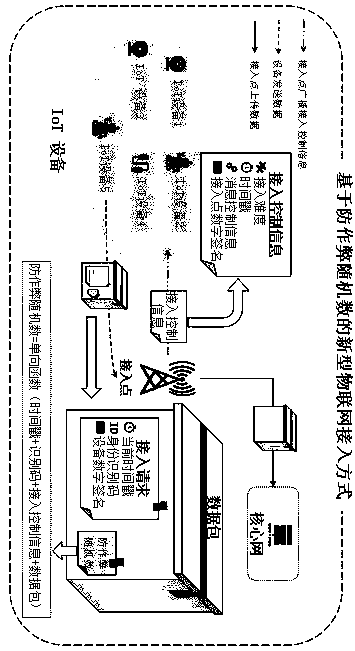
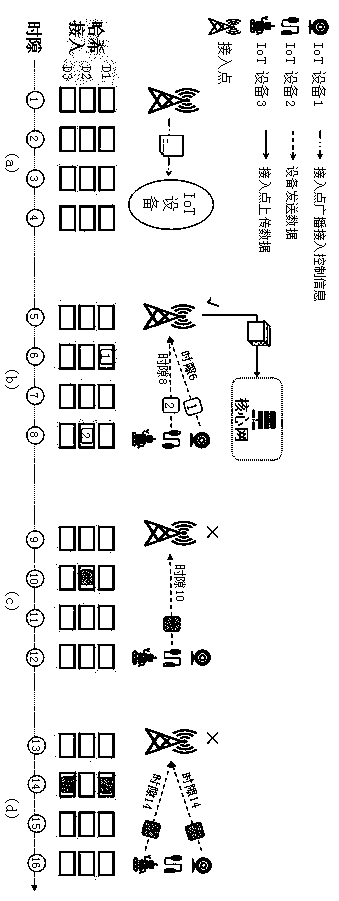
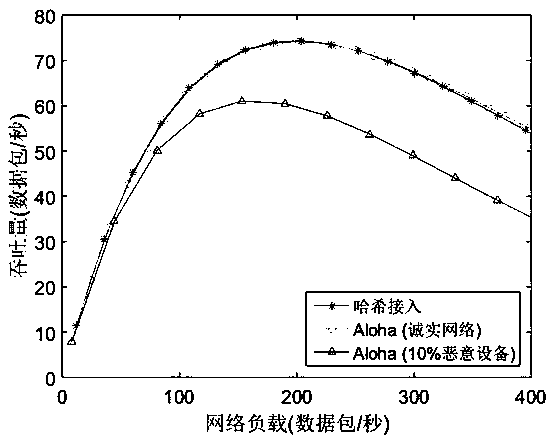
Novel Internet of Things access mode based on anti-cheating random number
InactiveCN110691420AResolve trust issuesPrevent Malicious BehaviorUser identity/authority verificationSecurity arrangementEngineeringLow power dissipation
The invention discloses a novel Internet of Things (IoT for short) access mode based on an anti-cheating random number. A traditional IoT access mode requires all IoT devices to comply with a random access criterion honest, but network fairness and overall efficiency will be seriously destroyed when a node has a selfish access behavior. According to the novel IoT access mode provided by the invention, the anti-cheating random number is utilized, and under the constraint of the access mode provided by the invention, the IoT devices which are not trusted with each other are forced to strictly comply with the random access criterion, so that the fairness and efficiency of the network are ensured. The access mechanism based on the anti-cheating random number is safe, reliable, small in calculated amount, easy to implement and suitable for general IoT equipment with low power consumption and low computing power.
Owner:SOUTHEAST UNIV
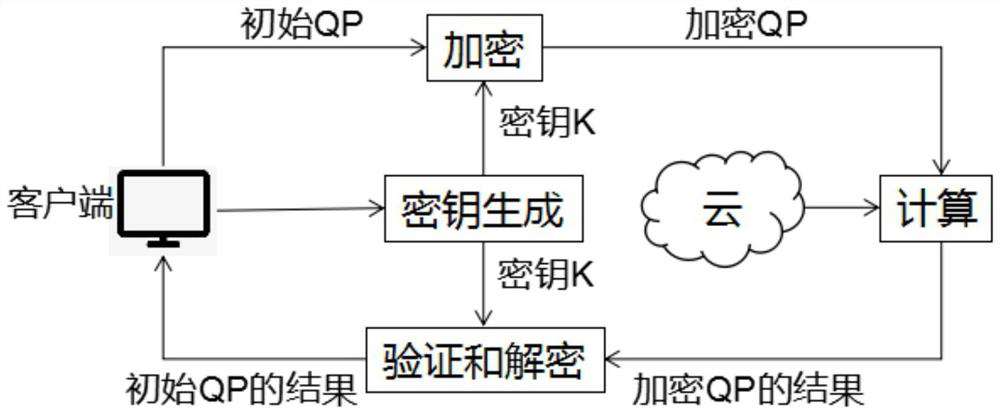
Verifiable constrained quadratic programming safety outsourcing calculation method and system
InactiveCN113271293APrivacy protectionSolve difficult problems that cannot be solved by quadratic programmingKey distribution for secure communicationOutsourcing computationCalculation methods
The invention relates to a verifiable constrained quadratic programming safe outsourcing calculation method and system.The client side can outsourcing calculation which cannot be conducted locally to a cloud server for calculation so as to reduce the calculation cost of a user, and the outsourcing process comprises the steps that firstly, the client side initializes setting, encrypts tasks needing outsourcing and sends the tasks needing outsourcing to the cloud server; then, the cloud server receives the task, performs calculation according to requirements, and returns a corresponding result to the client; and finally, the client verifies the correctness of the returned result, if the result is correct, the required original task result is obtained through decryption, otherwise, the result is refused to be accepted, and the cloud server is required to recalculate. According to the method provided by the invention, the client can solve the difficult problem which cannot be solved due to local resource limitation on the premise of protecting own data privacy. Meanwhile, the malicious behavior of the cloud server can be resisted.
Owner:SHANGHAI UNIV
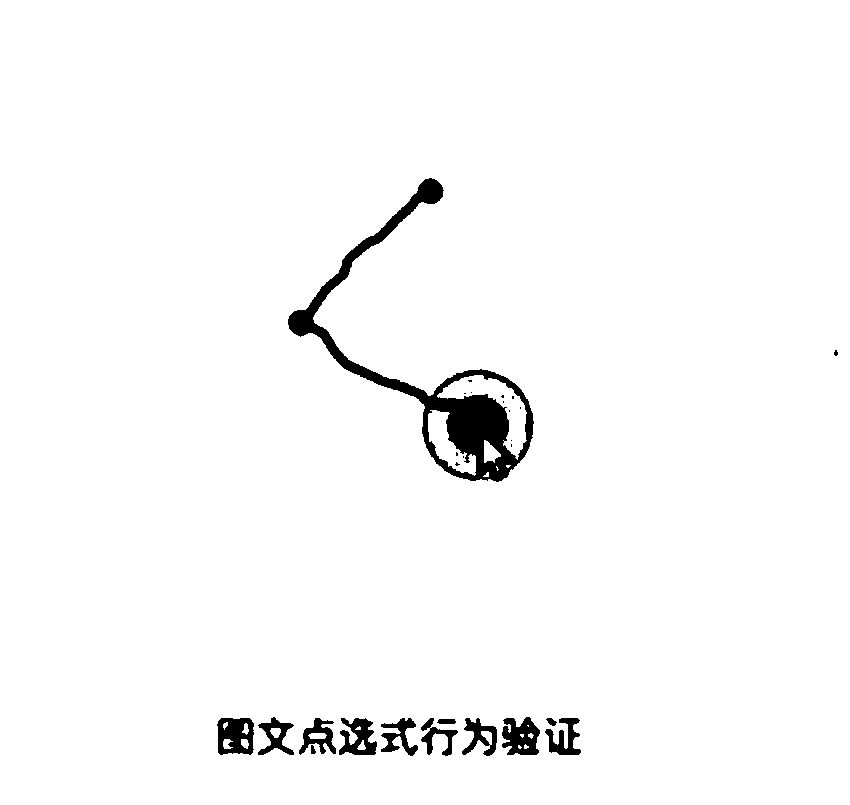
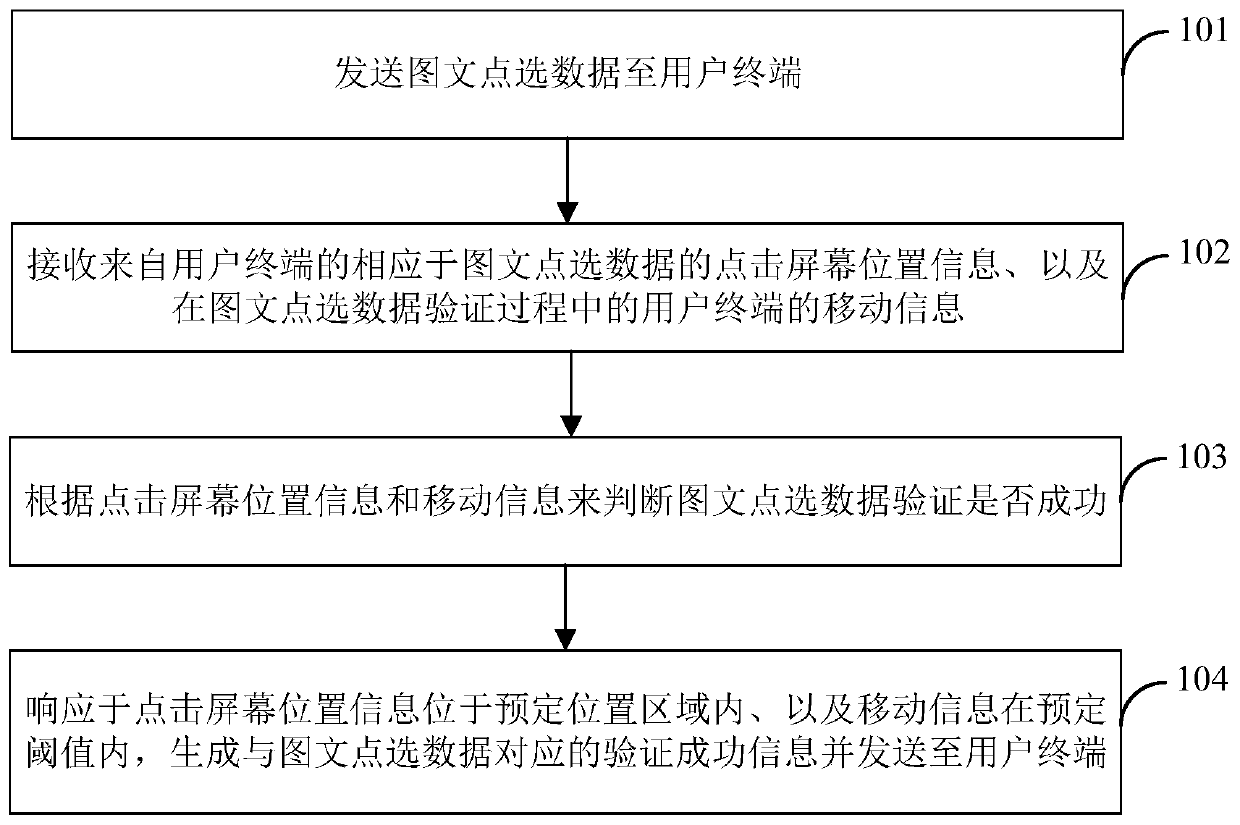
Verification method, device and system for image-text click data and mobile terminal
ActiveCN110519269APrevent Malicious BehaviorAccurate analysisPayment circuitsTransmissionData verificationReal-time computing
The invention discloses a verification method, device and system for image-text click data and a mobile terminal, and the method comprises the steps: transmitting image-text click data to a user terminal; receiving screen clicking position information corresponding to the image-text clicking data from the user terminal and movement information of the user terminal in the image-text clicking data verification process wherein the movement information comprises direction information, inclination information, rotation information and gravitational acceleration information; judging whether the image-text click data verification succeeds or not according to the click screen position information and the movement information; and in response to the fact that the click screen position information is located in the preset position area and the mobile information is located in the preset threshold, generating verification success information corresponding to the image-text click data and sendingthe verification success information to the user terminal. According to the invention, whether an operator is a person or a machine can be analyzed more accurately, and malicious behaviors of ticket refreshing through the machine or a program can be avoided.
Owner:INDUSTRIAL AND COMMERCIAL BANK OF CHINA
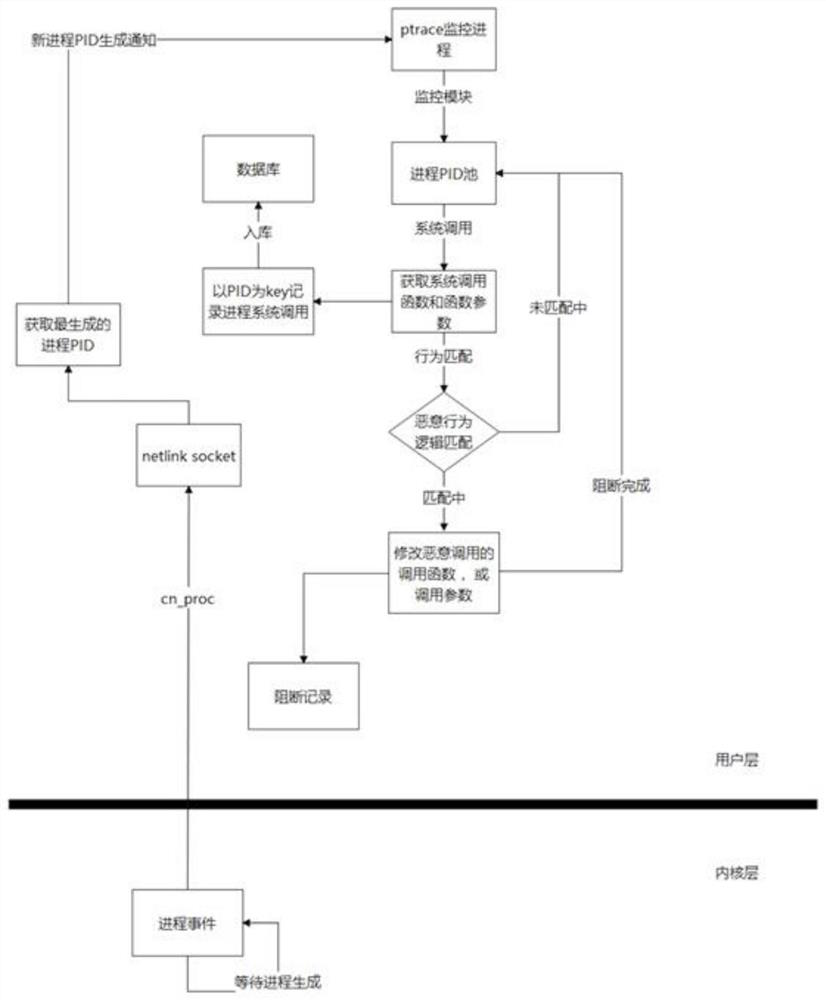
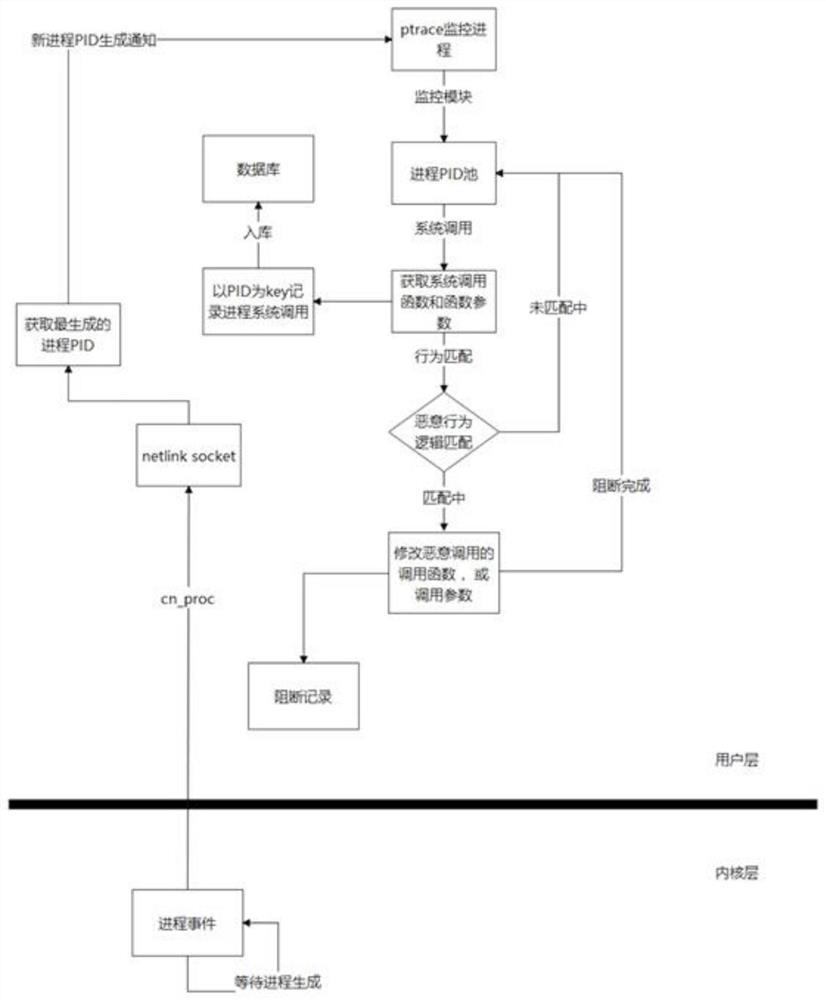
Tracking method and device for Linux application layer to monitor process generation and process behavior in real time
InactiveCN113961436AImprove fault toleranceCrash won'tHardware monitoringLinux kernelProtocol Application
The invention relates to the technical field of computers, and discloses a tracking method for a Linux application layer to monitor process generation and process behaviors in real time. The method comprises the following steps: S1, establishing a relation between the application layer and a kernel layer based on a netlink socker technology of a Linux system; S2, on the basis of netlink socker communication, obtaining events related to the process in the whole Linux system a through cn_proc, wherein process generation time exists, and then a newly-generated process PID can be obtained; and S3, then by using a ptrace technology provided by the Linux system, tracking, monitoring and specifying the newly generated process PID. According to the application layer process monitoring method, the error-tolerant rate is very high, even if the program crashes due to the internal running error of the program, the whole system crashes, the application layer monitoring process uses a connector mechanism provided by a Linux kernel, and the generation of the Linux process can be obtained by driving ten pieces through cn_proc in real time, and then the conditions of delay and inaccuracy caused by acquiring the generation condition of the Linux process by reading a / proc / PID catalog are avoided.
Owner:罗强
Security management method and device
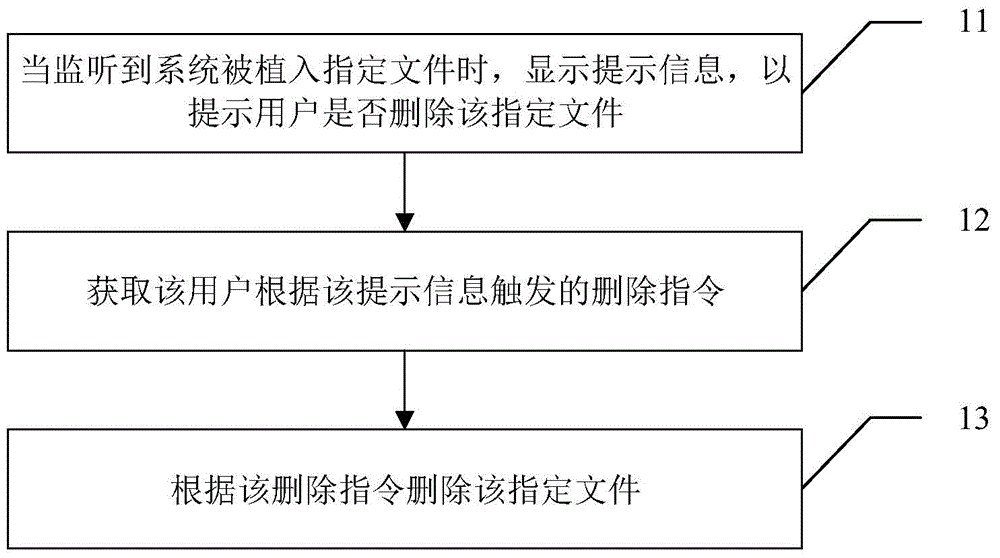
InactiveCN106203101APrevent Malicious BehaviorProtection securityPlatform integrity maintainanceComputer terminalApplication software
The invention provides a security management method applied to mobile terminals. The security management method comprises the following steps: when the fact that an assigned file is implanted into a system is monitored, a prompt message is displayed to prompt a user whether to delete the assigned file or not, wherein the assigned file is used for helping an application without a superuser permission obtain the superuser permission; a deletion instruction triggered by the user according to the prompt message is acquired; the assigned file is deleted according to the deletion instruction. Meanwhile, the invention provides a security management device. According to the security management method and device, the fact that a malicious application performs malicious acts by obtaining the superuser permission and endangers system security can be effectively prevented.
Owner:BEIJING ERENEBEN INFORMATION TECH
Automatic safety detection method for mobile application
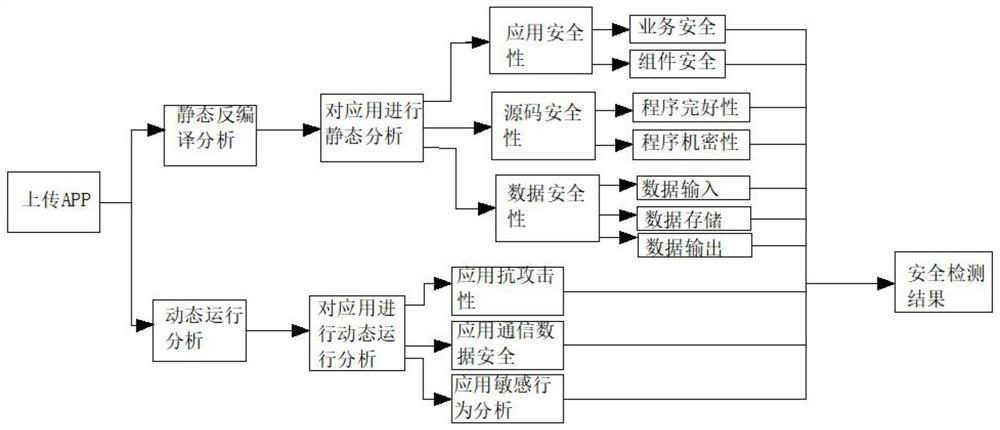
PendingCN113360905APrevent being piratedStable market returnsPlatform integrity maintainanceData integrationSystems engineering
The invention discloses an automatic safety detection method for mobile applications. The method comprises the following steps: S1, selecting an APP sample needing to be detected; s2, performing static analysis on the APP program file; s3, analyzing related data integration conditions in the APP program, and checking whether the related data integration conditions accord with vulnerability conditions or not with a public CVE vulnerability library; s4, the APP program is installed on the mobile phone; s5, running the APP program on the mobile phone, and monitoring sensitive behavior sources and communication data in the mobile phone so as to discover whether the APP program has sensitive behaviors and whether the communication data is safe; s6, illegal operation is conducted on the APP program, and whether the APP program has the corresponding defense capacity or not is judged. According to the method, great convenience can be provided for developers, certain manpower, material resource cost and time cost can be saved for the developers, and great economic benefits are brought to the developers.
Owner:上海蛮犀科技有限公司
Blockchain fragment enabling knowledge graph file storage method
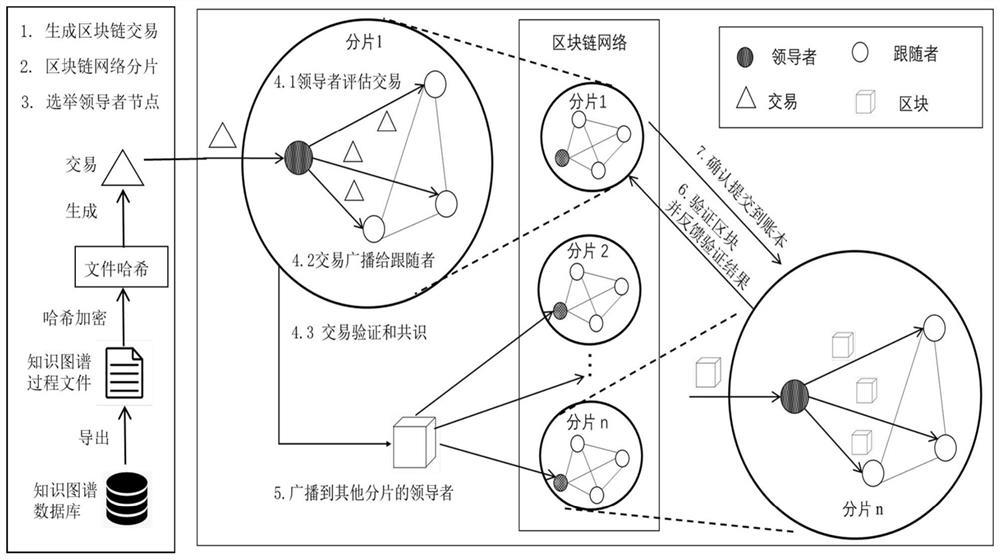
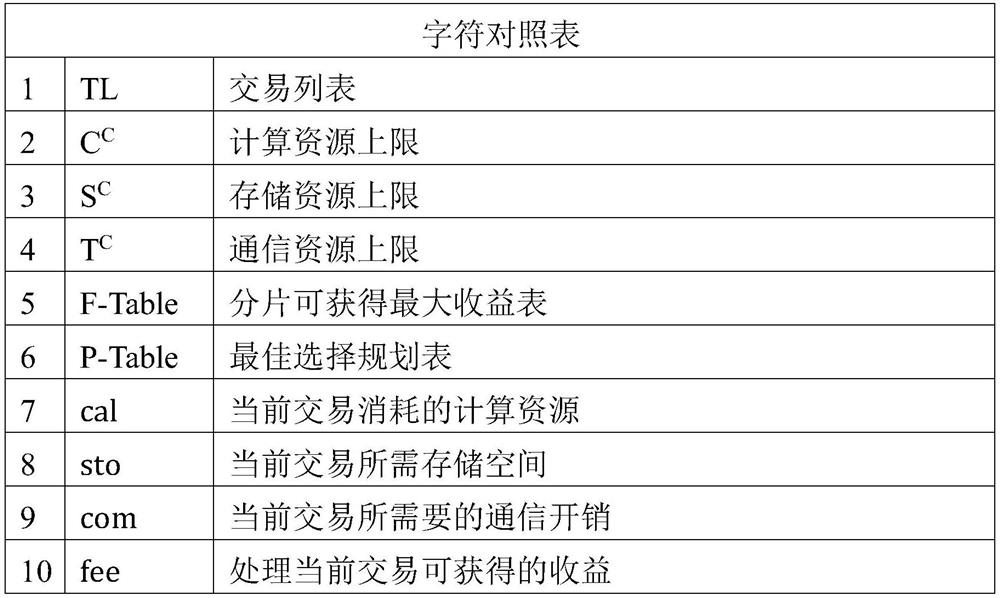
PendingCN113626875APrevent Malicious BehaviorEnsure transaction securityDatabase distribution/replicationDigital data protectionSafe storageDynamic programming
The invention relates to a blockchain fragment enabling knowledge graph file storage method, and belongs to the technical field of blockchain application. According to the method, the knowledge graph file is stored in the blockchain, so that the problems of safe storage and traceability of the knowledge graph construction file are solved. When a reasoning error or a file security problem occurs in the knowledge graph, the corresponding process file can be obtained from the blockchain according to a demand, and a repetitive construction process can be avoided. The method is based on an inter-fragment communication confirmation mechanism, and double-pattern attacks aiming at different fragments are prevented. Through a random verification function, asset mortgage and an improved practical Byzantine fault-tolerant mechanism, malicious behaviors of nodes are prevented, and transaction security in fragments is ensured. According to the method, the throughput of a blockchain system is improved by adopting an optimized fragmentation scheme, and under multiple constraint conditions, an optimal transaction selection scheme is given based on a dynamic programming algorithm to maximize the income of the fragmentation, so that efficient and reasonable transaction fragmentation is realized.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
Arrangement of blockchains with restricted transaction
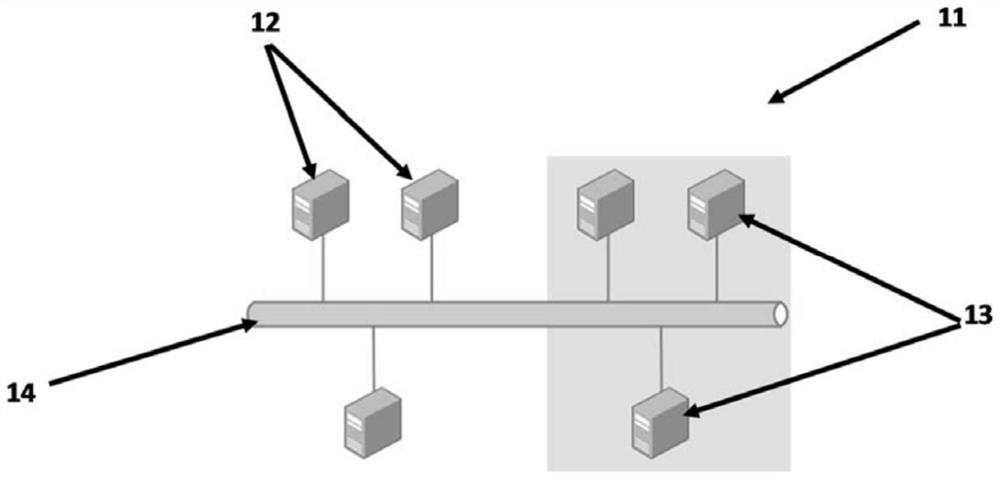
PendingCN112654972AEliminate redundant resourcesHigh impedanceDigital data information retrievalAnonymous user systemsTelecommunications networkEngineering
An arrangement of blockchains configured to distribute simultaneously at least one public transaction and / or one restricted transaction, where the arrangement includes a plurality of participant nodes (12) and a plurality of validator nodes (13) connected via a telecommunications network (14); where a proponent participant node (12) is configured to send to all the validator nodes (13) the content of a tx information transaction register, together with the identifier of a certain preset privacy group; to provide the blockchain system which distributes information transaction register blocks with anonymity and privacy capabilities; in such a way that at least one receiving participant node (12) connected to a blockchain network (11) is capable of deciphering, reading and executing the information transaction register blocks encrypted by the validator or mining nodes (13) of the blockchain network (11).
Owner:全基金银行独资有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com