Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
32results about How to "Increase the cost of cracking" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
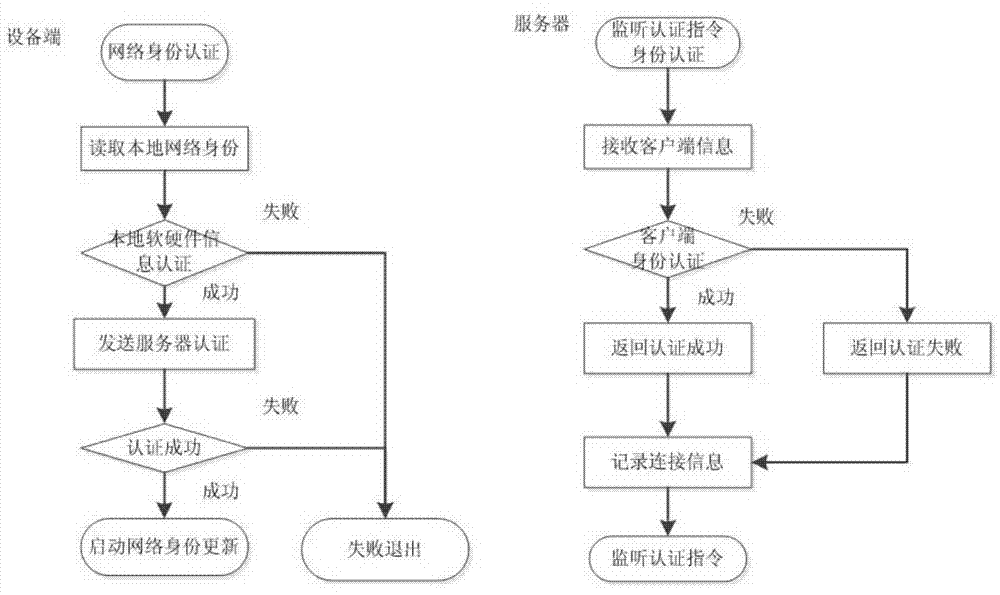
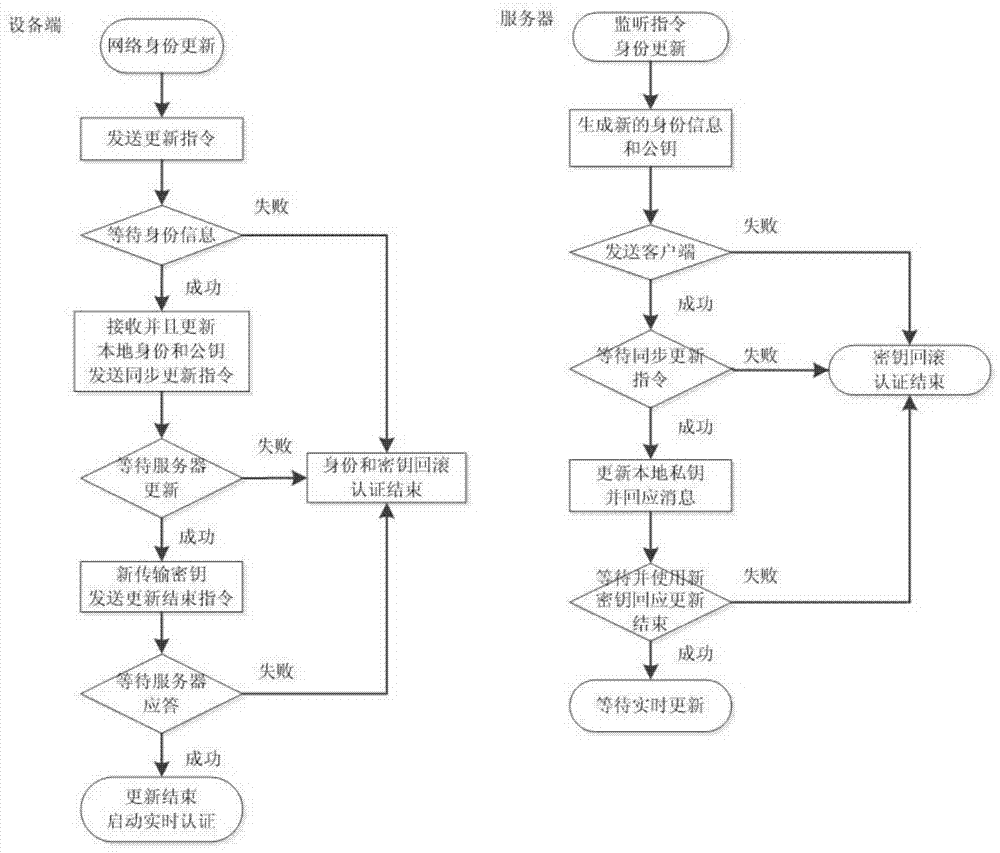
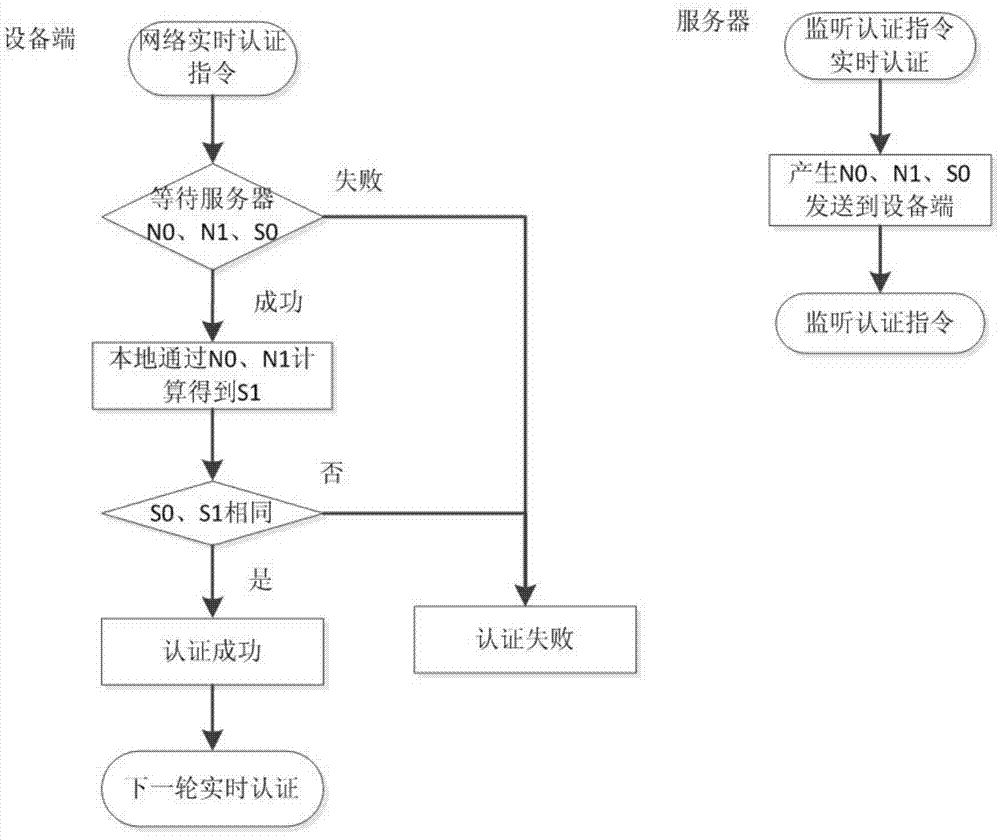
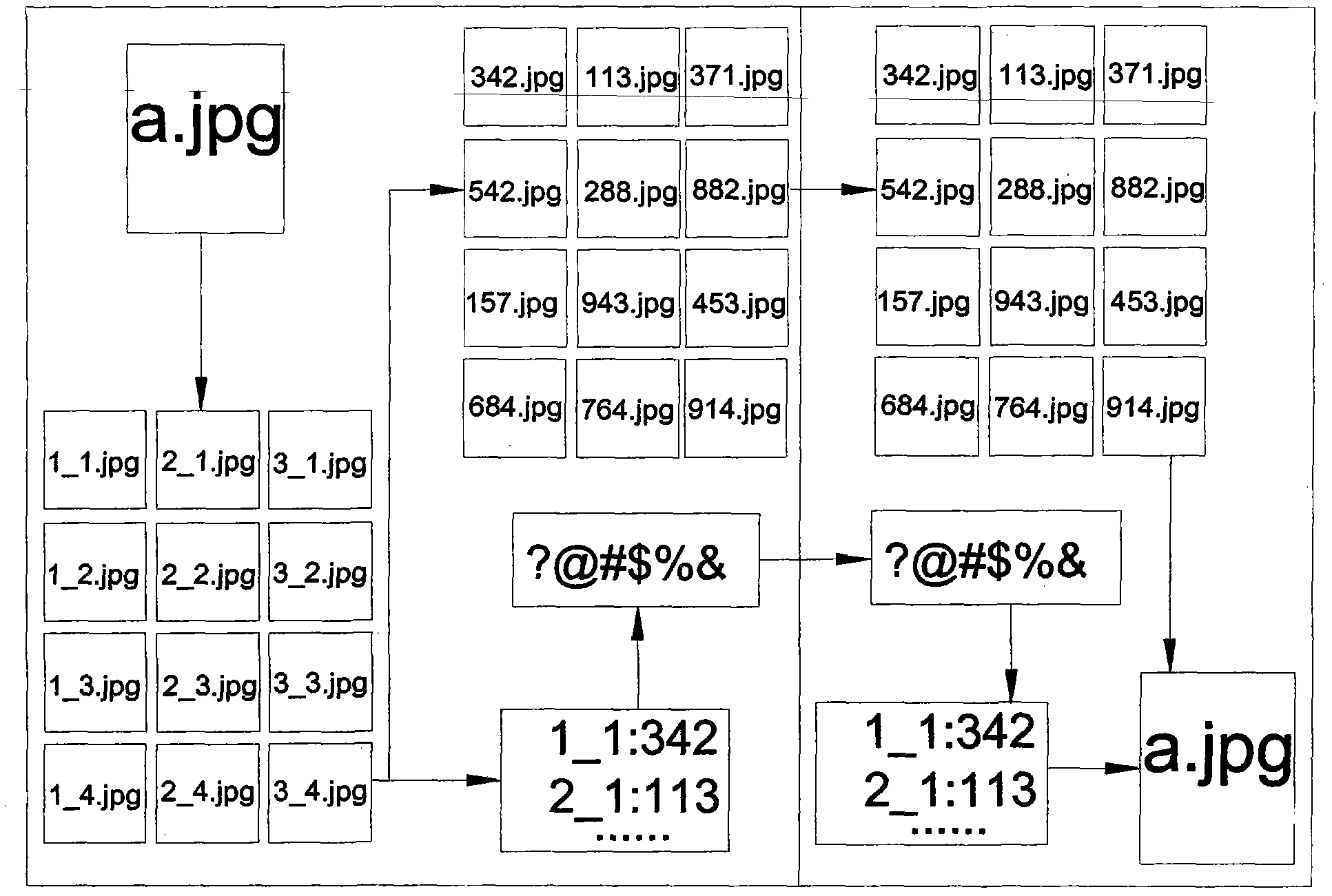
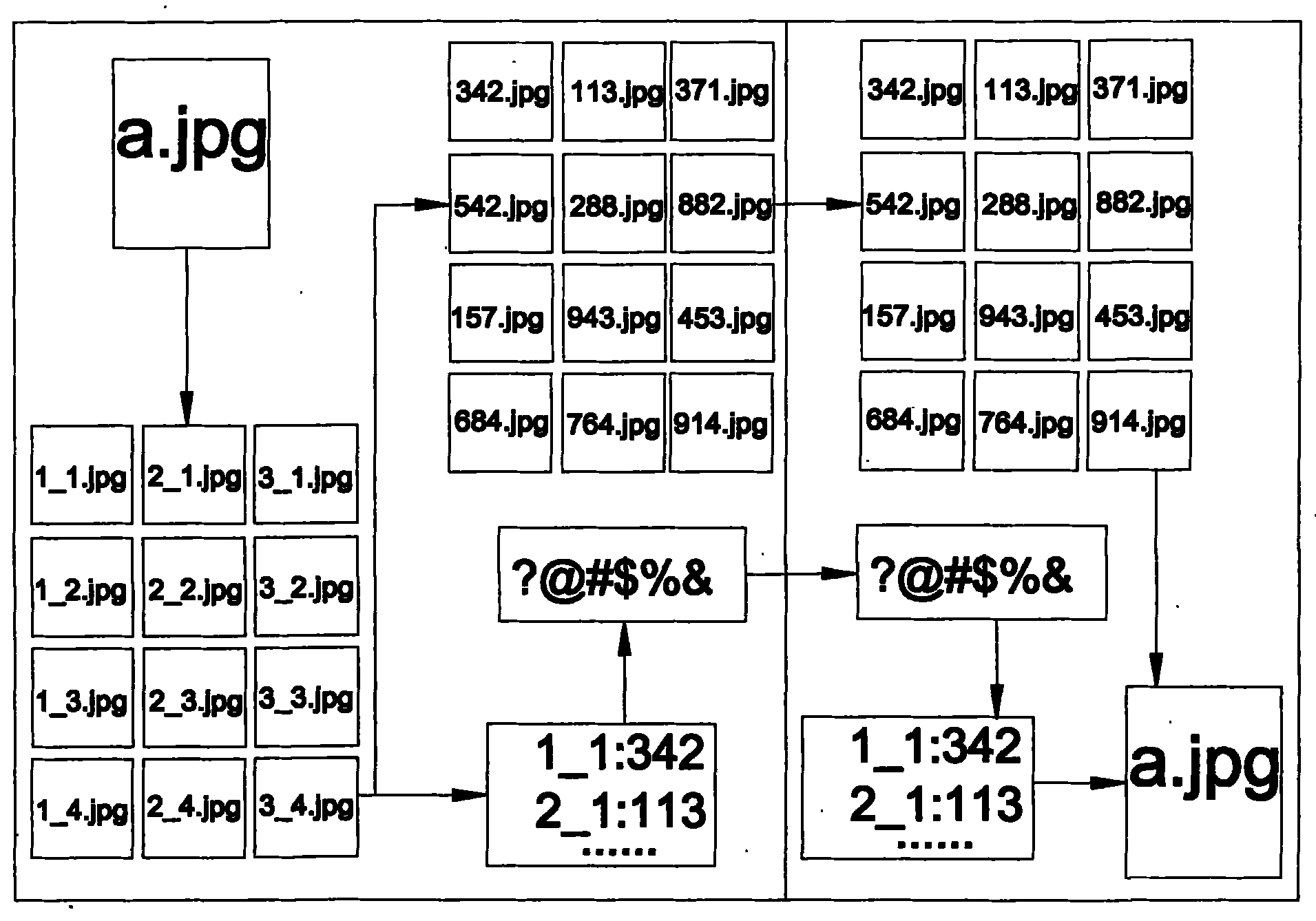
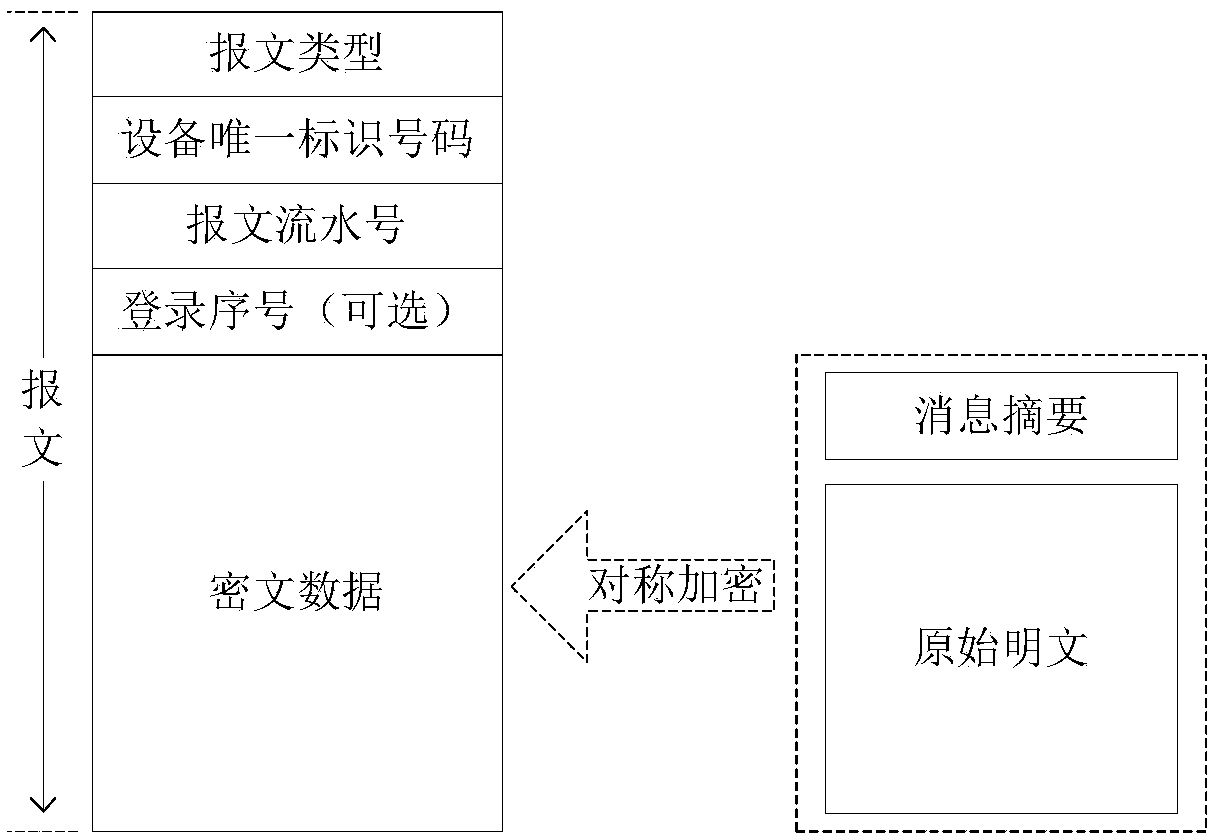
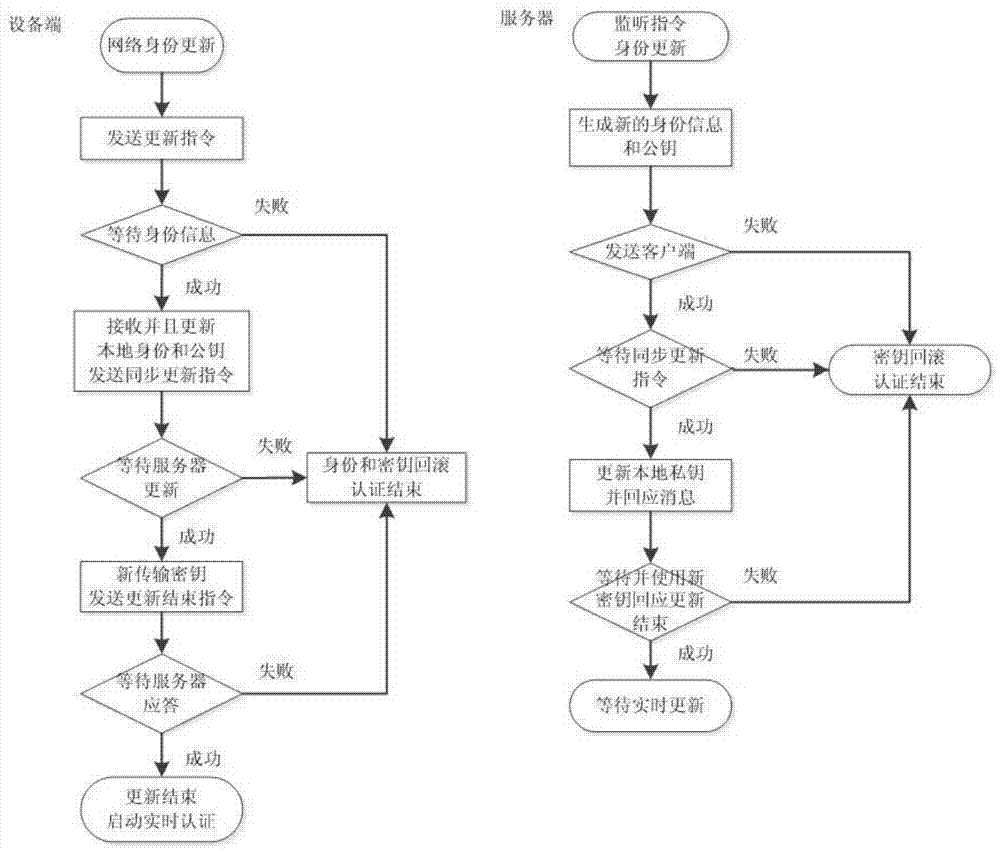
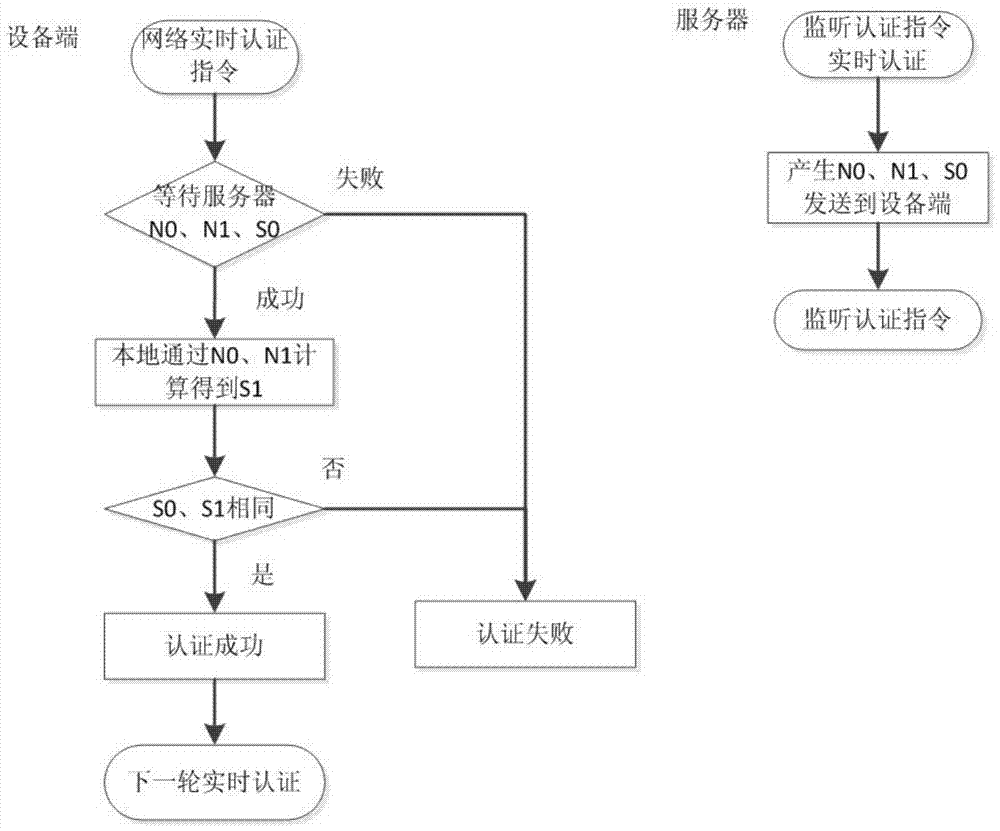
Network authentication method and system based on data link encryption transmission
ActiveCN104125239AIncrease the cost of crackingPrevent link snoopingSecuring communicationNetwork keyData monitoring
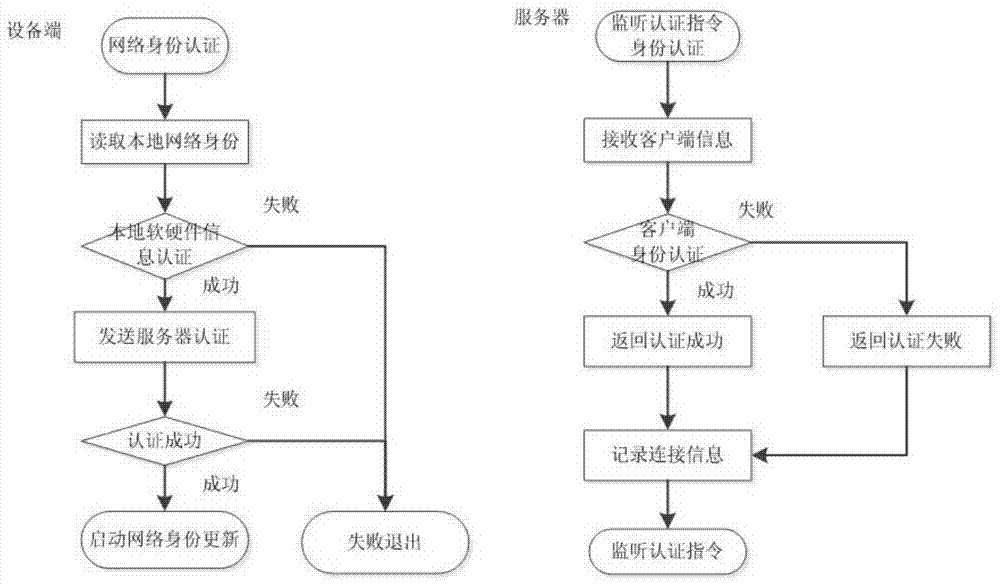
The invention relates to a network authentication method and system based on data link encryption transmission. The method is characterized in that the network link data are encrypted by the asymmetric algorithm and then transmitted, which avoids network monitoring and input; the network identity information is the specific device hardware and software information and has the uniqueness; a network key and the identity information are updated during starting the network authentication, in order to limit the ageing cycle of the network transmission key and the identity information; the symmetric encryption algorithm is carried out for random authentication, namely, real-time authentication, and thereby, the difficulty at breaking the data monitoring is raised, and transferring the device to other place to operate after the identity is authenticated successfully is effectively prevented. With the adoption of the method and system, the link can be effectively prevented from being monitored, and authentication files are prevented from releasing and spreading; once the authentication files are released and used and a legal user feeds back timely, a server can timely find out the device network information of a device end.
Owner:RUN TECH CO LTD BEIJING
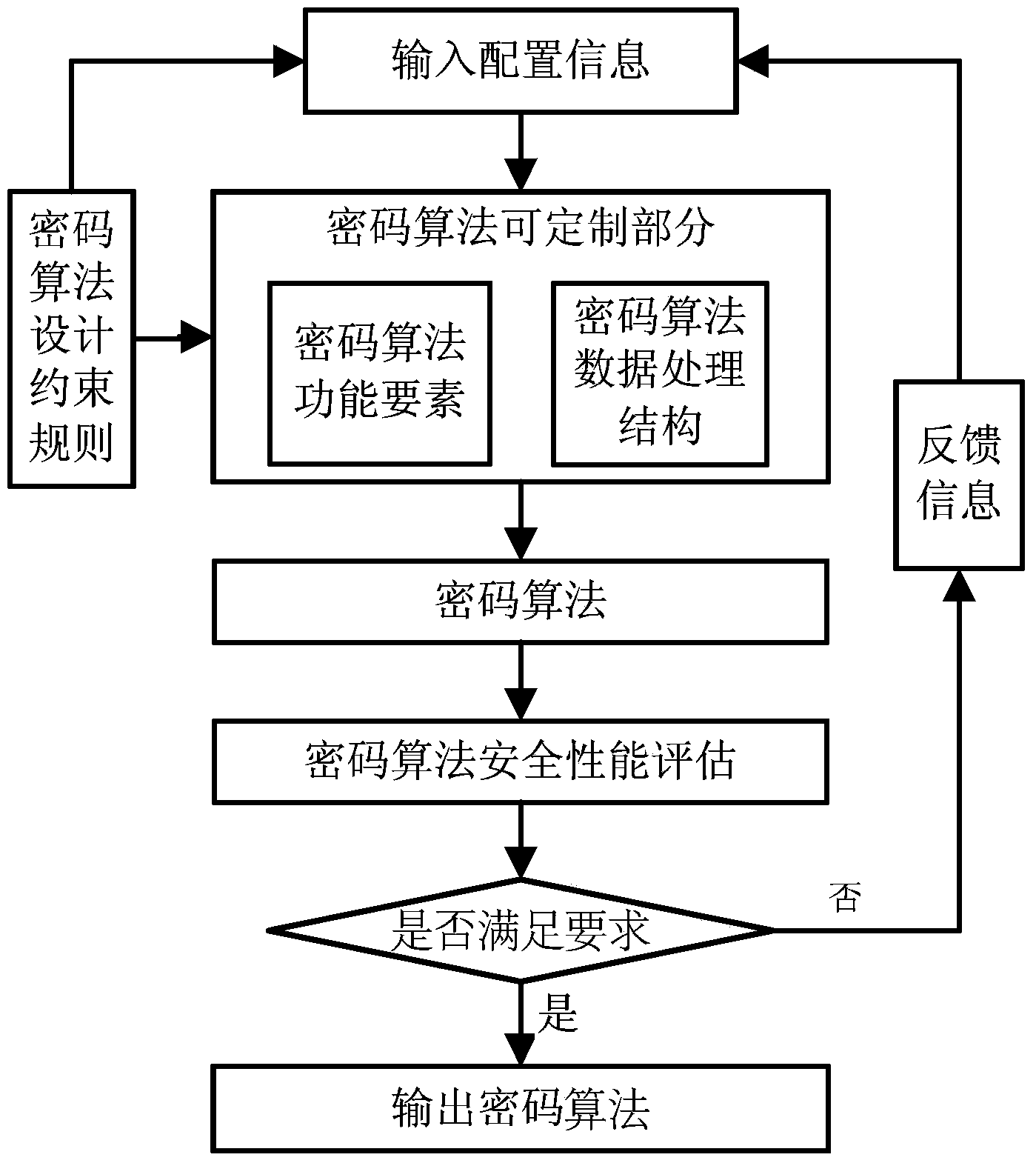
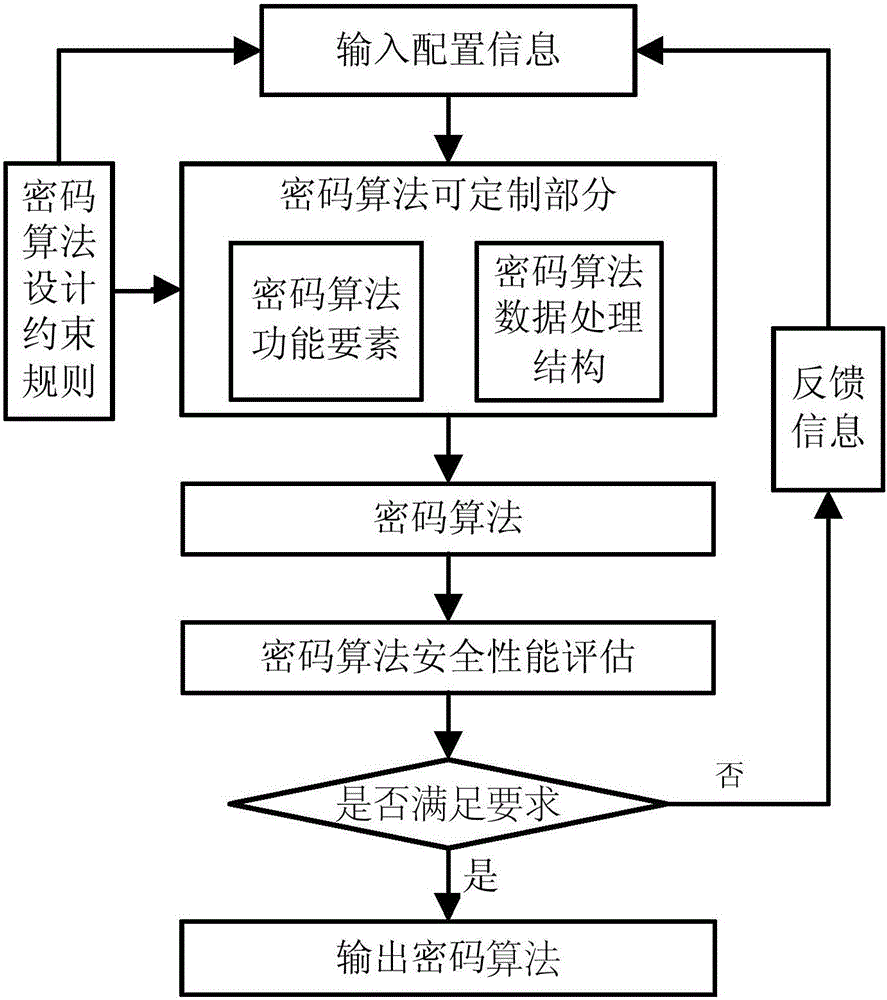
Cryptographic algorithm customizing method
ActiveCN104052595AReduce development cost and difficultyIncrease the cost of crackingSecuring communicationAssessment methodsData processing
The invention discloses a cryptographic algorithm customizing method. The cryptographic algorithm customizing method is characterized in that a customizable cryptographic algorithm functional element, a variable cryptographic algorithm data processing structure, a cryptographic algorithm design constraint rule and a cryptographic algorithm safety assessment method are provided, based on the cryptographic algorithm design constraint rule, the cryptographic algorithm functional element and the cryptographic algorithm data processing structure are specifically configured by a user, so that a customized cryptographic algorithm is obtained, a set of cryptographic algorithm safety assessment method is used for conducting safety assessment on the customized cryptographic algorithm, and if the assessment result meets the algorithm design requirement, the obtained cryptographic algorithm is a target cryptographic algorithm; otherwise, configuration information is adjusted, a novel customized cryptographic algorithm is produced again, and the safety is assessed until the customized cryptographic algorithm meets the design requirement. By the adoption of the method, the safety customized cryptographic algorithm can be efficiently designed by the user.
Owner:戴葵
Protection method suitable for multimedia data files in portable system
InactiveCN102214282AEnsure safetyAdjustable security levelProgram/content distribution protectionData fileWorkstation
The invention relates to a protection method suitable for multimedia data files in a portable system, comprising the following steps of: performing safety processing on multimedia files at non-portable computer system terminals (for example, computer devices with high performance, including desktop computers, servers, working stations, high-performance embedded computers and the like); downloading the processed result in a portable system terminal; and reducing the multimedia files by the portable system terminal. The protection method has the beneficial effects that: a plurality of types and formats of multimedia files in a portable system can be efficiently protected, the safety degree is adjustable, the computation workload is low, and the cracking difficulty is high.
Owner:苏州海客科技有限公司
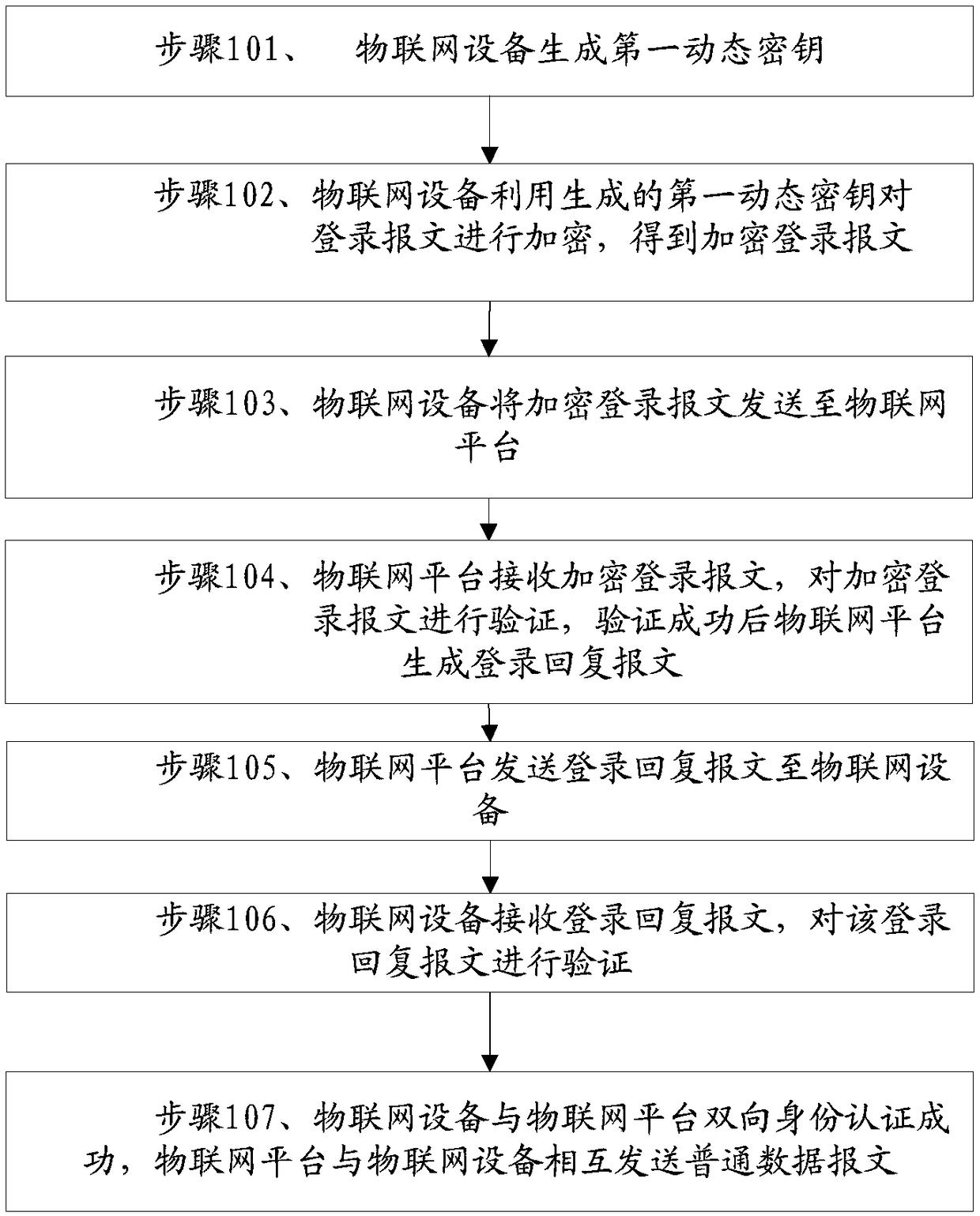
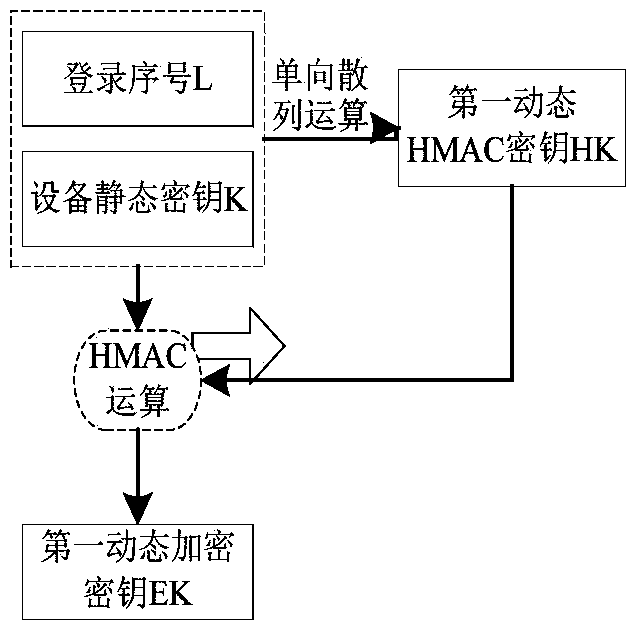
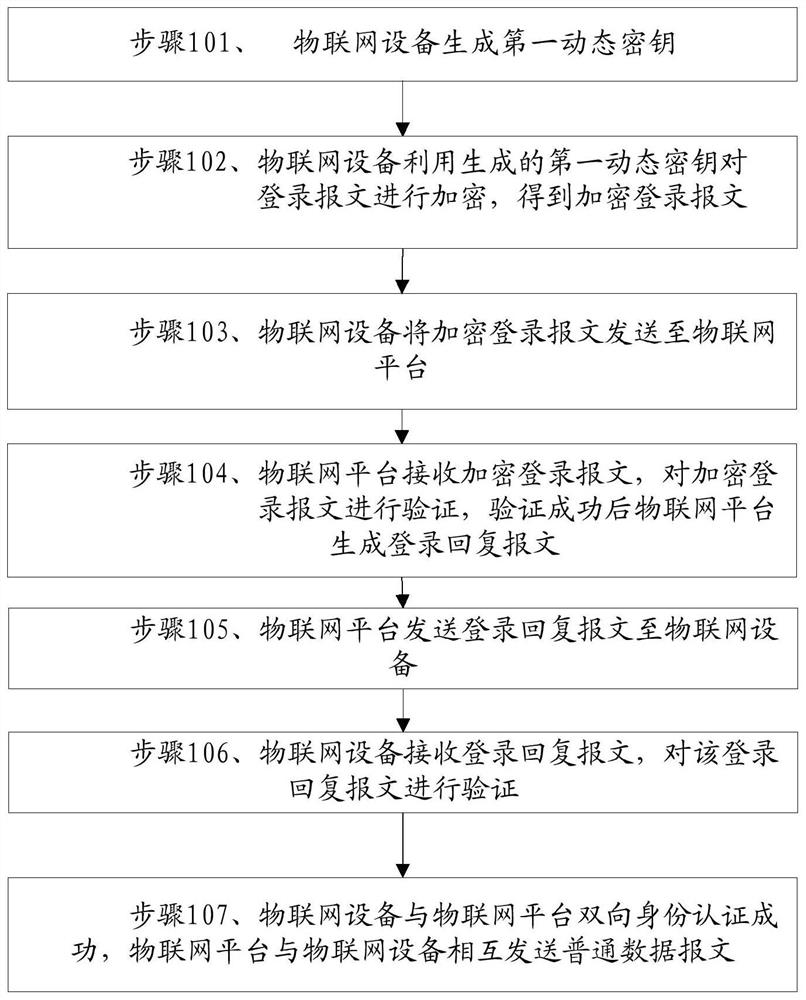
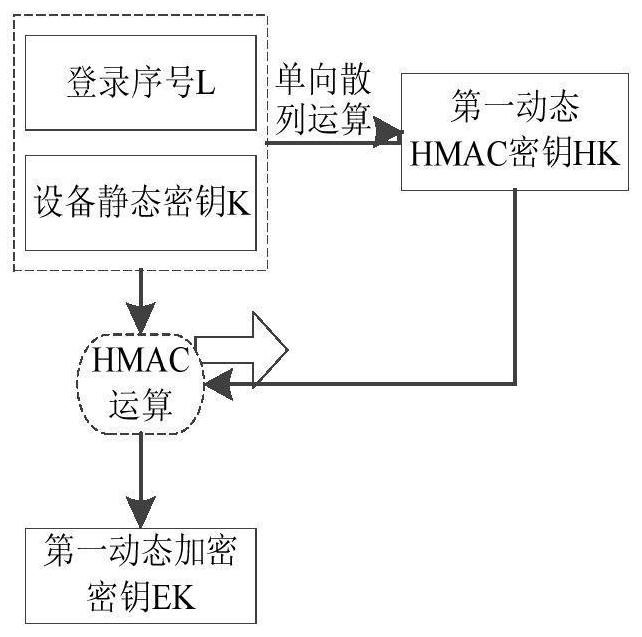
Dynamic encryption method for Internet of Things device based on login serial number
ActiveCN109361520ALow costReduce power consumptionKey distribution for secure communicationUser identity/authority verificationThe InternetSerial code
The application discloses a dynamic encryption method for an Internet of Things device based on a login serial number. The method includes steps: the Internet of Things device generates a first dynamic secret key; the Internet of Things device encrypts a login message by employing the generated first dynamic secret key and obtains an encrypted login message; the Internet of Things device transmitsthe encrypted login message to an Internet of Things platform; the Internet of Things platform receives and verifies the encrypted login message, and generates a login reply message after verification; the Internet of Things platform transmits the login reply message to the Internet of Things device; the Internet of Things device receives and verifies the login reply message; and bidirectional identity authentication of the Internet of Things device and the Internet of Things platform is successful, and the Internet of Things platform and the Internet of Things device mutually transmit ordinary data messages. According to the method, the pseudo-random dynamic secret key is generated through a static secret key and the login serial number of the Internet of Things device, and the securityof communication between the Internet of Things device and the Internet of Things platform is improved.
Owner:TAIHUA WISDOM IND GRP CO LTD
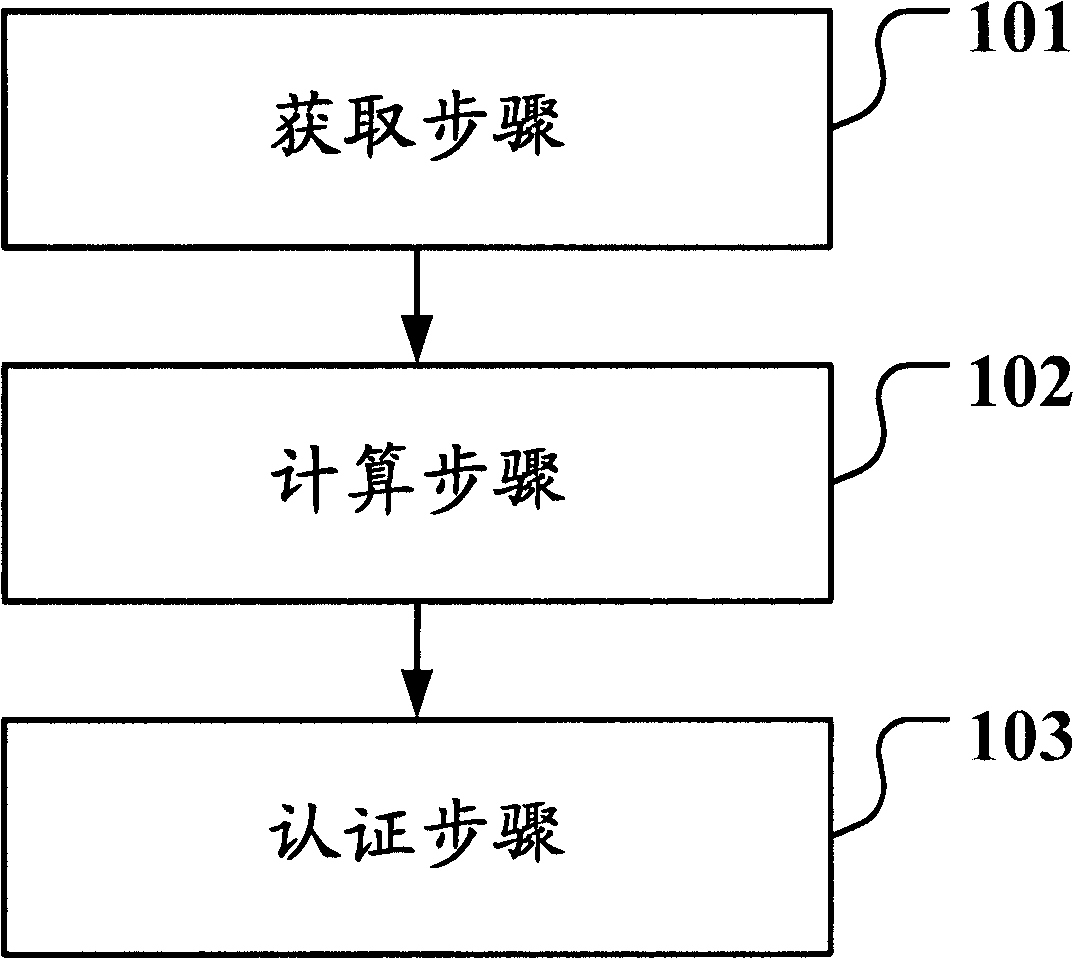
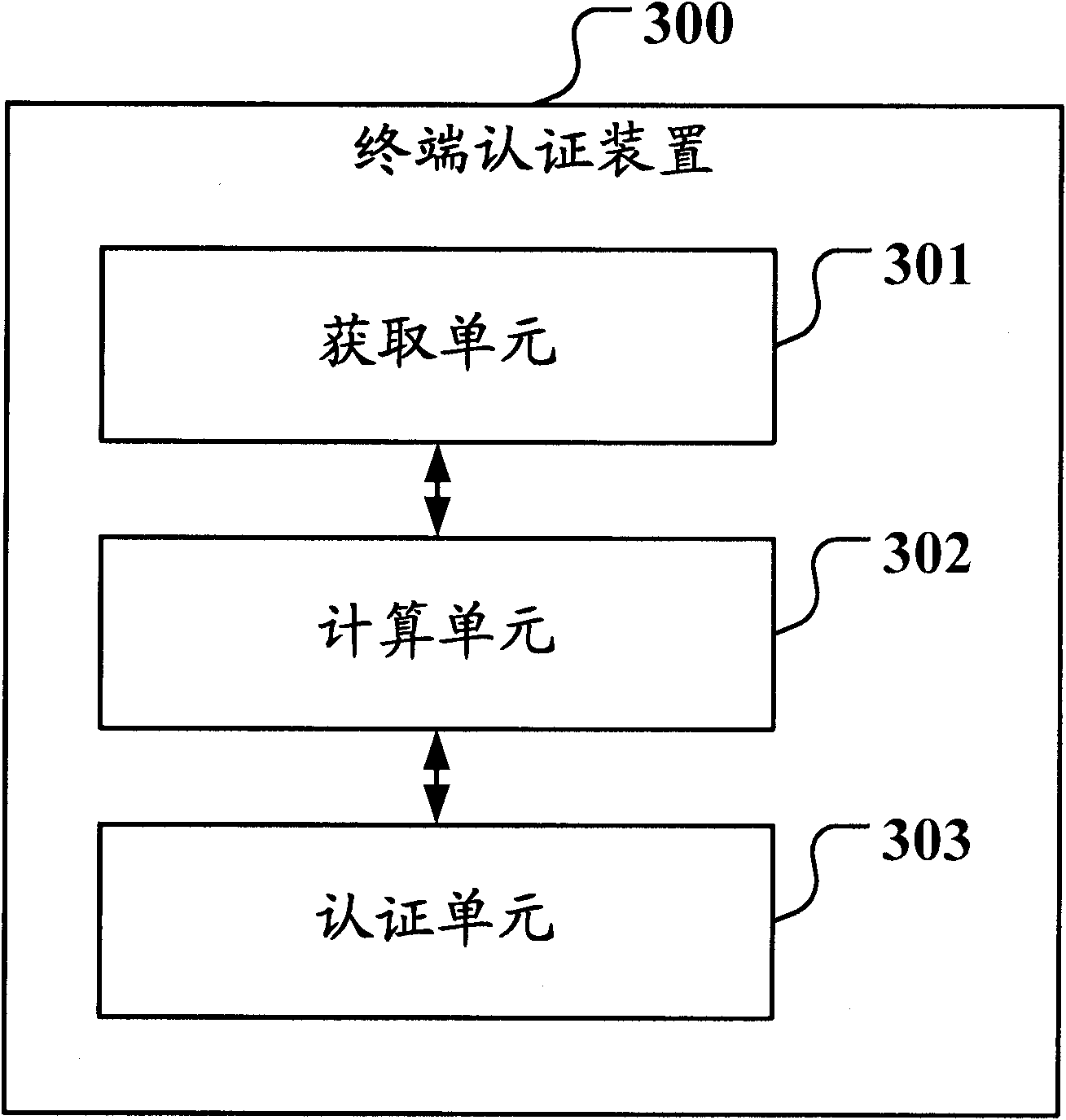
Method and device for authenticating terminal as well as EOC (Ethernet over Coax) terminal
InactiveCN102137074APrevent imitationLow costData switching by path configurationEthernet over coaxTerminal cost
The invention relates to a method and device for authenticating a terminal as well as an EOC (Ethernet over Coax) terminal. The method for authenticating the terminal comprises the following steps of: acquirement: acquiring characteristic domain information of the EOC terminal and first encryption control domain information which is prestored in the EOC terminal and generated according to a preset key and encryption algorithm based on the characteristic domain information; calculation: generating second encryption control domain information according to the preset key and encryption algorithm based on the characteristic domain information; and authentication: judging whether the first encryption control domain information and the second encryption control domain information accord with the preset authentication passing rule or not, allowing the EOC terminal to pass the authentication if the first encryption control domain information and the second encryption control domain information accord with the authentication passing rule; or otherwise, not allowing the EOC terminal to pass the authentication. The invention can achieve the purpose of carrying out the authentication control on the terminal on the basis of not increasing the terminal cost.
Owner:NEW H3C TECH CO LTD
High-expansibility password encrypted storage method
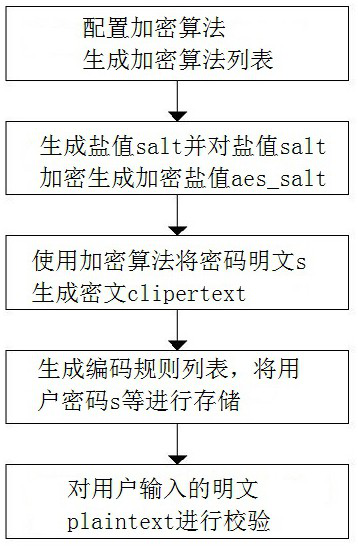
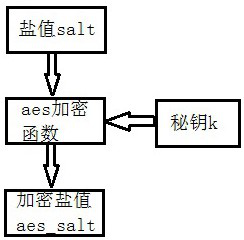
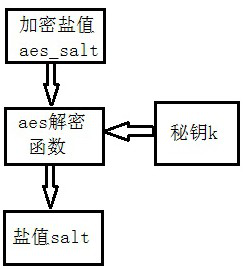
ActiveCN111984978AIncrease the difficultyIncrease the cost of crackingDigital data protectionDigital data authenticationCiphertextPassword
The invention provides a high-expansibility encrypted storage method. Different encryption algorithms are configured, salt value encryption is performed on salt values of the encryption algorithms once, and then encoding rules are set to realize storage of plaintext passwords, ciphertext passwords, salt values, encrypted salt values and the like of a user, so that password encrypted storage with high security, high transportability and high maintainability is realized. According to the method, the diversity of a password storage encryption algorithm is expanded, the salt value and the passwordare subjected to dual encryption and then coded and stored, meanwhile, interference factors are increased, and the password cracking difficulty is greatly increased. Meanwhile, a user-defined encryption algorithm, a password storage coding rule and a specified noise factor position and length are supported, so that the complexity and diversity of a password storage scheme can be flexibly improved. Meanwhile, the scheme is friendly to system upgrading and data migration, and the upgrading and extension of the system can be well met.
Owner:CHENGDU DBAPP SECURITY
Encryption method and system based on information transmission
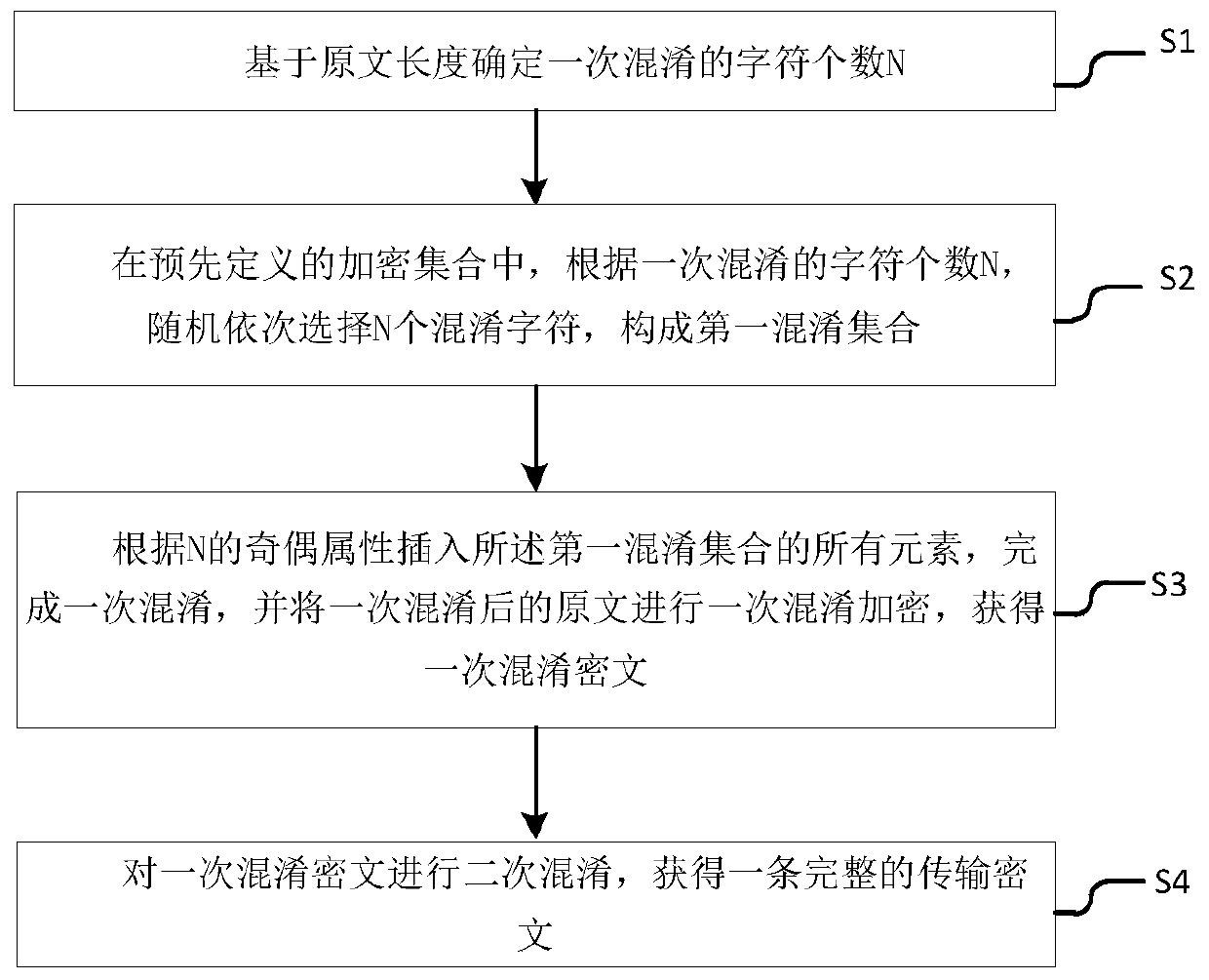
InactiveCN110474932AIncrease the cost of crackingReduce dependenceTransmissionComputer hardwareObfuscation
The invention provides an encryption method and system based on information transmission. The encryption method comprises the steps: determining the number N of characters confused once based on the length of an original text; in a predefined encryption set, randomly and sequentially selecting N confused characters according to the number N of the characters confused once to form a first confusedset; inserting all elements of the first obfuscated set according to odd-even attributes of N to finish one-time obfuscation, and performing one-time obfuscation encryption on the original text afterone-time obfuscation to obtain a one-time obfuscated ciphertext; and carrying out secondary obfuscation on the primary obfuscated ciphertext to obtain a complete transmission ciphertext. The encryption method disturbs the attacker by adopting the multiple obfuscation strategies, so that the cracking cost of the attacker is increased; depending on a universal base64 algorithm and a random number algorithm, the encryption method is suitable for parameter transmission of various scenes; and compared with other technologies, the scheme is less in dependence and lighter in weight.
Owner:NAT COMP NETWORK & INFORMATION SECURITY MANAGEMENT CENT
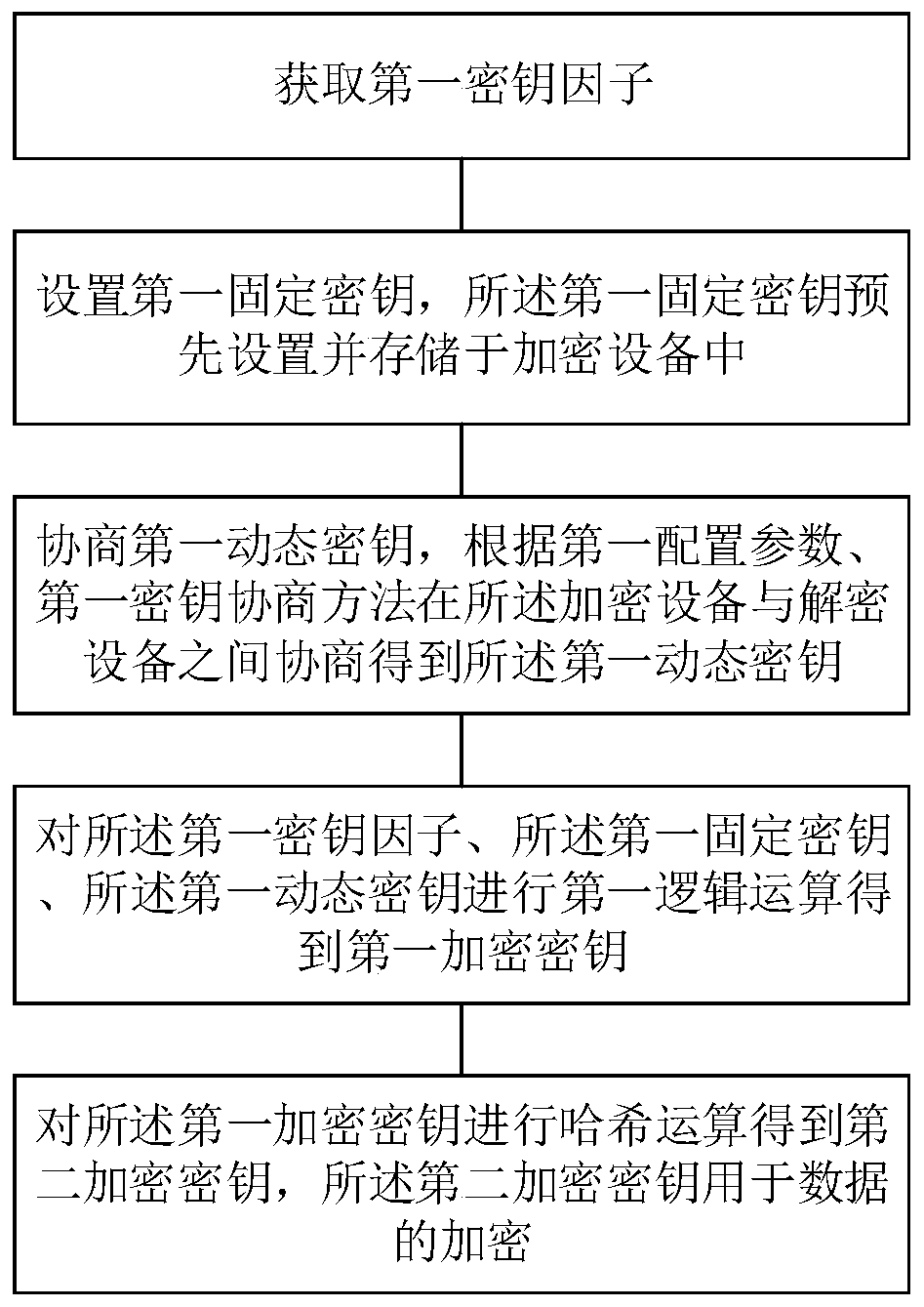
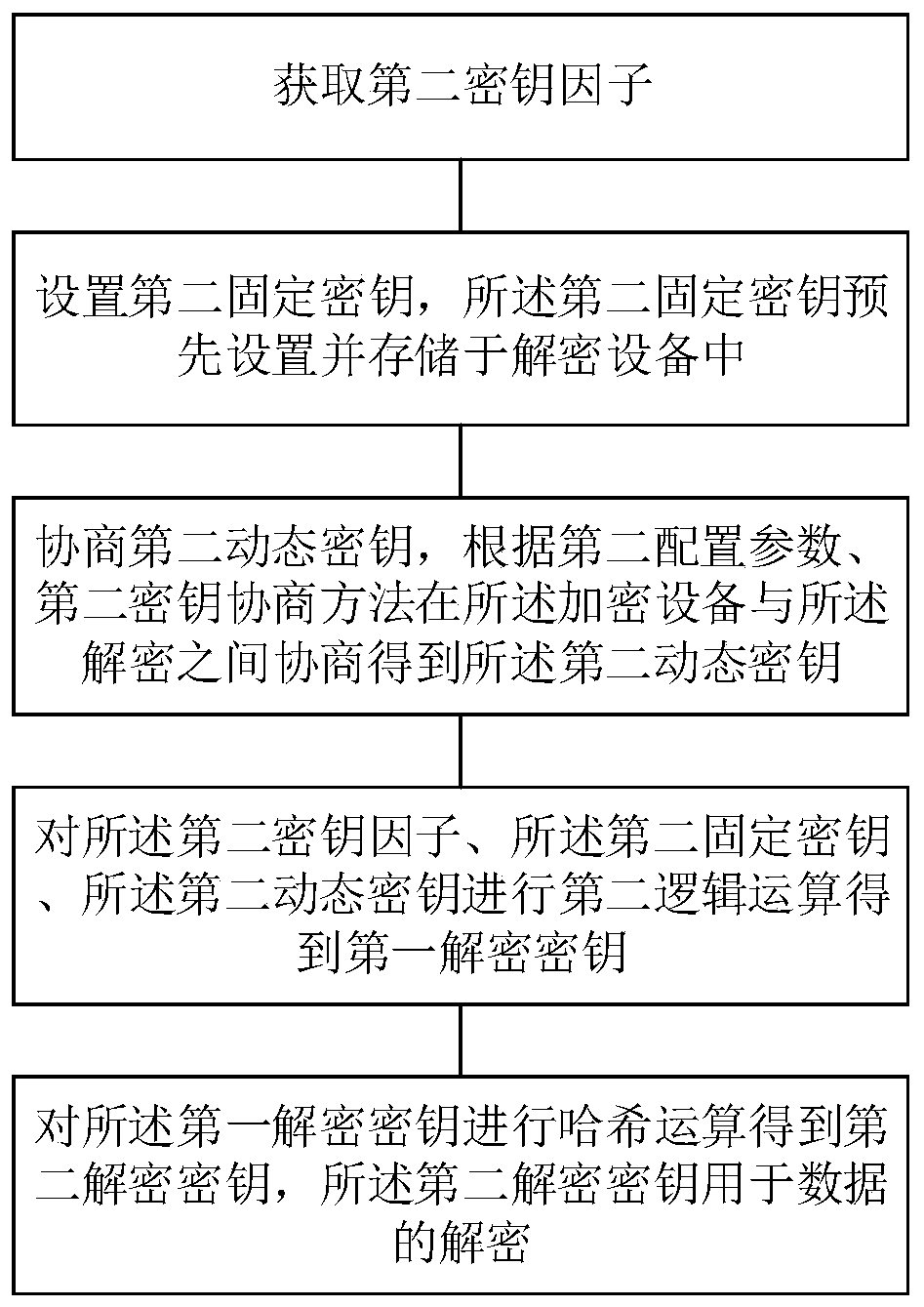
Encryption key generation and encryption method, decryption key generation and decryption method
PendingCN110798316AIncreased complexityImprove securityKey distribution for secure communicationMultiple keys/algorithms usageCryptographic key generationEngineering
The invention discloses an encryption key generation method, an encryption method, a decryption key generation method and a decryption method. The encryption key generation method comprises the following steps: acquiring a first key factor; setting a first fixed key, wherein the first fixed key is preset and stored in the encryption equipment; negotiating a first dynamic key, and negotiating between the encryption equipment and the decryption equipment by the first key negotiation method according to the first configuration parameter to obtain the first dynamic key; performing first logical operation on the first key factor, the first fixed key and the first dynamic key to obtain a first encryption key; and performing hash operation on the first encryption key to obtain a second encryptionkey, wherein the second encryption key is used for encrypting data. According to the encryption key generation method provided by the invention, one-packet-one-key are realized, the complexity of theencryption key is high, the security of data transmission is improved, the cracking difficulty is improved, the generated encryption key does not need to be repeatedly set in the data transmission, and the network data transmission performance is ensured.
Owner:西安瑞思凯微电子科技有限公司
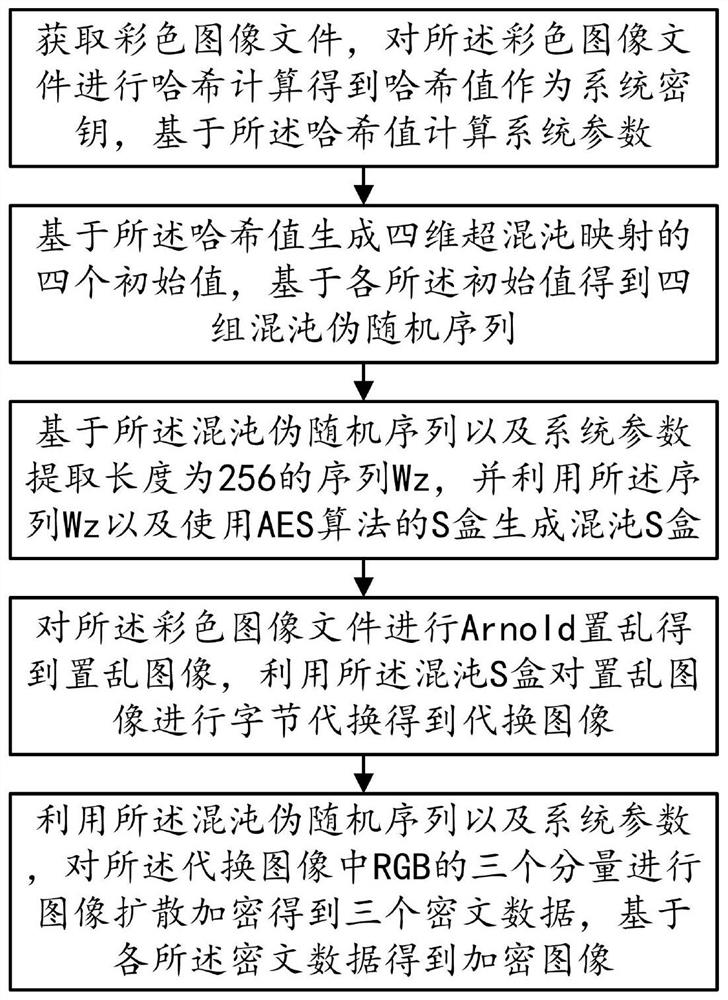
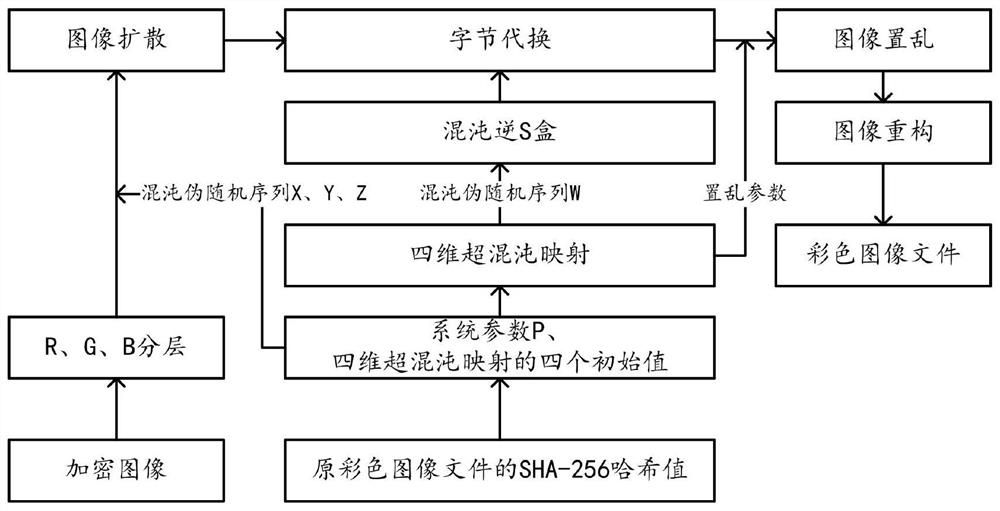
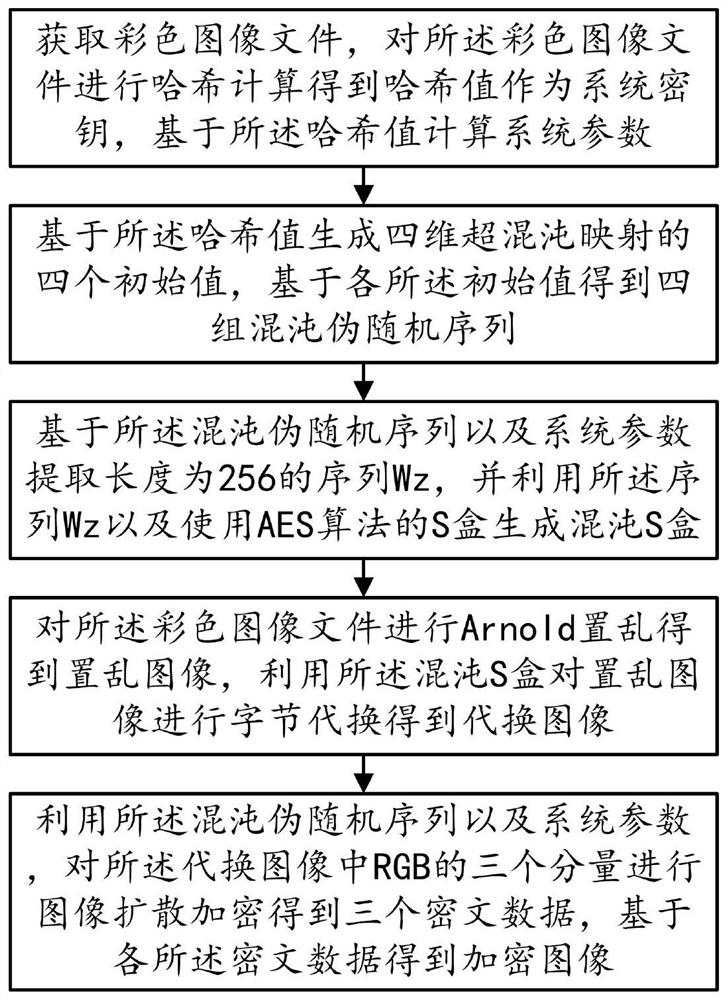
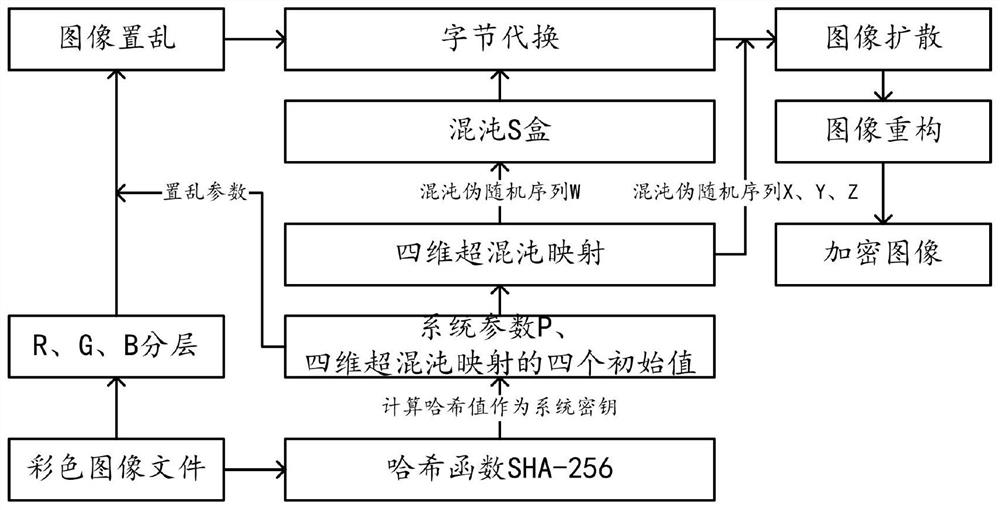
Image encryption method based on chaotic mapping and chaotic S-box substitution
ActiveCN112906043AImprove relevanceAvoid crackingDigital data protectionImage data processing detailsColor imageS-box
The invention provides an image encryption method based on chaotic mapping and chaotic S-box substitution in the technical field of image encryption, and the method comprises the steps: S10, obtaining a color image file, carrying out the Hash calculation, obtaining a Hash value, and calculating a system parameter based on the Hash value; step S20, generating four initial values of four-dimensional hyper-chaotic mapping based on the Hash values, and further obtaining four groups of chaotic pseudo-random sequences; s30, extracting a sequence Wz based on the chaotic pseudo-random sequence and system parameters, and generating a chaotic S box by using the sequence Wz and the S box using the AES algorithm; step S40, performing Arnold scrambling on the color image file to obtain a scrambled image, and performing byte substitution on the scrambled image by using a chaos S box to obtain a substituted image; and S50, performing image diffusion encryption on the three components of the RGB in the substitution image by using the chaos pseudo-random sequence and the system parameters to obtain three pieces of ciphertext data, and obtaining an encrypted image based on each piece of ciphertext data. The method has the advantage that the security of image encryption is greatly improved.
Owner:HUAQIAO UNIVERSITY
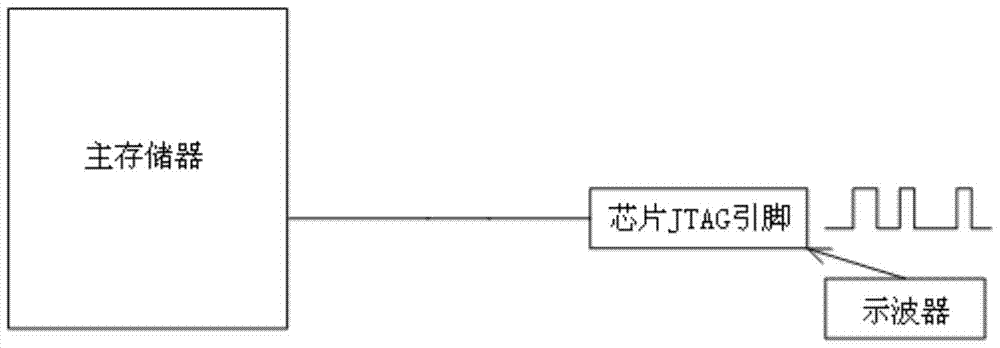
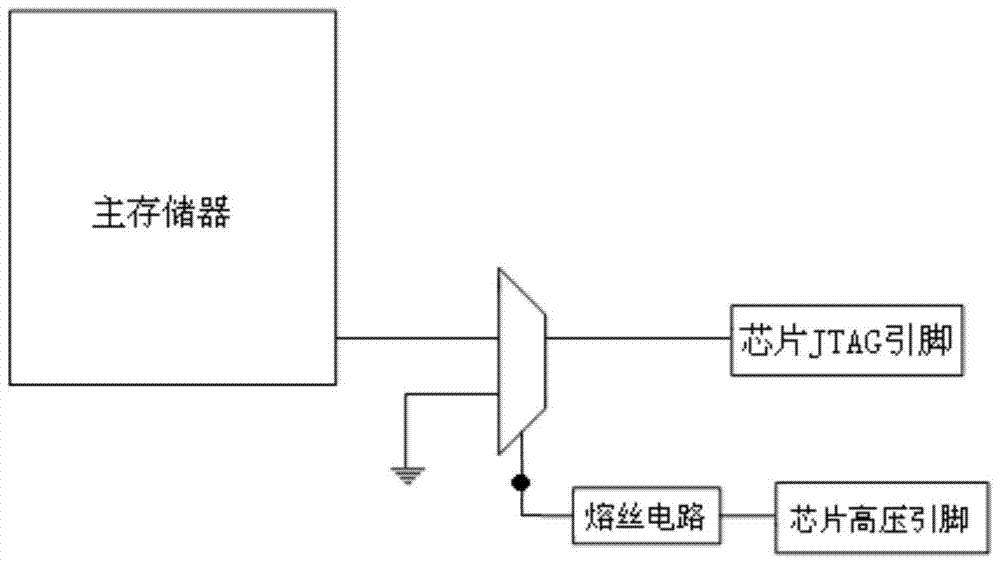
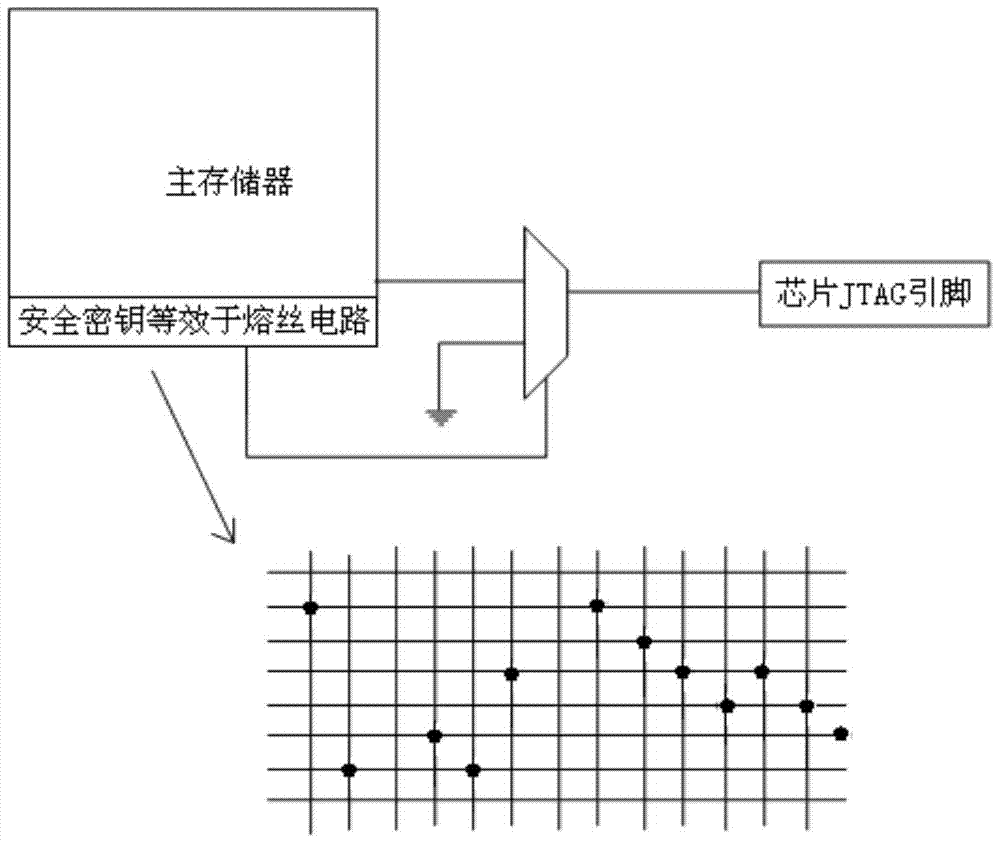
Method and circuit for realizing mcu security
ActiveCN104777761BImprove securityReduce power consumptionProgramme control in sequence/logic controllersPower-on resetElectricity
The invention discloses a method for realizing the safety of an MCU (micro controller unit). After the MCU is power-on, a main reset signal in an MCU chip is set to '1' by utilizing a power supply monitoring circuit, then an RC oscillation circuit in the MCU chip is started, and a power-on reset adaptive circuit is started at the same time; the power-on reset adaptive circuit immediately reads a 128-bit security key stored in a safety position of an Flash; the security key is stored in a password matching circuit and then the main reset signal is released; a JTAG (joint test action group) debugging interface is in an off state by default; after the MCU chip works, the password matching circuit starts working; when a password is externally input, the password matching circuit is used for performing matching confirmation on the password and the security key, and after matching is confirmed to be correct, the JTAG debugging interface is on, or otherwise, erasing the whole MCU chip. The invention further discloses a circuit for realizing the safety of the MCU. The method and the circuit can improve the safety of the ultra-low-power MCU and greatly increase the cracking cost of an invader.
Owner:SHANGHAI HUAHONG INTEGRATED CIRCUIT
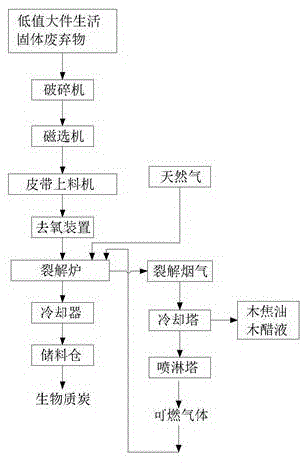
Low-value large solid waste treatment method and device
InactiveCN105618465ALow costSolve the problem of classified collection, classified transportation and final classified processingSolid waste disposalFurniture waste recoveryIron removalResource utilization
The invention discloses a low-value large solid waste treatment method and device. The treatment method comprises smashing and iron removal, deoxidation, pyrolysis and gas-oil phase separation. The treatment device comprises a solid waste supply system, a smashing and iron removal system, a belt feeding machine, deoxidation equipment, a pyrolysis furnace and a recovery system, which are connected in sequence. According to the device and the method provided by the invention, low-value large solid waste, especially foam-containing waste, such as abandoned desks, chairs, stools and sofas, is treated by means of smashing, carbonization and pyrolysis, so that at a collection station of low-value large solid waste, the problems about quantity reduction, harmlessness and resource utilization can be solved, and meanwhile the problems about collecting and transporting the waste separately and finally treating the waste separately are solved. Therefore, the problem that waste is classified at first and then is combined in waste classification is solved from the source, and the costs of waste landfill and incineration are greatly saved.
Owner:SHENZHEN GREEN ENERGY ENVIRONMENTAL SCI & TECH CO LTD
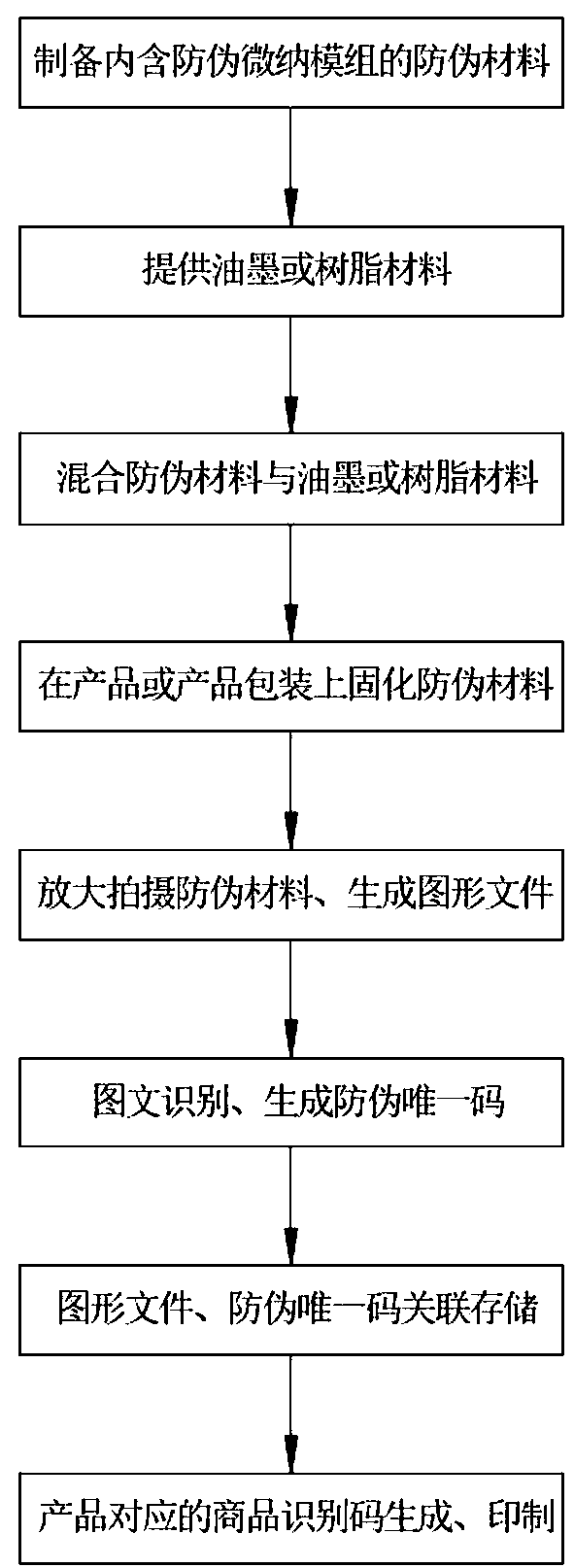
Method for generating anti-counterfeiting unique code and performing anti-counterfeiting authentication
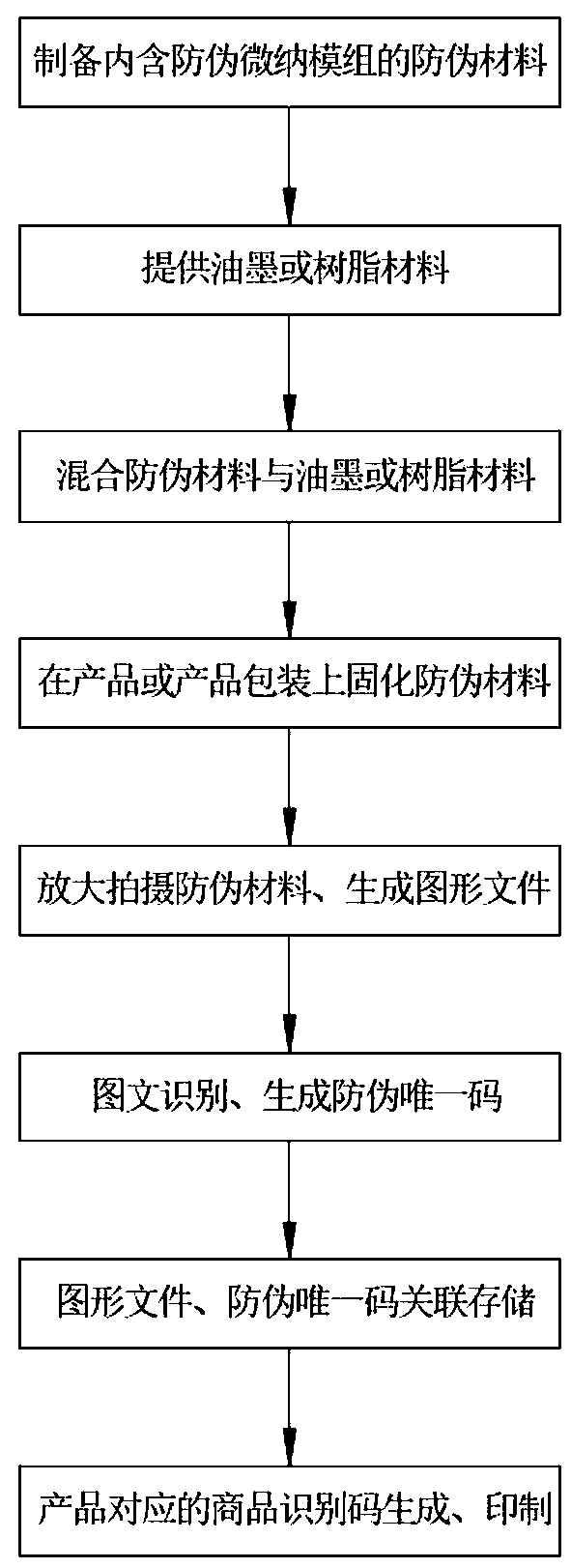
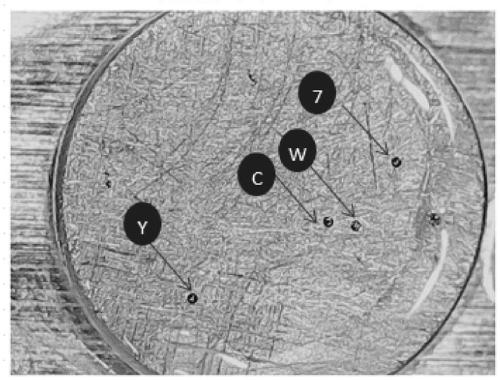
ActiveCN108154207AAvoid repetitionUniqueness guaranteedCommerceRecord carriers used with machinesImage contentComputer hardware
The invention discloses a method for generating an anti-counterfeiting unique code and performing anti-counterfeiting authentication. The method includes: generating the anti-counterfeiting unique code, to be more specific, preparing an anti-counterfeiting material, printing and solidifying the anti-counterfeiting material onto a product or a product package, shooting an anti-counterfeiting imagefile in a magnifying manner, performing storage and transmission, performing automatic identification by an image-text identification system, automatically generating and storing the anti-counterfeiting unique code, and generating and printing a commodity identification code; performing anti-counterfeiting authentication, wherein the anti-counterfeiting authentication is performed by scanning thecommodity identification code, inquiring an authenticity inquiry system, directly magnifying and observing the image content of the anti-counterfeiting material for rechecking and the like. The methodhas the advantages that multiple anti-counterfeiting measures are set during the generating of the anti-counterfeiting unique code, a multiple anti-counterfeiting authentication function is achieved,and counterfeiting preventing and authentication are linked with each other; anti-counterfeiting authentication manners are diversified, mutual corroboration of the different anti-counterfeiting authentication manners can be achieved, reverse copying and cracking is difficult, and good anti-counterfeiting performance is achieved; the method is convenient to use and especially suitable for the reliable counterfeiting preventing of high-value commodities in the intelligent Internet era.
Owner:福州固钛光电科技有限公司
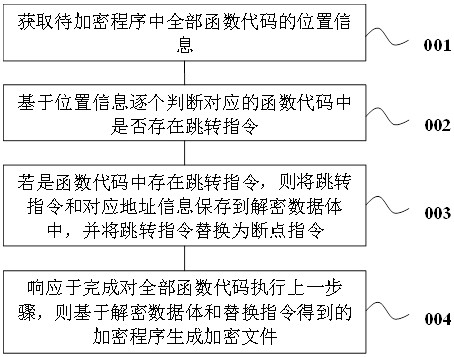
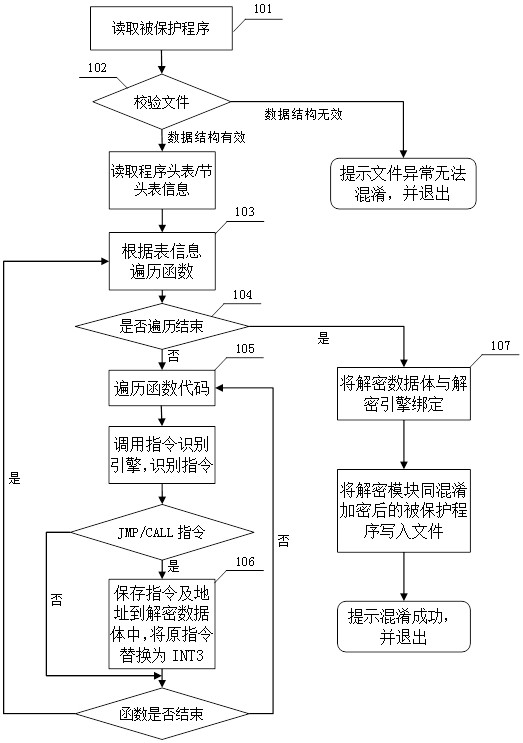
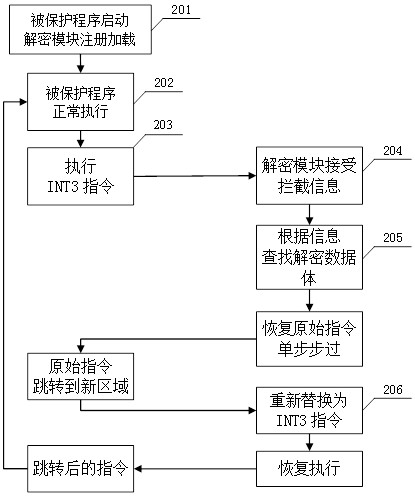
Code obfuscation encryption method and device, equipment and readable medium
ActiveCN113569269AHigh strengthImprove securityDigital data protectionProgramming languageTheoretical computer science
The invention discloses a code obfuscation encryption method. The method comprises the following steps: acquiring position information of all function codes in a to-be-encrypted program; judging whether jumping instructions exist in the corresponding function codes one by one based on the position information; if the jump instruction exists in the function code, storing the jump instruction and corresponding address information into a decrypted data body, and replacing the jump instruction with a breakpoint instruction; and in response to the completion of executing the previous step on all the function codes, generating an encrypted file based on an encryption program obtained by the decrypted data volume and the replacement instruction. The invention further discloses a code obfuscation encryption device, computer equipment and a readable storage medium. The original program process is disassembled through instruction replacement, and the encrypted and protected program is allowed to dynamically restore and disassemble the code during operation, so that the problem that the program is cracked due to the fact that a cracker stores the complete program code is prevented, and the security of the program is improved.
Owner:INSPUR SUZHOU INTELLIGENT TECH CO LTD
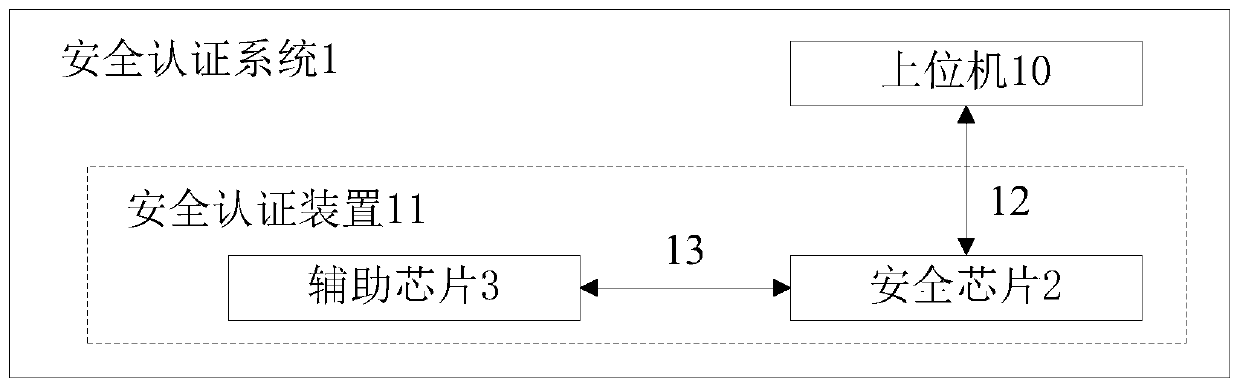
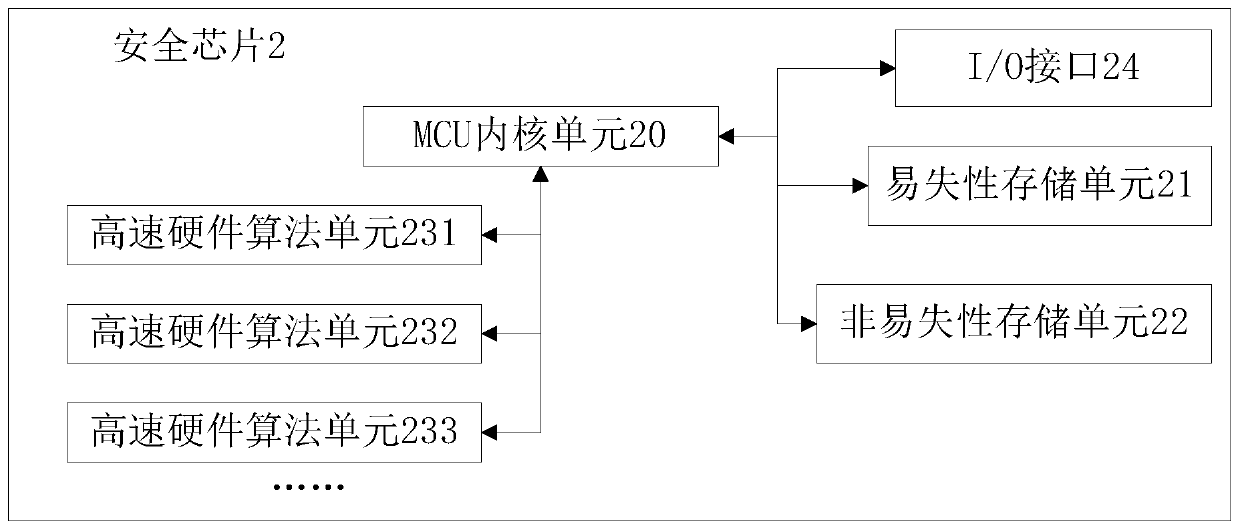
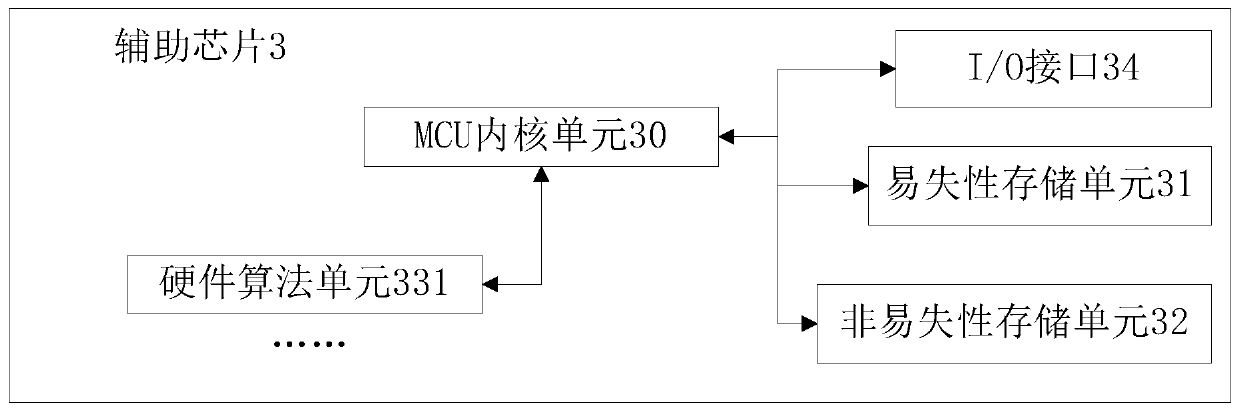
Security authentication method and system based on security chip and security chip
ActiveCN110909338AIncrease the cost of crackingImprove information securityDigital data authenticationSecure communicationSecurity authentication
The invention relates to a security authentication method and system based on a security chip and the security chip, and belongs to the technical field of security communication. The security authentication method comprises the steps that (1) a security chip sends a key acquisition request to an auxiliary chip in response to a security authentication request sent by an upper computer; (2) the auxiliary chip sends first ciphertext data encrypted by the security key to the security chip in response to the key acquisition request; and (3) the security chip decrypts the first ciphertext data to obtain a security key, and performs security authentication with the upper computer in combination with the code table data stored in the security chip. A security key and code table data required by security authentication are separately stored in a security chip and an auxiliary chip, so that the chip cracking difficulty is increased, the information security is improved, and the method can be widely applied to the field of communication and authentication equipment.
Owner:ZHEJIANG GEOFORCECHIP TECH CO LTD
A third party secure access method in the form of a service provider H5 application
The invention discloses a third party secure access method in an H5 application form of a service provider. The method comprises a third party backend, a service provider H5 end, a service provider gateway server side, the service provider authenticating end and the service provider back end; all ends are interacted.According to the invention, the problems of data leakage when the service provideraccesses the third party, data usage uncontrollability, increasement of the size of a third-party APP, access period long process complexity, and high development cost are solved. The invention provides a third party secure access method and system in an H5 application form of a service provider. When the method is applied, the whole H5 application is developed by a service provider, data cannotbe leaked to any third party, the problems that the size of a third party APP is increased and republishing is needed do not exist, the complexity is increased by adding random numbers, Hash, an AES encryption algorithm, public key and private key encryption and decryption and the like, and the cracking cost of the whole method is very high.
Owner:CHONGQING RURAL COMMERCIAL BANK CO LTD
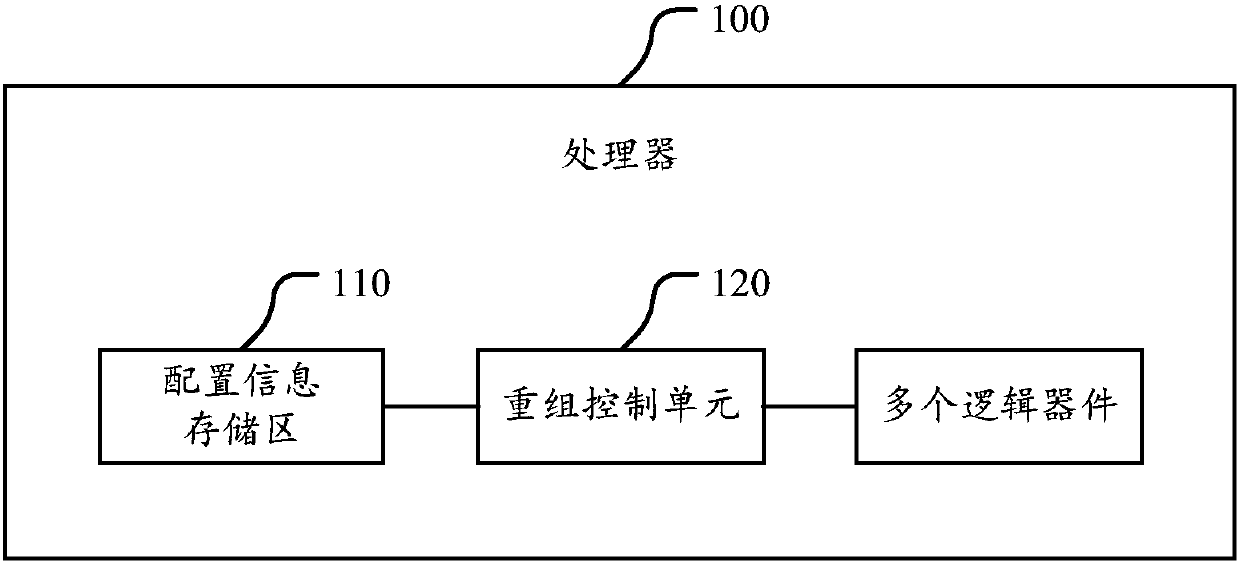
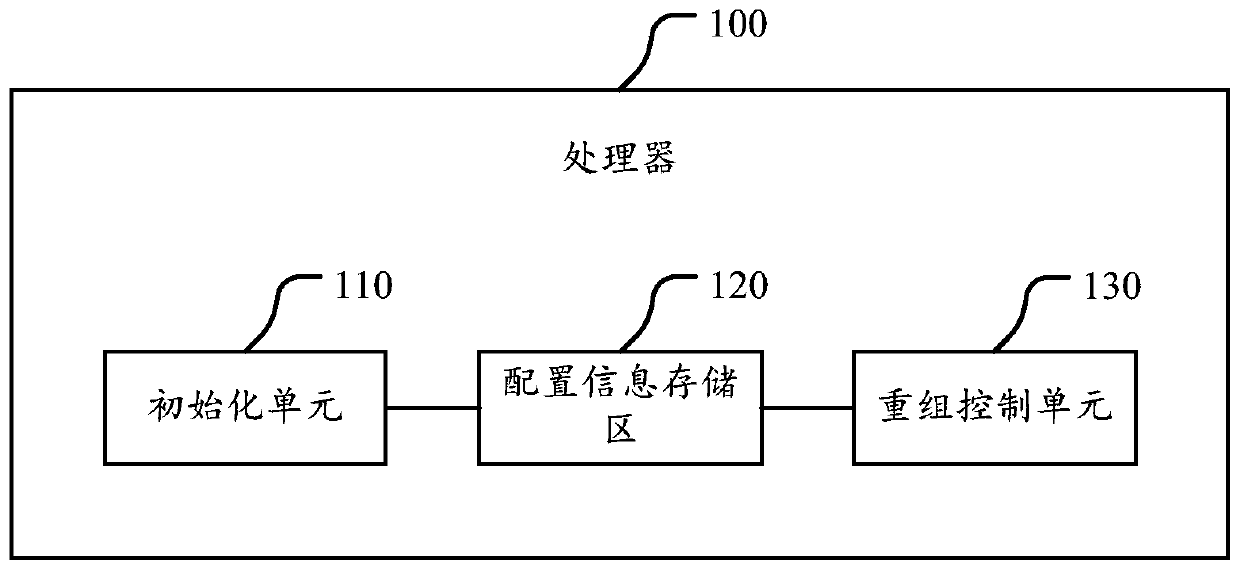
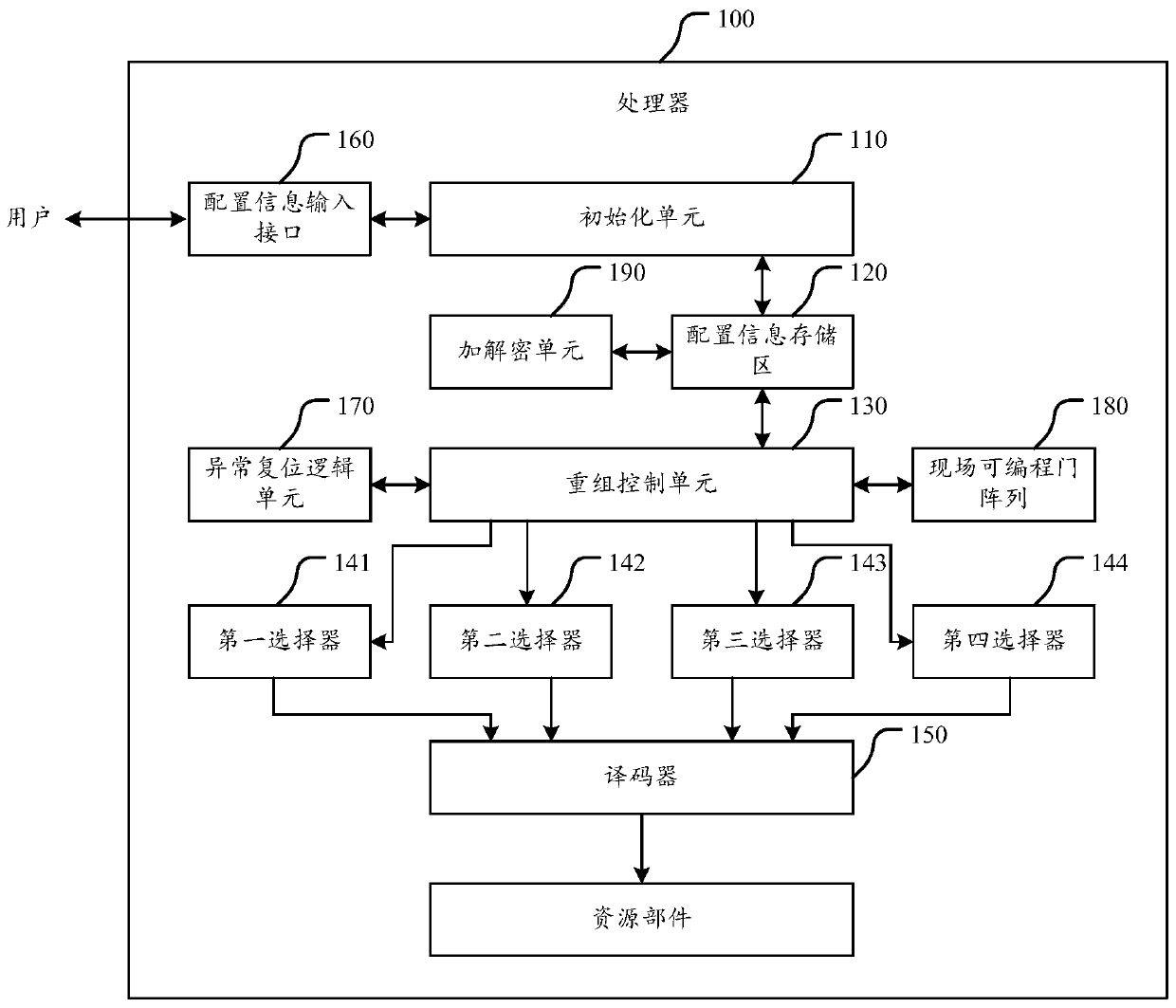
Processor
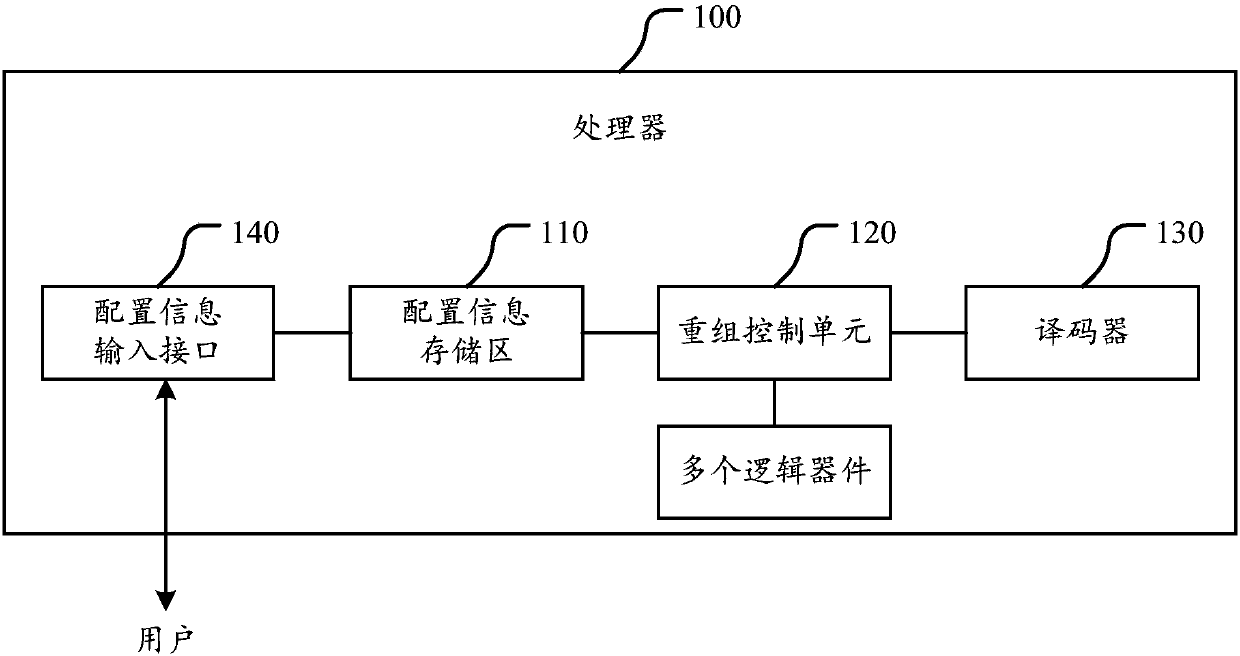
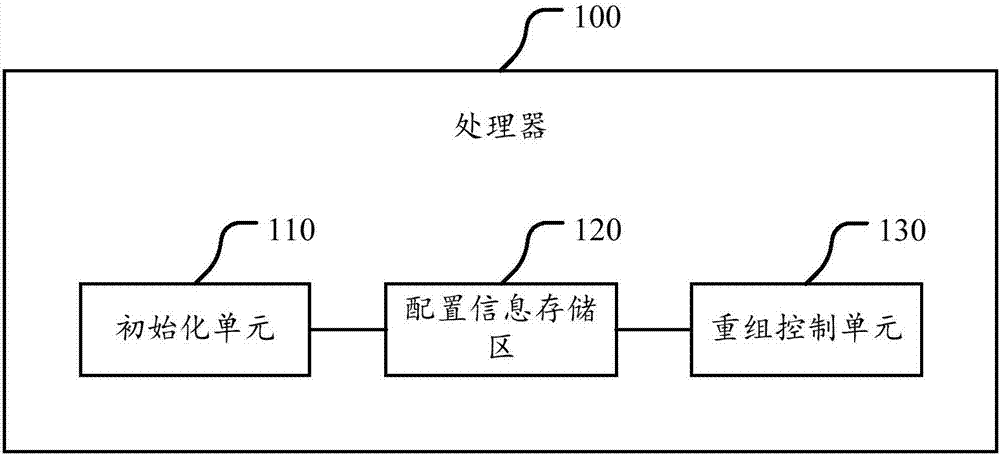
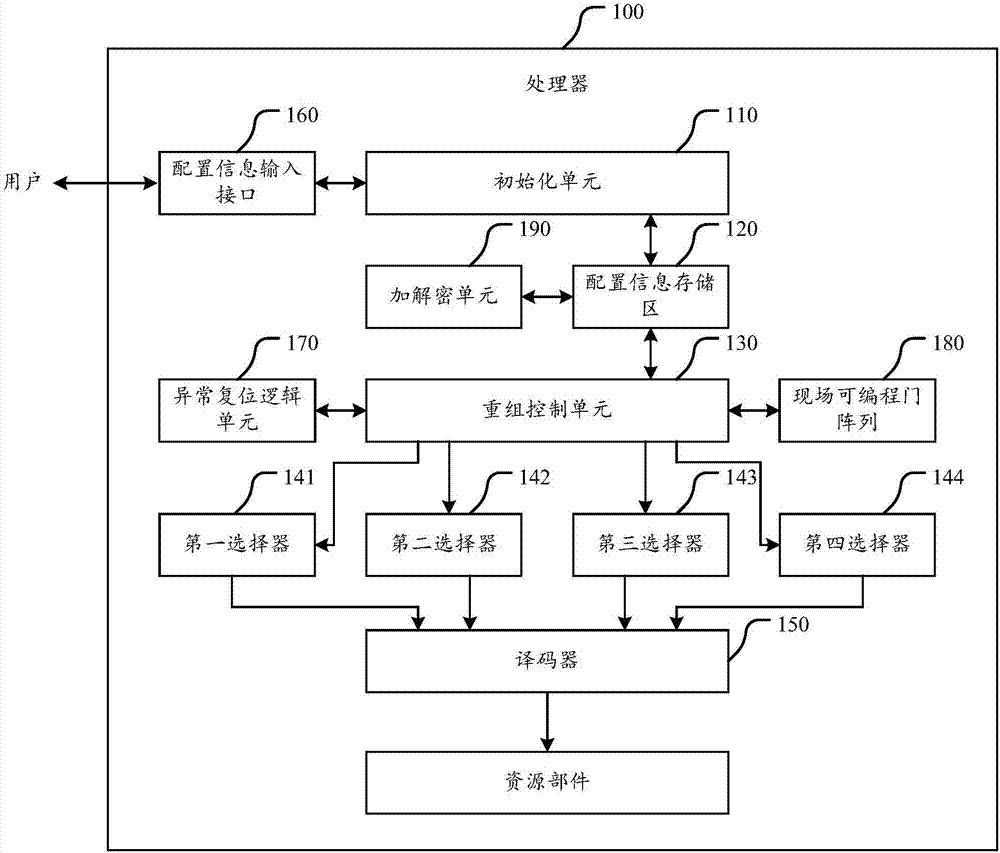
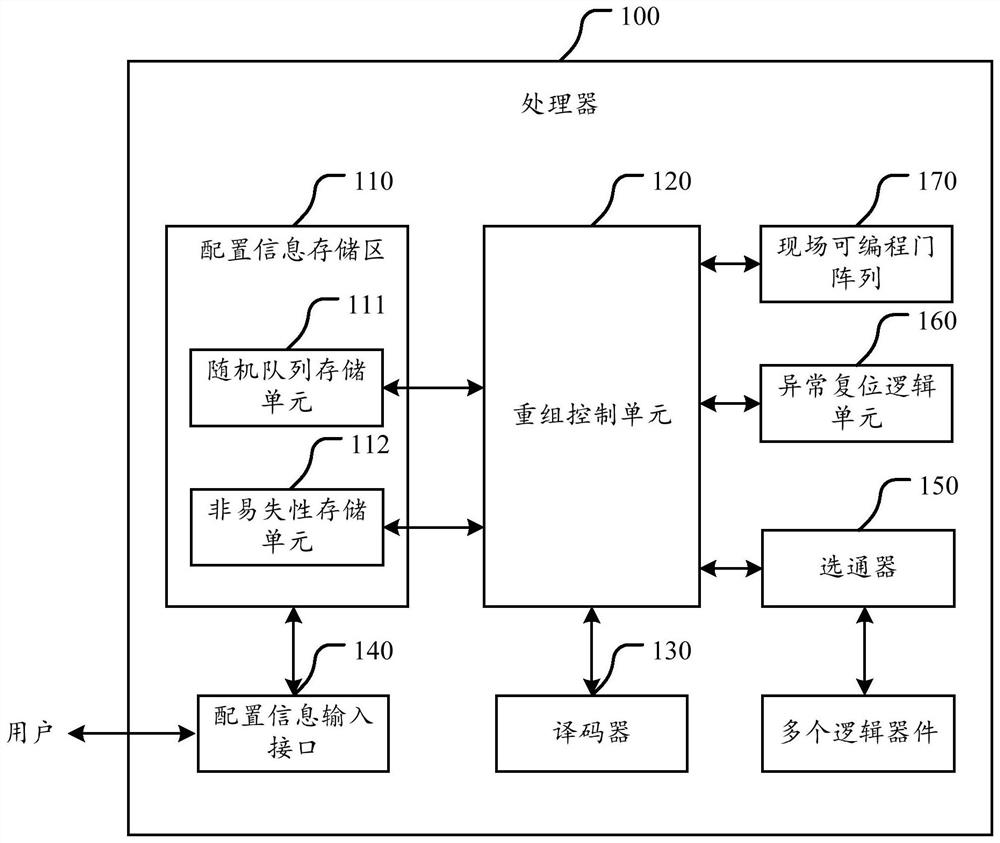
ActiveCN107729772AIncrease the cost of crackingImprove execution securityInternal/peripheral component protectionMachine execution arrangementsDevice formEmbedded system
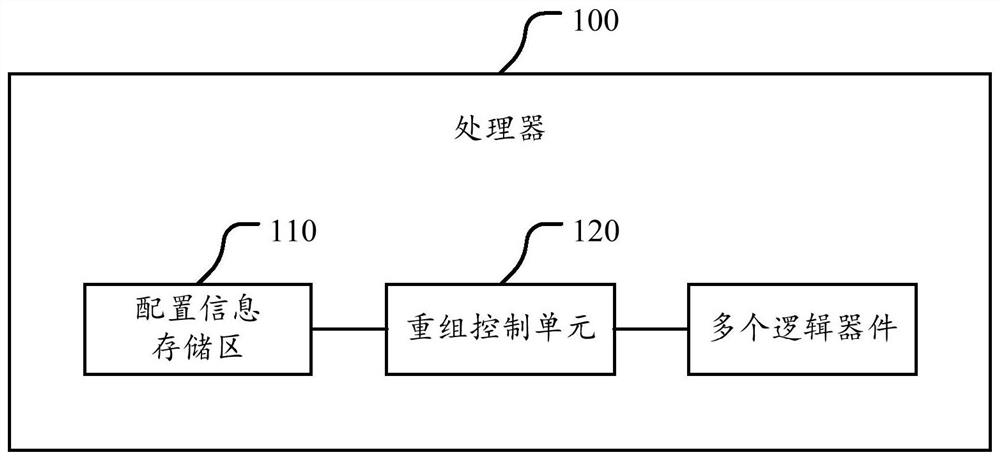
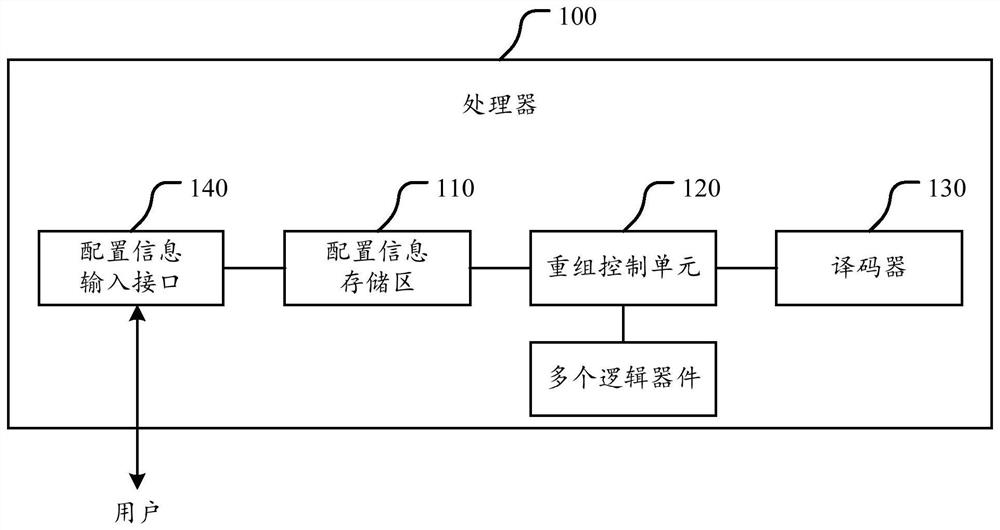
The invention discloses a processor. The processor comprises a configuration information storage region and a recombination control unit; the configuration information storage region is used for storing configuration information, and the configuration information comprises a recombination rule; the recombination control unit is used for controlling a connection relationship among logic devices inthe processor; and the recombination control unit is used for receiving a control instruction obtained by an application which is running in the processor through decoding, selecting the correspondinglogic devices to form a recombination circuit for executing the control instruction according to the recombination rule in the configuration information storage region, thereby realizing execution ofthe control instruction. The processor can control the logic devices forming the recombination circuit; and when one control instruction is realized, the processor can select the logic devices to beconnected to form different recombination circuits according to the recombination rule as needed, so that the cracking cost of the control instruction execution process is effectively reduced, the execution security of the control instruction corresponding to the application, in the processor, in the running process is improved, and the processor is securer and more stable.
Owner:北京多思科技工业园股份有限公司
Security policy version generation method
InactiveCN110636032AImprove securityImprove confidentialityKey distribution for secure communicationVersion controlComputers technologySecurity policy
The invention provides a security policy version generation method, which belongs to the field of computer technology and information security, and comprises the following steps that: a security policy version consists of a plurality of security policy rules, and each security policy rule consists of an algorithm, a secret key and a policy identifier; wherein the security policy version is dividedinto a security policy initial version and a security policy use version; wherein the security policy use version is generated through a security policy initial version, an increment factor and a PCode operation; wherein the PCode comprises a PCode algorithm function and a PCode operating environment, so that the security policy using version is generated by operation of the security policy initial version, the increment factor and the PCode algorithm function in the PCode operating environment. The security policy version provided by the invention can be dynamically changed and updated, is high in security, is difficult to crack even if the key is intercepted, can be widely applied to subway ticket checking terminals, POS terminals and the like, is also suitable for other automatic terminals with similar key systems, has good commercial value, and is worth popularizing.
Owner:咪付(广西)网络技术有限公司
Man-machine identification method based on sliding puzzle verification code
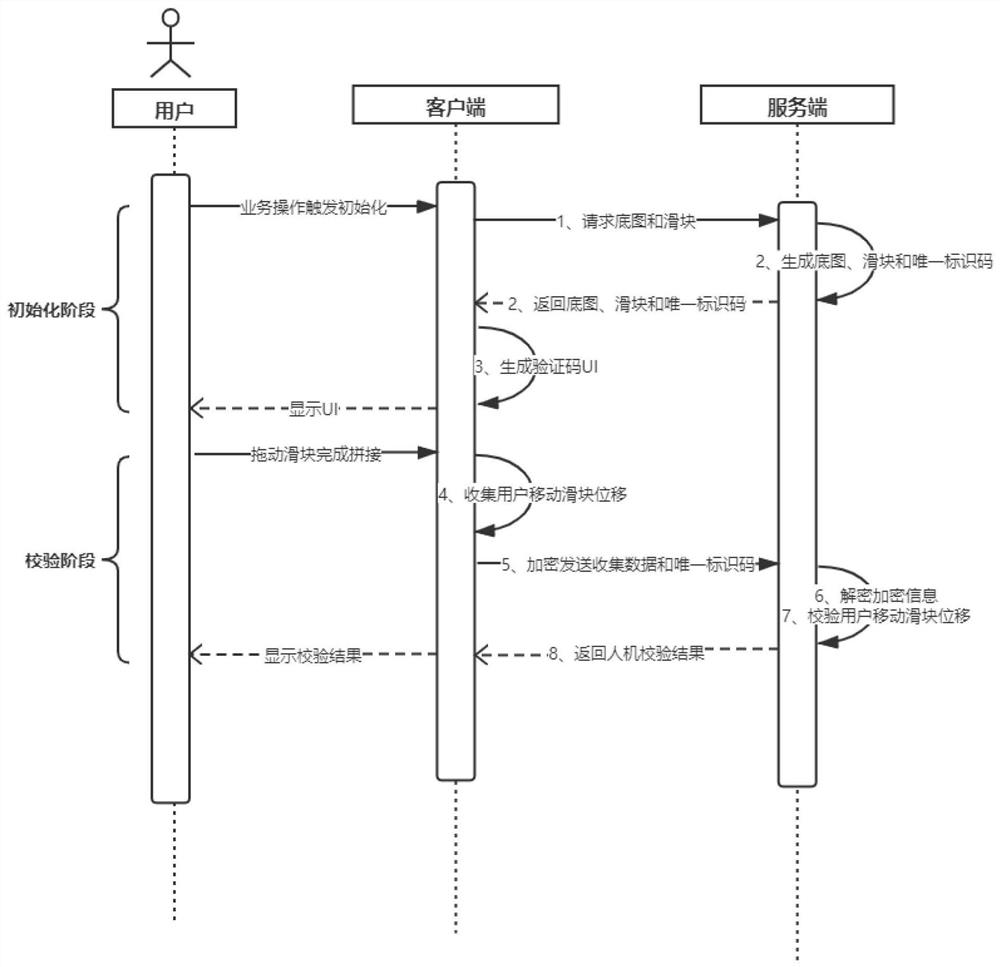
PendingCN112580012AAvoid exposureIncrease the difficulty of reverse decryptionDigital data authenticationAlgorithmTyping
The invention belongs to the field of user identification of computer information security, and relates to a man-machine identification method based on a sliding puzzle verification code. The method comprises the following steps: a client requests a server base map and a sliding block; the server generates a base map, a sliding block and a unique identification code and returns the base map, the sliding block and the unique identification code to the client; the client generates a verification code UI according to the base map and the sliding block; the client collects the displacement of theuser moving sliding block; the client encrypts the collected data and the unique identification code and sends the encrypted data and the unique identification code to the server; the server decryptsthe encrypted data of the client; and the server authenticates the man-machine and returns an authentication result. The method is distinguished from a traditional image-text verification code, so that a code printing recognition black industry tool is out of action, and a certain confrontation protection effect is achieved; meanwhile, the user does not need to identify graphic and text information and related typing operations, and only needs to drag the sliding block to finish picture splicing to finish verification, so that the user operation is simplified, and the user experience is optimized.
Owner:GUANGZHOU FAISCO INFORMATON TECH
Application obfuscation method and device, server and storage medium
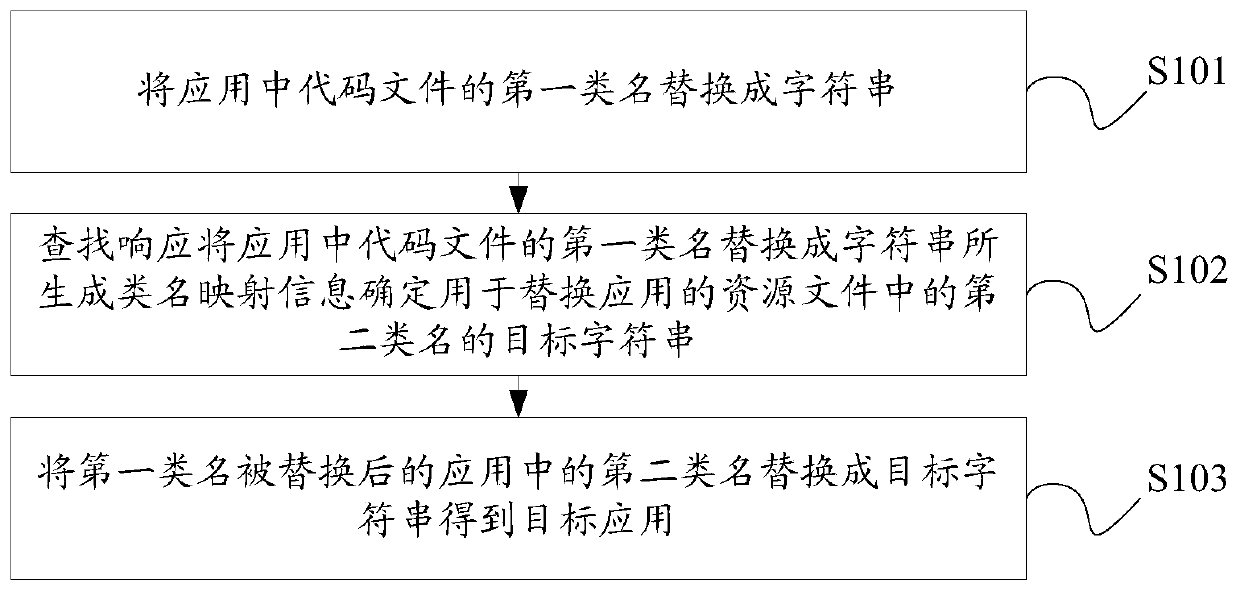
InactiveCN111177662AIncrease the difficultyProtect the fruits of laborProgram/content distribution protectionProgramming languageServer
The embodiment of the invention provides an application obfuscation method and device, a server and a storage medium. The method includes: replacing a first class name of a code file in an applicationwith a character string, wherein the character strings used for replacing the same first class name are the same, and character strings for replacing different first class names are different; secondly, searching response, replacing a first class name of a code file in the application with class name mapping information generated by the character string, and determining a target character stringused for replacing a second class name in a resource file of the application, wherein the class name mapping information comprises each first class name in the code file and a character string used for replacing the first class name; and finally, replacing the second class name in the application with the first class name replaced with the target character string to obtain the target application.According to the technical scheme provided by the invention, not only is the cracking cost of the application increased, but also the difficulty of reversely cracking the application is increased, sothat the labor fruits of technicians are protected, and the occurrence of loopholes is avoided.
Owner:ZHEJIANG SUPCON TECH
Processor
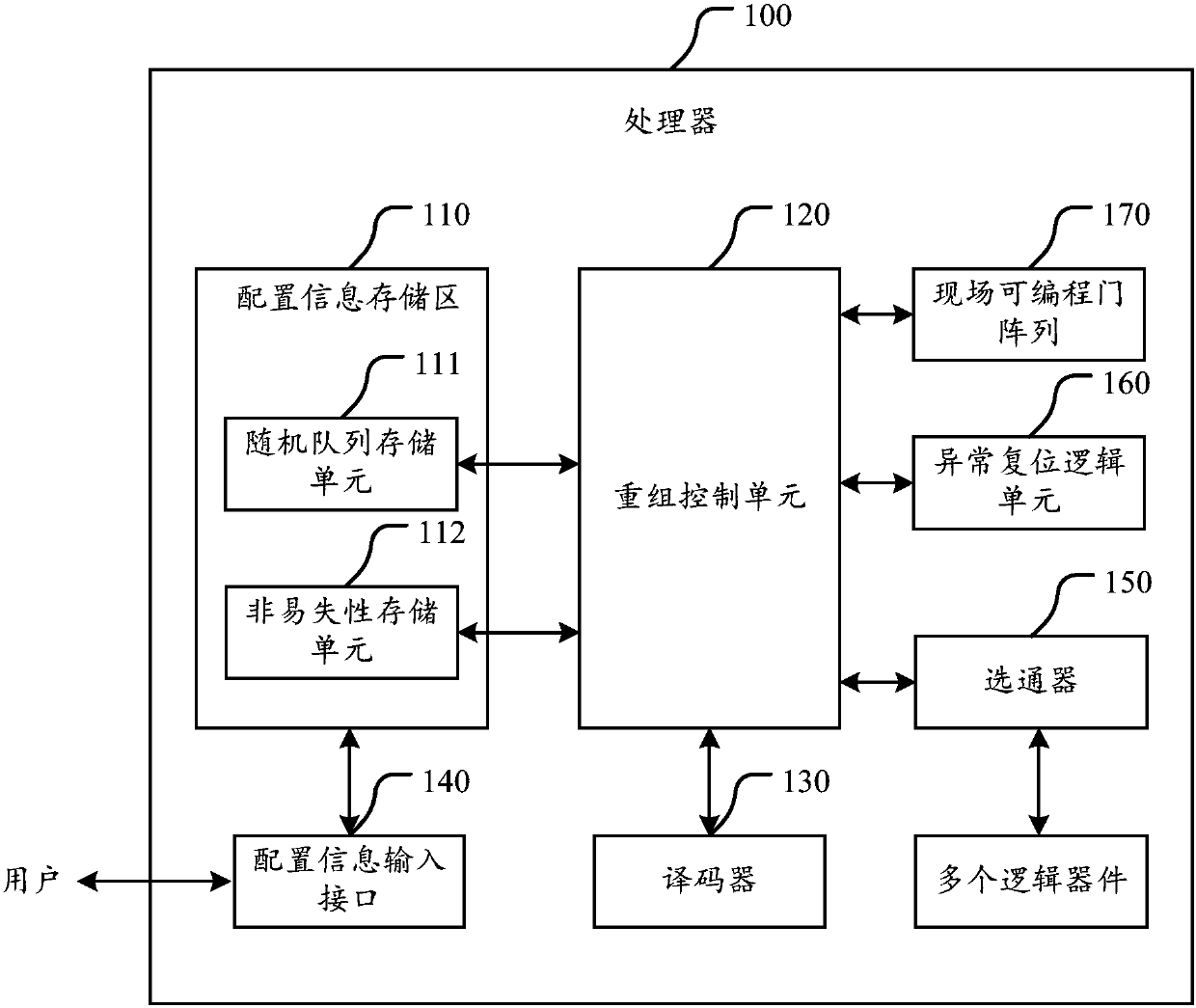
ActiveCN107358126AGuaranteed uptimeIncrease the cost of crackingRuntime instruction translationInternal/peripheral component protectionControl signalOperation safety
The invention discloses a processor. The processor comprises an initialization unit, a configuration information storage area and a recombination control unit. Before an application program is loaded, the initialization unit is used for changing each instruction in the application program according to the pre-set changing rule. The application program with the initial state and the changing rule are saved to the configuration information storage area. The recombination control unit is used for reading corresponding application programs with initial states and changing rules from the configuration information storage area. According to reversing rules of the changing rules, each instruction of the application programs with initial states is subjected to recombination operation. Each instruction subjected to recombination operation is inputted to a decoder for decoding. Obtained control signs are sent to corresponding resources component for execution. The scheme can effectively raise cracking cost of the application programs in the processor. Without changing decoding logic of the decoder, safe instructions meeting requirements of the decoder can be ingeniously inputted to the decoder for decoding through instruction recombination. Therefore, operation safety of the processor is ensured.
Owner:北京多思安全芯片科技有限公司
Cryptographic Algorithm Customization Method
ActiveCN104052595BReduce development costsReduce development difficultySecuring communicationReliability engineeringComputer engineering
The invention discloses a cryptographic algorithm customizing method. The cryptographic algorithm customizing method is characterized in that a customizable cryptographic algorithm functional element, a variable cryptographic algorithm data processing structure, a cryptographic algorithm design constraint rule and a cryptographic algorithm safety assessment method are provided, based on the cryptographic algorithm design constraint rule, the cryptographic algorithm functional element and the cryptographic algorithm data processing structure are specifically configured by a user, so that a customized cryptographic algorithm is obtained, a set of cryptographic algorithm safety assessment method is used for conducting safety assessment on the customized cryptographic algorithm, and if the assessment result meets the algorithm design requirement, the obtained cryptographic algorithm is a target cryptographic algorithm; otherwise, configuration information is adjusted, a novel customized cryptographic algorithm is produced again, and the safety is assessed until the customized cryptographic algorithm meets the design requirement. By the adoption of the method, the safety customized cryptographic algorithm can be efficiently designed by the user.
Owner:戴葵
A third-party secure access method in the form of a service provider's h5 application
The invention discloses a third-party security access method in the form of a service provider H5 application, including a third-party back end, a service provider H5 end, a service provider gateway server end, a service provider authentication end, and a service provider back end. Interaction, the present invention solves the problems existing in the prior art that the service provider’s service access to the third party will cause data leakage, uncontrollable data use, increase in the size of the third-party APP, long access period, complicated process, and high development costs , providing a third-party secure access method and system in the form of an H5 application for the service provider. When it is applied, the entire H5 application is developed by the service provider, and the data will not be leaked to any third party. There is no increase in the size of the third-party APP and The problem of republishing, adding random numbers, hashes, AES encryption algorithms, public key and private key encryption and decryption increases complexity, and the cracking cost of the whole method is very high.
Owner:CHONGQING RURAL COMMERCIAL BANK CO LTD
An Image Encryption Method Based on Chaotic Map and Chaotic S-Box Substitution
ActiveCN112906043BImprove relevanceAvoid crackingDigital data protectionImage data processing detailsColor imageS-box
The present invention provides an image encryption method based on chaotic mapping and chaotic S-box substitution in the technical field of image encryption, including: step S10, obtaining a color image file and performing hash calculation to obtain a hash value, based on the hash value calculation system Parameters; Step S20, generating four initial values of the four-dimensional hyperchaotic map based on the hash value, and then obtaining four sets of chaotic pseudo-random sequences; Step S30, extracting sequences based on the chaotic pseudo-random sequences and system parameters W z , using the sequence W z And use the S box of AES algorithm to generate chaotic S box; Step S40, carry out Arno l d scrambling to color image file to obtain scrambling image, utilize chaotic S box to carry out byte substitution to scrambling image and obtain replacement image; Step S50, Using chaotic pseudo-random sequence and system parameters, image diffusion encryption is performed on the three components of RGB in the substitution image to obtain three ciphertext data, and the encrypted image is obtained based on each ciphertext data. The invention has the advantages of greatly improving the security of image encryption.
Owner:HUAQIAO UNIVERSITY
a processor
ActiveCN107358126BGuaranteed uptimeIncrease the cost of crackingRuntime instruction translationInternal/peripheral component protectionComputer hardwareComputer architecture
The invention discloses a processor. The processor comprises an initialization unit, a configuration information storage area and a recombination control unit. Before an application program is loaded, the initialization unit is used for changing each instruction in the application program according to the pre-set changing rule. The application program with the initial state and the changing rule are saved to the configuration information storage area. The recombination control unit is used for reading corresponding application programs with initial states and changing rules from the configuration information storage area. According to reversing rules of the changing rules, each instruction of the application programs with initial states is subjected to recombination operation. Each instruction subjected to recombination operation is inputted to a decoder for decoding. Obtained control signs are sent to corresponding resources component for execution. The scheme can effectively raise cracking cost of the application programs in the processor. Without changing decoding logic of the decoder, safe instructions meeting requirements of the decoder can be ingeniously inputted to the decoder for decoding through instruction recombination. Therefore, operation safety of the processor is ensured.
Owner:北京多思安全芯片科技有限公司
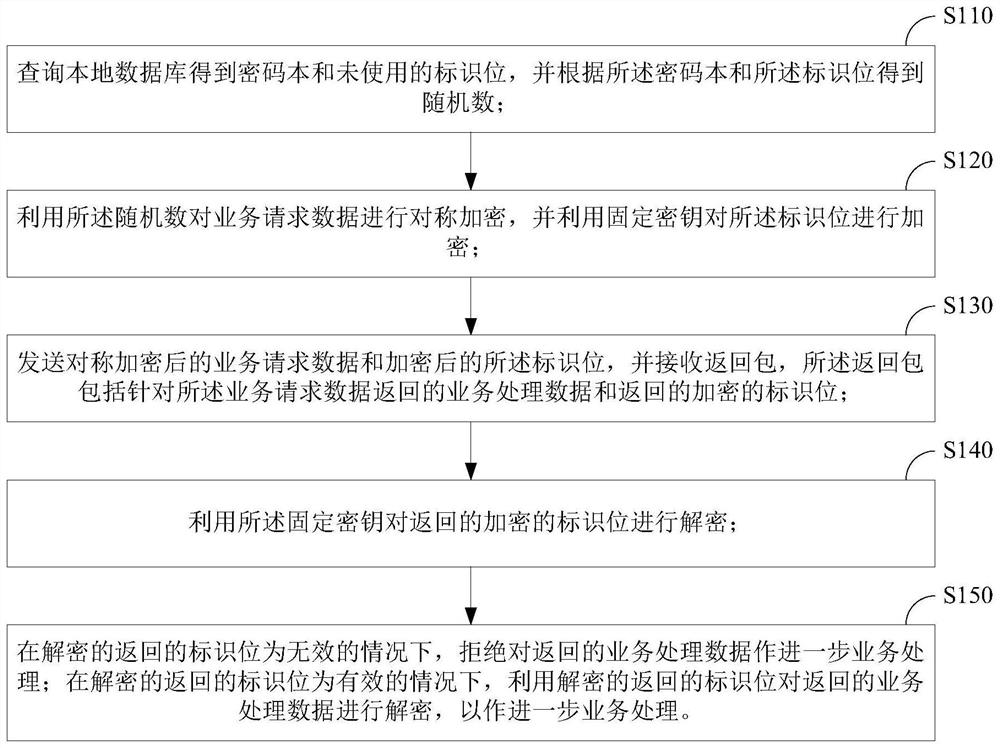
Business processing security verification method and device
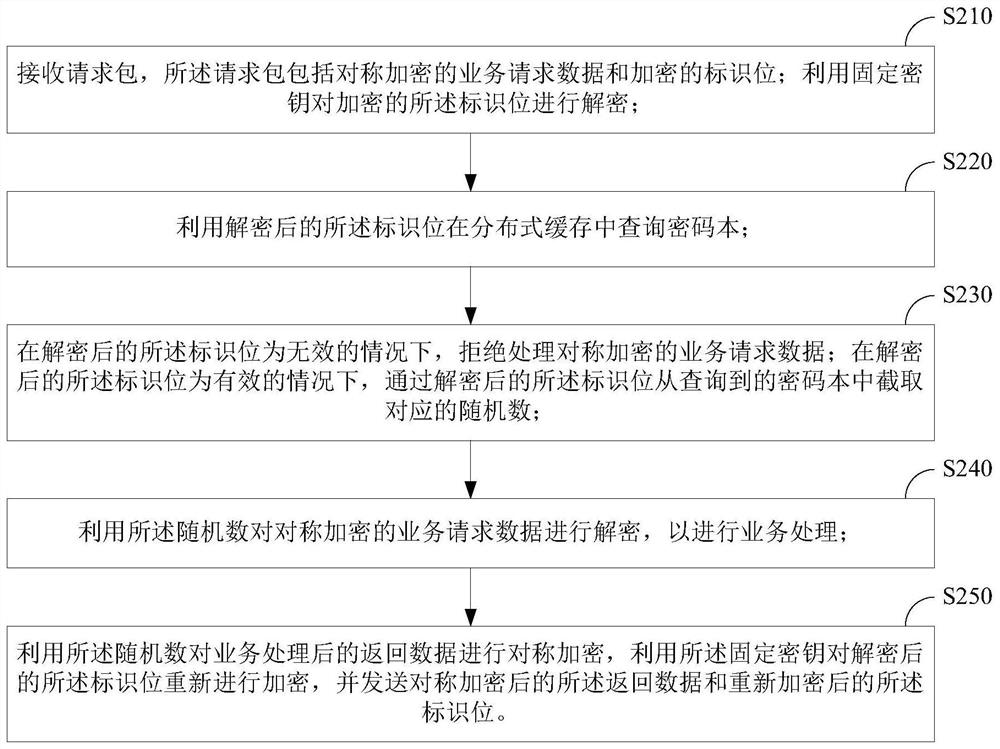
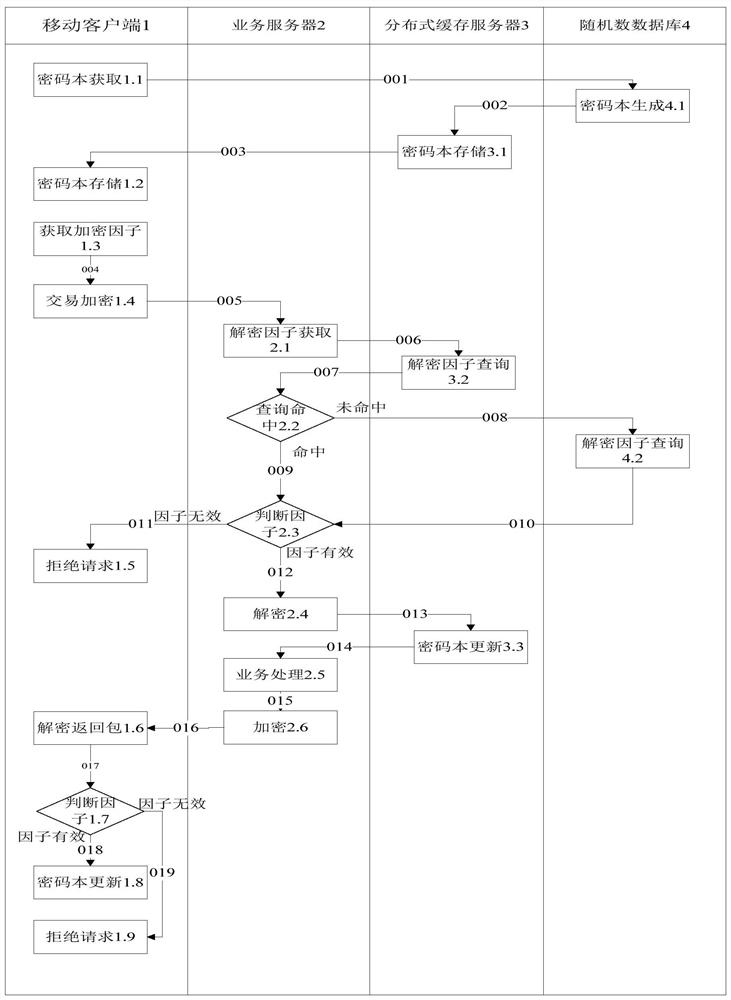
ActiveCN108810017BImprove securityIncrease the cost of crackingKey distribution for secure communicationMultiple keys/algorithms usageCode bookDatabase
The present invention provides a business processing safety verification method and device. The method includes: querying a local database to obtain a codebook and unused identification bits, and obtaining a random number according to the codebook and identification bits; using the random number to process the service request data Symmetric encryption, and use a fixed key to encrypt the identification bit; send the symmetrically encrypted service request data and the encrypted identification bit, and receive a return package, which includes the service processing data returned for the service request data and the returned encrypted identification bit; use the fixed key to decrypt the returned encrypted identification bit; in the case that the decrypted returned identification bit is invalid, refuse to perform further business processing on the returned business processing data; If the returned identification bit is valid, the returned service processing data is decrypted by using the decrypted returned identification bit for further service processing. The invention can improve the security of business processing.
Owner:INDUSTRIAL AND COMMERCIAL BANK OF CHINA
a processor
ActiveCN107729772BIncrease the cost of crackingImprove execution securityInternal/peripheral component protectionMachine execution arrangementsComputer architectureControl cell
The invention discloses a processor. The processor comprises a configuration information storage region and a recombination control unit; the configuration information storage region is used for storing configuration information, and the configuration information comprises a recombination rule; the recombination control unit is used for controlling a connection relationship among logic devices inthe processor; and the recombination control unit is used for receiving a control instruction obtained by an application which is running in the processor through decoding, selecting the correspondinglogic devices to form a recombination circuit for executing the control instruction according to the recombination rule in the configuration information storage region, thereby realizing execution ofthe control instruction. The processor can control the logic devices forming the recombination circuit; and when one control instruction is realized, the processor can select the logic devices to beconnected to form different recombination circuits according to the recombination rule as needed, so that the cracking cost of the control instruction execution process is effectively reduced, the execution security of the control instruction corresponding to the application, in the processor, in the running process is improved, and the processor is securer and more stable.
Owner:北京多思科技工业园股份有限公司
An anti-counterfeiting unique code generation and anti-counterfeiting verification method
ActiveCN108154207BVarious combinationsPrevent mass copying and counterfeitingCommerceRecord carriers used with machinesSoftware engineeringDatabase
The invention discloses a method for generating an anti-counterfeiting unique code and performing anti-counterfeiting authentication. The method includes: generating the anti-counterfeiting unique code, to be more specific, preparing an anti-counterfeiting material, printing and solidifying the anti-counterfeiting material onto a product or a product package, shooting an anti-counterfeiting imagefile in a magnifying manner, performing storage and transmission, performing automatic identification by an image-text identification system, automatically generating and storing the anti-counterfeiting unique code, and generating and printing a commodity identification code; performing anti-counterfeiting authentication, wherein the anti-counterfeiting authentication is performed by scanning thecommodity identification code, inquiring an authenticity inquiry system, directly magnifying and observing the image content of the anti-counterfeiting material for rechecking and the like. The methodhas the advantages that multiple anti-counterfeiting measures are set during the generating of the anti-counterfeiting unique code, a multiple anti-counterfeiting authentication function is achieved,and counterfeiting preventing and authentication are linked with each other; anti-counterfeiting authentication manners are diversified, mutual corroboration of the different anti-counterfeiting authentication manners can be achieved, reverse copying and cracking is difficult, and good anti-counterfeiting performance is achieved; the method is convenient to use and especially suitable for the reliable counterfeiting preventing of high-value commodities in the intelligent Internet era.
Owner:福州固钛光电科技有限公司
A network authentication method and system based on data link encrypted transmission
ActiveCN104125239BAvoid monitoringInhibit injectionSecuring communicationWeb authenticationNetwork link
Owner:RUN TECH CO LTD BEIJING
Bidirection control method for preventing fraudulent use of client end software
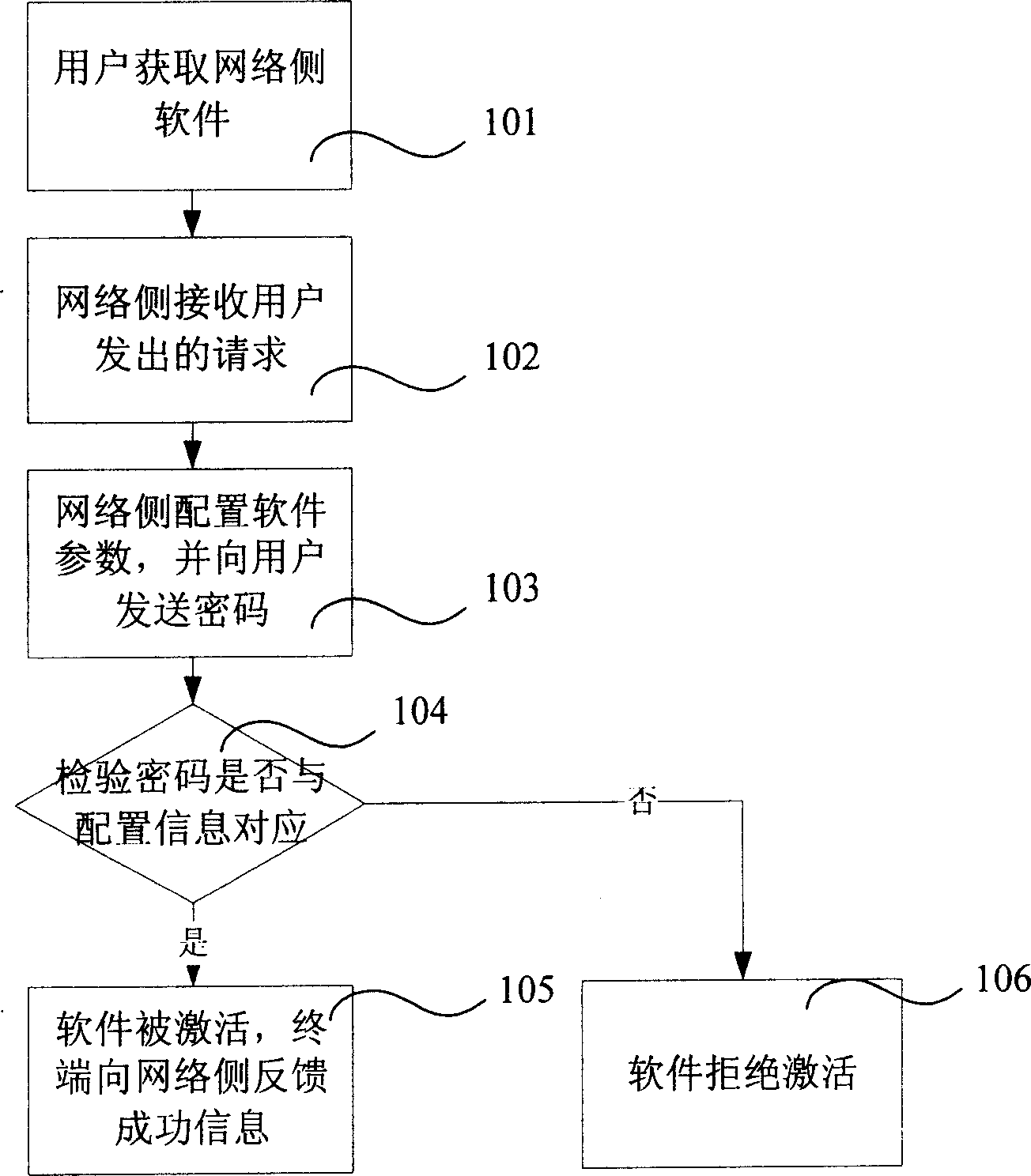
InactiveCN1753568AReduce theftEnsure safetyRadio/inductive link selection arrangementsSecurity arrangementControl mannerUser input
The inventive method consists of: the mobile communication network side receives the userí»s request of switching on the customerí»s end software mounted on the mobile terminal; the mobile communication network side transmits parameter setup information in accordance with the user number to the terminal and generates active cipher for notifying the users; the customer end software recovers the active cipher input by the users and detects if the active cipher corresponds to the setup information, if it does, the customer end software executes activating operation, if it doesní»t, the customer end software doesní»t execute activating operation. The user can take two-way control of activating the software via the active cipher at the terminal side to ensure the activating process. The encrypted means is used, so the invention can reduce the possibility of being stolen of the setup information and the active cipher.
Owner:CHINA MOBILE COMM GRP CO LTD
Dynamic encryption method of IoT devices based on login serial number
ActiveCN109361520BLow costReduce power consumptionKey distribution for secure communicationUser identity/authority verificationCommunications securityThe Internet
This application discloses a dynamic encryption method for an Internet of Things device based on a login serial number. The method includes: the Internet of Things device generates a first dynamic key; the Internet of Things device uses the generated first dynamic key to encrypt a login message to obtain an encrypted login message. Text; IoT device sends encrypted login message to IoT platform; IoT platform receives encrypted login message, verifies encrypted login message, and IoT platform generates login reply message after verification; IoT platform sends login reply The message is sent to the IoT device; the IoT device receives the login reply message, and verifies the login reply message; the two-way identity authentication between the IoT device and the IoT platform is successful, and the IoT platform and the IoT device send each other Ordinary datagram. The invention generates a pseudo-random dynamic key from the static key and the login serial number of the Internet of Things device, thereby improving the communication security between the Internet of Things device and the Internet of Things platform.
Owner:TAIHUA WISDOM IND GRP CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com