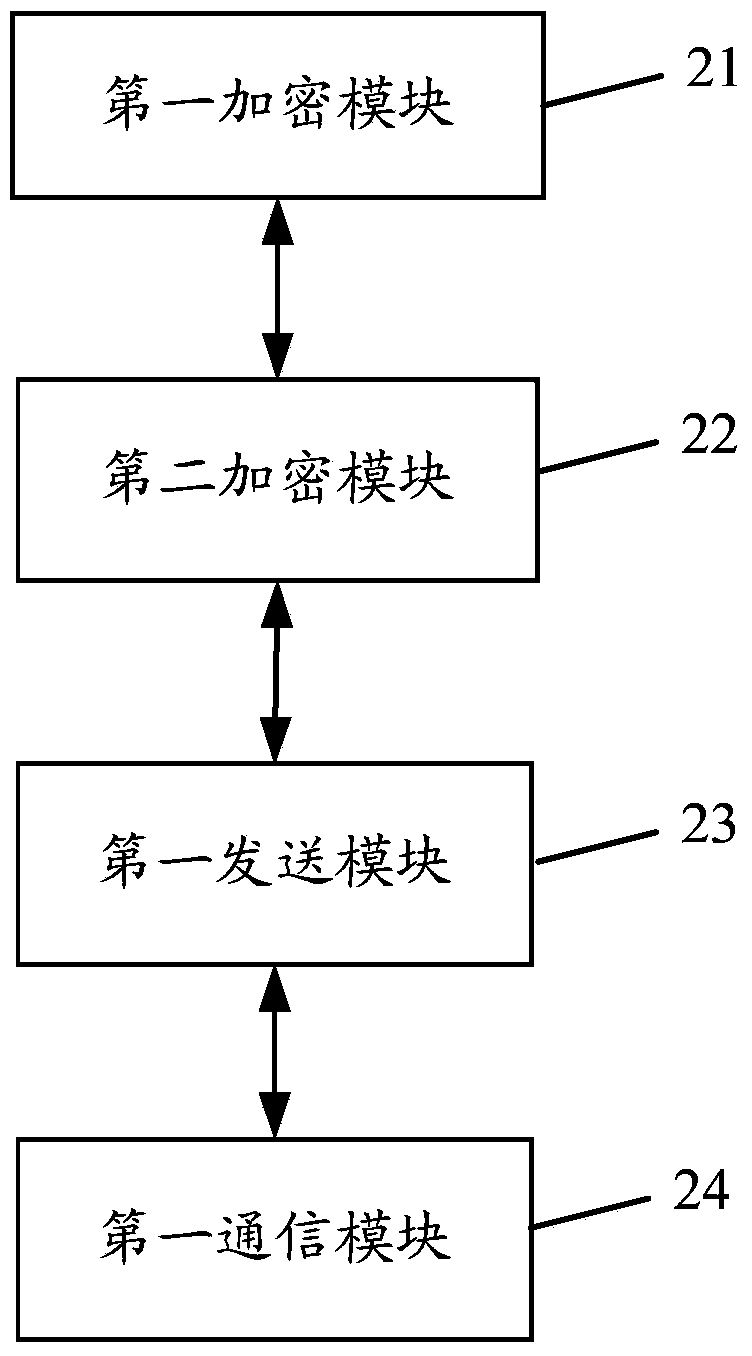
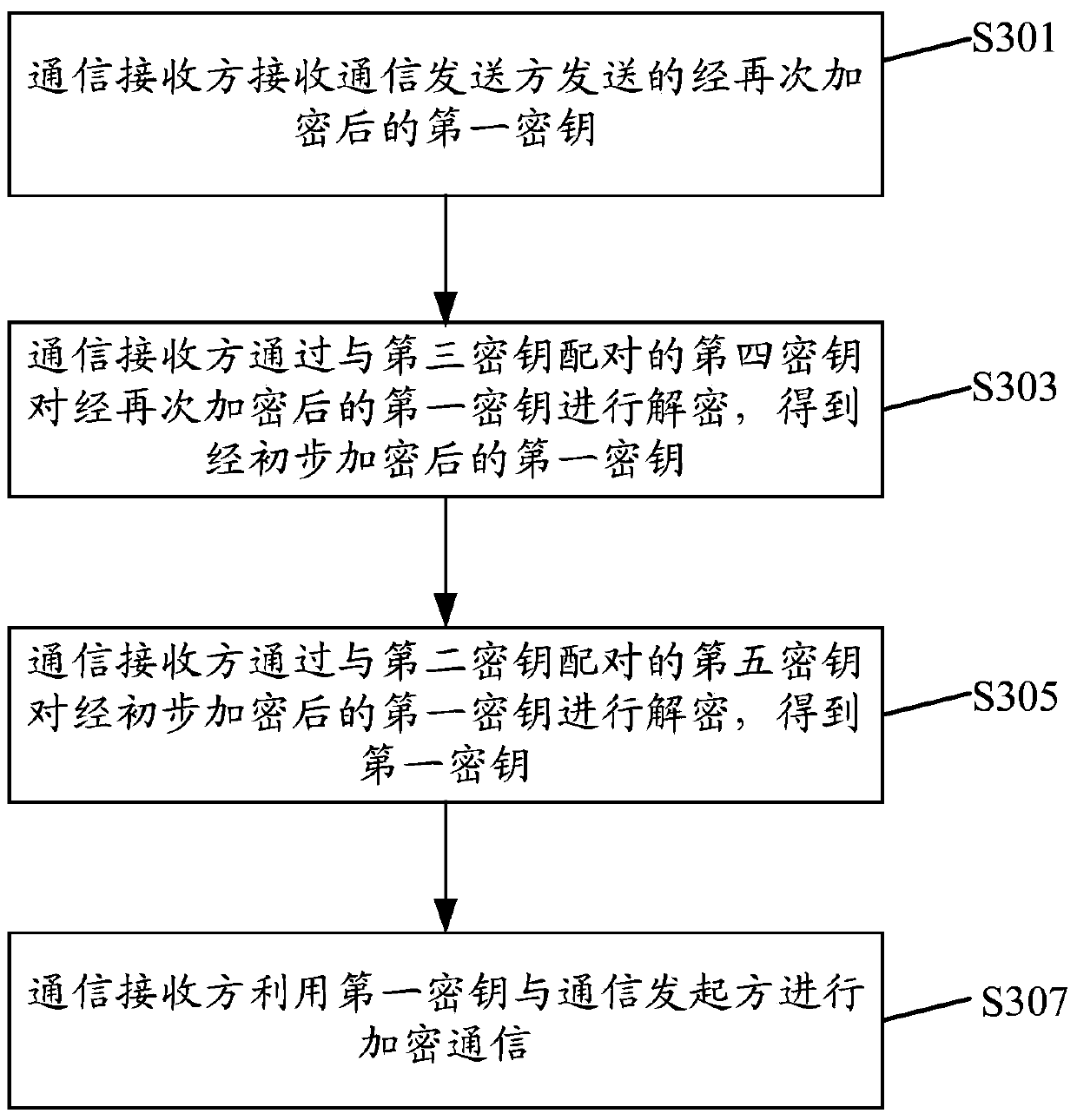
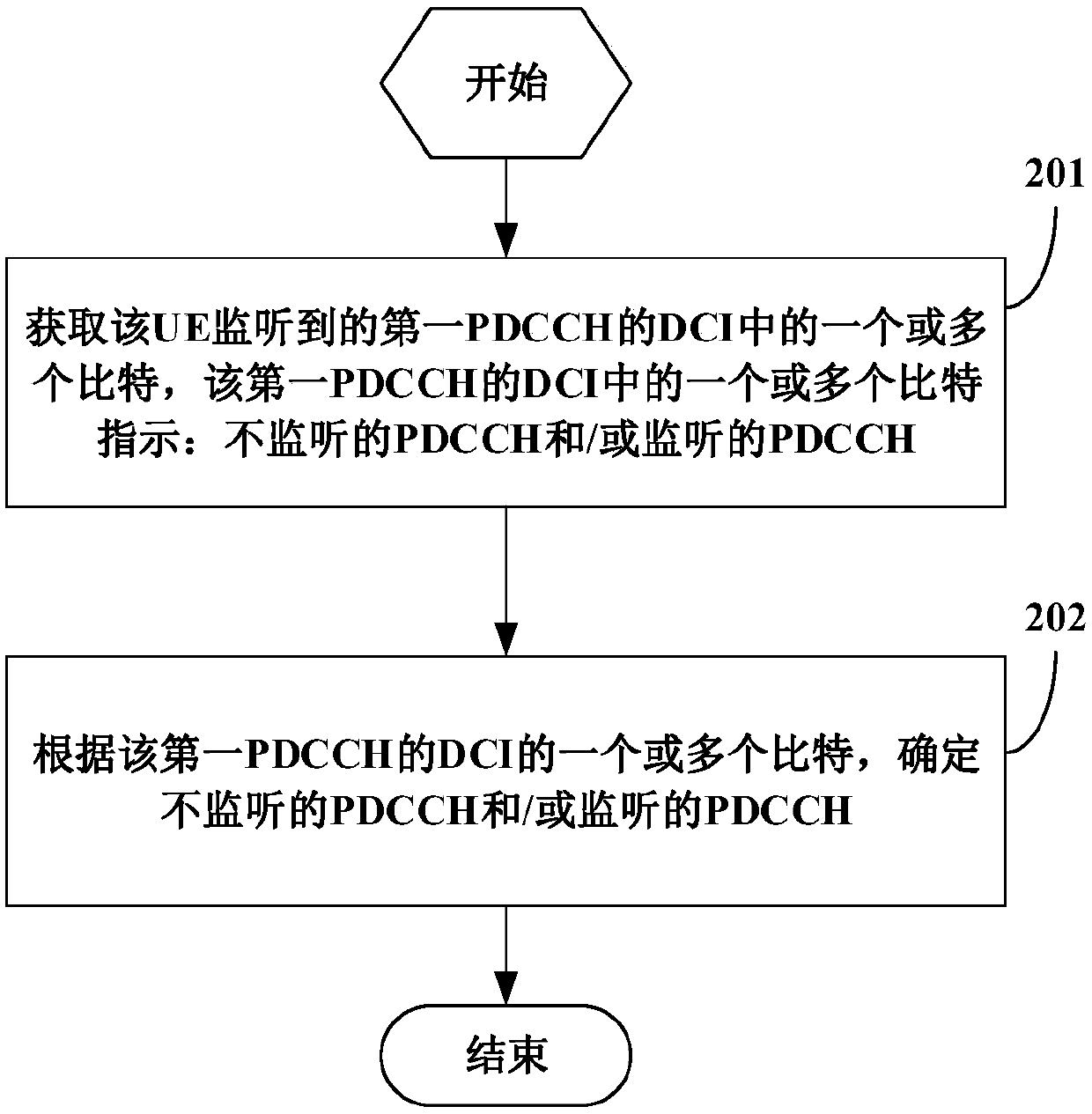
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
272results about How to "Avoid monitoring" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
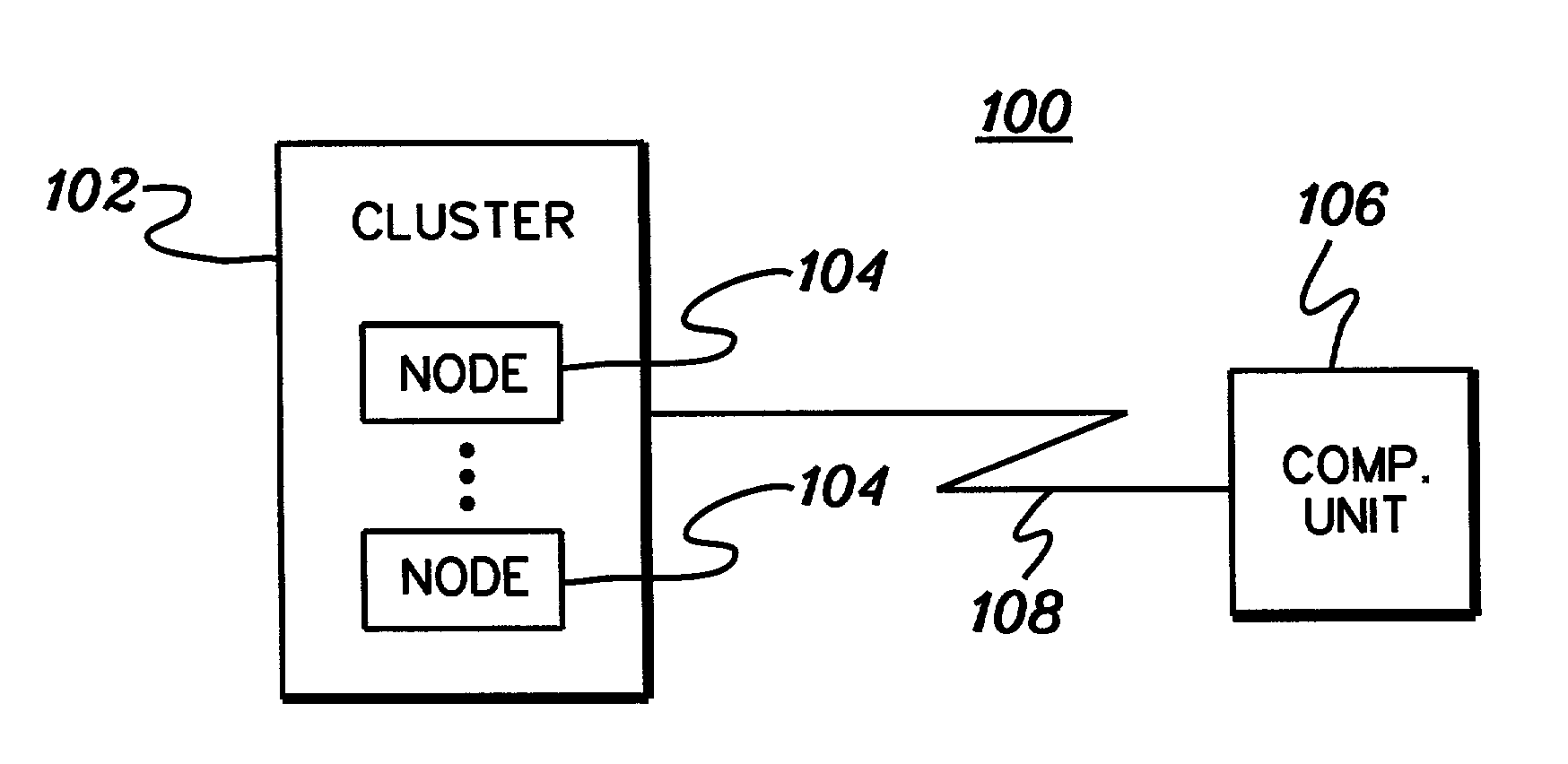
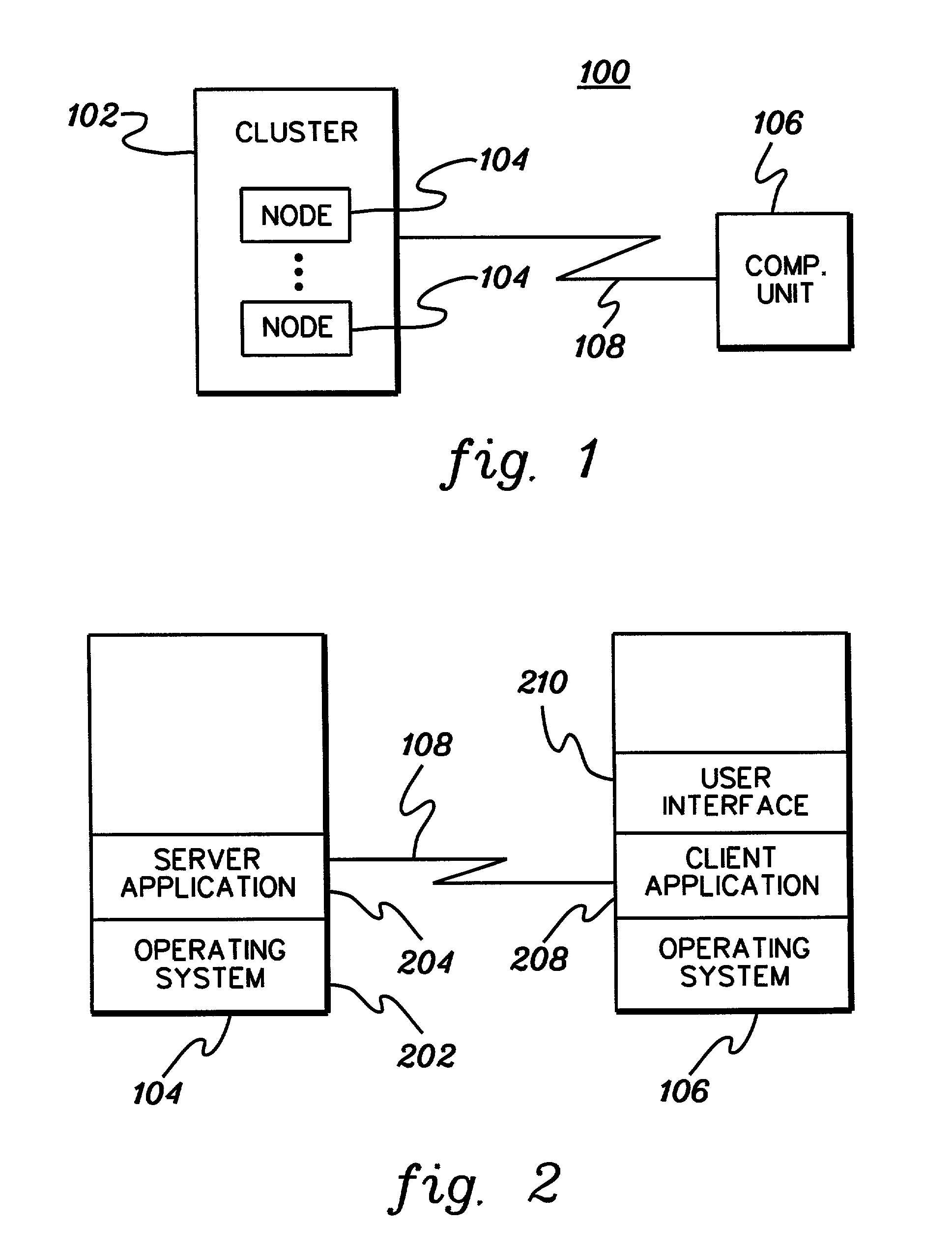
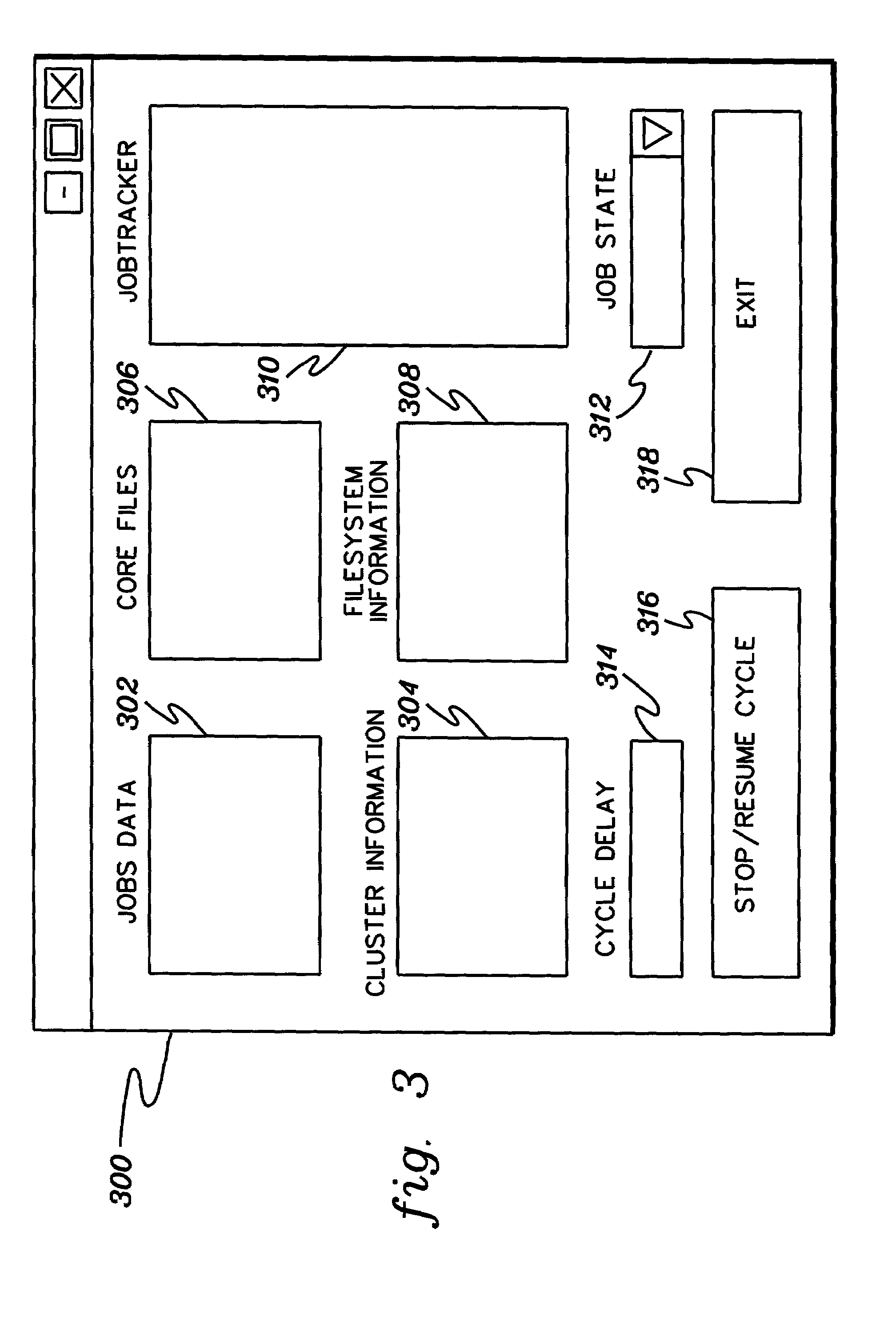
In-queue jobs information monitoring and filtering
InactiveUS7177823B2Easy to displayEasy accessDigitally marking record carriersDigital computer detailsFile systemApplication software
A remote monitor technique based on a client / server model is provided for a distributed computing system having a plurality of computing nodes. The remote monitor includes a server application for collecting jobs information on jobs in a queue of the system and a client application for presenting or employing the jobs information. The client application can display the jobs information in a single display window comprising multiple subwindows for various characteristics of the jobs information. Jobs information displayed by the client application can be periodically refreshed. The remote monitor enables a user to monitor in detail jobs of a state defined by the user. The remote monitor can also track usage of preselected filesystems and automatically trims filesystems if usage is higher than a defined threshold.
Owner:IBM CORP
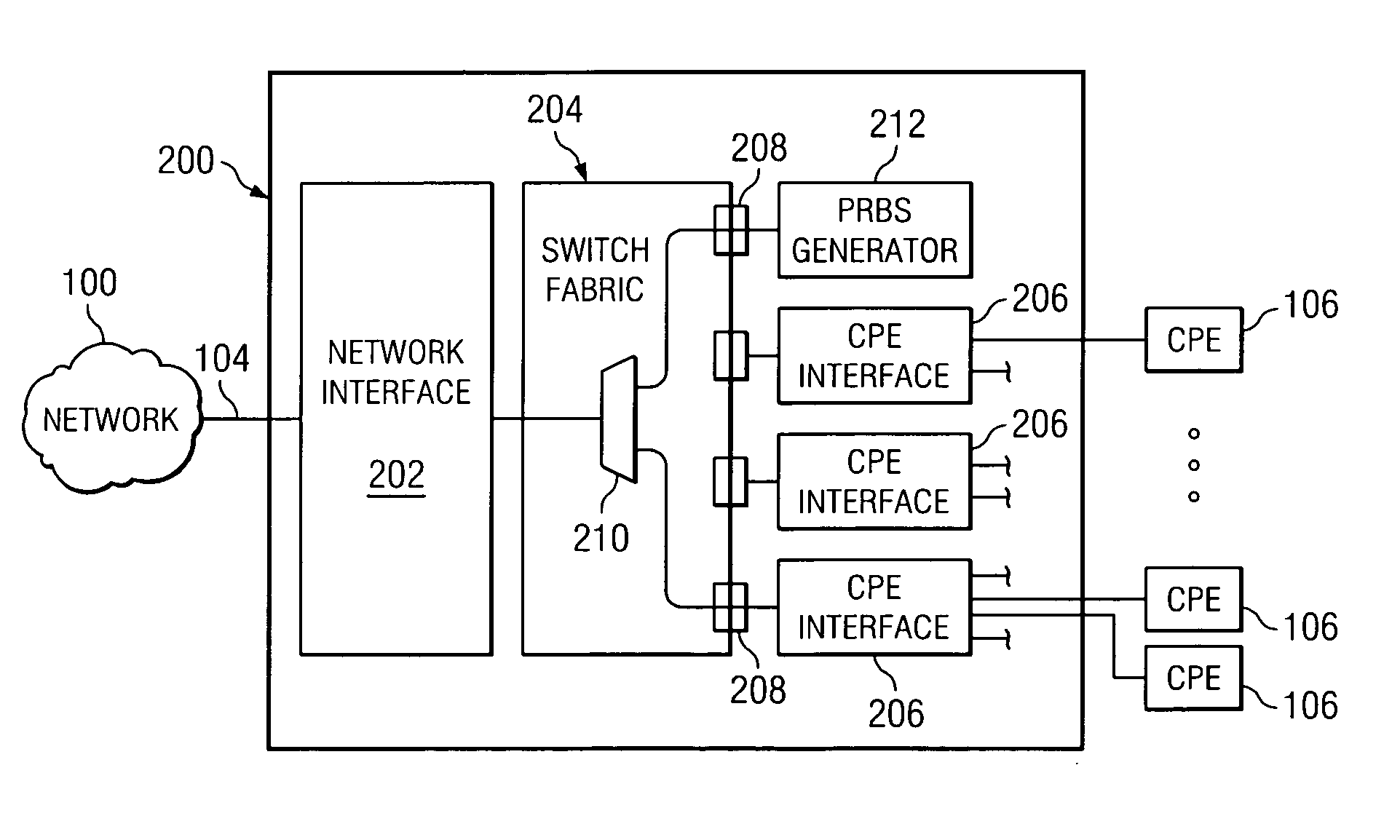
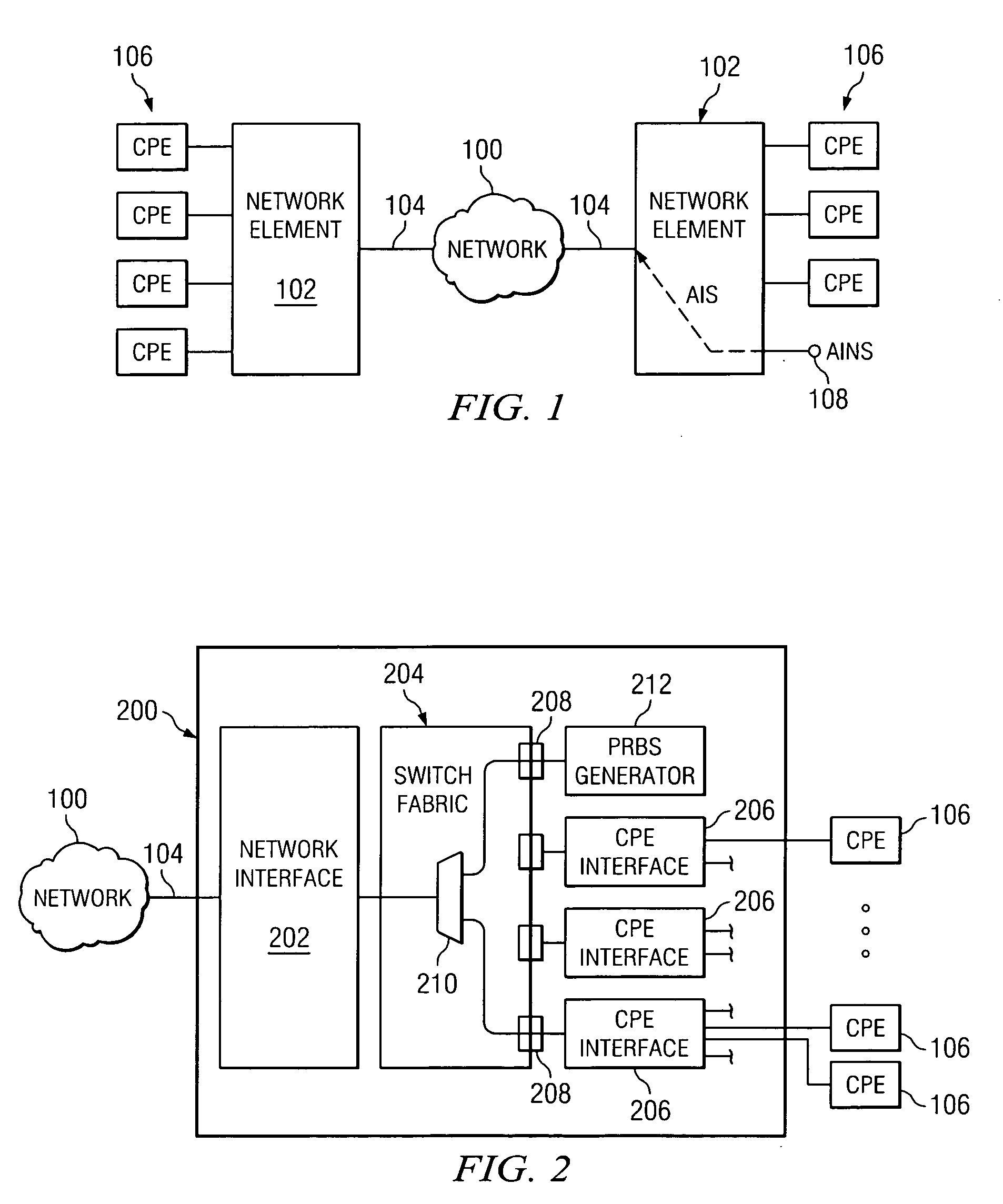
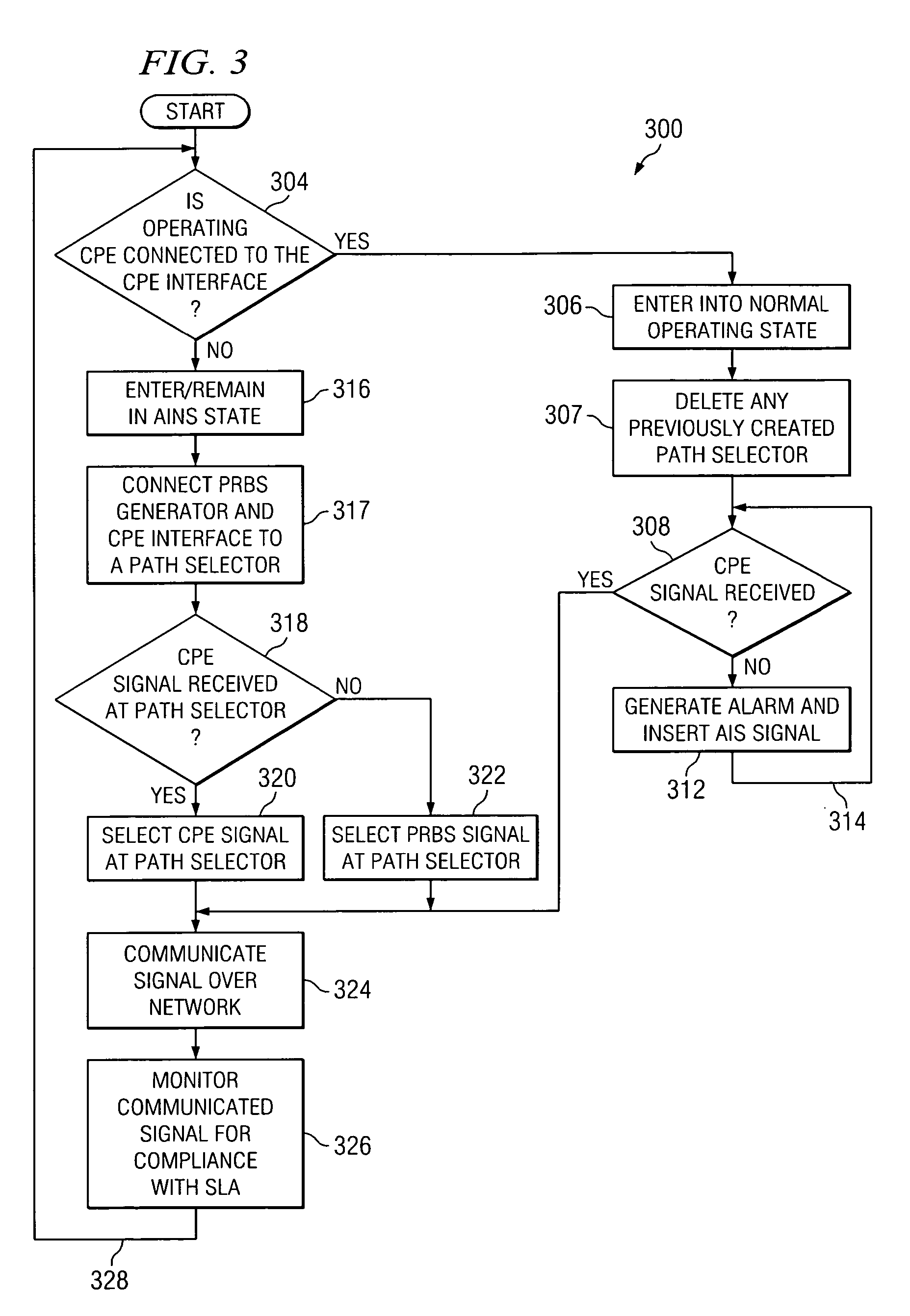
Method and system for monitoring idle network circuits
InactiveUS20060072470A1Eliminates and reduces of disadvantageEliminates and reduces of and problemError preventionTransmission systemsSignal generatorCustomer-premises equipment
A method is provided for monitoring a network that includes providing a path selector that can select between a first input and a second input, where the first input is coupled to a customer premises equipment interface that is operable to receive signals from customer premises equipment and the second input is coupled to a test signal generator that is operable to generate test signals. The method also includes determining whether operating customer premises equipment is coupled to an input of the customer premises equipment interface that is coupled to the first input of the path selector. If not, then an idle state is entered into. While in the idle state, it is determined whether a signal is received from the customer premises equipment interface at the first input of the path selector. The test signal received at the second input of the path selector is selected unless a signal is received from the customer premises equipment interface at the first input. The method also includes communicating the test signal from the path selector to the network.
Owner:FUJITSU LTD
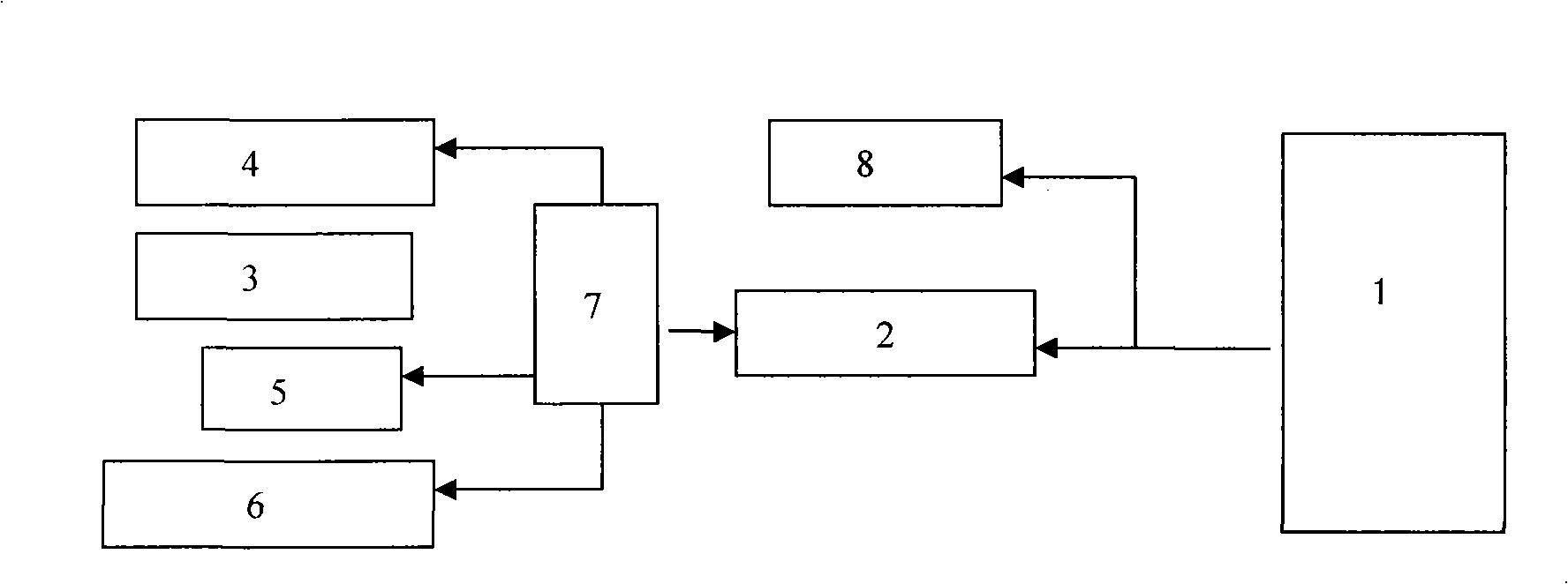
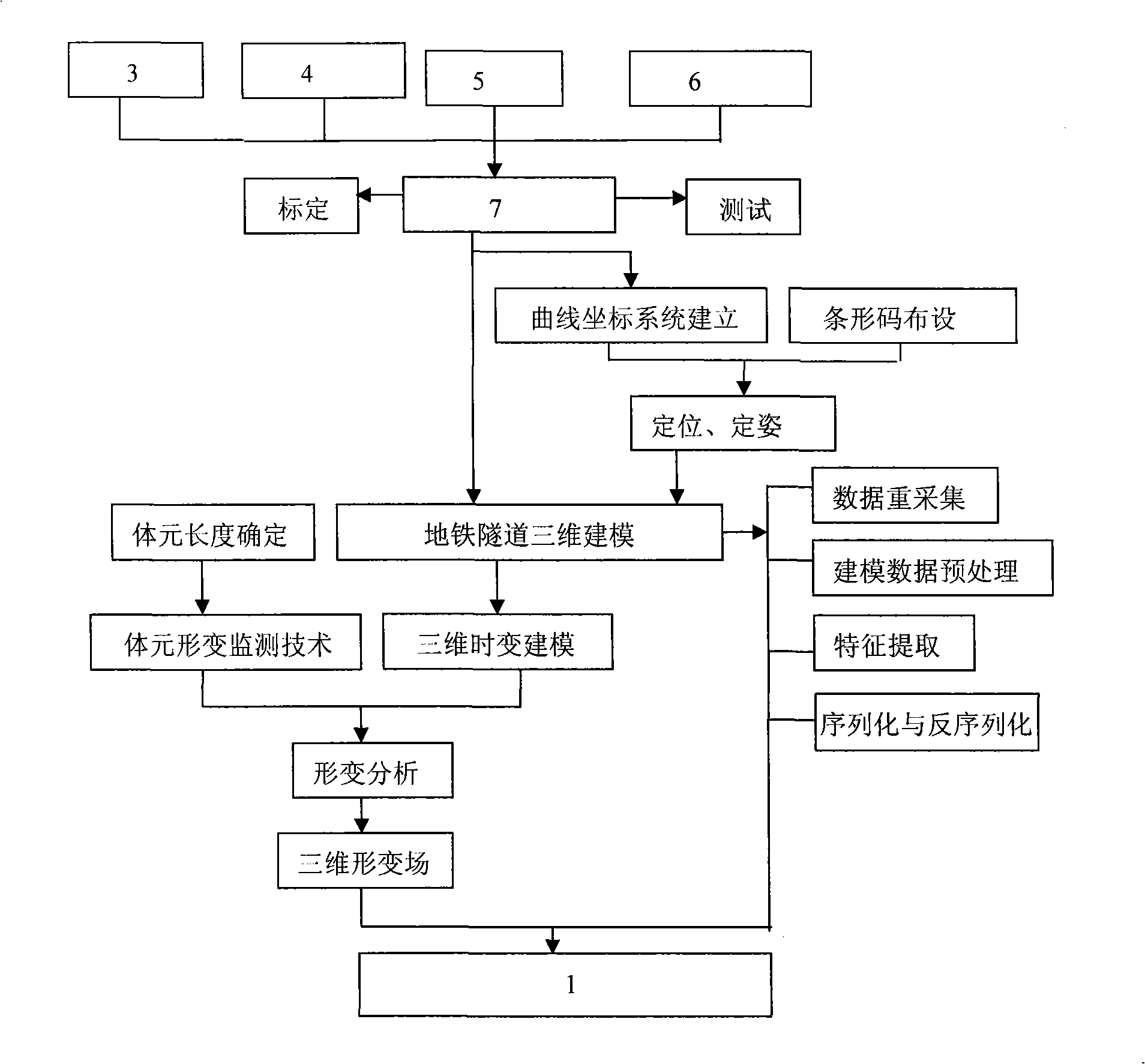
Tunnel volume element deformation movable monitoring system and method
InactiveCN101408410AQuick collectionDynamic acquisitionUsing optical meansProfile tracingPoint cloudMonitoring system
The invention discloses a tunnel body form deformation mobile monitoring system and a monitoring method thereof. The hardware comprises a laser scanner, a CCD camera, a speed meter, an inertial navigator, a central control unit and bar codes. The central operation control unit leads the hardware of each sensor to be synchronous, stores the data of each sensor and carries out the corresponding position and stature calculation so as to process the obtained point cloud data of the tunnel sections; the bar codes are distributed at the positions on the tunnel surface where the CCD camera can shoot and the storage position information of the bar codes is adopted as the position reference of moving carriers and sensors. The hardware of the tunnel body form deformation mobile monitoring system provided by the invention is helpful for quickly and dynamically collecting space data and for further carrying out the body form deformation analysis through three dimensional modeling and reconstruction of models so as to monitor the deformation process continuously.
Owner:SHANDONG UNIV OF SCI & TECH
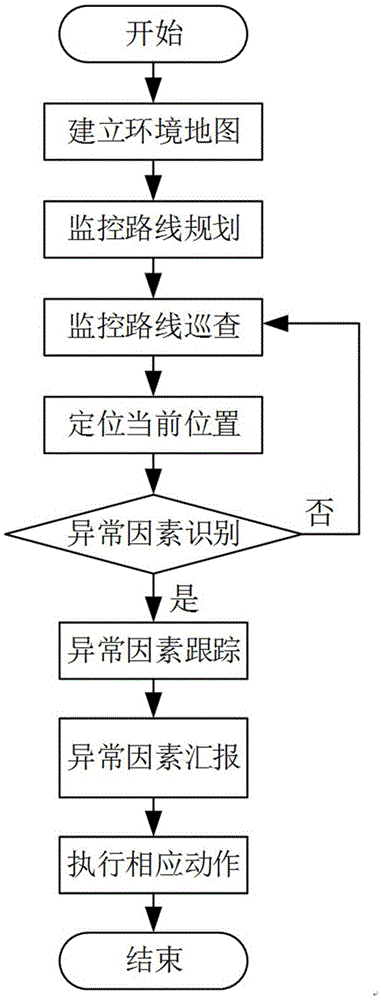
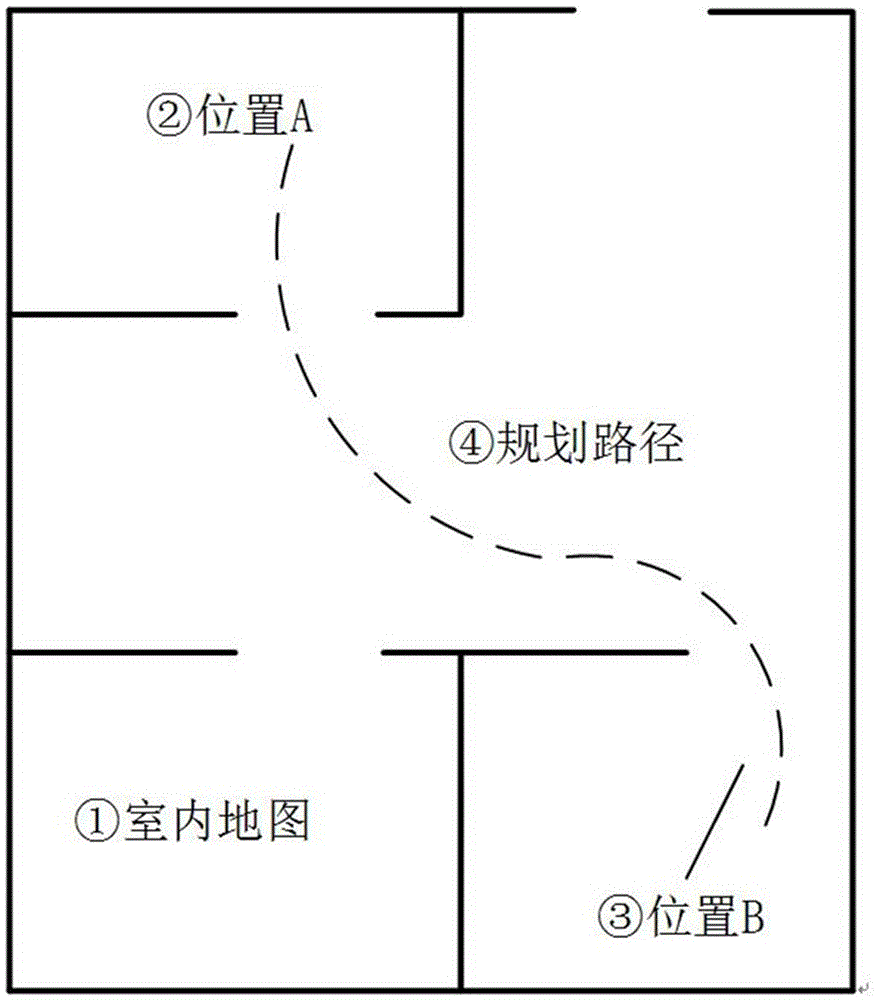
Robot security inspection method based on environment map and robot thereof
InactiveCN106598052AStrong initiativeAvoid monitoringTarget-seeking controlPosition/course control in two dimensionsEngineeringSecurity policy
The invention discloses a robot security inspection method based on an environment map and a robot thereof. The method comprises steps that a two-dimensional plane map of a whole monitoring region is established; monitoring routes are programmed; the present location position of the robot in the monitoring region is positioned; inspection steps are moved according to the programmed routes. Through the method and the robot thereof, traversal inspection is carried out according to the environment map to avoid monitoring dead angles; unsafe factors are actively discovered, and safety strategy confirmation is further carried out; the unsafe factors are actively tracked; normal work can be carried out in the night without auxiliary illumination. The method and the robot are advantaged in that strong initiative is realized, the unsafe factors are actively prevented, and validity, timeliness and stability of unannounced inspection are substantially improved.
Owner:NANJING AVATARMIND ROBOT TECH CO LTD
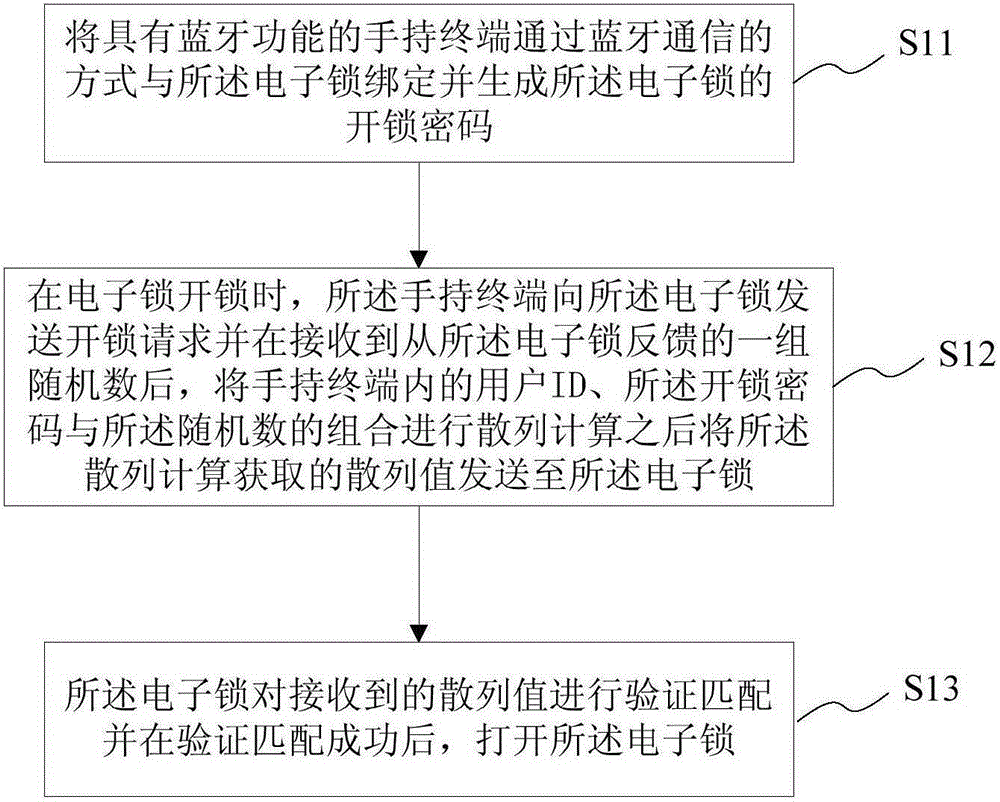
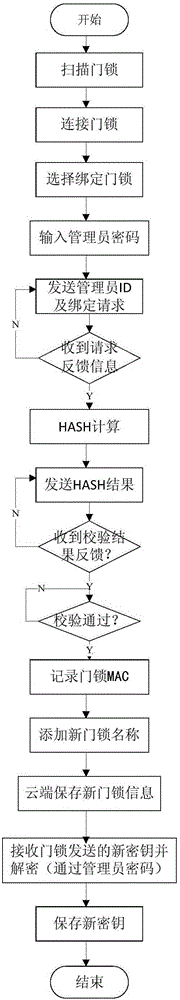
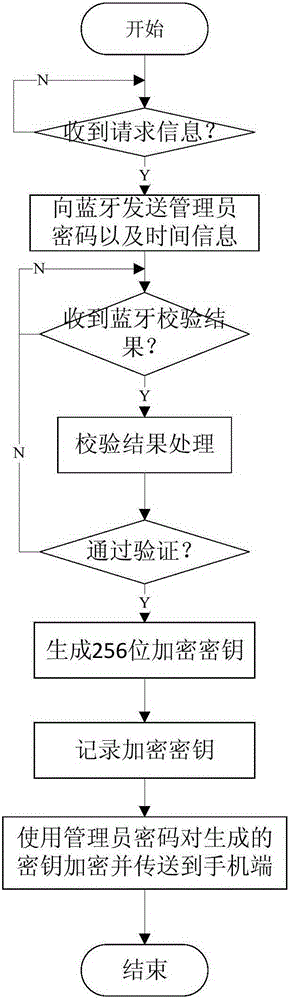
Bluetooth-based unlocking method, system and hand-held terminal and Bluetooth-based electronic lock
ActiveCN105184931AImprove securityAvoid monitoringIndividual entry/exit registersThird partyPassword
The invention provides a Bluetooth-based unlocking method, system and hand-held terminal and a Bluetooth-based electronic lock. The method comprises steps as follows: the hand-held terminal with a Bluetooth function is bound with the electronic lock in a Bluetooth communication manner, and an unlocking password of the electronic lock is generated; when the electronic lock is unlocked, the hand-held terminal sends an unlocking request and sends a hash value acquired through hash calculation to the electronic lock after a group of random numbers fed back from the electronic lock are received and a combination of user ID (identification), the unlocking password and the random numbers is subjected to hash calculation; the electronic lock matches the hash value acquired after hash calculation of the combination of the user ID, the unlocking password and the random numbers with a hash value received by the hand-held terminal, and the electronic lock is unlocked after matching succeeds. Interactive authentication is performed in a hash encryption manner, monitoring by a third party can be prevented, the condition of secret key disclosure is avoided, the unlocking speed is high, and the safety of the electronic lock is effectively improved.
Owner:上海觅奇智能科技有限公司
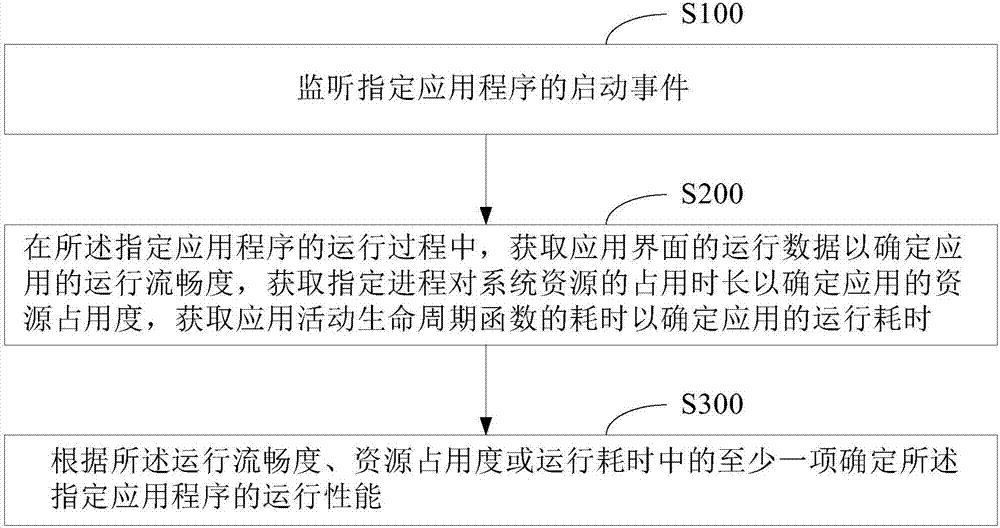
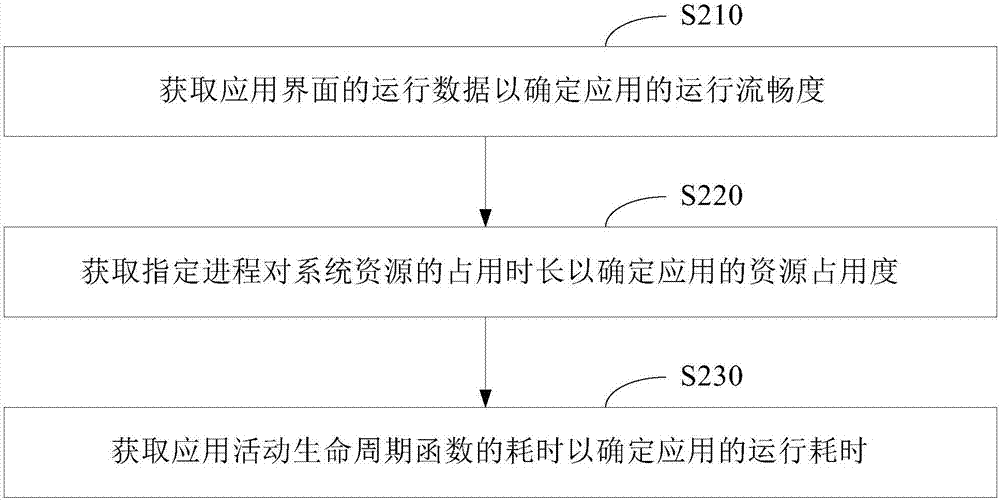
Method and device for determining operating performance of application program and mobile terminal
InactiveCN106874168AAvoid monitoringReduce collection workHardware monitoringOccupancy rateOperating system
The invention provides a method and a device for determining the operating performance of an application program. The method comprises the steps of monitoring a startup event of a specified application program, obtaining operating data of an application interface to determine the operating smoothness of the application in the operating process of the specific application program, obtaining occupation time of a specified application on a system resource to determine the resource occupancy rate of the application and obtaining elapsed time of an application activity assembly lifecycle function to determine the operating time of the application; and determining the operating performance of the specified application program according to at least one of the operating smoothness, the resource occupancy rate or the operating time. Only the specified application program is monitored, so that overall monitoring of all application programs can be avoided, the data collection work is reduced and the data collection efficiency is improved. Furthermore, the accuracy of judging the operating performance of the application can be effectively improved through collecting the data such as the operating smoothness, the resource occupancy rate and the operating time of the specified application. The invention further provides a mobile terminal.
Owner:BEIJING QIHOO TECH CO LTD
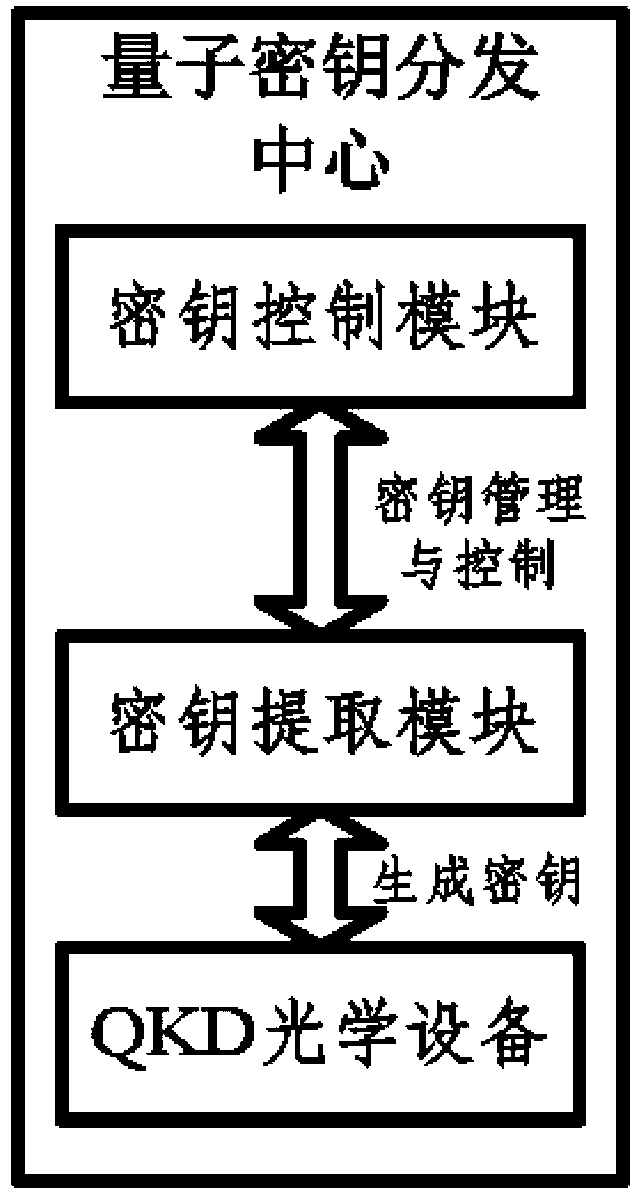
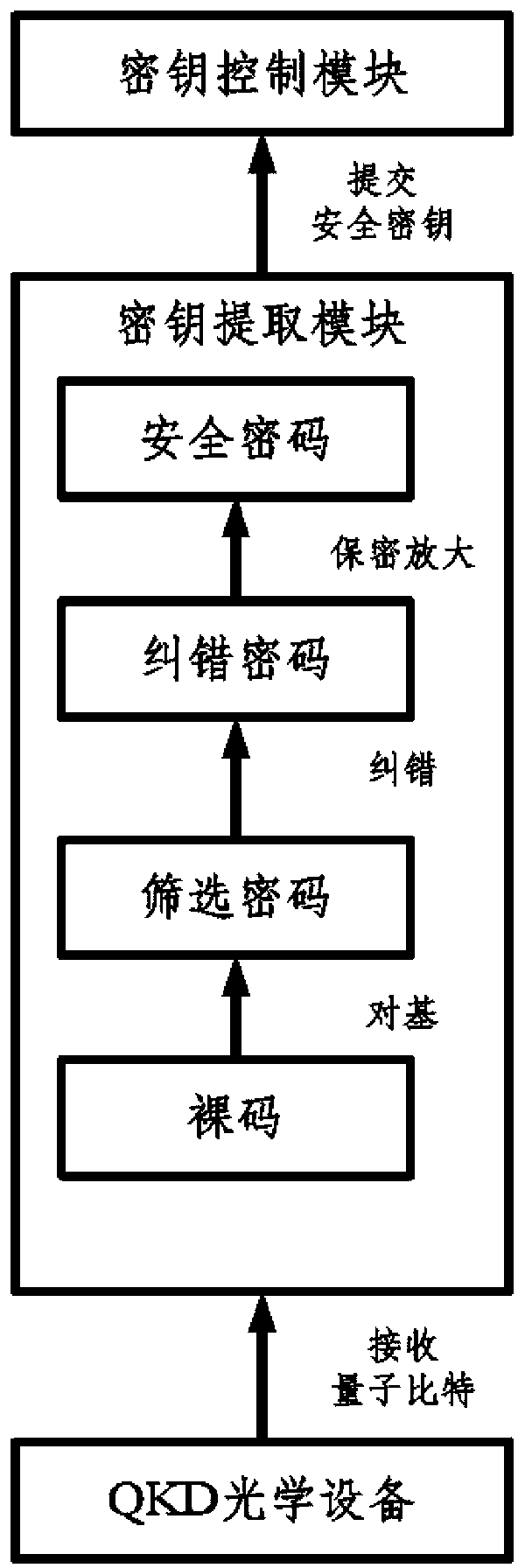
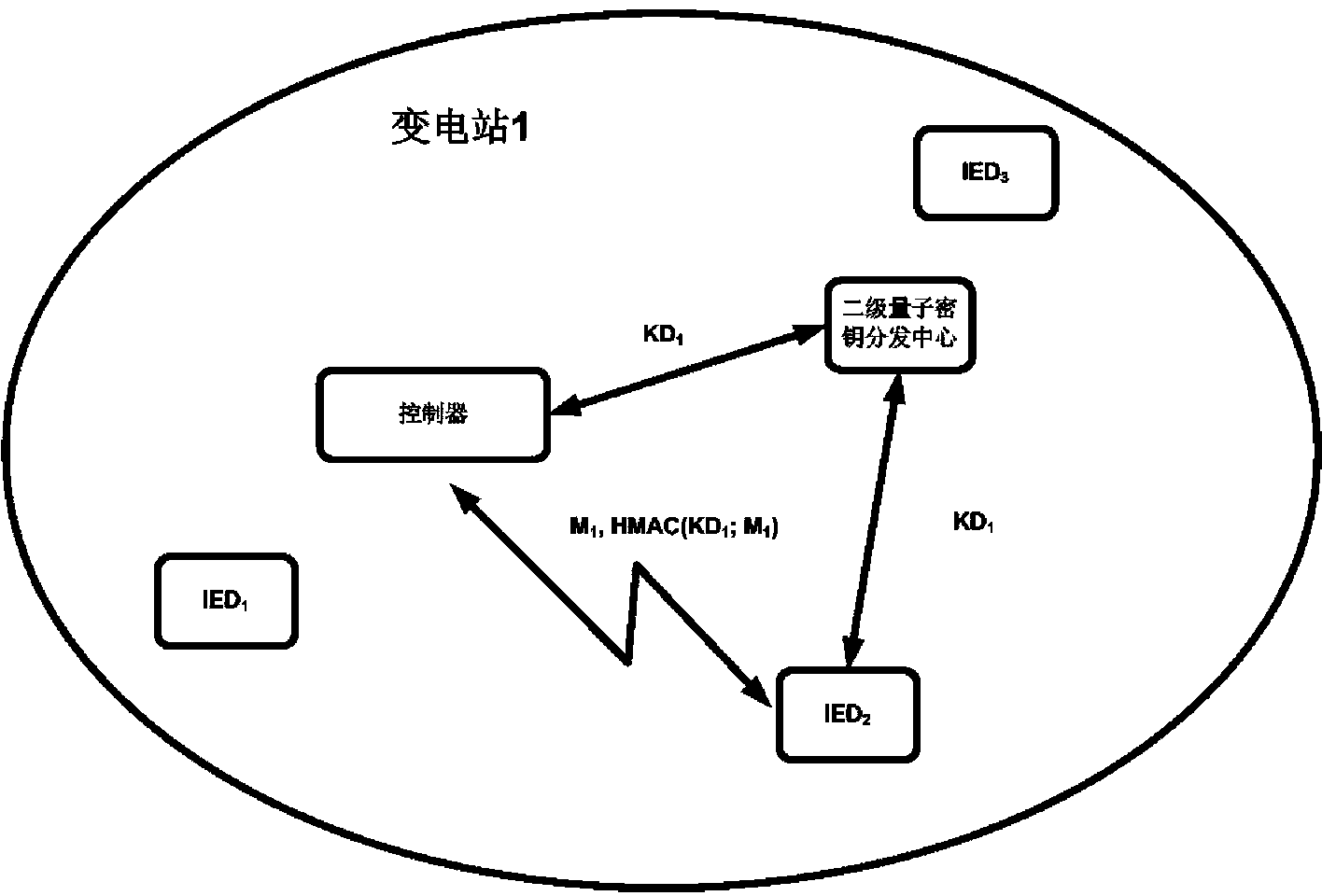
Transformer substation quantum communication model, quantum secret key distribution center and model achieving method
ActiveCN102983965AImprove efficiency and safetyEnhanced secure transportKey distribution for secure communicationKey distribution centerQuantum key distribution
The invention relates to a transformer substation quantum communication model, a quantum secret key distribution center based on the model and a model achieving method. The communication model is a quantum secret key distribution system and comprises a quantum secret key distribution (QKD) optical device, a secret key obtaining module and a secret key control module. The secret key control module, the secret key obtaining module and the QKD optical device are connected in sequence. The quantum secret key distribution center comprises two levels. A primary quantum secret key distribution center (QKDC) is configured in a control center, and a second QKDC is configured at the controller end of a transformer substation. By defining a password suite compatible with secret key distribution protocol and designing a secret key distribution method, the safety and the efficiency of secret key distribution are improved, safe transmission of data is strengthened, and stability and safety of a power system network in operation are guaranteed.
Owner:CHINA ELECTRIC POWER RES INST +2
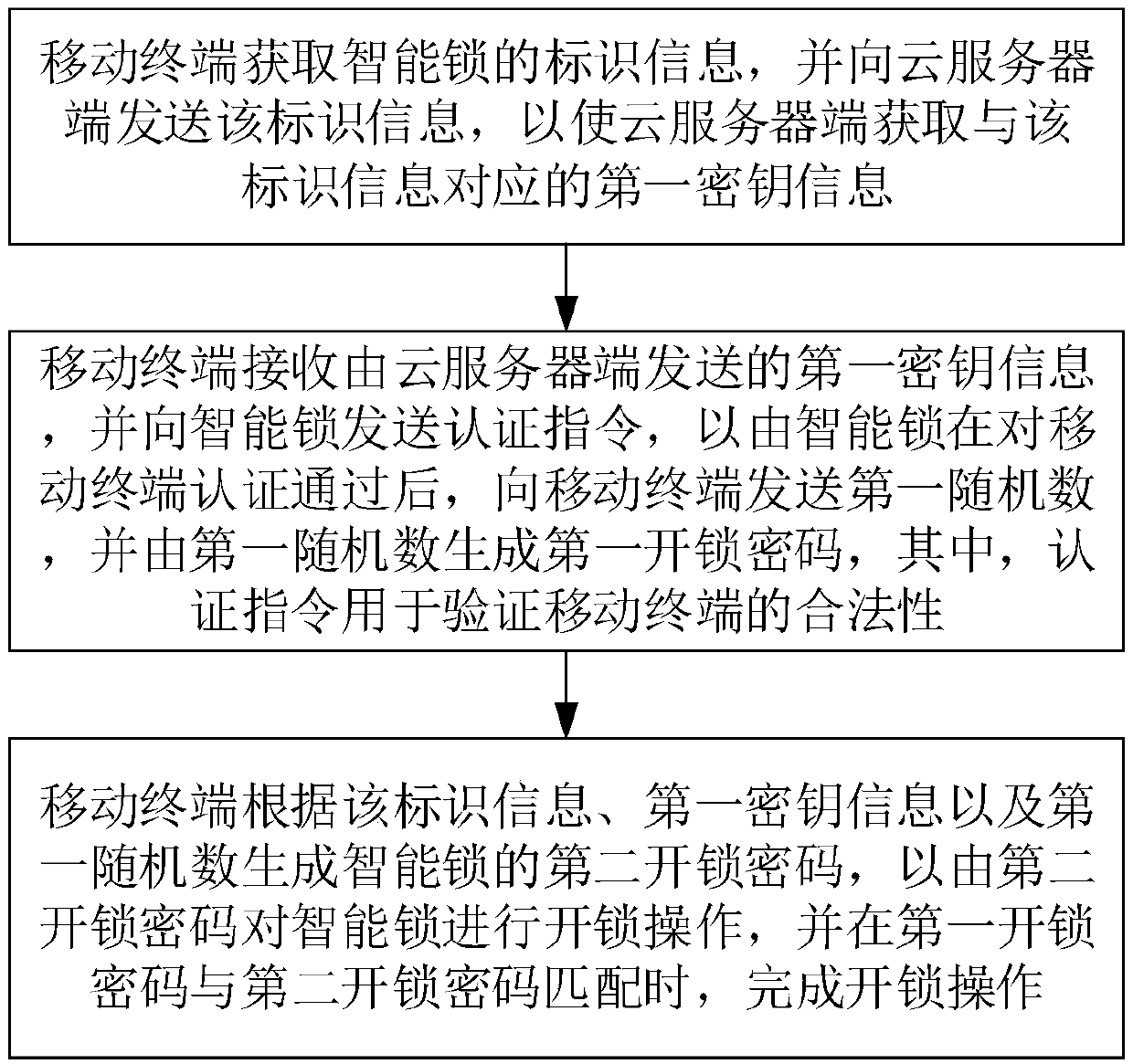
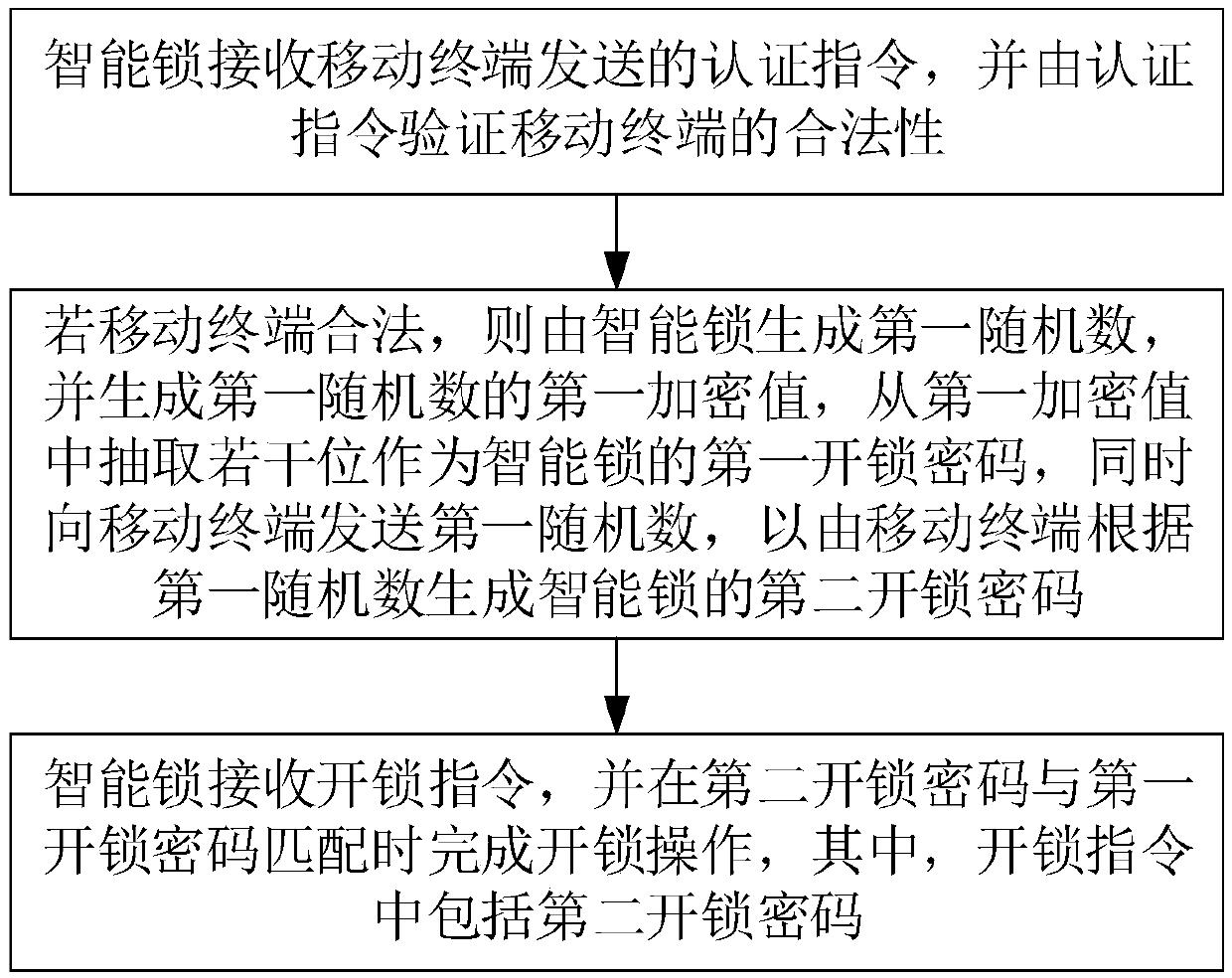
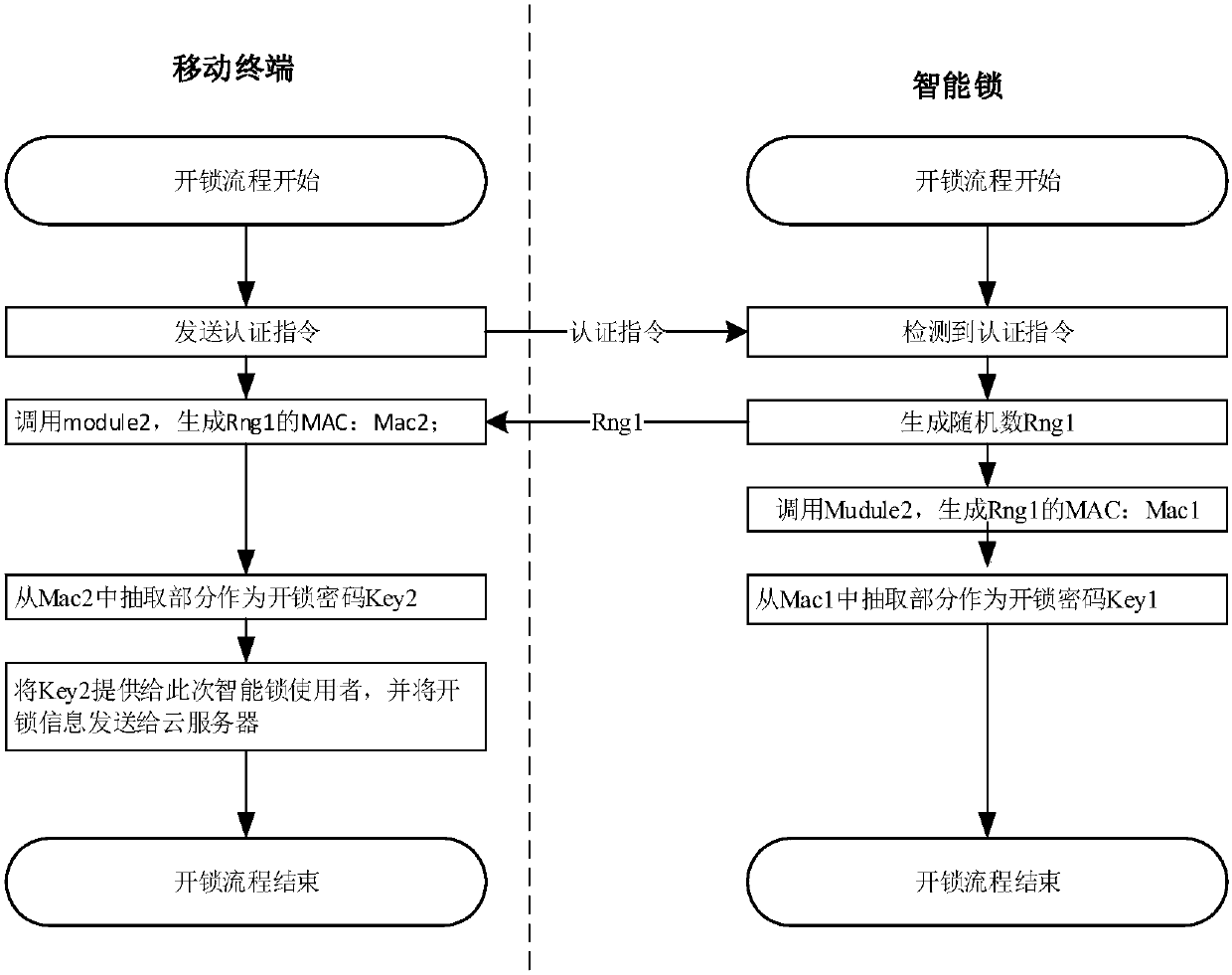
Control method and system for intelligent lock and related device
ActiveCN108055235AAvoid monitoringEnsure safetyIndividual entry/exit registersTransmissionComputer hardwareSecure communication
The invention discloses a control method and system for intelligent lock and a related device. The method comprises the steps that a mobile terminal acquires identification information of the intelligent lock and sends the identification information to a cloud server, so the cloud server acquires first key information corresponding to the identification information; the mobile terminal receives the first key information sent by the cloud server and sends an authentication instruction to the intelligent lock, so after the intelligent lock authenticates the mobile terminal successfully, the intelligent lock sends a first random number to the mobile terminal, and a first unlocking password is generated according to the first random number, wherein the authentication instruction is used for verifying legality of the mobile terminal; and the mobile terminal generates a second unlocking password of the intelligent lock according to the identification information, the first key information and the first random number, the unlocking operation is carried out on the intelligent lock according to the second unlocking password, and the unlocking operation is finished when the first unlocking password matches the second unlocking password. Through application of the method, the system and the related device, a secure communication demand among the cloud server, the intelligent lock and themobile terminal can be satisfied.
Owner:HUAZHONG UNIV OF SCI & TECH
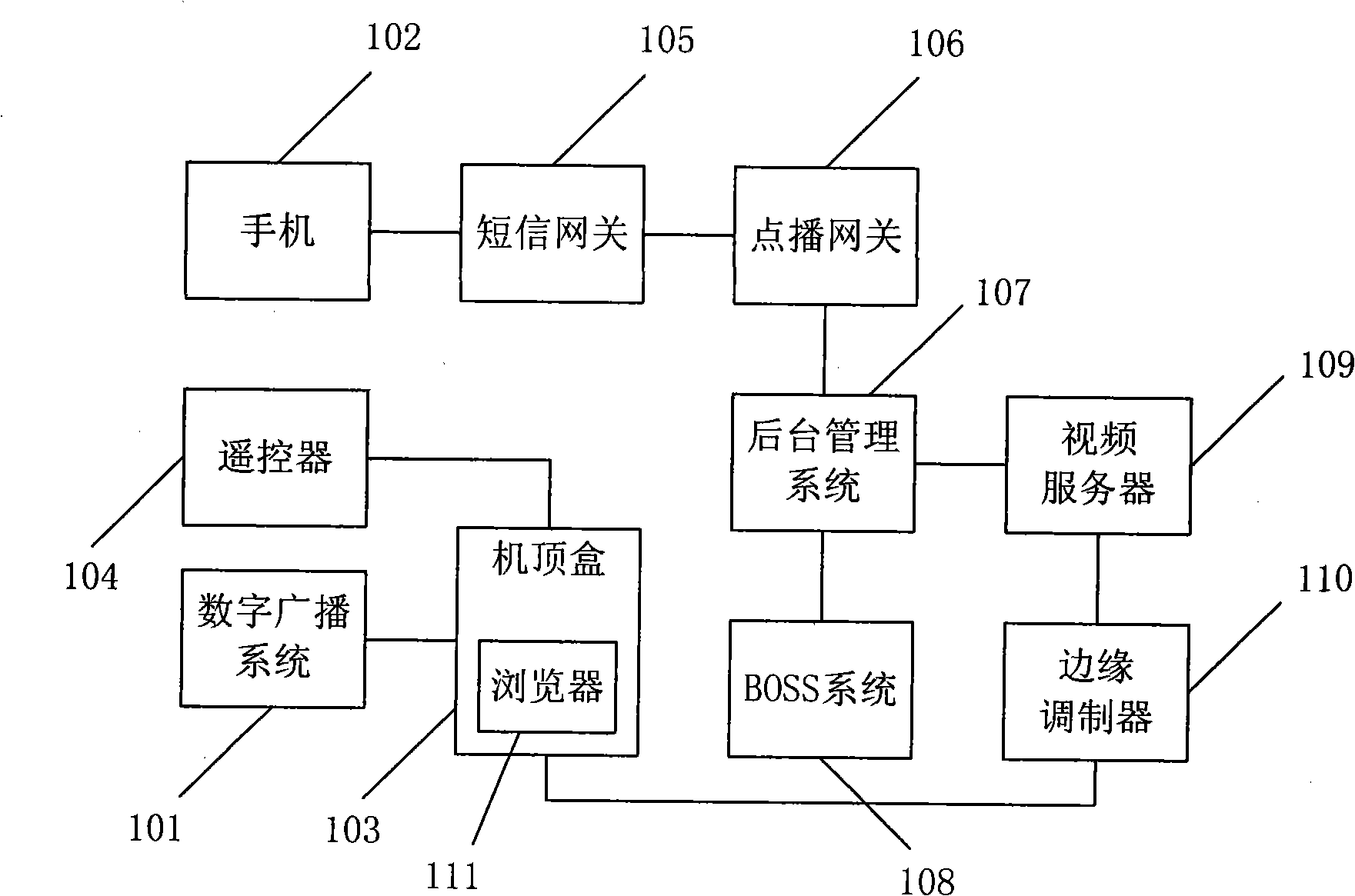
Program ordering method and system
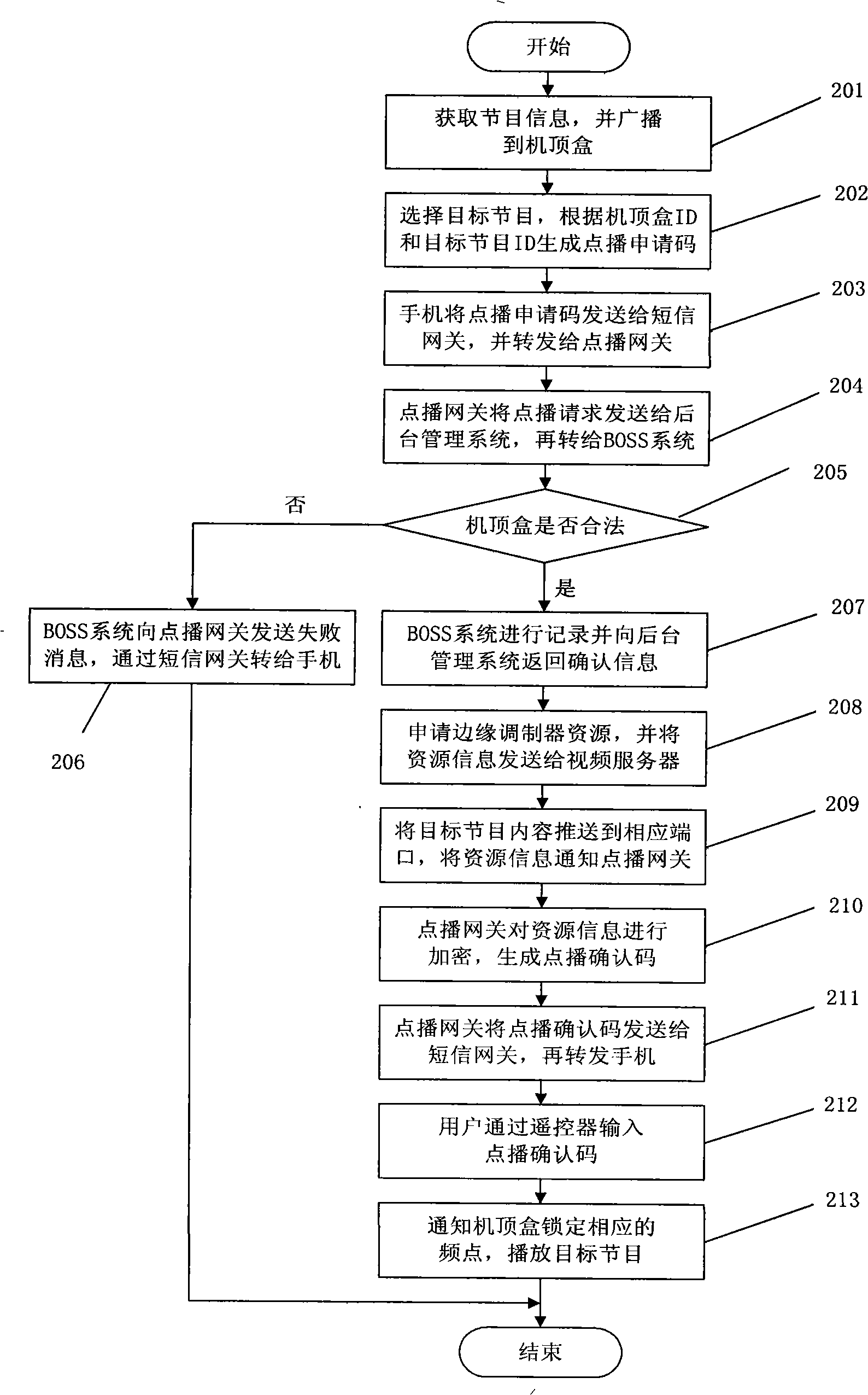
InactiveCN101309395AEasy to integrateAvoid monitoringTelevision system detailsAnalogue secracy/subscription systemsWeb browserResource information
The invention discloses a method and a system for displaying programs. Information is broadcasted to a set-top box by a digital broadcasting system; a target program is selected through a remote controller; a playing request code is generated by a set-top box browser according to the ID of the set-top box and the ID of the target program; the playing request code is sent to a short message gateway through a ,mobile phone, and then is forwarded to an playing gateway; a playing request is sent to a video playing system according to the playing request code; the video playing system applies for resources according to a resource list, and pushes the content of the target program to a corresponding port; the video playing system informs the playing gateway of resource information; the resource information is generated into an playing acknowledgement code through the on-demand gateway, and is forwarded to the mobile phone through the short message gateway; the playing acknowledgement code is input; corresponding frequency points are locked through the set-top box, to play the target program. By adopting the technical proposal of the method, the playing mode based on the handset and the set-top box can be provided, and the method is convenient and quick.
Owner:北京惠信博思技术有限公司
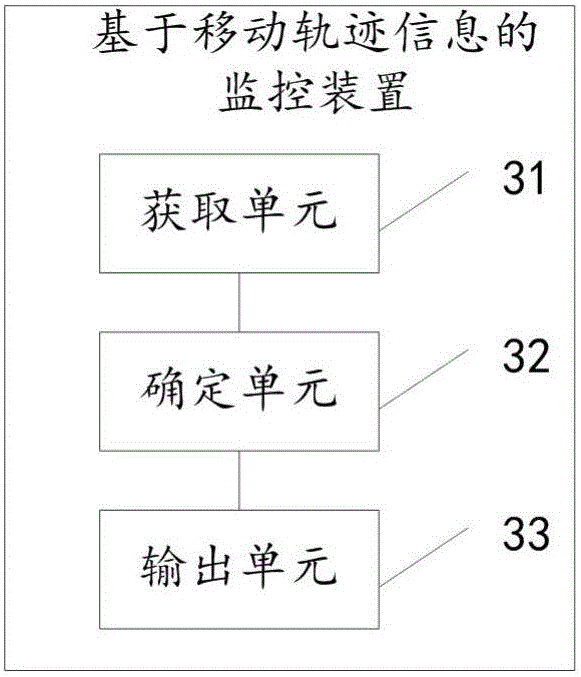
Monitoring method and device based on movement locus information
InactiveCN105916116AImprove monitoring efficiencyAvoid monitoringLocation information based serviceNetwork connectionReal-time computing
The invention discloses a monitoring method and device based on movement locus information, and relates to the technical field of communications. The method and the device can automatically track the locus of a user to be tracked, thereby improving the monitoring efficiency on the user to be tracked. The method comprises the steps of acquiring position information of each network connection device detecting identification information of a mobile terminal; determining user locus information corresponding to the identification information according to the position information of each network connection device; and if the user locus information satisfies a preset abnormal locus condition, outputting alarm information. The method and the device are suitable for monitoring based on movement locus information.
Owner:BEIJING QIHOO TECH CO LTD +1
Wireless sensor network node device used in underground coal mine
InactiveCN101621431AReduce energy consumptionExtended life cycleMining devicesNetwork topologiesLine sensorTunnel wall
The invention discloses a wireless sensor network node device used in an underground coal mine, which belongs to a hardware platform for personnel positioning and environmental monitoring based on a wireless sensor network in the underground coal mine. The wireless sensor network node device used in the underground coal mine is provided with wireless sensor fixed nodes (1) and wireless sensor mobile nodes (2); the sensor fixed nodes (1) are placed on a tunnel wall from space to space in the underground coal mine; and the sensor mobile nodes (2) are worn by mining personnel. The device has the following advantages: 1) the device has high positioning accuracy, and the mobile nodes carried by the personnel transmit wireless signals to communicate the approaching fixed nodes so as to determine the position of the device and improve the positioning precision; 2) both the wireless sensor fixed nodes and the wireless sensor mobile nodes have the capacity of bidirectional communication so as to accurately position the position of the personnel; 3) the design cost of the wireless sensor nodes is comparatively low, large amount of nodes can be arranged, and drain regions and blind points of positioning and monitoring are avoided; and 4) the arranged wireless sensor fixed nodes do not need wire connection, so the cost is low.
Owner:CHINA UNIV OF MINING & TECH
Electricity usage monitoring method and system
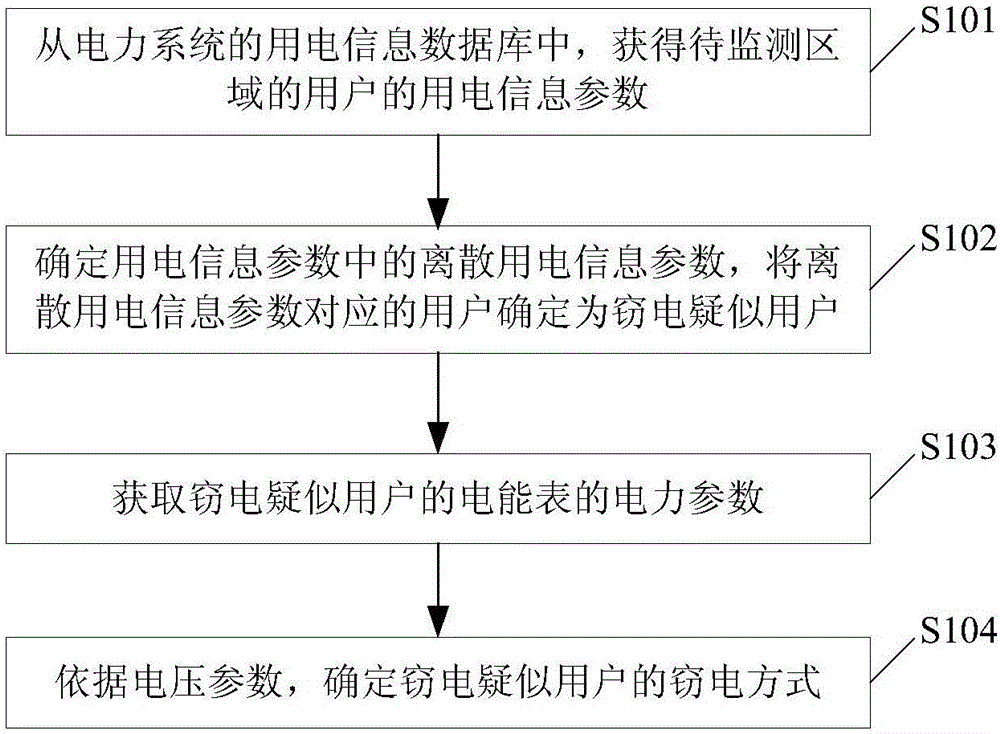
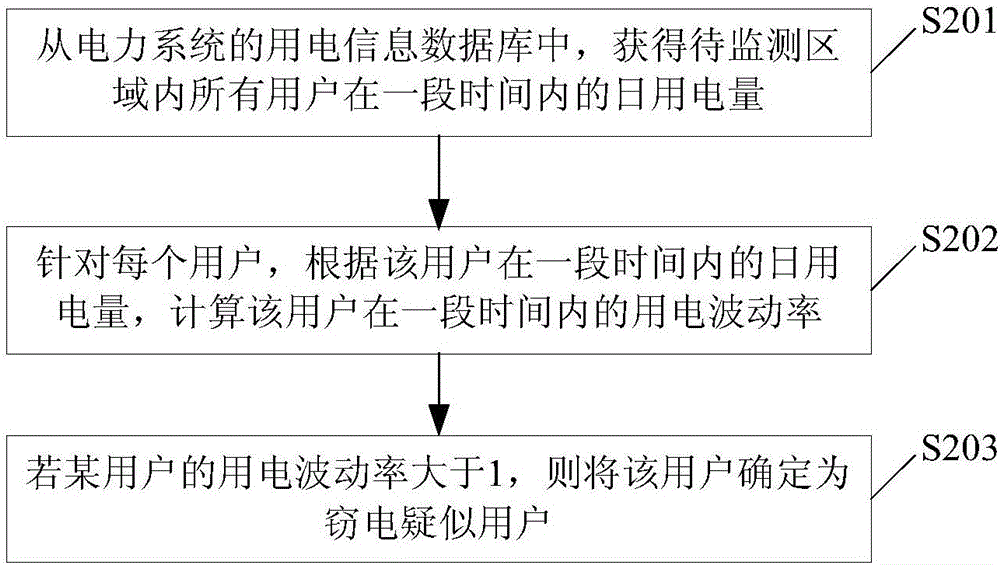
ActiveCN106645935AAvoid monitoringImprove monitoring efficiencyElectrical measurementsElectricityMonitoring system
The application provides an electricity usage monitoring method which comprises the following steps: a zone to be monitored is determined, a suspected electricity larceny user is preliminarily determined via electricity usage information parameters of the user in an electricity usage information database, electric power data of the suspected electricity larceny user is monitored, whether the suspected electricity larceny user is an electricity larceny user can be determined, and an electricity larceny mode of the electricity larceny user can be determined. According to the electricity usage monitoring method, users in the zone to be monitored are subjected to screening operation, monitoring of all users in the zone can be prevented, monitoring efficiency can be improved, the electricity larceny mode can be determined, and a basis is provided for human determination in a next step. The application also provides an electricity usage monitoring system to ensure application and implementation of the method in practice.
Owner:STATE GRID XIANGSHAN POWER SUPPLY +2
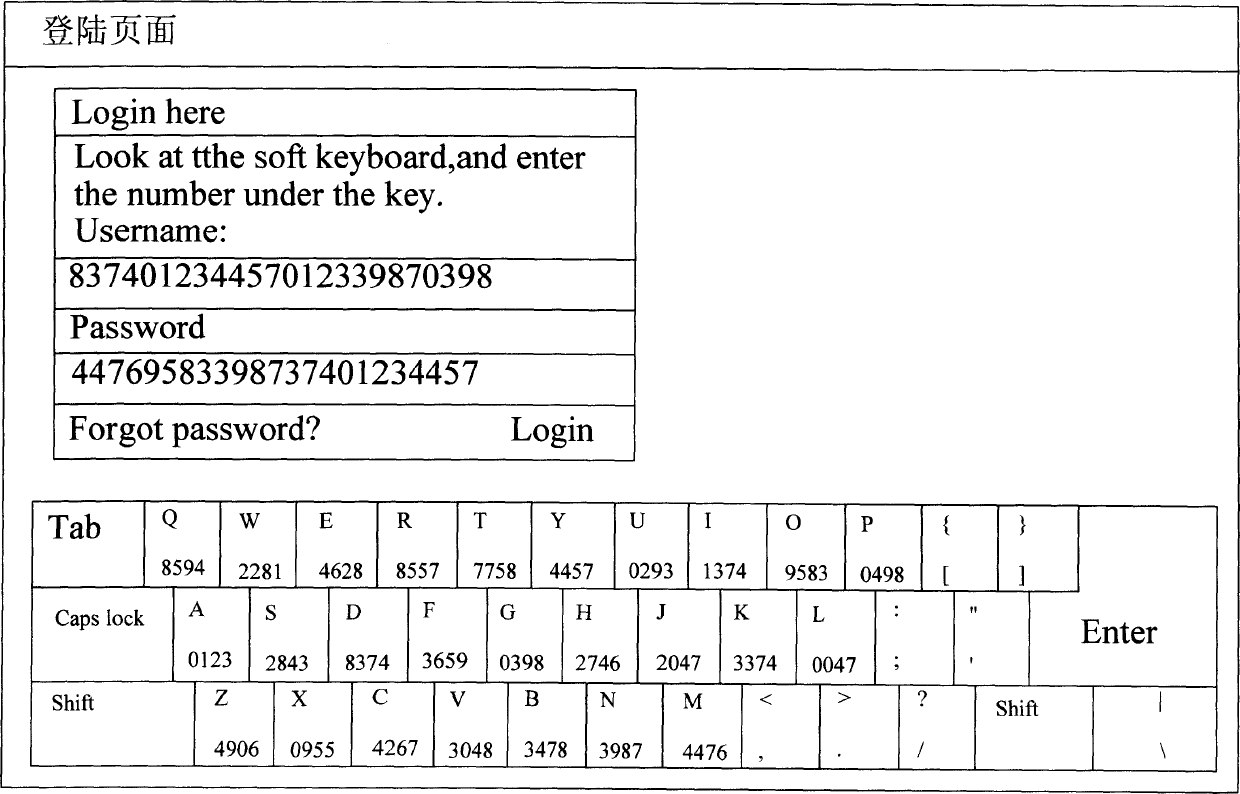
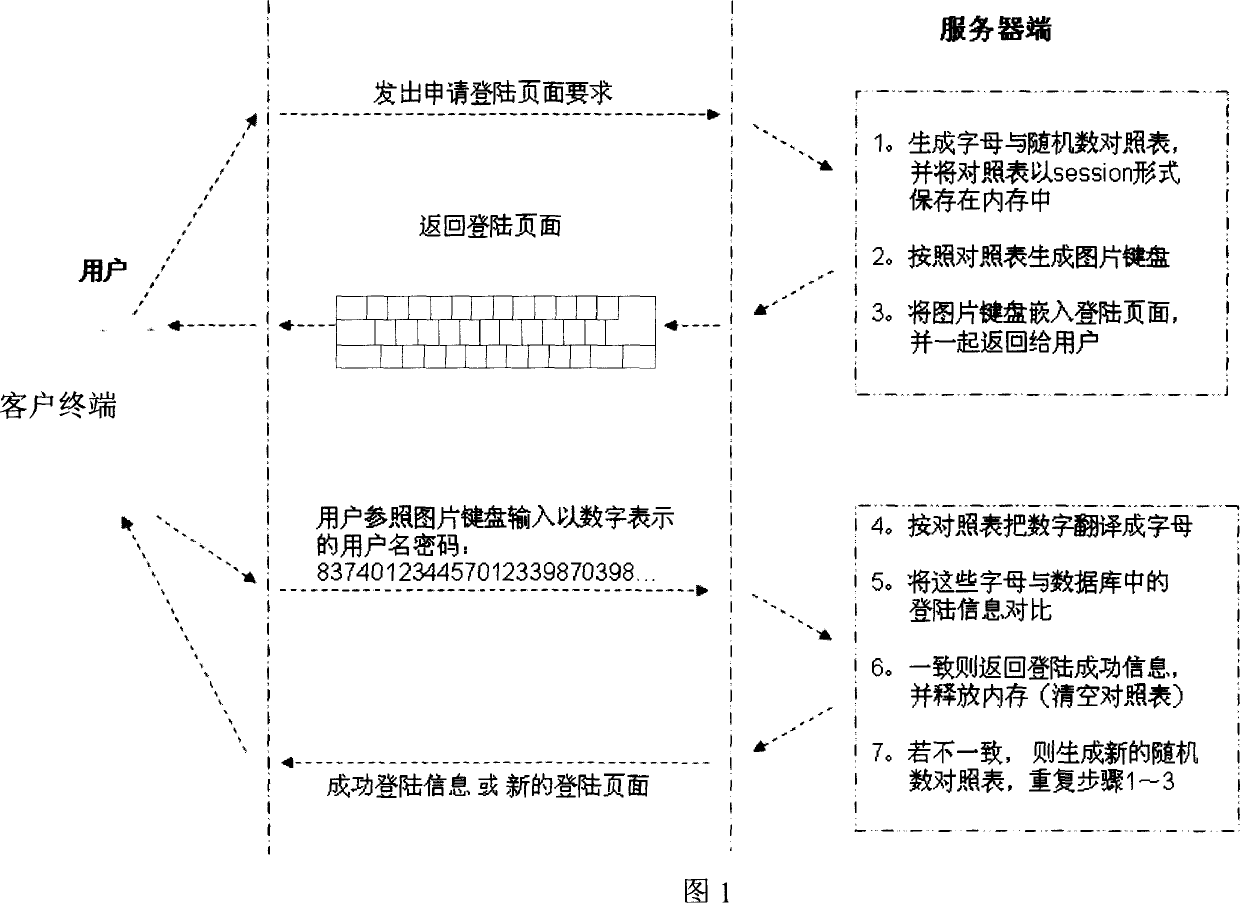
Network encryption system based on picture keyboard and operating method thereof
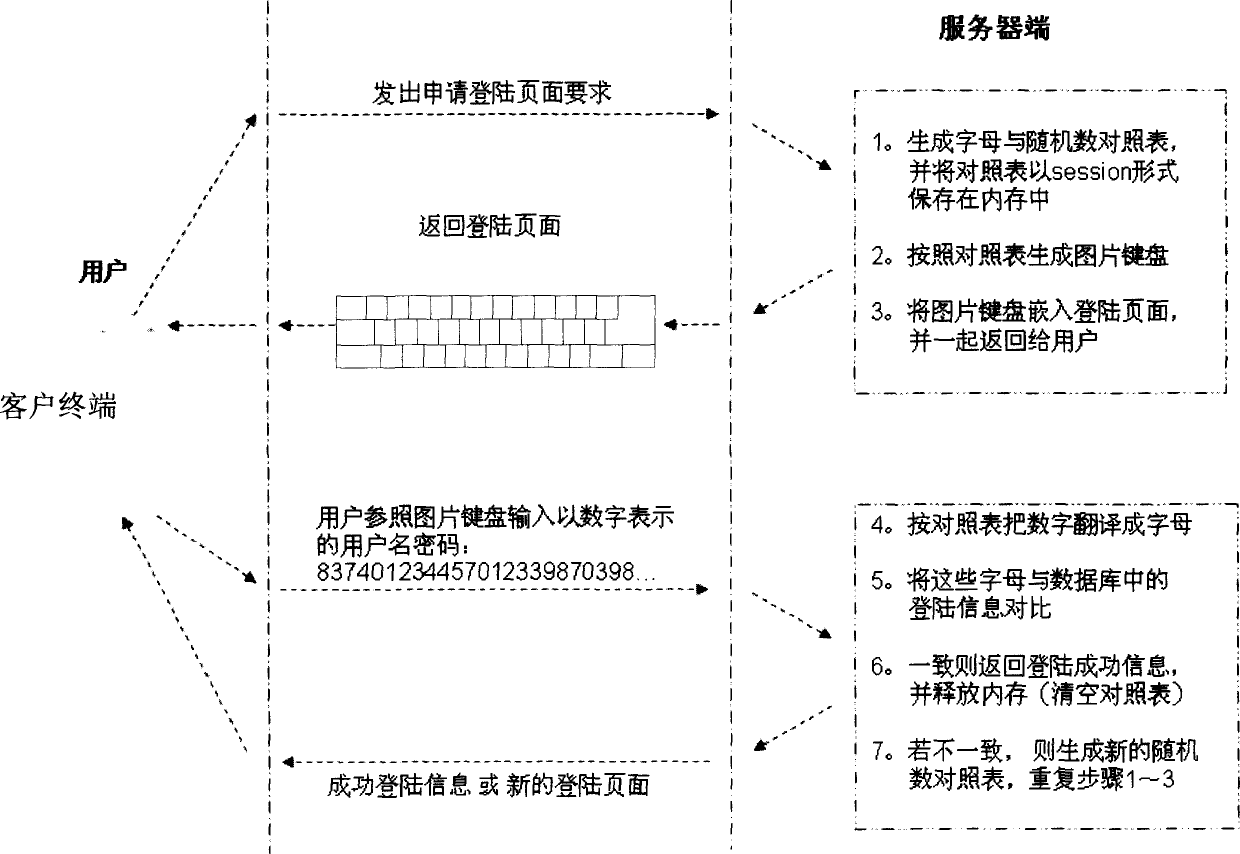
InactiveCN1825796AOvercoming theftOvercoming the problem of decipheringUser identity/authority verificationClient-sideComputer science
This invention discloses a system for realizing ciphered register or log of customer ends in the way of identity verification and a method, in which, the operation method includes: a customer end applies for register or log, a server responds it and generates a contrast list of each key character and an input code randomly and generates a contrast list of a soft keyboard or picture format then to send the picture, the register or log-on pages to the customer end, which displays it, a user logs on the register or the log verification information based on the keyboard picture or that of the contrast list to be transmitted to the server to check it in terms of the list.
Owner:刘大扬
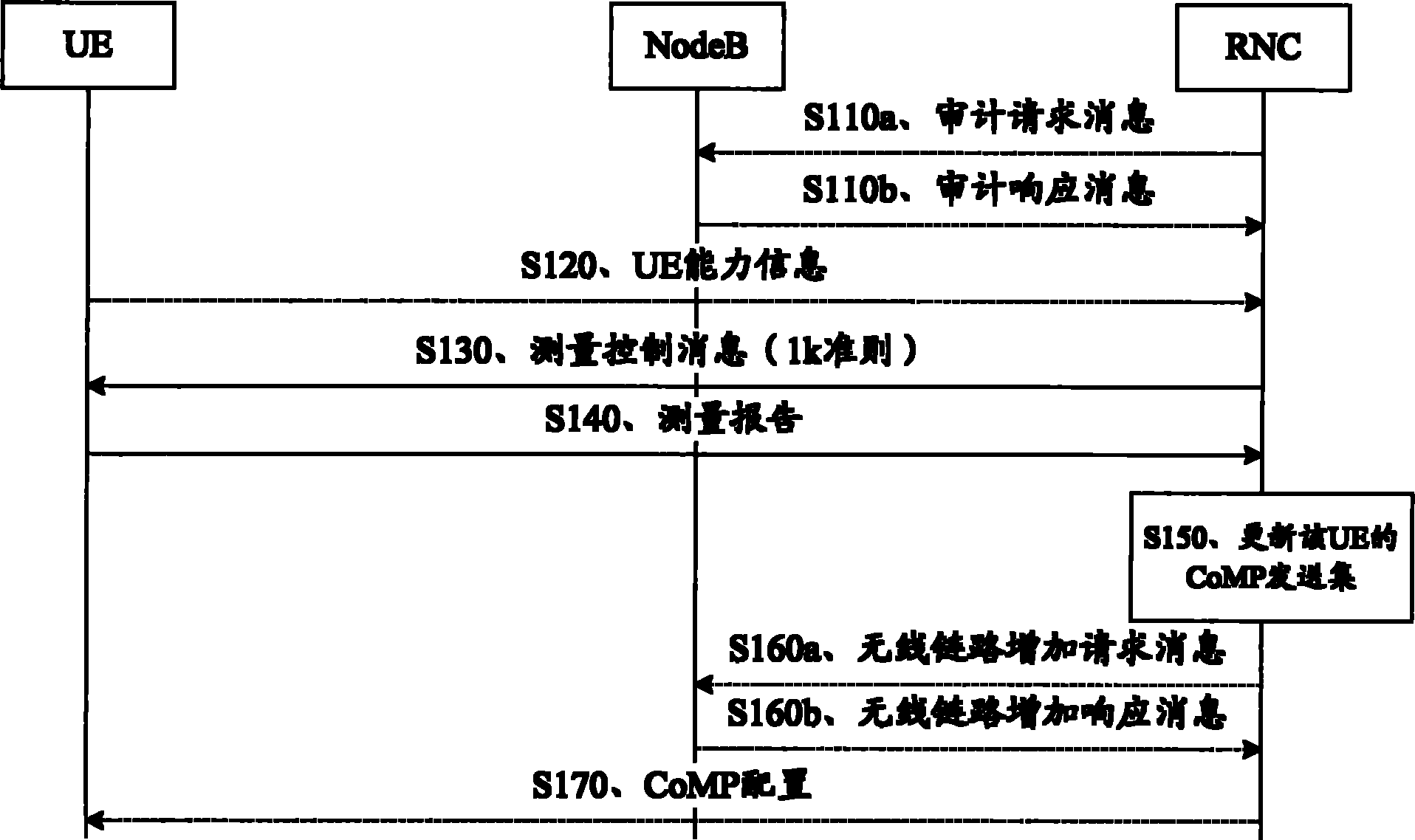
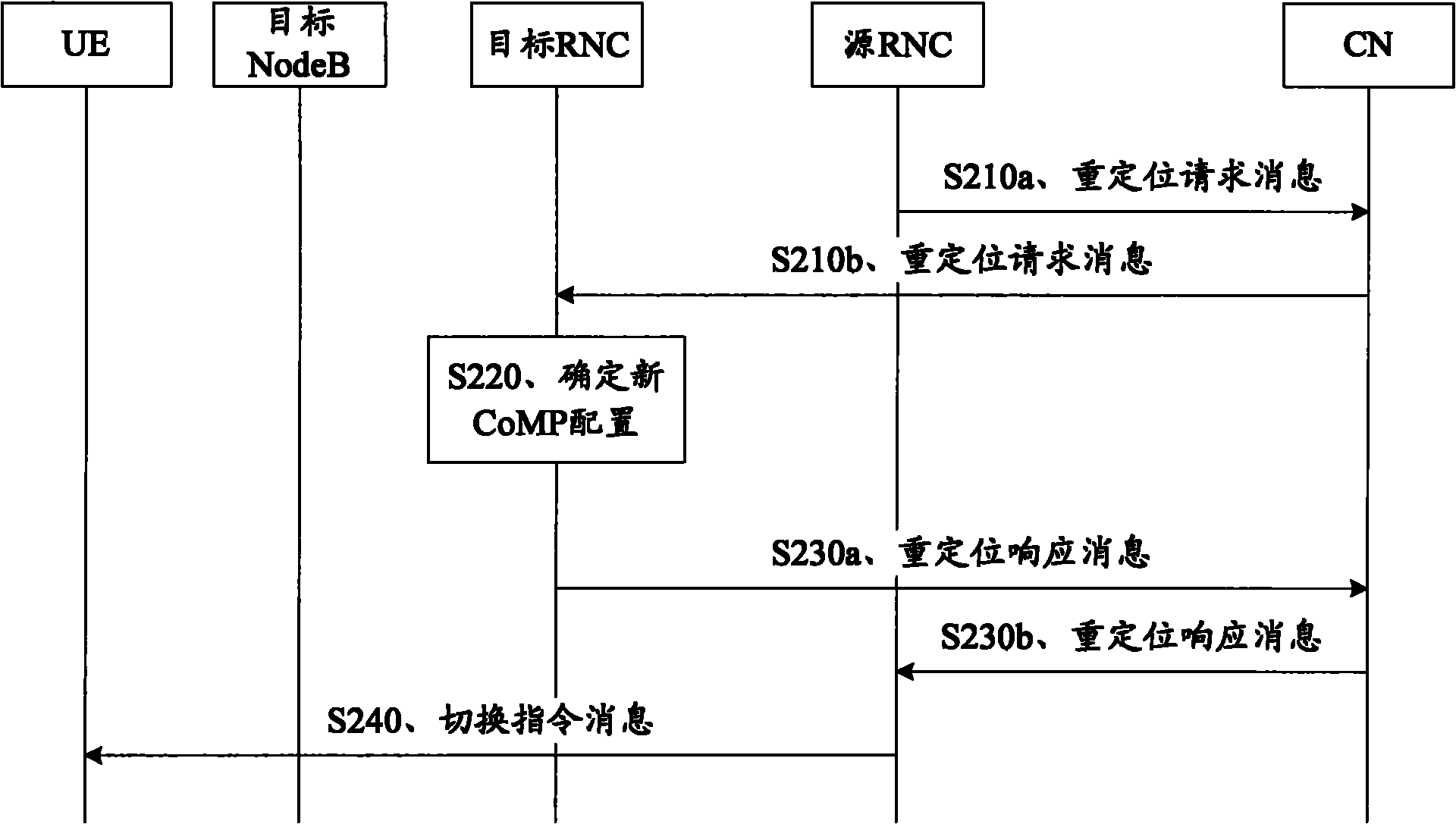
Method and device for updating CoMP (Coordinated Multi-point Transmission) sending set
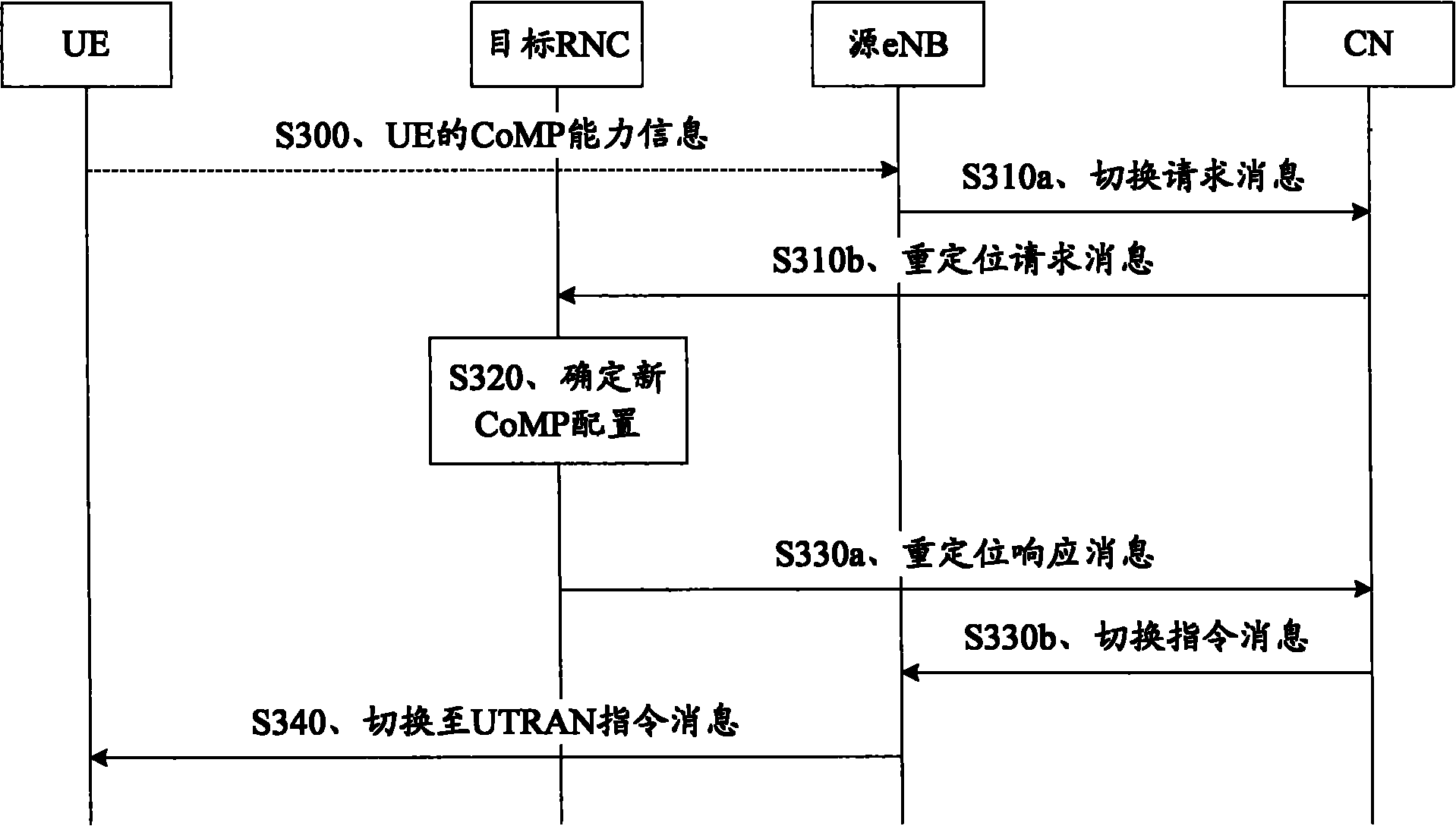
InactiveCN102255641AFlexible adjustmentImprove performanceSite diversityWireless communicationTelecommunicationsCell mass
The embodiment of the invention provides a method and a device for updating a CoMP (Coordinated Multi-point Transmission) sending set. The method for updating the CoMP sending set comprises the following steps: sending a 1k rule to UE (User Equipment) by an RNC (Radio Network Controller) and receiving a measurement report sent by the UE when the 1k rule is met, and updating the CoMP sending set of the UE by the RNC according to the measurement report, wherein the 1k rule contains any following condition for the UE to send the measurement report: cell mass of a cell which belongs to an activating set and does not belong to the CoMP sending set is more than the cell mass of at least one cell in the CoMP sending set, or cell mass of a cell which belongs to an activating set and does not belong to the CoMP sending set is more than an average value or weighted average value of the cell mass of at least two cells in the CoMP sending set. The method provided by the embodiment of the invention can be used for updating the CoMP sending set so as to flexibly adjust CoMP cooperated cells, thereby being beneficial to further improvements of the whole property of cells and the performance of cell edge users.
Owner:HUAWEI TECH CO LTD
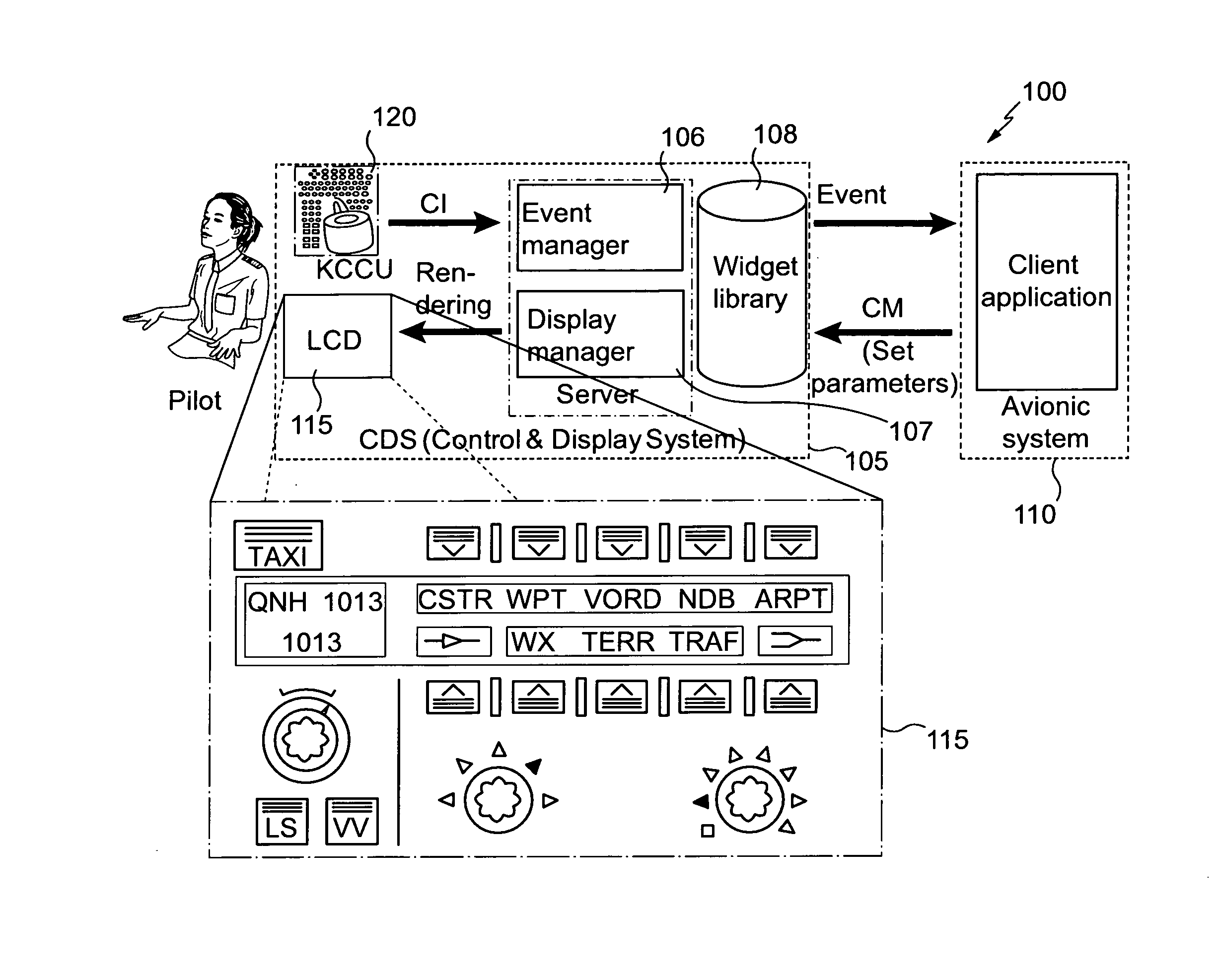
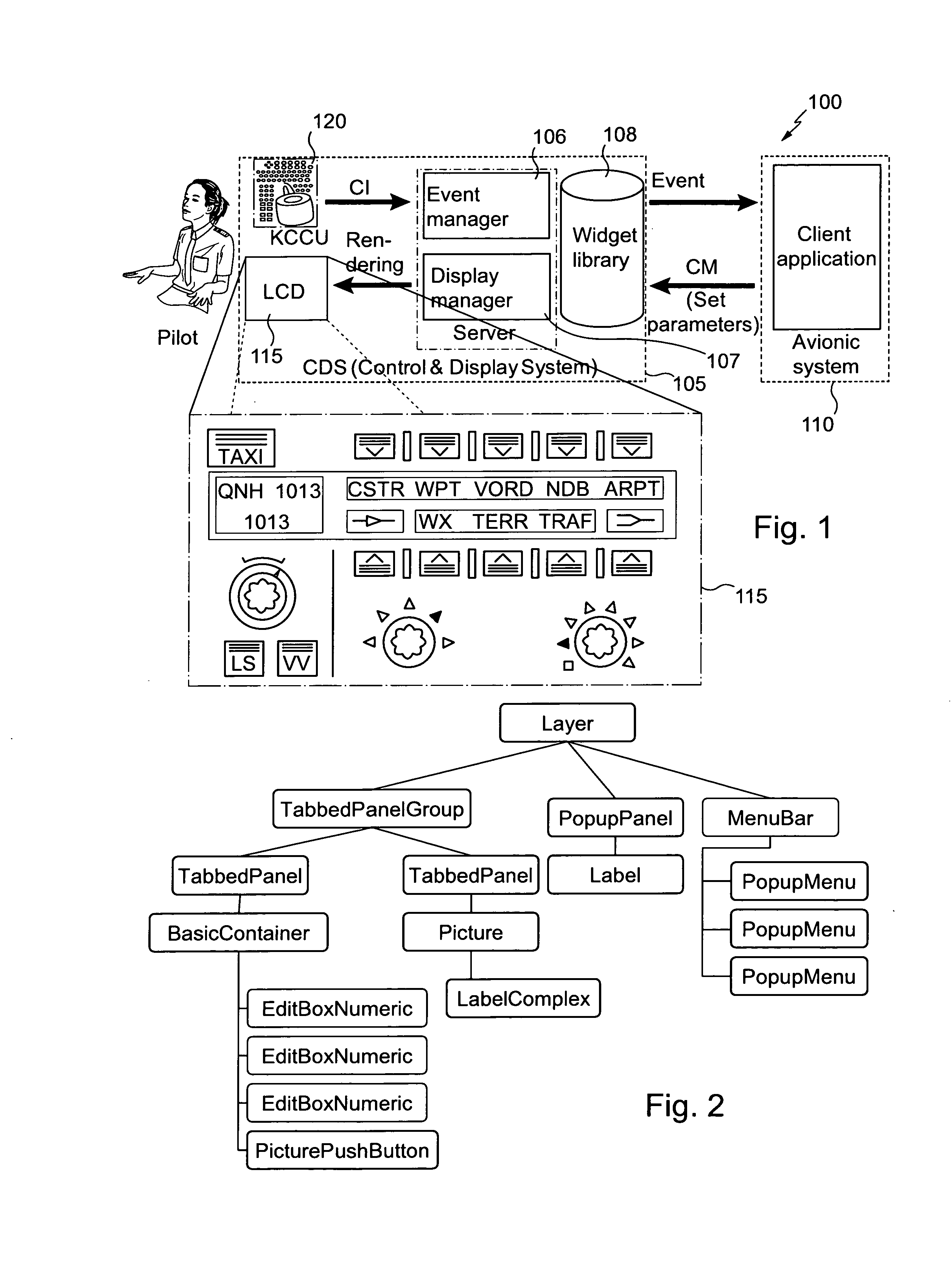
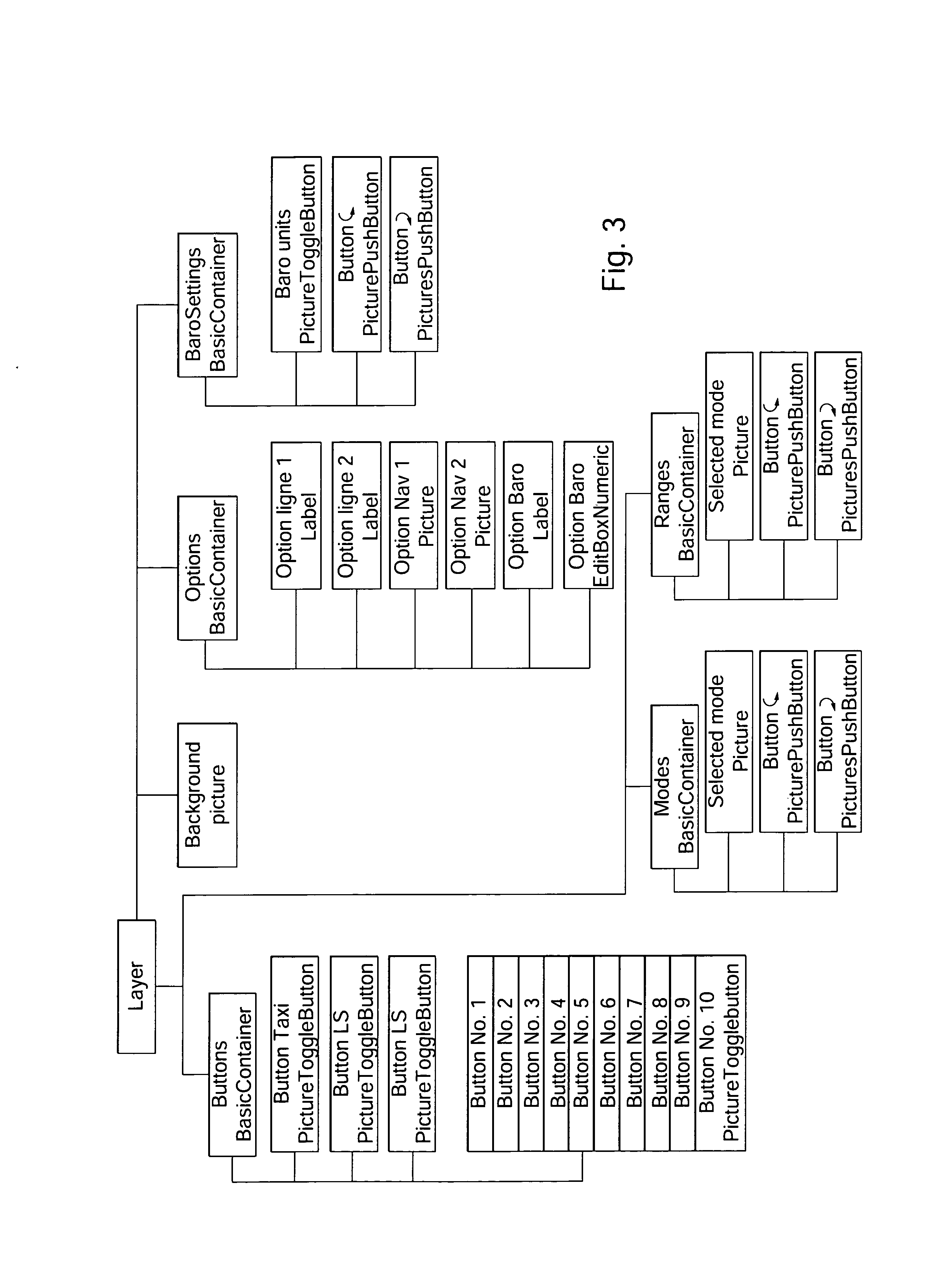
Method and system for monitoring a graphical interface in an aircraft cockpit
ActiveUS20130179842A1Raise security concernsPreventing situationError detection/correctionExecution for user interfacesGraphicsGraphical user interface
The invention relates in particular to a method and a system for monitoring a graphical interface in a computer system of an aircraft cockpit. The method comprises, in addition to the display of a graphical interface of a client application based on a tree structure of graphical interaction objects composing said graphical interface, the following steps: obtaining a plurality of graphical interaction objects having a tree-structure organization; creating and adding, to said obtained tree structure, at least one new graphical interaction object defining a critical graphical display zone; modifying the tree-structure dependency of at least one critical graphical interaction object, of the obtained tree structure to make it dependent from the new graphical interaction object defining the critical zone; and performing critical monitoring only of the critical graphical objects attached to the critical zone.
Owner:AIRBUS OPERATIONS (SAS)
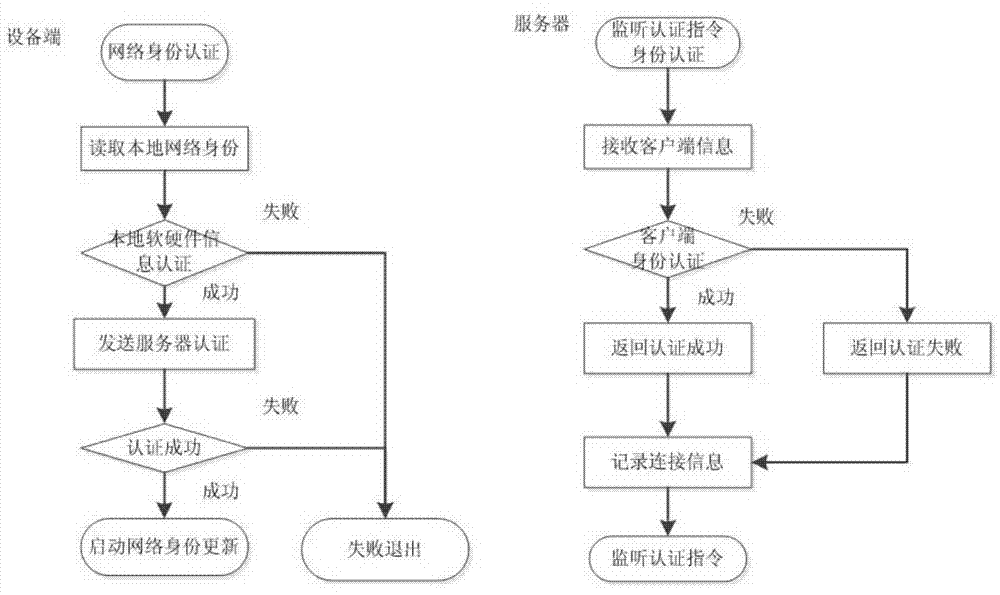
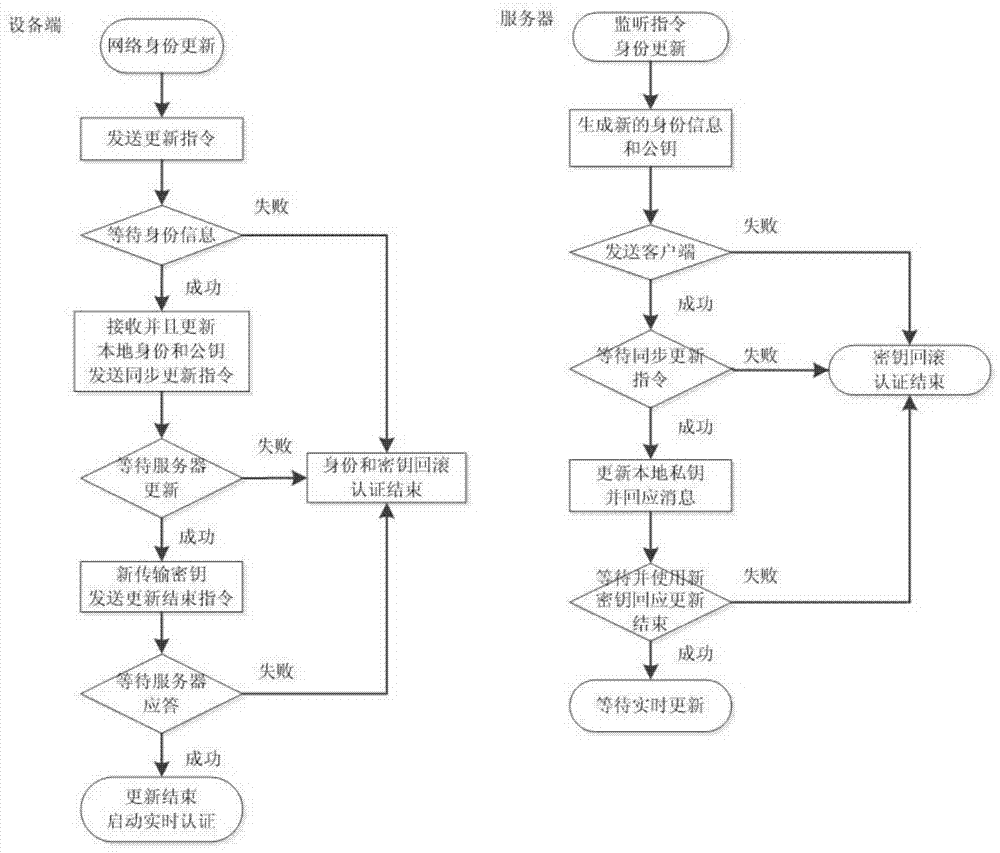
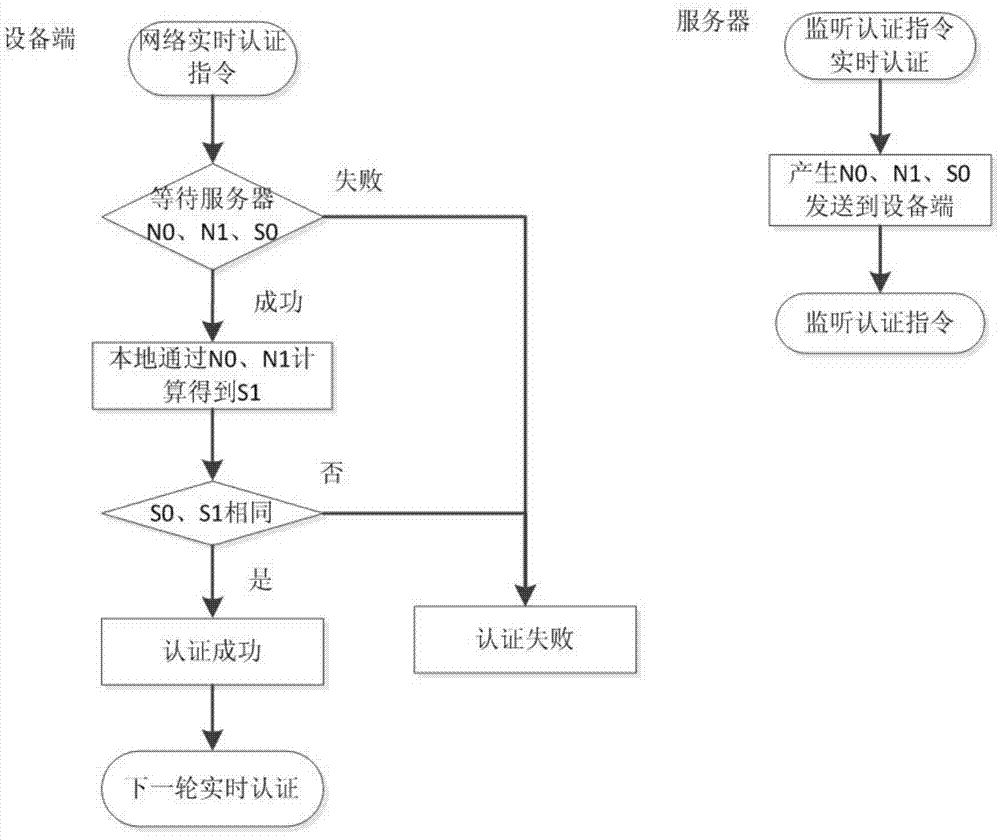
Network authentication method and system based on data link encryption transmission
ActiveCN104125239AIncrease the cost of crackingPrevent link snoopingSecuring communicationNetwork keyData monitoring
The invention relates to a network authentication method and system based on data link encryption transmission. The method is characterized in that the network link data are encrypted by the asymmetric algorithm and then transmitted, which avoids network monitoring and input; the network identity information is the specific device hardware and software information and has the uniqueness; a network key and the identity information are updated during starting the network authentication, in order to limit the ageing cycle of the network transmission key and the identity information; the symmetric encryption algorithm is carried out for random authentication, namely, real-time authentication, and thereby, the difficulty at breaking the data monitoring is raised, and transferring the device to other place to operate after the identity is authenticated successfully is effectively prevented. With the adoption of the method and system, the link can be effectively prevented from being monitored, and authentication files are prevented from releasing and spreading; once the authentication files are released and used and a legal user feeds back timely, a server can timely find out the device network information of a device end.
Owner:RUN TECH CO LTD BEIJING
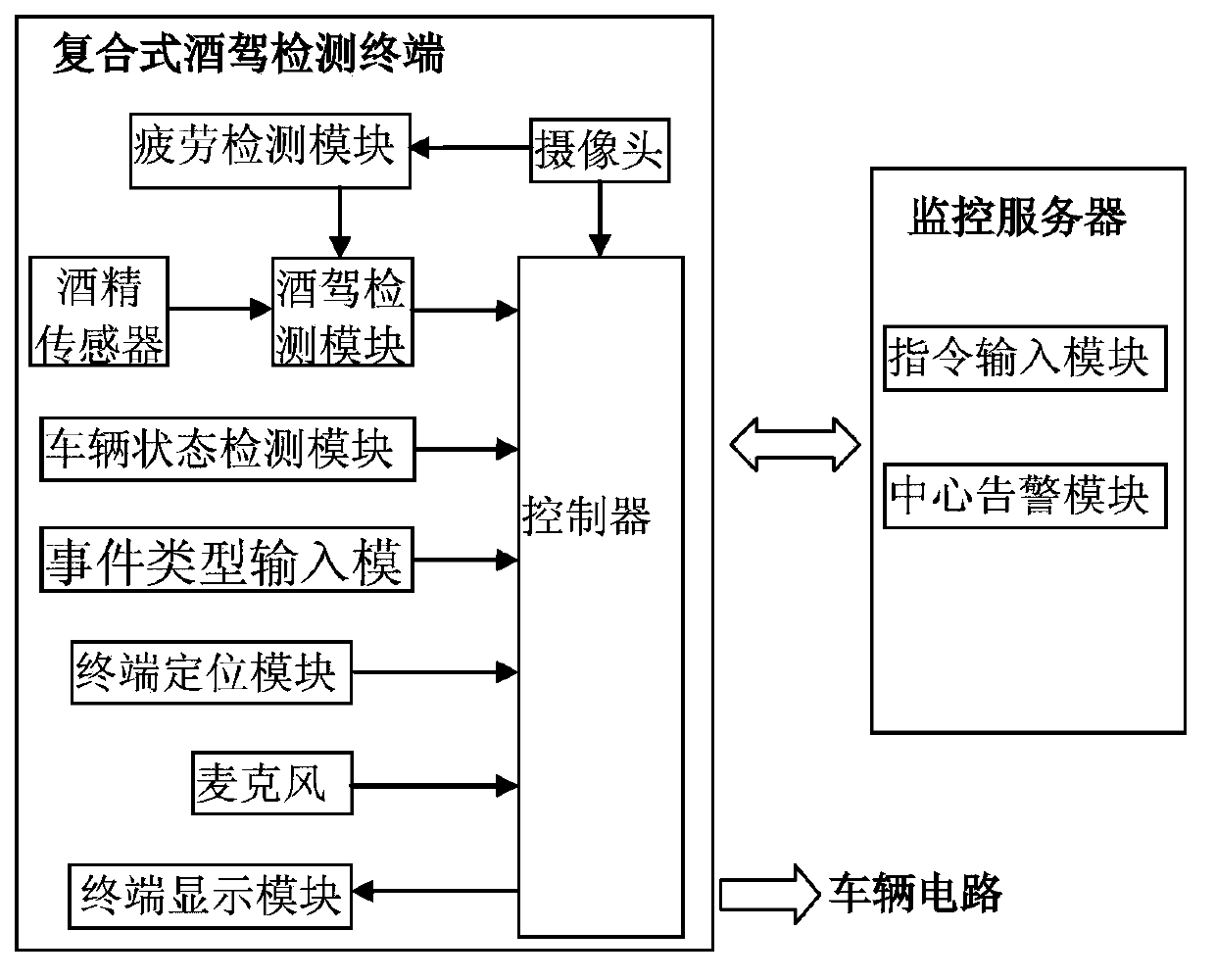
Drunk driving monitoring system, combined drunk driving detection terminal and scheduling server
ActiveCN103963645AAccurate monitoringAvoid monitoringTractorsPropulsion unit safety devicesMonitoring systemComputer terminal
The invention discloses a drunk driving monitoring system which comprises a combined drunk driving detection terminal and a monitoring server. The combined drunk driving detection terminal controls to disconnect a vehicle circuit, displays drunk driving warning information and sends the drunk driving warning information data to the monitoring server when the drunk driving extent reaches a set interval and a vehicle is in a startup state, and controls to connect the vehicle circuit when receiving an instruction of canceling drunk driving. The monitoring server, when receiving the drunk driving warning information data from the combined drunk driving detection terminal, displays the drunk driving warning information from the combined drunk driving detection terminal and can send an instruction of canceling drunk driving to the corresponding combined drunk driving detection terminal. The invention further discloses the combined drunk driving detection terminal and a scheduling server. According to the invention, drunk driving can be monitored accurately and can be found out and prohibited timely.
Owner:SHANGHAI FLEETY COMM
Method and system for conserving power in powerline network having multiple logical networks
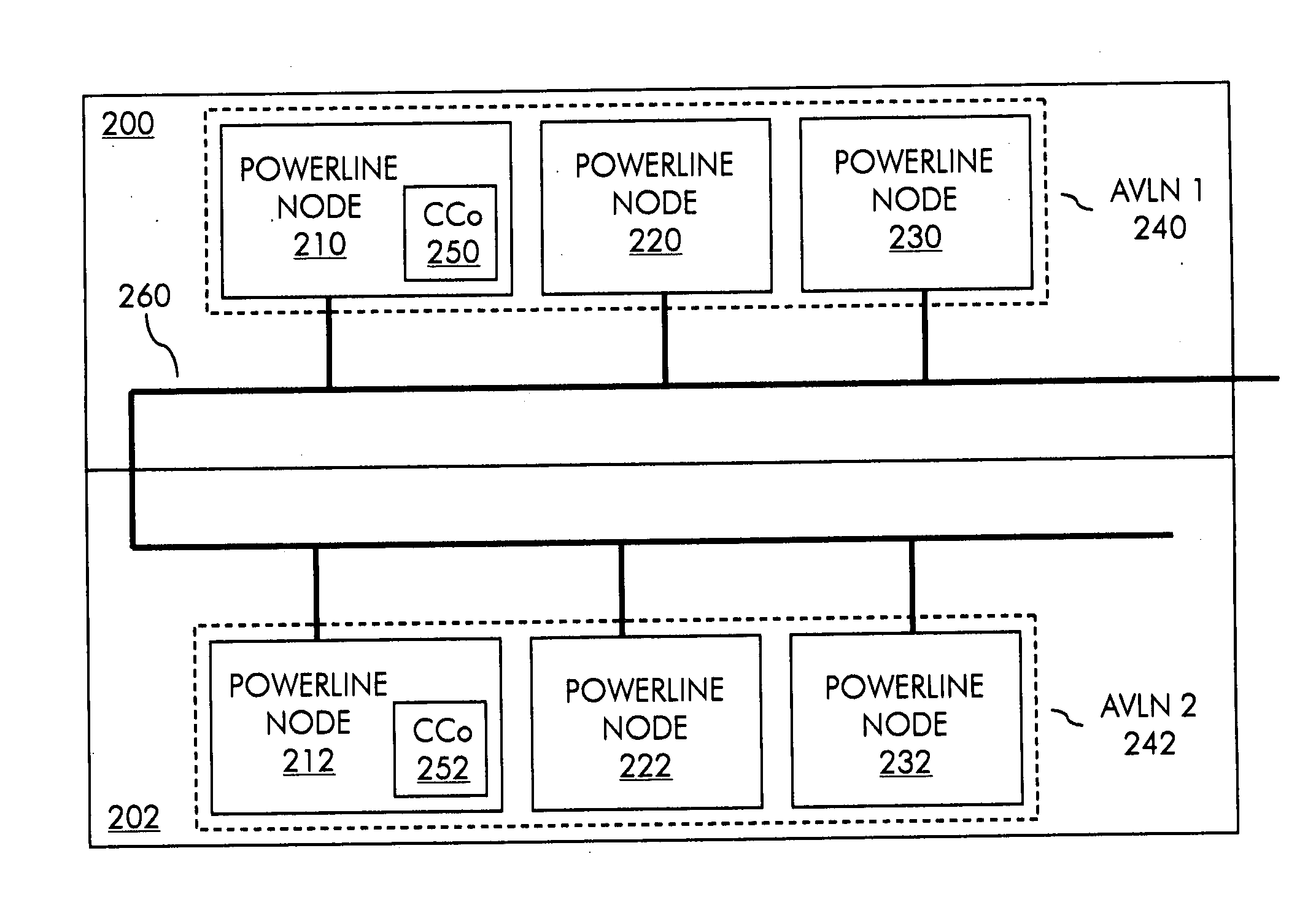
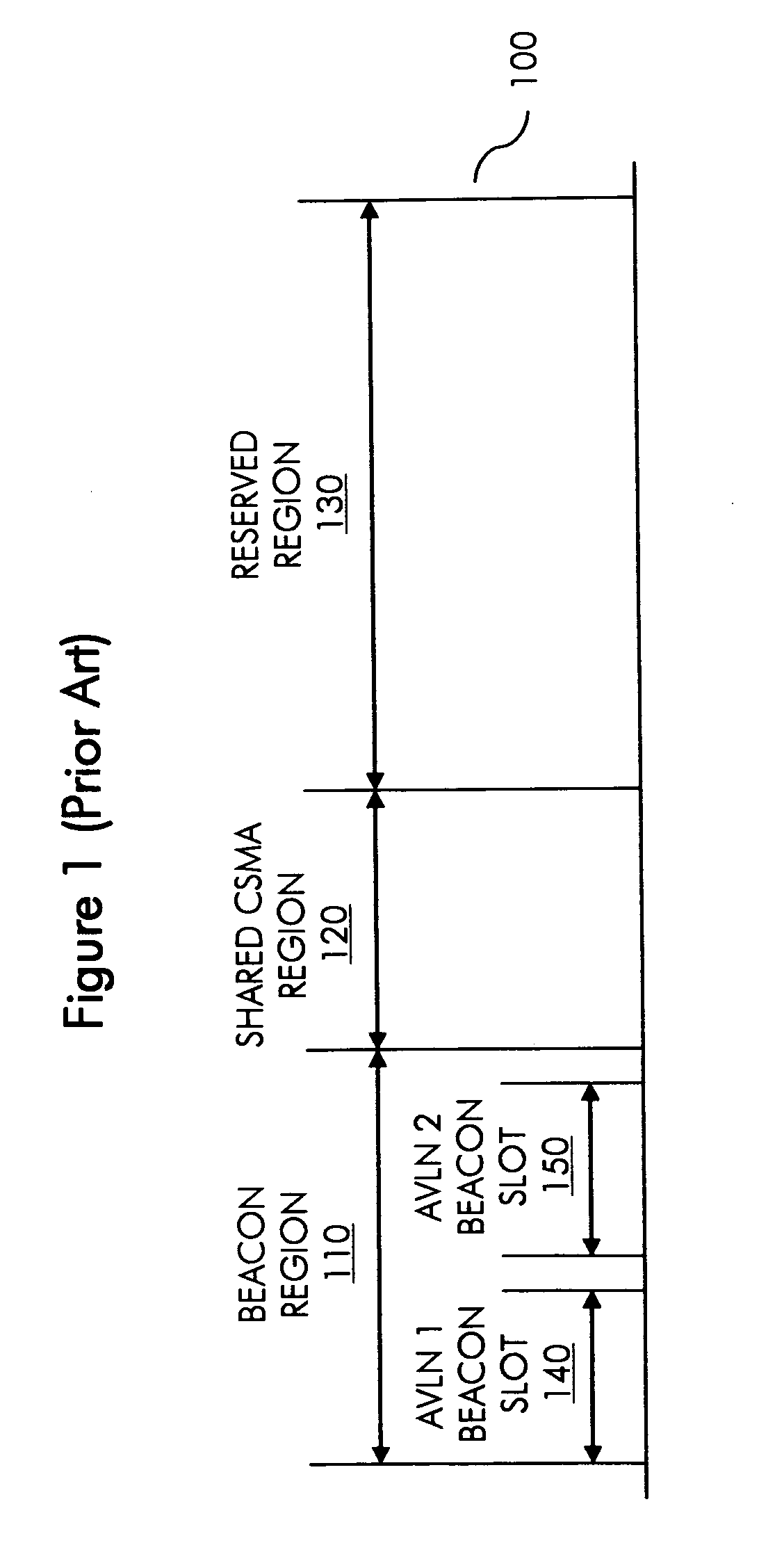
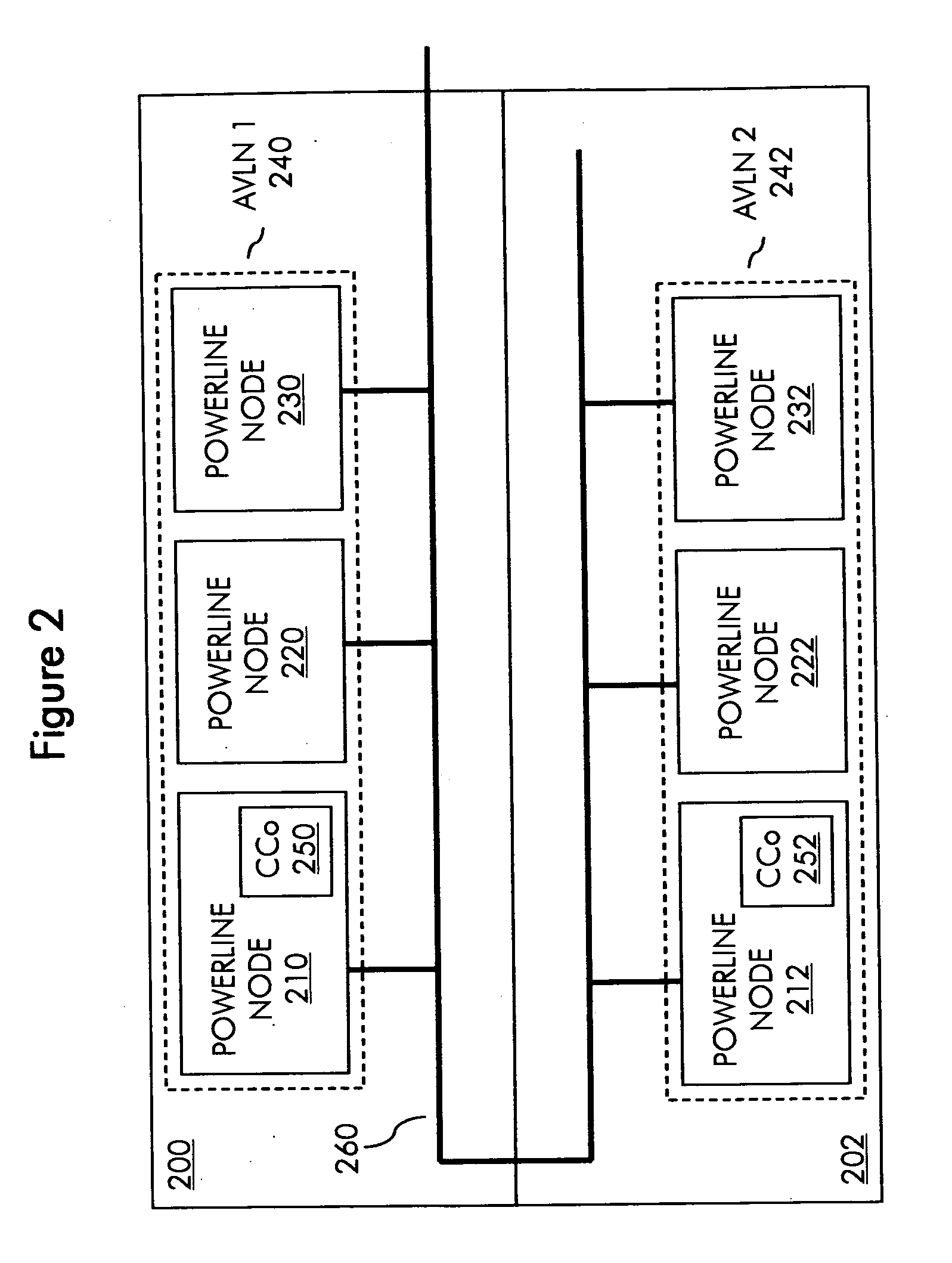
InactiveUS20100110911A1Avoid monitoringError preventionFrequency-division multiplex detailsCarrier signalHomePlug
A method and system for conserving power in a powerline network, such as a Homeplug AV (HPAV) network, that has multiple logical networks, such as multiple AV logical networks (AVLN). Power conservation is achieved through the expedient of a packet presence region (PPR) that informs nodes whether or not they need to monitor a shared carrier sense multiple access (CSMA) region in a particular beacon period.
Owner:SHARP LAB OF AMERICA INC
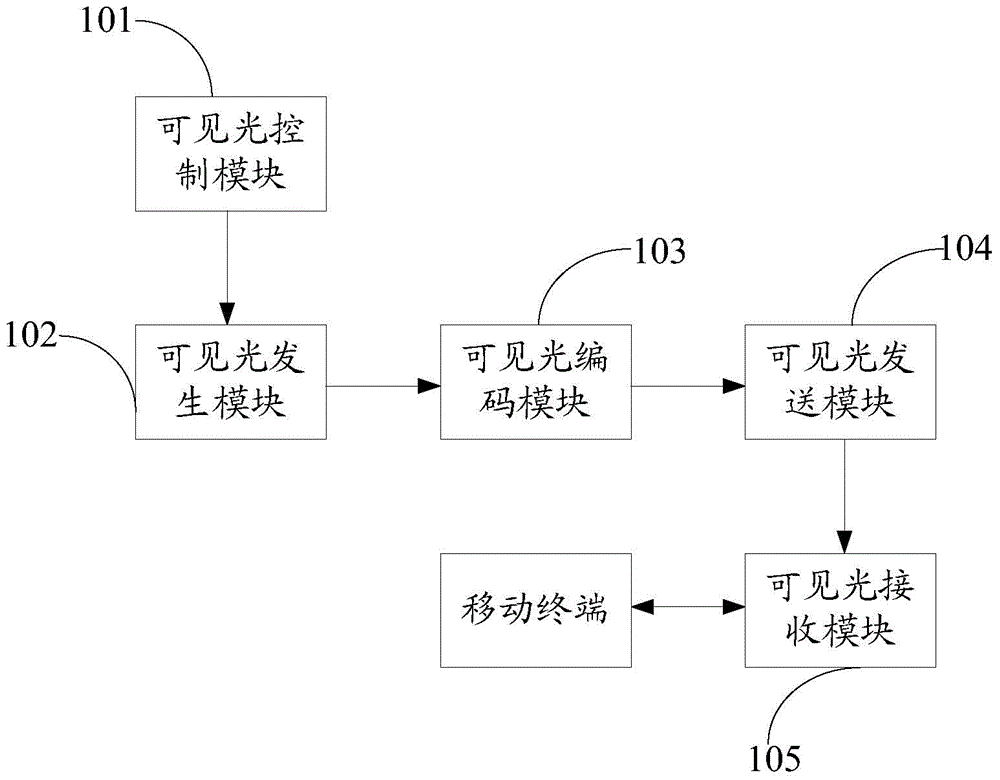
LED illumination-based visible light communication transmission method and system
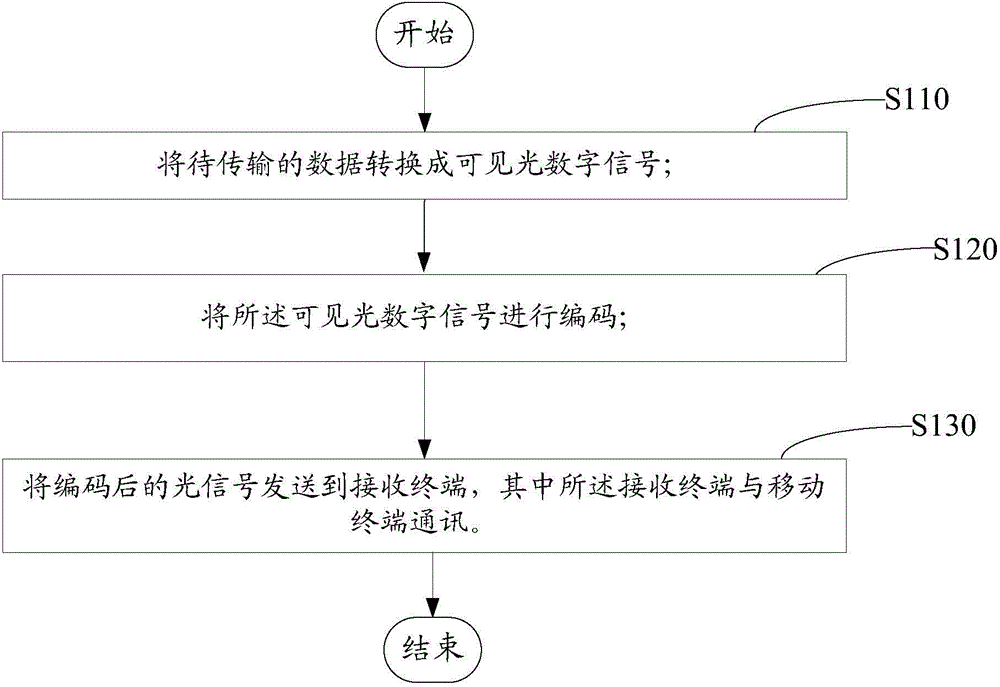
InactiveCN104868951AAvoid monitoringClose-range type systemsElectromagnetic receiversConfidentialityLight signal
The invention relates to an LED illumination-based visible light communication transmission method and system. According to the visible light communication transmission method and system, data to be transmitted are converted into visible light digital signals through a visible light generation module; a visible light control module is adopted to set a state in which the visible light generation module can emit visible light; a visible light encoding module is used for encoding the visible light digital signals; and a visible light sending module and a visible light receiving module are adopted to transmit encoded light signals; and therefore, the visible light receiving module which communicates with a mobile terminal can send the data to be transmitted to the mobile terminal. Since light signal transmission is adopted, when confidentiality is required, as long as visible light is shielded, data transmission can be prevented from being monitored.
Owner:SHENZHEN EASTFIELD LIGHTING
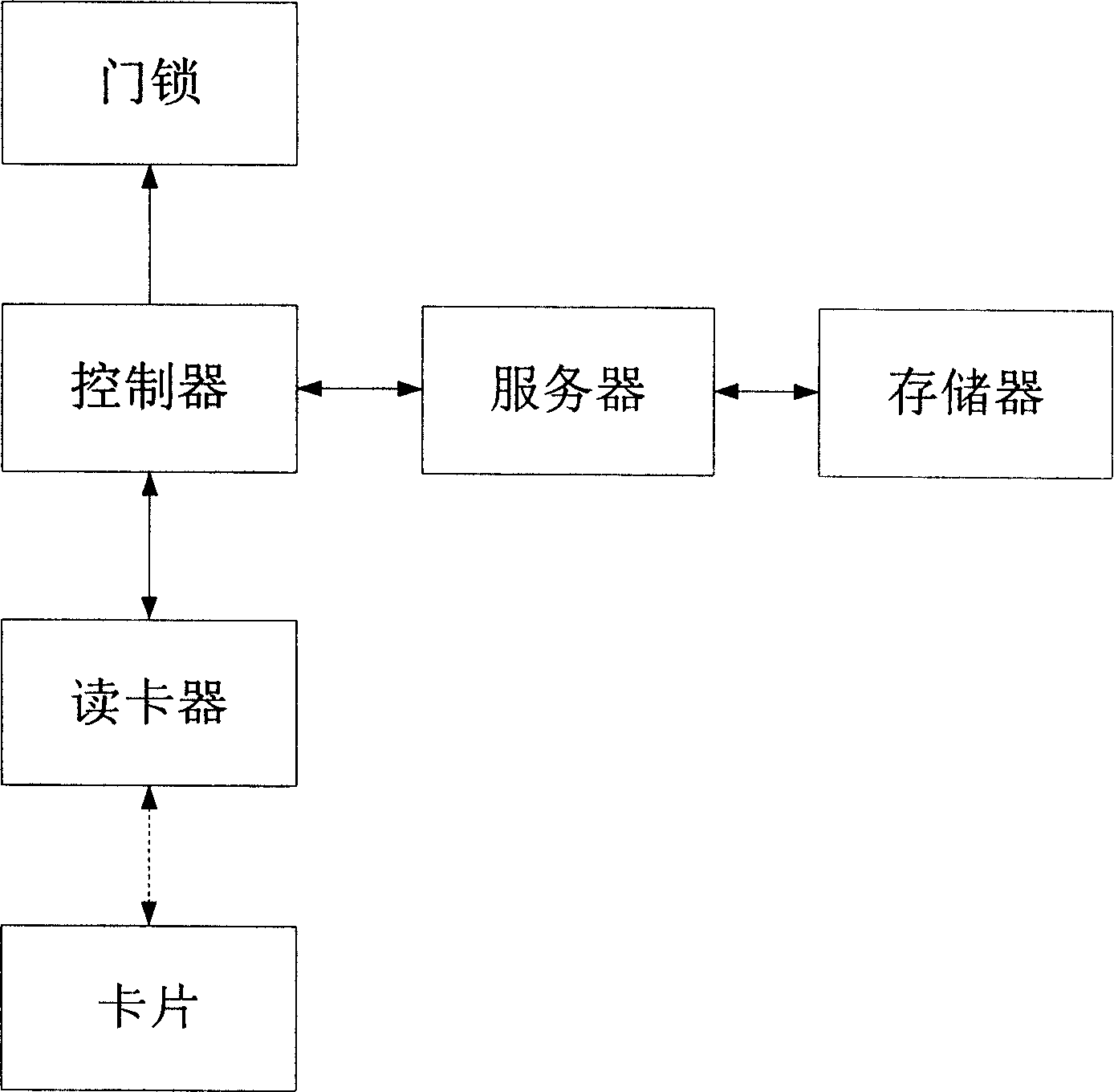
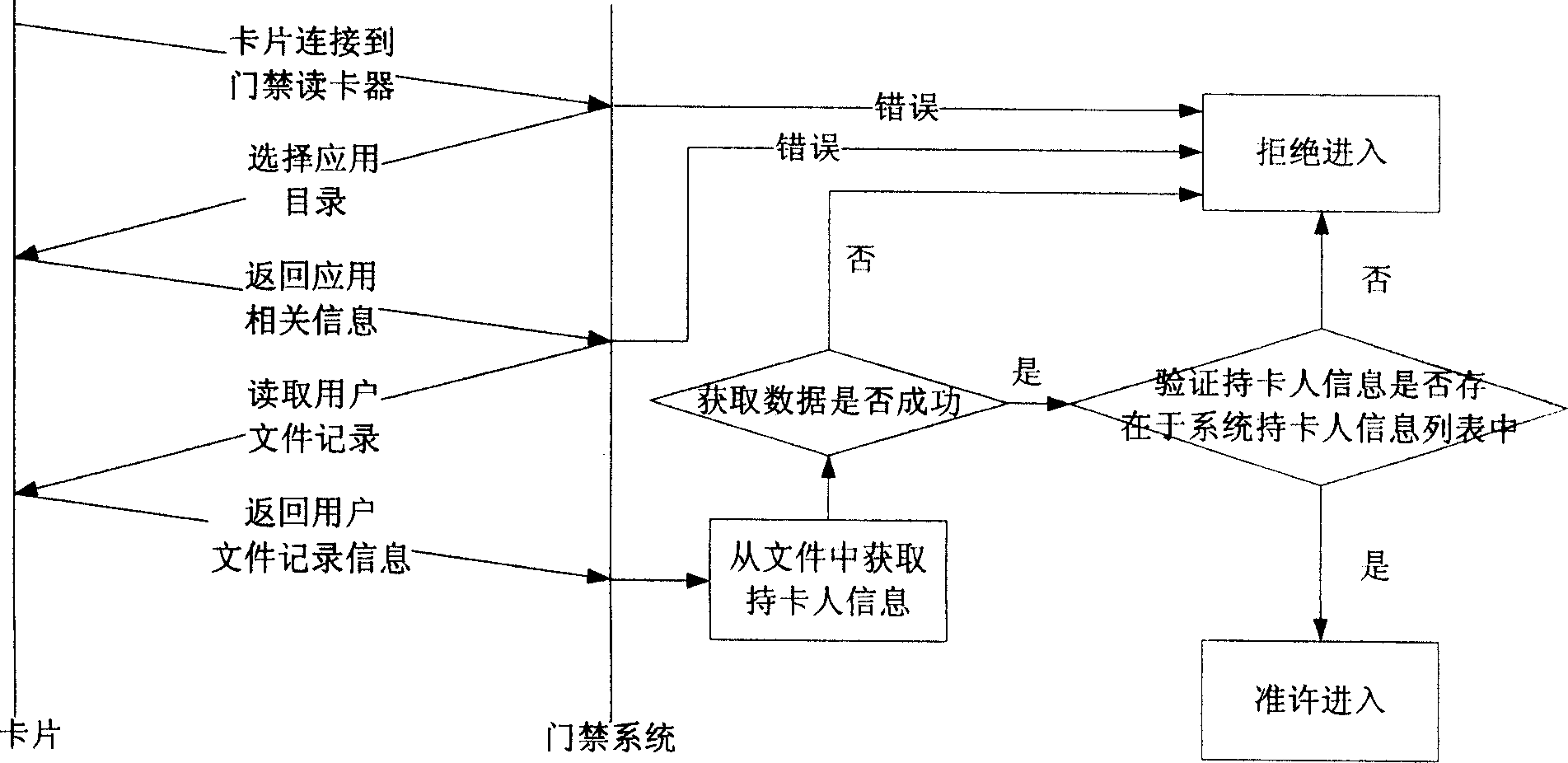
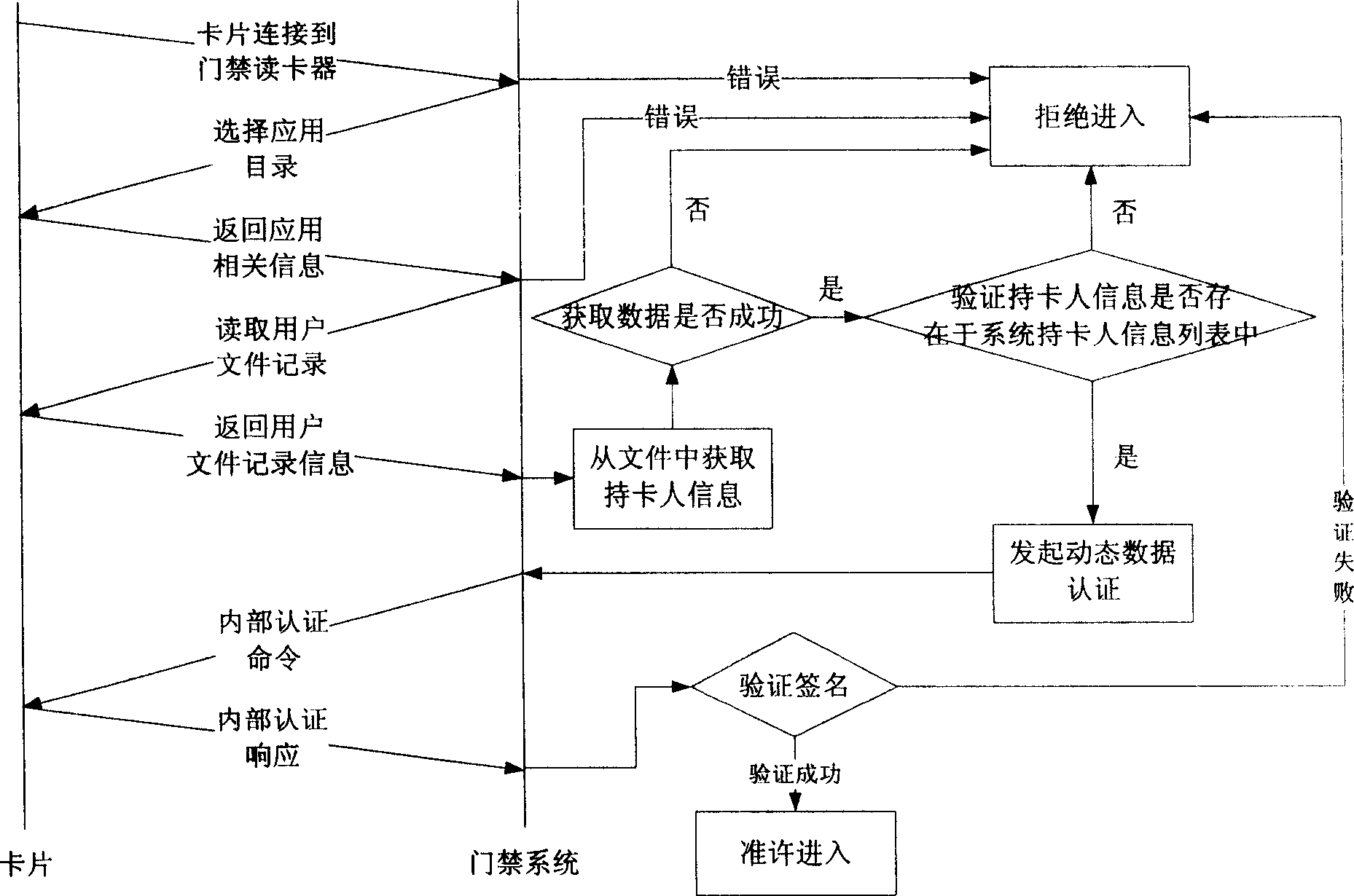
Application method of IC card in gate inhibition system based on financial criterion
ActiveCN1885351AReduce the link of issuing cardsAvoid monitoringIndividual entry/exit registersSystem safetyBusiness rule
Owner:FEITIAN TECHNOLOGIES
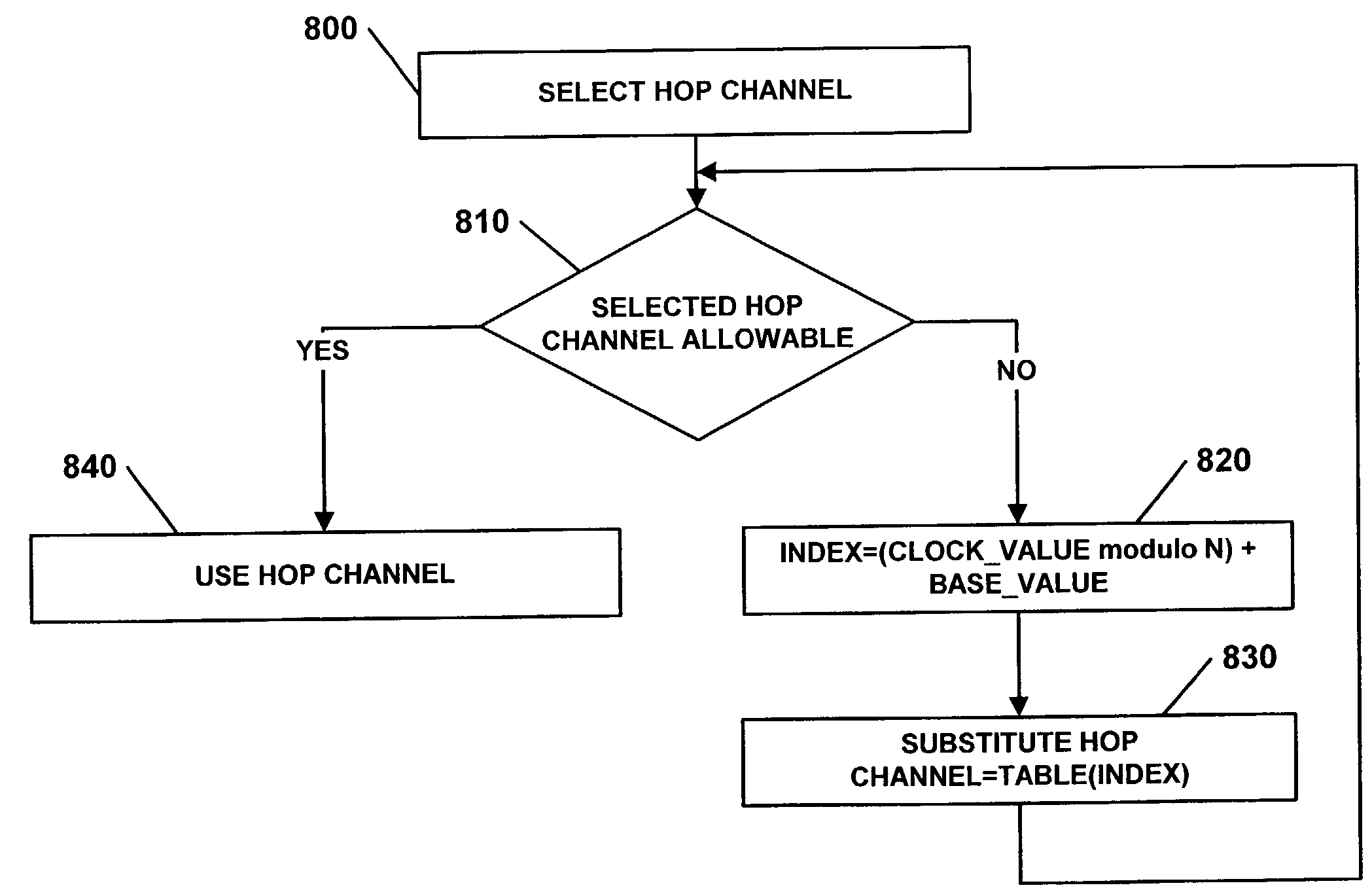
Methods and apparatus for adapting a hop sequence when establishing a communication connection
InactiveUS7245649B2Avoid monitoringQuick buildError preventionLine-faulsts/interference reductionPager
Methods and apparatus are provided for establishing a connection between a scanner device and a pager device over a sequence of hop channels. The scanner device is repetitively activated and a hop channel is selected from the sequence of hop channels as a function of a present phase. A determination is made as to whether the selected hop channel is a forbidden hop channel. A substitute hop channel is selected from the sequence of hop channels as the selected hop channel if the selected hop channel is a forbidden hop channel. The selected hop channel is monitored for receipt of a paging message during the present phase.
Owner:TELEFON AB LM ERICSSON (PUBL)
Method and device for sending and receiving communication information
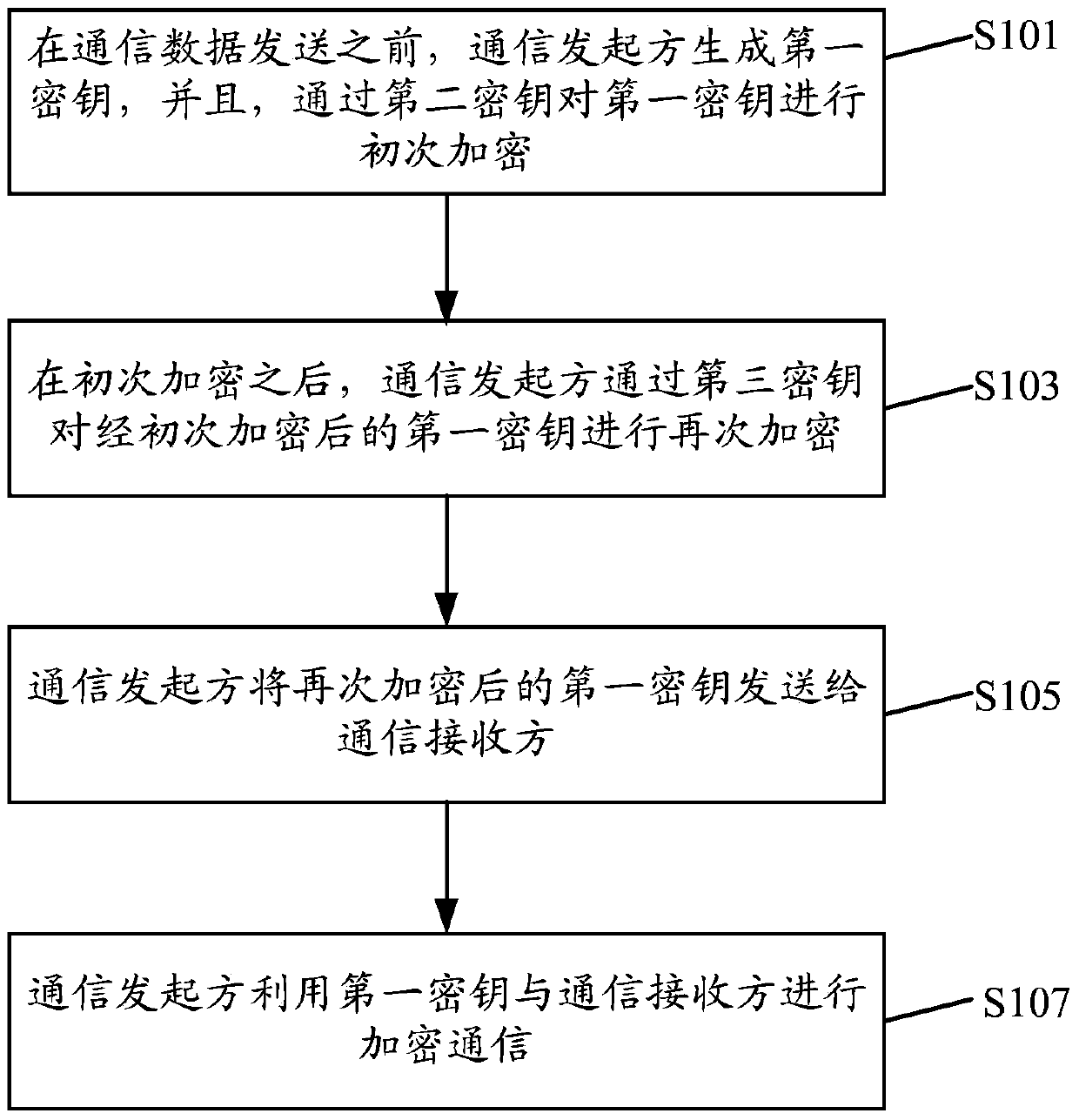
InactiveCN103561023APrevent monitoringAvoid disclosure of privacyTransmissionCommunications softwareEncryption
The invention discloses a method and device for sending and receiving communication information and a safety protection system. The method for sending the communication information includes the steps that a communication sending party generates a first secret key before communication data are sent, initial encryption is conducted on the first secret key through a second secret key, the communication sending party conducts secondary encryption on the initially-encrypted first secret key through a third secret key after initial encryption is conducted, the communication sending party sends the secondarily-encrypted first secret key to a communication receiving party, and the communication sending party is in encryption communication with the communication receiving party through the first secret key. Encryption is conducted on the communication data before the communication data are sent, secondary encryption is conducted on the encrypted communication data when the communication data are sent, and therefore dual-level protection is achieved for the communication data, communication software is prevented from monitoring the communication data of a user, and privacy is prevented from being revealed.
Owner:DAWNING CLOUD COMPUTING TECH CO LTD
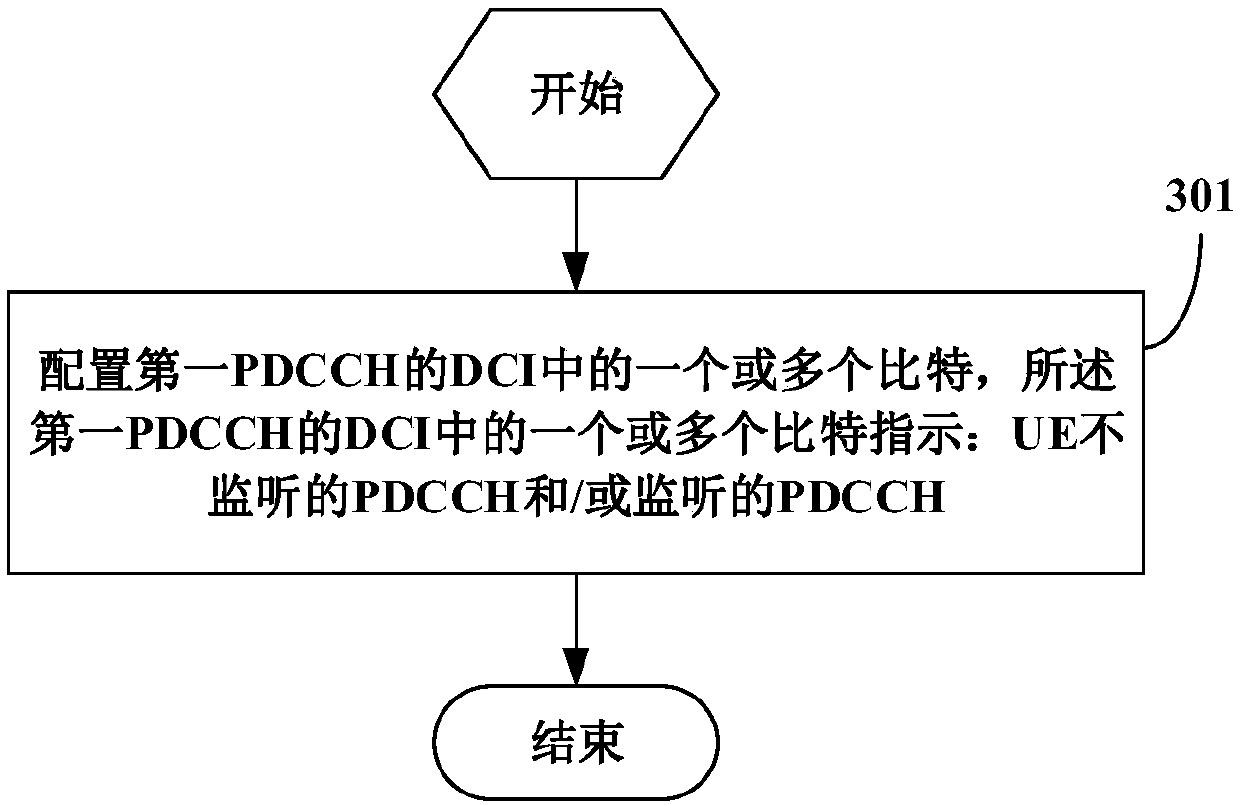
Method for monitoring physical downlink control channel, user equipment and network side equipment
ActiveCN110381569AAvoid monitoringReduce consumptionPower managementReceiver specific arrangementsControl channelComputer science
The embodiment of the invention provides a method for monitoring a physical downlink control channel, user equipment and network side equipment. The method comprises the following steps: acquiring oneor more bits in DCI of a first PDCCH monitored by UE, wherein the one or more bits in the DCI of the first PDCCH indicate an unmonitored PDCCH and / or a monitored PDCCH; and determining an unmonitored PDCCH and / or a monitored PDCCH according to one or more bits of the DCI of the first PDCCH. In this way, the UE is prevented from monitoring unnecessary PDCCH, and the power consumption of the UE can be reduced.
Owner:VIVO MOBILE COMM CO LTD
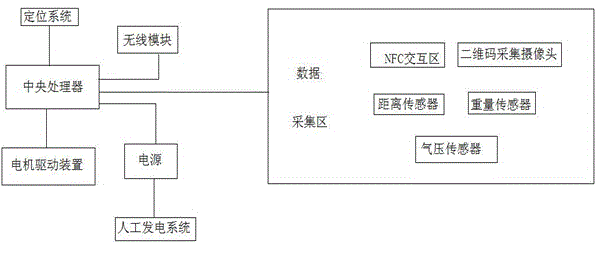
Electric vehicle safety control system and method
ActiveCN104670158AProlong damage timeGuarantee property securityAnti-theft devicesControl systemSafety control
The invention discloses an electric vehicle safety control method. The electric vehicle safety control method comprises a preparation process: when a mobile phone is in a certain range far away from an electric vehicle, enabling the electric vehicle to find the mobile phone which is getting close through technological manners such a Bluetooth or wireless local area network wifi through presetting and to transmit a preparation signal to the mobile phone such that both the electric vehicle and the mobile phone enter a preparation state; a starting process: clicking the NFC (Near Field Communication) interaction region of the electric vehicle by using mobile phone NFC to start a two-dimensional code acquisition camera, generating a disposable two-dimensional code with unfixed data through a designated algorithm by an application installed in the mobile phone in order to execute a confirmation operation during setting of functional parameters of the electric vehicle; enabling the authorized mobile phone to get close to the camera of the electric vehicle and displaying the correct two-dimensional code through a screen, wherein the electric vehicle is not started until the camera of the electric vehicle captures the two-dimensional code and verifies that the two-dimensional code is valid.
Owner:SHANDONG BEGREEN NEW ENERGY TECKNOLOGY CO LTD
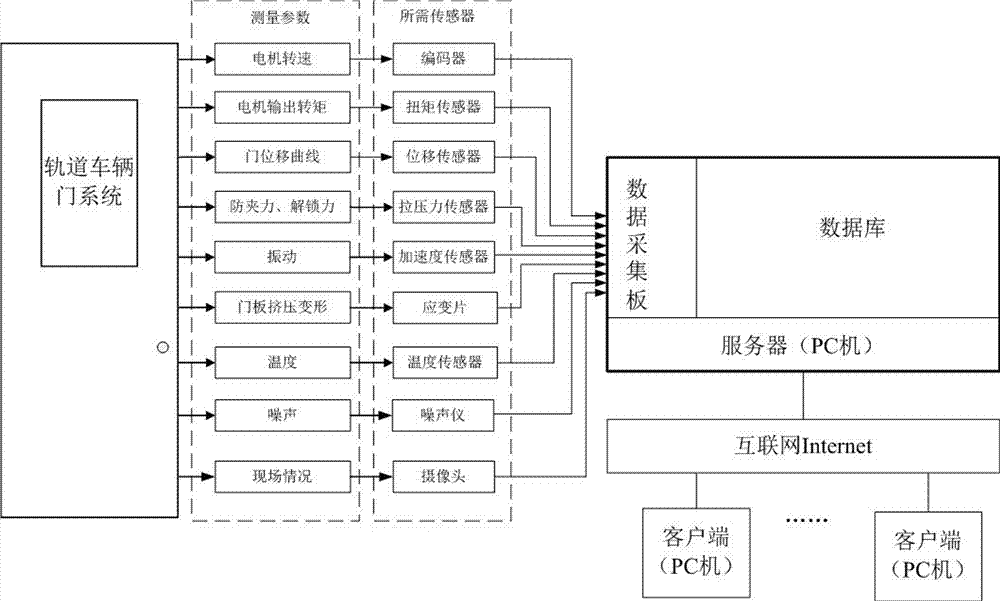
Remote monitoring system for rail vehicle door system and monitoring method thereof
InactiveCN107328589AKeep abreast of health statusAvoid failureProgramme controlComputer controlHuman–machine interfaceData acquisition
The invention provides a remote monitoring system for a rail vehicle door system and a monitoring method thereof. The remote monitoring system comprises a server and a data collection card, and further comprises the rail vehicle door system, a sensor, a client and human computer interface program, wherein the sensor is arranged on the rail vehicle door system, the output terminal of the sensor is connected to the input end of the data collection card, the data collection card is installed on the server, the human computer interface program and the database software are installed on the server, the human computer interface program is connected with the output terminal of the data collection card, the data acquired by the data collection card is displayed on the human computer interface on a real-time basis, the human computer interface program is connected with a database, the sensor data acquired by the data collection card is stored in the database, and the server and the client are PCs and are connected through the Internet. The maintenance cost and time for a door system are reduced, and maintenance efficiency is improved.
Owner:NANJING INST OF TECH +1
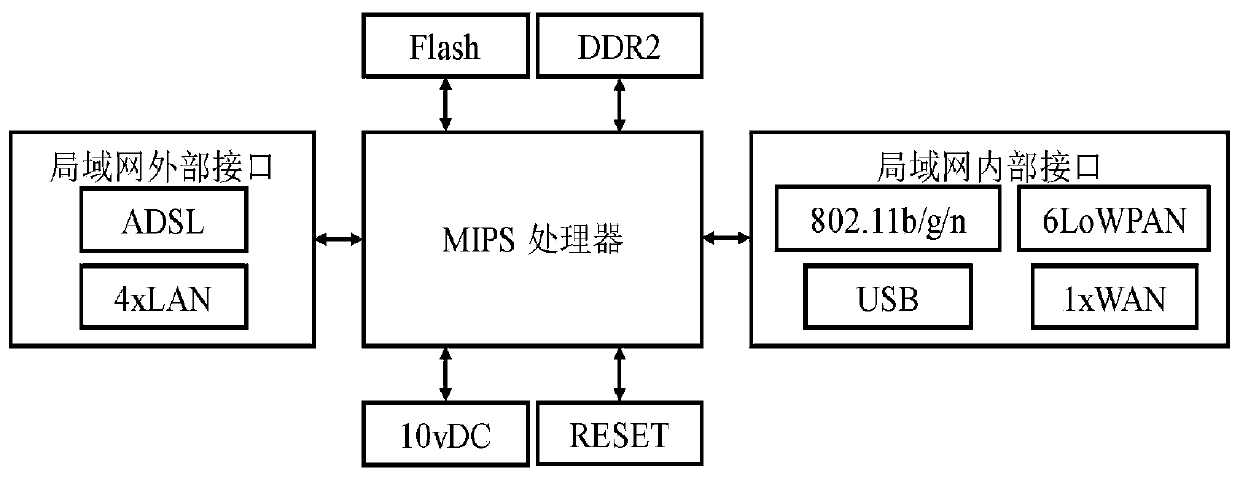
6LoWPAN-based intelligent fire-fighting service system for colleges and universities and design method
InactiveCN110996285APrevent illegal tamperingAvoid monitoringParticular environment based servicesTransmissionData acquisitionFire prevention
The invention discloses a 6LoWPAN-based intelligent fire-fighting service system for colleges and universities and a design method of the 6LoWPAN-based intelligent fire-fighting service system. The service system comprises a data acquisition layer, a data transmission layer, a data control layer and a system application layer, good interoperability of the 6LoWPAN can solve information isolation, the 6LoWPAN supports the intercommunication with other IEEE (Institute of Electrical and Electronic Engineers) 802.15. 4 equipment and supports the interconnection with other IP networks; through designing a data control layer based on fire-fighting big data, intelligentized analysis of data, intelligent control on fire-fighting equipment, a visual service platform is established; through analyzingand mining fire-fighting big data, the fire situation is predicted and a solution is formulated, the fire prevention and control efficiency is improved, the intelligence of a service platform is realized, the purposes of equipment management centralization, fire-fighting construction underlying data management intellectualization and management system platformization are achieved, and the systemhas the characteristics of high feasibility, convenience in networking and easiness in maintenance and upgrading.
Owner:CENT SOUTH UNIV +1
Wireless video monitoring system based on wide water domain
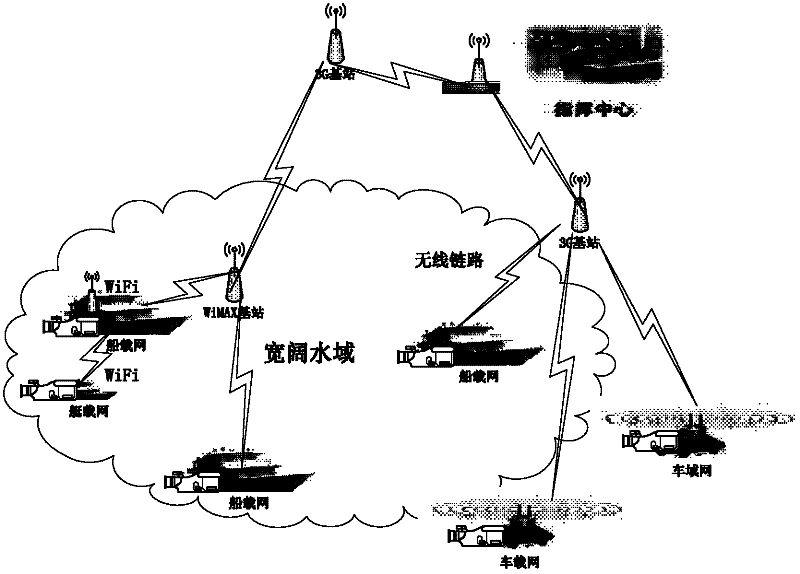
InactiveCN102368818AIncrease coverageFlexible detectionTelevision system detailsColor television detailsVideo transmissionThird generation
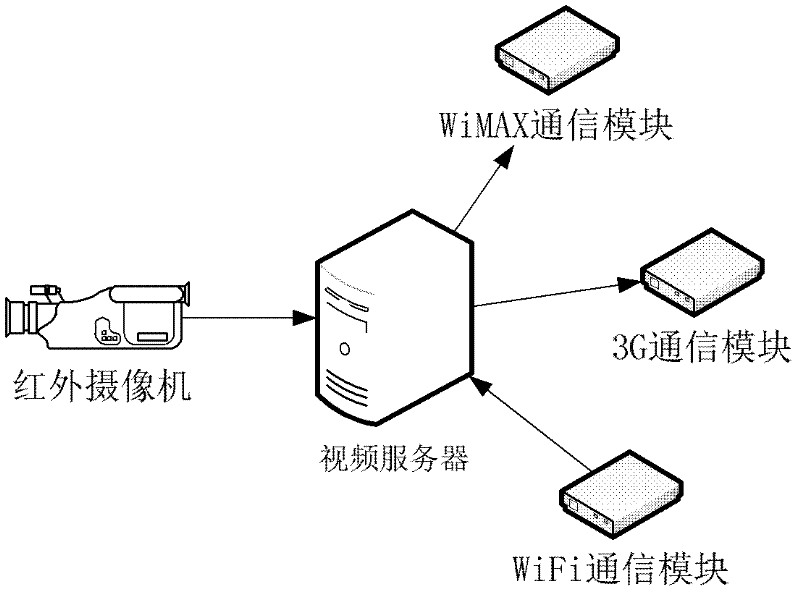
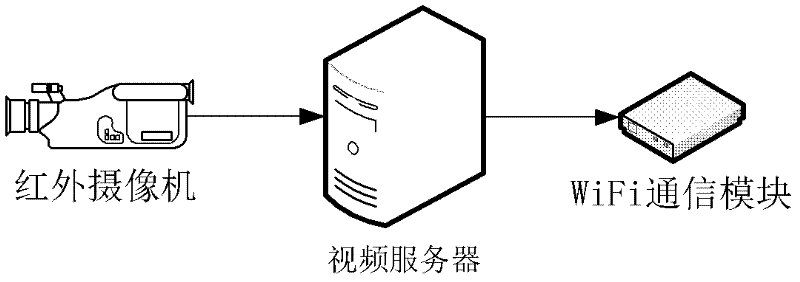
The invention discloses a wireless video monitoring system based on a wide water domain. A ship, vehicle and boat hybrid monitoring manner is adopted to establish a monitoring system, a wireless-based network-carrying system is constructed for a ship-vehicle-boat monitoring system, wireless network coverage is carried out by a 3G (The 3rd Generation Telecommunication)+WiMAX (Worldwide Interoperability for Microwave Access)+WiFi (Wireless Fidelity) hybrid architecture mode, servers are erected on a boat, a vehicle and a boat for transmitting and processing videos, and video data acquired by the ship, the vehicle and the boat are transmitted to a monitoring center through the network-carrying system. The monitoring system based on the wide water domain, provided by the invention, has the advantages of good coverage type, flexibility in detection, no influence from weather environment, and the like, can better avoid the defect brought by traditional satellites, can be used for monitoring the wide water domain in real time, has a aerial panorama with the formation time reduced from traditional 3-7 days to about 1-2 days, and can work under weather conditions such as rain, snow, fog and the like that the traditional satellites can not form an image and give a corresponding result image.
Owner:NANJING UNIV
Method, device and system for performing security prediction based on feature information
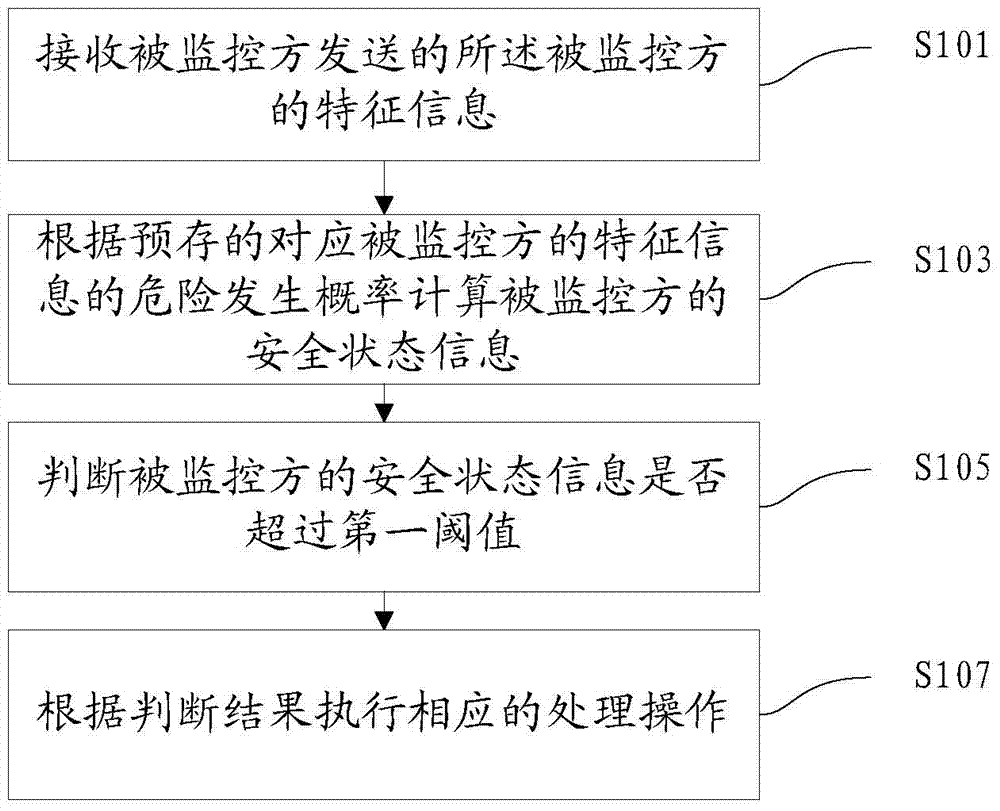
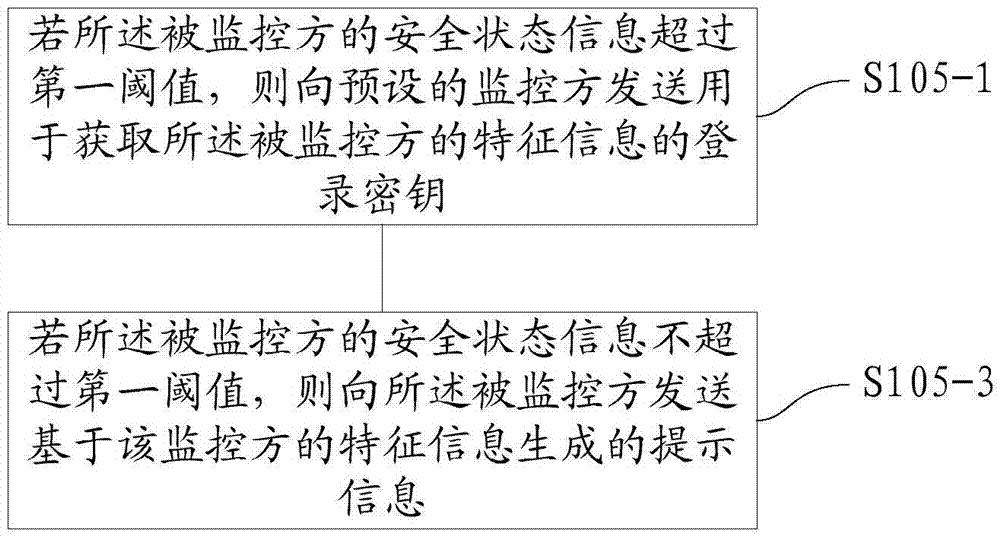
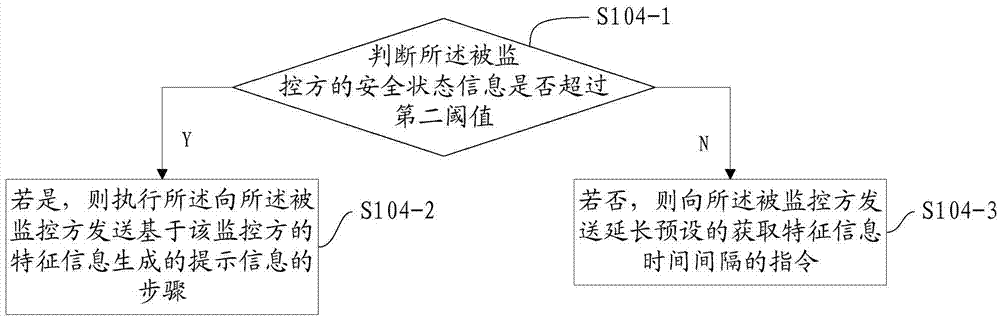
ActiveCN106921700AImprove personal safetyProtection securitySensorsMessaging/mailboxes/announcementsSecure stateOccurrence probability
The application discloses a method and device for performing security prediction based on feature information, an electronic device, a method and device for acquiring the feature information, an electronic device, and a system for performing security prediction based on the feature information. The method for performing security prediction based on the feature information comprises the following steps: receiving the feature information of a monitored party sent by the monitored party; calculating the security state information of the monitored party according to the prestored risk occurrence probability corresponding to the feature information of the monitored party; judging whether the security state information of the monitored party exceeds a first threshold; and executing corresponding processing operations according to the judgment result. By adopting the method disclosed by the application, the problem that potential safety hazards are caused as the preset monitoring hidden conditions cannot cover the potential risk factors in the surrounding environment can be solved, the hidden dangers that cannot be reflected by the spatial information can be monitored; and through the identification and early warning of the feature information, an alert is made before the occurrence of the hidden dangers to avoid the occurrence of the hidden dangers, and the problem of traffic waste can be solved.
Owner:ALIBABA GRP HLDG LTD
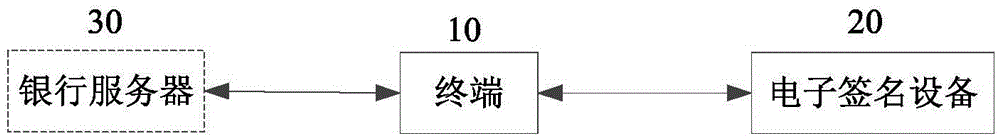
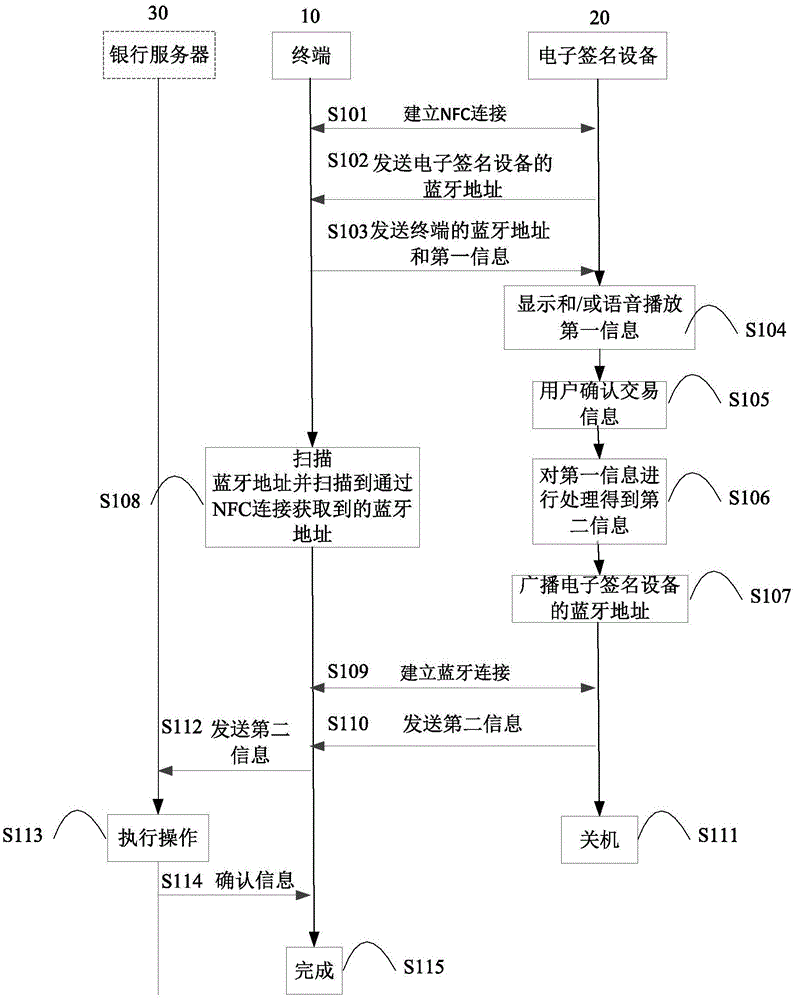
Data transmission method, terminal, electronic signature device and system
ActiveCN105162497APrevent data theft and snoopingEnsure data securityUser identity/authority verificationConnection managementData transmissionData security
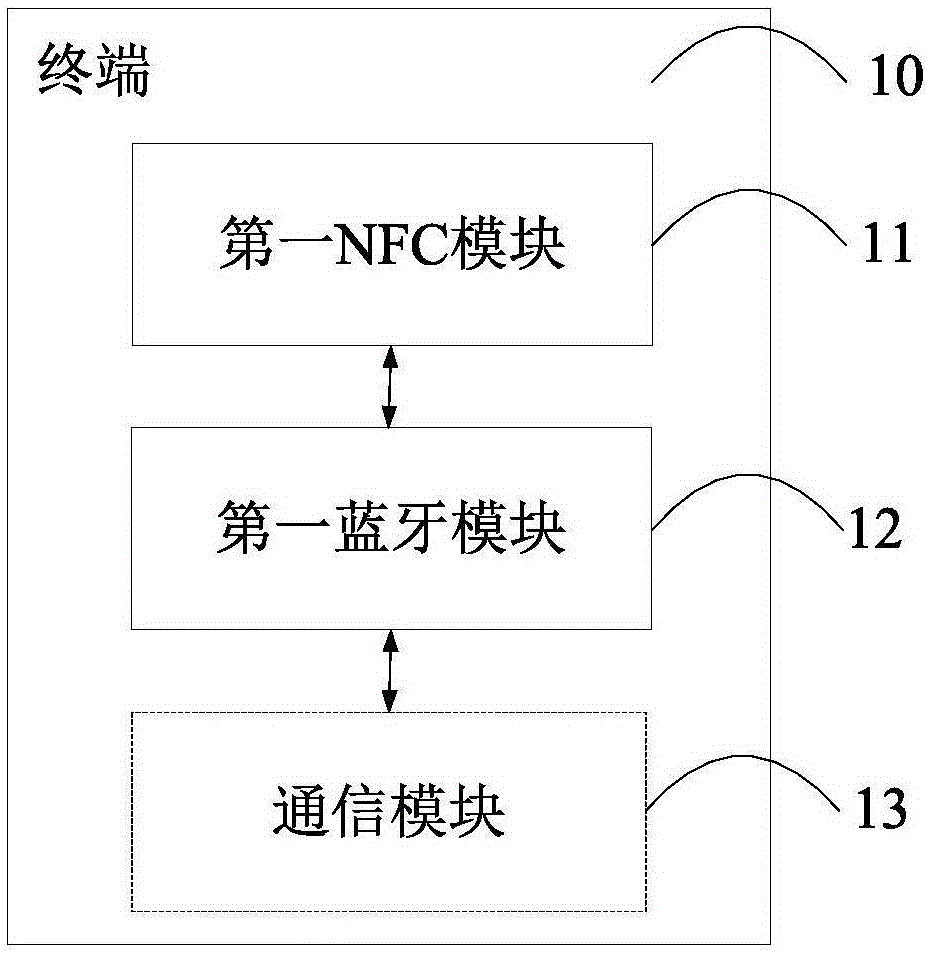
The invention provides a data transmission method. The data transmission method includes that the terminal is in NFC connection with an electronic signature device; the electronic signature device sends a Bluetooth address of the electronic signature device to the terminal through NFC connection; the terminal sends the Bluetooth address of the terminal and a first message to the electronic signature device through NFC connection; the electronic signature device processes the first message and obtains a second message and broadcasts the Bluetooth address of the electronic signature device; the terminal performs Bluetooth address scanning and acquires the Bluetooth address obtained through the NFC connection; the terminal establishes Bluetooth connection with the electronic signature device corresponding to the acquired Bluetooth address; the electronic signature device sends the second message to the terminal through Bluetooth connection. According to the invention, by the wireless connection means based on the combination of NFC technology and Bluetooth technology, abrasion of a wired interface is avoided, so that complicated matching processes of Bluetooth connection are avoided and data theft and interception are prevented. Therefore, data security is ensured, data transmission rate is improved and user experience is improved.
Owner:TENDYRON CORP
Method, device and equipment for creating vTPM (Virtual Trusted Platform Module) and computer readable storage medium
InactiveCN108170516AImprove securitySecurity impactSoftware simulation/interpretation/emulationVirtual machineTrusted Platform Module
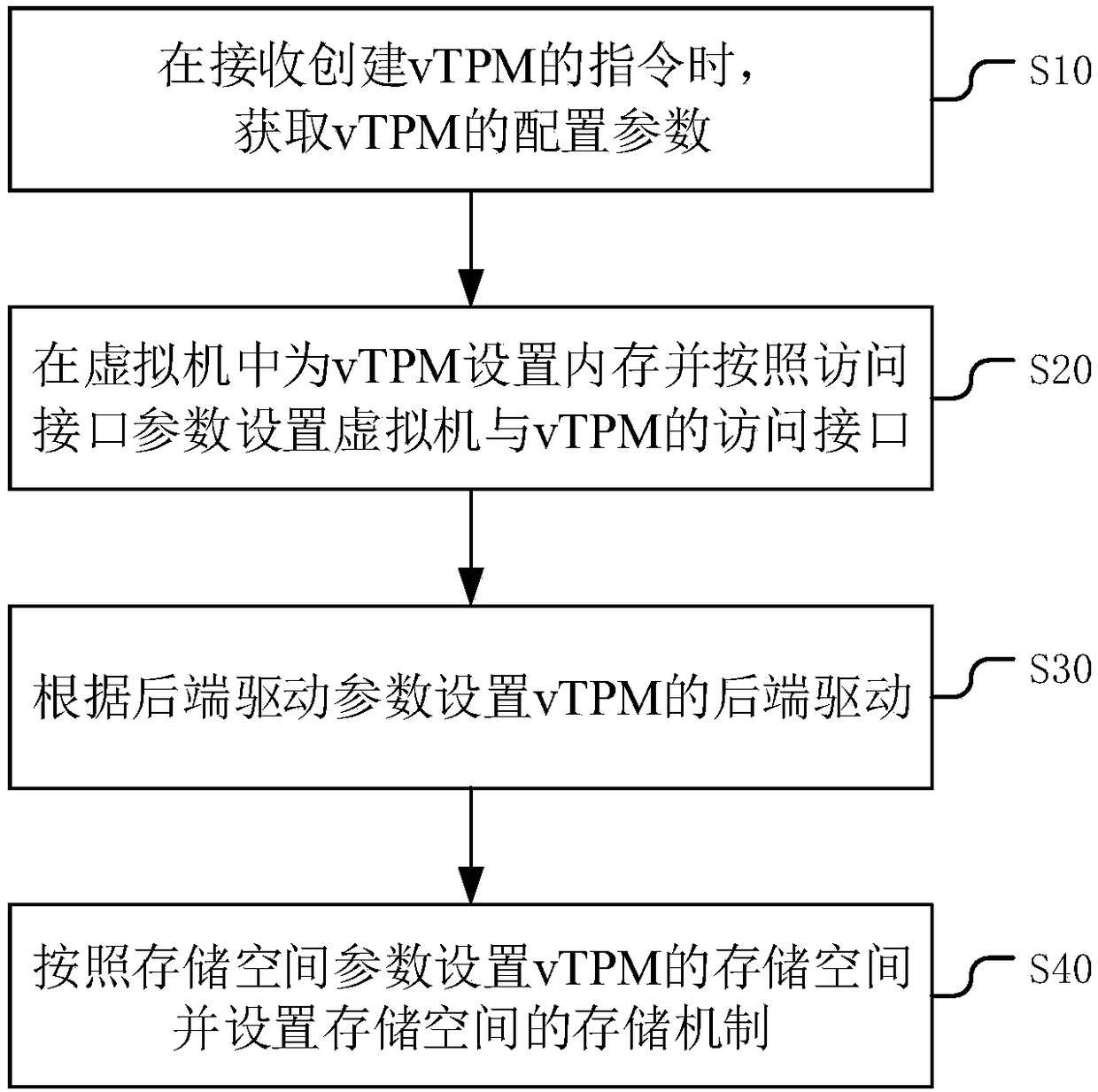
The application discloses a method for creating a vTPM (Virtual Trusted Platform Module). The method comprises the steps of: when receiving an instruction of creating the vTPM, acquiring configurationparameters of the vTPM, wherein the configuration parameters comprise an access interface parameter, a rear end driving parameter and a storage space parameter; then arranging a memory in a virtual machine for the vTPM and according to the access interface parameter, arranging an access interface of the virtual machine and the vTPM; according to the rear end driving parameter, arranging a rear end driver of the vTPM; and then according to the storage space parameter, setting a storage space of the vTPM and setting a storage mechanism of the storage space. By creating the vTPM in the virtual machine according to the configuration parameters, setting functions of the vTPM and providing a trusted root for the virtual machine, monitoring and operation on creation and application of the vTPM of the virtual machine by a host machine are avoided, and safety of the virtual machine is improved. The application further discloses a device and equipment for creating the vTPM and a computer readable storage medium which all have the above-mentioned beneficial effects.
Owner:INSPUR BEIJING ELECTRONICS INFORMATION IND
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com