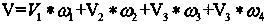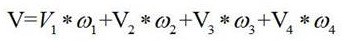Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
48results about How to "Increase attack cost" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
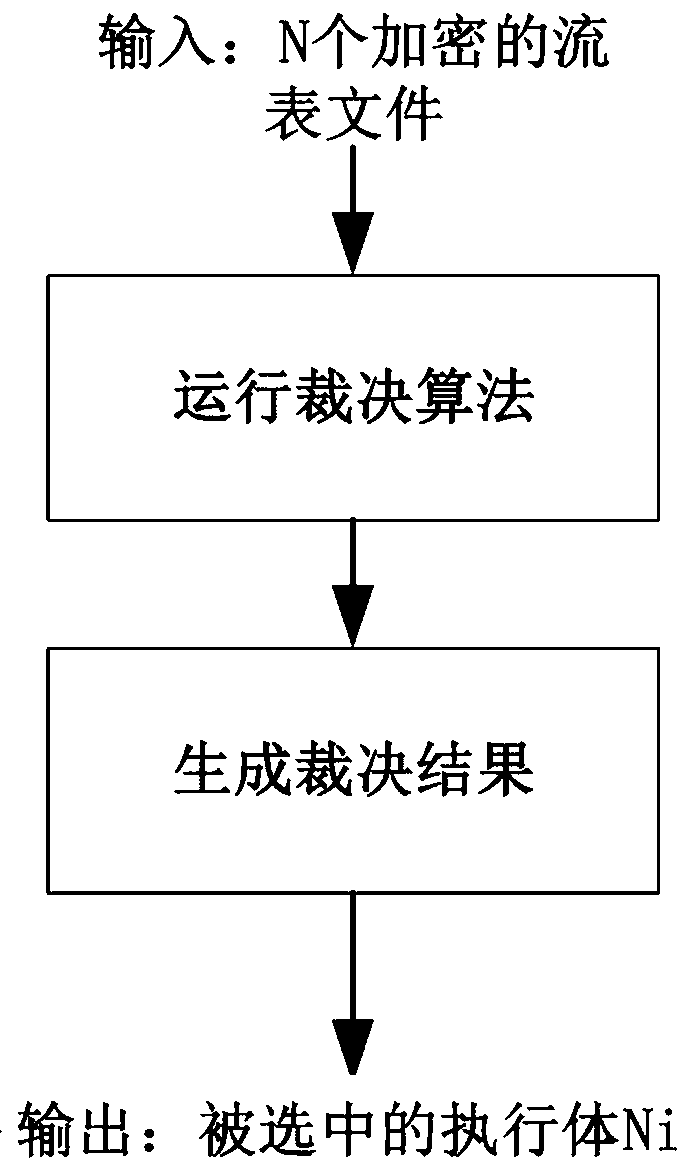
Mimetic defense-based network function deploying method in software defined network
ActiveCN109587168AIncrease attack difficulty and attack costImprove securityData switching networksVirtualizationSoftware-defined networking
The invention provides a mimetic defense-based network function deploying method in a software defined network. The method comprises the following steps: 1, virtual network functions are deployed on adata plane through a virtualization technology; 2, based on a mimetic architecture, a heterogeneous executor pool, a dispatcher and an adjudicator part are constructed on a control plane; 3, the dispatcher performs dynamic dispatching on heterogeneous executors in the heterogeneous executor pool based on business requirements of an application plane, and a business deployment strategy flow tablefile is generated; 4, the adjudicator adjudicates the business deployment strategy flow table file and outputs the number of the selected heterogeneous executor to the heterogeneous executor pool; and5, the heterogeneous executor pool controls the selected heterogeneous executor to issue the business deployment strategy flow table file to the data plane according to the number of the selected heterogeneous executor, and the business deployment strategy flow table file is guided to complete deployment of the network functions through the virtual network functions.
Owner:河南信大网御科技有限公司
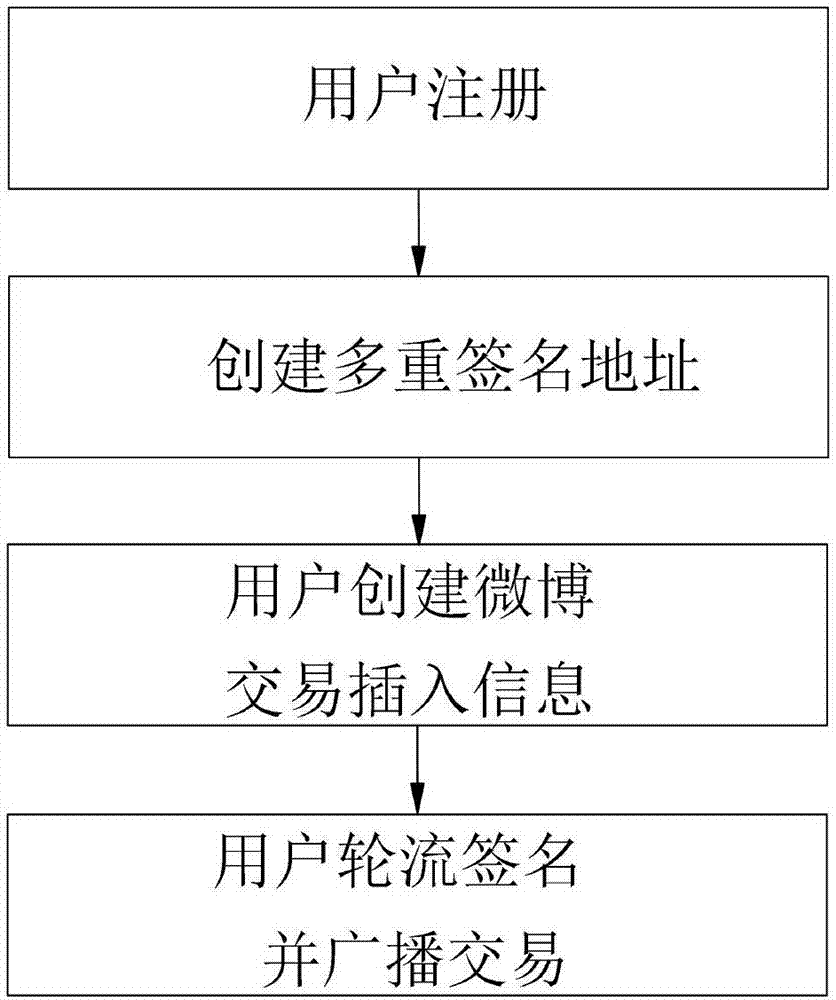
Micro-blog multi-signature method based on chain block
InactiveCN107370606ANo advertising will appearIncrease attack costUser identity/authority verificationMicrobloggingMultisignature
The invention relates to a micro-blog multi-signature method based on a chain block. The method comprises the following steps: 1, performing user registration to obtain a pair of public key and private key and an address for transaction and generated by the private key; 2, creating multi-signature addresses by m users by using the addresses obtained in step S1; 3, creating micro-blog sending transaction, and inserting to-be-sent information in the transaction by using an OP-RETURN operator, wherein the OP-RETURN operator is operated by the multi-signature addresses created in step S2, the multi-signature addresses support the authority of n of m; and 4, performing digital signature on the micro-blog transaction by the users onsite in turns, and broadcasting the micro-blog transaction after at least n signatures are obtained, and permanently recording the micro-blog transaction in the block chain after the success of the transaction. The micro-blog multi-signature method has the advantages of not worrying about tampering and deletion of the micro-blog, generating no advertising push, and having high security and high information credibility, etc.
Owner:SUN YAT SEN UNIV
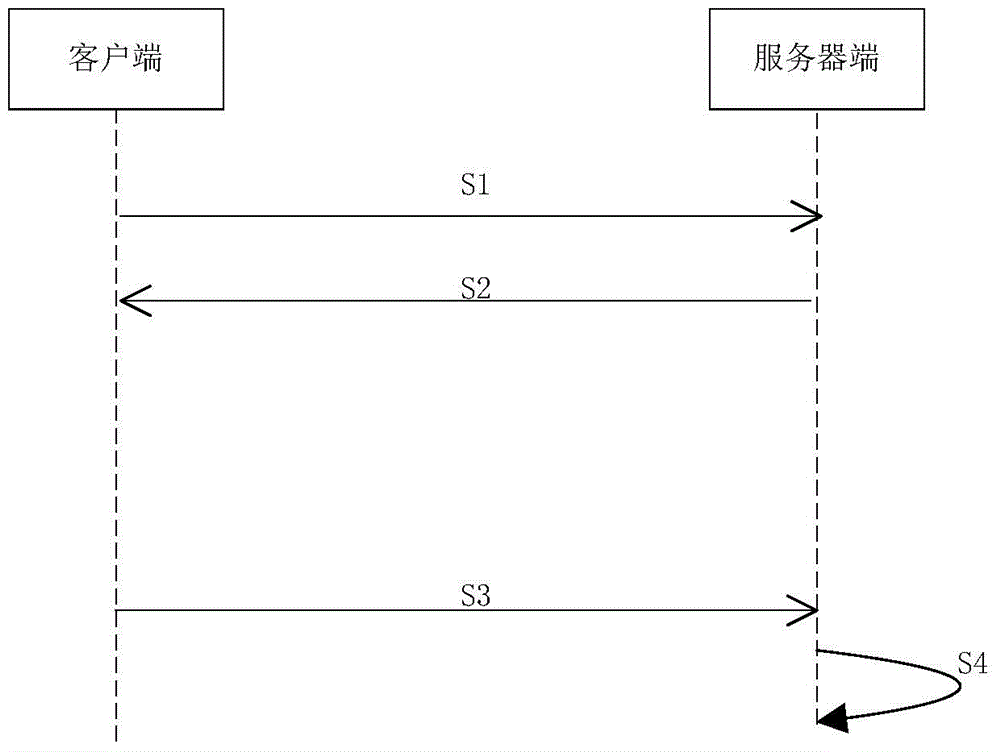
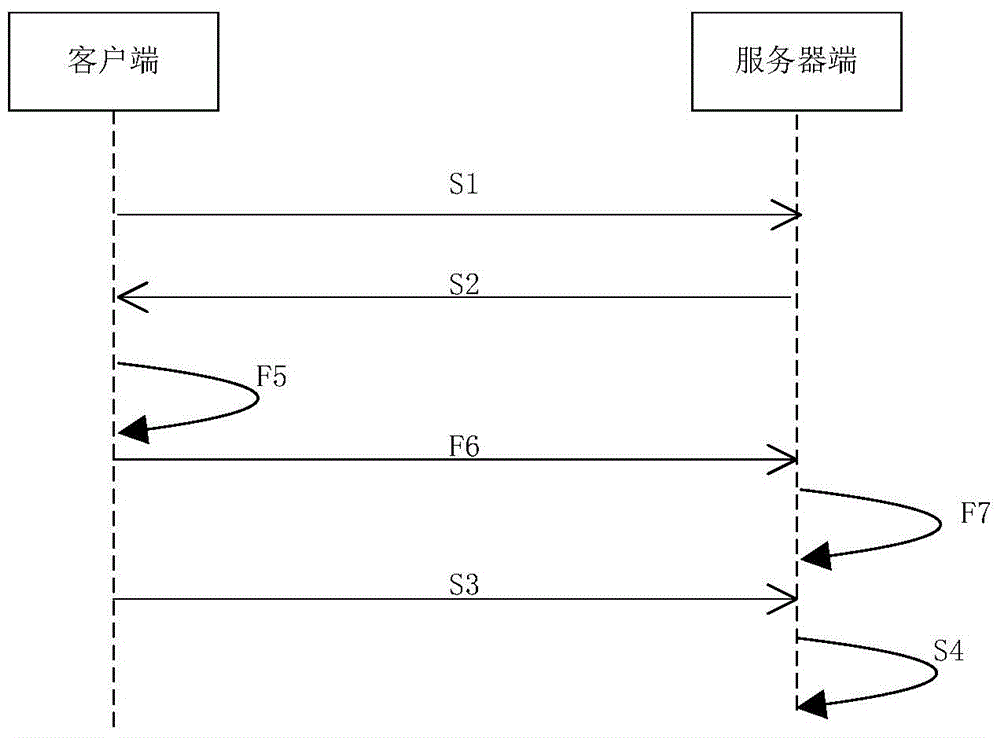
Dynamic signature method, client using the same and server
ActiveCN106330838AIncrease attack costImprove securityUser identity/authority verificationRequest–responseAuthentication
The invention discloses a dynamic signature method, a client using the same and a server. The method comprises steps that: an authentication request is sent to the server through the client; after the server receives the authentication request, an authentication request response message carrying a challenging value is sent to the client; the client selects a signature algorithm according to the challenging value in the authentication request response message, signs the generated authentication response message by using the selected signature algorithm and sends the authentication response message to the server; and the server receives the authentication response message, selects the signature algorithm according to the challenging value, and verifies the signature of the response message. If the verification is passed, the authentication is passed, or else an error is reported. According to the invention, a random signature algorithm is adopted, and even if a user key is leaked, an attacker does not know the signature algorithm and fails to forge the response message, so safety is improved.
Owner:ADVANCED NEW TECH CO LTD
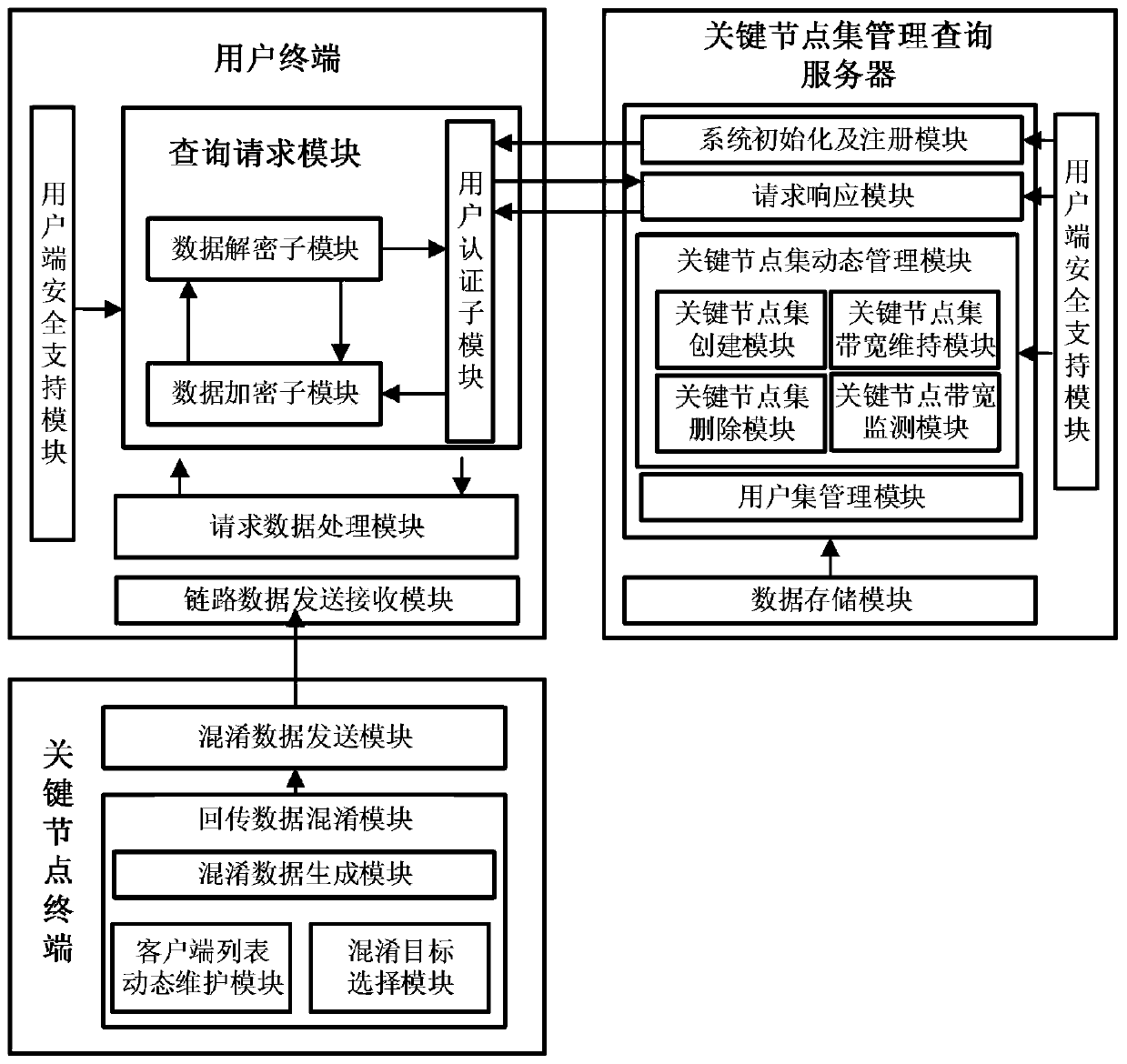
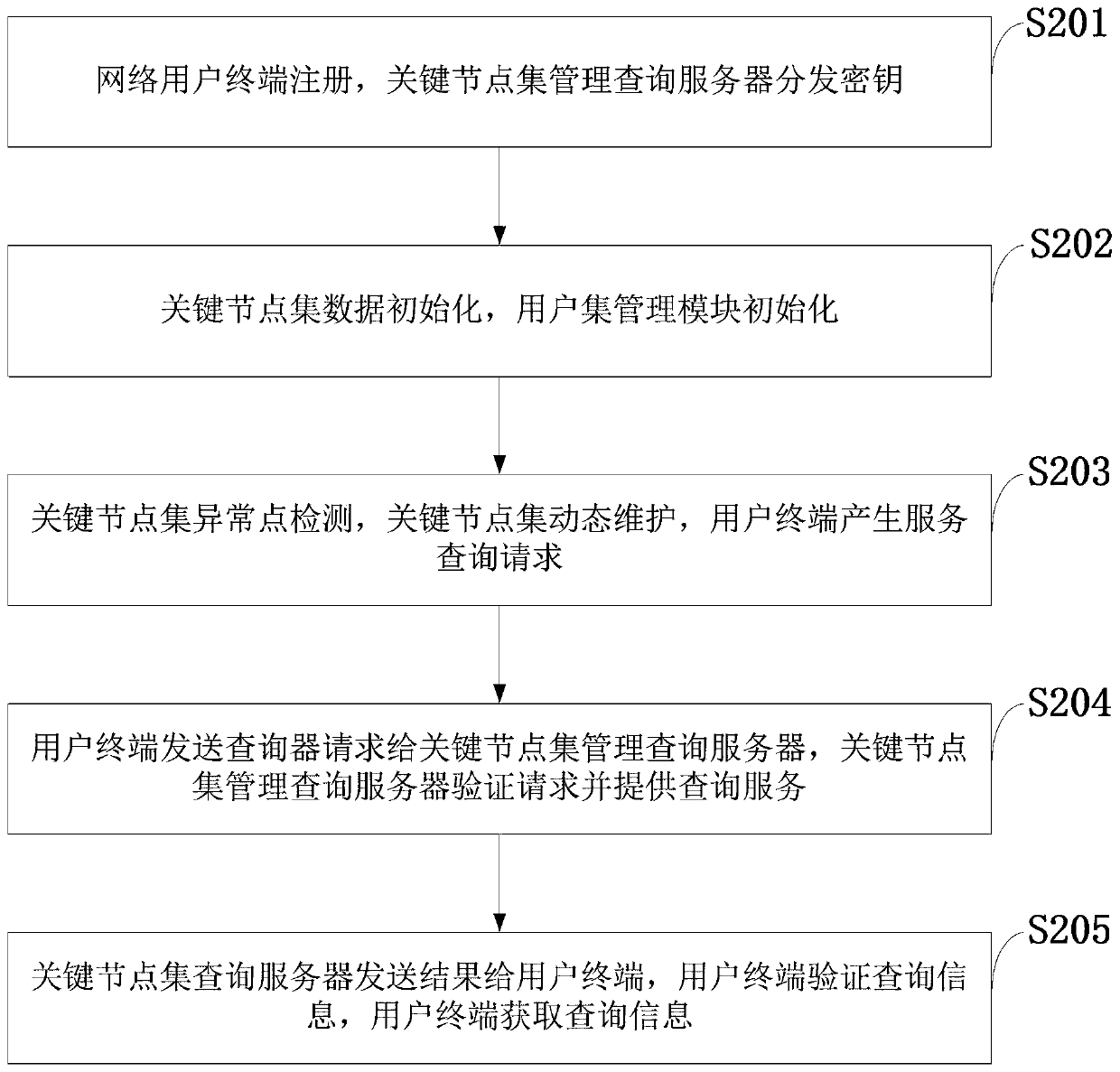
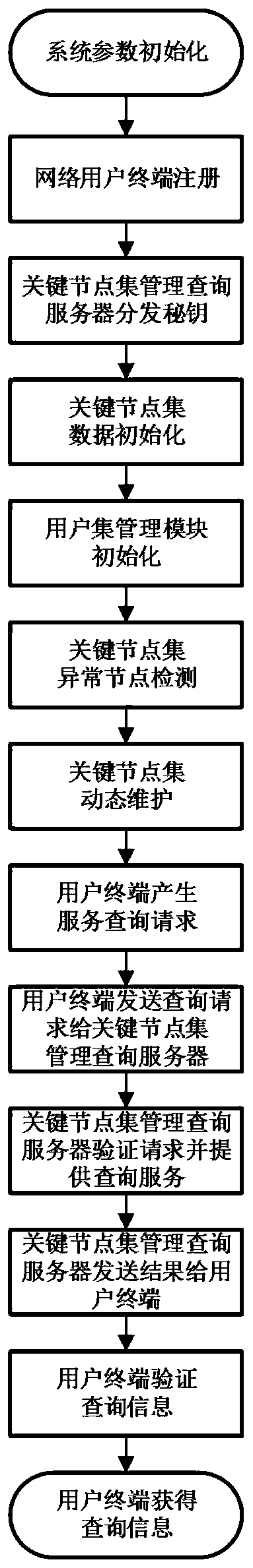
Management query system and method for hidden communication key node
ActiveCN111131145AIncrease attack costReduce overheadKey distribution for secure communicationUser identity/authority verificationCommunications systemEngineering
The invention belongs to the technical field of information security, and discloses a management query system and method for a hidden communication key node. The system comprises a key node set management query server, a network user terminal and a key node terminal. The key node set management query server can provide registration and key distribution services for the network user terminal, generate and manage a key node set and a user set, monitor bandwidth abnormal nodes and provide key node set query services for the network user terminal, the network user terminal can send an encrypted query service request to the key node set management query server, and the key node terminal generates an obfuscated target by adopting a UDP-based data backhaul obfuscation strategy when sending backhaul data to a client, and sends data to the real client and the obfuscated target at the same time. Management query of key nodes and an effective data backhaul confusion scheme are realized, the useridentity hiding performance is improved, and the method is used for enhancing the security of a hidden communication system.
Owner:XIDIAN UNIV
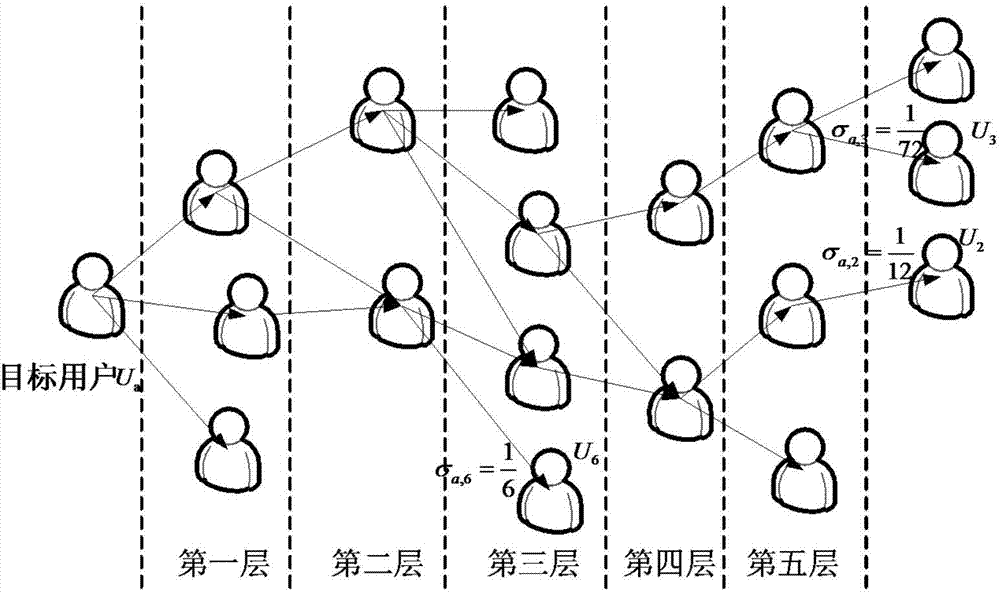
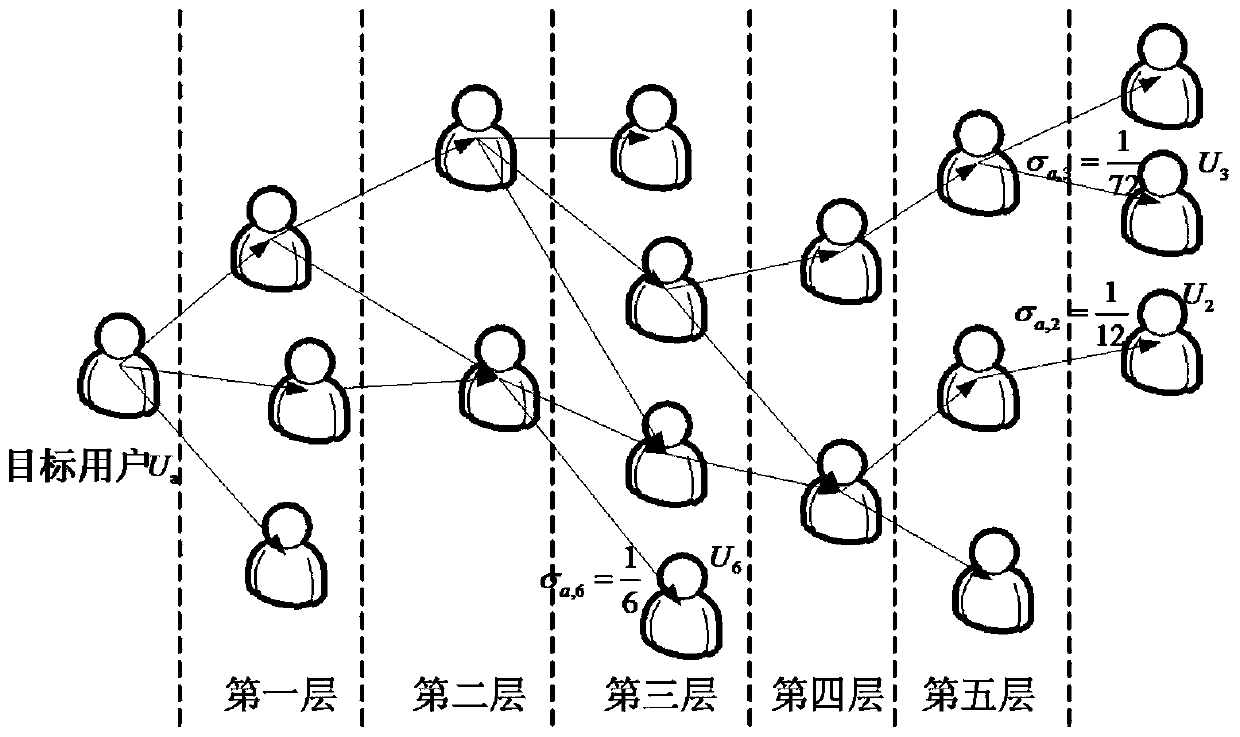
Food and beverage recommendation algorithm based on rating and feature similarity in social network
ActiveCN104850579AIncrease attack costImprove resistance to attackData processing applicationsSpecial data processing applicationsGreek letter sigmaSocial web
The invention discloses a food and beverage recommendation algorithm based on rating and feature similarity in a social network. The method mainly comprises the following steps: (1) building a user rating library in the current social network; (2) calculating the rating similarity between Ua and other users in the user rating library; (3) selecting k users having highest rating similarity with the Ua to obtain a rating similarity recommendation user set; (4) constructing a feature similarity model M=([chi]a, i, [delta]a, i, [sigma]a, i, [gamma]a, i) of the Ua; and (5) calculating feature similarity recommendation levels, and recommending top ranked items to a target user. According to the food and beverage recommendation algorithm, the feature similarity among users is taken as a second basis for the recommendation algorithm other than conventional rating similarity, and various user features are calculated, so that the attack cost is increased greatly; the attack resistance is enhanced greatly; and the recommendation accuracy is increased.
Owner:NANJING UNIV OF POSTS & TELECOMM
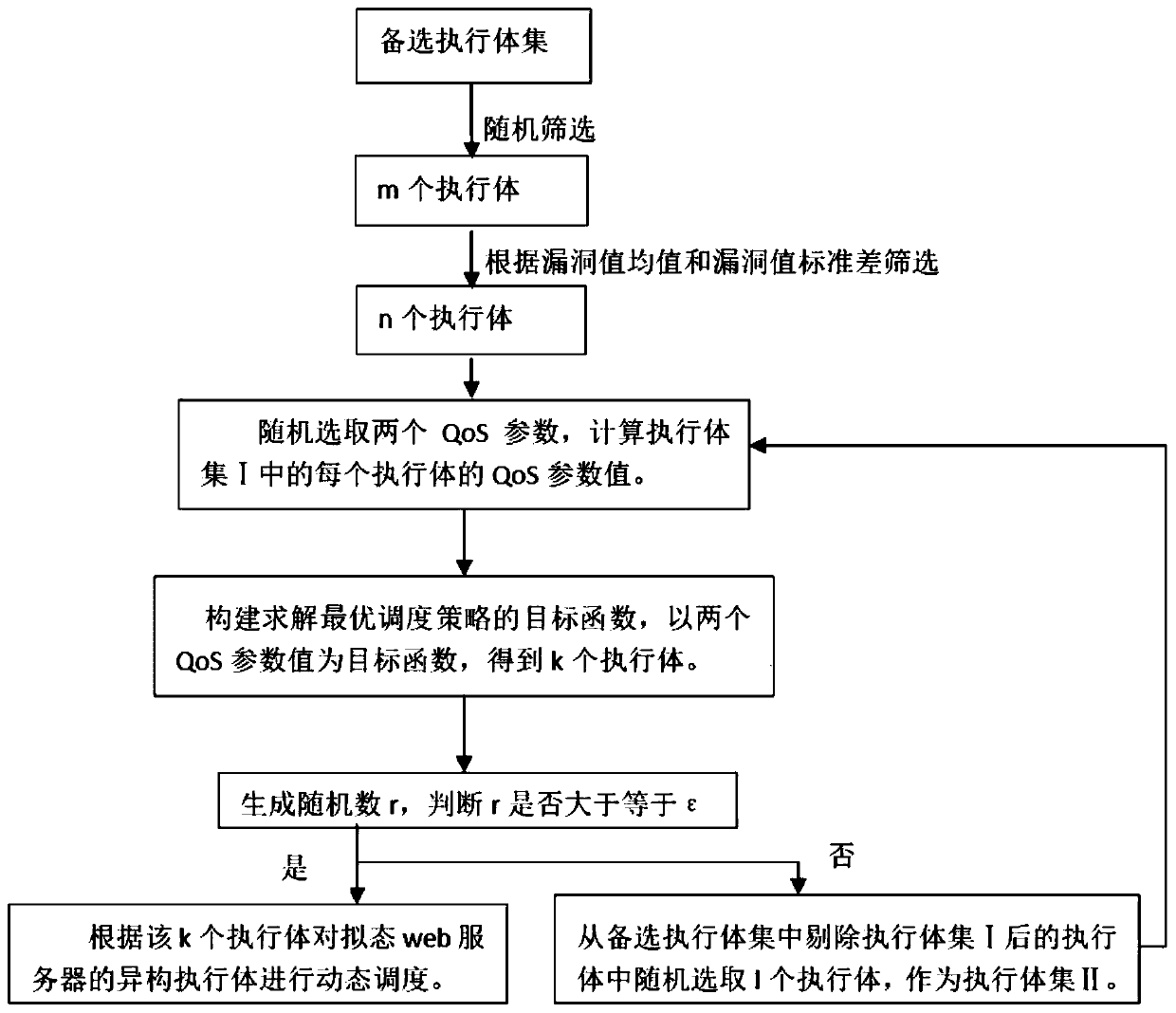
Executive scheduling method for mimicry structure Web server
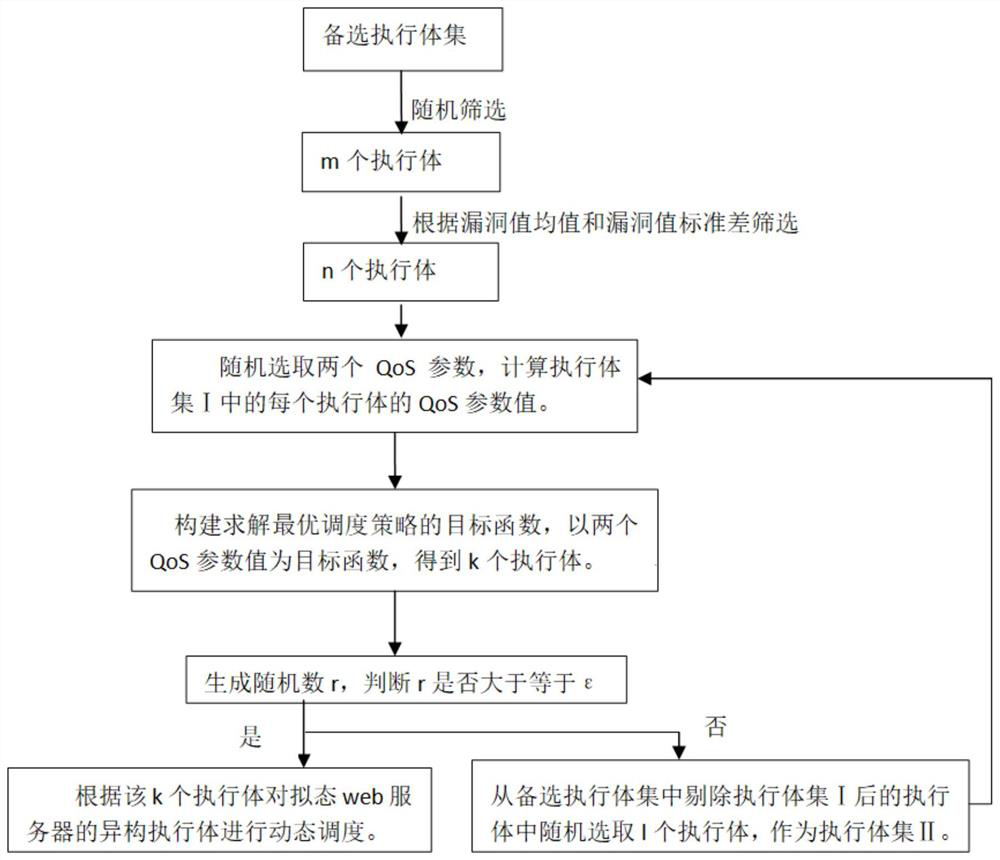
ActiveCN110855692AImprove defenseQuality assuranceMathematical modelsTransmissionQos quality of serviceOptimal scheduling
The invention discloses an executive scheduling method for a mimicry structure Web server, which comprises the following steps of: 1, generating an alternative executive set, randomly selecting m executive bodies, calculating a vulnerability value mean value and a vulnerability value standard deviation of each layer of software stack, and screening n executive bodies positioned in a vulnerabilityvalue threshold range; 2, randomly selecting two QoS parameters, and calculating QoS parameter values; 3, mapping the Bayesian-Stackelberg game model to a web server of the mimicry structure, and constructing an objective function for solving an optimal scheduling strategy; 4, substituting the two QoS parameter values into the target function to obtain k actuators with optimal QoS parameter values; and step 5, generating a random number r, and if r is greater than or equal to epsilon, dynamically scheduling the heterogeneous executors of the mimicry web server according to the k executors. Themethod has the beneficial effects that the confusion is increased and the defense capability is improved while the service quality of the Web server is ensured.
Owner:北京网聘信息技术有限公司
Virtualized packing method for Android local layer instruction compilation based on ELF infection
InactiveCN107480476AIncrease attack costGood compatibilityProgram/content distribution protectionVirtualizationInstruction code
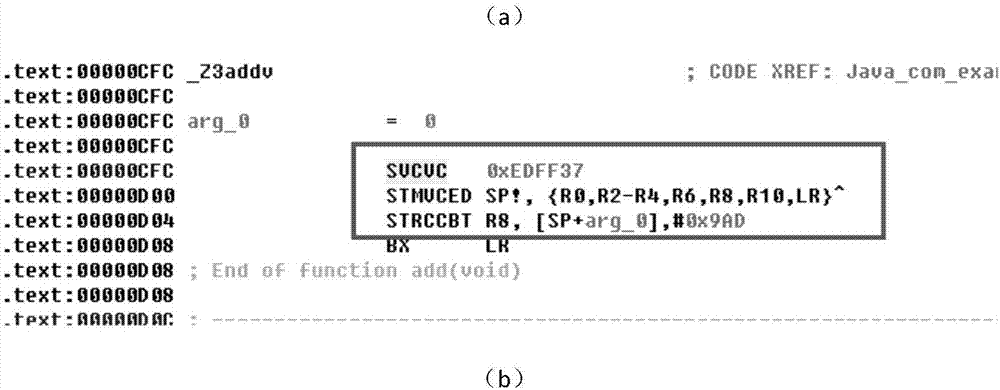
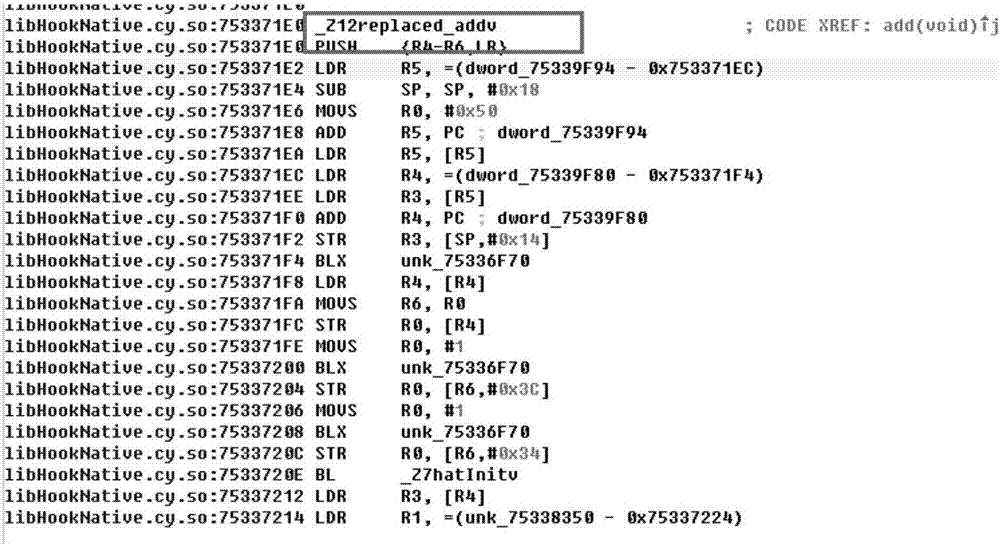
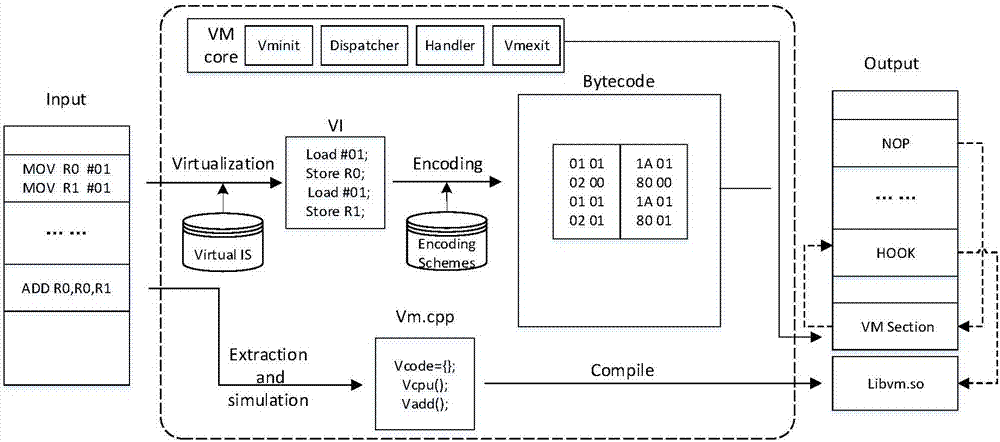
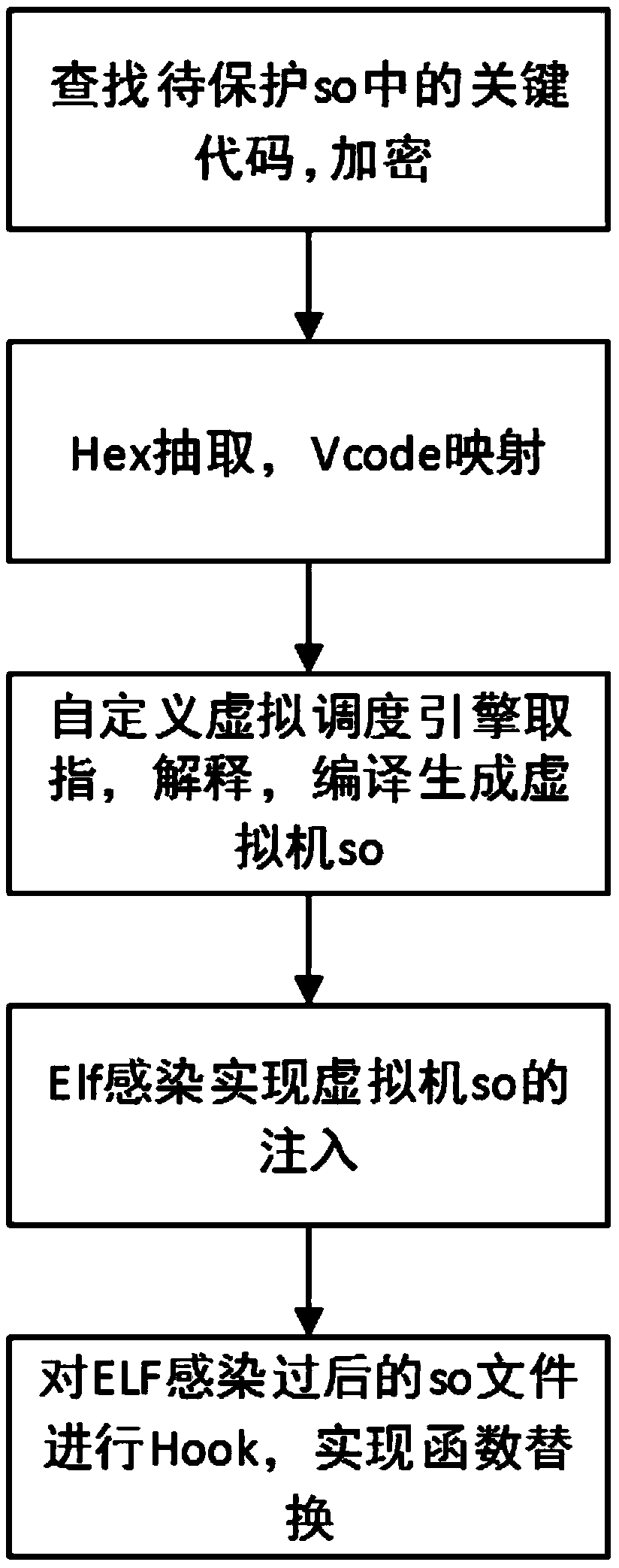
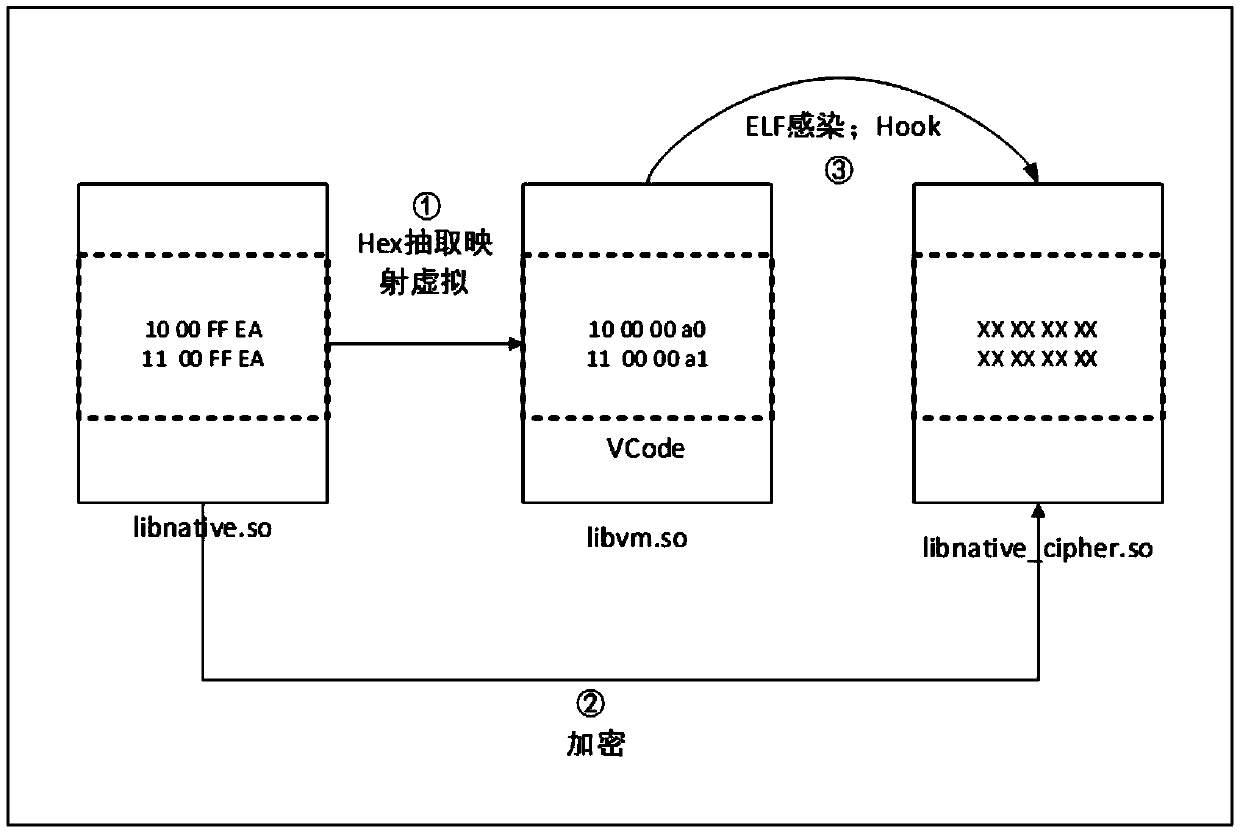
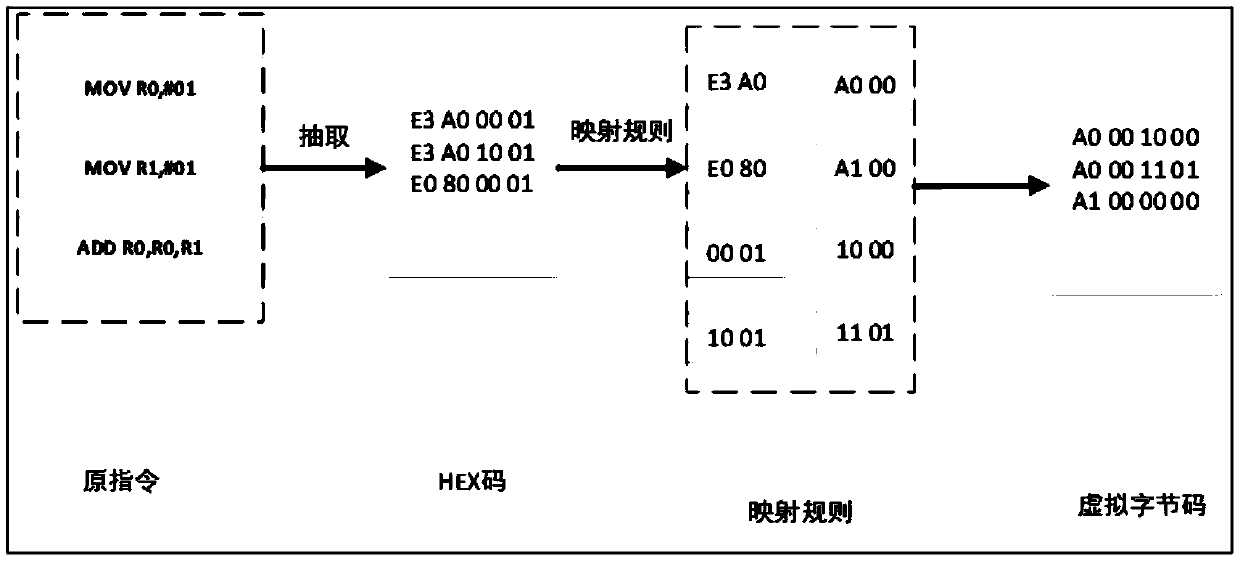
The invention discloses a virtualized packing method for Android local layer instruction compilation based on ELF infection. The method is characterized in that Hex extraction and mapping virtualization are conducted on a to-be-protected so document, so a so document of a virtual machine is formed; key code sections of the so document is encrypted, so an encrypted so document is formed; ELF infection is conducted on the encrypted so document by the so document of the virtual machine, so an infected so document is formed; and Hook replacement is conducted on the encrypted so document by a Cydia Substrate framework, so encrypted codes in the encrypted so document are replaced by virtual instruction codes in the so document of the virtual machine. The method disclosed by the invention applies an idea of virtualization in compilation. The idea does not involve problems generated from different ARM platform versions, so the method has high compatibility, prevents memory Dump analysis and increases attack cost of an attacker.
Owner:NORTHWEST UNIV
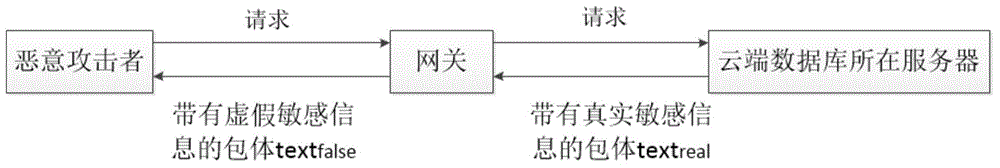
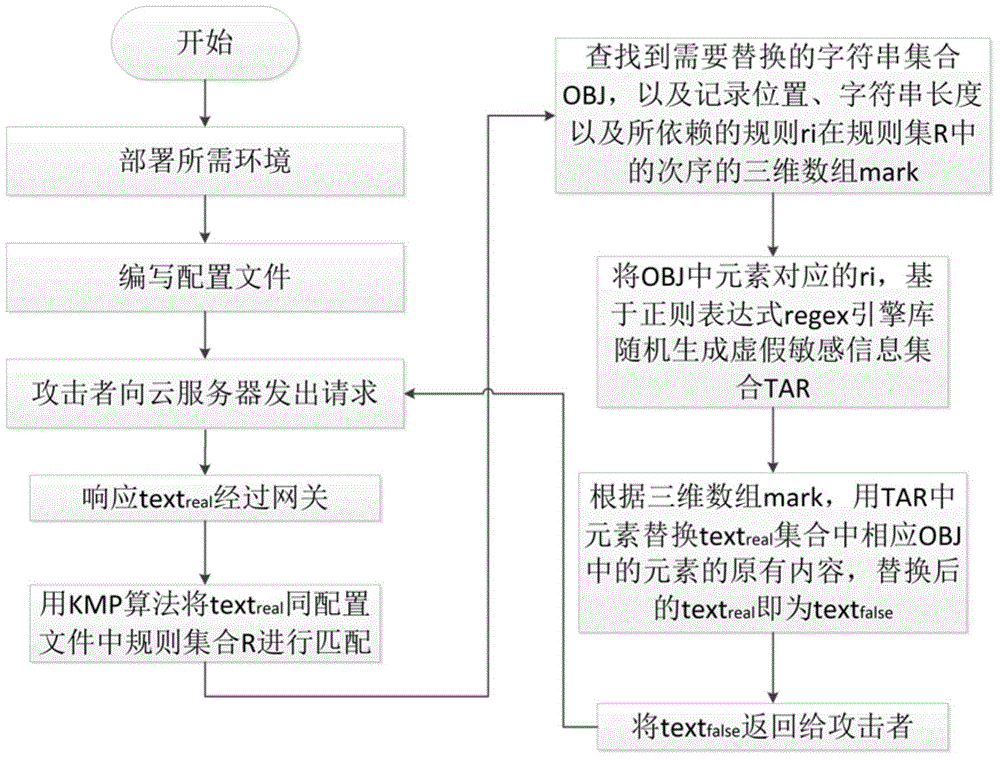
Method for randomly simulating sensitive information in cloud database
ActiveCN104966032AUse impactIncrease attack costDigital data protectionInternet privacyRandomization
The invention discloses a method for randomly simulating sensitive information in a cloud database. By adopting the method, the content of real sensitive information collected by an attacker can be replaced through a random simulating algorithm, the replacing simulated sensitive information is strictly generated according to the format of the context grammar of the real sensitive information, the attacker may take the simulated sensitive information as the real sensitive information, so the cost of attack can be raised to a certain extent. Valid users do not need the sensitive information or need a series of standard authorization processes to get the sensitive information, so the method will not influence valid users during usage.
Owner:ZHEJIANG UNIV
Financial POS system capable of resisting channel Trojan attack and anti-attack realization method thereof
InactiveCN102663863AThe attack method failsHigh riskDigital data protectionCash registersSubliminal channelPassword
The invention discloses a financial POS system capable of resisting a channel Trojan attack and an anti-attack realization method thereof. The system comprises a POS mainboard, an IC card box, a password keyboard, a user PIN disk, a nonvolatile memory, an IC card and a trust management party. The IC card box is connected with the POS mainboard. The password keyboard is connected with the IC card box. The POS mainboard is connected with the trust management party through an I / O interface. The IC card is connected with the trust management party through the IC card box. By using the system and the method of the invention, a subliminal channel can be reliably shielded on a POS terminal of a dealer. A card holder uses the private user PIN disk to confirm a transaction amount and output a PIN password so that the dealer and the card holder can avoid the attack of the channel Trojan.
Owner:GUANGZHOU UNIVERSITY +2
Android application program protection method based on dual ARM instruction virtualization
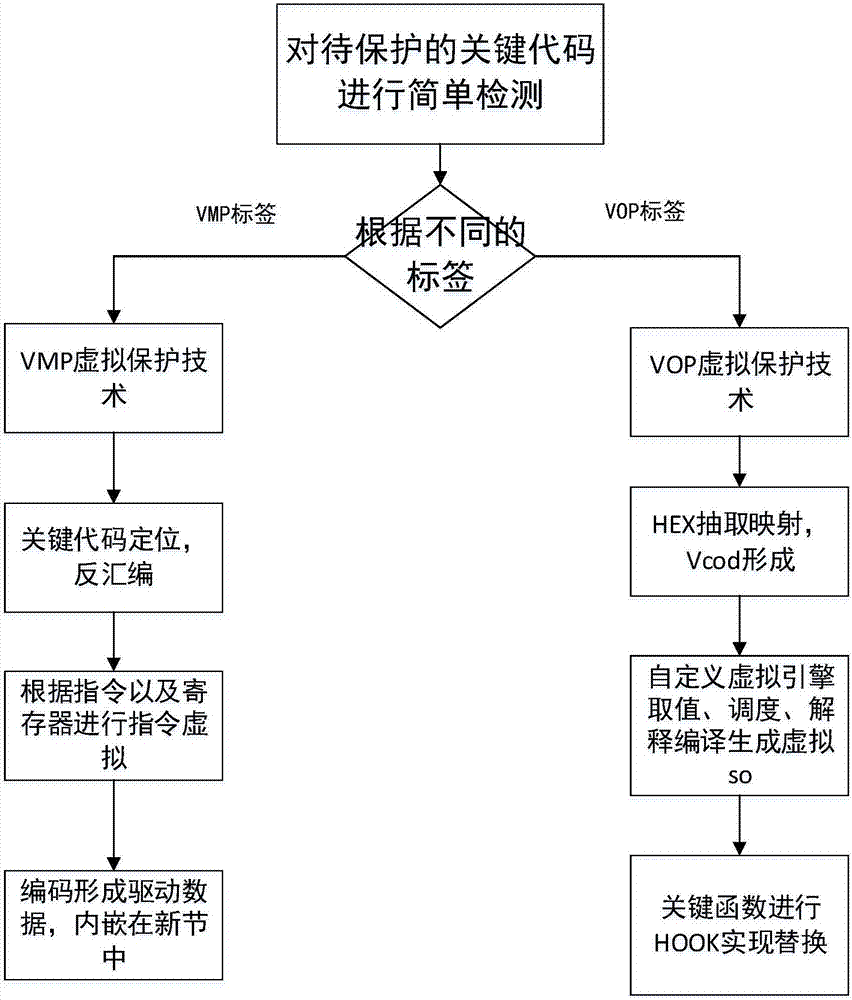
InactiveCN107577925AIncrease attack costProtection complexityProgram/content distribution protectionVirtualizationApplication software
The invention discloses an Android application program protection method based on dual ARM instruction virtualization. The method comprises the steps that key code segments needing to be protected ina so file are searched for, wherein the key code segments include a key code segment needing VOP protection and a key code segment needing VMP protection; Hex extraction and mapping virtualization areperformed on the key code segment needing VOP protection, and a VOP virtual machine so file is formed; the key code segment needing VOP protection is encrypted, Hook replacement is performed on the encrypted VOP key code segment, and a virtual instruction code in the VOP virtual machine so file is made to replace an encrypted code, corresponding to the encrypted VOP key code segment, in the so file; instruction virtualization is performed on the key code segment needing VMP protection, and a protected VMP virtual machine so file with virtual sections is formed; and driving data in the VMP virtual machine so file is made to replace the code, corresponding to the key code segment, in the so file. Through the method, two different virtual machine protection thoughts are combined, attack costof a reverser is increased, and the complexity of a protected program is enhanced.
Owner:NORTHWEST UNIV(CN)
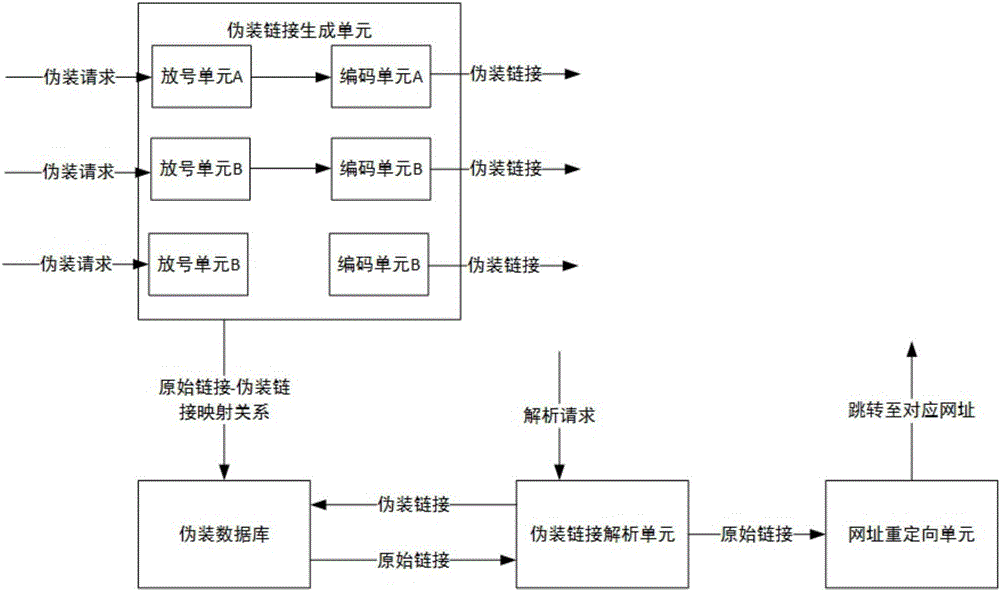
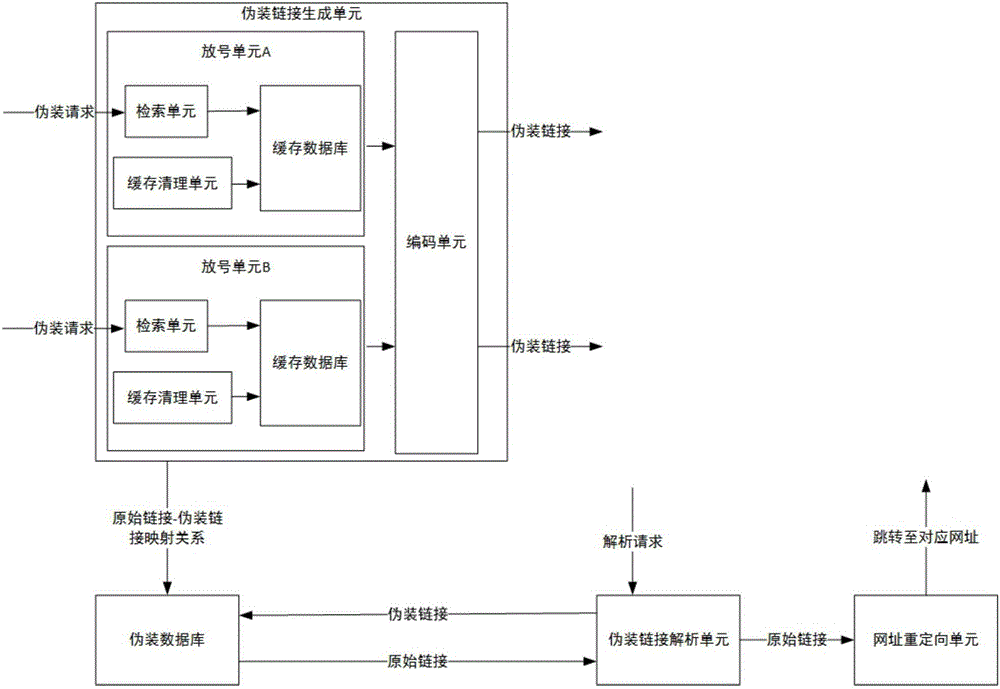
Link camouflage system and method
InactiveCN106817375AReduce the probability of malicious attacksIncrease attack costTransmissionUnique identifierDistributed computing
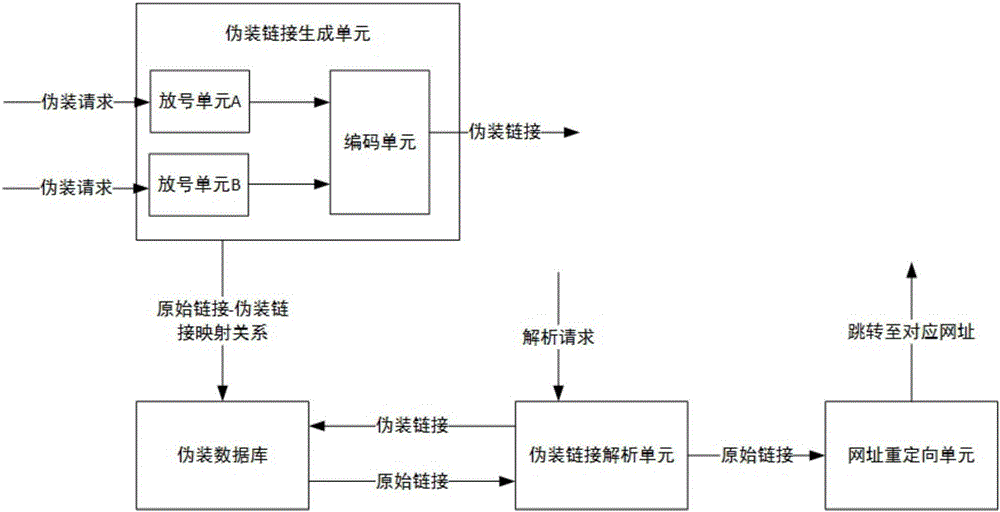
The present invention relates to a link camouflage system and a method. The system comprises a camouflage link creation unit and a camouflage database. The camouflage link creation unit is used for converting an original link in a camouflage request into a corresponding camouflage link, storing the mapping relationship between the original link and the camouflage link in the camouflage database, and returning the camouflage link to a requesting party. The camouflage link creation unit comprises N number allocation units and a coding unit. Each number allocation unit is used for allocating a number value to the camouflage request as the unique identifier of the camouflage request. The coding unit is used for converting the unique identifier into the camouflage link according to a predetermined coding rule. The difference between the initial values of the number values of the N number allocation units is N. Each number allocation unit also includes a calculation unit and the calculation unit progressively increases or decreases the number value of the above number allocation unit by N in response to each camouflage request, wherein N is greater than 1.
Owner:PHICOMM (SHANGHAI) CO LTD
Safety two-direction vector advantage comparison method based on block chain
ActiveCN111277406AReduce the burden onReduce computational overheadKey distribution for secure communicationDiscounts/incentivesAttackComputation process
The invention belongs to the field of cryptology and information security, and particularly relates to a security two-direction vector advantage comparison method based on a block chain. According tothe method, block chain and cloud outsourcing calculation is used as a basic framework, a block chain is used as a driving tool to replace a trusted third party to manage and supervise the whole calculation process, and normal operation of a vector is ensured. By means of cloud outsourcing computing, heavy computing tasks are transferred from a user to an outsourcing server with enough computing power, the burden of the user is relieved, and extra computing resources are fully utilized. According to the method, cloud outsourcing calculation and the block chain are combined, a reliable reward punishment mechanism is provided, the attack cost of a malicious server is greatly increased while the calculation overhead of a user is reduced, and therefore a semi-honest model protocol which is seriously limited in actual operation originally is guaranteed.
Owner:SUN YAT SEN UNIV
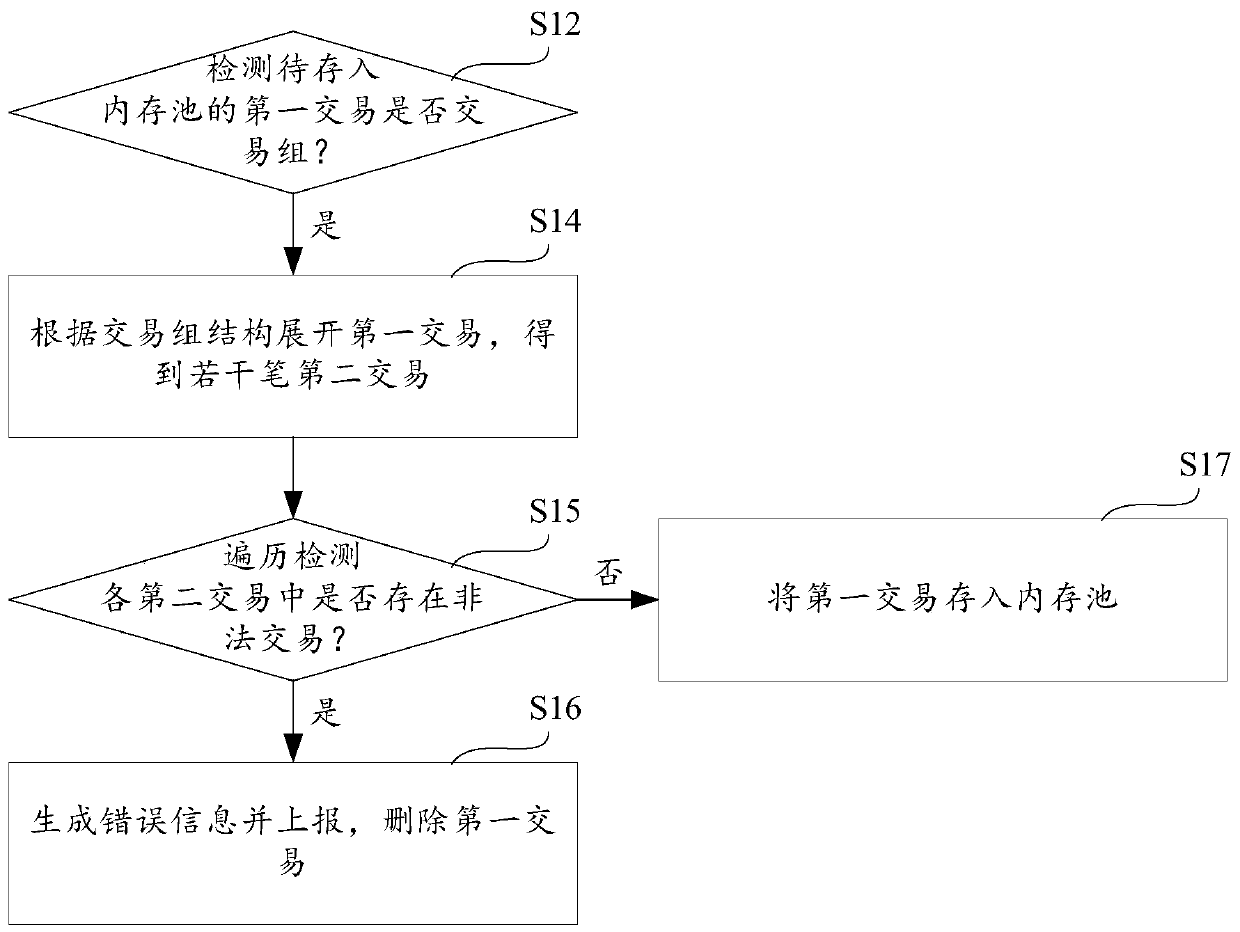
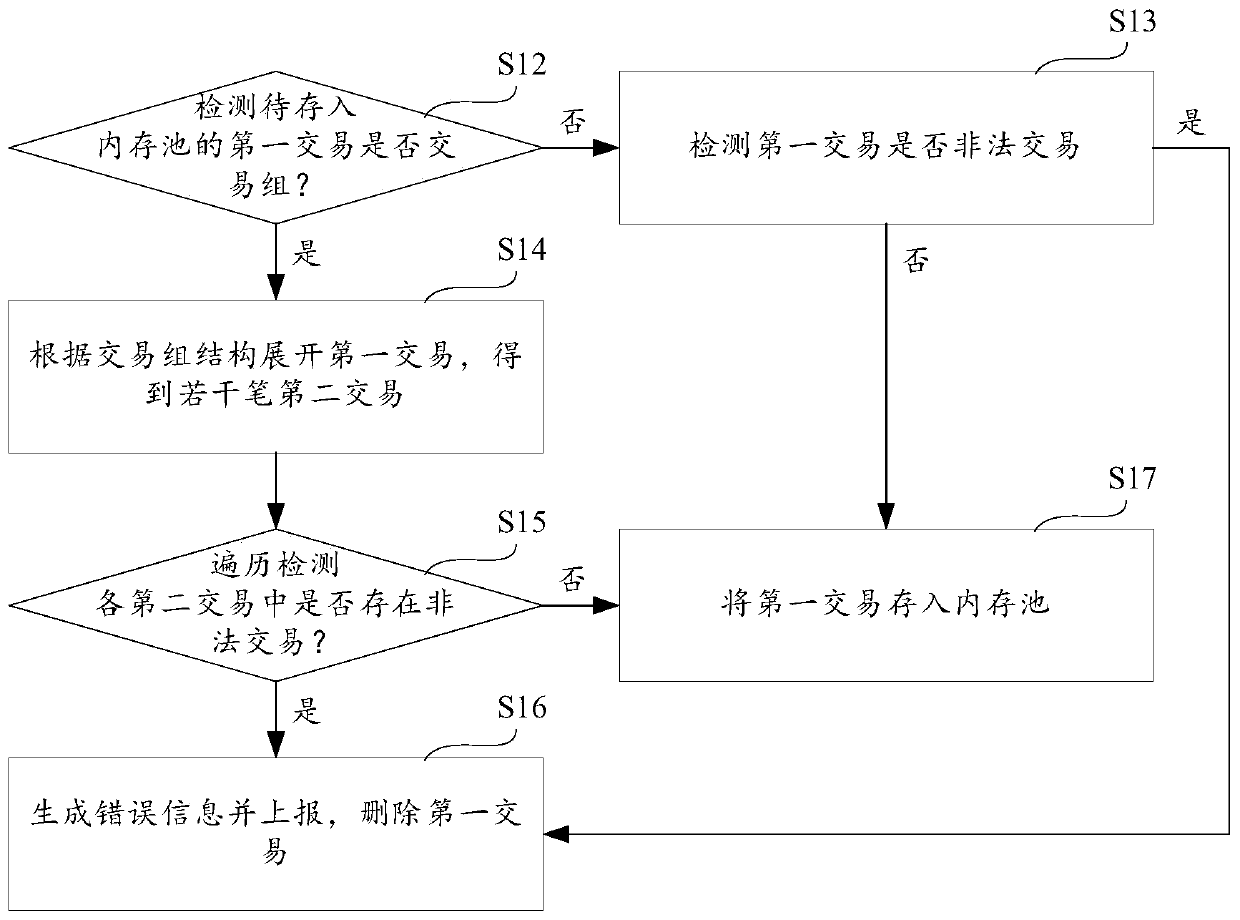
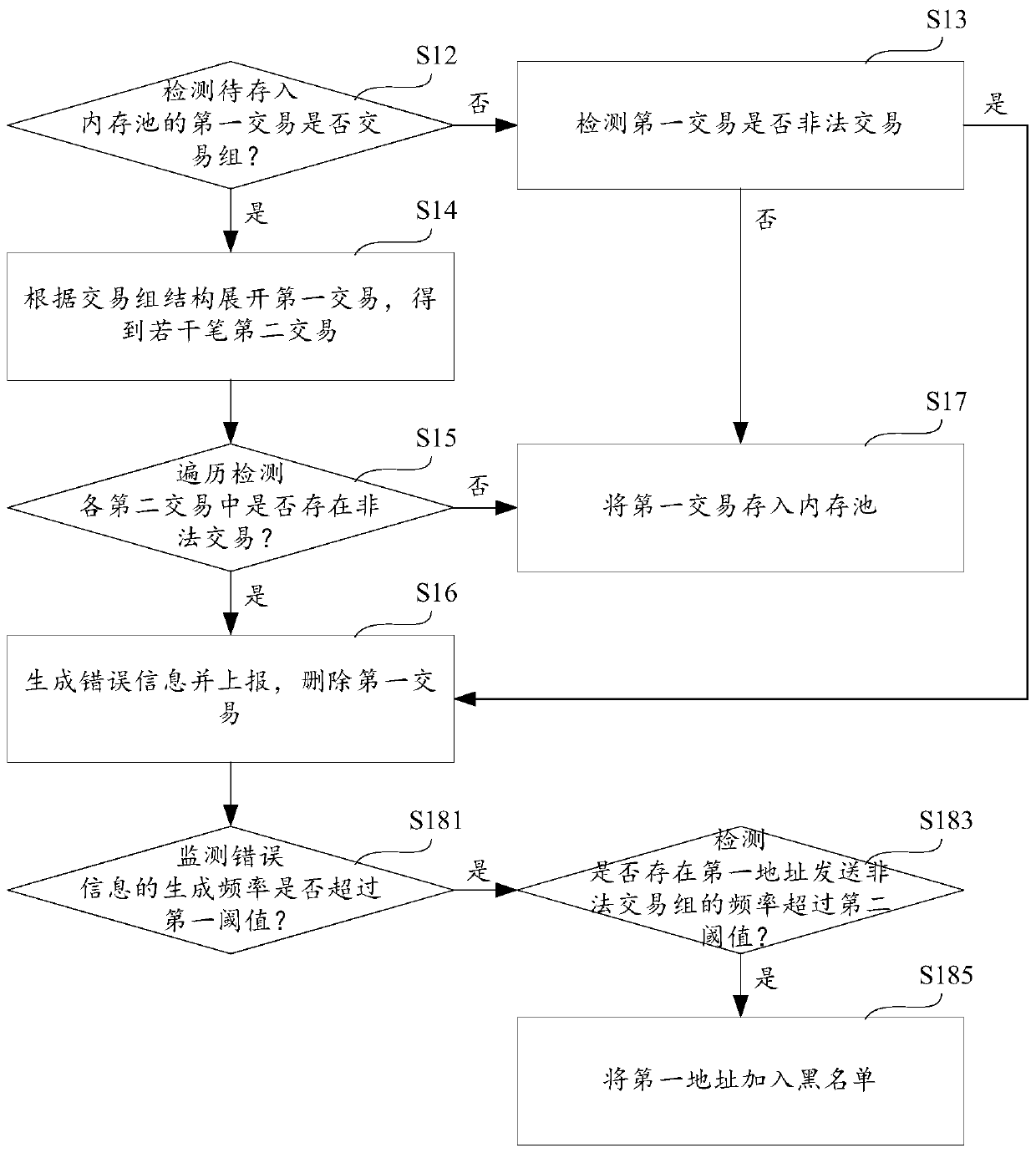
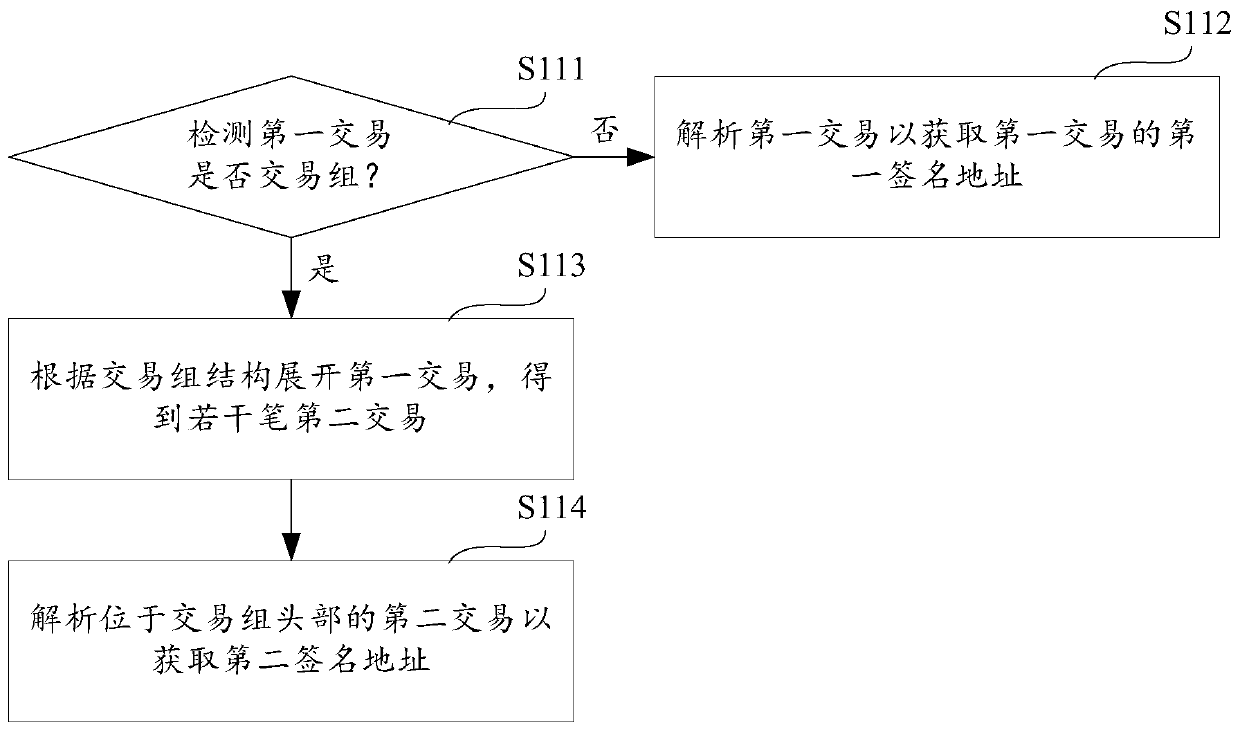
Transaction group attack protection method and device and storage medium
PendingCN110197372ANo congestionIncrease attack costFinancePayment protocolsFinancial transactionOperating system
The invention provides a transaction group attack protection method and device and a storage medium, and the method comprises the steps of detecting whether a first transaction to be stored in a memory pool has a transaction group: if yes, expanding the first transaction according to a transaction group structure, and obtaining a plurality of second transactions; traversing and detecting whether illegal transactions exist in the second transactions or not: if so, generating the error information and reporting the error information, and deleting the first transaction; and if not, storing the first transaction into a memory pool. According to the invention, each transaction in the transaction group is illegally detected before the transaction group is stored in the memory pool, and the transaction group comprising the illegal transaction is deleted, so that the transaction group comprising the illegal transaction cannot enter the memory pool, and the memory pool cannot be jammed by caching a large number of transaction groups comprising the illegal transaction.
Owner:HANGZHOU FUZAMEI TECH CO LTD
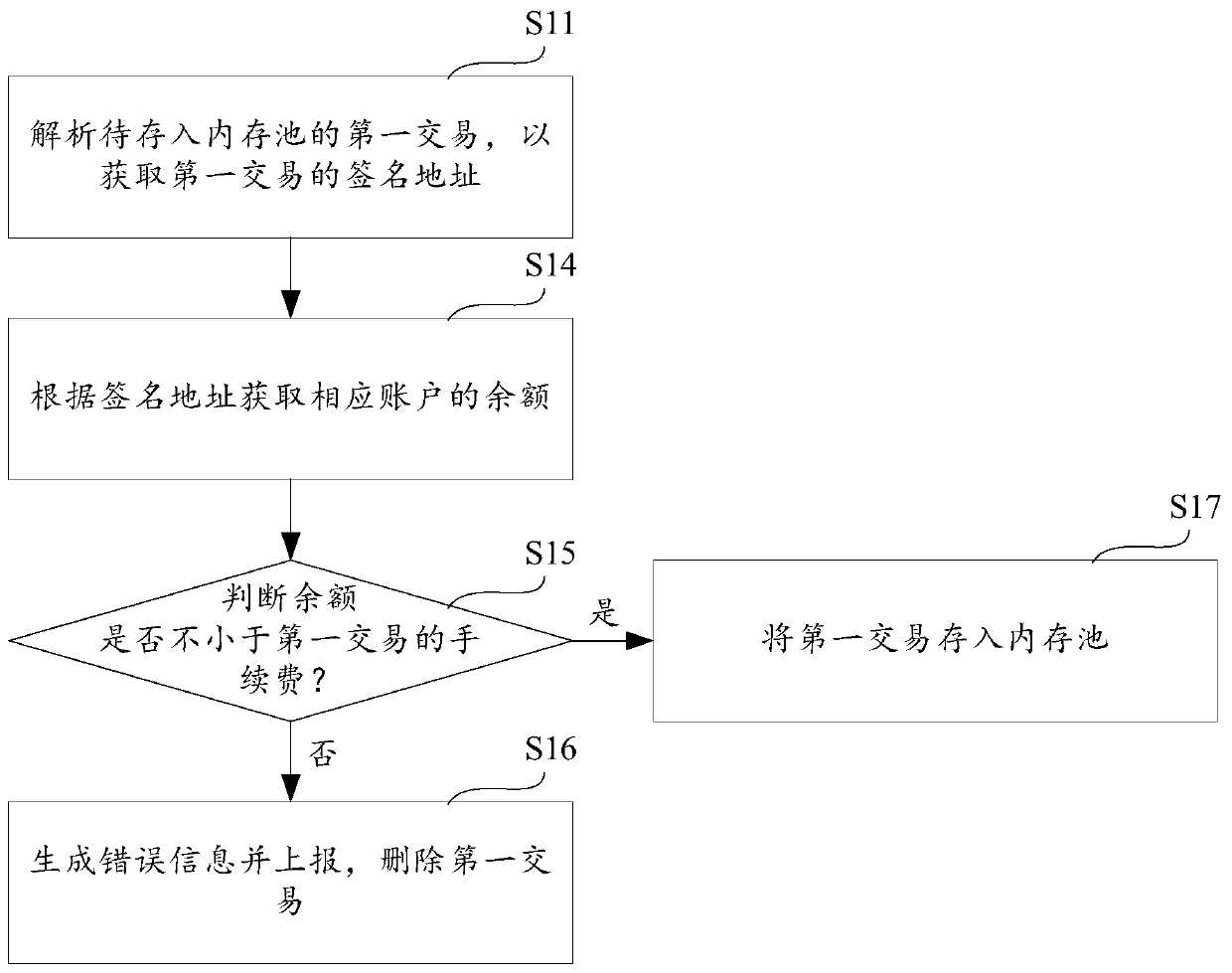
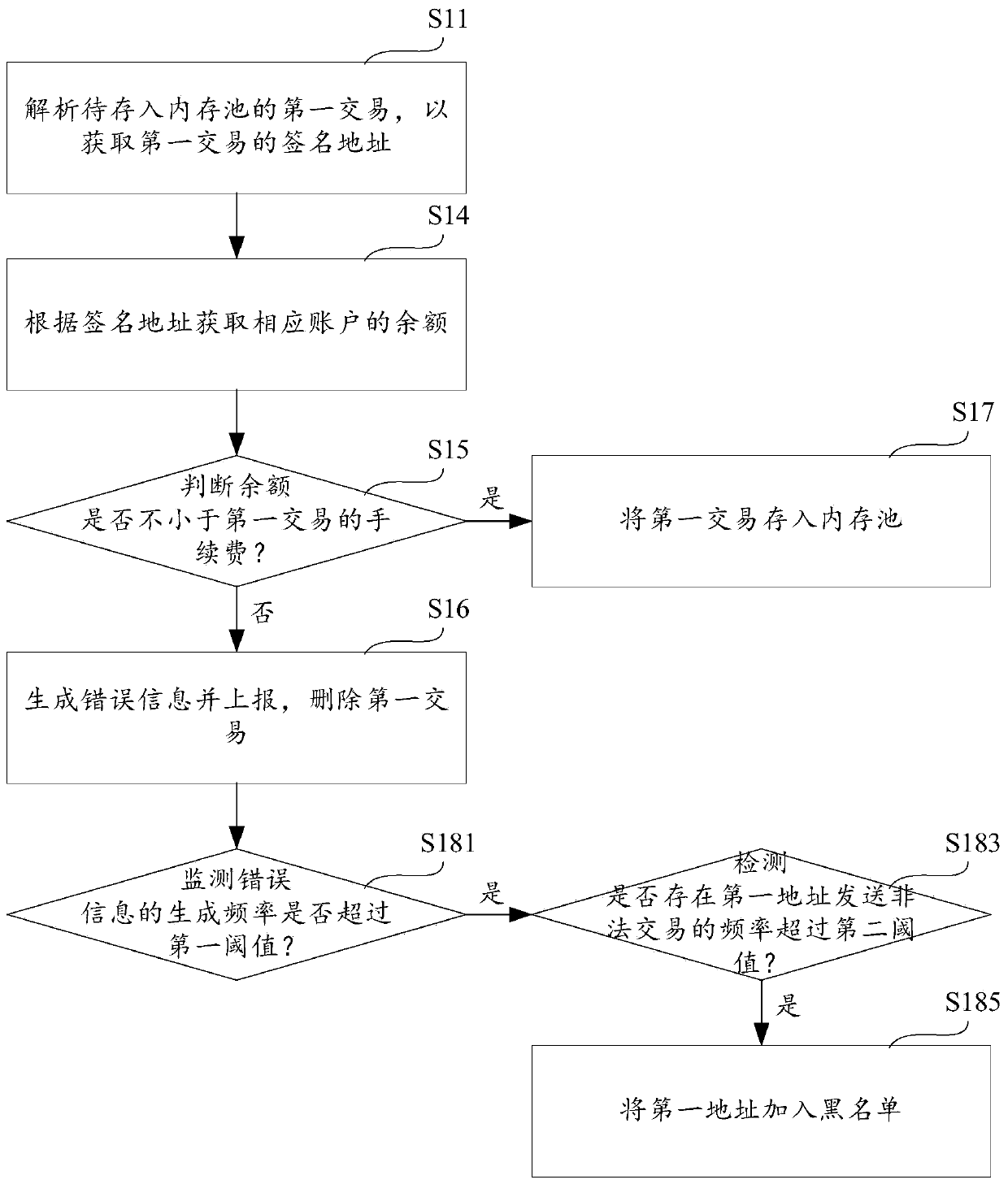
Anti-attack method, equipment and storage medium
PendingCN110189124ANo congestionIncrease attack costFinanceProtocol authorisationFinancial transactionComputer science
The invention provides an anti-attack method, equipment and a storage medium. The anti-attack method comprises the steps: analyzing a first transaction to be stored in a memory pool, so as to obtain asignature address of the first transaction; obtaining the balance of the corresponding account according to the signature address; judging whether the balance is not less than the service fee of thefirst transaction or not: if not, generating and reporting error information, and deleting the first transaction; and if so, storing the first transaction into the memory pool. The anti-attack methodanalyzes the address before the transaction is stored in the memory pool so as to obtain the account balance, and determines whether the balance is enough to pay the service fee, so as to filter the transaction with insufficient account balance, and guarantee the condition that the memory pool is jammed due to the fact that the account balance is not enough to pay the service fee.
Owner:HANGZHOU FUZAMEI TECH CO LTD
Php-based independent sql injection defense analysis alarm method and system thereof
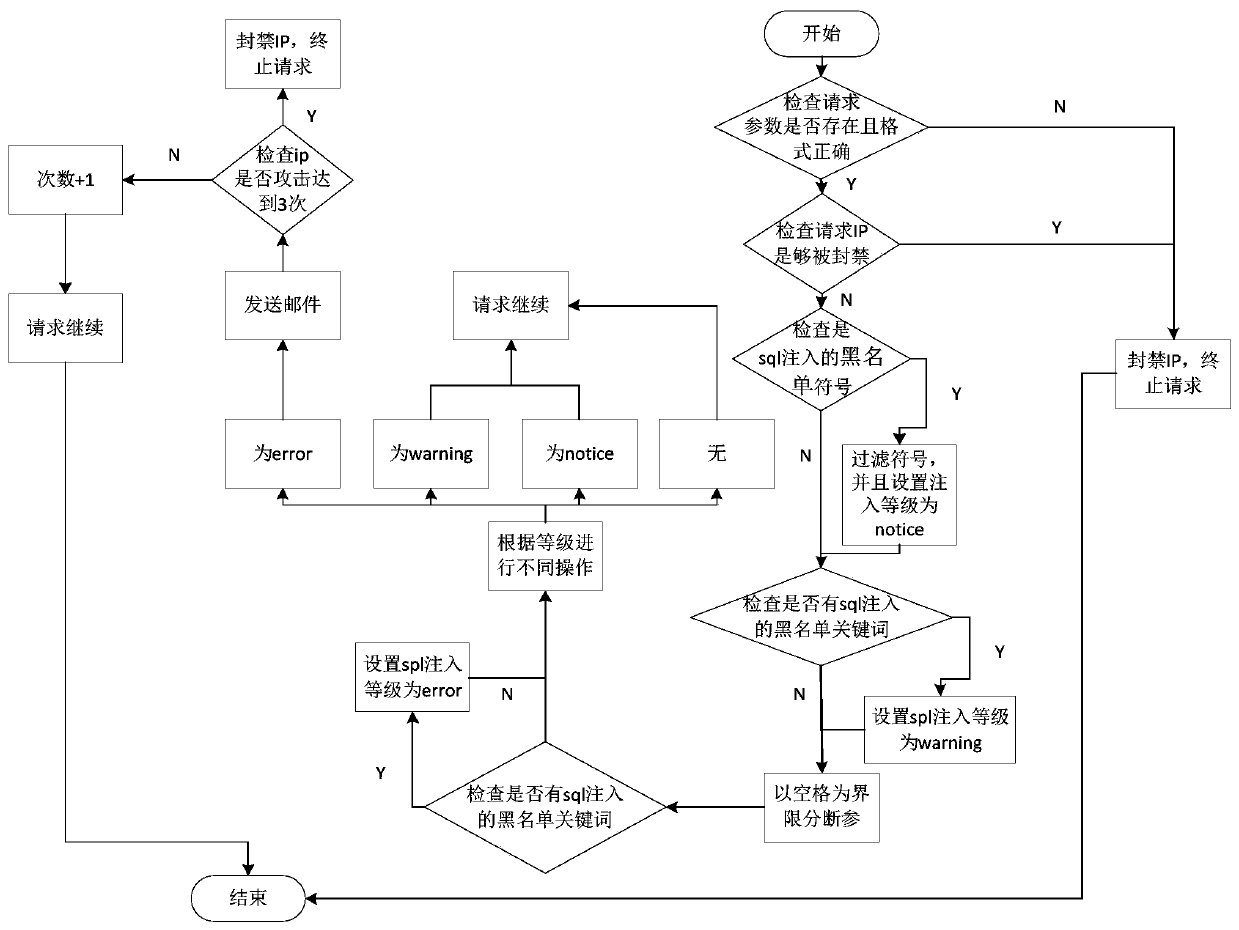
InactiveCN110474888AIncrease attack costProtection securityTransmissionSQL injectionComputer science
The invention discloses a php-based independent sql injection defense analysis alarm method and a system thereof, and the method comprises the steps: checking whether a request IP is a forbidden IP blacklist, ending the request if the request IP is the forbidden IP blacklist, and entering the next step if the request IP is not the forbidden IP blacklist; judging whether parameters of sql injectioncontain blacklist symbols, and if yes, setting the sql injection as a note level; judging whether parameters of sql injection contain blacklist keywords, and if yes, setting the sql injection as a winning level; dividing the parameters of the sql injection by taking a space as a criterion, judging whether the parameters contain blacklist keywords, and if yes, setting the sql injection as an errorlevel; and performing sql injection on the error level, checking whether the request ip injected by the sql is subjected to injection attacks for a specified number of times, and if yes, forbidding the request ip and listing the request ip into a forbidden IP blacklist. According to the method, measures are taken for the sql injection problem in an omnibearing manner, corresponding measures are taken for prevention, response, monitoring and recording, and the data security is protected to a greater extent.
Owner:GUANGDONG EFLYCLOUD COMPUTING CO LTD
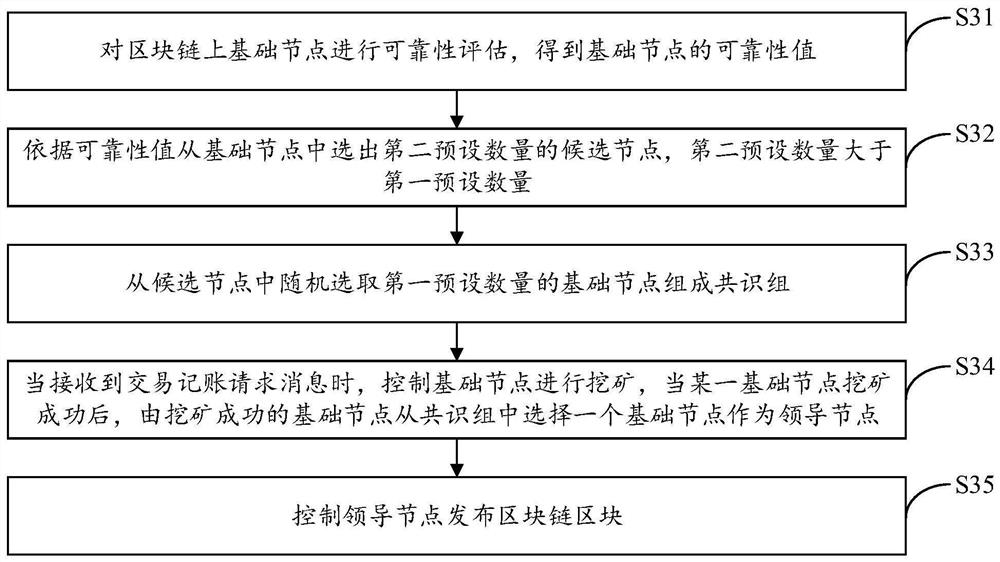
Blockchain consensus mechanism implementation method and device, equipment and storage medium
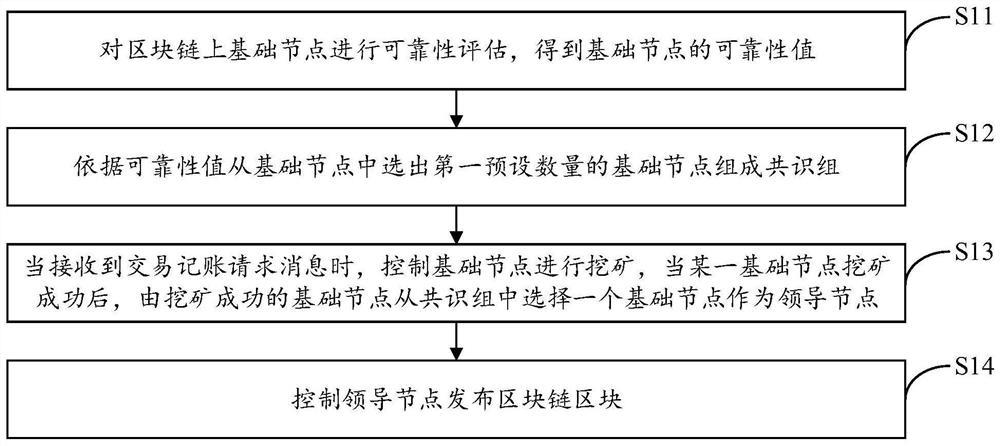
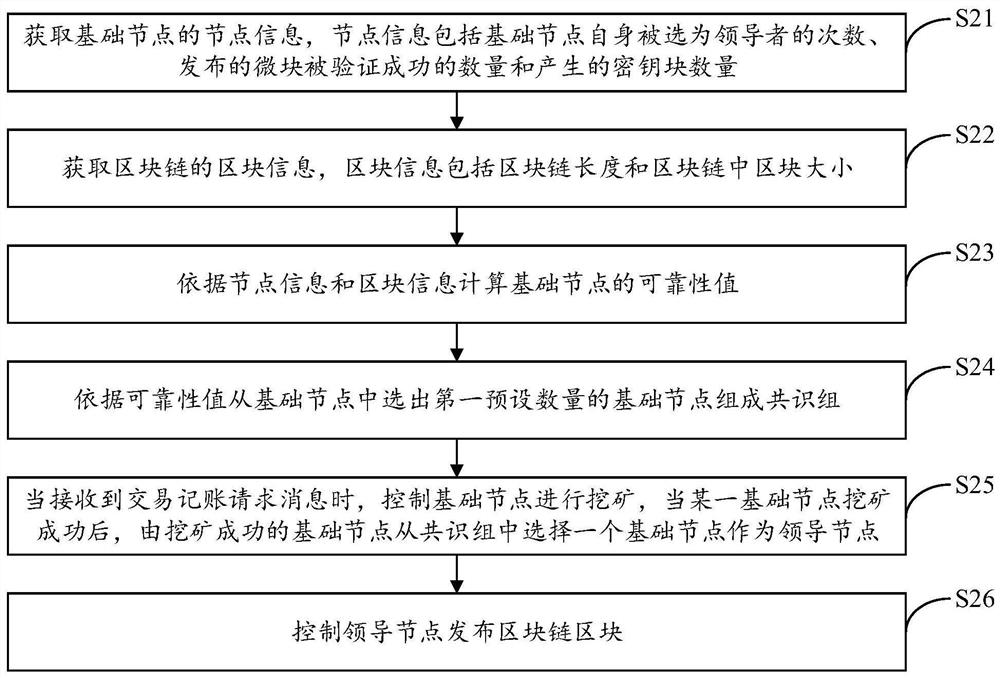
PendingCN112862607AImprove selectionImprove reliabilityFinanceDatabase distribution/replicationEngineeringConsensus
The invention provides a blockchain consensus mechanism implementation method and device, equipment and a storage medium, and the method comprises the following steps: carrying out the reliability evaluation of a basic node on a block chain, and obtaining a reliability value of the basic node; selecting a first preset number of basic nodes from the basic nodes according to the reliability values to form a consensus group; when a transaction bookkeeping request message is received, controlling the base nodes to carry out mining, and after a certain base node succeeds in mining, enabling the base node which succeeds in mining to select one base node from the consensus group to serve as a leader node; and controlling the leader node to publish the blockchain block. The method can achieve the purposes of saving computing resources, improving the transaction throughput and improving the anti-attack performance of the nodes.
Owner:PING AN TECH (SHENZHEN) CO LTD
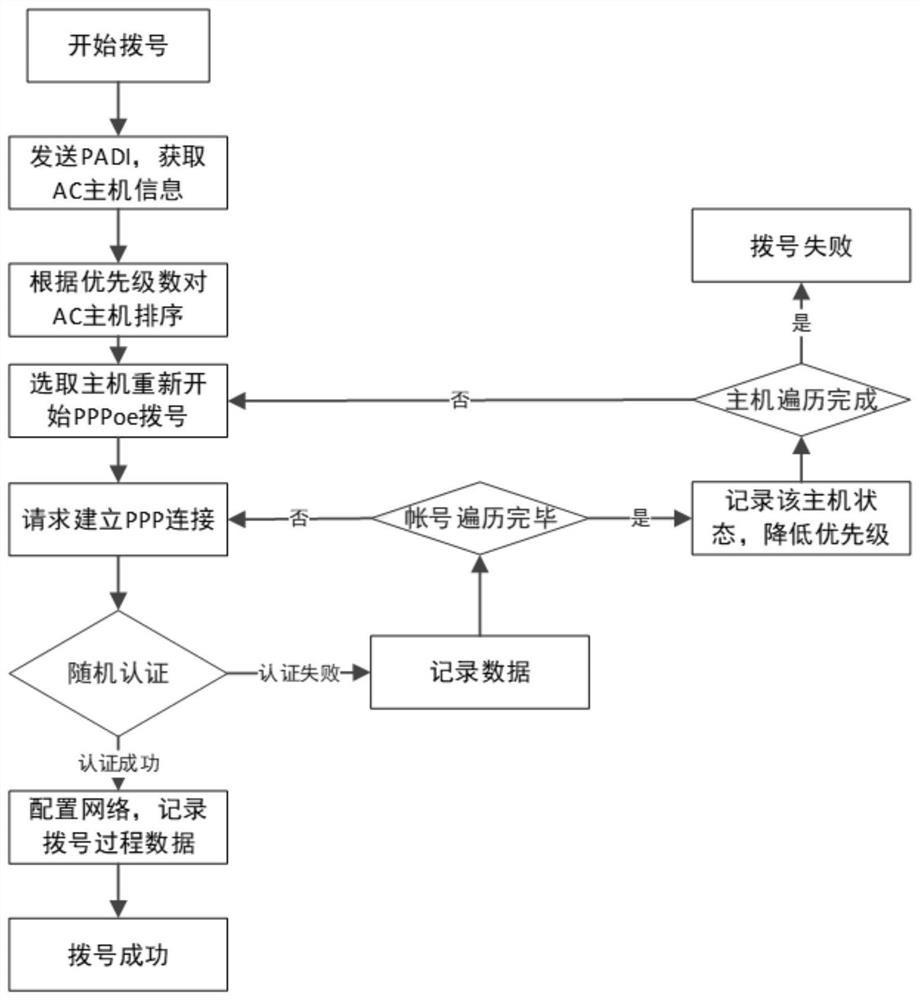
PPPoE dialing method
ActiveCN114338218AIncrease the difficultyIncrease attack costSecuring communicationPasswordEngineering
The invention discloses a PPPoE (Point-to-Point Protocol over Ethernet) dialing method. The method comprises the following steps: selecting an AC (Access Controller) server with the highest priority for dialing; a client starts to establish a data communication link, a plurality of disguised account passwords are produced on the basis of a real account password when the client dials, the disguised account passwords are firstly used for authentication, and the real account password participates in authentication in a certain random process; according to the invention, PPPoE dialing is carried out by using the disguised account password, the network environment is detected, the protection of the account password is enhanced, and the difficulty of acquiring the real account password by an attacker is increased.
Owner:SICHUAN JIUZHOU ELECTRONICS TECH
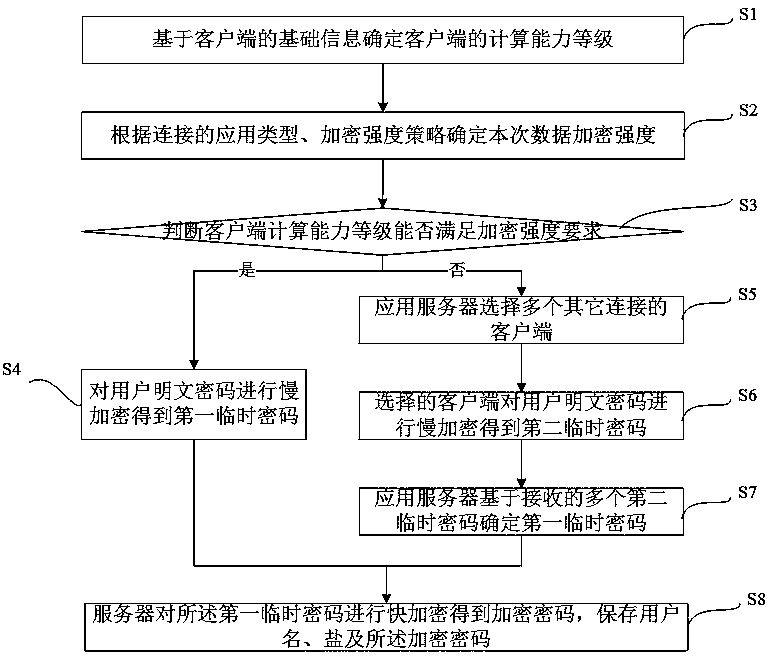
Big data network data protection method and system based on edge computing
ActiveCN111371813AAvoid computational processing overhead issuesAvoid excessive performance degradationUser identity/authority verificationApplication serverEdge computing
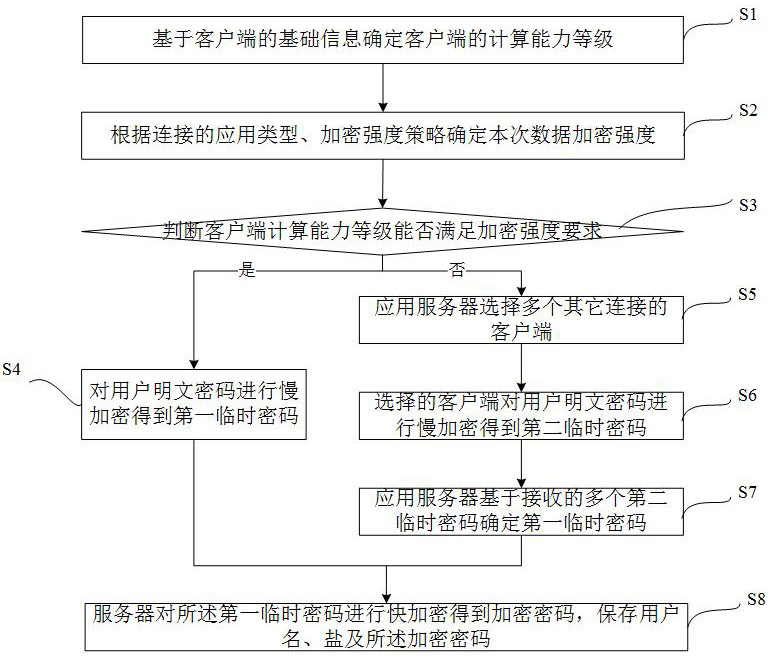
The invention discloses a big data network data protection method and system based on edge computing. The big data network data protection method comprises the steps of S1, determining a computing power level of a client; S2, determining the data encryption strength of this time; S3, judging whether the computing power level of the client can meet the encryption strength requirement or not, if yes, executing the step S4, and if not, executing the step S5; S4, slowly encrypting the plaintext password to obtain a first temporary password, and executing the step S8; S5, the application server selects a plurality of other connected clients, and sends the plaintext password, the salt and the encryption strength to the selected client; S6, slowly encrypting the plaintext password by the selectedclient to obtain a second temporary password; S7, the application server determines a first temporary password based on the plurality of received second temporary passwords; and S8, the server quickly encrypts the first temporary password to obtain an encrypted password, and stores the user name, the salt and the encrypted password. Effective balance between safety protection and calculation performance is achieved, and data safety is high.
Owner:杭州灿八科技有限公司
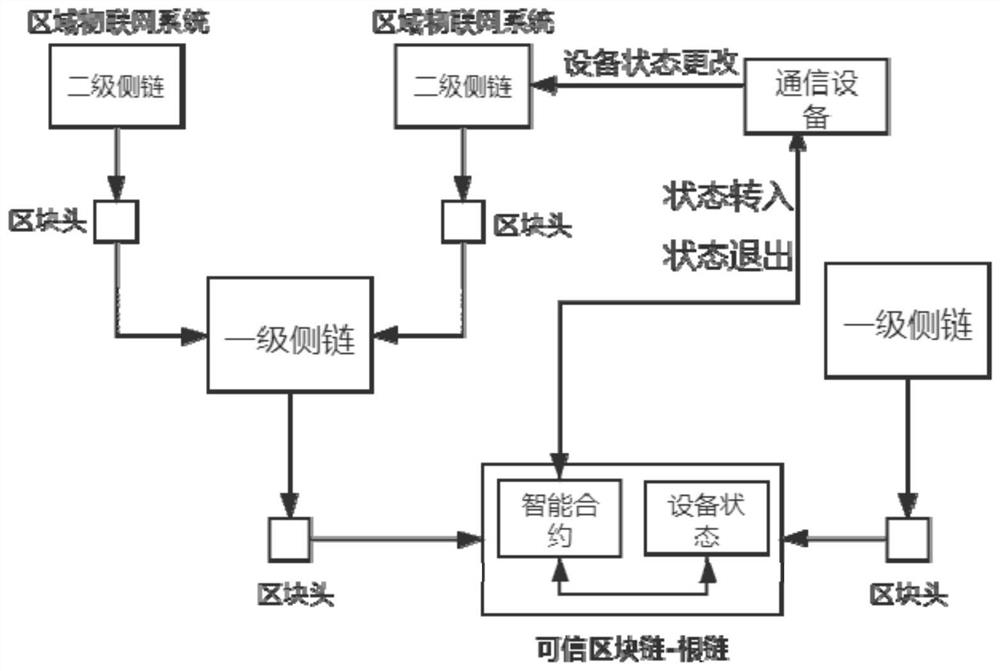
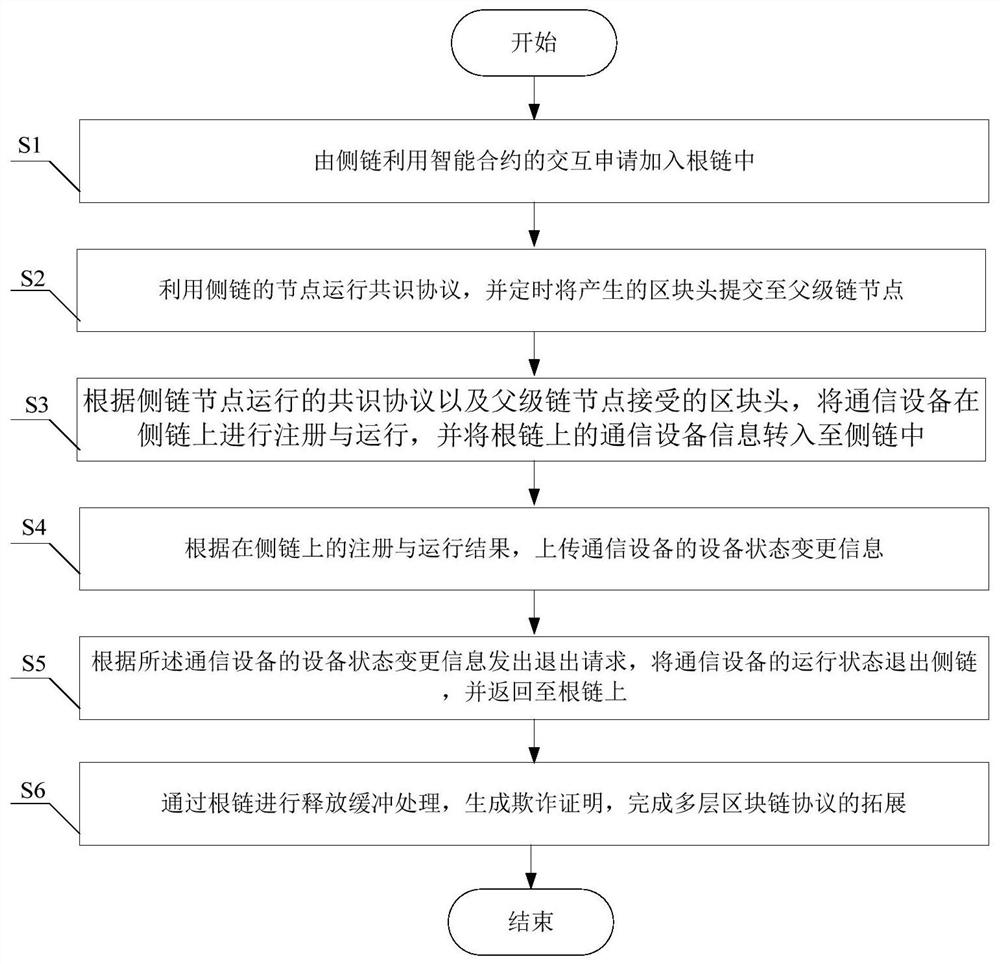
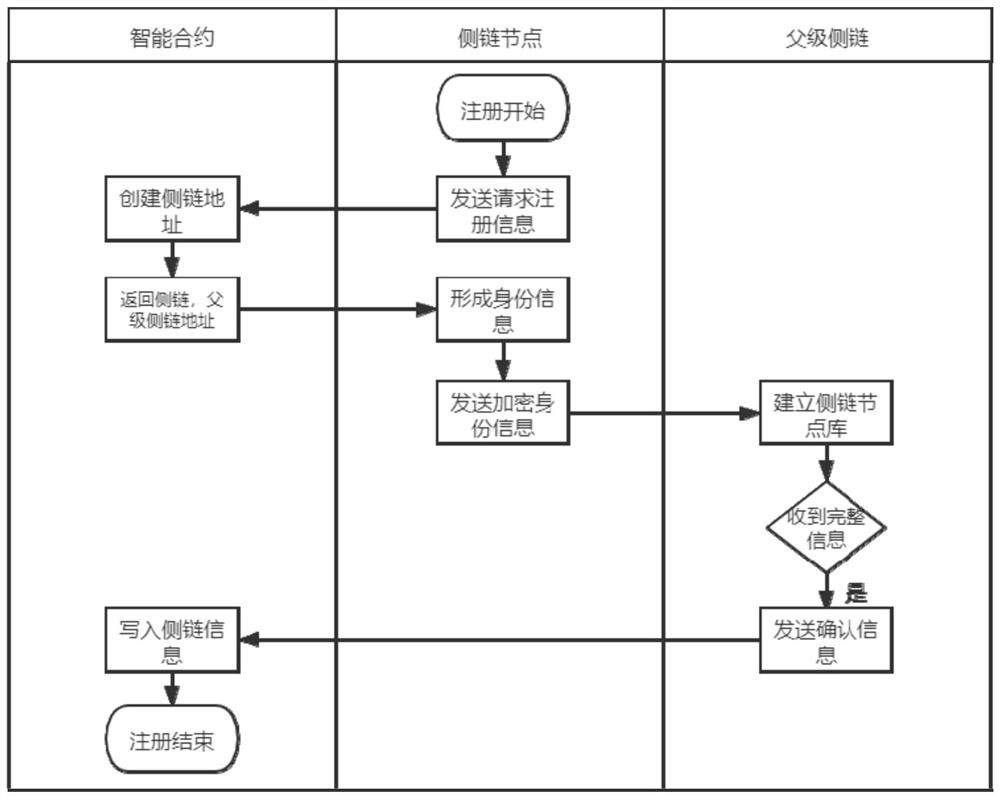
Multi-layer blockchain protocol expansion system and method based on communication-device-oriented system
The invention provides a multi-layer blockchain protocol expansion system and method based on a communication-device-oriented system, belongs to the technical field of blockchains. The system comprises a root blockchain, a plurality of side blockchains constructed on the root blockchain in a tree structure, and communication devices respectively connected with the root blockchain and the side blockchains. The invention aims to solve the problems that a blockchain expansion technology based on a trusted root blockchain is used for establishing a multi-layer blockchain expansion protocol oriented to the Internet of Things, and under the condition of ensuring the record security of communication equipment, the record change speed of the communication equipment on the root blockchain and the flexibility, autonomy and availability of the record change of the communication equipment are greatly expanded.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA +1
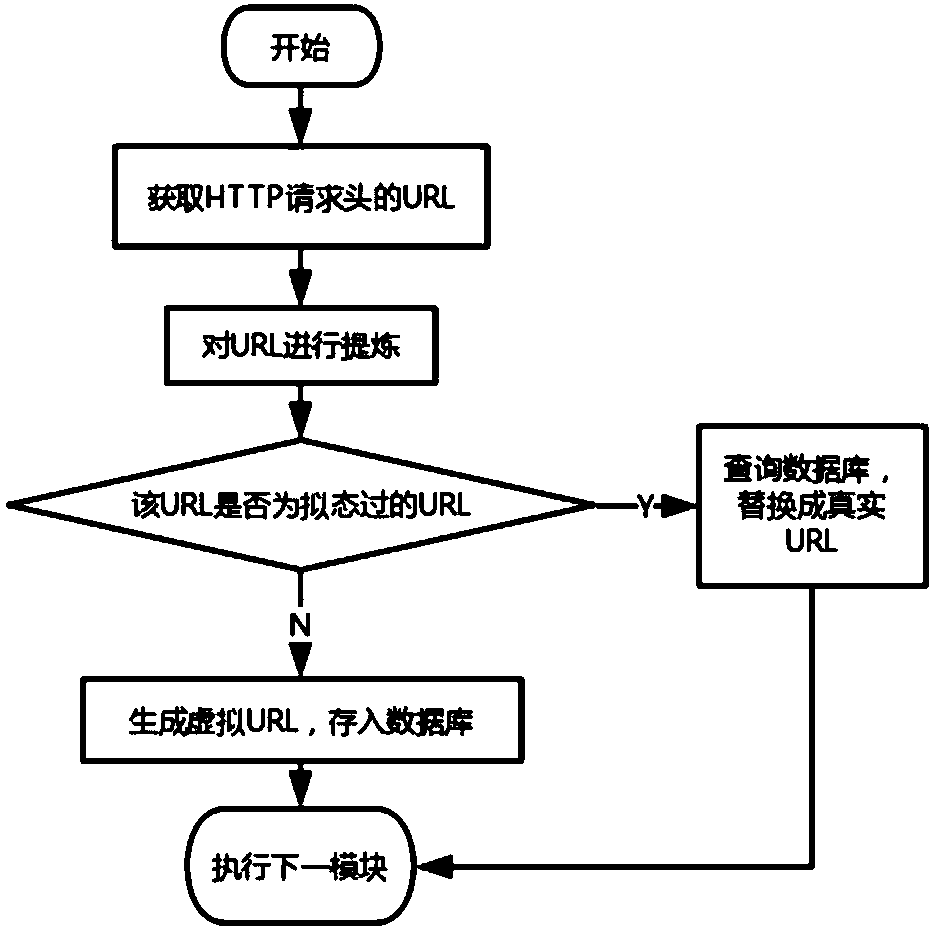
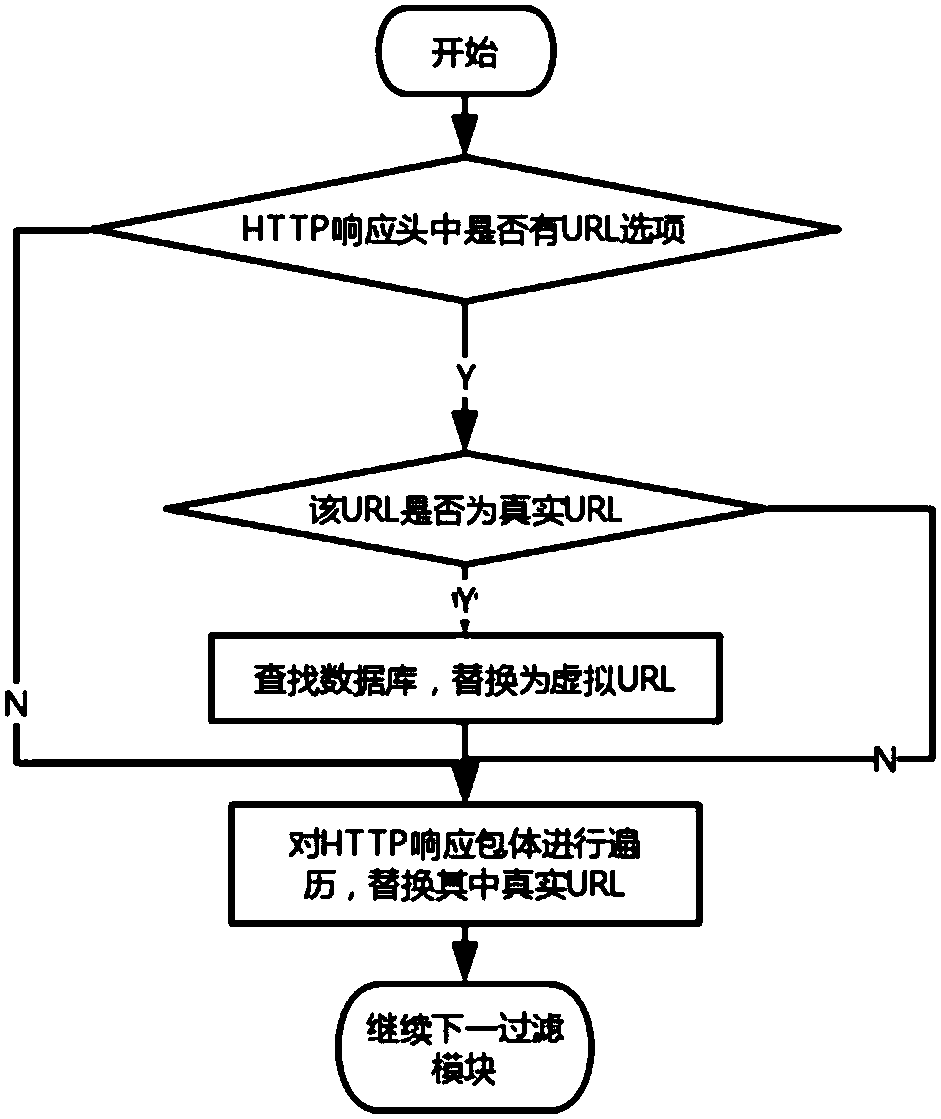
URL virtualization dynamic defense method for automatic attacks
InactiveCN109561102AIncrease the difficultyIncrease attack costTransmissionVirtualizationClient-side
The invention discloses a URL virtualization dynamic defense method for automatic attacks, which realizes the dynamic change of URL virtualization and thus solves the problems of unknown attacks and unknown threats in the network. The method comprises a client request processing step and a server response processing step which respectively process an HTTP message received from a client and an HTTPmessage transmitted from a server to the client. Under the premise of functional equivalence, URLs are enabled to dynamically change in a defender controllable manner and manifested to be dynamicallychanging targets which are difficult to be observed and predicted for attackers, thereby increasing the difficulty and cost of attacks against unknown vulnerabilities and backdoors.
Owner:国网思极网安科技(北京)有限公司 +5
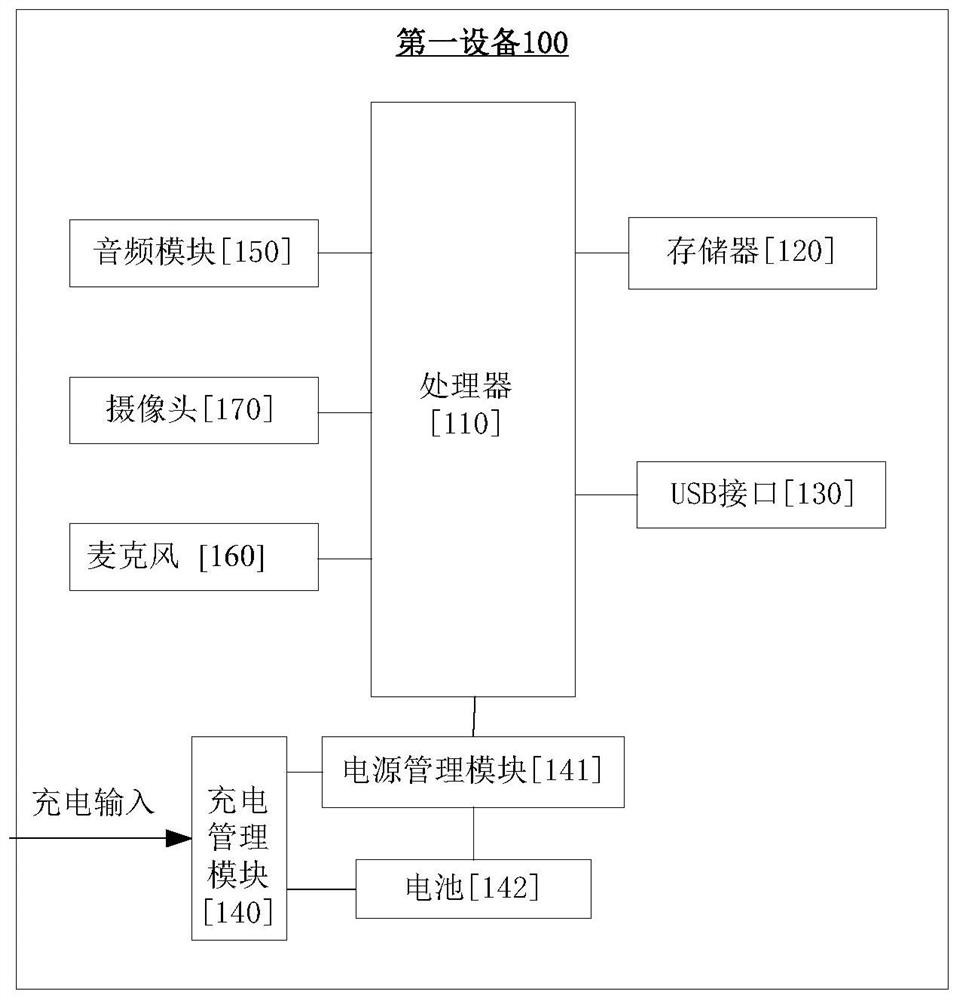
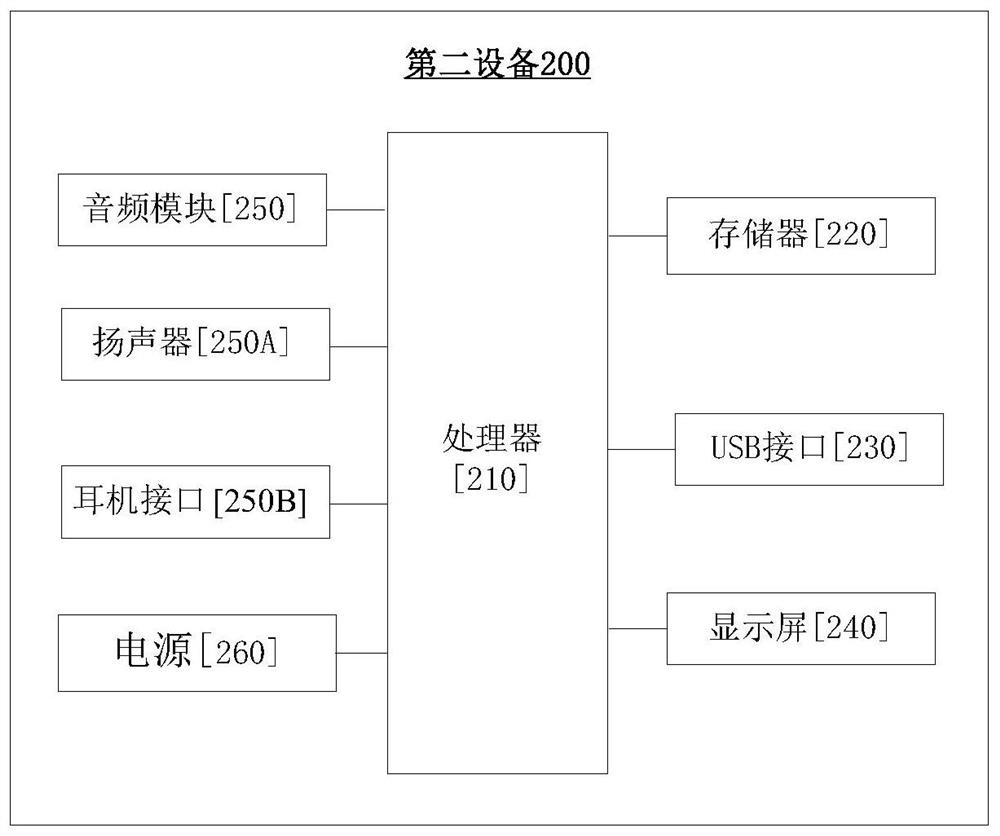
Method for establishing network connection and electronic equipment
InactiveCN112448935AGuaranteed reliabilityImprove securityKey distribution for secure communicationTelecommunicationsNetwork connection
The invention relates to the technical field of communication, and discloses a method for establishing network connection and electronic equipment. The method for establishing the network connection comprises the following steps: after first equipment and second equipment establish a data channel, periodically updating a session key, and sending the first session key to the second equipment through the data channel. Then the first equipment and the second equipment establish a first network channel. And then, under the condition that the second session key is received through the first networkchannel within the first preset duration and the second session key is the same as the first session key, the first equipment sends response information to the second equipment through the first network channel. It can be seen that the first equipment periodically updates the session key, and the reliability of the session key can be ensured. Accordingly, the first equipment authenticates the network channel by detecting whether the session key transmitted by the network channel is the same as the pre-generated session key so that the security of a mechanism for establishing the network channel can be improved.
Owner:HUAWEI TECH CO LTD
APT heuristic detection method and system based on abnormal component association
InactiveCN108073809AIncrease attack costReduce concealmentPlatform integrity maintainanceSoftware engineeringMatch rule
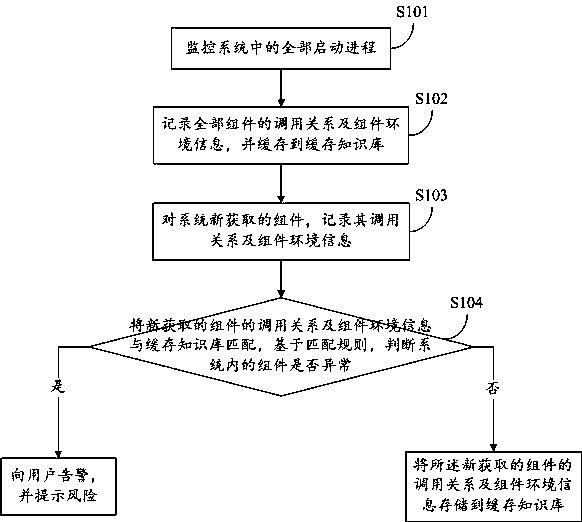
The invention provides an APT heuristic detection method and system based on abnormal component association. The method includes the steps of monitoring all startup processes in the system; recordingcall relations and component environment information of all components and buffering the call relations and the component environment information into a cache knowledge base; recording call relationsand component environment information of components newly acquired by the system; matching the call relations and the component environment information of the newly-acquired components with the cacheknowledge base, and determining whether the components in the system are abnormal based on matching rules; if yes, making an alarm to users and performing risk prompting, or else storing the call relations and the component environment information of the newly-acquired components into the cache knowledge base. The invention further provides a corresponding system and a storage medium. Through themethod, detect modularization, engineering, high concealment and complex APT attacks can be effectively detected.
Owner:HARBIN ANTIY TECH
Method and device for optimizing embedding parameters of anti-copy two-dimensional code
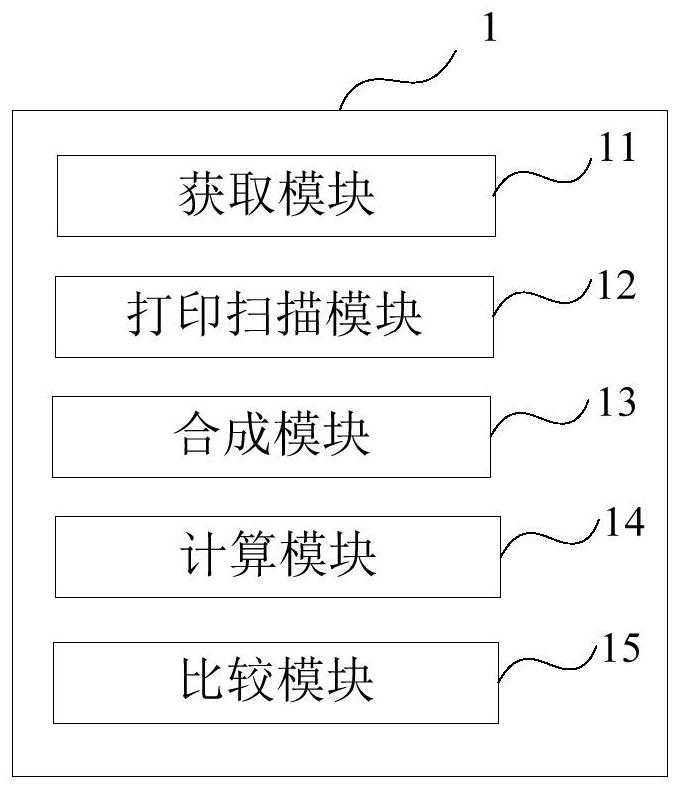
ActiveCN109829529BOptimizing Embedding ParametersIncrease attack costRecord carriers used with machinesAlgorithmTheoretical computer science
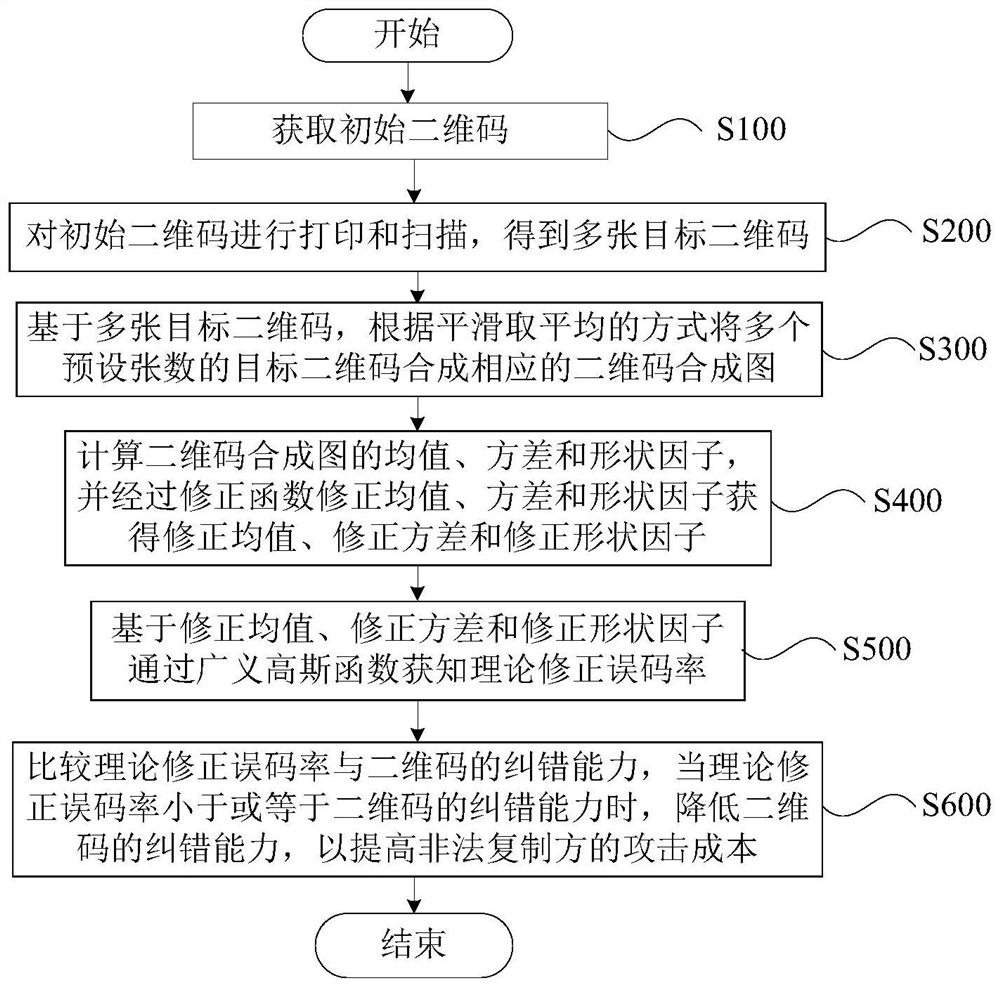
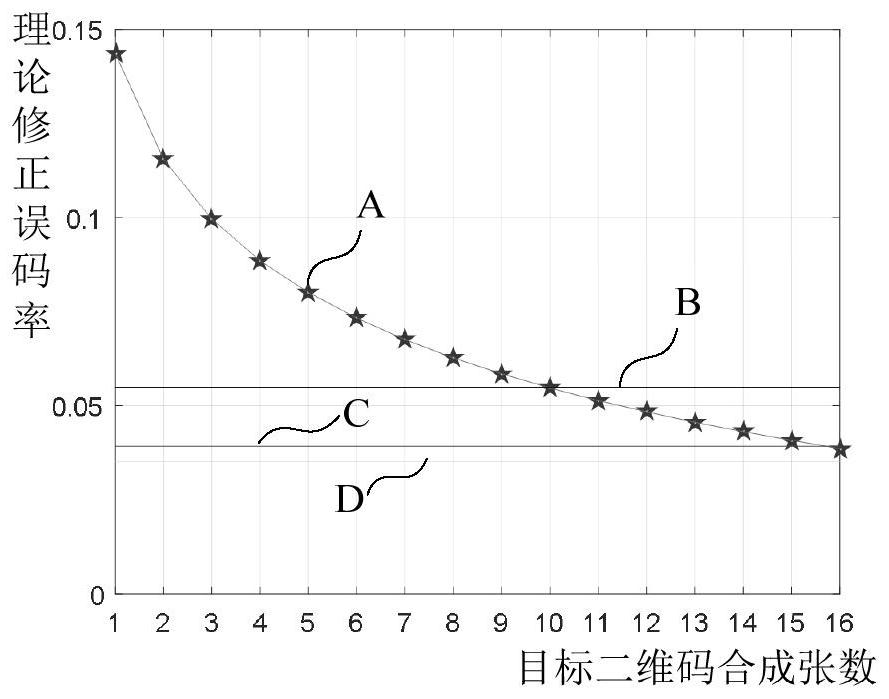
The present disclosure describes an optimization method for embedding parameters of an anti-copy two-dimensional code, which is characterized in that it includes: obtaining an initial two-dimensional code; printing and scanning the initial two-dimensional code to obtain multiple target two-dimensional codes; A target two-dimensional code, according to the method of smoothing and averaging, synthesize multiple target two-dimensional codes with a preset number of target two-dimensional codes into a corresponding two-dimensional code composite graph; calculate the mean value, variance and shape factor of the two-dimensional code composite graph, and correct them The corrected mean, corrected variance and corrected shape factor are obtained by modifying the mean, variance and shape factor of the function; the theoretical corrected bit error rate is obtained through the generalized Gaussian function based on the corrected mean, corrected variance and corrected shape factor; and the theoretical corrected bit error rate is compared with the two-dimensional The error correction ability of the code, when the theoretical corrected bit error rate is less than or equal to the error correction ability of the two-dimensional code, the error correction ability of the two-dimensional code is reduced to increase the attack cost of the illegal copying party.
Owner:SHENZHEN UNIV
A virtualization packing method based on elf infection android local layer instruction compilation
InactiveCN107480476BIncrease attack costProtection complexityProgram/content distribution protectionVirtualizationSoftware engineering
The invention discloses a method of compiling and virtualizing Android local layer instructions based on ELF infection. This method performs Hex extraction and mapping virtualization on the so file to be protected to form a virtual machine so file, and performs key code segments on the so file. Encrypt to form an encrypted so file; use the virtual machine so file to perform ELF infection on the encrypted so file to form an infected so file; use the Cydia Substrate framework to replace the encrypted so file with Hook, so that the virtual machine so file The virtual instruction code replaces the encrypted code in the encrypted so file. The present invention uses the idea of compile-time virtualization. This idea does not involve the problem of different ARM platform versions, so it has good compatibility, can prevent memory dump analysis and increases the attacker's attack cost.
Owner:NORTHWEST UNIV
Financial transaction system authentication method based on OCR identification
PendingCN112633271AEasy loginReduce entry costsFinanceCharacter and pattern recognitionText recognitionEngineering
The invention discloses a financial transaction system authentication method based on OCR identification, which comprises the following steps: acquiring picture information data of a user through an input interface and a calling recognition interface, and recognizing and reading the data by utilizing an OCR technology and combining a set algorithm; carrying out information identification, identifying the type of the user picture information data, carrying out authenticity check, and verifying whether the dynamic verification code is consistent with the displayed dynamic verification code or not; after the identification is successful, performing data check and field value integration, so that the data can be modified or filled by a user; after the field data is integrated, performing authority distribution and data processing of the user according to the output data, and triggering interaction of a transaction page. The user information identification login is performed by calling the OCR identification interface to perform image character identification of the user information and perform information verification and storage, so that the information input cost is reduced, the user authentication security mechanism is verified, the security risk is avoided, the input is accurate, the data correctness is ensured, and flexible configuration can be performed according to the system requirements.
Owner:中企云链(北京)金融信息服务有限公司
A restaurant recommendation algorithm based on score and feature similarity in social networks
ActiveCN104850579BIncrease attack costImprove resistance to attackData processing applicationsSpecial data processing applicationsRankingDegree of similarity
The invention discloses a restaurant recommendation algorithm based on rating and feature similarity in a social network, which mainly includes the following steps: 1) establishing a user rating database in the current social network; 2) calculating the rating similarity between Ua and other users in the user rating database ; 3) Select the k users with the highest rating similarity with Ua to obtain a set of recommended users with similar ratings; 4) Construct a feature similarity model M=(χa, i, δa, i, σa, i, γa, i); 5) Calculate the feature similarity recommendation degree and recommend the top-ranked items to the target users. In the present invention, the feature similarity between users is used as the second basis for the recommendation algorithm in addition to the conventional scoring similarity, and the calculation of various user features not only greatly increases the attack cost, but also greatly improves the anti-attack ability, and Improve the accuracy of recommendation.
Owner:NANJING UNIV OF POSTS & TELECOMM
Verification method, device and storage medium
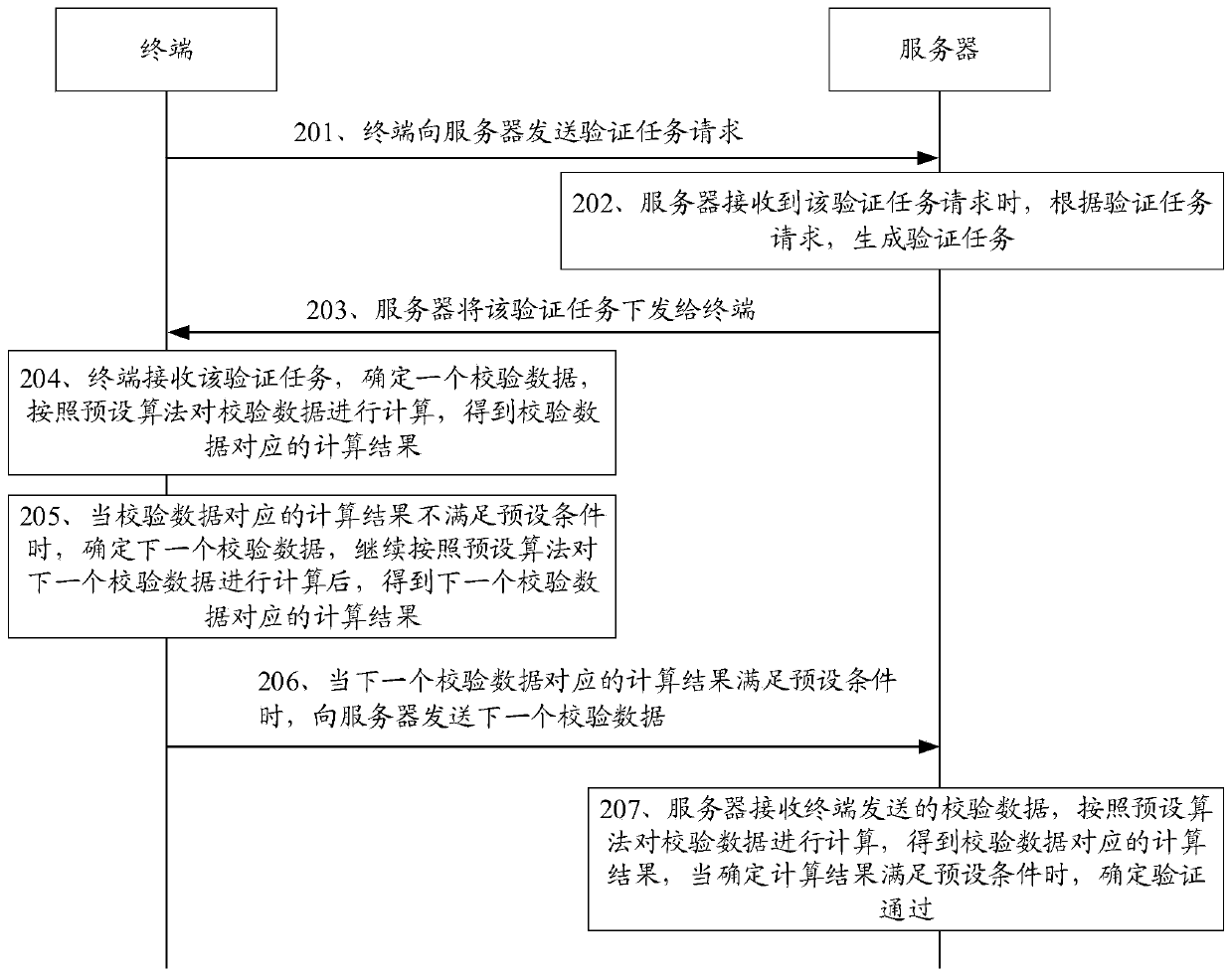
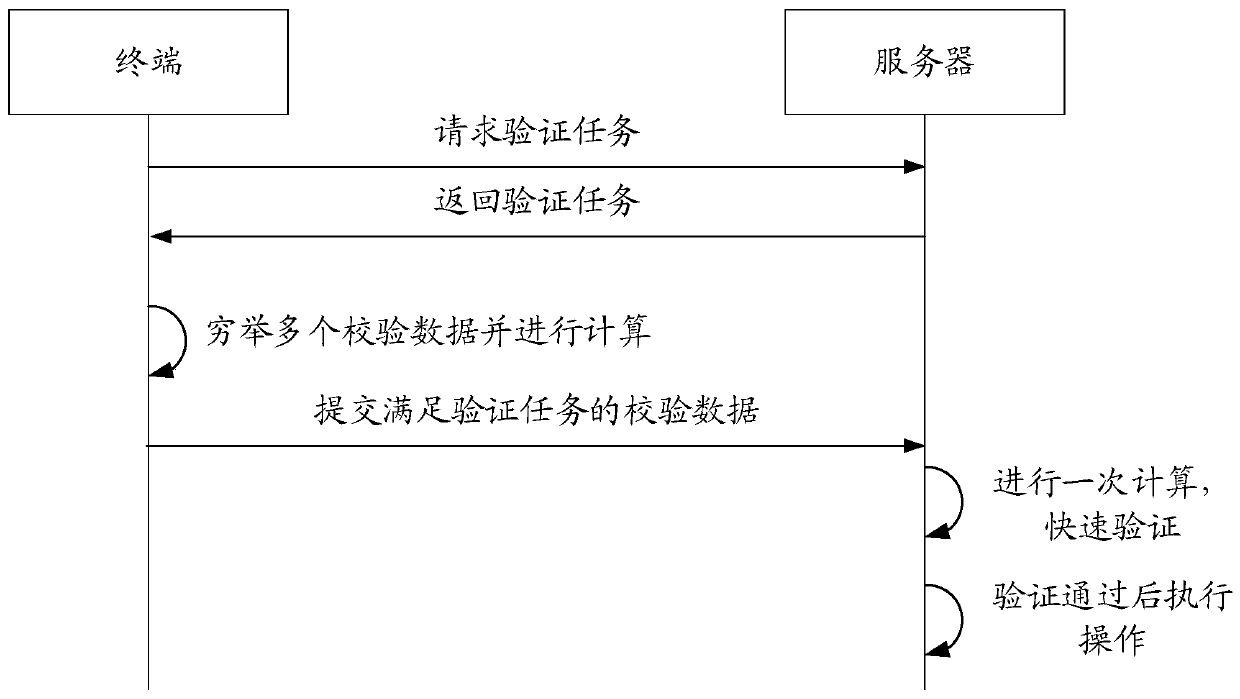
The embodiment of the invention discloses a verification method and device and a storage medium, and belongs to the field of information security. The method comprises the steps of obtaining a verification task, wherein the verification task comprises a preset algorithm and a preset condition; Determining at least one piece of verification data, and calculating the determined verification data according to a preset algorithm to obtain a calculation result corresponding to the determined verification data; And when a calculation result corresponding to the currently determined check data satisfies a preset condition, sending the currently determined check data to a server, calculating the currently determined check data by the server according to a preset algorithm; and when the calculationresult obtained by calculation satisfies the preset condition, determining that the verification is passed. According to the embodiment of the invention, under the condition that the security is ensured, the server only needs to calculate the verification data which are sent by the terminal and meet the verification task, and the verification data which do not meet the verification task do not need to be calculated, so that the workload of the server is reduced, and the working pressure of the server is reduced.
Owner:TENCENT TECH (SHENZHEN) CO LTD +1
A big data network data protection method and system based on edge computing
ActiveCN111371813BAvoid computational processing overhead issuesAvoid excessive performance degradationUser identity/authority verificationPlaintextApplication server
The invention discloses a big data network data protection method and system based on edge computing, including: S1, determining the computing power level of the client; S2, determining the data encryption strength; S3, judging whether the computing power level of the client can meet Encryption strength requirements, if yes, execute step S4, if not, execute step S5; S4, slowly encrypt the plaintext password to obtain the first temporary password, execute step S8; S5, the application server selects multiple other connected clients, and sends the plaintext The password, salt, and encryption strength are sent to the selected client; S6, the selected client slowly encrypts the plaintext password to obtain the second temporary password; S7, the application server determines the first temporary password based on the received multiple second temporary passwords; S8. The server fast-encrypts the first temporary password to obtain an encrypted password, and saves the user name, salt, and the encrypted password. The invention realizes an effective balance between security protection and computing performance, and has high data security.
Owner:杭州灿八科技有限公司
Executor Scheduling Method Oriented to Mimetic Construction Web Server
ActiveCN110855692BImprove defenseQuality assuranceMathematical modelsInference methodsQos quality of serviceOptimal scheduling
The present invention discloses an execution body scheduling method oriented to a web server with a mimic structure, comprising: step 1, generating a candidate execution body set, randomly selecting m execution bodies, and calculating the average value of the vulnerability value and the standard deviation of the vulnerability value of each layer of software stack , to screen n executives within the threshold range of the vulnerability value; step 2, randomly select two QoS parameters, and calculate the QoS parameter value; step 3, map the Bayesian-Stackelberg game model to the mimic structure On the web server of , construct the objective function for solving the optimal scheduling strategy; step 4, bring two QoS parameter values into the objective function, and obtain k execution bodies with the best QoS parameter values; step 5, generate random number r , if r≥ε, then dynamically schedule the heterogeneous executables of the mimic web server according to the k executables. The invention has the beneficial effects of increasing confusion and improving defense ability while ensuring the service quality of the Web server.
Owner:北京网聘信息技术有限公司
Sequence attack detection implementation method based on industrial firewall
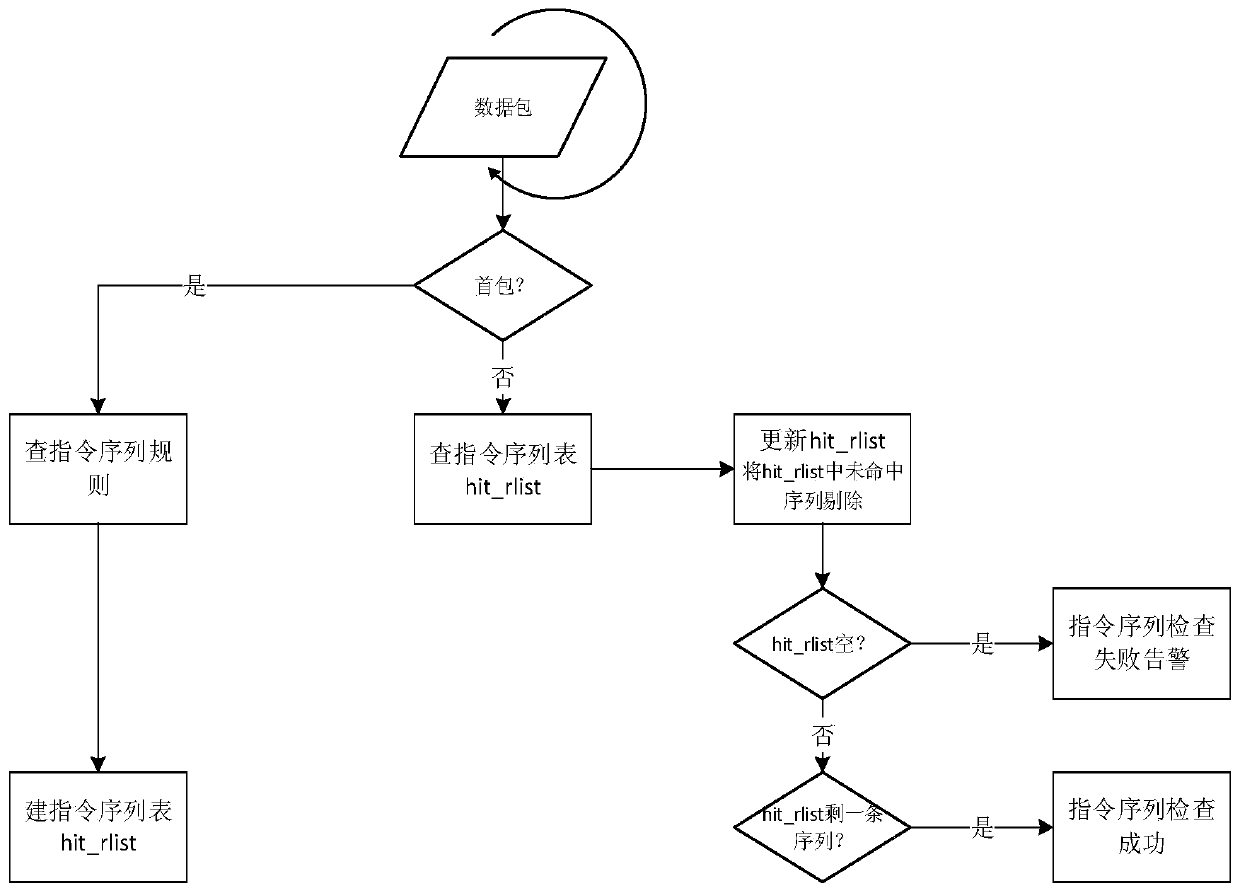
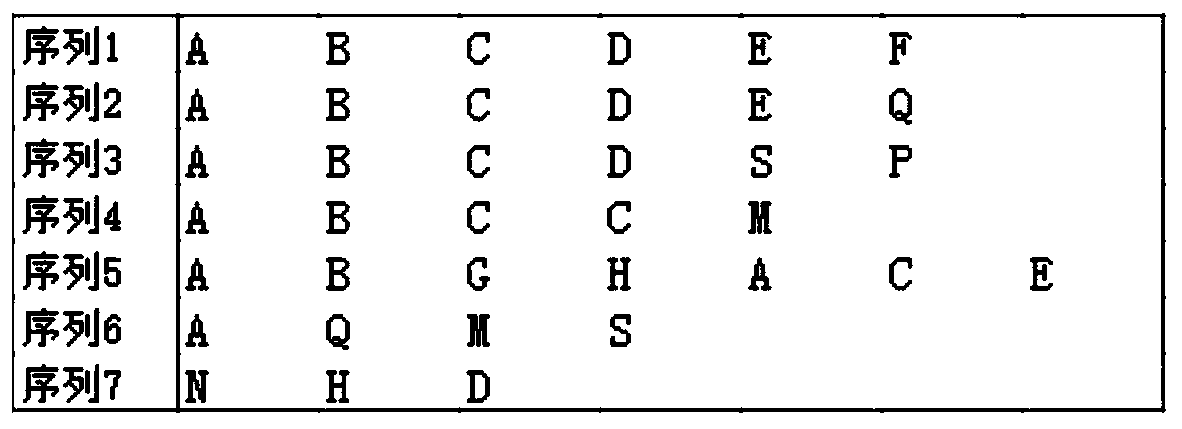
InactiveCN111245780AReduce downtimeIncrease attack costTransmissionInstruction sequenceIndustrial control system
The invention discloses a sequence attack detection implementation method based on an industrial firewall. The method comprises: a first instruction arrives, establishing an instruction sequence table, a next instruction arriving, checking the instruction sequence table, refreshing the instruction sequence table according to the hit situation, and subsequent instructions arriving until the instruction sequence table is empty or one instruction sequence remains. The method has the advantages that increasingly accurate targeted attacks can be dealt with, the attack cost is remarkably improved, and shutdown of an industrial control system is reduced. The sequence attack detection method is realized, and any sequence of illegal instructions are intercepted and warned, so that all instructionswith a sequence relationship in the industrial control system are normally operated in an ordered and legal state, and the possible harm of the industrial control system due to sequence attack or misoperation of a user is eliminated.
Owner:北京威努特技术有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com