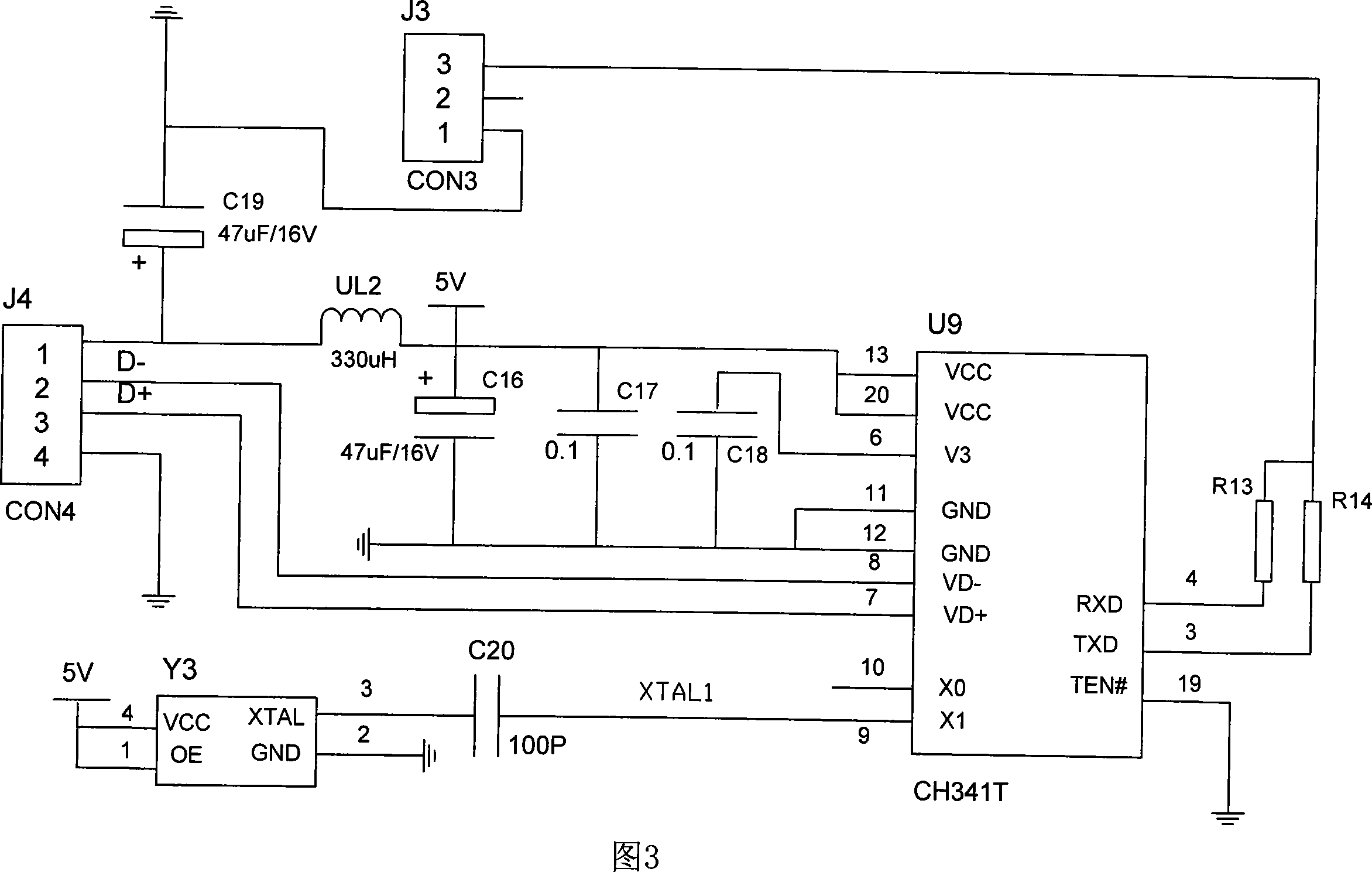
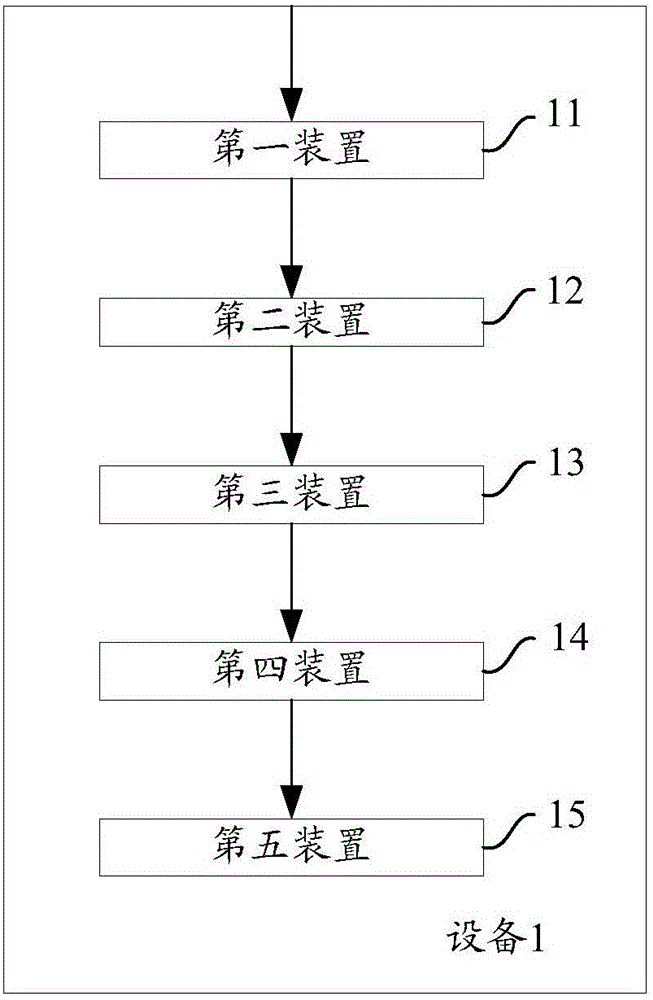
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
87results about How to "Implement rights management" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Kubernetes-based container management platform
ActiveCN108108223ARealize managementImplement rights managementResource allocationSoftware simulation/interpretation/emulationButt jointComputer science
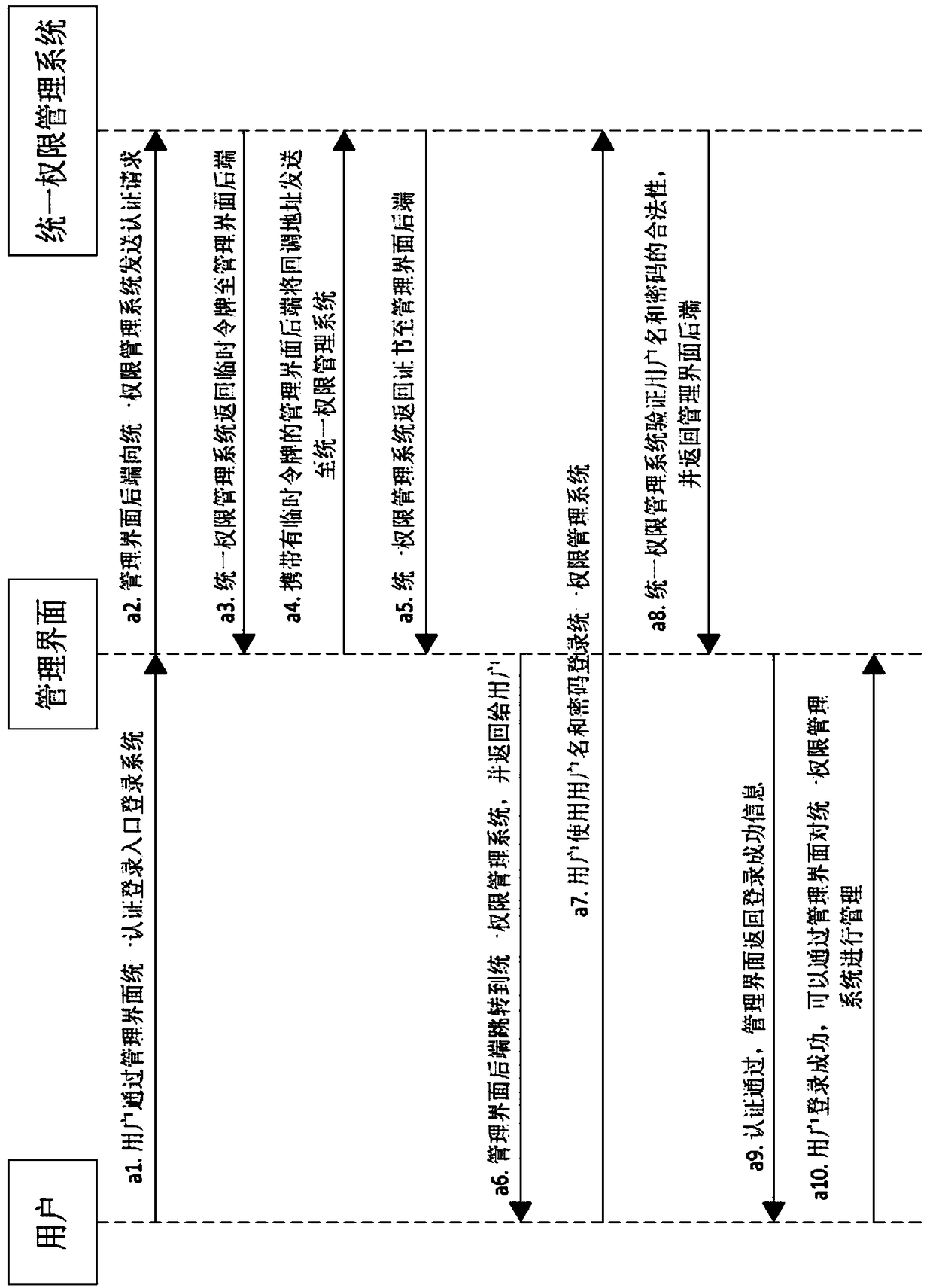
The invention discloses a Kubernetes-based container management platform. The platform comprises a management interface and a container cloud platform, wherein the management interface is used for carrying out operations and is in butt joint with a uniform authority management system on the basis of an Oauth2.0 protocol so as to ensure that users can access and manage the uniform authority management system through the management interface; and the container cloud platform is used for deploying a Kubernetes cluster under an Aliyun environment so as to ensure that the users can access resourcesof the Kubernetes cluster through the management interface. According to the platform, bottom Aliyun resources and container resources can be managed through a uniform platform, and through connection between the platform and the uniform authority management system, user information can be managed.
Owner:STATE GRID ZHEJIANG ELECTRIC POWER +2
Electronic lock management system
ActiveCN101216959AReduce volumeSimple key circuitIndividual entry/exit registersPrimary stationDatabase server
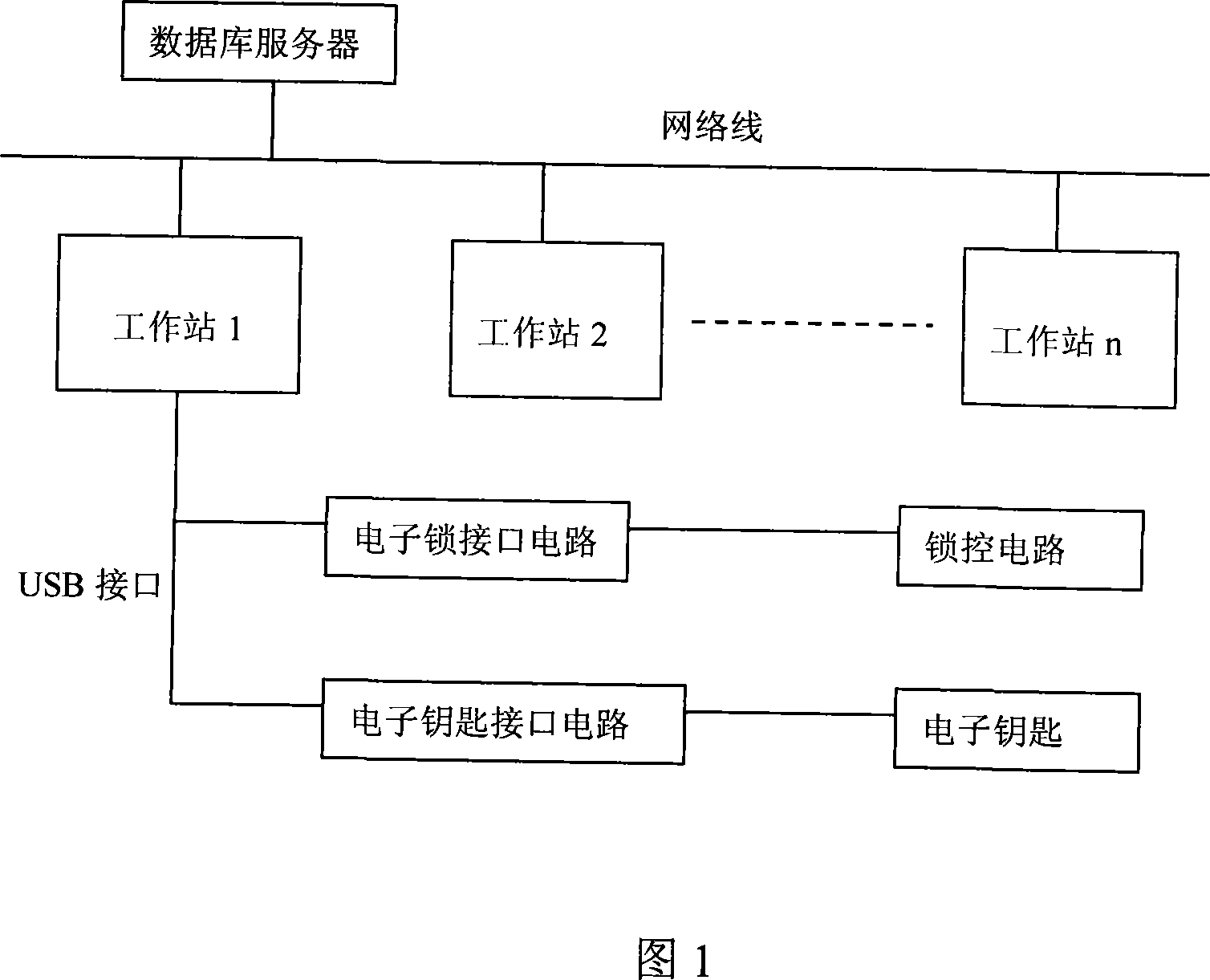
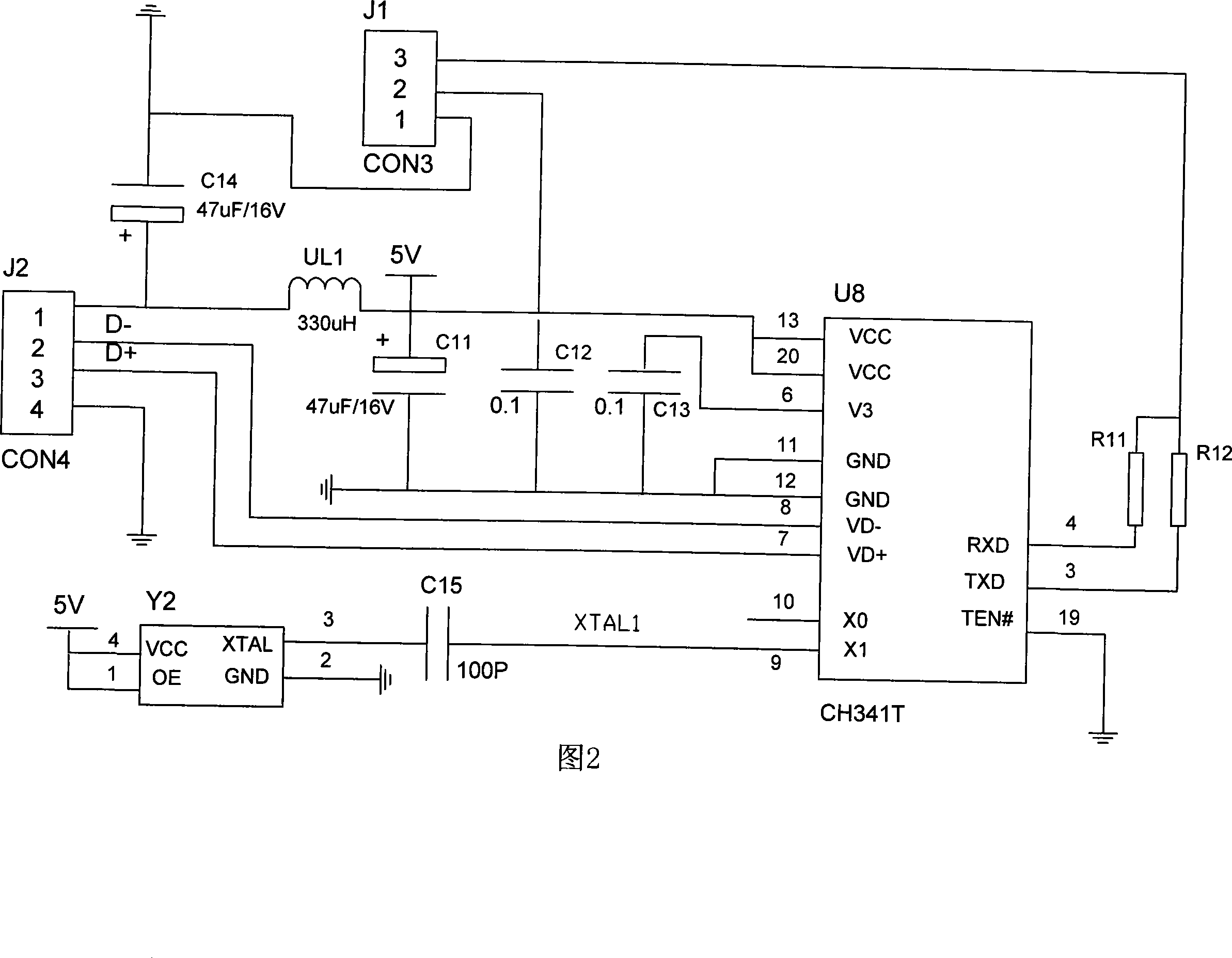
An electronic lock management system is characterized in that a main station system includes a database server and a set of network workstations; the database server is used for recording an unlocking process, storing unlocking authority of an electronic key and organization and personal information of a management department, and depositing parameters of the electronic lock and the electronic key; the database server and the set of network workstations constitute a network system; system management software is disposed in the network workstations, and provides management of an organizational structure, electronic lock initialization setting, electronic key initialization setting, electronic key authority management, and electronic key unlocking process management; and the network workstations are used for reading information in the electronic key for the electronic lock or downloading information into the electronic lock and the electronic key. The inventive system can satisfy management of electronic key unlocking process, and has the advantages of no need of electronic lock networking, low system cost and low power consumption.
Owner:HUAINAN POWER SUPPLY CO OF STATE GRID ANHUI ELECTRIC POWER CORPORATIO +1
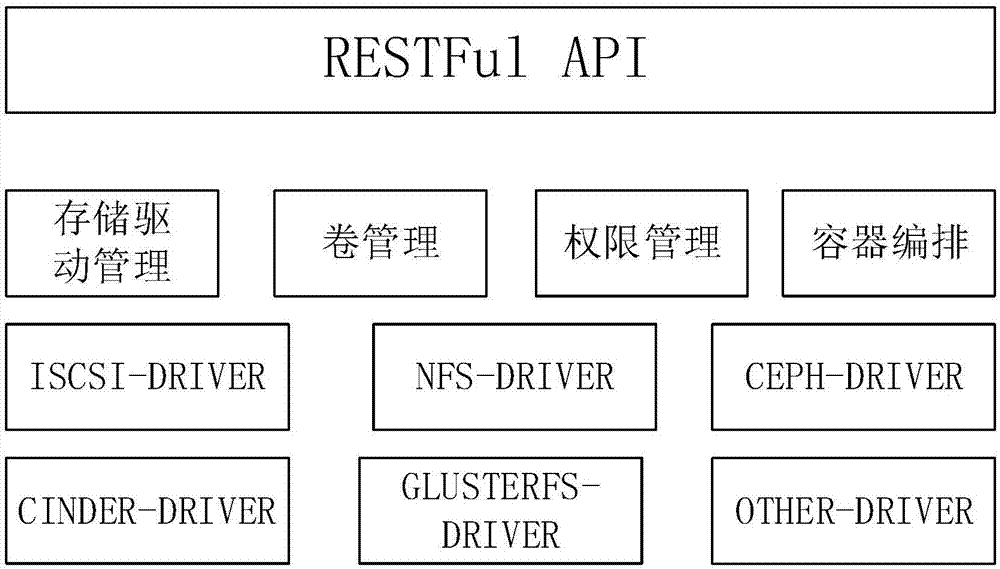
Container technology-based memory access method and system
InactiveCN107301022AUnified connectivityUnified accessInput/output to record carriersTransmissionContainerizationAccess method
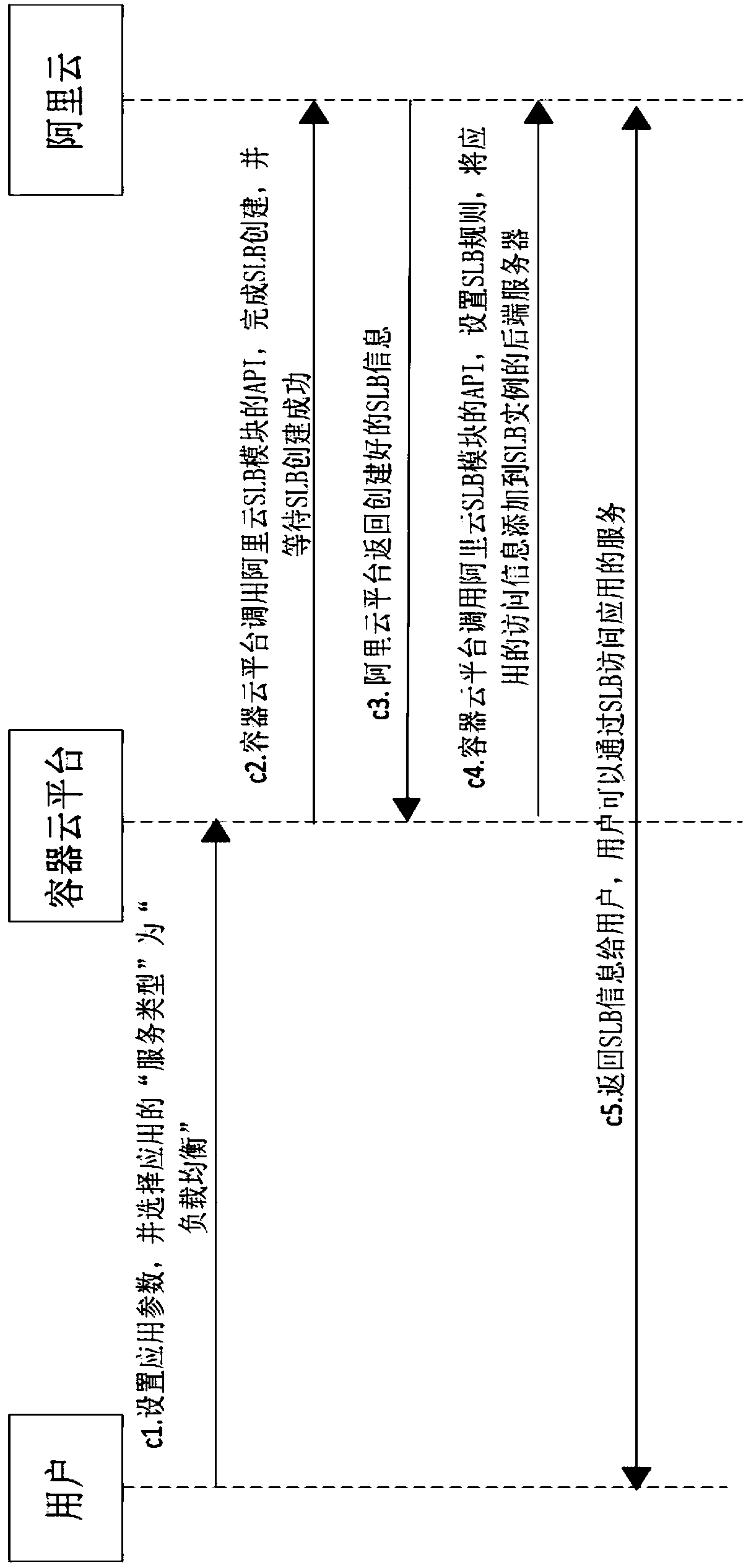
Embodiments of the invention relate to the field of cloud storage, in particular to a container technology-based memory access method and system. The system comprises a volume management module, a memory drive management module, an authority management module and a container arrangement module; wherein the volume management module is used for sending a volume creation request by a user through an interface or an API so as to realize the creation of different types of volumes, and managing the created volumes; the memory drive management module is used for receiving the volume creation request sent by the volume management module; the authority management module is used for calling an interface of Keystone so as to realize the authentication and authority management of the user; the container arrangement module is used for operating each memory drive at a corresponding calculation node in a container manner; the memory drives provide configuration files aiming at different arrangement frames; and the arrangement module calls APIs of the arrangement frames to realize the containerization and scheduling of each memory drive. According to the method and system, the high availability and load balance of each memory drive are realized.
Owner:北京溢思得瑞智能科技研究院有限公司 +1
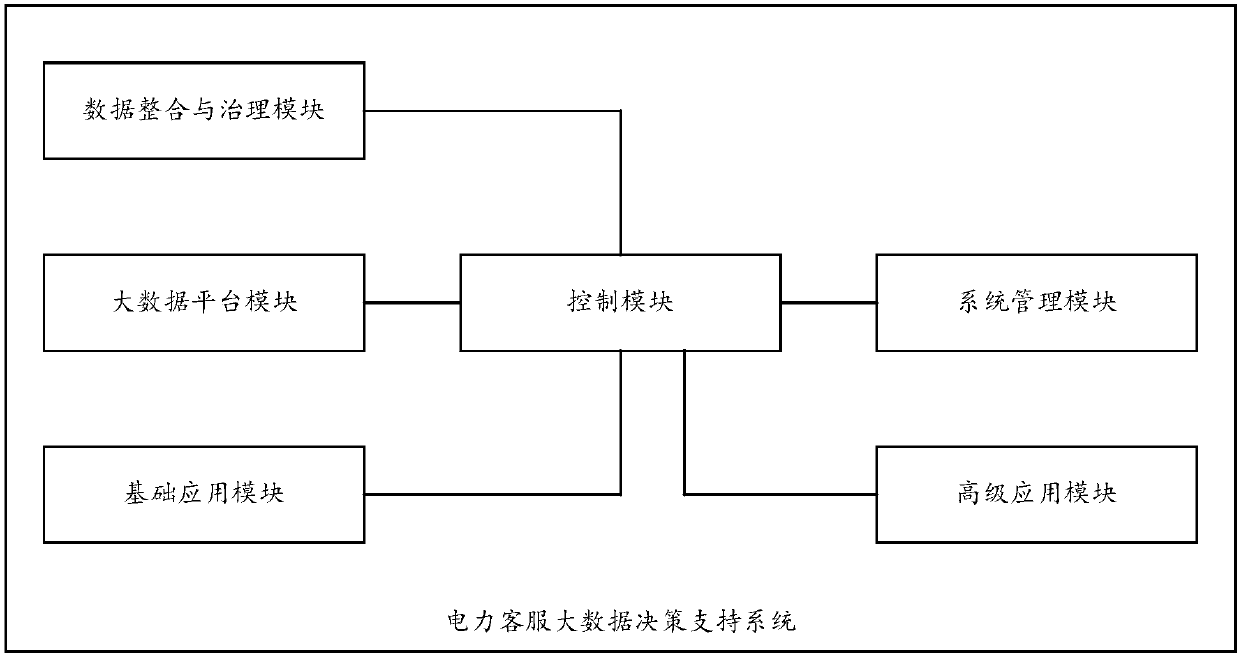
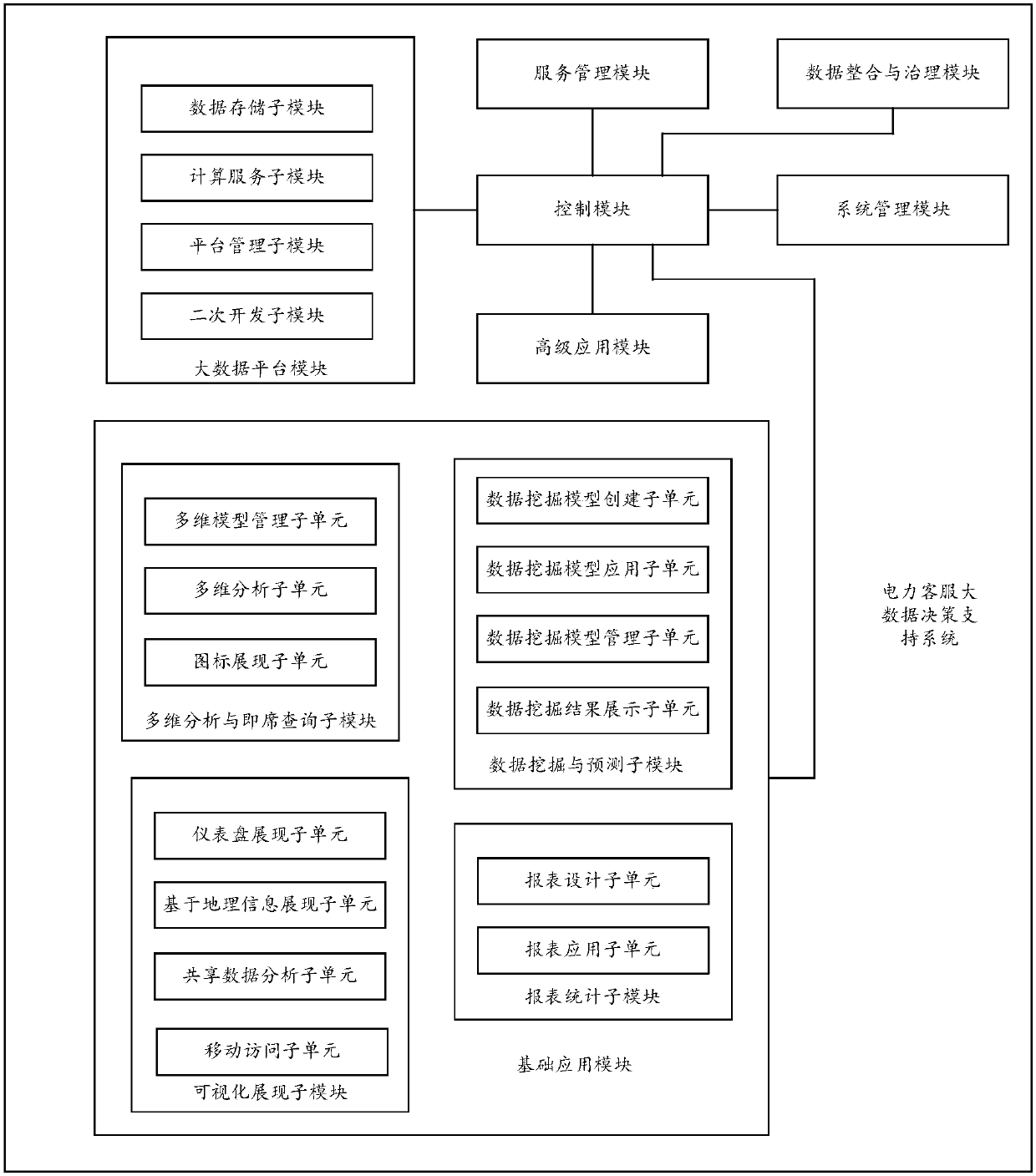
Electric power customer service big data decision support system
InactiveCN110163621ARealize the statistical report functionRealize functionCustomer relationshipSpecial data processing applicationsInformatizationData platform
The invention discloses an electric power customer service big data decision support system. The system comprises a control module, a big data platform module, a data integration and treatment module,a basic application module, a high-level application module and a system management module, and the control module is used for controlling the big data platform module, the data integration and treatment module, the basic application module, the high-level application module and the system management module to execute corresponding operation. Therefore, by implementing the embodiment of the invention, the electricity utilization rule and market behavior of a client can be discovered in vast quantities of power distribution and utilization data; and related business requirements of all-aroundcustomer service system support, fine decision of power grid operation, expansion of emerging business and reform support of the power market are met by combining power marketing management requirements, enterprise informatization management requirements and driving of power reform and new form of the power market.
Owner:GUANGZHOU POWER SUPPLY CO LTD
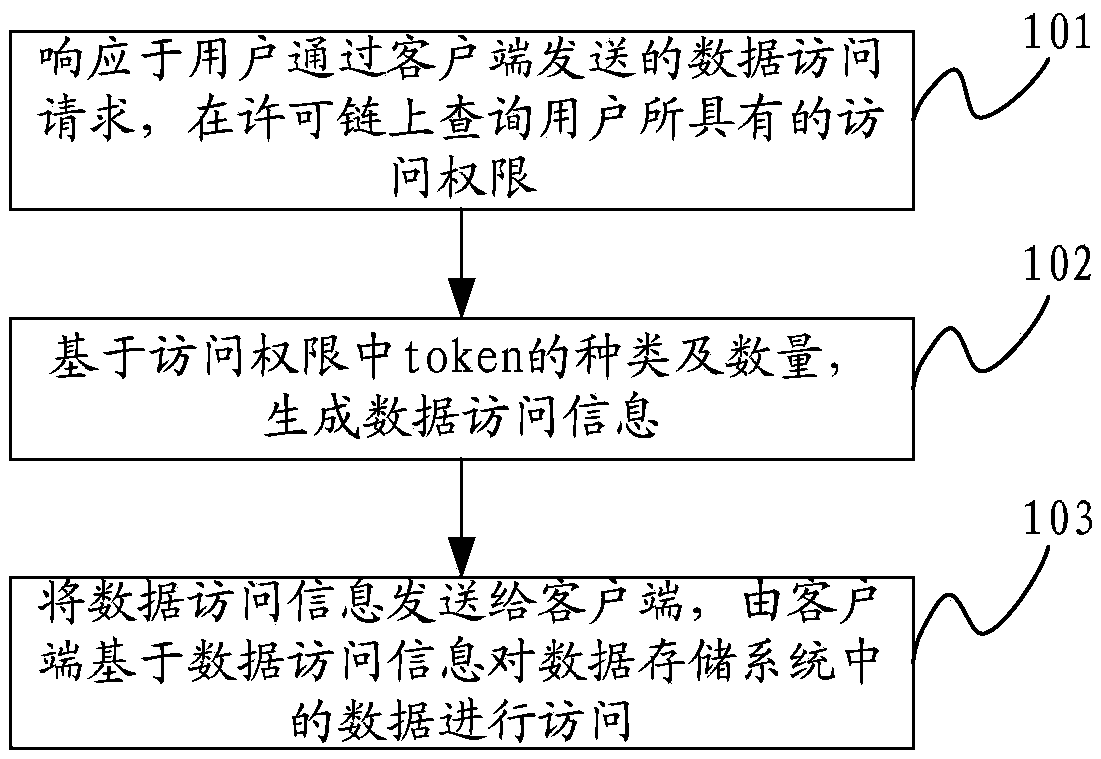
Data access method, access verification device and data storage system
ActiveCN108965299AAvoid inefficient data accessImprove data access efficiencyTransmissionClient-sideData storage system
The invention discloses a data access method, an access verification device and a data storage system. The data access method is applied to the access verification device, the access verification device has a preset license chain, permissions are respectively set for data and a user on the license chain, and the permissions are characterized by the type and number of tokens. The method comprises the following steps: querying the access permission of the user on the preset license chain in response to a data access request sent by the user through a client, wherein the access permission is characterized by the type and number of tokens; generating data access information based on the type and number of tokens in the access permission; and sending the data access information to the client, so that the client accesses the data in the data storage system based on the data access information.
Owner:湖南岳麓山数据科学与技术研究院有限公司
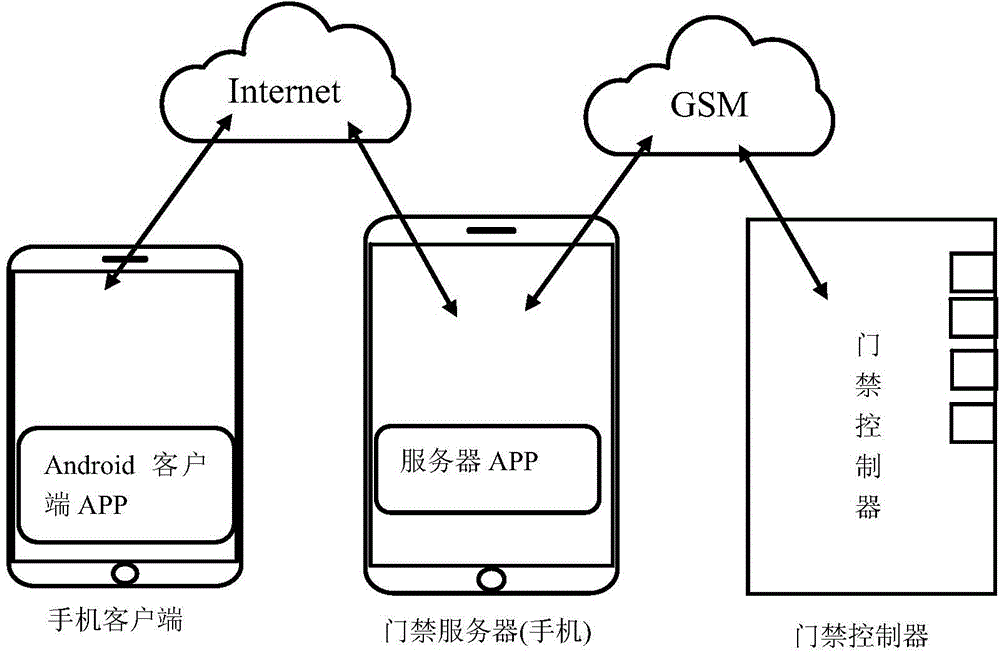
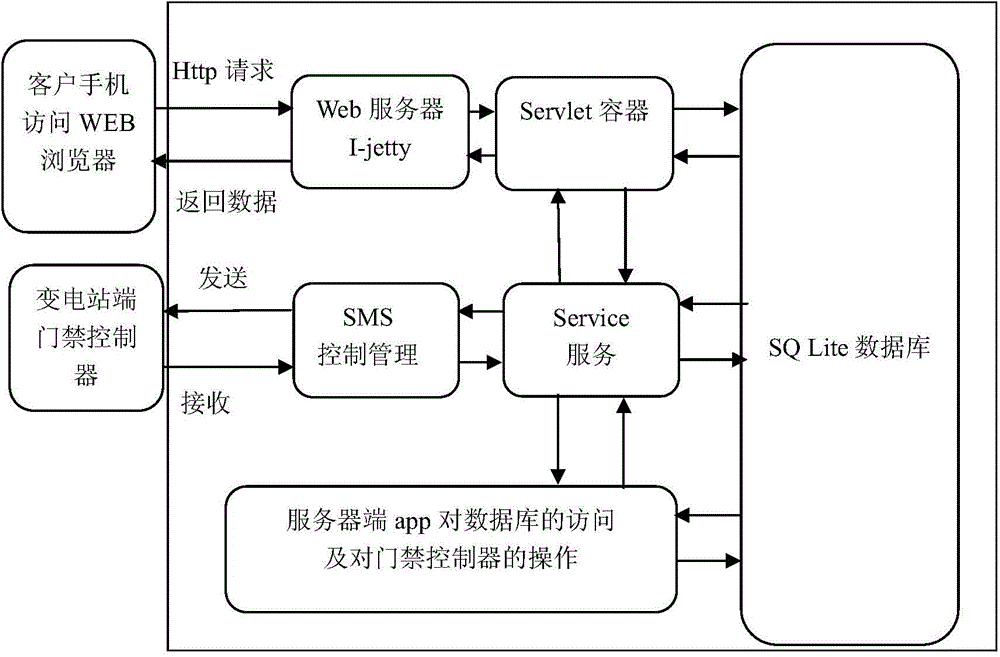
Unattended substation access control system and method based on intelligent mobile platform
The invention discloses an unattended substation access control system based on an intelligent mobile platform. The unattended substation access control system comprises a mobile phone client, an access control server and an access controller. An operation request is sent to the access control server through a wide area network by independence on app software of a smart phone, the access control server judges the operation request and then utilizes a mobile base station to send a GSM signal to the access controller at the front end of a substation, front-end equipment of the substation further controls to open a door, and a plurality of door locks of a plurality of substations in the same area can be controlled at the same time. Staffs can utilize smart phones to control the access and cardless door opening of the substations, so that the generated labor cost and vehicle cost are reduced, the substation entering efficiency is improved, and Internet of Things intelligence of the access control system is realized. The invention also discloses an unattended substation access control method based on the intelligent mobile platform.
Owner:江苏省电力公司太仓市供电公司
Data storage method and device
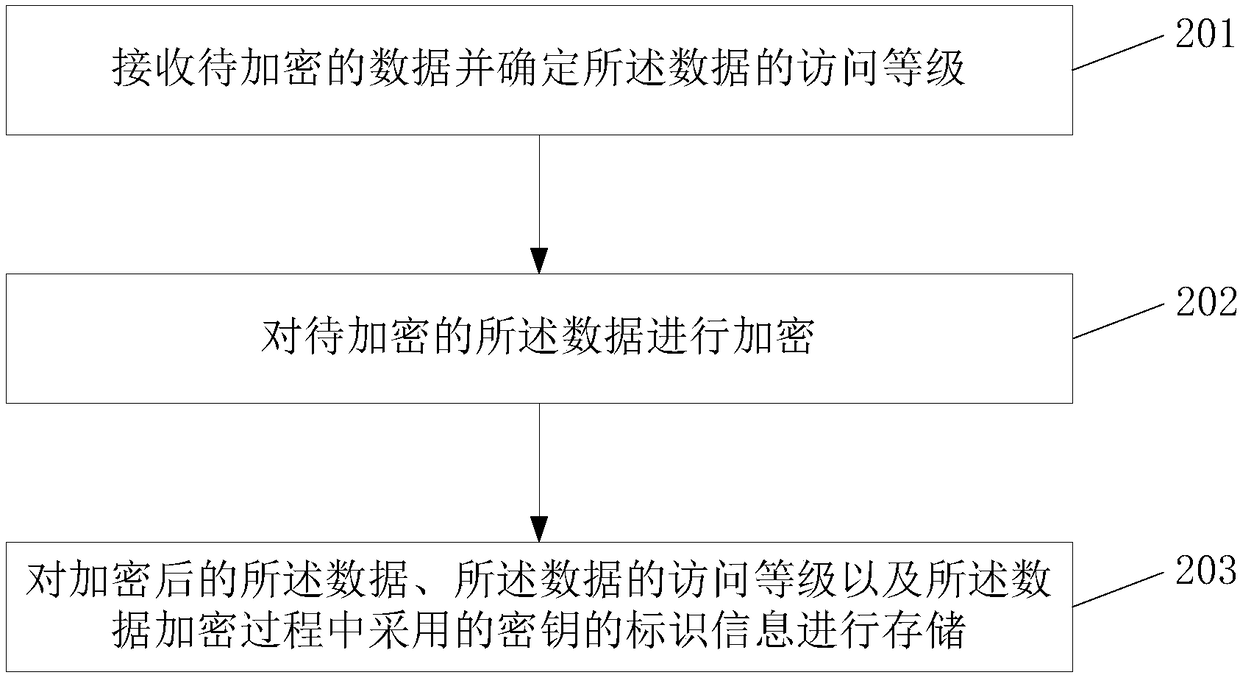
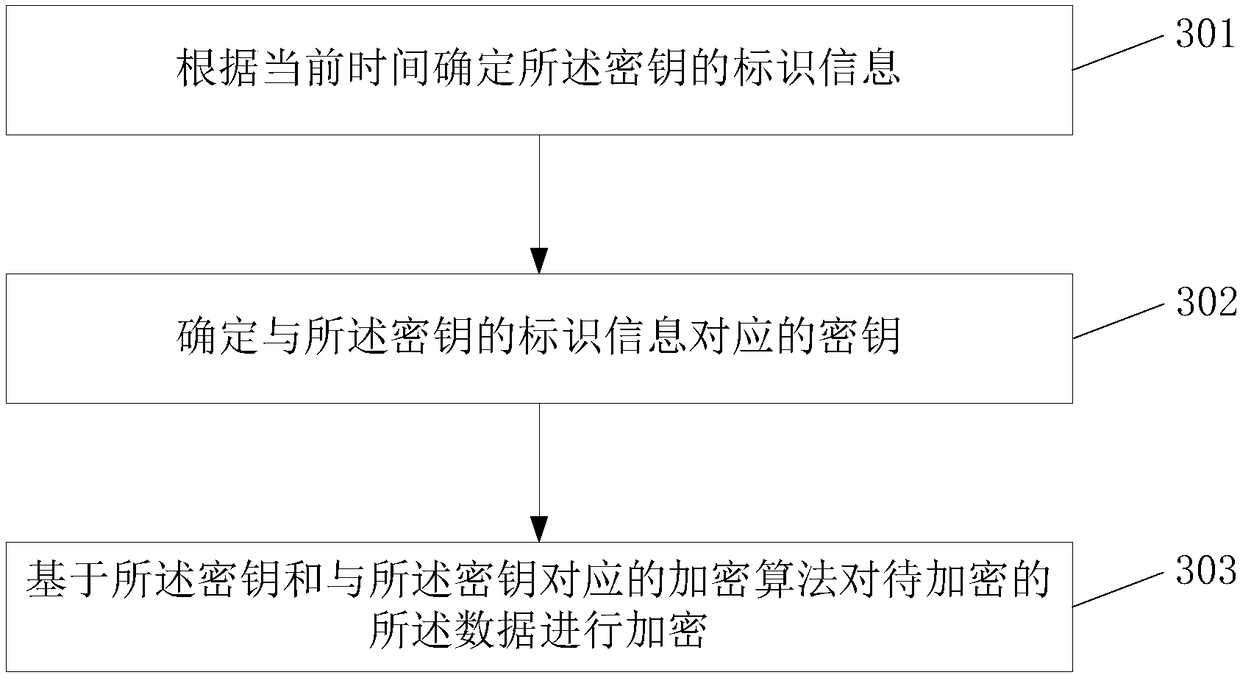
ActiveCN108520183AImplement rights managementEnsure safetyDigital data protectionData storeEncryption
The invention provides a data storage method and device. The method includes the steps of receiving to-be-encrypted data and determining the access level of the data; encrypting the to-be-encrypted data; storing the encrypted data, the access level of the data and identifier information of keys adopted during data encryption.
Owner:杭州橙鹰数据技术有限公司
Elevator calling system and elevator calling method based on two-dimensional codes and elevator
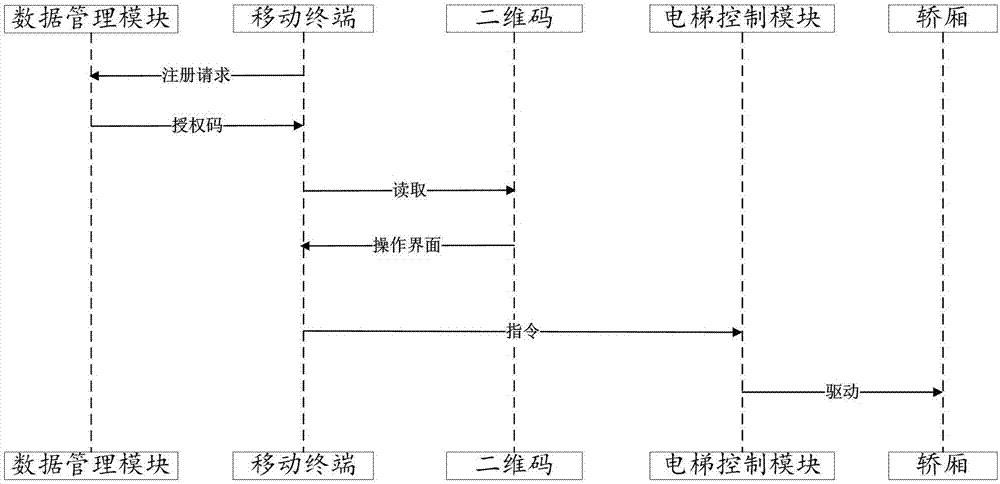
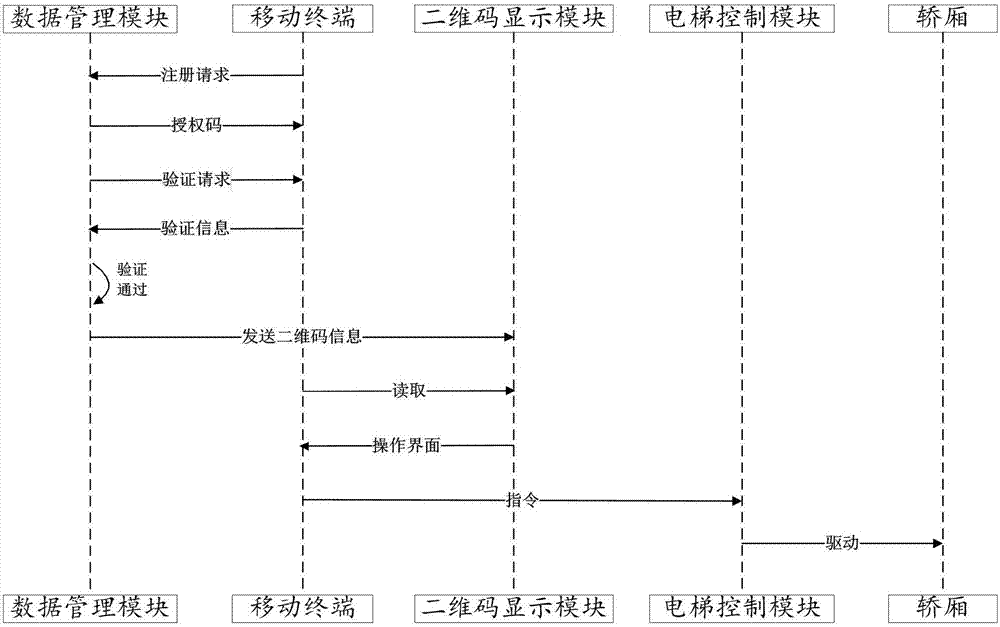
PendingCN107572318AImplement rights managementReduce setup costsElevatorsGraphicsGraphical user interface
The invention discloses an elevator calling system and an elevator calling method based on two-dimensional codes and an elevator. The elevator calling system comprises an elevator control module, a mobile terminal and a data management module; the mobile terminal is provided with a camera; the mobile terminal sends registration requests to the data management module; the registration requests comprise user identity information; the data management module returns authorization codes to the mobile terminal according to the registration requests; based on the authorization codes, the mobile terminal can obtain elevator operation graph user interfaces through scanning the two-dimensional codes; the mobile terminal sends operation instructions to the elevator control module through the interfaces; and the elevator control module drives the elevator to act according to the operation instructions. The elevator calling system has no need to issue access cards to save the cost, manages the elevator use authority through an electronic authentication mode, realizes elevator calling through scanning the two-dimensional codes, and is convenient to operate.
Owner:SJEC CORP
Method and terminal for setting permission of application and controlling restricted region
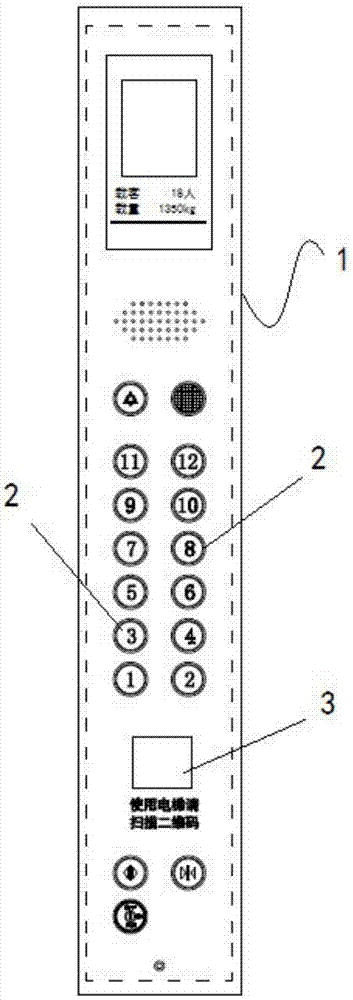
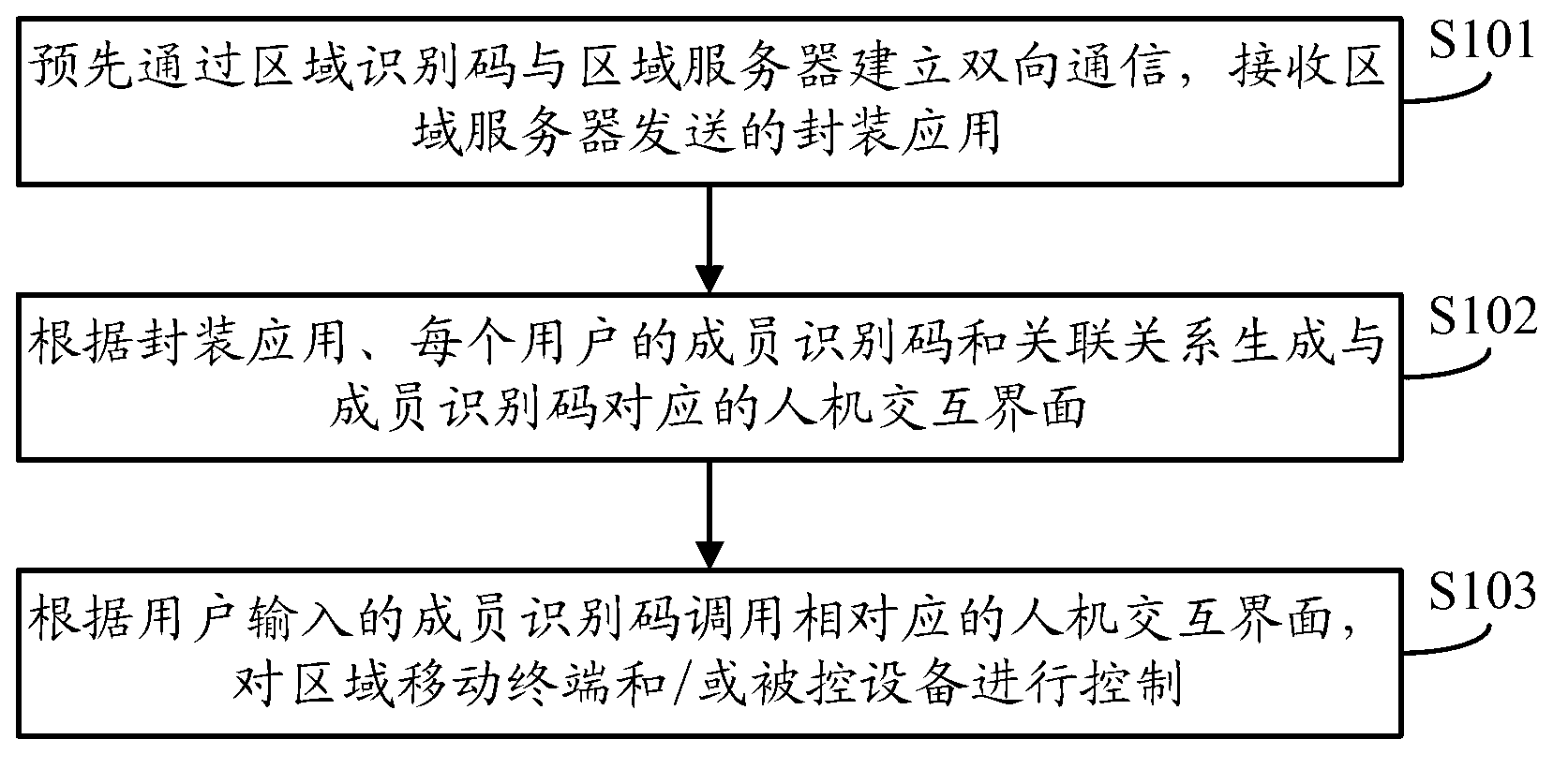
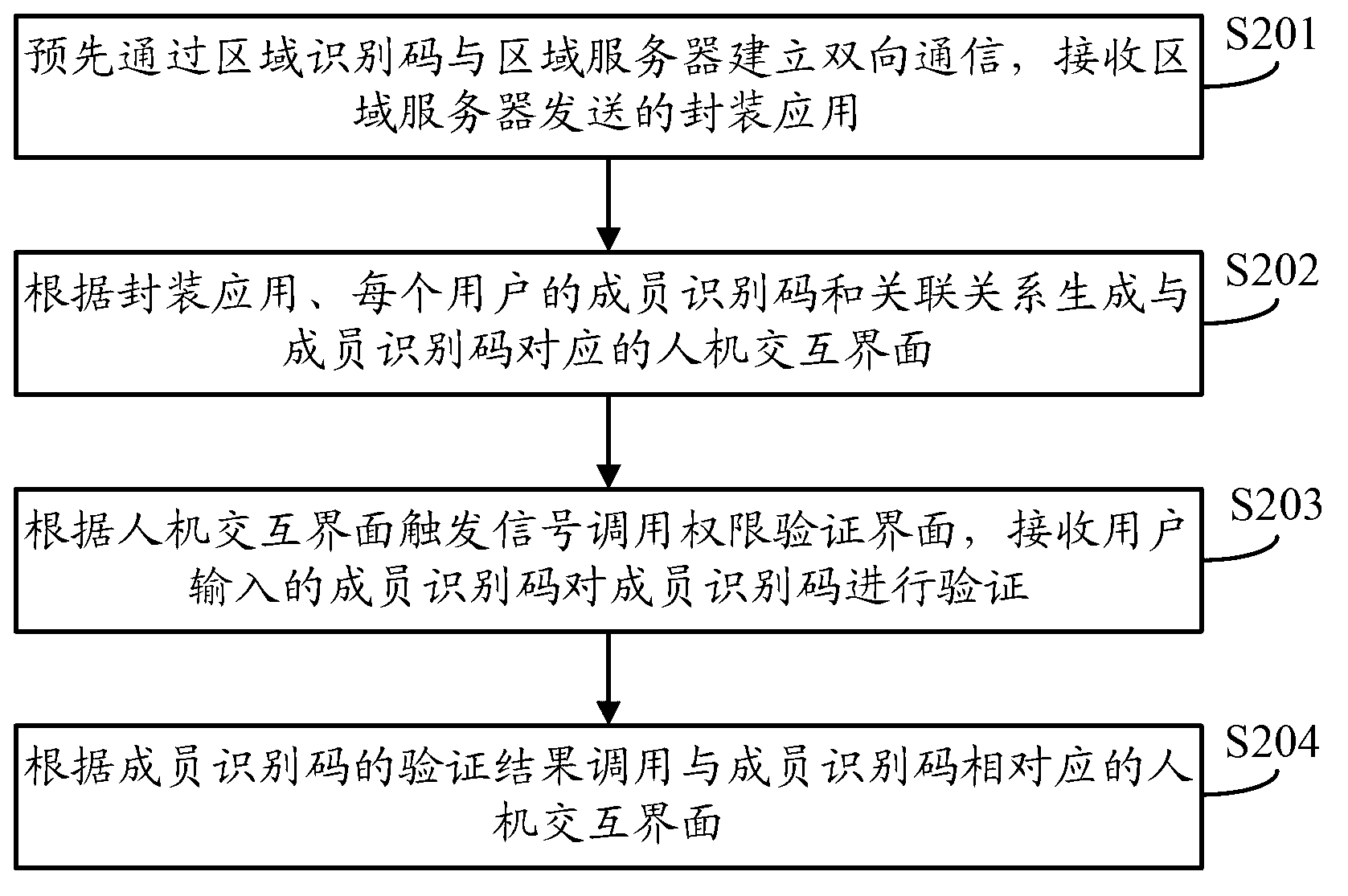
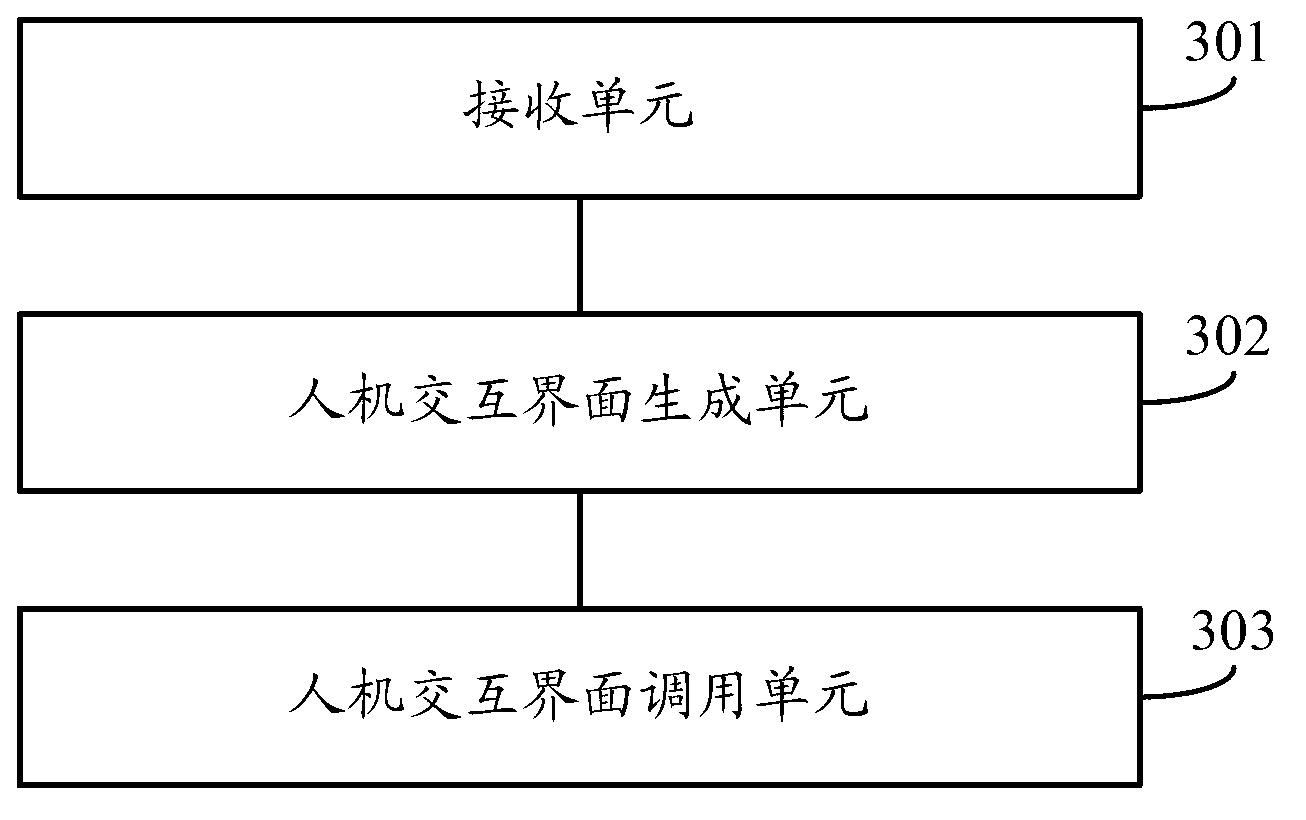
ActiveCN102938030AImplement rights managementDigital data authenticationTransmissionUser inputInteraction interface
The invention discloses a method and terminal for setting permission of an application and controlling a restricted region. The method disclosed by the invention comprises the following steps of: establishing bidirectional communication in advance by virtue of a region identification code and a region server, receiving an encapsulation application sent by the region server, and generating a human-computer interaction interface corresponding to a member identification code according to the encapsulation application and authority association between the member identification code of each member of multiple members and corresponding operating authorization; calling the corresponding human-computer interaction interface according to the member identification code input by the user, and controlling the region mobile terminal and / or controlled equipment of an icon identification in the human-computer interaction interface; or calling the encapsulation application of the icon identification in the human-computer interaction interface and controlling the region mobile terminal and / or controlled equipment corresponding to the encapsulation application. Communication is established by virtue of the region identification code and the restricted region while the encapsulation application is synchronized, and further authority association stored locally is combined, so that authority management for controlling the terminals in the restricted region by multiple users is realized.
Owner:周万荣
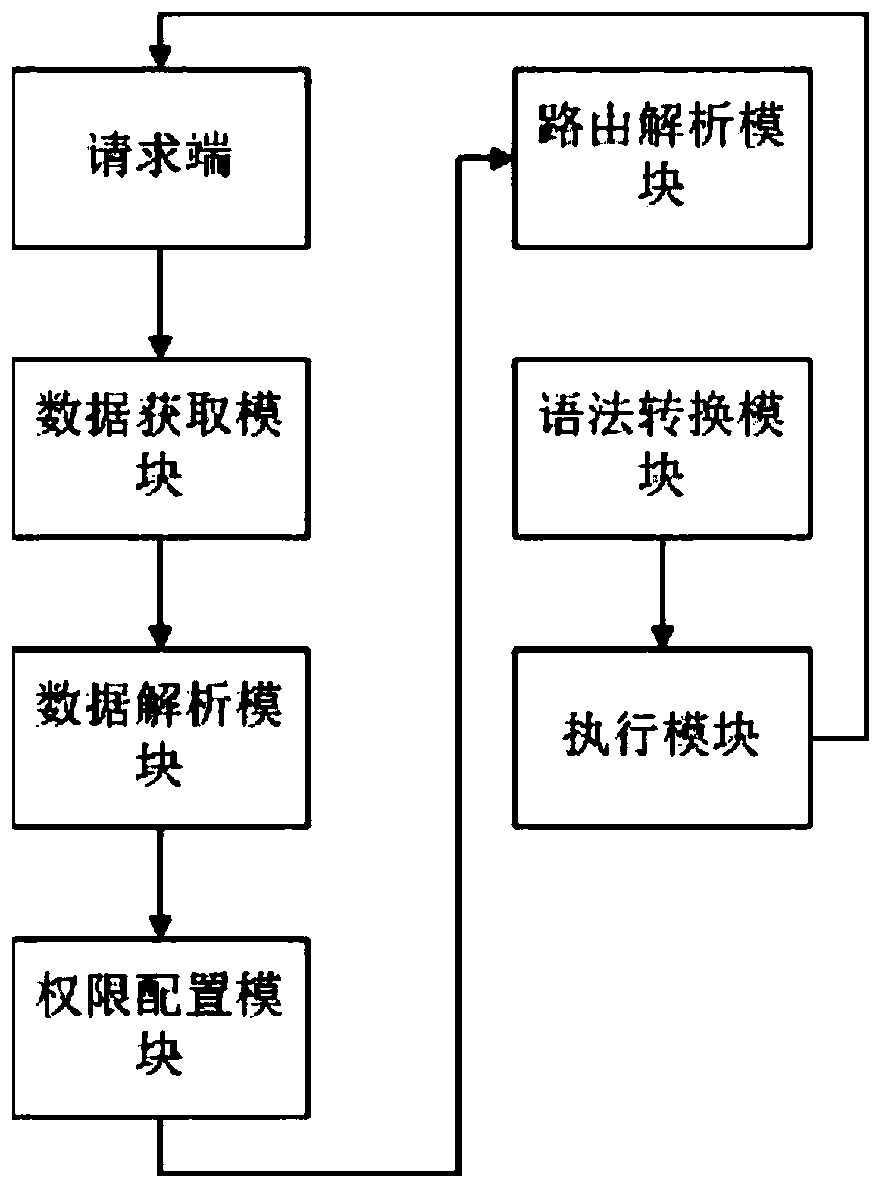
A method and system for uniformly processing heterogeneous data sources
InactiveCN109766352AImplement rights managementReduce technical difficultyDigital data information retrievalDigital data protectionData transformationNetwork Communication Protocols
The invention discloses a method and system for uniformly processing heterogeneous data sources. The method comprises the following steps of acquiring request end data; obtaining user information through the request end data and authenticating a user; analyzing the request end data, and determining a target database of the request end data; converting the request end data into a dialect corresponding to a target database; establishing a connection with the target database, executing the request end data through the converted dialect, and returning an execution result to the request end. The system comprises a data acquisition module, a data analysis module, an authority configuration module, a route analysis module, a grammar conversion module and an execution module. The method is based on MySql binary communication protocol communication. By converting the standard Sql statement into the target database dialect, the purpose of operating different types of databases and returning databy taking the unified Sql92 standard statement as an inlet is achieved, the implementation cost and the technical difficulty of cross-database heterogeneous data source unified processing are effectively reduced, and the efficiency of heterogeneous data source unified processing is improved.
Owner:CHENGDU SEFON SOFTWARE CO LTD
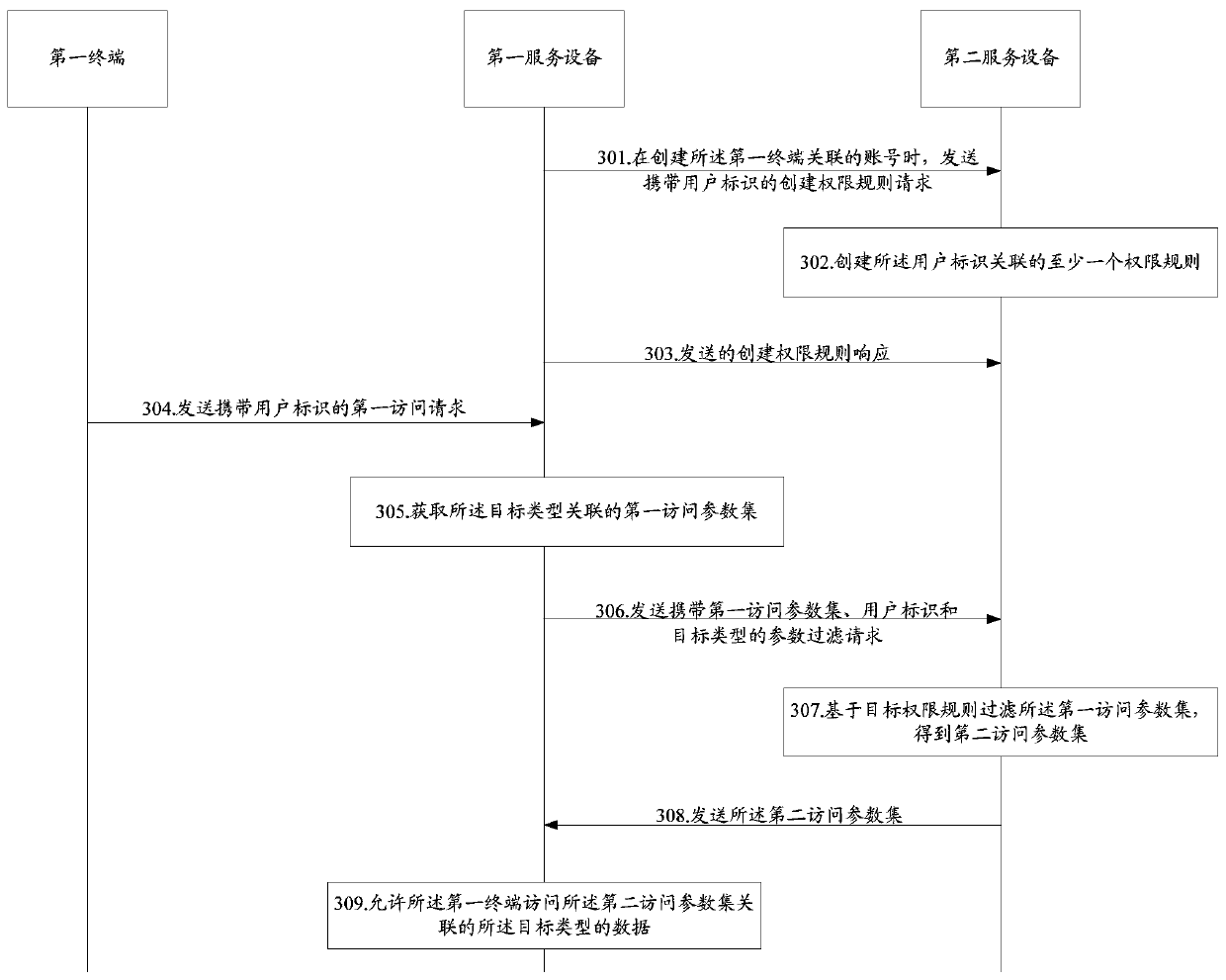
Authority processing method and related equipment
InactiveCN109815731AImplement rights managementAvoid delayDigital data protectionData accessRights management
The invention discloses an authority processing method and related equipment. The method is applied to first service equipment included in a data access system, the data access system further comprises second service equipment and a first terminal, the method comprises the steps that a first access request which is sent by the first terminal and carries a user identifier of the first terminal is received, and the first access request is used for requesting to access data of a target type; obtaining a first access parameter set associated with the target type; sending a parameter filtering request carrying the first access parameter set, the user identifier and the target type to the second service equipment; receiving a second access parameter set sent by the second service device for theparameter filtering request, the second access parameter being obtained by the second service device filtering the first access parameter set based on a target permission rule, and the target permission rule being associated with the user identifier and the target type; And allowing the first terminal to access the target type of data associated with the second access parameter set. According to the embodiment of the invention, authority management of data access is realized.
Owner:SHENZHEN INTELLIFUSION TECHNOLOGIES CO LTD
Permission management method and device based on intelligent contract
InactiveCN108846755AImplement rights managementMeet the complexity of rights managementFinanceDigital data authenticationRights managementStorage model
The invention provides a permission management method and device based on an intelligent contract. The method comprises the steps of obtaining a subject identifier, an object identifier and an operation relation between a subject and an object; according to the subject identifier, the object identifier and the operation relation, generating a unique permission storage identifier; and performing operation on permission control content information of the subject or the object according to the permission storage identifier. A data structure and the permission management method used by a Key-Valuedatabase are completed in the intelligent contract, and are not limited to a certain type of block chain technology. The method can be efficiently decoupled from the control of block chain nodes andthe like, is decoupled from a service model, realizes the permission management of small unit capacity, and does not depend on other systems. For a data storage model and unit capacity limitation of ablock chain, the operations of adding, modifying, querying, deleting and the like of existing block chain data are adapted, the permission management complexity of service requirements is met, and the requirements of the performance of usage experience and the like are met.
Owner:苏州朗润创新知识产权运营有限公司
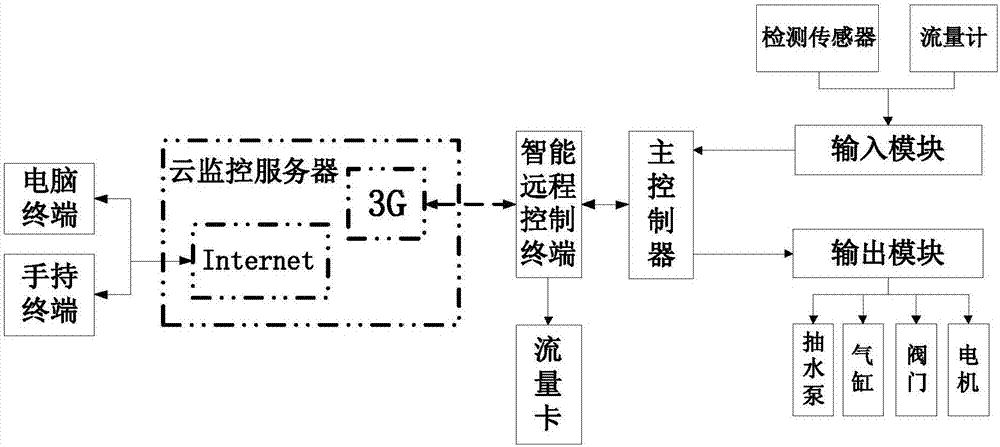
Intelligent sewage treatment device and method
PendingCN107089757ARealize remote maintenanceRealize data monitoringWater treatment parameter controlSpecific water treatment objectivesOperational costsUltrafiltration
The invention provides an intelligent sewage treatment device and method. The device comprises a container, as well as a mixing tank, a supermagnetic sewage purification box, a first water tank, an activated carbon filter device, a second water tank, a nano ultrafiltration device, a third water tank, a PAM addition device, a PAC addition device, an ammonia-nitrogen-free drug addition device, an activated carbon cleaning device, a disinfectant addition device, an ultrafiltration cleaning device, a water suction pump, a magnetic seed recovery device, a desliming device and an electric control cabinet which are located in the container. By adopting a supermagnetic separation and purification technology and container installation, the floor area is saved and transportation is convenient; remote maintenance and data monitoring of the intelligent sewage treatment device are achieved through a cloud server; wiring is not needed, a distance limit is avoided, only a mobile phone signal is needed, and a master-slave limit is avoided; data exchange of various modes, such as a one-to-many mode, a many-to-one mode and a many-to-many mode is achieved; and fault maintenance of maintenance personnel can be achieved at any place, and thus the operation cost is reduced.
Owner:BEIJING AREOSTANARD NEW TECH +1
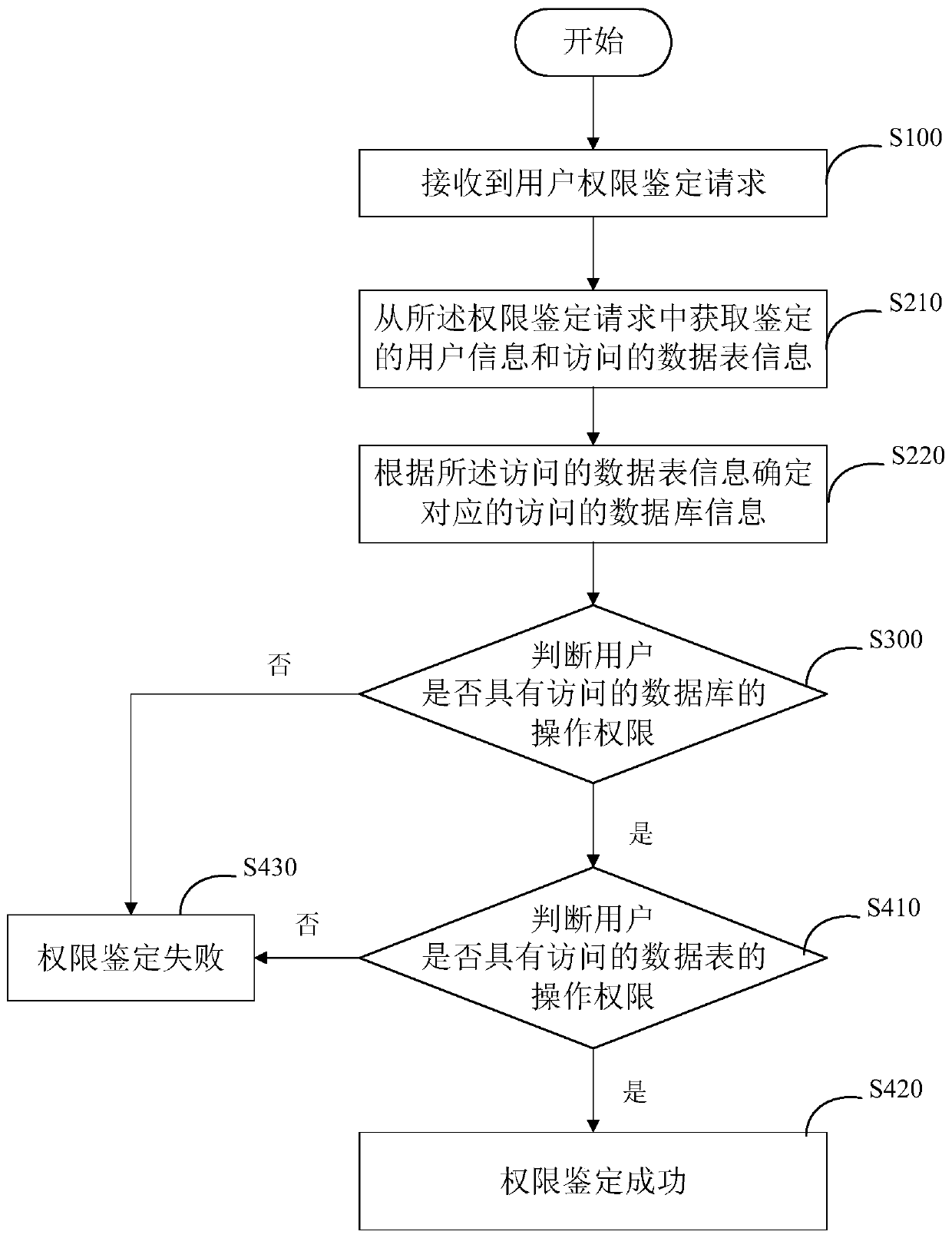
Authority management method, system and equipment and storage medium
InactiveCN111177789AEasy to controlImprove protectionDigital data protectionMulti-dimensional databasesUser PrivilegeBusiness enterprise
The invention provides an authority management method, system and equipment and a storage medium. The method comprises the steps of receiving a user authority identification request; acquiring authenticated user information and accessed database information from the authority authentication request; judging whether the user has the operation authority of the accessed database or not; and determining an authority identification result according to the judgment result. According to the invention, the database is used as assets for management and empowerment to realize right management, management and control of data assets with a database as a carrier are achieved, unified management of all warehouse authorities in an enterprise is achieved, management and control and protection of data areenhanced after a unified data warehouse is built and before data use and data enabling are conducted, unified big data authority management in the enterprise is achieved, and data asset safety is improved.
Owner:JIANGSU MANYUN SOFTWARE TECH CO LTD
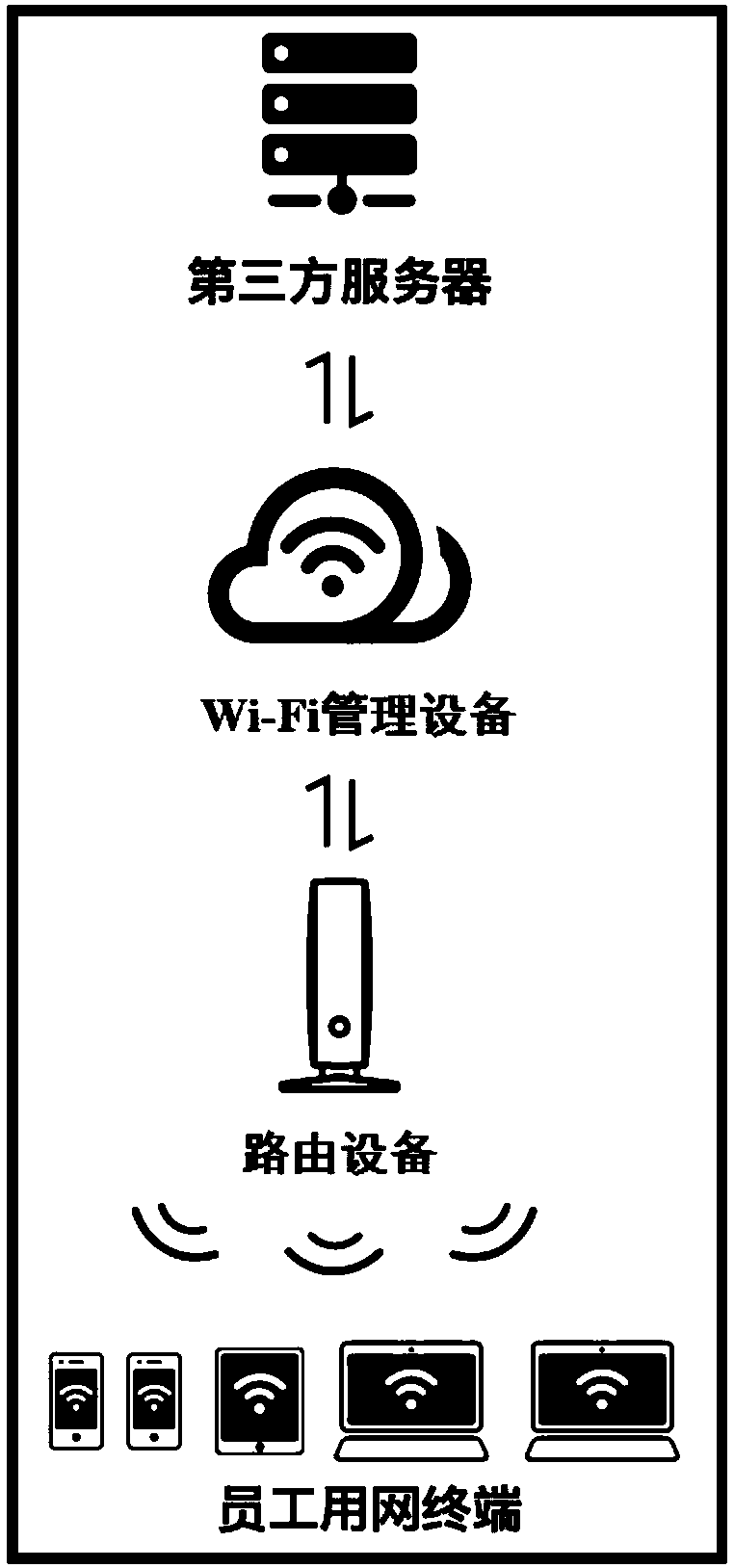
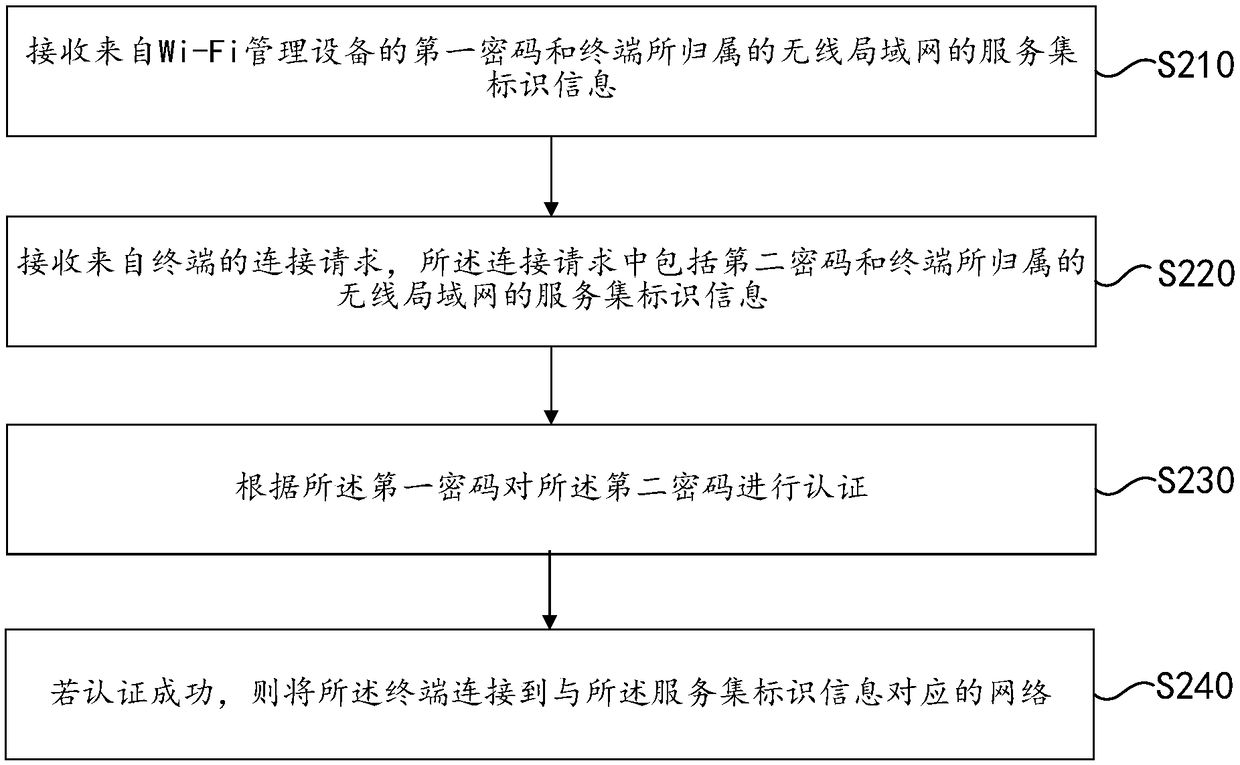
Intelligent security Wi-Fi management method and system
ActiveCN108990062AEasy to connect to the InternetReduce operating costsKey distribution for secure communicationAssess restrictionWi-FiOperational costs
The invention provides an intelligent security Wi-Fi management method and system. The method comprises the following steps: receiving a networking request from a terminal; Generating at least one password corresponding to the networking request; Acquiring service set identification information of a wireless local area network to which the terminal belongs; The service set identification information and at least one password corresponding to the networking request are sent to the terminal and the routing device so that the terminal connects the routing device using the password and the serviceset identification information. The embodiment of the invention realizes that a single service set identifier is used to support multiple terminals to connect with multiple passwords to a wireless local area network, and the original connection protocol and the use mode are not changed, and the one-key networking function is supported, so that the terminal can be conveniently and quickly networked. On this basis, Wi-Fi to carry out unified management, reduce the operating costs of Wi-Fi management, to ensure the safety, stability and efficient operation of the network.
Owner:QUANXUN HUIJU NETWORK TECH BEIJING CO LTD
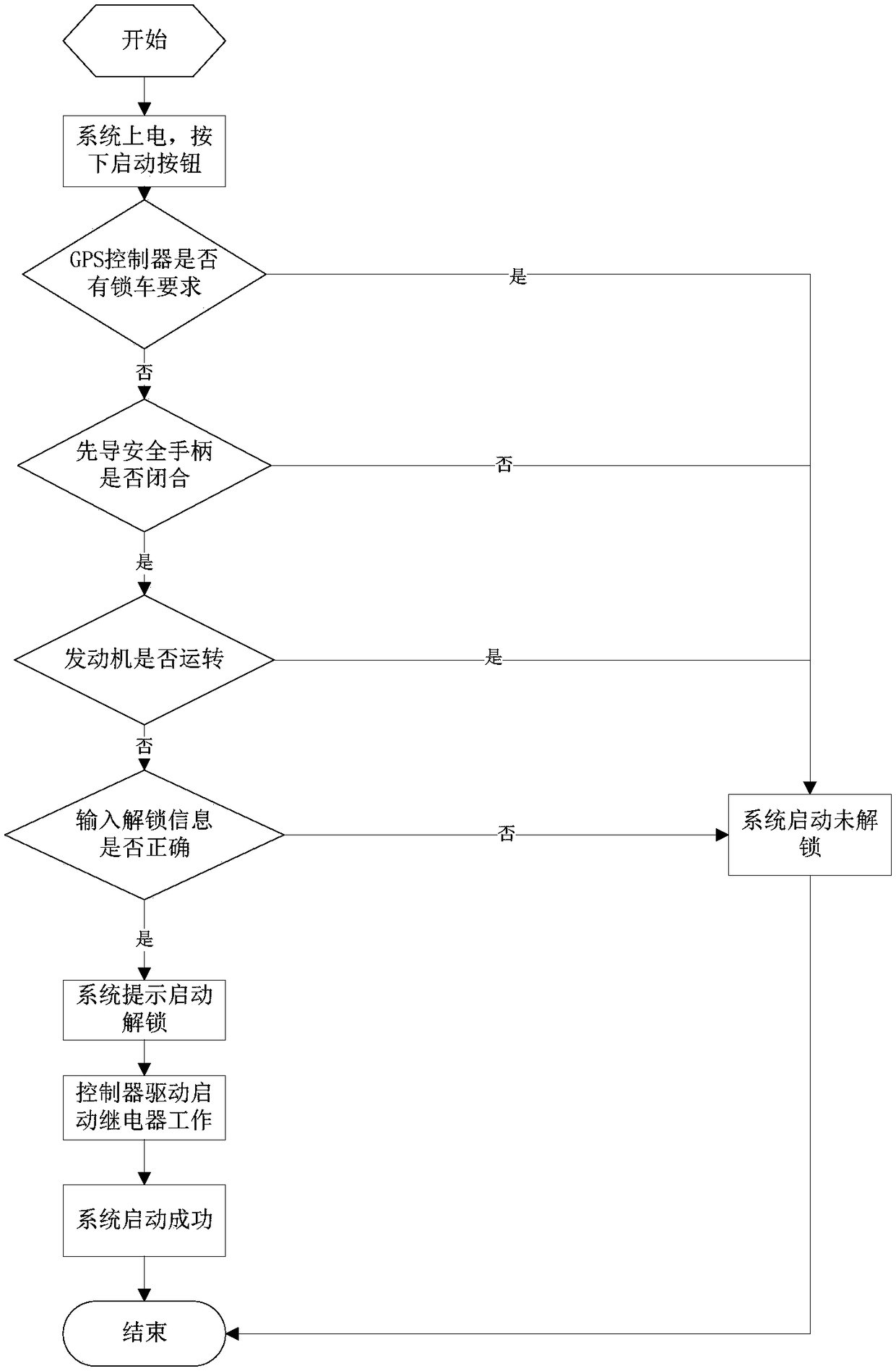
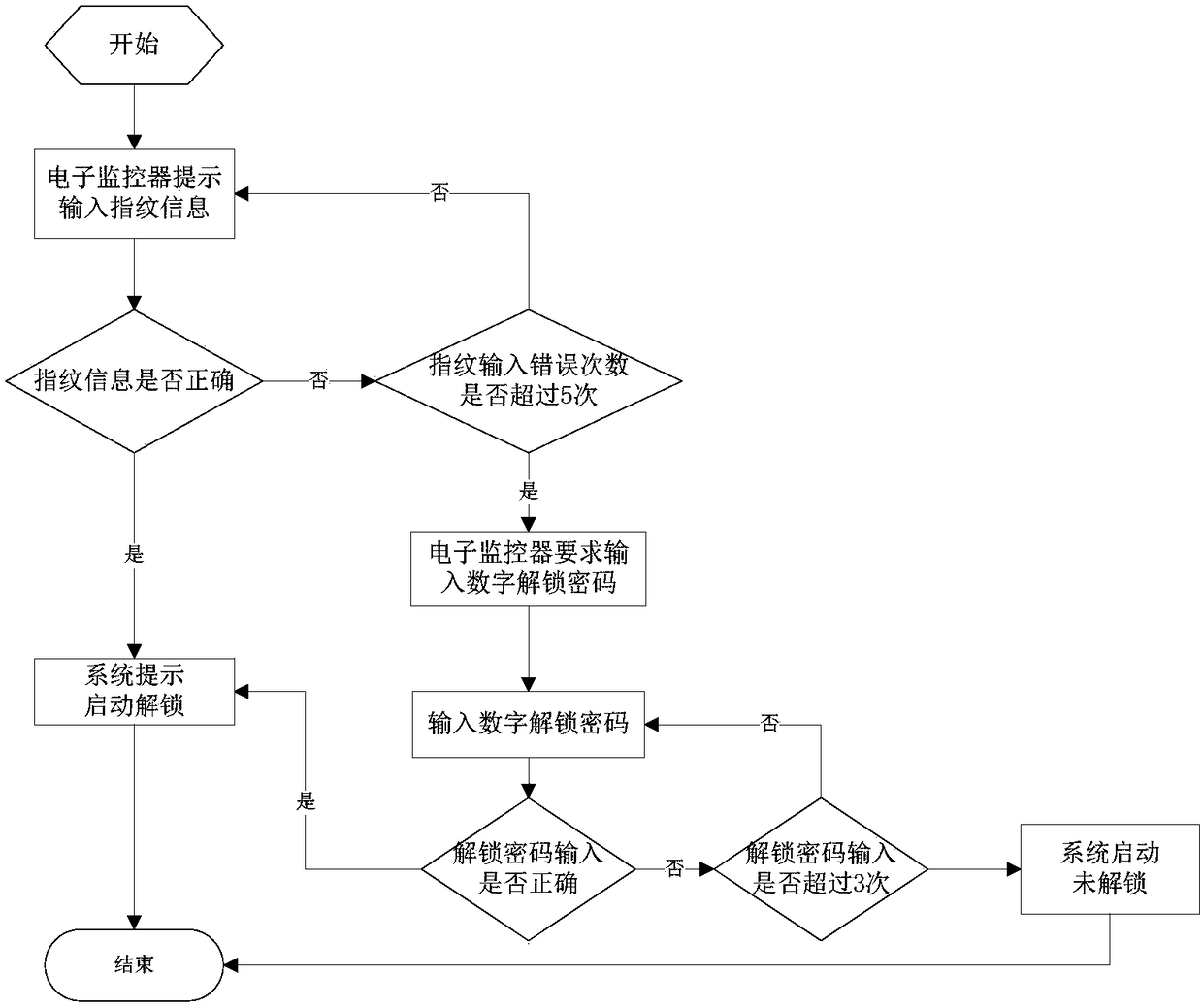
Excavator one-key start control device and method
ActiveCN108583507AStrengthen security managementImplement rights managementAnti-theft devicesOperabilityEngineering
The invention provides an excavator one-key start control device and method. The control device comprises a master controller, a guide handle, a guide pedal, an electronic monitor, a fingerprint identification module, a GPS controller, a GPS management platform, a mobile communication platform, a mobile phone client side, a one-key start module, a start relay, a guide safety handle, an engine controller and an emergency stop switch. A start key conventionally adopted in the prior art is saved through simplification, auxiliary start devices such as radio frequency are not needed, the inconvenience factor caused by the fact that a user forgets to carry an induction device is avoided, meanwhile, a one-vehicle one-key purpose is convenient to achieve, authorization control of a start system can be guaranteed under the condition that the one-vehicle one-key condition is guaranteed, start and operation authority management of excavator equipment can be achieved through combination with the latest fingerprint identification technology, the safety management level of a machine is improved, potential safety hazards generated by non-active control such as a secondary start and a mistaken stall are effectively prevented, and the operability and safety of the machine are effectively improved.
Owner:XCMG EXCAVATOR MACHINERY
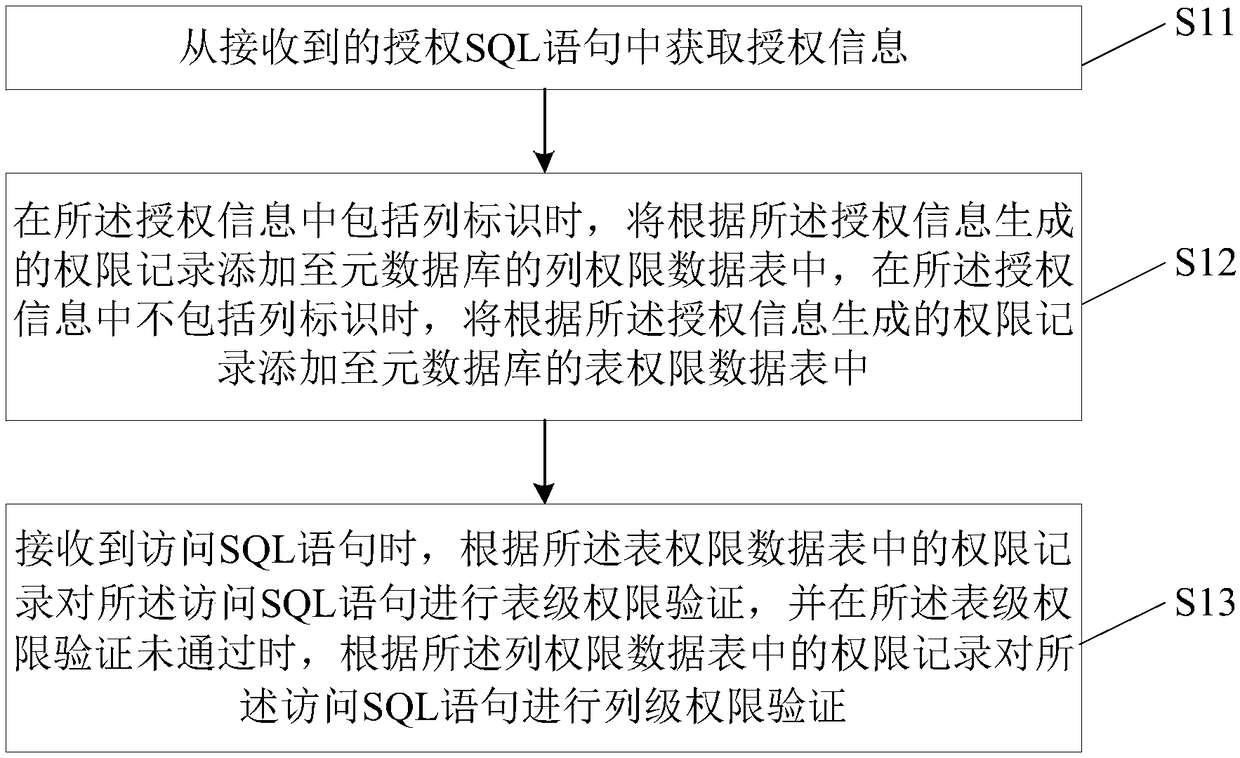
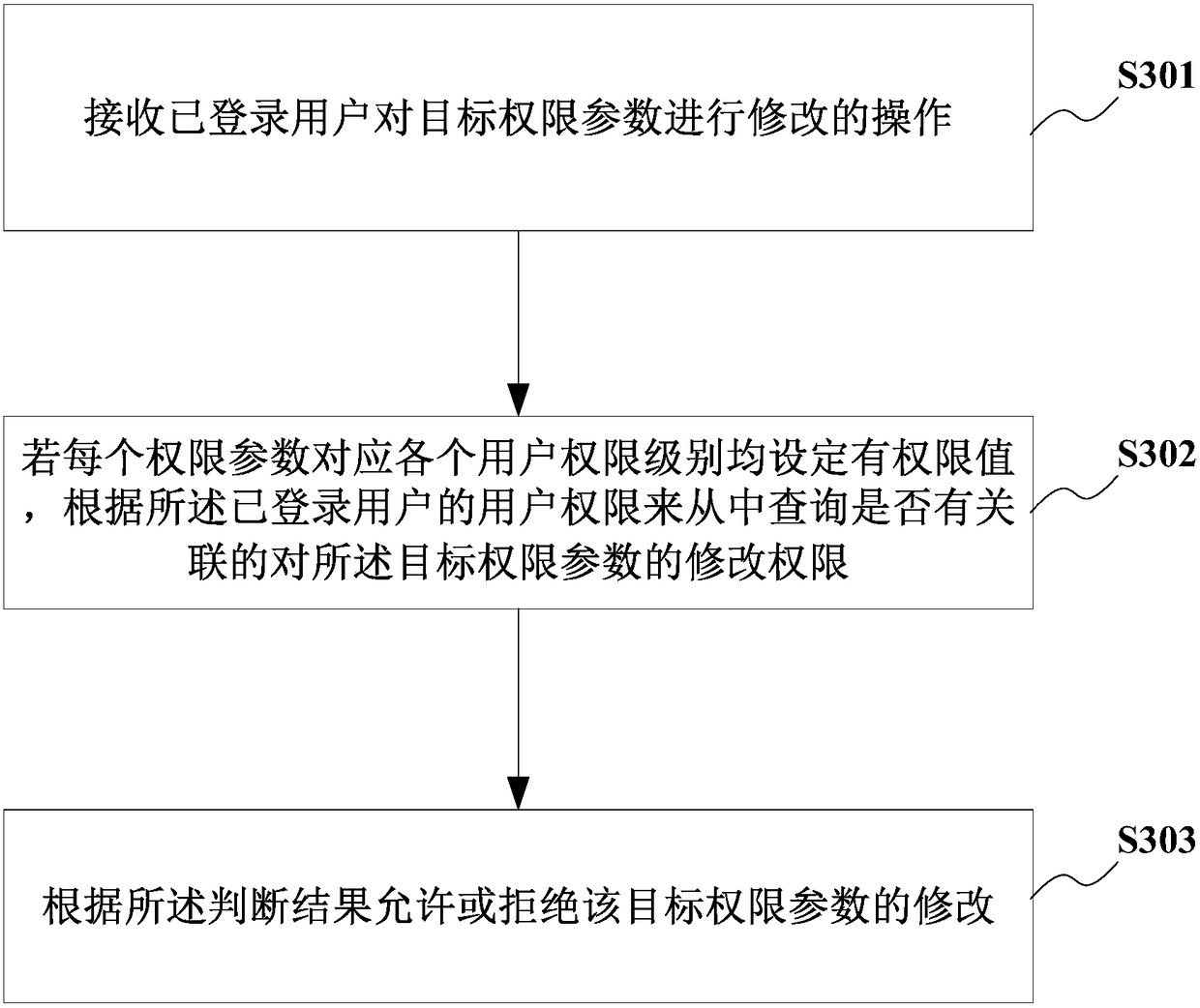
Authority management method and apparatus
The present disclosure relates to an authority management method and apparatus, including obtaining authorization information from a received authorization SQL statement; adding a right record generated according to the authorization information to a column right data table of a metadata database when the authorization information includes a column identifier, and adding a right record generated according to the authorization information to a table right data table of the metadata database when the authorization information does not include a column identifier; when the access SQL statement isreceived, table-level authority verification being performed on the access SQL statement according to the authority record in the table authority data table, and column-level authority verification being performed on the access SQL statement according to the authority record in the column authority data table when the table-level authority verification is not passed. By performing permission verification according to the column-level permission data table and the table-level permission data table, the right management method and the device according to the disclosed embodiment can realize fine-grained right management in SparkSQL.
Owner:NEW H3C BIG DATA TECH CO LTD
Supply chain access control system and method based on public chain smart contract
ActiveCN111797374AMeet traceability requirementsEffective data sharingDigital data authenticationManufacturing computing systemsControl systemFinancial transaction
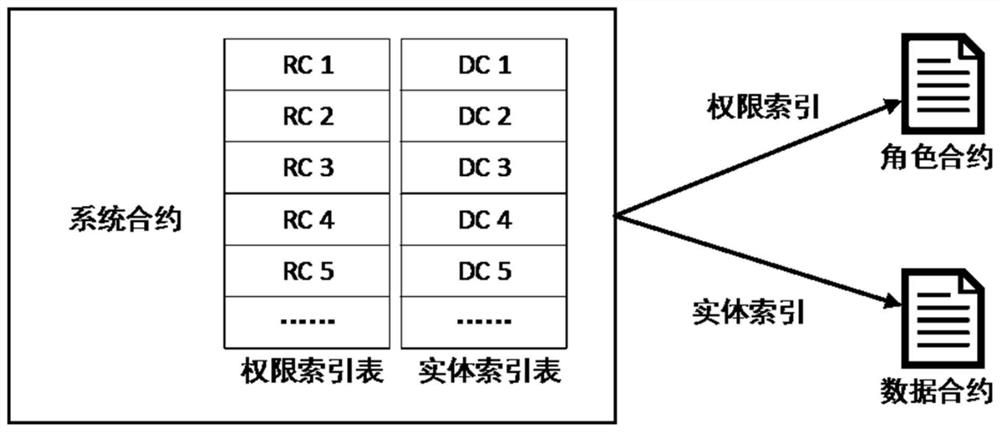
The invention relates to a supply chain access control system based on a public chain smart contract, which is used for access control in a block chain traceability scene. According to the system, anRBAC model is adopted, and the system comprises a system contract SC, role contracts RC and data contracts DC. The RBAC model comprises four types of agents which are associated with one another and an operation set OP, and the four types of agents are respectively a user agent u, a role agent r, a permission agent p and an object agent ob. The system contract SC is used for managing a user agentu, the role contracts RC are used for managing a role agent r and a plurality of permission agents p, and the data contracts DC are used for managing the object agent ob. The deployment transaction ofthe system contract SC serves as an entrance of the RBAC model and is firstly linked, and the multiple role contracts RC and the multiple data contracts DC are respectively called by the system contract SC. Compared with the prior art, the system has the advantage that data sharing convenience, data privacy security and the like are ensured at the same time.
Owner:浙江同善人工智能技术有限公司
Wireless linkage and controlling method and system
ActiveCN105933378AImprove compatibilityIncrease flexibilityTransmissionInformation transmissionControl system
The invention discloses a wireless linkage and controlling method, and the method comprises the steps: sensing and controlling trigger equipment or trigger event and sensing and controlling equipment associated information is added in the linkage information, and system main control equipment writes the linkage information in a wireless linkage node network; the sensing and controlling trigger equipment or trigger event makes the wireless linkage node network for storing the linkage information to acquire a trigger response through and controlling or sensing, and transmits the trigger response access information to sensing and controlling receiving equipment associated to the linkage information in a linkage sensing and controlling way or controls the working condition of the sensing and controlling receiving equipment. According to the invention, the sensing and controlling trigger equipment of the system has a dynamic access relation with the wireless linkage node network and can perform linkage information transmission and control on associated one or more sensing and controlling receiving equipment in a specific mode with preset control right, the equipment has better compatibility and flexibility than before, so that the convenience and safety of intelligent control can be improved.
Owner:SHENZHEN ALM SOUND TECH CO LTD
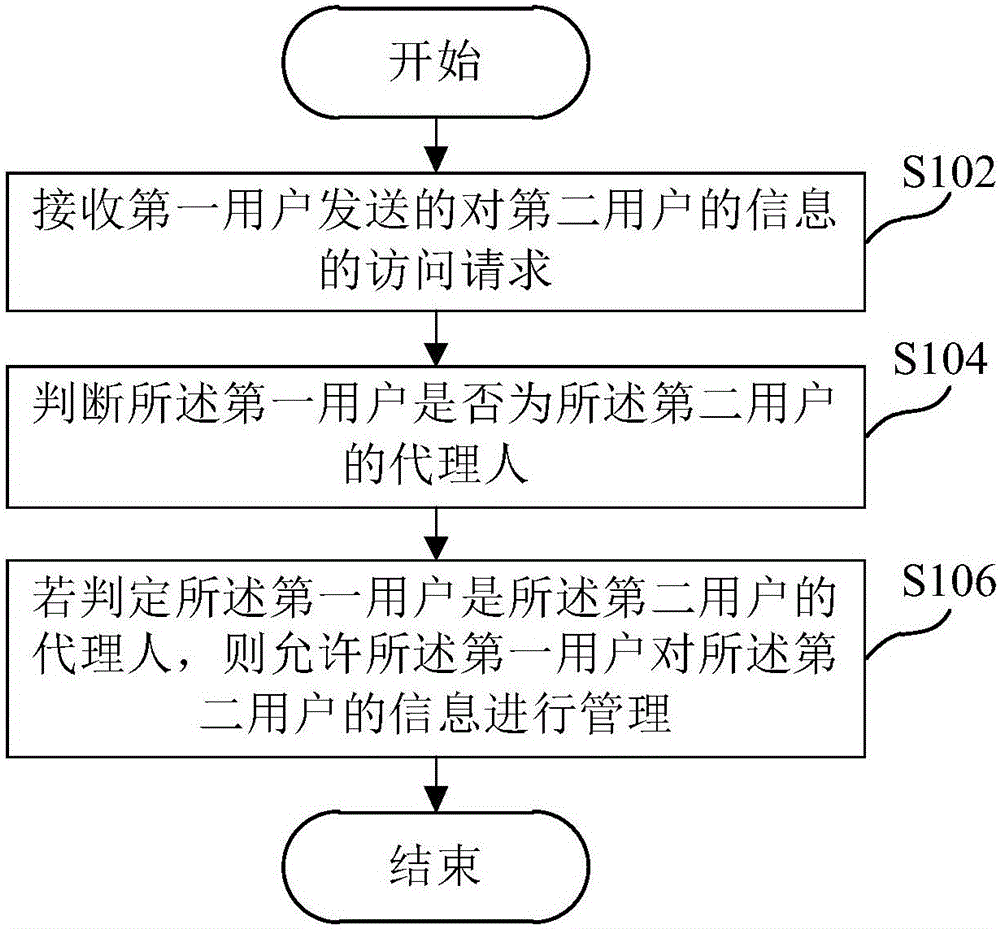
Method and equipment for managing user permission
ActiveCN105956459AAvoid permission controlImplement rights managementDigital data authenticationCouplingDEVS
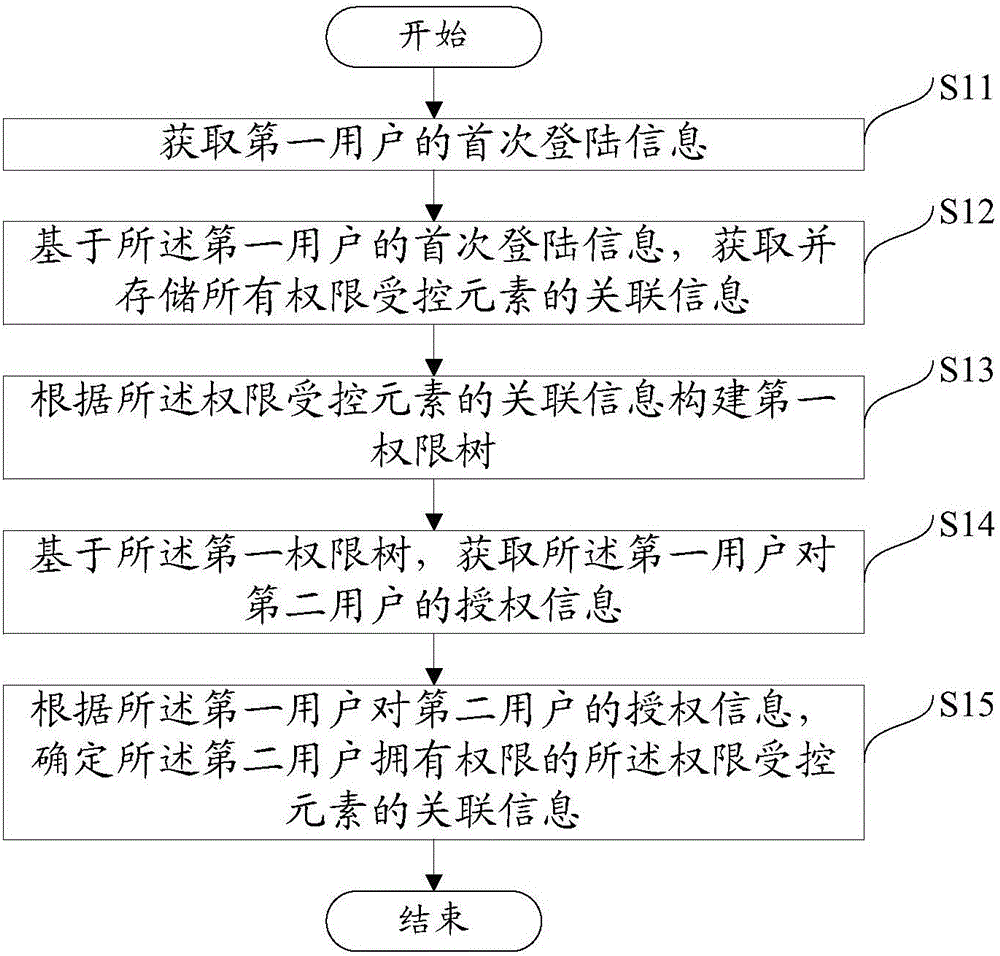
The invention aims to provide a method and equipment for managing user permission. Compared with the prior art, the method comprises the following steps: firstly, obtaining first-time login information of a first user; then, on the basis of the first-time login information of the first user, obtaining and storing association information of all permission controlled elements; successively, according to the association information of all the permission controlled elements, constructing a first permission tree, and obtaining authorization information of the first user for a second user on the basis of the first permission tree; and then, according to the authorization information of the first user for the second user, determining association information of the permission controlled elements of the permission owned by the second user. The method realizes user permission management through a low-coupling, extensible and high-performance way so that a phenomenon that development personnel compile a great quantity of logic decision codes to carry out permission control is avoided. Furthermore, the permission controlled elements can be increased or reduced according to a user instruction so that flexibility and expansibility is improved.
Owner:上海佳依佳信息科技有限公司
Industrial service authority management method and device, and machine tool equipment
The invention provides an industrial service authority management method and device, and machine tool equipment. The method comprises the following steps: acquiring information to be verified and userauthority level information that are stored in an information device; verifying the read information to be verified, wherein the information to be verified comprises one kind of device identifier information, unit identifier information or user information, or a plurality of kinds of combinations of the above information; if the information to be verified is successfully verified, permitting a user corresponding to the information to be verified to log in; detecting a service function accessed by the user during operation, wherein the service function is pre-associated with an authority parameter, and the authority parameter is provided with pre-assigned required authority level information; judging whether a user authority level is above a required authority level or not according to theuser authority level information; and permitting or rejecting use of the service function according to a judgment result. The method and device and the equipment provided by the invention have the advantages that the authority information in the information device is read through the machine tool equipment, and the various service functions corresponding to the authority information are determined through a preset authority identification mechanism for use, so that automatic authority management for the machine tool equipment is achieved.
Owner:SYMG SHANGHAI INTELLIGENCE SYST CO LTD
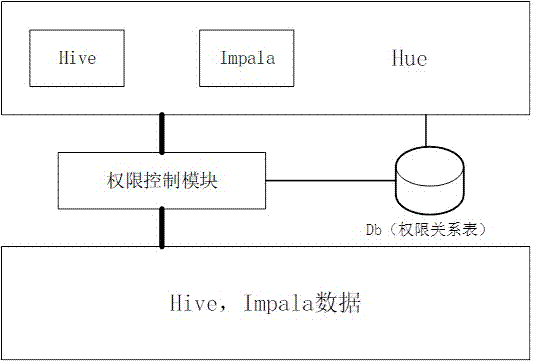
Permission management system based on Hue
InactiveCN107358069AFlexible allocation of permissionsFix access issuesProgram/content distribution protectionExecution for user interfacesRights managementHue
The invention relates to a permission management system based on Hue. The system comprises a permission control module, a permission relation table module and a data storage module. The permission control module is used for obtaining Hue login information, and the Hue login information refers to the Hue login information of a data analyst and at least comprises a login account; the permission relation table module is used for recording the access permissions of the login account logging in the Hue to libraries and tables and providing the permission control module with access permission information; the data storage module is used for storing data and forming the corresponding libraries and tables. According to the access permission information, the libraries and the tables which can be read by the login account are obtained by the permission control module and transmitted to the corresponding login account by the permission control module. According to the system, based on the Hue, through secondary development, the permission management system is built and used for managing the permissions of the libraries and the tables in Hive and Impala, the problem of the access permissions of different data analysts to the libraries and the tables in the Hive and the Impala is amicably solved, and the permissions of the libraries and the tables can be flexibly assigned to different users.
Owner:塞纳德(北京)信息技术有限公司
Method and device for managing authority
InactiveCN106778354AGuaranteed privacy of personal dataRealize managementDigital data protectionWorld Wide WebRequest for information
Owner:TAIKANG LIFE INSURANCE CO LTD
Method for controlling access authority and terminal device
ActiveCN108681427AShort timeImplement rights managementInput/output processes for data processingTerminal equipment
Owner:VIVO MOBILE COMM CO LTD
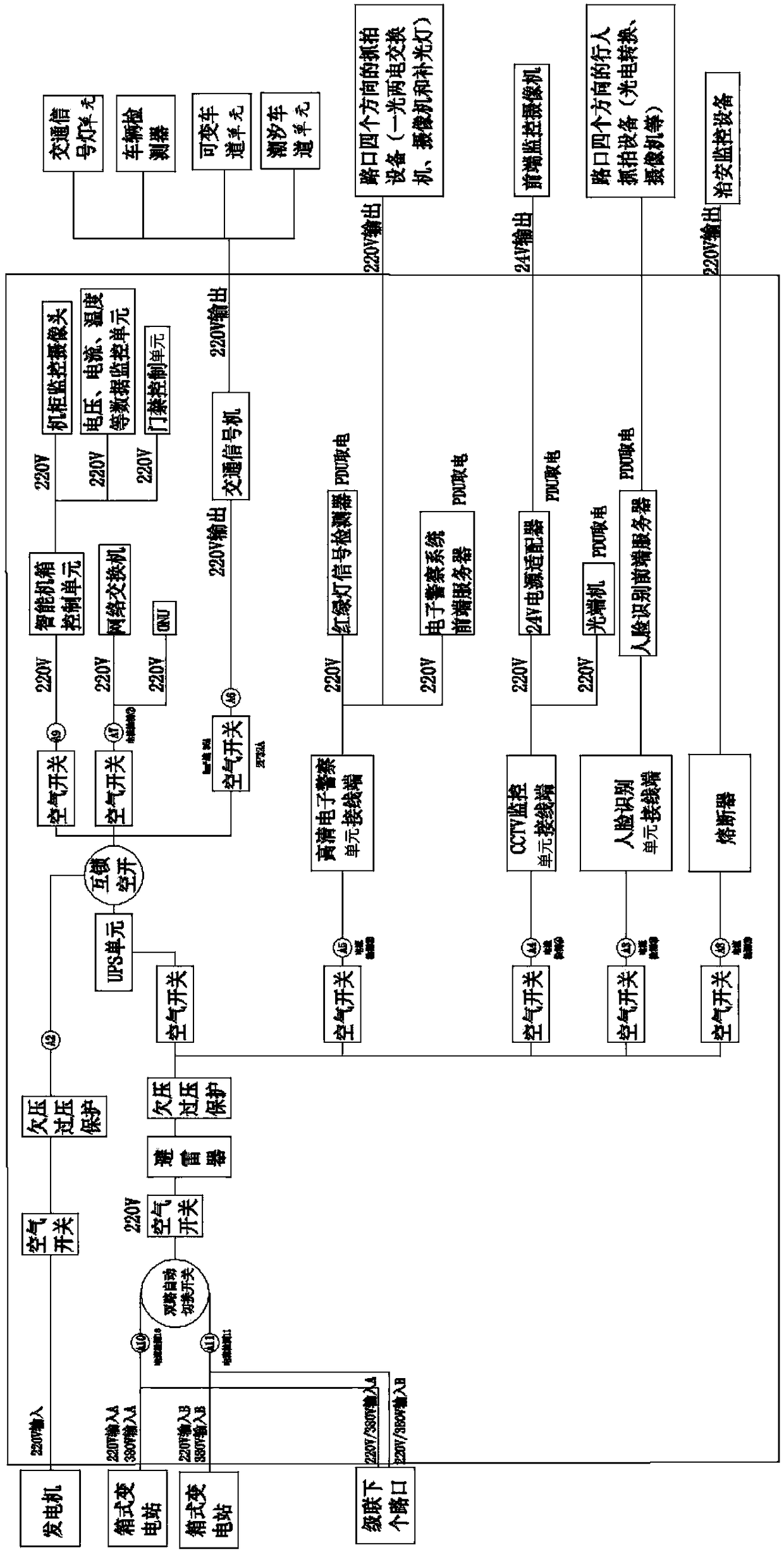
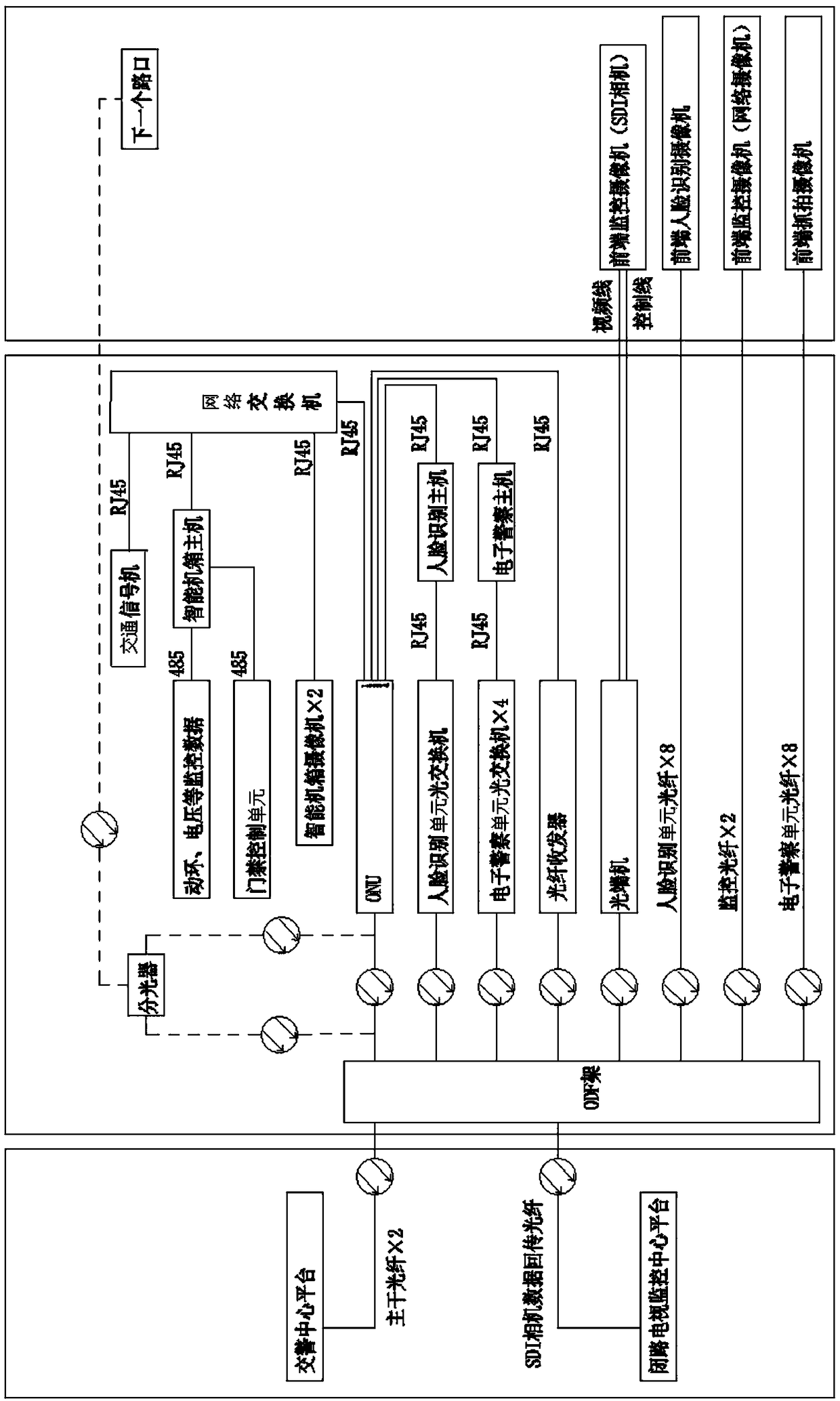
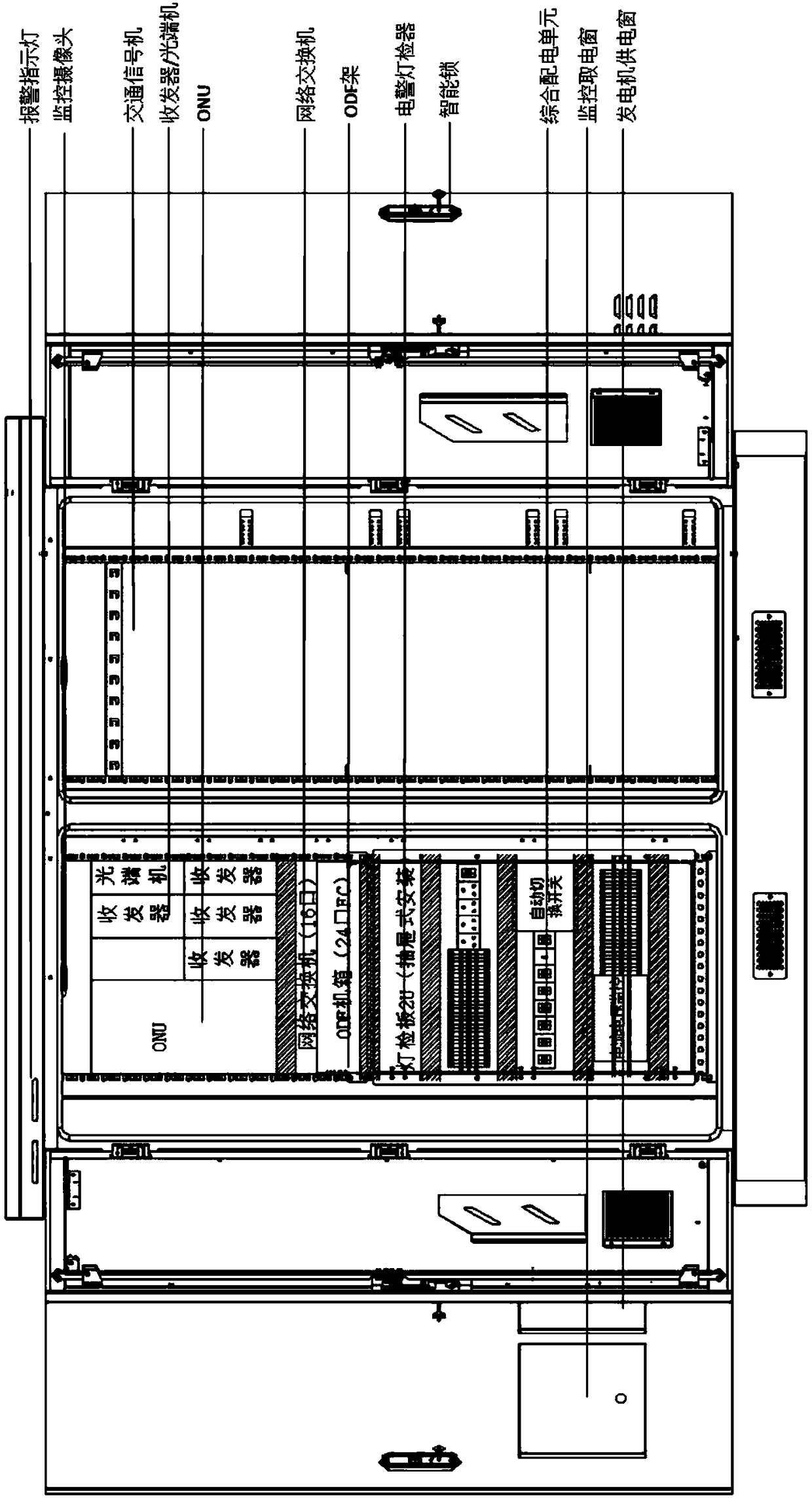
Integrated traffic information comprehensive management and control equipment used for crossroads
ActiveCN108399761AHigh degree of integrationSmall footprintControlling traffic signalsEmergency power supply arrangementsTraffic signalTraffic network
The invention discloses integrated traffic information comprehensive management and control equipment used for crossroads. The equipment comprises a power supply module, a comprehensive information management and control unit, a network transmission module, an equipment box control module and a traffic signal control module; an output end of the power supply module is respectively electrically connected with the comprehensive information management and control unit, the network transmission module, the equipment box control module and the traffic signal control module; the comprehensive information management and control unit is respectively in communication connection with the network transmission module, the equipment box control module and the traffic signal control module. The highly integrated crossing traffic comprehensive management and control equipment is provided, the occupying space is small, the unified management is convenient, the operation management of a front end stand-alone system is achieved, the equipment can access to a central platform according to a communication protocol, and it is convenient for a traffic network system to manage and control a single crossroad.
Owner:深圳市交通科学技术研究所 +1
Embedded file system based on norflash
ActiveCN107908364ASimple formatEasy to understandInput/output to record carriersEmbedded applicationsMemory footprint
The invention discloses an embedded file system based on norflash. The system comprises the following steps that: 1: sector management: each sector contains one piece of sector header information, andthe sector header information comprises a sector state, a sector number id, an erasing frequency, a backup sector id, a backup sector erasing frequency and header structure verification information;and 2: file management: all files and folders are numbered, and file catalogs and files are continuously stored behind the sector header information. By use of the system, the basic requirements of auser for file storage management in a large-sector norflash memory can be easily met in an embedded application. Sector damage can be immediately found when the file is operated, and the sector is dynamically replaced. Memory occupation is small without buffering one sector, sector erasing use is balanced, and requirements on the file system in a small system can be favorably met.
Owner:NO 30 INST OF CHINA ELECTRONIC TECH GRP CORP
Block chain file sharing method and device, storage medium and electronic equipment
PendingCN112100144AImplement rights managementGuaranteed concealmentDatabase distribution/replicationDigital data protectionCryptographic key generationSoftware engineering
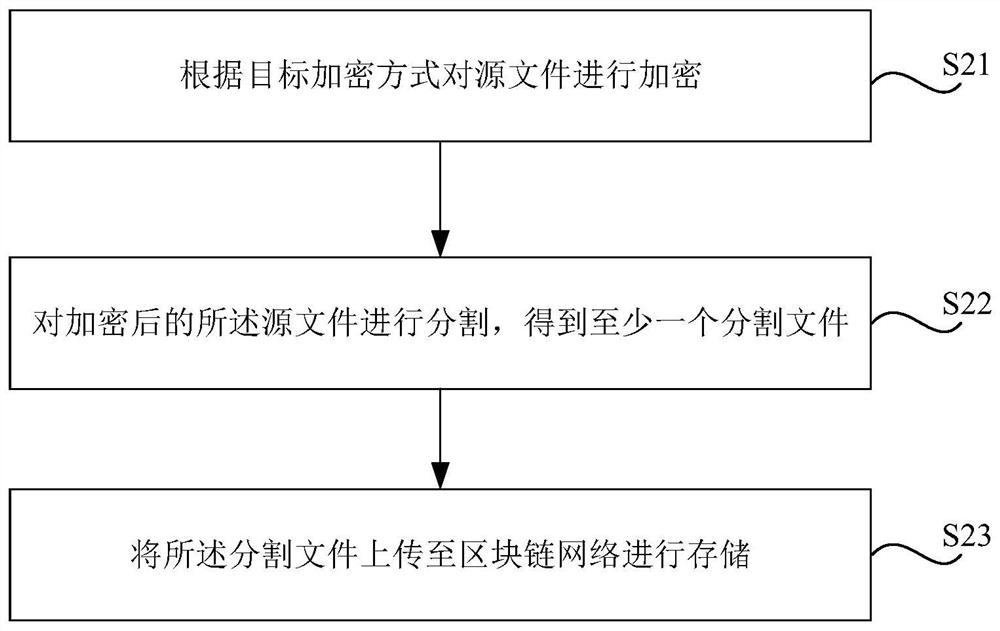
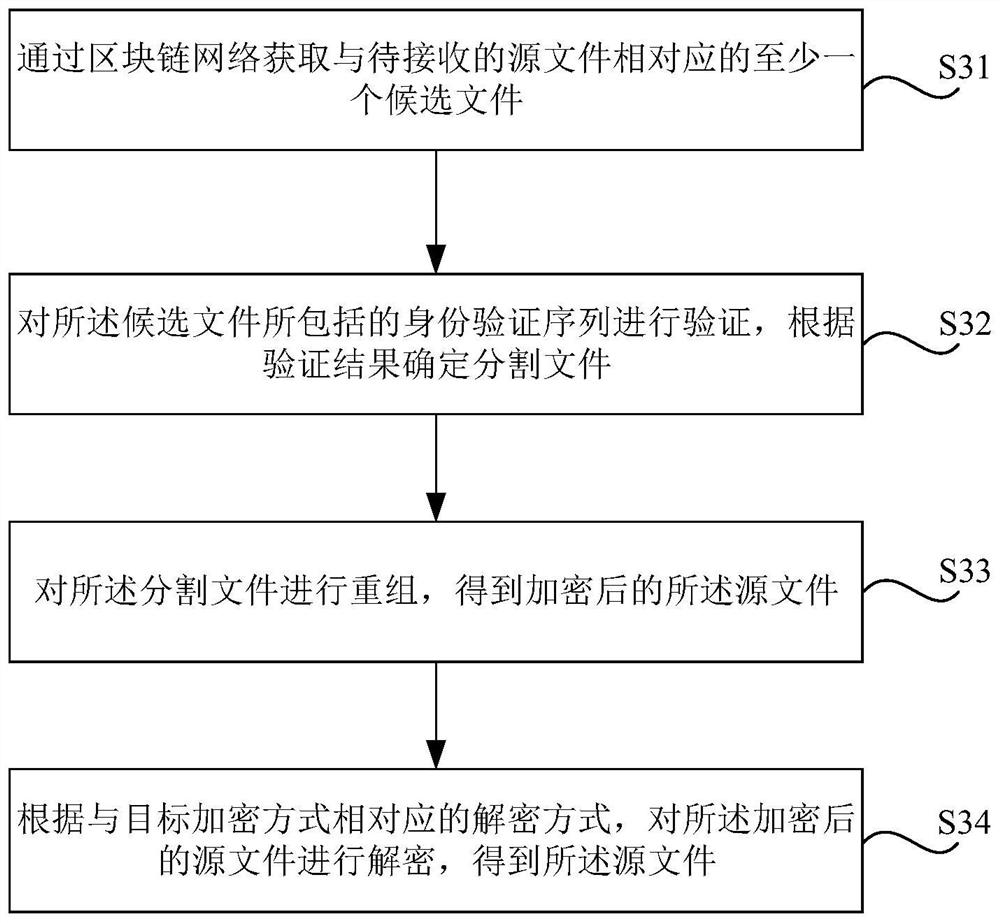
The invention relates to a blockchain file sharing method and device, a storage medium and electronic equipment. The method comprises the steps: encrypting a source file according to a target encryption mode under the condition that the method is applied to a file sender; segmenting the encrypted source file to obtain at least one segmented file; uploading the segmented file to a block chain network for storage, wherein the segmented file comprises an identity verification sequence generated based on an encryption key, the identity verification sequence is used for a file receiver to verify whether the received file is the segmented file or not, and the encryption key is a key used by the target encryption mode. According to the scheme, the file uploaded to the blockchain is encrypted, sothat other blockchain nodes cannot obtain detailed information of the file except the specified file receiver, and authority management of the file on the blockchain is realized.
Owner:NEUSOFT CORP +1
A user data management method and device based on a block chain
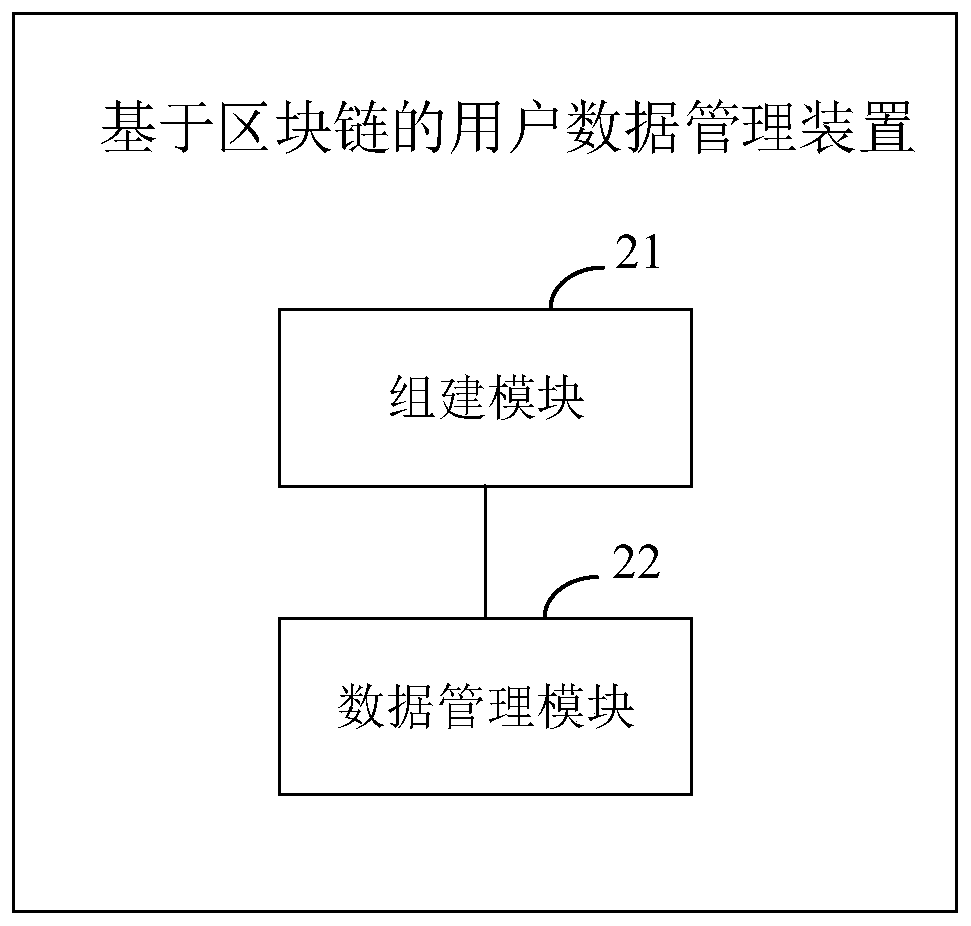
InactiveCN109903046AImplement rights managementAchieve securityPayment protocolsTransmissionTerminal equipmentData management
The embodiment of the invention provides a user data management method and device based on a block chain. The method comprises the steps that a block chain data management system used for user data management is established; Wherein the block chain data management system comprises a user terminal equipment node and a network service provider node; And the user terminal equipment node and each network service provider node realize authority management and security management of the user data through the block chain data management system. According to the embodiment of the invention, authoritymanagement and security management of the user data are realized in a block chain manner.
Owner:CHINA INTERNET NETWORK INFORMATION CENTER
Intelligent material management device
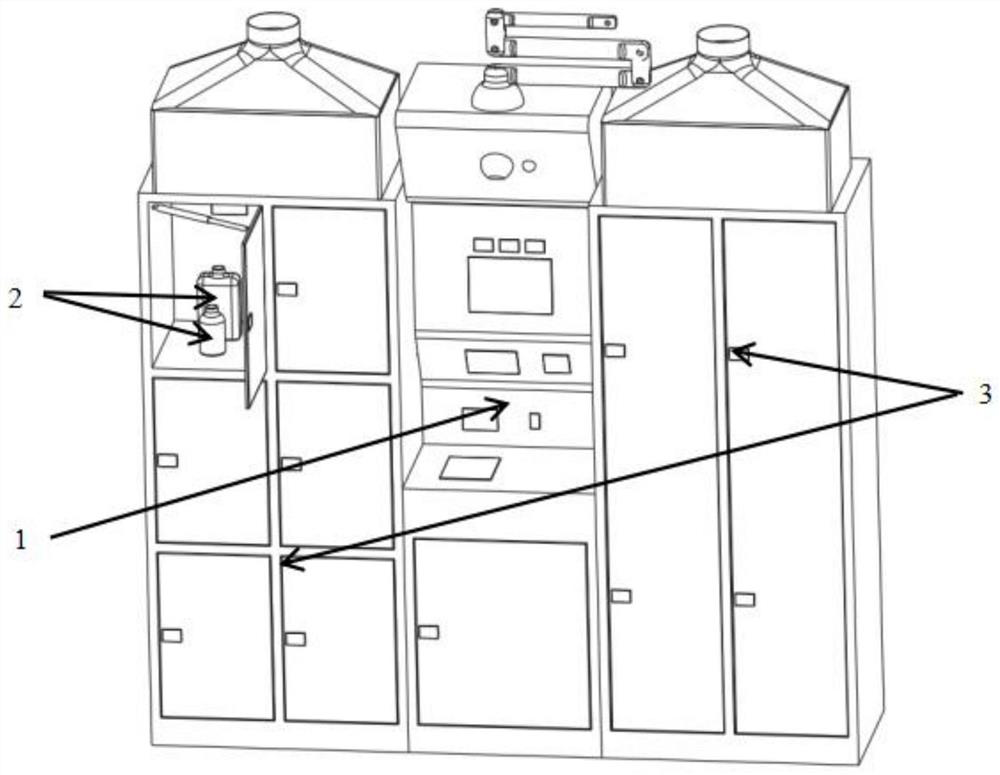
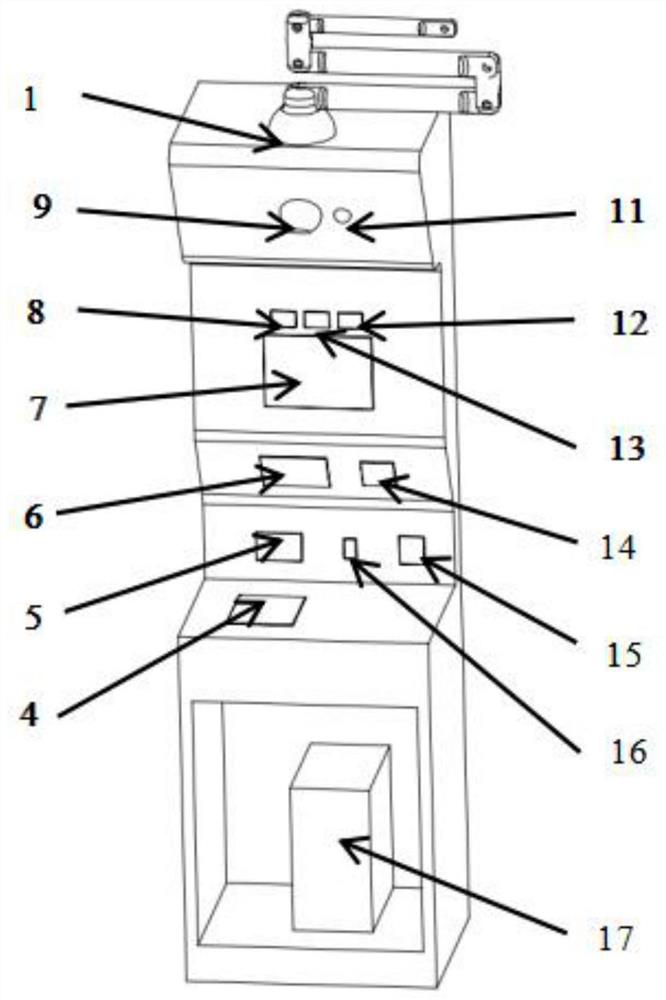
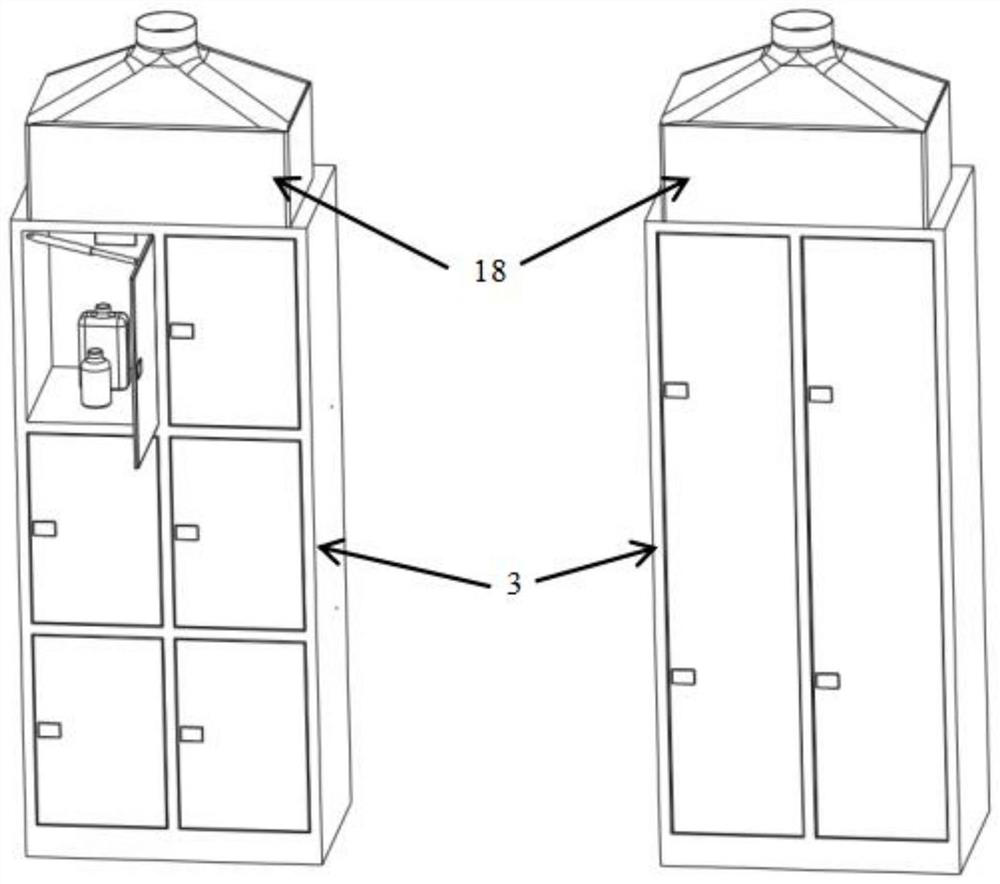
InactiveCN112863071AImplement rights managementReal-time monitoring of storage environmentInput/output for user-computer interactionCo-operative working arrangementsData transmissionCard reader
The invention discloses an intelligent material management device which comprises hardware and software; the hardware comprises a material management platform, a material container and a material storage cabinet, and the material management platform and the material storage cabinet are connected for data transmission and exchange; a precision balance module, an RFID reader-writer module, a control module, a touch display screen module, a face recognition module, a monitoring camera module, an automatic manipulator, a human shape sensing module, a gesture recognition module, a voice recognition module, an audio playing module, an all-purpose card reader-writer module, a fingerprint recognition module and an uninterruptible power supply module are mounted on a shell of the material management platform. The intelligent automatic material management device is easy to operate, the application, the receiving, the returning and the whole storage process of materials are controlled, the operation process and the generated data information are automatically recorded and uploaded to the server, and various alarm information and processing states and results of the alarm information are automatically recorded and tracked.
Owner:上海合极数据科技有限公司
Data display method and device of table component, storage medium and electronic equipment
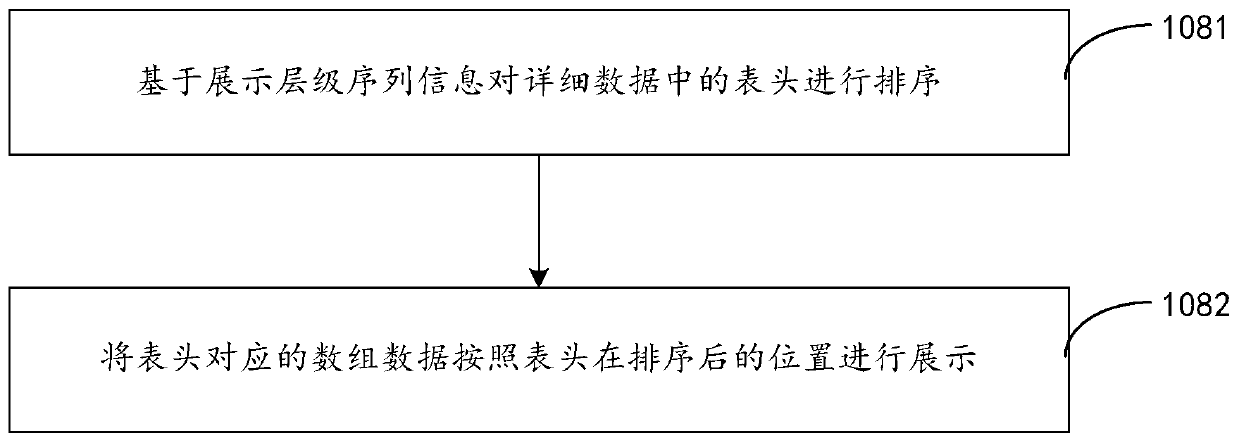
InactiveCN110750581AImplement rights managementEnsure safetyDigital data authenticationSpecial data processing applicationsData displayEngineering
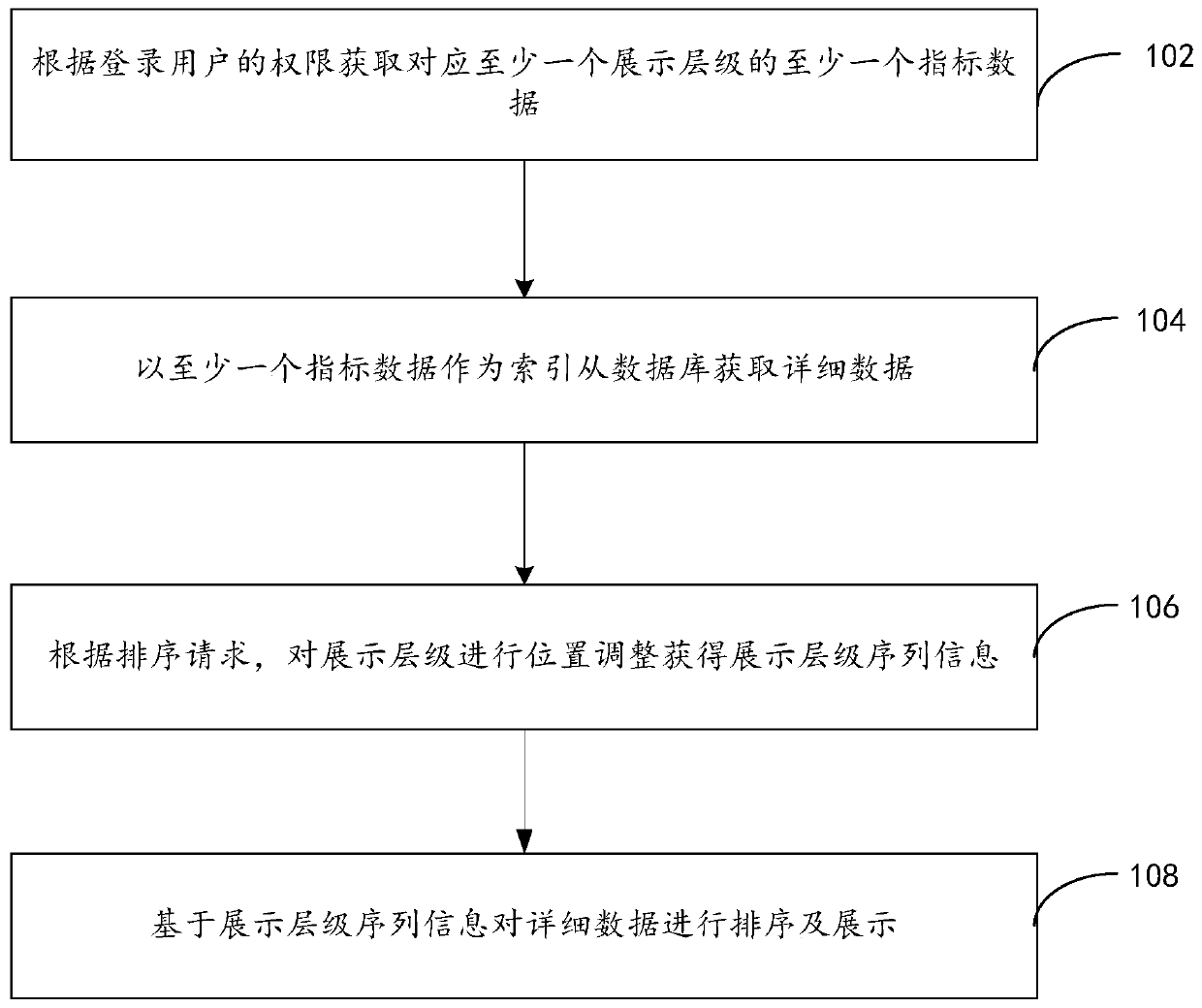
The embodiment of the invention discloses a table component data display method and device of a table component, a storage medium and electronic equipment, and the method comprises the steps: obtaining at least one piece of index data corresponding to at least one display level according to the authority of a login user; wherein each piece of index data corresponds to one display level, and each display level comprises at least one piece of index data; acquiring detailed data from a database by taking the at least one index data as an index; according to the sorting request, performing position adjustment on the display hierarchy to obtain display hierarchy sequence information; sorting and displaying the detailed data based on the display hierarchy sequence information. Aaccording to theembodiment, the corresponding data is obtained according to the authority of the login user, authority management of data display is achieved, the login user can only see the data in the authority ofthe login user, and data safety is guaranteed.
Owner:BEIKE TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com