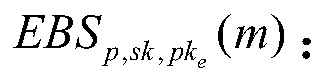Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
38results about How to "Guaranteed transmission security" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Method and device for having access to wireless network
InactiveCN104378801ASimplify the access control processRealize automatic discoveryAssess restrictionNetwork topologiesWireless mesh networkMulticast address
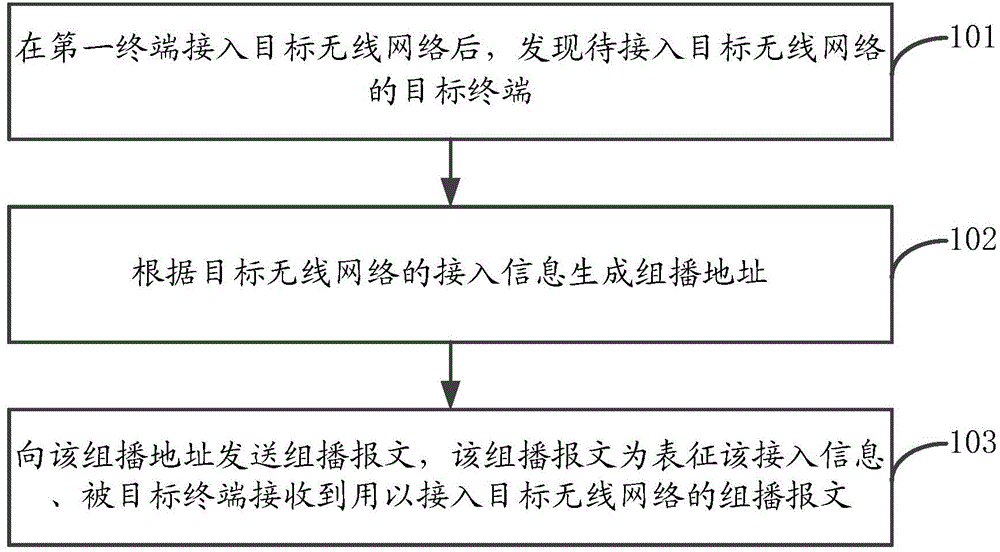
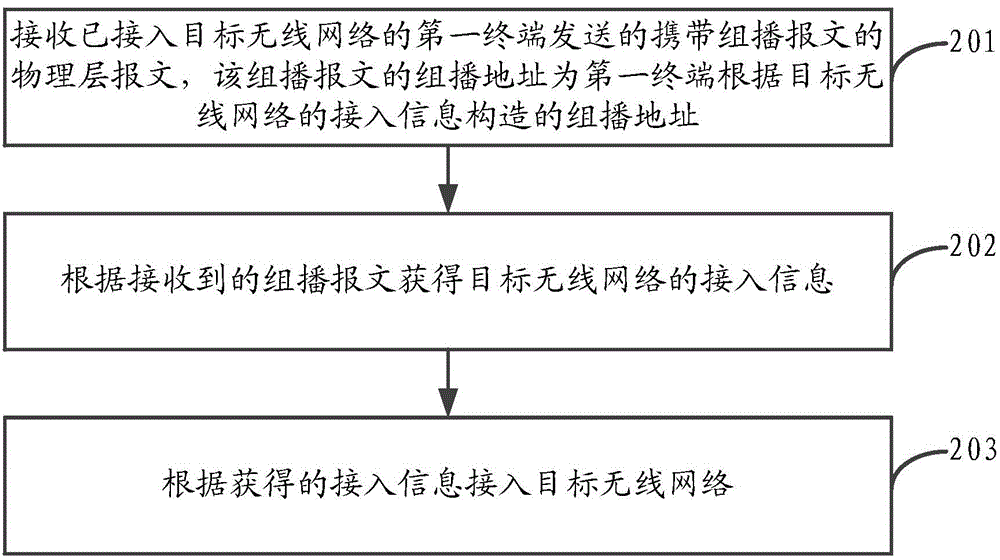
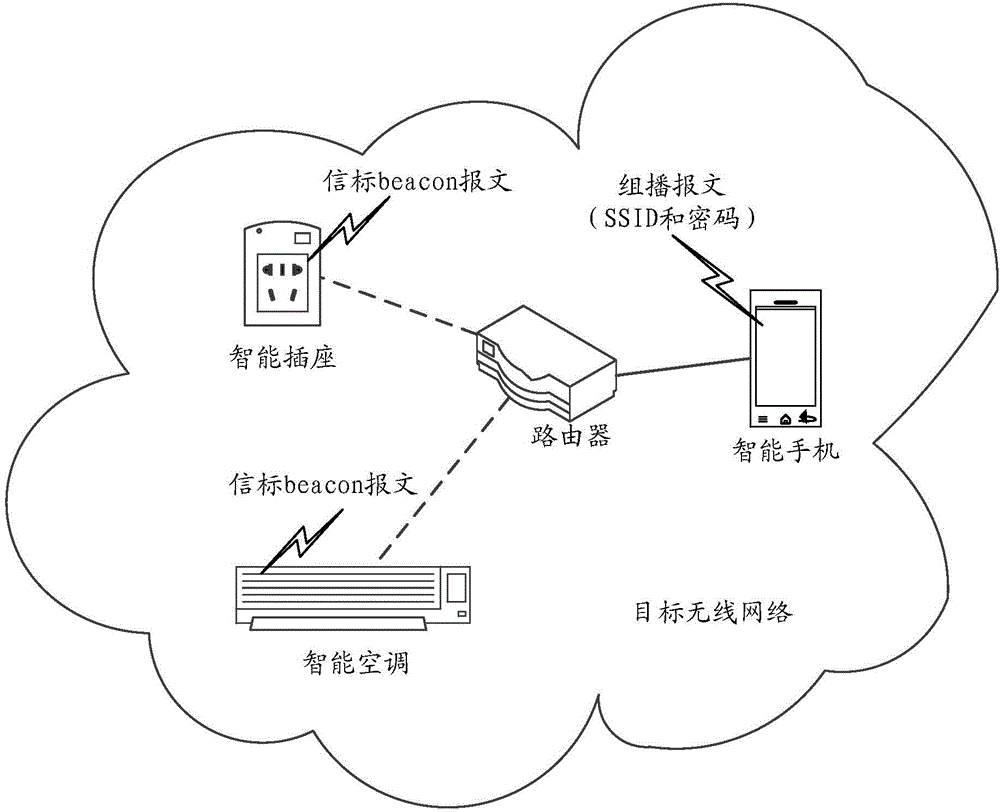
The invention relates to a method and device for having access to a wireless network. The method includes the steps of finding a target terminal which is going to have access to the target wireless network after a first terminal has access to the target wireless network, generating a multicast address according to the access information of the target wireless network, and sending multicast messages to the multicast address, wherein the multicast messages are multicast messages which represent the access information and are received by the target terminal and used for having access to the target wireless network. By means of the method and device, under the condition that the first terminal does not stop the access to the target wireless network, the target terminal can have access to the target wireless network; thus, compared with the related technology where access switching needs to be conducted, the method and device have the advantages that the access control process can be simplified, and the efficiency of the target terminal having access to the target wireless network can be improved.
Owner:XIAOMI INC
Lift remote monitoring and warning system based on radio network
InactiveCN1887674ASolve the need to installSolve the shortcomings of debugging monitoring softwareTransmission systemsRadio transmissionRadio networksWeb browser
The lift remote monitoring and warning system based on radio network includes a lift monitoring system and a radio network communication system. The key technological points of the present invention include that the lift monitoring system with lift controller is connected to the lift monitoring module and the GSM module in the lift monitoring module is connected to the data server in B / S software structure via the radio communication network in USSD transmission mode, and that the lift monitoring system has its monitoring terminal connected to the Internet Web browser. The lift remote monitoring and warning system realizes the monitoring and warning of lift via the Internet, and the advantages of simple site configuration, low cost, fast response speed, convenient data transmission, etc.
Owner:隋舒杰 +1
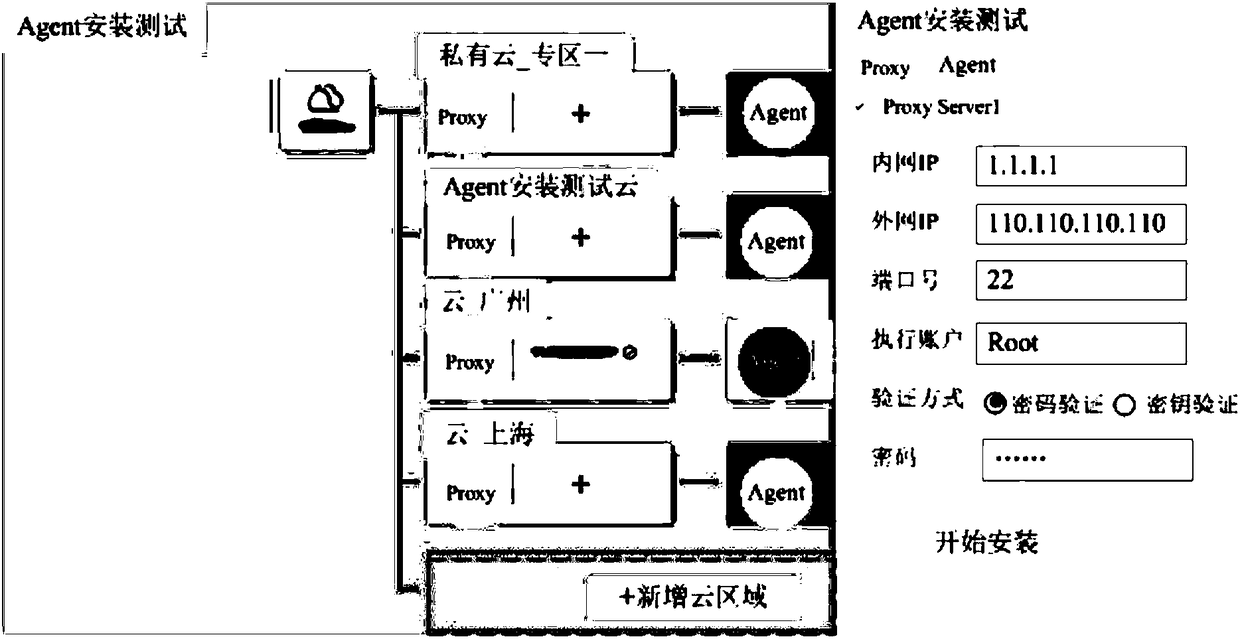
Software cross-cloud deployment method, computer device and storage medium
ActiveCN108509203AImplement automatic deploymentHigh speedTransmissionSoftware deploymentSoftwareCloud deployment
The invention provides a software cross-cloud deployment method, a deployment server and a storage medium. The method comprises the steps of obtaining a software deployment request, wherein the deployment request comprises a target transfer machine identifier, a target machine identifier, a to-be-deployed software installation package and a first check file corresponding to a target machine; sending a connection request to a target transfer machine, wherein the connection request comprises the first check file; receiving a connection response message returned by the target machine; and sendinga deployment instruction to the target transfer machine, wherein the deployment instruction comprises the to-be-deployed software installation package and the target machine identifier. Through the method, automatic deployment of a software installation task can be realized; cross-cloud batch task deployment is facilitated; the task deployment speed and efficiency are improved; and the technicalproblems of complex installation process and poor flexibility in the prior art are solved.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Data access method and equipment adopting same
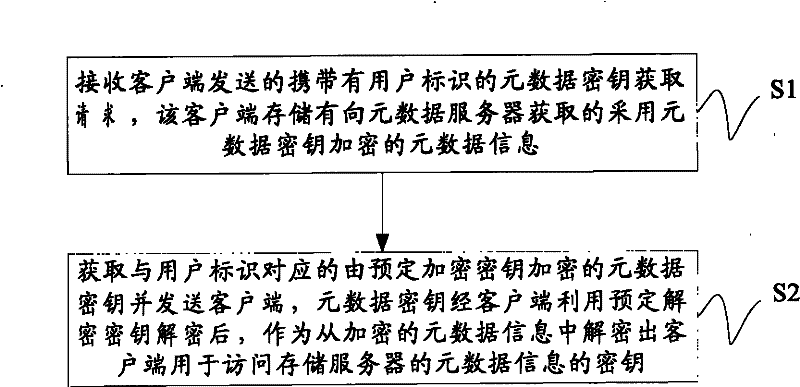
ActiveCN102457561AGuaranteed transmission securityPublic key for secure communicationUser identity/authority verificationAccess methodData access
The invention discloses a data access method and equipment adopting the same. In the data access method disclosed by the invention, metadata information is encryption information; when accessing a storage server according to the metadata information, a client side needs to acquire a metadata key according to user identification, and obtain the metadata information by decrypting the encryption information according to the key, therefore, an unauthorized client side can not obtain the metadata key according to the user identification, further the metadata information can not be decrypted, and then the phenomenon that an unauthorized client side accesses a metadata server to acquire metadata information and then accesses the storage server through the metadata information can be avoided.
Owner:JIANGNAN INST OF COMPUTING TECH
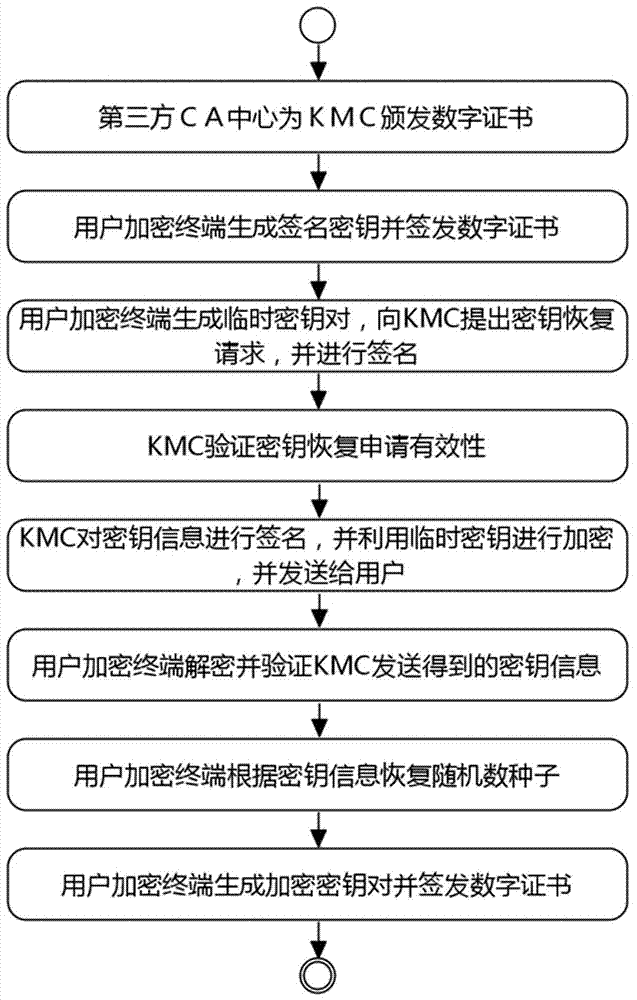
Multi-KMC key recovery method
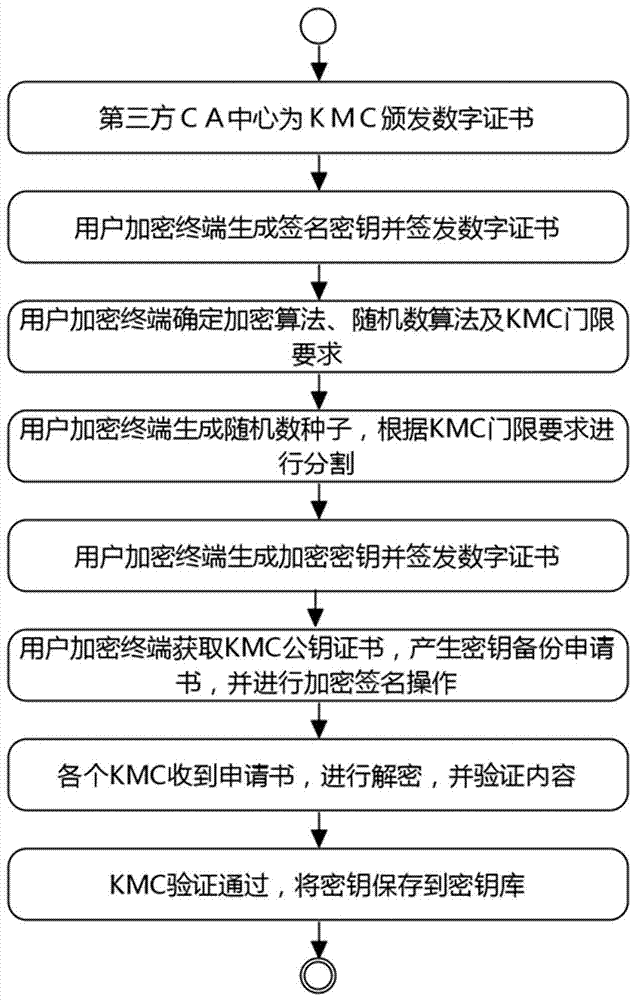
InactiveCN107171796AGuaranteed StrengthSimplify complexityKey distribution for secure communicationUser identity/authority verificationThird partyTransmission security
The invention discloses a multi-KMC key recovery method. The method is realized through two parts including key backup and key recovery, wherein the key backup comprises the following steps of making a third-party CA center issue a digital certificate to each participator, utilizing a user encryption terminal to generate random numbers, utilizes a threshold algorithm to carry out partitioning on a key according to the set KMC threshold number, signing the divided random numbers, utilizing a public key of each KMC to encrypt and uploading to the KMC to carry out key backup; the key recovery comprises the following steps of making a key request for the corresponding KMC according to the KMC threshold number and recovering the key from the user encryption terminal. The method has the following characteristics that 1) the generation intensity of the random numbers is guaranteed and the operation complexity is simplified; 2) even if the part of KMC is broken, the key cannot be leaked, and even if the part of KMC is destroyed, the recovery of the backup key can be also guaranteed; and 3) the security of the encryption key is guaranteed and the key transmission security is also guaranteed.
Owner:JINAN INSPUR HIGH TECH TECH DEV CO LTD
High safety communication technology based on two-way time domain waveform aliasing
InactiveCN103428124AImprove transmission securityEnsure transmission securityTransmitter/receiver shaping networksSecure communicationInformation transmission
The invention discloses a high safety communication technology based on two-way time domain waveform aliasing and belongs to the technical field of communication. The existing local signals of two communication parties are fully utilized to perform aliasing and covering on each other's signals. The two communication parties transmit and receive mixed signals. Each communication party receives and separates the signals of the other party and allows the same to be mixed with local signals for transmission. The cooperating parties can separate the signals by using local signals and waveform reconstruction offset to complete normal communication. Non-cooperating parties do not know signal samples of the cooperating parties, the mixed signals cannot be separated, and information transmission safety is guaranteed. The method aiming at the situation that communication information safety faces increasingly large threats has the advantages that the signals transmitted in channels are mixed by two signals, safety communication of the whole communication process can be achieved, and no extra communication bandwidth is needed.
Owner:中国人民解放军总参谋部第五十七研究所
Mobile terminal and method for safely sharing picture
InactiveCN106453056AEnsure safetyImprove securitySubstation equipmentData switching networksMemory cardsComputer terminal
The invention provides a method for safely sharing a picture. The method comprises the following steps: acquiring a picture resource; acquiring a sharing mode corresponding to the picture resource, wherein the sharing mode comprises a first safe mode and a second safe mode, the first safe mode is used for saving the acquired picture resource in a hidden directory of a memory card, and the second safe mode is used for encrypting the acquired picture resource to obtain the encrypted picture, sharing the encrypted picture and deleting the acquired picture resource; and processing the acquired picture resource according to the acquired sharing mode. The invention further provides a mobile terminal. Through the adoption of the mobile terminal and the method for safely sharing the picture provided by the invention, a plurality of safe modes for picture sharing are set to prevent other people from stealing the picture uploaded by the user through a network, the security of the picture sharing is improved, the picture laboriously conceived and creatively photographed by the user cannot be stolen by other people.
Owner:NUBIA TECHNOLOGY CO LTD
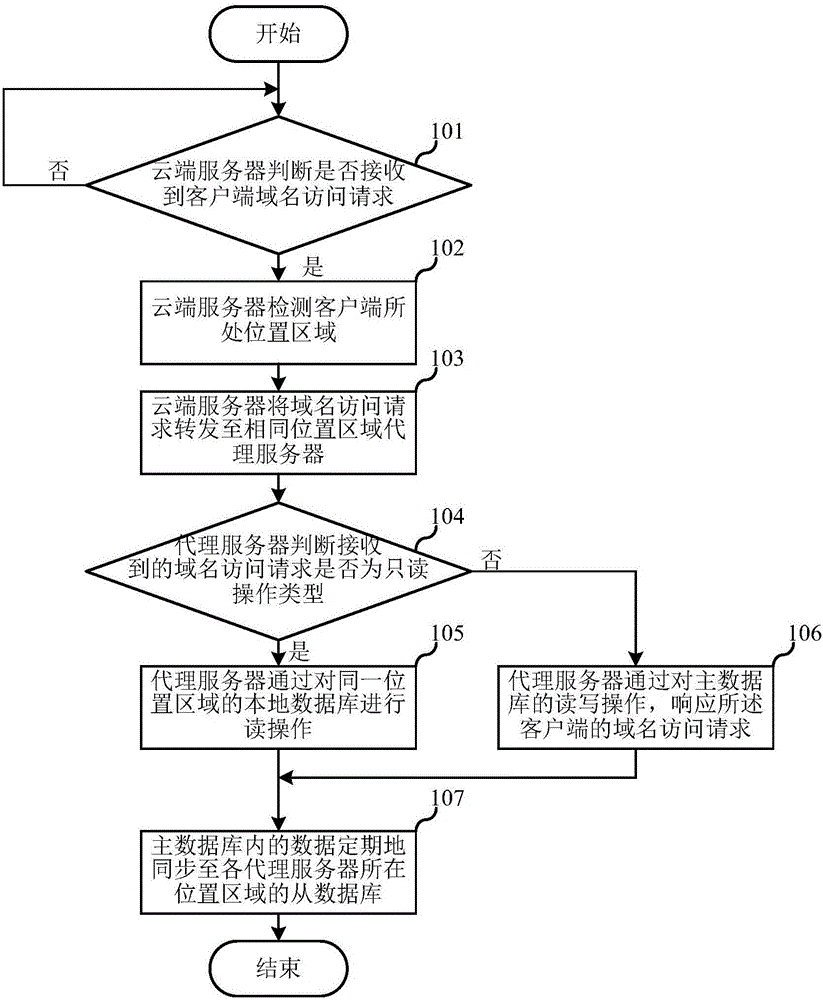
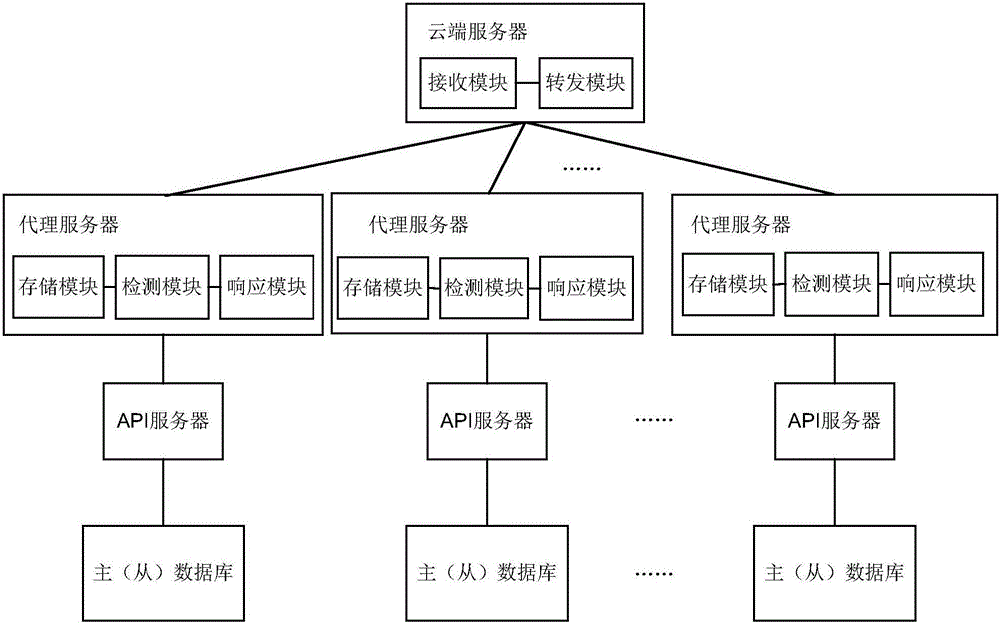
Multi-database data access method and system and proxy server
The invention relates to the field of information technologies and communication, and discloses a multi-database data access method and system and a proxy server. The multi-database data access method disclosed by the invention comprises the following steps that: access requests to various domain names are divided into a read operation type and a write operation type in advance; the proxy server, which is in the same position area with a client side initiating a domain name access request, detects the operation type of the domain name access request according to the domain name access request of the client side; if the operation type of the domain name access request is the read operation type, the proxy server responds to the domain name access request of the client side through read operation of a local database in the same position area; if the operation type of the domain name access request is the write operation type, the proxy server responds to the domain name access request of the client side through read and write operation of a master database; and data in the master database is regularly synchronized to a slave database in the position area, where various proxy servers are. Compared with the prior art, the read-only operation response speed of the databases is ensured; and furthermore, the database synchronization robustness is ensured.
Owner:LETV HLDG BEIJING CO LTD +1
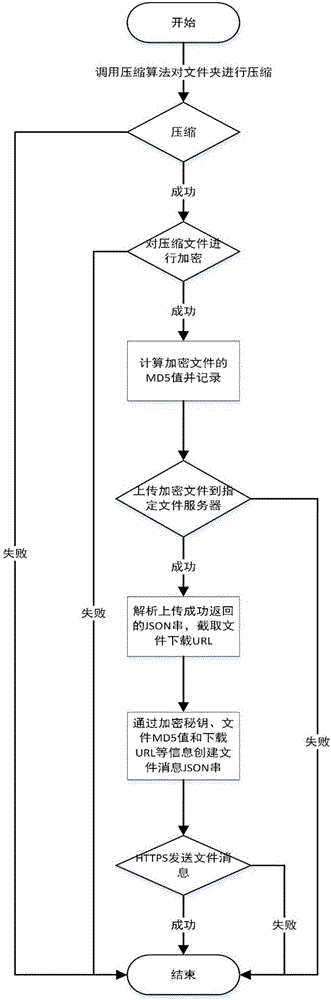
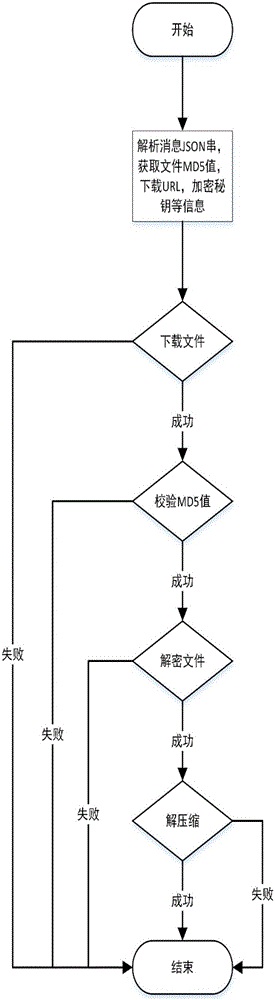
File transfer method based on file mapping encryption
InactiveCN106254336AImprove transmission efficiencyGuaranteed transmission securityUser identity/authority verificationComputer hardwareHypertext Transfer Protocol over Secure Socket Layer
The invention discloses a file transfer method based on file mapping encryption. The file transfer method comprises the steps of: (1) compressing a file to be transferred; (2) subjecting the compressed file to binary encryption; (3) calculating and recording an MD5 value of the encrypted file; (4) uploading the encrypted file to a specified file server; (5) parsing a JSON string returned after successful upload, and intercepting a URL for file download; (6) creating a file message and a JSON string on the basis of a secret key encrypted in the step (2), the MD5 value obtained in the step (3) and the URL obtained in the step (5); (7) and sending the file message and the JSON string thereof by means of HTTPS. The file transfer method has the advantages of adopting a powerful compression algorithm, satisfying high compression of large files, providing an efficient transferring speed, ensuring security in the file transfer process by encrypting the file, and effectively guaranteeing transfer security of users.
Owner:BEIJING VRV SOFTWARE CO LTD
Encrypted blind signature method based on quantum secret communication technology
PendingCN110601822ASolve reversible problemsSolve secure transmissionKey distribution for secure communicationUser identity/authority verificationObfuscationDistribution system
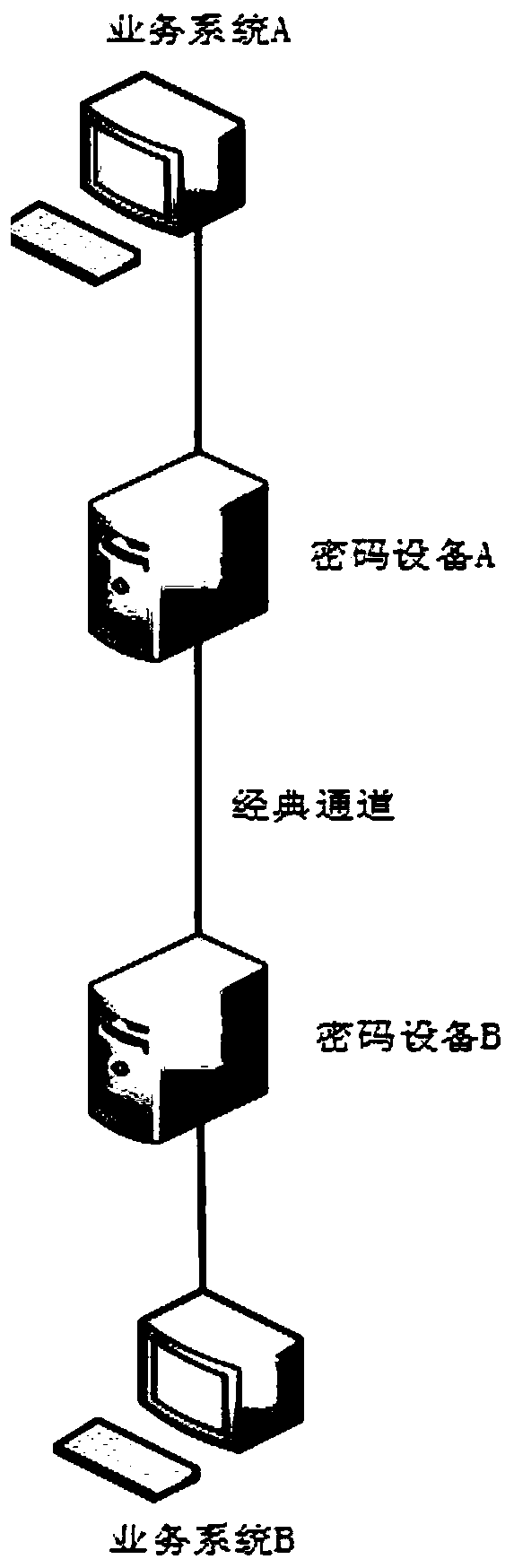
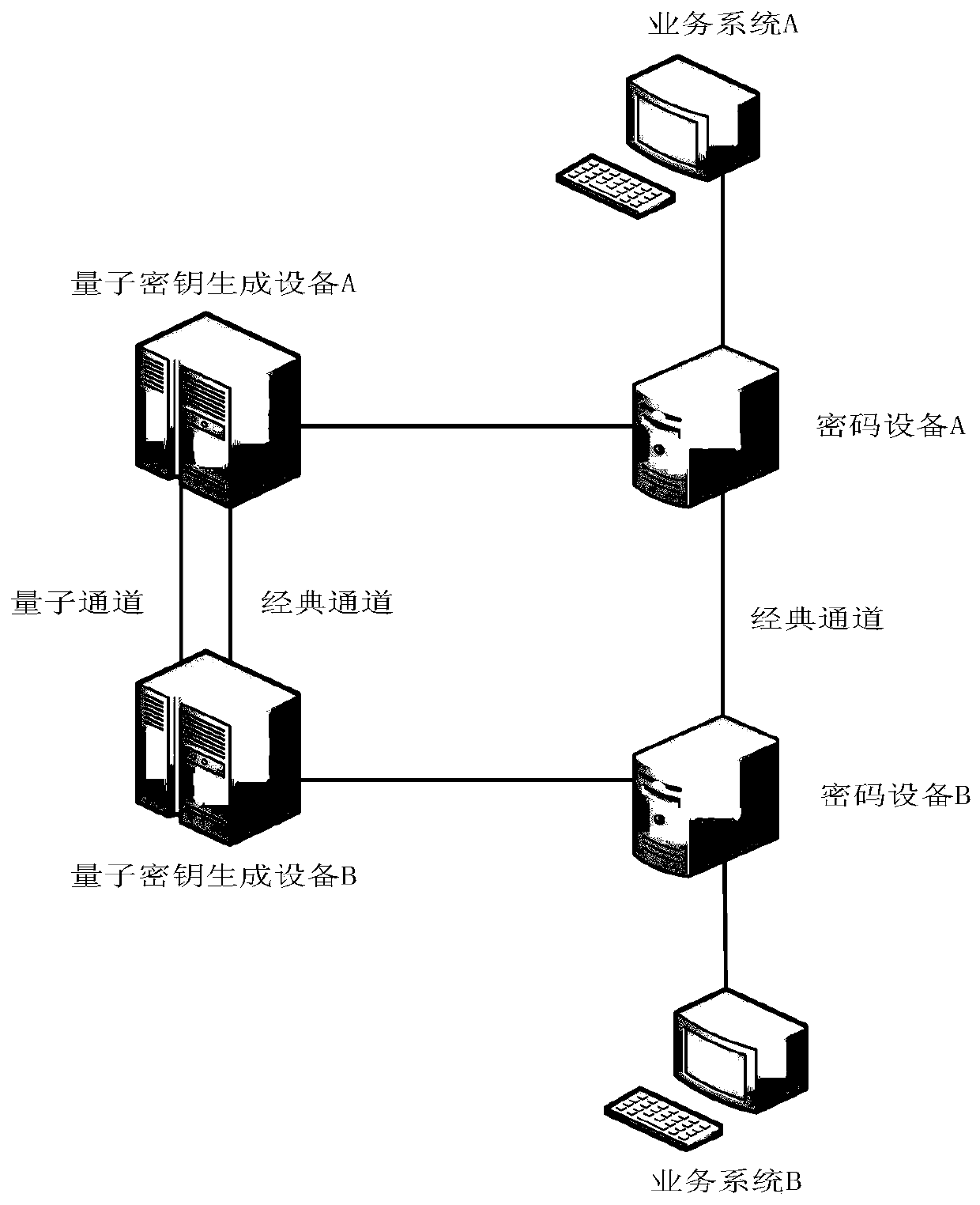
The invention discloses an encrypted blind signature method based on a quantum secret communication technology. According to the method, the encrypted blind signature function is obfuscated by adopting an obfuscation technology, so that the code of the code obtained by reverse engineering of an enemy is an obfuscated code, the blindness and the one-mcore unforgeability under the encrypted blind signature obfuscator are proposed, and a source program is prevented from being obtained by a user or an unauthorized user. Then, in the protocol interaction process, a cooperation mode of a quantum keygeneration device and an encryption device is adopted, and the transmission security is ensured through a quantum key security distribution system of the quantum key generation device.
Owner:STATE GRID CORP OF CHINA +4
Monitoring video encryption transmission method, device, equipment and medium
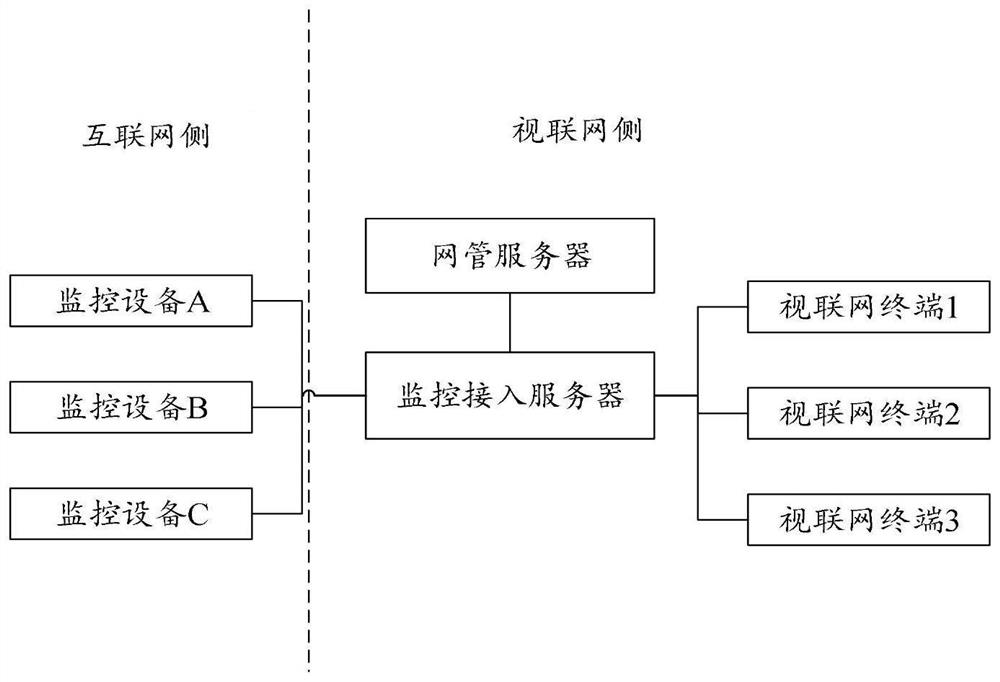
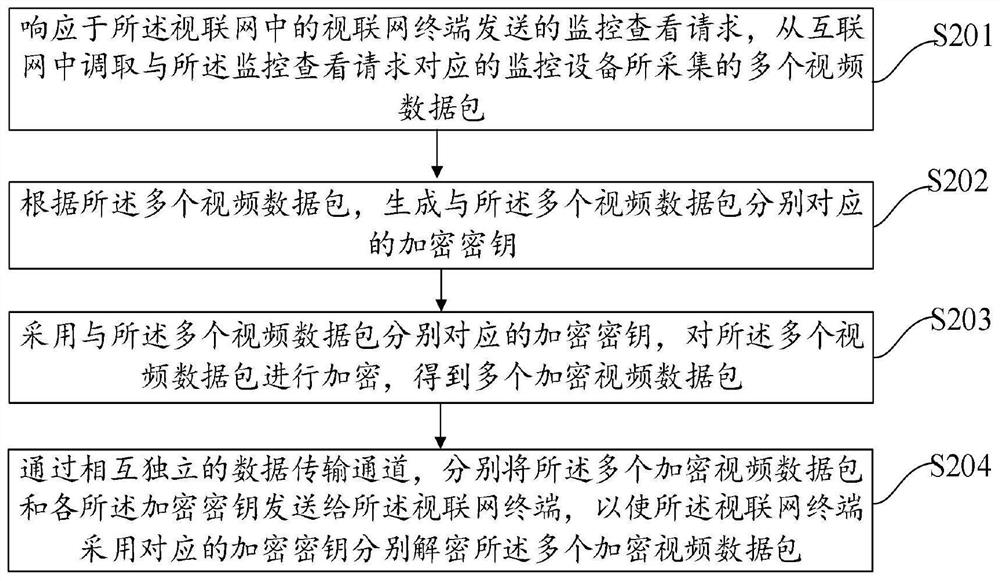
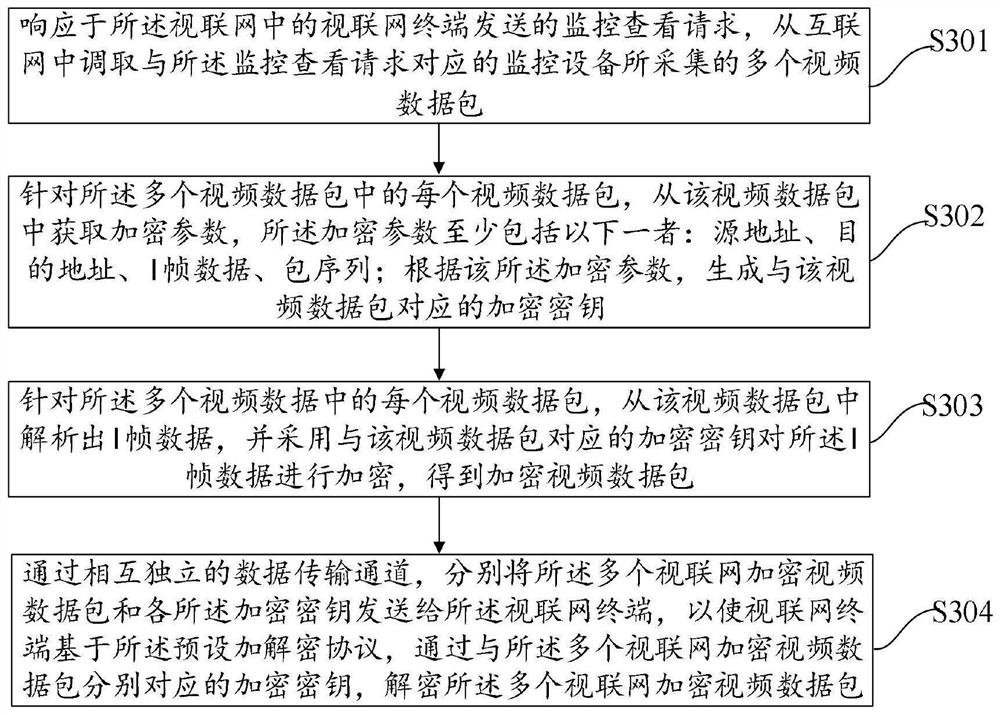
PendingCN111953656AGuaranteed transmission securityEnsure safetyMultiple keys/algorithms usageData packThe Internet
The embodiment of the invention provides a monitoring video encryption transmission method and device, electronic equipment and a storage medium, and is applied to a monitoring access server in the articulated naturality web, and the method comprises the steps: responding to a monitoring check request transmitted by an articulated naturality web terminal in the articulated naturality web, callinga plurality of video data packets acquired by monitoring equipment corresponding to the monitoring check request from the Internet; generating encryption keys respectively corresponding to the plurality of video data packets according to the plurality of video data packets; encrypting the plurality of video data packets by adopting encryption keys respectively corresponding to the plurality of video data packets to obtain a plurality of encrypted video data packets; and respectively sending the plurality of encrypted video data packets and each encryption key to the articulated naturality webterminal through mutually independent data transmission channels, so that the articulated naturality web terminal respectively decrypts the plurality of encrypted video data packets by adopting the corresponding encryption keys. By adopting the technical scheme of the invention, the security of calling the monitoring video from the Internet can be improved.
Owner:VISIONVERA INFORMATION TECH CO LTD
Data acquisition device and data acquisition method
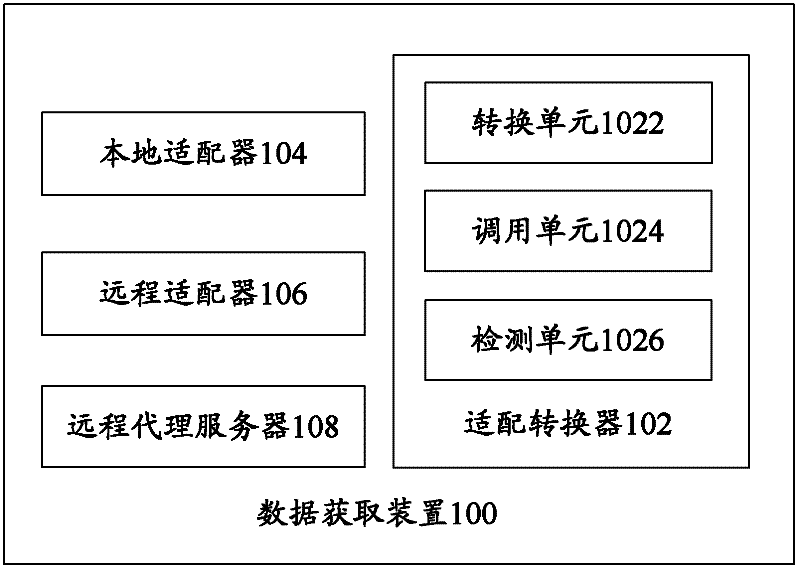
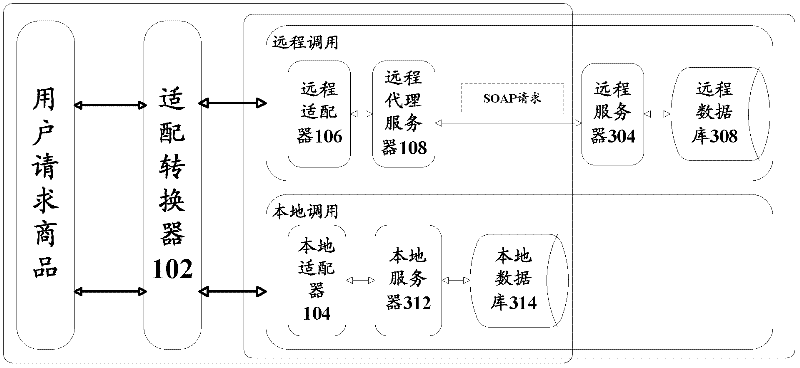
ActiveCN102571777AImprove transmission efficiencyGuaranteed transmission securityData switching networksMarketingData acquisitionSystem pressure
The invention provides a data acquisition device for acquiring needed data from a heterogeneous system, which comprises an adaptor that comprises a conversion unit and an invoking unit. The conversion unit converts the identifier of the needed data received and transfers the identifier to the invoking unit to meet the data format request of the heterogeneous system, receives a retrieval result from a local server or a remote server, and converts the retrieval result and feeds the retrieval result to a client. The invoking unit is used to invoke the local server, and retrieves in a local database according to the converted identifier. If the local server does not retrieve the needed data, the remote server is invoked, retrieves in a remote data according to the converted identifier and transfers the retrieval result to the conversion unit. The invention further provides a data acquisition method that can improve the transfer efficiency of data and relieve the system pressure on the basis of guaranteeing the data transfer safety.
Owner:CHANJET INFORMATION TECH CO LTD
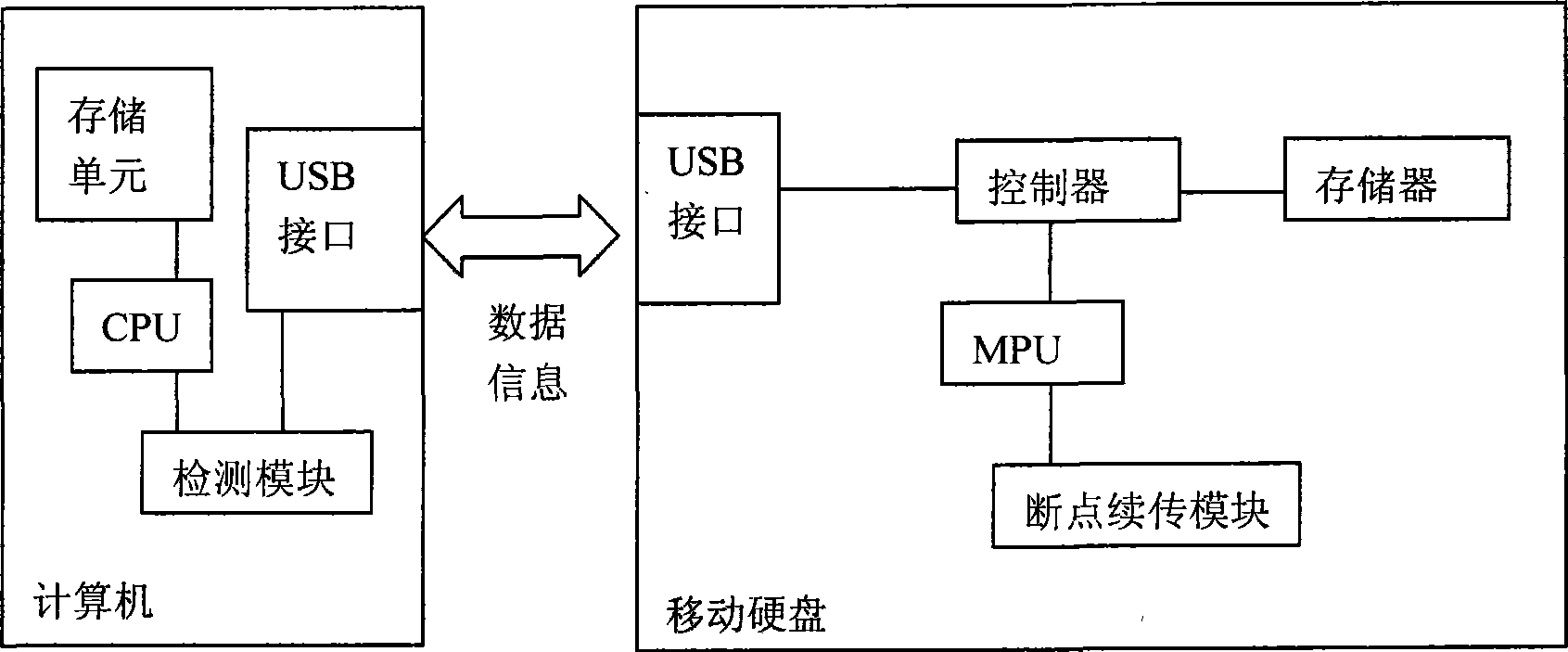
Mobile storage equipment with breakpoint continuous transmission
ActiveCN101546251AGuaranteed transmission securityIntegrity guaranteedInput/output to record carriersSpecial data processing applicationsRemovable mediaMicroprocessor
The invention relates to mobile storage equipment with breakpoint continuous transmission, which comprises an interface for interchanging data with peripheral equipment, a controller connected with the interface, a memory connected with the controller, and a microprocessor connected with the controller. The mobile storage equipment also comprises a breakpoint continuous transmission module connected with the microprocessor and a detection module connected with the microprocessor and used for detecting file situations. The breakpoint continuous transmission module is connected with the controller and is used for adding running marks for the transmitted data, and the running marks are the marks sequentially added into the file data at regular intervals.
Owner:AIGO ELECTRONICS TECH
Network security authentication and data protection device using Beidou communication satellite
PendingCN106656486ANovel structural designImprove reliabilityKey distribution for secure communicationRadio transmissionNetwork communicationEncryption
The invention discloses a network security authentication and data protection device using the Beidou communication satellite. The device comprises a host, a display screen and an alarm indicator lamp are arranged on the host, a Beidou antenna is arranged at the upper end of the host, an RJ45 network interface is formed in one side of the host, a core circuit board is arranged in the host, an intelligent processing chip, a network communication module, an alarm module, a display module, an SAM security module, a security storage module and a Beidou RD / RN communication module are arranged on the core circuit board, and the network security authentication and data protection device disclosed by the invention has the advantages of having a novel structure design, and being able to greatly improve the reliability and security of the network security authentication technology and data encryption protection.
Owner:BEIJING DINGHE SIRUI SOFTWARE TECH CO LTD
Encryption transmission method for Internet of Things security based on quantum random numbers
InactiveCN110190952AGuaranteed transmission securityLower performance requirementsKey distribution for secure communicationUser identity/authority verificationArray data structureThe Internet
The invention relates to the technical field of Internet of Things transmission, in particular to an encryption transmission method for Internet of Things security based on a quantum random number, which comprises the following steps of: 1, a random number generated by a quantum true random number generator is taken as a cipher book, and the same identification code for the cipher book is stored at a hardware end and a server end; 2, after receiving the verification request, the server obtains two groups of cipher book subscript random number sequences from the quantum true random number generator; step 3, the hardware end replces the two groups of cipher book subscript random number sequences with an encryption key and a serial number query key according to the array subscript of the cipher book; 4, when the data is sent, the sending end encrypts the transmission data channel; the receiving end decrypts the received data; and 5, if the transmission sequence number does not correspondto the server, the transmission sequence number is re-acquired through the sequence number query key. According to the encryption transmission method for the Internet of Things security based on the quantum random number, the transmission security of the Internet of Things can be ensured, the performance requirement on an MCU is reduced, and the power consumption requirement is reduced.
Owner:浙江神州量子通信技术有限公司
Service request transmission method and device, and electronic equipment
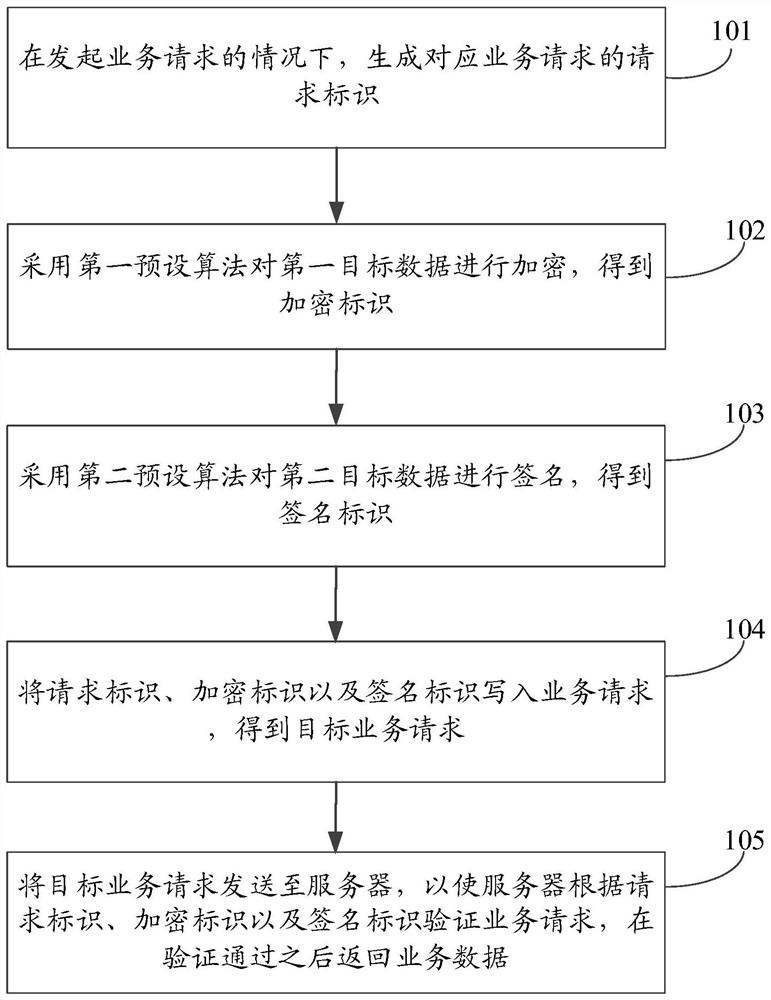
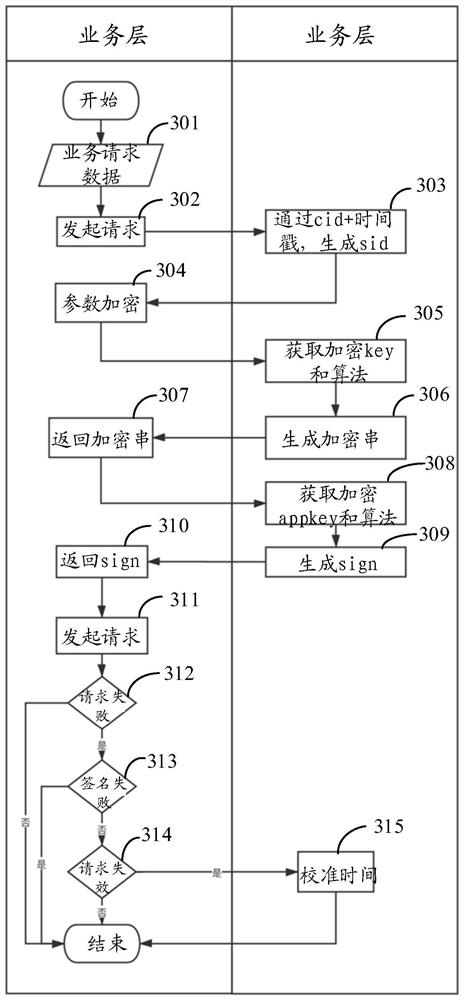
ActiveCN112291201AIncrease the difficulty of crackingAvoid possible problems in the encryption and decryption processTransmissionEngineeringEncryption decryption
The embodiment of the invention provides a service request transmission method and device and electronic equipment. The method is applied to a client, and comprises the following steps: generating a request identifier corresponding to a service request under the condition of initiating the service request; encrypting the first target data by adopting a first preset algorithm to obtain an encryptedidentifier; signing the second target data by adopting a second preset algorithm to obtain a signature identifier; writing the request identifier, the encryption identifier and the signature identifier into the service request to obtain a target service request; and sending the target service request to a server. In the embodiment of the invention, in the process of transmitting the service request, the request parameter does not need to be encrypted. And meanwhile, adding the request identifier, the encryption identifier and the signature identifier into the service request for the server toverify the service request. And possible problems of the request parameters in the encryption and decryption process are avoided.
Owner:BEIJING 58 INFORMATION TTECH CO LTD
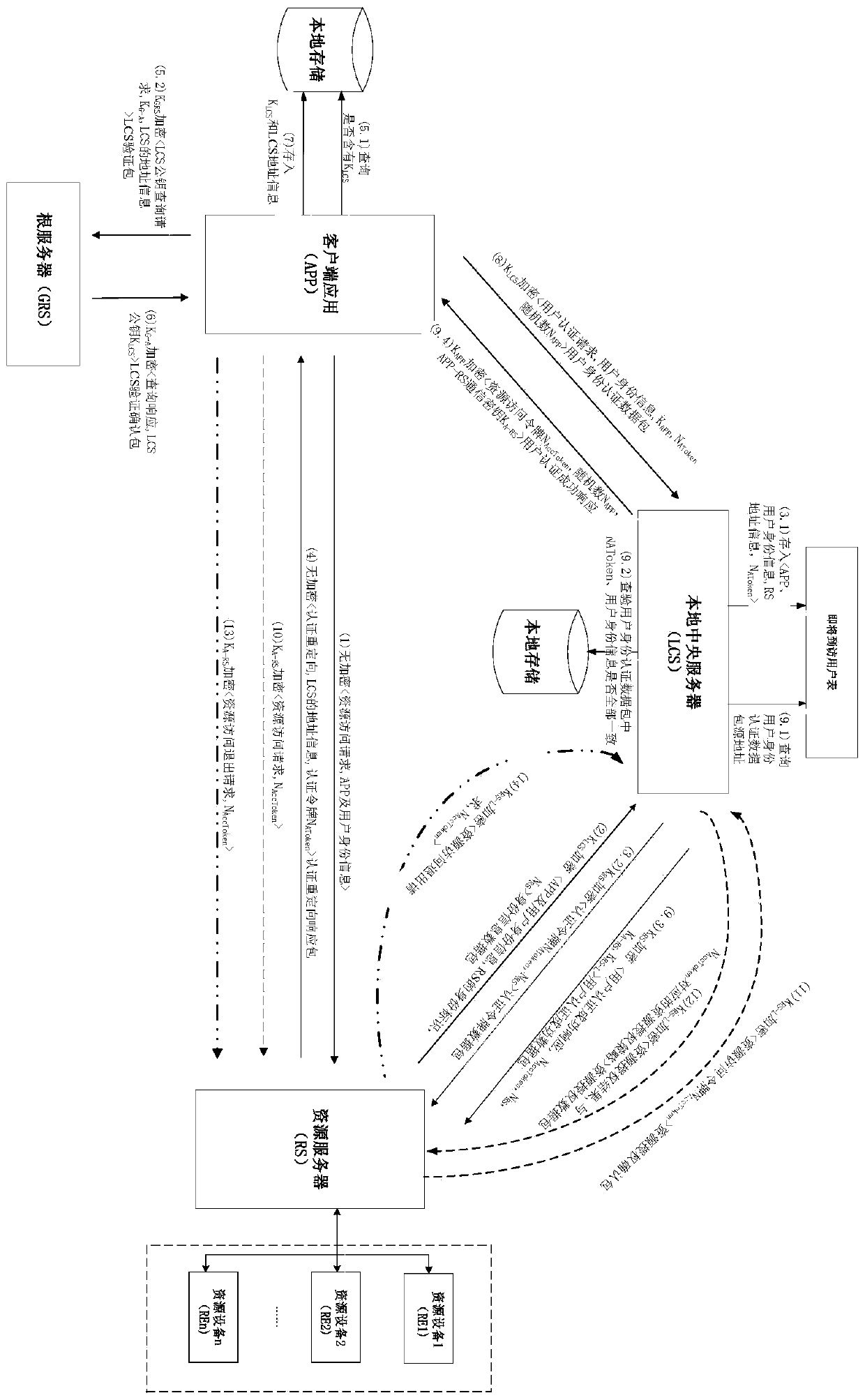
Lightweight certificateless industrial Internet of Things access control method and system
ActiveCN111526130AAlleviate resource pressureGuaranteed transmission securityKey distribution for secure communicationUser identity/authority verificationEngineeringIndustrial Internet
The invention discloses a lightweight certificateless industrial Internet of Things access control method and system. According to the method, a local central server responsible for authorization carries out identity authentication on two parties according to an OAuth thought; different from ACE-OAuth, traditional (such as certificate-based) communication key negotiation needs to be carried out before authentication. According to the method, a local server is used as a trusted third party; two-way authentication between a user and a resource server is realized by using challenge response basedon a public key, a token and a password; communication key negotiation is integrated into an authentication process; the resource server does not need to distribute, receive and verify certificates while the security is ensured; the number of interactive rounds in the authentication process can be effectively reduced, then the communication data transmission amount and the key negotiation calculation consumption including CPU occupation, disk occupation, memory occupation and the like are effectively reduced, and the method is more dominant in safety and practicability and is more suitable for resource-limited environments such as the industrial Internet of Things.
Owner:HANGZHOU DIANZI UNIV
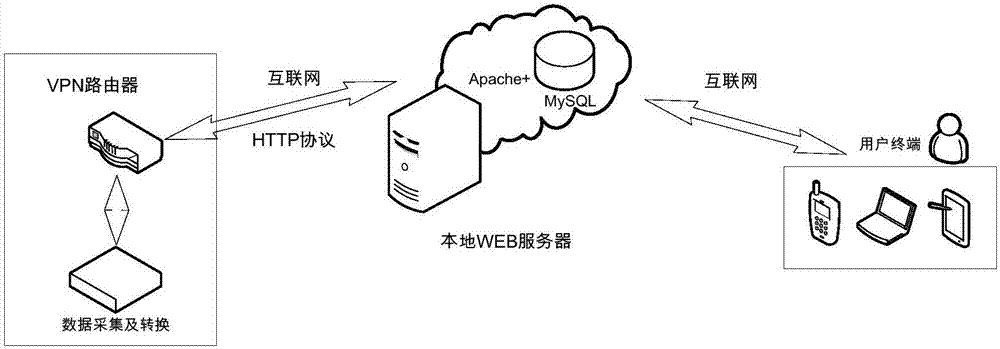
Web server-based dairy cow environment data monitoring system
InactiveCN107577197AGuaranteed transmission securityEasy to handleProgramme controlComputer controlInformatizationWeb service
The invention provides a web server-based dairy cow environment data monitoring system. The system comprises a sensor group, a local server and a serial port server. The sensor group is used for acquiring the environmental data of a dairy cow site, and transmitting the environmental data to the serial port server. The serial port server is used for collecting the environmental data, and transmitting the environmental data to the local server. The local server is used for storing and processing the environmental data. According to the invention, the breeding and the informatization are fully combined, so that the breeding is more scientific. Meanwhile, the basic data of each breeding base are collected and recorded in a database, so that the foundation is laid for later-stage big data analysis. Through analyzing the basic data, guiding suggestions are provided for the cow breeding technology in China. At the same time, the daily management of the dairy cow breeding can be integrated.
Owner:CHINA AGRI UNIV
User-defined encryption information transmission method and system
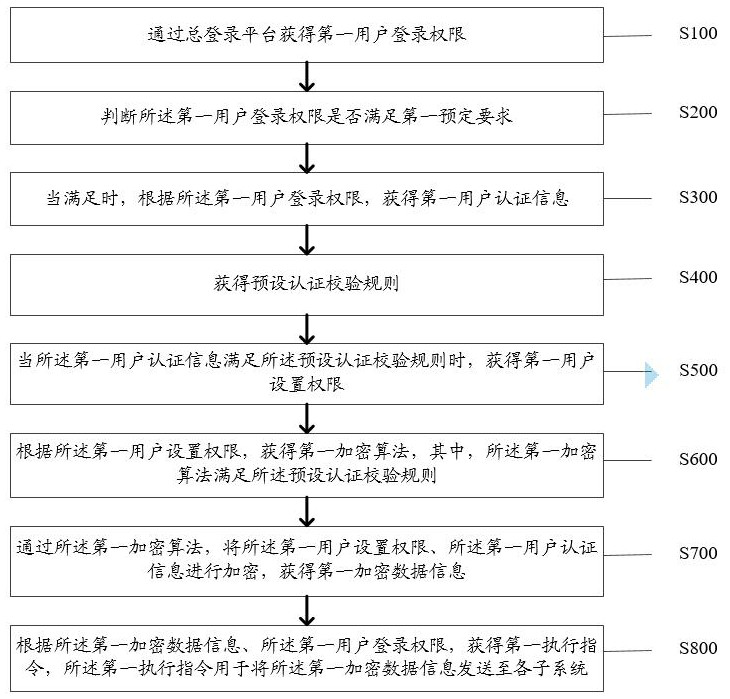
ActiveCN112800406AImprove work efficiencyEnsure safetyDigital data protectionDigital data authenticationInformation transmissionBusiness enterprise
The invention discloses a user-defined encrypted information transmission method and system. The method comprises the following steps: obtaining a first user login permission through a total login platform; judging whether the first user login permission meets a first predetermined requirement or not; if yes, obtaining first user authentication information according to the first user login permission; obtaining a preset authentication verification rule; when the first user authentication information meets a preset authentication verification rule, obtaining a first user setting permission; obtaining a first encryption algorithm according to the first user setting permission, wherein the first encryption algorithm meets a preset authentication verification rule; encrypting the first user setting permission and the first user authentication information through a first encryption algorithm to obtain first encrypted data information; and according to the first encrypted data information and the first user setting permission, obtaining a first execution instruction for sending the first encrypted data information to each subsystem. The technical problems that multiple systems are needed for business handling of financial enterprises, operation is complex, and safety problems exist if login passwords are unified are solved.
Owner:SHANGHAI HANDPAL INFORMATION TECH SERVICE
Vehicle and digital key pairing method and device
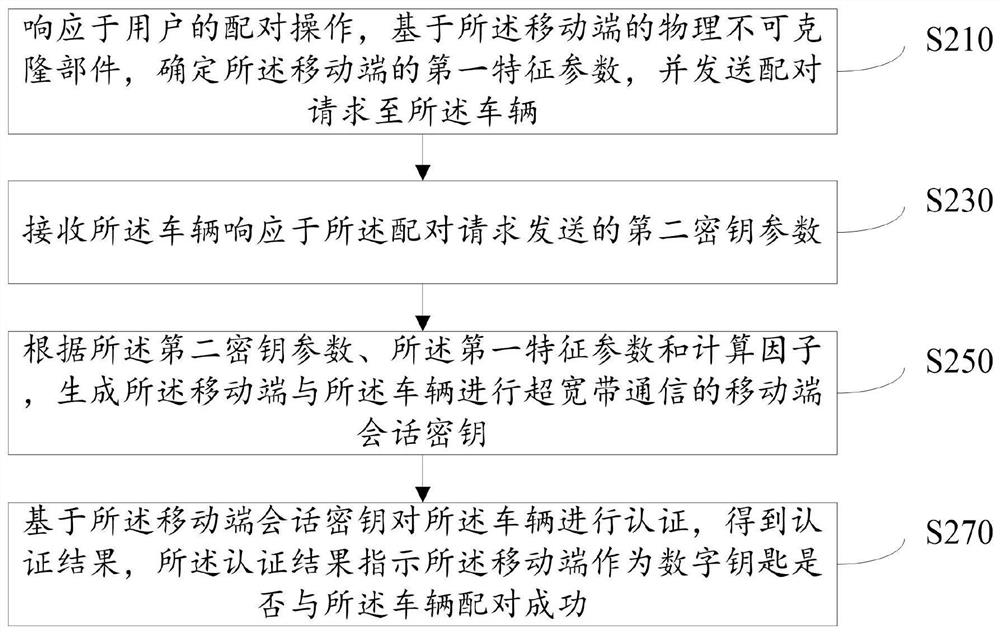
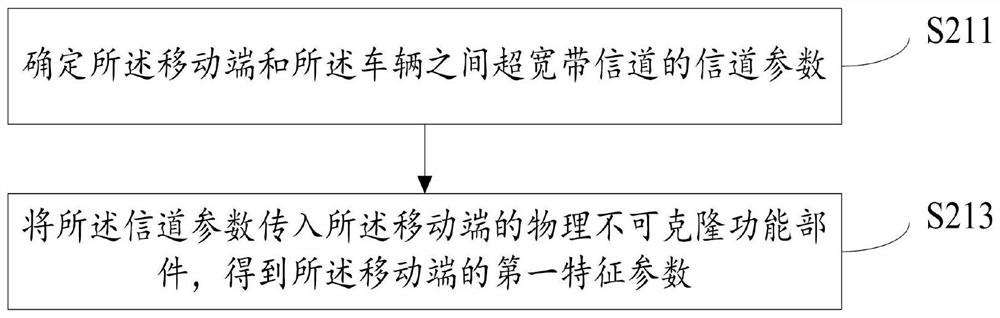
PendingCN113613197APrevent leakageSimplify the build processParticular environment based servicesVehicle wireless communication serviceMobile endEmbedded system
The invention discloses a vehicle and digital key pairing method and device, and the method comprises the steps: in response to a pairing request sent by a mobile terminal, determining a second feature parameter of a vehicle based on a physical unclonable component of the vehicle; determining a first key parameter and a calculation factor according to the pairing request sent by the mobile terminal; generating a vehicle session key according to the first key parameter, the second feature parameter and the calculation factor; and authenticating the mobile terminal based on the vehicle session key to obtain an authentication result, wherein the authentication result indicates whether the mobile terminal as a digital key is successfully paired with the vehicle or not. According to the scheme provided by the invention, the shared key can be generated based on the physical unclonable components of the vehicle and the mobile terminal and a key exchange algorithm without the intervention of a cloud server, so that the authentication of the vehicle and the mobile terminal is realized, the pairing security of the shared key is guaranteed, and the pairing process of the digital key and the vehicle is simplified.
Owner:CHINA AUTOMOTIVE INNOVATION CORP
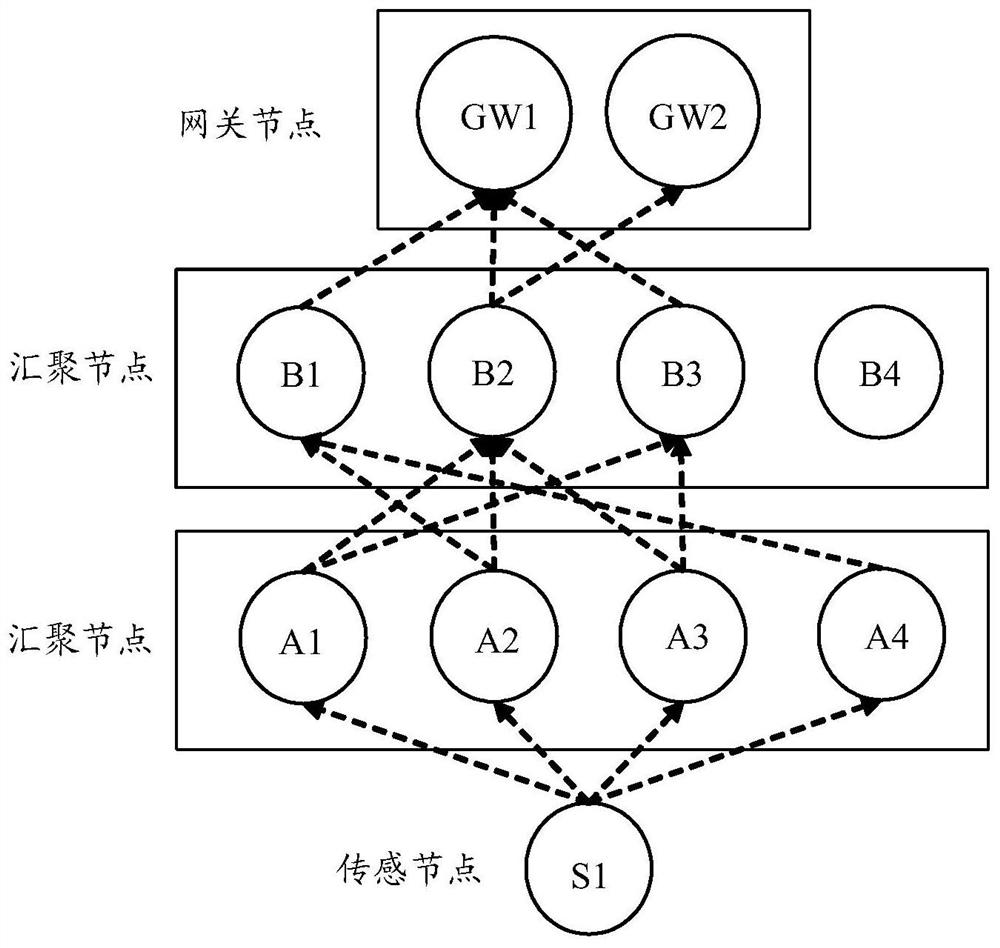
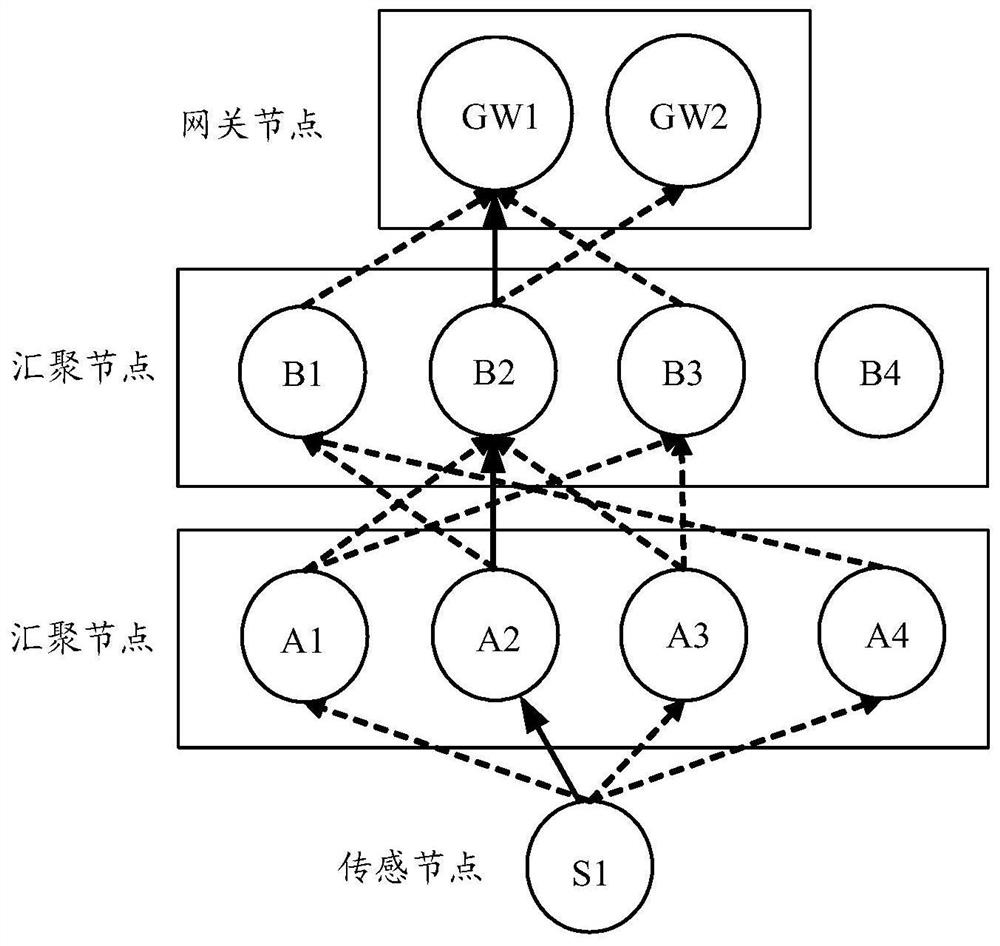
Method for acquiring node trust value based on detection route in energy harvesting wireless sensor network to avoid black hole node attack
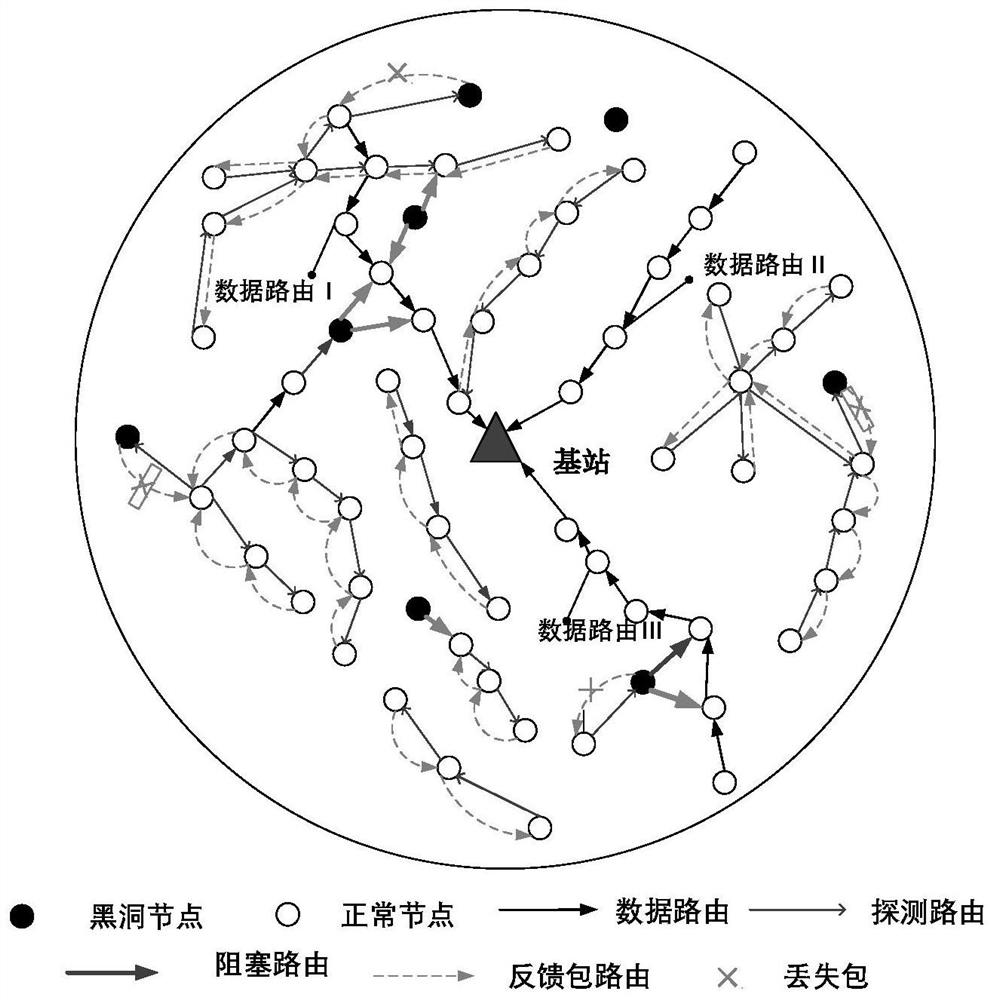
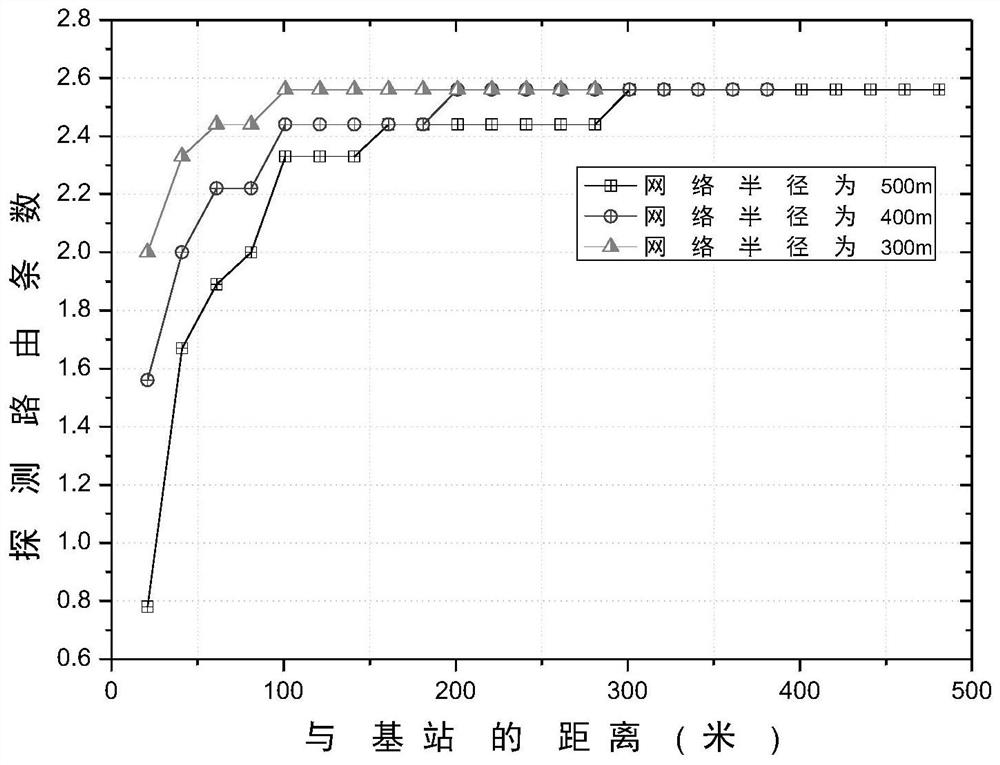
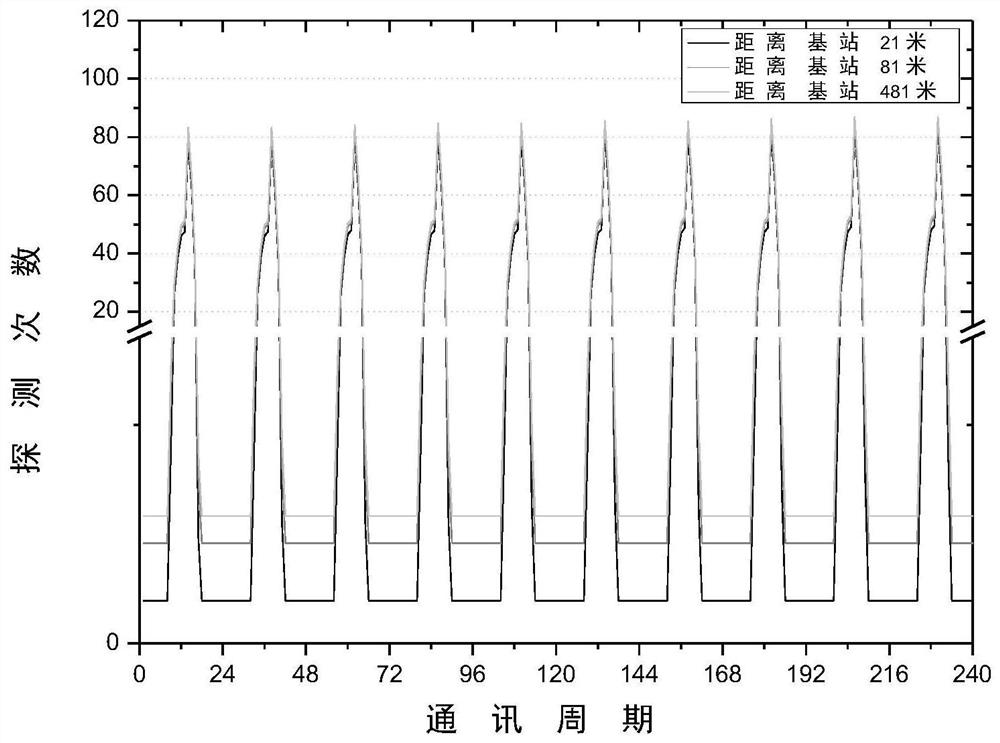
InactiveCN112911584AGuaranteed transmission securityTrust value increaseNetwork topologiesTransmissionComputer networkPacket loss
The invention discloses a method for acquiring a node trust value based on a detection route in an energy harvesting wireless sensor network to avoid black hole node attack. In the energy harvesting wireless sensor network, the energy of the nodes, in addition to meeting the data routing energy required for transmitting data packets among the nodes, remains. According to the method, the residual energy of the nodes can be fully utilized, and the detection route is established among the nodes in the network. Establishment of the detection route comprises sending a detection packet and receiving a feedback packet, and because a black hole node cannot correctly distinguish a data packet and the detection packet, malicious packet loss behaviors occur in the transmission process of the detection route, and position information of the detection route is exposed. According to the position information of the black hole node acquired by the detection route, the credibility of the malicious node is reduced, so that the node with higher credibility is selected to transmit the data packet in the transmission process of the next-hop data route. Through calculation of the node trust value, black hole nodes can be effectively avoided, and the data routing success rate of the network is improved. The residual energy of the nodes is fully utilized, and the energy utilization rate of the network is improved.
Owner:CENT SOUTH UNIV
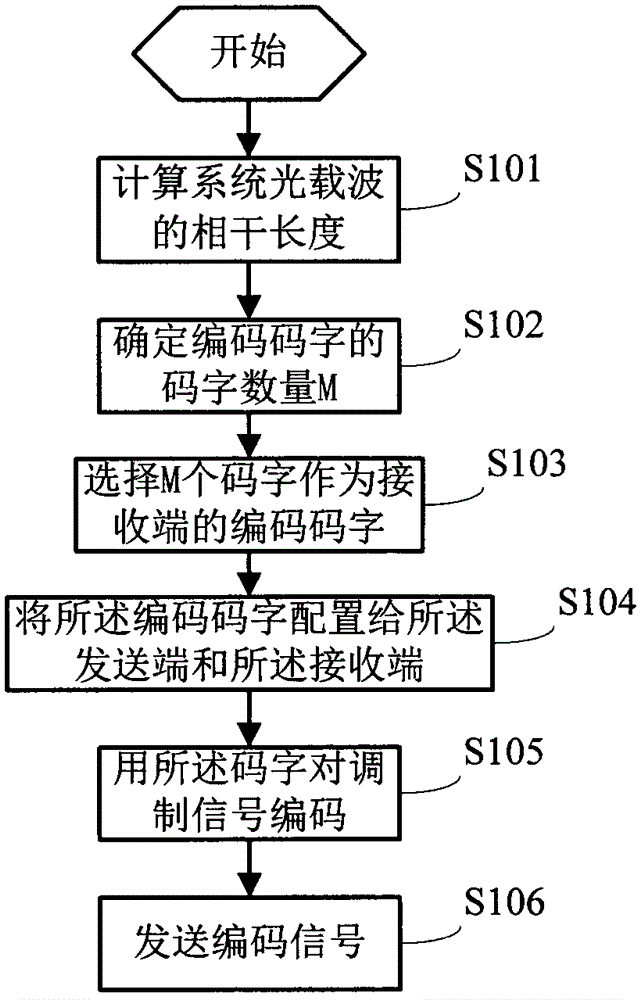
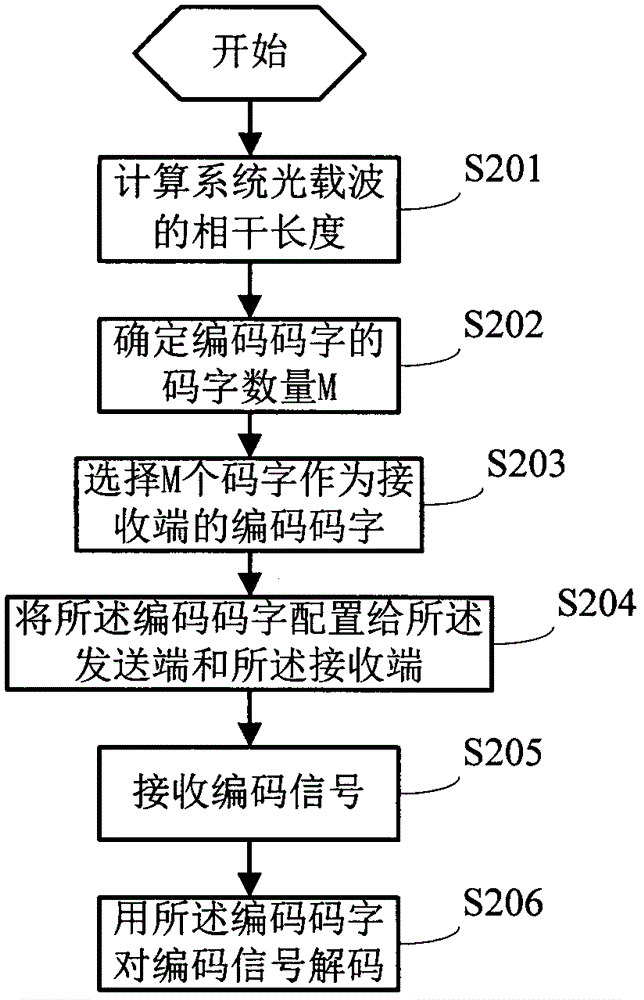
Encoding and decoding method for optical code division multiplexing system
InactiveCN104486025AGuaranteed transmission securityReduce complexityMultiplex system selection arrangementsWavelength-division multiplex systemsDecoding methodsStatistical time division multiplexing
The embodiment of the invention discloses an encoding and decoding method for an optical code division multiplexing system. The method comprises the following steps that the codeword number M of encoding codewords is selected according to the coherence length of light carriers and the pulse width of the light carriers; the M codewords are selected as encoding codewords of a receiving end; a sending end carries out encoding on modulating signals sent to the receiving end by the encoding codewords according to preset code hopping rules, and an encoding signal is generated; the receiving end receives the encoding signal sent by the sending end; the receiving end carries out decoding on the encoding signal by the encoding codewords of the receiving end according to the preset code hopping rules. The technical scheme has the advantages that on the basis of guaranteeing the transmission security of the system, the complexity of the system is effectively reduced, and the transmission efficiency is improved.
Owner:梁宇
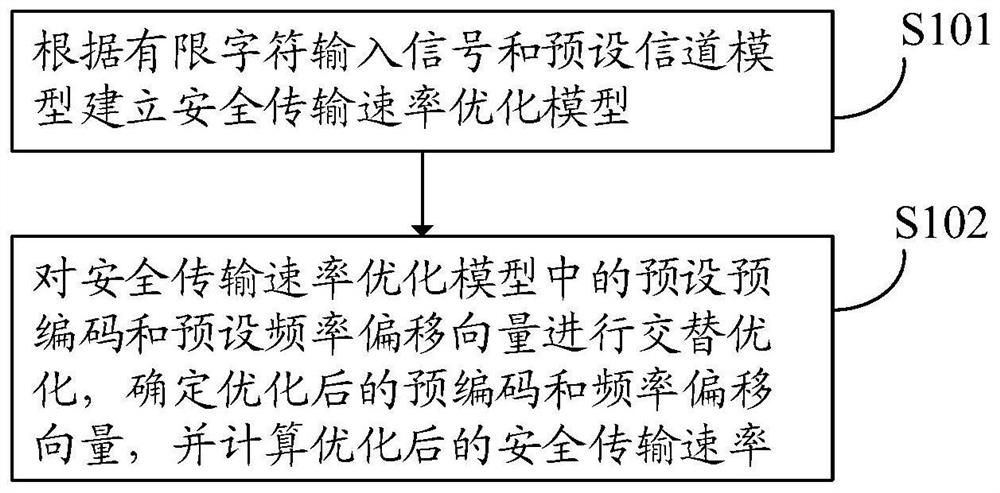
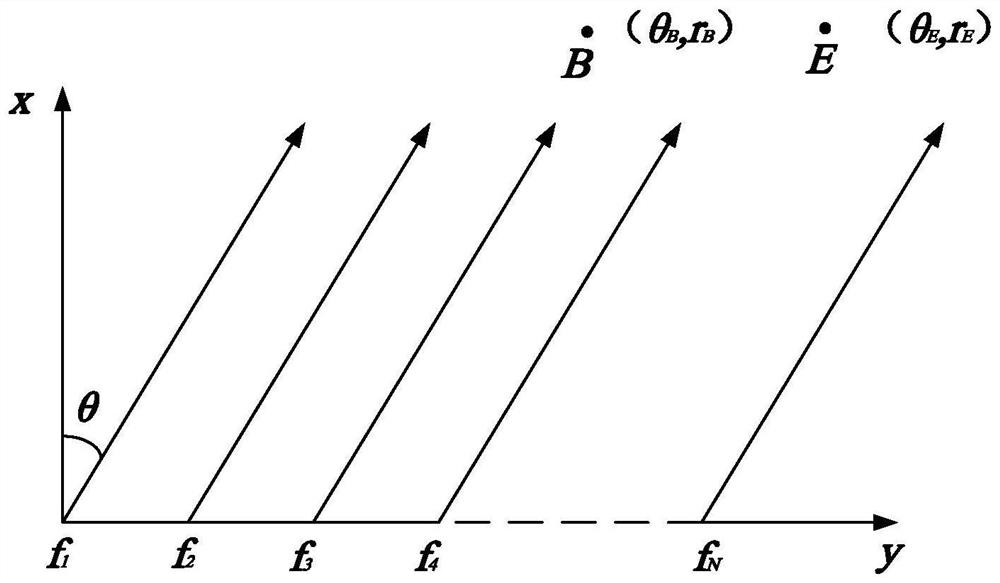
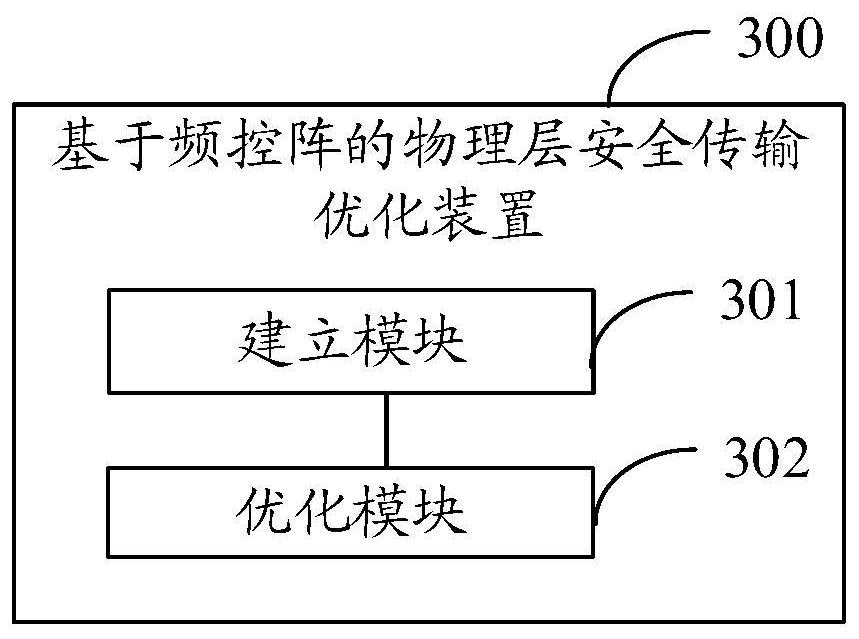
Physical layer secure transmission optimization method and device based on frequency control array
ActiveCN113067813AGuaranteed transmission securityTransmission monitoringPrecodingSecure transmission
The invention provides a physical layer secure transmission optimization method and device based on a frequency control array, electronic equipment and a storage medium. The method comprises the following steps that a secure transmission rate optimization model is established according to a limited character input signal and a preset channel model; and the preset precoding vector and the preset frequency offset vector in the secure transmission rate optimization model are alternately optimized, the optimized precoding vector and the optimized frequency offset vector are determined, and the optimized secure transmission rate is calculated, so that the security of the physical layer secure transmission system in practical application is improved.
Owner:BEIJING UNIV OF POSTS & TELECOMM
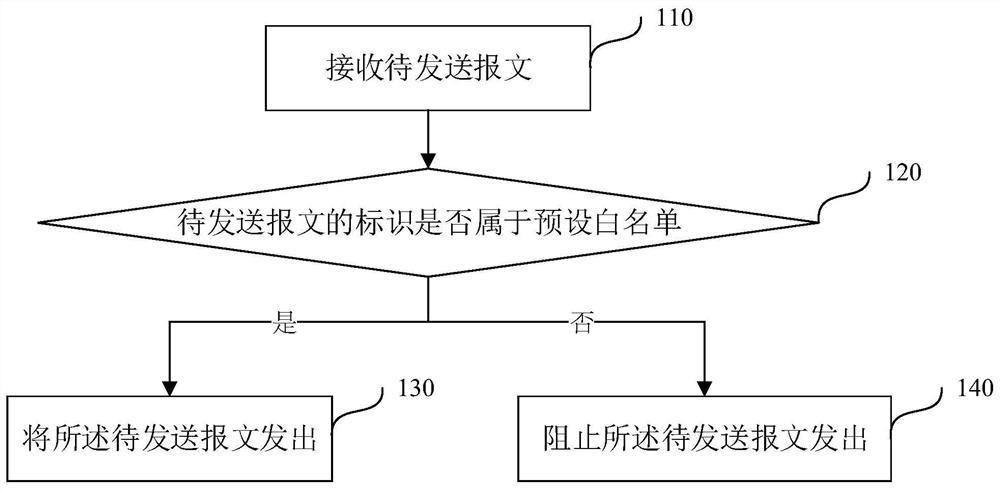
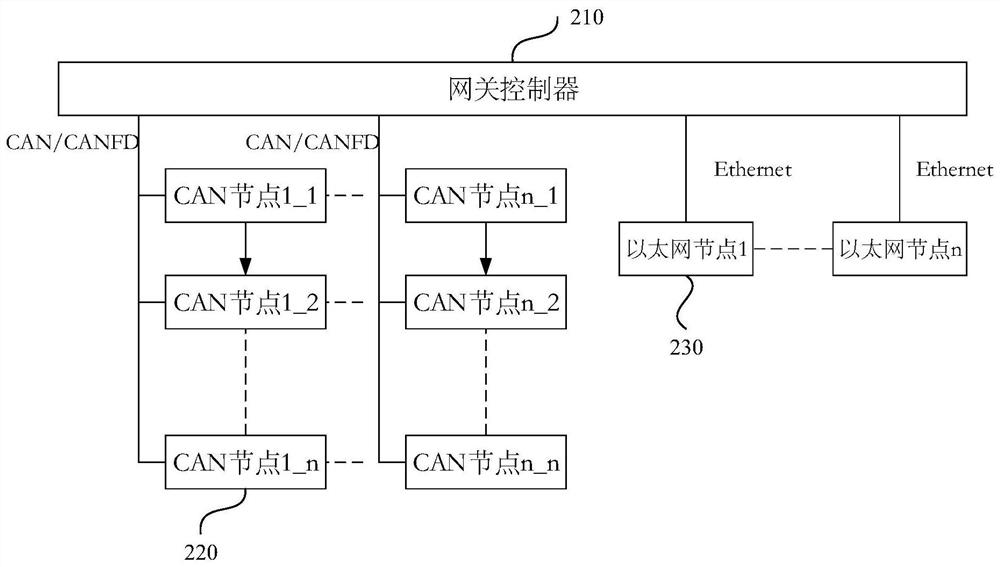
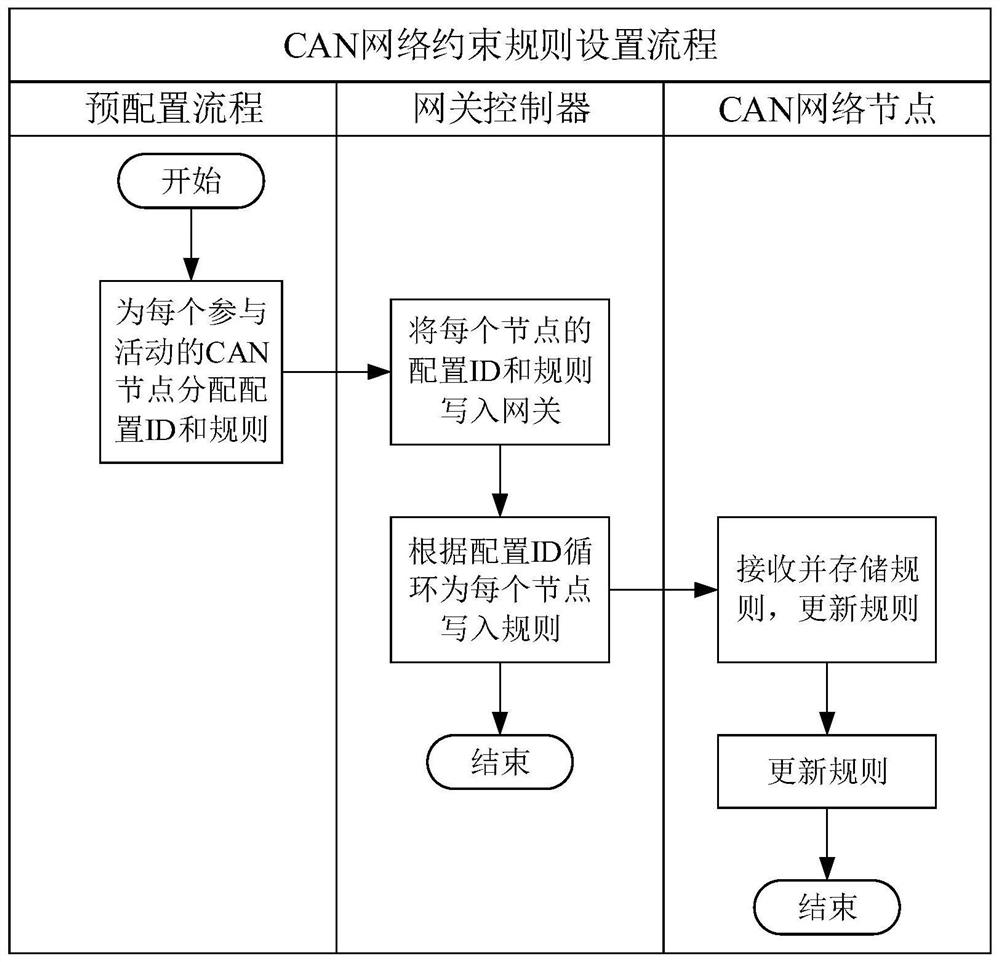
Message transmission method and device, electronic equipment and storage medium
The embodiment of the invention discloses a message transmission method and device, electronic equipment and a storage medium. The method is applied to a CAN node driver in communication connection with a gateway controller. The gateway controller is also in communication connection with at least one Ethernet node. The method comprises the steps of when a to-be-sent message is received, determining whether an identifier of the to-be-sent message belongs to a preset white list or not; and if the identifier of the to-be-sent message belongs to the preset white list, sending the to-be-sent message, otherwise, stopping sending the to-be-sent message. According to the technical scheme of the embodiment of the invention, the safety of message transmission is improved.
Owner:SHANGHAI YINGHENG ELECTRONICS
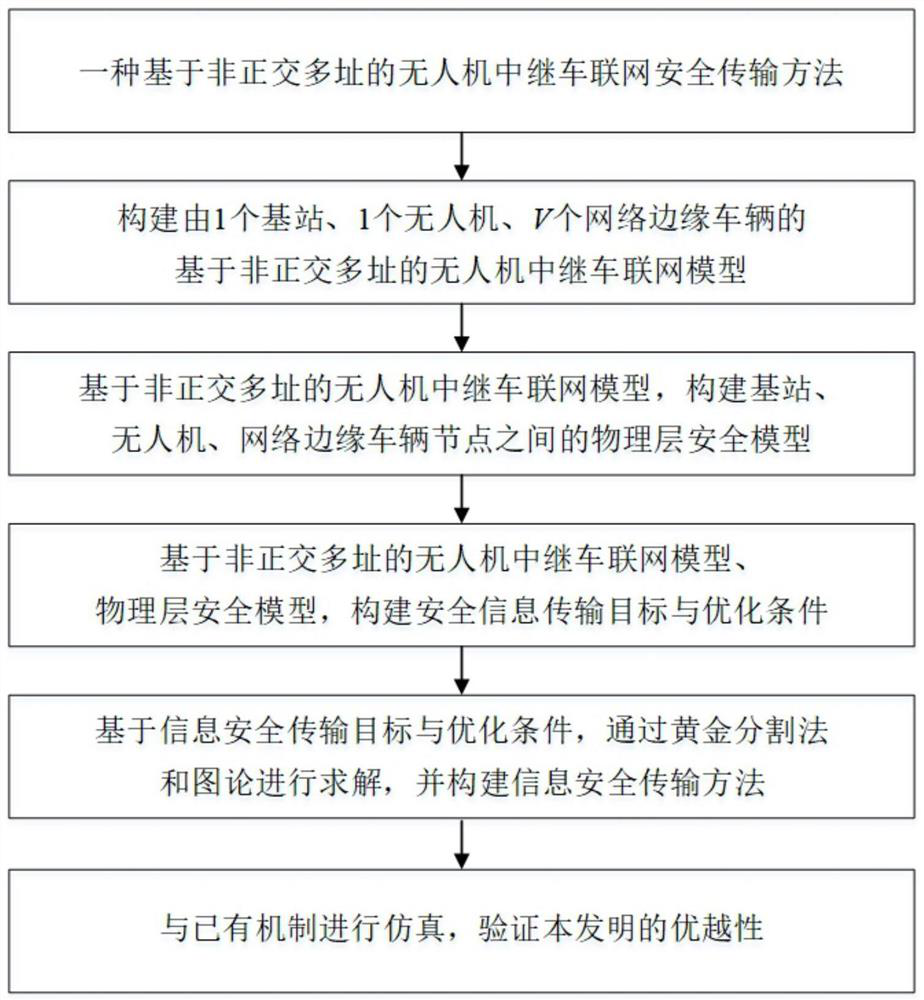
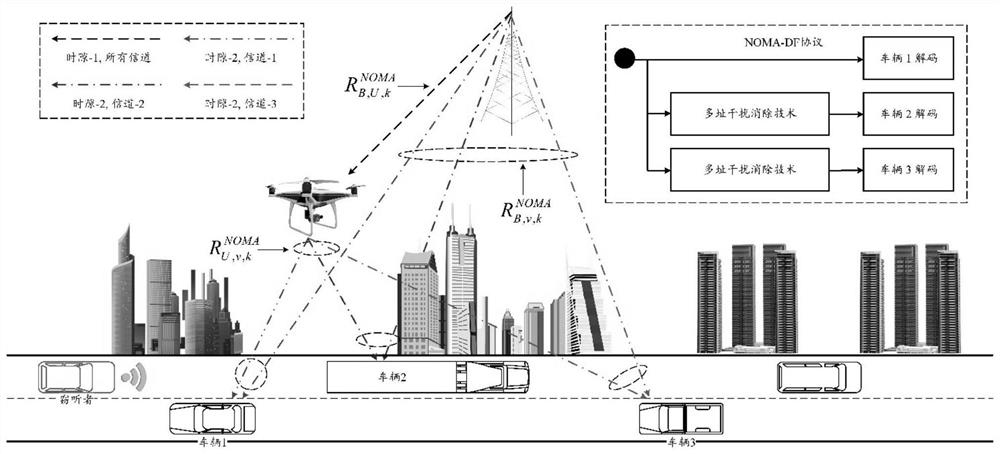
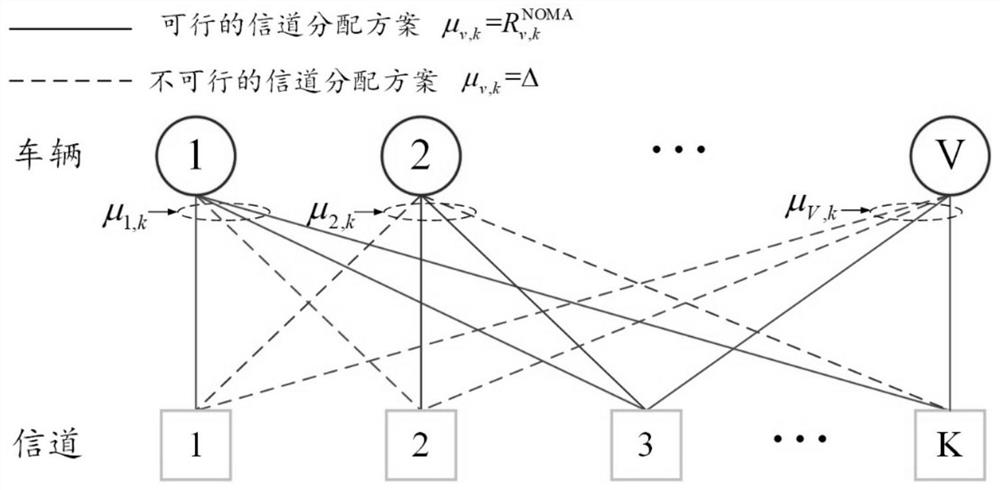
Unmanned aerial vehicle relay Internet of Vehicles secure transmission method based on non-orthogonal multiple access
PendingCN113194443AIncrease data transfer rateGuaranteed transmission securityPower managementParticular environment based servicesData transmissionTrunking
The invention discloses a unmanned aerial vehicle relay Internet of Vehicles secure transmission method based on non-orthogonal multiple access. The method comprises the following steps of: firstly, constructing a unmanned aerial vehicle relay Internet of Vehicles model based on non-orthogonal multiple access and comprising one base station, one unmanned aerial vehicle and V network edge vehicles; constructing a physical layer security model among the base station, the unmanned aerial vehicle and network edge vehicle nodes based on the unmanned aerial vehicle relay Internet of Vehicles model based on non-orthogonal multiple access; then, based on the unmanned aerial vehicle relay Internet of Vehicles model and the physical layer security model, constructing an unmanned aerial vehicle relay Internet of Vehicles secure information transmission target and optimization conditions; and finally, obtaining a solution through a golden section method and a graph theory based on the unmanned aerial vehicle relay Internet of Vehicles information secure transmission target and optimization conditions, and constructing an unmanned aerial vehicle relay Internet of Vehicles information secure transmission method. Compared with an existing mechanism, on the premise that the information transmission security is guaranteed, the total data transmission rate from the base station to the vehicle in the unmanned aerial vehicle relay Internet of vehicles can be increased.
Owner:RES & DEV INST OF NORTHWESTERN POLYTECHNICAL UNIV IN SHENZHEN +1
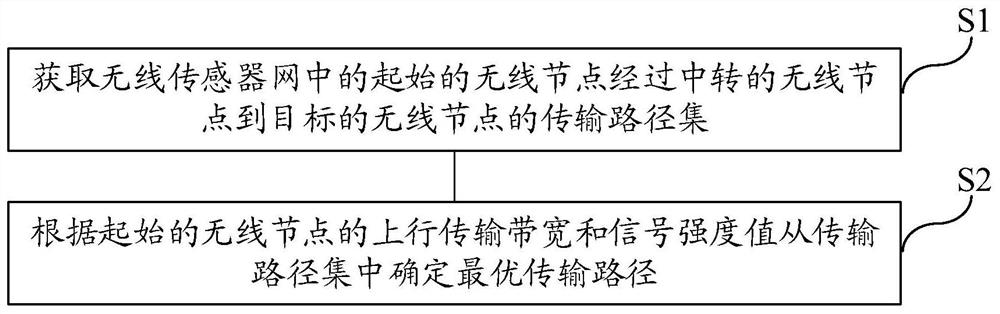
Method, medium and system for acquiring secure multi-hop transmission path of wireless sensor network
ActiveCN112867082AImprove effectivenessImprove reliabilityNetwork topologiesUplink transmissionEngineering
The invention discloses a method, a medium and a system for acquiring a secure multi-hop transmission path of a wireless sensor network. The acquisition method comprises the steps: acquiring a transmission path set from a starting wireless node in the wireless sensor network to a target wireless node through a transit wireless node, wherein the starting wireless node is a sensing node, the target wireless node is a gateway node, and the transit wireless node is at least one level of aggregation node; and determining an optimal transmission path from the transmission path set according to the uplink transmission bandwidth and the signal intensity value of the initial wireless node. According to the embodiment of the invention, under the condition that the power consumption of the sensing node is not increased, the transmission security and the information effectiveness are ensured, the reliability of a wireless network is improved, and the security of a multi-hop protocol is ensured.
Owner:国网宁夏电力有限公司超高压公司 +1
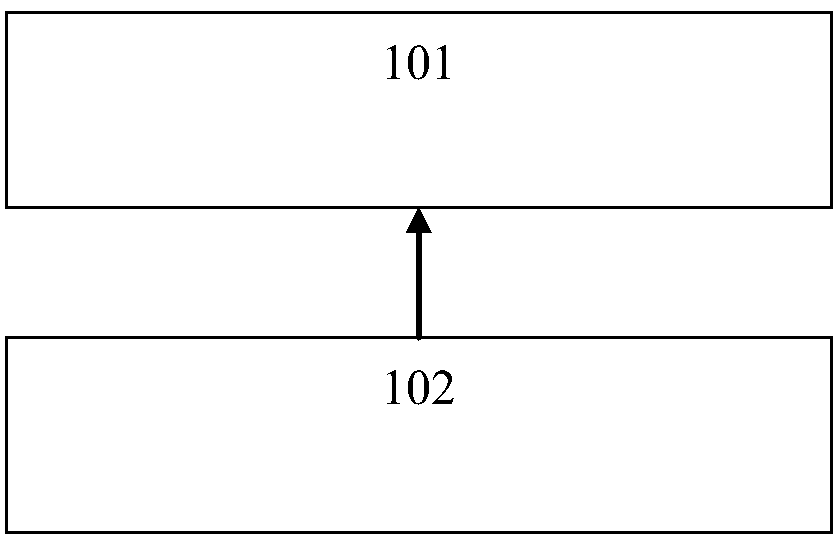
Wind Power Equipment Reliability Management Information System
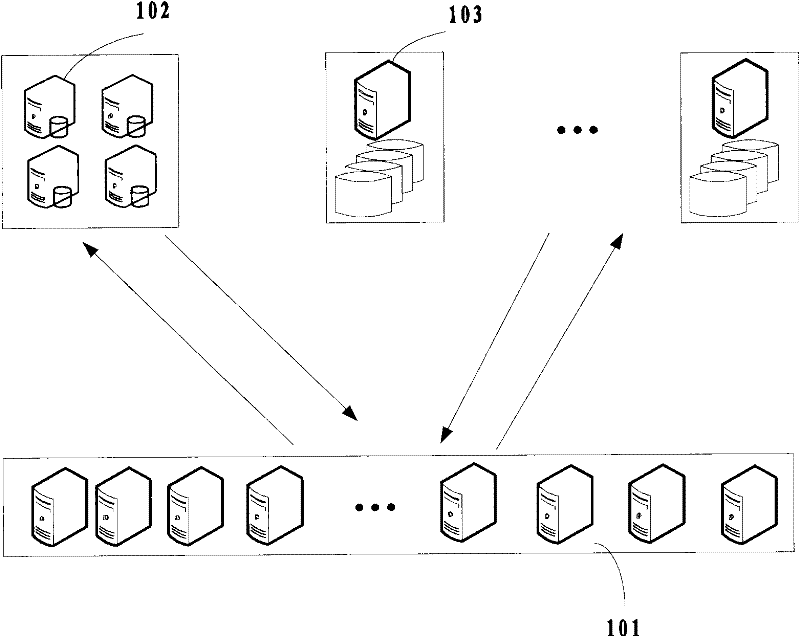
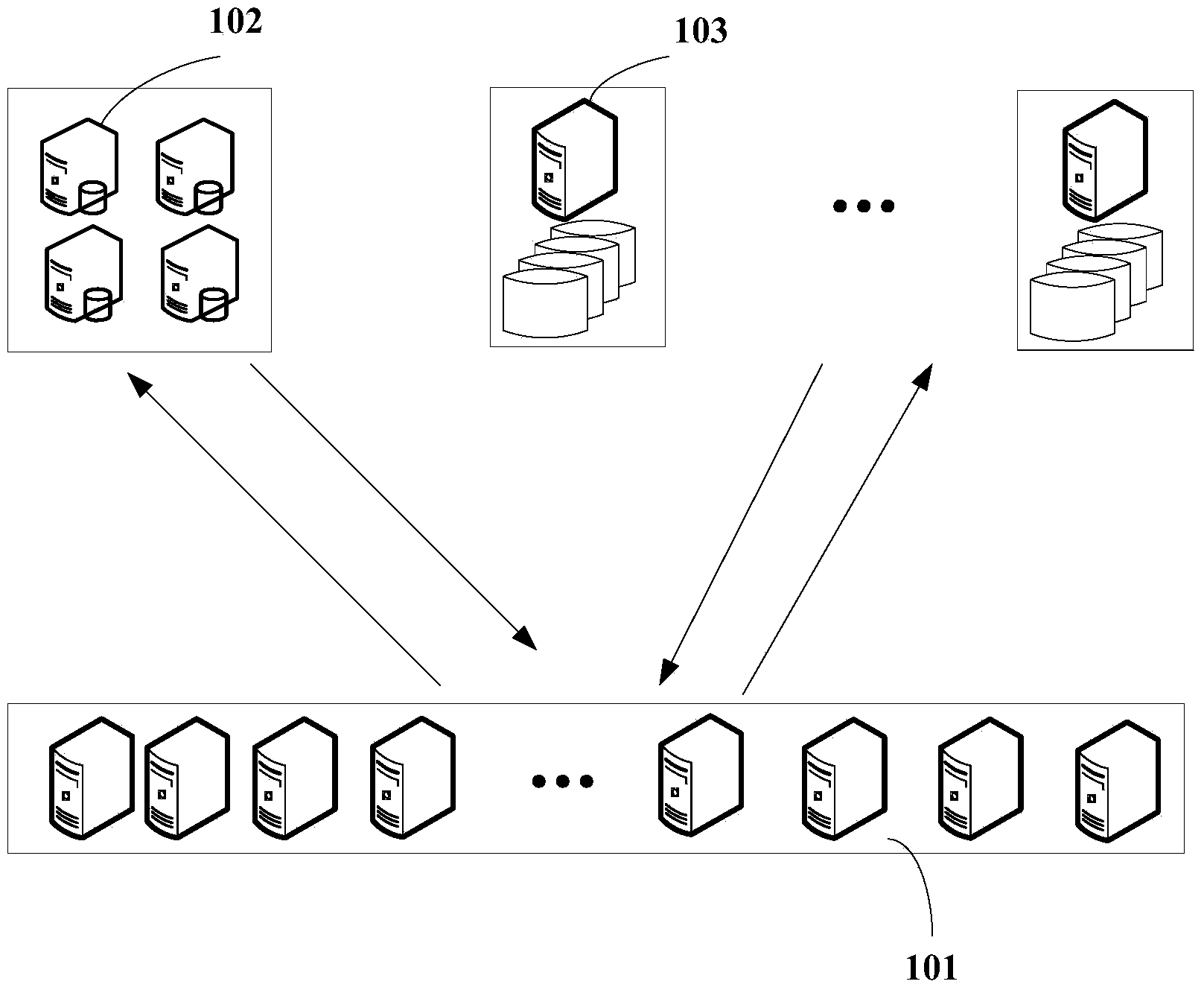
InactiveCN106094790BGuaranteed transmission securityGuaranteed accuracyElectric testing/monitoringManagement efficiencyElectric field
The invention provides a wind power equipment reliability management information system which belongs to the technical field of wind power and computer communication. The system comprises a data integration platform 102 and a reliability management platform 101. The data integration platform is used for unifiedly collecting the wind turbine monitoring data of a number of wind turbine monitoring systems which monitor wind turbine units in a wind power plant. The reliability management platform is connected with the data integration platform, and is used for collating and analyzing the wind turbine monitoring data collected by the data integration platform to acquire the equipment reliability information of each wind turbine unit in the wind power plant. According to the invention, the system can automatically collect the information of the wind power plant, automatically judges and classifies events according to the collected data, and automatically analyzes and records responsible persons and causes of key events, so as to improve the management efficiency and accuracy of the wind power equipment reliability.
Owner:INNER MONGOLIA DATANG INT NEW ENERGY
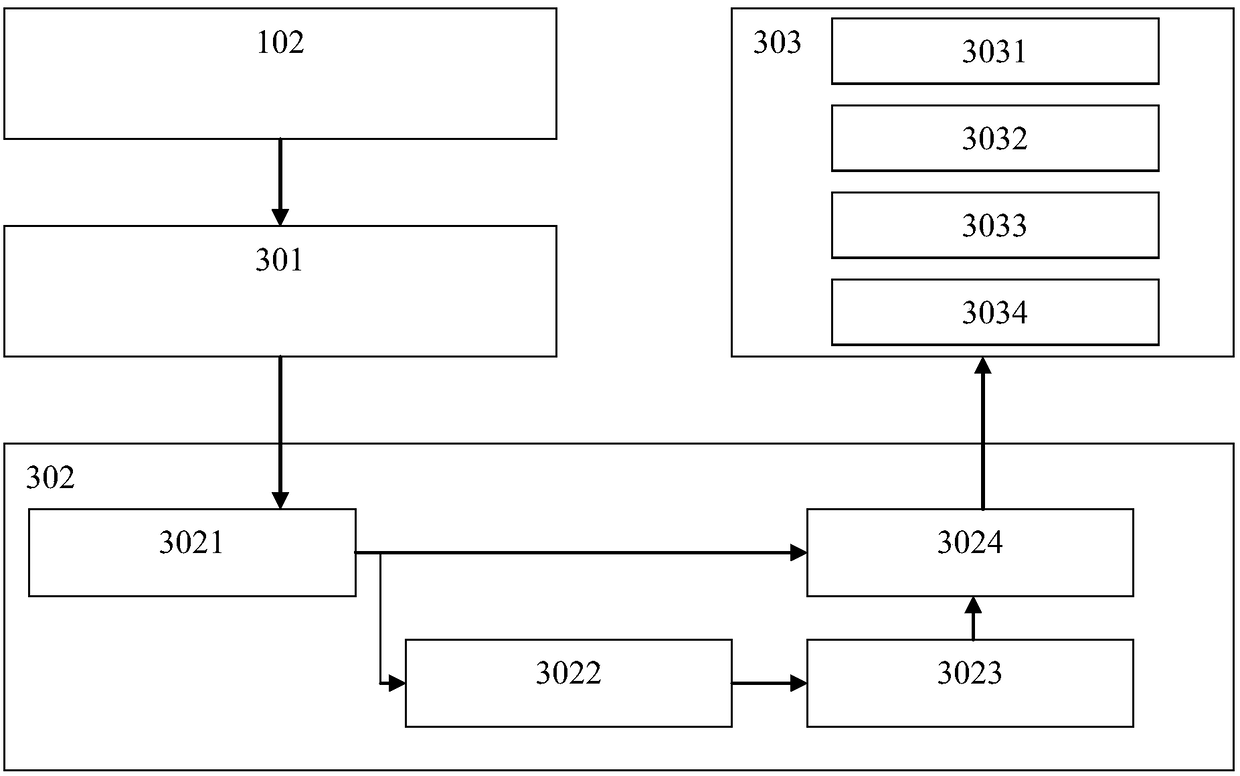
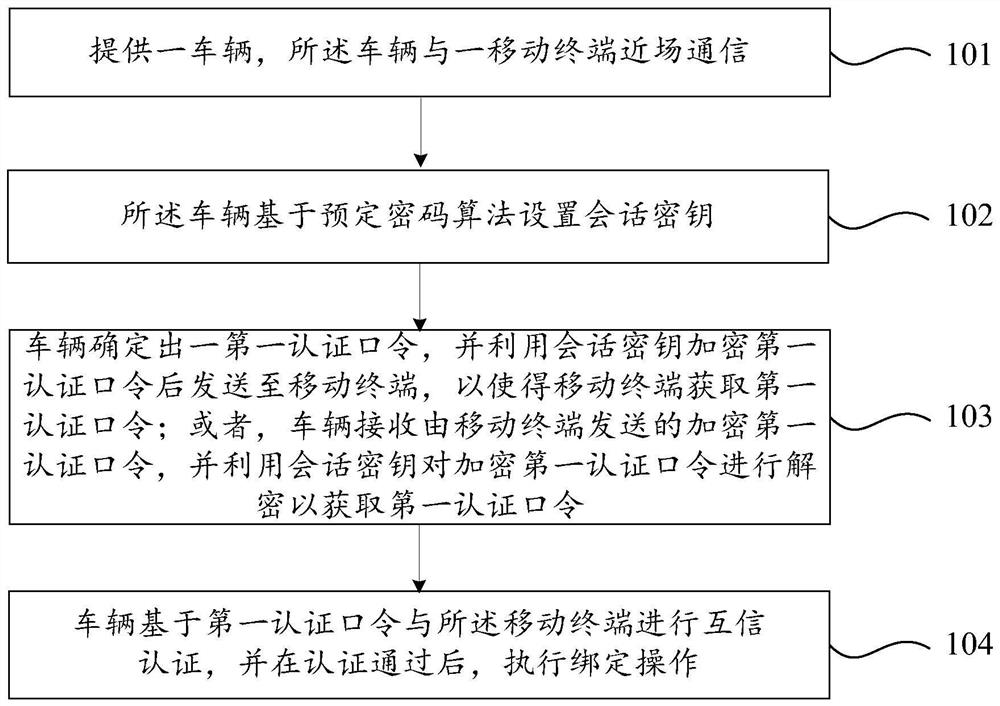
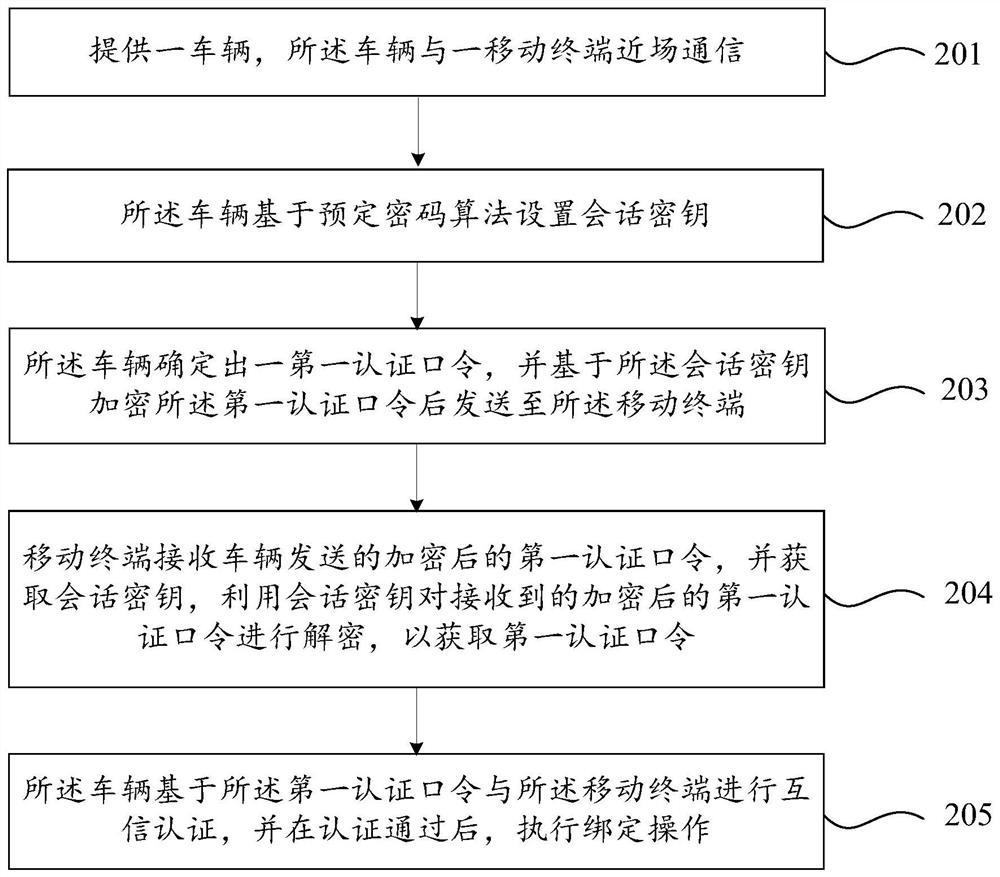
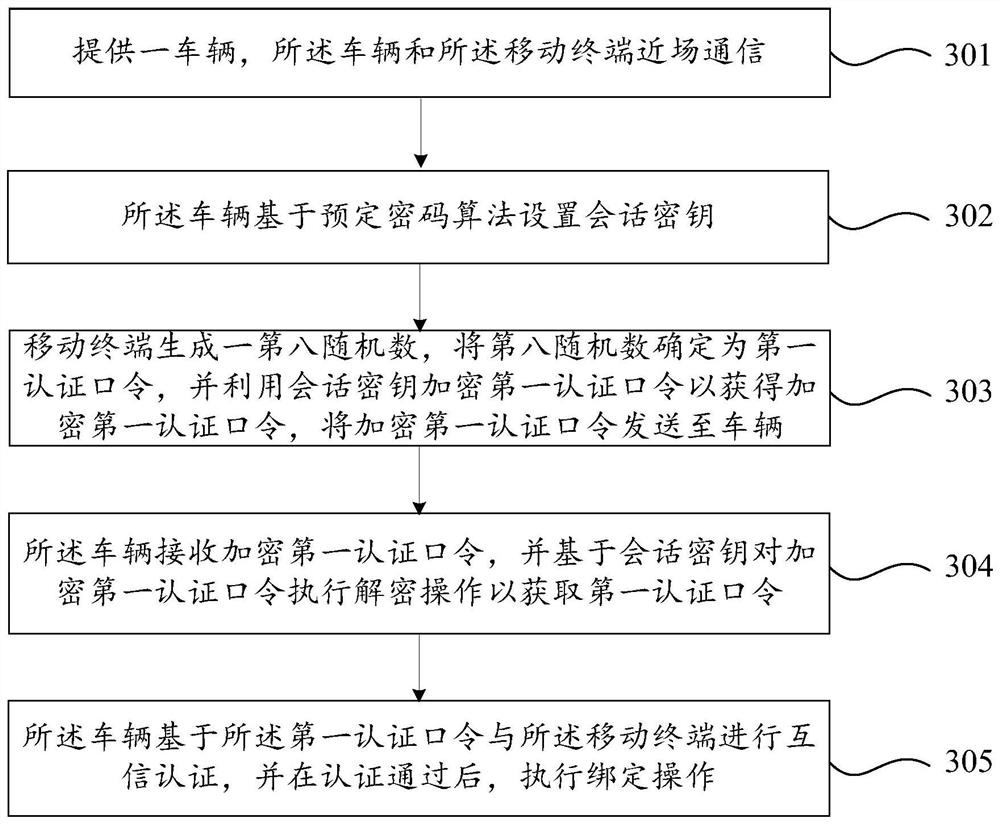
Vehicle and mobile terminal binding method and system
PendingCN113099457AAvoid interceptionGuaranteed transmission securitySecurity arrangementShort range communication servicePasswordEngineering
The invention provides a vehicle and mobile terminal binding method and system, and the method comprises the steps: a vehicle is provided, which is in near field communication with a mobile terminal; the vehicle sets a session key based on a predetermined cryptographic algorithm; the vehicle determines a first authentication password, encrypts the first authentication password by using the session key, and sends the encrypted first authentication password to the mobile terminal; or, the vehicle receives an encrypted first authentication password sent by the mobile terminal, and decrypts the encrypted first authentication password by using the session key to obtain the first authentication password; and the vehicle performs mutual trust authentication with the mobile terminal based on the first authentication password, and performs binding operation after the authentication is passed. The vehicle and mobile terminal binding method and system provided by the invention are wide in application range and high in safety.
Owner:UNITED AUTOMOTIVE ELECTRONICS SYST
A lightweight certificateless industrial internet of things access control method and system
ActiveCN111526130BAlleviate resource pressureGuaranteed transmission securityKey distribution for secure communicationUser identity/authority verificationMemory footprintEngineering
The invention discloses a lightweight access control method and system for the industrial internet of things without a certificate. According to the idea of OAuth, the local central server responsible for authorization authenticates both parties. Unlike ACE‑OAuth, which requires traditional (such as certificate-based) communication key negotiation before authentication, this method uses the local server as a trusted first Three parties, use public key-based challenge responses, tokens and passwords to realize two-way authentication between users and resource servers, and integrate communication key negotiation into the authentication process, while ensuring security, resource servers do not need to distribute and receive certificates and verification, which can effectively reduce the number of interactive rounds in the authentication process, thereby effectively reducing the amount of communication data transmission and key negotiation calculation consumption, including CPU occupation, disk occupation, memory occupation, etc., which is more advantageous in terms of security and practicability , more suitable for resource-constrained environments such as the Industrial Internet of Things.
Owner:HANGZHOU DIANZI UNIV
Data access method and equipment adopting same
ActiveCN102457561BGuaranteed transmission securityPublic key for secure communicationUser identity/authority verificationAccess methodData access
The invention discloses a data access method and equipment adopting the same. In the data access method disclosed by the invention, metadata information is encryption information; when accessing a storage server according to the metadata information, a client side needs to acquire a metadata key according to user identification, and obtain the metadata information by decrypting the encryption information according to the key, therefore, an unauthorized client side can not obtain the metadata key according to the user identification, further the metadata information can not be decrypted, and then the phenomenon that an unauthorized client side accesses a metadata server to acquire metadata information and then accesses the storage server through the metadata information can be avoided.
Owner:JIANGNAN INST OF COMPUTING TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com