Vehicle and mobile terminal binding method and system
A technology for mobile terminals and vehicles, which is applied in the field of binding methods and systems between vehicles and mobile terminals, and can solve problems such as low security and small scope of application
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
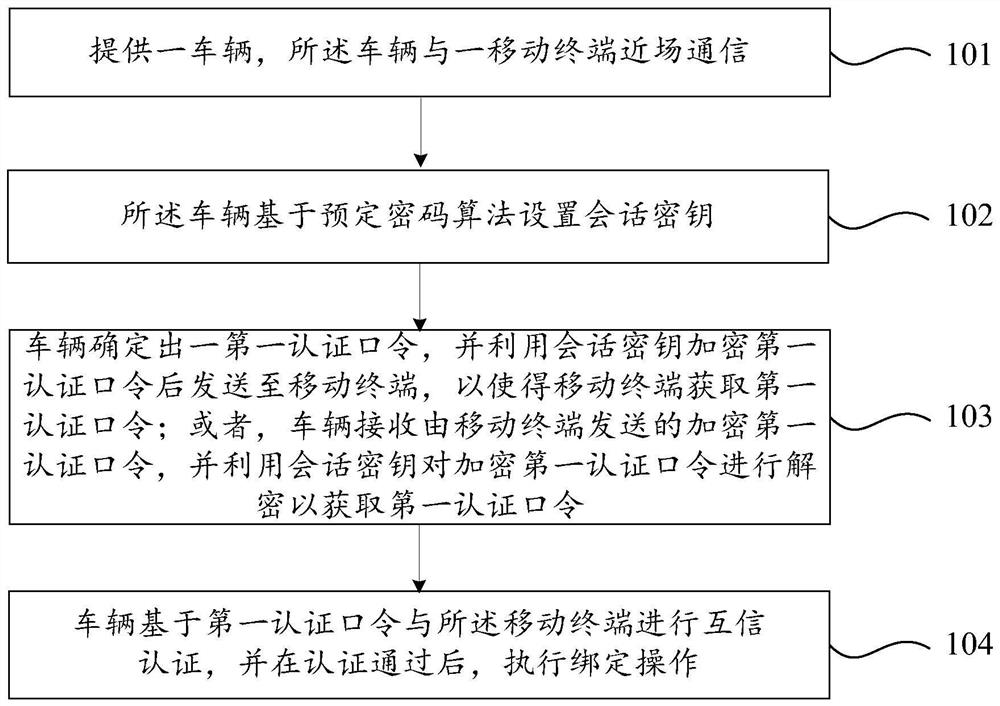
[0087] The predetermined encryption algorithm is a symmetric encryption algorithm. And, in the first embodiment, it is described by taking the vehicle as an example to determine the first authentication password, encrypt the first authentication password based on the session key, and then send it to the mobile terminal. specific, figure 2 A flow chart of a binding method between a vehicle and a mobile terminal provided in Embodiment 1 of the present invention, as shown in figure 2 As shown, the binding method of the vehicle and the mobile terminal includes:
[0088] Step 201. Provide a vehicle, and the vehicle communicates with a mobile terminal in near field.
[0089] In step 202, the vehicle sets a session key based on a predetermined cryptographic algorithm.
[0090] Wherein, when the vehicle sets the session key, the mobile terminal will also set the session key. Specifically, the method for setting the session key by the vehicle and the mobile terminal may include b...
Embodiment 2
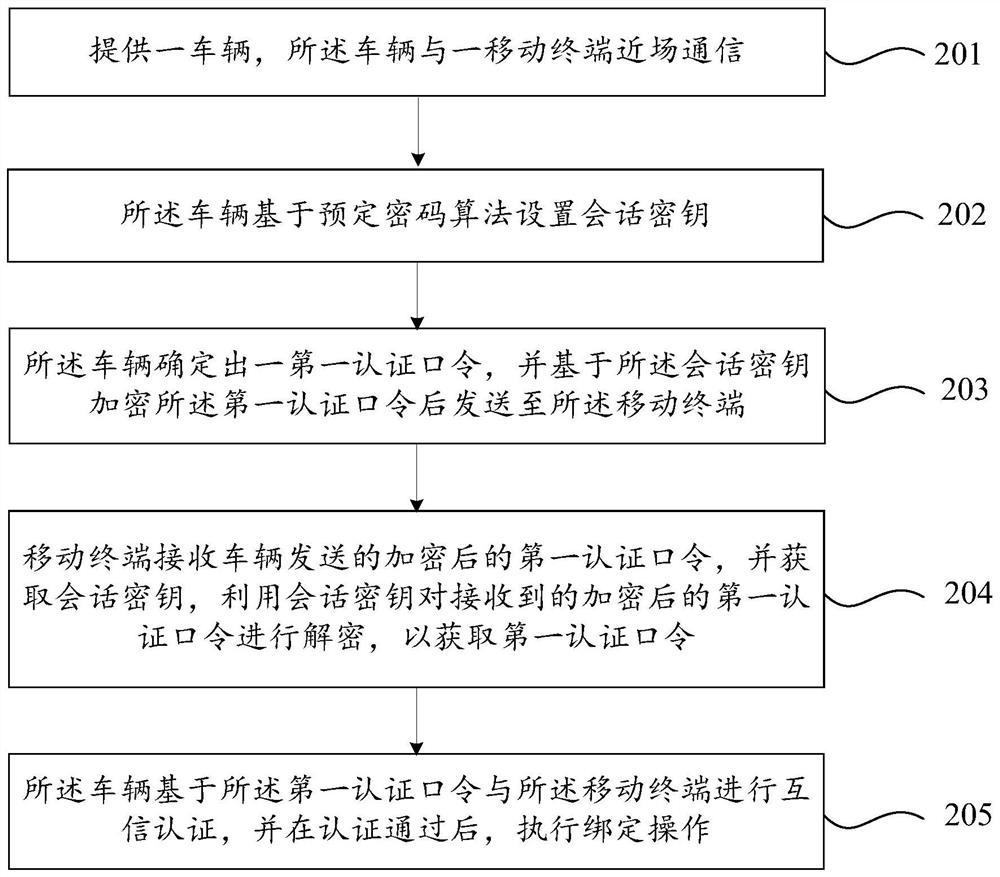
[0118] The predetermined encryption algorithm is a symmetric encryption algorithm. And, the difference between the second embodiment and the first embodiment above is that in the second embodiment, the first authentication password is not determined by the vehicle, but the first authentication password is determined by the mobile terminal, and the vehicle receives the first authentication password sent by the mobile terminal. encrypting the first authentication password, and performing a decryption operation on the encrypted first authentication password based on the session key to obtain the first authentication password. specific, image 3 A flow chart of a binding method between a vehicle and a mobile terminal provided in Embodiment 2 of the present invention, as shown in image 3 As shown, the binding method of the vehicle and the mobile terminal includes:
[0119] Step 301. Provide a vehicle, and the vehicle communicates with the mobile terminal in near field.
[0120]...
Embodiment 3
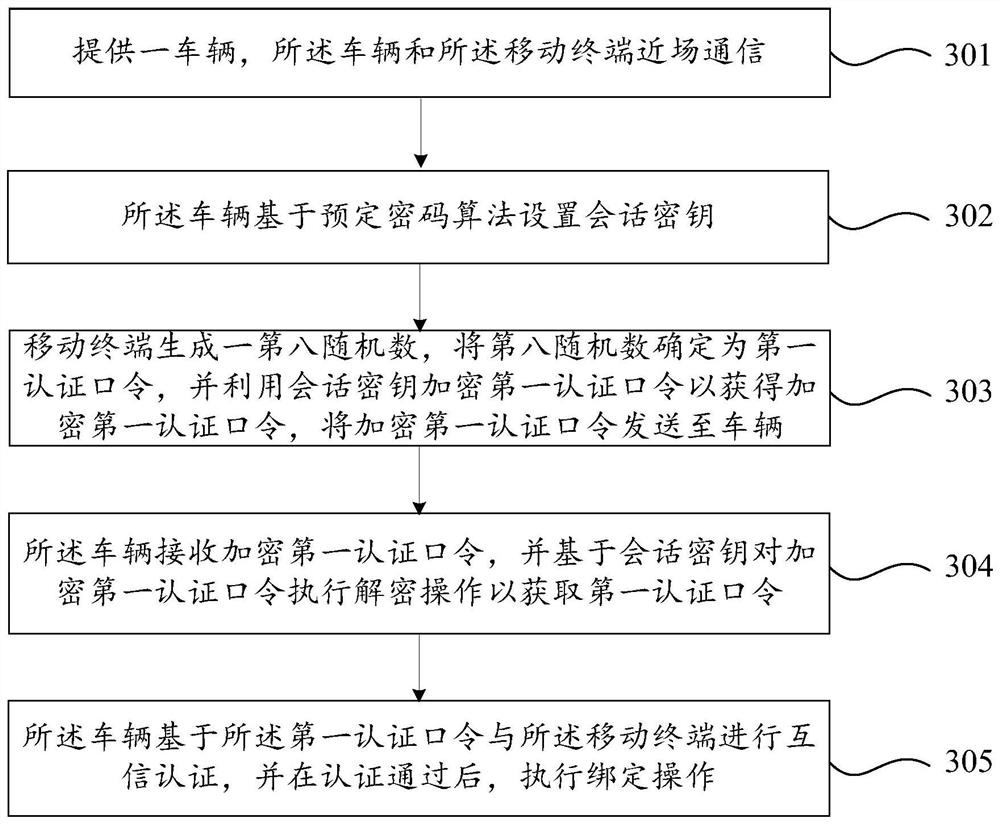
[0129] The predetermined encryption algorithm includes an asymmetric encryption algorithm. And, in the third embodiment, instead of the vehicle determining the first authentication password, the mobile terminal determines the first authentication password, and the vehicle receives the encrypted first authentication password sent by the mobile terminal, and based on the session key The first decryption operation is performed on the encrypted first authentication password to obtain the first authentication password as an example for description. Figure 4 It is a flow chart of a binding method between a vehicle and a mobile terminal provided in Embodiment 3 of the present invention, as shown in Figure 4 As shown, the method includes:
[0130] Step 401. Provide a vehicle, and the vehicle communicates with a mobile terminal in near field.
[0131] Step 402, the vehicle sets a session key based on a predetermined cryptographic algorithm.
[0132] Wherein, when the vehicle sets ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com