Message transmission method and device, electronic equipment and storage medium
A message transmission and message technology, applied in transmission systems, digital transmission systems, electrical components, etc., can solve problems such as inability to directly borrow, inability to mount functional operating systems, and remote intrusion.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
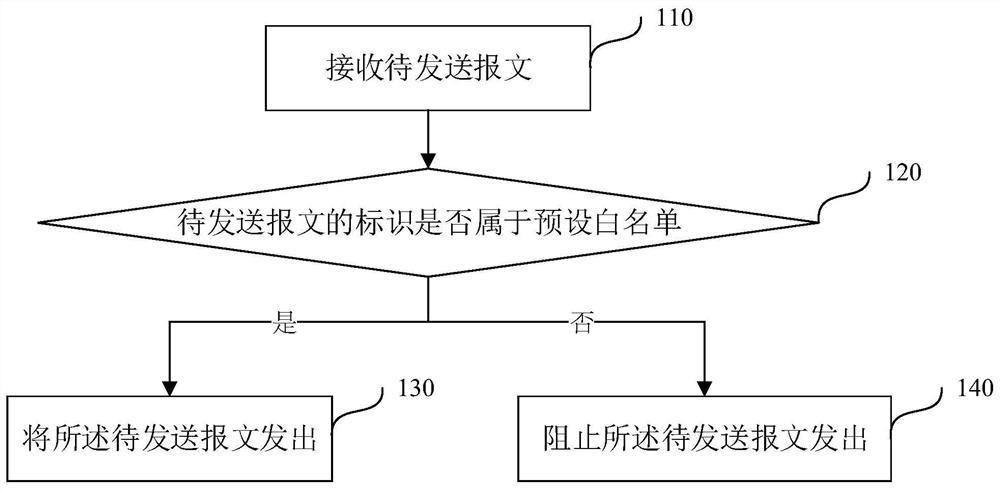
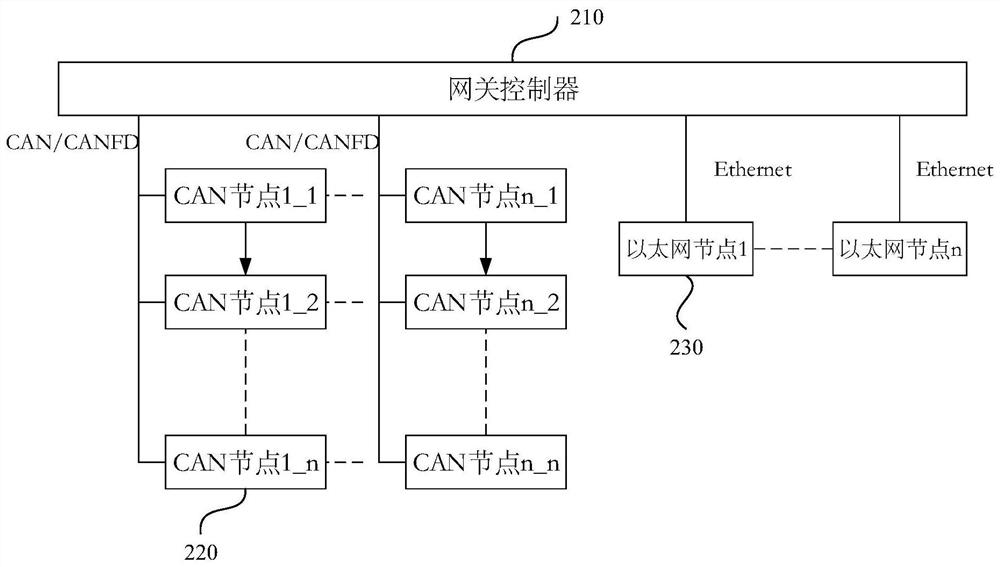
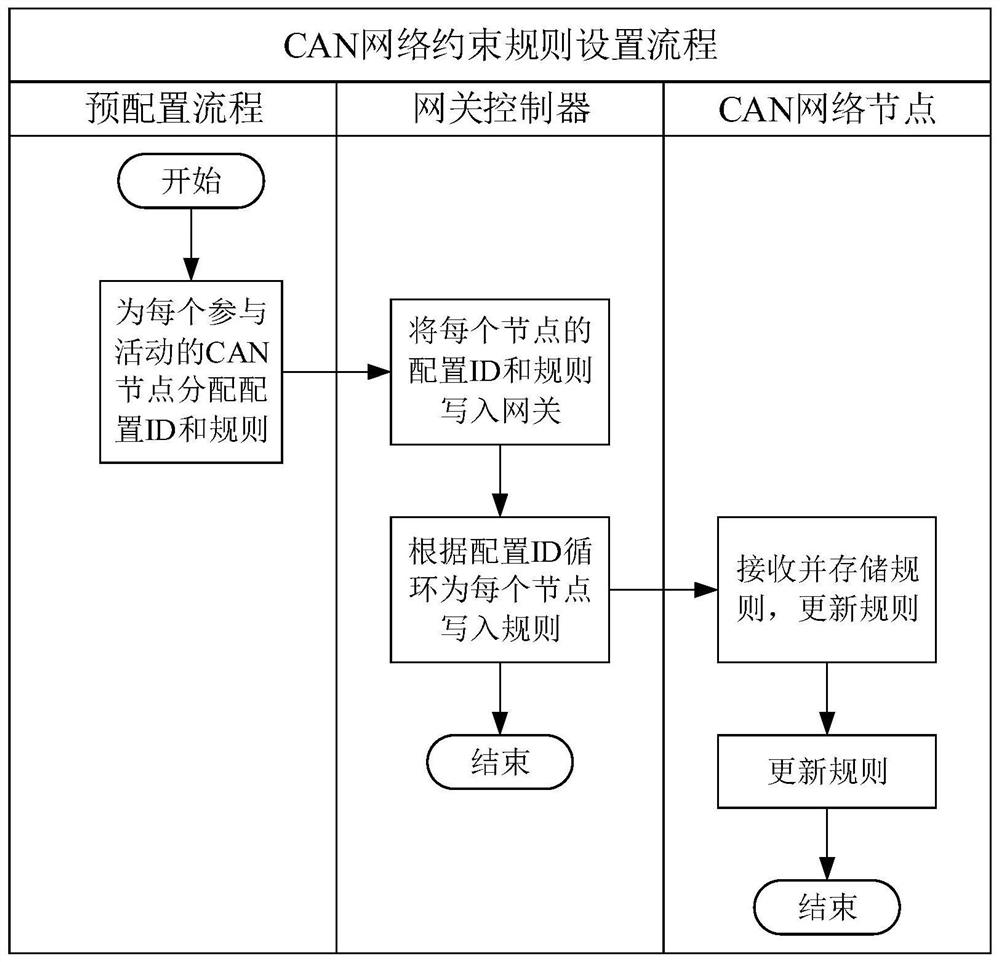
[0068] figure 1 It is a schematic flow chart of a message transmission method provided by Embodiment 1 of the present invention. This method is applicable to vehicle-mounted networks, specifically, Ethernet is used as the core of the entire network, and the traditional CAN distributed network is used in the vehicle-mounted network application , designed to improve the security of message transmission. Since most of the network nodes in the vehicle are embedded devices, which cannot mount a powerful operating system, it is impossible to directly use the traditional network firewall to ensure the security of the network, so the technical solution of the embodiment of the present invention is proposed. The method can be executed by a message transmission device, and the device can be implemented in the form of software and / or hardware. The message transmission method provided in this embodiment is applied to a CAN node driver communicatively connected to a gateway controller, an...
Embodiment 2
[0079] Figure 4 It is a schematic flowchart of a message transmission method provided by Embodiment 2 of the present invention. On the basis of the above-mentioned embodiments, the method provided by this embodiment is applied to the gateway controller, and the gateway controller is respectively connected to at least one CAN node driver and at least one Ethernet node in order to improve Security of transmitted messages.
[0080] Such as Figure 4 As shown, the method includes the following steps:
[0081] Step 410: When receiving a message from the first Ethernet node to the second Ethernet node, determine whether the message carries encrypted data.
[0082] Step 420: If the message carries encrypted data, decrypt the encrypted data based on the first key agreed with the first Ethernet node to obtain decrypted data.
[0083] Step 430: Encrypt the decrypted data based on the second key agreed with the second Ethernet node to obtain ciphertext.
[0084] Step 440: Replace t...
Embodiment 3
[0104] Figure 8 Embodiment 3 of the present invention provides a message transmission device, which is integrated in a CAN node driver communicatively connected to a gateway controller, and the gateway controller is also communicatively connected to at least one Ethernet node. Such as Figure 8 As shown, the device includes: a determining module 810 and a sending module 820 .
[0105] Among them, the determining module 810 is used to determine whether the identifier of the message to be sent belongs to the preset white list when receiving the message to be sent; the sending module 820 is used to determine whether the identifier of the message to be sent belongs to the preset white list; If a white list is set, the message to be sent is sent, otherwise, the message to be sent is prevented from being sent.
[0106] Further, the device further includes: a configuration module, configured to configure the preset whitelist for the CAN node driver through a gateway controller.
...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com