User-defined encryption information transmission method and system
A technology for encrypting information and transmission methods, which is applied in the field of custom encrypted information transmission methods and systems, and can solve problems such as complex operations and security issues
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
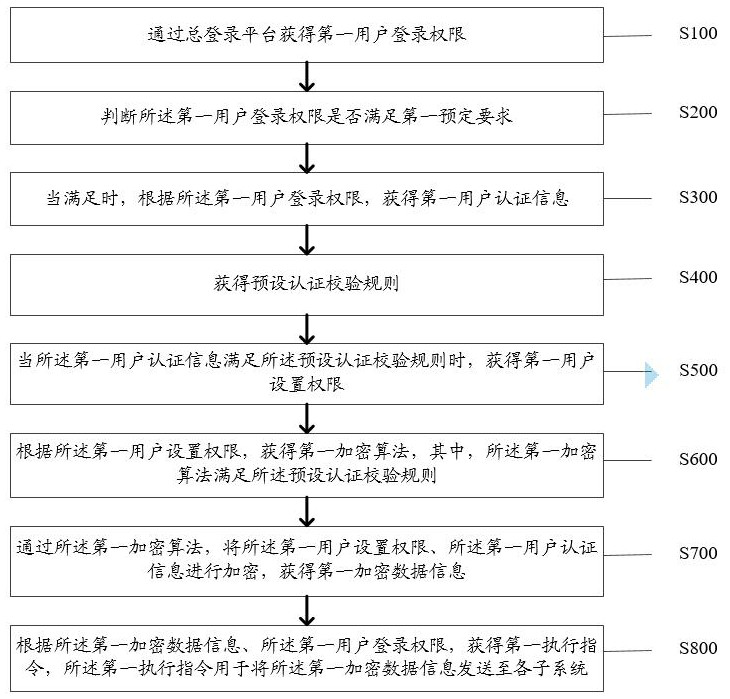
[0032] Such as figure 1 As shown, the embodiment of the present application provides a custom encrypted information transmission method, which is applied to an integrated business processing platform, and the integrated business processing platform includes a general login platform and multiple subsystems, and the total login platform and the described A plurality of subsystem data connections, the method comprising:
[0033]Step S100: Obtain the first user login authority through the total login platform;
[0034] Step S200: judging whether the login authority of the first user meets the first predetermined requirement;
[0035] Specifically, the integrated business processing platform has a unified business login portal through which users enter their own account information, and the server of the integrated business processing platform checks the account information. When the account information meets the login requirements of the server, the first The login authority cor...
Embodiment 2
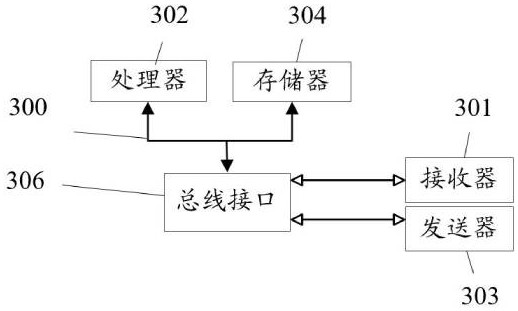
[0090] Based on the same inventive concept as that of a self-defined encrypted information transmission method in the foregoing embodiments, the present invention also provides a self-defined encrypted information transmission system, such as figure 2 As shown, the system includes:
[0091] The first obtaining unit 11, the first obtaining unit 11 is used to obtain the first user login authority through the total login platform;
[0092] A first judging unit 12, configured to judge whether the first user login authority meets a first predetermined requirement;
[0093] The second obtaining unit 13, the second obtaining unit 13 is configured to obtain the first user authentication information according to the first user login authority when it is satisfied;
[0094] A third obtaining unit 14, the third obtaining unit 14 is used to obtain preset authentication verification rules;
[0095] A fourth obtaining unit 15, configured to obtain the setting authority of the first user ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com