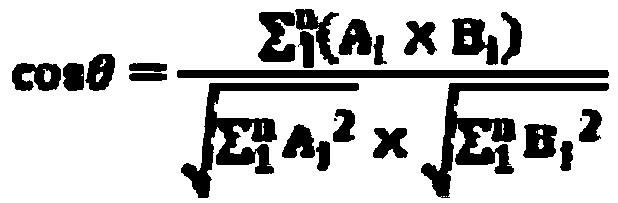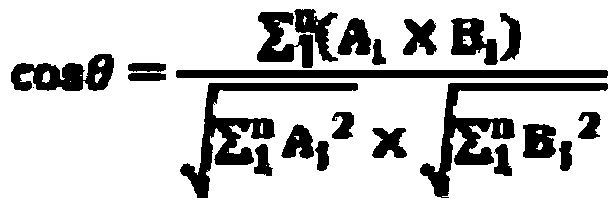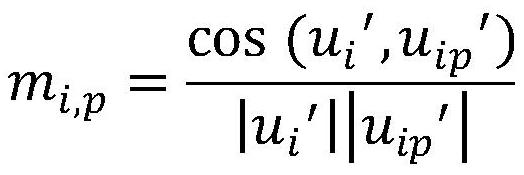Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
44results about How to "Full excavation" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
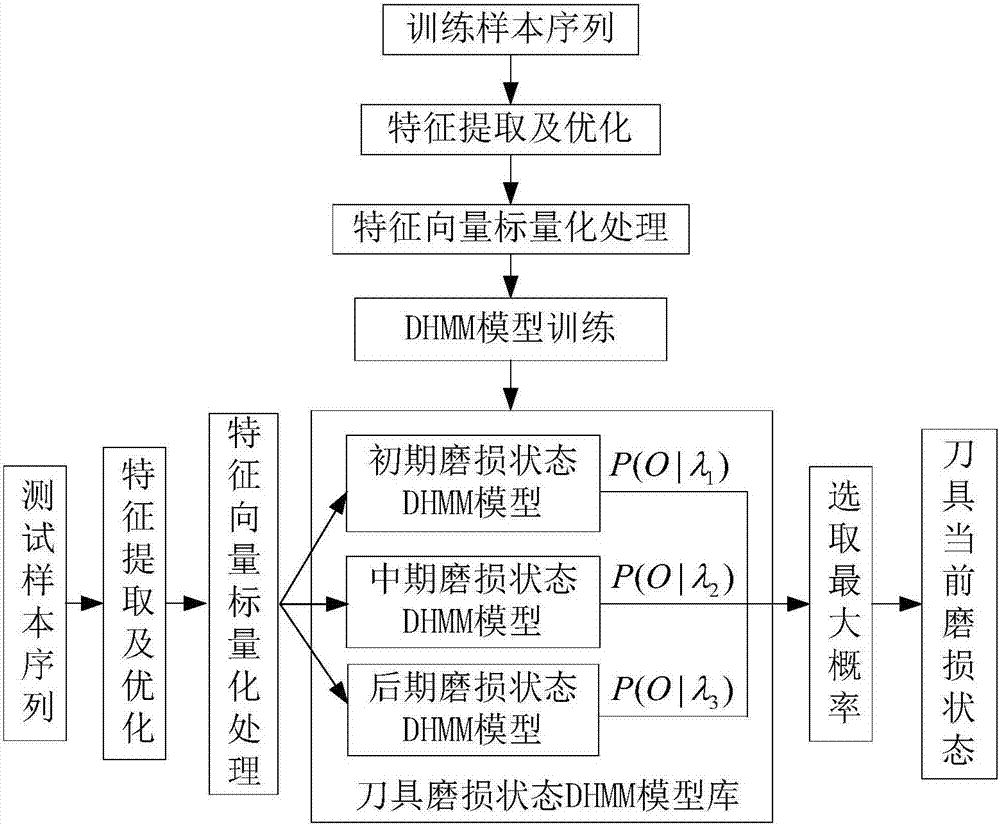
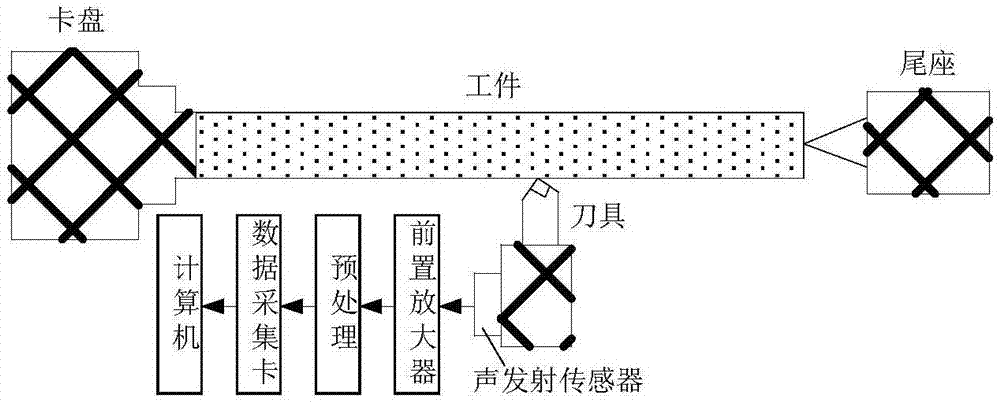
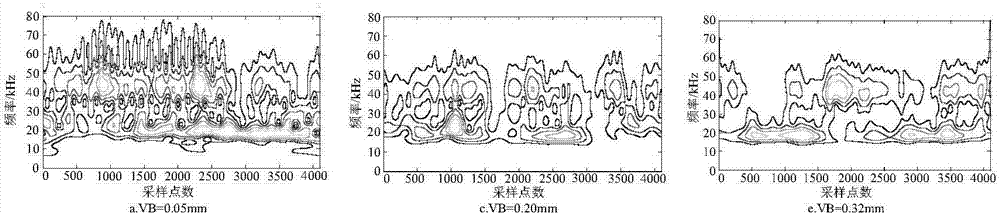
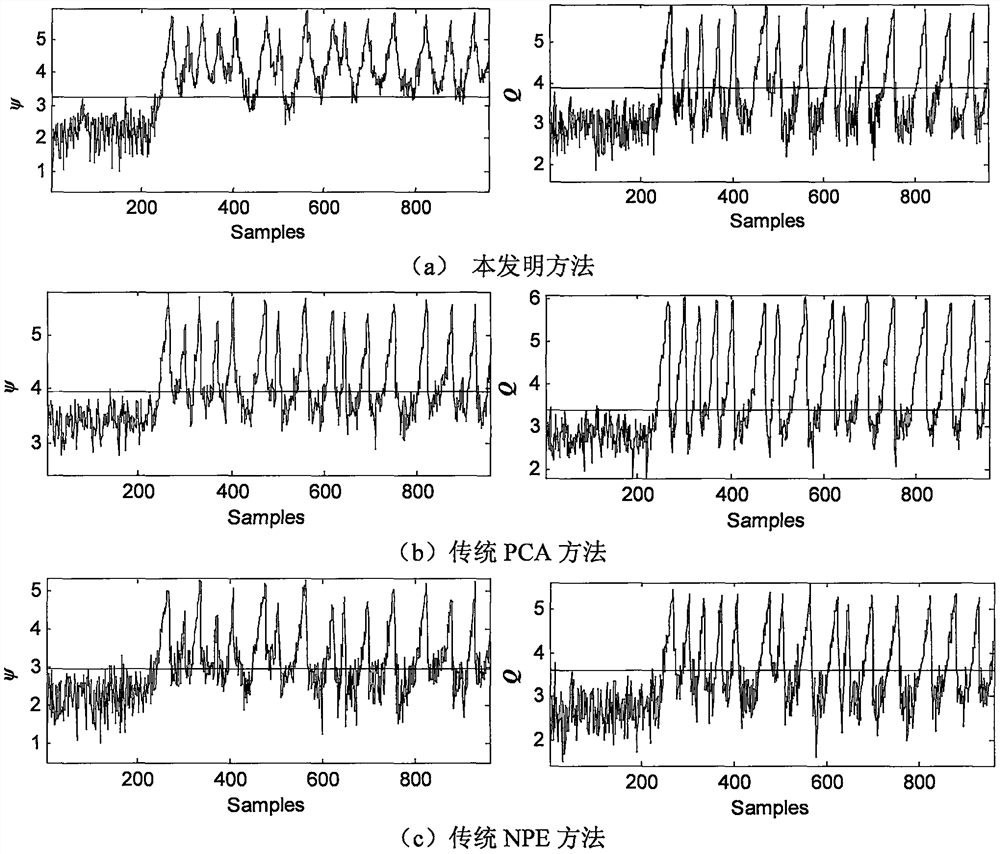
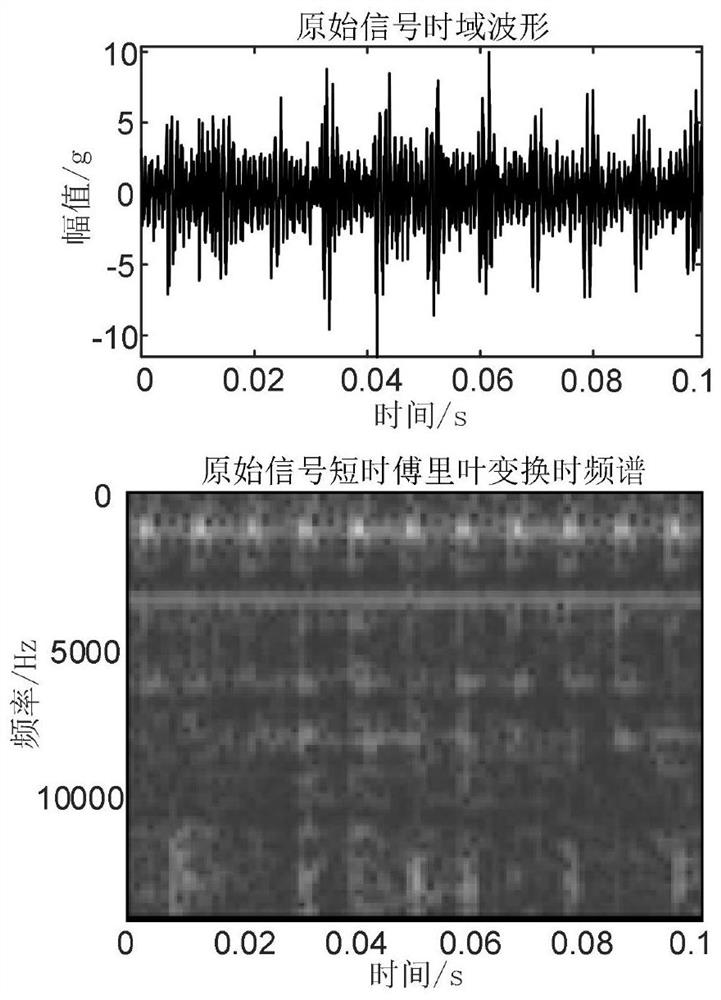
Monitoring method based on image features and LLTSA algorithm for tool wear state
ActiveCN107378641ARealization of wear status monitoringFully automatedMeasurement/indication equipmentsTime–frequency analysisTool wear
The invention relates to a monitoring method based on image features and an LLTSA algorithm for a tool wear state. According to the method, an image texture feature extraction technology is introduced into the field of tool wear fault diagnosis, and monitoring for the tool wear state is realized in combination with three flows of ' signal denoising', 'feature extraction and optimization' and 'mode recognition'. The method comprises the steps of firstly, acquiring an acoustic emission signal in a tool cutting process through an acoustic emission sensor, and carrying out signal denoising processing through an EEMD diagnosis; secondly, carrying out time-frequency analysis on a denoising signal through S transformation, converting a time-frequency image to a contour gray-level map, extracting image texture features through a gray-level co-occurrence matrix diagnosis, and then further carrying out dimensionality reduction and optimization on an extracted feature vector through a scatter matrix and the LLTSA algorithm to obtain a fusion feature vector; and finally training a discrete hidden Markov model of the tool wear state through the fusion feature vector, and establishing a classifier, thereby realizing automatic monitoring and recognition for the tool wear state.
Owner:NORTHEAST DIANLI UNIVERSITY
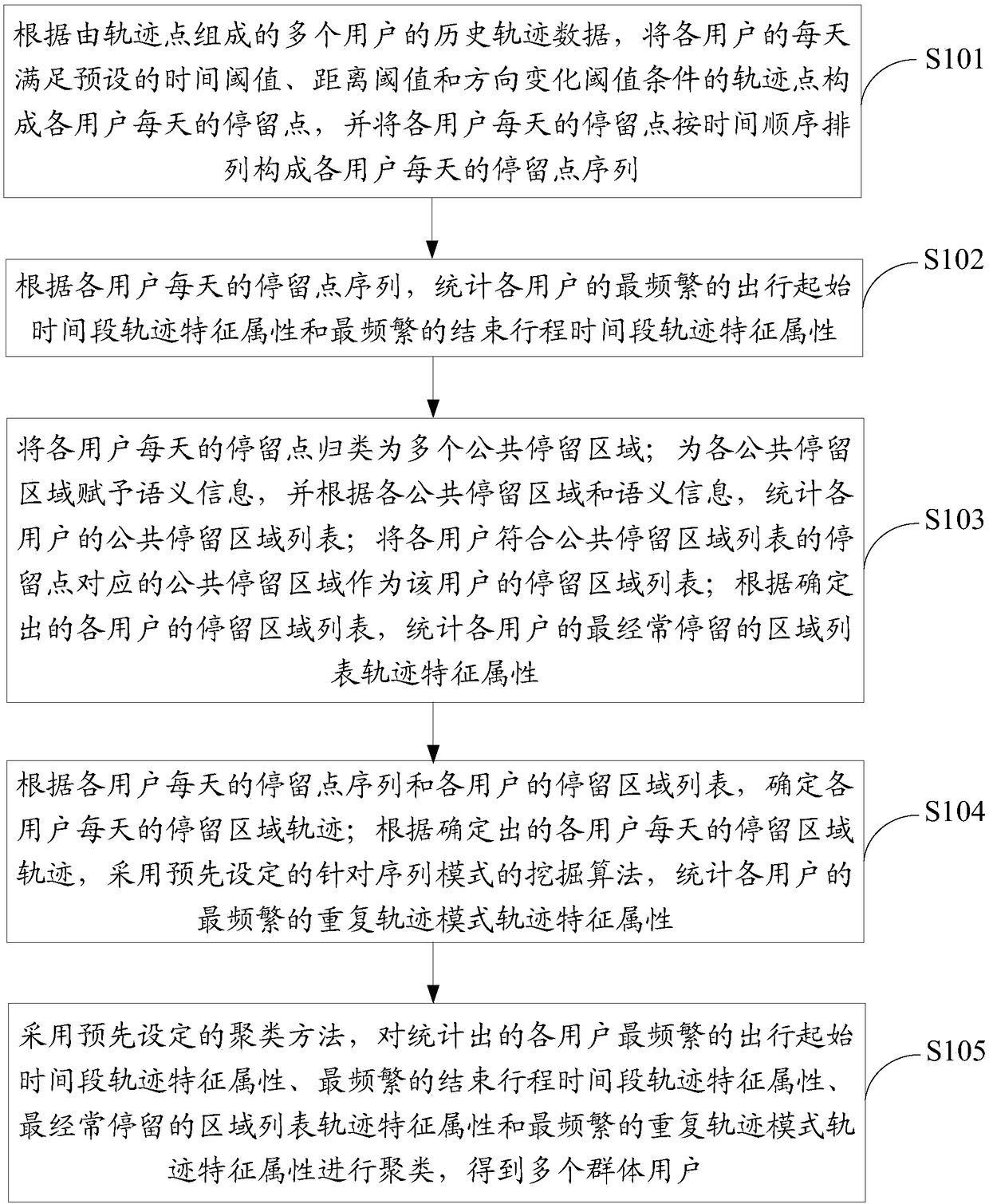
Group user mining method and apparatus
ActiveCN108509434AFull excavationCharacter and pattern recognitionSpecial data processing applicationsStart timeData mining
The invention discloses a group user mining method and apparatus. The method comprises the steps of forming daily stay points of users by daily track points, meeting preset time threshold, distance threshold and direction change threshold conditions, of the users according to historical track data, consisting of the track points, of the users, and classifying the daily stay points of the users into multiple public stay regions with semantic information; based on the stay points meeting the preset time threshold, distance threshold and direction change threshold conditions and the public stay regions with the semantic information, performing statistics on most frequent travel starting time period track feature attributes, most frequent travel ending time period track feature attributes, most frequent stay region list track feature attributes and most frequent repeated track mode track feature attributes of the users; and clustering the four track feature attributes of the users into multiple group users by adopting a preset clustering method. Therefore, the group users can be mined more comprehensively based on the historical track data.
Owner:CHINA MOBILE COMM LTD RES INST +1
Vulnerability mining detection method, server, device and system
The invention discloses a vulnerability mining detection method, server, device and system. The method comprises the following steps: acquiring suspicious sample logs uploaded by clients; performing duplication elimination on the acquired suspicious sample logs; and inputting suspicious sample logs left after duplication elimination into a sandbox, performing scanning to obtain a scanning log, and determining whether samples corresponding to the suspicious sample logs have vulnerabilities or not according to the scanning log. In the scheme, the clients are taken as probes spreading all over the Internet to collect the suspicious sample logs corresponding to suspicious files, so that relevant information of the samples in which vulnerabilities exist possibly in the Internet can be mined comprehensively. Then, samples in which security vulnerabilities exist really are determined from the samples in which the vulnerabilities exist possibly according to the scanning log, so that actual security situations of the samples are determined. Scanning is performed in the sandbox on a server side, so that an enclosed running environment is provided for the suspicious sample logs, and the security of the server side in a detection process is ensured.
Owner:360 TECH GRP CO LTD
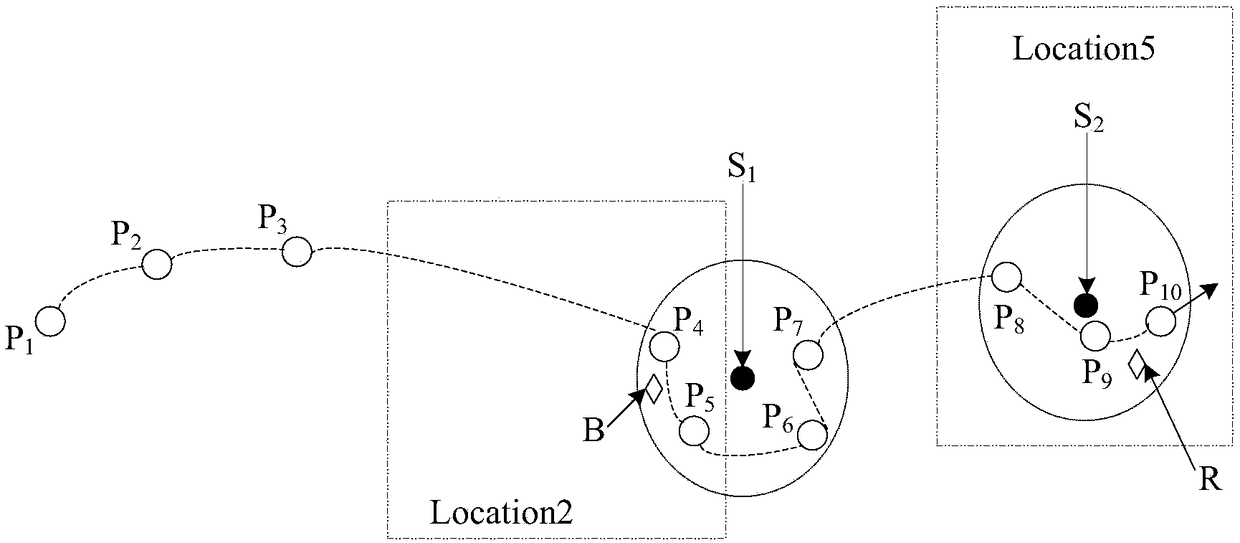
Mobile phone user behavior similarity analysis method based on mobile big data
PendingCN110572813AHigh degree of business fitAble to learnMachine learningNetwork data managementSimilarity analysisCrowds
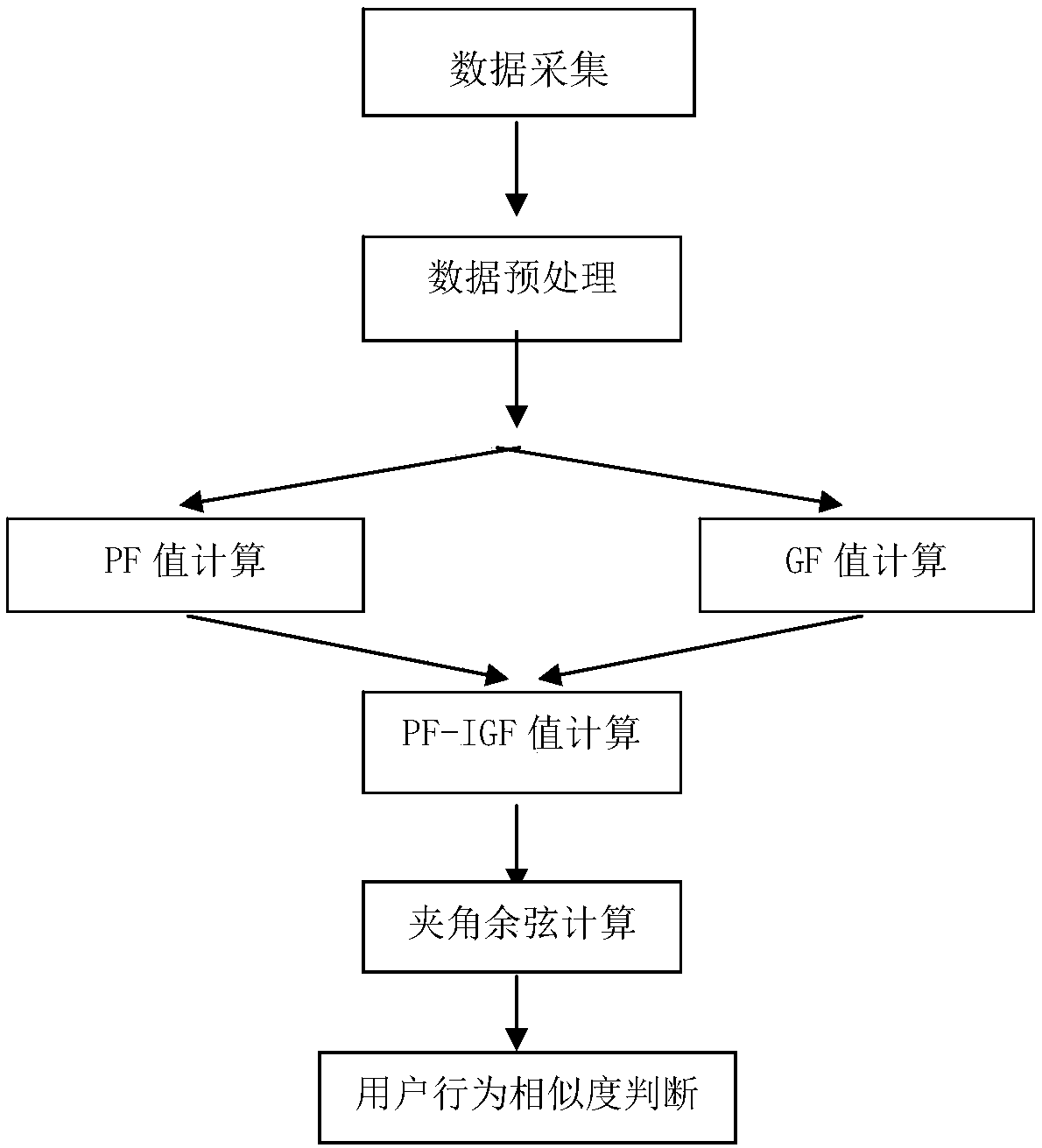
The invention provides a mobile phone user behavior similarity analysis method based on mobile big data, and the method comprises the steps: collecting the movement track information of a user group in a time period through the signaling data of a telecom operator; counting the occurrence frequency or residence time length PF of each user in each sector in the time period and the mean value GF ofthe occurrence frequency or residence time length of all the users in each sector, and calculating PF / GF to obtain a PF-IGF value of each user; calculating an included angle cosine value of the PF-IGFvalues of every two mobile phone users, and judging the behavior similarity of the two users according to the obtained included angle cosine value: the larger the included angle cosine value theta is, the closer of the activity behavior tracks of the two mobile phone users are; wherein the smaller the value of the included angle cosine value is, the more irrelevant of the activity behavior tracksof the two mobile phone users are. The method can be used for researching the similarity degree between every two persons and finding the similar crowd of each person in a specified range.
Owner:北京融信数联科技有限公司
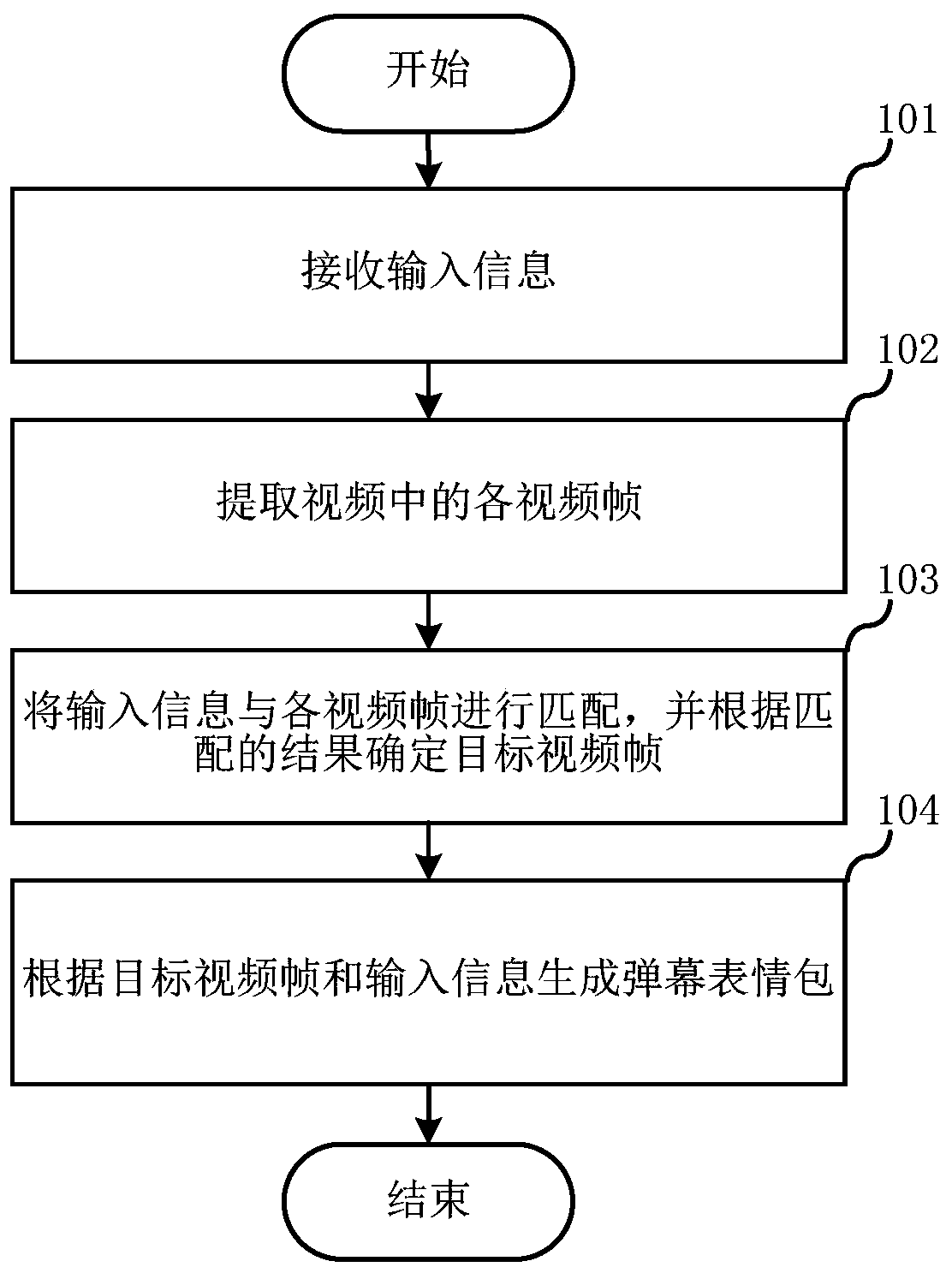
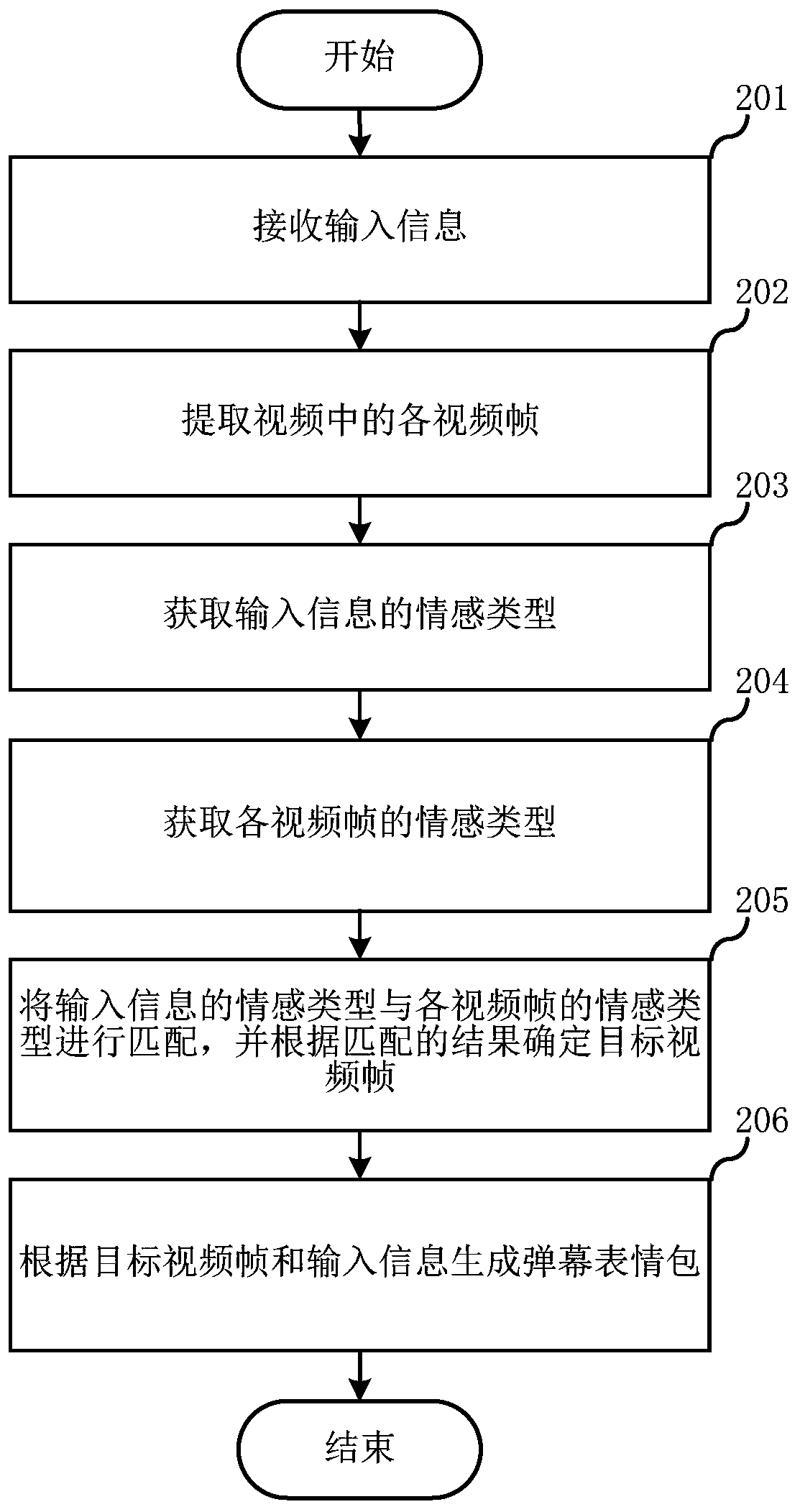
Bullet screen expression package generation method, electronic equipment and readable storage medium
InactiveCN110719525AFull excavationAccurate and comprehensive measurementSelective content distributionComputer hardwareComputer graphics (images)
The embodiment of the invention relates to the technical field of multimedia, and discloses a bullet screen expression package generation method, electronic equipment and a computer readable storage medium. According to the invention, the method for generating the bullet screen expression package comprises the following steps: receiving input information; extracting each video frame in the video;matching the input information with each video frame, and determining a target video frame according to a matching result; and generating the bullet screen expression package according to the target video frame and the input information, so that the efficiency and real-time performance of generating the bullet screen expression package can be improved.
Owner:MIGU CO LTD +1
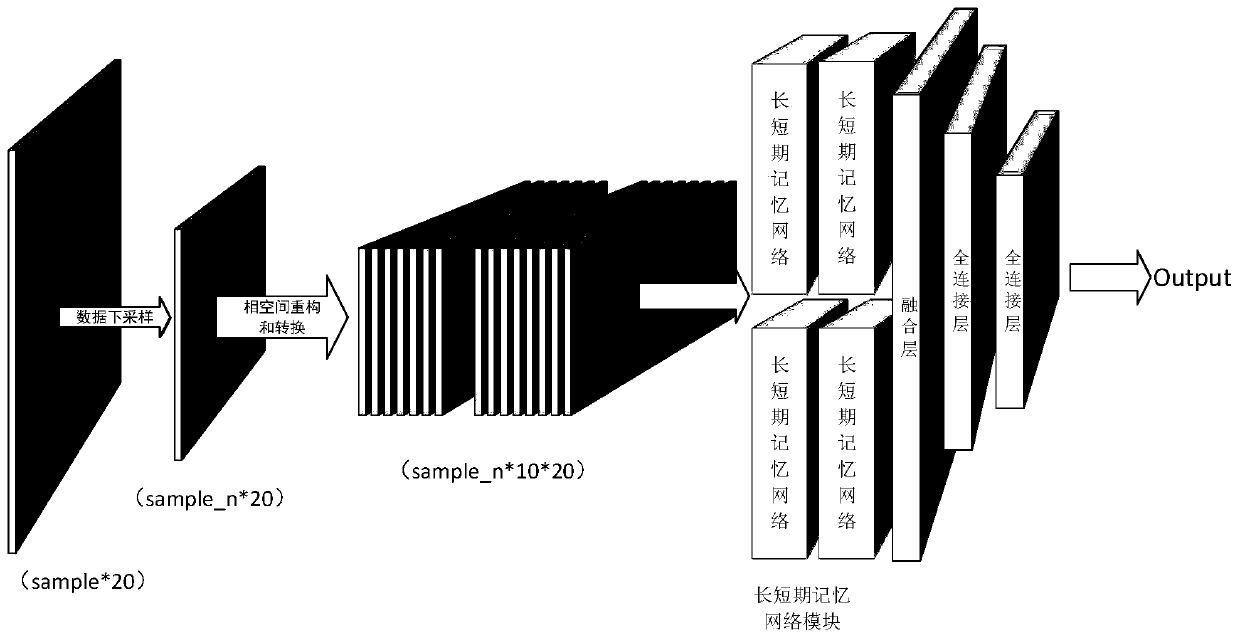
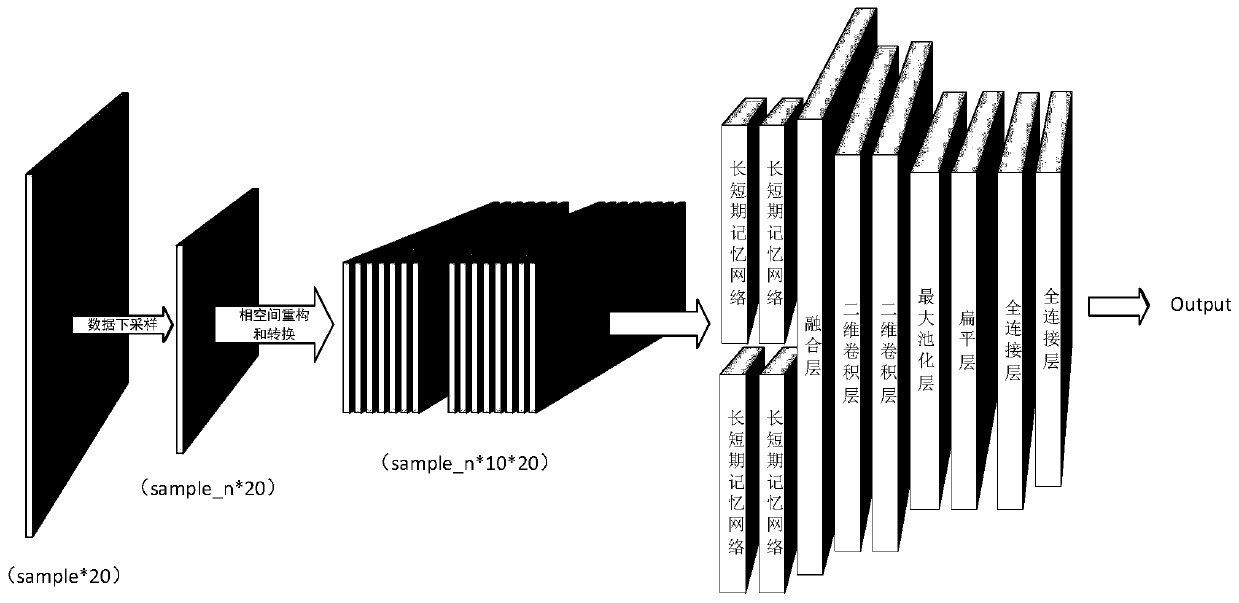
Sensor data classification method based on phase space reconstruction
PendingCN111461201AAvoid defectsReduce sizeCharacter and pattern recognitionNeural architecturesTerm memoryComputer vision
The invention discloses a sensor data classification method based on phase space reconstruction, and the method comprises the steps: 1), mapping a one-dimensional sensor time sequence to an m-dimensional phase space through the phase space reconstruction based on coordinate delay so that sensor data exposes implicit key information to acquire a phase space track matrix; 2) inputting the extracteddata of each sensor at the moment i into a long-short-term memory network module, and setting the time step length input by the long-short-term memory network to be the embedded dimension m of phase space reconstruction; and 3) inputting the RGB matrix of the state information analogy image output by each long-term and short-term memory network into a two-dimensional convolutional neural network module, and inputting features extracted by the two-dimensional convolutional neural network into a full connection layer to obtain a classification result. The problems of limitation of an original one-dimensional sensor data structure and limitation of sensor data classification accuracy are solved, and the sensor data at the time point can be accurately classified.
Owner:CHONGQING UNIV +1
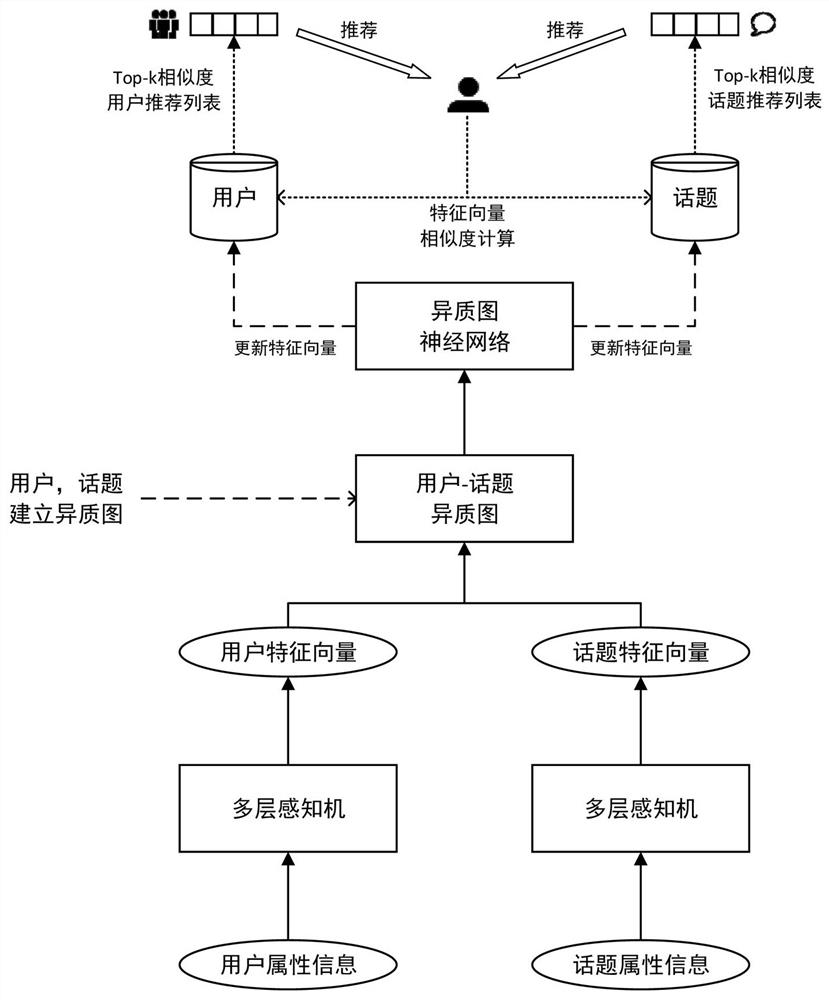
Social recommendation method based on multi-feature heterogeneous graph neural network
ActiveCN113254803AFull excavationImprove experienceData processing applicationsDigital data information retrievalInformation transmissionData science
The invention discloses a social recommendation method based on a multi-feature heterogeneous graph neural network. The method comprises the following steps: extracting various attribute information of social network users and topics for coding; processing the user coding information and the topic coding information through a multi-layer perceptron to obtain initial feature vector representation of each user and topic; establishing a heterogeneous graph by taking users and topics as nodes, inputting the heterogeneous graph into a heterogeneous graph neural network, performing information transmission in the graph in combination with an attention mechanism, and updating feature vector representation; and performing similarity calculation on the user feature vectors, and selecting top-k users and top-k topics with the highest similarity with the user vectors for recommendation. Various types of attribute information of the users and the topics is extracted at the same time, the users and the topics serve as nodes at the same time to establish the heterogeneous graph, social information can be mined more comprehensively, information transmission and aggregation are carried out through the heterogeneous graph neural network, features of the users and interested topics of the users are deeply fused, and recommendation accuracy and user experience are improved.
Owner:JINAN UNIVERSITY
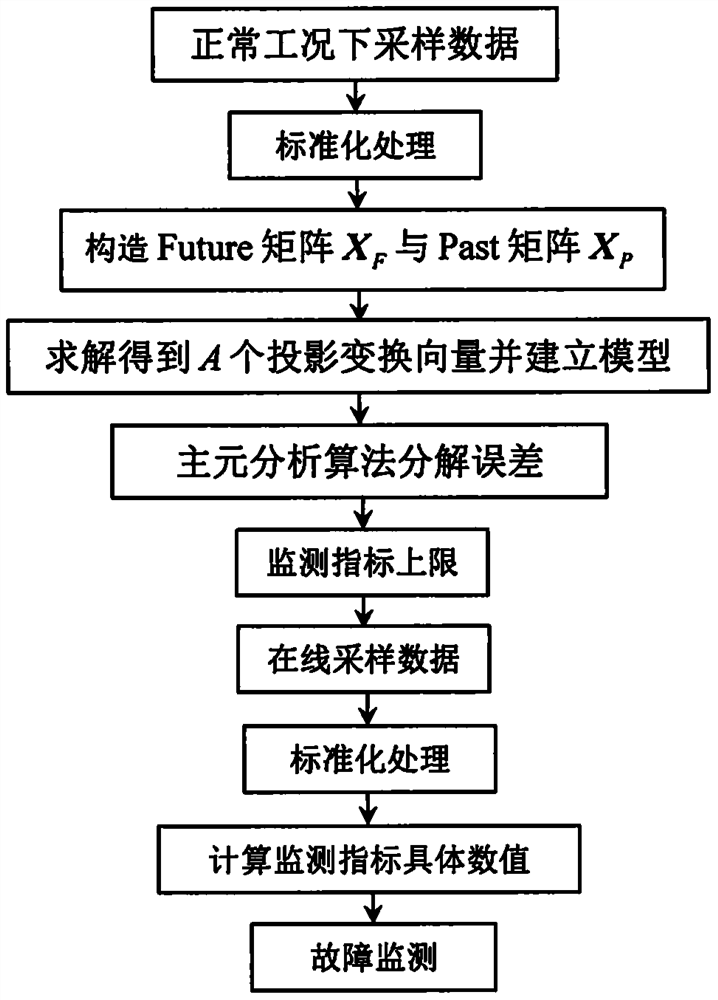
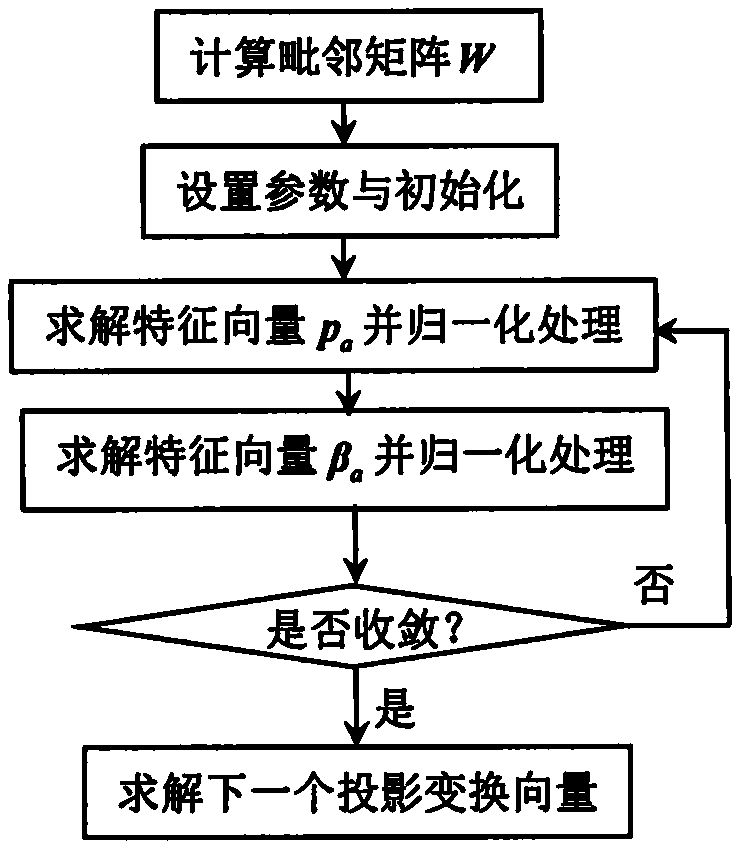
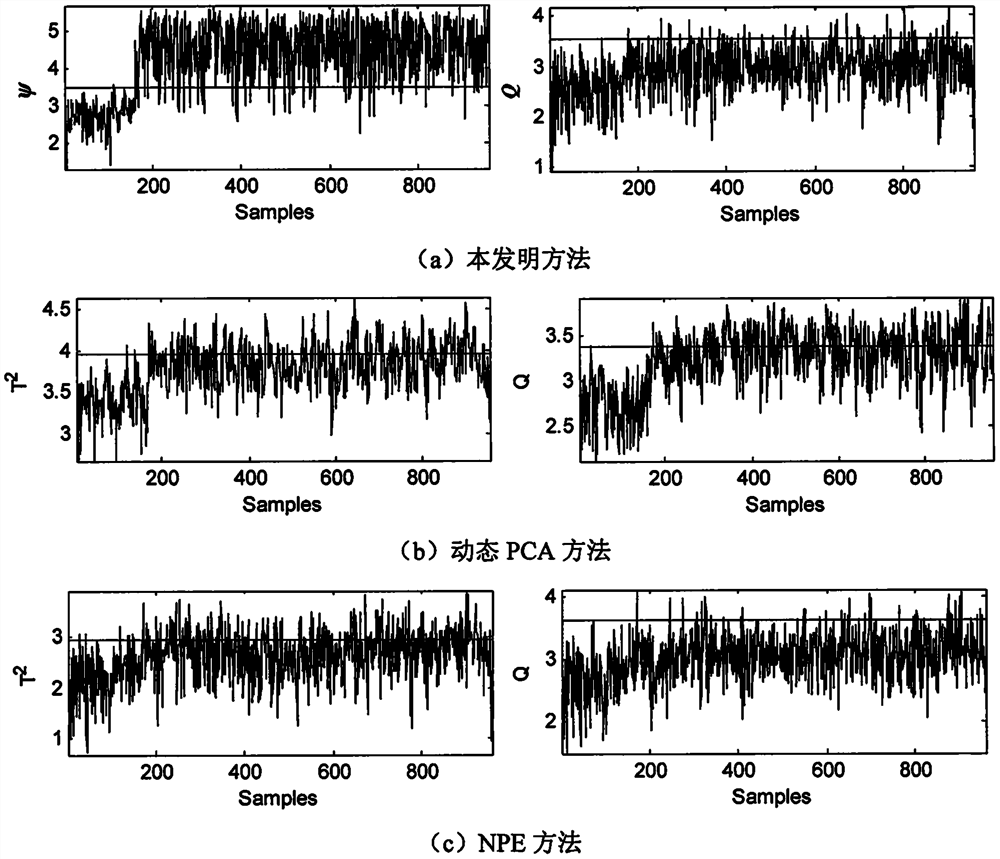
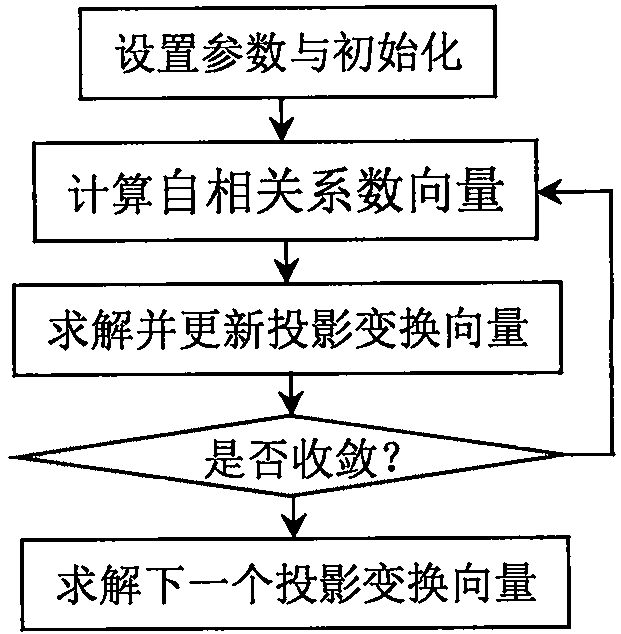
Fault monitoring method based on sequence correlation locality preserving projection algorithm
ActiveCN111913460AGuaranteed OrthogonalityFull excavationProgramme controlElectric testing/monitoringFeature miningAlgorithm
The invention discloses a fault monitoring method based on a sequence correlation locality preserving projection algorithm, and aims to infer a brand-new data feature mining algorithm and implement fault monitoring based on the algorithm. Specifically, the method comprises the following steps: combining time sequence correlation maximization and local neighbor structure minimization into a targetfunction; in the solving process, guaranteeing the mutual orthogonal characteristic between the projection transformation vectors; and finally, executing fault monitoring by utilizing the extracted potential features and model errors. Compared with a conventional method, a sequence correlation locality preserving projection algorithm involved in the method is a brand-new feature extraction algorithm, considers the autocorrelation features and local neighbor features at the same time in the projection transformation process, guarantees the orthogonal characteristic of projection transformationvectors, and can mine the hidden useful information in the training data more comprehensively. Therefore, the method provided by the invention is a more preferable fault monitoring method.
Owner:NINGBO UNIV
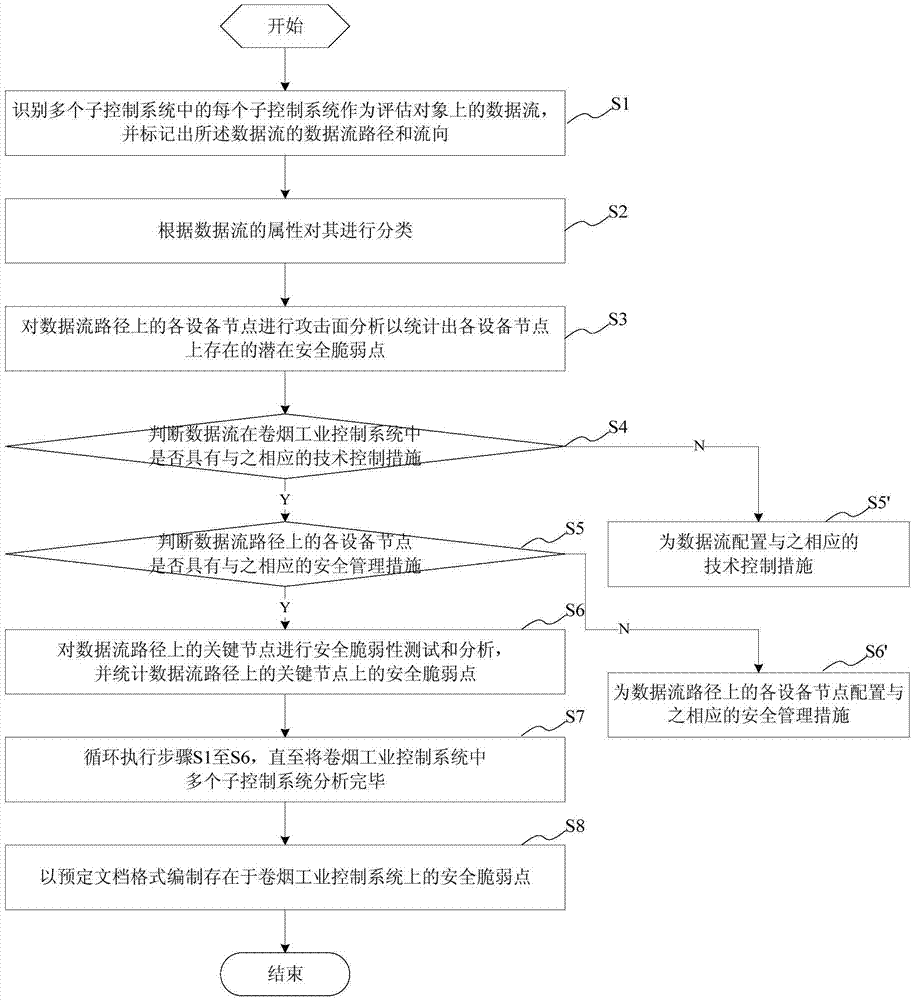
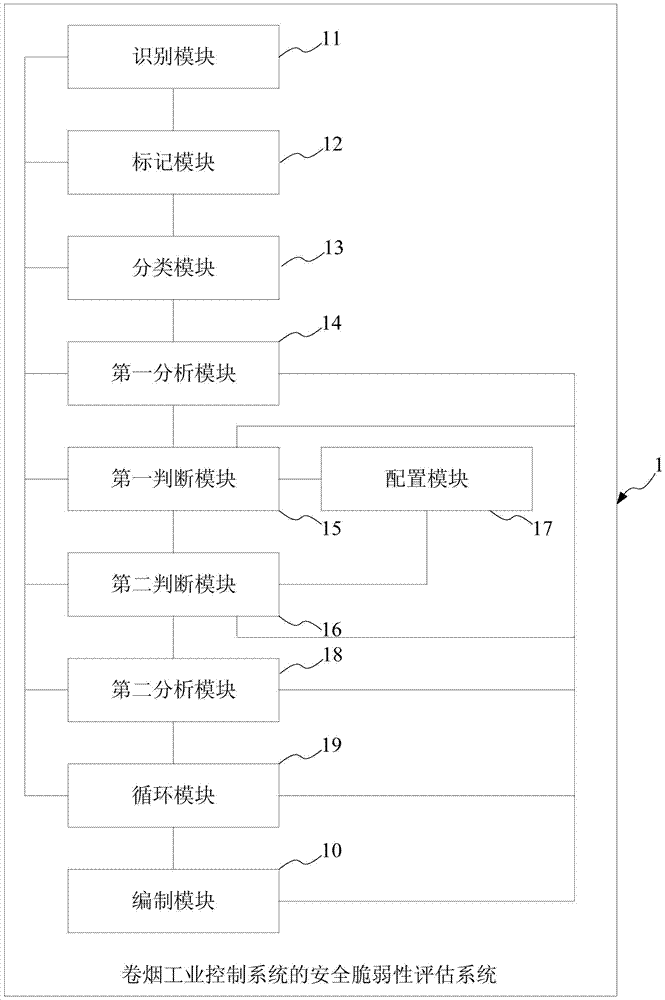
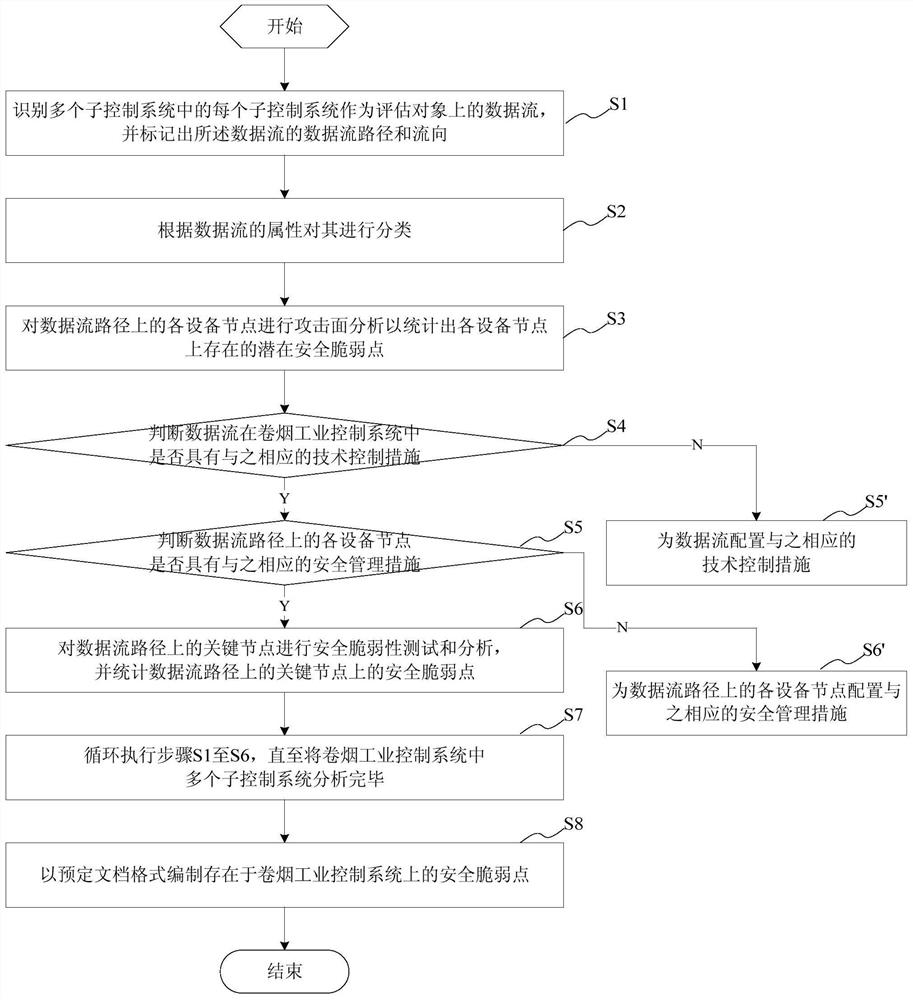
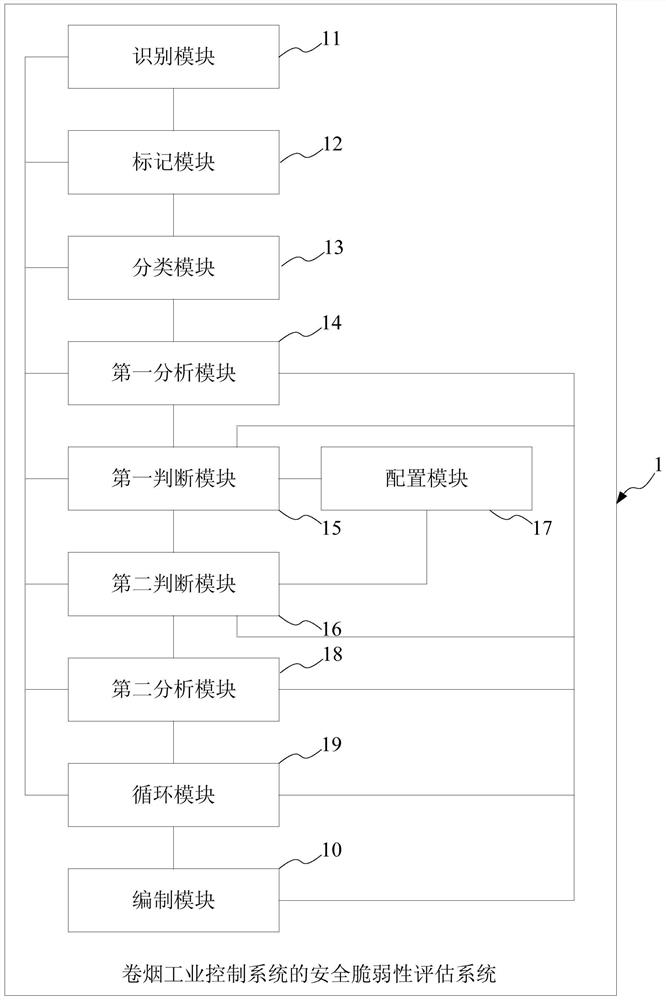
Security vulnerability assessment method, system and device for cigarette industry control system
The invention provides a security vulnerability assessment method for a cigarette industry control system. The method comprises the steps of identifying data streams, and tagging data stream paths and stream directions of the data streams; classifying the data streams according to attributes of the data streams; analyzing an attack surface; judging whether the data streams have technical control measures corresponding to the data streams in the cigarette industry control system or not; if yes, judging whether equipment nodes on the data stream paths have security management measures corresponding to the equipment nodes or not; if yes, performing security vulnerability testing and analysis on key nodes on the data stream paths, performing statistics on security vulnerability points on the key nodes on the data stream paths, and compiling the security vulnerability points existent in the cigarette industry control system in a predetermined document format; and if the equipment nodes on the data stream paths do not have the security management measures corresponding to the equipment nodes, configuring the security management measures corresponding to the equipment nodes for the equipment nodes on the data stream paths, and if the data streams do not have the technical control measures corresponding to the data streams in the cigarette industry control system, configuring the technical control measures corresponding to the data streams for the data streams. According to the security vulnerability assessment method, the security vulnerability of the cigarette industry control system can be assessed more comprehensively and more accurately.
Owner:SHANGHAI TOBACCO GRP CO LTD
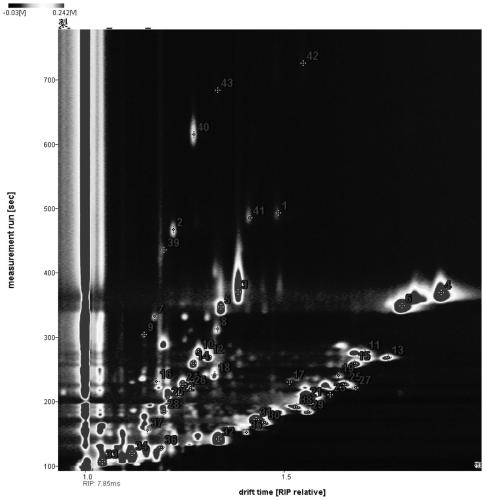
GC-IMS pear production place distinguishing method based on aromatic substance fingerprint spectrum
PendingCN111398470AFull excavationGuaranteed accuracyComponent separationMaterial analysis by electric/magnetic meansPEARStatistical analysis
The invention discloses a GC-IMS pear production place distinguishing method based on an aromatic substance fingerprint spectrum. According to the invention, a headspace gas chromatography-ion mobility spectrometry instrument is used for detecting pears from different producing areas; GC-IMS sample data are obtained; the GC-IMS sample data is subjected to statistical analysis through LAV analysissoftware and GC * IMS Library Search Software qualitative software of the instrument, and GC-IMS fingerprint spectrums of volatile aroma components of the pears from all production places are obtainedfor distinguishing the production places of the pears. The GC-IMS technology is applied to collection and trace analysis of complex aroma substances in the pears from different producing areas, comprehensive fingerprint information is provided for distinguishing the producing areas of the pears, rapid and accurate distinguishing of the producing areas of the pears from different producing areas is achieved, and theoretical basis and data support are provided for identifying and tracing the producing areas of the pears.
Owner:INST OF QUALITY STANDARDS & TESTING TECH FOR AGRO PROD OF SHANDONG ACADEMY OF AGRI SCI
Physiological parameter measuring method based on multi-scale fusion network
ActiveCN112806977AGood for daily monitoringRealize measurementEvaluation of blood vesselsSensorsContinuous measurementSignal quality
The invention provides a physiological parameter measuring method based on a multi-scale fusion network. The method comprises the following steps of sampling physiological signals and generating a one-dimensional physiological signal data sequence; performing noise filtering on data fragments meeting the signal quality requirement through data fragment division and signal quality evaluation; performing mathematical transformation on the data fragments to generate a multi-dimensional input data tensor; extracting potential features from input data by utilizing the multi-scale fusion network to obtain estimated values of physiological parameters; by identifying a measurement mode identifier, taking a mean value of all the estimated values as a physiological parameter measurement value in a static mode; and taking a one-dimensional continuous data sequence formed by all the estimated values as a physiological parameter continuous measurement value in a dynamic mode. According to the method, complementary information of different scales in the signals can be fully extracted, accurate measurement of the physiological parameters is achieved, the application range of the method covers the measurement of all the physiological parameters, and the method has certain application value in the fields of cardiovascular disease research and signal processing research.
Owner:FUDAN UNIV
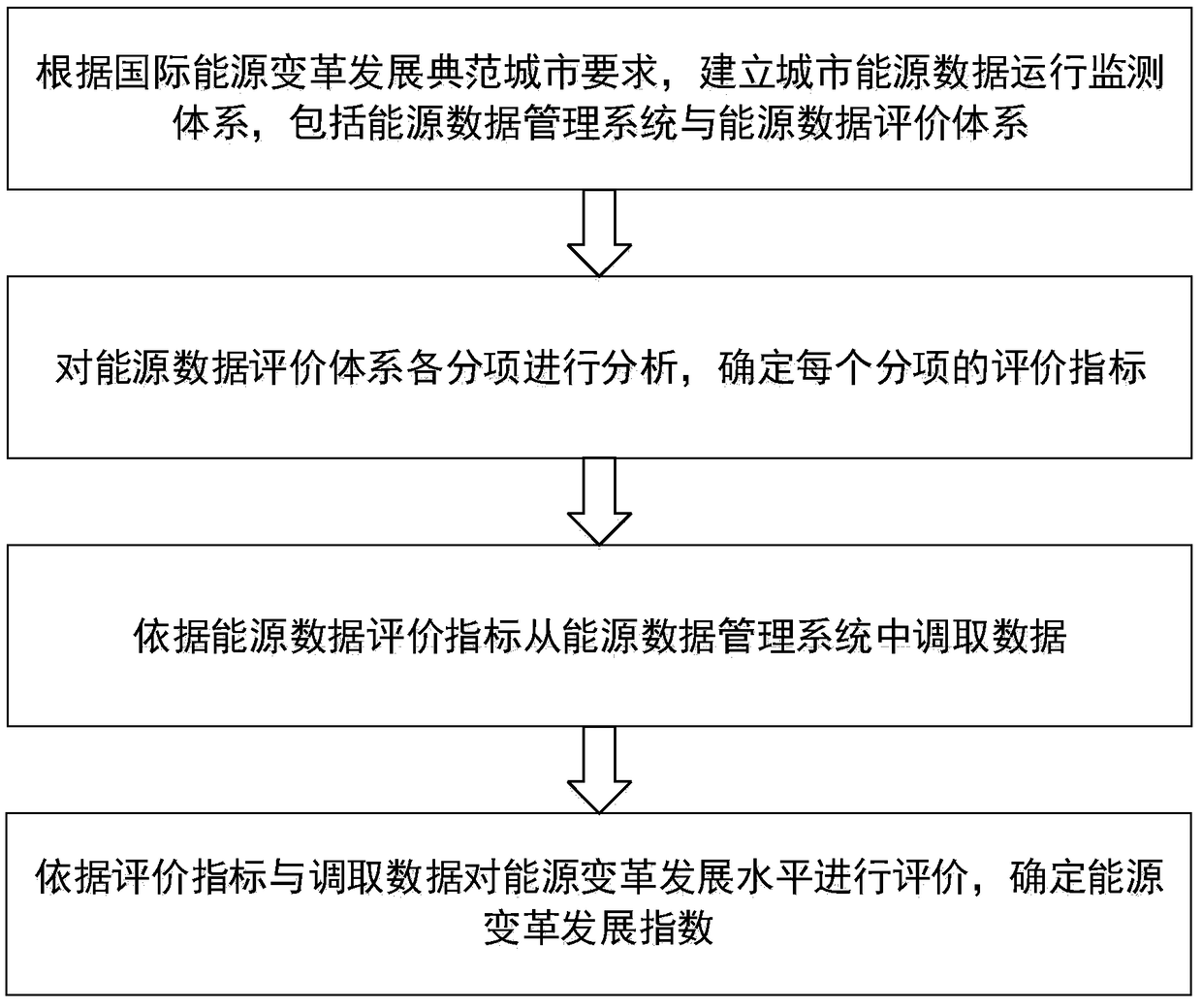
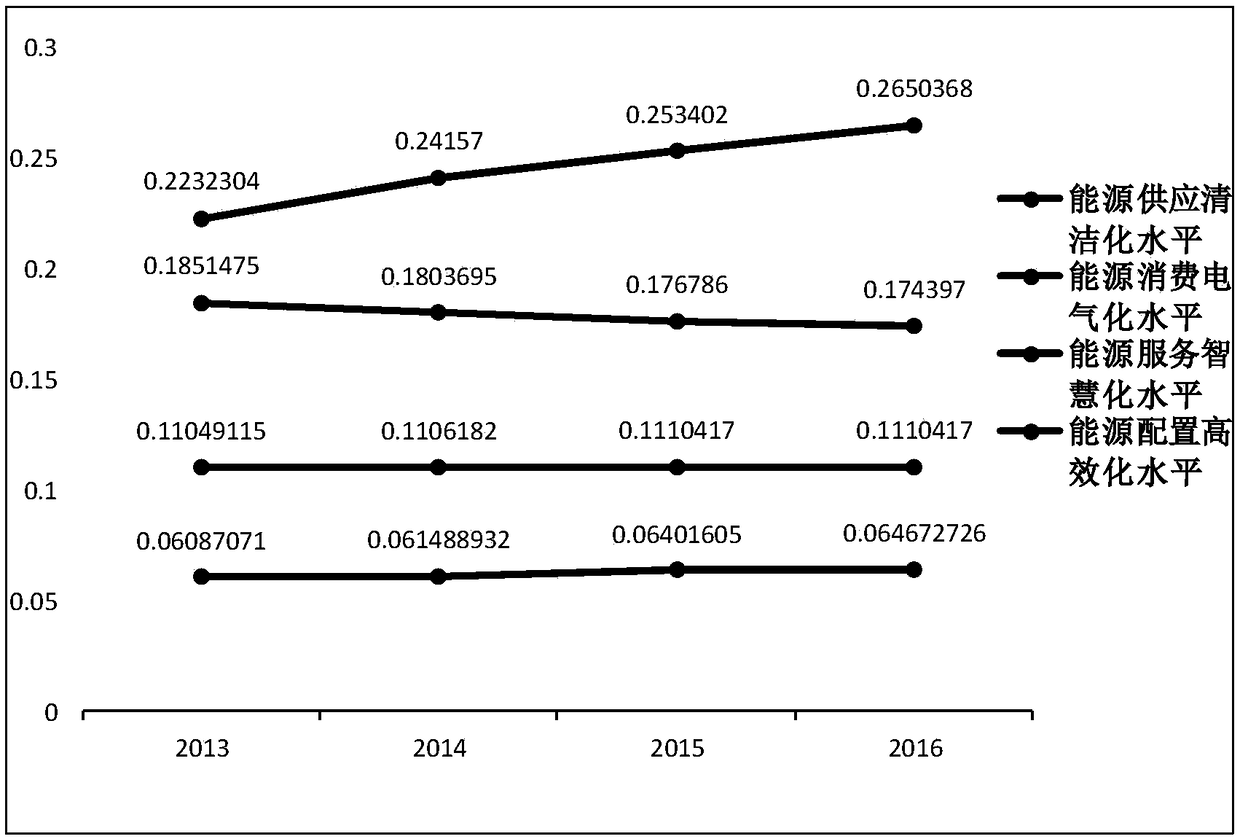
An urban energy data management and operation monitoring method
InactiveCN109409637AFull excavationReasonable planning adviceTechnology managementResourcesEnergy developmentData management
An urban energy data management and operation monitoring method is provided. The method includes mining urban energy data and establishing hierarchical management model of urban energy data; by selecting the evaluation index and applying the analytic hierarchy process to establish the index evaluation model and other steps. The invention has the advantages that the energy data types can be comprehensively mined, a complete energy data management system can be constructed, and the functions thereof can be added at the application layer according to the needs of the energy department. Furthermore, taking the construction of international energy model city as the goal, the quantitative index system which can objectively evaluate the urban energy development status is given, and the reasonableplanning suggestions for urban energy reform are provided.
Owner:JIANGSU ELECTRIC POWER CO
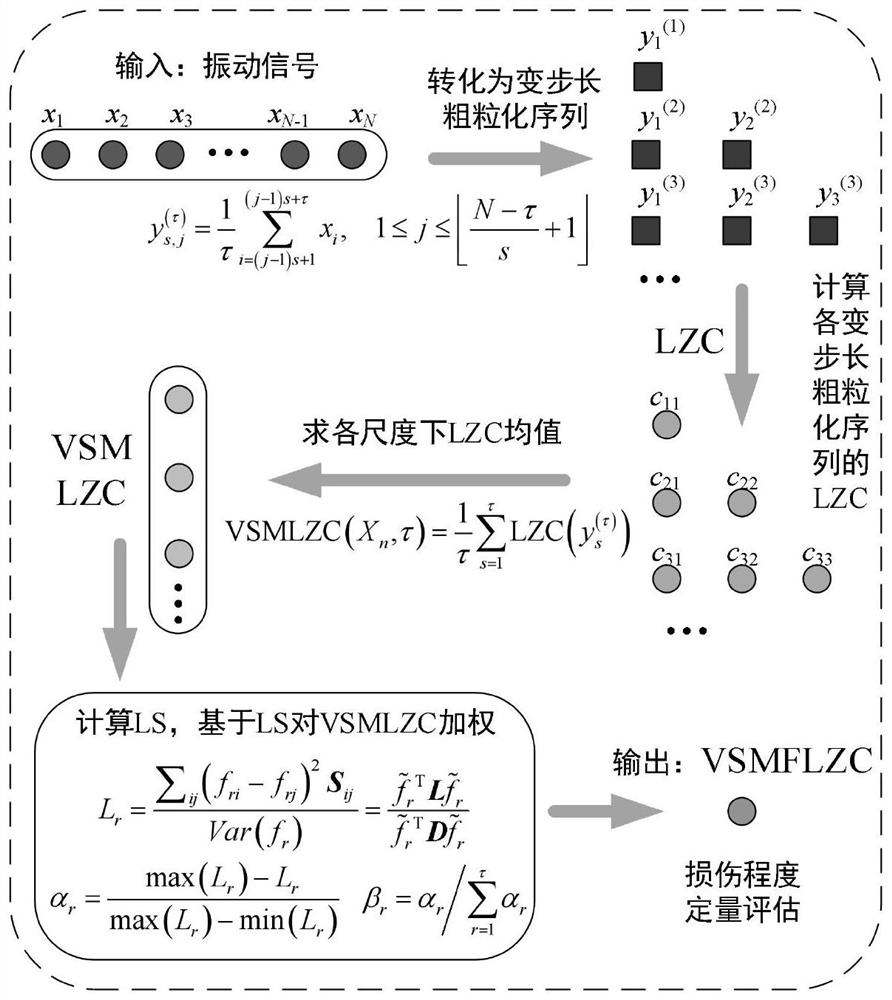
Fault severity evaluation method based on variable-step multi-scale complexity fusion index
PendingCN114037215AFull excavationExtract comprehensiveMachine part testingResourcesRound complexityAlgorithm
The invention discloses a fault severity evaluation method based on a variable-step size multi-scale complexity fusion index. According to the method, firstly, a variable step size multi-scale strategy is put forward, fault features are mined more comprehensively by optimizing a coarse graining process, and the strategy solves a problem that deep information is difficult to mine due to single-scale analysis of a traditional complexity index (LZC); a problem that the calculation result is inaccurate due to the fact that the sequence length of a traditional multi-scale complexity index (MLZC) is shortened along with the increase of the scale is solved, and a variable step size multi-scale complexity index (VSMLZC) is constructed. Compared with a traditional complexity index, the method is advantaged in that fault features can be mined more accurately and comprehensively, and early fault diagnosis and damage degree evaluation of the rotating equipment are achieved.
Owner:SUZHOU UNIV
Combined cutterhead of rectangular top pipe heading machine
The invention discloses a combined cutterhead of a rectangular top pipe heading machine. The combined cutterhead comprises a rectangular cylinder. The outer edge of an excavation surface of the rectangular cylinder is provided with a peripheral guardrail which is arranged in a rectangular manner. Peripheral cutters are equidistantly welded at the front edge position of the peripheral guardrail. One circle of the excavation surface of the rectangular cylinder is provided with reinforcing blocks which are equidistantly welded on one circle of the excavation surface of the rectangular cylinder and are integrally formed with the inner wall of the peripheral guardrail. The middle part of the excavation surface and four hanging corners of the rectangular cylinder are respectively provided with amain installing hole and auxiliary installing holes. Through the combined design of the main cutterhead assembly and the auxiliary cutterhead assembly, an excavation area and excavation strength canbe enlarged; a main cutterhead assembly and an auxiliary cutterhead assembly have the same structure and respectively comprise a wheel hub and outer protecting ring; the axial position of the wheel hub is provided with a fish tail cutterhead; and through the fish tail cutterhead which projects in an axial direction, preliminary fragmentation excavation in a tunneling process of a pipe pushing jackcan be realized; and a pressure which is generated in a tunneling process can be shared through arranging a plurality of web plates.
Owner:淮南中泰矿山装备制造有限公司
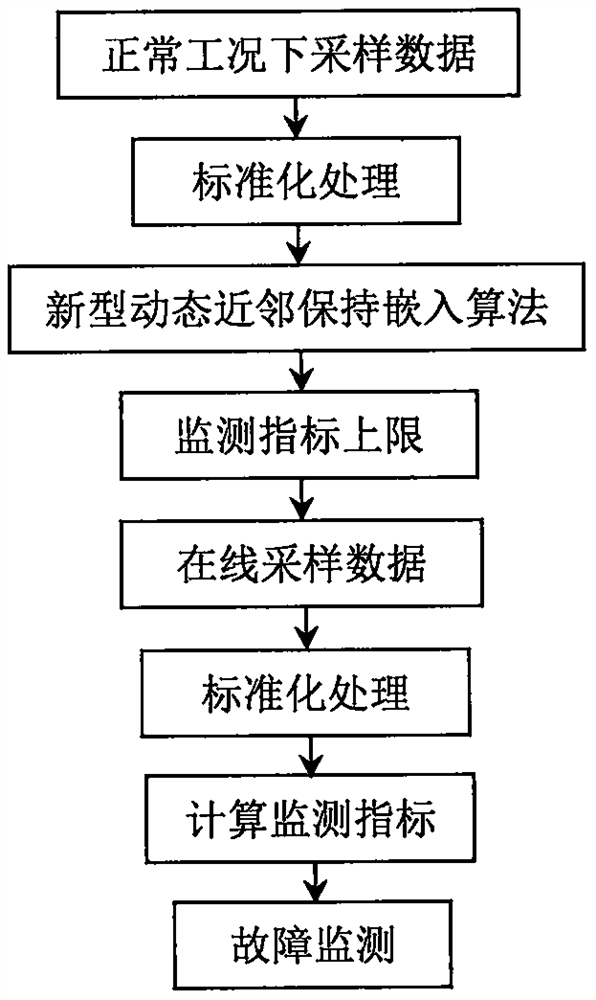
Process monitoring method based on novel dynamic neighbor preserving embedding algorithm
PendingCN111914206AFull excavationGood effectComplex mathematical operationsEngineeringArtificial intelligence
The invention discloses a process monitoring method based on a novel dynamic neighbor preserving embedding algorithm, and aims to solve the problem of how to mine hidden autocorrelation features and local neighbor structure features in training data at the same time and monitor the running state of a production process based on the mining of the hidden autocorrelation features and the local neighbor structure features. The method has the advantages that firstly, the novel dynamic neighbor preserving embedding algorithm involved in the method is a brand-new algorithm, autocorrelation characteristics and local neighbor characteristics are considered at the same time, and hidden useful information in training data can be mined more comprehensively; and secondly, in a specific embodiment, compared with a traditional dynamic process monitoring method, the method provided by the invention can achieve a more excellent effect on fault monitoring. Therefore, the method provided by the inventionis a more optimal dynamic process monitoring method.
Owner:NINGBO UNIV
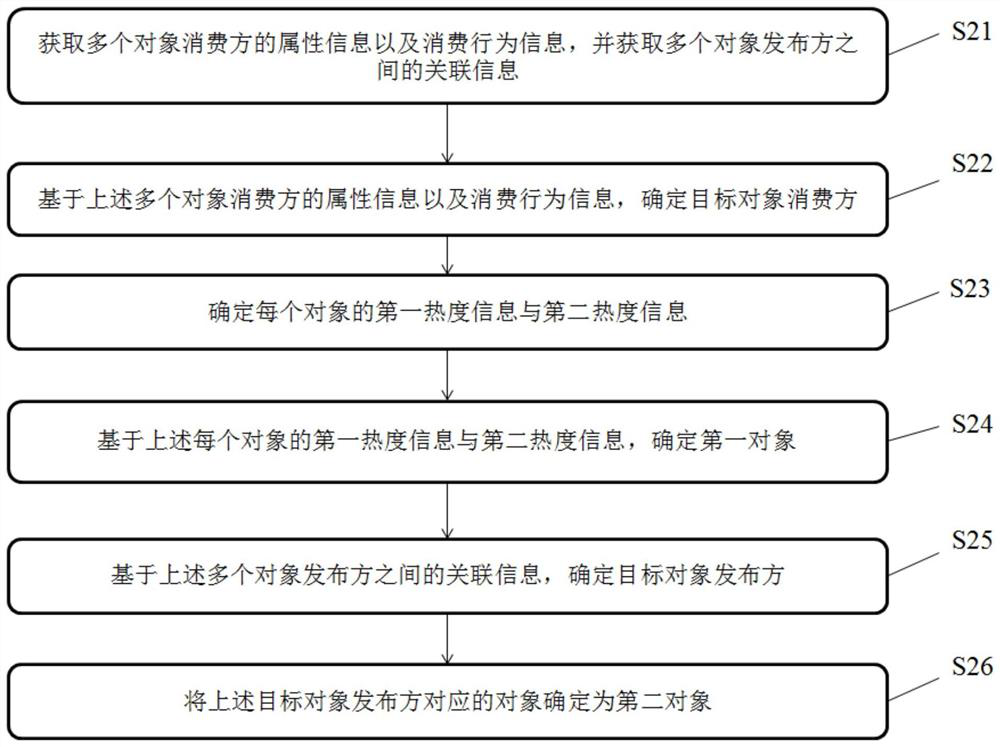
Target object determination method and device and storage medium
PendingCN113468402AQuick digExcavate accuratelyText database queryingSpecial data processing applicationsEngineeringComputer vision
The invention relates to a target object determination method and device and a storage medium, and the method comprises the steps: obtaining the attribute information and consumption behavior information of a plurality of object consumers, and obtaining the association information between a plurality of object publishers; determining a target object consumer based on the attribute information and the consumption behavior information of the plurality of object consumers; determining first popularity information and second popularity information of each object; determining a first object based on the first popularity information and the second popularity information of each object; determining a target object publisher based on the association information among the plurality of object publishers; determining an object corresponding to the target object publisher as a second object; and determining a target object according to the first object and the second object. According to the invention, the target object can be rapidly, accurately and comprehensively mined.
Owner:BEIJING DAJIA INTERNET INFORMATION TECH CO LTD
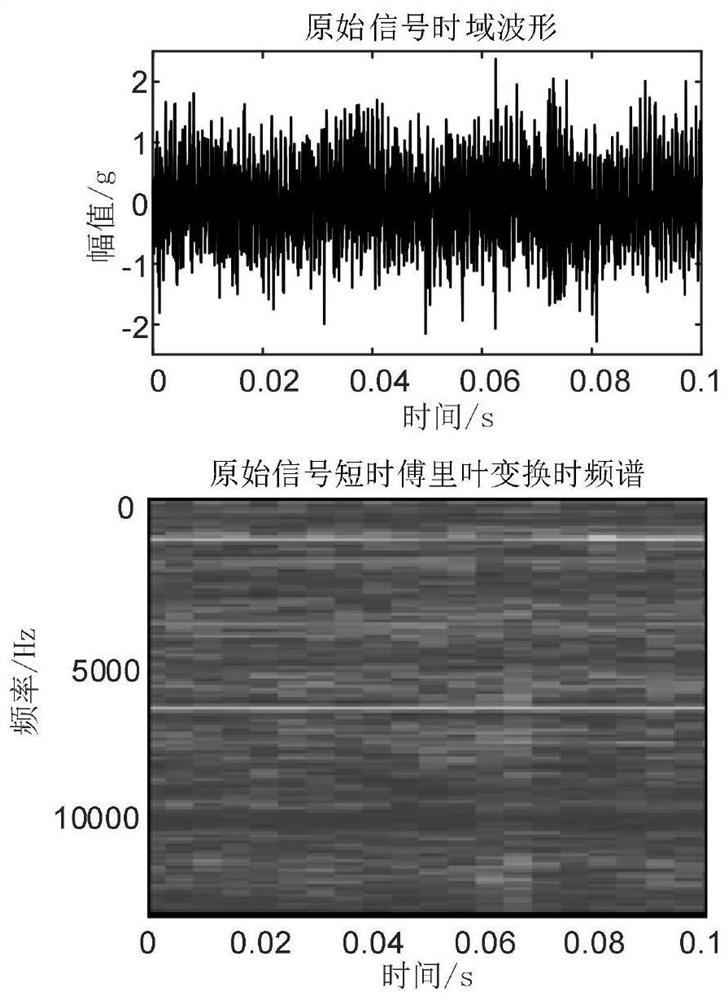
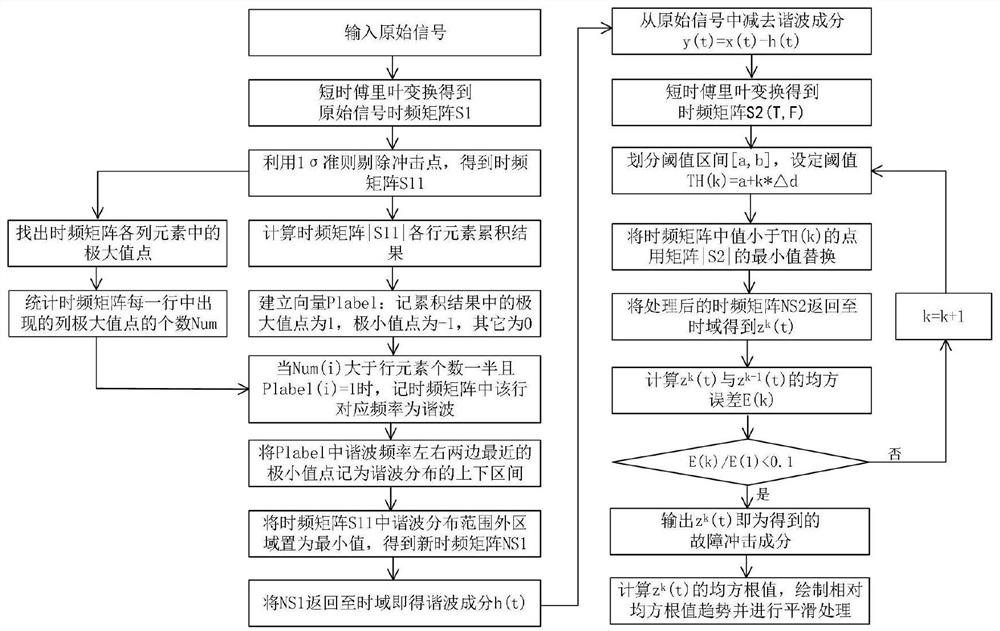
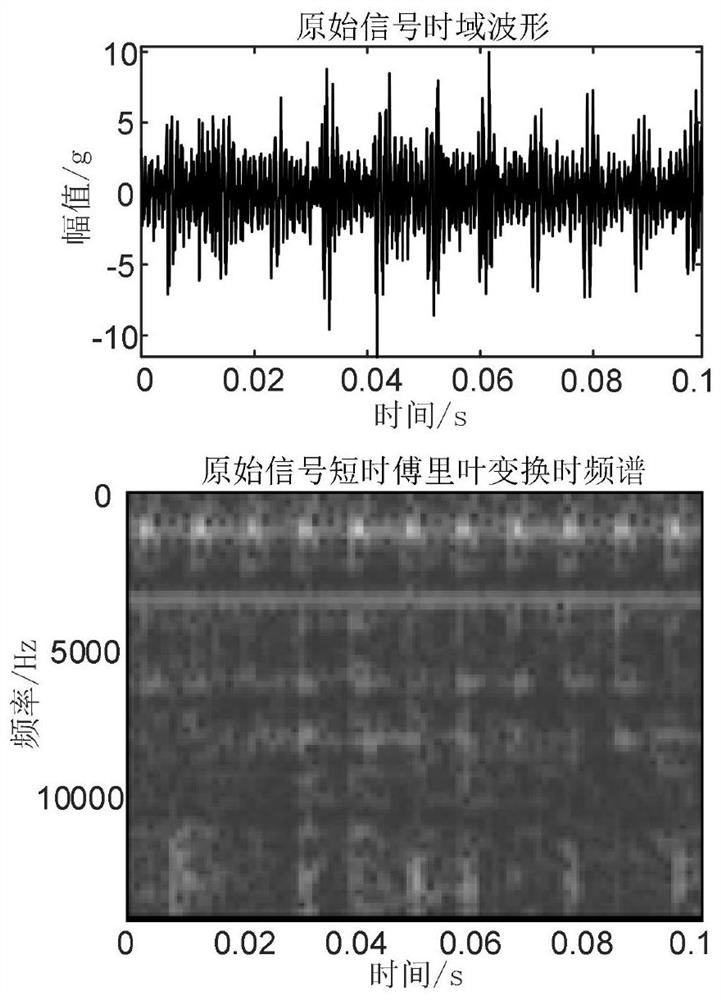
Rolling bearing degradation index extraction method based on time-frequency feature separation
ActiveCN113567127ANon-stationaryEfficiently characterize degradation processesMachine part testingComplex mathematical operationsTime domainFrequency spectrum
The invention discloses a rolling bearing degradation index extraction method based on time-frequency feature separation. The method comprises the steps of firstly calculating a time-frequency spectrum of a bearing original signal, secondly, determining the number of maximum value points at the same moment and the number of maximum value points at the same frequency in the time-frequency matrix, determining the harmonic distribution position and range in combination with the line accumulation result of the time-frequency matrix, retaining a harmonic distribution area, filtering other areas, and performing inverse short-time Fourier transform on the processed time-frequency matrix to a time domain so as to realize extraction of harmonic components, after subtracting the harmonic component from the original signal, extracting the fault impact component through threshold noise reduction, and finally calculating the relative root-mean-square value of the extracted fault impact component to serve as a rolling bearing degradation index. According to the method, the prominent harmonic components in the time-frequency spectrum are filtered in advance based on the time-frequency characteristics so as to enhance the fault impact components, serious distortion generated when the impact components are extracted through threshold noise reduction is avoided, the rolling bearing degradation index is calculated for the extracted fault impact components, and the index can effectively represent the bearing degradation process.
Owner:XI AN JIAOTONG UNIV +1
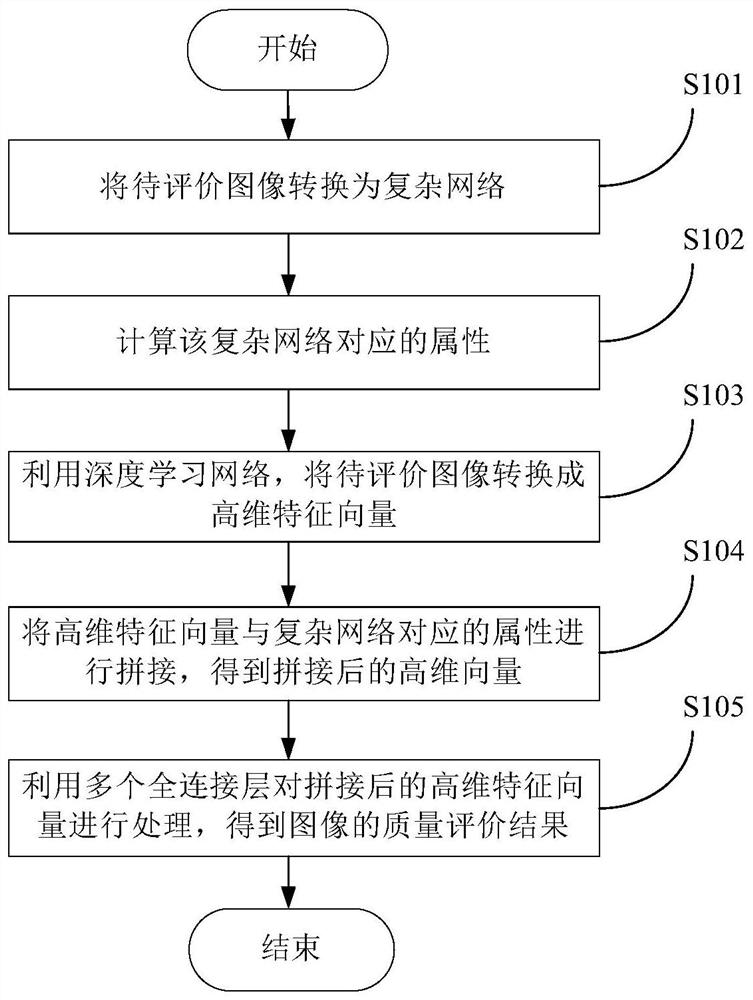
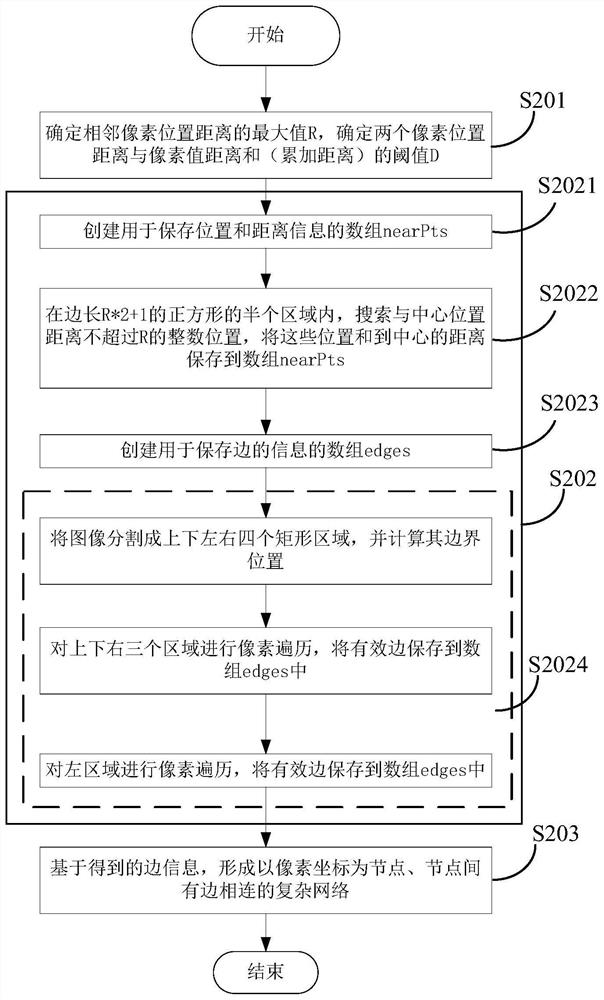
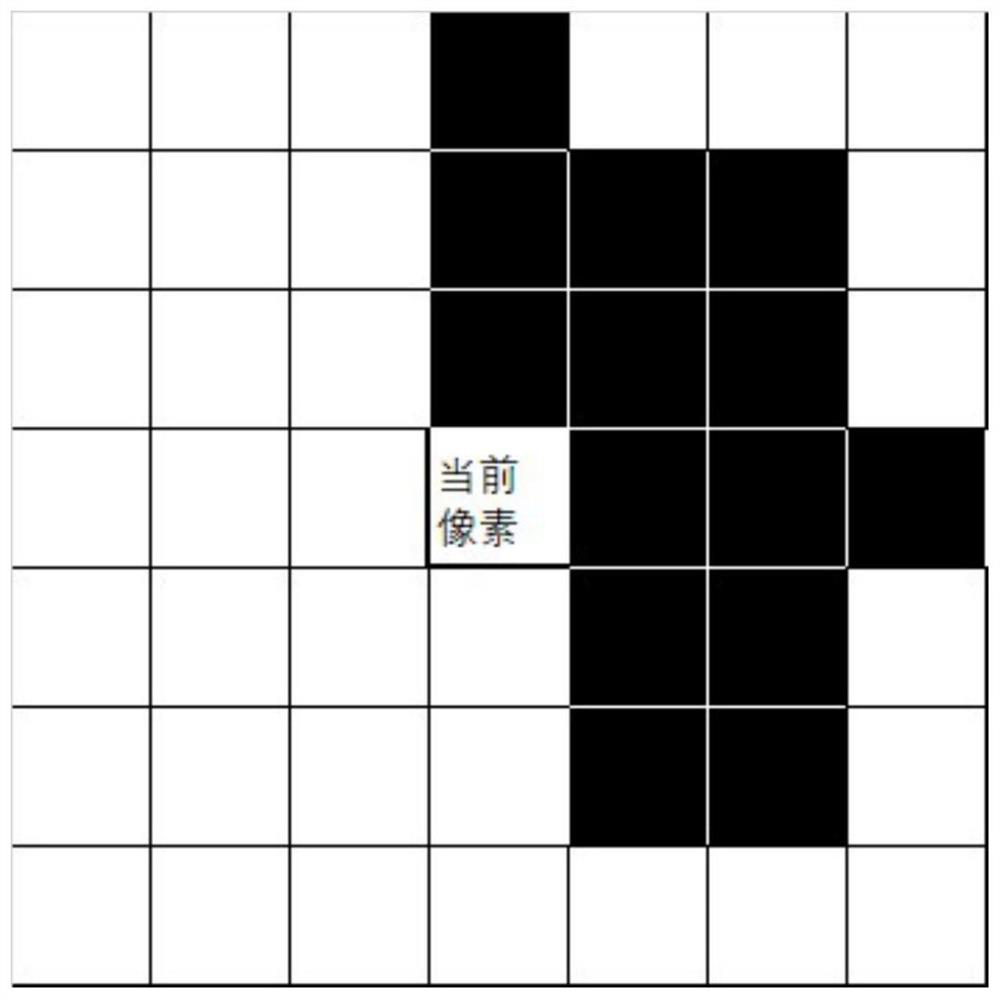
Image quality evaluation method and device based on complex network and storage medium
PendingCN111862084AImprove accuracyFull excavationImage enhancementImage analysisEvaluation resultFeature extraction
The invention provides an image quality evaluation method and device based on a complex network and a storage medium. The method comprises the following steps: quickly converting an image to be subjected to quality evaluation into a complex network; while a mainstream deep learning algorithm is used for carrying out feature extraction on the image, combining the features of a complex network; finally, processing the spliced information through a full connection network, and fully integrating the features extracted in the two different modes together to obtain a final quality evaluation result.Through two different processing modes for the image, the image information is mined more comprehensively, the accuracy of image quality evaluation is improved, and the effect of image quality evaluation is enhanced.
Owner:东软教育科技集团有限公司
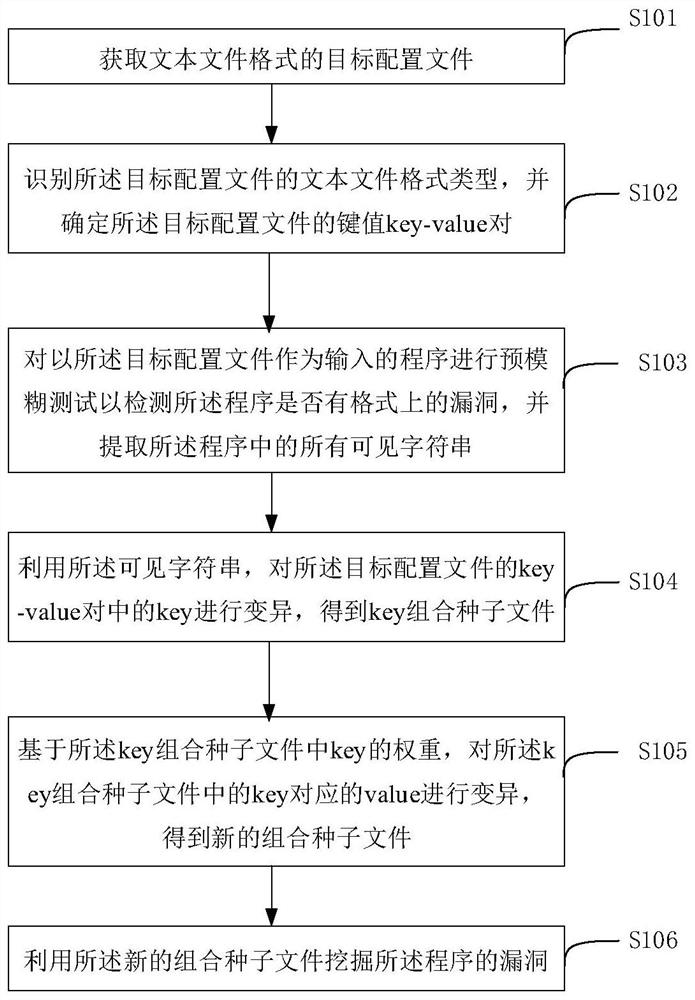
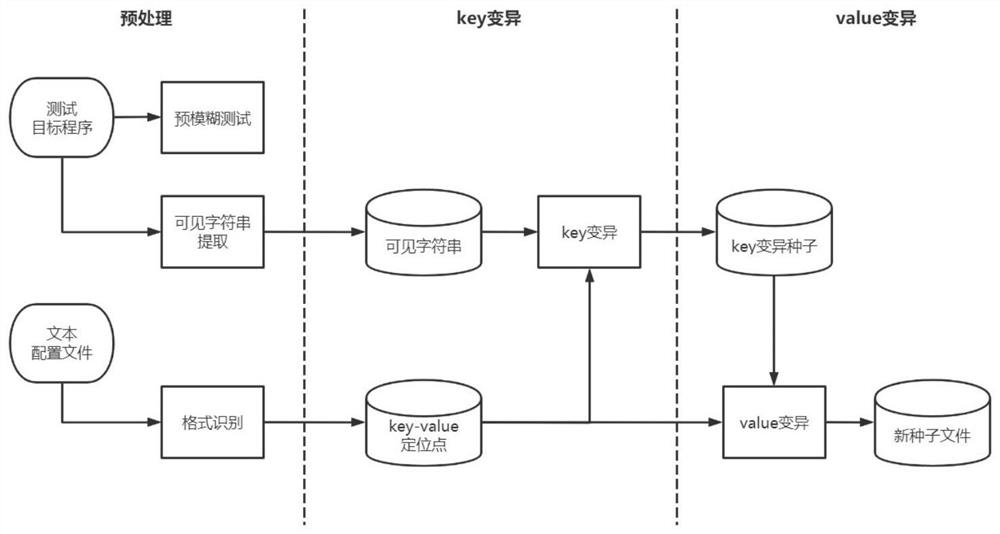
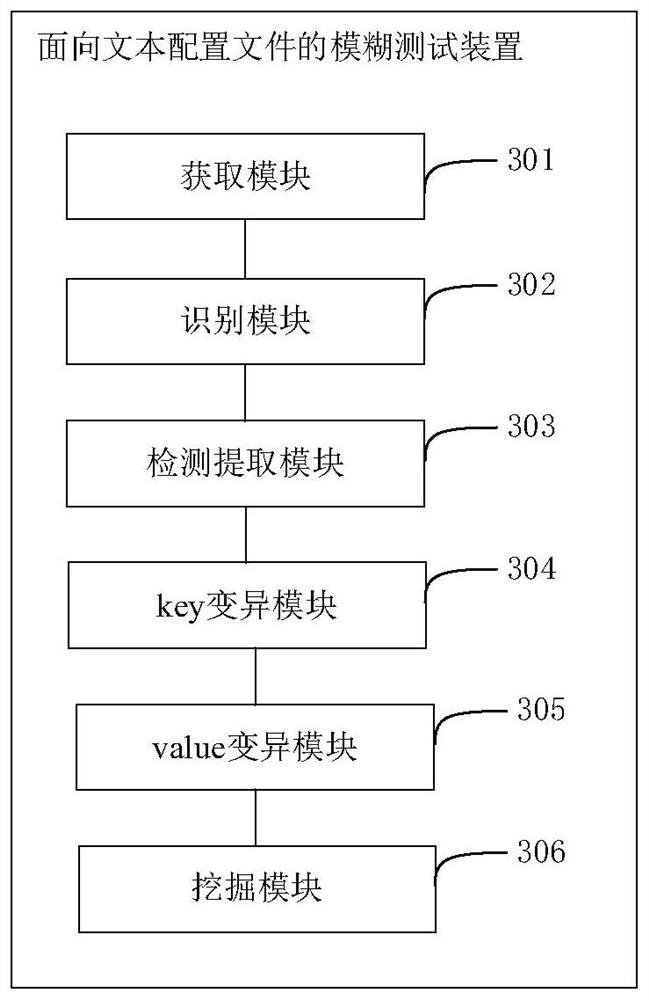
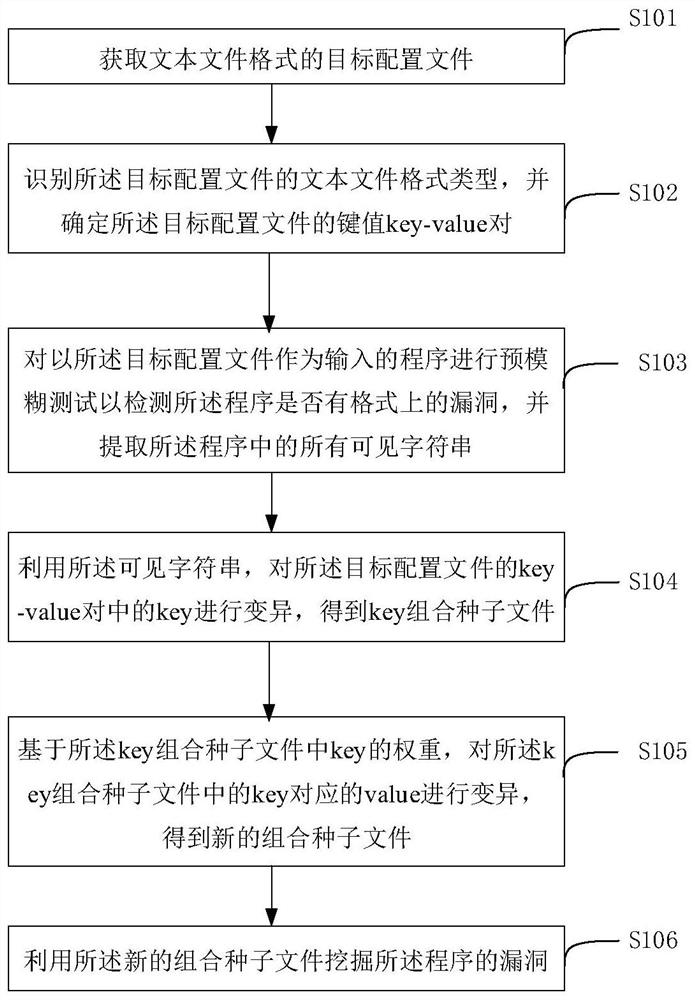
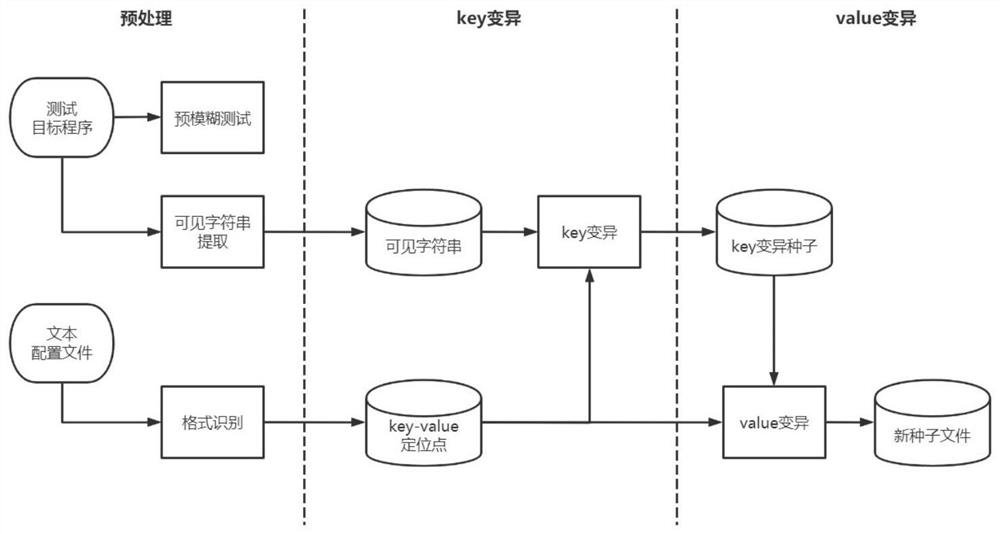
Text configuration file-oriented fuzzy test method and device
ActiveCN111913877AImprove fuzz testing efficiencyFull excavationSoftware testing/debuggingProgramming languageTest efficiency
The embodiment of the invention provides a text configuration file-oriented fuzzy test method and device, and the method comprises the steps: recognizing a text file format type of a target configuration file, and determining a key value key value pair of the target configuration file; performing a pre-fuzzy test on a program taking the target configuration file as an input to detect whether the program has a vulnerability in format or not, extracting all visible character strings in the program, and mutating keys in a key pair of the target configuration file to obtain a key combination seedfile; and on the basis of the weight of the key in the key combination seed file, mutating the value corresponding to the key in the key combination seed file to obtain a new combination seed file, and mining the vulnerability of the program. According to the embodiment of the invention, deep vulnerabilities in a program are comprehensively mined, and the text configuration file-oriented fuzzy test efficiency is improved.
Owner:INST OF INFORMATION ENG CHINESE ACAD OF SCI
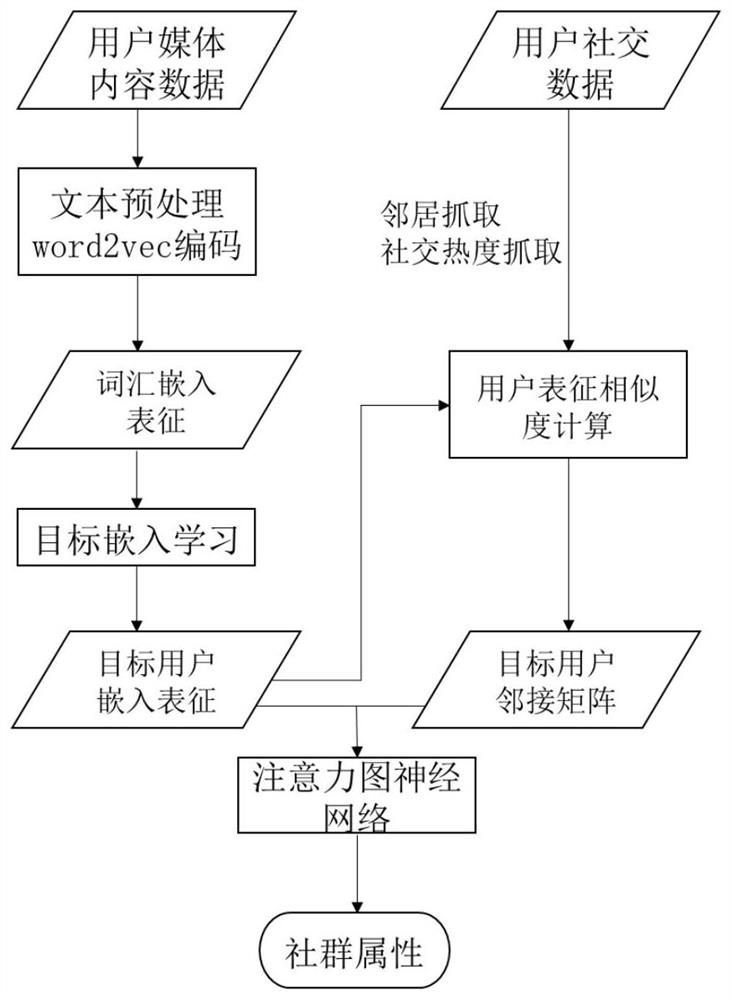
Hidden community attribute acquisition method and system based on attention graph neural network
PendingCN113807978AFully retain the characteristics of community attributesExcavate accuratelyData processing applicationsNatural language data processingSocial mediaGraph neural networks
The invention discloses a hidden community attribute acquisition method based on an attention graph neural network. The method comprises the following steps: learning all vocabularies in a user social media data vocabulary library through a word vector model Word2vec network to obtain embedded representation vectors of all the vocabularies; performing normalization weighting on embedding representation vectors of user social media data vocabularies, and obtaining embedding representation of a target user based on a target embedding layer of a forward full-connection network; based on the user social network and the social activity information, generating embedded representations of neighbor users of the target user, and calculating a weight social matrix according to the embedded representations of the neighbor users; and training a social popularity weighted attention graph neural network according to the weight social matrix, and generating a hidden community attribute classification result of the target user by using the attention graph neural network and the embedded representation of the target user. The invention also provides a corresponding hidden community attribute acquisition system based on the attention graph neural network.
Owner:NO 709 RES INST OF CHINA SHIPBUILDING IND CORP
Intrusion detection method based on traceability graph
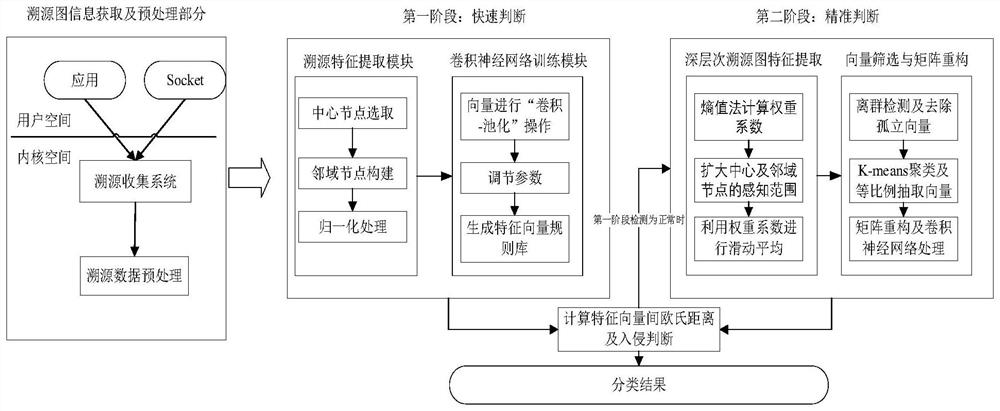
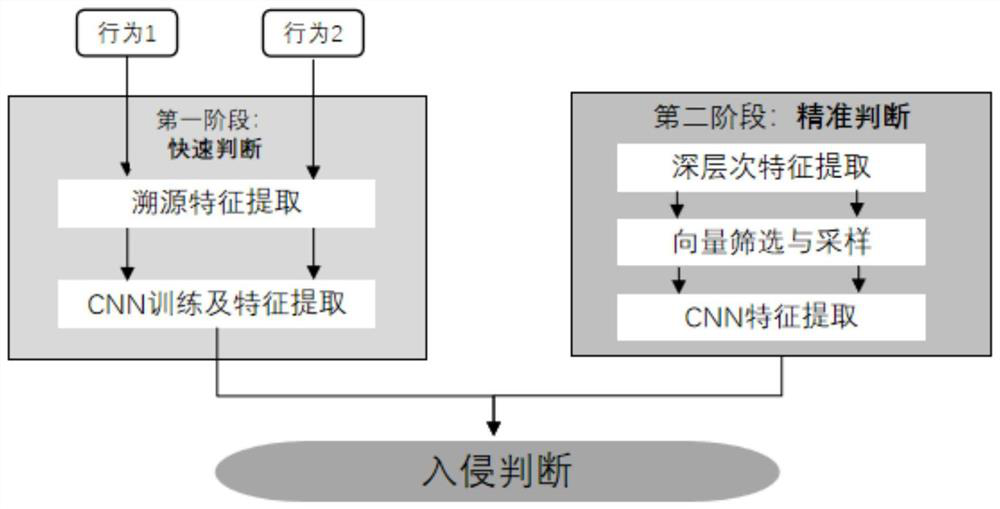
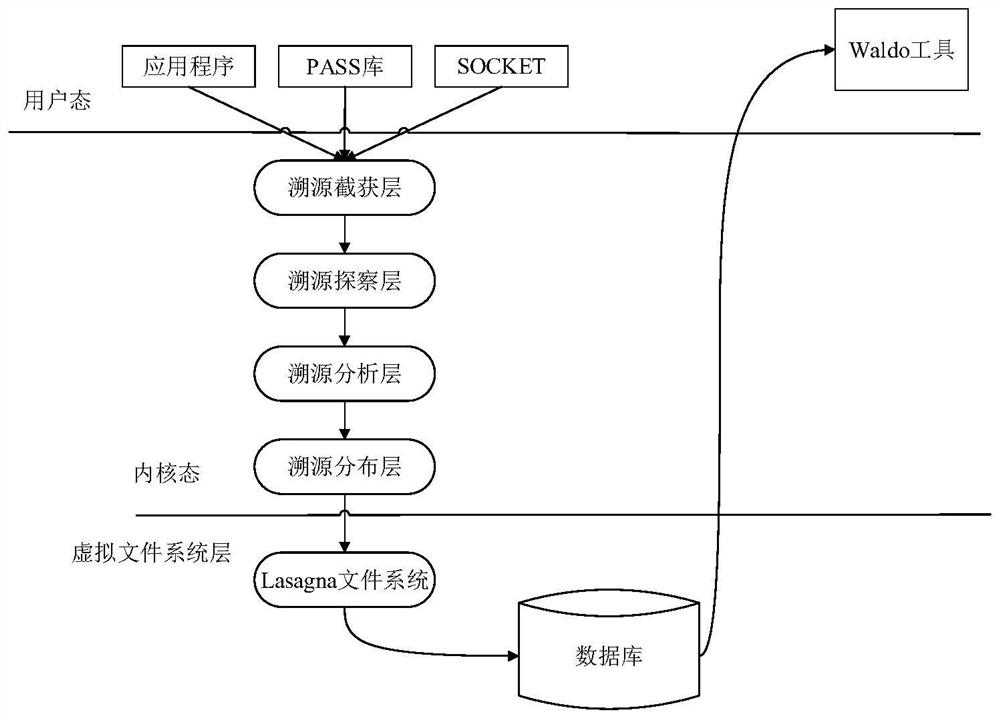
ActiveCN114710344AFull excavationSolve the performance overhead problemPlatform integrity maintainanceNeural architecturesData miningData science
The invention discloses an intrusion detection method based on a traceability graph, and belongs to the field of computer system security, and the method comprises the steps: obtaining a traceability graph of a to-be-detected behavior, and calculating the node importance; rapid judgment and accurate judgment are carried out. In the rapid judgment stage, N1 nodes with high importance and corresponding K1 neighborhood nodes are selected, the traceability graph is converted into a first neighborhood matrix through a mapping rule, so that main body features of the traceability graph are rapidly extracted, if the difference m1 between the features and normal rule behaviors is larger than a threshold ThH during detection, intrusion behaviors are judged, and if the difference m1lt is larger than a threshold ThH, the traceability graph is judged to be intrusive behaviors; if so, judging that the behavior is normal; if yes, judging whether TLt; tilt; Tilt; if yes, entering a precise judgment stage: expanding a central node N2 (N2gt; n1) and a neighborhood node K2 (K2gt; (K1) scale, deeply mining the traceability graph, constructing a second neighborhood matrix and extracting features, if the difference between the features and normal rule behaviors is m < 2lt >; if Th, determining the behavior as a normal behavior, otherwise, determining the behavior as an abnormal behavior. According to the invention, intrusion detection can be efficiently and accurately realized.
Owner:HUAZHONG UNIV OF SCI & TECH
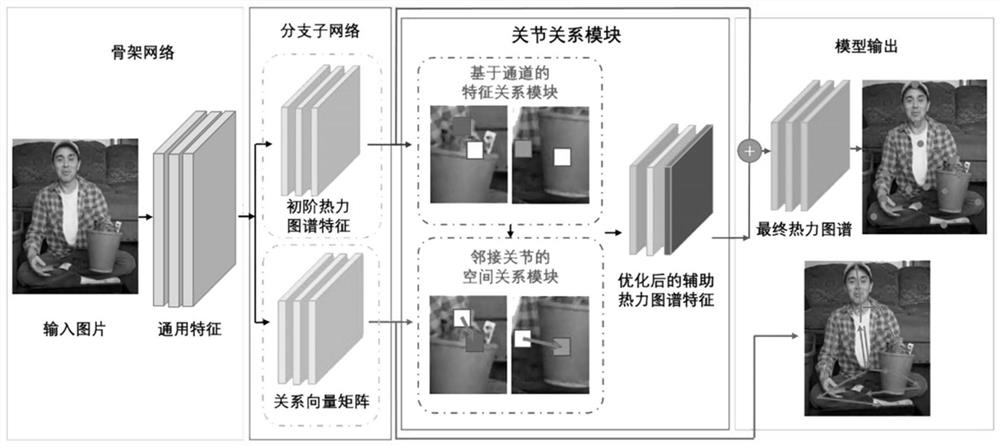
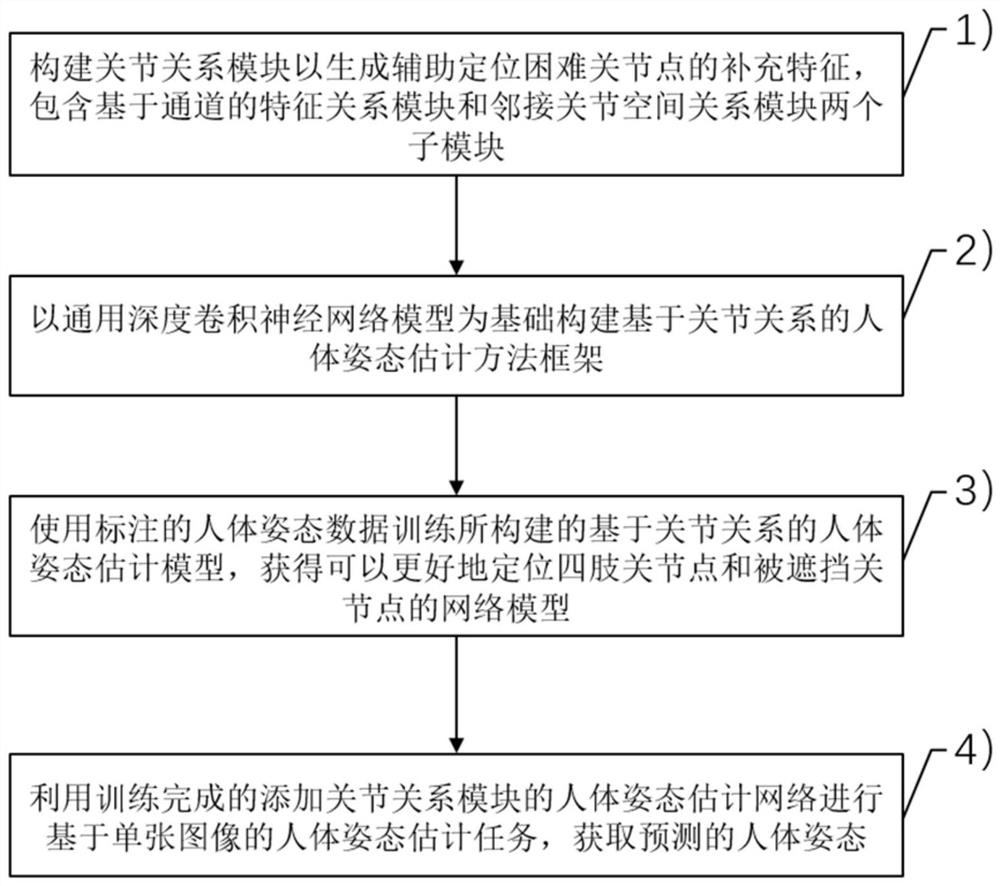
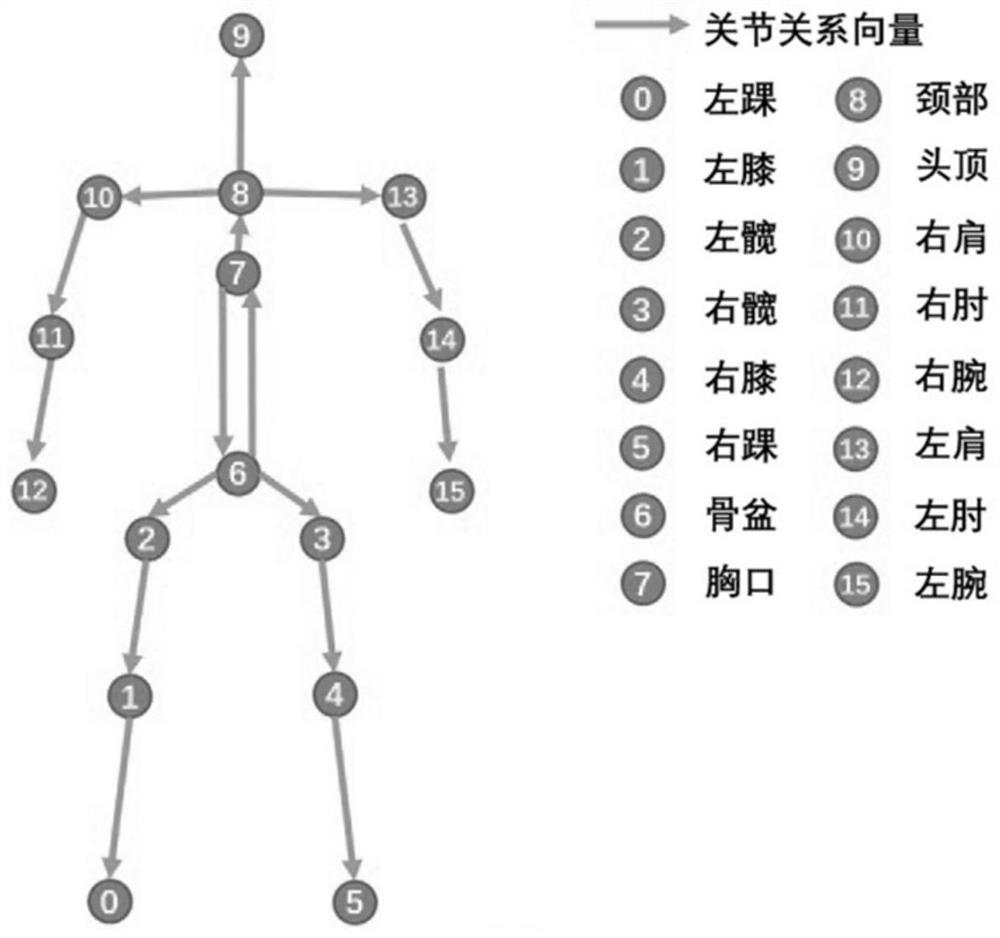
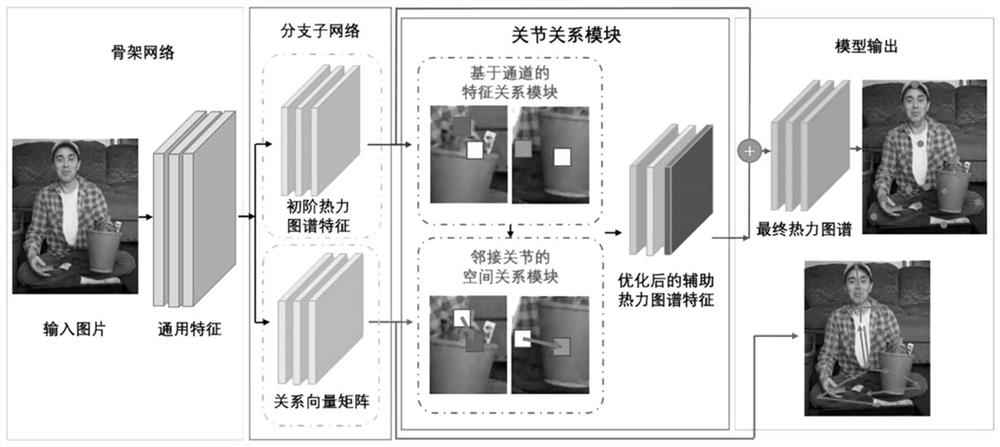
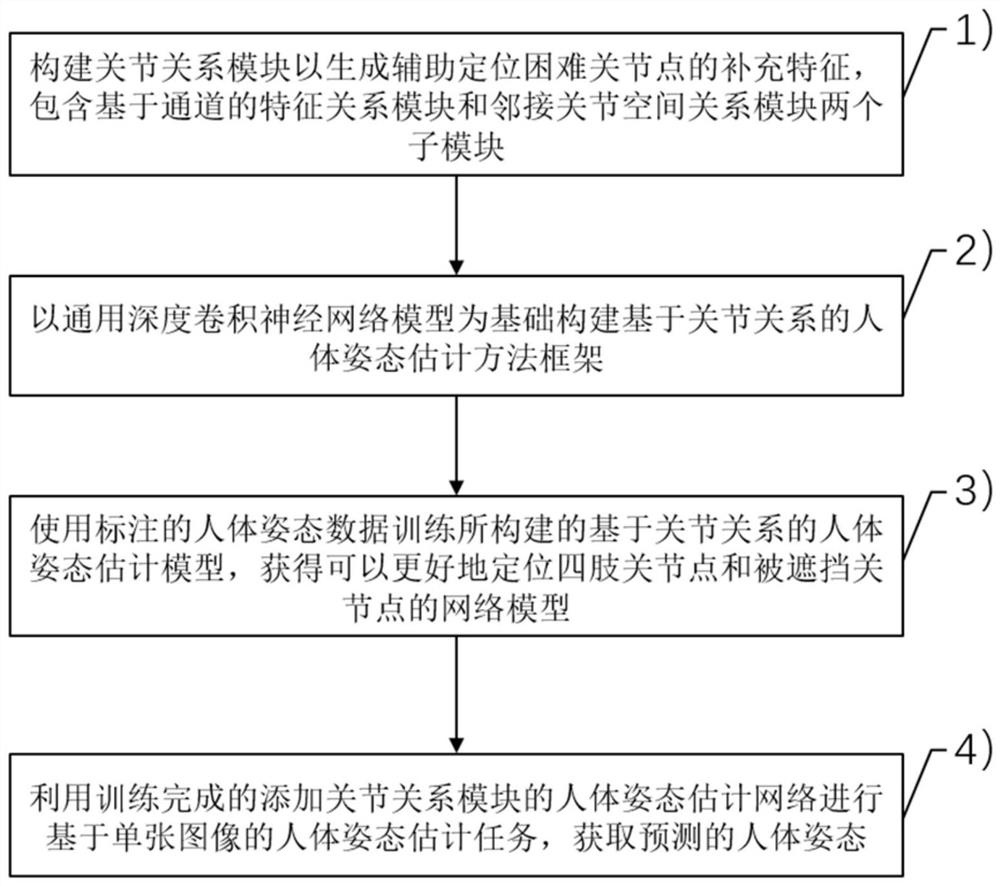
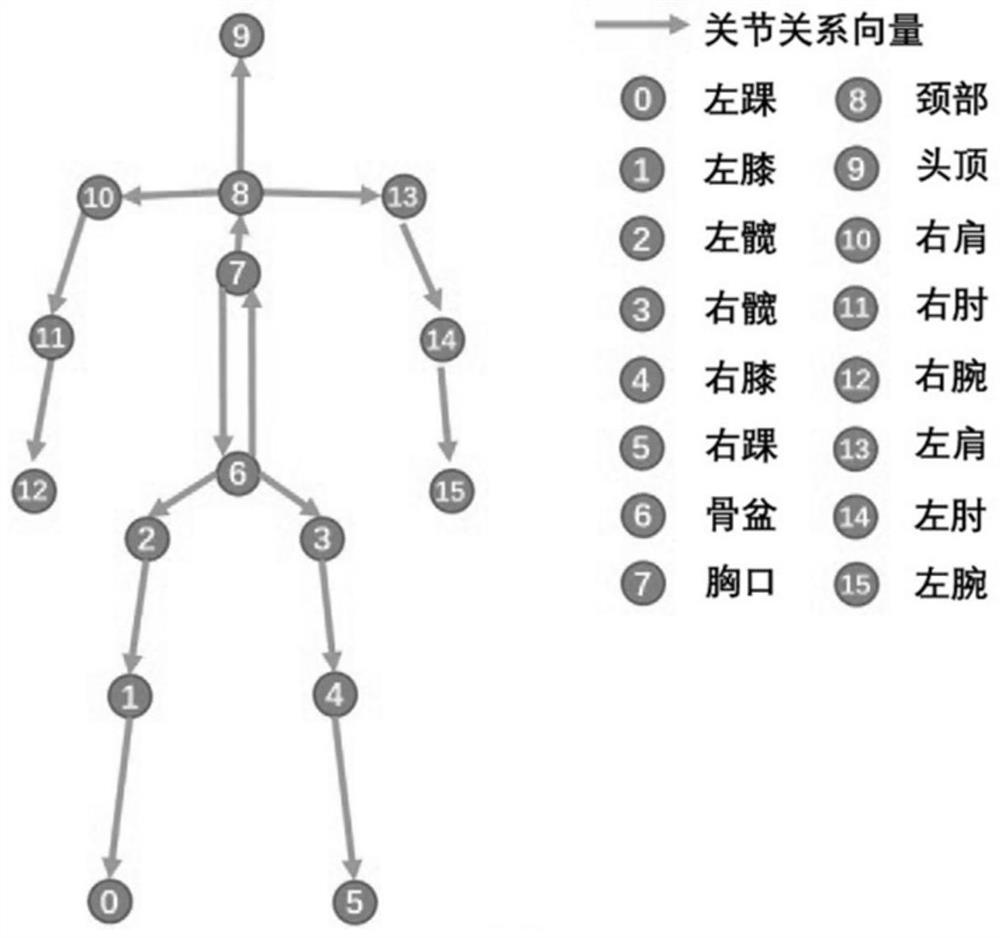
Human body posture estimation method based on joint relation
ActiveCN113435293APrecise positioningGood recognition effectCharacter and pattern recognitionNeural architecturesWrist jointsLimb joint
The invention relates to a human body posture estimation method based on a joint relation, and the method comprises the following steps: S1, constructing a joint relation module which comprises two sub-modules: a channel-based feature relation module and an adjacent joint space relation module; s2, constructing a human body posture estimation model based on a joint relation; s3, training a human body posture estimation model based on a joint relation by utilizing the marked human body posture data; and S4, performing a human body posture estimation task based on a single image by using the trained human body posture estimation model added with the joint relation module to obtain a predicted human body posture. Compared with the prior art, the invention effectively overcomes the problem that the positions of four-limb joints with high degree of freedom, such as wrist joints, ankle joints and shielded invisible joints, are difficult to detect in the image, and is high in human body posture estimation accuracy.
Owner:TONGJI UNIV
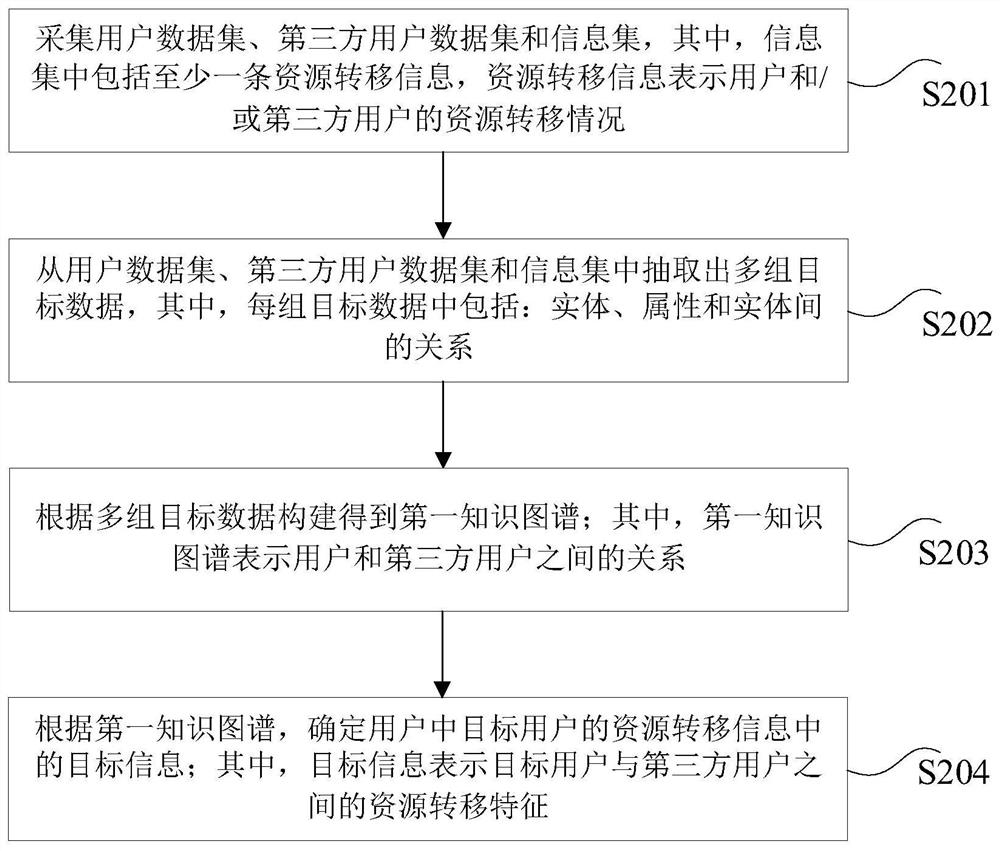
Target information determination method, device and equipment
PendingCN111708897AFull excavationEfficient miningFinanceOther databases indexingThird partyData set
The invention provides a target information determination method, device and equipment, and the method comprises the steps: collecting a user data set, a third-party user data set and an information set, wherein the information set comprises at least one piece of resource transfer information, and the resource transfer information represents the resource transfer condition of a user and / or a third-party user; extracting multiple groups of target data from the user data set, the third-party user data set and the information set, wherein each group of target data comprises entities, attributes and relationships among the entities; constructing a first knowledge graph according to the multiple groups of target data; determining target information in resource transfer information of a target user in the users according to the first knowledge graph, wherein the target information represents a resource transfer characteristic between a target user and a third-party user. In the embodiment ofthe invention, the data can be efficiently and accurately screened by utilizing the first knowledge graph containing the information set, so that the bank auditing efficiency is improved.
Owner:CHINA CONSTRUCTION BANK
A Rolling Bearing Degradation Index Extraction Method Based on Time-Frequency Feature Separation
ActiveCN113567127BNon-stationaryEfficiently characterize degradation processesMachine part testingComplex mathematical operationsFrequency spectrumTime spectrum
A rolling bearing degradation index extraction method based on time-frequency feature separation. Firstly, the time-frequency spectrum of the bearing original signal is calculated; secondly, by determining the number of maximum points at the same time and maximum points at the same frequency in the time-frequency matrix, Determine the position and range of harmonic distribution based on the row accumulation results of the time-frequency matrix, retain the harmonic distribution area, filter out other areas, and inverse short-time Fourier transform the processed time-frequency matrix to the time domain to realize the extraction of harmonic components ; After subtracting the harmonic components from the original signal, the threshold value noise reduction is carried out to extract the fault impact components, and finally the relative root mean square value is calculated for the extracted fault impact components as the rolling bearing degradation index; the present invention pre-filters based on time-frequency characteristics The prominent harmonic components in the time spectrum are removed to enhance the fault impact components, avoiding serious distortion when threshold noise reduction is used to extract the impact components, and the rolling bearing degradation index is calculated for the extracted fault impact components, which can effectively characterize the bearing degradation process.
Owner:XI AN JIAOTONG UNIV +1
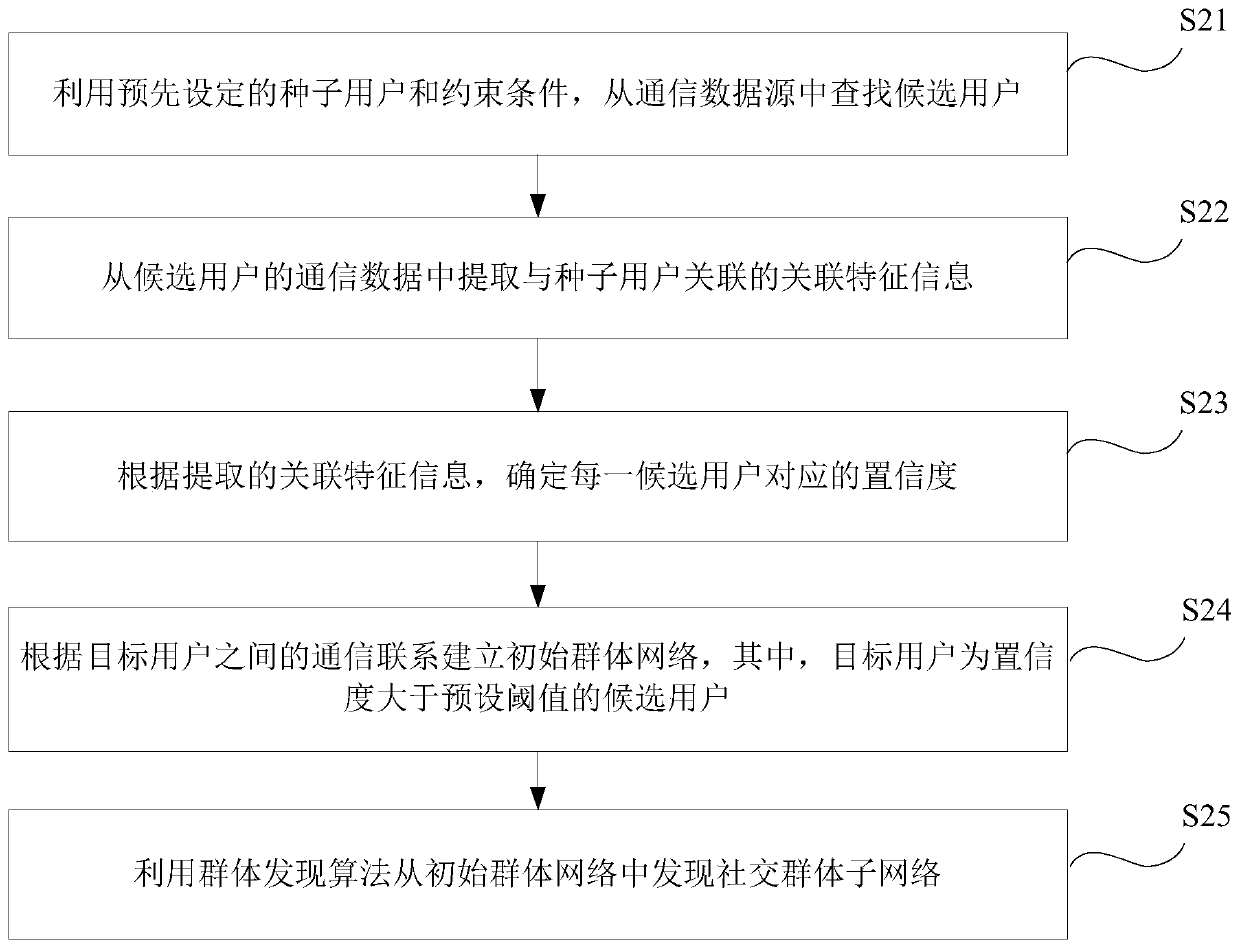
Social group discovery method and device and storage medium
ActiveCN110704612AFull excavationHigh precisionData processing applicationsSemantic analysisGroup discoveryData mining
The invention provides a social group discovery method, a social group discovery device and a storage medium, which are used for improving the social group discovery precision and accuracy. The socialgroup discovery method comprises the following steps: searching candidate users from a communication data source by using a preset seed user and a constraint condition, the candidate users comprisinga first user communicating with the seed user and / or a second user satisfying the constraint condition; extracting associated feature information associated with the seed user from the communicationdata of the candidate user; determining confidence corresponding to each candidate user according to the extracted associated feature information; determining the candidate users of which the confidence coefficients are greater than a preset threshold value as target users; establishing an initial group network according to the communication relationship between the target users; and discovering asocial group sub-network from the initial group network by utilizing a group discovering algorithm.
Owner:NAT COMP NETWORK & INFORMATION SECURITY MANAGEMENT CENT +1
A fuzzy testing method and device for text configuration files
ActiveCN111913877BImprove fuzz testing efficiencyFull excavationSoftware testing/debuggingProgramming languageConfigfs
Embodiments of the present invention provide a text configuration file-oriented fuzz testing method and device, the method comprising: identifying the text file format type of the target configuration file, and determining the key-value pair of the target configuration file; Carry out pre-fuzz test to the program that uses described target configuration file as input to detect whether described program has the loophole on format, and extract all visible character strings in described program, to the key-value pair of described target configuration file The key in the key is mutated to obtain the key combination seed file; based on the weight of the key in the key combination seed file, the value corresponding to the key in the key combination seed file is mutated to obtain a new combination seed file, and the program bugs. The embodiment of the present invention realizes comprehensively digging deeper loopholes in programs, and improves the efficiency of fuzzy testing for text configuration files.
Owner:INST OF INFORMATION ENG CHINESE ACAD OF SCI
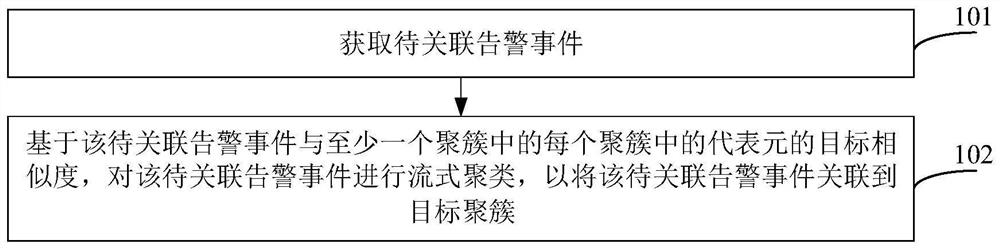
Alarm event association method and device, electronic equipment, medium and program product
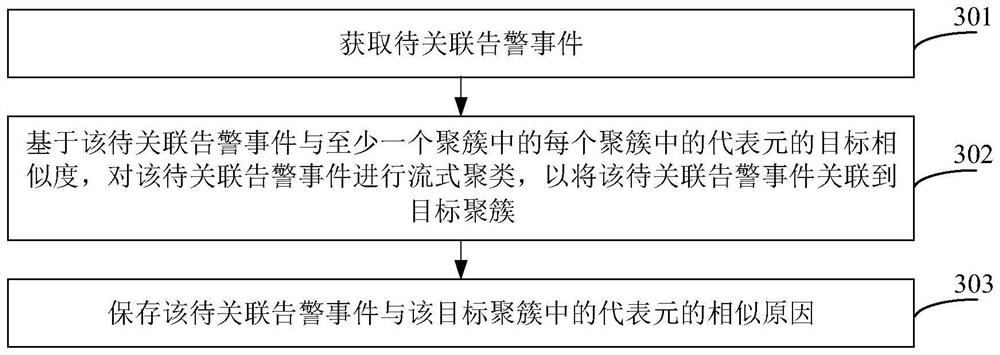
PendingCN114461792AImprove clustering effectFull excavationCharacter and pattern recognitionSpecial data processing applicationsEngineeringDegree of similarity
The embodiment of the invention relates to an alarm event association method and device, electronic equipment, a medium and a program product, and the method comprises the steps: obtaining a to-be-associated alarm event; based on the target similarity between the to-be-associated alarm event and the representative element in each cluster in the at least one cluster, performing streaming clustering on the to-be-associated alarm event so as to associate the to-be-associated alarm event to a target cluster; wherein the representative element in each cluster is an alarm event in the corresponding cluster, and the target similarity comprises text content similarity and / or index data similarity. According to the embodiment of the invention, on the basis of the text content similarity and / or the index data similarity, the similarity between the to-be-associated alarm events and the representative elements in each cluster is measured, and the to-be-associated alarm events are clustered in real time, so that the association effect and the clustering effect can be effectively improved.
Owner:ALIBABA (CHINA) CO LTD
Perceptual Big Data Hierarchical Perception Compression Coding Method
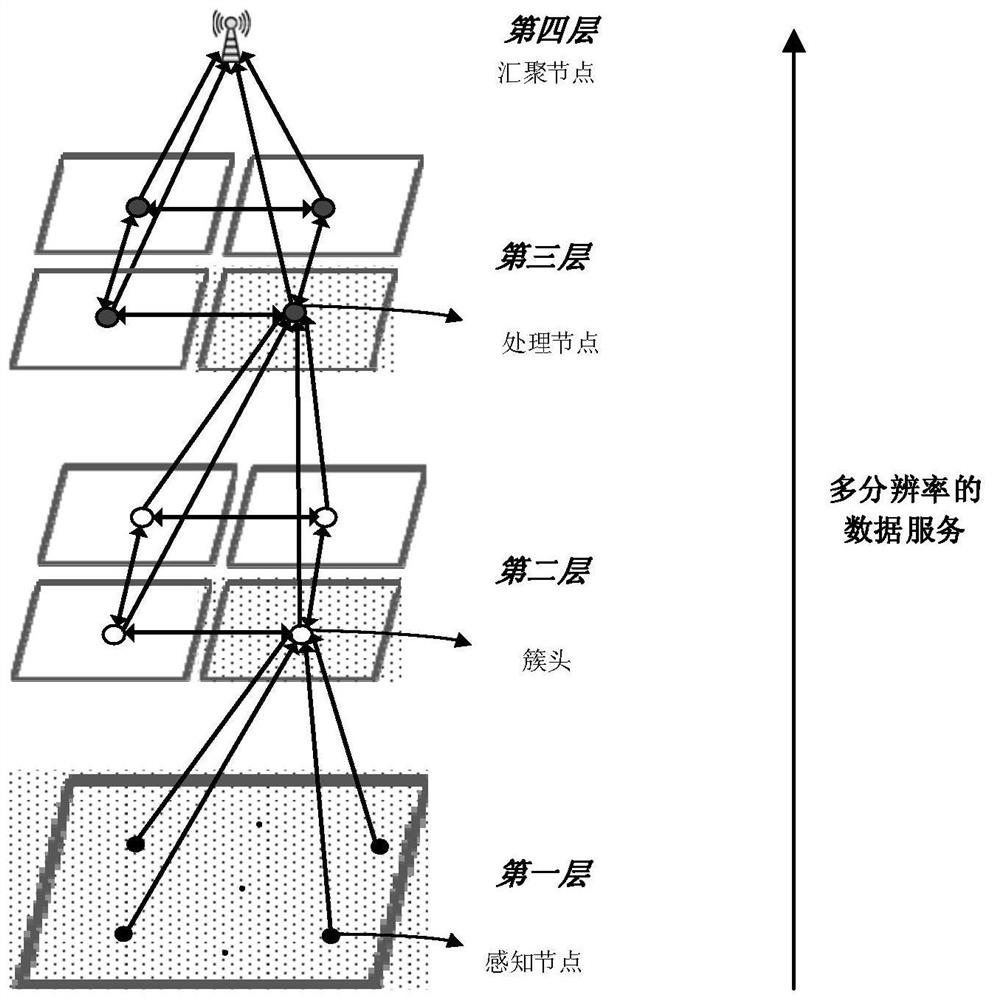
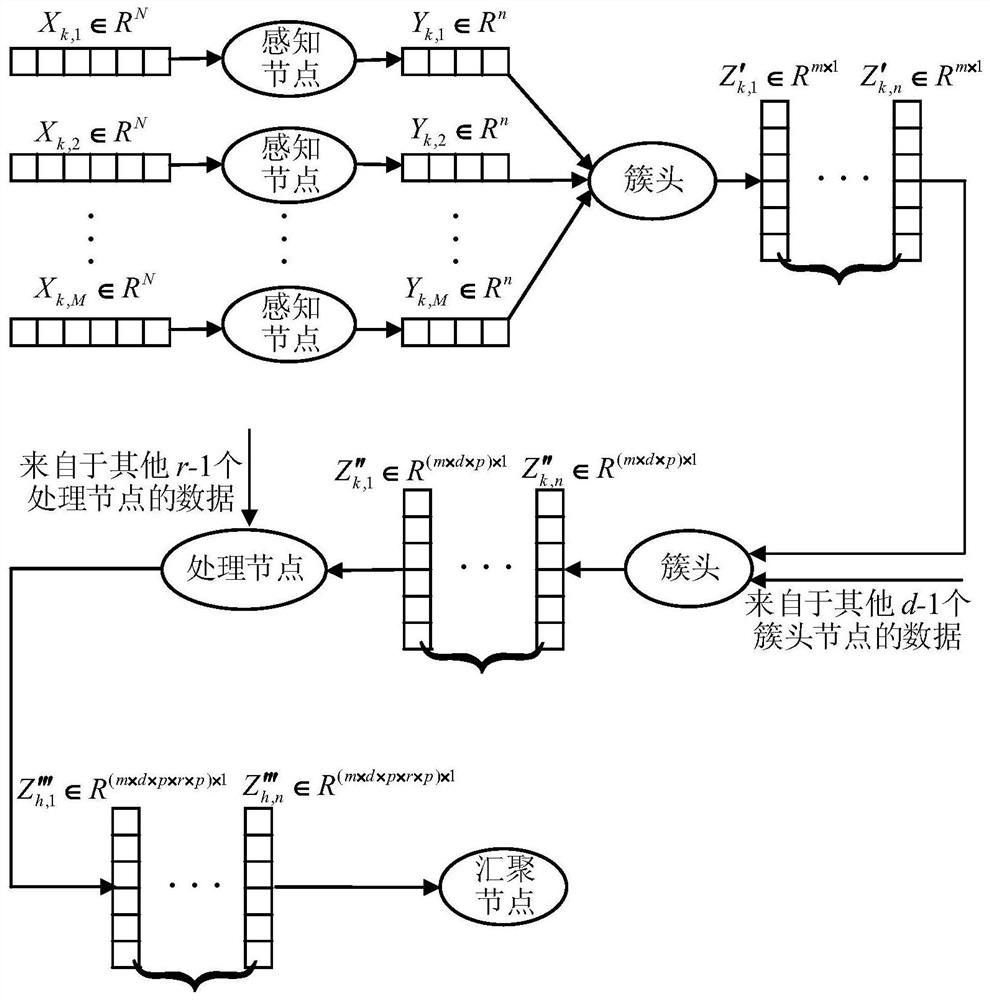
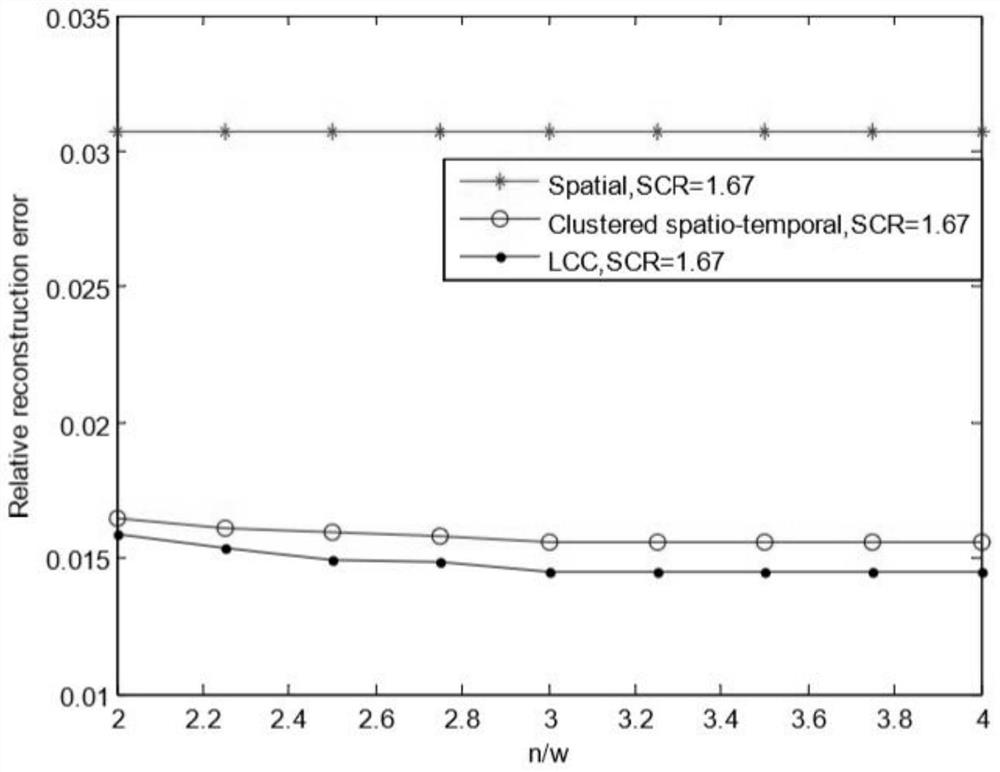
ActiveCN108494758BReduce the number of transfersFull excavationTransmissionPattern recognitionOriginal data
The invention discloses a sensing big data hierarchical sensing compressed coding method. The sensing big data hierarchical sensing compressed coding method comprises steps that a sensing node is usedfor compressing and sampling of original data, and is used to transmit the data to a cluster head node; the cluster head node is used for the compressing and coding of the compressed and sampled datareceived from a lower layer and the data received from other cluster head nodes, and is used to transmit the data to a processing node by using a probability p; the processing node is used to code the data received from the lower layer and the data received from other processing nodes, and is used to transmit the coded data to an aggregation node by using the probability p; the aggregation node is used for decoding operation, and approximate original data is acquired. By combining with the network coding, the compressing sensing, and the hierarchical sensing theories, the space-time correlation of the sensing big data is fully excavated, especially the space-time correlation of the inter-cluster data is fully excavated, and therefore multi-resolution data service is provided for user of different types, and at the same time, an ideal hypothesis of sharing an observation matrix in advance is eliminated.
Owner:NANJING UNIV OF POSTS & TELECOMM
A Human Pose Estimation Method Based on Joint Relationship
ActiveCN113435293BEasy to identifyPrecise positioningBiometric pattern recognitionNeural architecturesPattern recognitionHuman body
The present invention relates to a human body posture estimation method based on joint relationship, comprising the following steps: S1: building a joint relationship module, including two sub-modules, a channel-based feature relationship module and an adjacent joint space relationship module; S2: building a human body based on joint relationship Pose estimation model; S3: use the labeled human pose data to train the human pose estimation model based on the joint relationship; S4: use the trained human pose estimation model with the joint relationship module to perform the human pose estimation task based on a single image, and obtain the prediction human body posture. Compared with the prior art, the present invention effectively overcomes the problem that it is difficult to detect the position of limb joints with high degrees of freedom such as wrist joints, ankle joints and hidden invisible joints in the image, and the accuracy of human body posture estimation is high.
Owner:TONGJI UNIV
Security vulnerability assessment method, system and equipment for cigarette industrial control system
The invention provides a security vulnerability assessment method for a cigarette industry control system. The method comprises the steps of identifying data streams, and tagging data stream paths and stream directions of the data streams; classifying the data streams according to attributes of the data streams; analyzing an attack surface; judging whether the data streams have technical control measures corresponding to the data streams in the cigarette industry control system or not; if yes, judging whether equipment nodes on the data stream paths have security management measures corresponding to the equipment nodes or not; if yes, performing security vulnerability testing and analysis on key nodes on the data stream paths, performing statistics on security vulnerability points on the key nodes on the data stream paths, and compiling the security vulnerability points existent in the cigarette industry control system in a predetermined document format; and if the equipment nodes on the data stream paths do not have the security management measures corresponding to the equipment nodes, configuring the security management measures corresponding to the equipment nodes for the equipment nodes on the data stream paths, and if the data streams do not have the technical control measures corresponding to the data streams in the cigarette industry control system, configuring the technical control measures corresponding to the data streams for the data streams. According to the security vulnerability assessment method, the security vulnerability of the cigarette industry control system can be assessed more comprehensively and more accurately.
Owner:SHANGHAI TOBACCO GRP CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com