Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
441results about How to "Reduce the number of transfers" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
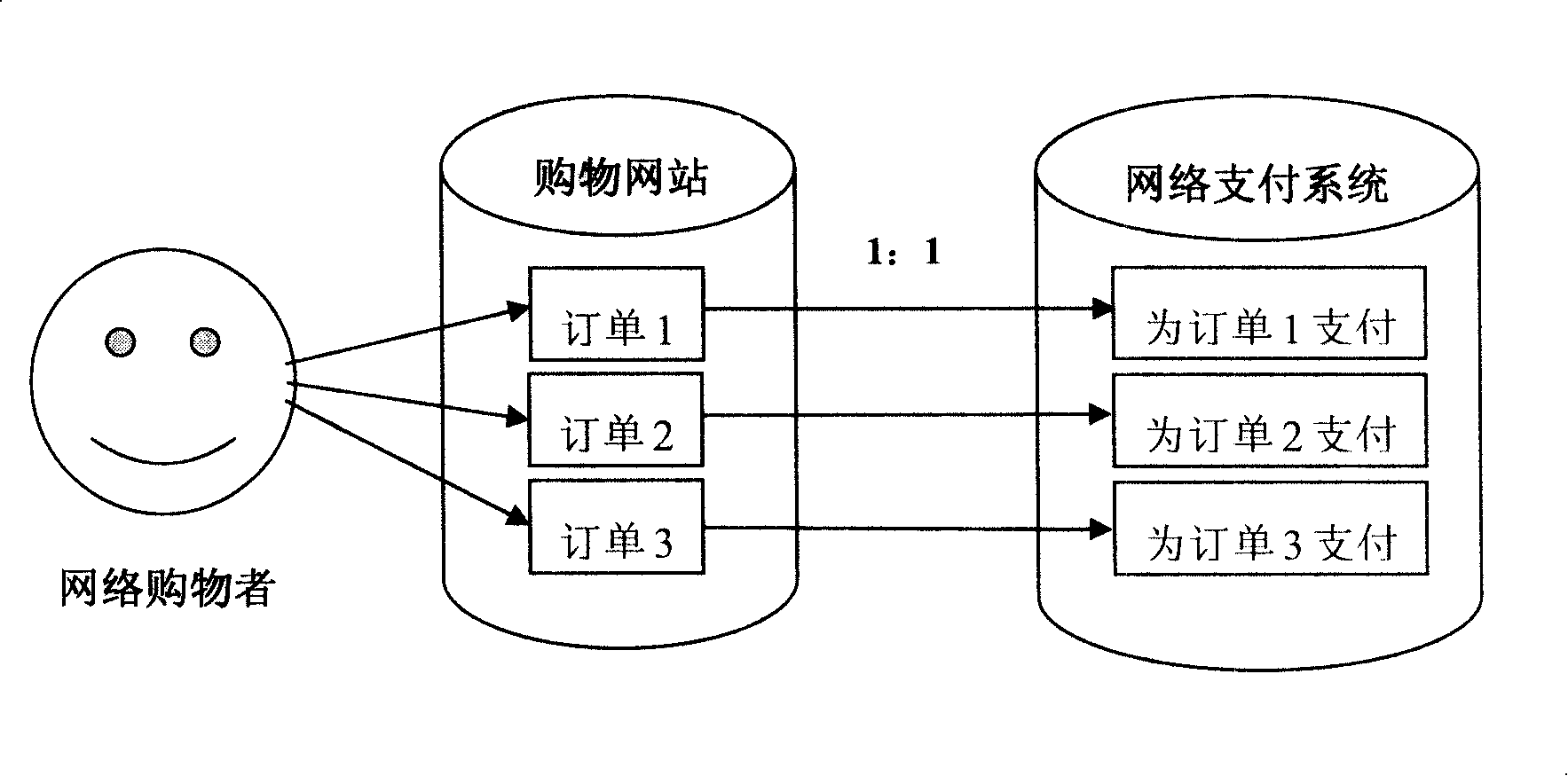
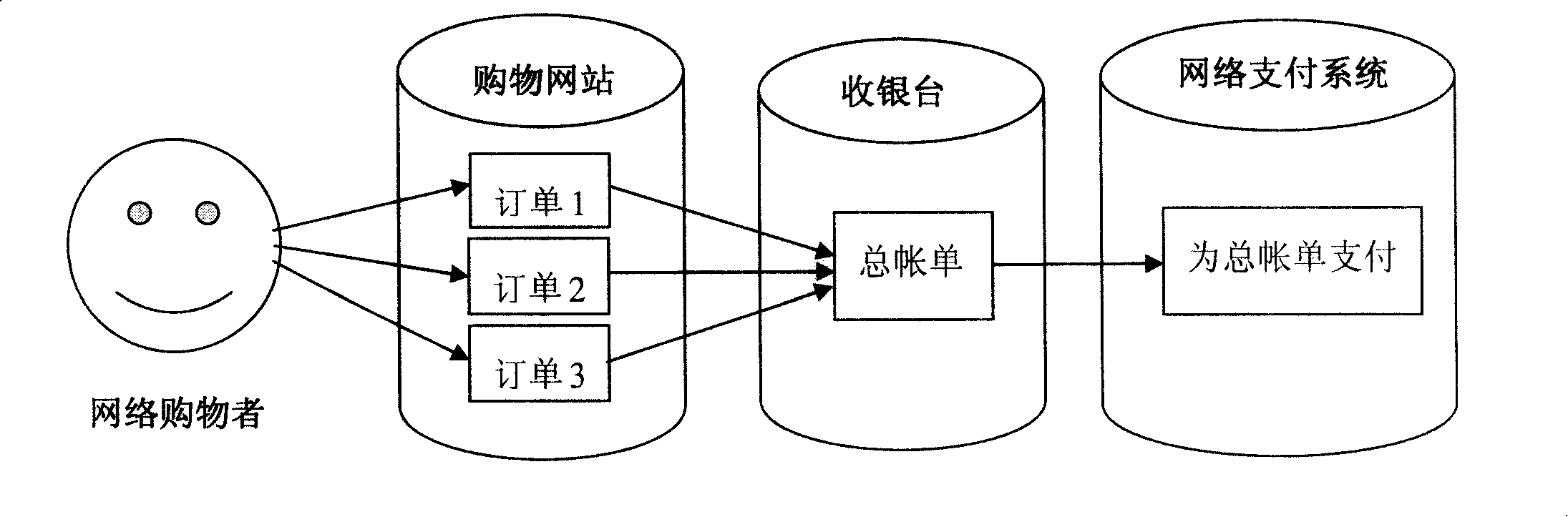
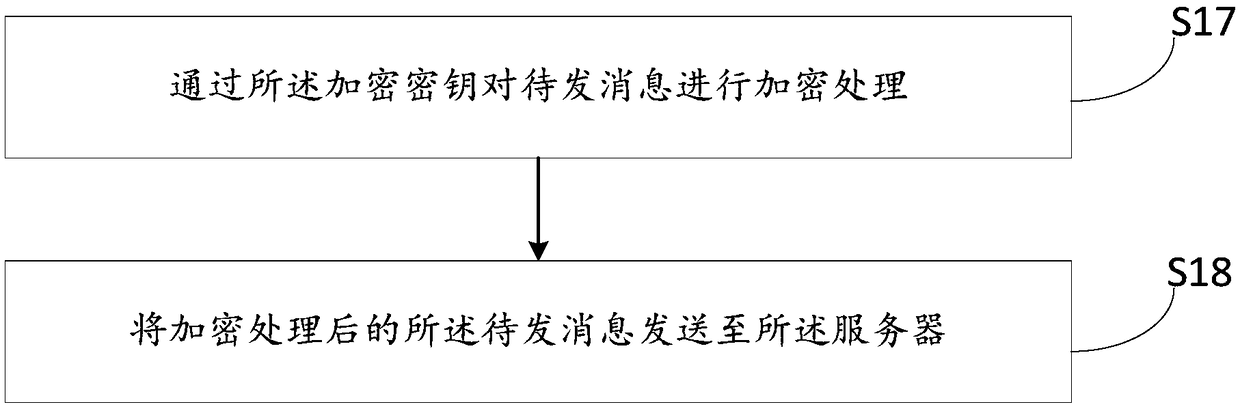
System and method of network payment
ActiveCN101231722AReduce the number of transfersReduce the number of operationsPayment architectureBuying/selling/leasing transactionsPaymentUser needs
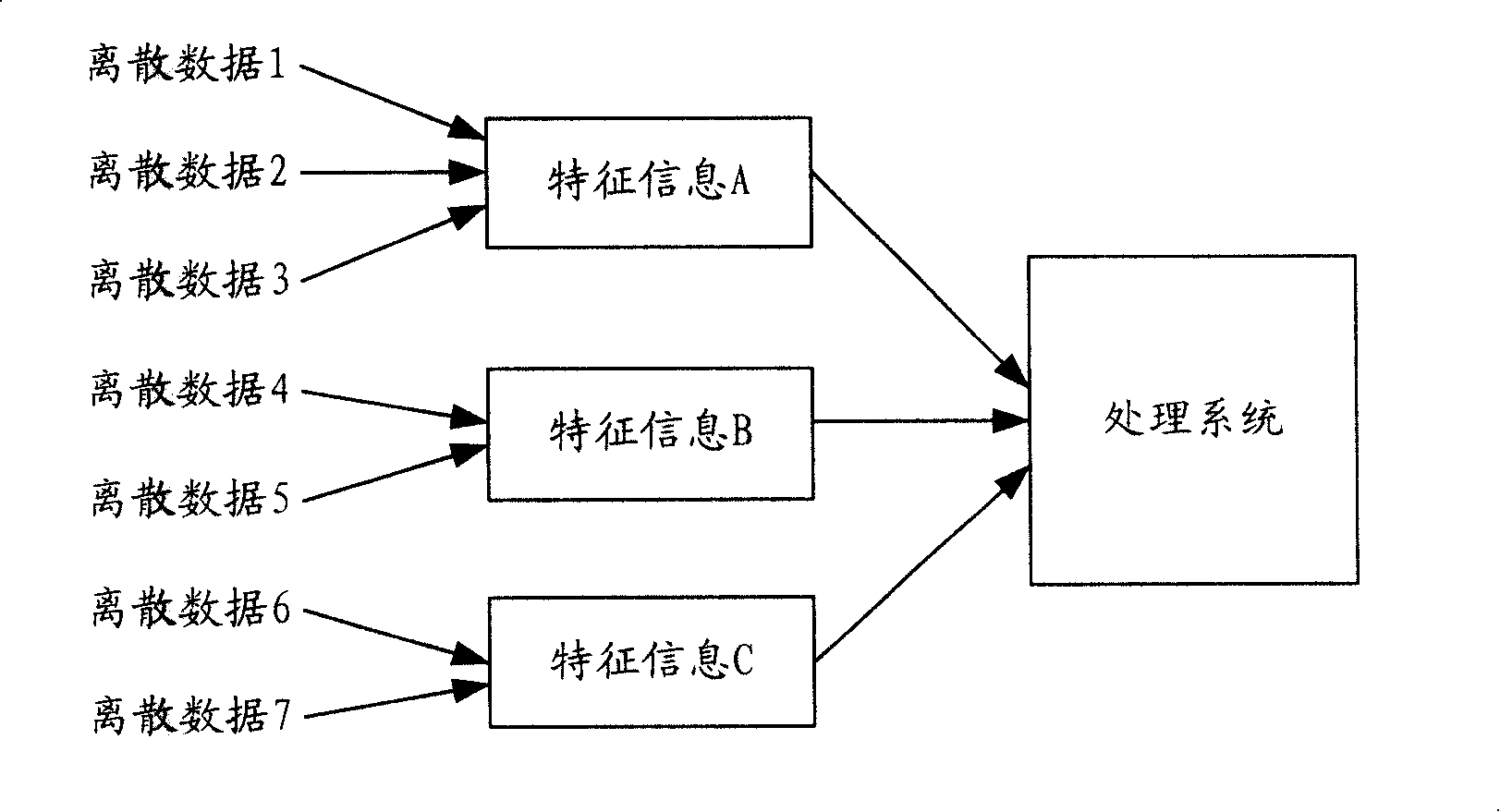
The invention discloses a centralized processing method for scattered data, as well as an application thereof. The invention which is applied as a network payment method as well as a system thereof solves the problem in the prior mode that the scattered data cause repetitive operations during the treating process, thereby occupying the network resources and consuming the transmission time, as well as the problems of complicate operation and easy error, which are caused by the prior payment service that a user needs to pay for each order in the real application. The method comprises the following steps that: the scattered data are received, and are temporarily stored; the characteristic information in the scattered data is identified; the scattered data with the same or the corresponding characteristic are sent out to a processing system in a centralized way; the processing system treats all scattered data with the same or the corresponding characteristic in a unified way. The invention sends out the scattered data with the same or the corresponding characteristic in a unified way, thereby reducing the times of the network transmission, and saving the network resources and the transmission time. Besides, a plurality of processing operations can be executed at one time, thereby greatly saving the operation time and improving the treatment efficiency.
Owner:ALIBABA GRP HLDG LTD
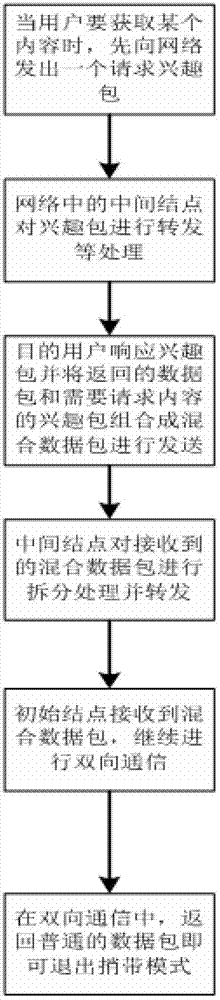
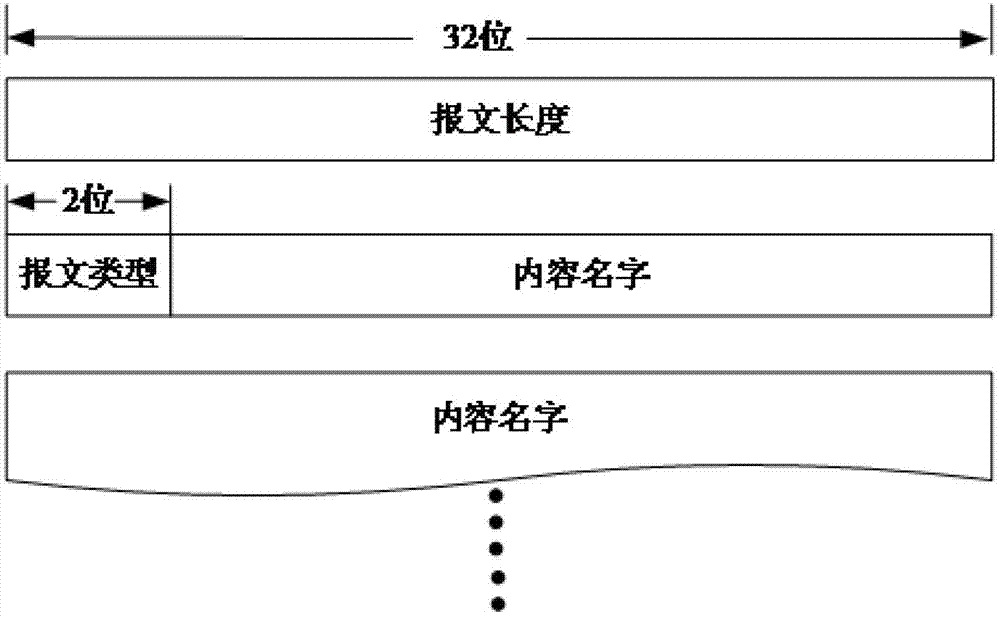
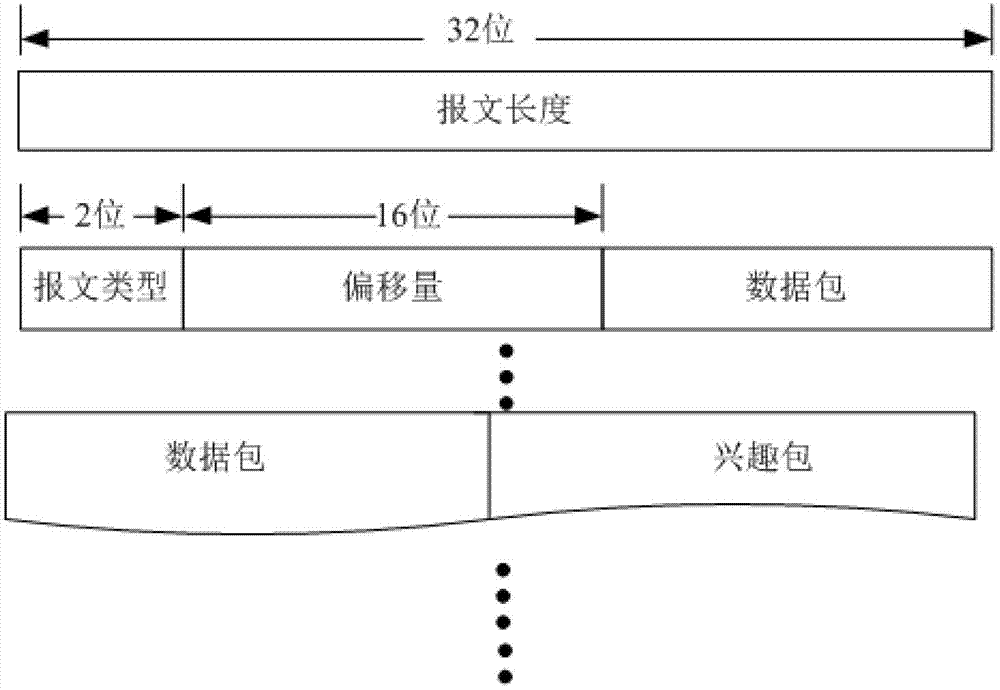
Method of sending data package and incidentally sending reverse interest package in content center network
InactiveCN103118013AReduce the number of transfersIncrease the amount of informationData switching networksSpecial data processing applicationsNetwork packetInformation quantity
The invention discloses a method of sending a data package and incidentally sending a reverse interest package in content center network. The method includes the following steps : step 1, sending the interest package to the network to by a user A show that the user A is interested in the content; step 2, an intermediate node dealing with a request when the intermediate node in the network receives the interest package; step 3, combining a response data package and the interest package which needs to be requested by the user A to form a mixed data package by a user B when the user B wants to send a data request to the user A; step 4, the intermediate node splitting the mixed data package into a data package and a reverse interest package when the intermediate node in the network receives the mixed data package and respectively dealing with the data package and the reverse interest package; step 5, splitting the mixed data package by the user A when the user A receives the mixed data package, receiving the data package and delivering the data package to primary requested program, and meanwhile responding to the interest package by the user A and producing a corresponding data package. The method of sending the data package and incidentally sending the reverse interest package in content center network reduces transmission times of the package and improves information quantity and efficiency in once transmission.
Owner:XIDIAN UNIV
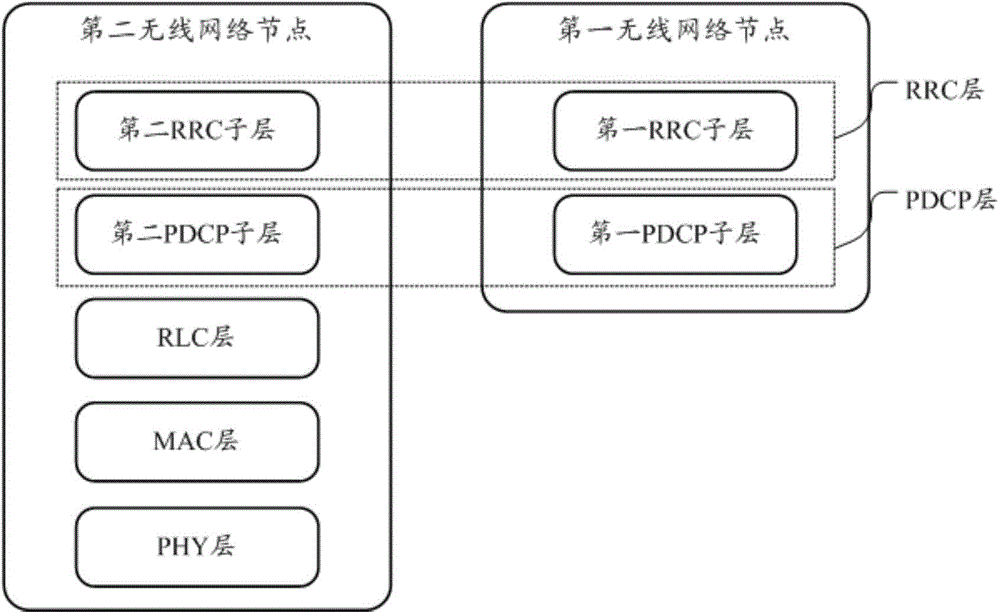
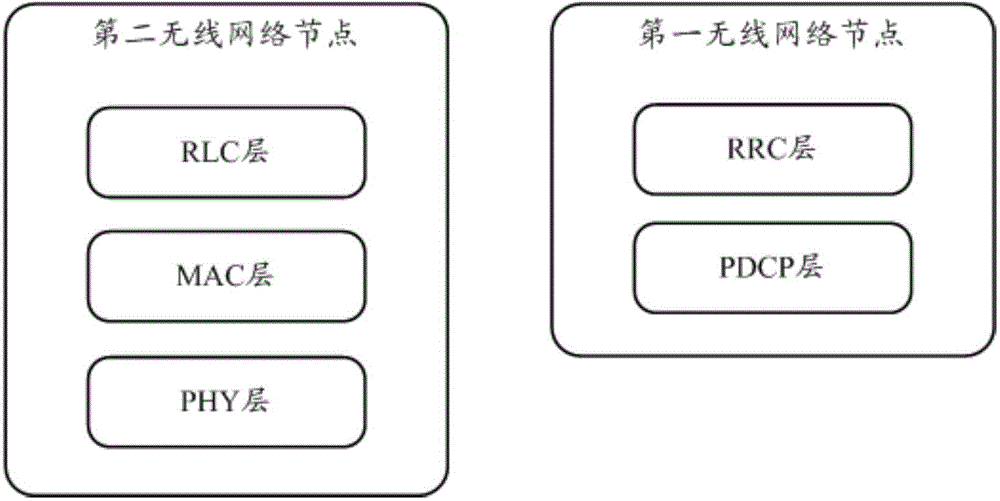
Data transmission method, wireless network node and communication system
ActiveCN106332048AReduce the number of transfersReduce demandNetwork traffic/resource managementConnection managementCommunications systemRadio networks
The embodiment of the invention discloses a data transmission method, and the method comprises the following steps that a first wireless network node reminds the bearing type of a downlink data packet; the first wireless network node transmits the downlink data packet to a second wireless network node under the condition that the bearing type is the signaling radio bearing SRB so that the second wireless network node performs the function of a grouped data aggregation protocol PDCP layer for the downlink data packet; or the first wireless network node performs a function of a PDCP layer for the downlink packet and transmits the processed downlink packet to the second radio network node under the condition that the bearing type is a data radio bearer DRB. Correspondingly, the embodiment of the present invention also discloses a wireless network node that can reduce transmission bandwidth and time delay requirements.
Owner:HUAWEI TECH CO LTD
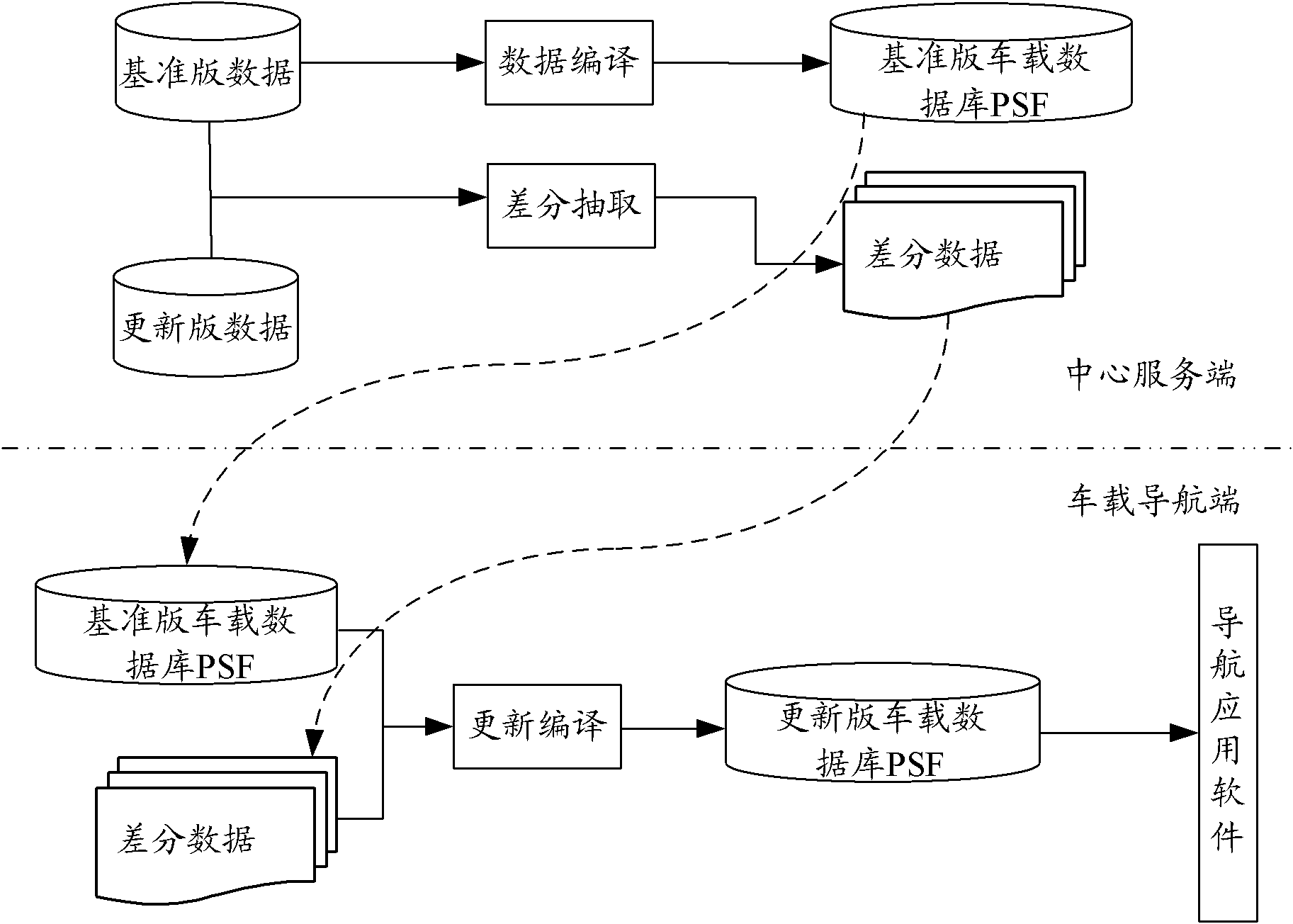
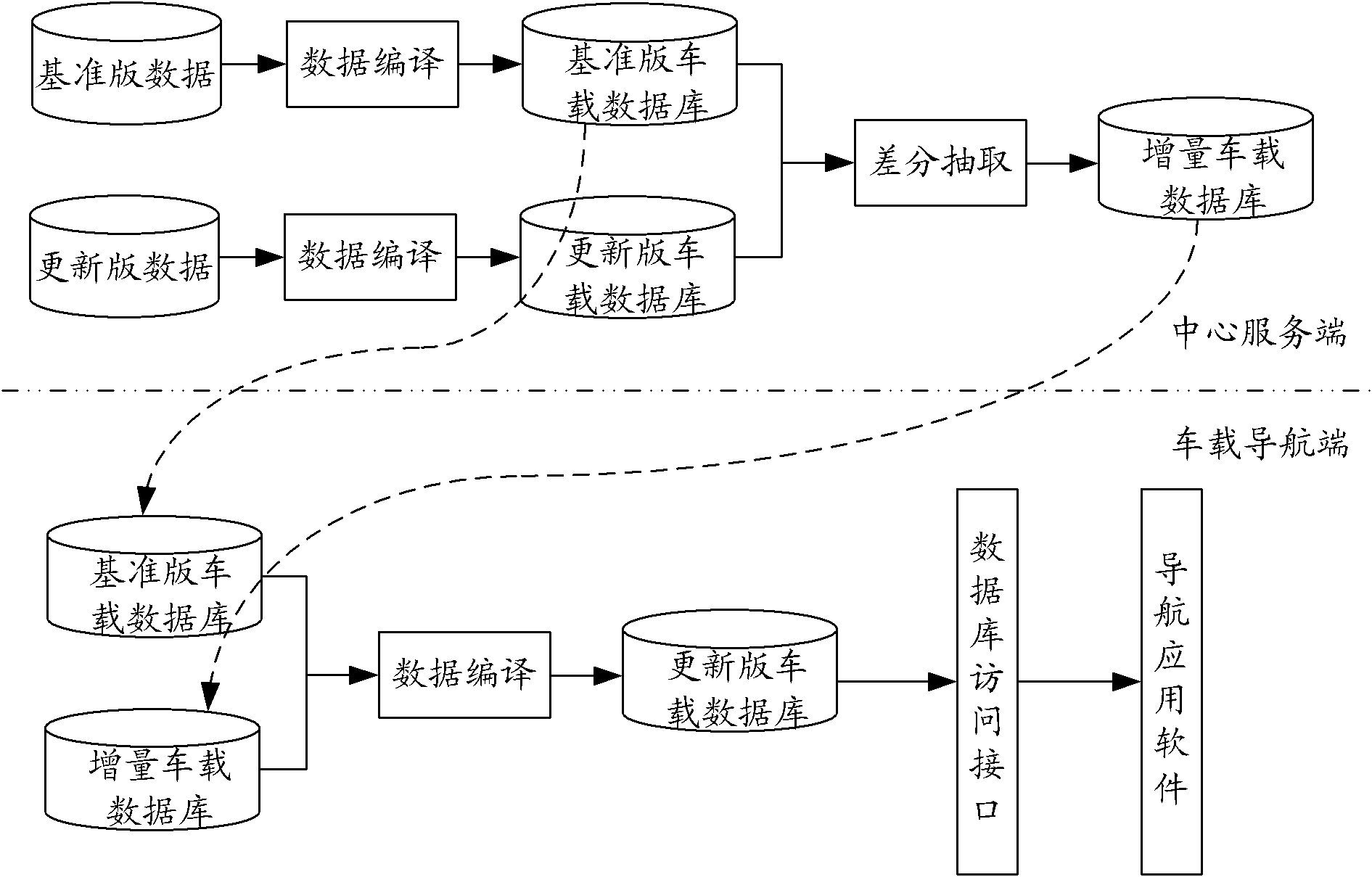
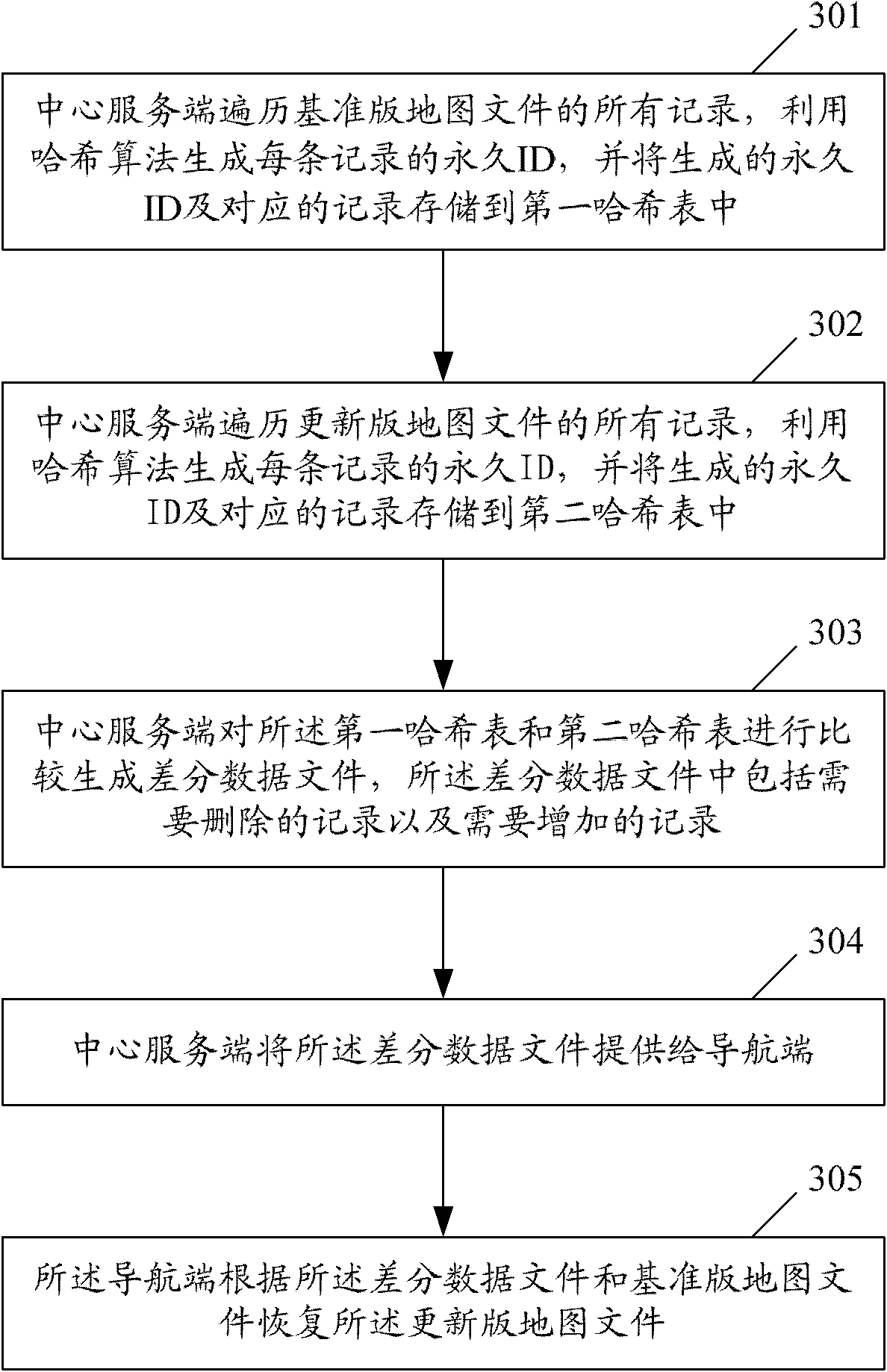
Method, device and system for updating increment of navigation electronic map
ActiveCN102607577AEasy extractionReduce the amount requiredInstruments for road network navigationData fileData dependent
The invention provides a method, a device and a system for updating the increment of a navigation electronic map. The method comprises the following steps of: traversing all records of a reference edition map file, generating the permanent ID of each record by the Hash algorithm, and storing the generated permanent IDs and the corresponding records in a first hash table; traversing all records of an updated edition map file, generating the permanent ID of each record by the Hash algorithm, and storing the permanent IDs and the corresponding records in a second hash table; comparing the first hash table with the second hash table to generate a differential data file, wherein the differential data file contains records needing to be deleted and records needing to be added; and providing the differential data file to a navigation terminal so that the navigation terminal restores the updated edition map file according to the differential data file and the reference edition map file. The method is capable of realizing the increment updating of the navigation electronic map without recording and adding the permanent IDs during data production.
Owner:NAVINFO
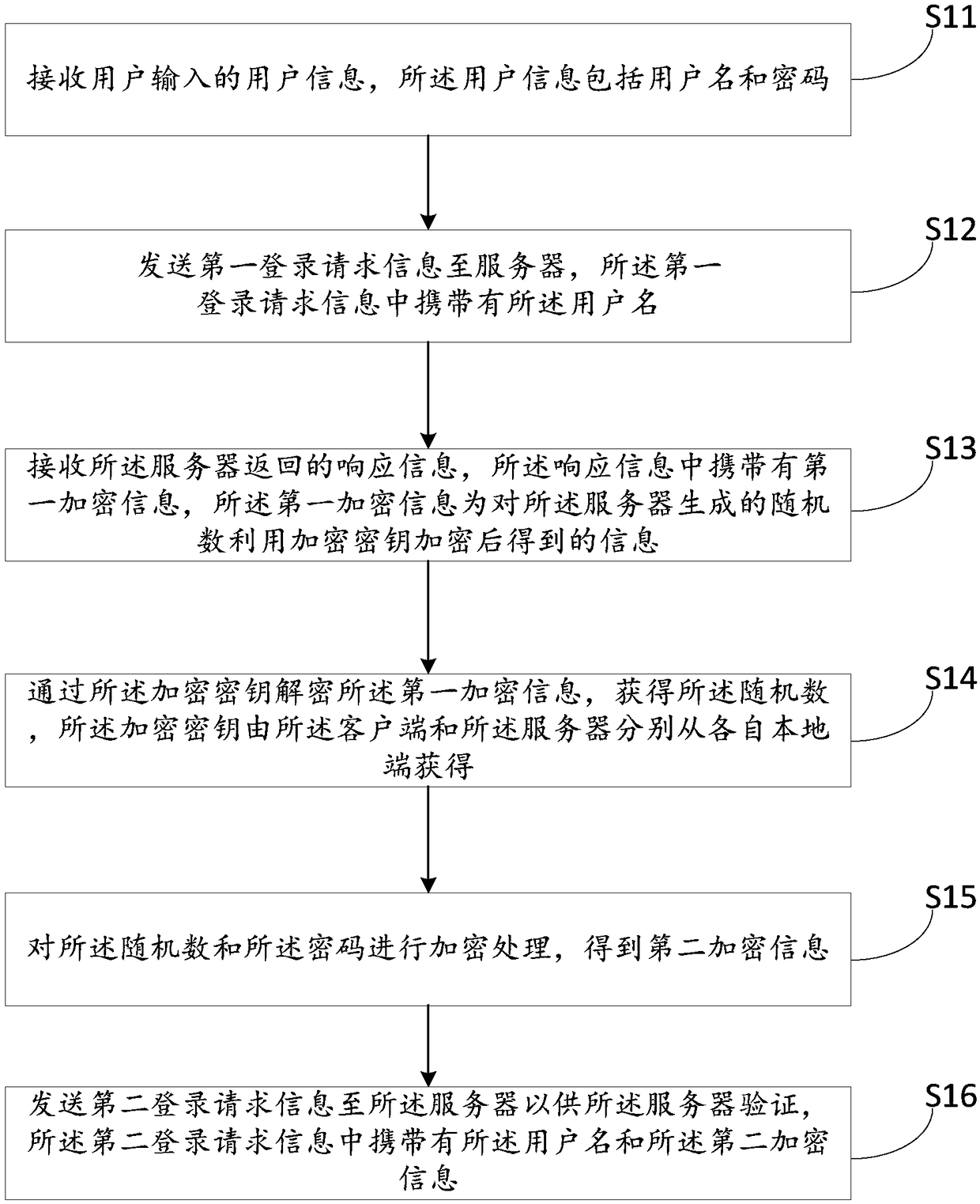
Information transmission method, client, server and computer readable storage medium
ActiveCN109347835AEnsure safetyPrevent theftKey distribution for secure communicationInformation transmissionPassword
The invention relates to the technical field of communications, and discloses an information transmission method, a client, a server and a computer readable storage medium. The method comprises the following steps: receiving user information input by a user; sending first login request information to the server; receiving response information returned by the server, the response information carrying first encrypted information, and the first encrypted information being information acquired by encrypting a random number generated by the server by an encryption key; decrypting the first encrypted information through the encryption key to acquire the random number, the encryption key being acquired by the client and the server respectively from own local sides; encrypting the random number and a password to acquire second encrypted information; and sending second login request information to the server, the second login request information carrying a user name and the second encrypted information. Verification information for each login is different, so that a replay attack can be prevented; and furthermore, the encryption key is not required to be subjected to network switching between the client and the server, so that the security of the encryption key is guaranteed.
Owner:SUZHOU KEDA TECH
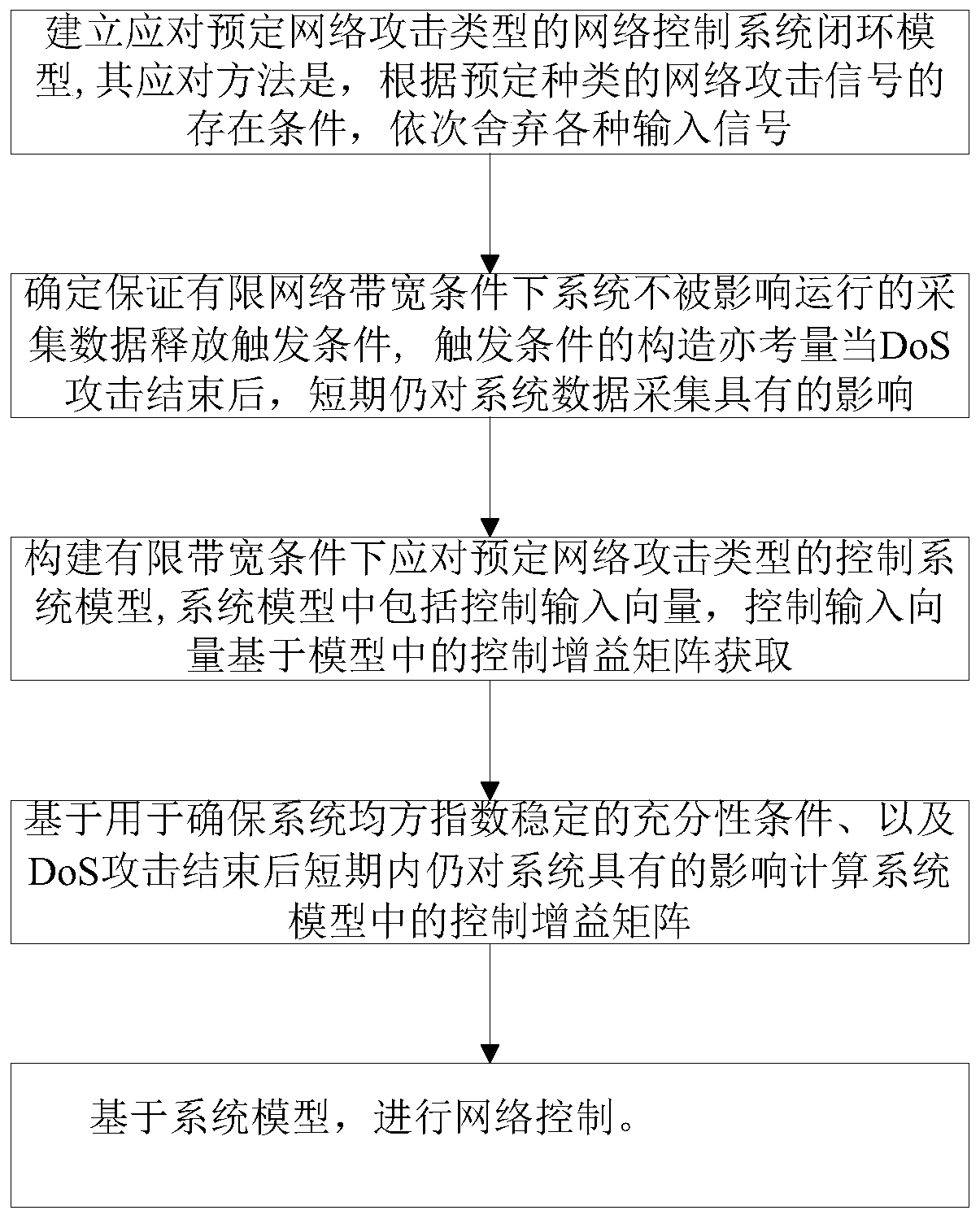
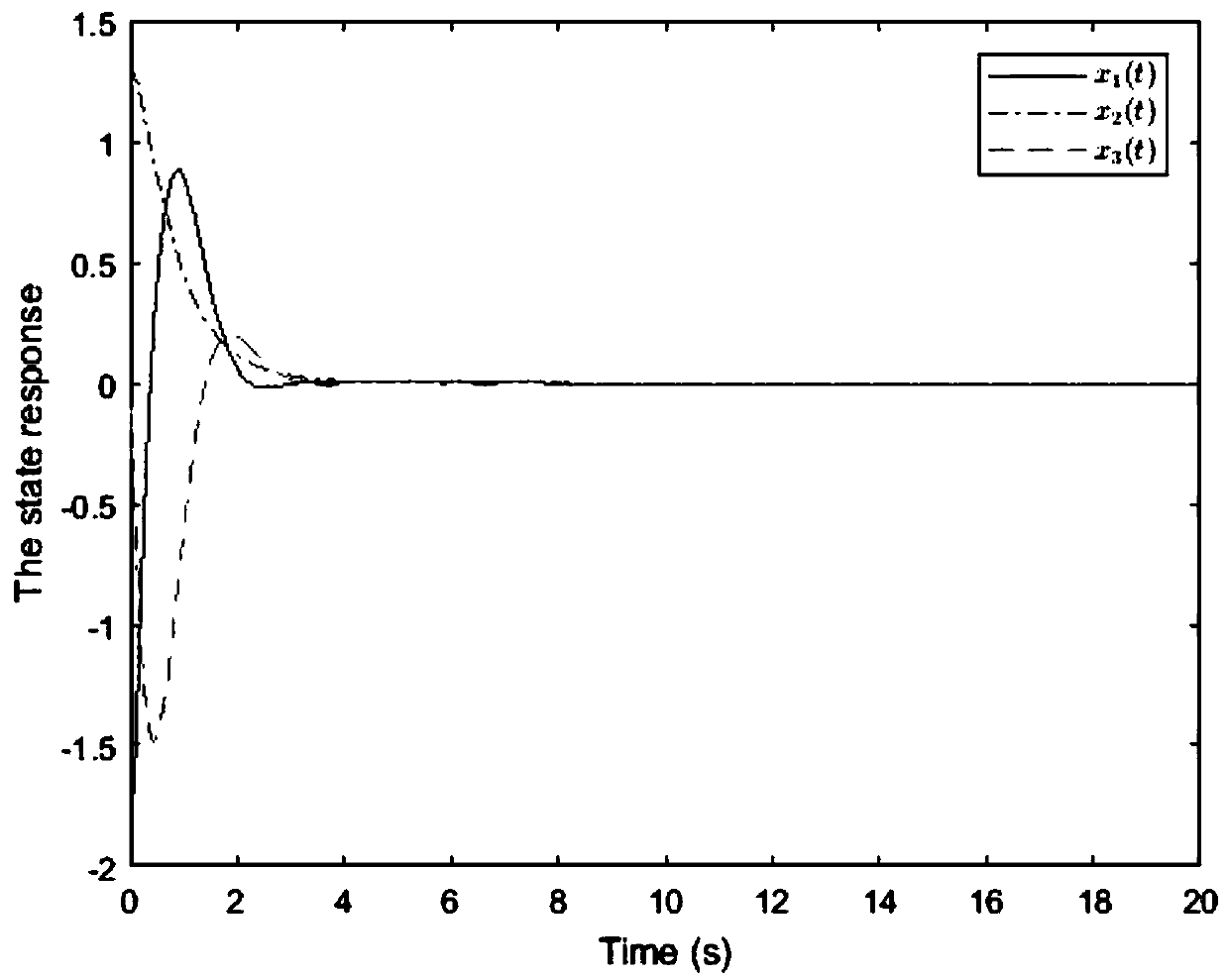
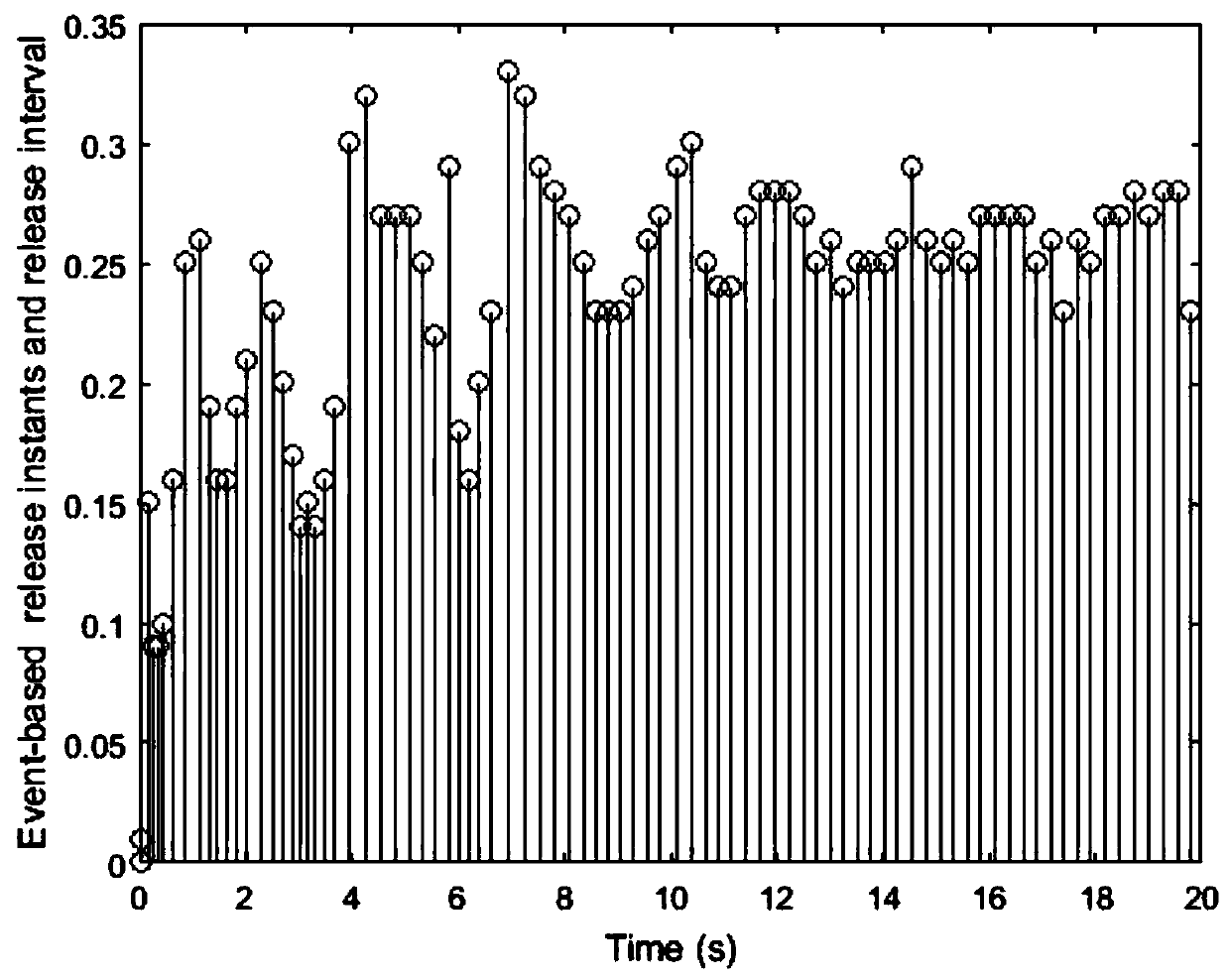
Security control method of event-driven network control system under multi-network attack
ActiveCN110213115AImprove stabilityReduce the number of transfersData switching networksLyapunov stabilityEvent trigger
The invention provides a security control method of an event-driven network control system under a multi-network attack. Considering the network transmission security problem, a random network spoofing attack, a replay attack and a DoS attack are sequentially introduced, and a system closed-loop model under the multi-network attack is established. Further considering the constraint of the limitednetwork bandwidth, an event trigger mechanism is introduced to screen and release sampling data meeting a preset event trigger condition to the network for transmission, thereby establishing a new switching system model on the basis of the system closed-loop model. Based on a switching system model, a Lyapunov stability theory is utilized to obtain a sufficiency condition for enabling the system to meet the stability of a mean square index, and a group of linear matrix inequalities is solved to obtain the gain of the state feedback controller. Compared with an existing controller design method, safe and stable operation of the network control system under the influence of multi-network attacks is guaranteed, meanwhile, the data transmission frequency is reduced, and limited network bandwidth resources are saved.
Owner:NANJING UNIV OF FINANCE & ECONOMICS
Method and device for transmitting and acquiring uplink HARQ feedback information
ActiveCN106797283AImprove experienceReduce Feedback LatencyError prevention/detection by using return channelSignal allocationData transmissionUser equipment
The invention provides a method and a device for transmitting and acquiring uplink HARQ feedback information, wherein the method comprises the steps of acquiring a service priority sequence list of downlink subframes; according to the service priority sequence list, multiplexing the HARQ feedback information of the downlink subframes according to a sequence that the service priorities reduce from highest to lowest, and obtaining to-be-transmitted HARQ feedback information; successively assigning uplink subframes to the to-be-transmitted HARQ feedback information, and transmitting the to-be-transmitted HARQ feedback information to a base station. According to the method for transmitting the uplink HARQ feedback information, user equipment can preferably transmit the HARQ feedback information of the subframes with low time delay requirement. When the base station acquires a transmission error of time-delay-sensitive service data, the downlink subframes which carry the time-delay-sensitive service data can be preferably retransmitted, thereby shortening transmission time of the time-delay-sensitive service data.
Owner:BEIJING XIAOMI MOBILE SOFTWARE CO LTD
Method and equipment for announcing media access control (MAC) address information
ActiveCN103078969AReduce the number of transfersSave network resourcesNetworks interconnectionVirtualizationInterconnection
The invention discloses a method and equipment for announcing media access control (MAC) address information. The method is applied to a virtualization network which consists of edge devices respectively in site networks of large two-layer interconnection. The method comprises the following steps of: competing for a primary device according to the priority by the edge devices respectively in the site networks in the same virtualization network case; sending a link-state packet (LSP) in which MAC address information required to be announced is packaged to the primary device when the edge devices respectively in the site networks need to announce the MAC address information if the device is a non-primary device; sending the LSP in which the MAC address information required to be announced is packaged to all neighbor devices of the device if the device is the primary device; and transmitting the received LSP to other neighbor devices except an LSP sender after the LSP in which the MAC address information is packaged is received by the edge devices respectively in the site networks if the device is the primary device. By adopting the method and equipment for announcing the MAC address information, network resources used during a process of announcing the MAC address information can be reduced.
Owner:XINHUASAN INFORMATION TECH CO LTD
Network transmission method for large extensible markup language (XML) document
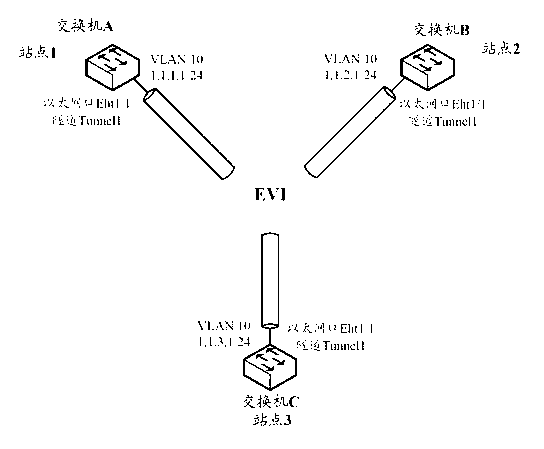
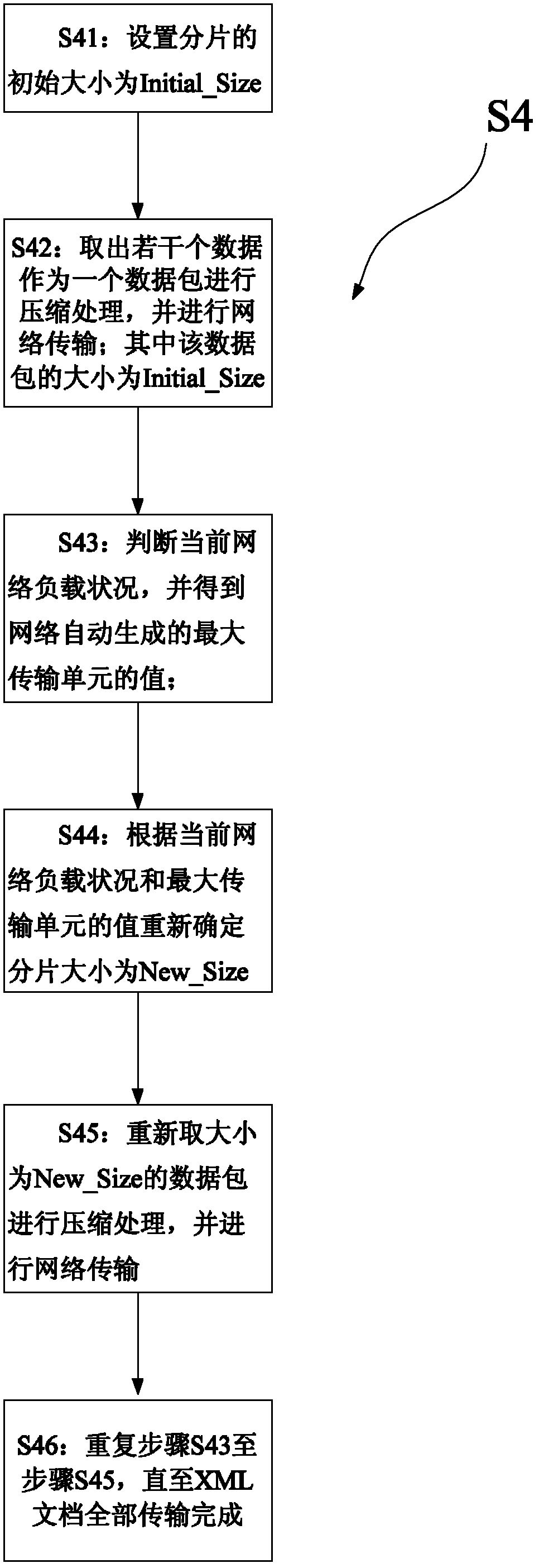
InactiveCN102571966AReduce the number of transfersImprove transmission efficiencyTransmissionReal-time computingMaximum transmission unit
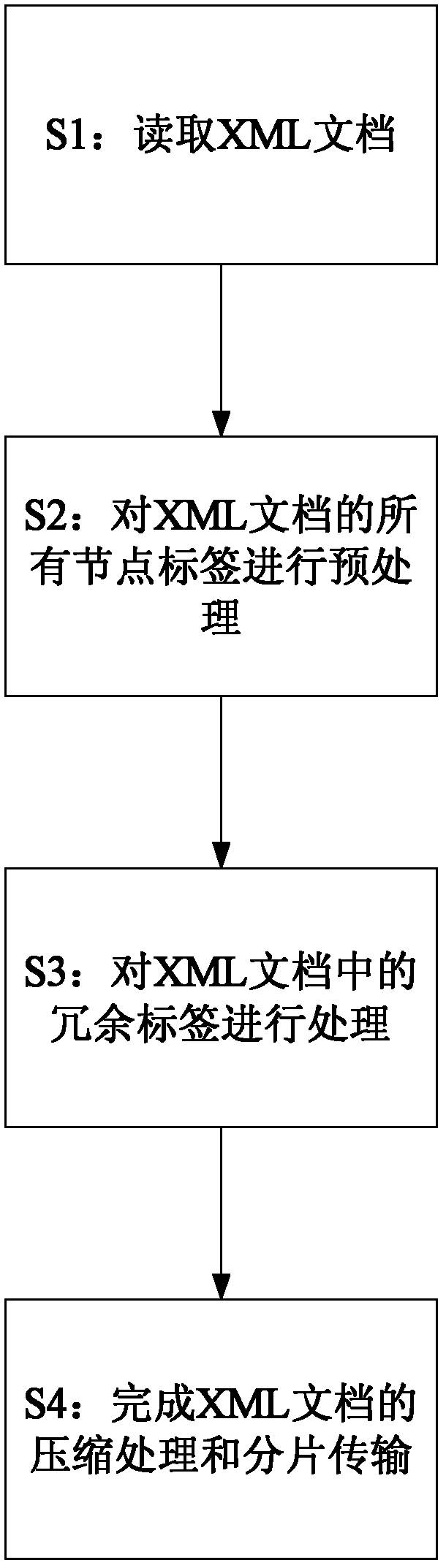
The invention discloses a network transmission method for a large extensible markup language (XML) document. The method comprises the following steps of: 1, reading the XML document; 2, preprocessing all node tags in the XML document; 3, processing redundant tags in the XML document; and 4, finishing the compression processing and fragmentation transmission of the XML document. The step 4 further comprises the following steps of: 41, setting an initial fragmentation size to be Initial_Size; 42, extracting a plurality of pieces of data to form a data packet for the compression processing and the network transmission, wherein the size of the data packet is Initial_Size; 43, judging a current network load condition, and obtaining a value of a maximum transmission unit; 44, re-determining a fragmentation size to be New-Size according to the current network load condition and the value of the maximum transmission unit; 45, re-extracting a data packet with the size of New-Size for the compression processing and the network transmission; and 46, repeating the steps 43 to 45.
Owner:PEKING UNIV FOUNDER GRP CO LTD +2
Security event triggering control method for load frequency control system under DoS attack
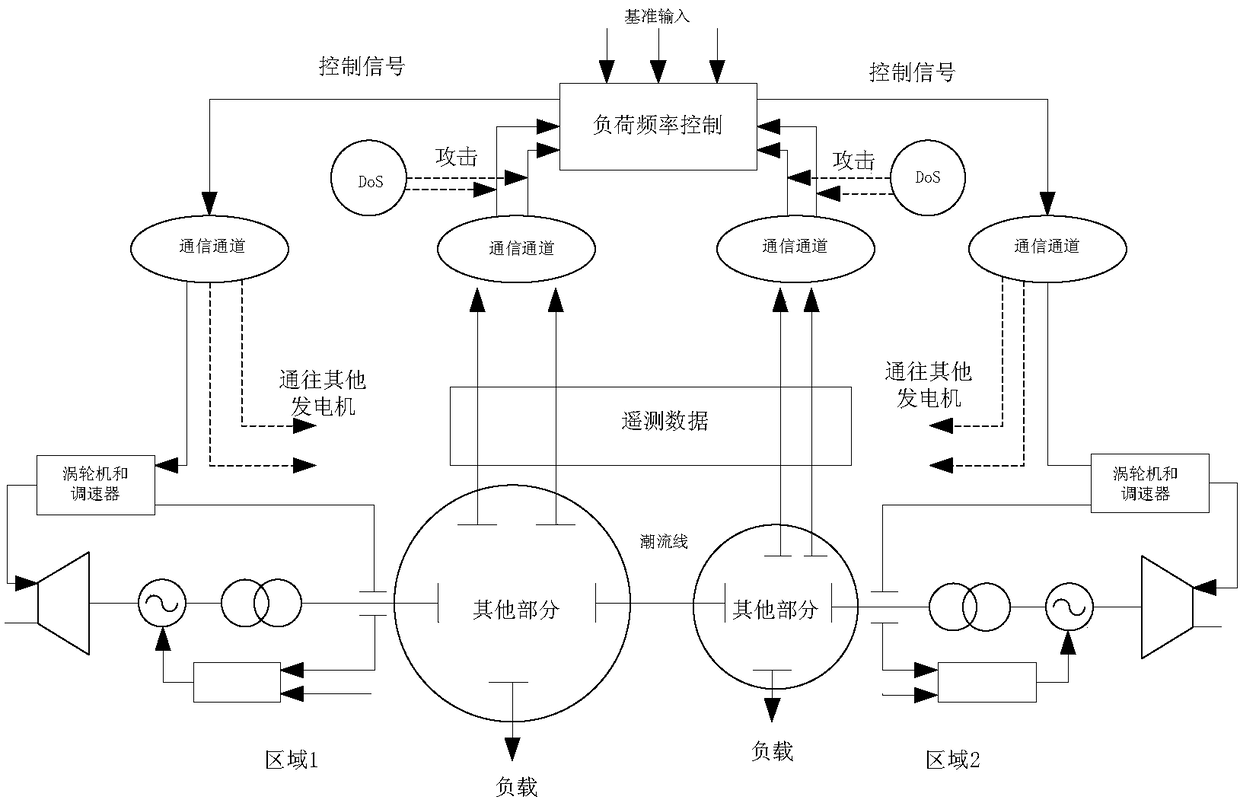
InactiveCN108258681AReduce the number of transfersReduce delivery pressurePower oscillations reduction/preventionEvent triggerElectric power system
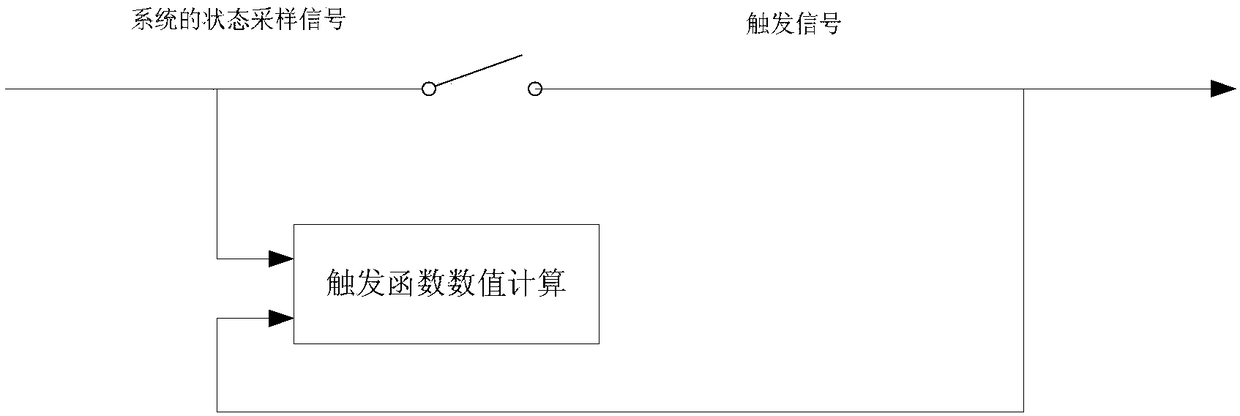
The invention discloses a security event triggering control method for a load frequency control system under DoS attack. In view of the current situation in which a load frequency control system of amulti-region power system may suffer from network attacks, DoS attack is introduced to build a switching system model in order to solve the security control problem. Moreover, in view of the current situation of limited bandwidth resources, an event triggering mechanism is introduced. The main idea of the event triggering mechanism is as follows: whether a current sampling signal satisfies a preset triggering algorithm is detected; if the current sampling signal does not satisfy the preset triggering algorithm, the sampling signal is transmitted to a controller; and otherwise, the sampling signal is abandoned. Through improvement from the two aspects, it is ensured that the system can run safely and smoothly under the premise of global stability, the number of redundant signals transmittedis reduced, the network transmission pressure is reduced, and bandwidth resources and energy required for communication are saved.
Owner:NANJING UNIV OF POSTS & TELECOMM
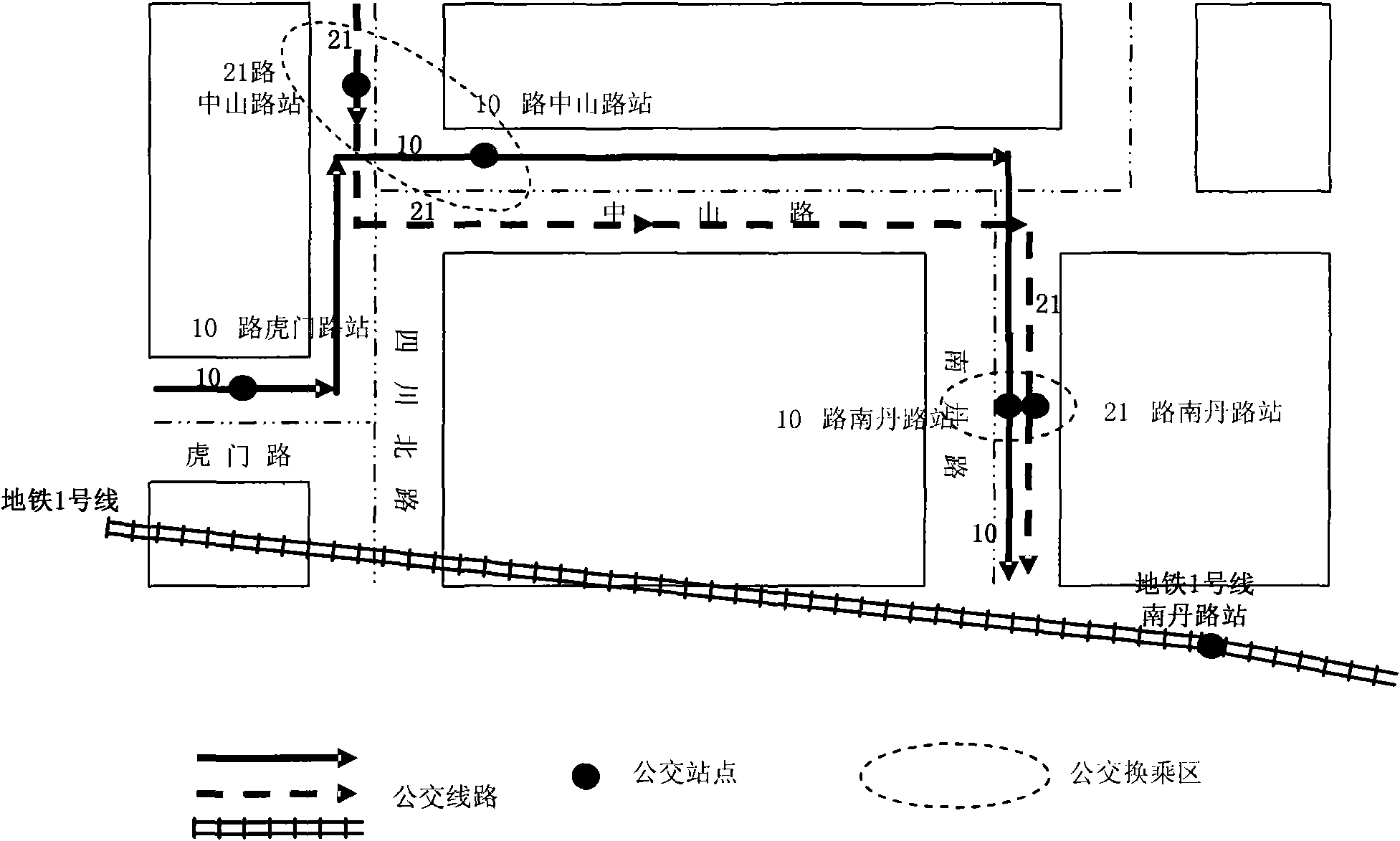
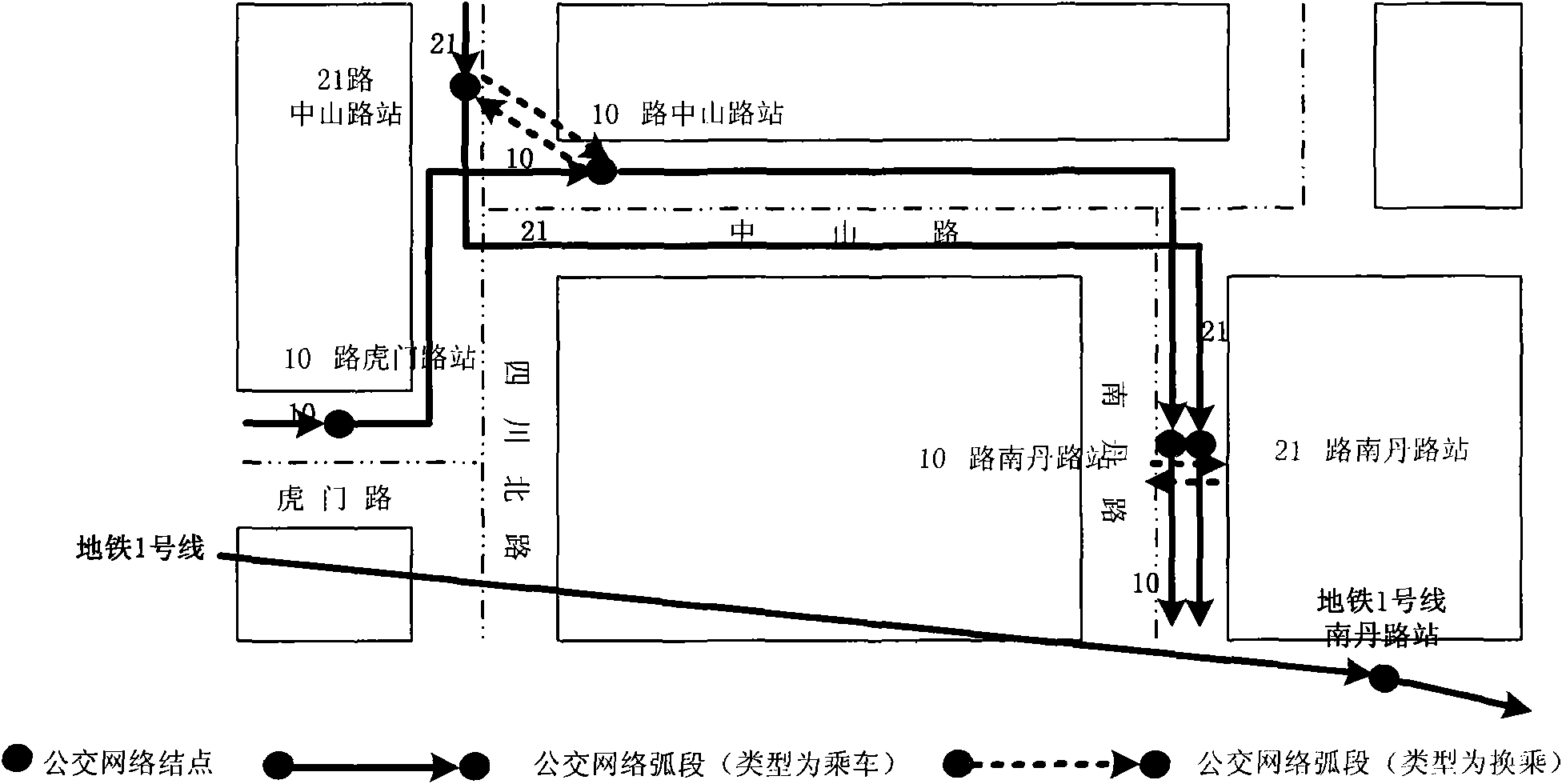
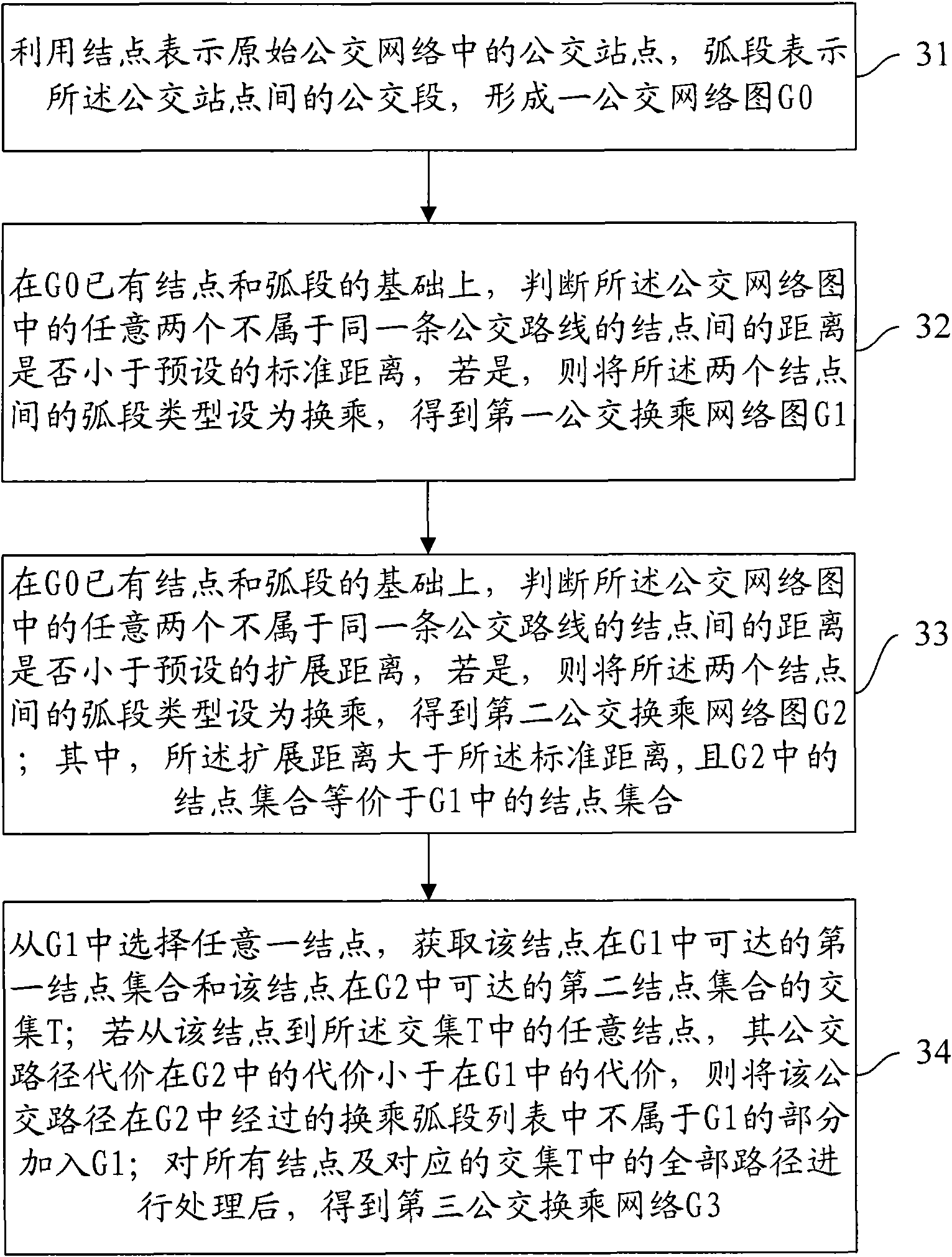
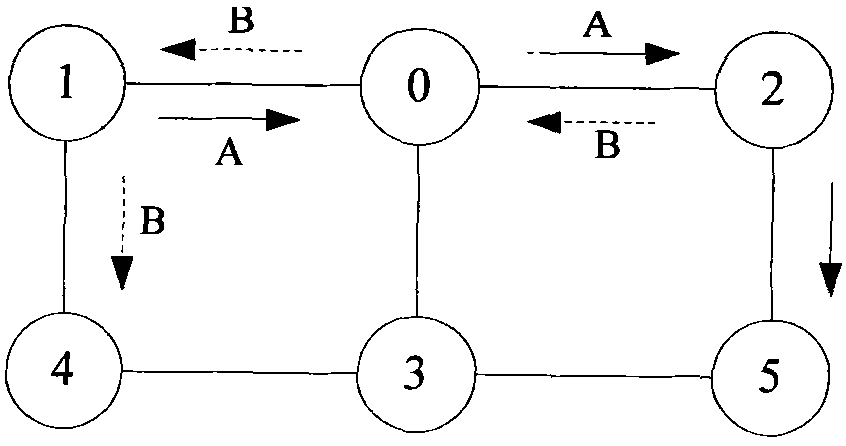
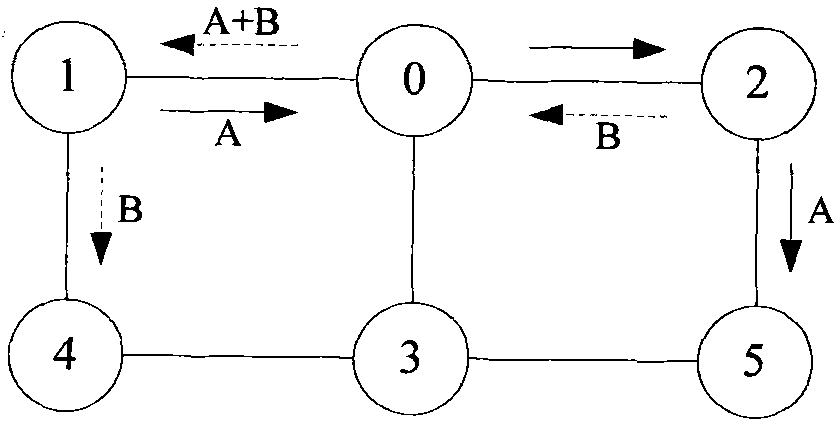
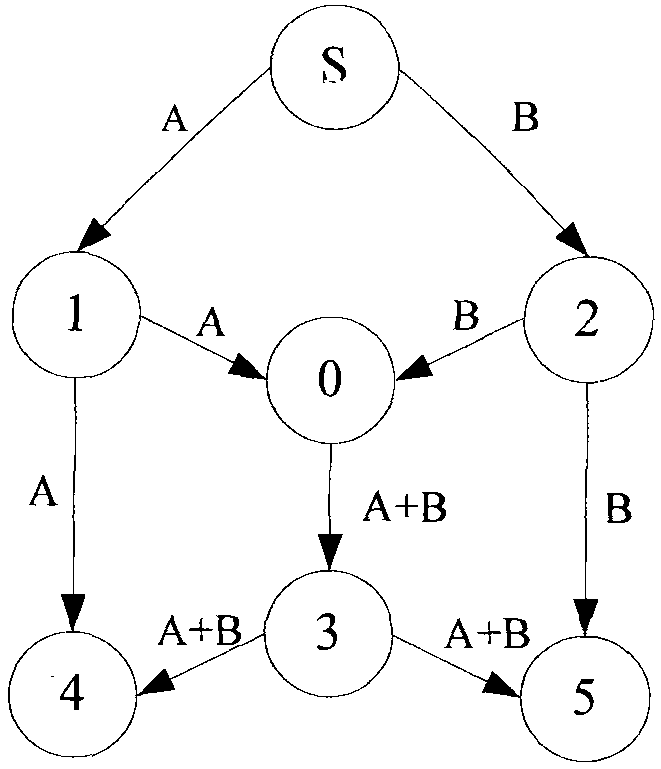
Method and device for constructing bus transfer network
InactiveCN101650705AReduce travel costsBest travel optionSpecial data processing applicationsEmbedded systemStandard distance
The invention provides method and device for constructing bus transfer network. The method comprises the following steps: when the distance between every two junctions belonging to different bus linesis shorter than a preset standard distance, the arc distance between the two junctions is set as transfer to obtain G1; when the distance between every two junctions belonging to different bus linesis shorter than a preset extending distance, the arc distance between the two junctions is set as transfer to obtain G2, wherein the extending distance is larger than the standard distance; a junctionis selected from G1 to obtain an intersection T of a first junction collection that the junction can reach in G1 and a second junction collection that the junction can reach in G2; from the mode to any junction in the intersection T, the cost for taking bus in G2 is less than that in G1, and the parts of the bus line in the list of the interchange arc sections of G2 but out of G1 are added to G1;and all bus lines in all the junctions and corresponding intersection T are processed to obtain G3. The invention is beneficial to providing a better choice for traveling.
Owner:NAVINFO
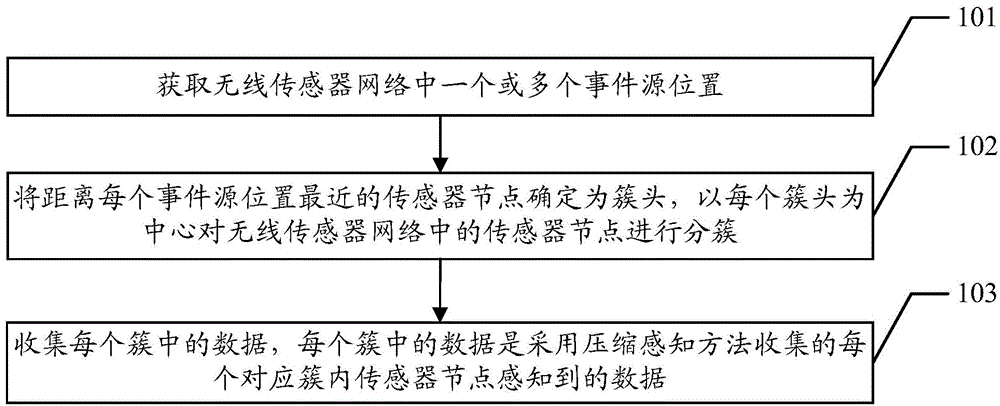
Compressive sensing based dynamic clustering wireless sensor network data collecting method and device
ActiveCN104618947AExtend your lifeStrong correlationNetwork topologiesWireless sensor networkingSensor node
The embodiment of the invention discloses a compressive sensing based dynamic clustering wireless sensor network data collecting method. The compressive sensing based dynamic clustering wireless sensor network data collecting method comprises the steps of obtaining one or more event source positions in a wireless sensor network, determining a sensor node nearest to each event source position as a cluster head and clustering the sensor nodes in the wireless sensor network with each cluster head as center; collecting data in each cluster, wherein the data sensed by the sensor nodes in each corresponding cluster are collected by means of a compressive sensing method. The embodiment of the invention discloses further provides a compressive sensing based dynamic clustering wireless sensor network data collecting device. The compressive sensing based dynamic clustering wireless sensor network data collecting device and method can use an event source as the center to perform clustering, utilize the compressive sensing technology to collect the data in the clusters, perform dynamic clustering on the wireless sensor network according to position change of the event source and accordingly enable the data collected in the nodes in the clusters to be high in dependency, transmission times can be fewer at the same accuracy, and accordingly the service life of the network is prolonged.
Owner:THE PLA INFORMATION ENG UNIV
Clean room environment-based safe virtual machine migration method
ActiveCN105700945AEnsure credibleImprove migration efficiencyProgram initiation/switchingSoftware simulation/interpretation/emulationConfidentialityTransfer procedure
The invention provides a clean room environment-based safe virtual machine migration method. Through the method, the credibility of physical computers is validated before the migration of a virtual machine, so that the virtual machine can be migrated onto a credible physical computer, and the confidentiality and integrity of the virtual machine data in the transmission process can be ensured. According to the method, the number of migration iterations can be decreased to a certain extent, so that the migration efficiency is improved; and the method is simple in realization process and easy to operate.
Owner:CENT SOUTH UNIV
Apparatus and method for implementing OTA based on bearer independent protocol
ActiveCN101222514AIncrease transfer rateReduce overheadRadio/inductive link selection arrangementsTransmissionComputer hardwareTransmission protocol
The invention discloses a device for carrying unrelated protocol-based realization of over the air download, comprising a movable network protocol module, a transmission protocol module and a carrying unrelated protocol module, wherein the movable network protocol module is used to store and realize the movable network protocol stack which is used as a data transmission channel; the transmission protocol module is used to store and realize the transmission protocol stack and builds up a transmission layer connection with a far end server end by adopting the transmission protocol; the carrying unrelated protocol module is used to receive the data sent by a client end by the carrying unrelated protocol, send the data of the client end to the far end server by the transmission protocol stack, the transmission layer connection and the movable network protocol stack, receive the data which are sent to the client end by the far end server by the movable network protocol stack, the transmission protocol stack and the transmission layer connection and send the data to the client end by the carrying unrelated protocol, thereby improving the transmission rate and the transmission safety and reliability of the data in the over the air download.
Owner:ZTE CORP
Fruit and vegetable picking robot and control method thereof
ActiveCN109773788ASimple structureLow costProgramme-controlled manipulatorPicking devicesCamera imageControl system
The invention discloses a fruit and vegetable picking robot and a control method thereof. The fruit and vegetable picking robot includes a mobile platform, a picking mechanical arm, a picking hand, acontrol system and a trailer. The mobile platform is connected with the trailer. The picking mechanical arm is installed on the mobile platform, and the picking hand is installed at the tail end of the mechanical arm. An eye-in-hand camera for obtaining pose information of a target object is mounted at the edge of the picking hand, the picking hand is provided with a vacuum picking device for picking fruits and vegetables, and the vacuum picking device conveys the fruits and vegetables to the trailer through vacuum tubes. A parallel adjusting mechanism is driven by six servo electric cylindersto realize the six-degree-of-freedom pose adjustment of the camera. The control system is used for processing the generation and transmission of camera image information and pose adjustment commands.The fruit and vegetable picking robot has the advantages of low cost, high precision, wide application range and the like, and is conveniently used in the picking process of various agricultural fruits and vegetables.
Owner:XI AN JIAOTONG UNIV
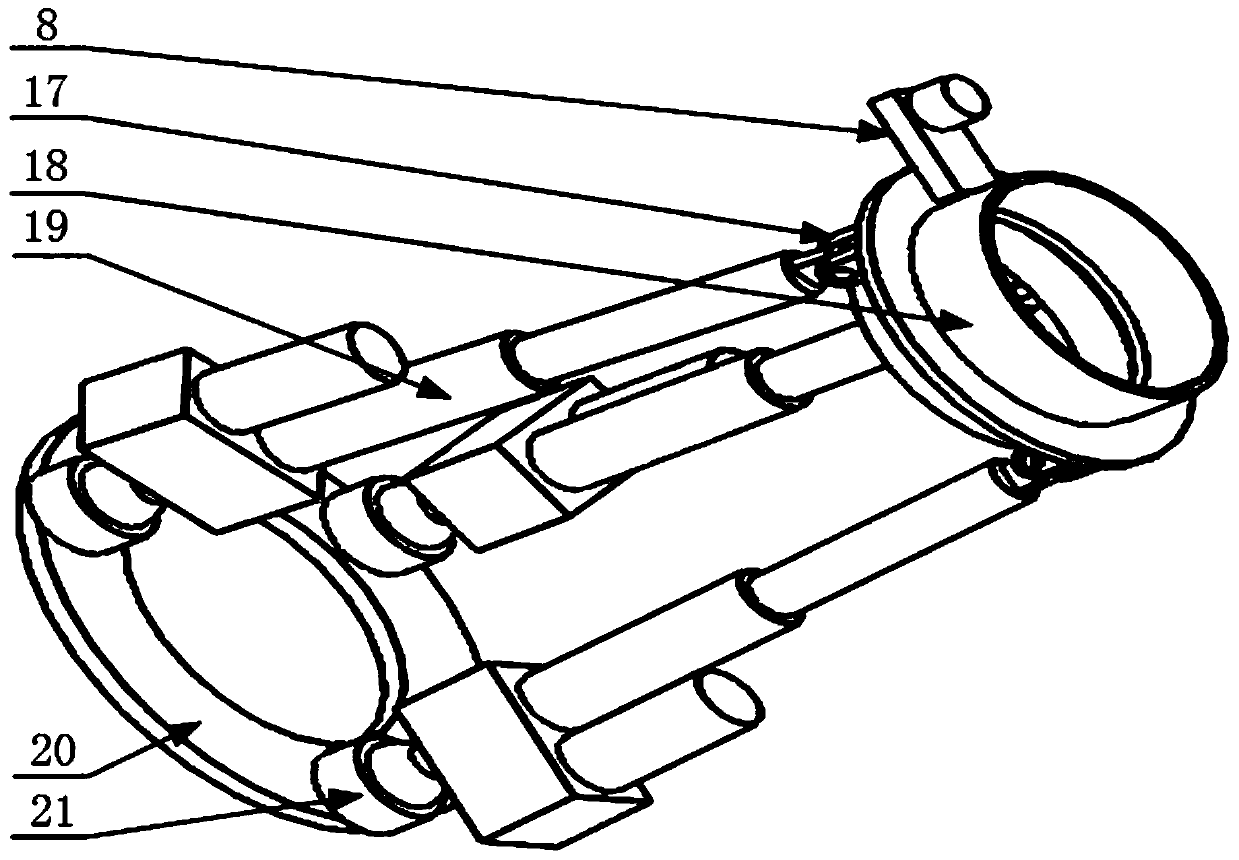
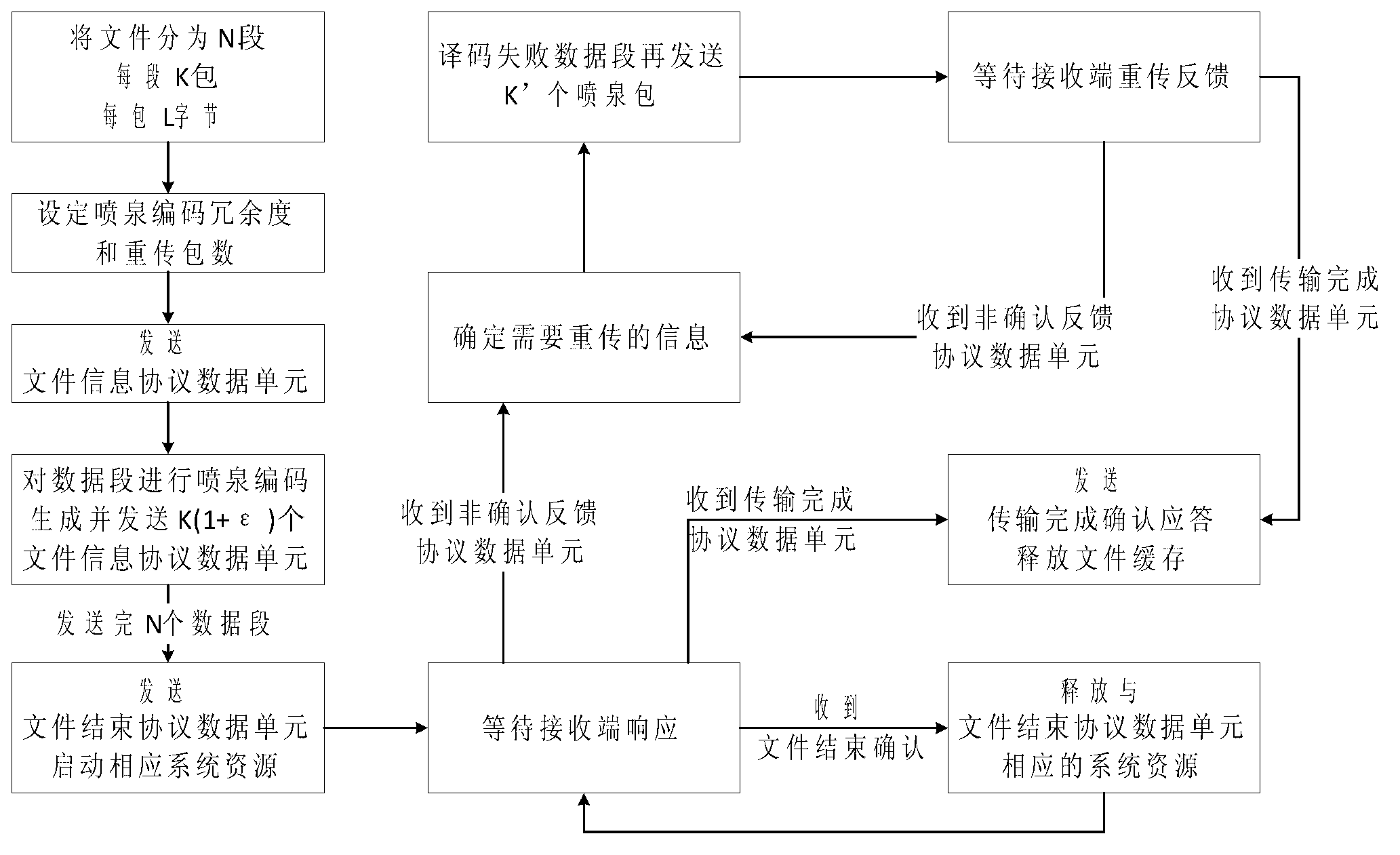
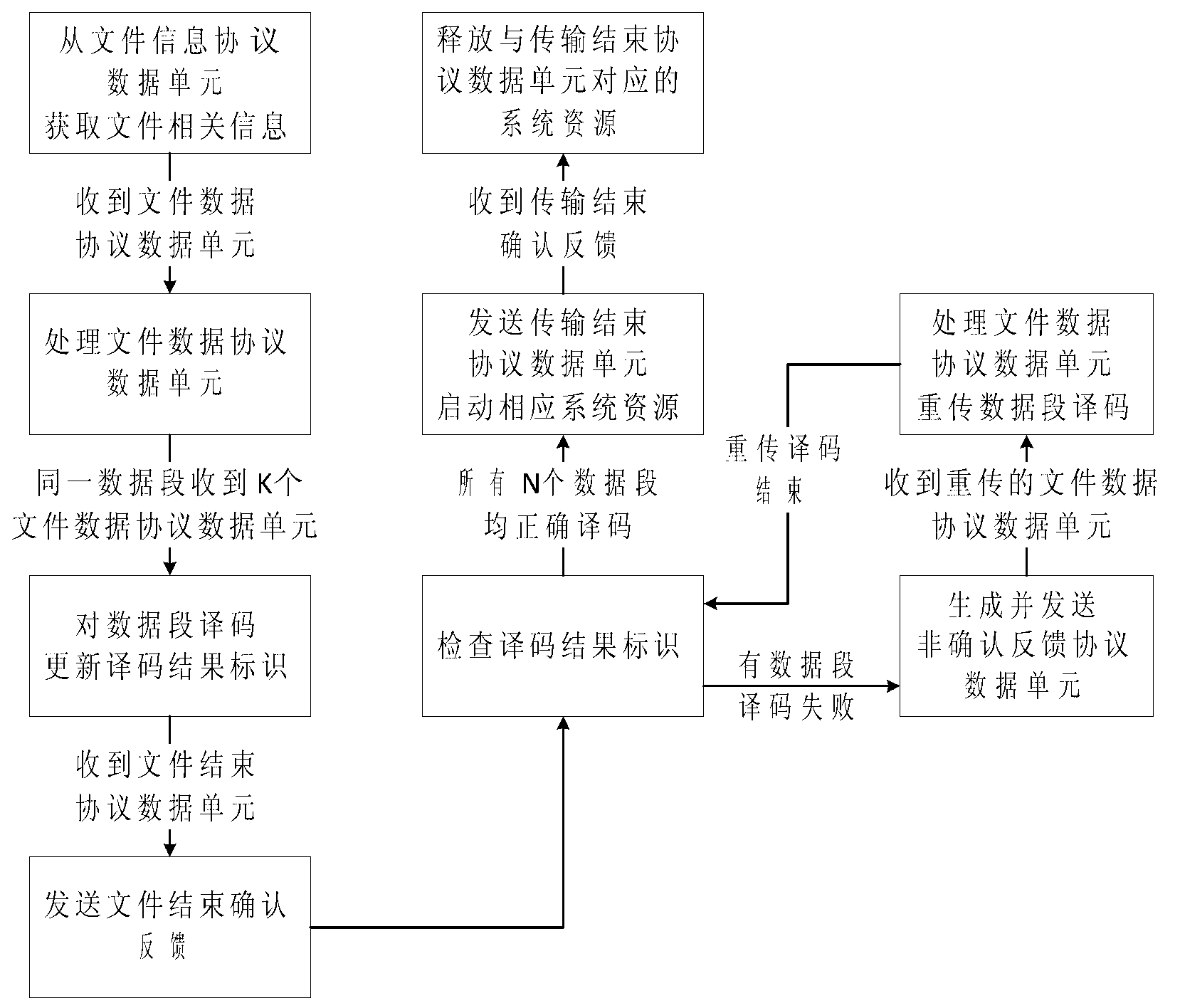
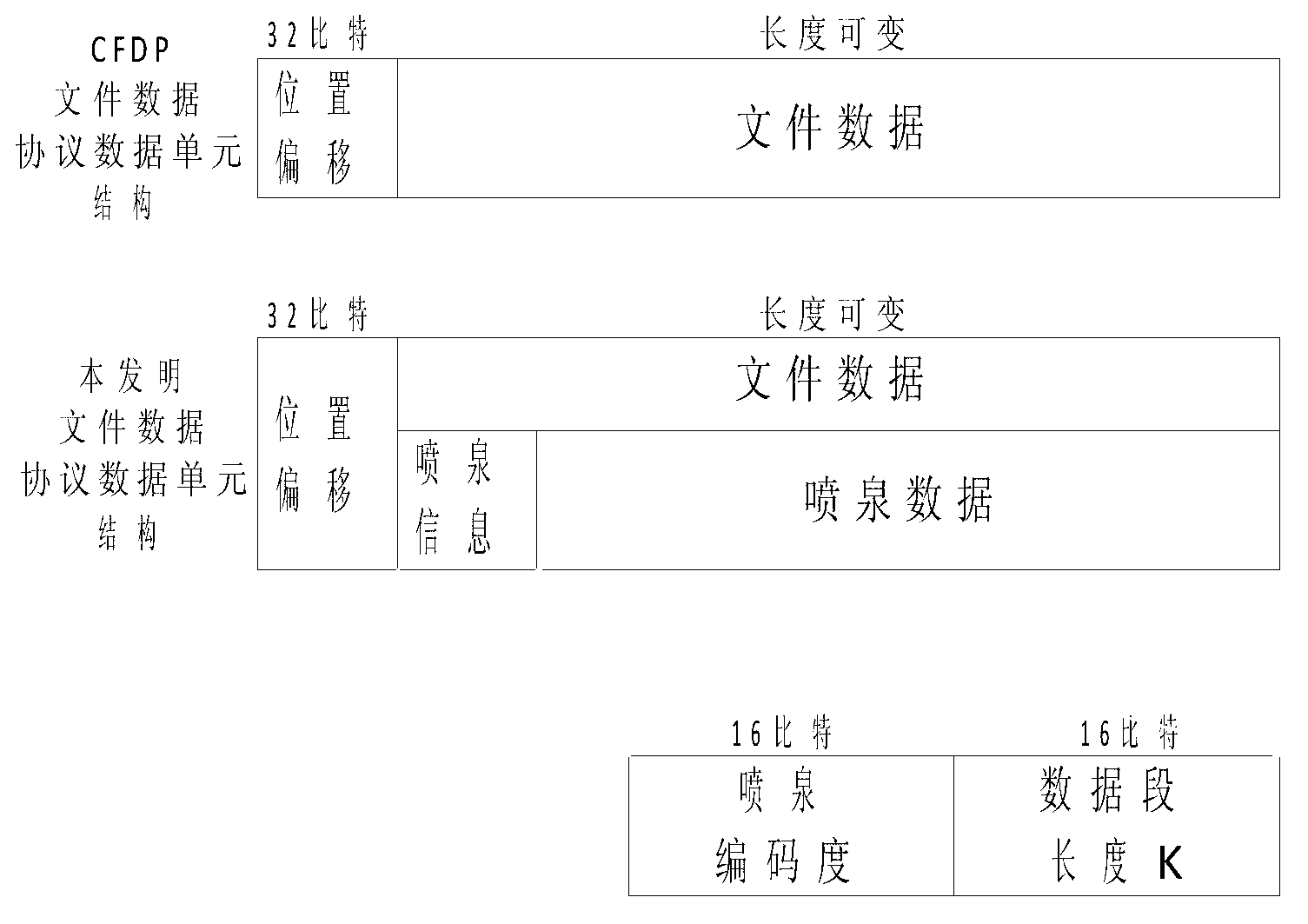
File transmission method in deep space communication
InactiveCN103078707AIncrease the probability of a successful transferReduce the number of transfersError prevention/detection by using return channelReliable transmissionSuccessful transmission
The invention relates to a file transmission method in deep space communication and belongs to the technical field of deep space communication. According to the method, the predetermined coding redundancy is used for carrying out fountain coding on file data grouping, then, the sending is carried out through a link, a mode that a sending end actively stops is adopted, the one-step successful transmission probability of files is improved, the file transmission efficiency is improved, the bandwidth waste in large delay deep space communication environment caused by the passive stop of the sending end is avoided, and the link utilization rate is improved; and meanwhile, a reliable file transmission method in CFDP (CCSDS (consultative committee for space data system) file delivery protocol) is combined, the contents of a file data PDU (protocol data unit) and the contents of an NAK (negative acknowledge) PDU are defined, the reliable transmission of deep space files on the basis of the fountain coding is realized, and good protocol compatibility and practicability are realized.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
CTP plate making method and apparatus by using ink jet imaging principle
InactiveCN100562804CEliminate cumbersome operationsLow costPlate printingFoil printingLatent imageFrequency modulation
The invention discloses a CTP direct plate-making method and equipment using the principle of inkjet imaging. Using the principle of inkjet imaging, an inkjet printer is used to spray hydrophilic ink onto the surface of a hydrophilic plate to form a lipophilic information recording area. Photocuring or heat curing stabilizes the printed information on the surface of the printing plate and can be printed on the machine. The method of the invention utilizes the principle of ink-jet imaging, and the loss of information in the plate making process is very small. When the frequency modulation software and the printer parameters are properly matched, 100% loss-free transfer can basically be realized. In addition, this technology can avoid the process of ordinary silver salt plate making and photosensitive or thermal CTP plate making to make a latent image first and then develop it. It saves the film and subsequent development process, and is the most direct CTP technology.
Owner:BEIJING ZHONGKE NANO THINK PRINT TECH
Access control method, apparatus, server, and storage medium for application program interface
ActiveCN109067728AReduce complexityReduce the number of transfersDigital data authenticationTransmissionThird partyReverse proxy
The invention relates to an access control method, apparatus, server, and storage medium foran application program interface, belonging to the communication field, and used in a reverse proxy server which is arranged at the front end of a target server.The method comprises: receiving a first API access request sent by a third party application; the first API access request is used for requesting access to a target API in the target server; authenticating the third party application according to the authentication information in the first API access request; sending a second API access requestto the target server when the authentication to the third party application passes, wherein the second API access request is used for triggering the target server to call the service content corresponding to the target API and returning the service content to the third party application.The invention can solve the technical problems that the authentication server is additionally built on the basisof the original API access system, and the deployment difficulty and complexity of the server are high, and can reduce the complexity of server deployment.
Owner:SUZHOU KEDA TECH
Method for network code sensing cross-layer energy-saving routing in wireless sensor network
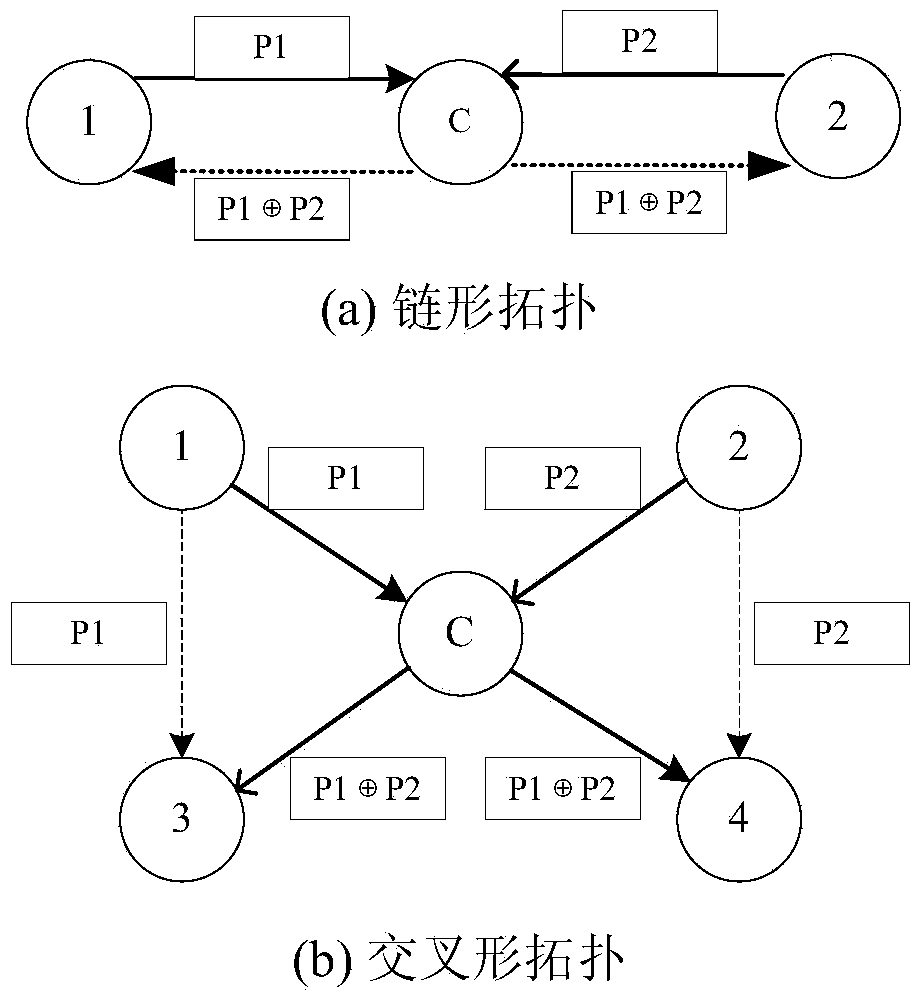
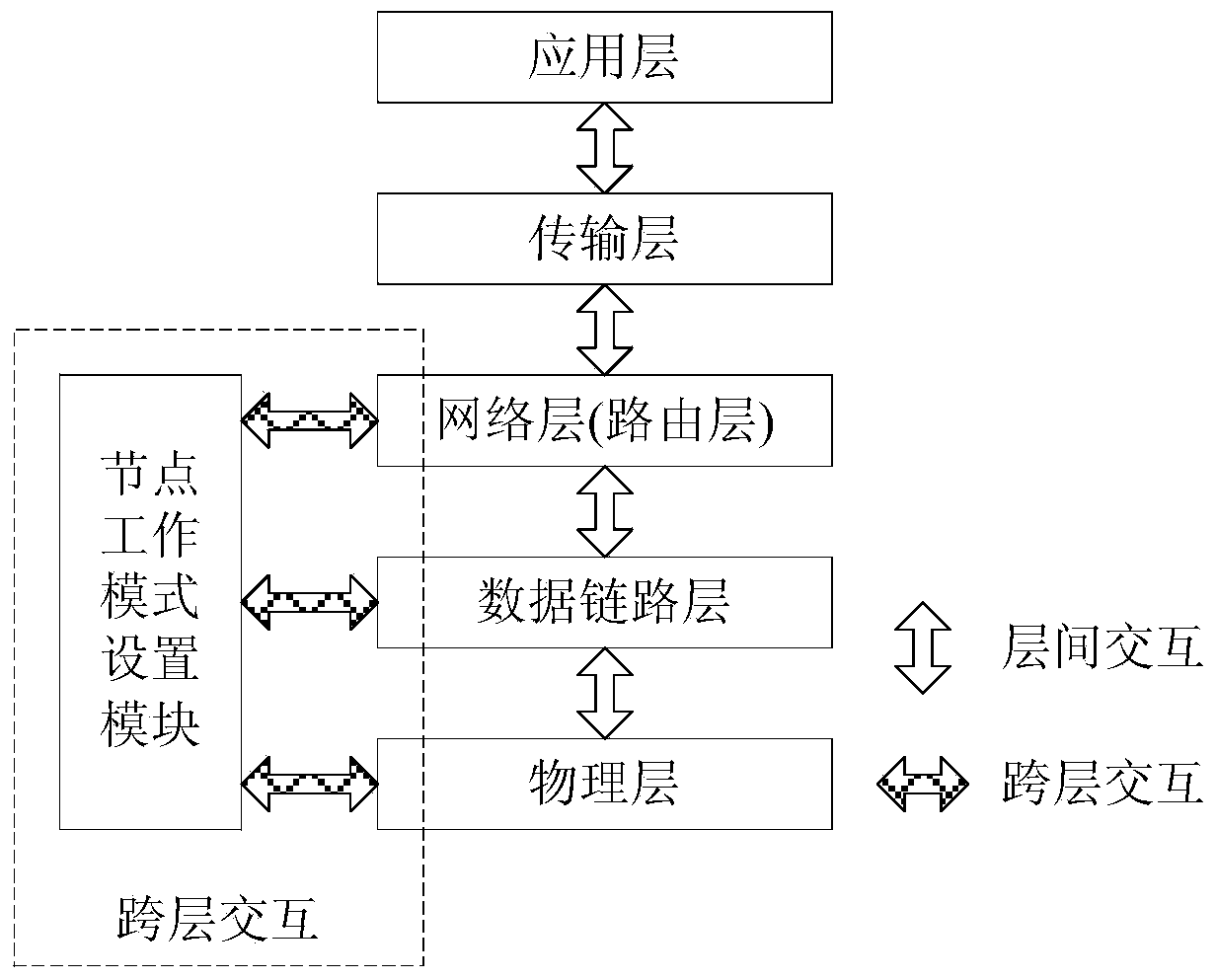
ActiveCN103458487AReduce the number of transfersImprove data transfer efficiencyPower managementHigh level techniquesMobile wireless sensor networkNetwork code
The invention discloses a method for network code sensing cross-layer energy-saving routing in a wireless sensor network. The method for network code sensing cross-layer energy-saving routing in the wireless sensor network mainly comprises the steps that (1) inter-flow network coding is used to reduce the frequency of data transmission and energy consumption, (2) a cross-layer mechanism among a network layer, a data link layer and a physical layer is used to determine monitoring nodes in a network, then a large amount of energy consumption, used for unnecessary monitoring, of nodes is reduced, the lifetime of the nodes is prolonged, and therefore the lifetime of the network is prolonged. According to the method for network code sensing cross-layer energy-saving routing in the wireless sensor network, the cross-layer mechanism is used for network code sensing routing, the number of the monitoring nodes is greatly reduced by means of the cross-layer mechanism on the premise that the inter-flow network coding is used to reduce the frequency of data transmission and the energy consumption, unnecessary energy consumption of a large number of nodes for monitoring in existing network code sensing routing is eliminated, therefore, energy consumption of sensing nodes in the wireless sensor network is reduced, and the network lifetime of the sensor network is prolonged.
Owner:YANCHENG INST OF TECH
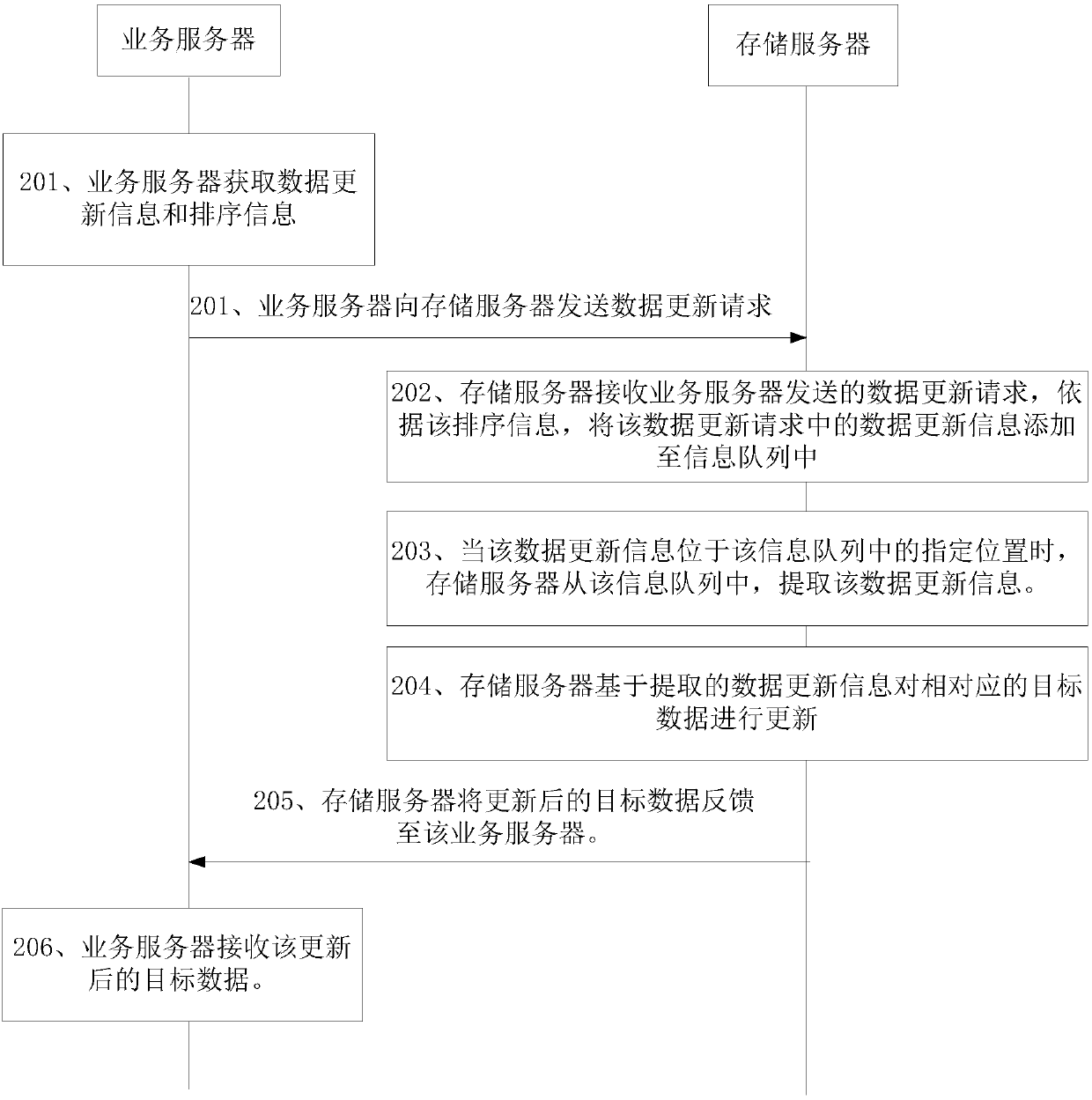
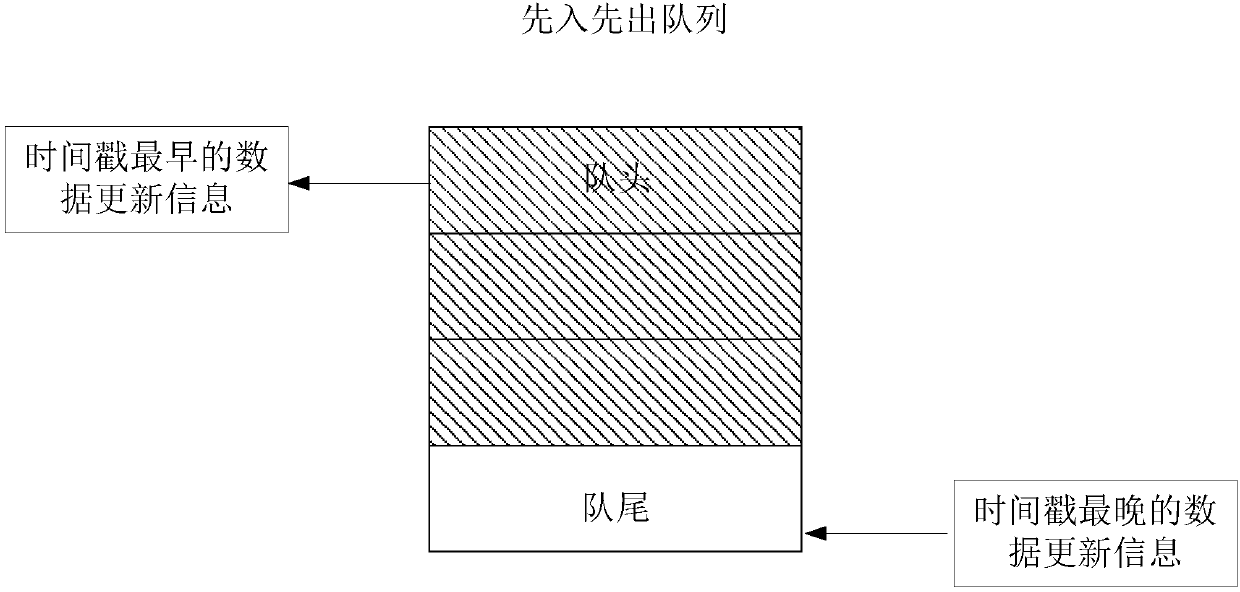
Data updating method, device and system
The invention discloses a data updating method, device and system, and belongs to the technical field of networks. The method comprises the steps that a data updating request sent by a service serveris received, wherein the data updating request comprises data updating information and ordering information; the data updating information in the data updating request is added into an information queue according to the ordering information; and when the data updating information is located at a specific position in the information queue, the data updating information is extracted from the information queue, corresponding target data is updated on the basis of the extracted data updating information, and the updated target data is fed back to the service server. According to the data updatingmethod, device and system, a queuing mechanism is provided, data updating information of multiple data updating requests can be ordered in the information queue, conflicts caused by updating the sametarget data simultaneously are avoided, the transmission number is decreased, the transmission resources are saved, the data updating speed is increased, and the data updating efficiency is improved.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Method for centralized allocation of time slots of industrial wireless network in TSCH mode
ActiveCN107276628AShorten the timeReduce latencyTransmissionWireless communicationRefresh cycleData transmission time
The invention discloses a method for centralized allocation of time slots of an industrial wireless network in a TSCH mode and aims at improving the problems of determinacy and reliability of the industrial wireless network and reducing the network delay. According to the method, the deterministic scheduling of the network can be guaranteed, so that the high reliability is realized; field equipment sends data to route equipment according to the refresh cycle priority under a scheduling mechanism of the method; the route equipment receives data of the field equipment, selects a storage stack according to the data priority, carries out aggregation on the data from different field equipment according to the data priority in order to generate a data packet when the network communication traffic is too large and forwards the data packet according to the data priority at the route equipment. The scheduling method adopts the ways of refresh cycle priority and data priority to guarantee that each equipment has an opportunity of sending the data to a gateway, so that the determinacy and the reliability of the network are improved, and furthermore, through adoption of an aggregation way, the network data transmission times and the network transmission cost can be reduced, so that the low delay is realized.
Owner:CHONGQING UNIV OF POSTS & TELECOMM +1
Wireless mesh network coding method
ActiveCN102487306AOptimize data forwarding mechanismImprove network throughputError prevention/detection by using return channelWireless mesh networkOriginal data
The invention discloses a wireless mesh network coding method. By using a current COPE coding algorithm, coding gain is low. By using the method of the invention, the above problem can be solved. In the method of the invention, for a participated XOR original data packet, a DESN identification is added in a packet header of the generated data packet so as to identify a destination node of the original data packet. A receiving side determines whether the receiving side itself or a neighbor is the destination node through the DESN identification and different strategies are executed. The receiving side only needs to perform decoding to the link which is used to enter into a relay node and perform routing to the link which is used to enter into a target node. Through using the above mechanism, network coding performance can be increased. The method of the invention can be used in various kinds of communication networks. Times of transmissions of the original data packet can be reduced. Network coding gain and network throughput can be effectively increased. The method has a good practical value. A new path is provided for the research and the design of the network coding.
Owner:盐城市景能电气设备有限公司
Load-balance-based satellite network on-demand routing method
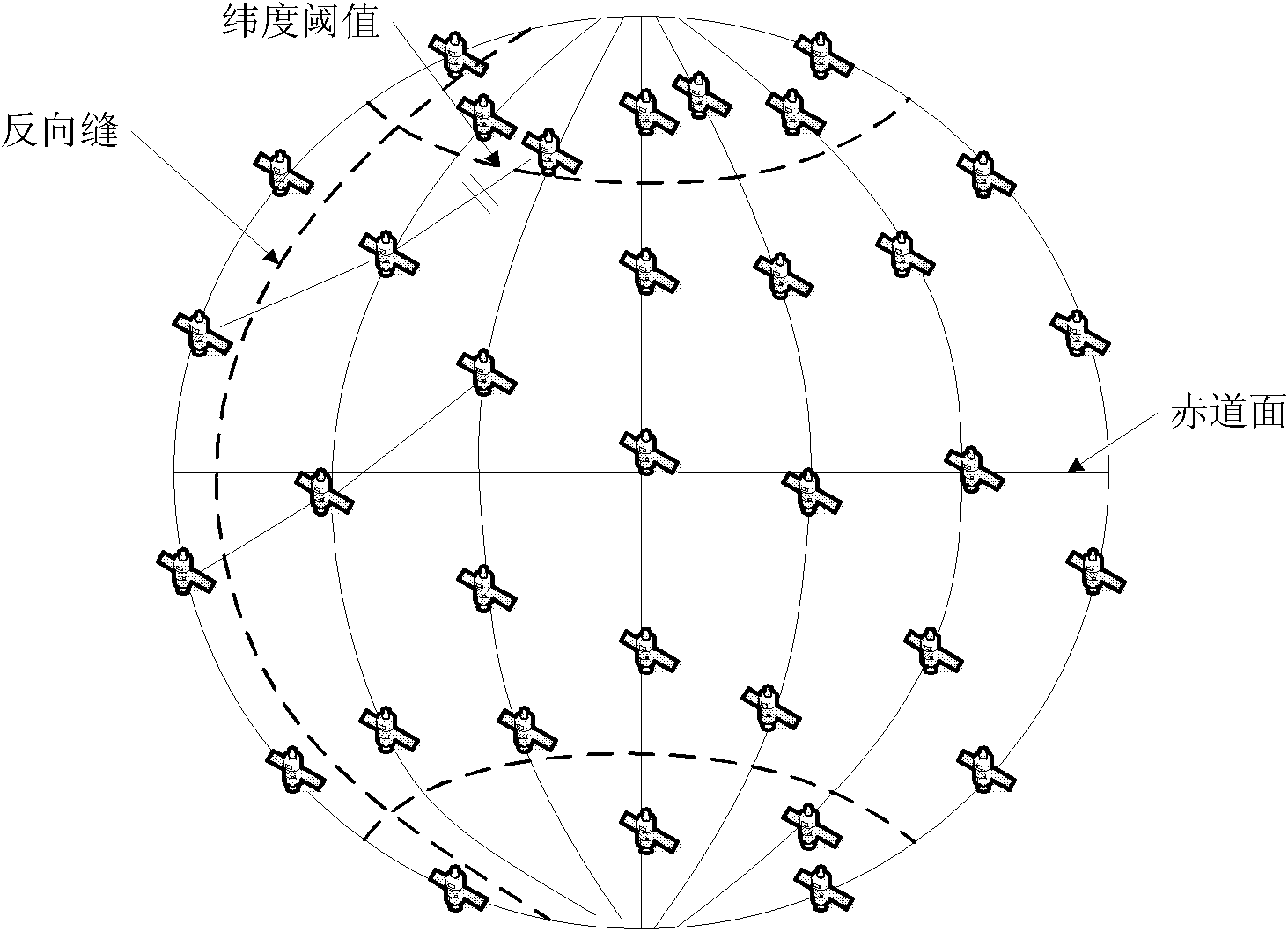
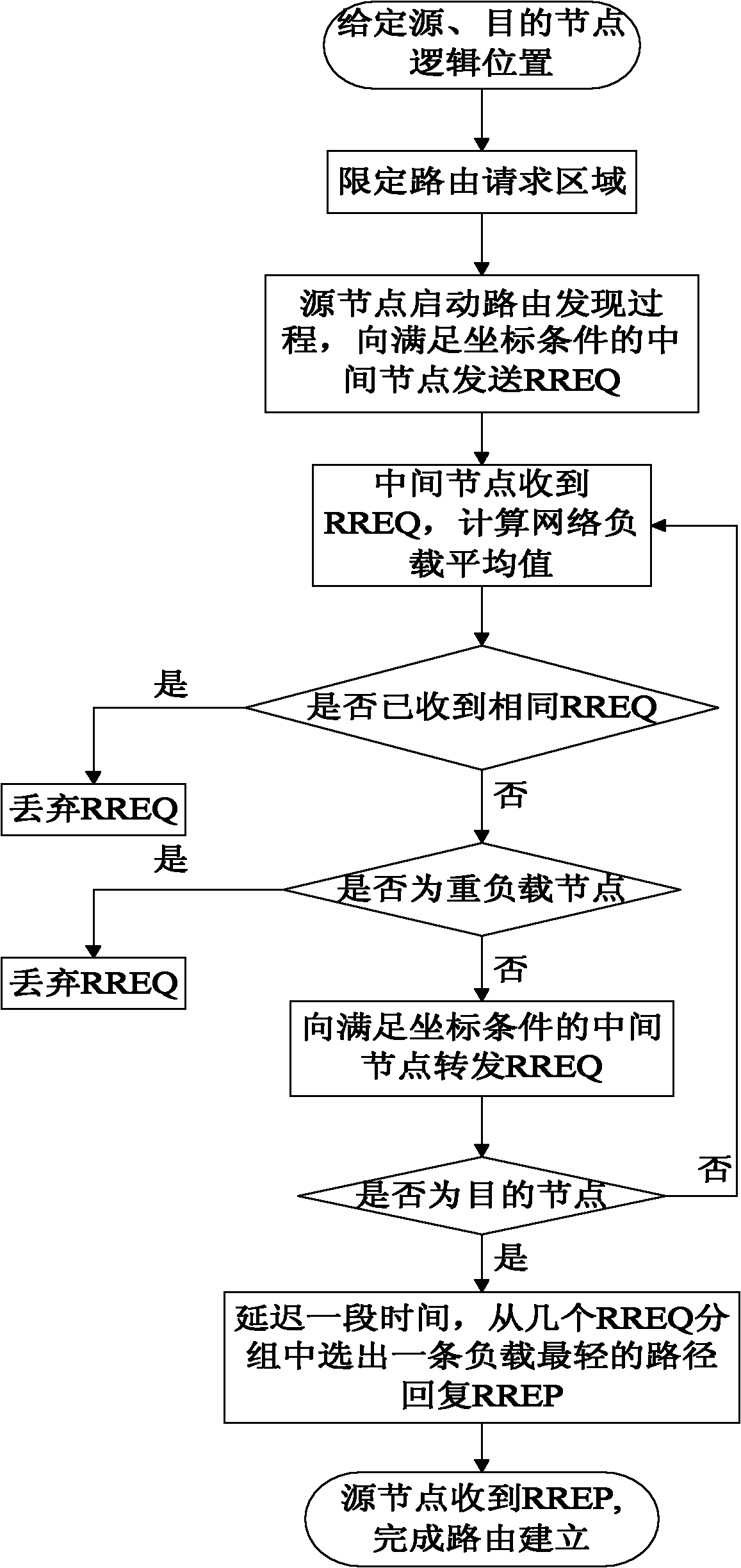
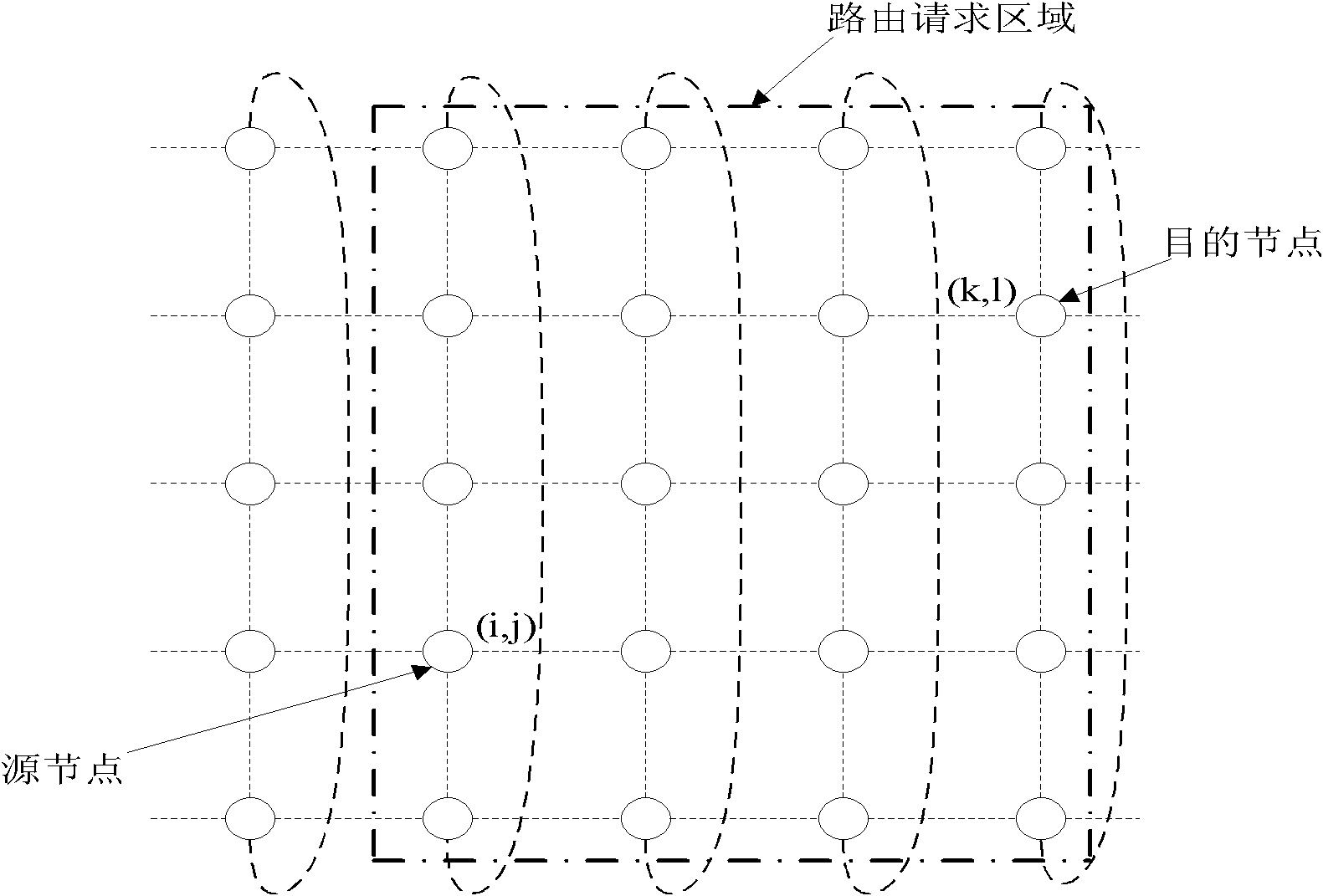
InactiveCN102231896ALimit broadcast rangeReduce overheadNetwork traffic/resource managementNetwork topologiesTraffic capacityDelayed response
The invention discloses a load-balance-based satellite network on-demand routing method, which mainly solve the problem of unbalanced traffic load in the conventional satellite network. The load-balance-based satellite network on-demand routing method comprises the following steps that: when a source node sends data, the minimum rectangular region of a routing request is limited according to orientations of the source node and a target node; the source node sends a routing request (RREQ) packet to an intermediate node in the minimum rectangular region; when receiving the RREQ packet for the first time, the intermediate node starts a node load judgment mechanism and selectively forwards the RREQ packet according to a judgment result; when the intermediate node forwards the RREQ packet, theRREQ packet is forwarded to a node with the consistent direction with the target node; the target node replies a routing response (RREP) packet to a route with the minimum load value from the received RREQ packet in a delayed response mode; and after receiving the RREP packet, the source node starts to send data so as to complete the route discovery process. Compared with a method employing the conventional routing protocol, the load-balance-based satellite network on-demand routing method has the advantages that: the accurate traffic load balance of the satellite network can be realized; andthe cost of a network route is reduced.
Owner:XIDIAN UNIV
Spatio-temporal clustering method for compressive data gathering
InactiveCN105682171AEffective calculationReduce the number of transfersNetwork topologiesData switching networksNODALBalancing network
The invention discloses a spatio-temporal clustering method for compressive data gathering. The spatio-temporal clustering method comprises the steps of: 1, an initialization stage; 2, spatio-temporal correlation measurement; 3, network clustering; 4, compressive data gathering; 5, data reconstruction. In the network clustering step, aggregation nodes obtain clustering information according to a calculated value of spatio-temporal correlation and broadcast the information to the whole network, and intra-cluster nodes select cluster head nodes dynamically. By adopting the steps, the spatio-temporal clustering method for compressive data gathering reduces data transmission times under the condition of same reconfiguration error, balances network energy consumption, prevents a certain node from dying too early due to energy consumption, and prolongs network lifetime.
Owner:BEIHANG UNIV
Access method of remote data
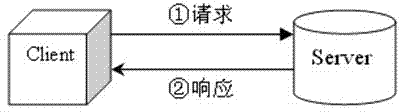
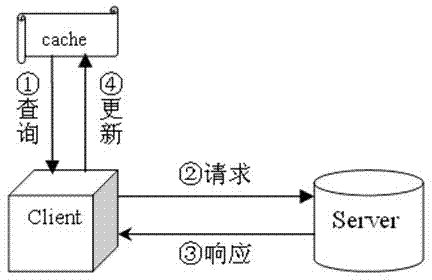
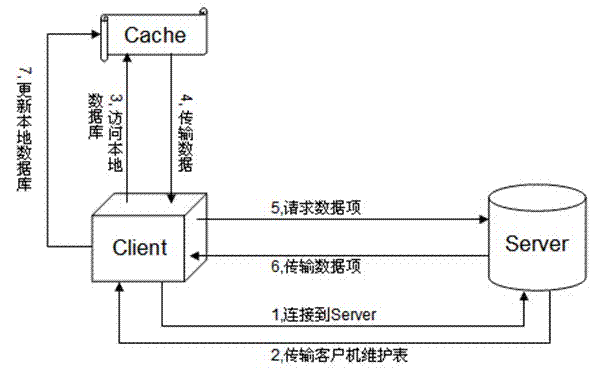
InactiveCN102521252AImprove access efficiencyReduce the number of transfersSpecial data processing applicationsAccess methodData access
The invention relates to the field of data transmission, and discloses an access method of remote data. The access method concretely comprises the following steps of: step 1, establishing one data base which is called as a local caching data base on a magnetic disk at a client side; step 2, connecting the client side to a server, inquiring the client side maintenance list of the client side in the data base of the server, and updating the local caching data base of the client side according to the content of the client side maintenance list; and step 3, when the client side needs to access one data item of the data base, firstly, inquiring the local caching data base, and then requesting the data item towards the server if the data item does not exist in the local caching data base. The active propelling is carried out by utilizing local caching and data updating; the access of most network data is localized; furthermore, the local data item is only updated when the local data item is necessary to be updated; the transmission times and the total transmission flow rate of the remote data are reduced; and the access efficiency of the data is improved.
Owner:SICHUAN CHANGHONG ELECTRIC CO LTD
Folding skateboard bag
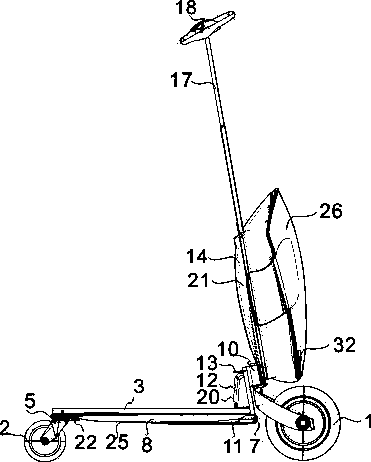
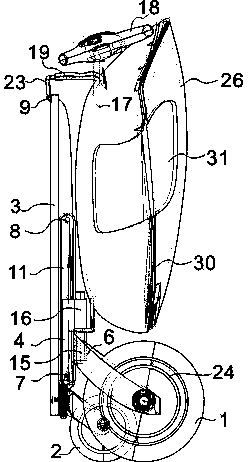
InactiveCN103507895ASeamless connectionSmall size when foldedLuggageFoldable cyclesElectric machineryStructural engineering
The invention discloses a folding skateboard bag which is a complementing type transportation tool, wherein the folding skateboard bag comprises a folding pedal, a case, rolling wheels, a guide mechanism, a brake system, a motor, a battery and a motor control system. The folding skateboard bag integrates portability, passing ability and economy, the case is designed into a commuting tool which is low in weight, high in strength, and capable of being folded easily, being carried indoors and into other transportation tools, the seamless combination of individual slow traffic, public transport and a destination is achieved, a user can go out flexibly, and the problem of a last mile is solved.
Owner:罗轶
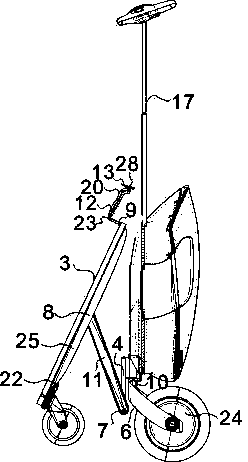
Hinged folding scooter bag
InactiveCN103661731AImprove travel experienceEfficient use ofLuggageFoldable cyclesControl systemSlide plate
The invention discloses a hinged folding scooter bag comprising a folding footboard, a bag body, wheels, a guide mechanism, a brake system, a motor, a battery, and a motor control system. The hinged folding scooter bag is portable, trafficable and comfort for driving, can be ridden, pulled or carried, can be carried in other vehicles or indoors, allows start and destination to be linked seamlessly, is a novel complementary vehicle, helps improve experience of travel by bus, allows subways and rapid transit systems to be more conveniently utilized, provides less frequent vehicle transferring, and makes time of going shorter, so that traffic jam is alleviated and greenhouse gas emission is reduced. The hinged folding scooter bag can be quickly folded with one hand at one step and is flexible to steer. The battery in the hinged folding scooter bag is used as a mobile power source. The volume of the hinged folding scooter bag can be varied according to travel needs.
Owner:罗轶
Label information transmission method and device
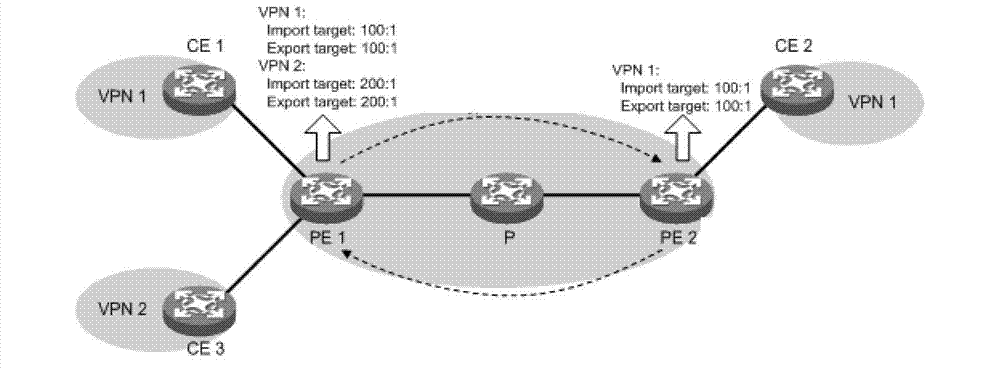
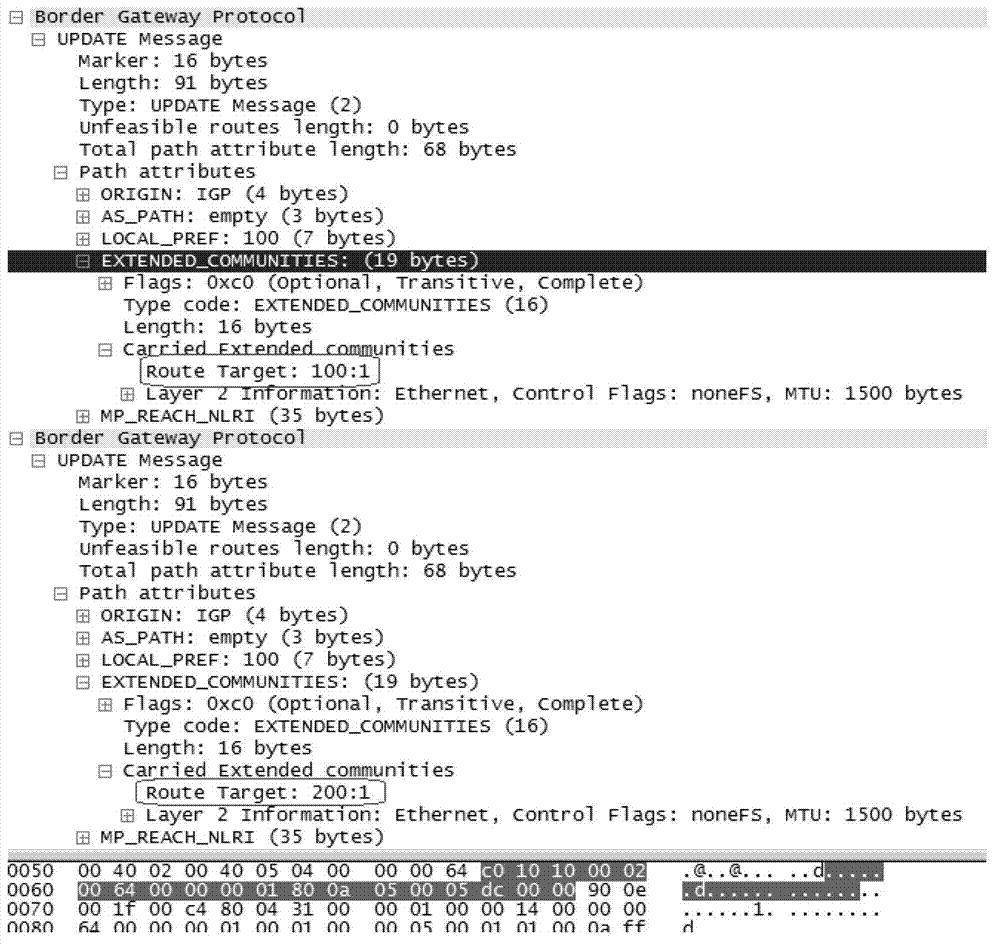
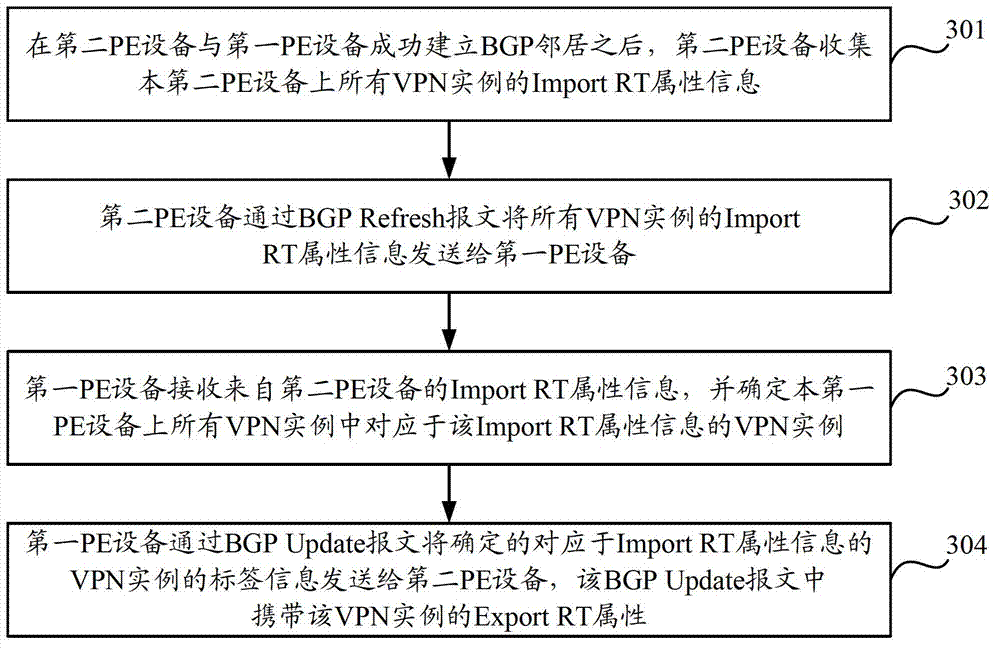
ActiveCN103209125AReduce the number of transfersAvoid transmissionData switching networksBorder Gateway ProtocolInformation transmission
The invention discloses a label information transmission method and device. The label information transmission method includes that a first PE (Provider Edge) device receives Import RT (Route Target) attribute information from a second PE device; the first PE device confirms VPN (Virtual Private Network) cases which are corresponding to the Import RT attribute information in all VPN cases; and the first PE device sends label information of the VPN cases which are corresponding to the Import RT attribute information to the second PE device through a BGP (Border Gateway Protocol) Update message. The label information transmission method and system has the advantages of avoiding transmitting unnecessary BGP Update messages and reducing the transmission number of the BGP Update messages.
Owner:NEW H3C TECH CO LTD
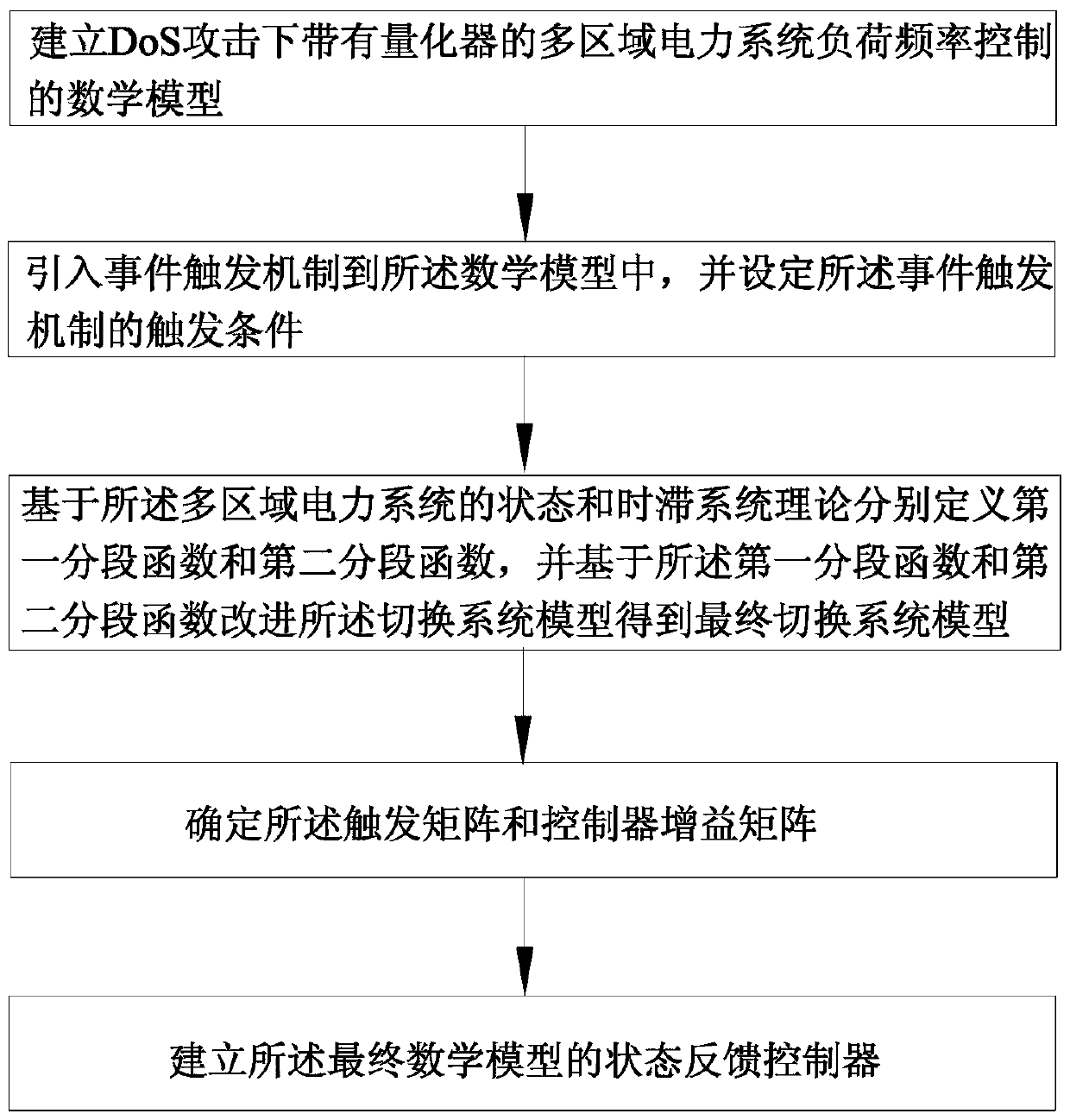
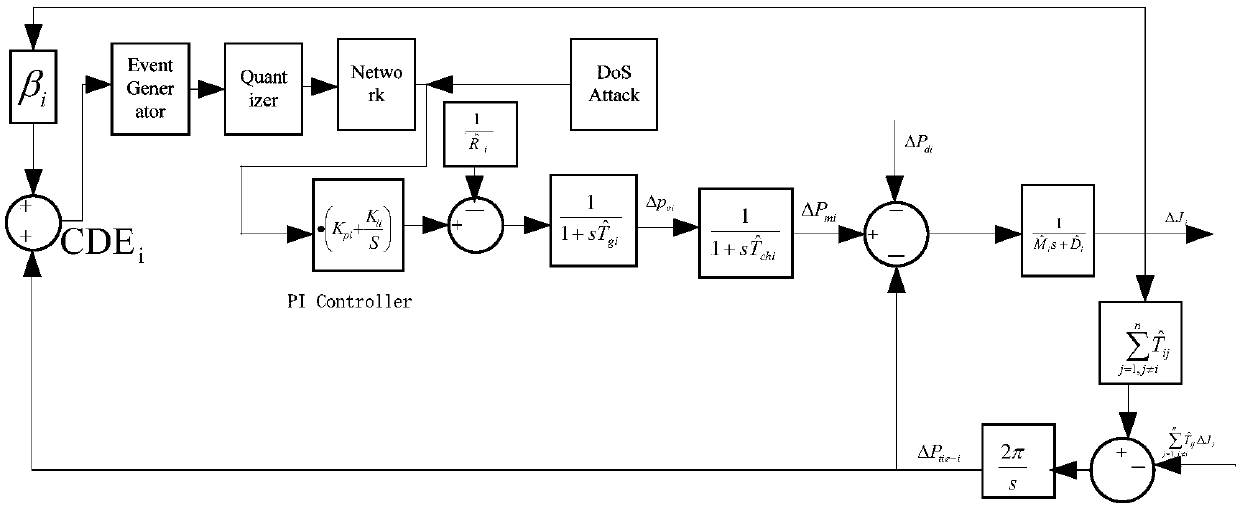
Load frequency quantification control method based on event trigger mechanism under DoS attacks
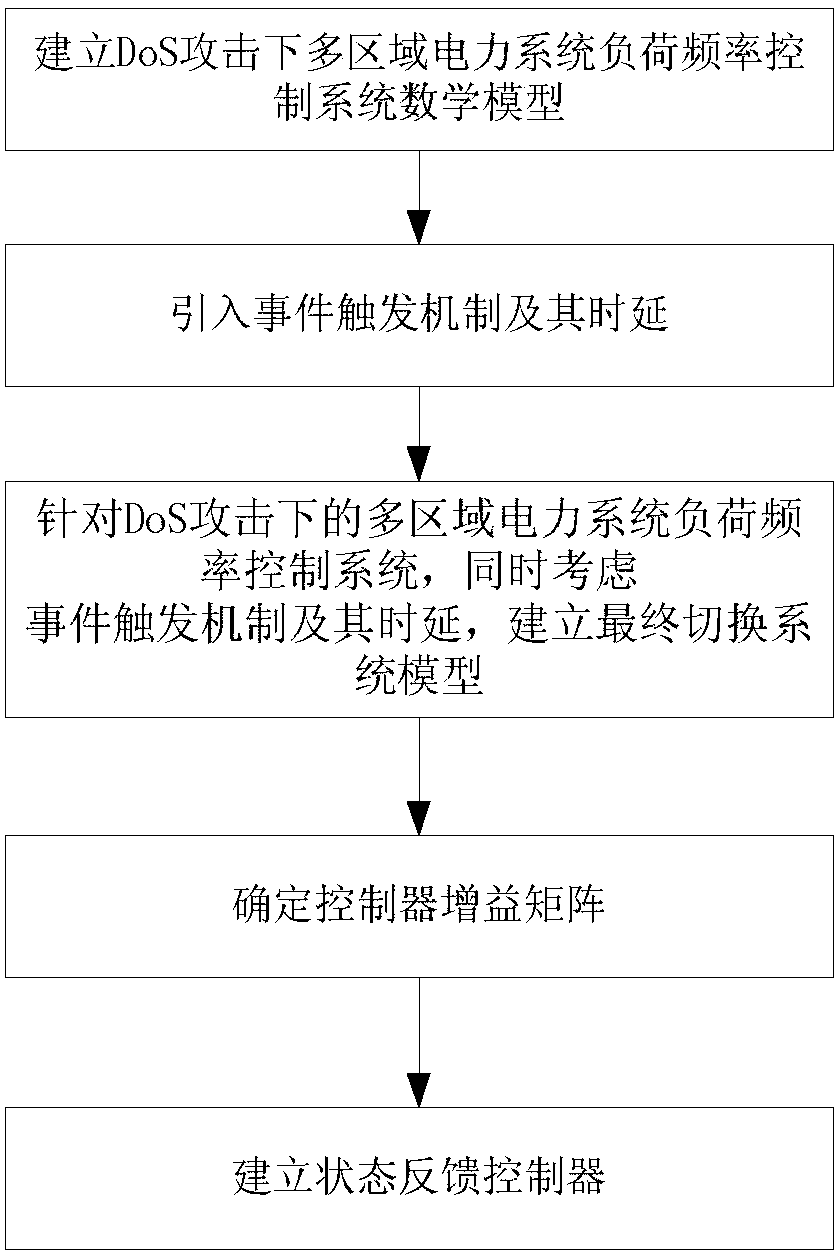
ActiveCN109672177AReduce sizeReduce the number of transfersAc network circuit arrangementsTime delaysElectric power system
The invention discloses a load frequency quantification control method based on an event trigger mechanism under DoS attacks, which is specifically applied to the load frequency quantification controlin a multi-region electric power system. The method comprises the following steps of: establishing a switching system model of load frequency control of the multi-region electric power system with aquantification device under the DoS attacks; introducing the event trigger mechanism into the switching system model and setting trigger conditions of the event trigger mechanism; defining a first segment function and a second segment function based on the state of the multi-region electric power system and a time delay system theory respectively; improving the switching system model based on thefirst segment function and the second segment function to obtain a final switching system model; determining a trigger matrix and a controller gain matrix; establishing a state feedback controller ofthe final switching system model. According to the method provided by the invention, stable and safe operation of a load frequency control system of the multi-region electric power system is ensured;meanwhile, network bandwidth resources occupied in a communication process and needed energy sources can be reduced.
Owner:NANJING UNIV OF POSTS & TELECOMM
Terminal and access point finding method for communicating with stealth access point
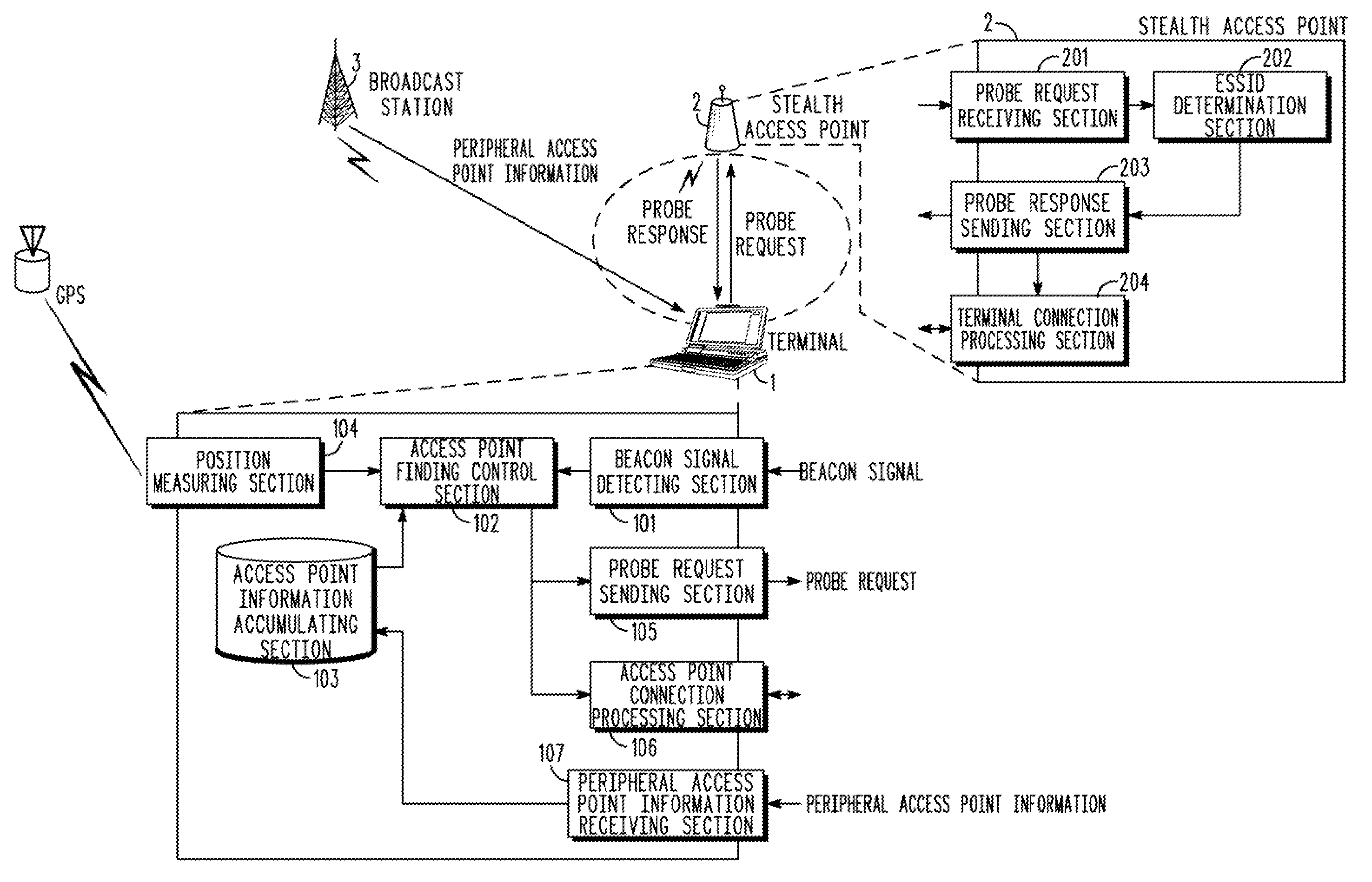
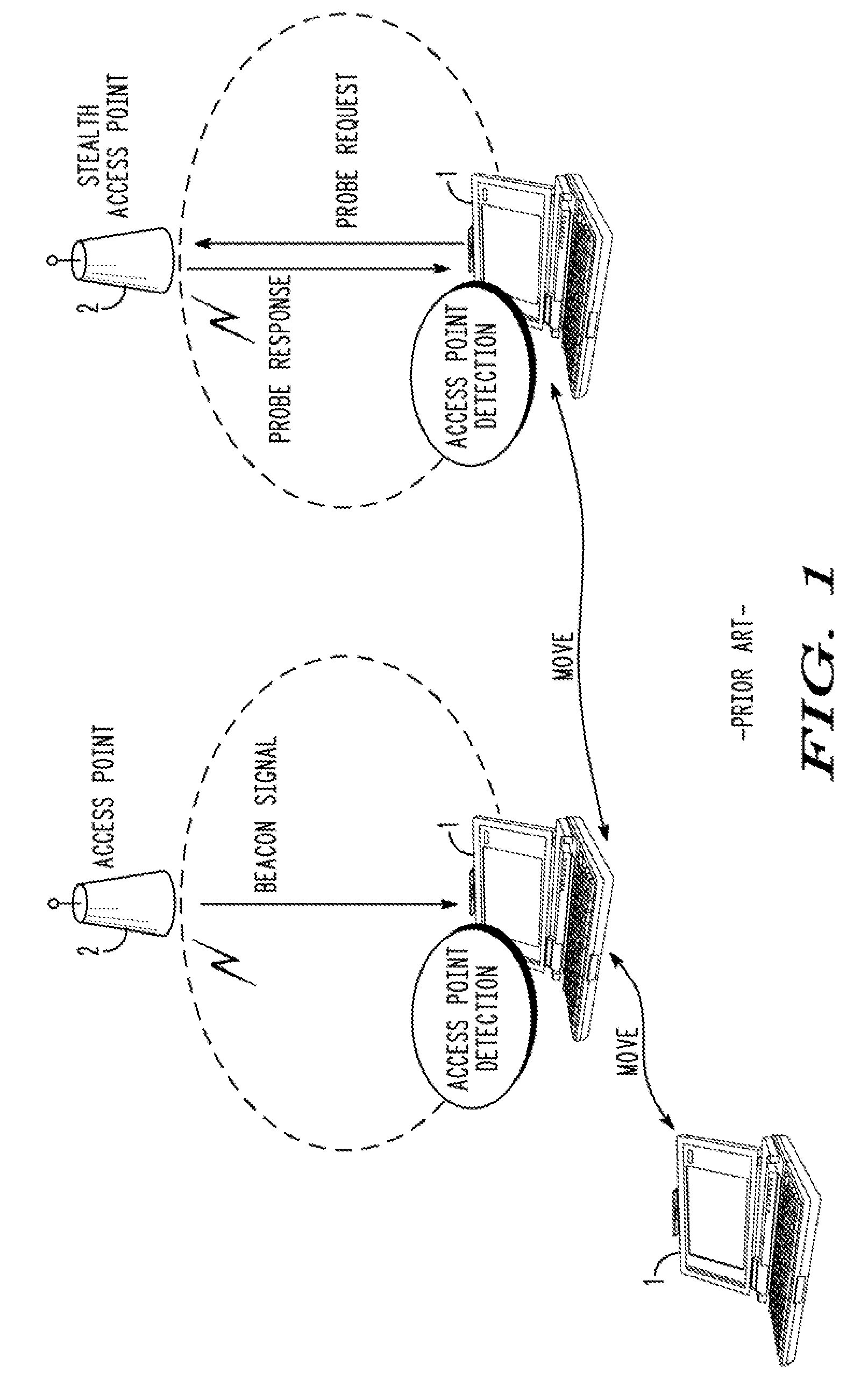
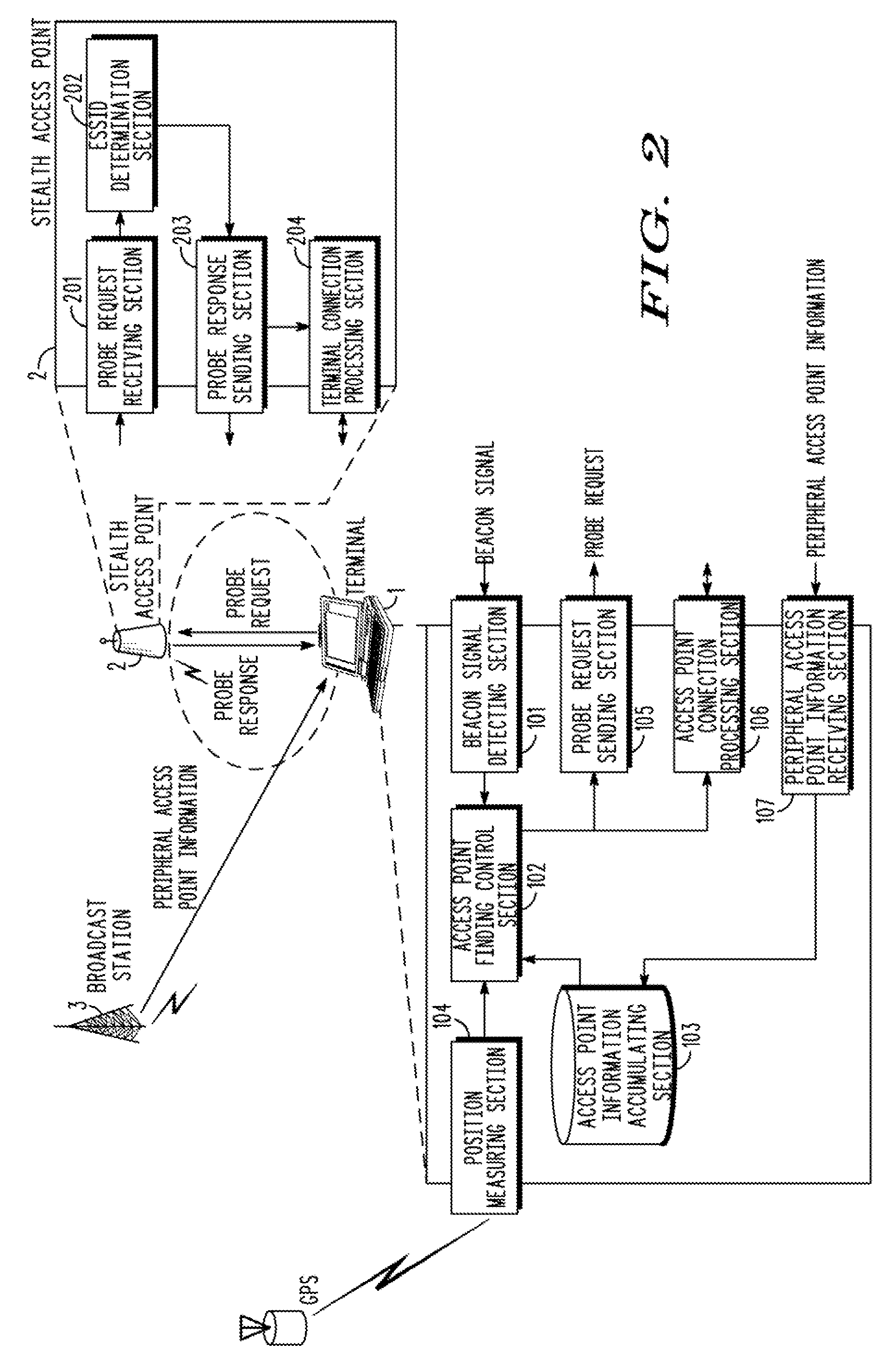
InactiveUS20090049519A1Reduce the number of transfersNetwork can be reducedAssess restrictionDigital data processing detailsFindings methodsBeacon
There is provided a terminal that is capable of not sending a useless probe request to detect a stealth access point. The terminal communicates with a normal access point that reports a network identifier and a stealth access point that does not report a network identifier. The terminal includes an access point information accumulating section 103 for accumulating access point information that indicates whether each access point is a normal access point or a stealth access point, a beacon signal detecting section 101 for listening for and detecting a beacon signal, a probe request sending section 105 for sending a probe request, and an access point finding control section 102 for controlling the beacon signal detecting section 101 to detect the beacon signal with respect to the normal access point, and controlling the probe request sending section 105 to send the probe request with respect to the stealth access point.
Owner:KDDI CORP +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com