Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
460 results about "Network clustering" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
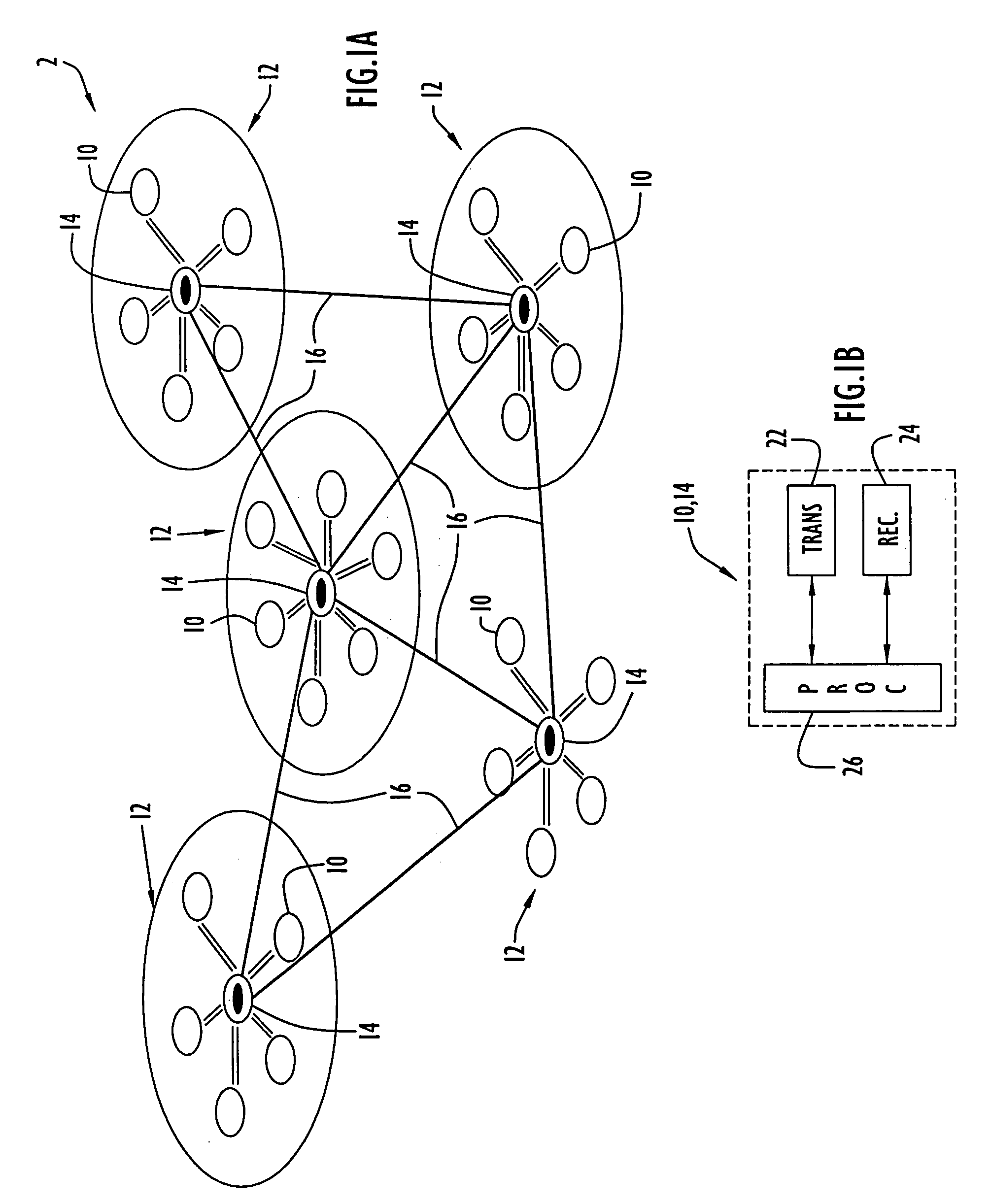
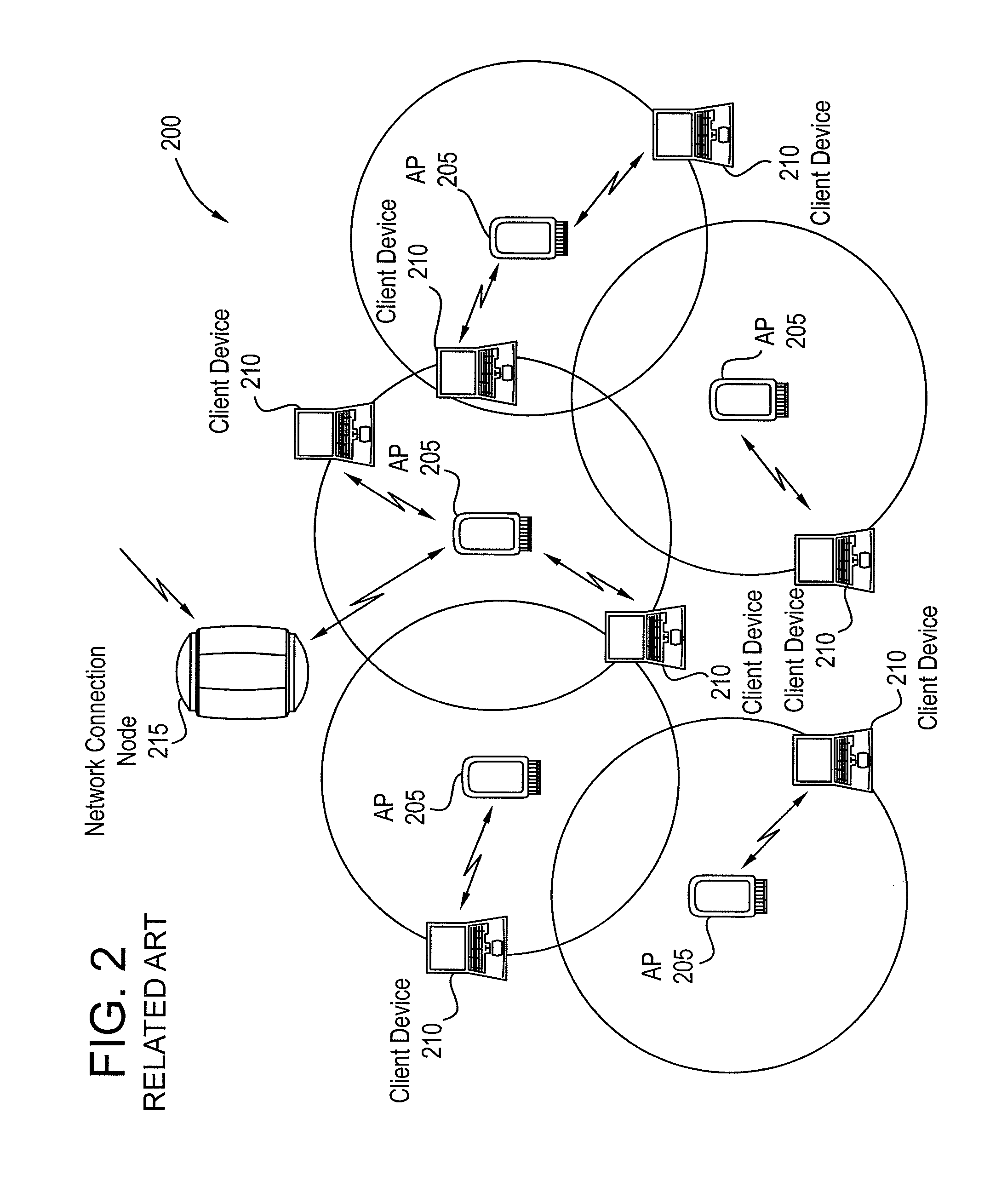
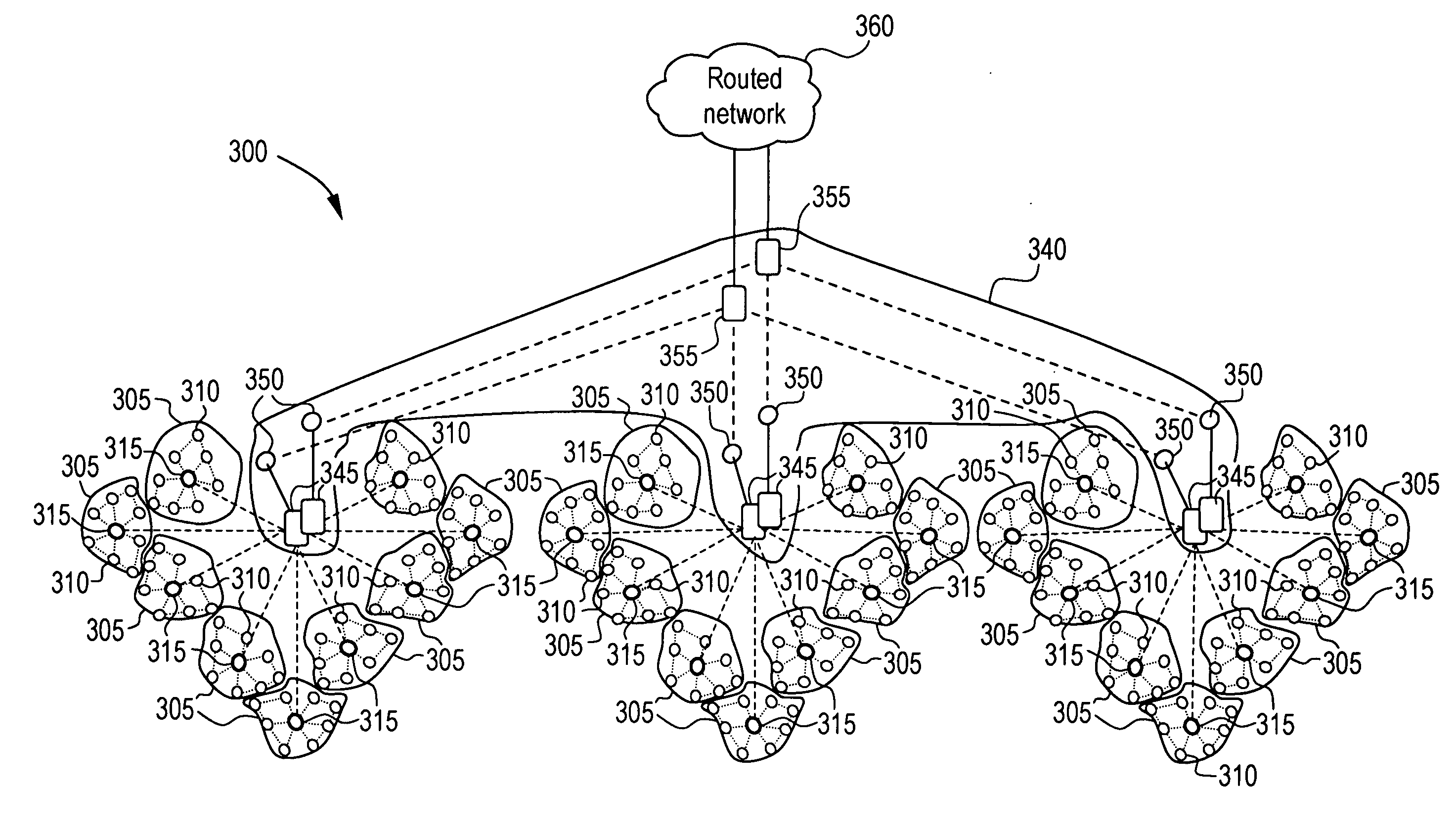
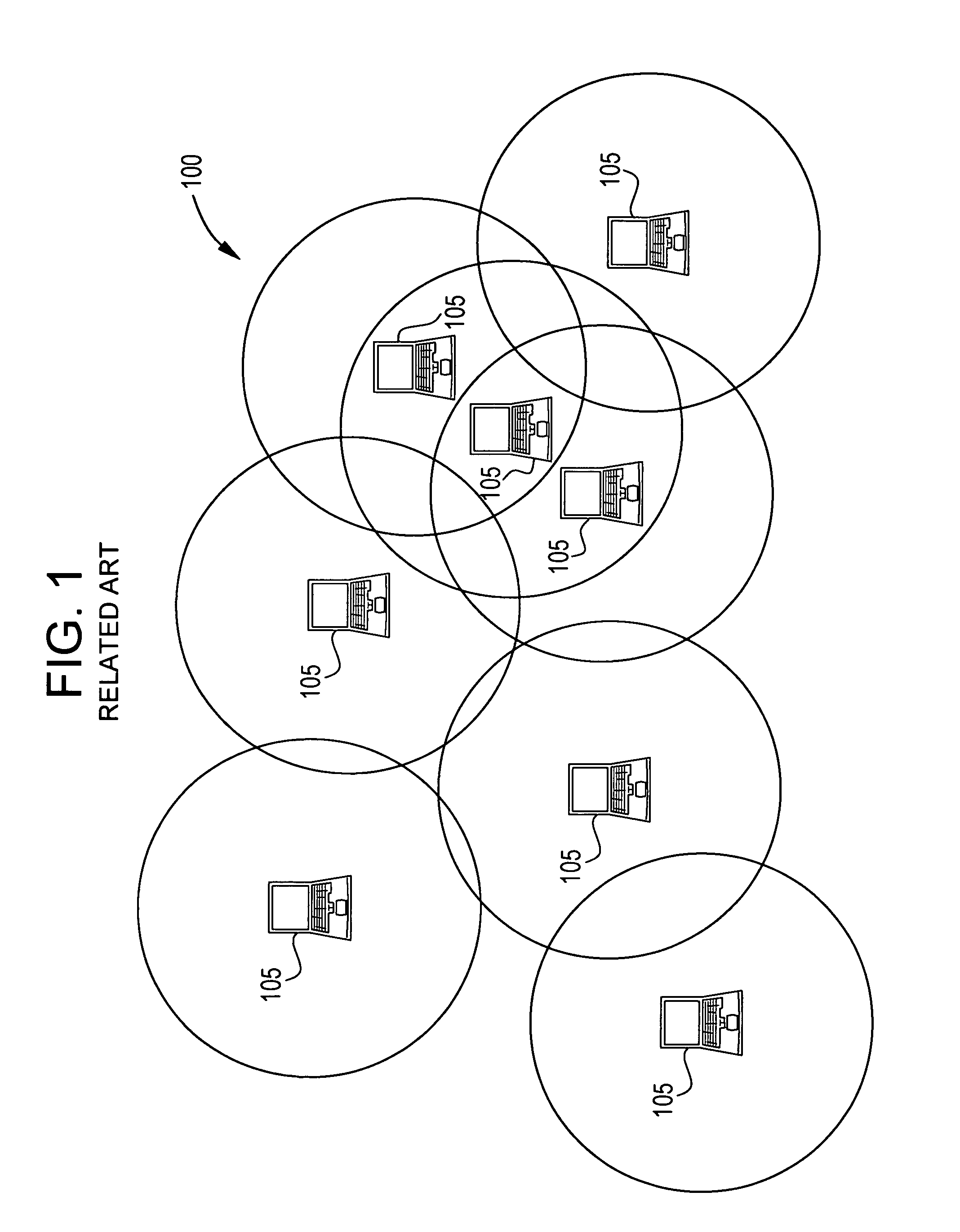
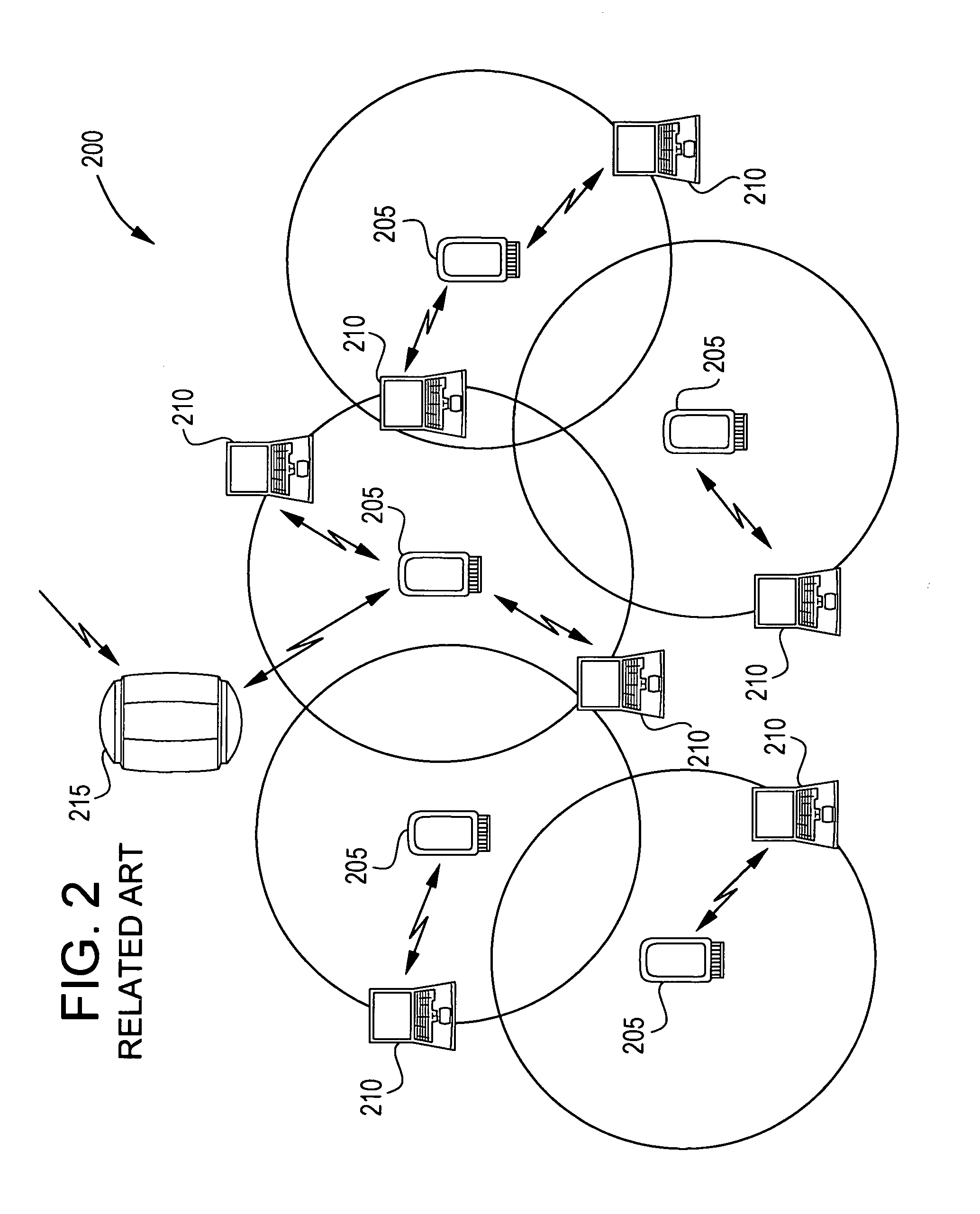
A cluster network is two or more computing devices working together for a common computing purpose. These networks take advantage of the parallel processing power of the computing devices.
Apparatus and methods for real-time multimedia network traffic management & control in wireless networks
InactiveUS20100318652A1Facilitate real-time network managementEasy to manufactureMultiple digital computer combinationsTransmissionReal-time webNetwork management
The invention is directed to network management systems and methods that provide substantially real-time network management and control capabilities of multimedia streaming traffic in telecommunications networks. The invention provides pre-emptive and autonomous network management and control capabilities, and may include shared intelligence of embedded systems—Heterogeneous Sensor Entities (HSE) and the Sensor Service Management (SSM) system. HSEs are distributed real-time embedded systems provisioned in various network elements. HSEs performs fault, configuration, accounting, performance and security network management functions in real-time; and real-time network management control activations and removals. SSM facilitates automated decision making, rapid deployment of HSEs and real-time provisioning of network management and control services. The service communication framework amongst various HSEs and the SSM is provided by the Heterogeneous Service Creation system. The proposed network management procedure provides real-time network management and control capabilities of multimedia traffic in wireless networks and clusters of independent networks respectively.
Owner:KENT STATE UNIV
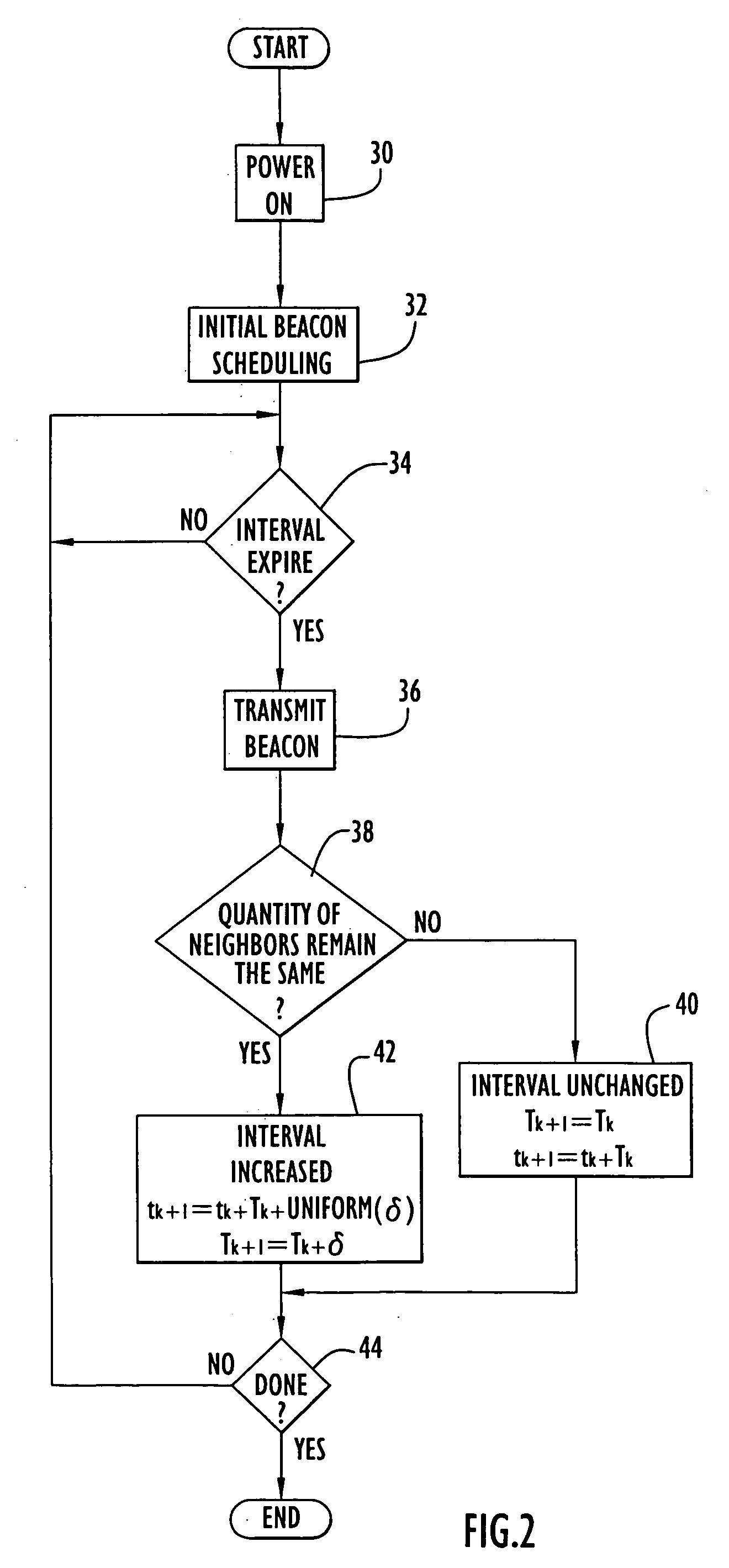
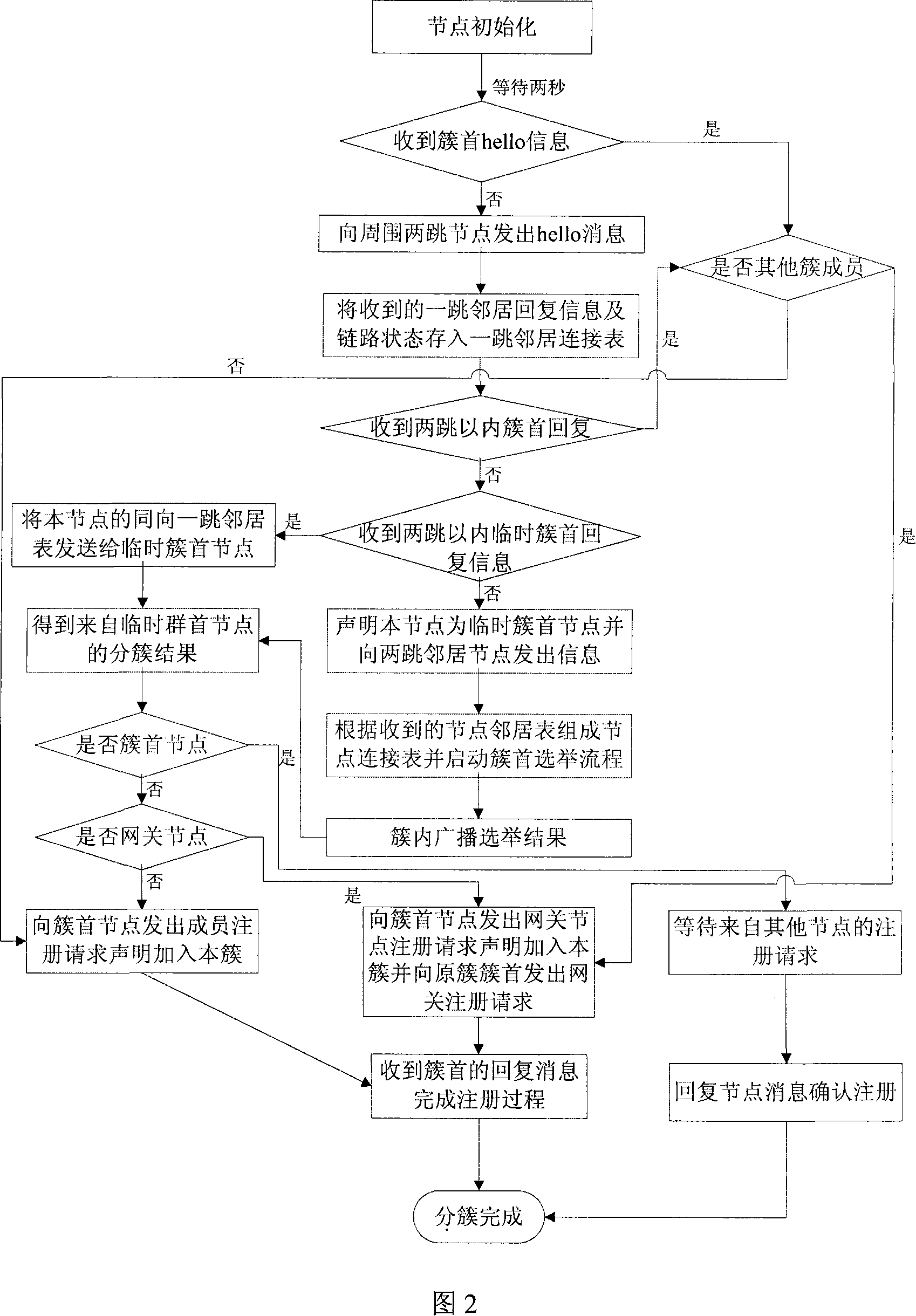
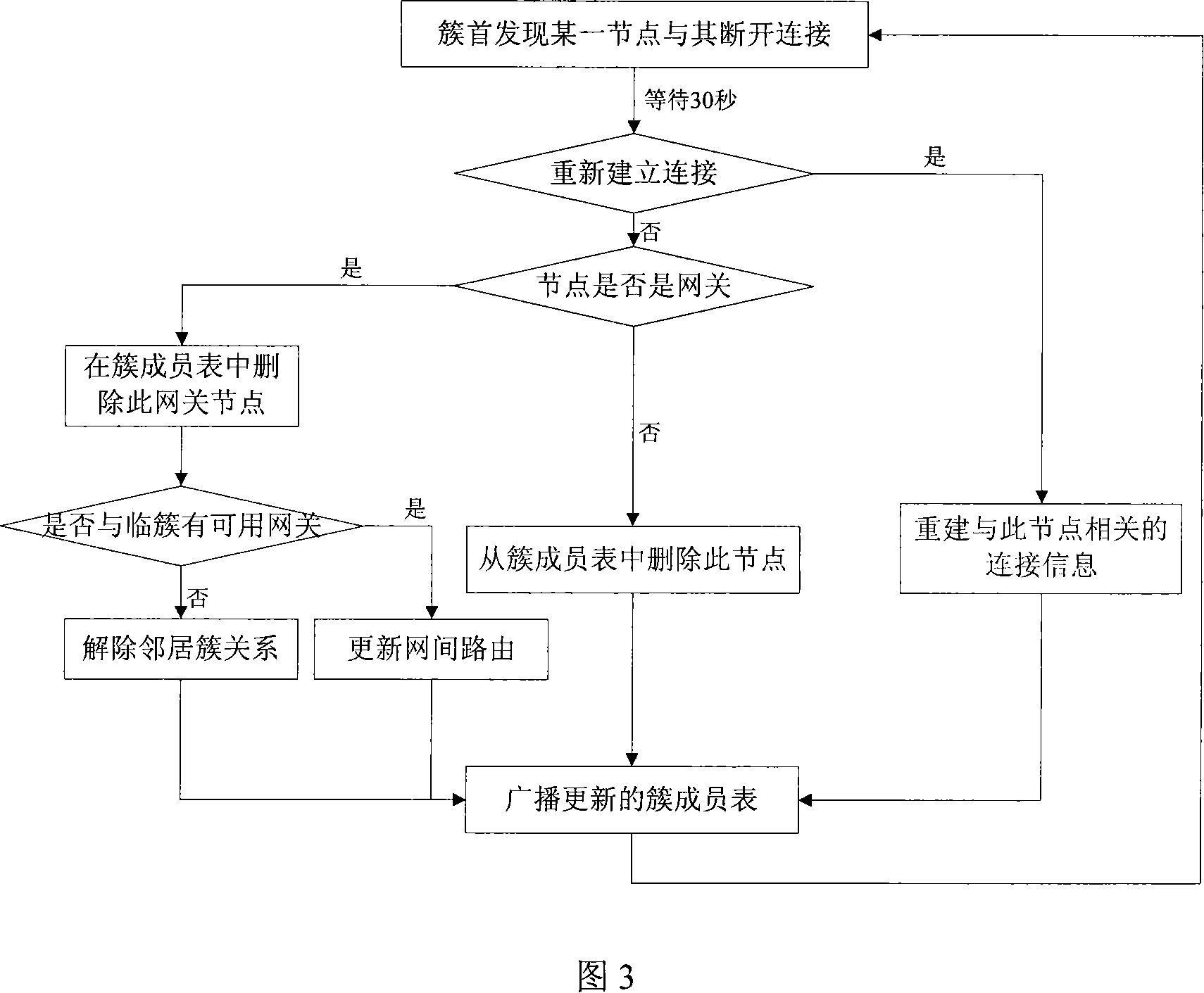
Method and apparatus for communication network cluster formation and transmission of node link status messages with reduced protocol overhead traffic
InactiveUS6980537B1Facilitate cluster formationQuantity minimizationNetwork traffic/resource managementAssess restrictionNetwork sizeProtocol overhead
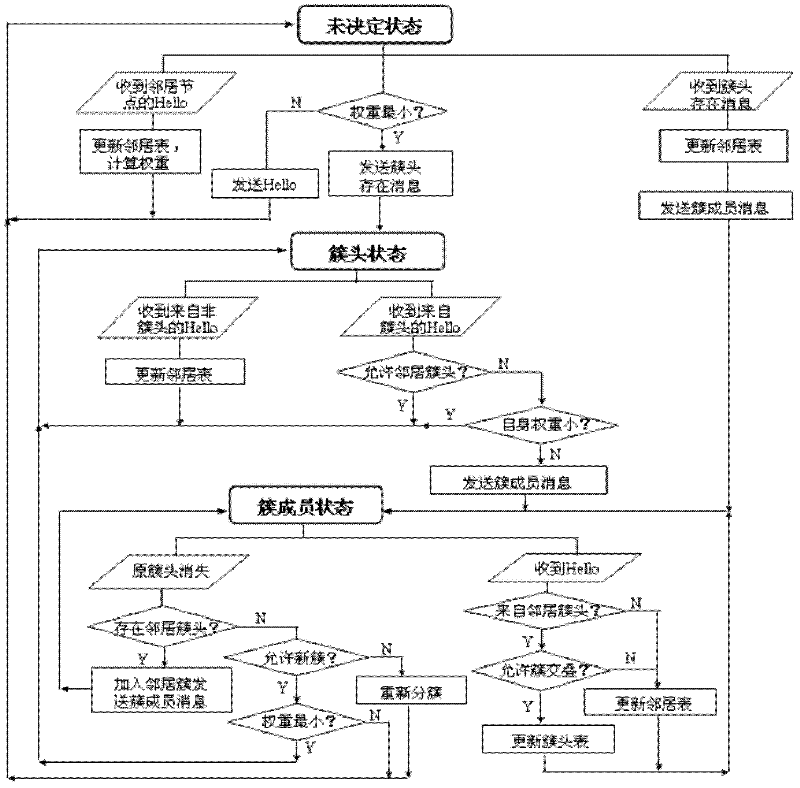
The present invention facilitates cluster formation within a communications network by utilizing network topology information to designate network nodes that are crucial for relaying traffic as cluster head nodes, while remaining network nodes are designated as member nodes. A beacon packet transmission rate of a network node or the interval between successive beacon packet transmissions by that node is adjusted by the present invention to facilitate cluster formation independent of network size and varying initial start times of network nodes. In addition, the present invention utilizes the above described cluster formation technique to form a three tier architecture for transmission or flooding of routing information from head node databases throughout the network. The cluster formation technique is applied to cluster head nodes to form an additional network tier of super nodes that distribute routing information, while cluster head nodes route network data traffic. The databases of cluster head nodes are examined subsequent to flooding of head node database information by super nodes, where data missing from a head node database is requested from a corresponding super node, thereby eliminating transmissions of acknowledgment messages.
Owner:STINGRAY IP SOLUTIONS LLC
System and method for enforcing network cluster proximity requirements using a proxy
InactiveUS20060233372A1Satisfies requirementLimit deliverySecret communicationTransmissionSystems approachesNetsniff-ng
A system, method and computer program for enforcing network cluster proximity requirements using a proxy is useful in preventing unauthorized devices from receiving encrypted broadcast content intended for only authorized users within a network cluster. The current art allows users to remotely establish trust via a cryptographic handshake. This results in encrypted broadcast content being delivered to unauthorized devices. The present invention assures that encrypted broadcast content is delivered to only authorized devices, allowing authorized remote devices to receive encrypted broadcast content while preventing unauthorized remote devices from doing so. The present invention enforces network proximity requirements to authorized devices within a defined area by timing the cryptographic handshaking, and by authorizing device proxies within a geographic area for retransmitting to authorized remote devices outside said geographic area.
Owner:IBM CORP
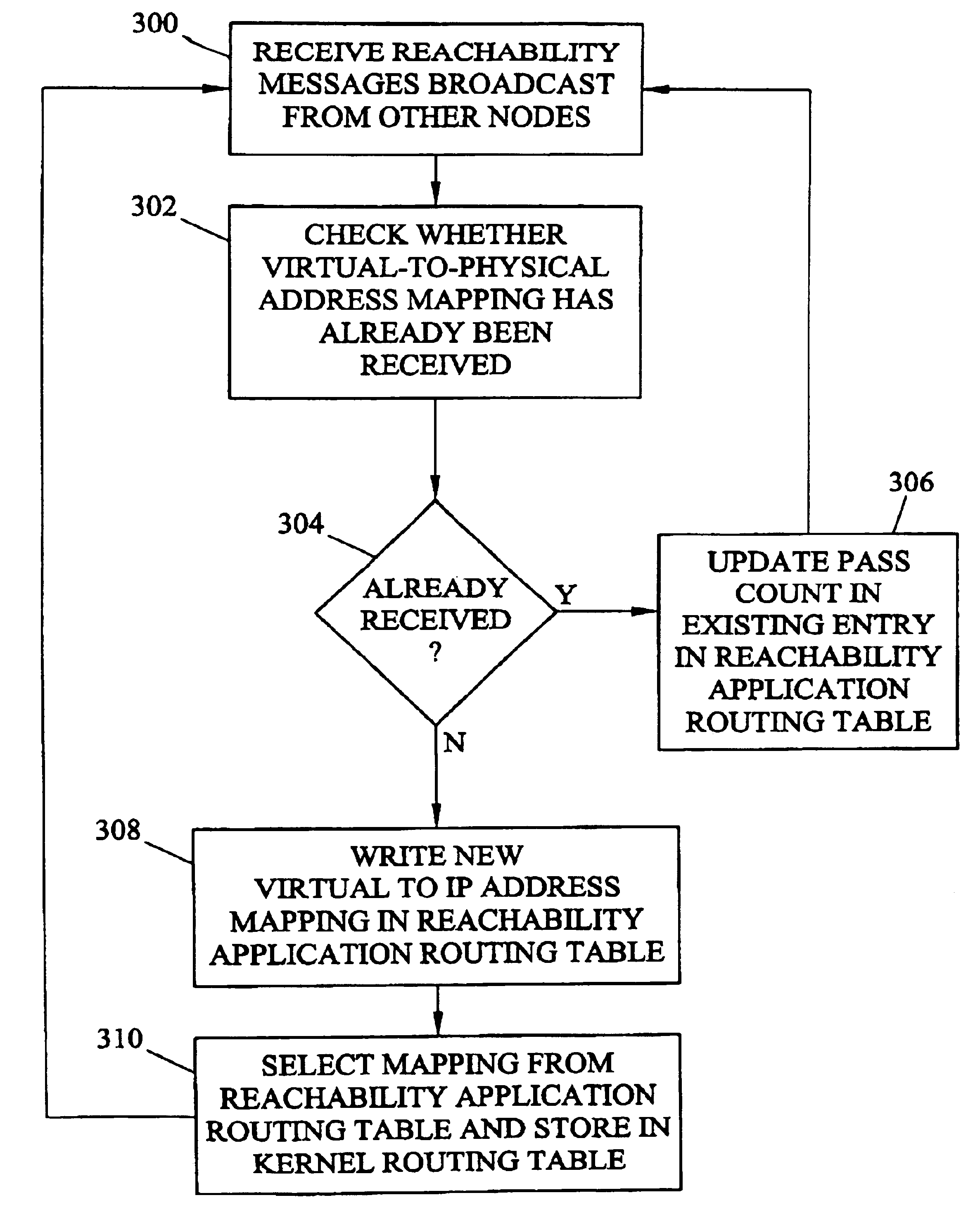
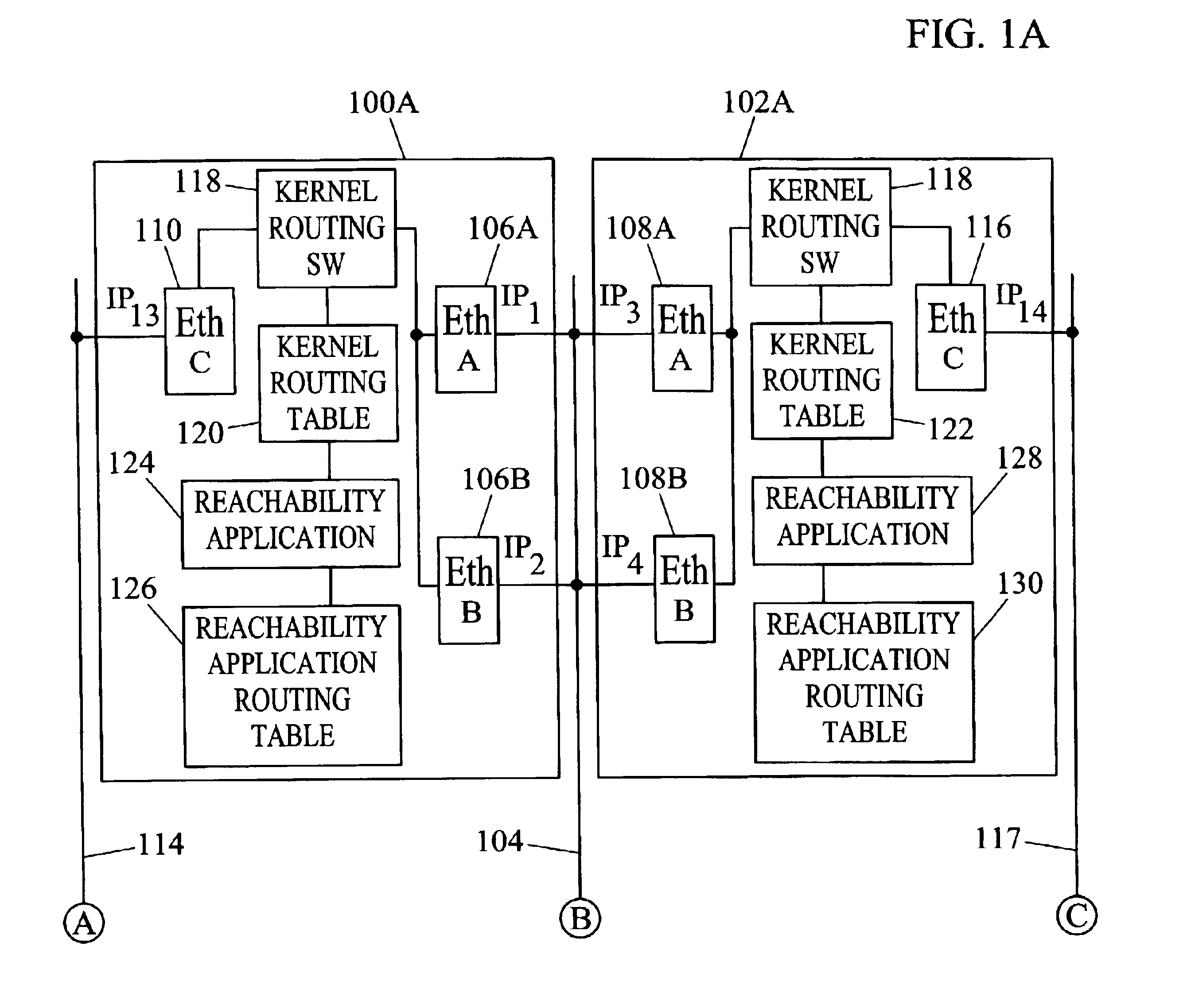
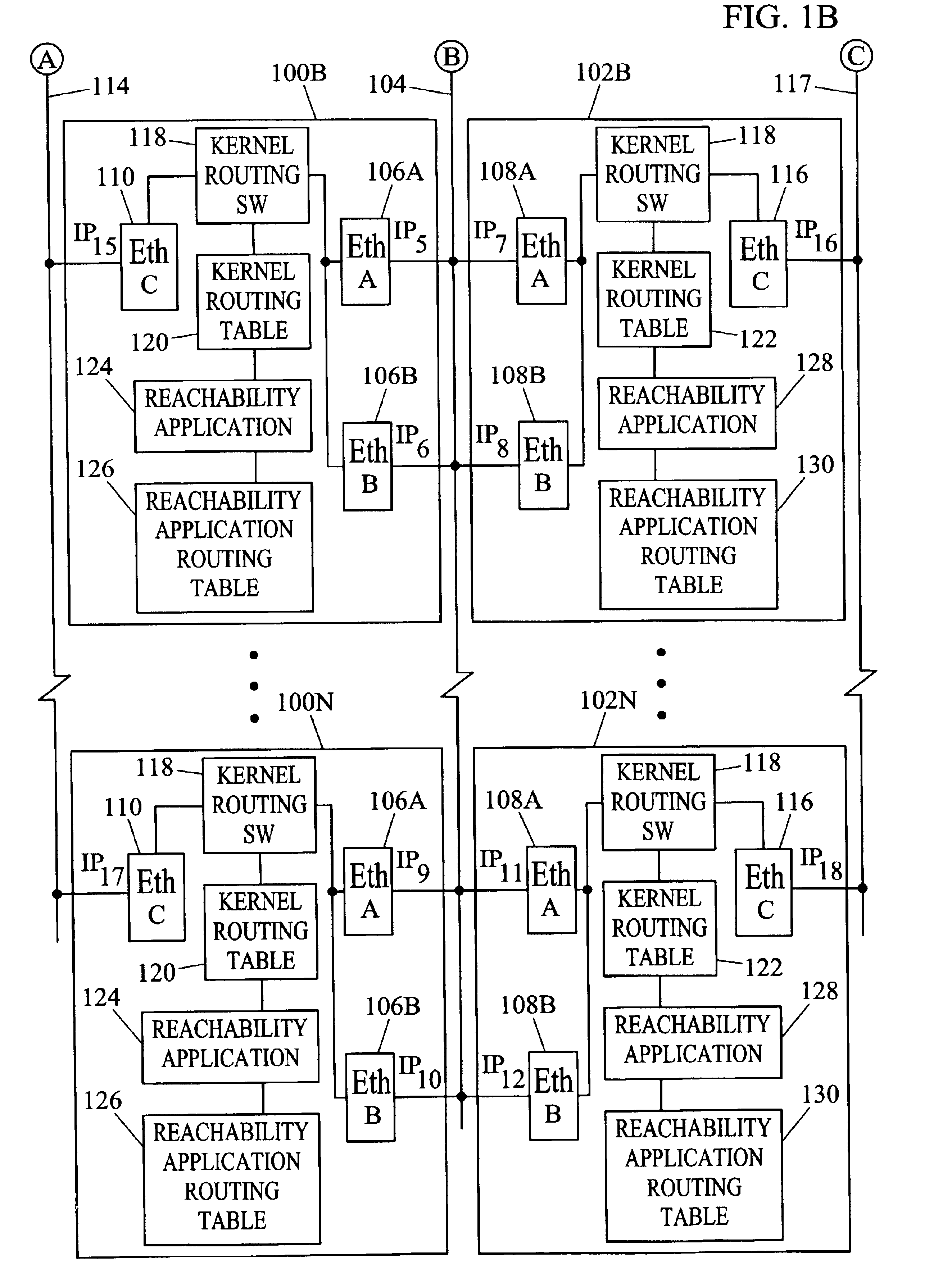
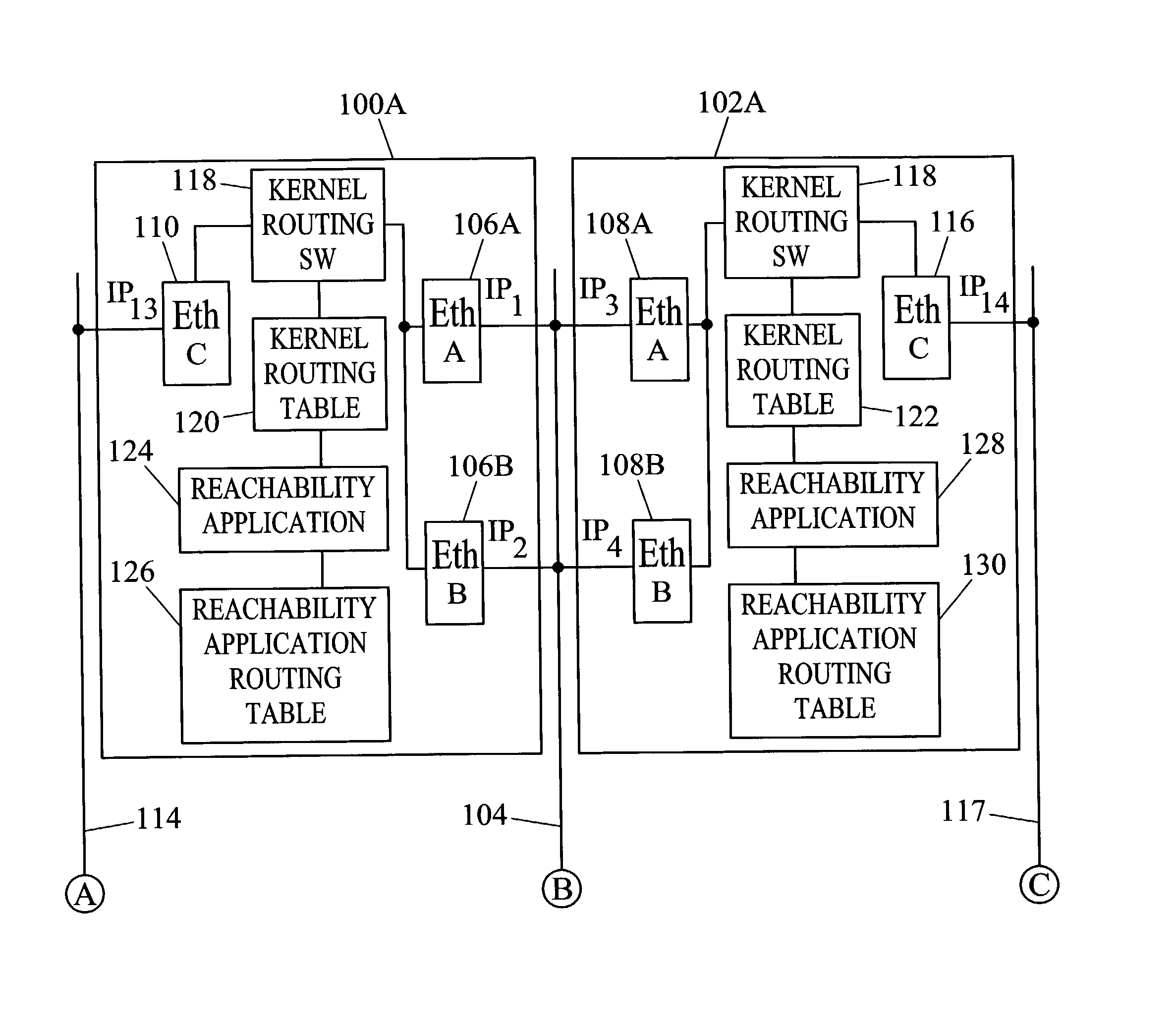
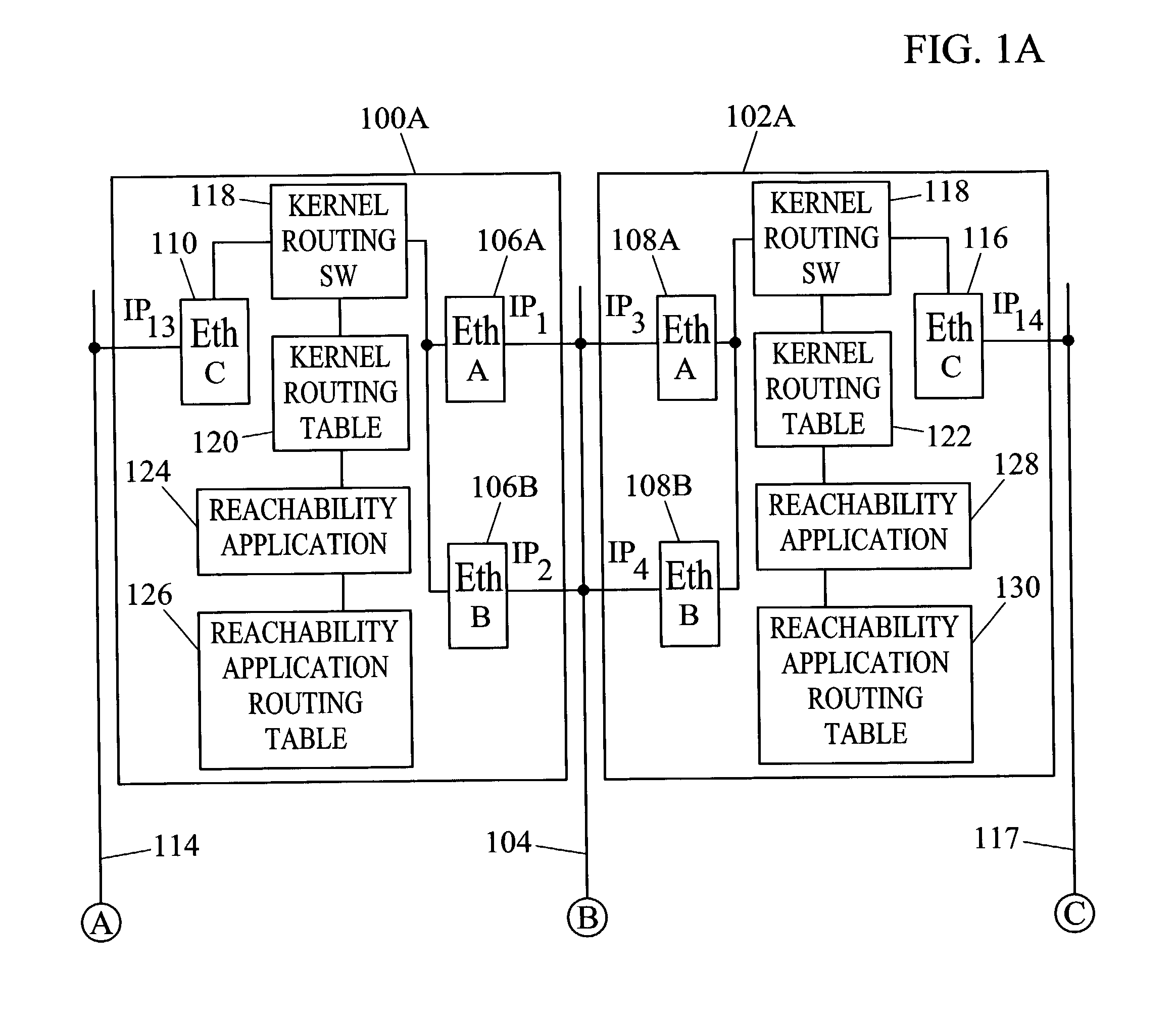
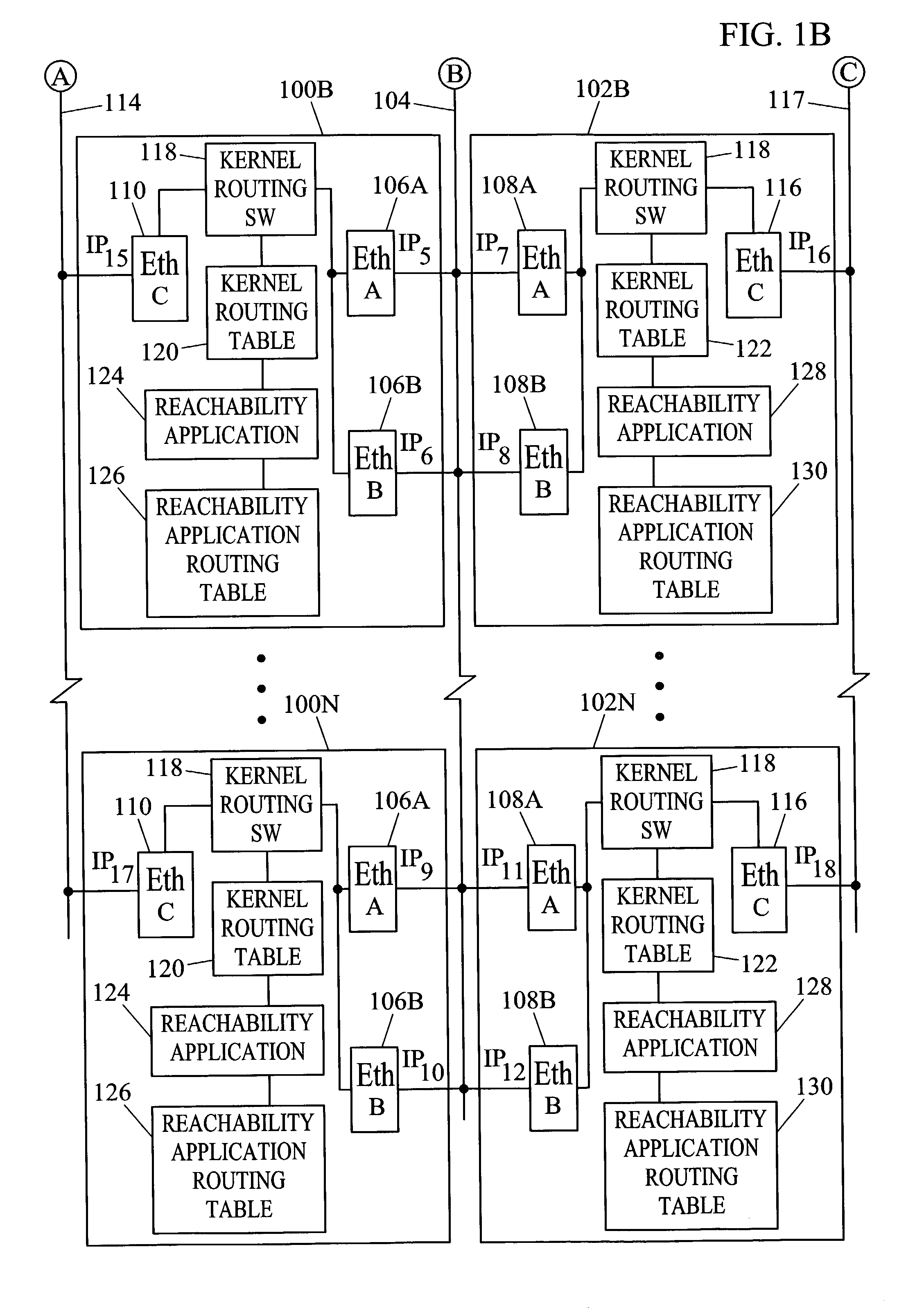
Methods and systems for exchanging reachability information and for switching traffic between redundant interfaces in a network cluster
InactiveUS6954794B2Shorten the timeQuick switchSpecial service provision for substationTime-division multiplexTraffic capacityRouting table
Owner:TEKELEC GLOBAL INC
Energy efficient wireless sensor network routing method
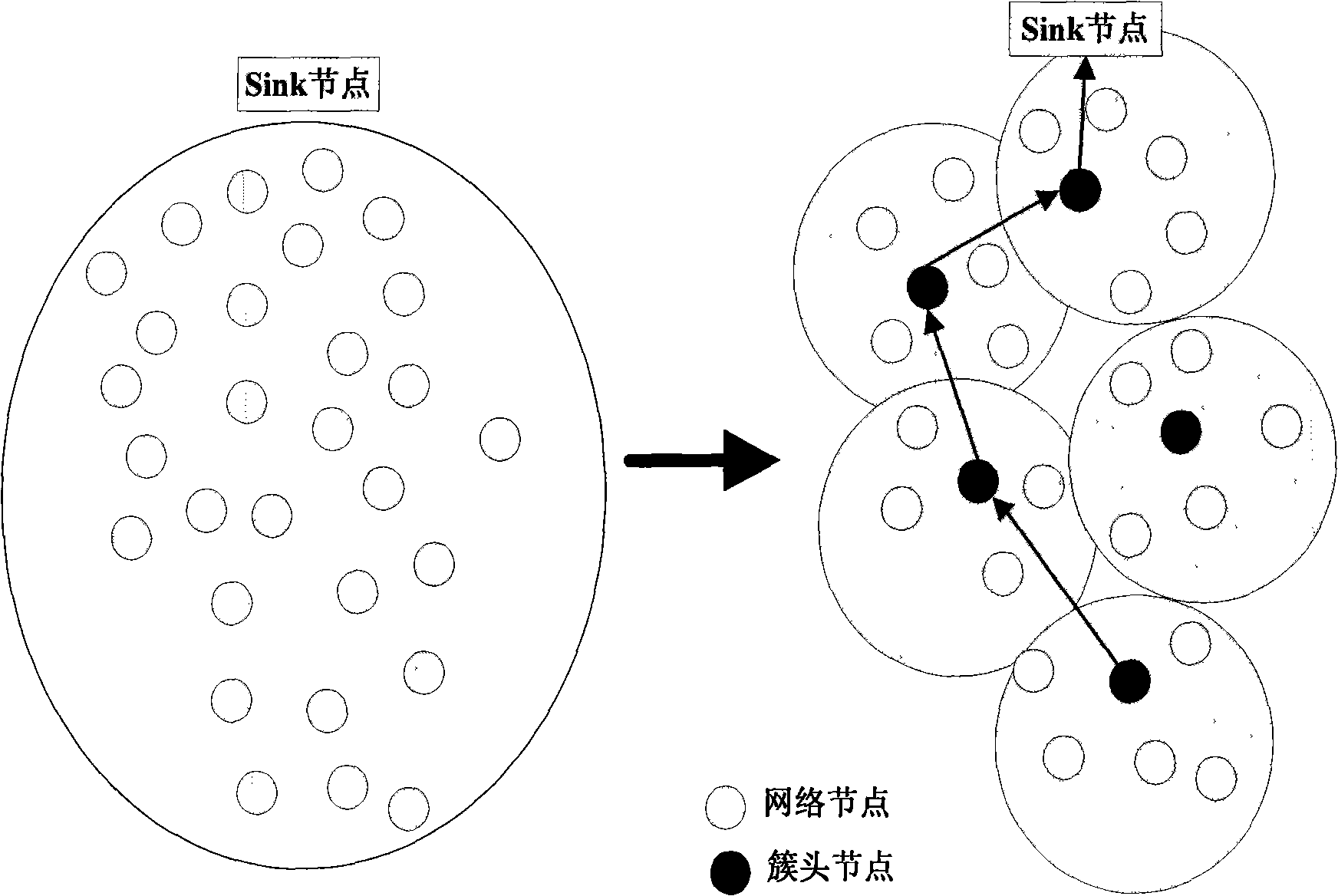
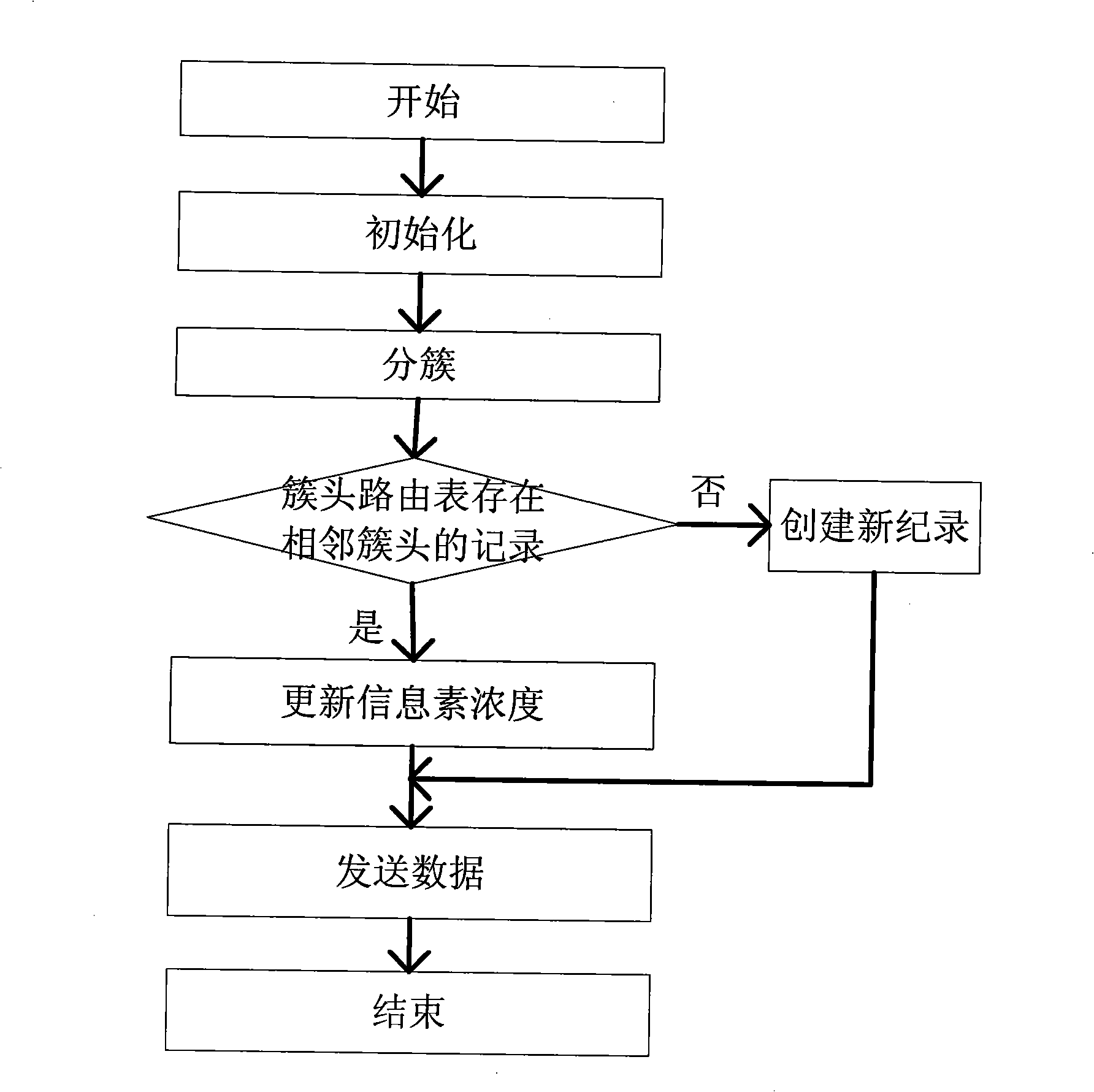
InactiveCN101360051AReduce energy consumptionBalance Energy ExpenditureEnergy efficient ICTData switching by path configurationTotal energyNetwork clustering
The invention discloses a routing method for the wireless sensor network with efficient energy, which is suitable for the layered sensor network structure. The routing method is composed of initialization, cluster building, adjacent clusters routing and routing maintenance, wherein, an initialization process of the protocol makes a Sink node obtain a topology and network average energy of the sensor network, and each node obtains hop counts from the node to the Sink node; in the stage of the cluster building, a repeated division method is used to divide sensor network clusters, the divided clusters are even, and a leader cluster node is undertaken by nodes with higher residual energy; the adjacent clusters routing uses an ant colony algorithm to determine the probability of using a link to send information according to the link pheromone concentration, and the link pheromone concentration is increased with the information transmission on the link and is reduced with the time going; and the routing maintenance stage is responsible for updating link pheromone concentration, and makes the nodes inside the cluster with higher residual energy undertake the leader cluster in turn. The routing method can reduce the consumption of the network total energy, can balance the consumption of the node energy and can prolong the network life cycle.
Owner:XIDIAN UNIV
High-efficiency controlling method of wireless sensor network topology
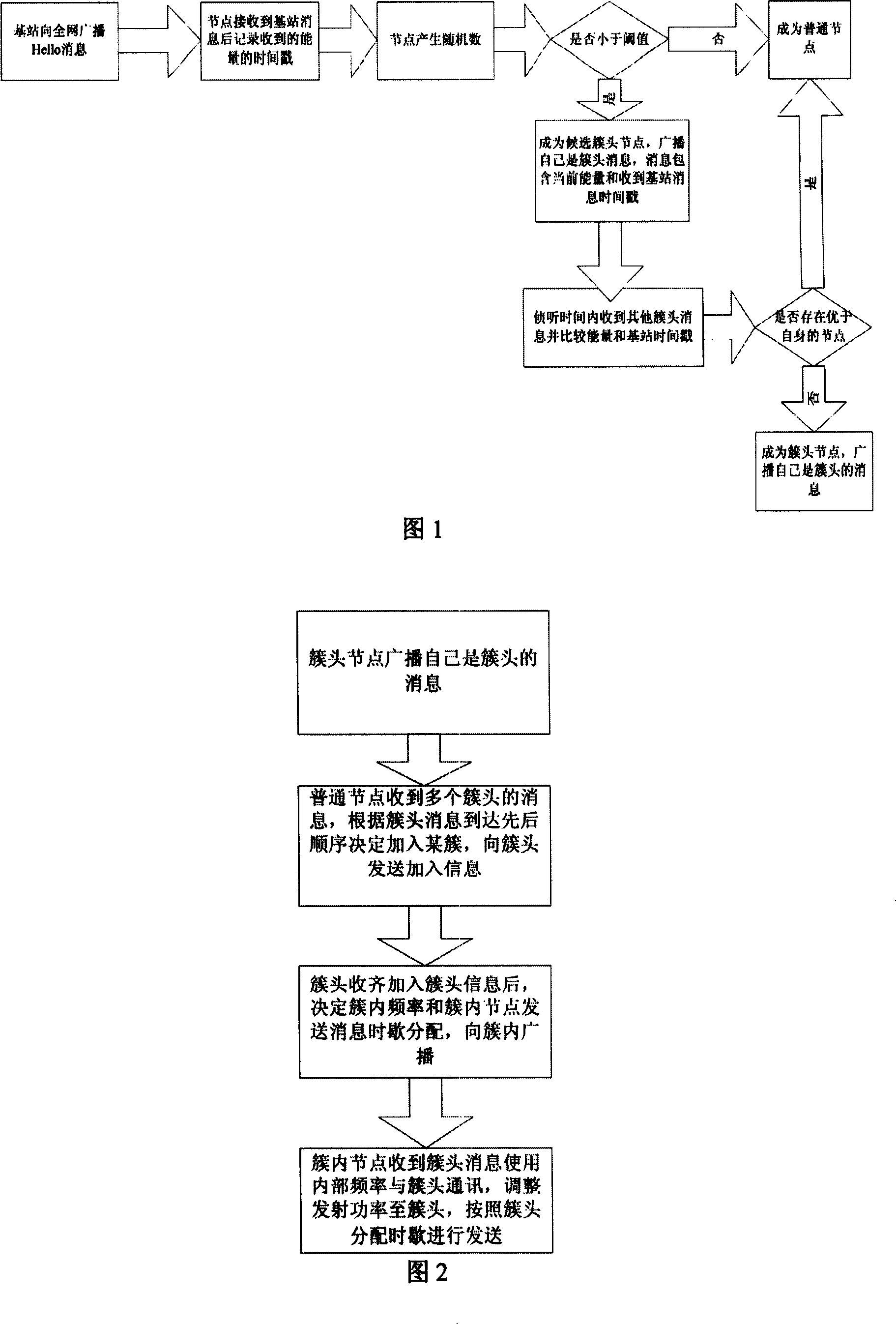
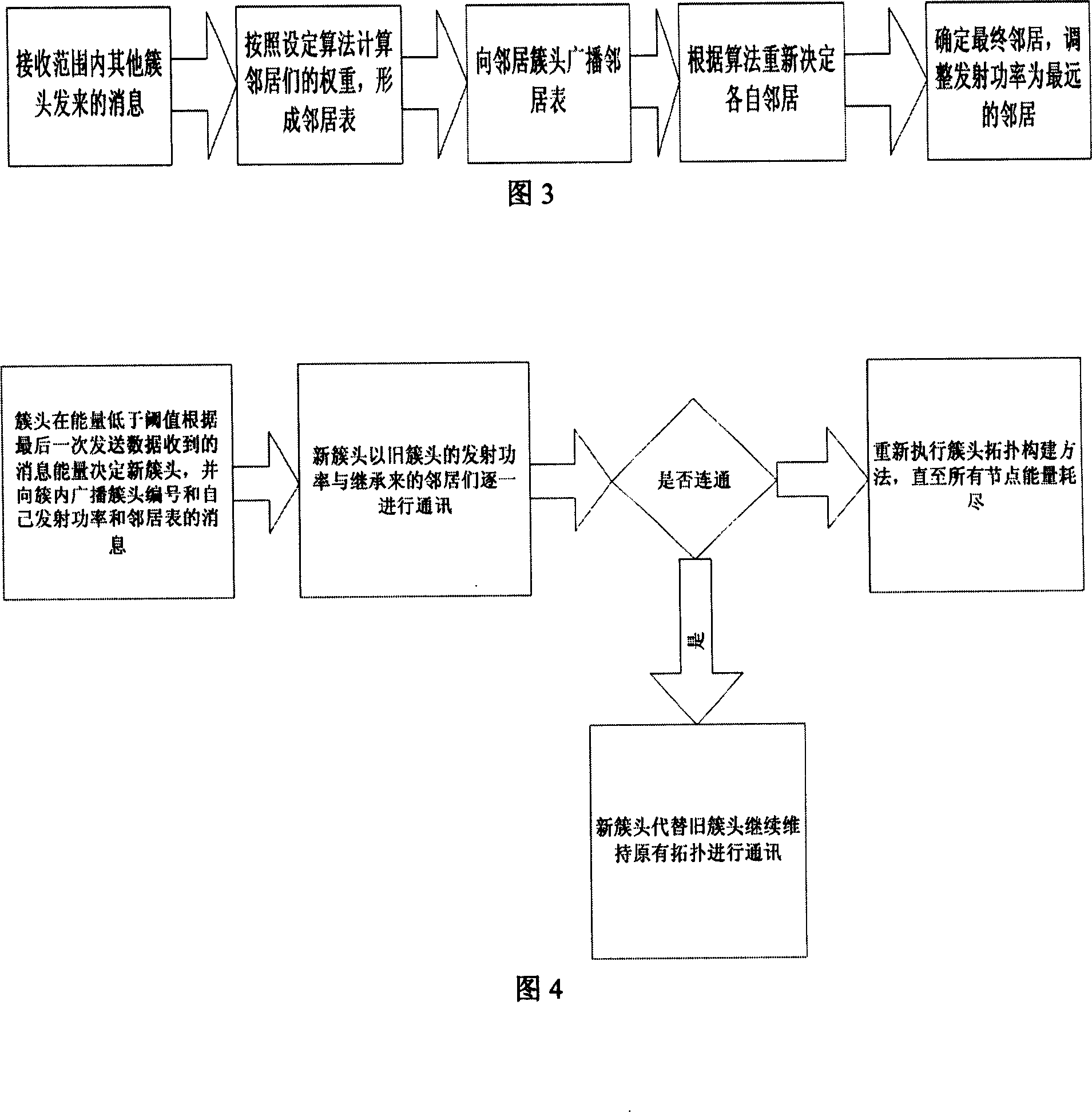
InactiveCN101013987ARevise the assumption of flat distribution of nodesExtend the life cycleEnergy efficient ICTTransmission control/equalisingWireless sensor networkingSensor node
The invention relates to one efficient wireless sensor network topological control method, which combines topological control cluster division method and power control method and comprises the following steps: a, dividing the network clusters and selecting cluster head point; b, forming cluster inner network; c, processing power control on cluster point to form final network topological structure; after failure, re-establishing network topological structure.
Owner:NANJING UNIV OF POSTS & TELECOMM
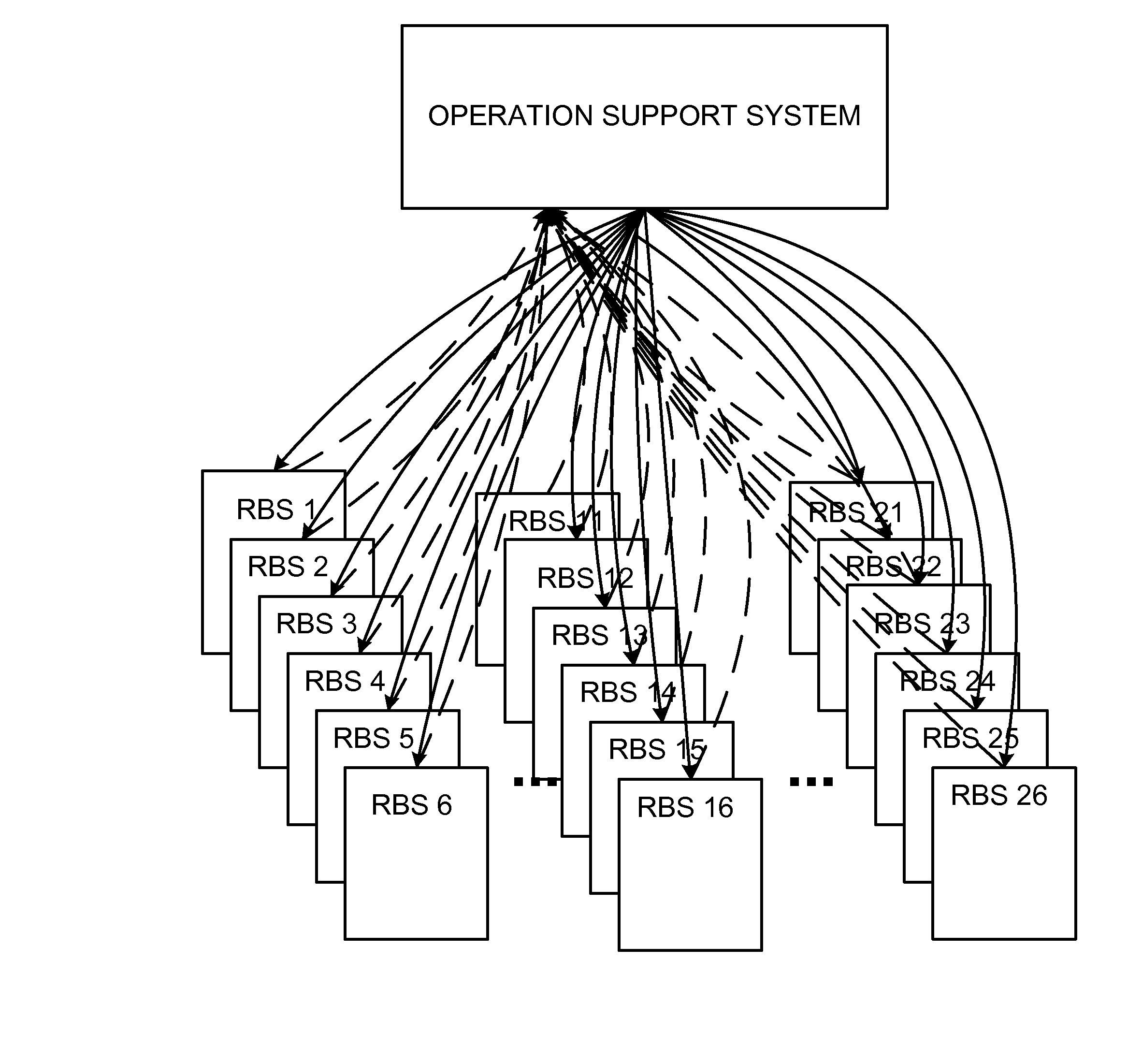
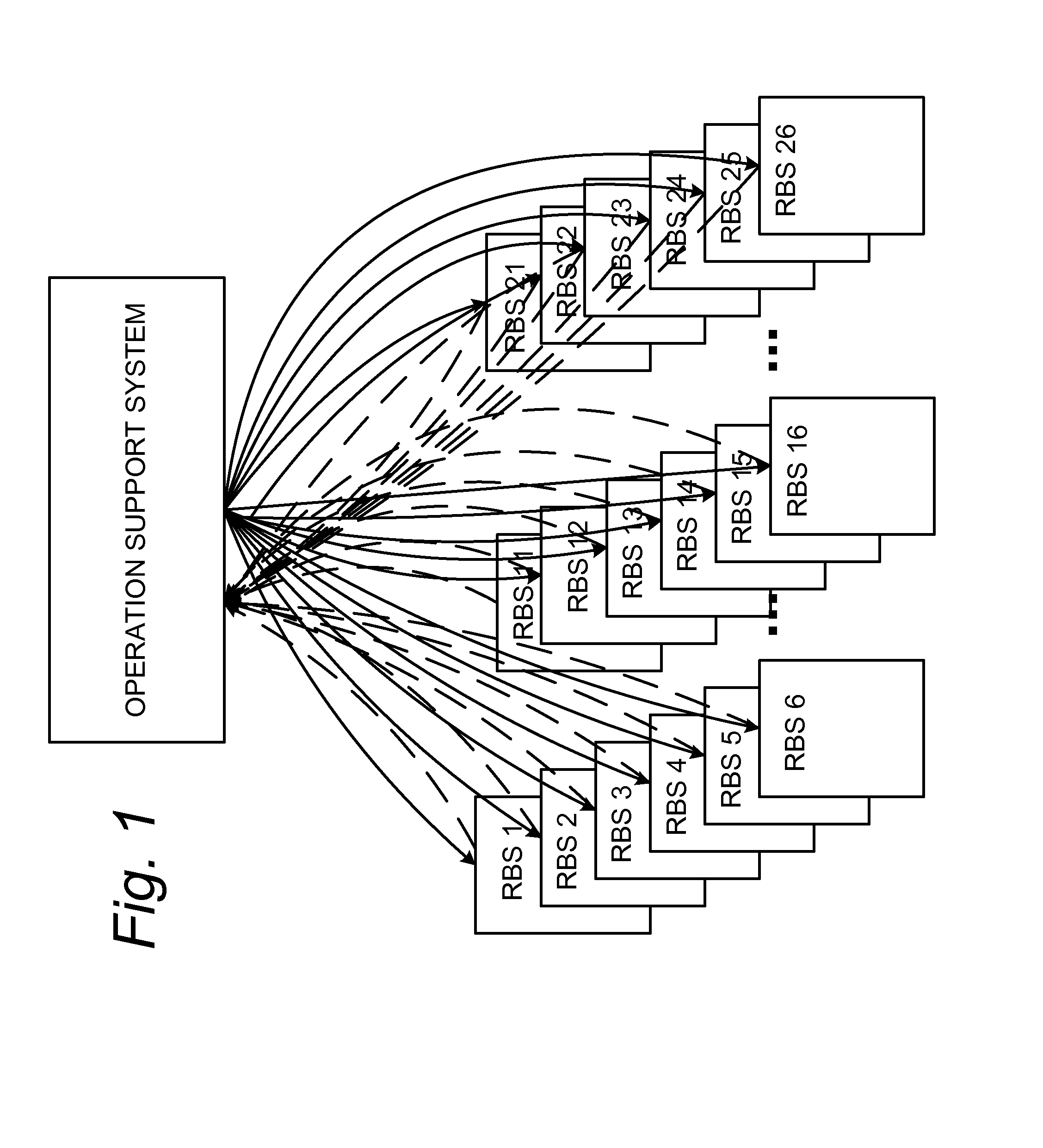
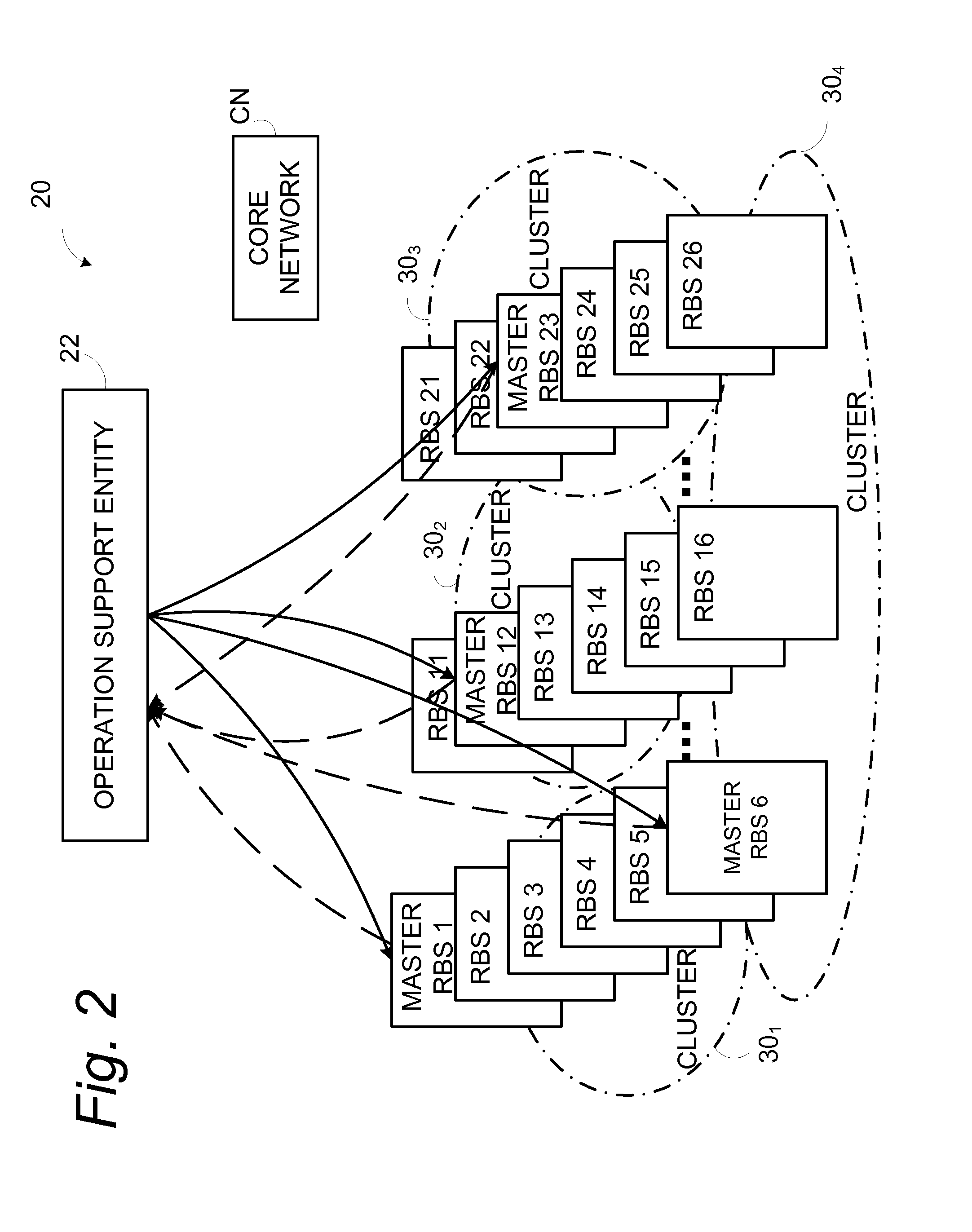
Upgrading software in radio base station nodes
ActiveUS20090119655A1Digital computer detailsSpecific program execution arrangementsTelecommunications networkCluster based
A cluster-based, delegated software upgrade scheme facilitates software upgrade for radio base station nodes comprising a cluster of a flat radio access telecommunications network. The plural radio base stations are grouped into clusters (30), and a master radio base station (RBSM) designated for each cluster. The master radio base station (RBSM) is used to initiate software upgrade of the radio base stations comprising the cluster. The master radio base station (RBSM) can also perform a monitoring of implementation of the software upgrade at the radio base stations of the cluster, and on the basis of the monitoring, determine whether a cluster-wide software upgrade is successful. In one of its example modes, the master radio base station can further prepare a software upgrade report which confirms / summarizes implementation of the software upgrade at the radio base stations of the cluster.
Owner:TELEFON AB LM ERICSSON (PUBL)
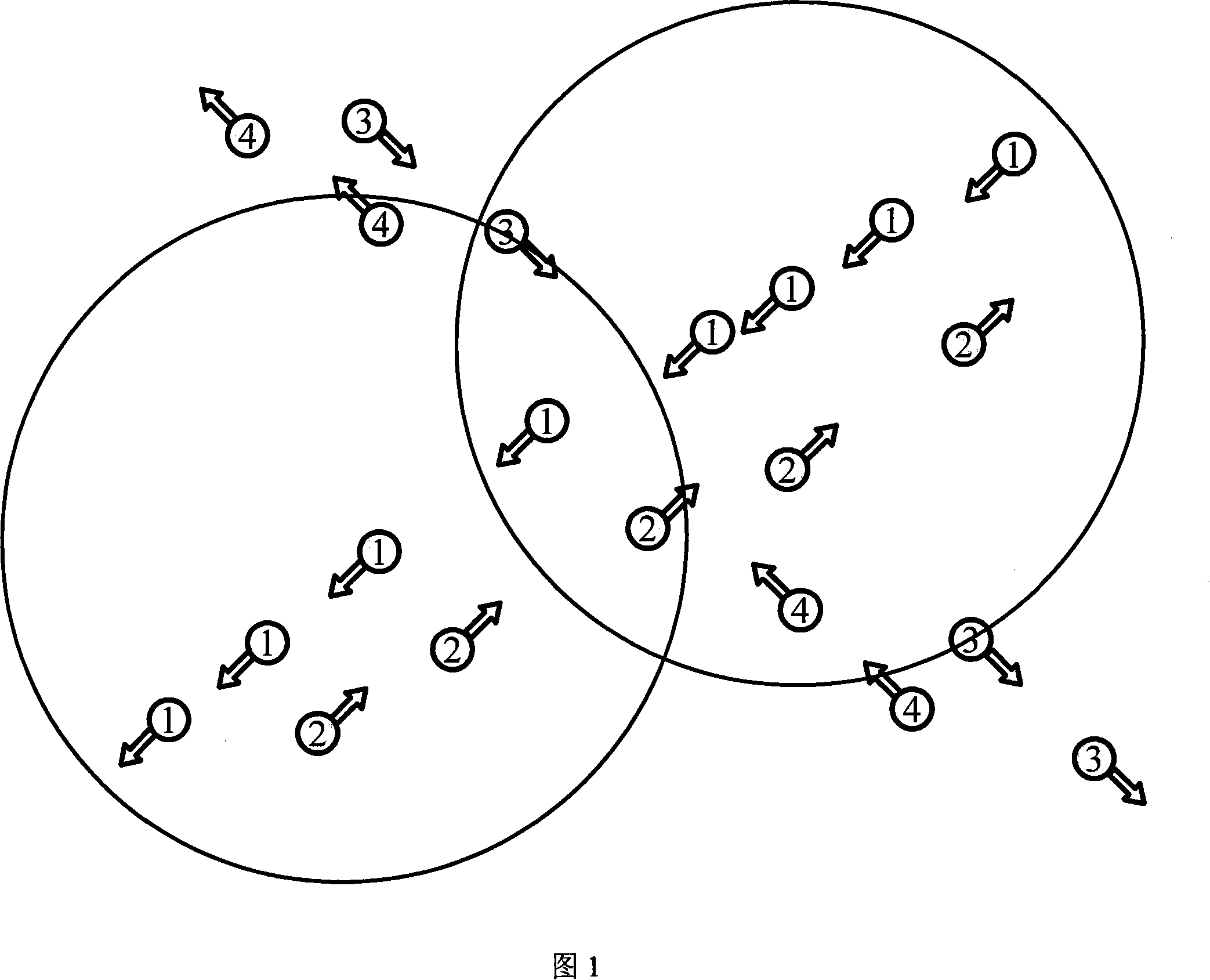
Method for clustering vehicle mounted Ad hoc network based on signal strength
InactiveCN101207572AImprove performanceLighten the computational burdenNetwork topologiesData switching by path configurationIn vehicleInformation quantity
The invention discloses a clustering method for the in-vehicle Ad hoc network based on the signal strength, and provides a network clustering and maintaining method which starts with the vehicle directional information, and enables the vehicles running along the same direction to participate in the process that the same cluster is formed and maintained. After a node is initialized, tentative cluster-heads are established among the vehicles running along the same direction, neighbor linked lists are formed in the two-hop range of the tentative cluster-heads, the node which has the maximum nodal connection signal strength is a cluster-head node, and other nodes are common nodes or gateway nodes of the cluster; the maintenance process is based on the vehicle directional information and the nodal connection signal strength. As considering the vehicle directional information and the nodal connection strength signal, the invention has the advantages that the in-vehicle Ad hoc network clustering structure is stable by comparing with other methods under the urban traffic environment, the node alternating times and the clustering related control information quantity are less, the problem that the in-vehicle Ad hoc network performance is low under the urban traffic environment is solved, the cluster service life is prolonged, and the network state is improved.
Owner:UNIV OF SCI & TECH BEIJING
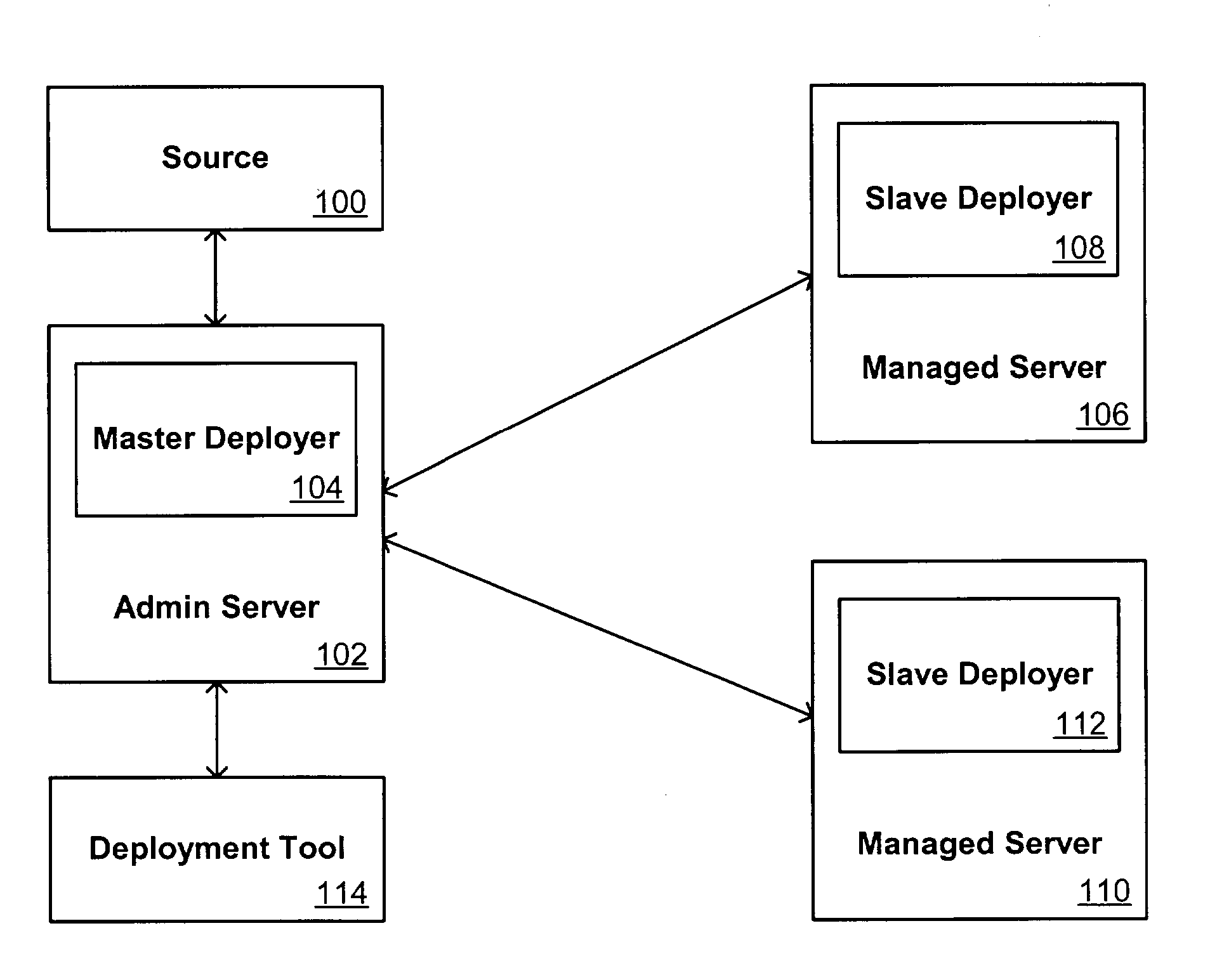
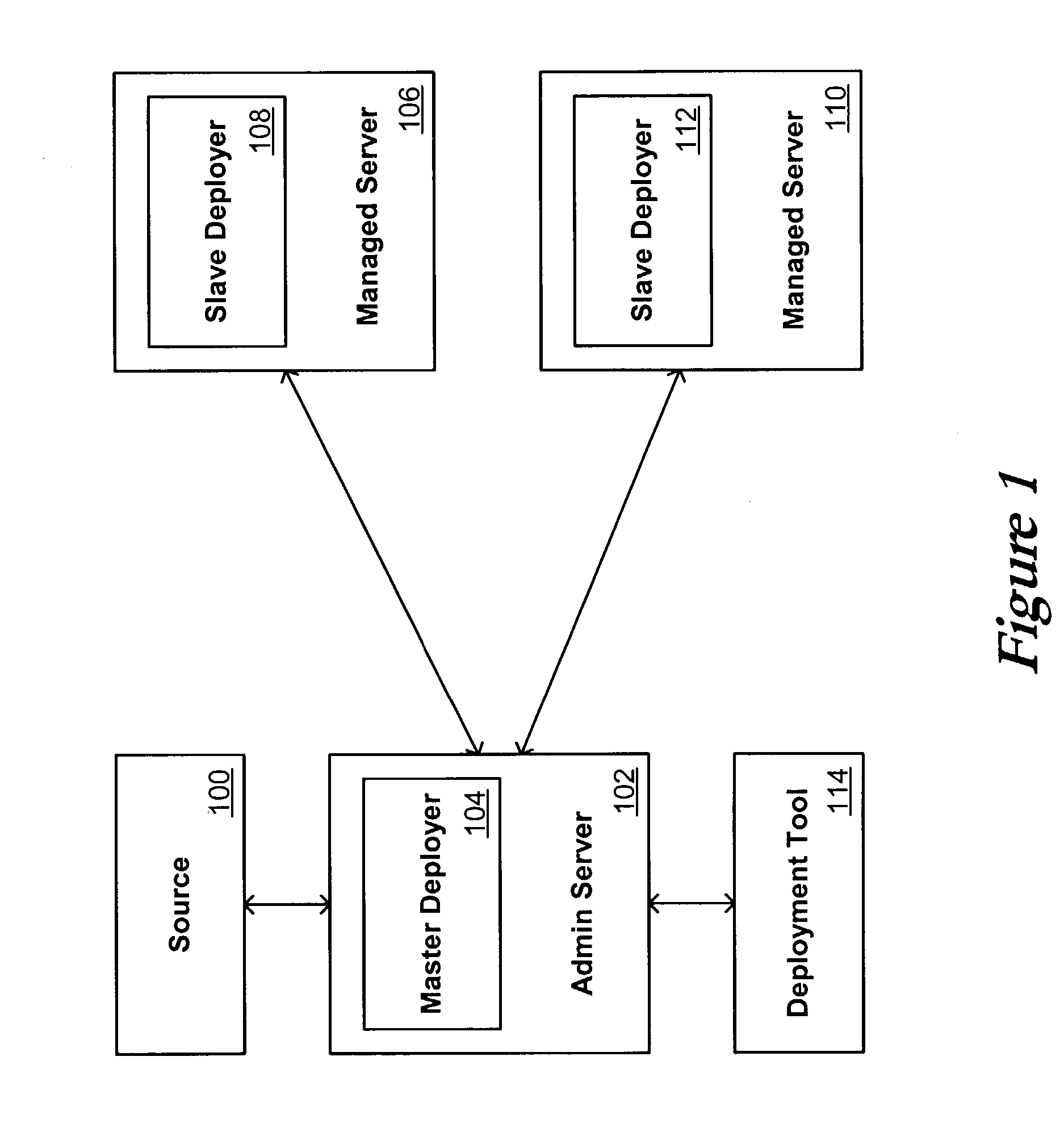
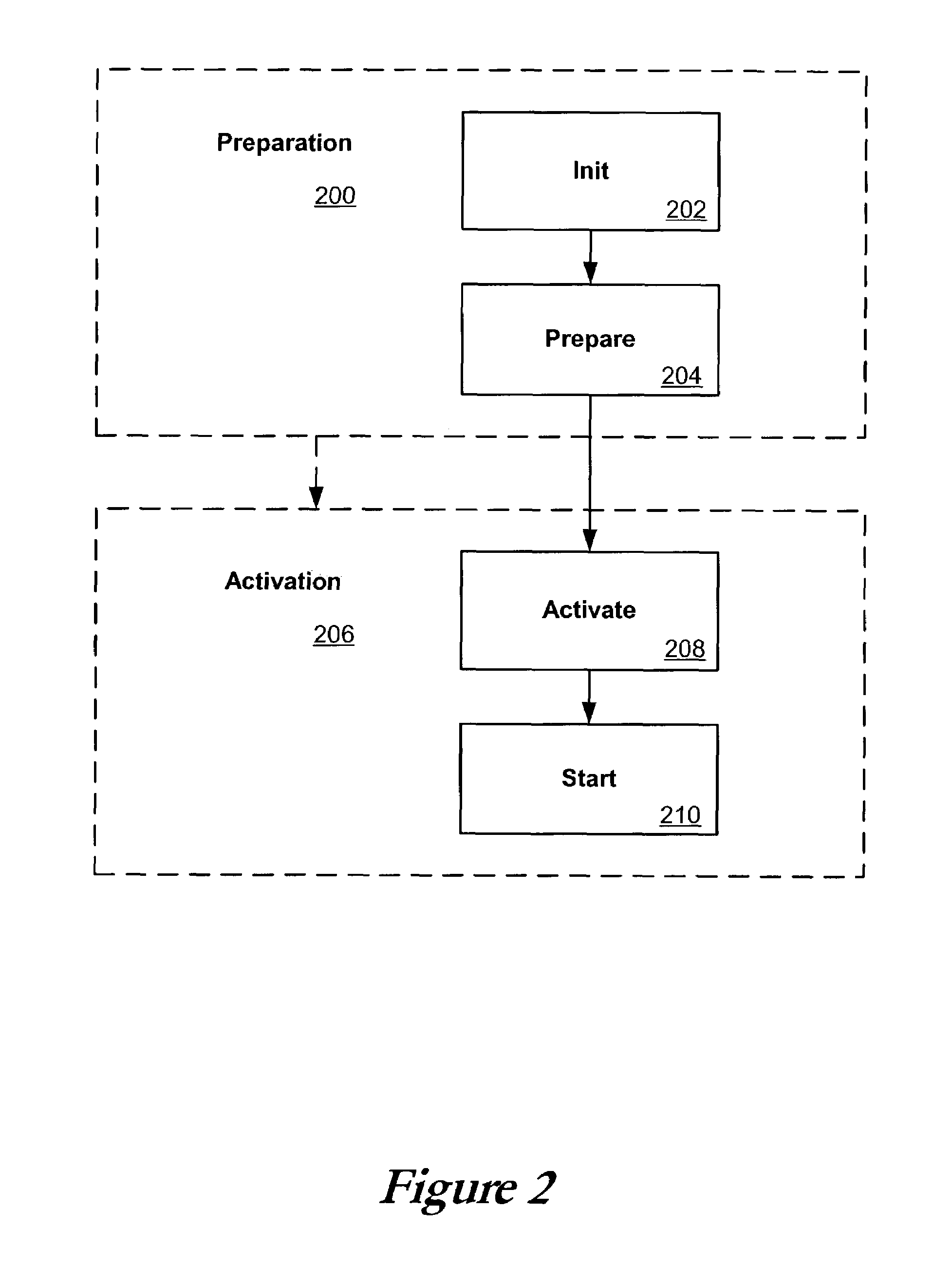
Systems and methods for application deployment
ActiveUS7228326B2Special service for subscribersMultiple digital computer combinationsApplication softwareBiological activation
Owner:ORACLE INT CORP
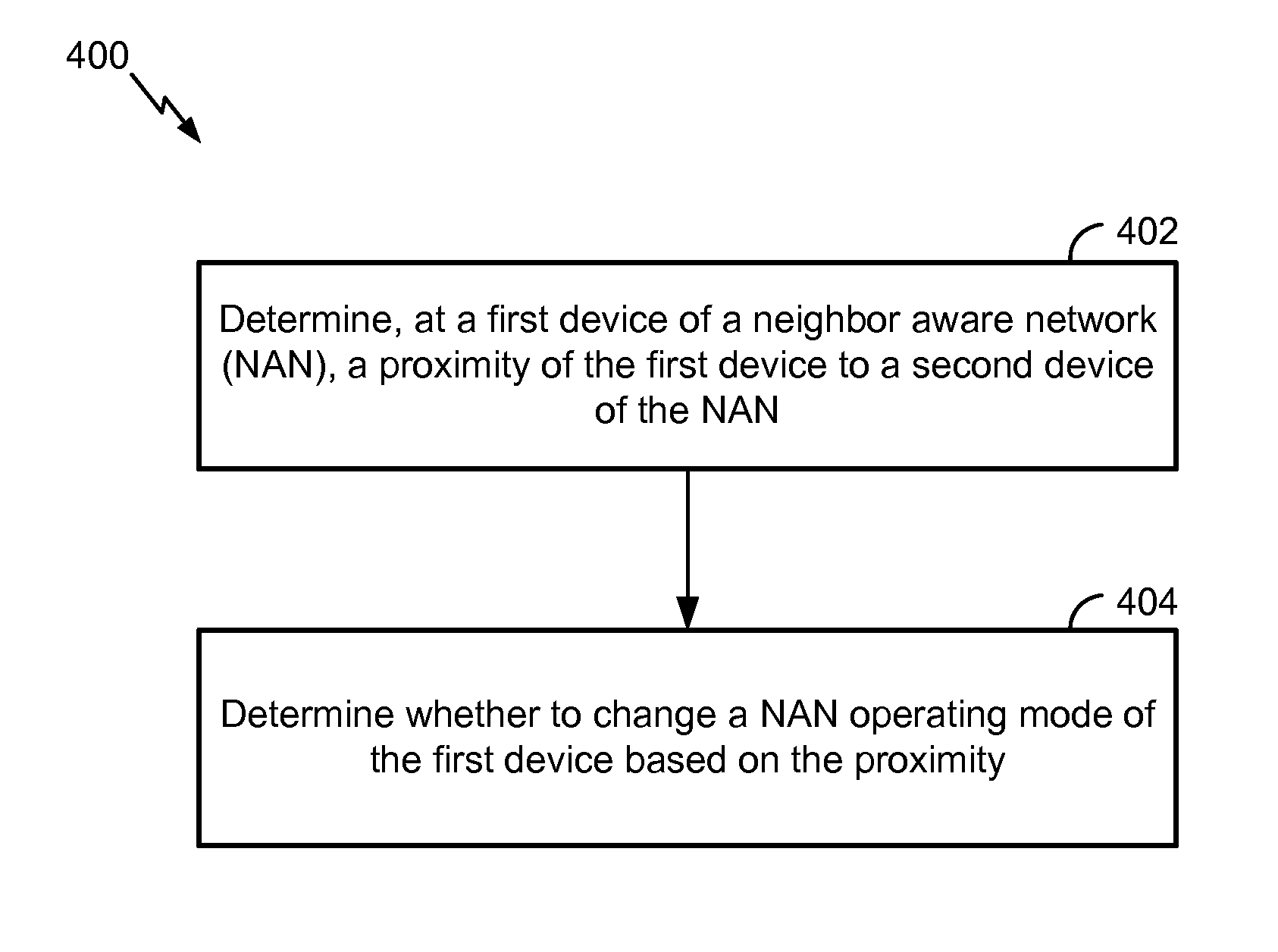
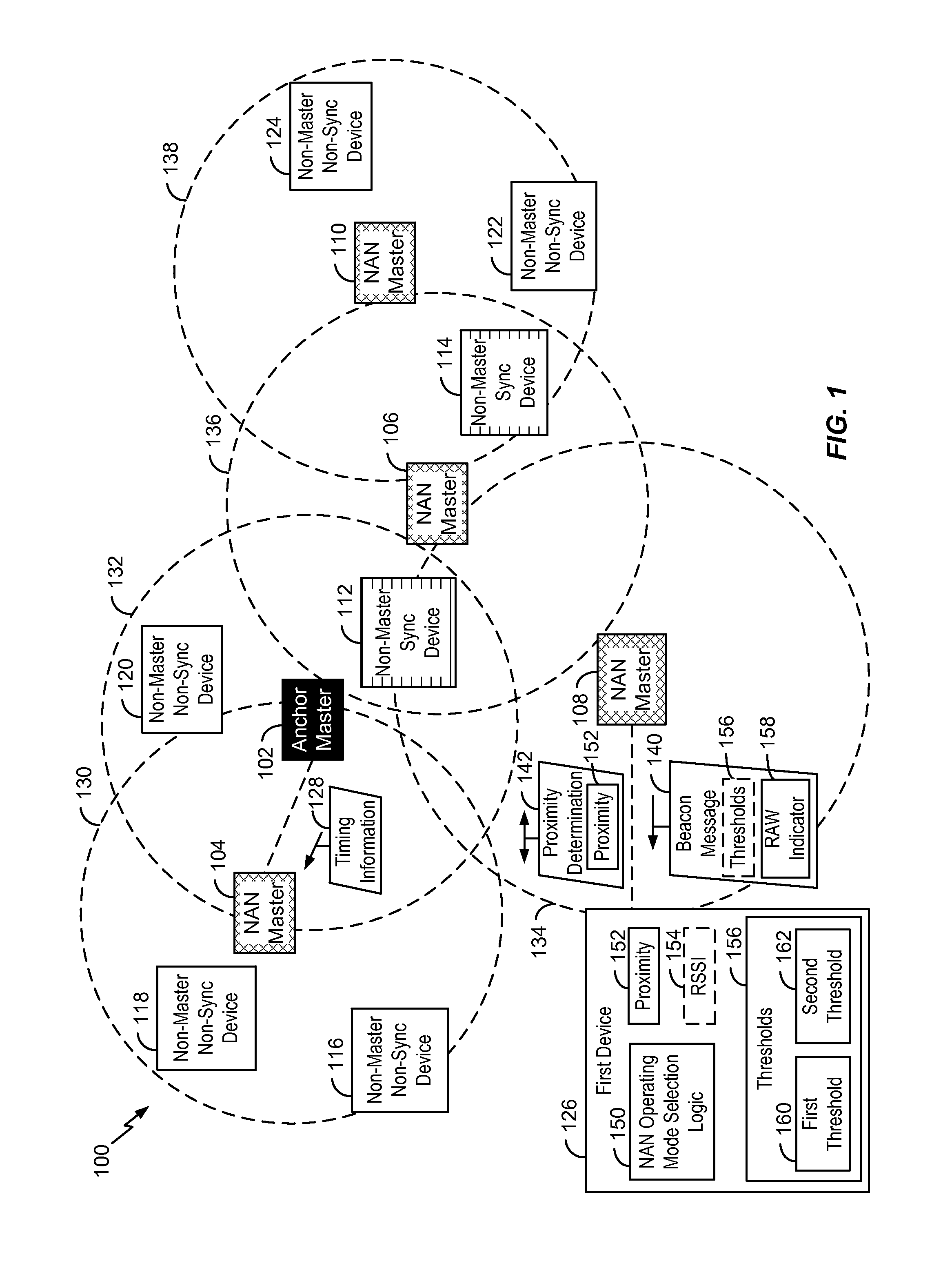
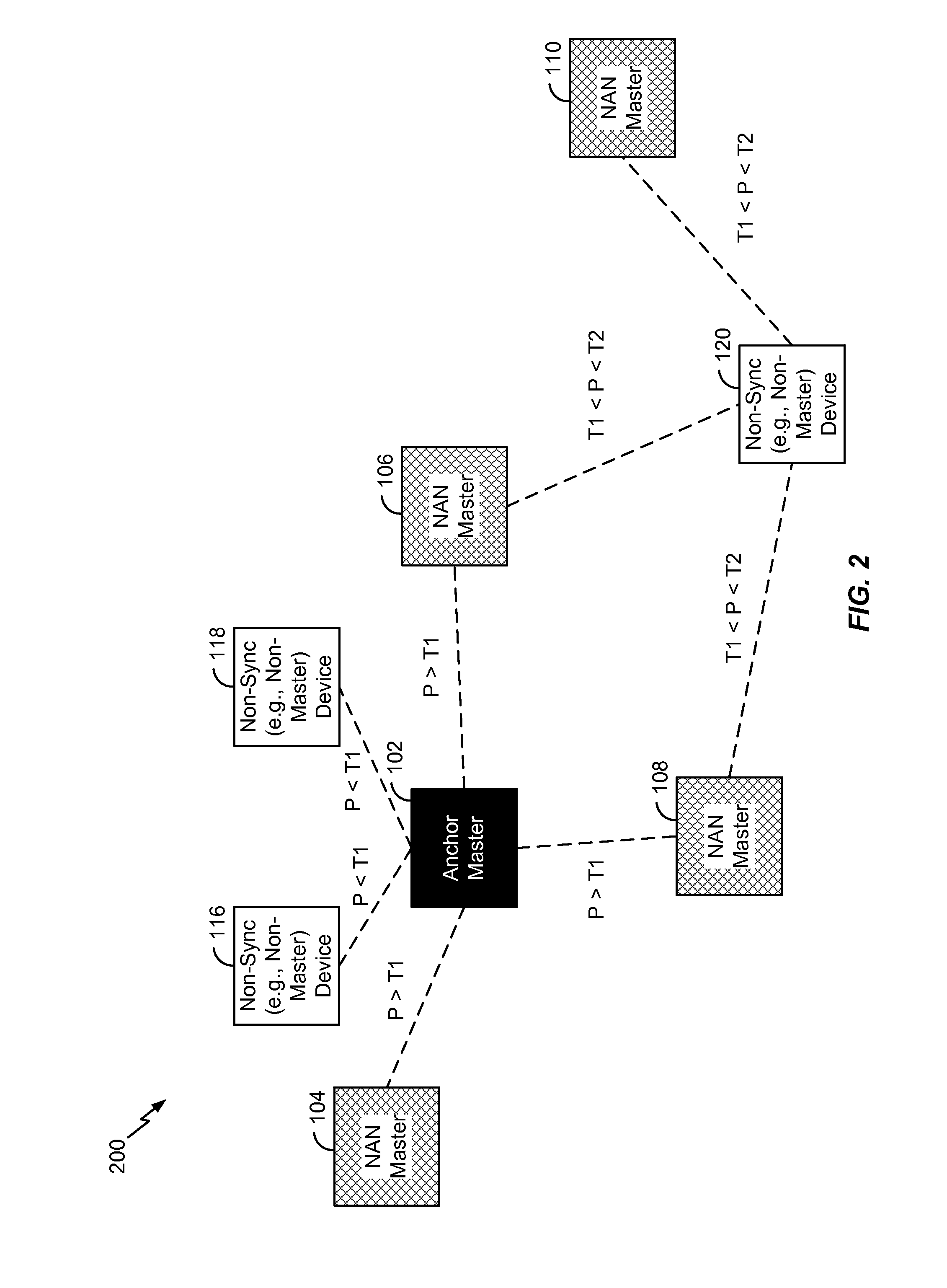
Neighbor aware network cluster topology establishment based on proximity measurements
InactiveUS20150350027A1Reduce power consumptionLess powerPower managementSynchronisation arrangementNetwork clusteringReal-time computing
Owner:QUALCOMM INC
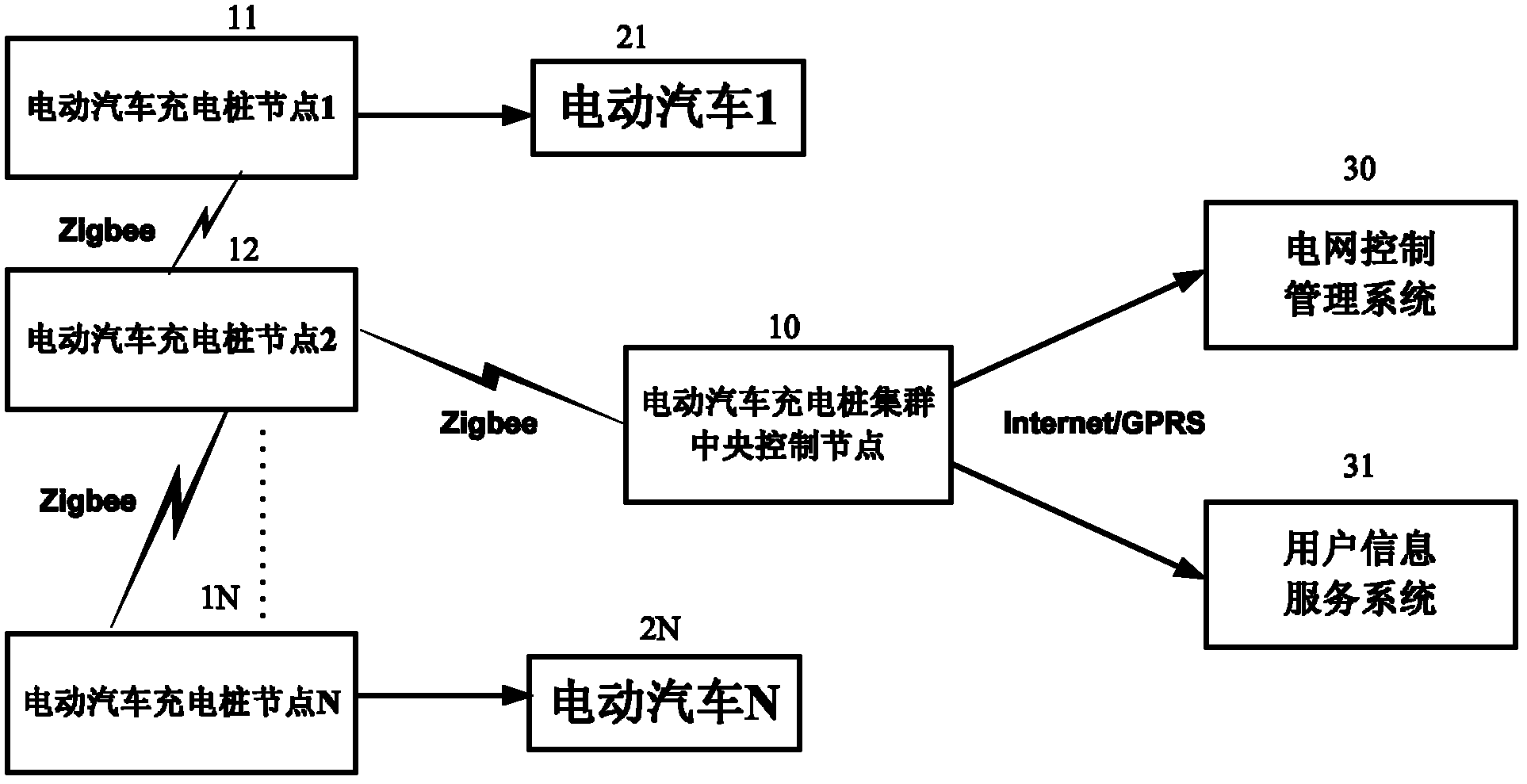
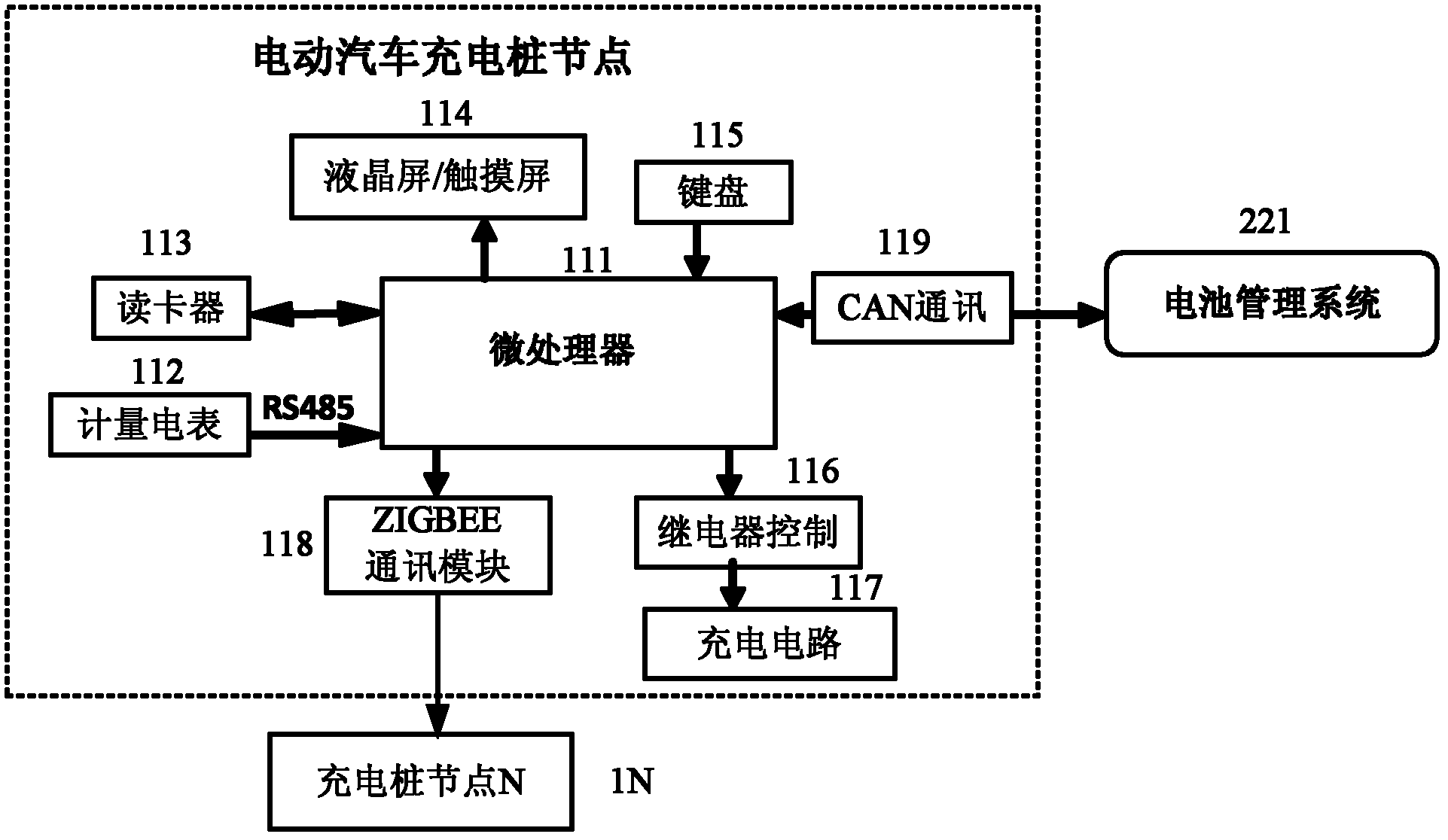
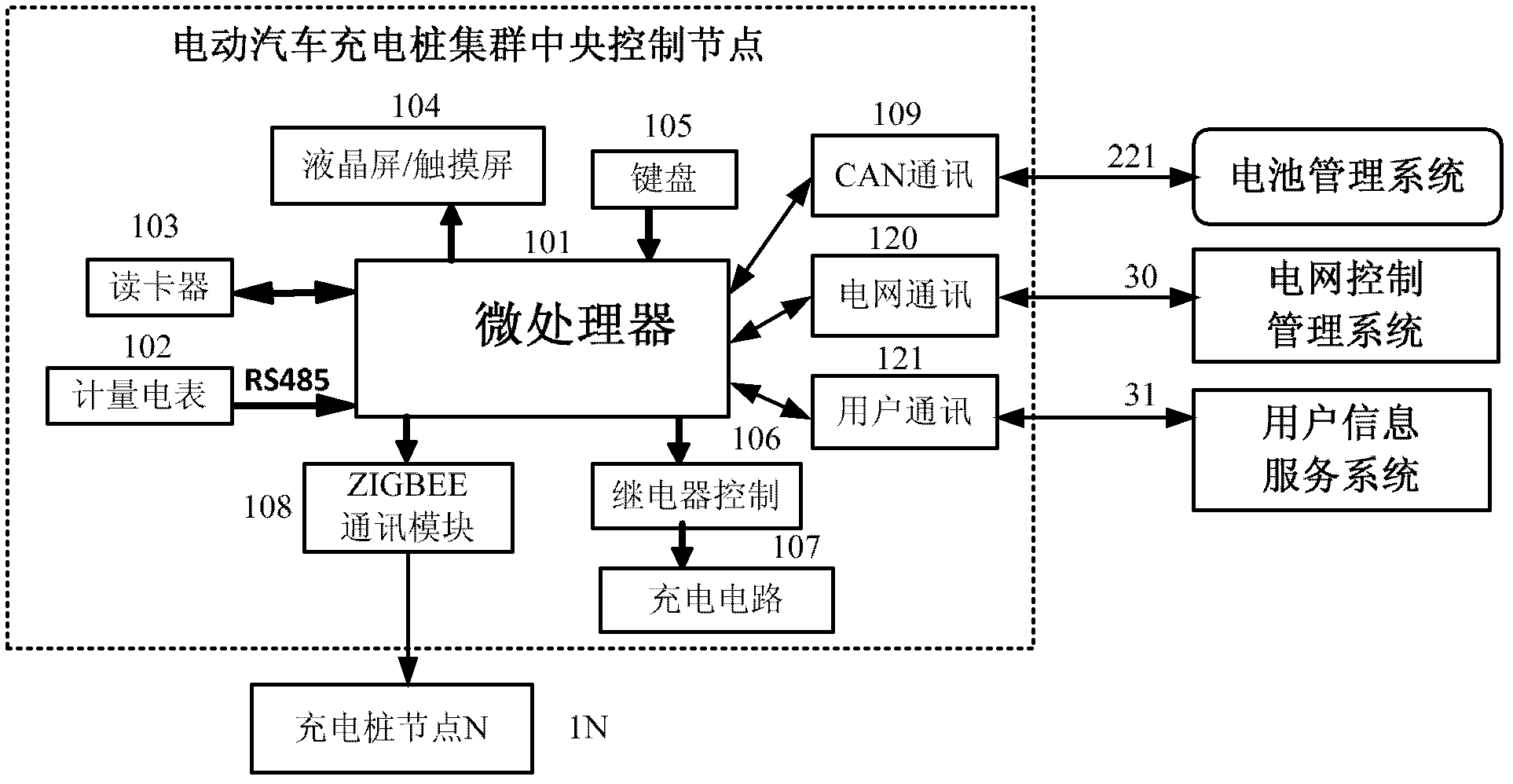
Electric vehicle intelligent interactive charging network cluster system
ActiveCN102215261AReal-time control of the charging processReduce demandTransmission systemsNetwork topologiesGeneral Packet Radio ServiceCode division multiple access
The invention provides an electric vehicle intelligent interactive charging network cluster system, comprising multiple electric vehicle charging post nodes (11,..., 1N), multiple electric vehicles (21,..., 2N), an electric vehicle charging post cluster central control node (10), a grid control management system (30), and a user information service system (31). The electric vehicle charging post node (1N) is connected with the electric vehicle (2N) to charge the power batteries of the electric vehicle; the electric vehicle charging post cluster central control node (10) and the electric vehicle charging post nodes (11,..., 1N) realize networking connection by means of wireless Zigbee communication; the power system control management system (30) and the electric vehicle charging post cluster central control node (10) are connected by means of Internet wired communication or GPRS (general packet radio service), CDMA (code division multiple access) and WIFI (wireless fidelity) wireless communication; and the user information service system (31) and the electric vehicle charging post cluster central control node (10) realize wireless connection by means of GPRS, CDMA and WIFI.
Owner:INST OF ELECTRICAL ENG CHINESE ACAD OF SCI
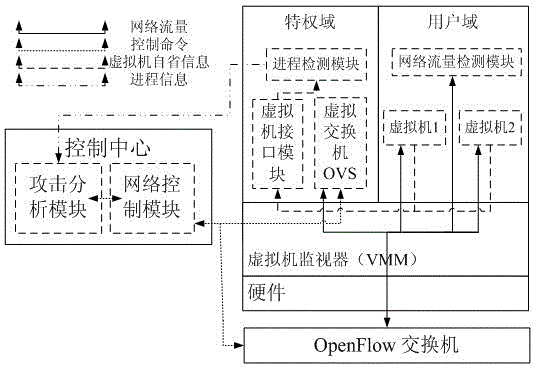
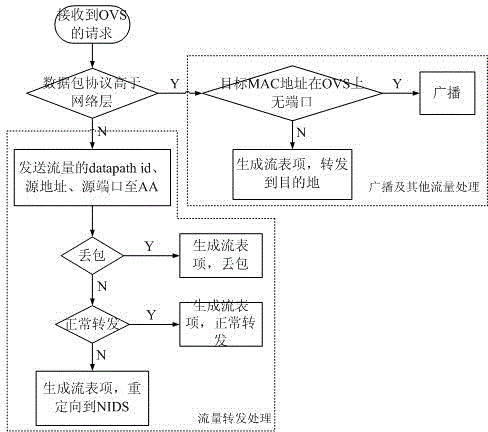
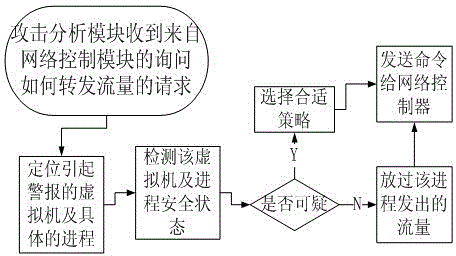
Security defensive system and defensive method based on software-defined network
ActiveCN104023034AGuaranteed service qualityReduce distractionsTransmissionNetwork controlAttack analysis
The invention relates to the technical field of computer security, and in particular to a security defensive system and a defensive method based on a software-defined network. The security defensive system comprises a network control module, an attack analysis module, a progress detection module and a network flow detection module, wherein the network control module is used for intercepting a network data packet between virtual machines and used for forwarding acquired flow information to the attack analysis module; the attack analysis module is used for receiving flow information from the virtual machines of the network control module, used for scheduling the progress detection module to detect whether the progress is questionable, and used for scheduling the network flow detection module to execute deep detection on questionable flow if necessary. Aiming at expansion of virtual switches for flow forwarding among virtual machines in a conventional virtual machine server, the invention discloses a deep defensive system which is capable of intercepting, detecting and reorienting the flow, and the purposes of preventing and stopping attack behaviors of virtual machines of a network cluster are achieved.
Owner:WUHAN UNIV
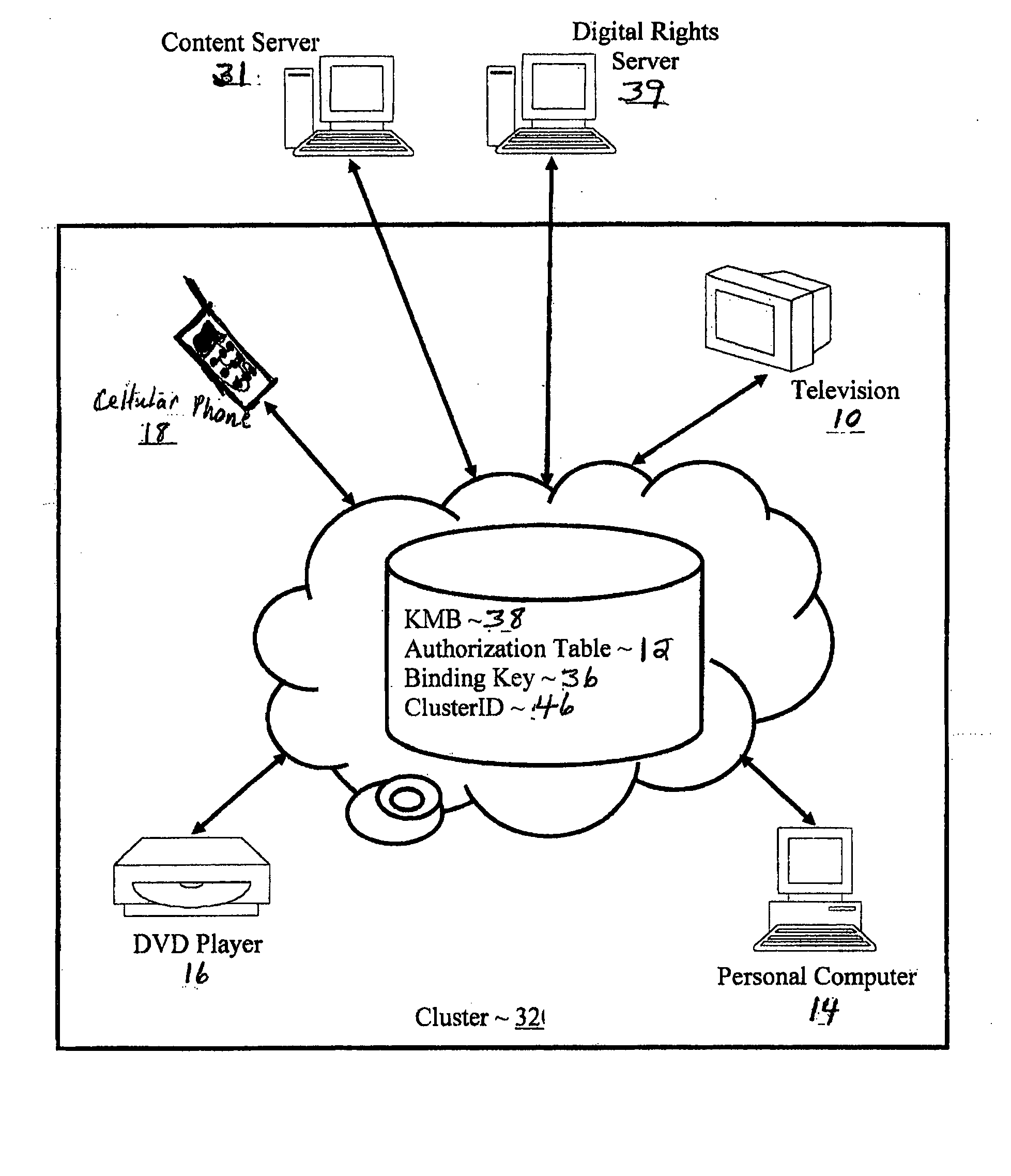
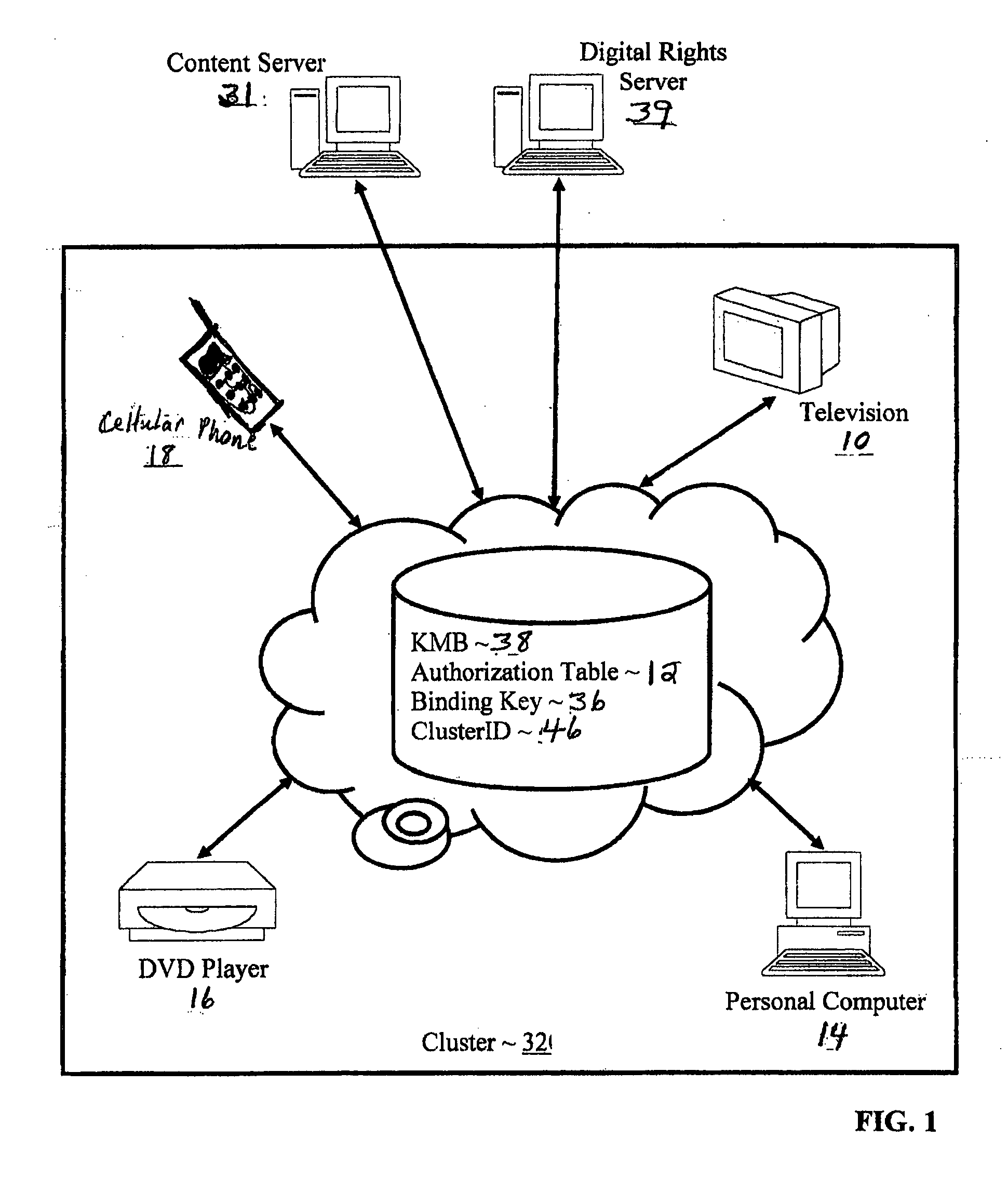
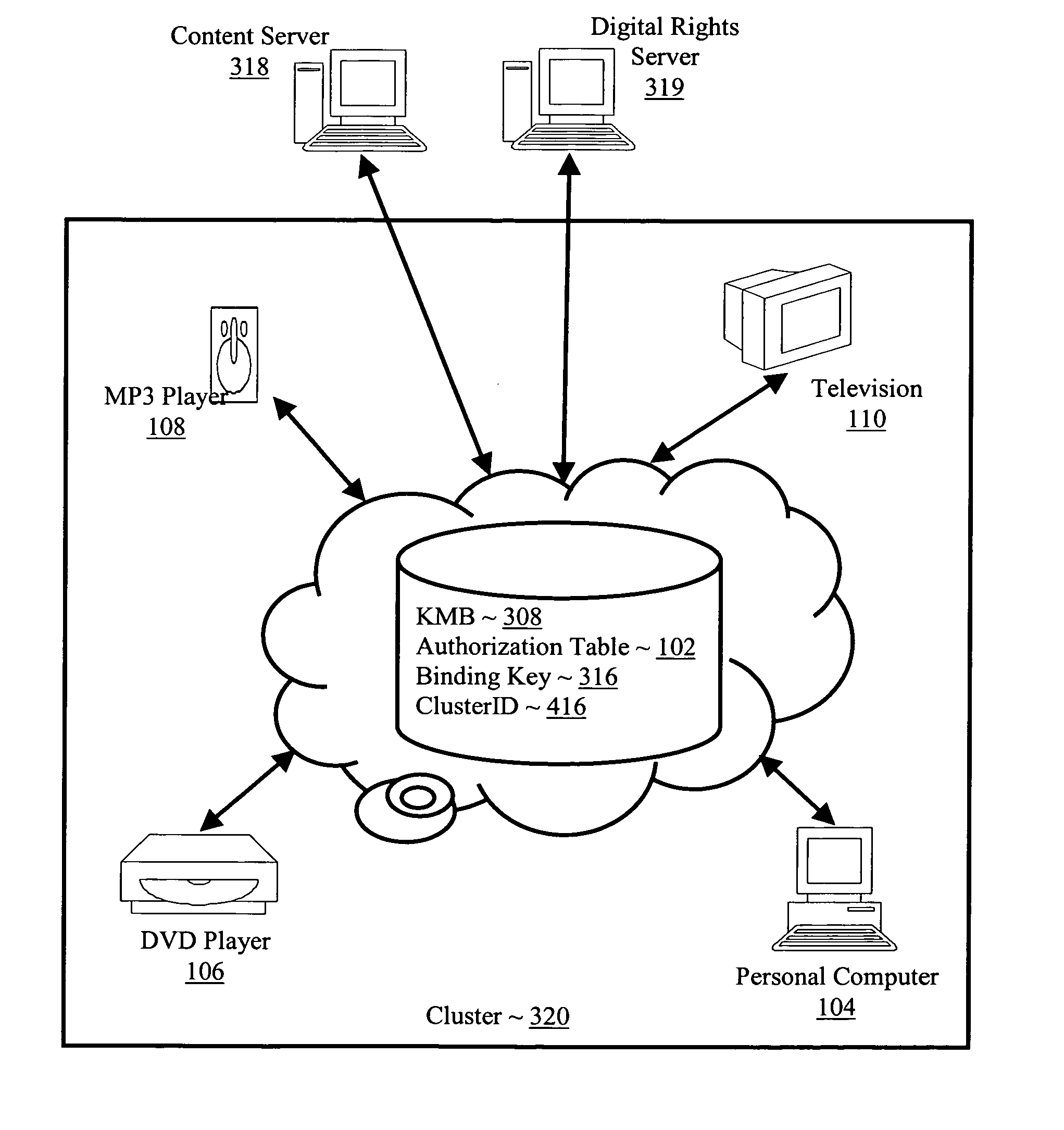
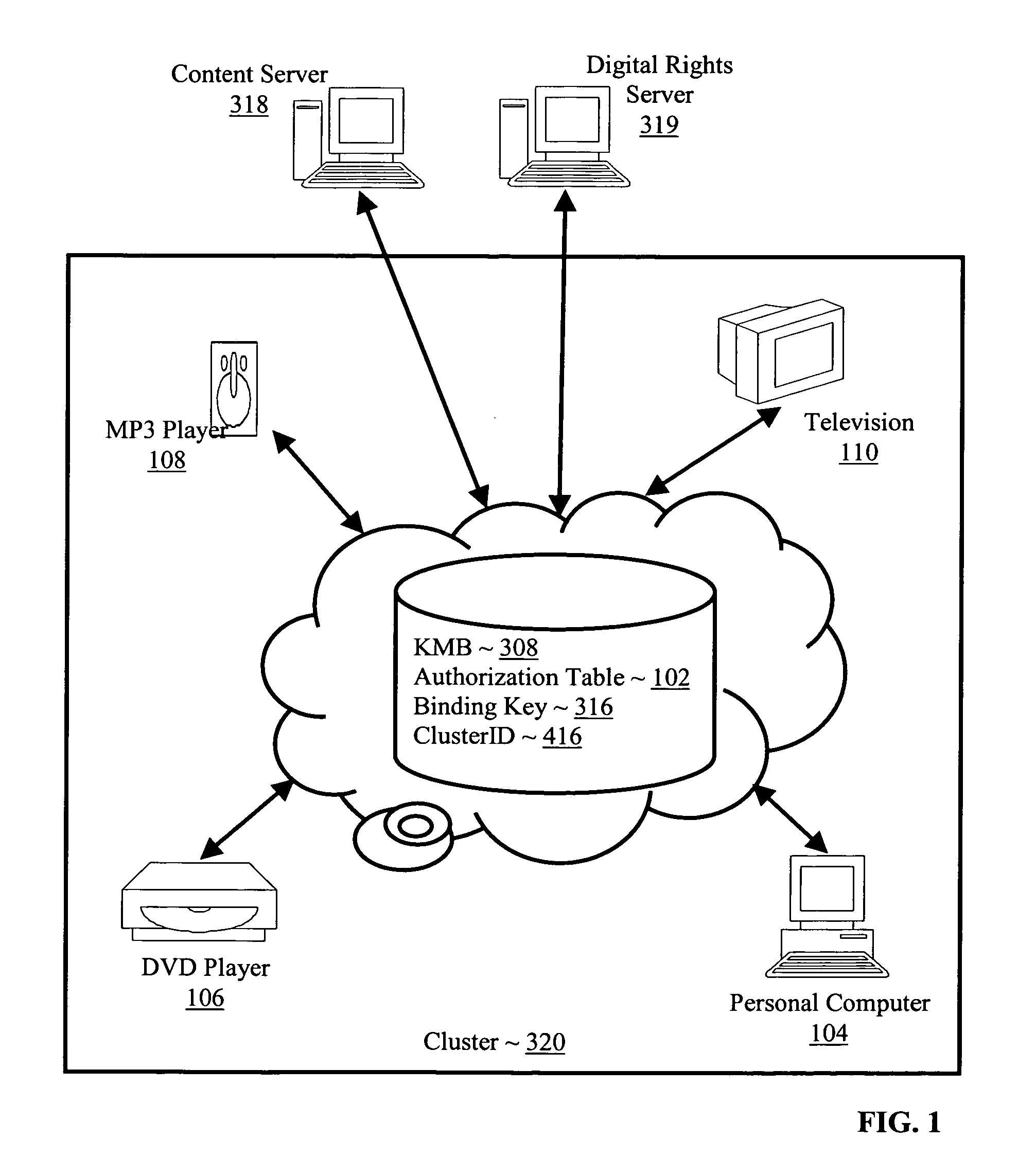
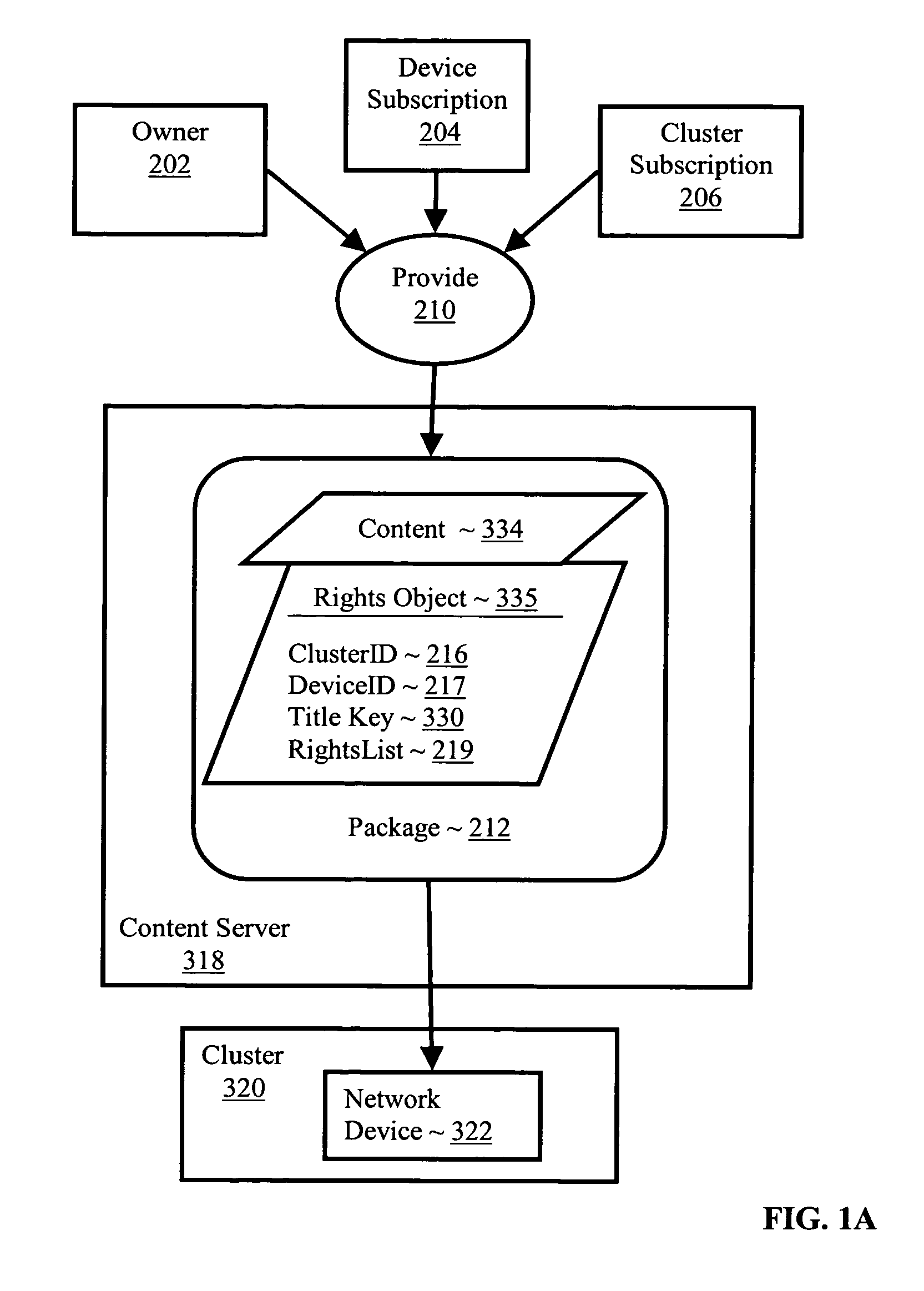
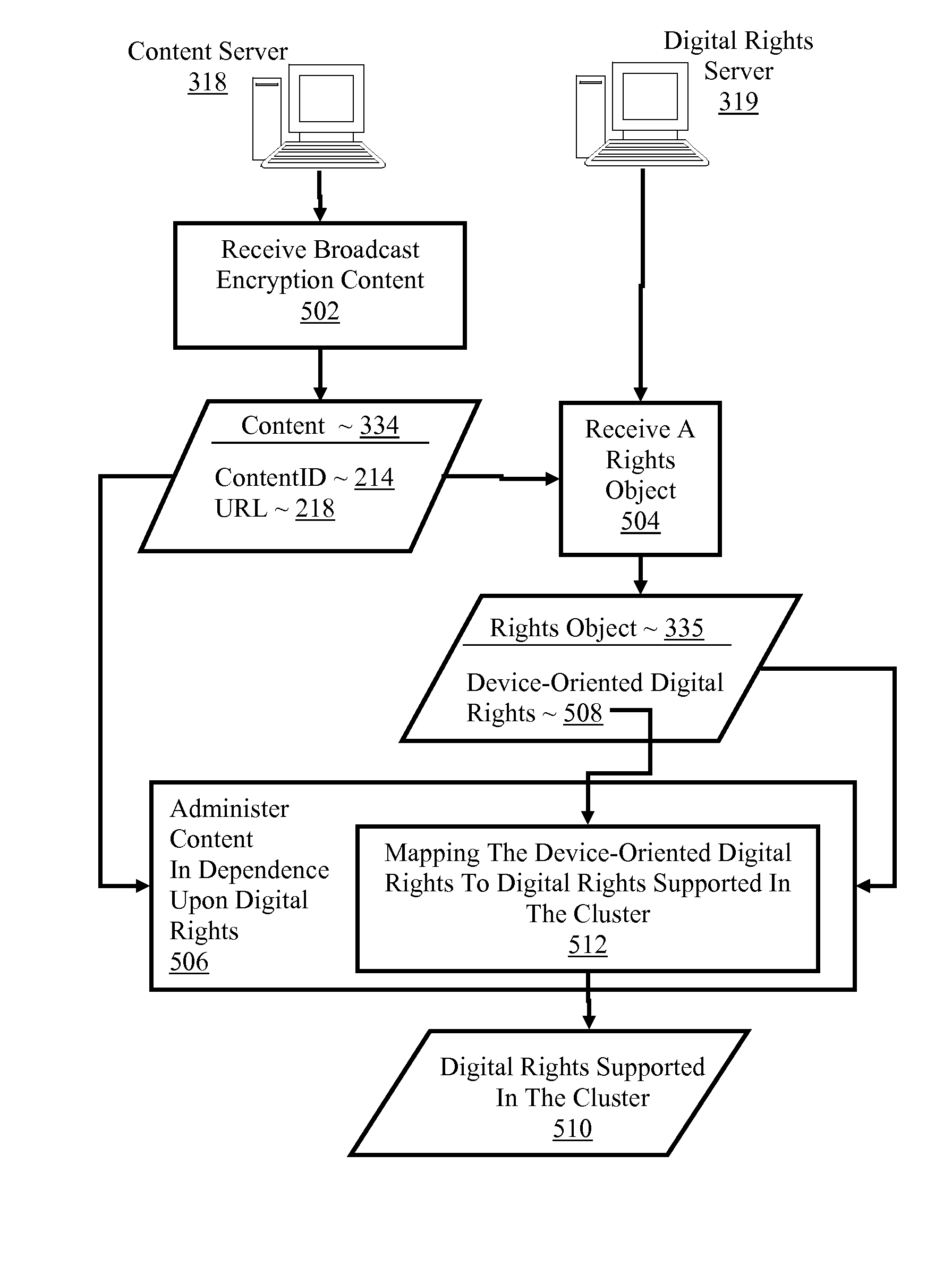
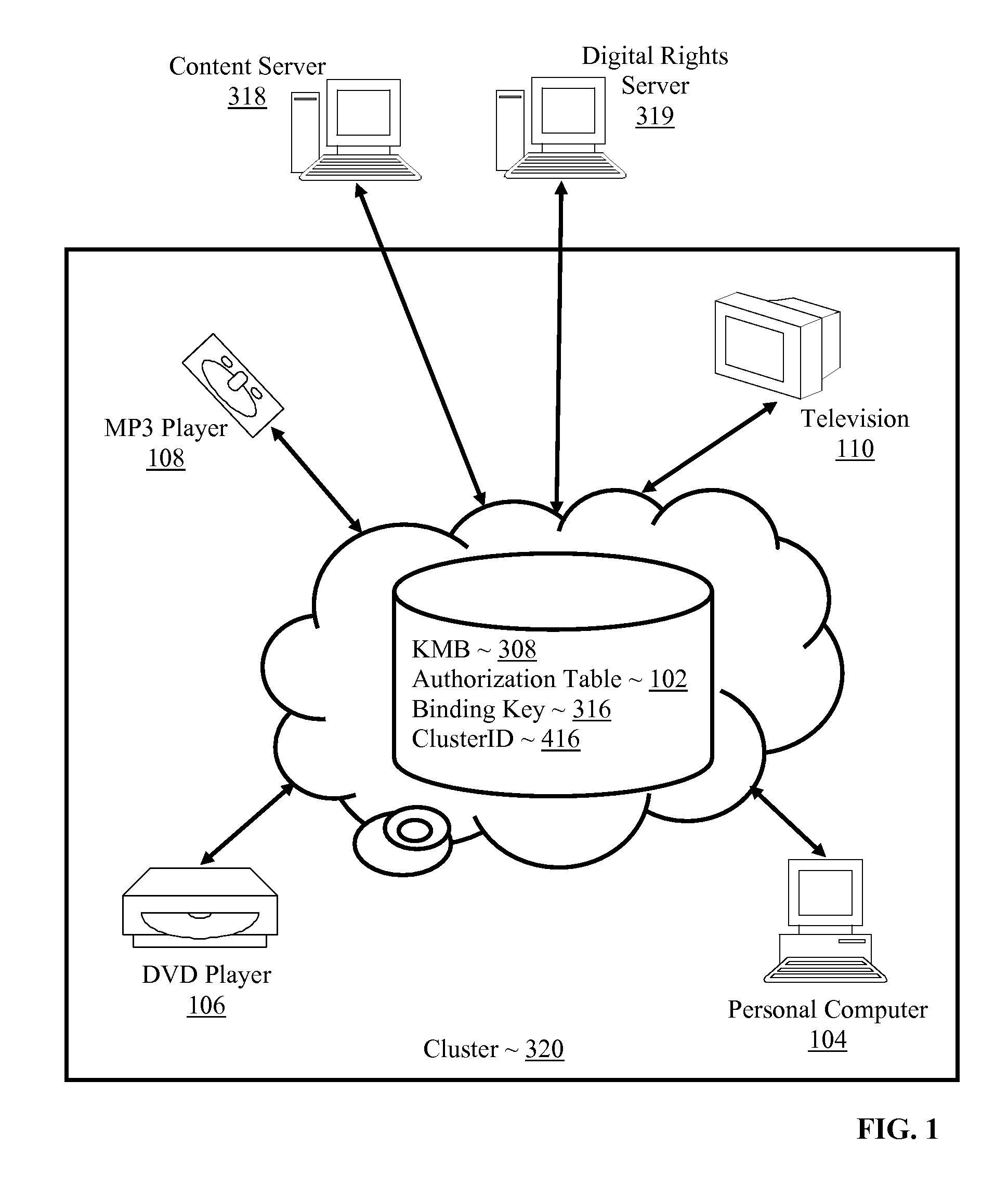
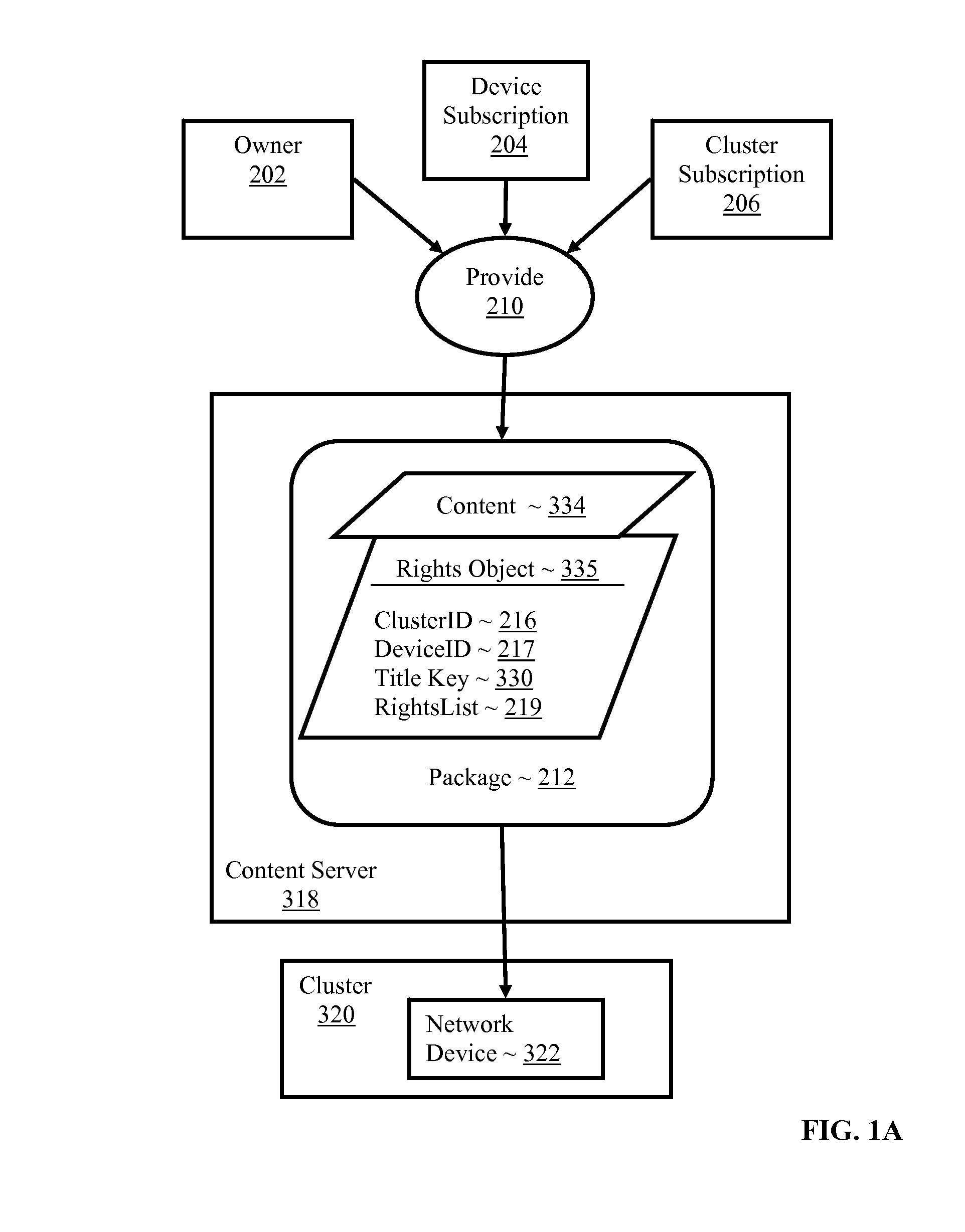
Controlling with rights objects delivery of broadcast encryption content for a network cluster from a content server outside the cluster
InactiveUS20060059573A1Digital data processing detailsAnalogue secracy/subscription systemsAuthorizationNetwork clustering
Methods, systems, and products are disclosed for controlling with rights objects delivery of broadcast encryption content for a network cluster from a content server outside the cluster that include receiving in the content server from a network device a key management block for the cluster, a unique data token for the cluster, and an encrypted cluster id; calculating a binding key for the cluster in dependence upon the key management block for the cluster, the unique data token for the cluster, and the encrypted cluster id; inserting a title key into a rights object defining rights for the broadcast encryption content; and sending the rights object to the cluster. In typical embodiments, the rights for content include an authorization for a play period and an authorized number of copies of the broadcast encryption content to devices outside the cluster.
Owner:IBM CORP
Method, device and system for joining in neighbor awareness network cluster
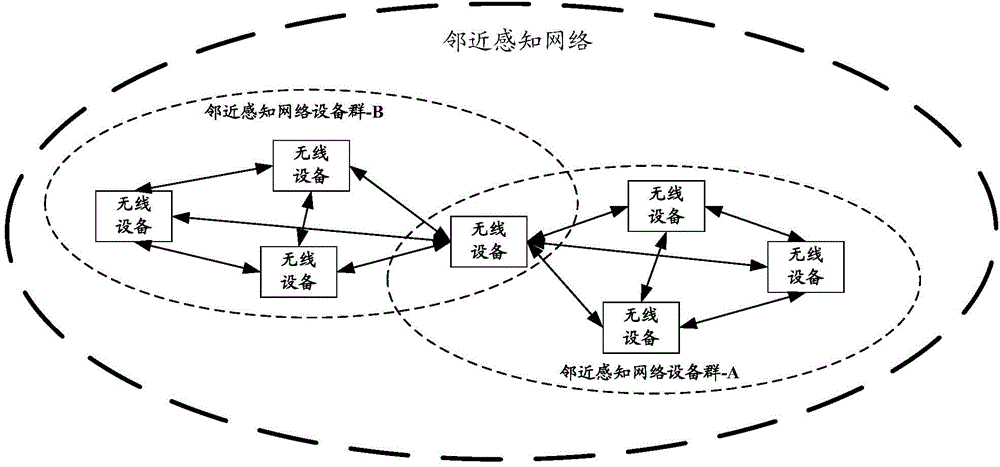
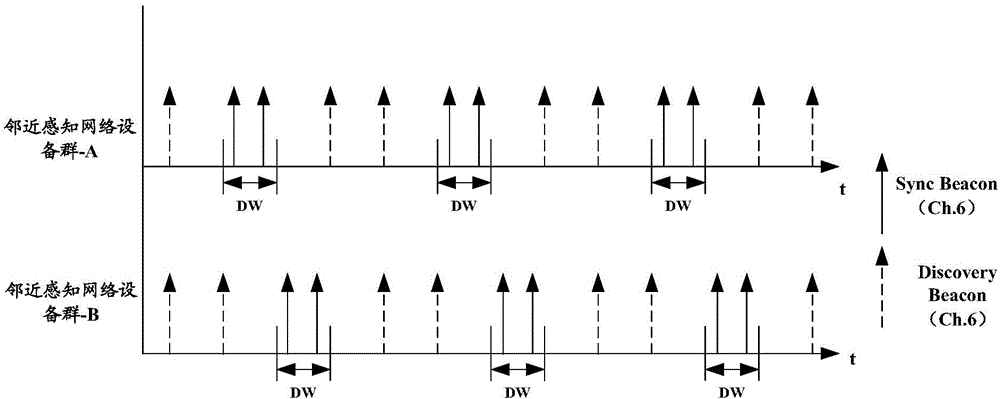
ActiveCN104378800AShort working hoursReduce power consumptionAssess restrictionNetwork topologiesTelecommunicationsNetwork clustering
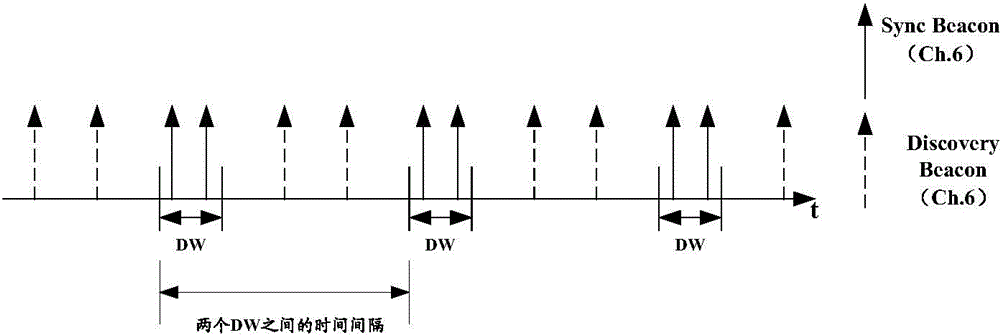
Disclosed are a method, device and system for joining a Neighbor Awareness Network (NAN) cluster. When a wireless device in a first NAN cluster scans and finds a second NAN cluster, if joining the second NAN cluster is necessary, then the wireless device leaves the first NAN cluster and joins the second NAN cluster; as the wireless device does not join a plurality of NAN clusters at the same time, the wireless device has low power consumption; in addition, as times goes on, when all the wireless devices in the first NAN cluster leave the first NAN cluster and join the second NAN cluster, the discovery window (DW) of the first NAN cluster on the working channel will not be occupied, thus increasing available resources on the working channel.
Owner:HUAWEI DEVICE CO LTD
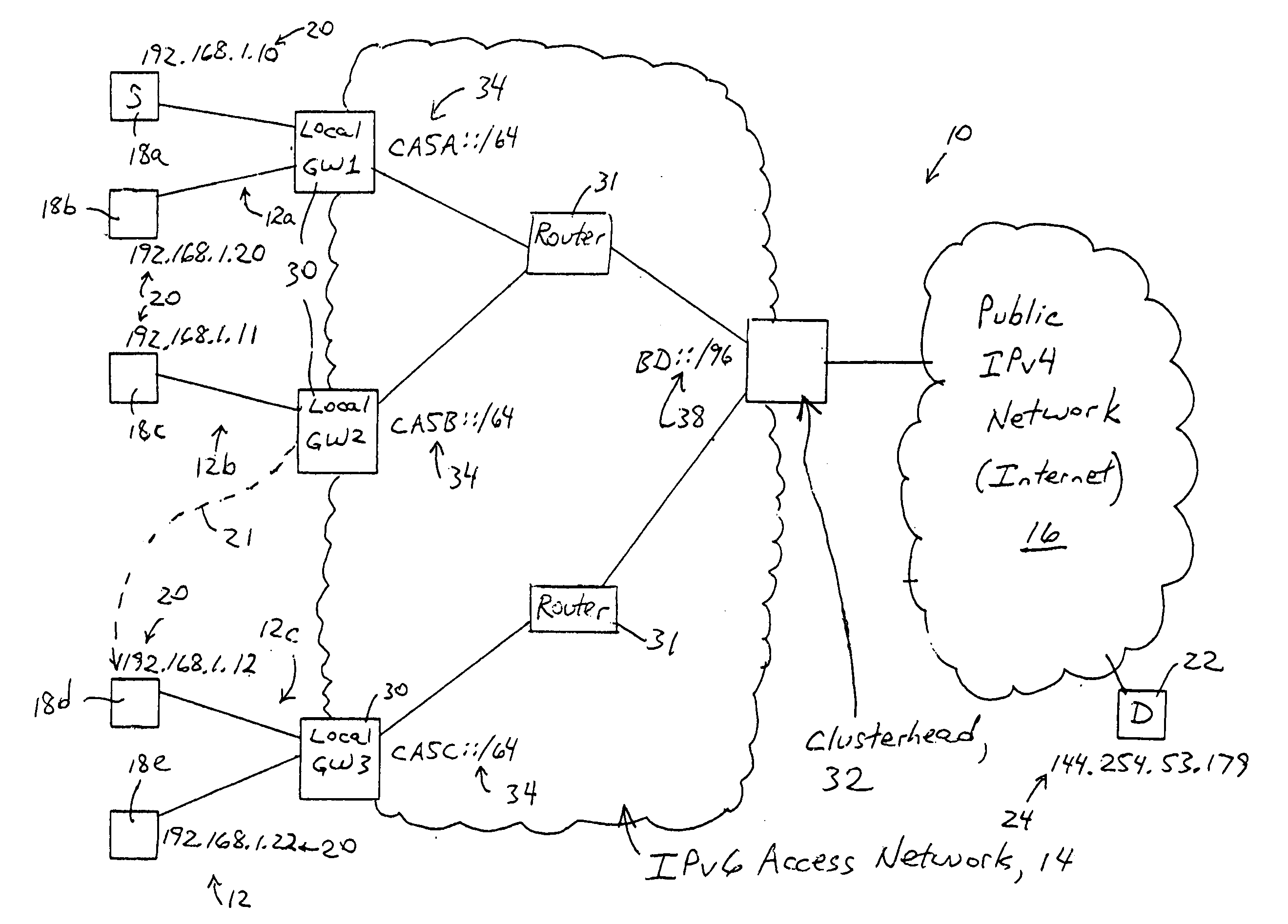
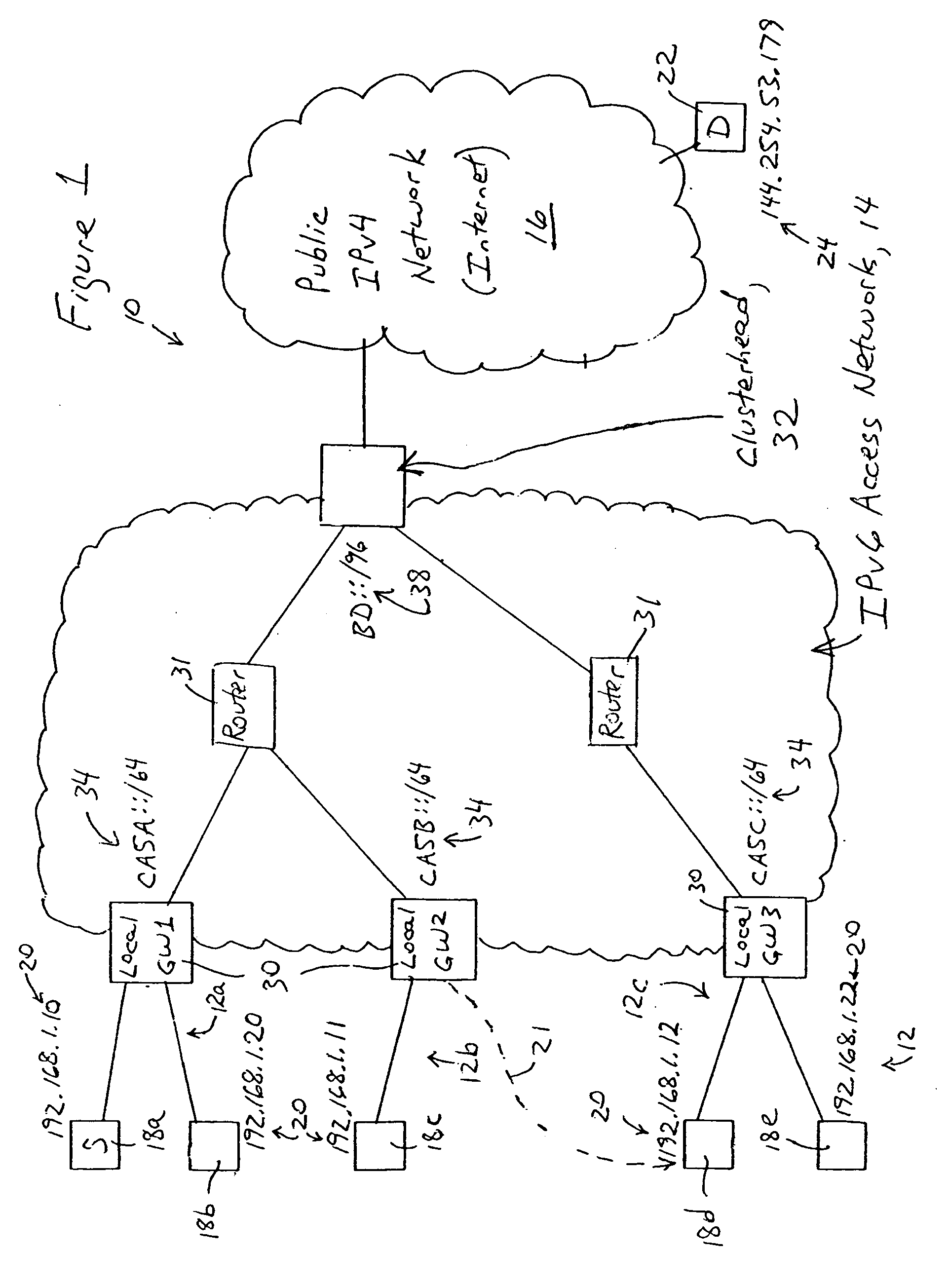
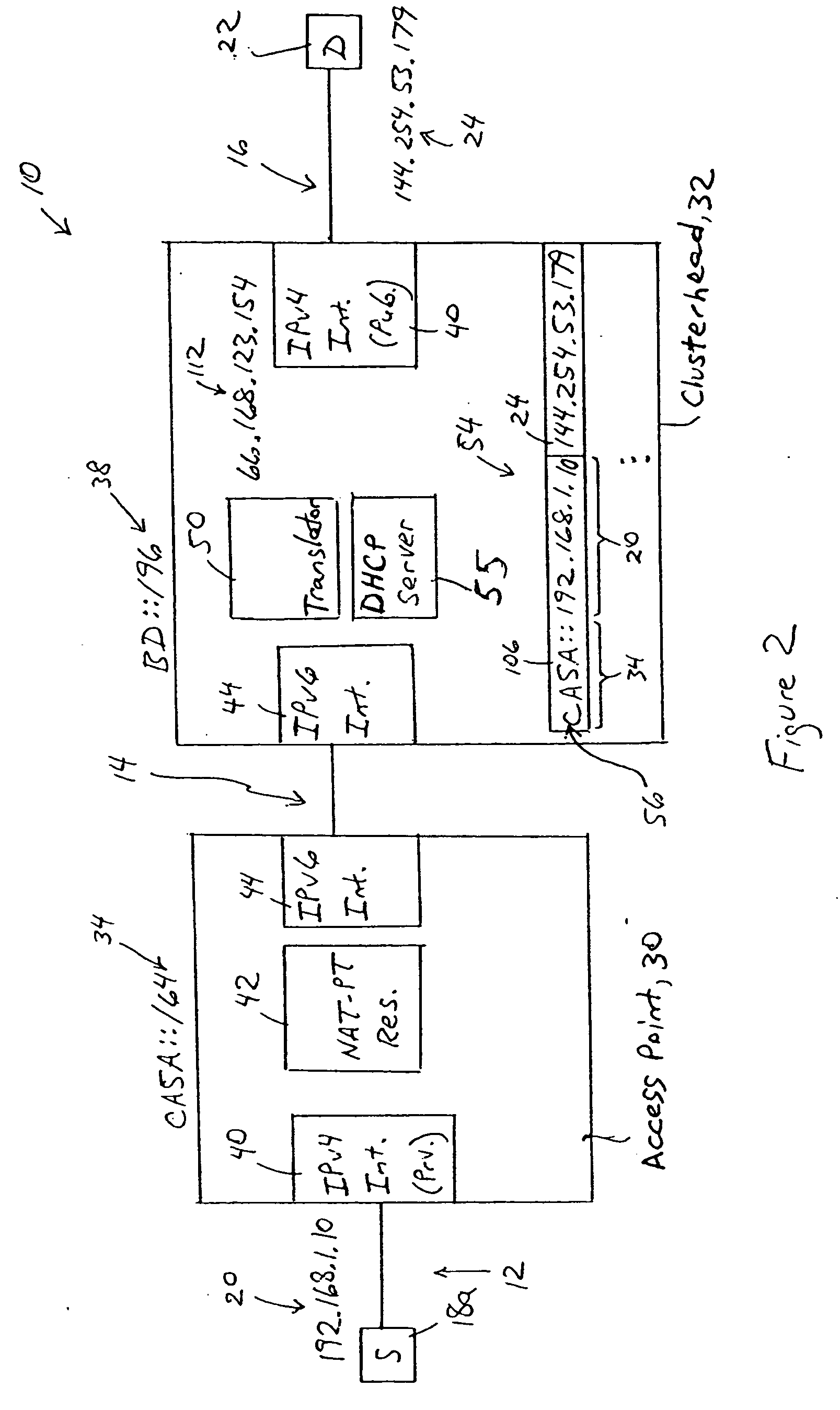
Access network clusterhead for providing local mobility management of a roaming IPv4 node
InactiveUS20060227792A1Stay connectedTime-division multiplexData switching by path configurationAccess networkMobility management
An IPv4 host is able to maintain connectivity within an access network while moving among access points of the access network, based on receiving a unique assigned IPv4 address from a clusterhead of the access network. Any DHCP request by the IPv4 host is sent via the connecting access point to the clusterhead. The clusterhead, providing connectivity for hosts in the access network to a wide area network based on respective entries, assigns the IPv4 address to the IPv4 host, based on storing an entry including the IPv4 address and an IP-based identifier of the connecting access point, and sends a DHCP response to the IPv4 host via the connecting access point. A second DHCP request from the IPv4 host to a second access point causes the clusterhead to update the entry with the second access point identifier, enabling the IPv4 host to continue use of the assigned IPv4 address.
Owner:CISCO TECH INC
Webpage clustering method based on node property label propagation
InactiveCN102768670AEfficient miningPremium DiggingSpecial data processing applicationsFeature vectorRound complexity
The invention provides a webpage clustering method based on node property label propagation, which comprises the following steps: structuring a topological structure diagram model according to the link relationship of the webpage; building property feature vector for each node in the diagram model; initializing node labels in the network; iteratively updating the node labels according to the topological structure and the node property; and defining the condition of stopping updating the node labels. With the method, effective and high-quality webpage clustering can be realized within the nearly linear time only by extracting the topological relationship of the internet and the property information marking webpage characteristics without knowing priori knowledge such as the quantity and the scale of webpage groups and the like or predefining parameters such as the critical value and the like. The algorithm is simple in concept, easy to understand and realize and lower in time complexity, and can generate high-quality network clustering result, so as to apply to large-scale internet.
Owner:HARBIN ENG UNIV
Methods and systems for exchanging reachability information and for switching traffic between redundant interfaces in a network cluster
InactiveUS20040078481A1Quick switchShorten the timeDigital computer detailsData switching networksComputer networkRouting table
Methods and systems for exchanging reachability information and for switching between redundant interfaces in a network cluster are disclosed. Nodes in the network cluster are connected via redundant links and exchange reachability messages at periodic intervals. Each node includes a kernel routing table used to route messages and a reachability application routing table for storing reachability information used to update entries in the kernel routing table. Each node executes a predetermined algorithm for selecting entries in the reachability application routing table to be written to the kernel routing table.
Owner:TEKELEC GLOBAL INC
Scheduling method and scheduling information synchronizing method in wireless ad hoc network
InactiveUS20100268825A1Reducing rescheduling timePower managementNetwork traffic/resource managementWireless ad hoc networkCluster based
A decentralized scheduling method in a wireless ad hoc network is provided which includes grouping nodes in the network cluster by cluster, determining a cluster head of each cluster, and sequentially performing scheduling cluster by cluster. Accordingly, it is possible to provide an efficient cluster-based scheduling method which is quickly adapt to changes and reduces power consumption.
Owner:IND ACADEMIC CORP FOUND YONSEI UNIV +1
Wireless sensor network data transmission method based on LEACH protocol
InactiveCN107529201AImprove transmission efficiencyDelayed deathNetwork topologiesHigh level techniquesLine sensorWireless sensor networking
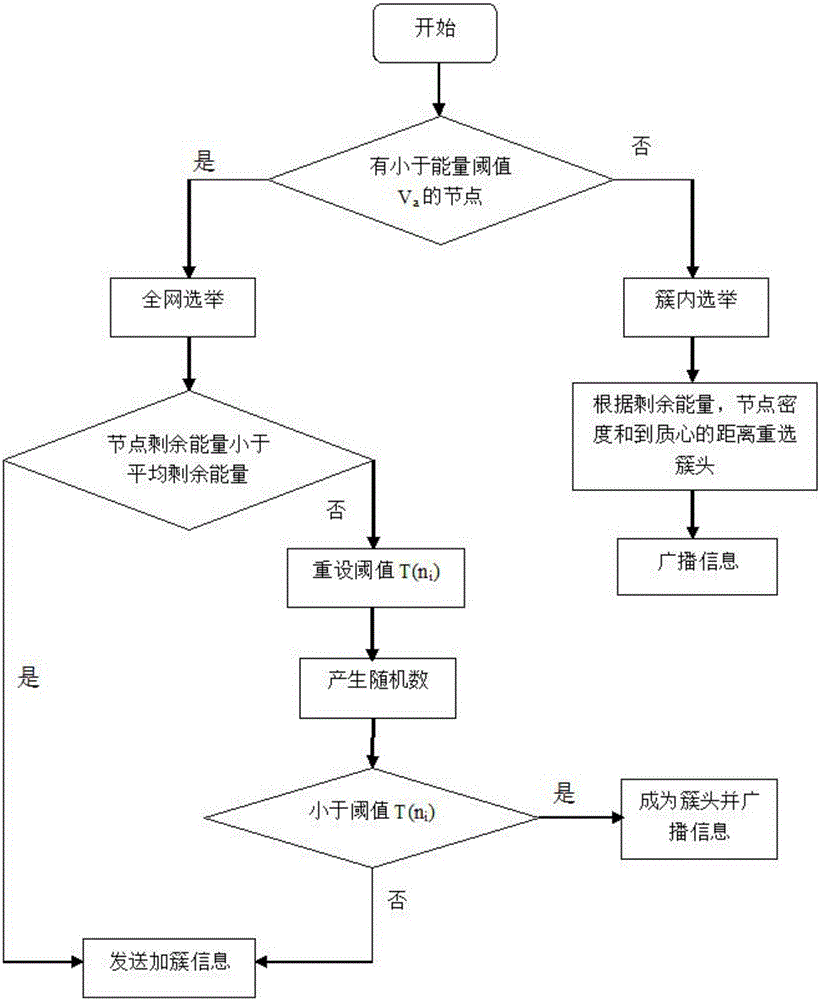
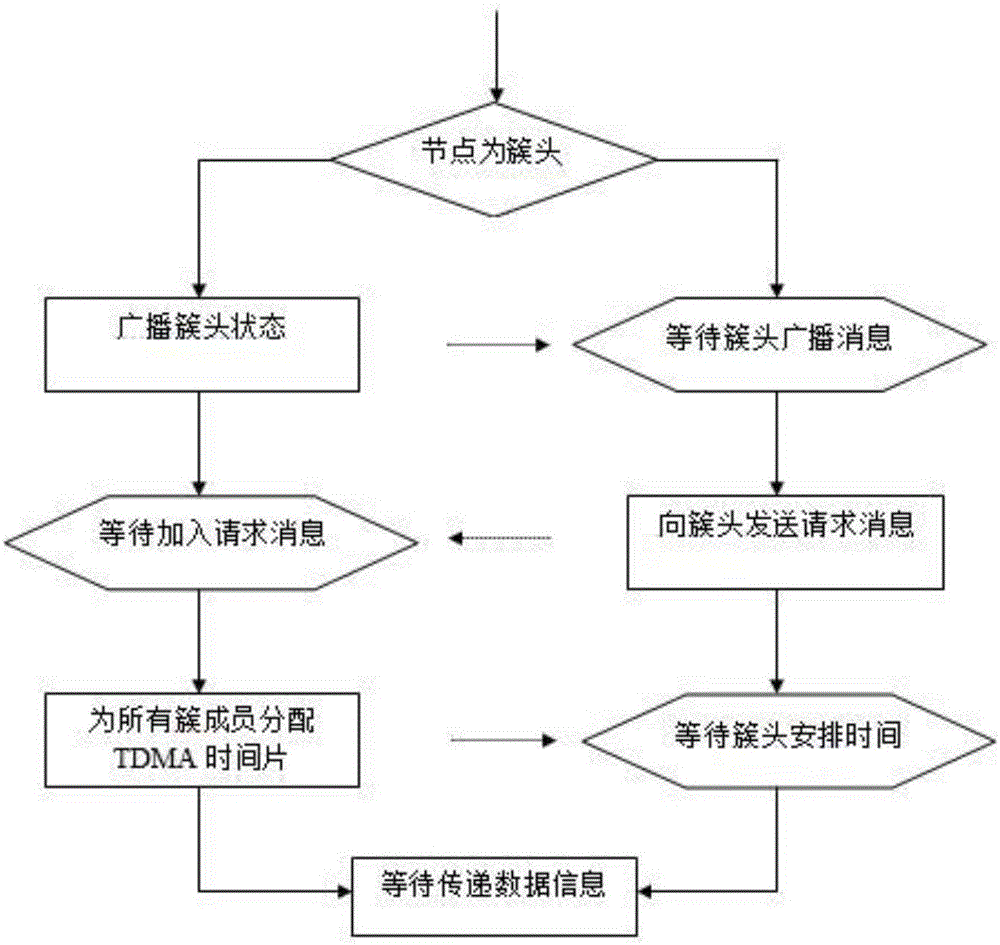
The invention belongs to the technical field of a wireless sensor network system, and discloses a wireless sensor network data transmission method based on a LEACH protocol. By setting an energy threshold Va, a data transmission process is divided into whole-network cluster head election and in-cluster cluster head election; when energy is smaller than the energy threshold Va in all cluster heads, a whole-network election method is adopted, so that each node in a region has the chance to become a cluster head; and when energy is greater than the energy threshold Va in all the cluster heads, in-cluster election is carried out, new in-cluster cluster heads are selected according to constraint conditions of residual energy, a node density and a distance to an in-cluster mass center, a structure of a cluster is unchanged, and a non-cluster-head node is elected in the cluster to be used as a new cluster head. According to the invention, by an optimal cluster head rate of a wireless sensor network, all subsequent simulation experiments can be carried out, and various practice scenes can be more accurately and reliably simulated.
Owner:WUHAN ZHONGYUAN ELECTRONICS INFORMATION
Method for Distributed Hierarchical Admission Control across a Cluster
InactiveUS20080008090A1Consumption rateReduce probabilityError preventionTransmission systemsAdmission control algorithmClient-side
A network cluster is provided herein having a plurality of cluster members. In order to control the admission of client requests sent to the cluster, one member of the cluster is elected “reservation coordinator.” The reservation coordinator runs a reservation algorithm for controlling the distribution of rate capacity across members of the cluster. For example, each member of the cluster may reserve some amount of rate from the coordinator to allow for passing of client requests. To ensure that each member is provided with the appropriate rate capacity, each member of the cluster runs an estimation algorithm to determine whether or not additional rate capacity should be reserved from the reservation coordinator, or released back into the cluster for redistribution. The estimation algorithm is run in real-time and allows the admission control algorithm to adapt to changes in rate distribution.
Owner:IBM CORP
Multichannel video play and large screen display method
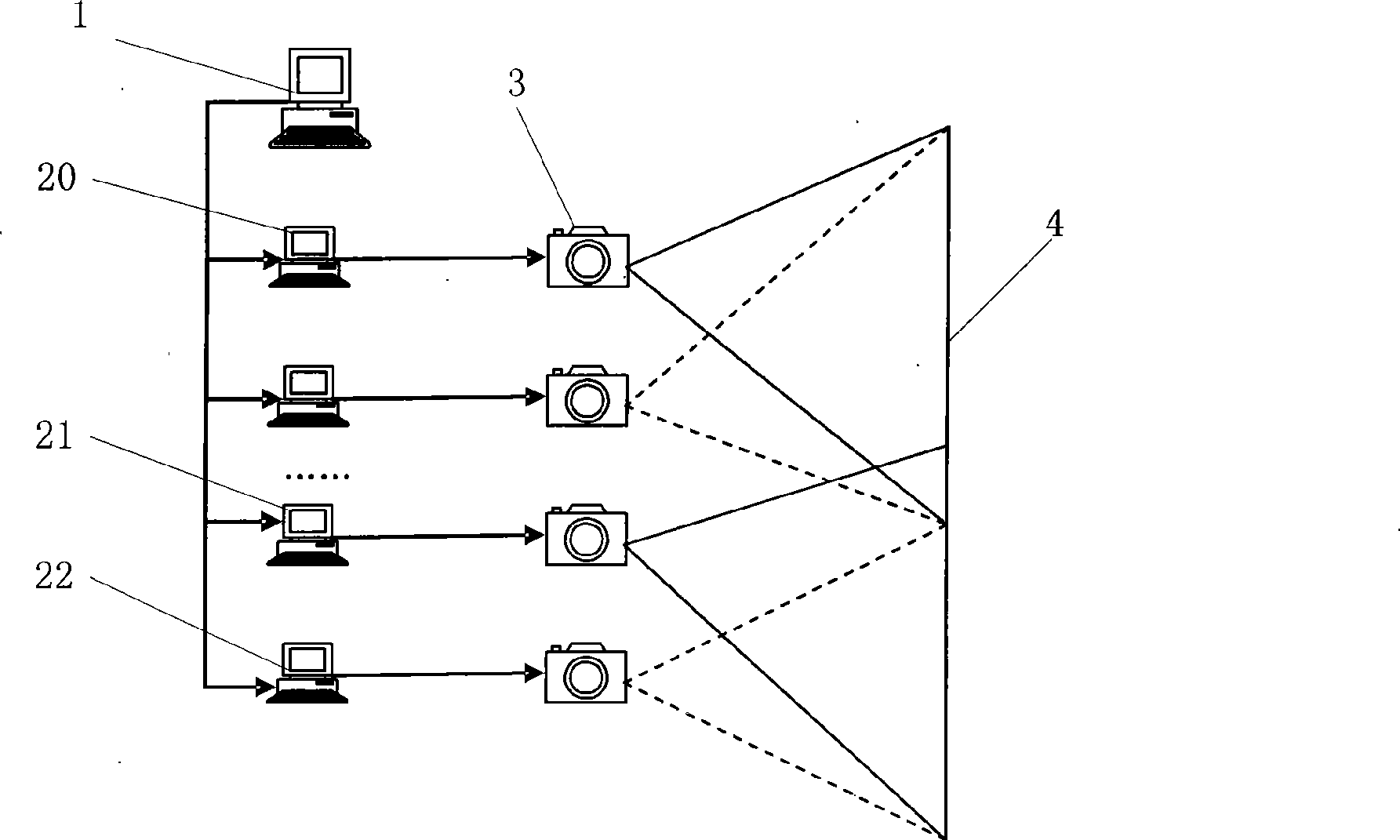
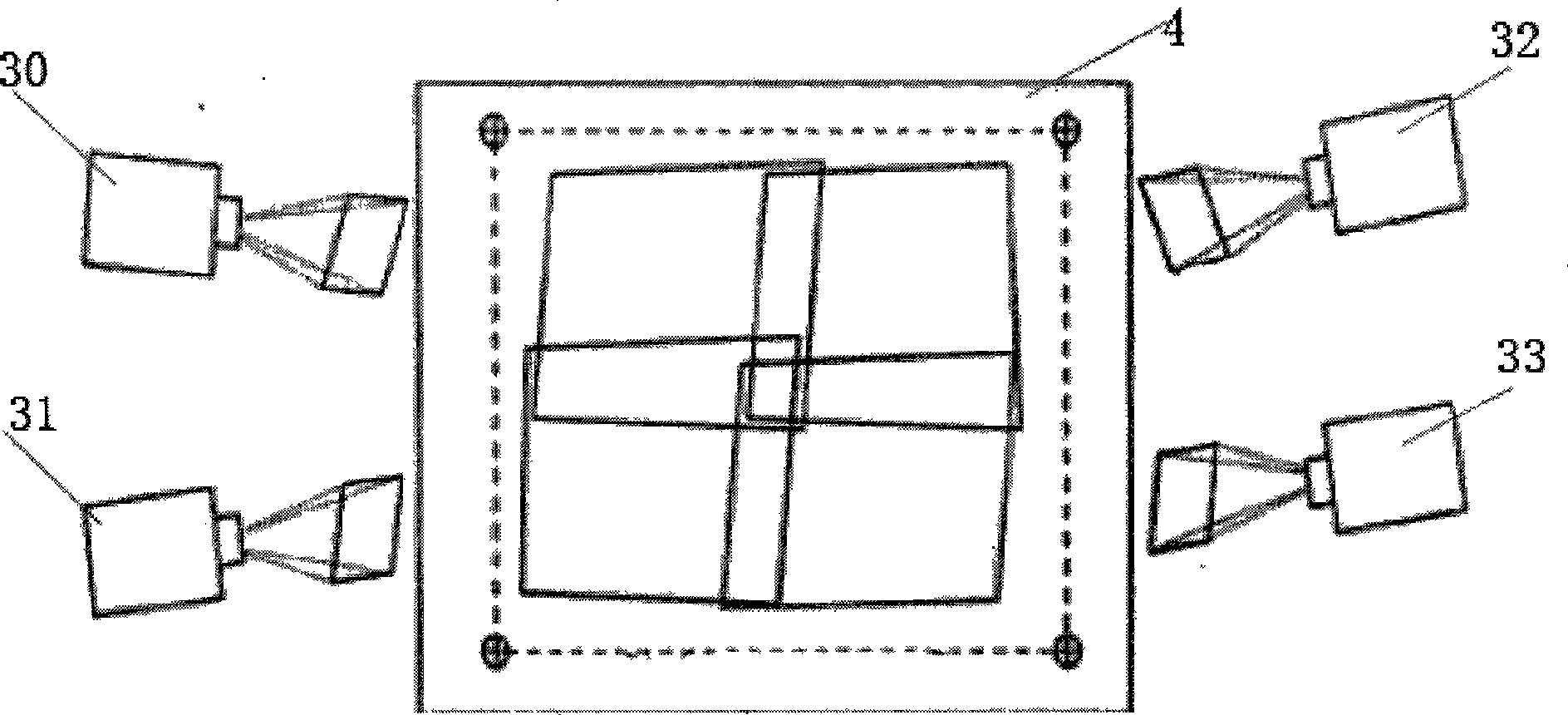
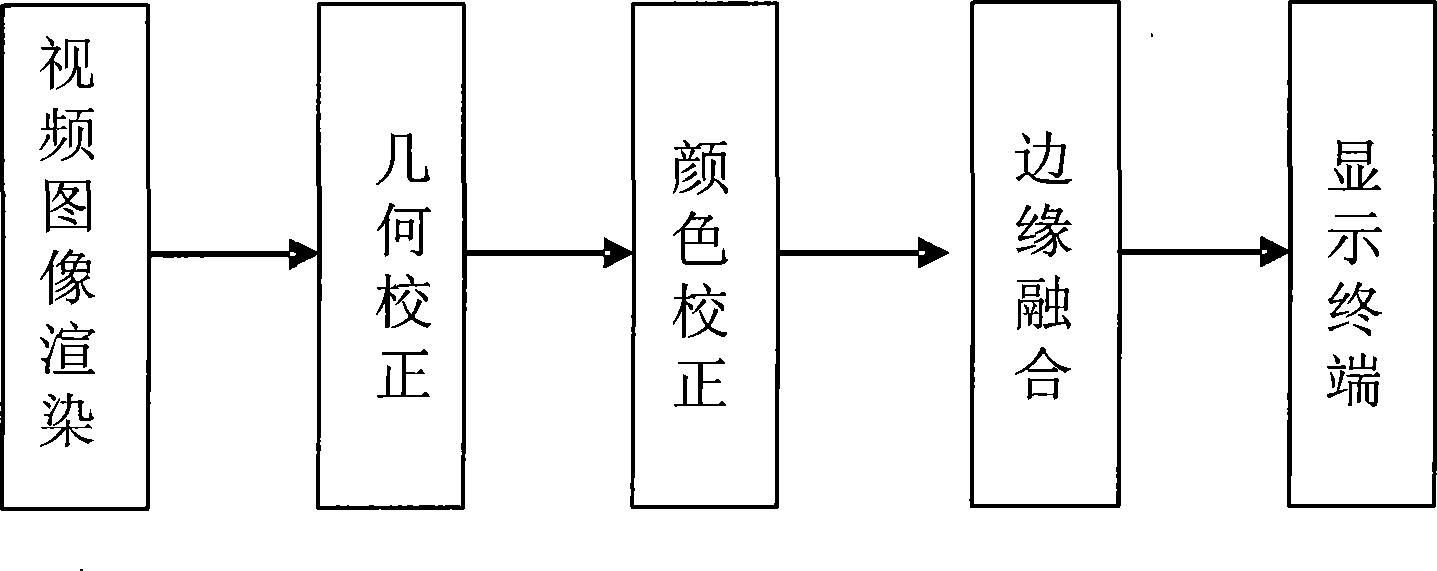
InactiveCN101442653AAvoid restrictionsSolve the effect of brightnessTelevision signal transmission by single/parallel channelsSteroscopic systemsLarge screenOutput device
The invention discloses a multi-channel video playing and large-screen display method, which comprises the following steps: (1) starting a main control computer and a player in a computer network cluster; (2) opening multi-channel video playing software, establishing a video file which needs to be played, and selecting an operating mode by the multi-channel video playing software according to information such as configuration parameters, the attribute of the video file, and the attribute of output equipment; (3) entering a blocking mode for the multi-channel video playing software which operates on the player, synchronously playing the video file at the position specified by the main control computer until the main control computer is started to send an instruction of beginning playing, and continuously playing, and outputting images generated by the player to display equipment, and finally outputting the images to a large screen to be spliced into an intact picture; and (4) when the main control computer resends a synchronous instruction of playing, resynchronizing the playing position of the video file on the multi-channel video playing software which operates on the player until the playing of a video is finished or a user manually exits from the video playing software.
Owner:BEIHANG UNIV
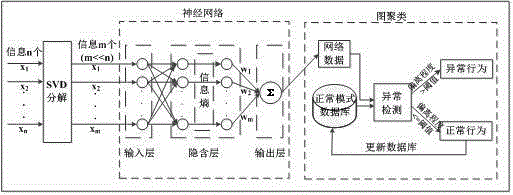
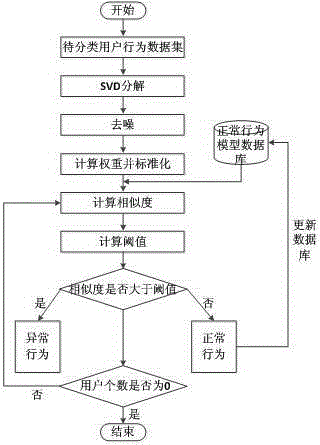
User abnormal behavior detection method based on neural network clustering
ActiveCN105224872AFacilitate accurate diagnosisImprove signal-to-noise ratioCharacter and pattern recognitionPlatform integrity maintainanceHidden layerNerve network
The invention discloses a user abnormal behavior detection method based on neural network clustering. The method comprises: firstly, performing SVD decomposition and denoising on a behavior data set matrix of a user, and inputting the denoised matrix to an input layer of a neural network, and then calculating weight of all attributes of each user in a hidden layer of the neural network, and standardizing the weight, outputting the weight in an output layer, and finally respectively calculating similarity value of each user and each user in a normal behavior model database and a threshold value, if the similarity value is larger than the threshold value, behavior being abnormal behavior, and carrying out corresponding prompt and precautionary measures, otherwise, the behavior being normal behavior, and combining the behavior in the normal model database to upgrade the database in real time. Through cooperation of each part, the method effectively realizes high detection rate and low false alarm rate.
Owner:HENAN UNIV OF SCI & TECH
Server and method for deploying virtual machines in network cluster
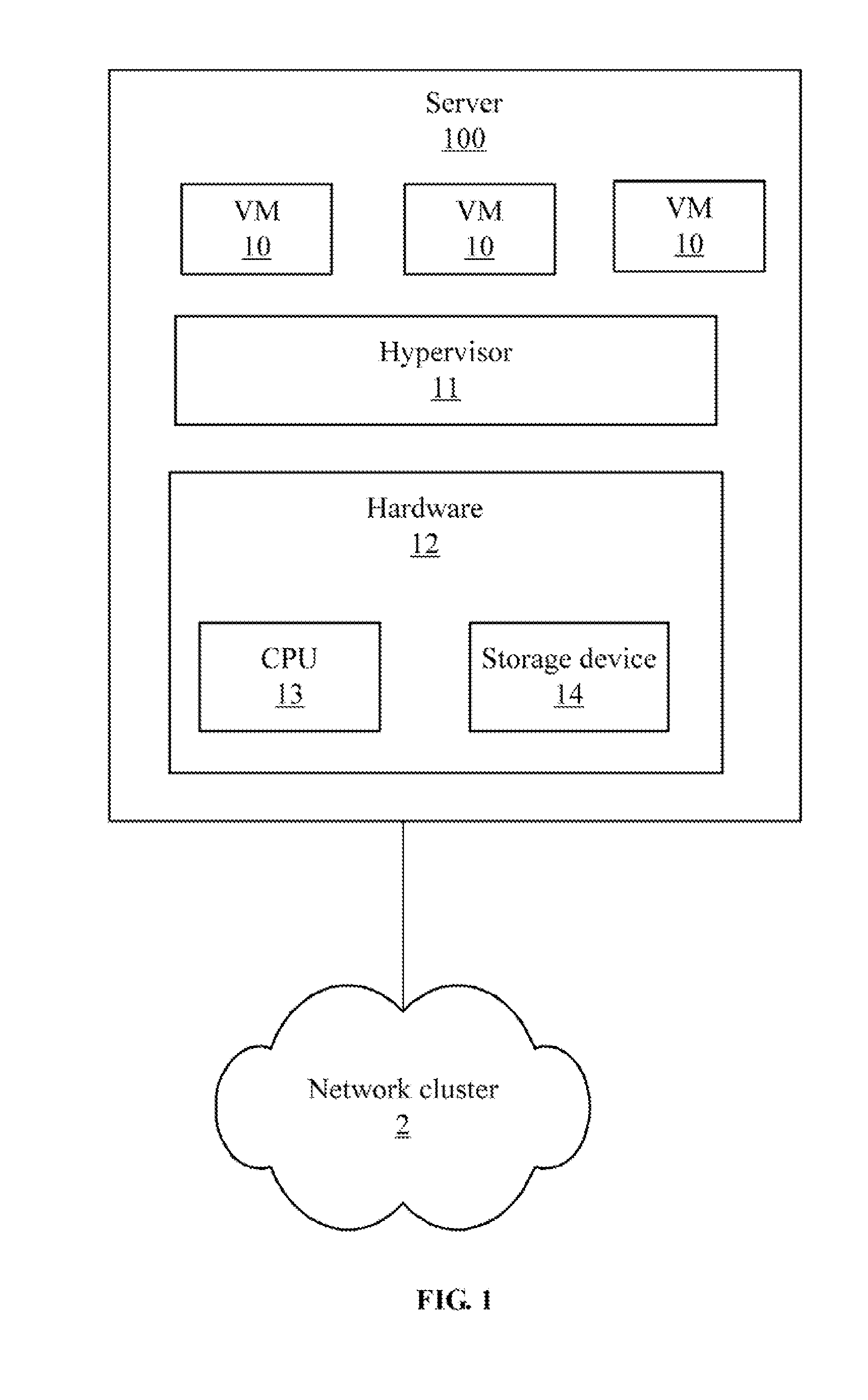
InactiveUS20130219391A1Software simulation/interpretation/emulationMemory systemsIp addressResource utilization
A server for deploying virtual machines (VMs) in a network cluster is provided. The server sets template information for creating VMs, creates a VM based on the template information, receives an IP address assigned to the VM by a dynamic host configuration protocol (DHCP), and deploys the VM into the network cluster. The server then monitors a resource utilization ratio of the network cluster. When the ratio of the network cluster is more than a first preset ratio, the server creates a new VM based on the template information and deploys the new created VM into the network cluster. When the ratio of the network cluster is less than a second preset ratio , the server decreases available resource of the network cluster by suspending or deleting a created VM in the network cluster.
Owner:HON HAI PRECISION IND CO LTD
Virtual root bridge
InactiveUS7944853B2Assess restrictionData switching by path configurationComputer networkEngineering
Owner:TELEFON AB LM ERICSSON (PUBL)
Virtual root bridge
ActiveUS20070159983A1Assess restrictionData switching by path configurationDistributed computingNetwork clustering
Owner:TELEFON AB LM ERICSSON (PUBL)
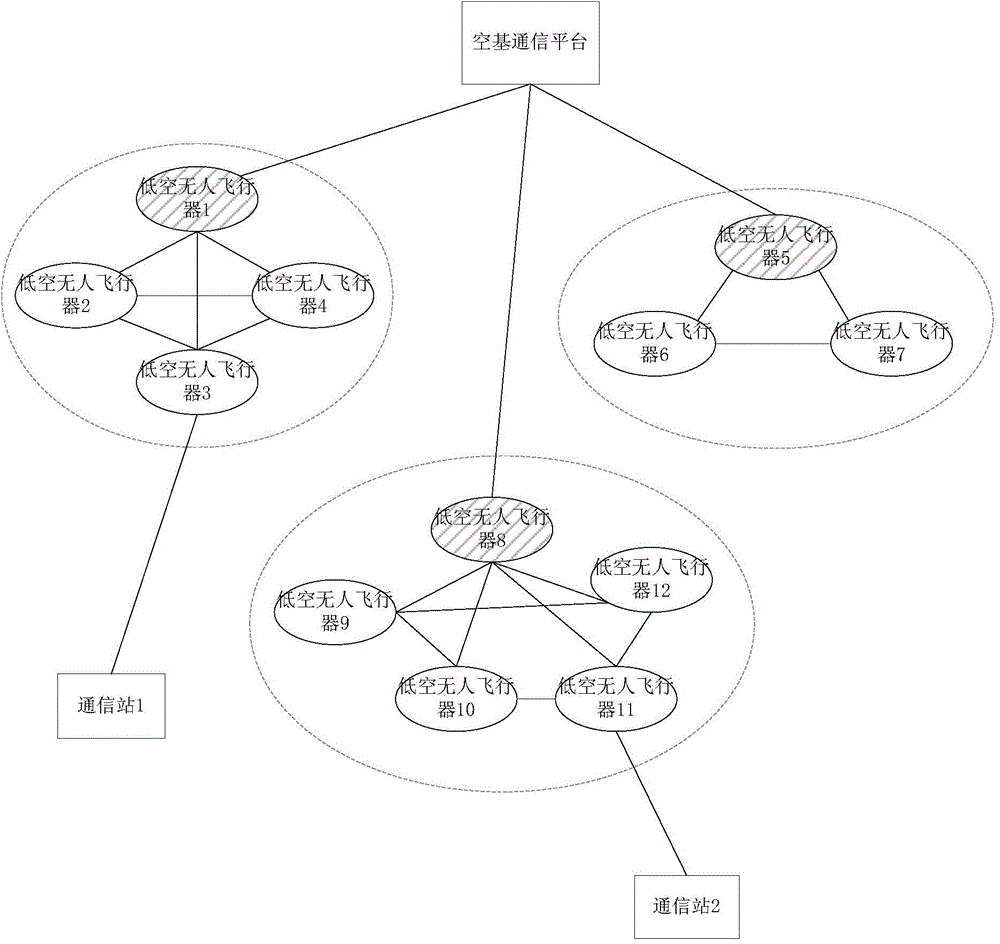
Measurement and control communication method and system based on low-altitude unmanned aerial vehicle self-network
InactiveCN104581862AAvoid congestionVersatilityNetwork topologiesCommunications systemInformation networks
The invention provides a measurement and control communication method and a measurement and control communication system based on a low-altitude unmanned aerial vehicle self-network, which are wide in acting coverage range and can realize cooperative matching and dynamic stabilization. The method comprises the steps of performing self-network clustering on low-altitude unmanned aerial vehicles at different heights in different regions; respectively linking the low-altitude aerial vehicles to an airborne communication platform and a ground communication terminal by taking a cluster as a unit; regularly updating and maintaining clusters in the low-altitude unmanned aerial vehicle self-network. The system comprises the airborne communication platform and a plurality of low-altitude unmanned aerial vehicles; the space-based communication platform is communicated with the low-altitude unmanned aerial vehicles, the ground communication terminal and other airborne communication platforms; the low-altitude unmanned aerial vehicles carry task loads and are used for being communicated with the airborne communication platform, the ground communication terminal and other low-altitude unmanned aerial vehicles. The airborne communication platform and all the self-networked low-altitude unmanned aerial vehicles are organized to form a two-layer composite three-dimensional information network. Therefore, the integral efficiency of the system is improved, and the stability is high.
Owner:NO 63655 TROOPS OF THE CHINESE PEOPLES LIBERATION ARMY
Wireless sensor network energy conservation method based on redundancy controlling and clustering routing
InactiveCN103024814AGive full play to comprehensive advantagesImprove performancePower managementEnergy efficient ICTBalancing networkClustered data
The invention discloses a wireless sensor network energy conservation method based on redundancy controlling and clustering routing. The wireless sensor network energy conservation method combines a probability estimation based redundant node control algorithm with a node energy consumption balancing clustering routing protocol which considers multiple factors to realize energy conservation, wherein the probability estimation based redundant node control algorithm includes a method for defining and finding a redundant node and sleep of the redundant node, and the node energy consumption balancing clustering routing protocol considering multiple factors includes LEACH (low energy adaptive clustering hierarchy) based network clustering of introduced clustered factors, redundant data fusion, cluster data forwarding with distance and angle comprehensively considered, and confirmation of cluster rotating period. On the premise of meeting network connectivity degree and cover degree, the wireless sensor network energy conservation method based on redundancy controlling and clustering routing balances network load and improves energy efficiency of nodes to the greatest extent, so that the purpose for prolonging network service life is achieved.
Owner:PLA UNIV OF SCI & TECH
Controlling With Rights Objects Delivery Of Broadcast Encryption Content For A Network Cluster From A Content Server Outside The Cluster
InactiveUS20090016533A1Digital data processing detailsAnalogue secracy/subscription systemsAuthorizationNetwork clustering
Owner:INT BUSINESS MASCH CORP
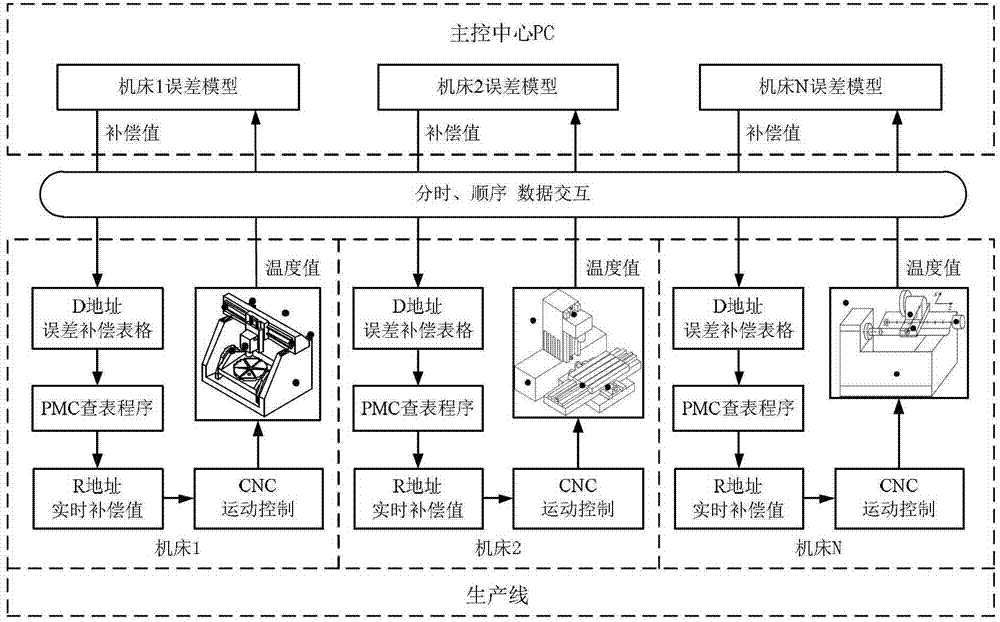
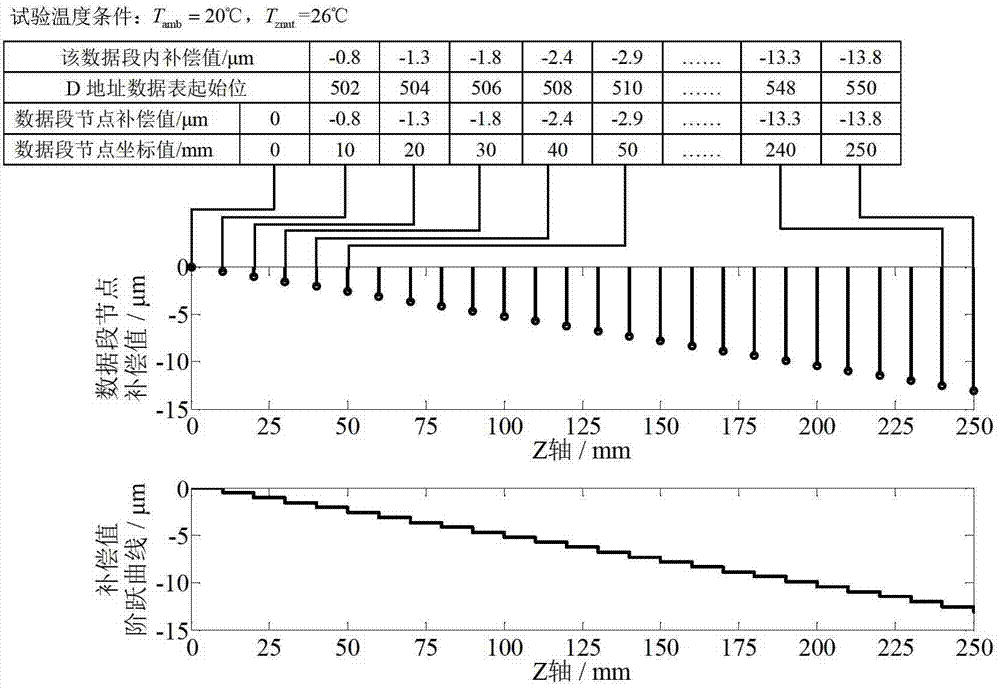
Network cluster-control-based numerical control machine tool error real-time compensation system and compensation method
ActiveCN103048968AImplementation statusLow costComputer controlSimulator controlNumerical controlData acquisition
The invention discloses a network cluster-control-based numerical control machine tool error real-time compensation system and a network cluster-control-based numerical control machine tool error real-time compensation method. The compensation system comprises a hardware part and a software part built in hardware, wherein the hardware part comprises a master control center personal computer (PC), a router, a built-in Ethernet port or a personal computer memory card international association (PCMCIA) Ethernet card, a temperature sensor and a temperature data acquisition card; and the software part comprises a temperature acquisition module, an error modeling and calculating module, a cluster-control compensation module and a machine tool state network monitoring module. By the compensation system and the compensation method, error real-time compensation and working state information monitoring can be performed on a plurality of numerical control machine tools on a production line at the same time; the movement precision of the numerical control machine tools is improved in batches; and therefore, the compensation efficiency and the final machining precision are greatly improved.
Owner:SHANGHAI JIAO TONG UNIV
Wireless ad-hoc emergency communication network based on network cluster and message ferrying
InactiveCN102368863AImprove scalabilityReduce complexityNetwork topologiesHigh level techniquesEmergency rescueComputer science
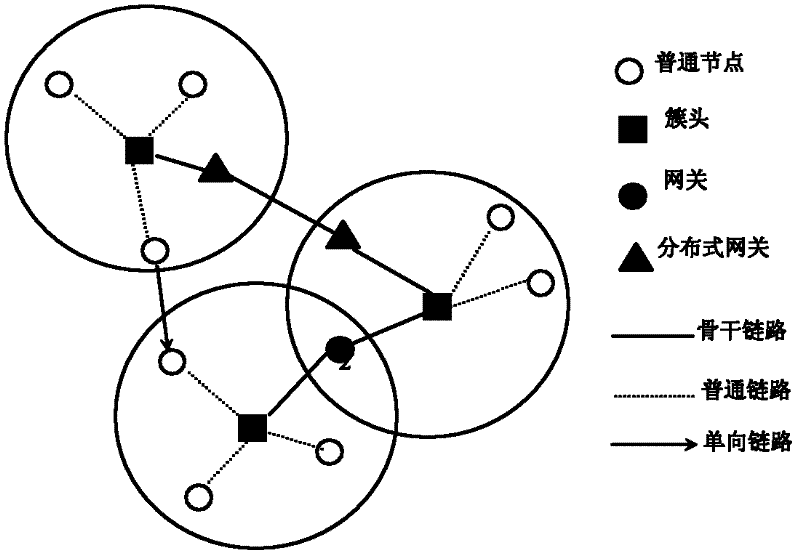
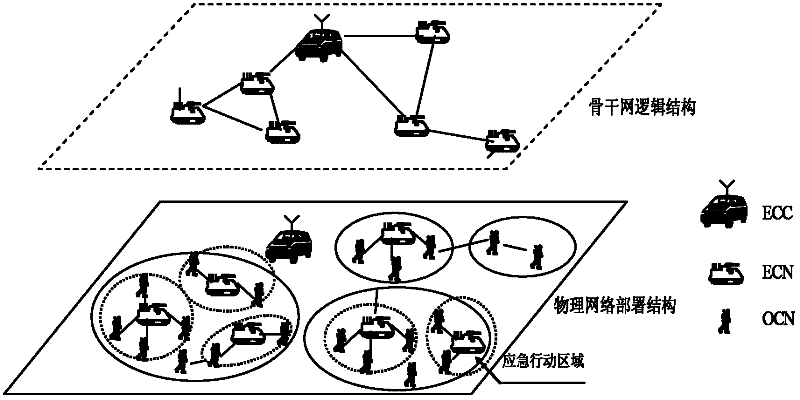
The invention discloses a wireless ad-hoc emergency communication network based on network cluster and message ferrying. The network comprises an emergency on-site command center (ECC), multiple emergency rescue special communication nodes (ECNs), a great quantity of ordinary communication nodes (OCNs) and a moderate number of ferrying nodes, wherein the ECC can be used as a command coordination node of the whole emergency communication network and a cluster node of the ECNs in the coverage area of the ECC; the ECNs can be used as cluster nodes of the OCNs in the coverage area of the ECNs; the cluster nodes and gateway nodes are interconnected to form wireless backbone networks (WBNs), the OCNs are connected with handy WBNs to which the OCN belong; and relay communication can be realized among the OCNs in different WBNs through the ferrying nodes. The communication network provided by the invention dynamically integrates the network cluster mechanism and the message ferrying mechanism, thus enhancing the reliability and timeliness of information delivery.
Owner:PLA UNIV OF SCI & TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com