Security defensive system and defensive method based on software-defined network
A software-defined network and security defense technology, applied in the field of security defense systems to reduce interference, protect system security, and ensure network service quality
Active Publication Date: 2014-09-03
WUHAN UNIV
View PDF6 Cites 51 Cited by
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Therefore, these traditional network security technologies cannot well solve the problem that this paper focuses on: detecting harmful virtual machines in time, and blocking them when they try to connect with other virtual machines, preventing attacks from happening
However, due to the use of the results of user-level programs, misjudgments may be caused by tampering with the results
Method used
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
View moreImage
Smart Image Click on the blue labels to locate them in the text.
Smart ImageViewing Examples
Examples
Experimental program
Comparison scheme
Effect test
Embodiment
[0041] The embodiments of the present invention are described in detail below. This embodiment is implemented on the premise of the technical solution of the present invention, and detailed implementation methods and specific operating procedures are provided, but the protection scope of the present invention is not limited to the following implementation example.
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
Login to View More PUM
 Login to View More
Login to View More Abstract
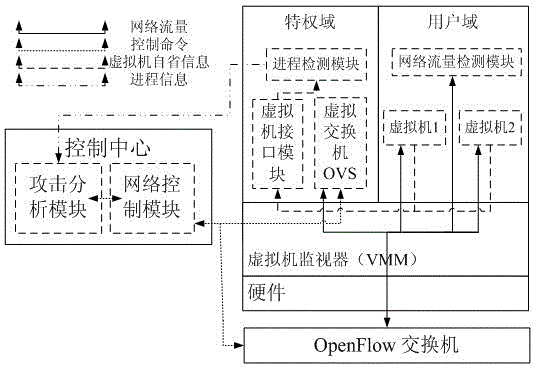
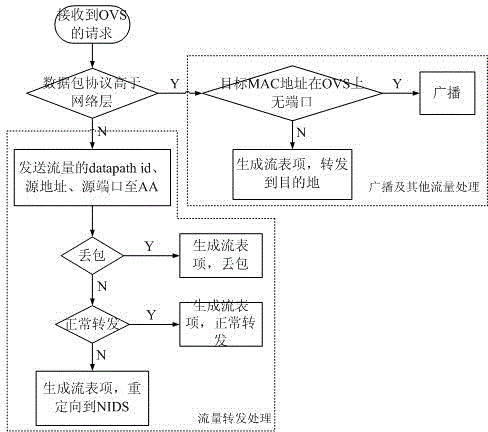
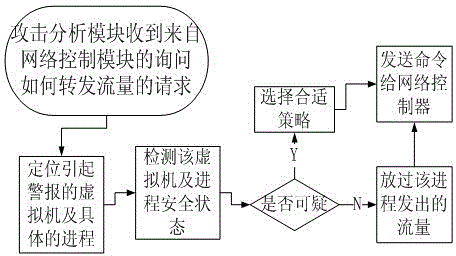
The invention relates to the technical field of computer security, and in particular to a security defensive system and a defensive method based on a software-defined network. The security defensive system comprises a network control module, an attack analysis module, a progress detection module and a network flow detection module, wherein the network control module is used for intercepting a network data packet between virtual machines and used for forwarding acquired flow information to the attack analysis module; the attack analysis module is used for receiving flow information from the virtual machines of the network control module, used for scheduling the progress detection module to detect whether the progress is questionable, and used for scheduling the network flow detection module to execute deep detection on questionable flow if necessary. Aiming at expansion of virtual switches for flow forwarding among virtual machines in a conventional virtual machine server, the invention discloses a deep defensive system which is capable of intercepting, detecting and reorienting the flow, and the purposes of preventing and stopping attack behaviors of virtual machines of a network cluster are achieved.
Description
[0001] technical field [0002] The present invention relates to a defense system in the field of computer security, in particular to a security defense system and defense method based on a software-defined network. Background technique [0003] There are many technologies that focus on detecting infected virtual machines and protecting other virtual machines in the cloud from them, such as firewalls and intrusion detection systems (Intrusion Detection System, IDS). At the network layer, traditional network firewalls and network-based intrusion detection systems (Network-based Intrusion Detection System, NIDS) are built in the "monitored network - outside the firewall" mode. This mode is not suitable for the situation where the infected virtual machine and the attack target are in the same cloud host, because the information collected by the network firewall and NIDS must be the information entering and leaving the monitored network. At the host level, personal firewalls, H...
Claims
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
Login to View More Application Information
Patent Timeline
 Login to View More
Login to View More IPC IPC(8): H04L29/06
Inventor 崔竞松郭迟张萌田昌友
Owner WUHAN UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com