Security vulnerability assessment method, system and equipment for cigarette industrial control system
An industrial control system and control system technology, applied in the cigarette industry, can solve the problems of high cost of simulation environment, incomplete and inaccurate security vulnerability assessment, etc., and achieve the effect of reducing the cost of enterprises
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
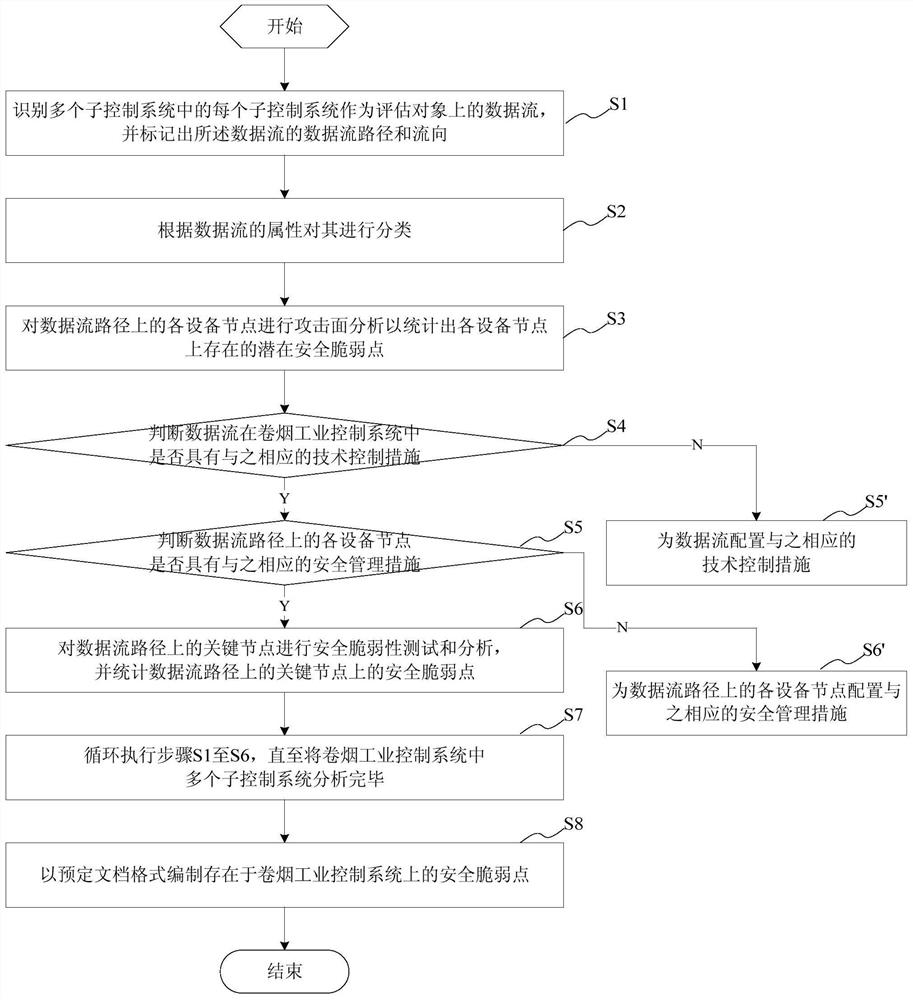
[0040]This embodiment provides a security vulnerability assessment method of a cigarette industrial control system, the cigarette industrial control system includes a plurality of sub-control systems, and the security vulnerability assessment method of the cigarette industrial control system includes the following steps:
[0041] identifying each of the plurality of sub-control systems as a data flow on the evaluation object, and marking the data flow path and direction of the data flow;
[0042] classifying said data stream according to its attributes;
[0043] Analyzing the attack surface of each device node on the data flow path to calculate the potential security vulnerabilities existing on each device node;
[0044] Judging whether the data flow has corresponding technical control measures in the cigarette industrial control system; if yes, perform the next step, if not, configure corresponding technical control measures for the data flow;
[0045] Judging whether each d...
Embodiment 2
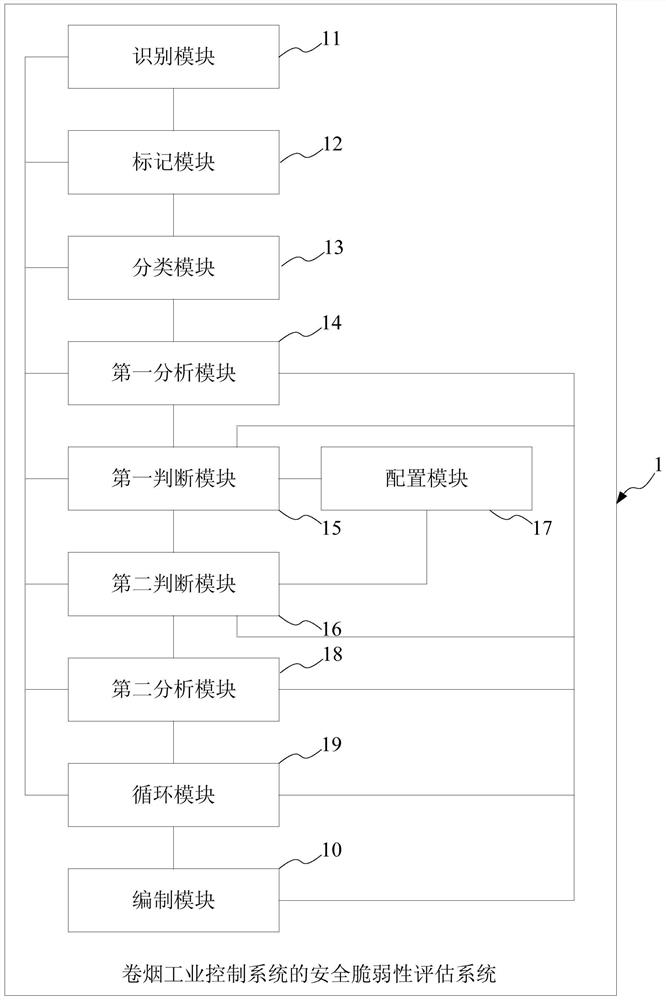
[0085]This embodiment provides a security vulnerability assessment system of a cigarette industrial control system, the cigarette industrial control system includes multiple sub-control systems, and the security vulnerability assessment system of the cigarette industrial control system includes:
[0086] an identification module, configured to identify each of the plurality of sub-control systems as a data flow on an evaluation object;
[0087] A marking module, connected to the preprocessing module, for marking the data flow path and flow direction of the data flow;
[0088] A classification module, connected to the marking module, for classifying the data stream according to its attributes;
[0089] The first analysis module is connected with the identification module, the marking module, and the classification module, and is used to analyze the attack surface of each device node on the data flow path to count the potential security vulnerabilities existing on each device no...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com