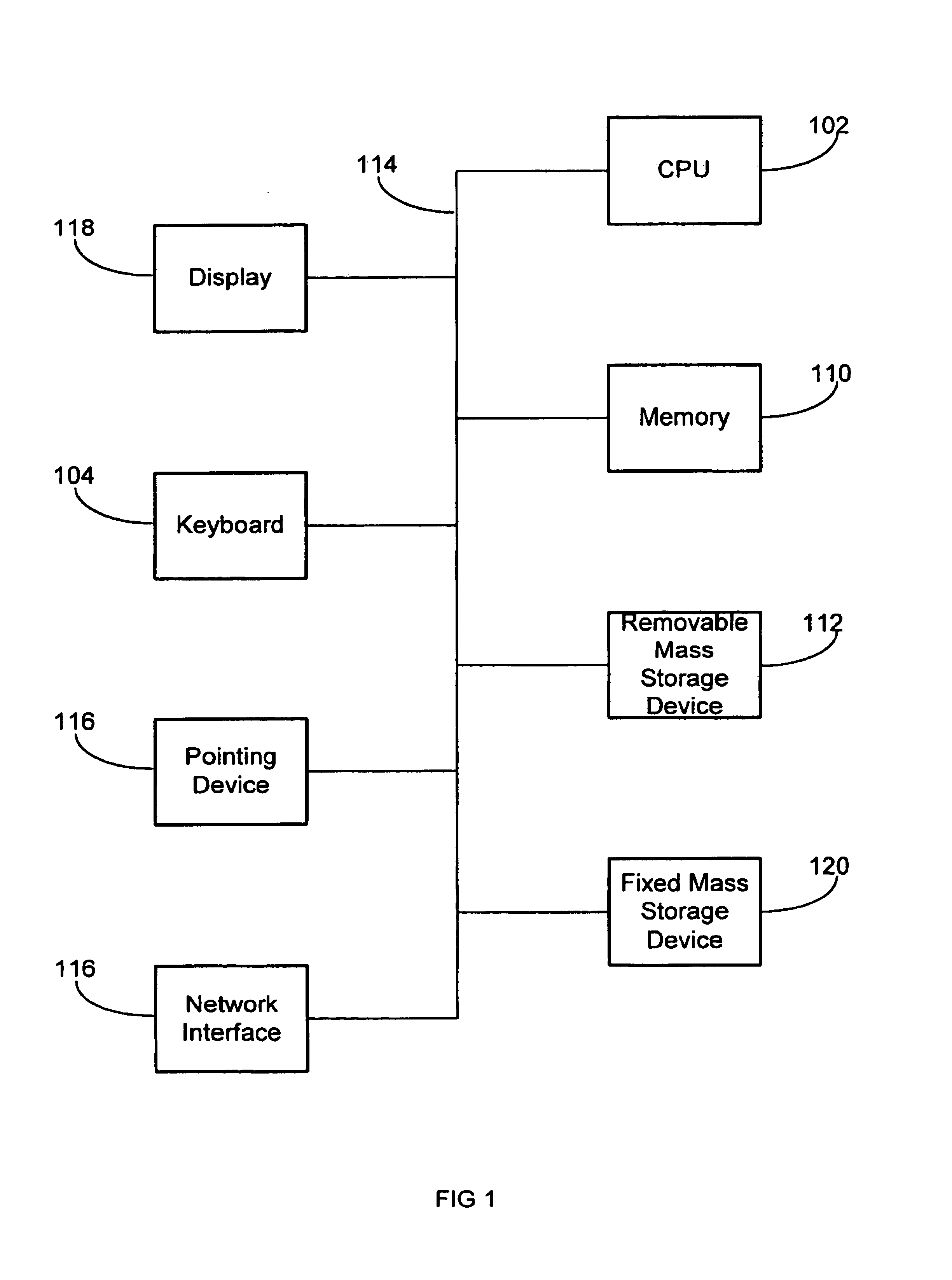
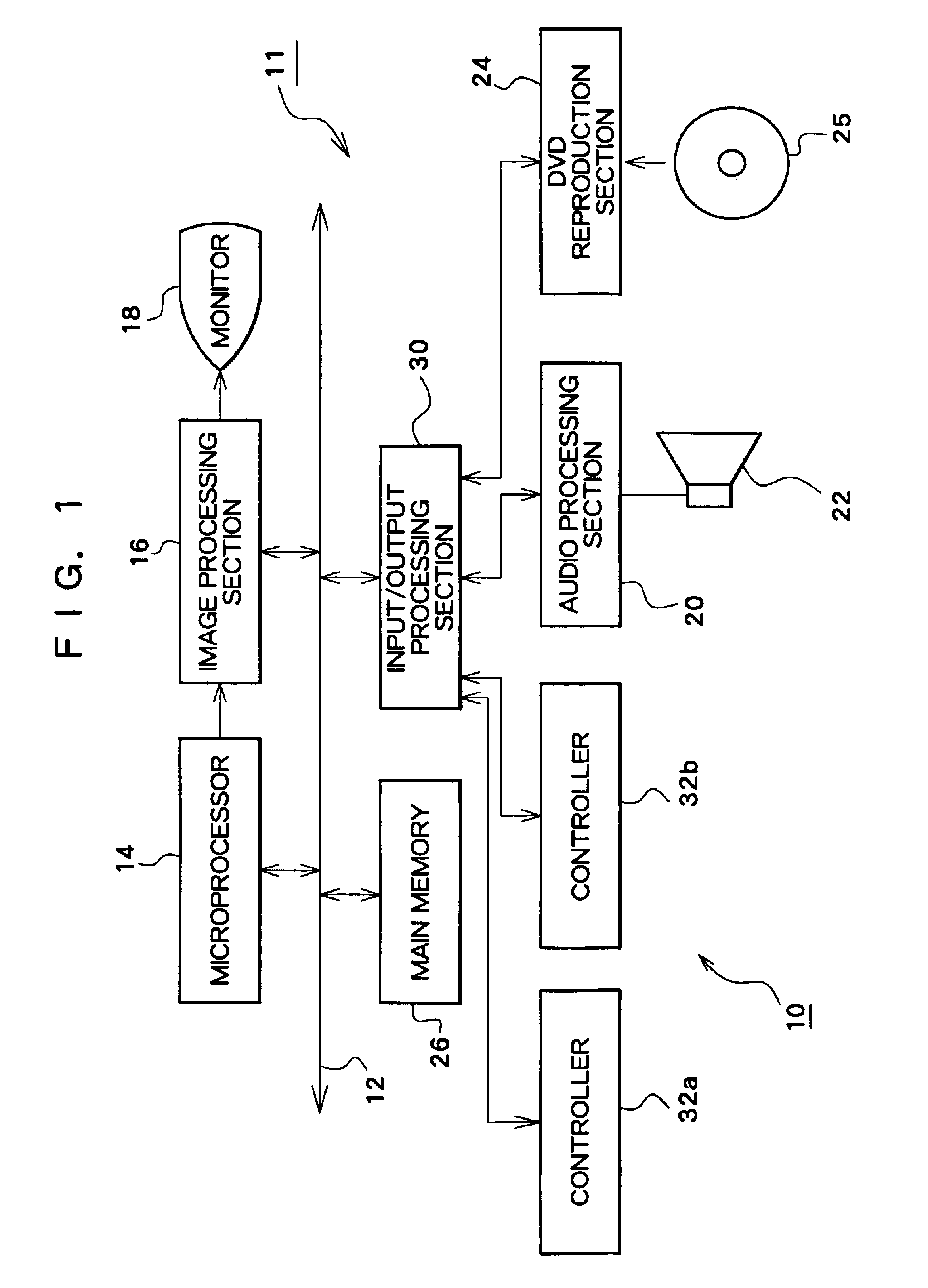
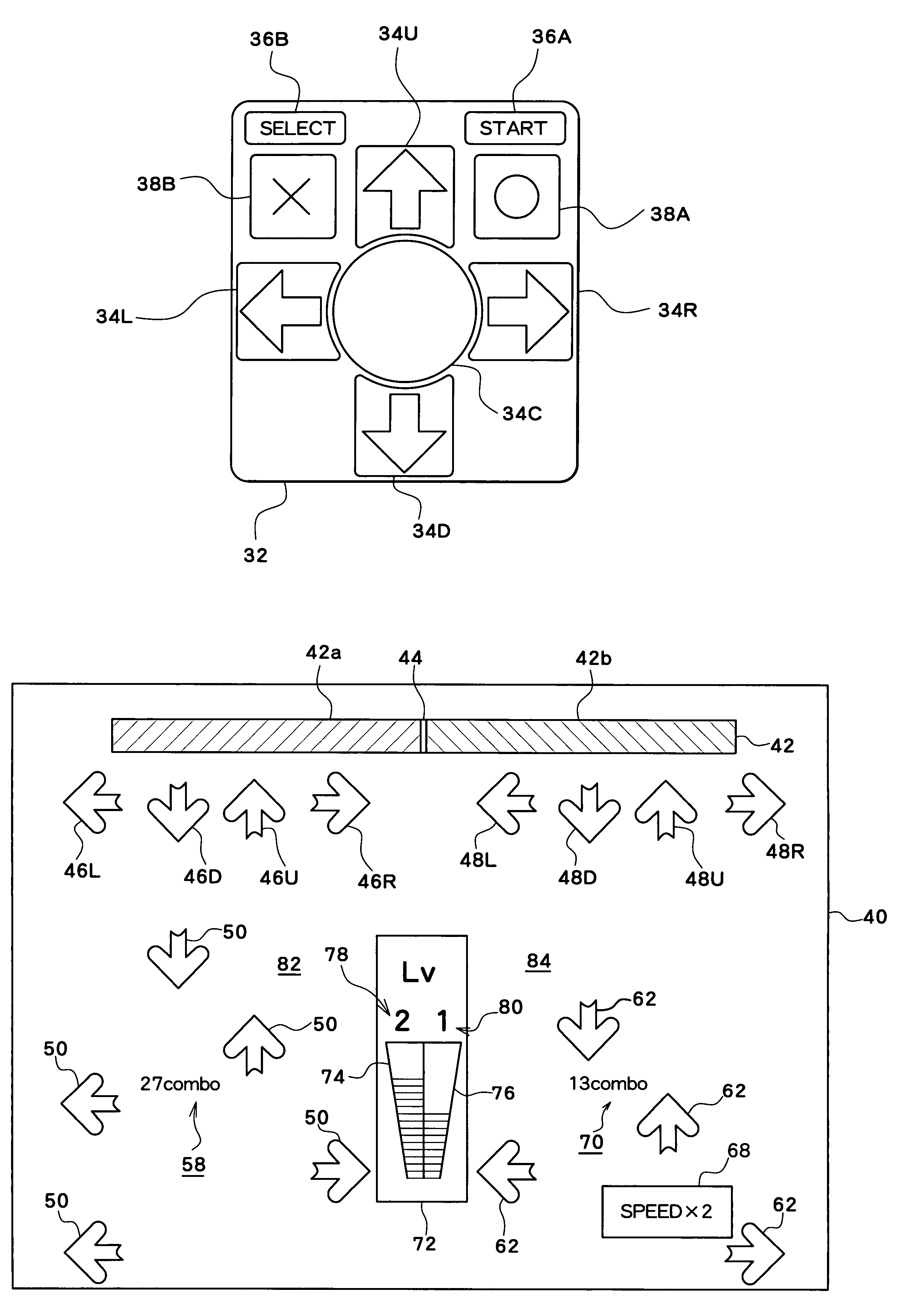
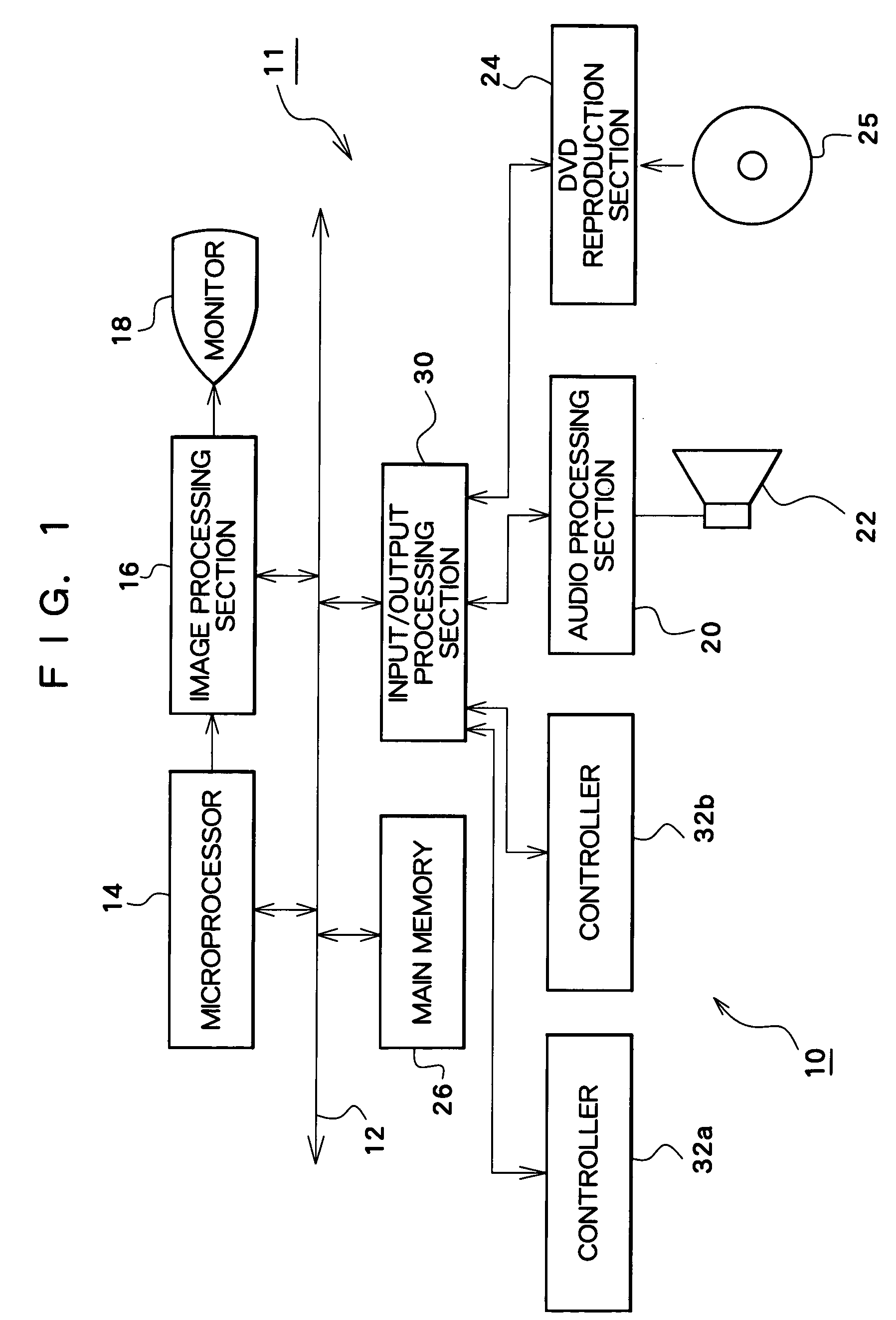
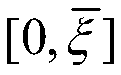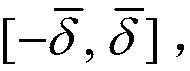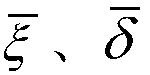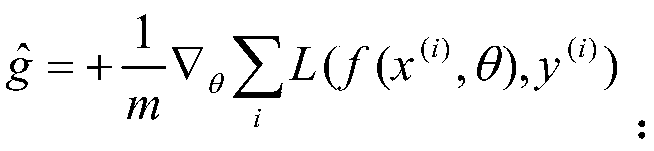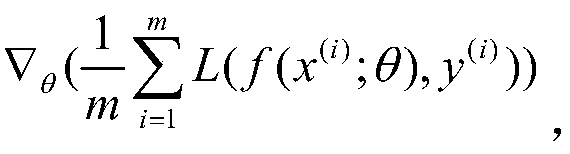Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
1150 results about "Time step" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
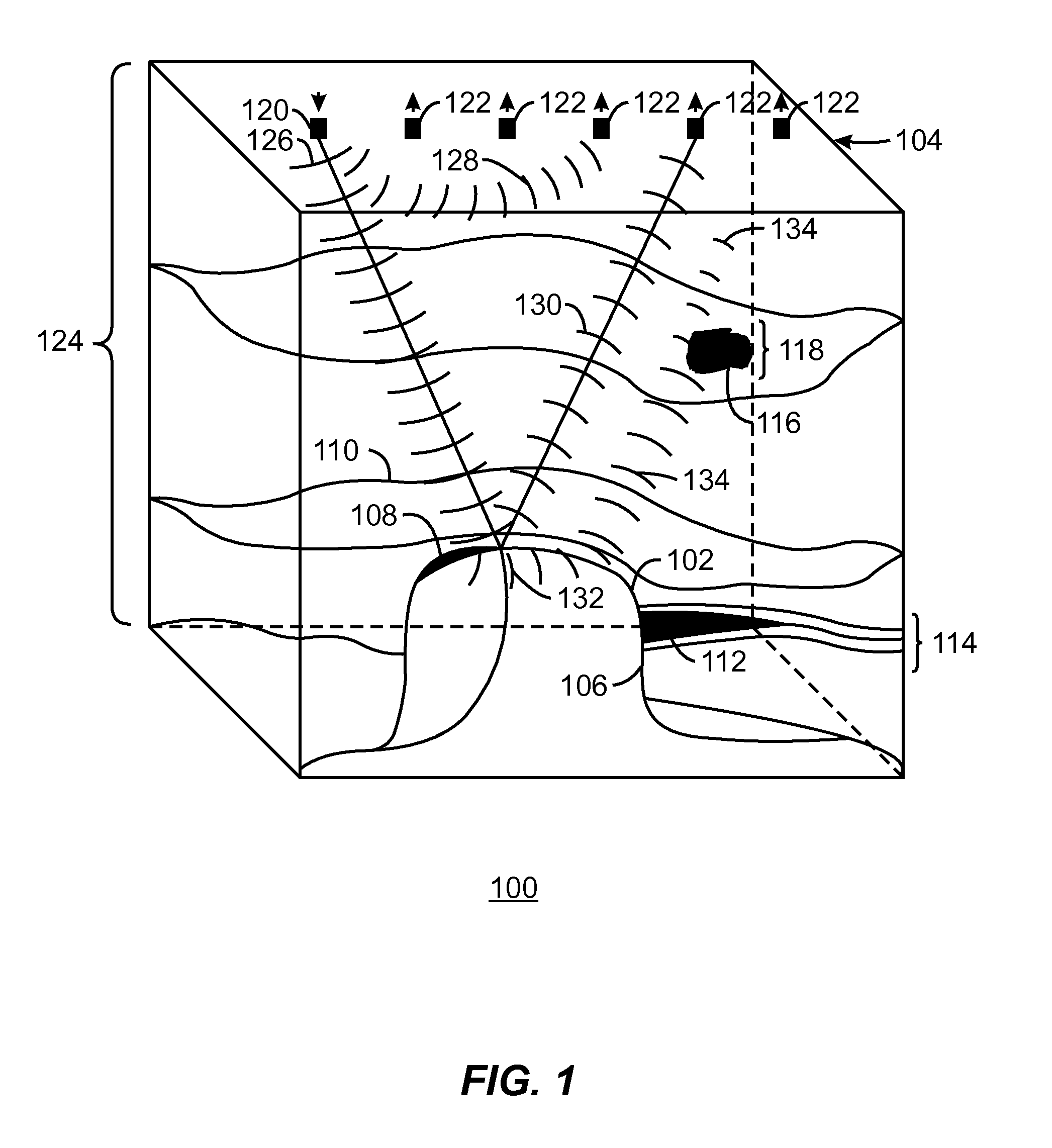
Simulations for Hydraulic Fracturing Treatments and Methods of Fracturing Naturally Fractured Formation
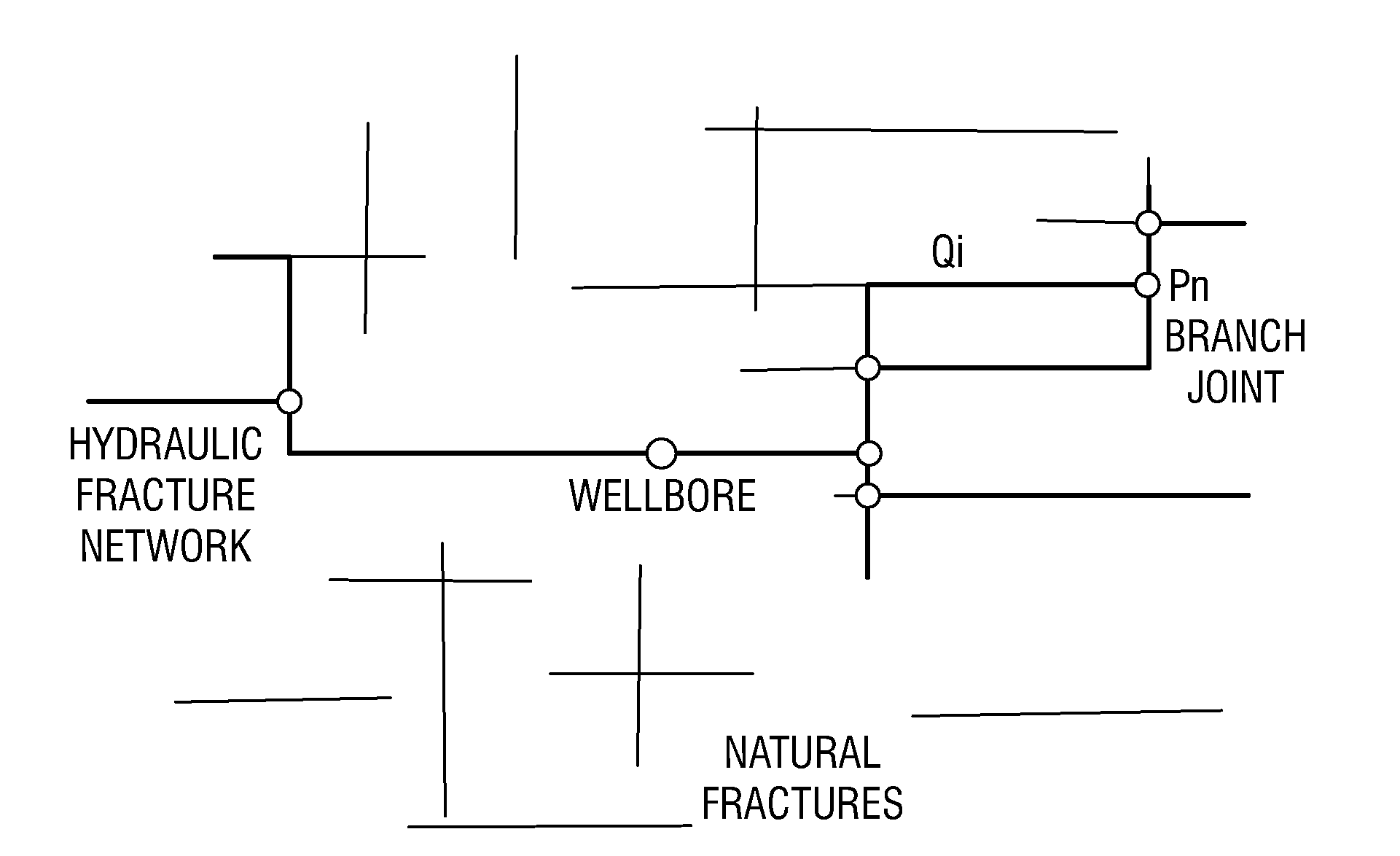
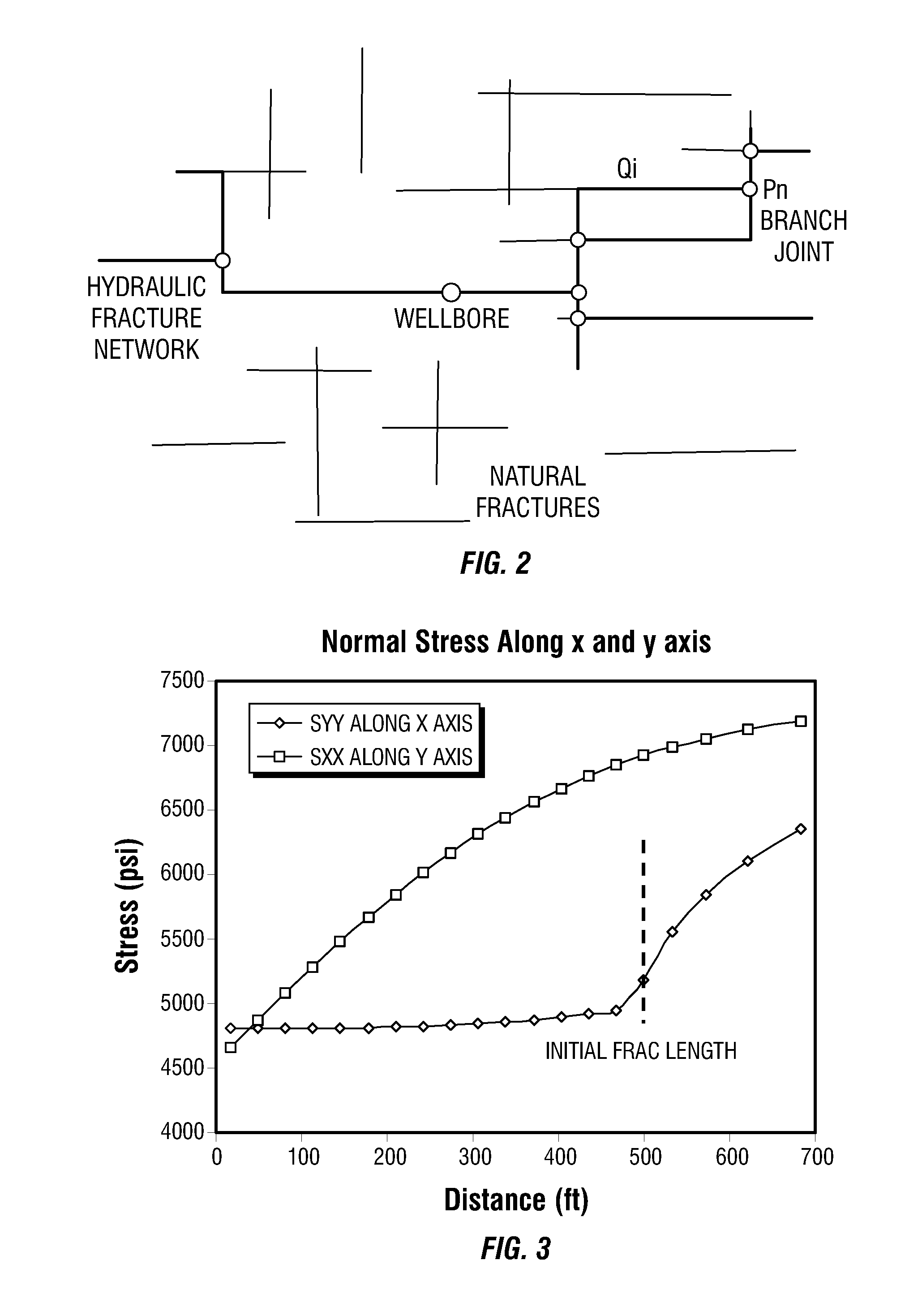
A hydraulic fracture design model that simulates the complex physical process of fracture propagation in the earth driven by the injected fluid through a wellbore. An objective in the model is to adhere with the laws of physics governing the surface deformation of the created fracture subjected to the fluid pressure, the fluid flow in the gap formed by the opposing fracture surfaces, the propagation of the fracture front, the transport of the proppant in the fracture carried by the fluid, and the leakoff of the fracturing fluid into the permeable rock. The models used in accordance with methods of the invention are typically based on the assumptions and the mathematical equations for the conventional 2D or P3D models, and further take into account the network of jointed fracture segments. For each fracture segment, the mathematical equations governing the fracture deformation and fluid flow apply. For each time step, the model predicts the incremental growth of the branch tips and the pressure and flow rate distribution in the system by solving the governing equations and satisfying the boundary conditions at the fracture tips, wellbore and connected branch joints. An iterative technique is used to obtain the solution of this highly nonlinear and complex problem.
Owner:SCHLUMBERGER TECH CORP
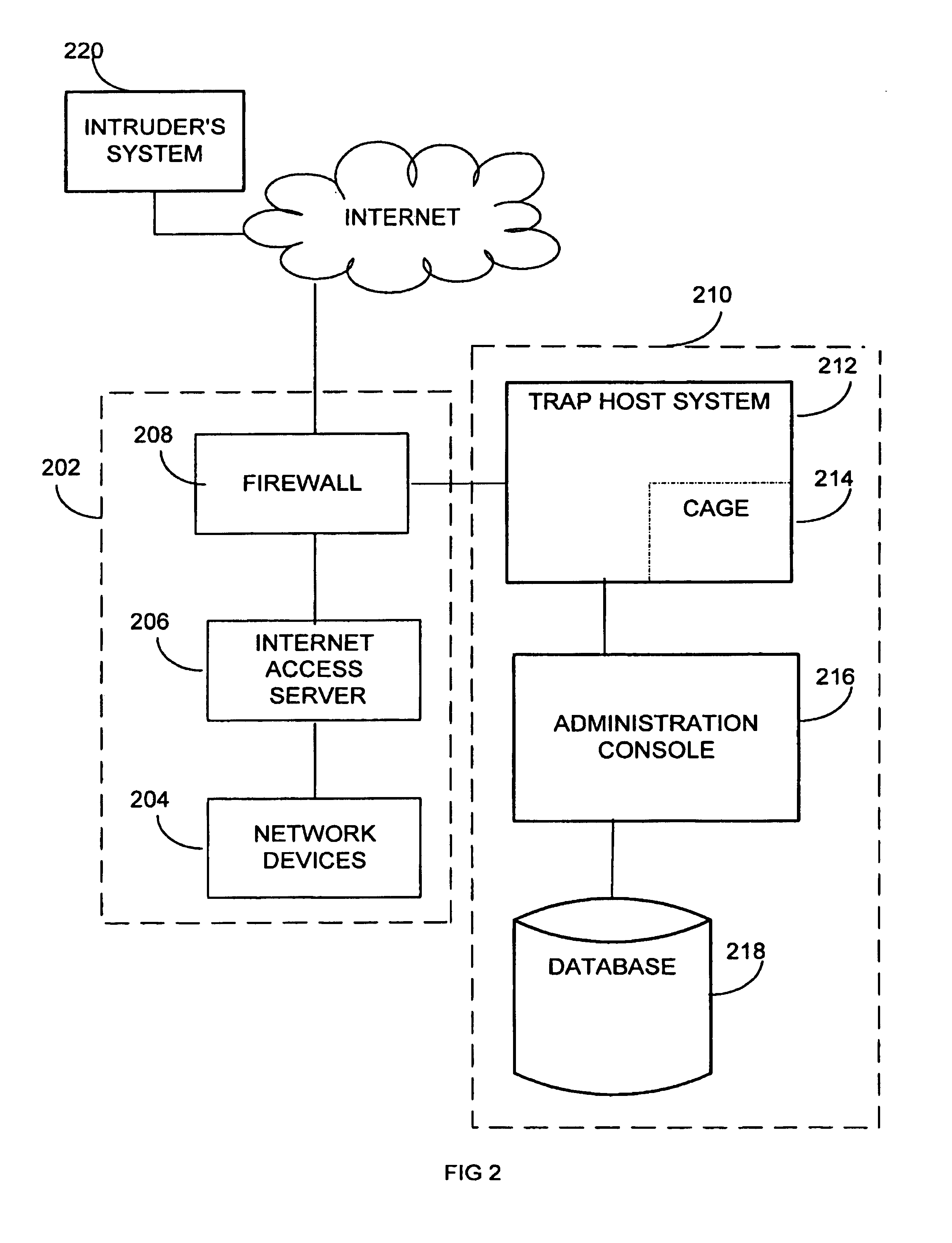
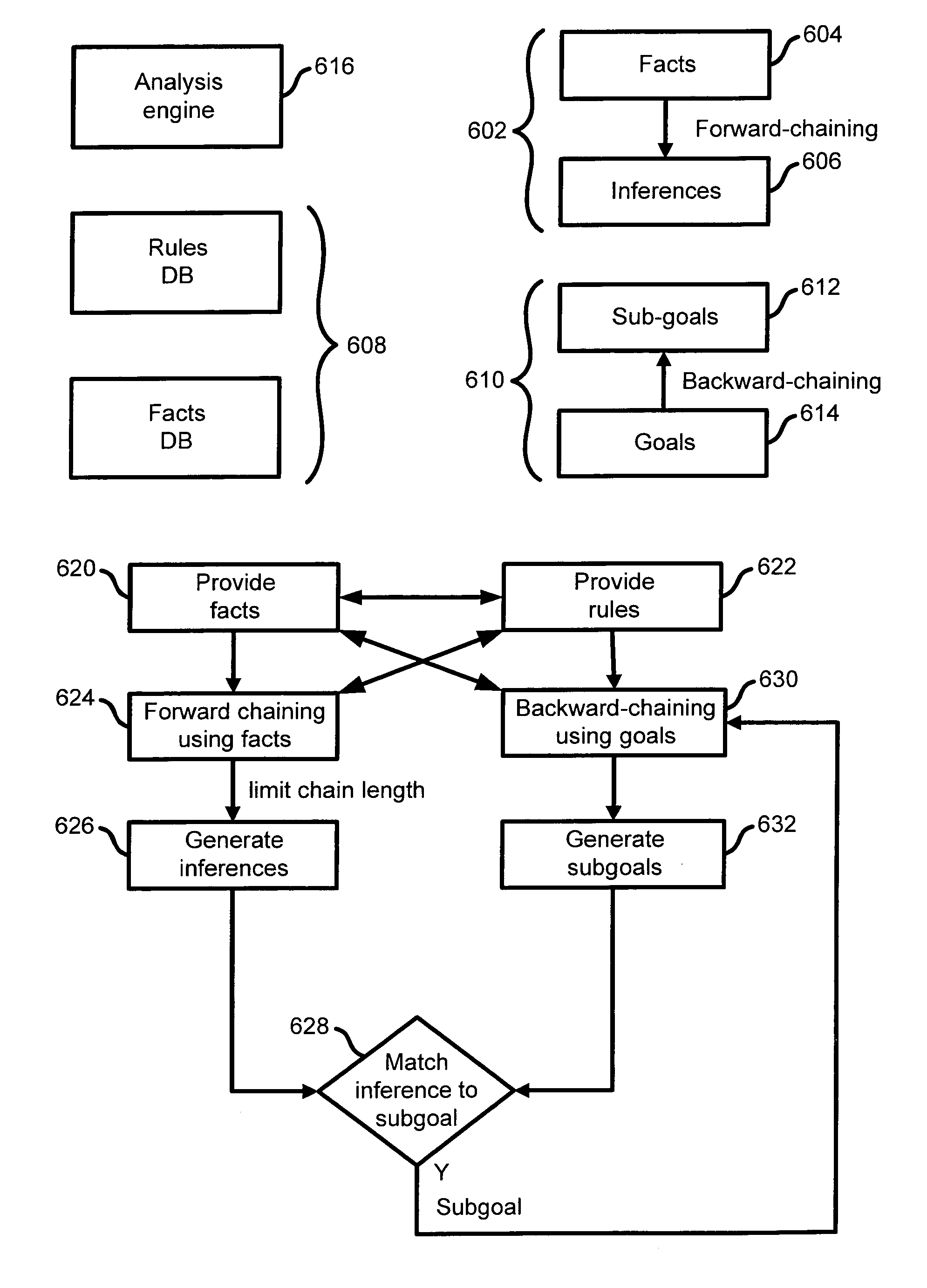
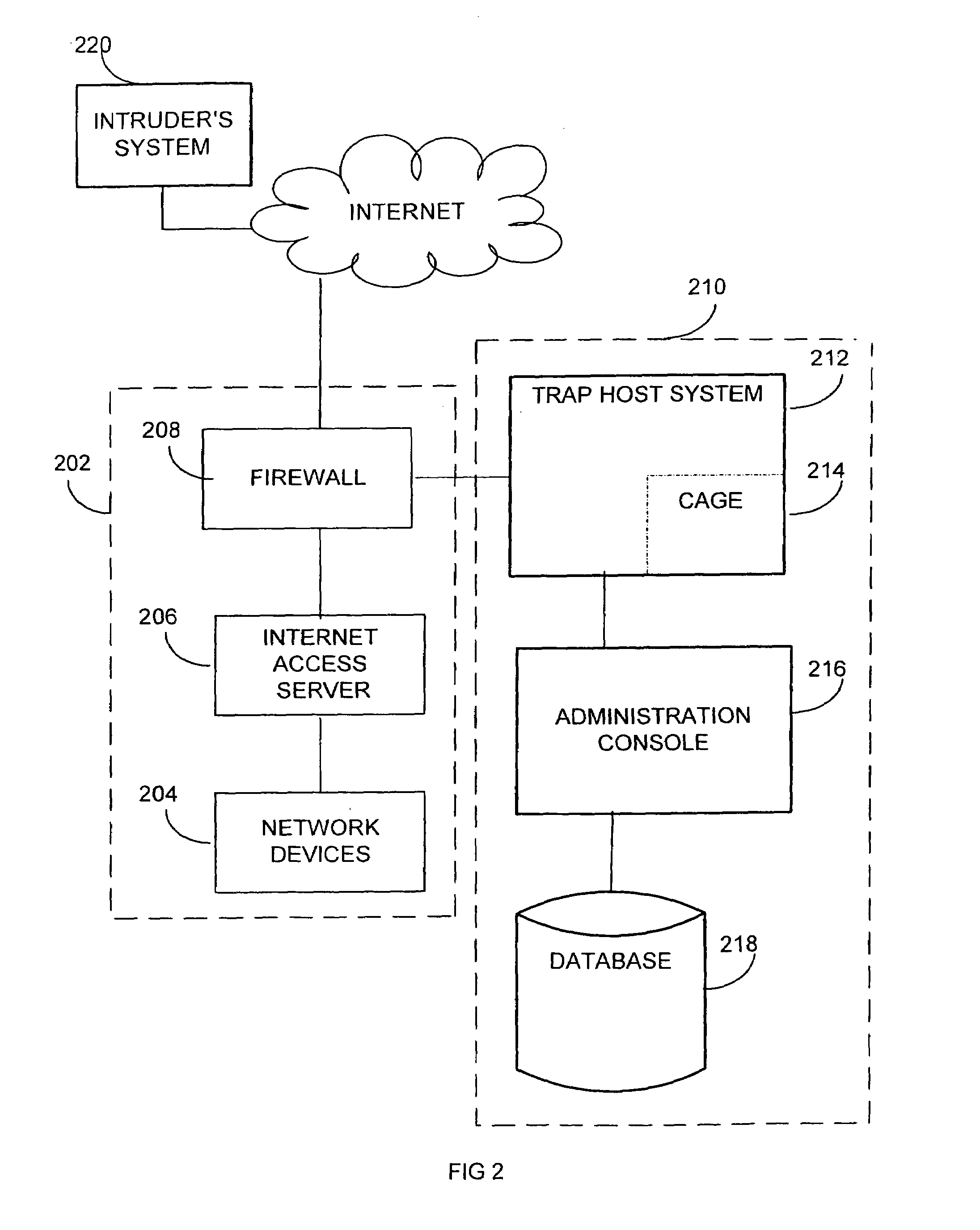
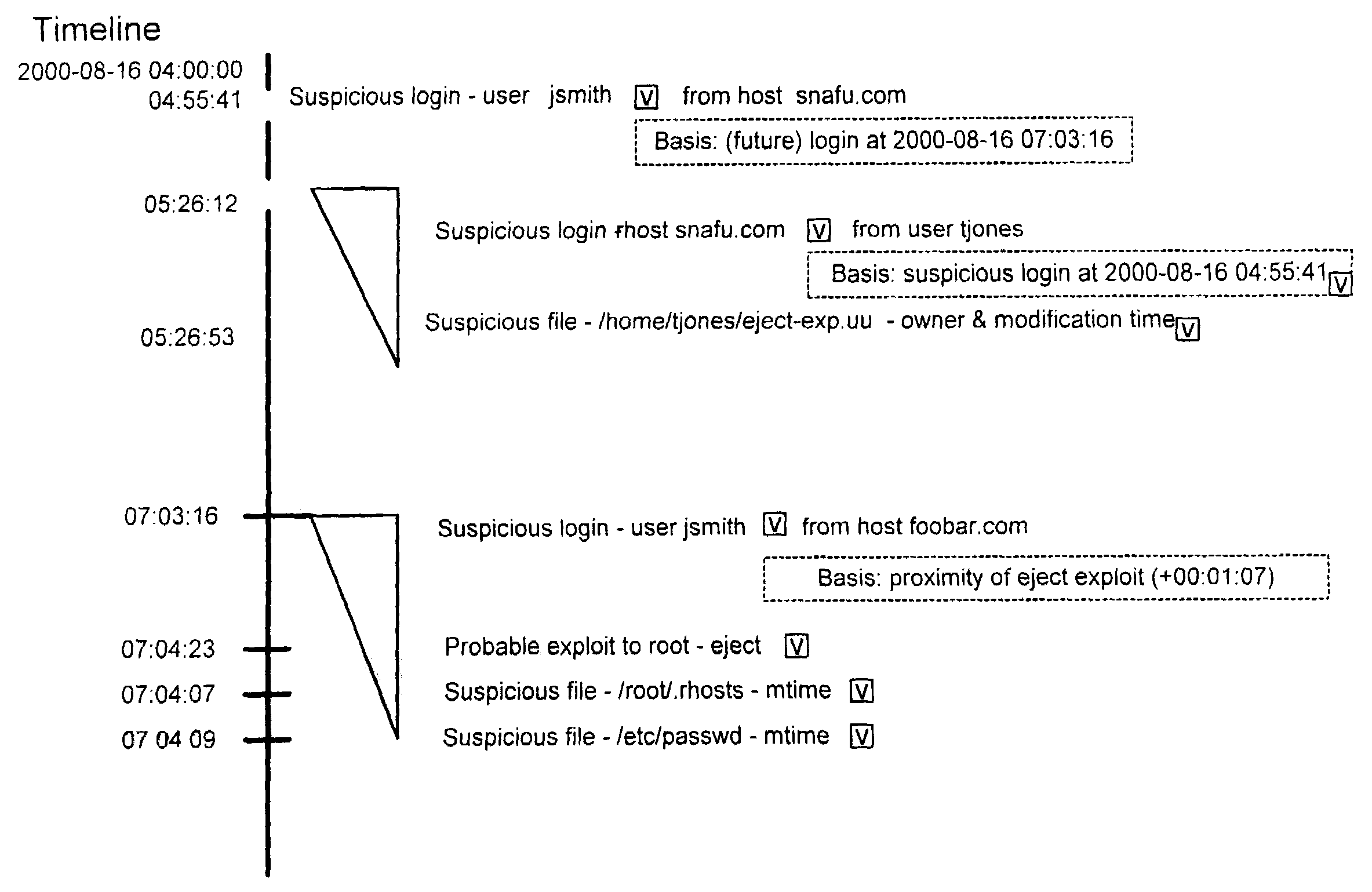
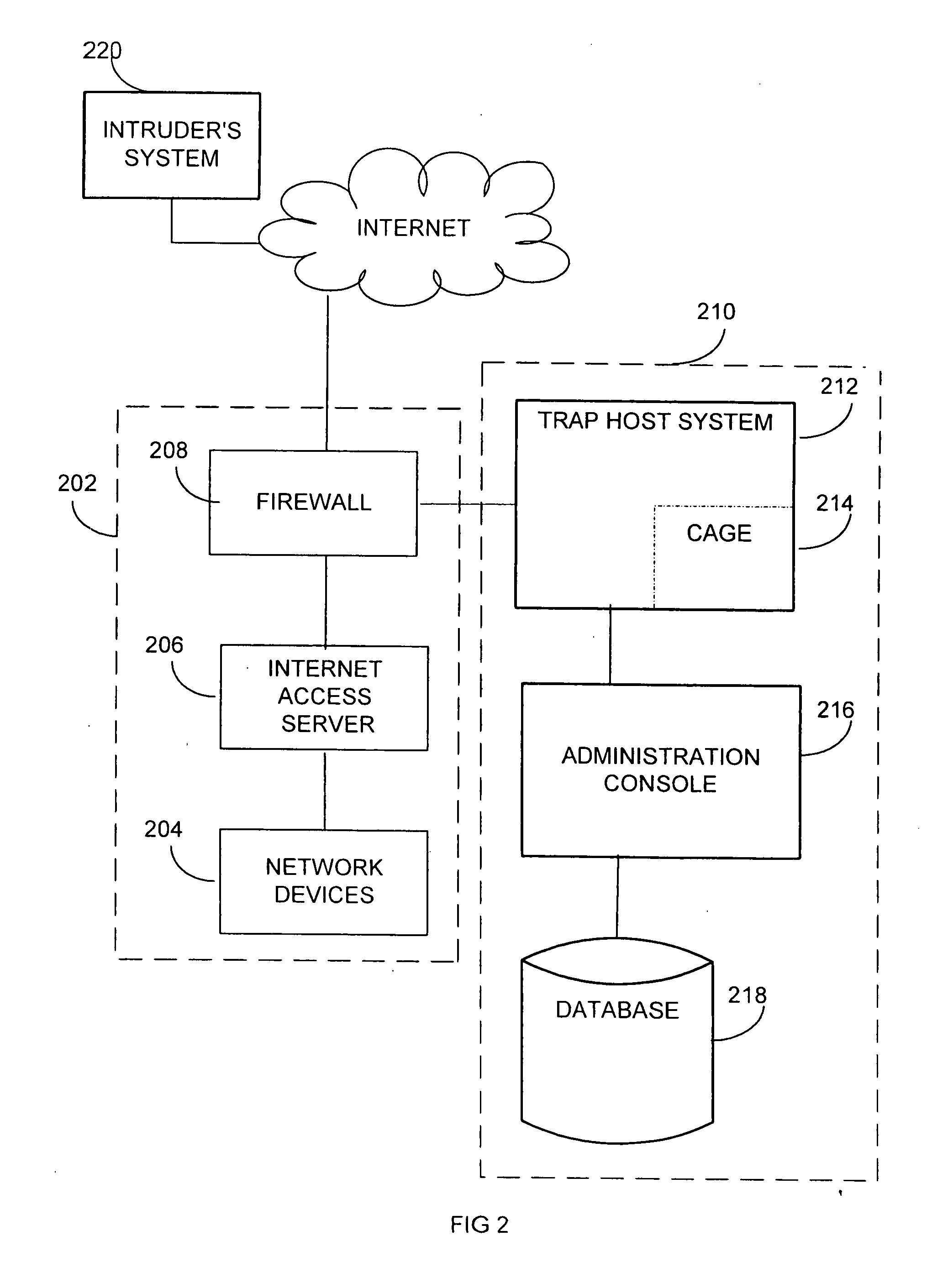
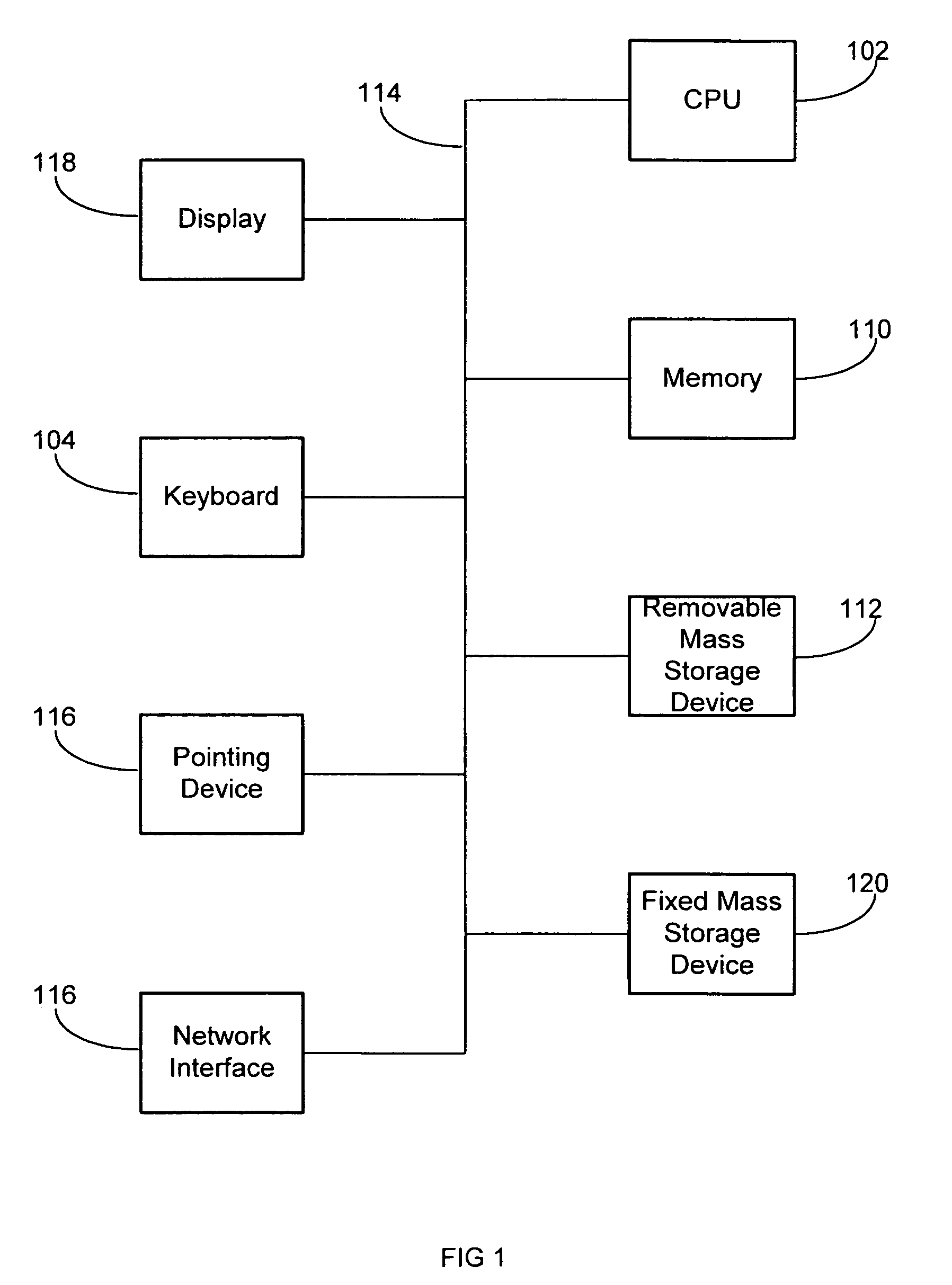
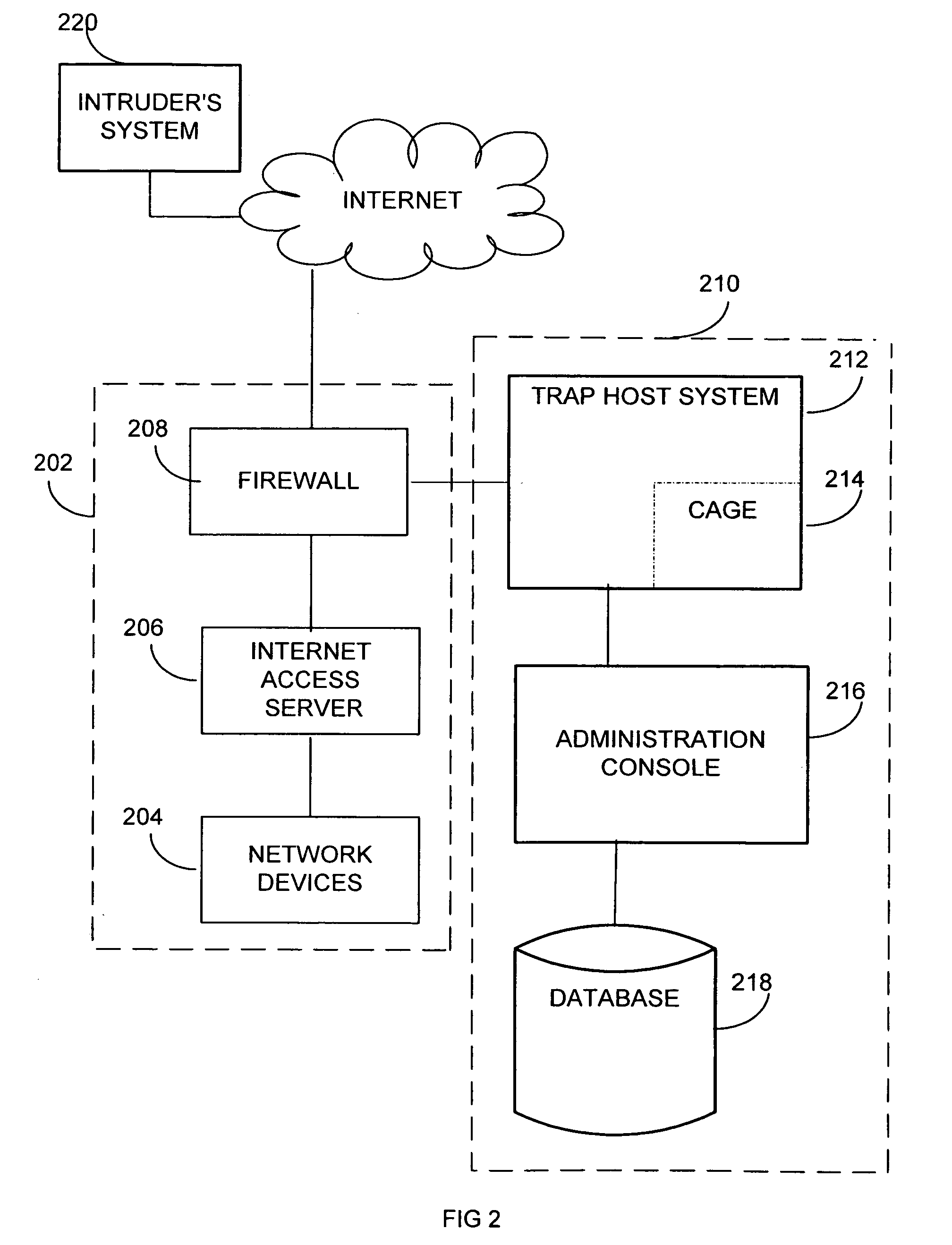
Extensible intrusion detection system
InactiveUS7065657B1Overcome problemsEnabling detectionDigital data processing detailsHardware monitoringTimestampAccess time
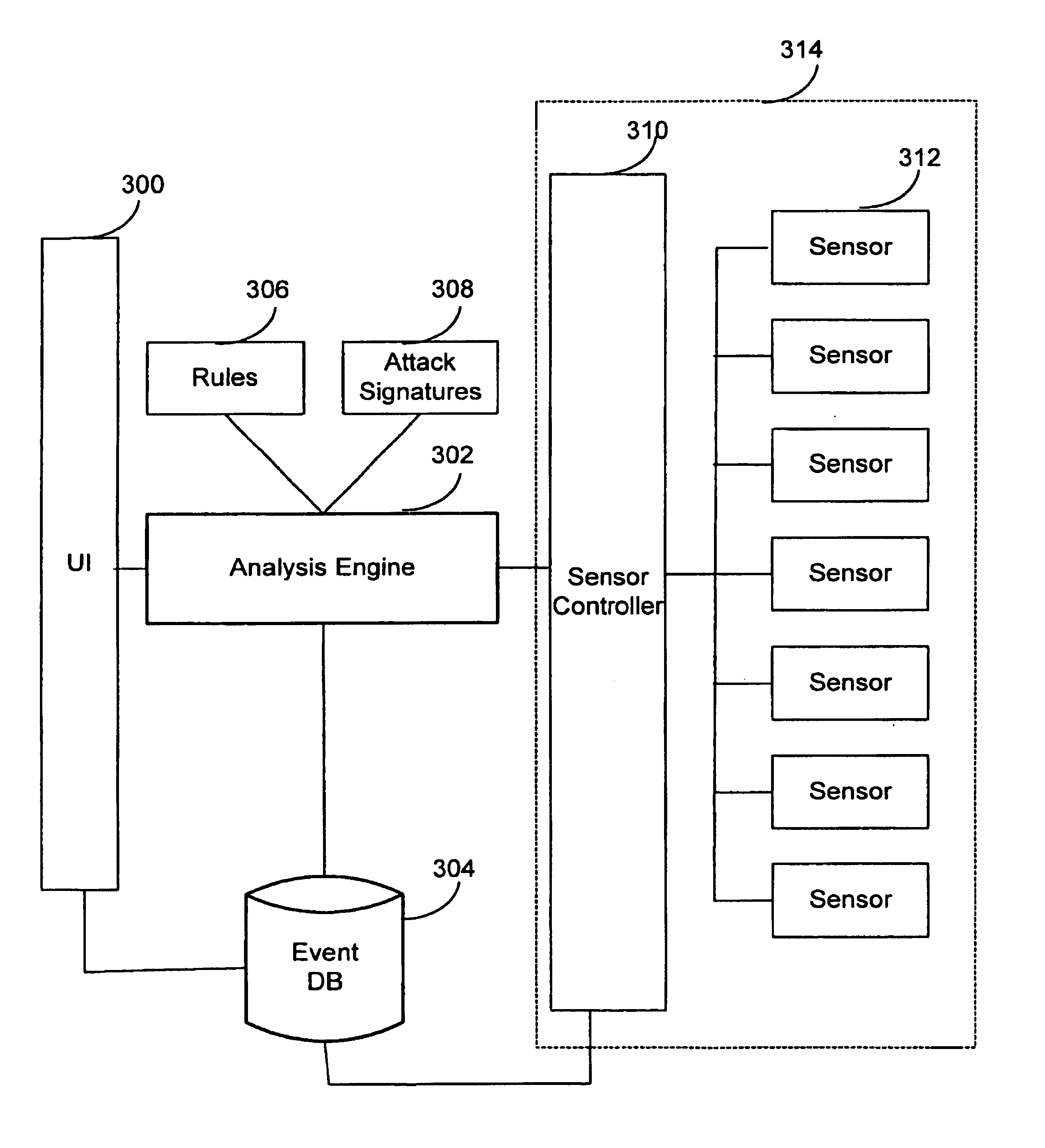
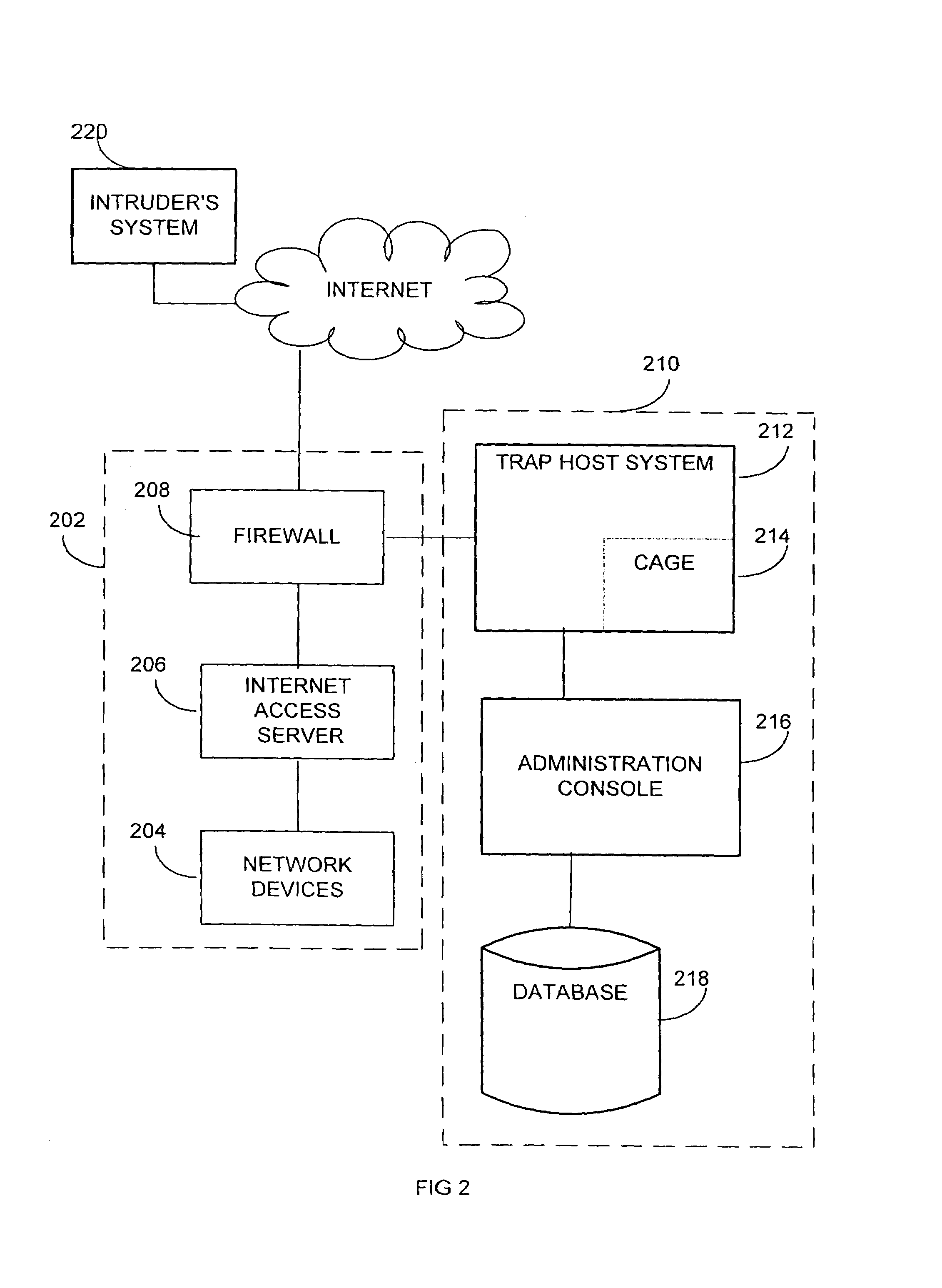
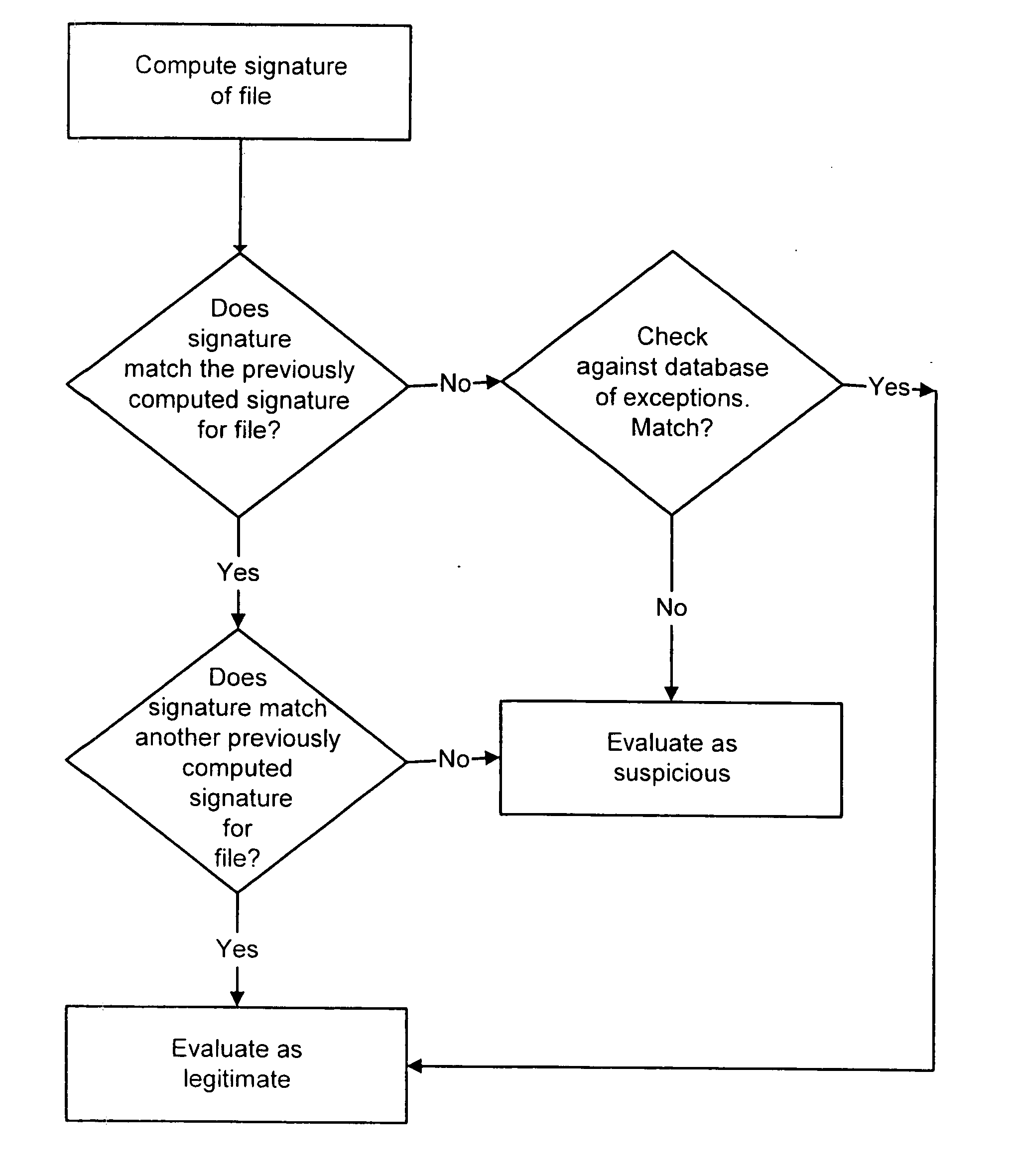
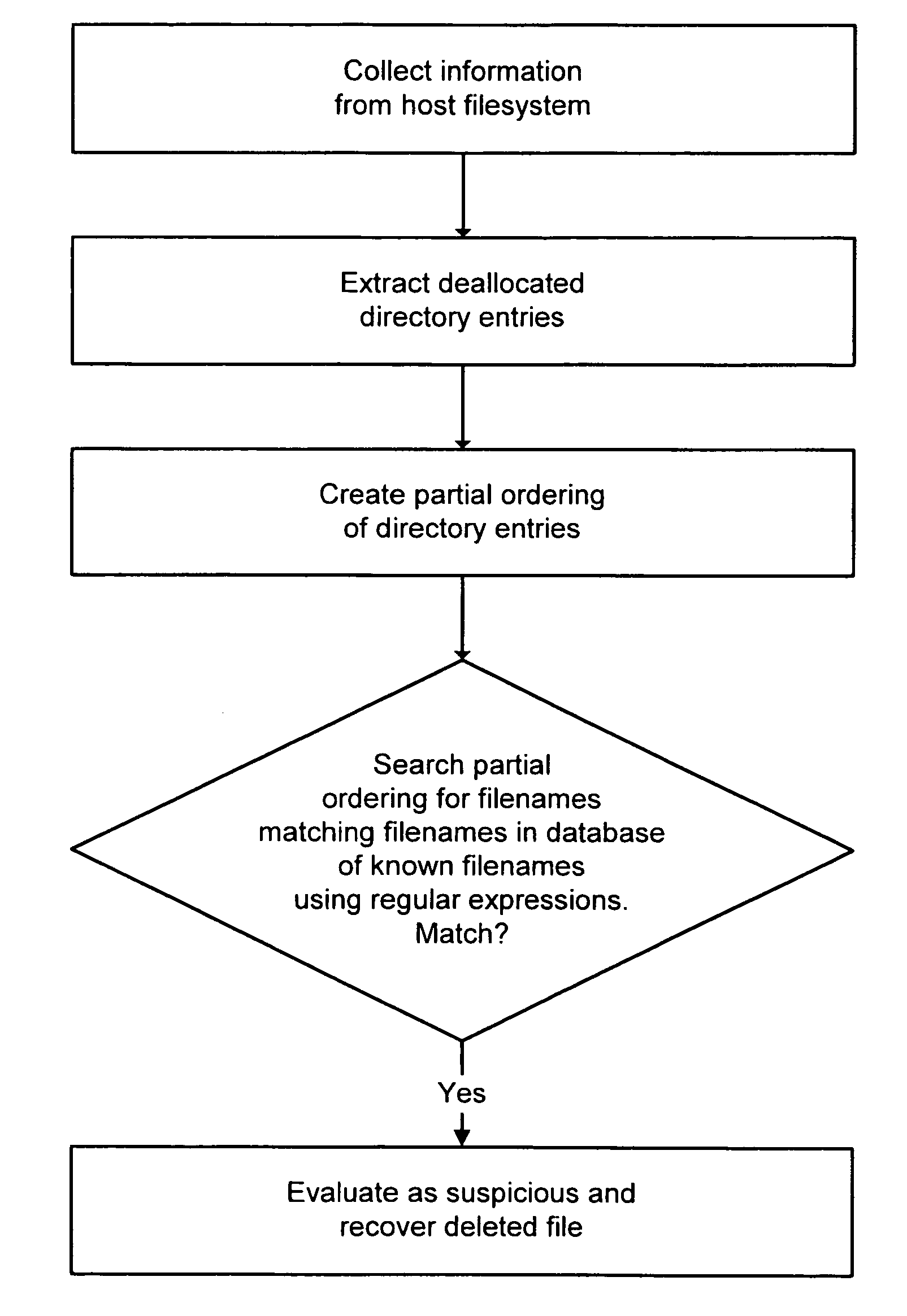
A system and method are disclosed for detecting intrusions in a host system on a network. The intrusion detection system comprises an analysis engine configured to use continuations and apply forward- and backward-chaining using rules. Also provided are sensors, which communicate with the analysis engine using a meta-protocol in which the data packet comprises a 4-tuple. A configuration discovery mechanism locates host system files and communicates the locations to the analysis engine. A file processing mechanism matches contents of a deleted file to a directory or filename, and a directory processing mechanism extracts deallocated directory entries from a directory, creating a partial ordering of the entries. A signature checking mechanism computes the signature of a file and compares it to previously computed signatures. A buffer overflow attack detector compares access times of commands and their associated files. The intrusion detection system further includes a mechanism for checking timestamps to identify and analyze forward and backward time steps in a log file.
Owner:SYMANTEC CORP
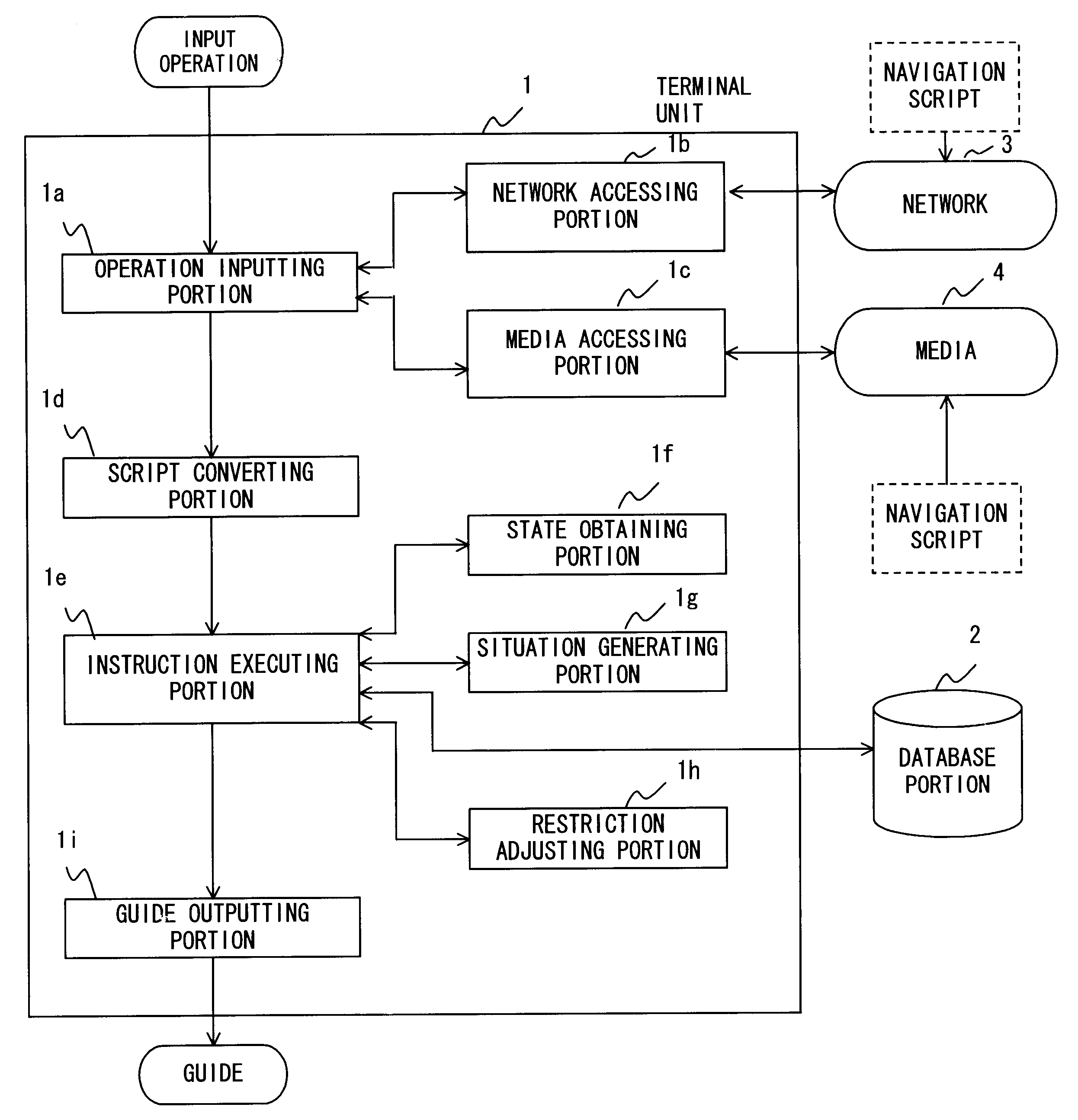
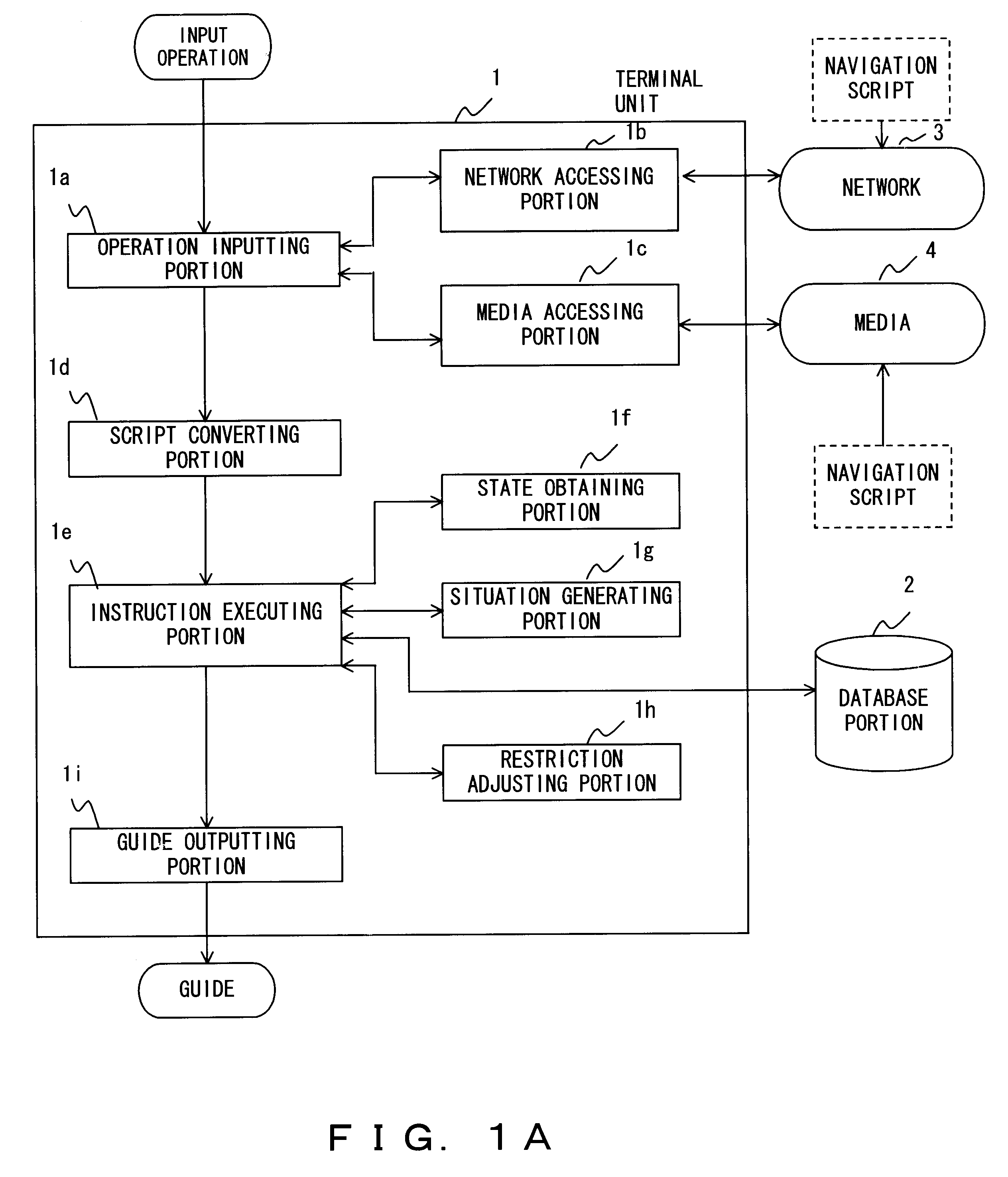
Navigation information presenting apparatus and method thereof
InactiveUS6381534B2Efficient processingEfficient inputTelevision system detailsInstruments for road network navigationHuman–computer interactionMarine navigation
Owner:FUJITSU LTD
Navigation information presenting apparatus and method thereof
InactiveUS20010020211A1Efficient processingEfficient inputTelevision system detailsInstruments for road network navigationHuman–computer interactionMarine navigation
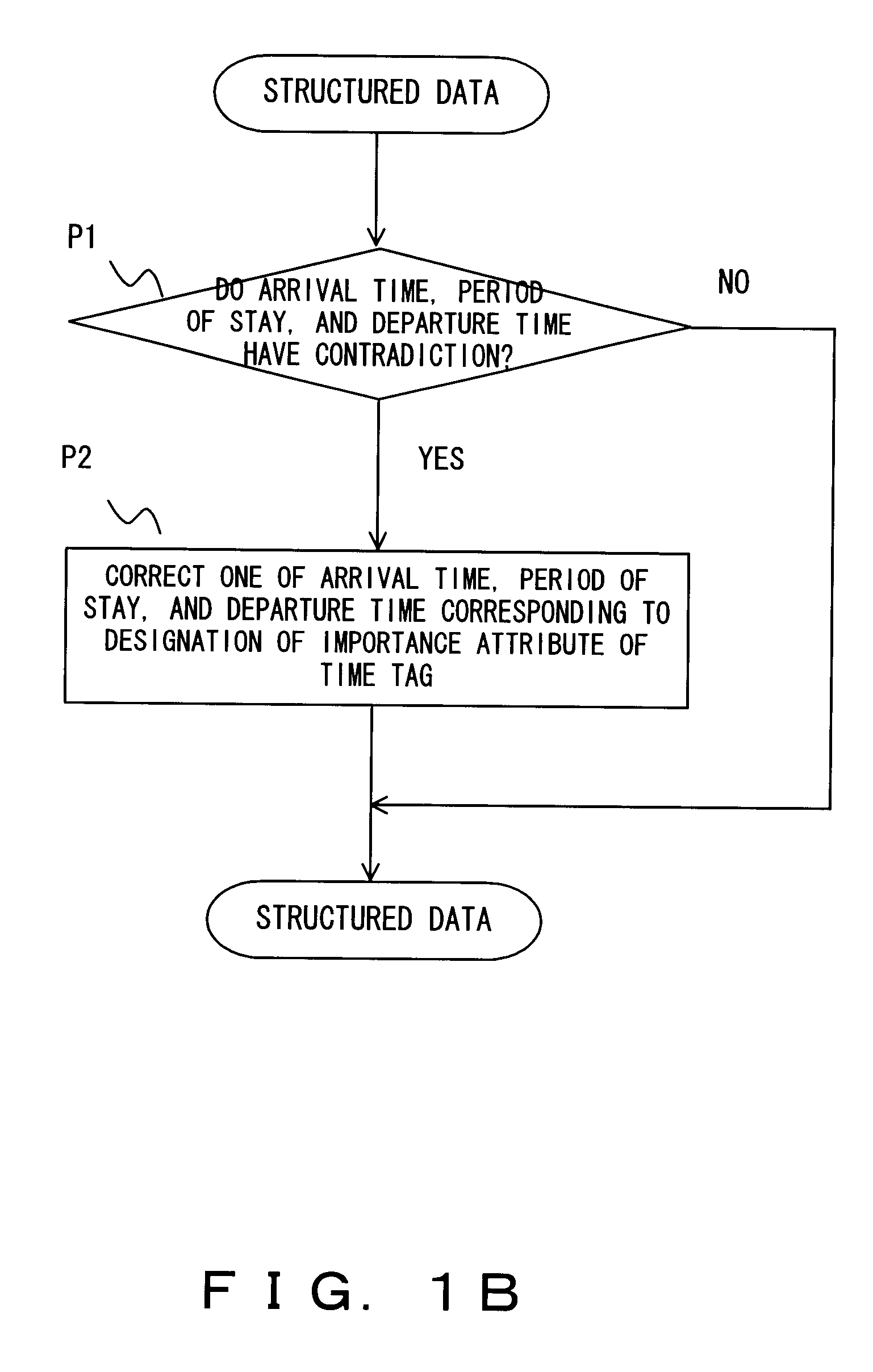
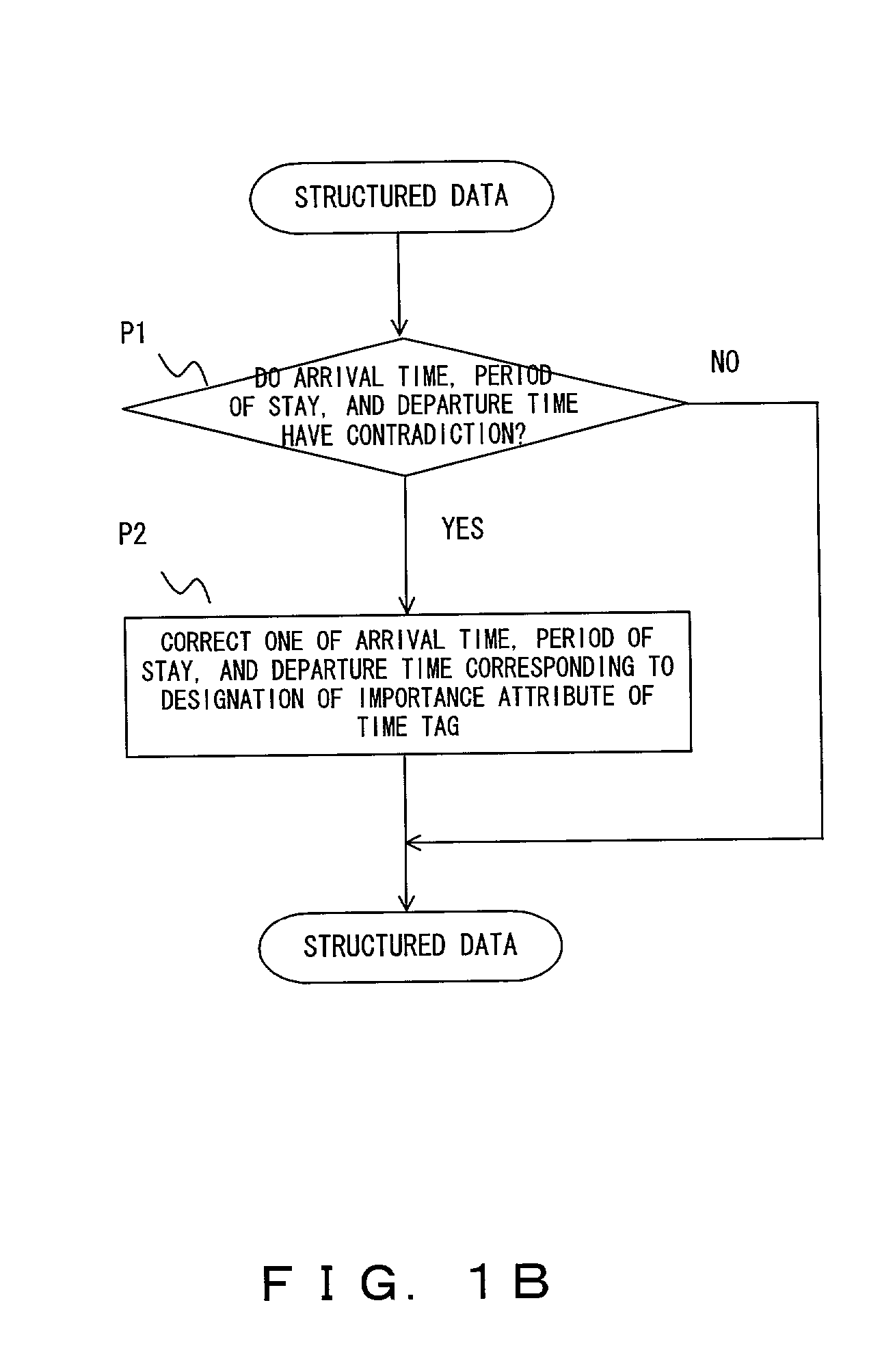
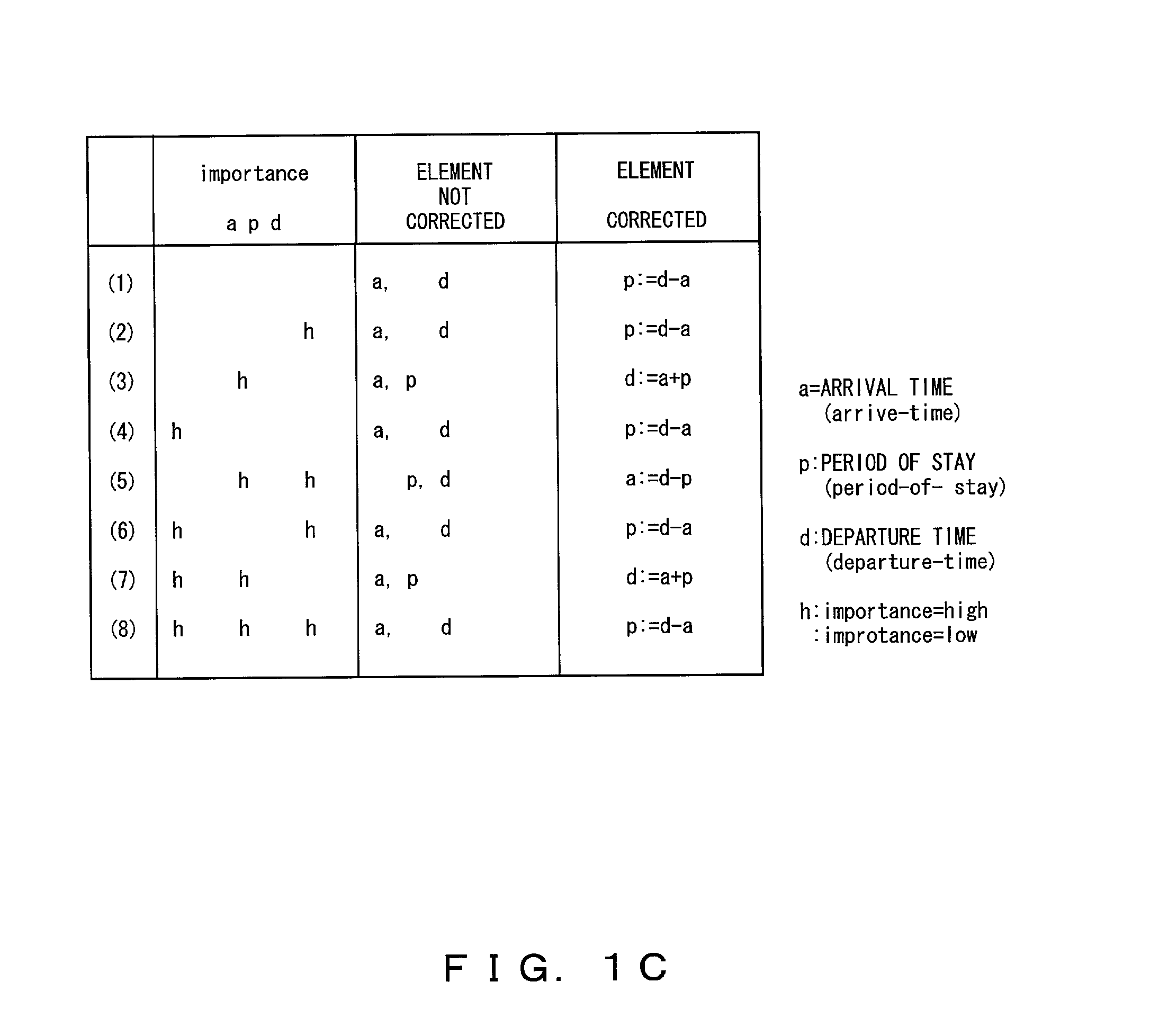
When a navigation script has a contradiction with respect to time and place, a navigation information presenting apparatus adjusts the contradiction, executes instructions of the navigation script corresponding to restriction information, and presents the navigation information to the user. In addition, the navigation information presenting apparatus presents navigation information to the user at a timing corresponding to information representing traveling speed and / or time step.
Owner:FUJITSU LTD
System and method for detecting computer intrusions
InactiveUS6996843B1Overcome problemsEnabling detectionMemory loss protectionDigital computer detailsTimestampAccess time
A system and method are disclosed for detecting intrusions in a host system on a network. The intrusion detection system comprises an analysis engine configured to use continuations and apply forward- and backward-chaining using rules. Also provided are sensors, which communicate with the analysis engine using a meta-protocol in which the data packet comprises a 4-tuple. A configuration discovery mechanism locates host system files and communicates the locations to the analysis engine. A file processing mechanism matches contents of a deleted file to a directory or filename, and a directory processing mechanism extracts deallocated directory entries from a directory, creating a partial ordering of the entries. A signature checking mechanism computes the signature of a file and compares it to previously computed signatures. A buffer overflow attack detector compares access times of commands and their associated files. The intrusion detection system further includes a mechanism for checking timestamps to identify and analyze forward and backward time steps in a log file.
Owner:SYMANTEC CORP
System and method for using timestamps to detect attacks
InactiveUS7203962B1Overcome problemsEnabling detectionMemory loss protectionDigital computer detailsTimestampContinuation
A system and method are disclosed for detecting intrusions in a host system on a network. The intrusion detection system comprises an analysis engine configured to use continuations and apply forward- and backward-chaining using rules. Also provided are sensors, which communicate with the analysis engine using a meta-protocol in which the data packet comprises a 4-tuple. A configuration discovery mechanism locates host system files and communicates the locations to the analysis engine. A file processing mechanism matches contents of a deleted file to a directory or filename, and a directory processing mechanism extracts deallocated directory entries from a directory, creating a partial ordering of the entries. A signature checking mechanism computes the signature of a file and compares it to previously computed signatures. A buffer overflow attack detector compares access times of commands and their associated files. The intrusion detection system further includes a mechanism for checking timestamps to identify and analyze forward and backward time steps in a log file.
Owner:SYMANTEC CORP
System and method for using timestamps to detect attacks
InactiveUS20070157315A1Overcome problemsEnabling detectionMemory loss protectionError detection/correctionData packProcess mechanism
A system and method are disclosed for detecting intrusions in a host system on a network. The intrusion detection system comprises an analysis engine configured to use continuations and apply forward- and backward-chaining using rules. Also provided are sensors, which communicate with the analysis engine using a meta-protocol in which the data packet comprises a 4-tuple. A configuration discovery mechanism locates host system files and communicates the locations to the analysis engine. A file processing mechanism matches contents of a deleted file to a directory or filename, and a directory processing mechanism extracts deallocated directory entries from a directory, creating a partial ordering of the entries. A signature checking mechanism computes the signature of a file and compares it to previously computed signatures. A buffer overflow attack detector compares access times of commands and their associated files. The intrusion detection system further includes a mechanism for checking timestamps to identify and analyze forward and backward time steps in a log file.
Owner:SYMANTEC CORP
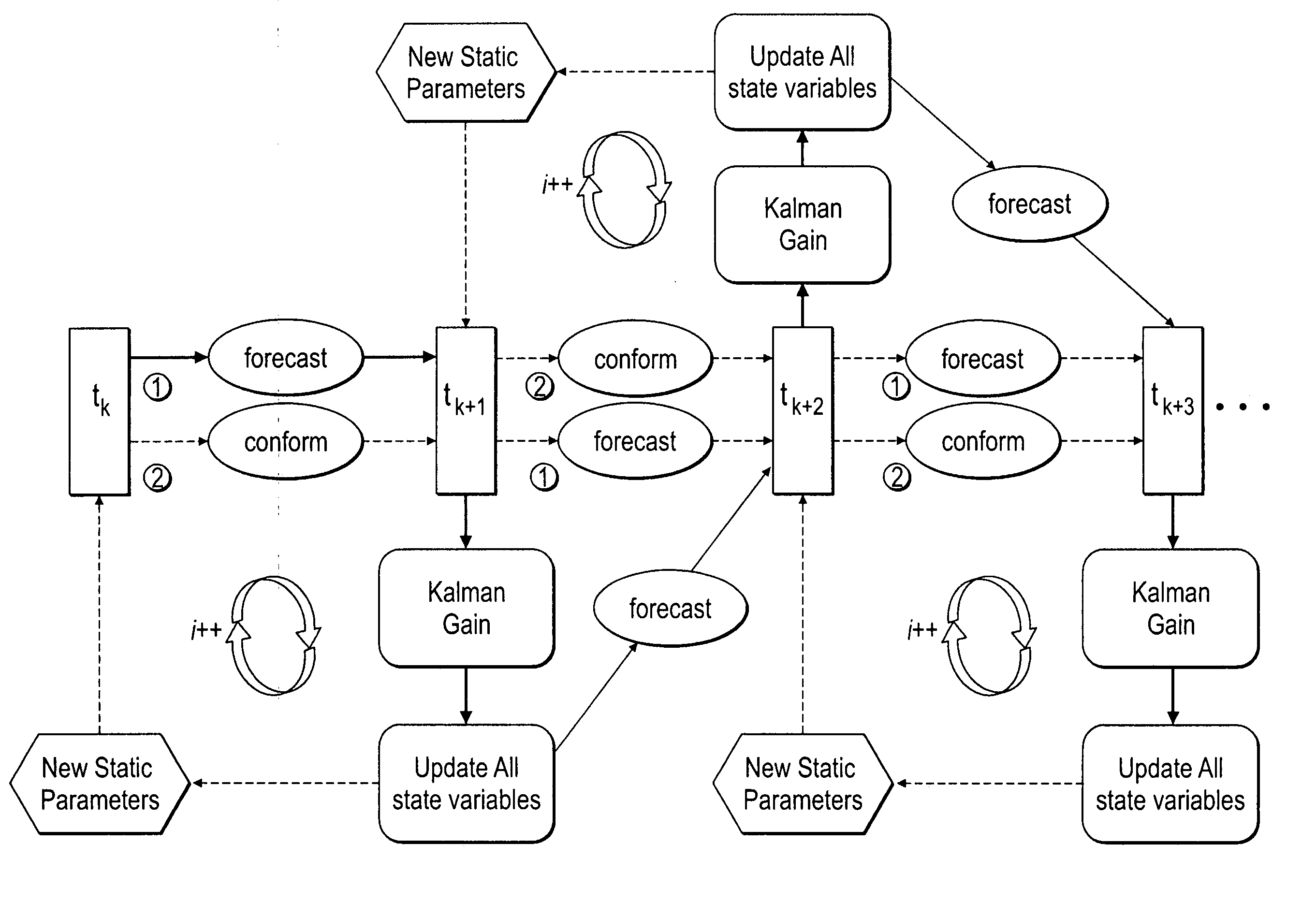
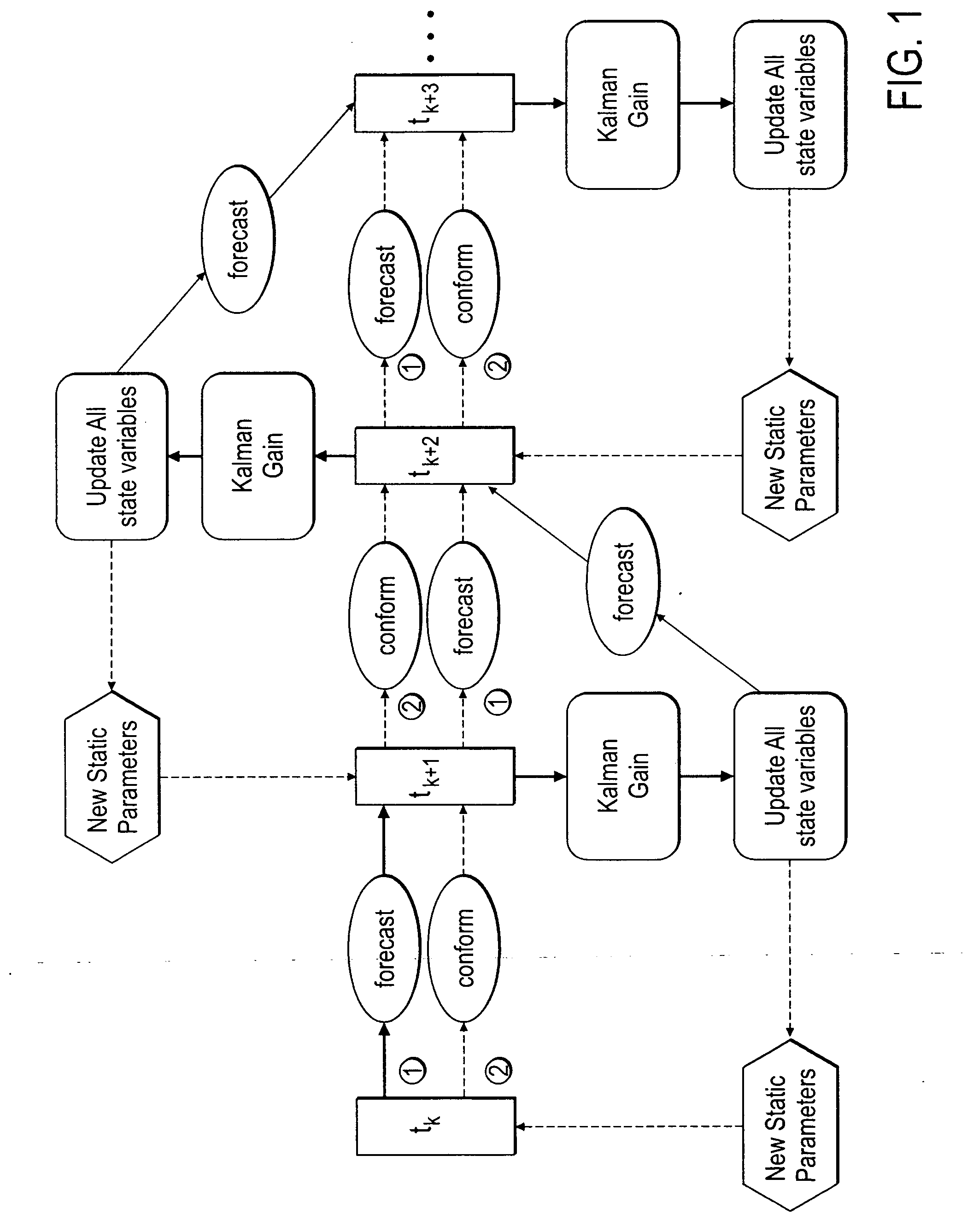
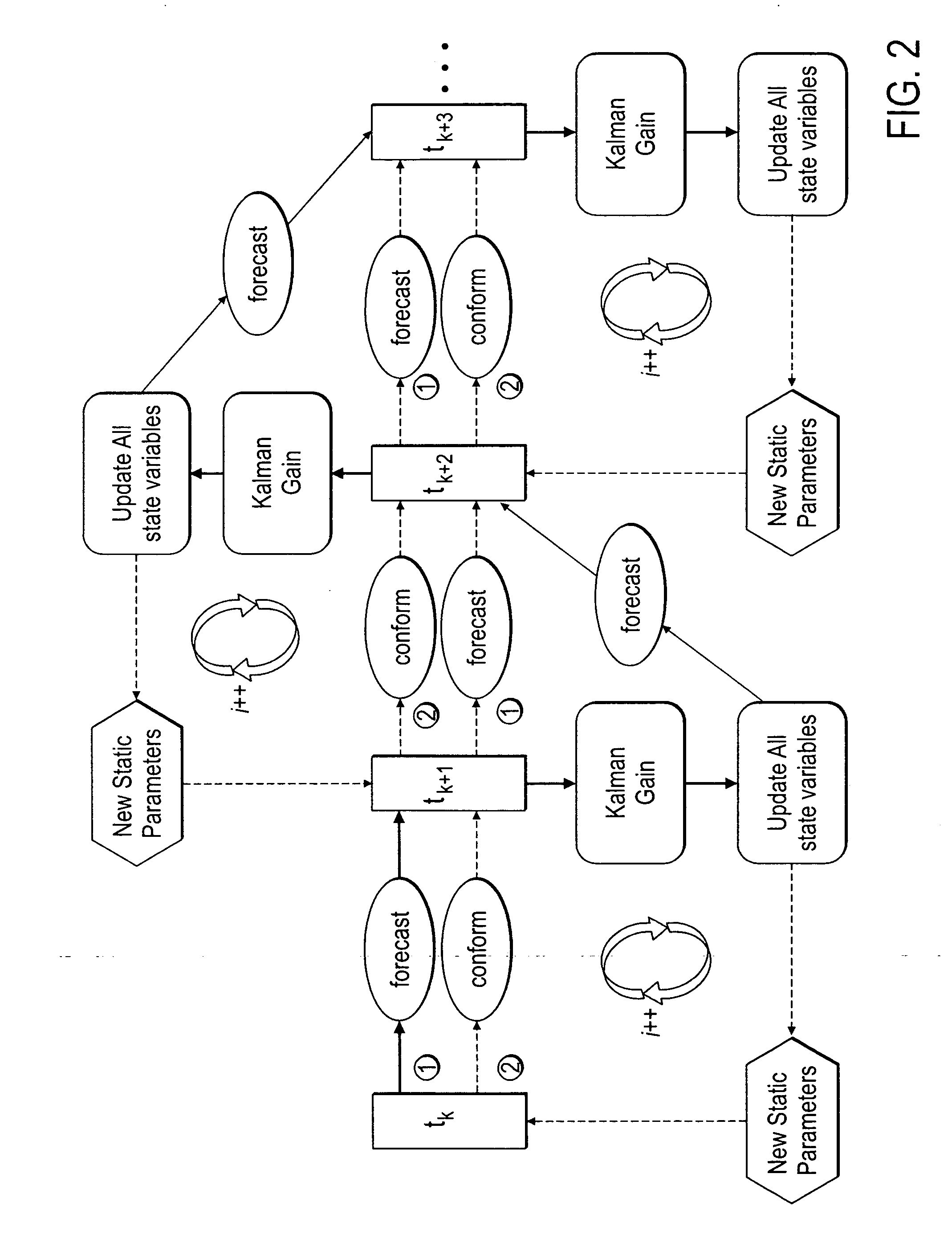
Method, system and apparatus for real-time reservoir model updating using ensemble Kalman filter
ActiveUS20070118346A1Reduce in quantityEnsure correct executionFluid removalComputation using non-denominational number representationKaiman filterState variable
A method, system and apparatus for real-time reservoir model updating using ensemble Kalman filters is described. The method includes a conforming step for bring bringing static and dynamic state variables into conformance with one another during a time step of the updating. Also, an iterative damping method is used in conjunction with the conformance step to account for nonGaussian and nonlinear features in a system. Also, a re-sampling method is described which reduces the ensemble size of reservoir models which are to be updated.
Owner:CHEVROU USA INC
Autonomous underwater vehicle trajectory tracking control method based on deep reinforcement learning
ActiveCN108803321AStabilize the learning processOptimal target strategyAdaptive controlSimulationIntelligent control
The invention provides an autonomous underwater vehicle (AUV) trajectory tracking control method based on deep reinforcement learning, belonging to the field of deep reinforcement learning and intelligent control. The autonomous underwater vehicle trajectory tracking control method based on deep reinforcement learning includes the steps: defining an AUV trajectory tracking control problem; establishing a Markov decision-making process model of the AUV trajectory tracking problem; constructing a hybrid policy-evaluation network which consists of multiple policy networks and evaluation networks;and finally, solving the target policy of AUV trajectory tracking control by the constructed hybrid policy-evaluation network, for the multiple evaluation networks, evaluating the performance of eachevaluation network by defining an expected Bellman absolute error and updating only one evaluation network with the lowest performance at each time step, and for the multiple policy networks, randomly selecting one policy network at each time step and using a deterministic policy gradient to update, so that the finally learned policy is the mean value of all the policy networks. The autonomous underwater vehicle trajectory tracking control method based on deep reinforcement learning is not easy to be influenced by the bad AUV historical tracking trajectory, and has high precision.
Owner:TSINGHUA UNIV
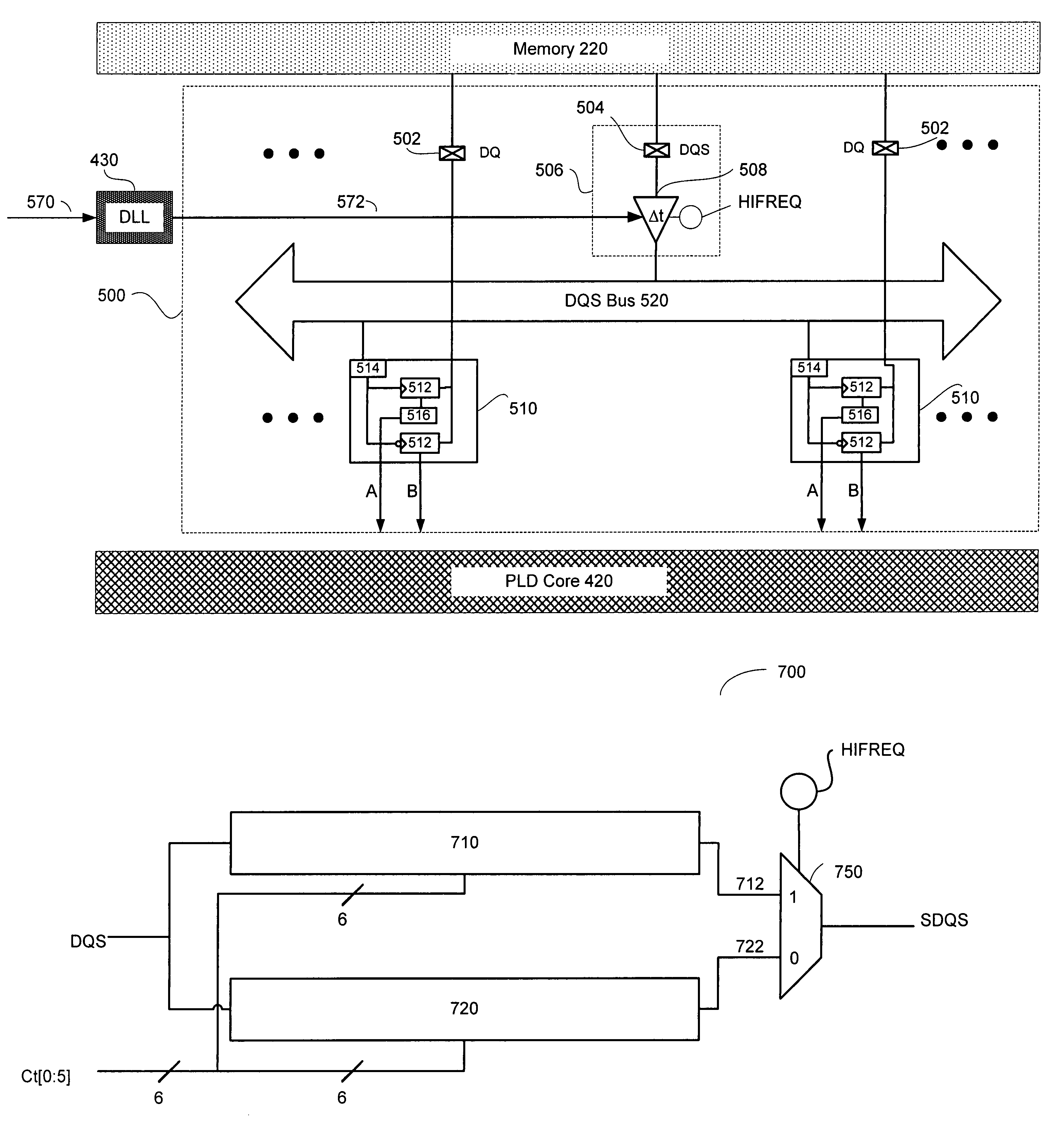
Memory interface phase-shift circuitry to support multiple frequency ranges
The present invention provides a phase shift circuit that supports multiple frequency ranges. The phase shift circuit receives a plurality of control bits and causes a phase shift in a received signal, the phase shift corresponding to a number of time steps, the number depending on the control bits, and the time step is selected from a plurality of different time steps based on a frequency range associated with the received signal.
Owner:BROOKE LAWRENCE L +1
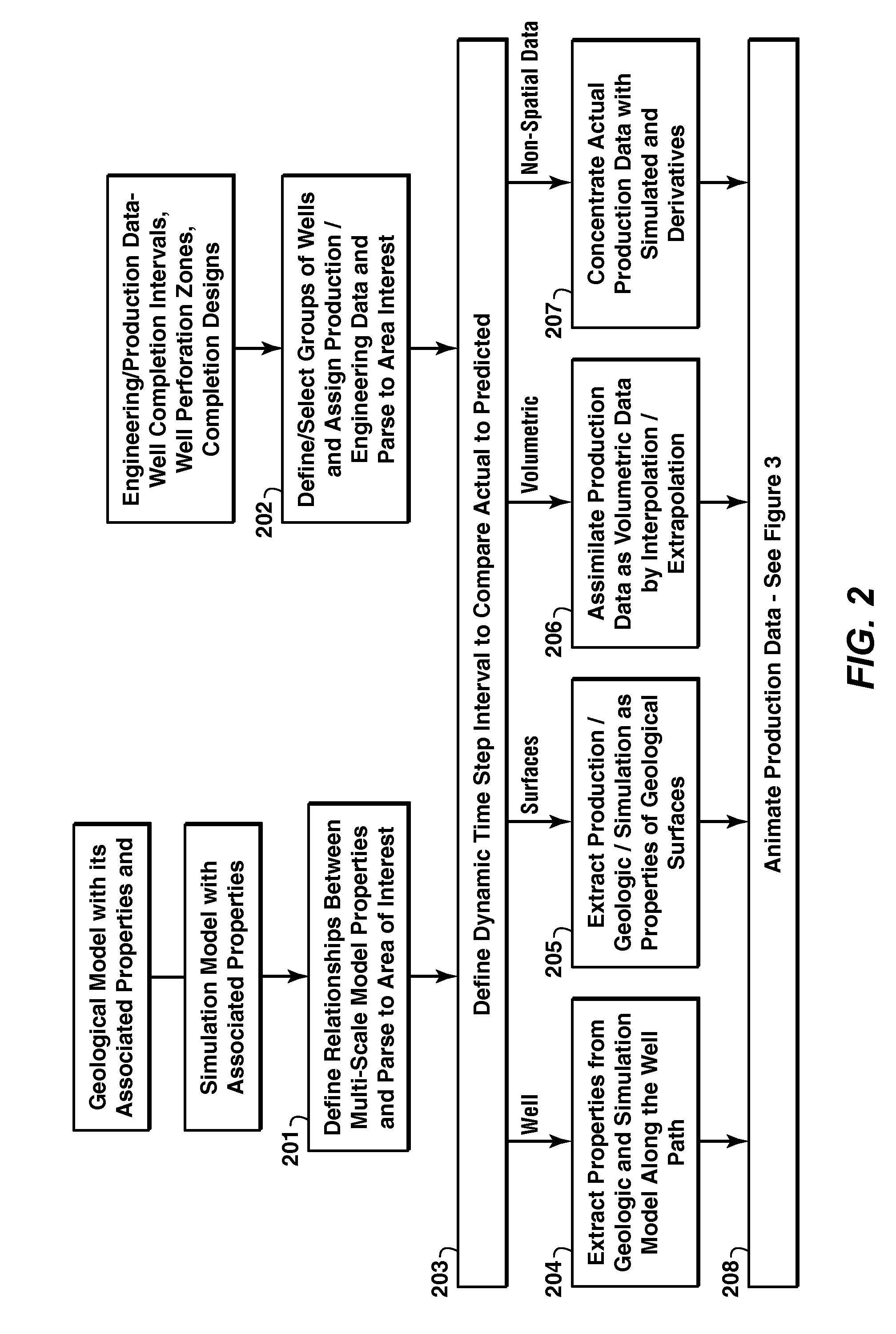
Iterative Reservoir Surveillance
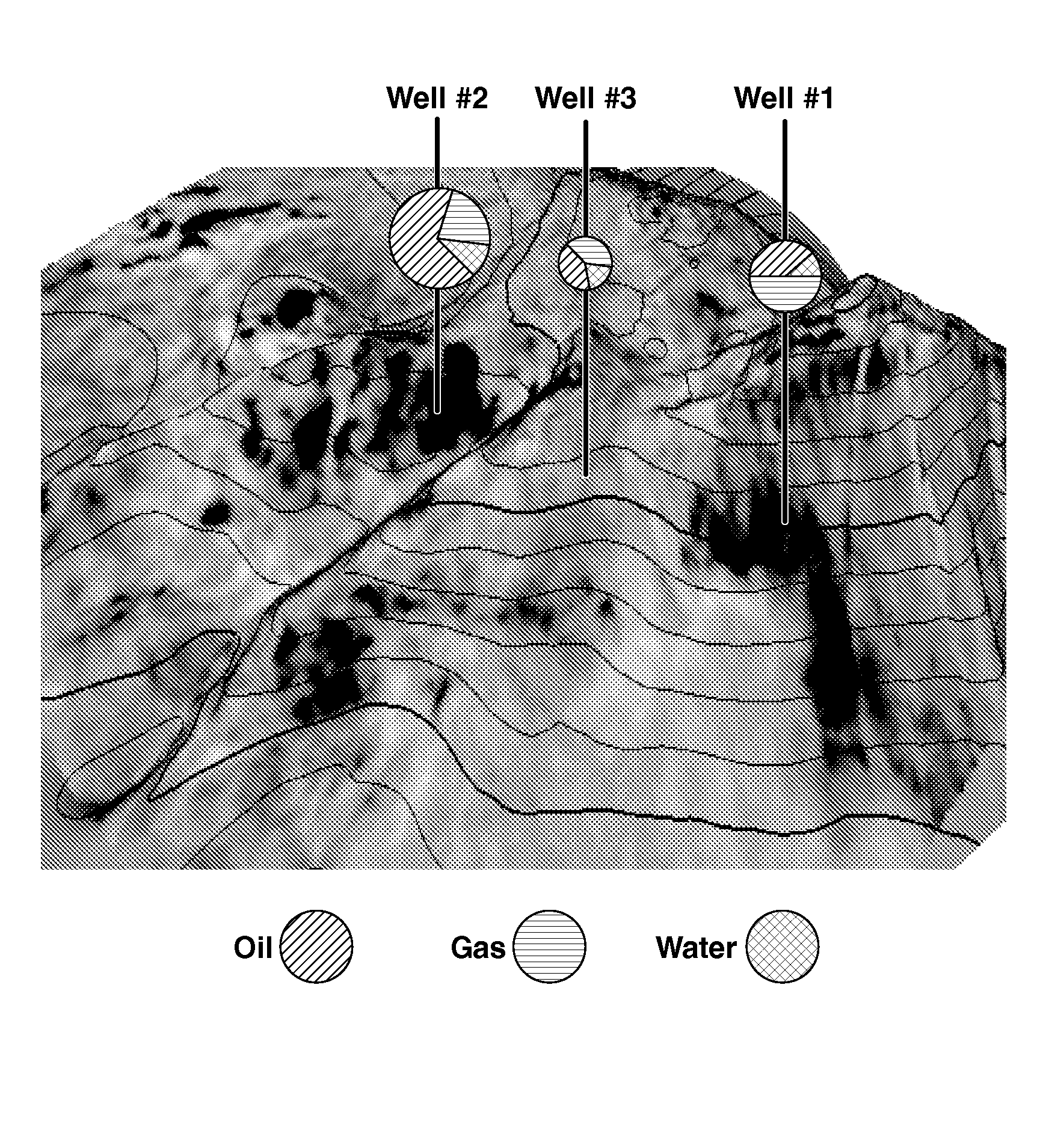
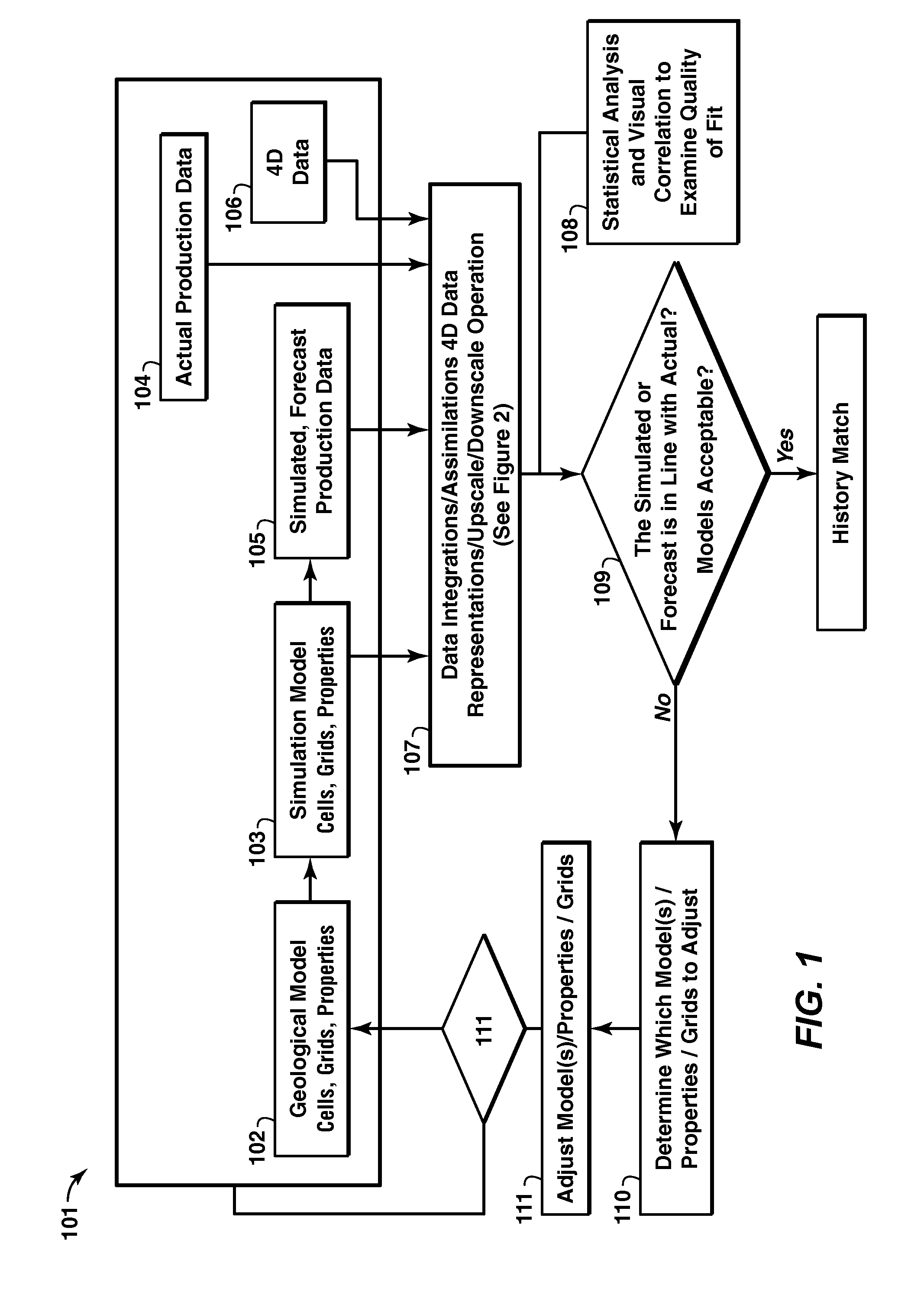
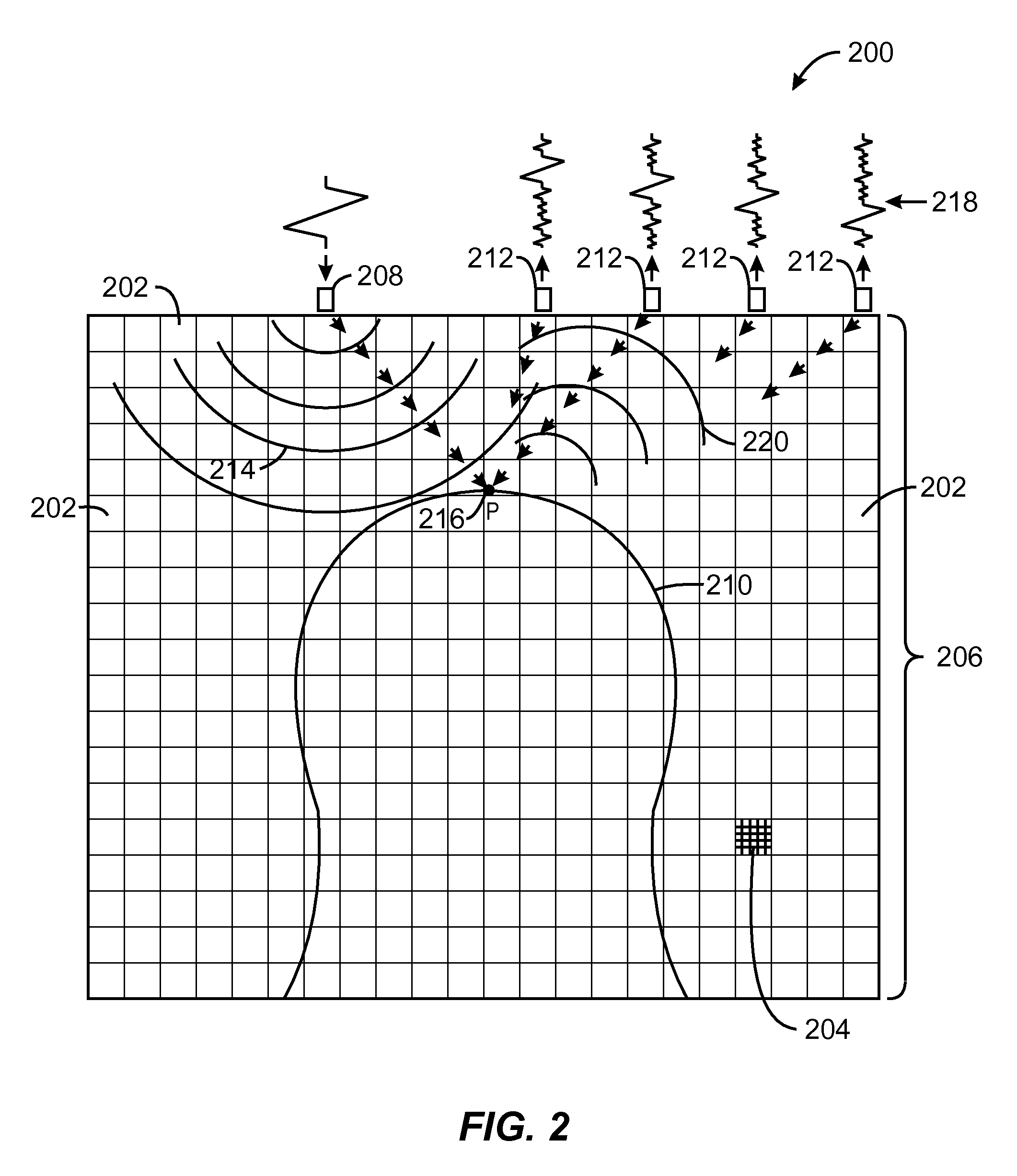
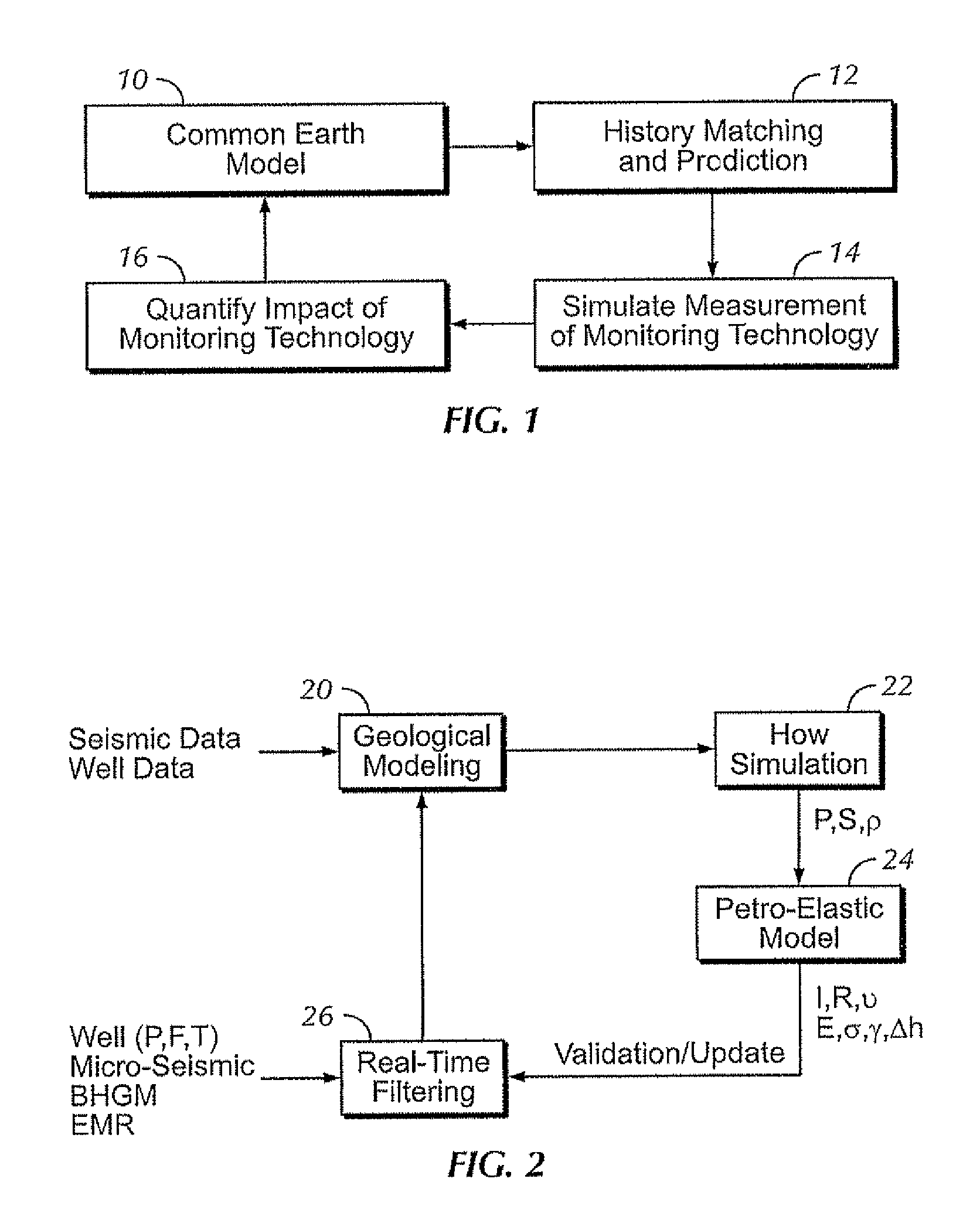
Method for reservoir surveillance using a three-dimensional Earth Model (101) to improve and expedite the surveillance at all scales of investigation (field, reservoir, fault compartment, and individual well) and at all time steps (minutes, hours, days, months, years). The new method allows users to rapidly identify anomalous field and well performance (109) and provides capability to investigate root causes of the performance deviation from predicted (110). Animated co-rendered displays (107) of the earth model and actual (104) and simulated (105) production data enable the user to interactively determine model adjustments back at the basic level of the Earth Model, which are then propagated to a geologic model (102) and then to the reservoir simulator (103) to update it (111) in a physically constrained way.
Owner:EXXONMOBIL UPSTREAM RES CO
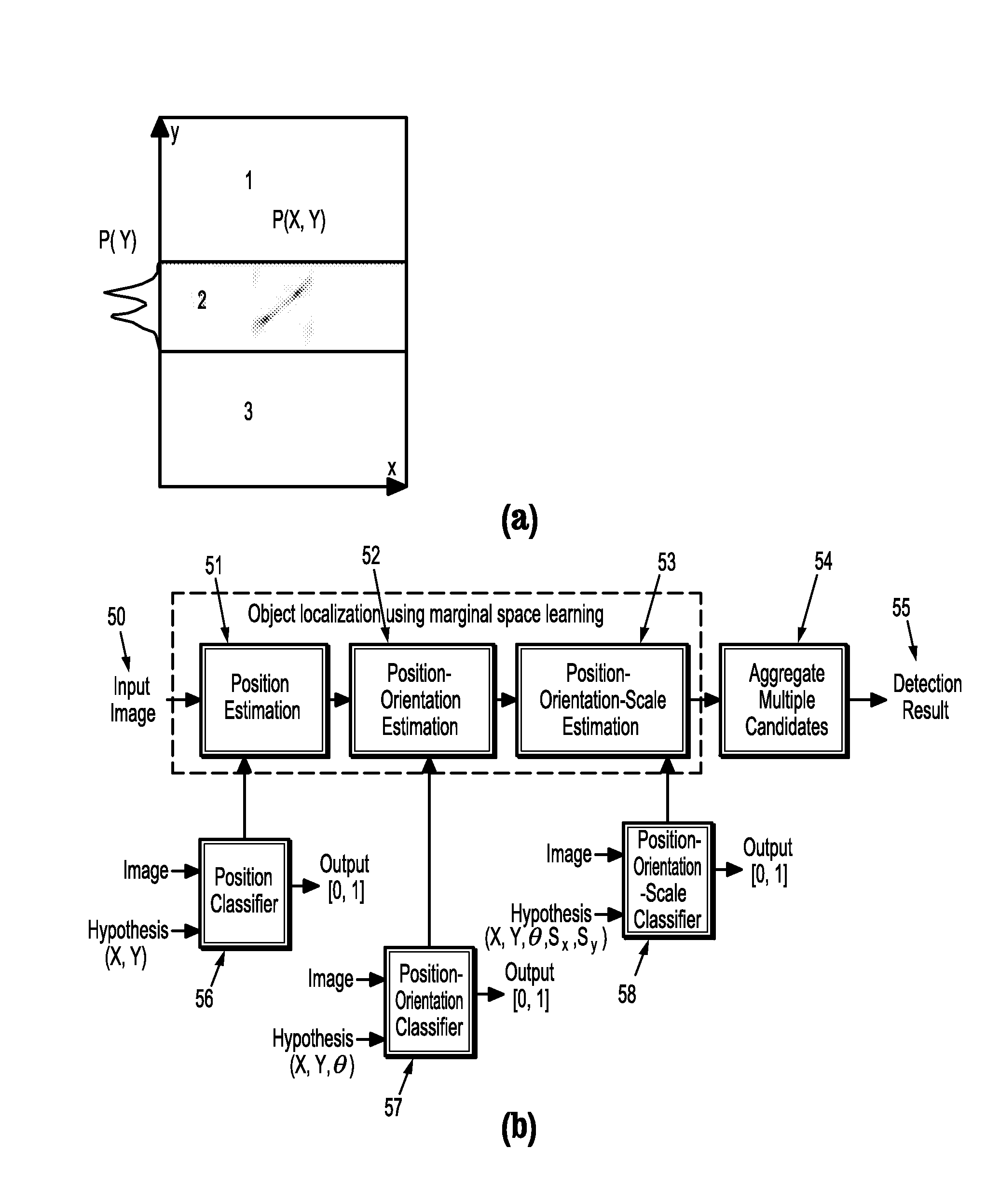
Marginal space learning for multi-person tracking over mega pixel imagery
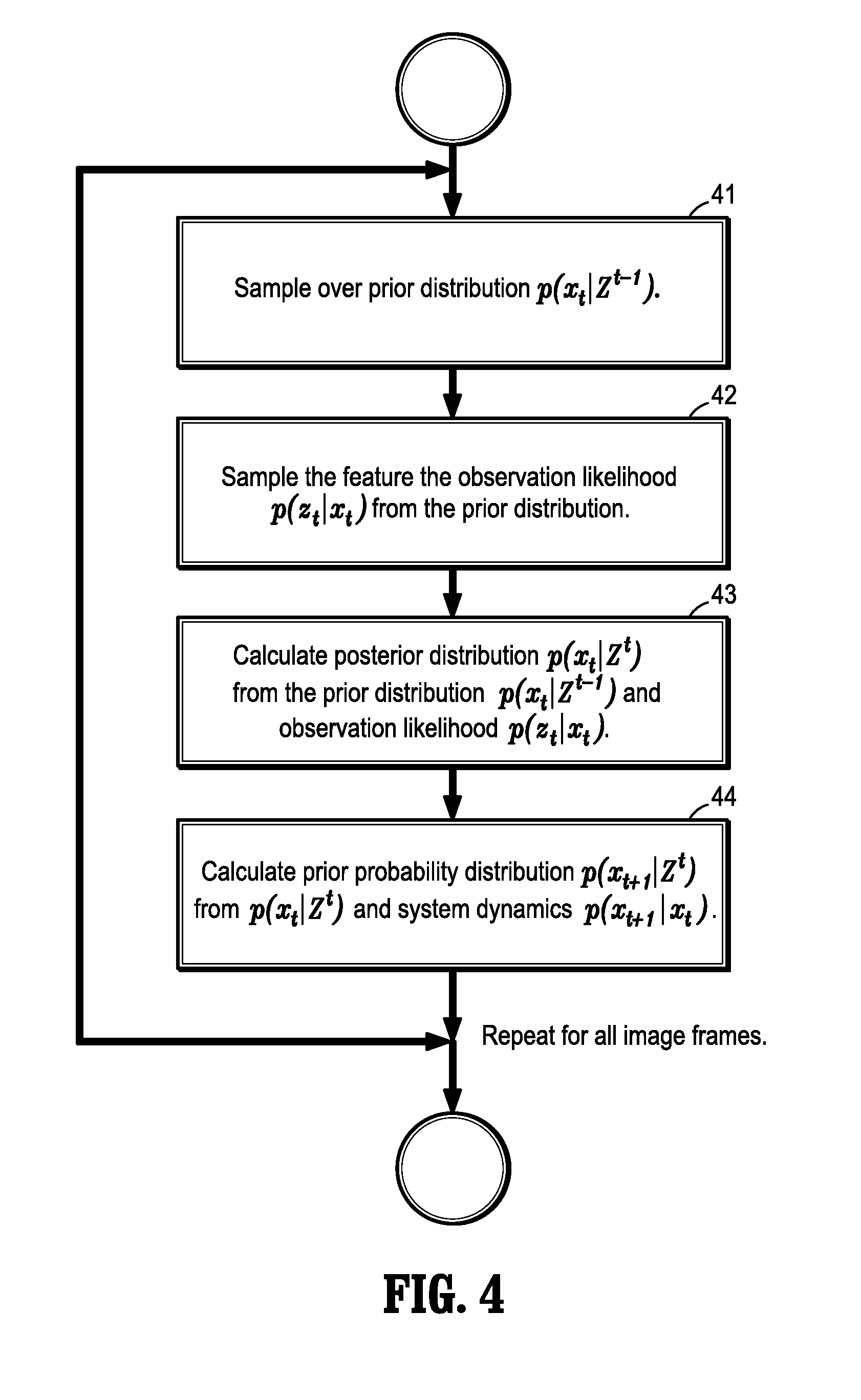
ActiveUS20120274781A1Facilitate high accuracy target trackingFacilitate re-acquisitionTelevision system detailsImage enhancementHypothesisMarginal space learning
A method for tracking pedestrians in a video sequence, where each image frame of the video sequence corresponds to a time step, includes using marginal space learning to sample a prior probability distribution p(xt|Zt−1) of multi-person identity assignments given a set of feature measurements from all previous image frames, using marginal space learning to estimate an observation likelihood distribution p(zt|xt) of the set of features given a set of multi-person identity assignments sampled from the prior probability distribution, calculating a posterior probability distribution p(xt|Zt) from the observation likelihood distribution p(zt|xt) and the prior probability distribution p(xt|Zt−1), and using marginal space learning to estimate the prior probability distribution p(xt+1|Zt) for a next image frame given the posterior probability distribution p(xt|Zt) and a probability p(xt+1|xt), where the posterior probability distribution of multi-person identity assignments corresponds to a set of pedestrian detection hypotheses for the video sequence.
Owner:SIEMENS HEALTHCARE GMBH
Method and system for checkpointing during simulations
ActiveUS20110288831A1Reduce computing costMinimal costAcoustic presence detectionSeismic data acquisitionParallel computingComputer memory
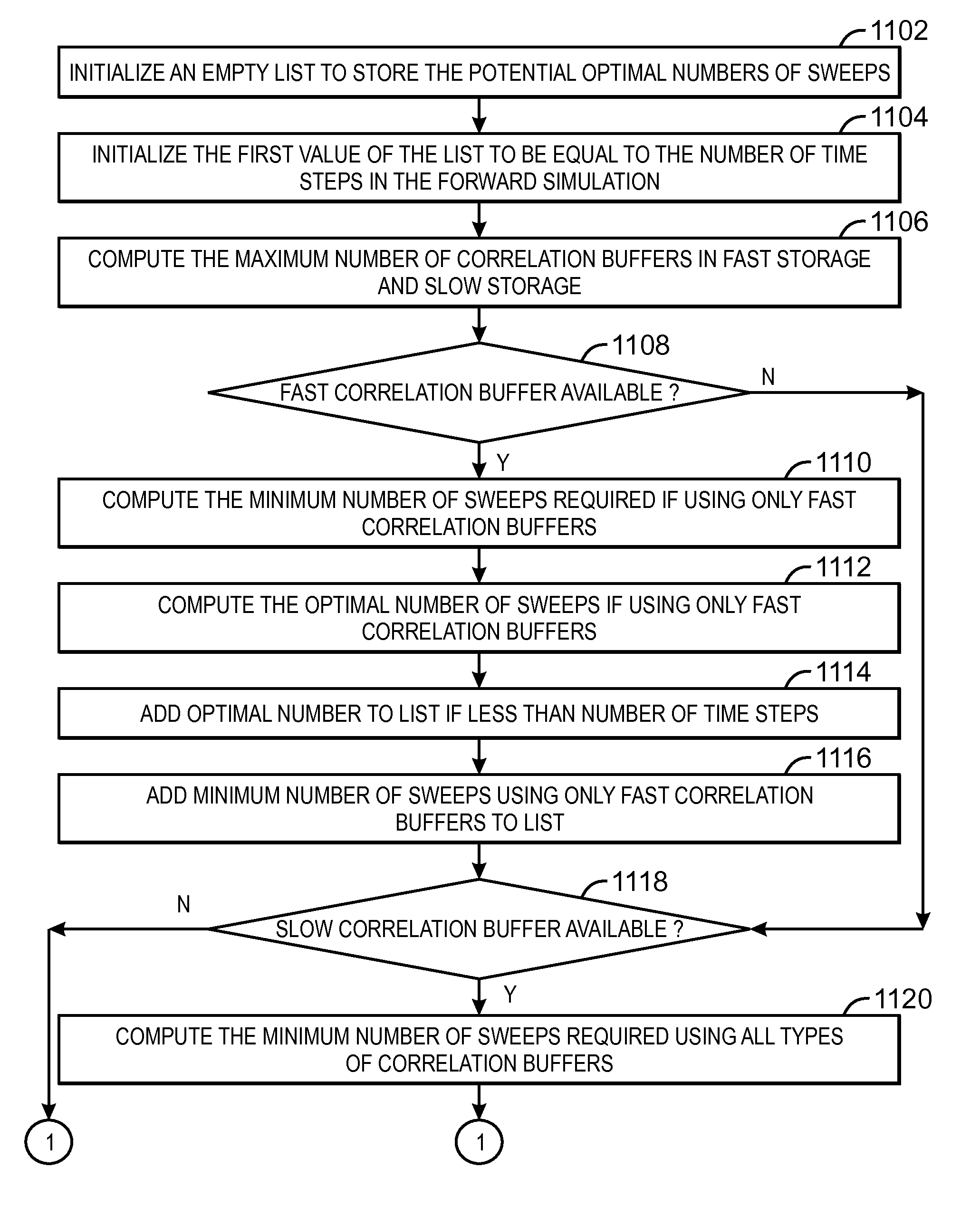
Method and system for more efficient checkpointing strategy in cross correlating (316) a forward (328) and backward (308) propagated wave such as in migrating (326) or inverting seismic data. The checkpointing strategy includes storing in memory forward simulation data at a checkpointed time step, wherein the stored data are sufficient to do a cross correlation at that time step but not to restart the forward simulation. At other checkpoints, a greater amount of data sufficient to restart the simulation may be stored in memory (314). Methods are disclosed for finding an optimal combination, i.e. one that minimizes computation time (1132), of the two types of checkpoints for a given amount of computer memory (1004), and for locating a checkpoint at an optimal time step (306, 1214, 1310). The optimal checkpointing strategy (1002) also may optimize (1408) on use of fast (1402) vs. slow (1404) storage.
Owner:EXXONMOBIL UPSTREAM RES CO
Vehicle autonomous parking path programming method used for multiple parking scenes
ActiveCN105857306APlanning results are safe and feasibleEasy to trackControl devicesRange of motionParking guidance and information
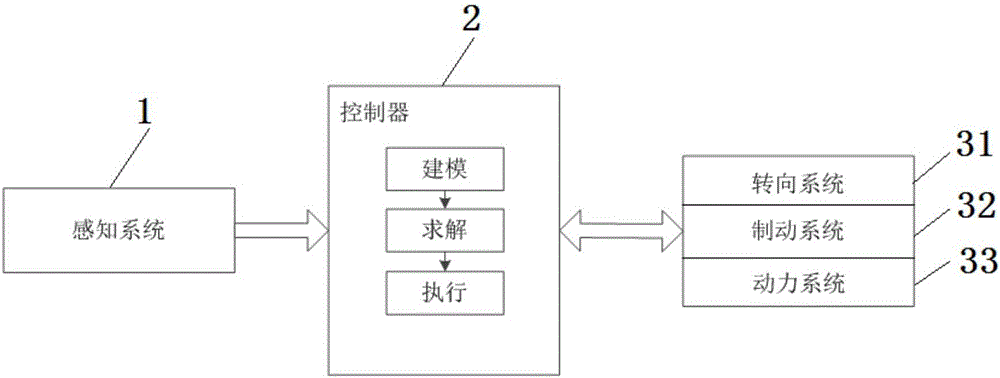
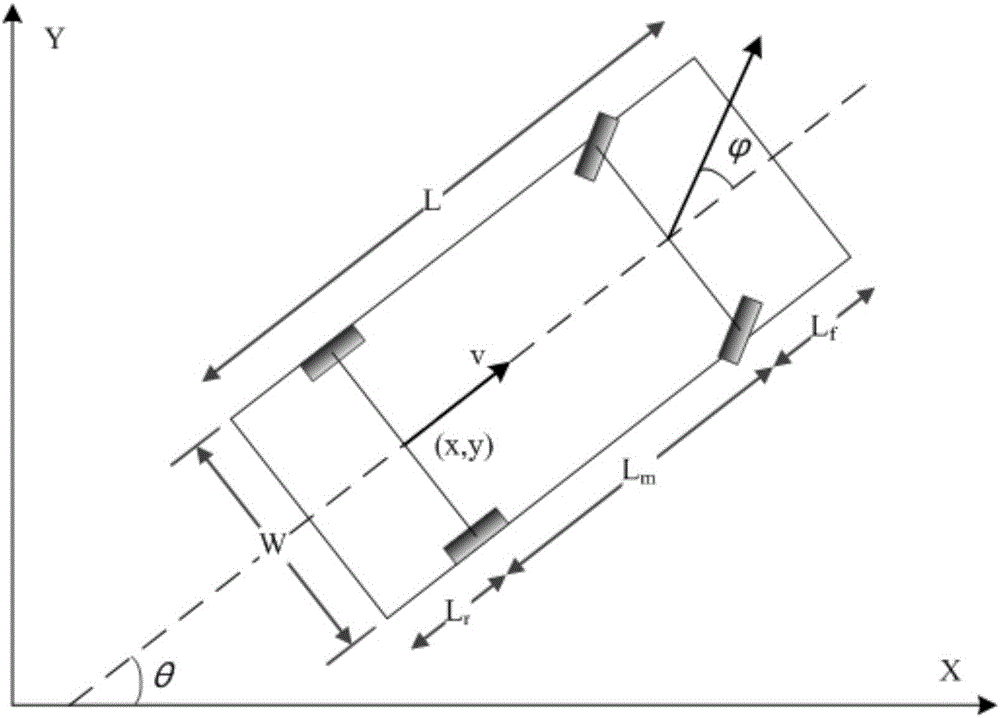
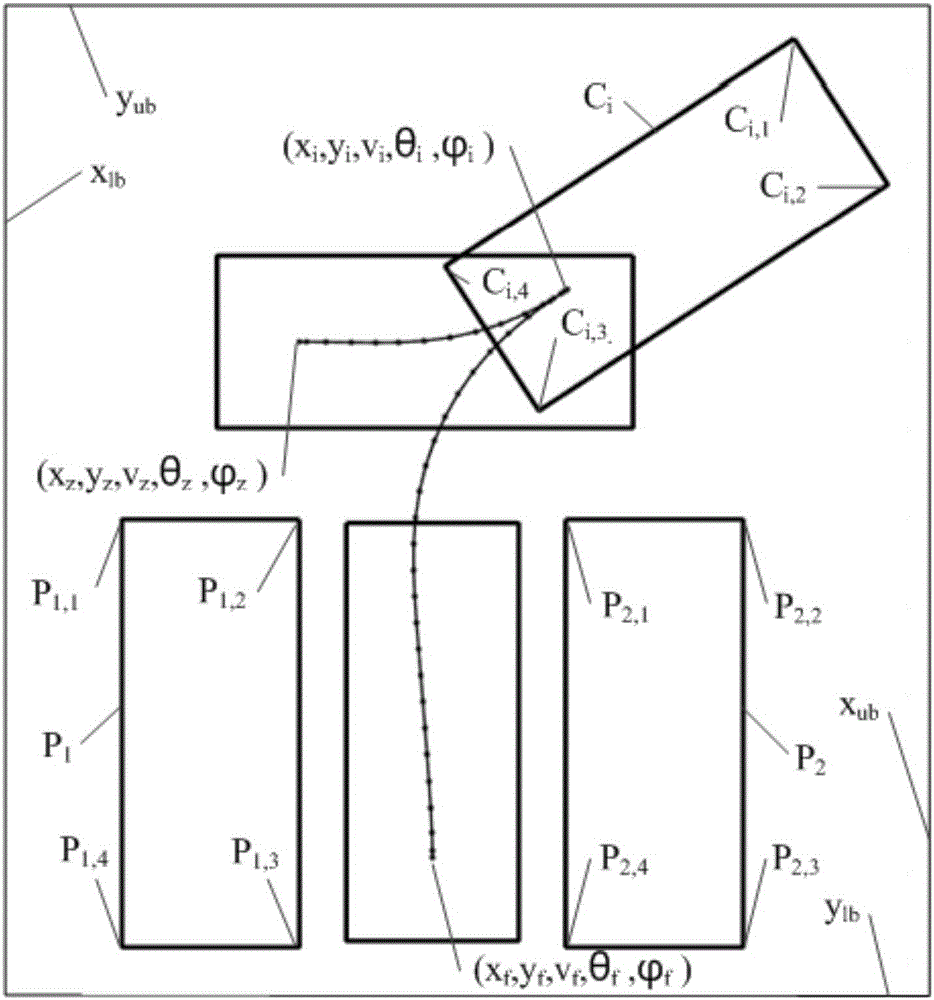
The invention provides a vehicle autonomous parking path programming method used for multiple parking scenes. The method is used for automatically parking a vehicle in a parking space through an autonomous parking system when the autonomous parking system detects the available parking space. The method includes the steps that target parking space information is detected, and a parking scene is determined; the initial state and target state of the to-be-parked vehicle are determined; a vehicle kinematics differential equation is established; state variables and control variables of the vehicle are segmented, equidistance sampling is performed on each segment according to certain time step, and to-be-optimized variables are obtained; an equality constraint, boundary constraints and inequality constraints of the to-be-optimized variables are formed; motion range constraints of the to-be-parked vehicle are formed according to the motion range limit in the parking process of the vehicle; an optimization objective is determined, and an objective function is established; and by means of a nonlinear programming solver, an optimal solution of a parking path is obtained. The vehicle autonomous parking path programming method is suitable for the multiple parking scenes, the design is reasonable, abundant information can be provided so as to control autonomous parking of the vehicle, and the security coefficient is high.
Owner:HEFEI INSTITUTES OF PHYSICAL SCIENCE - CHINESE ACAD OF SCI
Game machine, game processing method and information storage medium
InactiveUS20020025842A1Enhancing its appealVideo gamesSpecial data processing applicationsSimulationTime step
Owner:KONAMI DIGITAL ENTERTAINMENT CO LTD
Price and risk evaluation system for financial product or its derivatives, dealing system, recording medium storing a price and risk evaluation program, and recording medium storing a dealing program
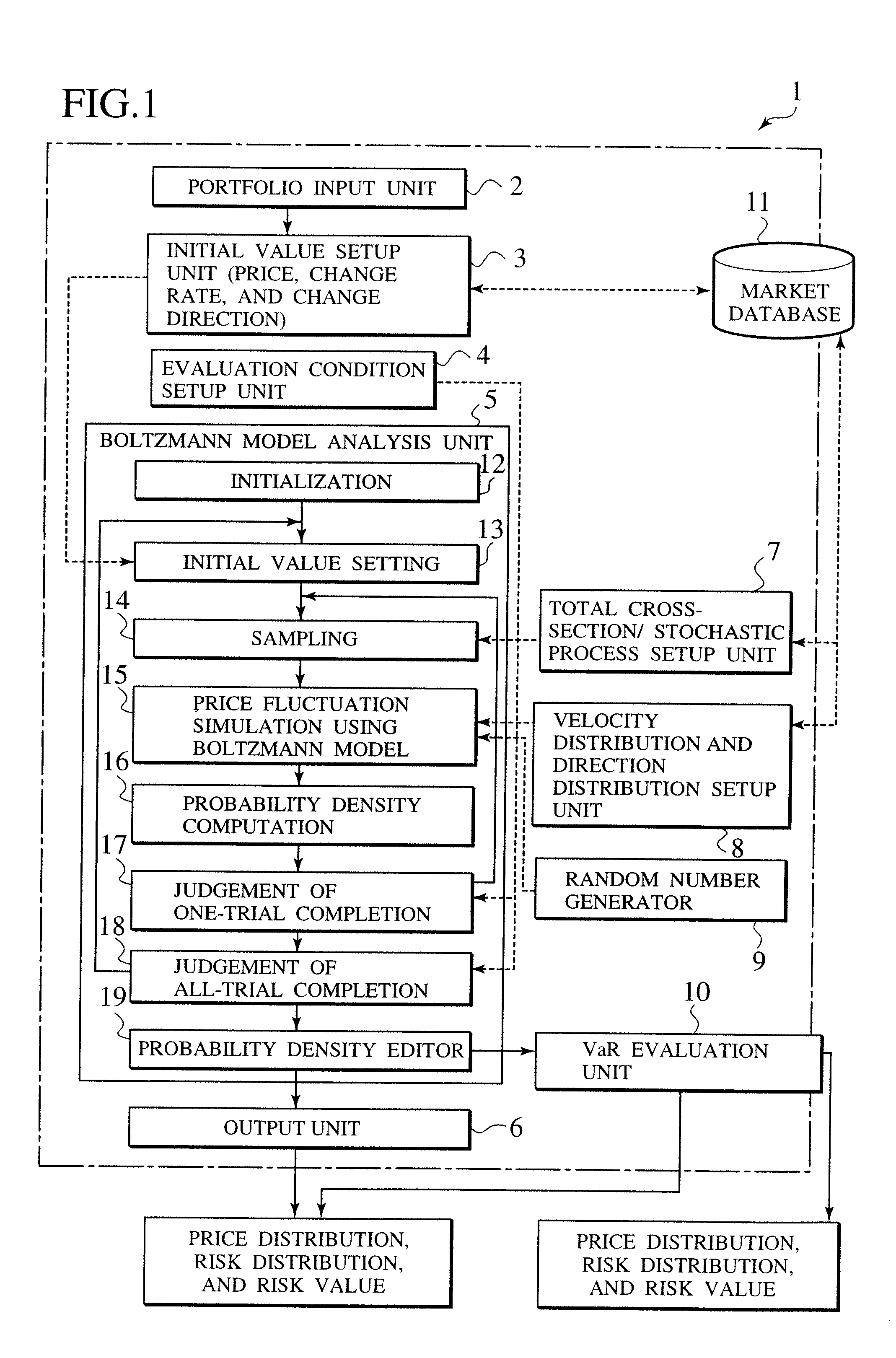
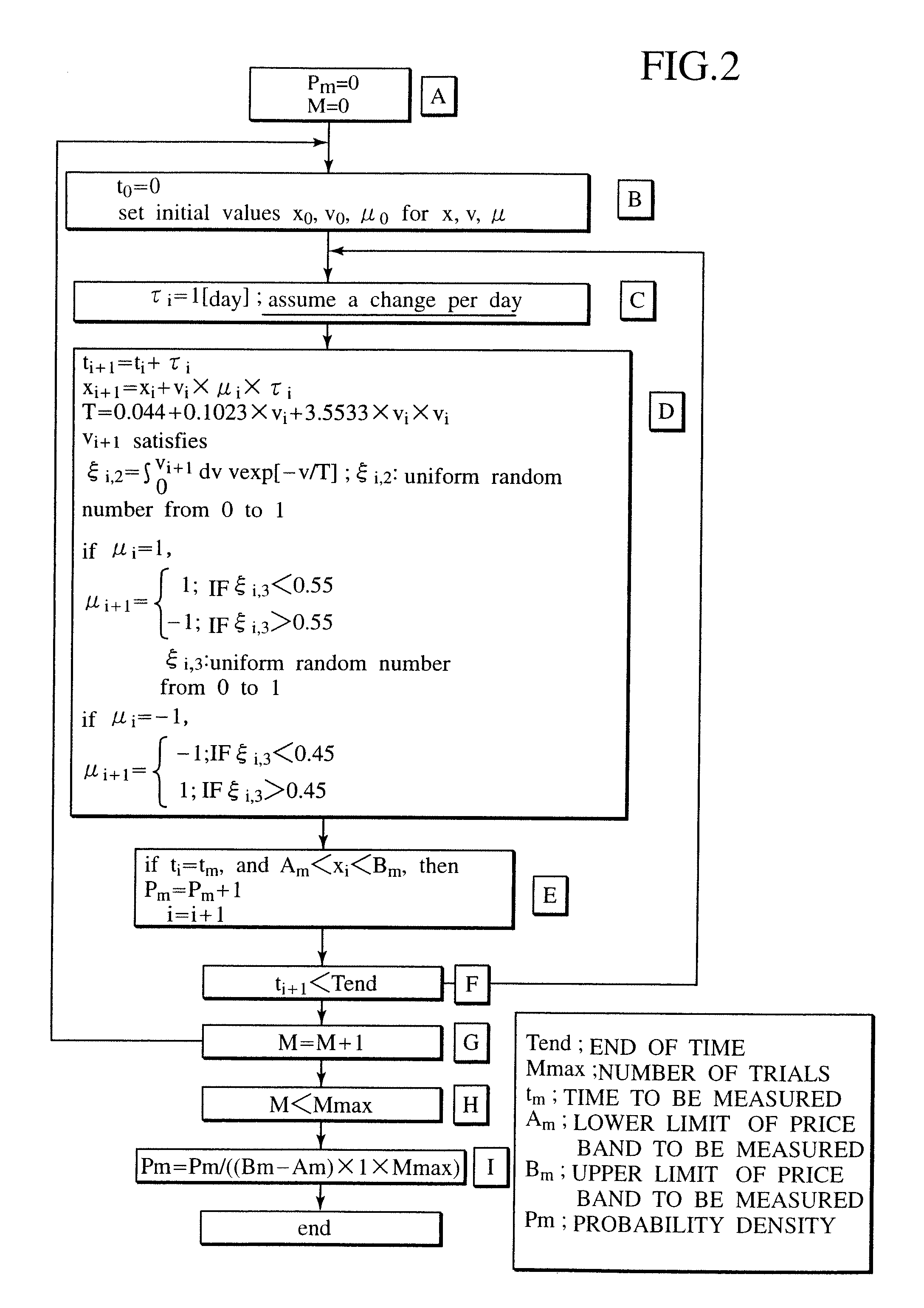
A system for correctly evaluating a price distribution and a risk distribution for a financial product or its derivatives introduces a probability density function generated with a Boltzmann model at a higher accuracy than the Gaussian distribution for a probability density. The system has an initial value setup unit and an evaluation condition setup unit. Initial values include at least one of price, price change rate, and the price change direction of a financial product. The evaluation conditions include at least time steps and the number of trials. The Boltzmann model analysis unit receives the initial values and the evaluation conditions, and repeats simulations of price fluctuation, based on the Boltzmann model using a Monte Carlo method. A velocity / direction distribution setup unit supplies the probability distributions of the price, price change rate, and the price change direction for the financial product to the Boltzmann model analysis unit. A random number generator for a Monte Carlo method employed in the analysis by the Boltzmann model, and an output unit displays the analysis result. A dealing system applies the financial Boltzmann model to option pricing, and reproduces the characteristics of Leptokurcity and Fat-tail by linear Boltzmann equation in order to define risk-neutral and unique probability measures. Consequently, option prices can be evaluated in a risk-neutral and unique manner, taking into account Leptokurcity and Fat-tail of a price change distribution.
Owner:KK TOSHIBA
System and method for using login correlations to detect intrusions
InactiveUS7085936B1Overcome problemsEnabling detectionDigital data processing detailsUnauthorized memory use protectionContinuationTimestamp
A system and method are disclosed for detecting intrusions in a host system on a network. The intrusion detection system comprises an analysis engine configured to use continuations and apply forward- and backward-chaining using rules. Also provided are sensors, which communicate with the analysis engine using a meta-protocol in which the data packet comprises a 4-tuple. A configuration discovery mechanism locates host system files and communicates the locations to the analysis engine. A file processing mechanism matches contents of a deleted file to a directory or filename, and a directory processing mechanism extracts deallocated directory entries from a directory, creating a partial ordering of the entries. A signature checking mechanism computes the signature of a file and compares it to previously computed signatures. A buffer overflow attack detector compares access times of commands and their associated files. The intrusion detection system further includes a mechanism for checking timestamps to identify and analyze forward and backward time steps in a log file.
Owner:SYMANTEC CORP
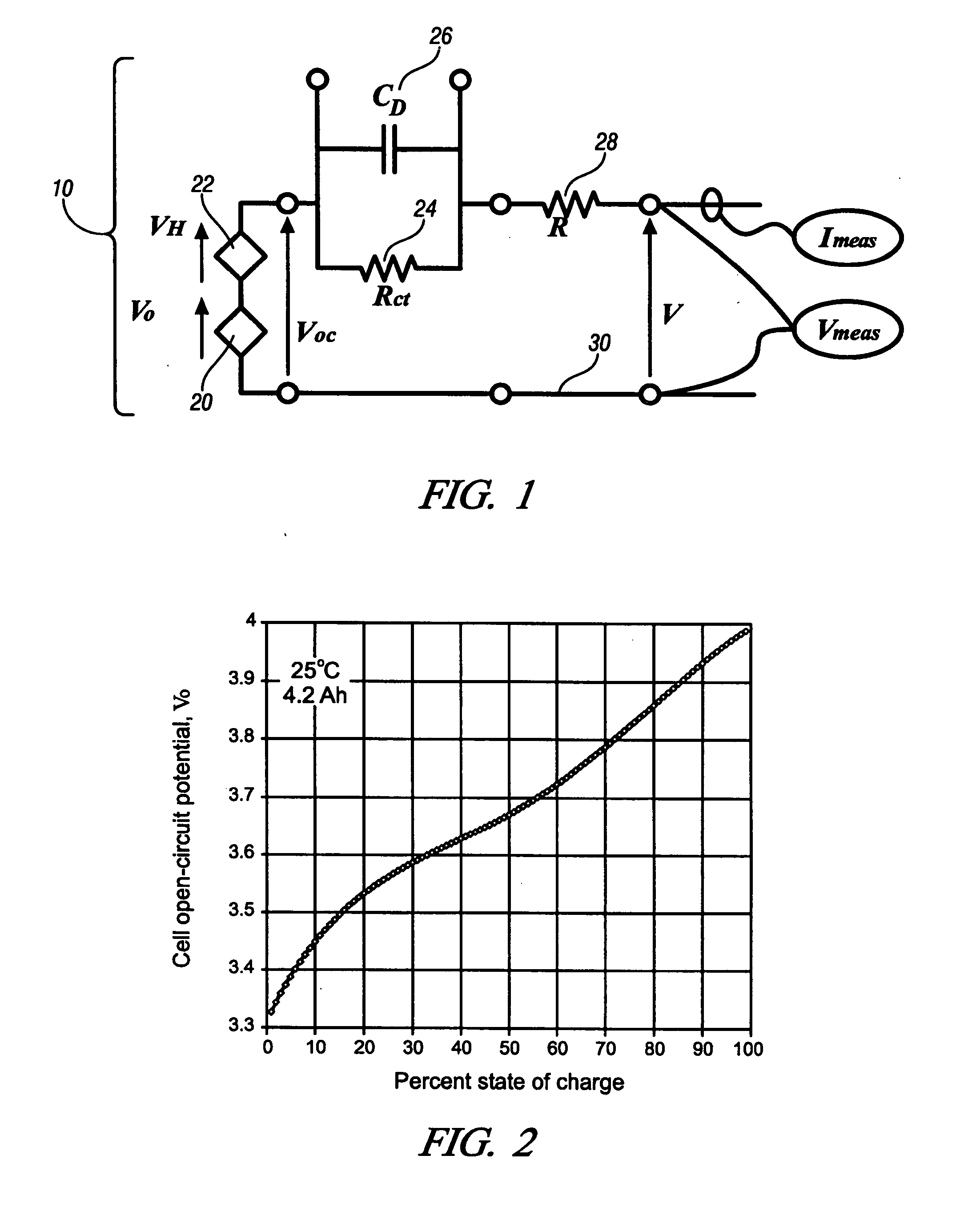
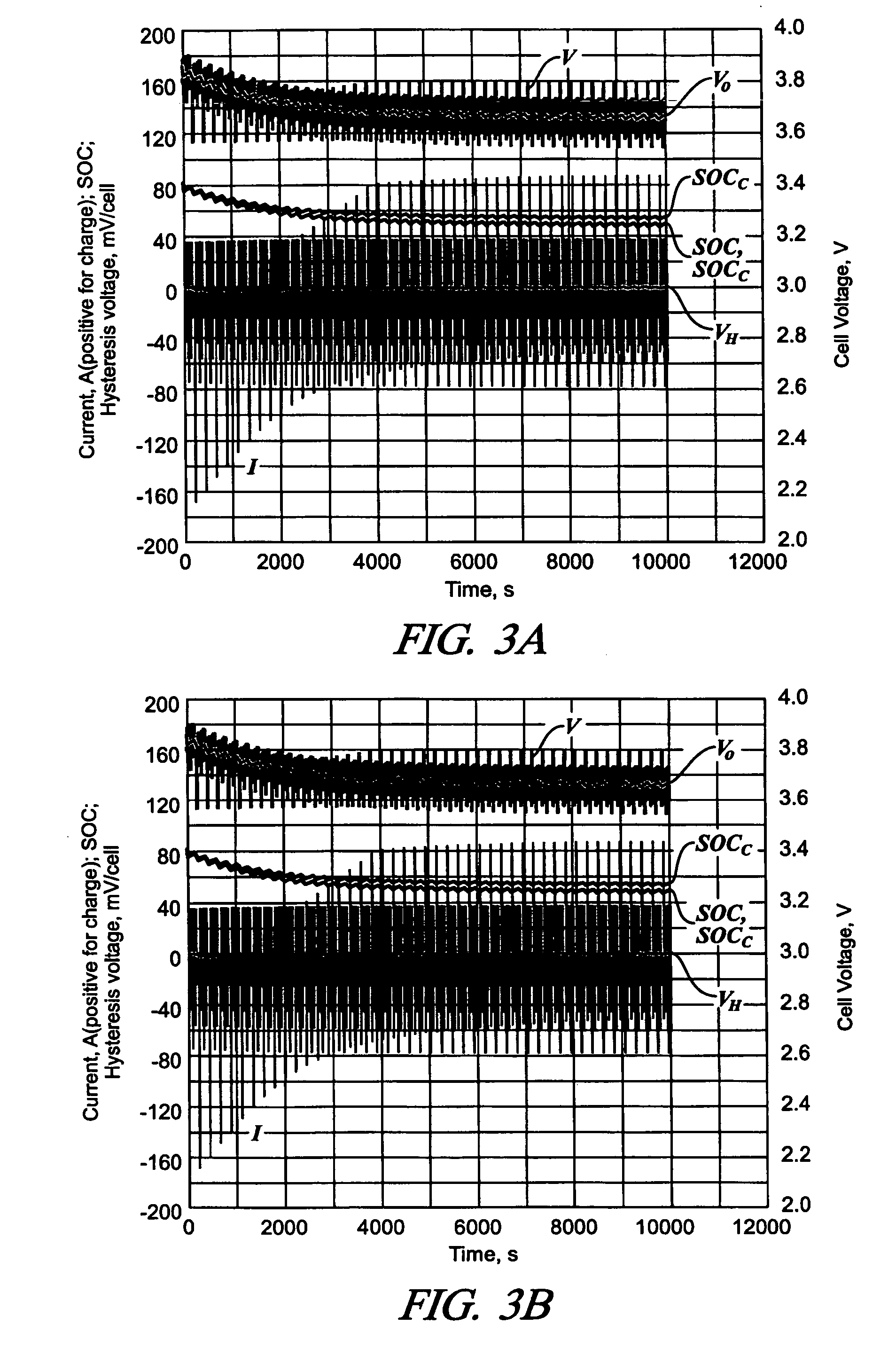
Method for control and monitoring using a state estimator having variable forgetting factors
ActiveUS20060284600A1Stable resistance valueImprove accuracyBatteries circuit arrangementsElectrical testingAlgorithmForgetting factor
A recursive algorithm is provided for adaptive multi-parameter regression enhanced with forgetting factors unique to each regressed parameter. Applications of this algorithm can include lead acid batteries, nickel-metal hydride batteries, and lithium-ion batteries, among others. A control algorithm is presented, having an arbitrary number of model parameters, each having its own time-weighting factor. A method to determine optimal values for the time-weighting factors is included, to give greater effect to recently obtained data for the determination of a system's state. A methodology of weighted recursive least squares is employed, wherein the time weighting corresponds to the exponential-forgetting formalism. The derived mathematical result does not involve matrix inversion, and the method is iterative, i.e. each parameter is regressed individually at every time step.
Owner:GM GLOBAL TECH OPERATIONS LLC
Methods and systems for improved integrated circuit functional simulation
InactiveUS20050091025A1Reduce in quantityElectrical apparatusComputer aided designSymbolic simulationBinary decision diagram
Methods and systems for performing symbolic simulation, including techniques for translating a conventional simulation into a symbolic simulation, for handling wait and delay states, and for performing temporally out-of-order simulations. Additional techniques for extracting a signal graph from an HDL representation of a device, for representing signal values as functions of time using binary decision diagrams, and for computing minimal signal sets for accurate simulation. Techniques and methods for improving waveform dumping, reducing the waveform database, and for combining out-of-order simulation or reduced time steps with conventional time-based simulation.
Owner:VENTURE LENDING & LEASING IV
Intelligent System for Collecting Readings From Electric Meters
InactiveUS20080186201A1Good expansion possibilityImprove management efficiencyElectric signal transmission systemsTariff metering apparatusFeature completeCarrier signal
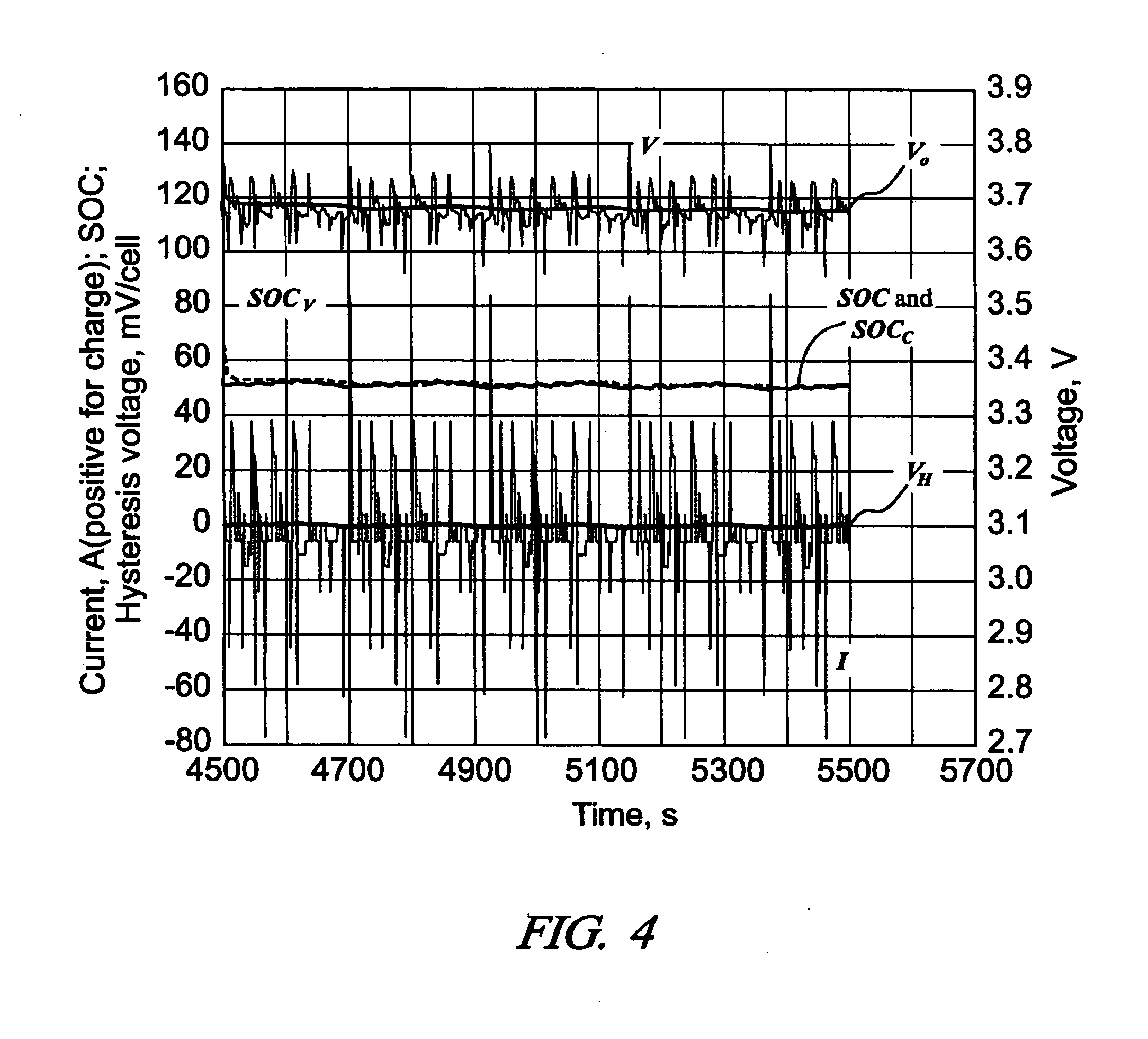
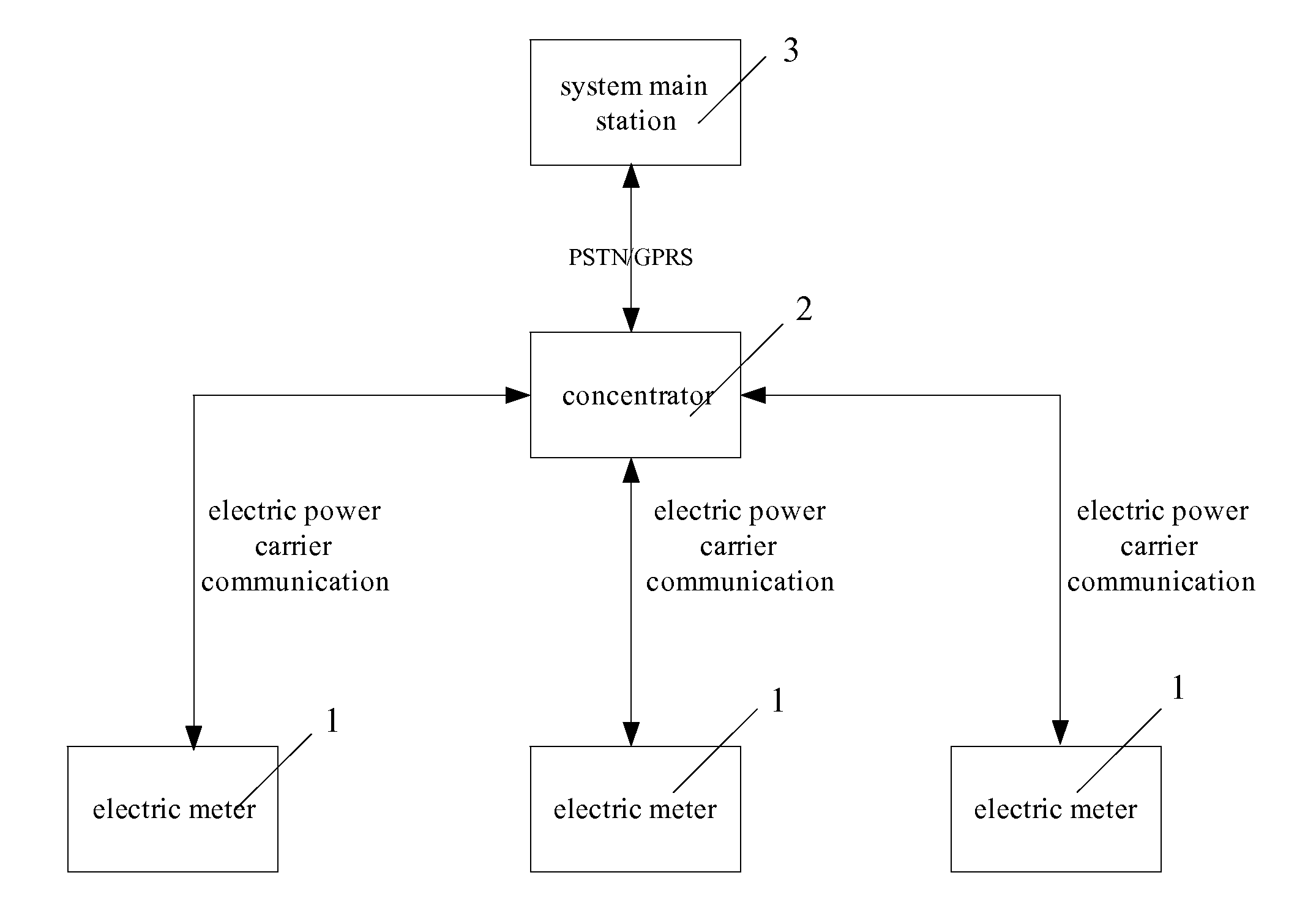
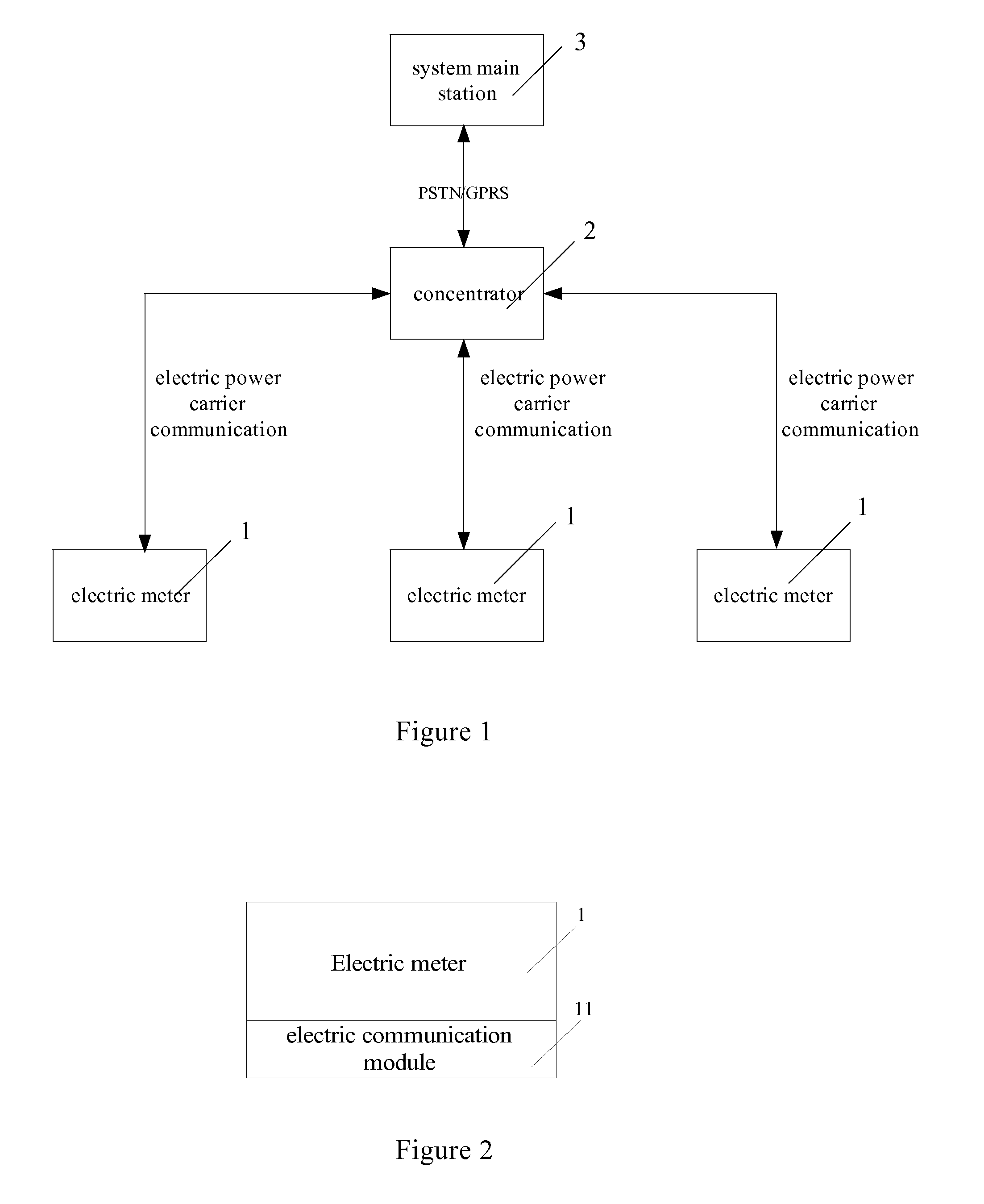
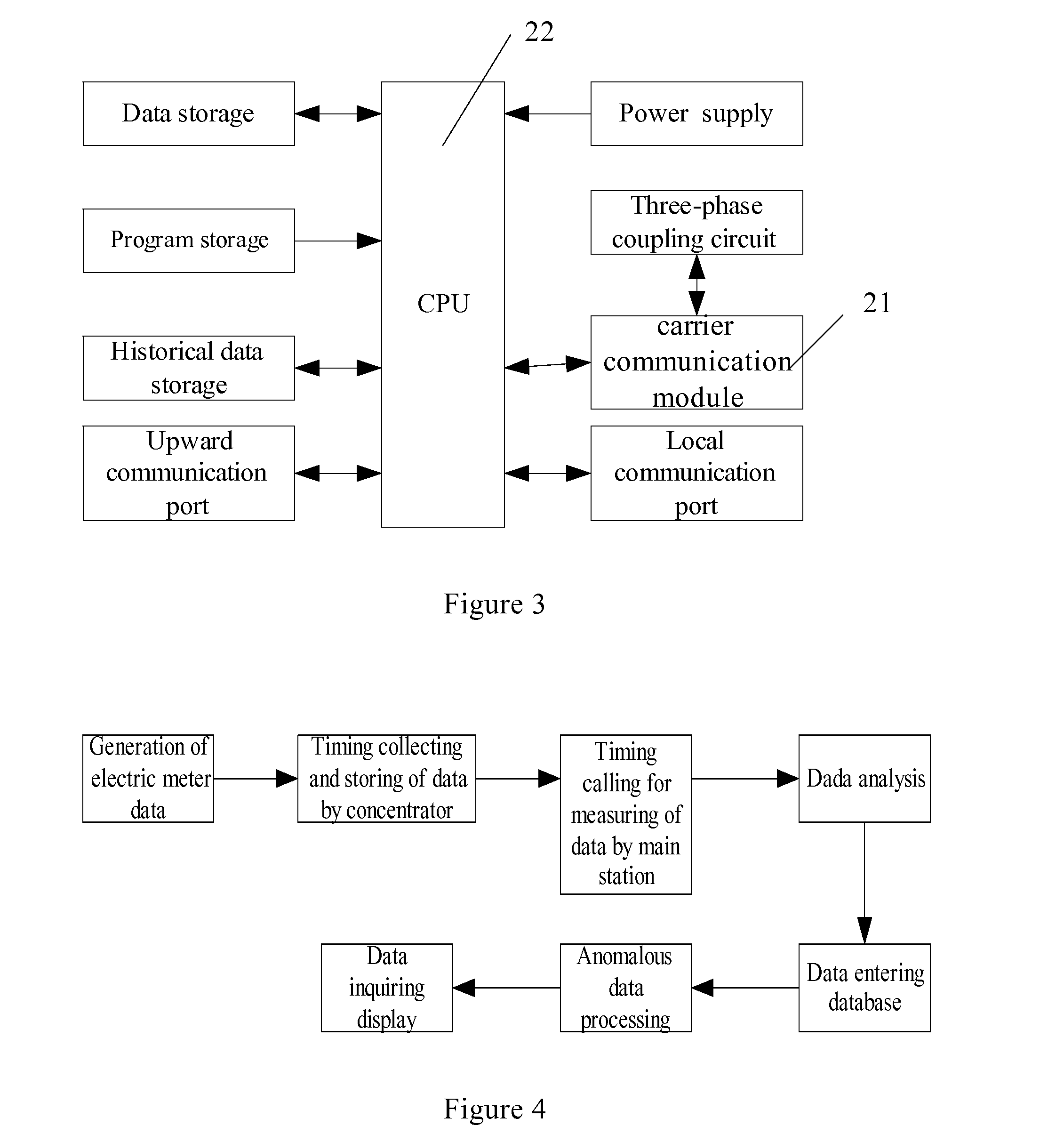
An intelligent system for collecting readings from electric meters, comprising the following components: several electric meters, a data concentrator connected to the electric meters, and a system main station connected to the concentrator wirelessly, in which: the electric meter for recording the consumed quantity of electricity by user, metering the quantity of electricity, measuring demand and making a fault recording, and supporting a time-sharing measurement and communication with the data concentrator by electric power carrier; a concentrator for providing intelligent relay management, implementing the communication with the electric meters and the system main station, the management of communication route of electric meters and the storage function of data; the system main station for realizing a stable bi-directional communication with the concentrator and several electric meters, reading data in the concentrator, collecting information on electric energy, synchronizing the time of the concentrator and the electric meters associated therewith, renewing time step tariff rate and meter parameters of the electric meters. Bi-directional stable communication between the main station and the intelligent electric meters and collection of electrical energy information and the adjustment of parameters of electric meters can be realized by transmission medium in the present invention. The system of the present invention features complete functions, stable user-friendly operation interface, and has good expansion potential. Therefore this system is an important technical means for user-side management. The present invention greatly improves management efficiency and economic benefits in the electrical power department.
Owner:SHANGHAI JIULONG ELECTRIC POWER GROUP +1
Game machine, game processing method and information storage medium
Owner:KONAMI DIGITAL ENTERTAINMENT CO LTD
Game machine, game processing method and information storage medium
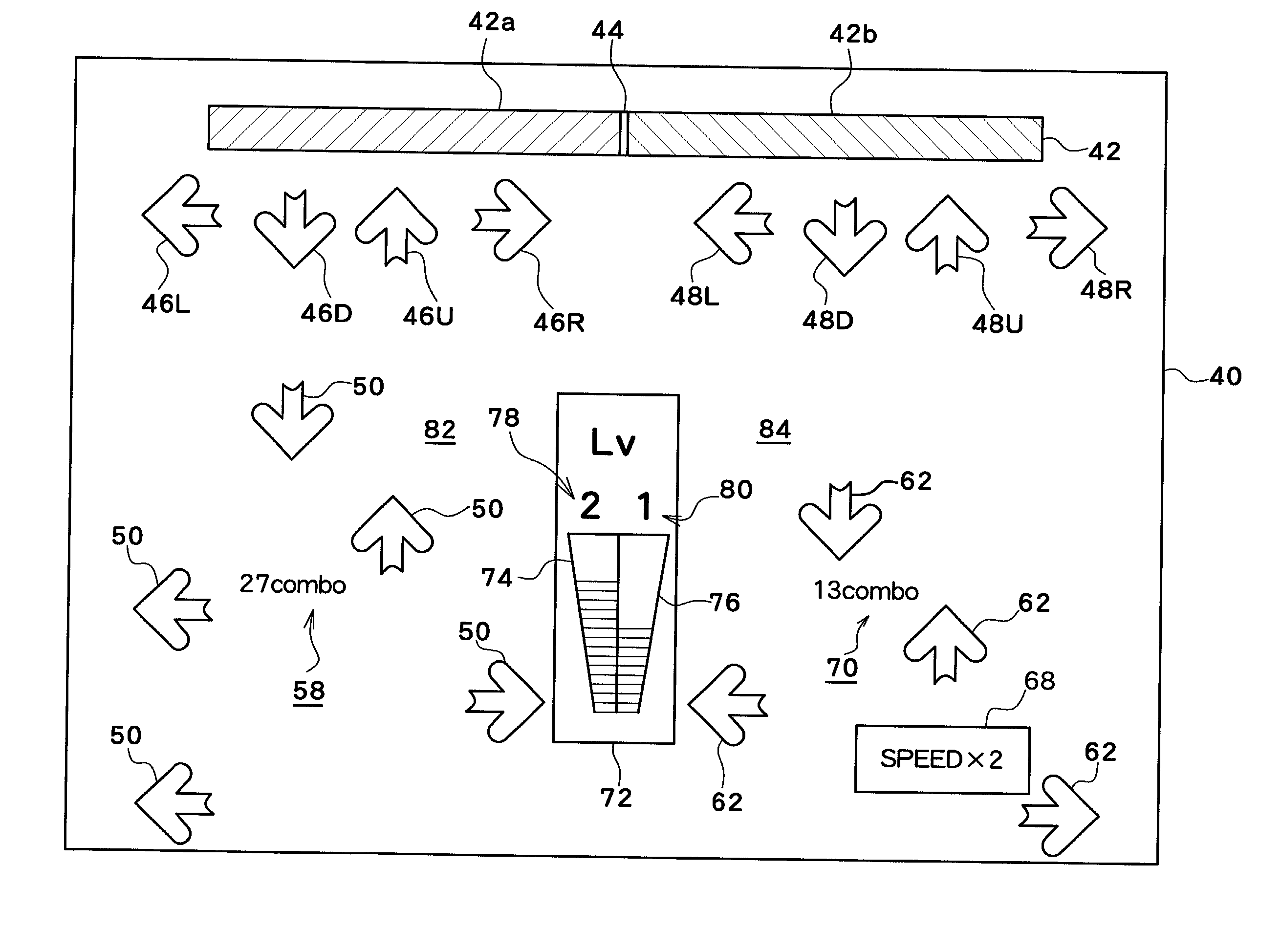
InactiveUS7128649B2Increase attractivenessCosmonautic condition simulationsRegistering/indicating time of eventsSimulationGame machine
A music-oriented game machine with a feature to increase a feeling of competitiveness between players. Based on an evaluation of a performance of the first and second players based on their steps, the number of times step timing is presented as guidance is varied. Specifically, while reference arrows (46, 48) are displayed, a plurality of timing guidance arrows (50, 62) approaching the reference arrows (46, 48) are also displayed on a game screen image (40). As a result, guidance as to where step timing is arriving is shown to the player. Then, a speed at which the reference arrows (46, 48) approach the timing guidance arrows (50, 62), respectively, is changed from a default speed to speeds of half, twice, and three-times the default speed based on the result of evaluation on the respective player's stepping performances, to thereby change the guidance level.
Owner:KONAMI DIGITAL ENTERTAINMENT CO LTD
Method for Predicting Outputs of Photovoltaic Devices Based on Two-Dimensional Fourier Analysis and Seasonal Auto-Regression
InactiveUS20130262049A1Generation forecast in ac networkData processing applicationsRegression analysisPredictive methods
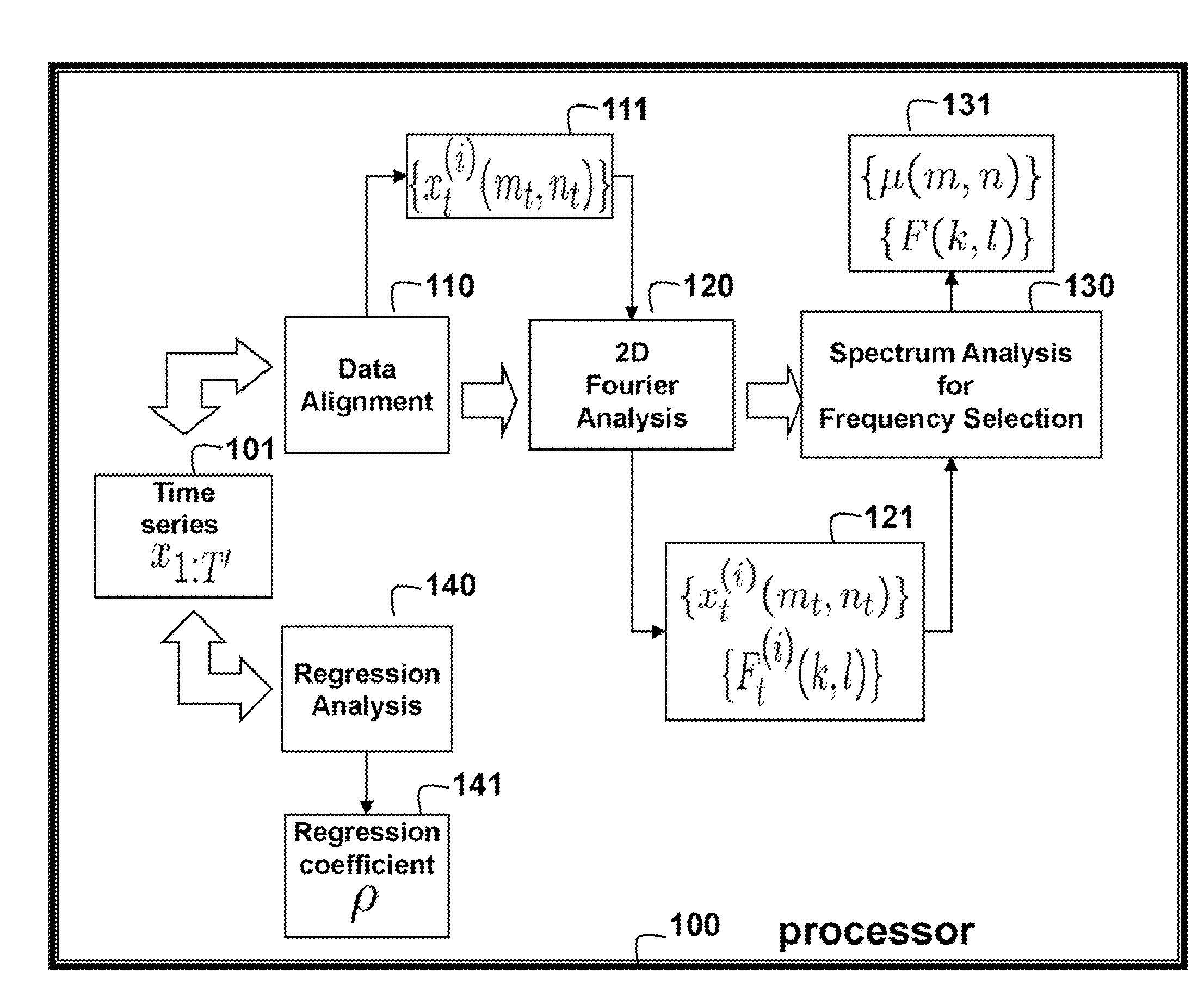
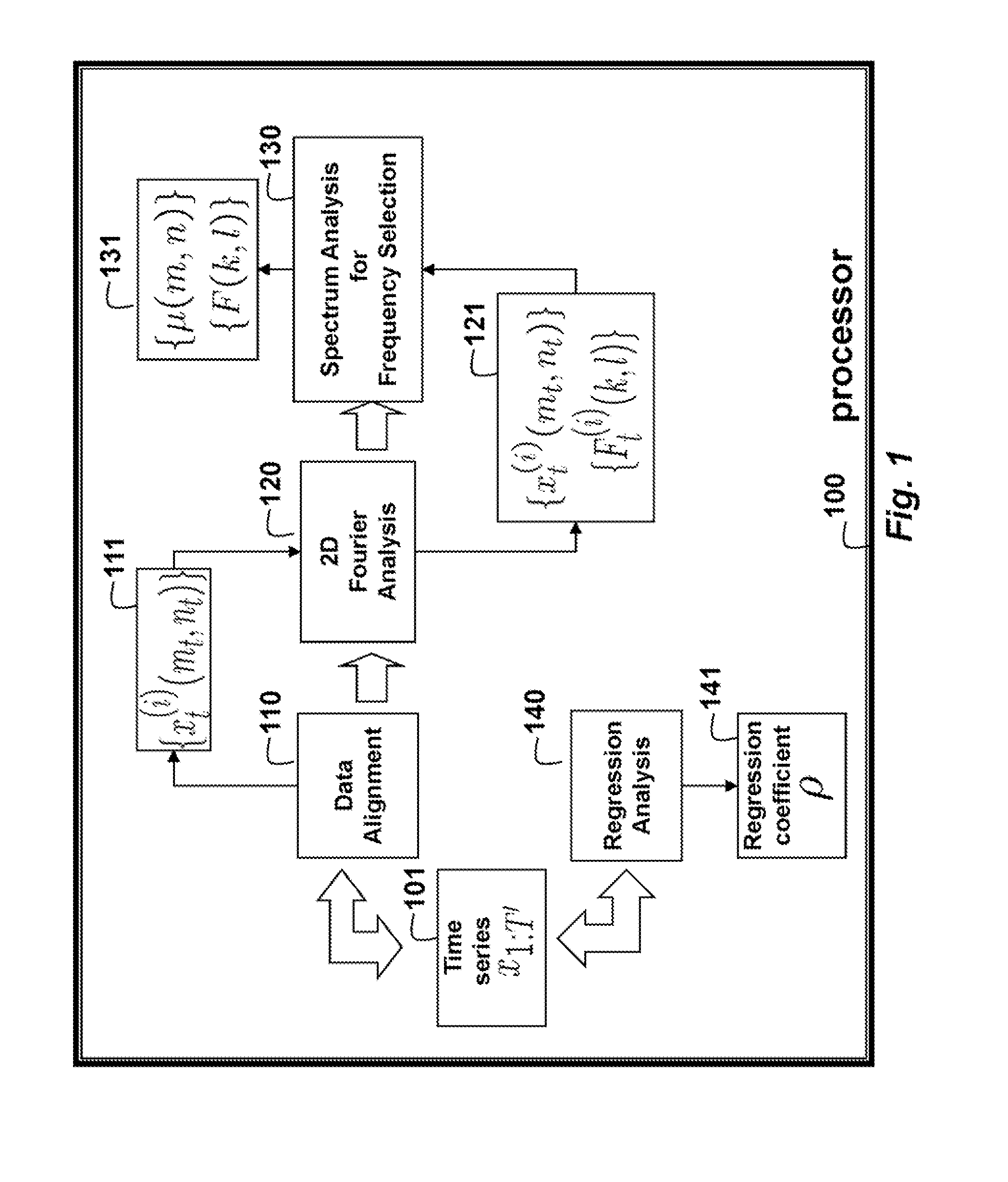
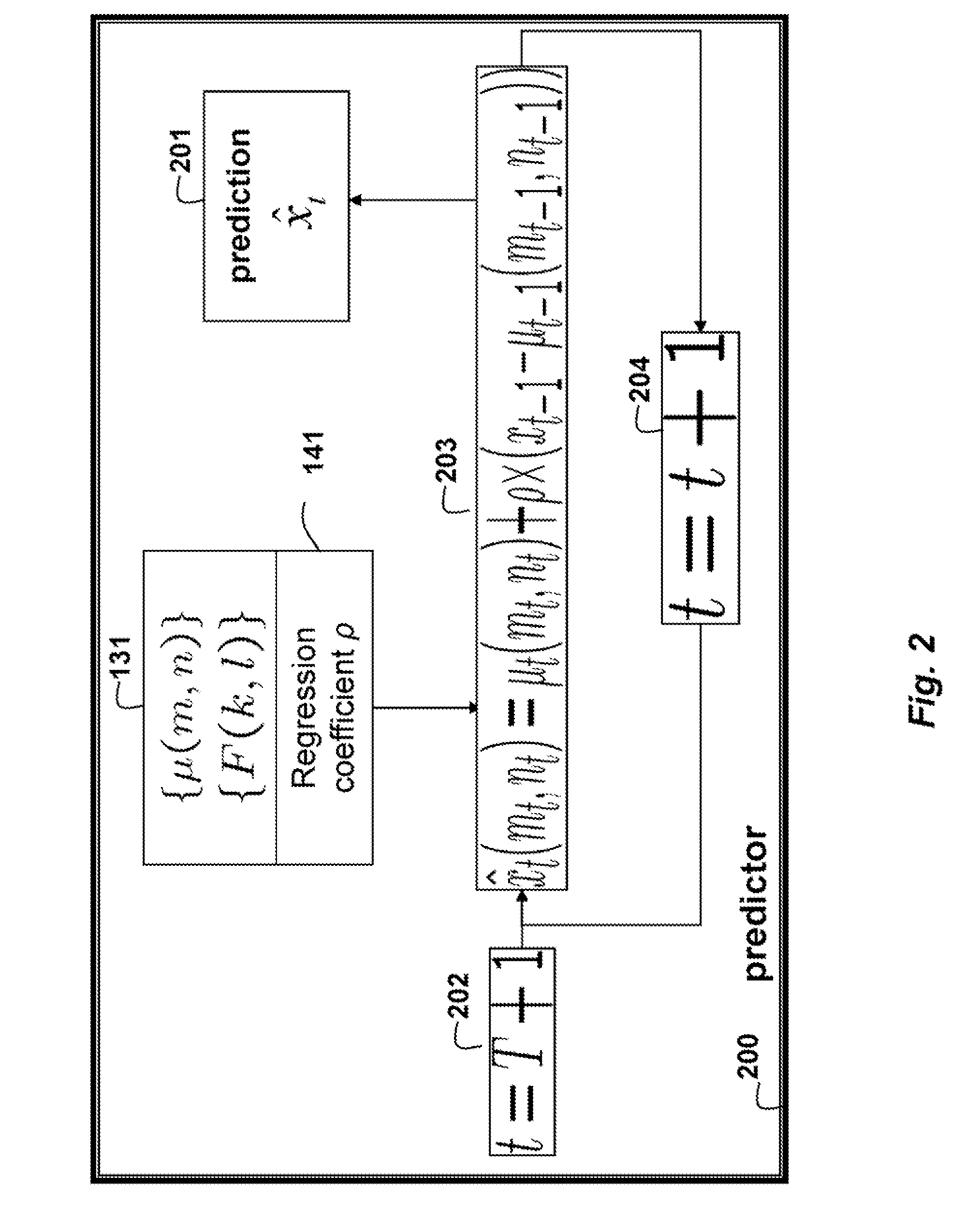
An output of a photovoltaic (PV) device is predicted by applying Fourier analysis to historical data to obtain frequencies and a mean of the frequencies in the data. Regression analysis is applied to the data to obtain a regression coefficient. Then, the prediction is a sum of the mean at the time step and a deviation from the mean at a previous time step, wherein the means are represented and approximated by selected frequencies, and the deviation for the previous time step is weighted by the regression coefficient.
Owner:MITSUBISHI ELECTRIC RES LAB INC
Methods and systems for searching and associating information resources such as web pages
InactiveUS20050171946A1Data processing applicationsDigital data information retrievalInformation resourceLibrary science
Disclosed is a method for detecting additional relevant resources in relation to a predefined initial number of resources, consisting of the following steps: a) a set of referencing resources consisting of all resources being linked to at least one of the initial resources is detected; b) a set of potential resources consisting of all resources referenced by the referencing resources is established; c) for each potential resource, a potential-resource relevance score is calculated between said potential resource and all initial resources on the basis of existing links in the referencing resources to the potential resource and the initial resources, and also on the basis of the relevance scores of referencing resources assigned to each referencing resource; d) for each referencing resource, a referencing-resource relevance score is recalculated on the basis of links occurring in said referencing resource to the potential resources and also on the basis of the potential-resource relevance score assigned to the potential resources in step c); e) step c), and if necessary several times step d) followed by step c), is repeated if necessary; f) said additional relevant resources are identified as the potential resources having the highest potential-resource relevance scores.
Owner:MAIM ENRICO
Game machine, game processing method and information storage medium
Owner:KONAMI DIGITAL ENTERTAINMENT CO LTD
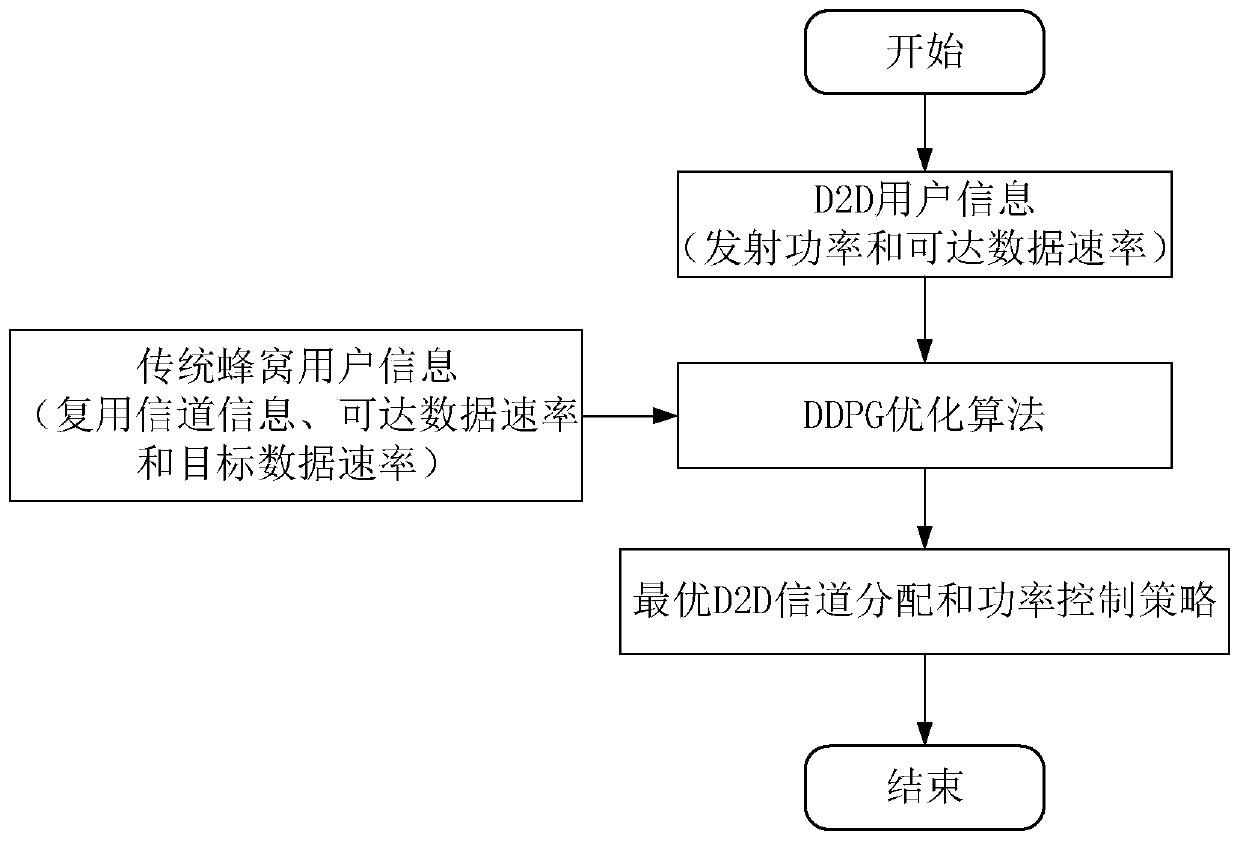
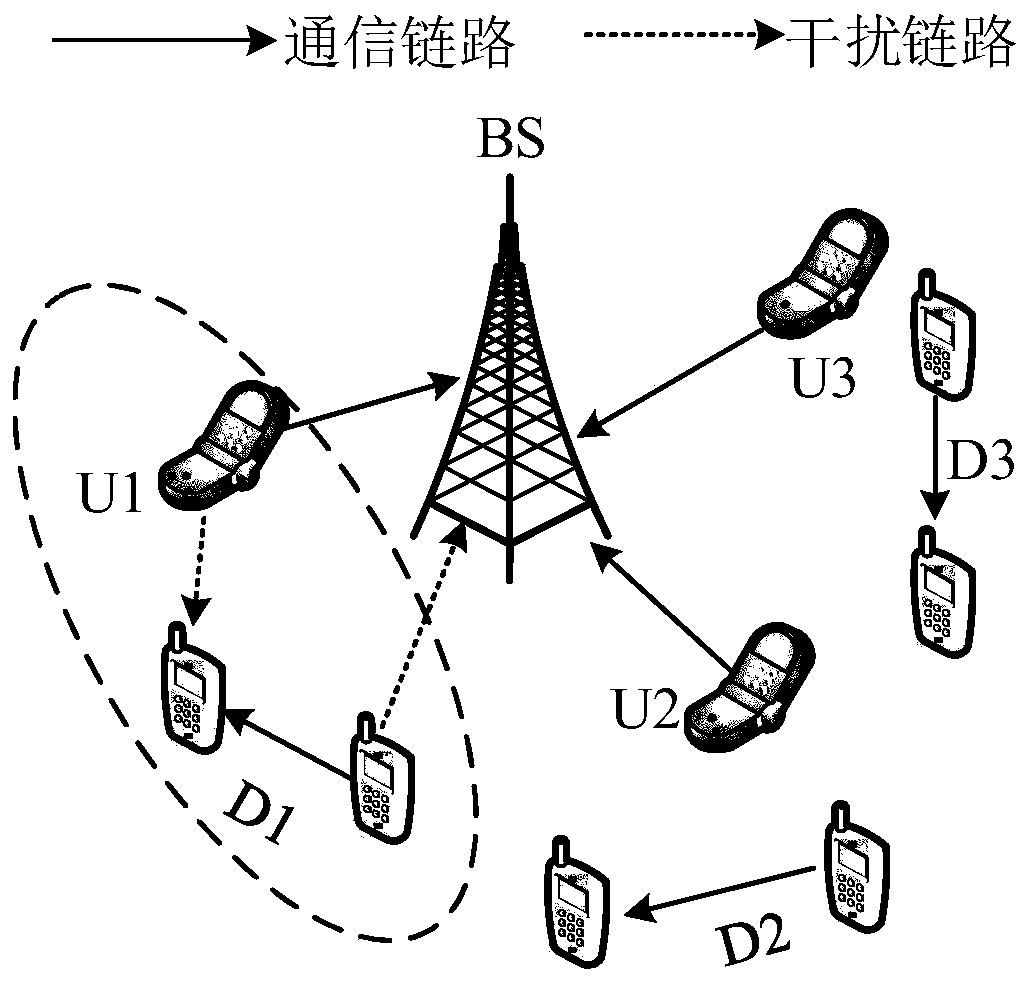
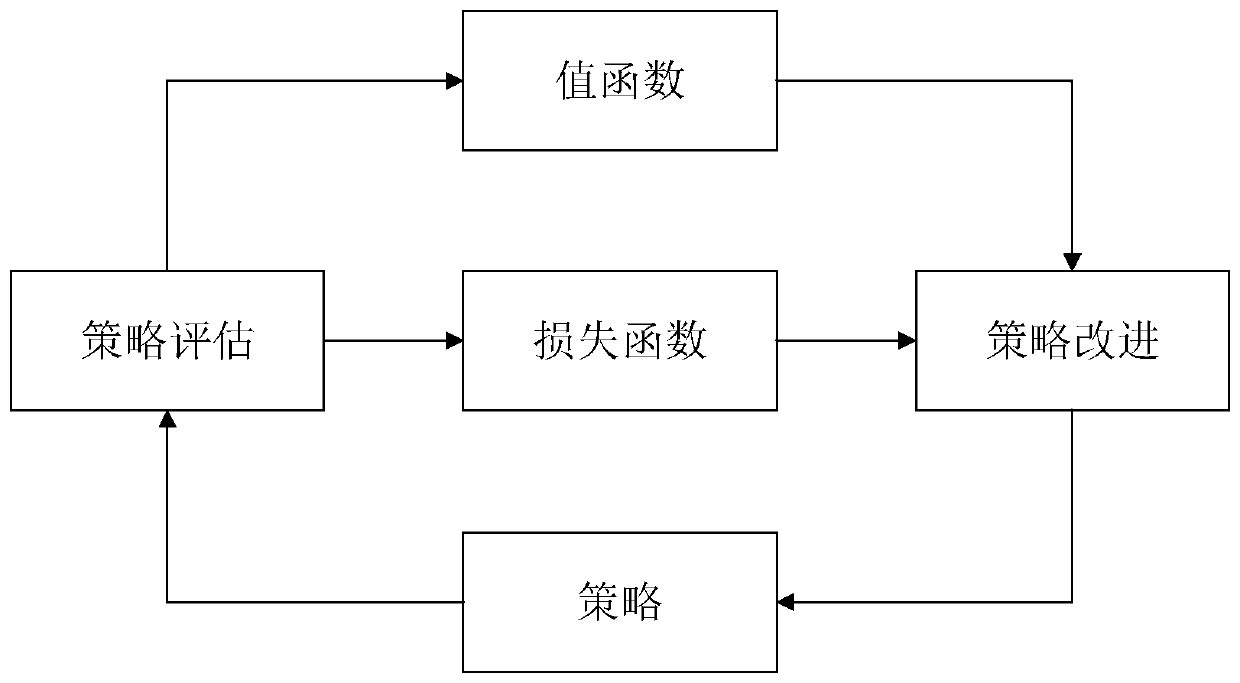
A D2D user resource allocation method based on a deep reinforcement learning DDPG algorithm
ActiveCN109862610AReduce distractionsImprove throughputPower managementResourcesRelevant informationTransmitted power
The invention discloses a D2D user resource allocation method based on a deep reinforcement learning DDPG algorithm. According to the invention, cellular users and D2D user related information are utilized; an optimal D2D user channel allocation and transmitting power combined optimization strategy is obtained by utilizing a deep reinforcement learning method; D2D users select appropriate transmitting power and distribution channels to reduce interference to cellular users and maximize own information rate, efficient resource distribution is achieved under the condition that QoS of the cellular users is not affected, the throughput of a cellular network is improved, and the requirement for green communication is met. The DDPG algorithm effectively solves the joint optimization problem of D2D user channel distribution and power control; t the method is stable in performance in optimization of a series of continuous action spaces, the time step required for solving the optimal solution is far less than that required by DQN, and compared with a DRL method based on a value function, the deep strategy gradient method based on the AC framework is higher in strategy optimization efficiency and higher in solving speed.
Owner:HUAZHONG UNIV OF SCI & TECH
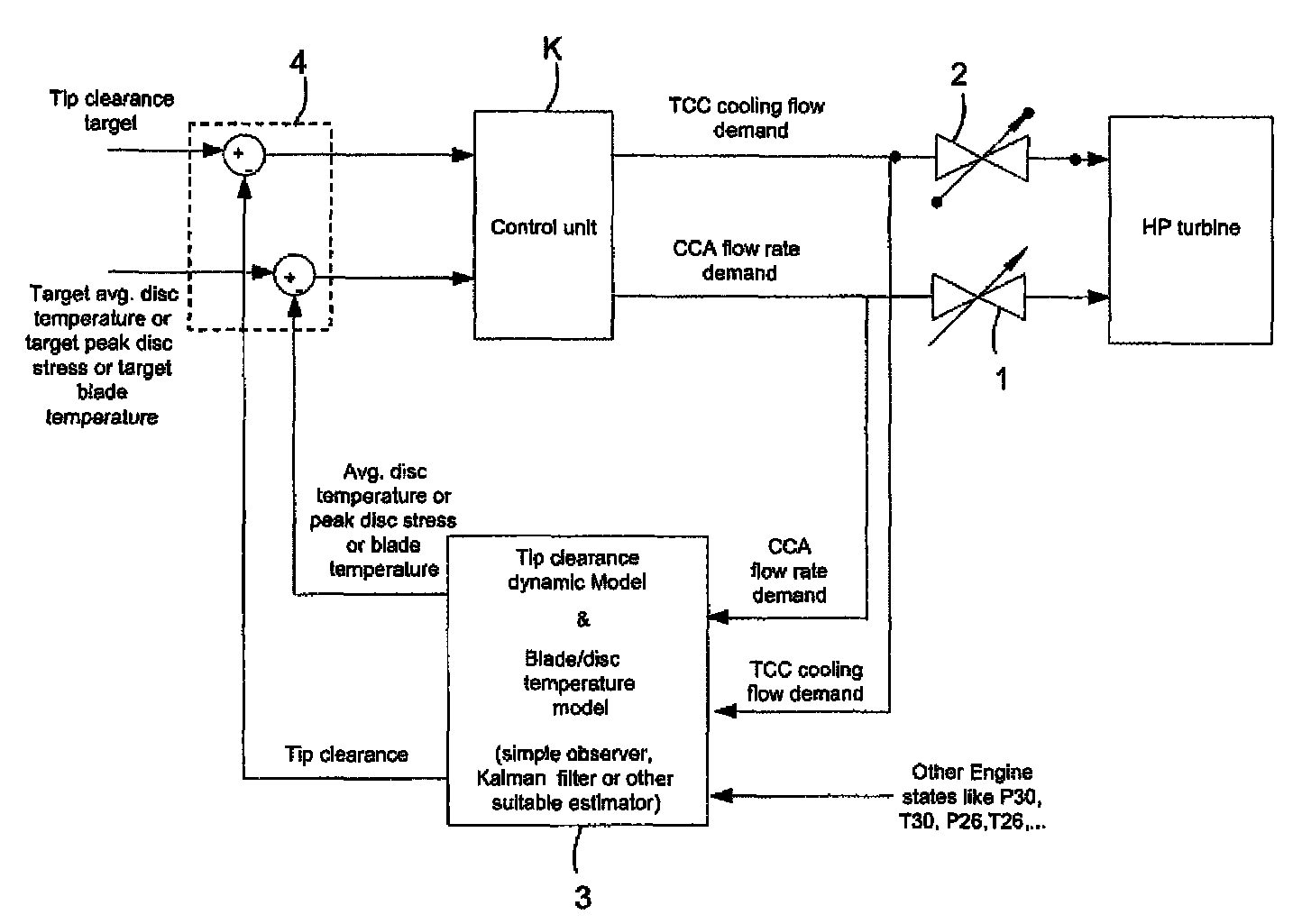
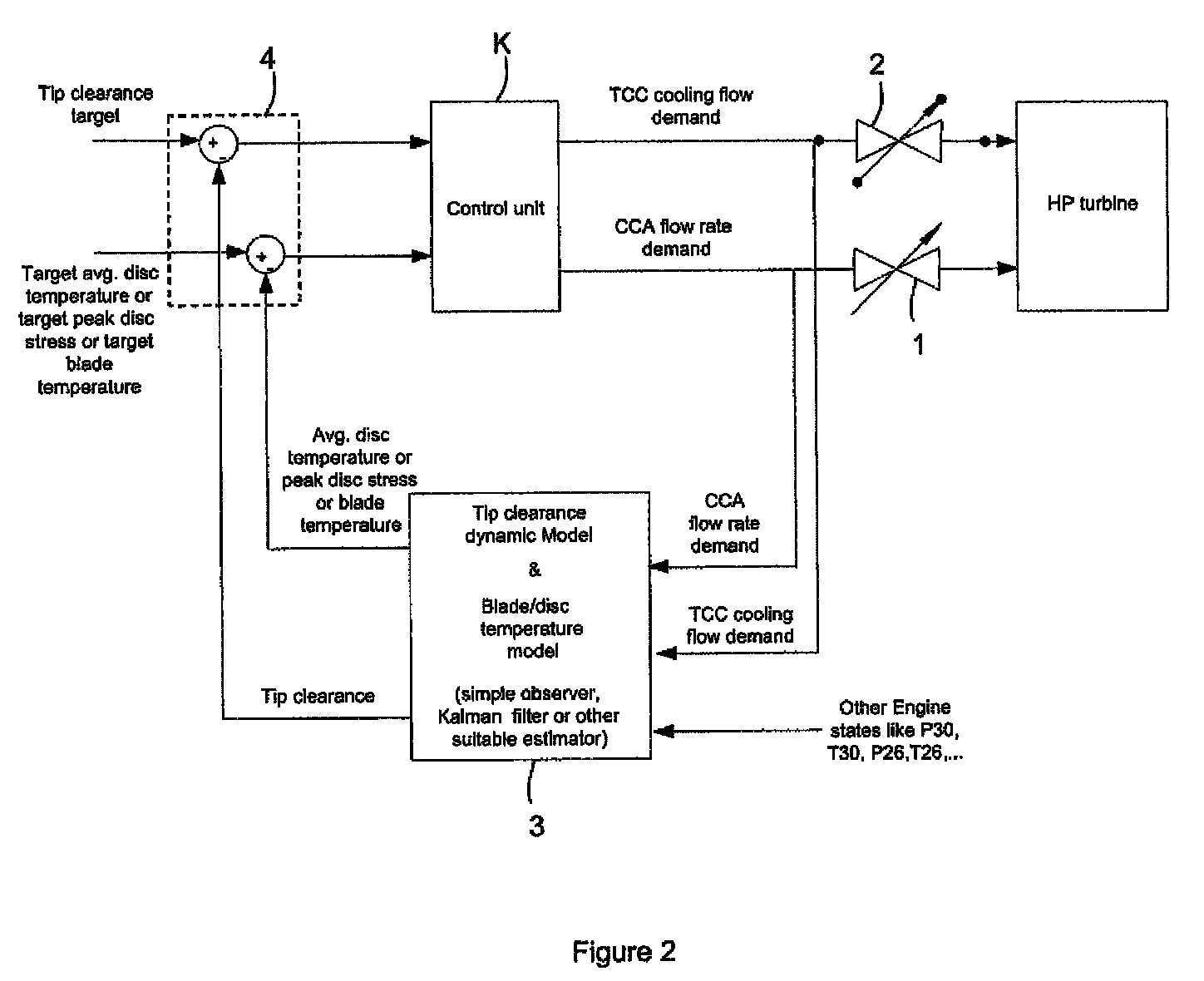
Gas turbine engine having a multi-variable closed loop controller for regulating tip clearance
ActiveUS9255492B2Improve engine efficiencyImprove efficiencyEngine fuctionsTurbine/propulsion engine coolingCombustorTurbine blade
A gas turbine engine has, in flow series, a compressor section, a combustor, and a turbine section. The gas turbine engine further has a system (i) for cooling the turbine section and (ii) for providing tip clearance control between turbine blades of the turbine section and a plurality of circumferentially distributed segments which form an annular shroud surrounding the outer tips of the turbine blades. The system includes a turbine section cooling sub-system which diverts a first cooling air flow received from the compressor section to a heat exchanger and then to the turbine section to cool components thereof. The first cooling air flow by-passes the combustor and is cooled in the heat exchanger. The turbine section cooling subsystem has a first valve arrangement which regulates the first cooling air flow. The system further includes a tip clearance control sub-system which supplies a second cooling air flow to an engine case to which the segments are mounted. The second cooling air flow regulates thermal expansion of the case and thereby controls the clearance between the segments and the outer tips. The tip clearance control sub-system has a second valve arrangement which regulates the second cooling air flow. The system further includes a closed-loop controller which issues first and second demand signals to respectively the first and the second valve arrangements. Each of the first and second demand signals are determined on the basis of: (i) a value of the first demand signal at a previous time step, and a measurement or estimate of turbine section component temperature, and (ii) a value of the second demand signal at a previous time step, and a measurement or estimate of tip clearance.
Owner:ROLLS ROYCE PLC
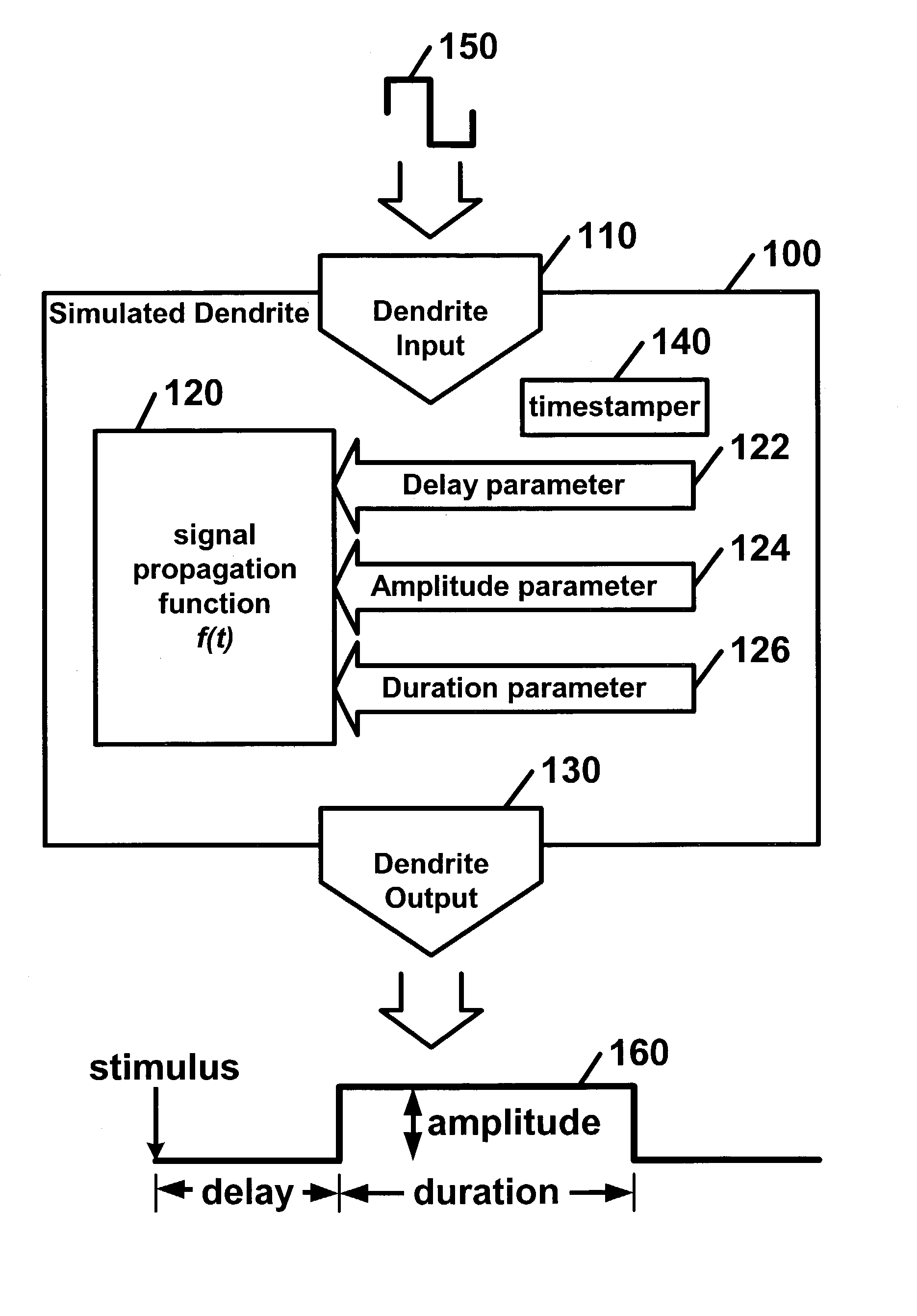
Neural processor
InactiveUS7174325B1Simple methodLarge structureDigital computer detailsNeural architecturesDendriteNeural processing
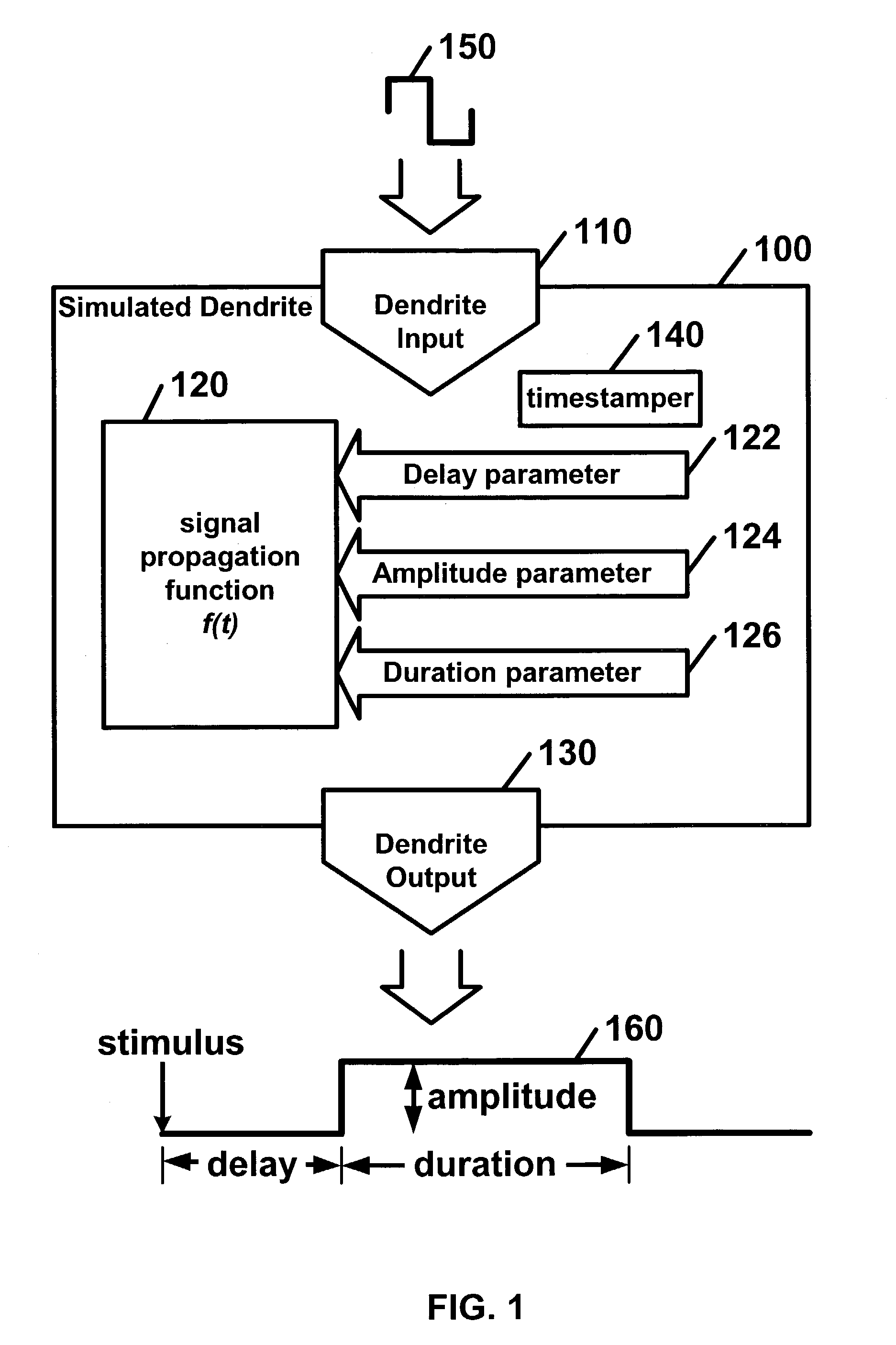
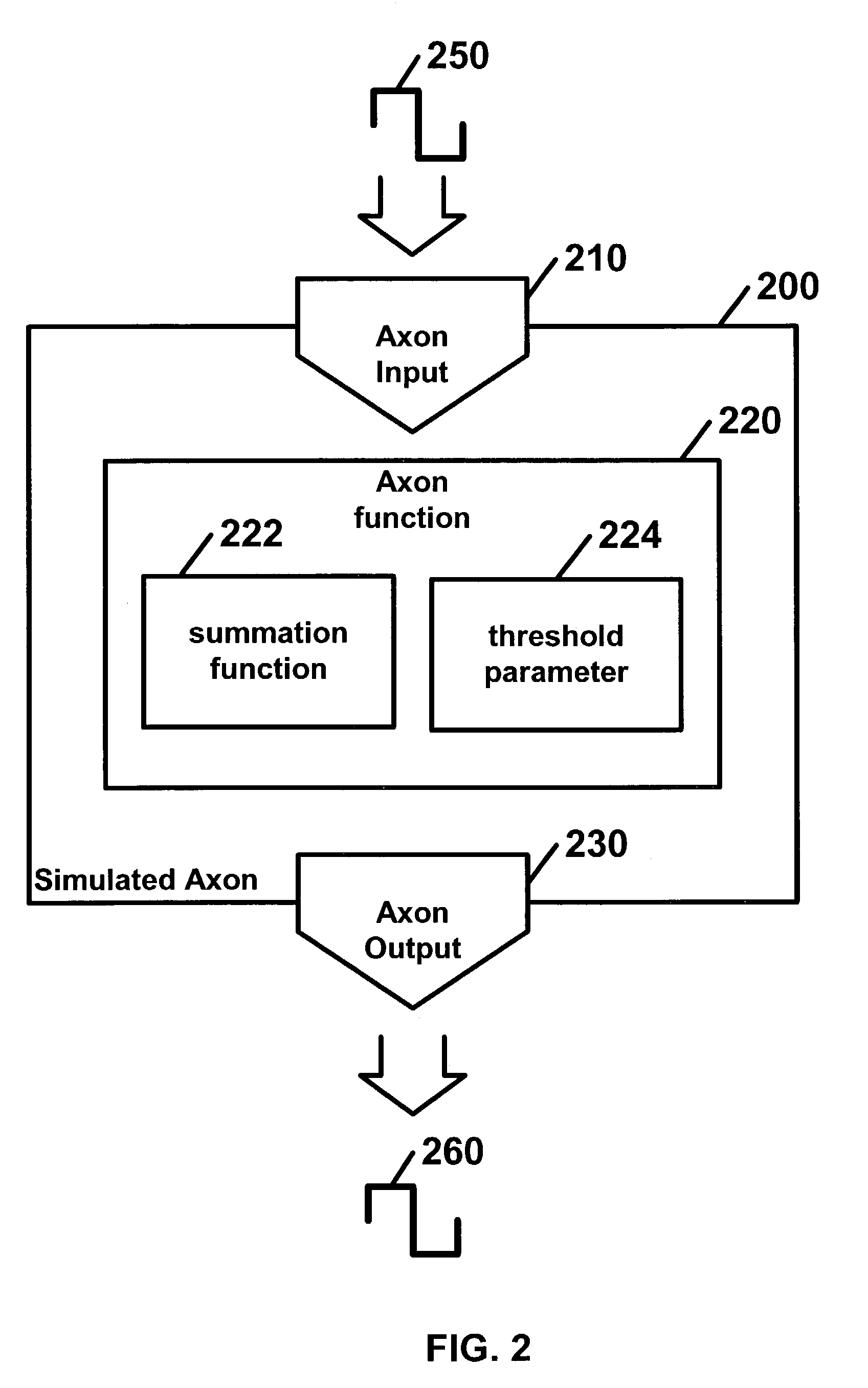
Disclosed is a digital neural processor comprising at least one neural processing element. The neural processing elements including at least one simulated dendrite and a simulated axon. Each of the simulated dendrites may include: a dendrite input capable of receiving at least one dendrite input signal and a dendrite signal propagation function capable of calculating a dendrite output signal in discrete time steps from each dendrite input signal. The signal propagation function may further include a delay parameter; a duration parameter; and an amplitude parameter. The simulated axon includes an axon input capable of receiving dendrite output signals, an axon function, capable of calculating an axon output signal from dendrite output signal(s) and an axon output capable of outputting the axon output signal.
Owner:GEORGE MASON INTPROP INC
Automated event monitoring system for online reservoir simulation
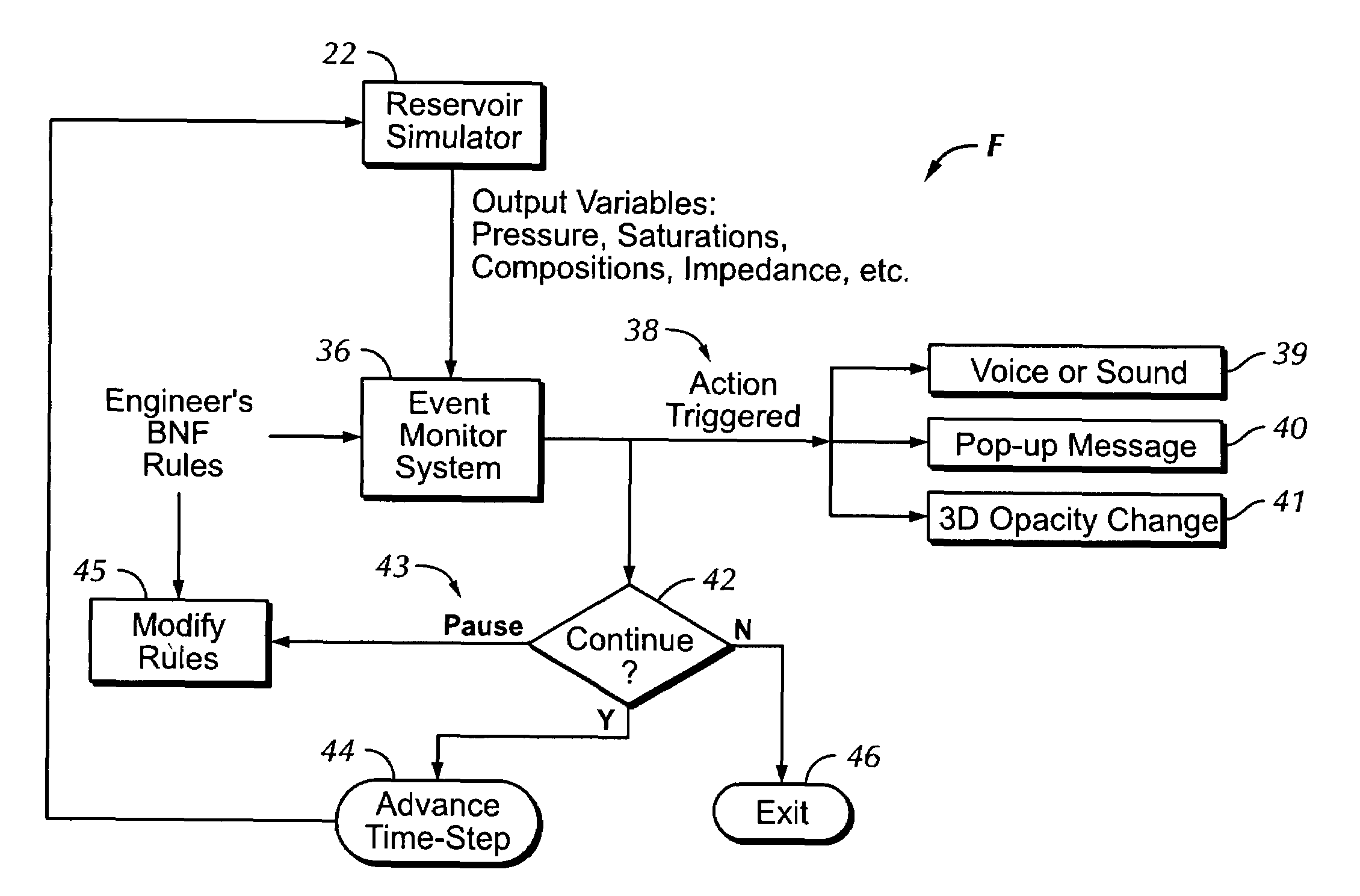
ActiveUS7660711B2Electric/magnetic detection for well-loggingProgram loading/initiatingBatch processingMulti dimensional data
Owner:SAUDI ARABIAN OIL CO
Reservoir prediction method based on bidirectional recurrent neural network
The invention relates to a reservoir prediction method based on a bidirectional recurrent neural network. The reservoir prediction method includes: generating well seismic data, generating well markeddata, generating a marked dataset, building and training the bidirectional recurrent neural network, storing a trained model, extracting seismic data corresponding to all geographic positions in a region, and performing prediction on the seismic data to acquire probability distribution of reservoirs below the whole region. A one-to-one corresponding relation between each sampling point and reservoirs and non-reservoirs is established, wherein input of each time step is n-dimension seismic data of each sampling point while output of the same is corresponding reservoir or non-reservoir marks. An optimal model is acquired by training marked samples and adjusting hyper-parameters, in this way, unmarked data can be predicted to finally generate a predicted seismic body of same dimension, and value of each sampling point is prediction probability between 0 and 1, so that the method has good effect on reservoir prediction.
Owner:CHINA PETROLEUM & CHEM CORP +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com