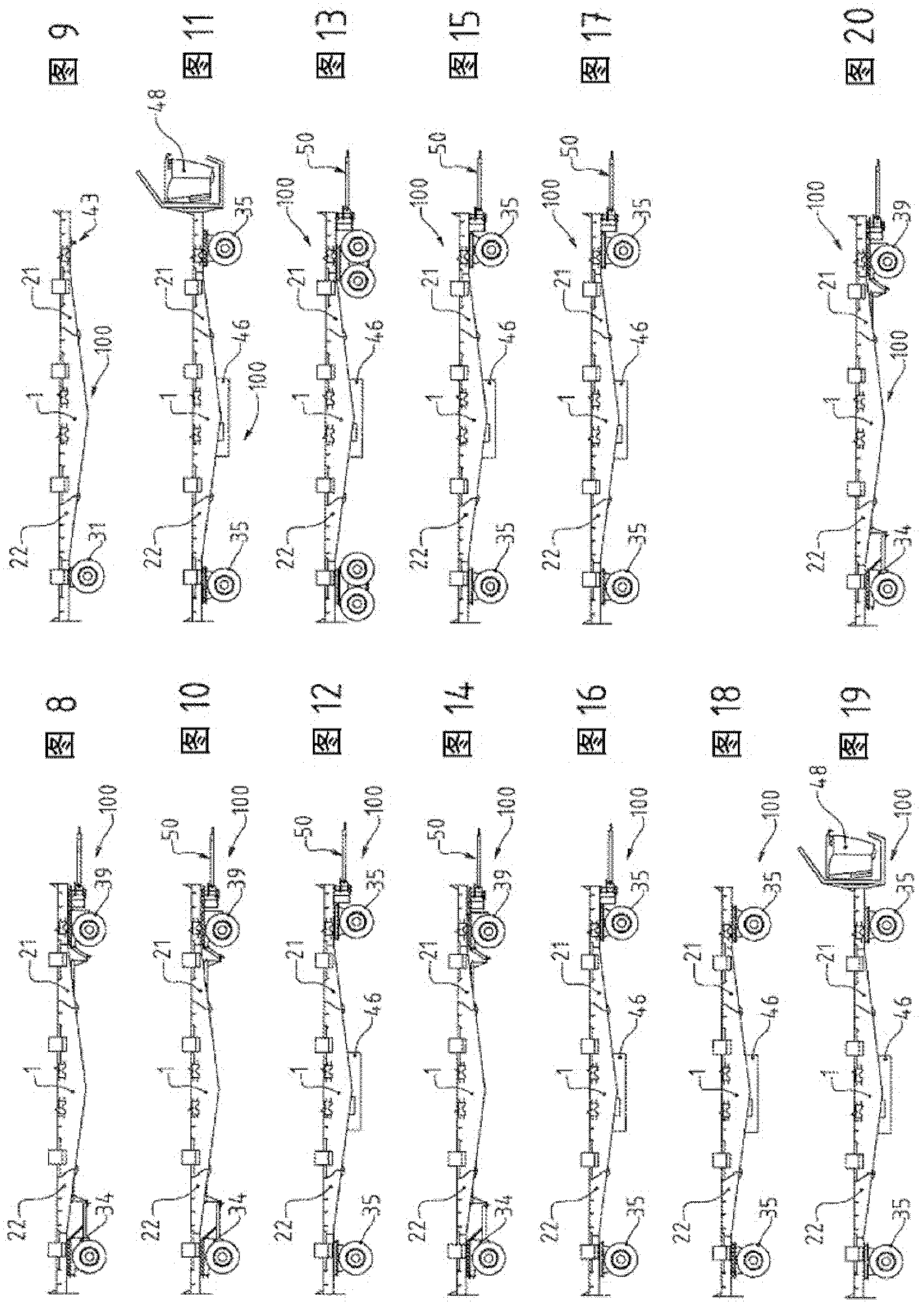Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
31results about How to "Fix usability issues" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
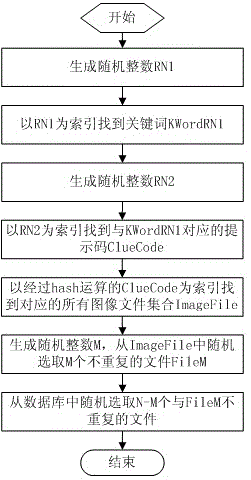
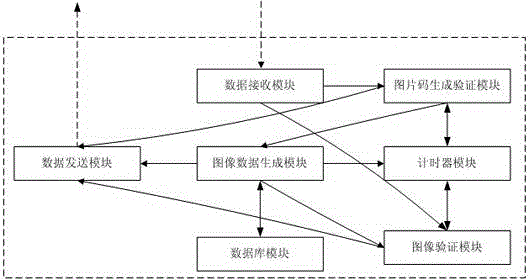
Intelligent image verification method and intelligent image verification system
InactiveCN102624705AFix usability issuesFix security issuesTransmissionComputer hardwareValidation methods
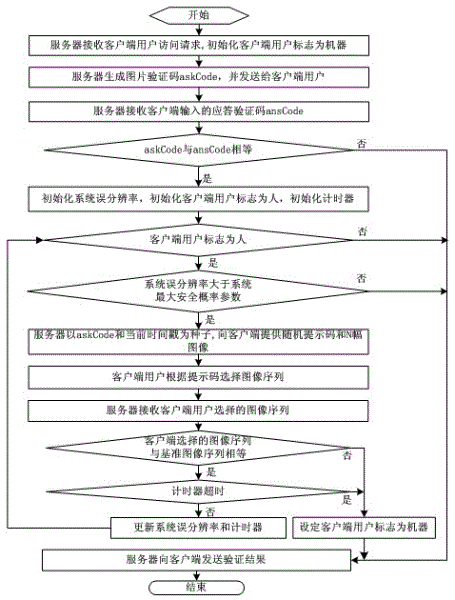
The invention discloses an intelligent image verification method and an intelligent image verification system. The system comprises a data receiving module, an image code generating and verifying module, a timer module, an image data generating module, a database module, an image verification module and a data transmitting module. The data receiving module is used for receiving access requests, image verification code input and image selection sequence of a client user, the image code generating and verifying module is used for generating and verifying image verification codes, the timer module is used for performing timing and aging limiting for client access, the image data generating module is used for randomly generating prompting codes and corresponding N images, the database module is used for performing storage and index access for processing keywords, the prompting codes and image filenames, the image verification module is used for comparing the received image selection sequence of the client user with the image sequence generated by the image data generating module, and the data transmitting module is used for transmitting the image verification codes, the prompting codes, the N images and verification results to the client user, wherein the prompting codes and the N images are generated during image verification. By the aid of the intelligent image verification method and the intelligent image verification system, contradiction between usability and safety of an existing system is solved, whether the client user is a machine or not can be automatically identified, and network safety is improved.
Owner:SOUTHWEST PETROLEUM UNIV
Process threading-based copy-protection system and copy-protection storage medium
ActiveCN102495982AFix security issuesFix usability issuesUnauthorized memory use protectionPlatform integrity maintainanceOperational systemDigital content
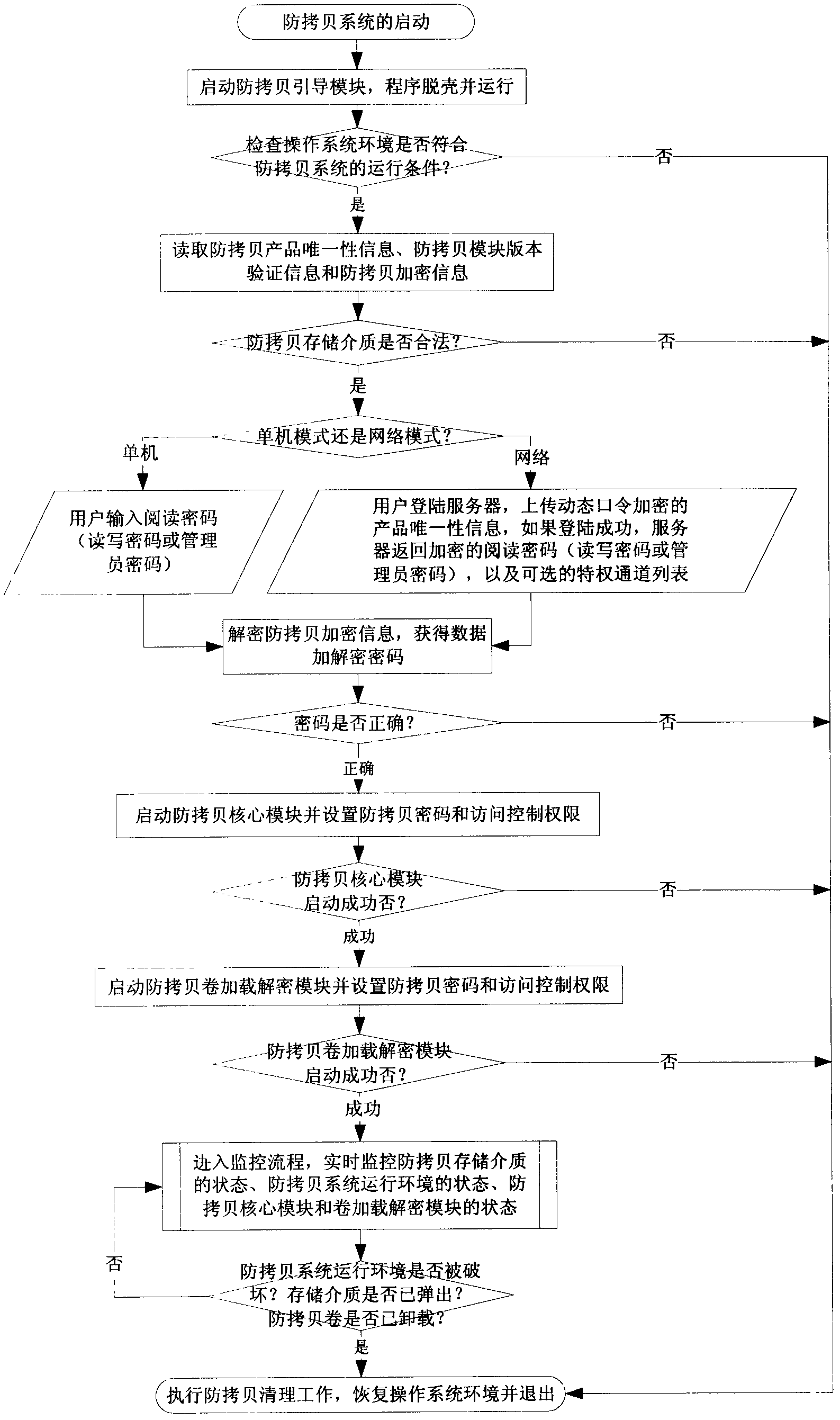
The invention relates to the technical field of copy-protection and anti-piracy of computer information security and data security, in particular to a process threading copy-protection system and a copy-protection storage medium. In the system, a copy-protection lead module, a copy-protection core module and a copy-protection loading decryption module are arranged in the copy-protection storage medium, and copy-protection information cannot be copied illegally under an arbitrary condition by virtue of cooperative operation of the three modules. The system is used for solving the problems of security, availability and usability of the information security copy-protection technology, and is applicable in multiple industries and fields, so that digital content is protected from illegal copy, stealing and piracy; the basic unit of the information security copy-protection technology is firstly locked as a process and a thread of a current basic execution unit in an operation system, and is combined with a corresponding copy-protection storage medium technology to expand all security defense lines, so that the aims of protecting data and media assets of users from illegal copy, duplication and piracy are achieved.
Owner:CHENGDU QIQIAO SOFTWARE
Anonymous collaboration method based on differential privacy under MapReduce framework
InactiveCN107862220AFix usability issuesFix security issuesDigital data protectionData setDifferential privacy
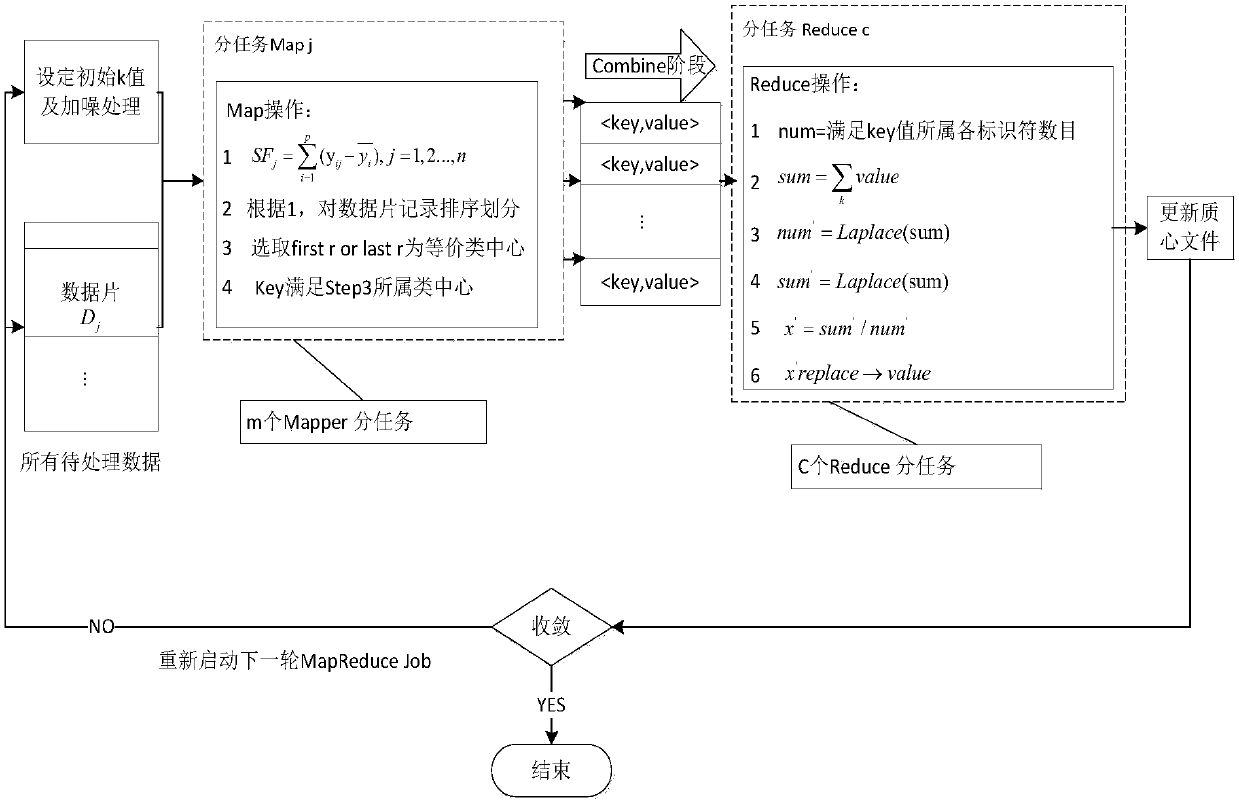
The invention discloses an anonymous collaboration method based on differential privacy under a MapReduce framework. The method combines an anonymous privacy protection technology with a differentialprivacy protection technology to improve the computation rate under the MapReduce framework; the method is used for solving contradiction between data availability and security, on the basis of the data anonymous privacy protection technology, a Laplace noise mechanism is added to strengthen privacy protection performance, and on the basis that a data set improves the data processing efficiency through the MapReduce framework, it is still maintained that data has high security and availability.
Owner:HOHAI UNIV
Method and device for generating self-defined services, computer equipment and storage medium
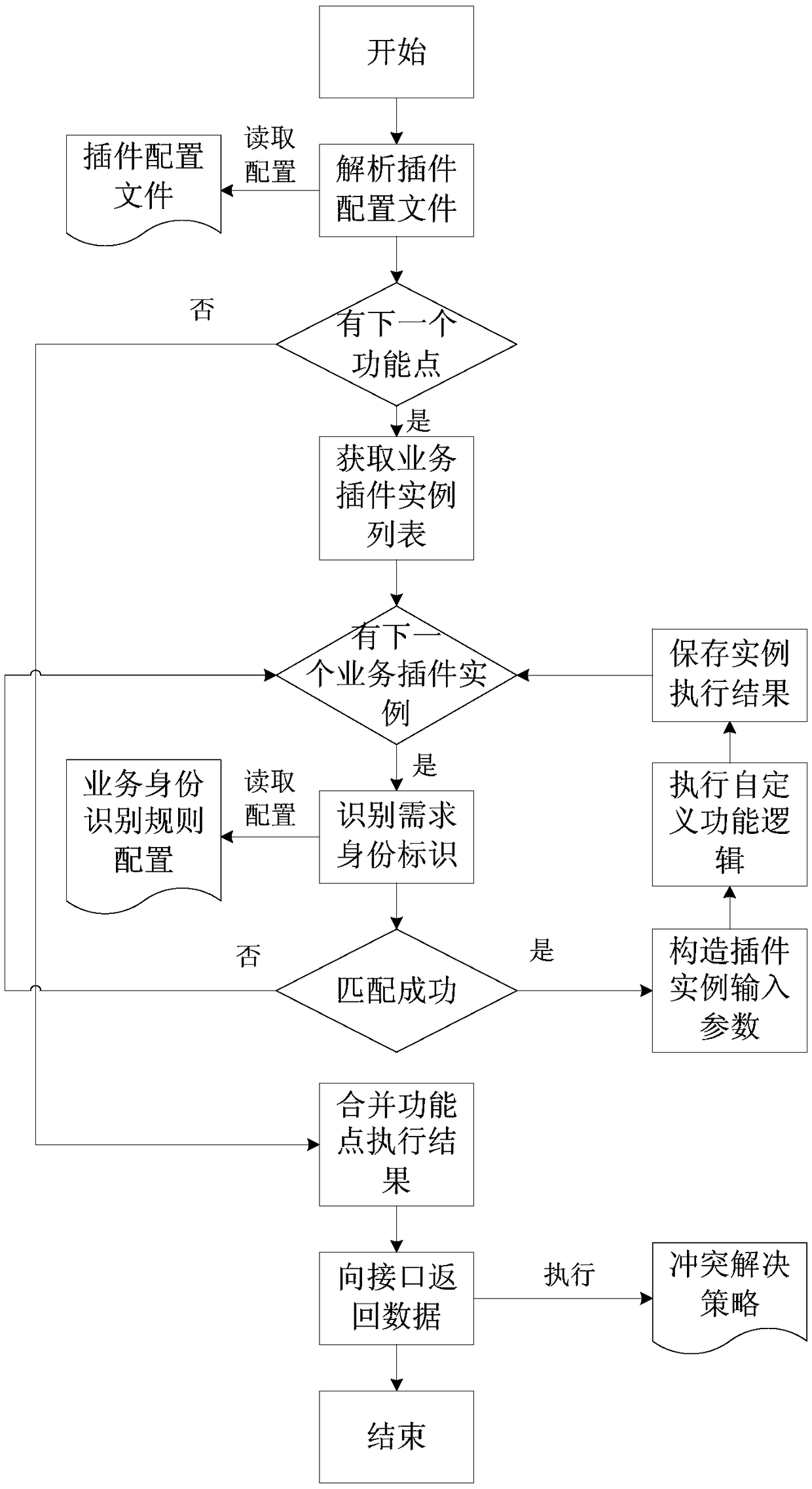
ActiveCN108920135AFlexible support for individual needsFix usability issuesCreation/generation of source codePersonalizationFunction point
The embodiment of the invention discloses a method and device for generating self-defined services, computer equipment and a storage medium. The method includes the steps that a service interface obtains service requirement information; the service interface corresponds to multiple function points, the function points are correlated with a list of service plug-in instances, and the service plug-ininstances are generated through a plug-in configuration file corresponding to the service interface; the service interface obtains the service plug-in instances matched with requirement identity identifications in the list of the service plug-in instances corresponding to all the function points respectively, and obtains function point execution results corresponding to all the function points respectively according to the obtained service plug-in instances and requirement parameter information; the service interface combines the function point execution results corresponding to all the function points respectively to obtain a service processing result corresponding to the service requirement information. In the technical scheme, the method flexibly supports personalized requirements of all the services and fault isolation of all the services.
Owner:杭州贝购科技有限公司
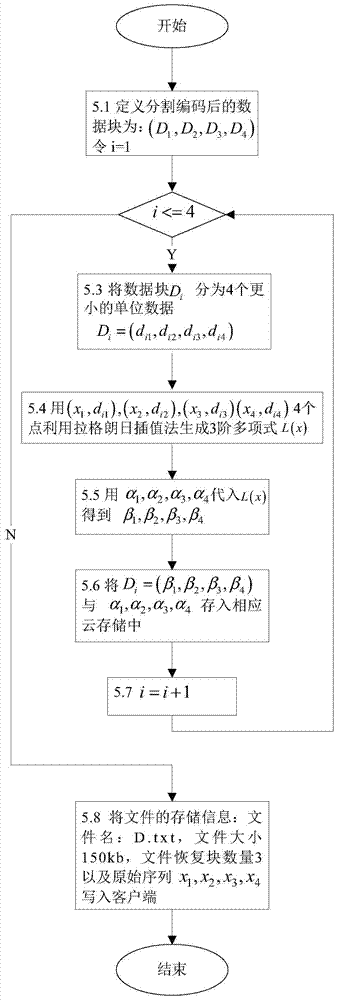
Data hiding method based on Lagrange interpolation method and multiple clouds
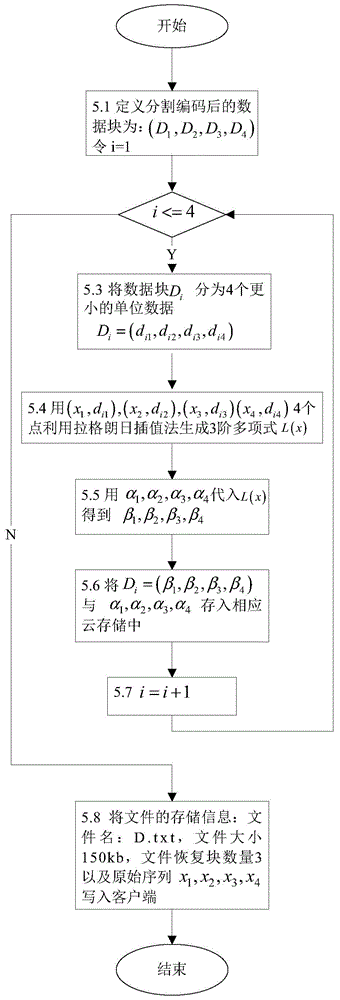
InactiveCN104915609ATolerate mistakesFix usability issuesDigital data protectionInformation recoveryConfidentiality
The invention discloses a data hiding method based on a Lagrange interpolation method and multiple clouds, which is applied in a system under a multi-cloud environment. The system comprises four parts: a user, a client, a data uploading layer, a data downloading layer and the clouds; before data are uploaded, an information segmentation algorithm of Reed Solomon erasure codes is used for segmenting the user data on the client, the Lagrange interpolation method is then used for carrying out information hiding on each block of segmented data, and finally, each block of data is stored in a different cloud storage. During data downloading, the data only need to be obtained from part of the cloud storages, the Lagrange interpolation method is first used for carrying out hidden information recovery on each block of data, and a recovery algorithm in Reed Solomon is then used for merging the data blocks to recover the original data. The data hiding method based on the Lagrange interpolation method and the multiple clouds solves the availability problem of services and the limitation of a single cloud storage; while reducing storage spaces, the usage of the Reed Solomon algorithm can tolerate the errors of the cloud storages; the usage of the Lagrange interpolation method solves the confidentiality problem of data, protecting the privacy of user data.
Owner:WUHAN UNIV OF SCI & TECH
Dynamic self-adaptive SRAM type FPGA system fault tolerance method based on BRAM detection
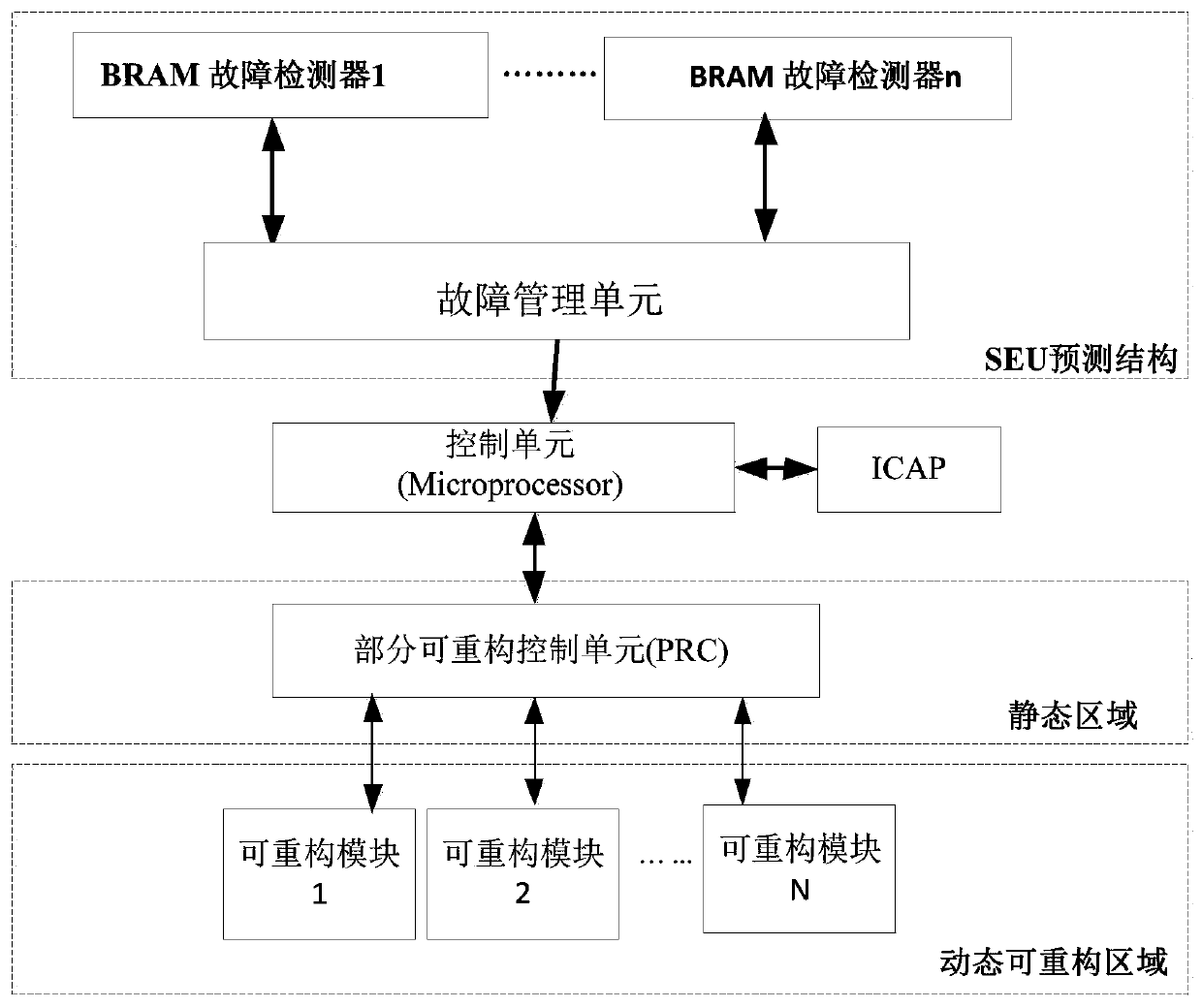
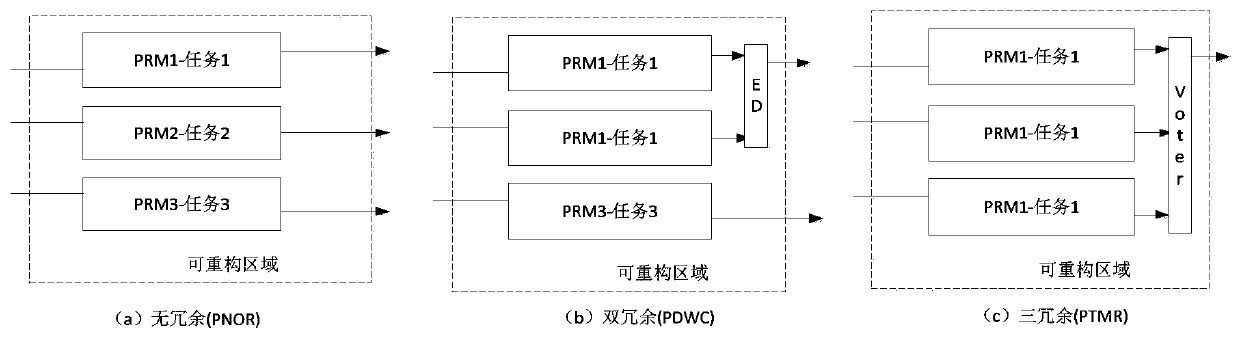
ActiveCN111338833AFix usability issuesSolve resource problemsNon-redundant fault processingEnergy efficient computingStatic random-access memoryControl cell
The invention relates to a dynamic self-adaptive SRAM (Static Random Access Memory) type FPGA (Field Programmable Gate Array) system fault tolerance method based on BRAM detection, which belongs to the field of intelligent fault tolerance systems and comprises the following steps of: 1) dividing a reconfigurable region and a static region on an SRAM type FPGA; 2) constructing a dynamic adaptive structure fusing non-redundancy to multi-redundancy for a part of dynamic reconstruction area on the FPGA; 3) designing an SEU rate detection structure based on a BRAM embedded block, carrying out faultcounting, and detecting and correcting errors; 5) calculating a current turnover rate, and judging a redundancy scheme needing to be adopted; 6) implementing a redundancy scheme through a control unit of the FPGA system; and 7) calculating and evaluating the availability and performance of the adaptive FPGA system. Conditions in actual application of the FPGA are comprehensively considered, contradiction between availability and performance resources is balanced, an adaptive redundant structure of the FPGA system is dynamically changed according to the predicted radiation level (SEU rate), the task execution efficiency of the system is improved, the power consumption of the system without faults is reduced, and good portability is achieved.
Owner:BEIHANG UNIV
Method for designing optimal PID parameters of closed-loop control system of nuclear power plant
PendingCN112666821AFix usability issuesEffective theoretical calculation basisControllers with particular characteristicsAdaptive controlLoop controlNuclear power
The invention belongs to the technical field of nuclear industry intelligent algorithm application, and particularly relates to a method for designing optimal PID parameters of a closed-loop control system of a nuclear power plant. The method comprises the following steps of: S1, determining the closed-loop control system and a controlled object needing PID parameter optimization; S2, performing nuclear power plant analogue simulation on a nuclear power plant design verification platform, and operating the closed-loop control system; S3, determining a model structure and model parameters of the controlled object, and identifying the controlled object by using a genetic algorithm to obtain model parameters for optimal identification; S4, carrying out PID parameter optimization by using a genetic algorithm to obtain the optimal PID parameters; S5, substituting the controlled object model and the optimal PID parameters into a closed-loop control system block diagram for simulation through mathematical software until the optimal PID parameters meet engineering index requirements; and S6, writing the optimal PID parameters meeting the engineering index requirements into an engineering design file. The PID parameters obtained by adopting the method can be applied to debugging and operation of the closed-loop control system of the nuclear power station.
Owner:CHINA NUCLEAR POWER ENG CO LTD
Method and system for achieving availability of RMB cashier counter on foreign trade e-commerce platform
InactiveCN106897870AImprove experienceReduce operational riskPayment architectureExecution for user interfacesCustomer attritionAutomatic routing
The invention relates to a method and system for achieving the availability of an RMB cashier counter on a foreign trade e-commerce platform. The method is characterized in that through a process in which the RMB cashier counter monitors JOB (scripts), the availability of payment modes, including UnionPay payment, quick payment, third-party payment and platform account payment, can be automatically detected, and different processing procedures can be carried out according to different situations; if a bank payment mode is unavailable, whether a backup channel exists or not is detected; if the backup channel exists, automatic routing to a new bank of the backup channel is carried out for payment; and if the new bank payment mode is still unavailable, a bank payment icon is hidden. The method has the advantages that a client can freely choose an available payment mode during payment, and can give priority to the payment mode with the lowest cost, so that the user experience for foreign trade e-commerce platform payment is improved, client loss caused by slow payment and unsatisfactory experience on the platform is prevented, the availability of the RMB cashier counter on the foreign trade e-commerce platform is achieved, and operation risks of the platform are reduced.
Owner:数贸科技(北京)有限公司
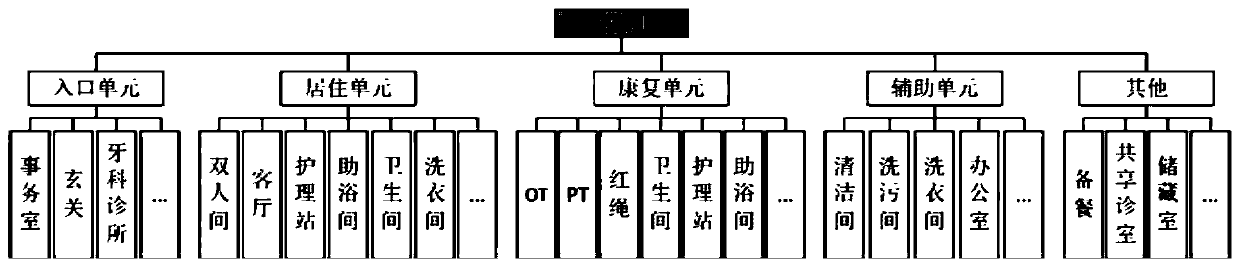
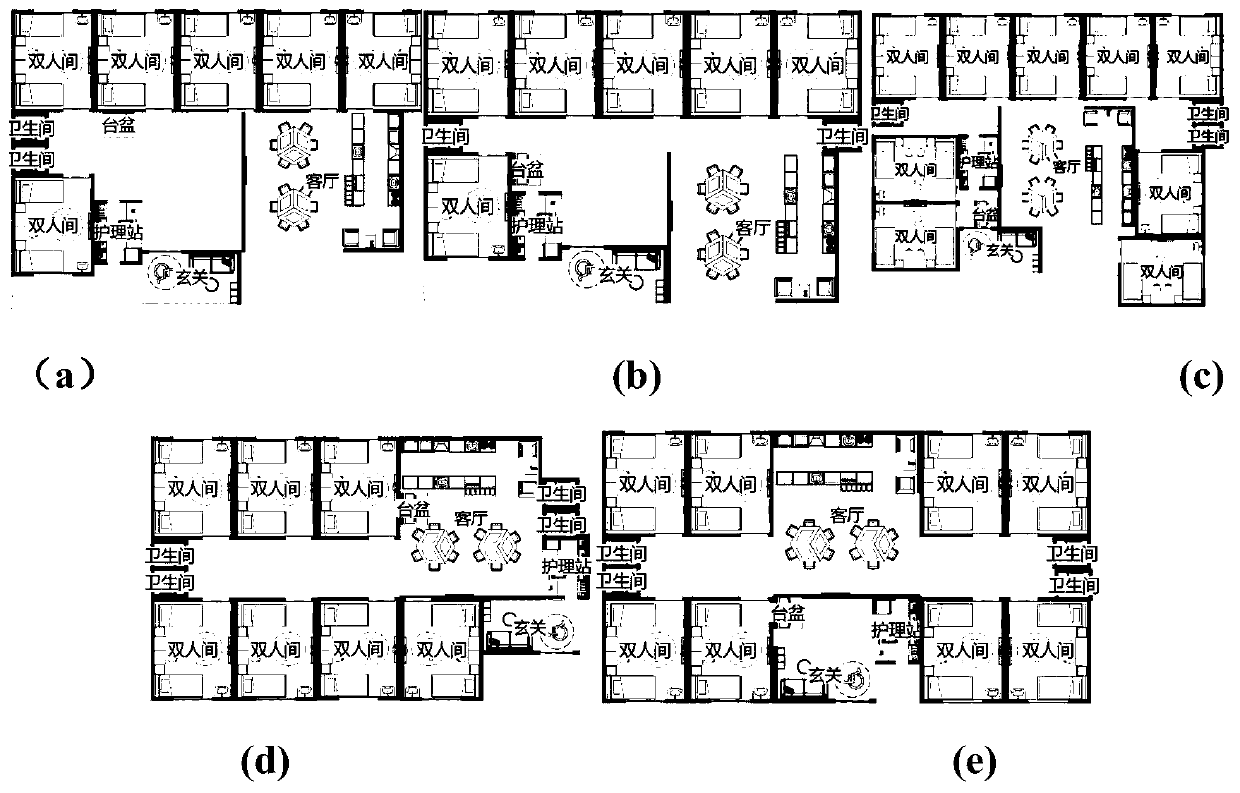
Rule-driven collaborative interactive spatial layout automatic design method
ActiveCN111241619AImprove performanceFix usability issuesGeometric CADModelSimTheoretical computer science
The invention discloses a rule-driven collaborative interactive spatial layout automatic design method. The method is combined with human intelligence, an algorithm and priori knowledge to perform spatial automatic layout design. The method comprises the following steps that firstly, computerized rule extraction, encoding and modeling are performed on a redundant and regular layout process, and then a spatial layout scheme meeting constraint conditions in a self-driven manner is generated based on a computerized rule, so that the workload of a designer is reduced, and the designer focuses on ahigh-professionality design link. Then, a man-machine collaborative interactive optimization process is adopted, and the ubiquitous defects of availability, flexibility, attractiveness and the like of an existing computerized design method are overcome. According to the invention, the spatial layout design of a miniature old-age care institution is taken as an embodiment, an online automatic layout design platform iCareDesigner is designed, and a user can access the platform at a web end, input spatial feature description, generate a spatial design scheme by one key, and perform online interactive revision and optimization.
Owner:EAST CHINA NORMAL UNIV
Data processing method and device
ActiveCN104965882AFix usability issuesImprove usabilitySpecial data processing applicationsDatabase design/maintainanceUsabilityLarge scale data
The invention discloses a data processing method and device and belongs to the field of databases. The method comprises: determining a to-be-processed data line in a data table; educing the to-be-processed data line in n batches; deleting the data line which is educed in each batch from the data table; or, deleting the data line from the data table after the data line is archived to another data table. According to the data processing method and device disclosed by the invention, the educed data line is deleted by virtue of multi-batch data educing operation and less data educing operation of each batch, so that the problem in the correlated technology that the usability of the database is affected by relatively long data deleting time is solved; and when the large-scale data is deleted or archived, the data table is not locked on a large scale, the pressure on the data table in unit time is relatively small and the performance of the data table is not affected, so that the effect of the usability of the data table is improved.
Owner:XIAOMI INC
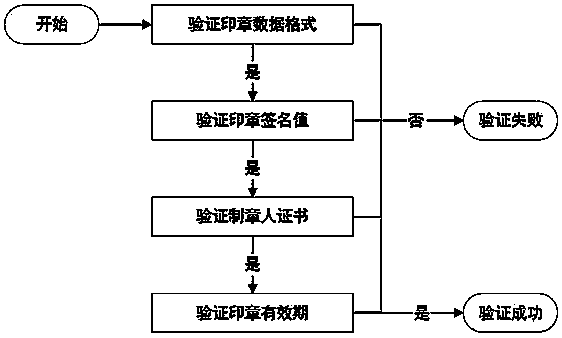
Electronic certificate ex-warehouse method based on OFD format
InactiveCN110532812ASolve the problem of authenticityResolve integrityDigital data protectionPasswordDocument format
The invention discloses an electronic certificate ex-warehouse method based on an OFD format document format. The method comprises the following steps: selecting information needing to be added according to an ex-warehouse demand, and generating an impression picture with a specified size; generating standard seal data according to the signature password technical specification and the informationrequired by the signature password technical specification; detecting whether the generated seal data meets specifications and specification standard requirements or not; the user selects a positionwhere information needs to be added for ex-warehouse; verifying the PIN code of the key disk required by the user signature; stamping the newly generated seal at a specified position; generating standard signature data according to the signature password technical specification; and according to data specification requirements of an OFD format, generating the generated seal data and signature datato a specified position in the document. According to the invention, the validity of the signature data of the original electronic certificate is ensured, other instructions and information can be added during ex-warehouse, and new seal data can be synthesized again and stamped into the electronic certificate to be delivered.
Owner:江西金格科技有限公司
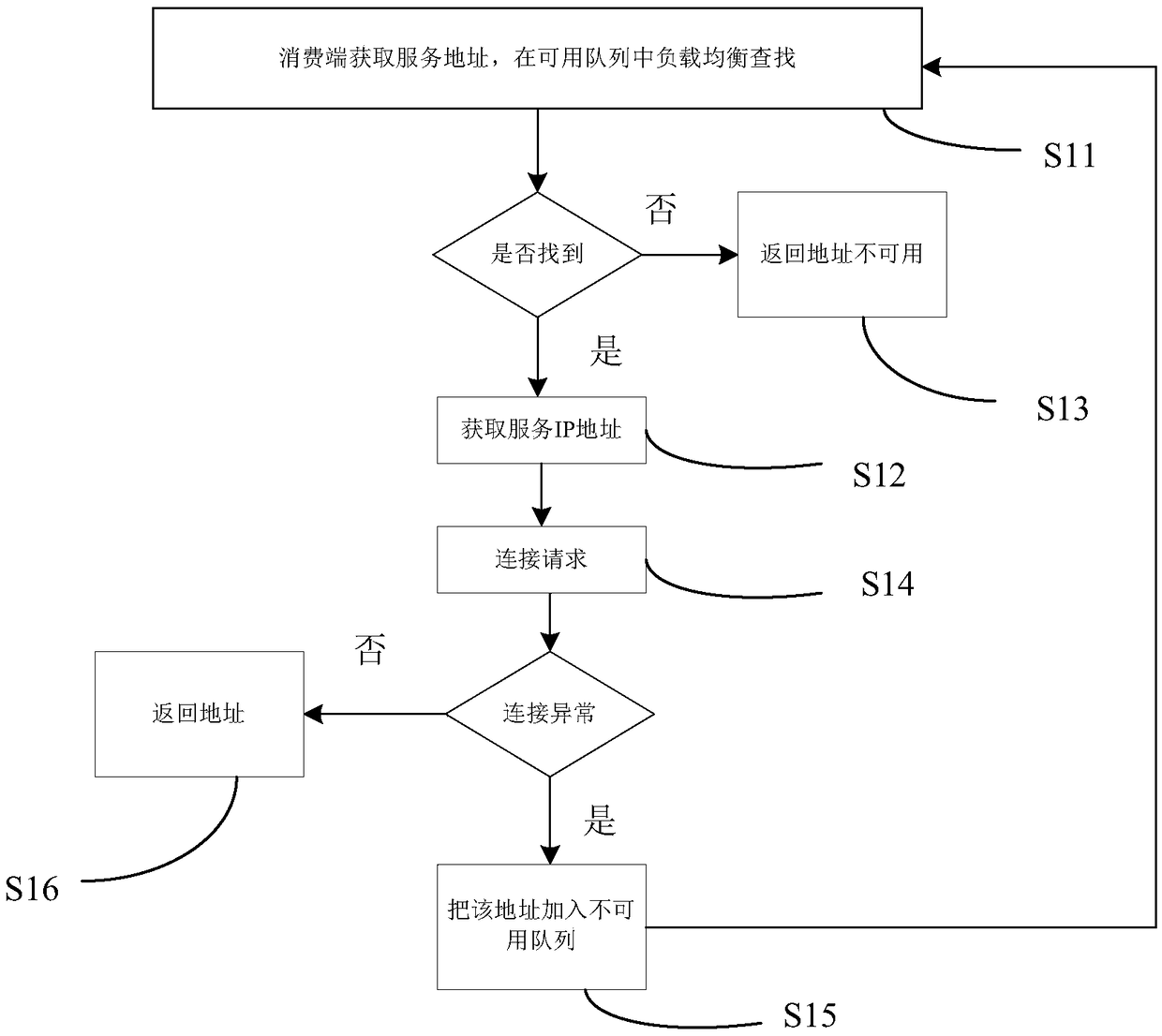
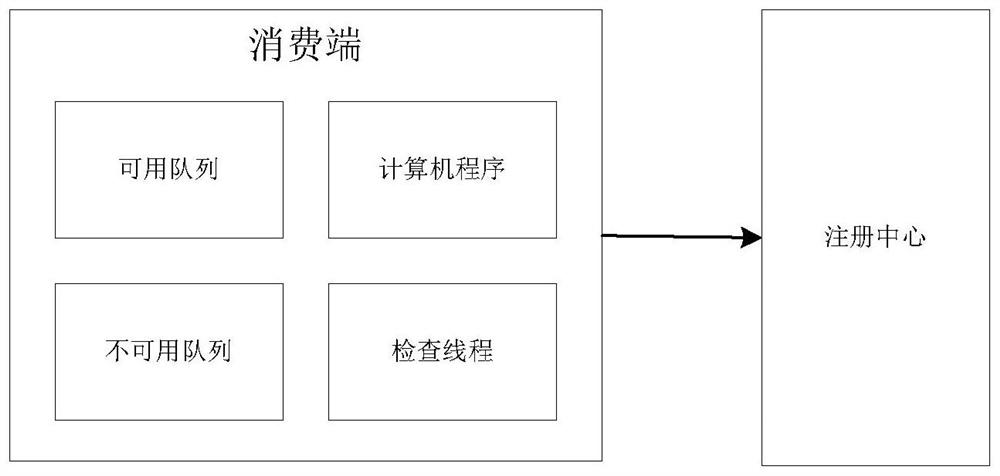
Dynamic load balancing method and system based on dual queues and registration center
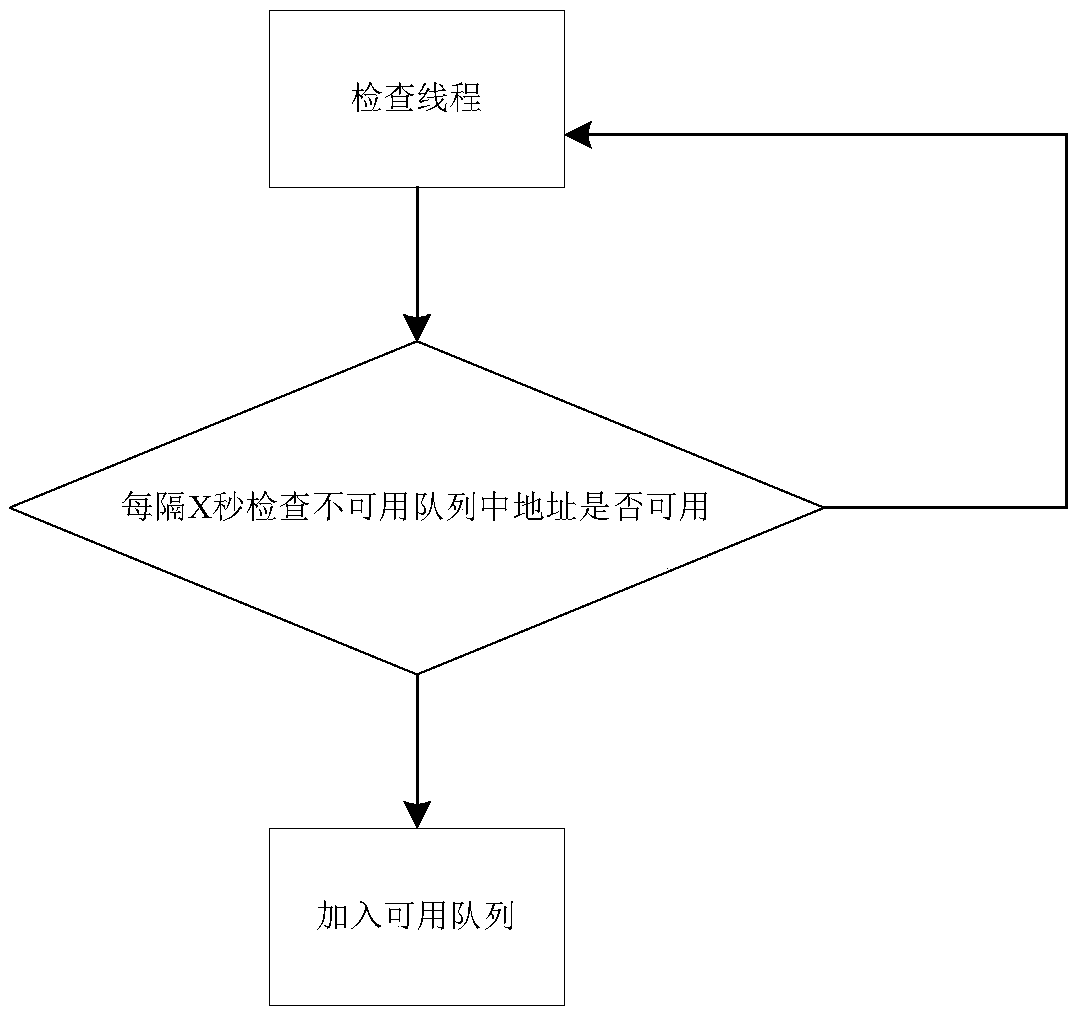
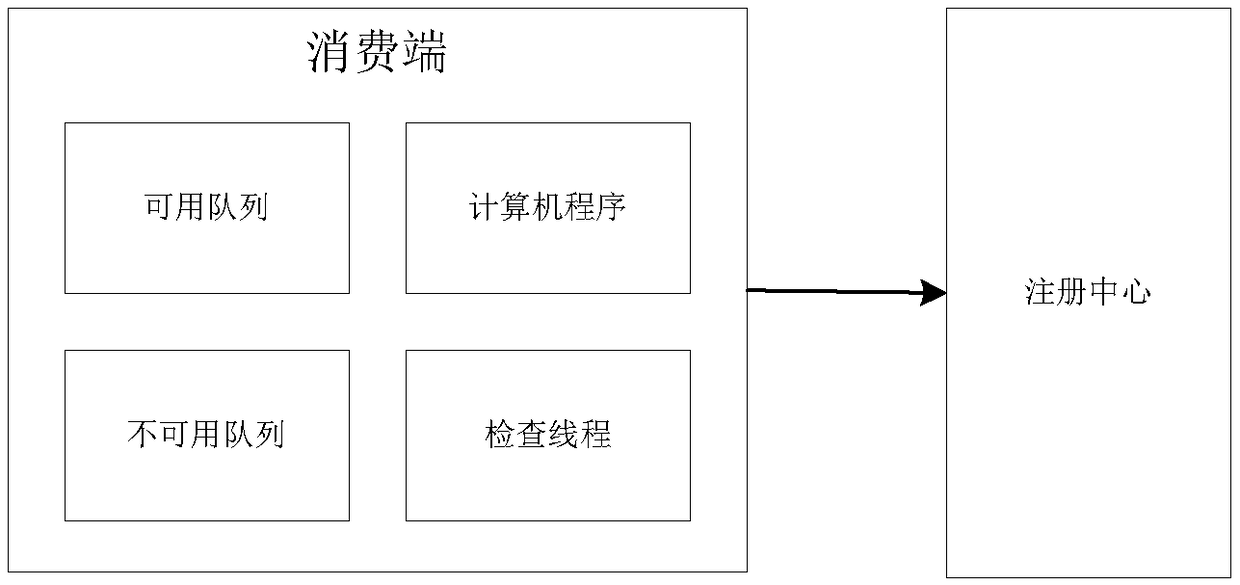
ActiveCN109413209AFix usability issuesReduced availabilityTransmissionBulk queueDistributed computing
The invention discloses a dynamic load balancing method and system based on dual queues and a registration center, and aims to ensure that an available service address can be got certainly when the service is available. According to the technical scheme, an available queue, an unavailable queue, the registration center and a timing mechanism are introduced, so that the availability of an address returned to a consuming end is ensured.
Owner:上海金融期货信息技术有限公司
Interactive design method and system of multidimensional data analysis system interface
PendingCN110109654AReduce learning costsFix usability issuesSoftware designMulti-dimensional databasesData analysis systemDesign methods
The invention discloses an interactive design method and system of a multidimensional data analysis system interface. The method comprises the following steps of step S1, defining the necessary elements in a page, wherein the necessary elements in the page comprise but are not limited to a business space classification entrance, a data measurement selection component, a data dimension-based screening component, a data time-based screening component, a data grouping component and a data presentation component; S2, dividing a service space based on a service space design method of an MOLDA model; S3, dividing the contents of the data metric selection component, the data dimension-based screening component, the data time-based screening component and the data grouping component into a plurality of blocks according to the division of the business space by the business space classification entrance; and S4, outputting a multi-dimensional data analysis result through the data presentation component.
Owner:SUN YAT SEN UNIV
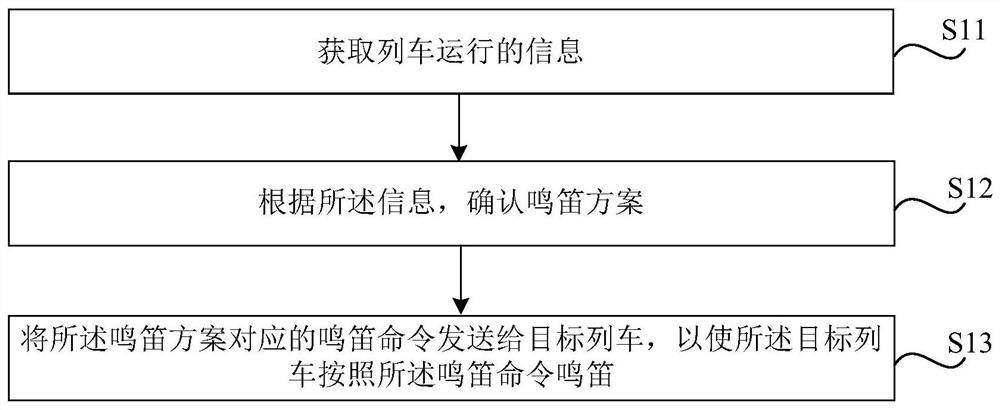
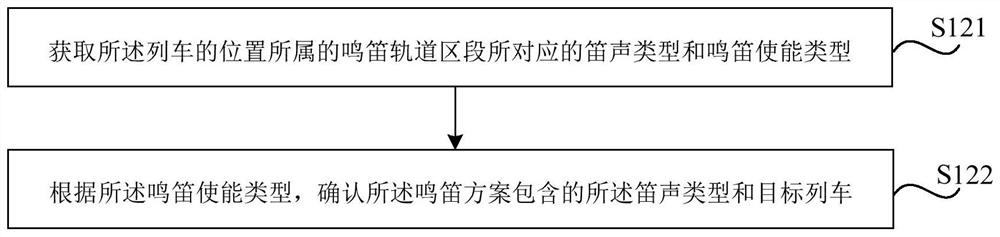
Method and device for controlling whistling of train and storage medium
ActiveCN112141163AAvoid Manual HornAddress the degree of automationSignalling indicators on vehicleAutomatic train operationReliability engineering
The invention relates to a method and device for controlling the whistling of a train and a storage medium, which are used for solving the technical problems of high degree of automation and low usability and safety of an automatic train operation system because manual train whistling is needed in the prior art. The method for controlling the whistling of the train comprises the steps of obtainingtrain operation information; determining a whistling scheme according to the information; and sending a whistling command which corresponds to the whistling scheme to a target train, so that the target train whistles according to the whistling command.
Owner:BYD CO LTD
A dynamic load balancing method and system based on double queues and registration center
ActiveCN109413209BFix usability issuesReduced availabilityTransmissionDynamic load balancingEngineering
The invention discloses a dynamic load balancing method and system based on double queues and a registration center, which ensures that available service addresses can be obtained when there are available services. The technical solution is: the present invention guarantees the usability of returning the address of the consumer by introducing double queues of available queues and unavailable queues, a registration center and a timing mechanism.
Owner:上海金融期货信息技术有限公司
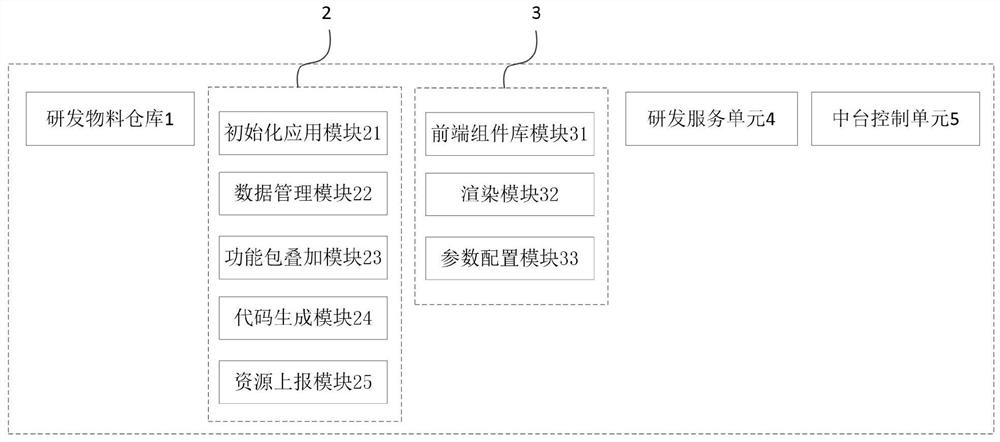
A software low-code development system and development method combined with the theory of middle platform architecture
ActiveCN112650475BImprove R&D efficiencyReduce write volumeSoftware designSoftware reuseBusiness enterpriseSoftware engineering
The present invention relates to the field of software development, in particular to a software low-code development system and a development method combined with the middle platform architecture theory; the software low-code development system includes a research and development material warehouse as a place for depositing middle-end capabilities, and as a consumption middle-end capability The low-code development platform of the site is used as the page design unit of the mid-stage carrier of the front-end capability, the research and development service unit and the mid-stage control unit of the mid-stage capability technology base; The combination of tools not only effectively improves the R&D efficiency of the enterprise, but also provides a clear division of labor for low-code developers; by packaging the business into function packages and superimposing them to realize system development, it effectively solves the contradiction between usability and practicality , and the amount of repeated code writing can be greatly reduced without increasing development costs. At the same time, each functional module in the system can be customized, making the development system more applicable.
Owner:广州云徙科技有限公司
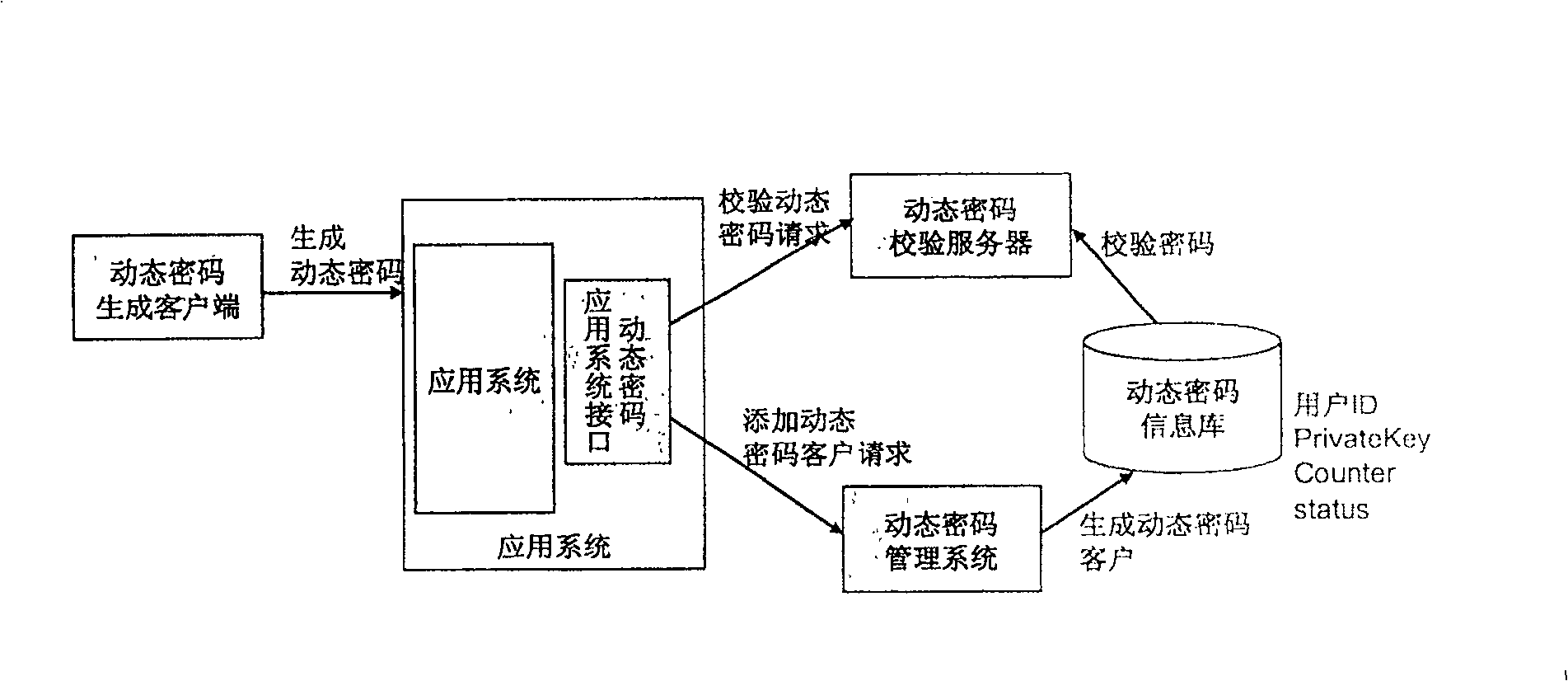
Dynamic cipher system and method based on mobile communication terminal
InactiveCN100518411CEnsure safetyTroubleshoot time synchronization issuesSecurity arrangementSecuring communicationClient-sideCurrent time
The present invention is a dynamic password system and method based on a mobile communication terminal, which includes a mobile communication terminal and a dynamic password verification server; The password generation time is combined with a symmetric encryption algorithm to generate a dynamic password, and the dynamic password is output; the dynamic password verification server has: a dynamic password verification unit, which is used to obtain the dynamic password and solve the dynamic password from the dynamic password obtained. Password generation time, compare this dynamic password generation time with the current dynamic password verification server system time, if the two times are synchronized, then use the same algorithm as the symmetric encryption algorithm to generate a verification code, if the dynamic password is the same as the verification code If the verification codes are the same, the dynamic password passes the verification. Therefore, the cost problem of the hardware client and the time synchronization problem are solved, and the security of the system is guaranteed.
Owner:北京宇信科技集团股份有限公司 +2
An intelligent image verification method and system
InactiveCN102624705BFix usability issuesFix security issuesTransmissionComputer hardwareValidation methods
The invention discloses an intelligent image verification method and an intelligent image verification system. The system comprises a data receiving module, an image code generating and verifying module, a timer module, an image data generating module, a database module, an image verification module and a data transmitting module. The data receiving module is used for receiving access requests, image verification code input and image selection sequence of a client user, the image code generating and verifying module is used for generating and verifying image verification codes, the timer module is used for performing timing and aging limiting for client access, the image data generating module is used for randomly generating prompting codes and corresponding N images, the database module is used for performing storage and index access for processing keywords, the prompting codes and image filenames, the image verification module is used for comparing the received image selection sequence of the client user with the image sequence generated by the image data generating module, and the data transmitting module is used for transmitting the image verification codes, the prompting codes, the N images and verification results to the client user, wherein the prompting codes and the N images are generated during image verification. By the aid of the intelligent image verification method and the intelligent image verification system, contradiction between usability and safety of an existing system is solved, whether the client user is a machine or not can be automatically identified, and network safety is improved.
Owner:SOUTHWEST PETROLEUM UNIV
Internet of Things search system based on artificial intelligence control and search method thereof
InactiveCN111078741AFix usability issuesSolve data security issuesDatabase management systemsSpecial data processing applicationsThe InternetEngineering
The invention discloses an Internet of Things search system based on artificial intelligence control. An input end of an artificial intelligence terminal is connected with an input module; an output end of the input module is connected with an input end of an execution module; an output end of the execution module is connected with an input end of an intelligent search module; an output end of theintelligent search module is connected with an input end of a database calling module; an output end of the database calling module is connected with an input end of an information acquisition module; an output end of the information acquisition module is connected with an input end of an intelligent identification module, an output end of the intelligent identification module is connected with an input end of the collection module, an output end of the collection module is connected with an input end of an intelligent extraction display module, and an output end of the intelligent extractiondisplay module is connected with an input end of the intelligent storage module. According to the invention, the problem that an Internet of Things search system is inconvenient to store is avoided,so that the Internet of Things search system can be well stored and is convenient to use next time.
Owner:GUANGDONG POWER GRID CO LTD +1
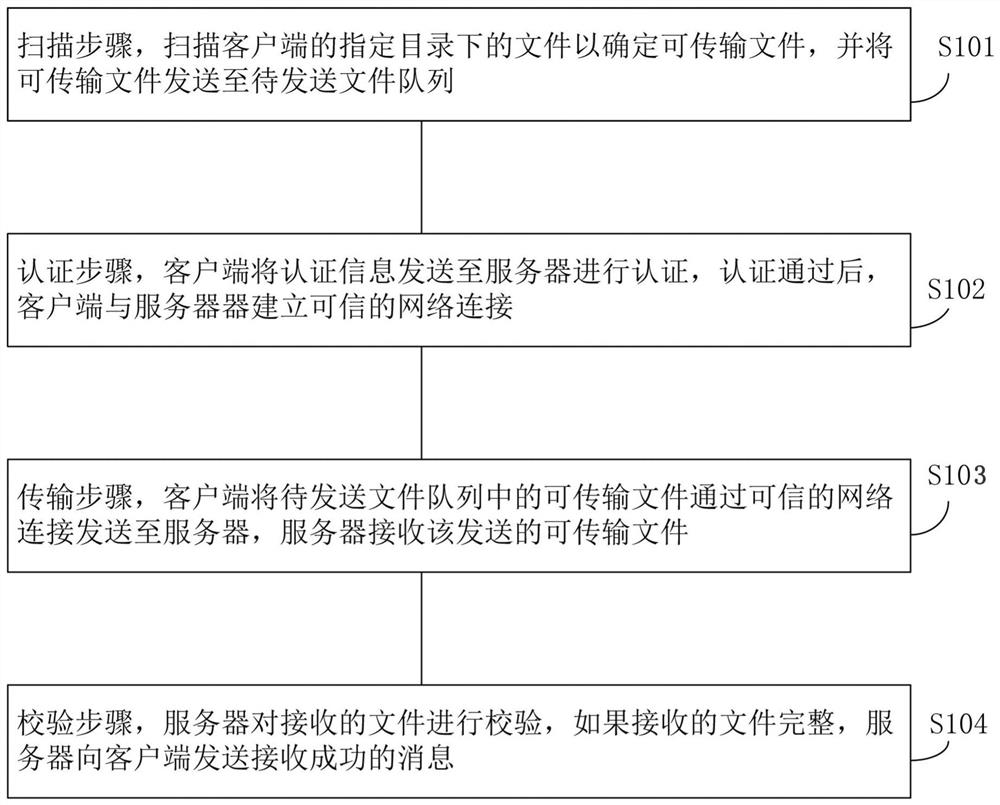
A trusted file transfer method and system
ActiveCN109309730BRealize monitoringMonitor transfersEncryption apparatus with shift registers/memoriesNetwork connectionSoftware engineering
Owner:张魏
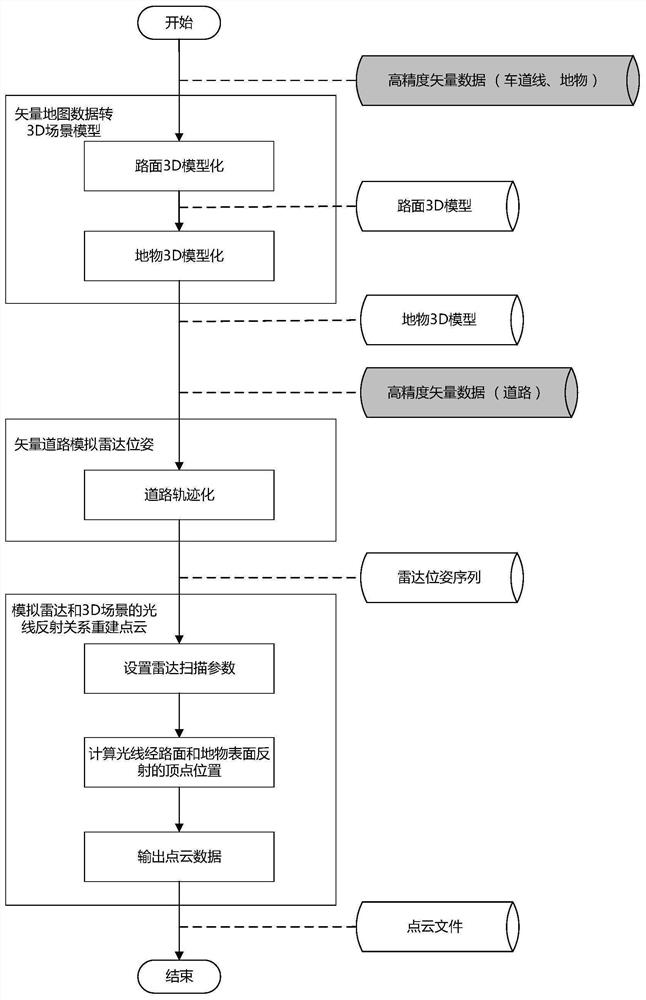
Three-dimensional point cloud reconstruction method and system based on high-precision vector map
PendingCN114114318AFix usability issuesEasy to useElectromagnetic wave reradiationPoint cloudAlgorithm
The invention relates to a three-dimensional point cloud reconstruction method and system based on a high-precision vector map. The three-dimensional point cloud reconstruction method comprises the following steps: respectively converting road surfaces and ground objects in high-precision vector map data into 3D scene models; simulating a laser radar pose according to a vector road in the high-precision vector map data, wherein the vehicle laser radar pose comprises a position and a forward direction; setting various parameters to simulate the visual condition of the laser radar so as to simulate the light reflection relation of the 3D scene, and carrying out calculation to obtain points in the visual range of the laser radar for point cloud reconstruction; the 3D point cloud can be efficiently and stably reconstructed from the high-precision vector map, and the availability problem of the vector map in a point cloud scene is solved.
Owner:WUHAN ZHONGHAITING DATA TECH CO LTD
A user privacy protection method based on path selection report
ActiveCN108882152BFix usability issuesReduce computing consumptionNetwork topologiesLocation information based servicePathPingPrivacy protection
Owner:ANHUI UNIVERSITY OF TECHNOLOGY
Renewable energy system based on current detection for data center
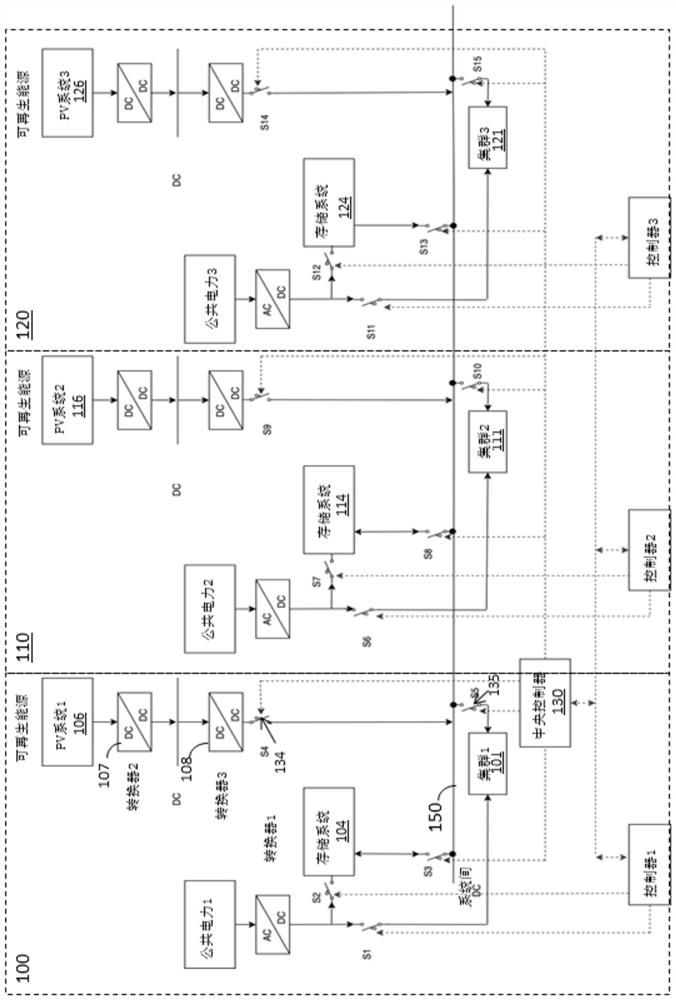
PendingCN114791762ALow costReduced service/maintenance costsDc network circuit arrangementsBatteries circuit arrangementsRenewable energy systemProcess engineering
The invention discloses a renewable energy system based on current detection for a data center. The power supply system comprises an inter-system bus, one or more renewable energy systems and one or more second switches, wherein each second switch is coupled to one renewable energy system and is used for connecting the corresponding renewable energy system to the inter-system bus. The power supply system further includes one or more current detection circuits, each current detection circuit coupled to one renewable energy system to detect an output current of a corresponding renewable energy system. The power supply system further comprises a central controller coupled to the inter-system bus and configured to activate the corresponding second switch to connect the corresponding renewable energy system to the inter-system bus in response to the output current of the corresponding renewable energy system being higher than a predetermined threshold current, to provide renewable power to at least one of the one or more server clusters or storage systems.
Owner:BAIDU USA LLC
A fault-tolerant method for dynamic adaptive sram type fpga system based on bram detection
ActiveCN111338833BFix usability issuesSolve resource problemsNon-redundant fault processingEnergy efficient computingControl cellSelf adaptive
The invention relates to a dynamic adaptive SRAM type FPGA system fault-tolerant method based on BRAM detection, which belongs to the field of intelligent fault-tolerant systems and comprises the following steps: 1) dividing reconfigurable regions and static regions on the SRAM type FPGA; Part of the dynamic reconfiguration of the regional structure combines no-redundancy to multi-redundancy dynamic adaptive structure; 3) Design the SEU rate detection structure based on the BRAM embedded block, count the faults and detect and correct errors; 5) Calculate the current flip rate and judge The redundancy scheme that needs to be adopted; 6) Implement the redundancy scheme through the control unit of the FPGA system; 7) Calculate and evaluate the availability and performance of the adaptive FPGA system. The present invention comprehensively considers the situation in the actual application of the FPGA, weighs the contradiction between usability and performance resources, and dynamically changes the adaptive redundant structure of the FPGA system according to the expected radiation level (SEU rate), thereby improving the efficiency of the system when performing tasks, reducing the It ensures the power consumption of the system when there is no failure, and has good portability.
Owner:BEIHANG UNIV
Unmanned equipment key management system, method, device and equipment and storage medium
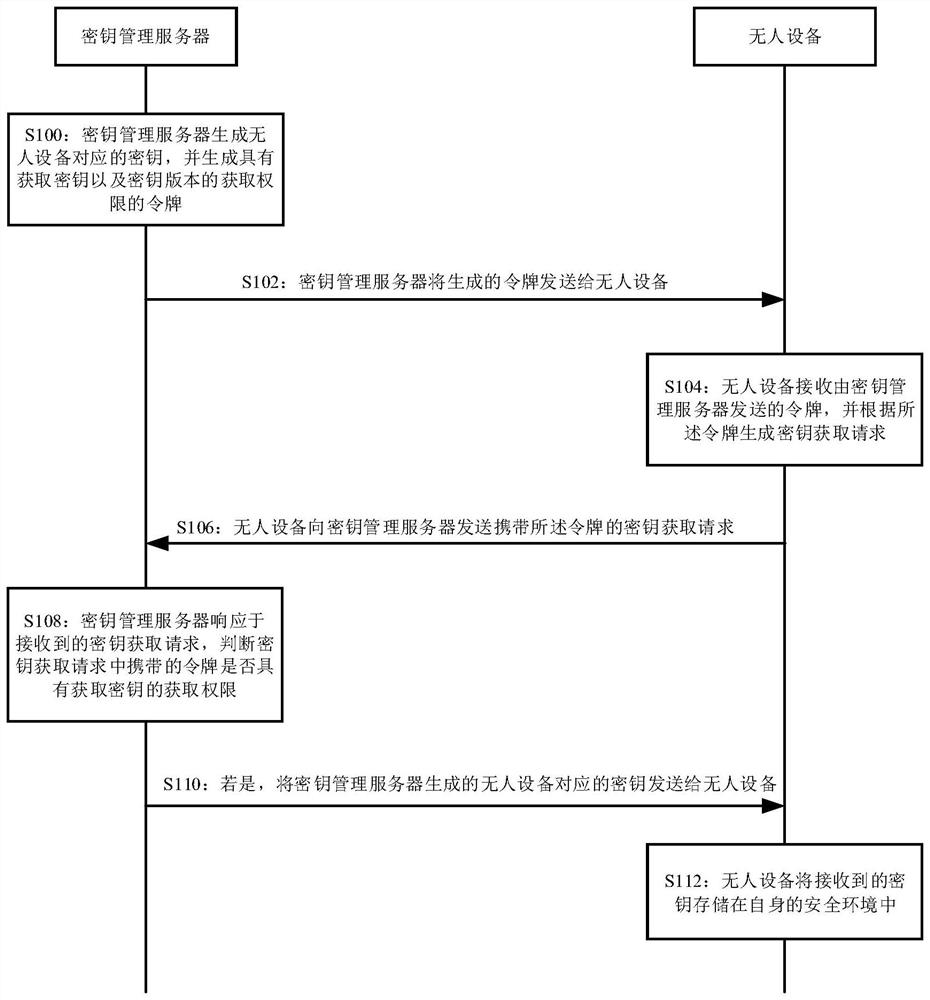
PendingCN114301606AFix usability issuesKey distribution for secure communicationUser identity/authority verificationKey storageManagement system
The invention discloses an unmanned device key management system, method, device and equipment and a storage medium, a key management server obtains a request based on a key version carrying a token sent by an unmanned device, and sends a current version of a key to the unmanned device under the condition of judging that the token carried in the request has an obtaining permission; and when the unmanned device determines to update the key according to the current version of the key, the unmanned device requests to acquire the key of the current version from the key management server, and stores the key of the current version in the own security environment. It can be seen that in the unmanned device key management system and method provided by the present specification, the unmanned device stores the key sent by the key management server in its own secure environment, and even if the unmanned device is located in an area where communication signals are poor, the key stored in its own secure environment can be used, thereby improving the security of the unmanned device. The problem of availability of the secret key when the unmanned device is in signal disconnection is solved.
Owner:BEIJING SANKUAI ONLINE TECH CO LTD
A custom service generation method, device, computer equipment and storage medium
ActiveCN108920135BFlexible support for individual needsFix usability issuesCreation/generation of source codePersonalizationFunction point
The embodiment of the present invention discloses a custom service generation method, device, computer equipment and storage medium. The method includes: the service interface obtains service demand information; the service interface corresponds to multiple function points, and the list of function points and service plug-in instances Associated, the business plug-in instance is generated through the plug-in configuration file corresponding to the business interface; the business interface obtains the business plug-in The plug-in instance and the demand parameter information obtain the execution results of the function points corresponding to each function point; the business interface combines the execution results of the function points corresponding to each function point to obtain the business processing results corresponding to the business requirement information. The technical solution of the embodiment of the present invention realizes flexible support of individual requirements of each service and fault isolation of each service.
Owner:杭州贝购科技有限公司
Modular and scaleable port vehicle
The invention relates to a central module (1) for a modular vehicle (100). The module is characterized in that it comprises, on either side of a loading surface (10), a first end (IA) having a first junction surface (11) and a second end (IB) opposite said first end (IA) having a second junction surface (12) that is symmetrical nonparallel to said first surface (11), each of the latter designed to be capable of complementarily engaging with a complementary junction surface (23) of a side module (2) capable of engaging with the central module (1) by buttressing assembly. The invention relates to a modular vehicle (100) comprising such a module (1). The vehicle is characterized in that the latter is assembled, at each end (IA; IB) thereof, to a side module (2), one side module comprising means for running on the ground (30). The invention relates to a train of vehicles comprising such a vehicle (100).
Owner:ENVISION VEHICLE ENG NOVASIO TECH EVENT
Data processing method and device
ActiveCN104965882BFix usability issuesImprove usabilitySpecial data processing applicationsDatabase design/maintainanceUsabilityLarge scale data
The invention discloses a data processing method and device and belongs to the field of databases. The method comprises: determining a to-be-processed data line in a data table; educing the to-be-processed data line in n batches; deleting the data line which is educed in each batch from the data table; or, deleting the data line from the data table after the data line is archived to another data table. According to the data processing method and device disclosed by the invention, the educed data line is deleted by virtue of multi-batch data educing operation and less data educing operation of each batch, so that the problem in the correlated technology that the usability of the database is affected by relatively long data deleting time is solved; and when the large-scale data is deleted or archived, the data table is not locked on a large scale, the pressure on the data table in unit time is relatively small and the performance of the data table is not affected, so that the effect of the usability of the data table is improved.
Owner:XIAOMI INC
Distributed file system data import method and device
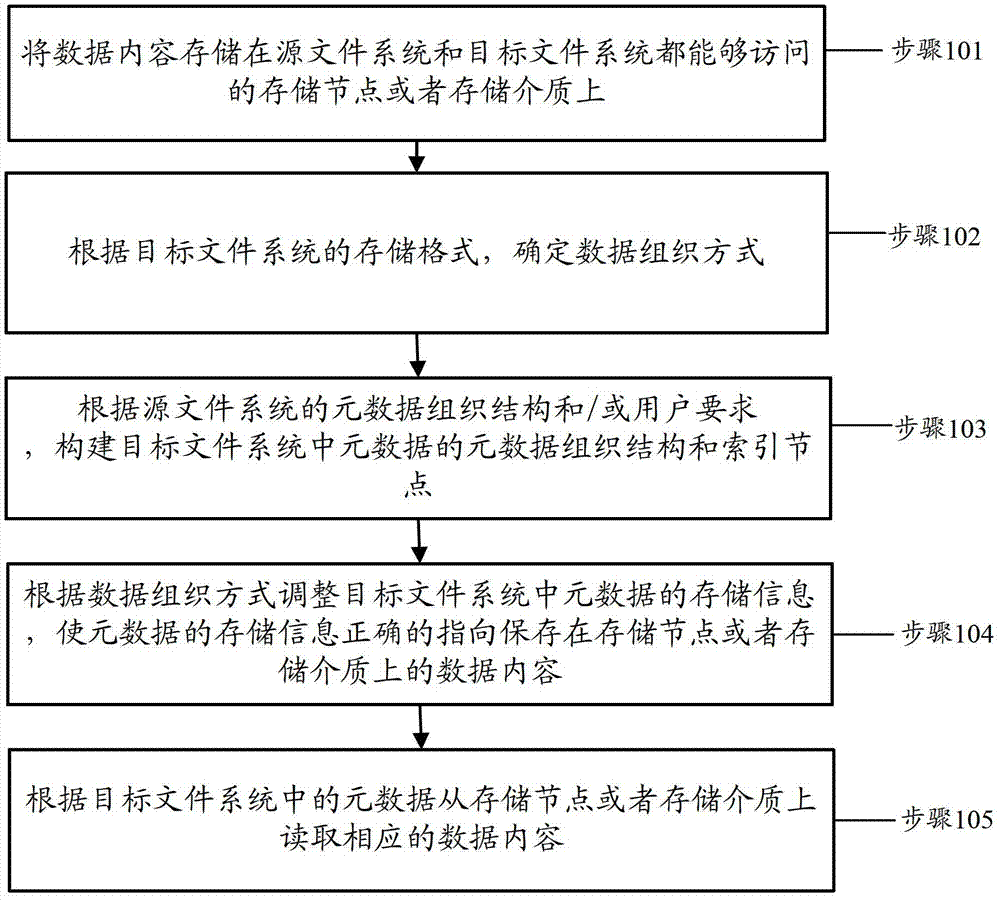
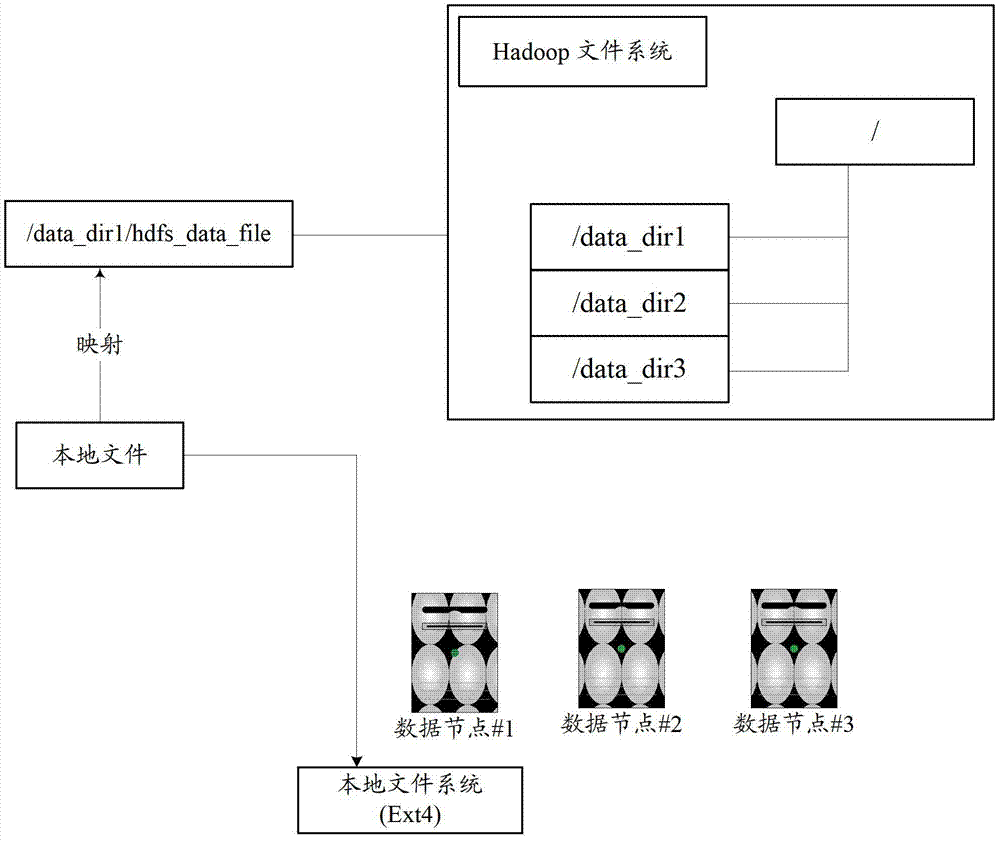
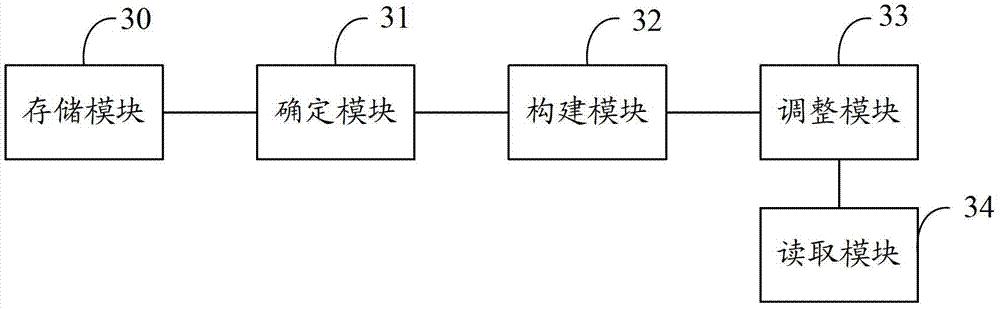
InactiveCN104077315BFix usability issuesSave resourcesSpecial data processing applicationsDistributed File SystemData content
The invention discloses a distributed file system data importing method and a distributed file system data importing device. The method comprises the following steps that: data contents are stored onto a storage node or a storage medium capable of being accessed by a source file system and a target file system; a data organization mode is determined according to a storage format of the target file system; an index node and a metadata organization structure of metadata in the target file system are built according to a metadata organization structure of the source file system and / or requirements of users; the storage information of the metadata in the target file system is regulated according to the data metadata mode, so the storage information of the metadata correctly points to the data contents stored on the storage node or the storage medium; and the corresponding data contents are read from the storage node or the storage medium according to the metadata in the target file system.
Owner:NAT COMP NETWORK & INFORMATION SECURITY MANAGEMENT CENT +1
A Data Hiding Method Based on Lagrange Interpolation and Cloudiness
InactiveCN104915609BTolerate mistakesFix usability issuesDigital data protectionInformation recoveryOriginal data
The invention discloses a data hiding method based on a Lagrange interpolation method and multiple clouds, which is applied in a system under a multi-cloud environment. The system comprises four parts: a user, a client, a data uploading layer, a data downloading layer and the clouds; before data are uploaded, an information segmentation algorithm of Reed Solomon erasure codes is used for segmenting the user data on the client, the Lagrange interpolation method is then used for carrying out information hiding on each block of segmented data, and finally, each block of data is stored in a different cloud storage. During data downloading, the data only need to be obtained from part of the cloud storages, the Lagrange interpolation method is first used for carrying out hidden information recovery on each block of data, and a recovery algorithm in Reed Solomon is then used for merging the data blocks to recover the original data. The data hiding method based on the Lagrange interpolation method and the multiple clouds solves the availability problem of services and the limitation of a single cloud storage; while reducing storage spaces, the usage of the Reed Solomon algorithm can tolerate the errors of the cloud storages; the usage of the Lagrange interpolation method solves the confidentiality problem of data, protecting the privacy of user data.
Owner:WUHAN UNIV OF SCI & TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com