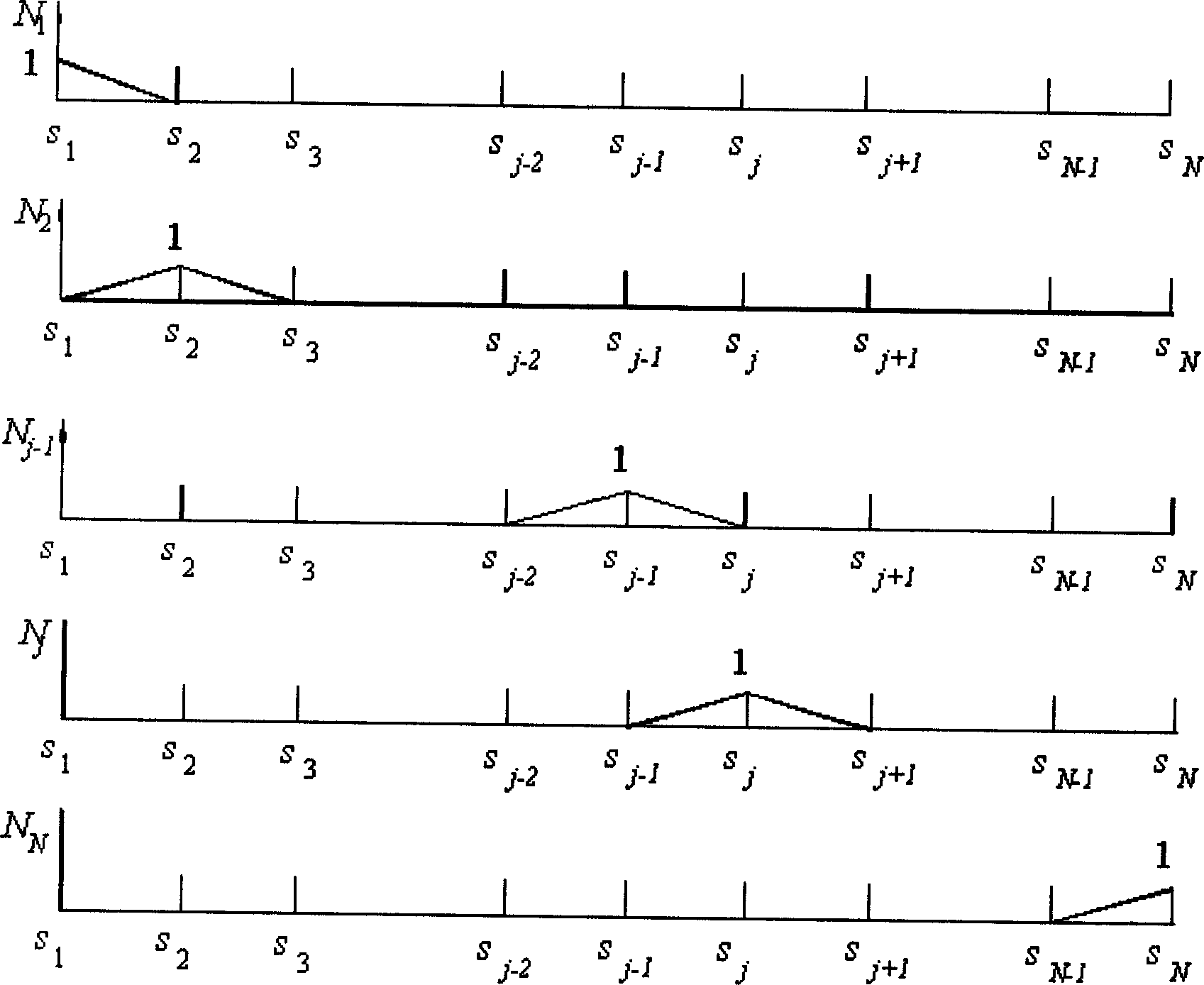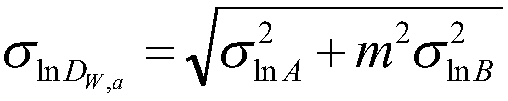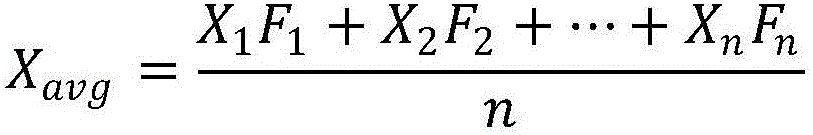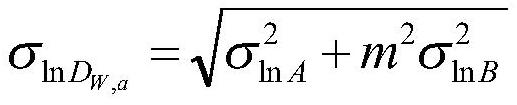Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
46results about How to "Determine security" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
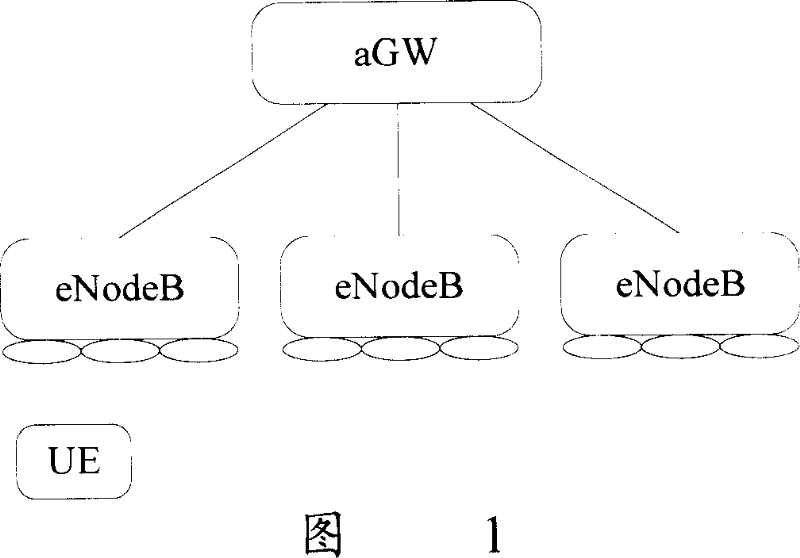
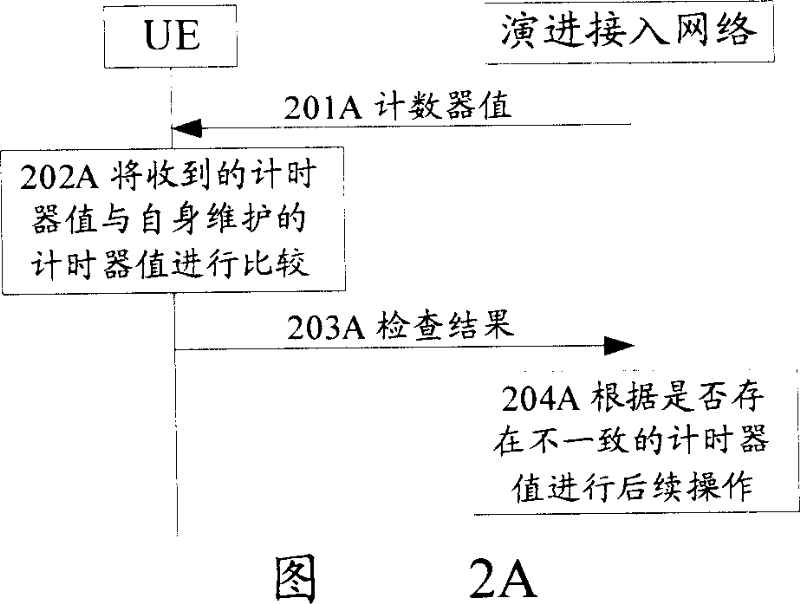
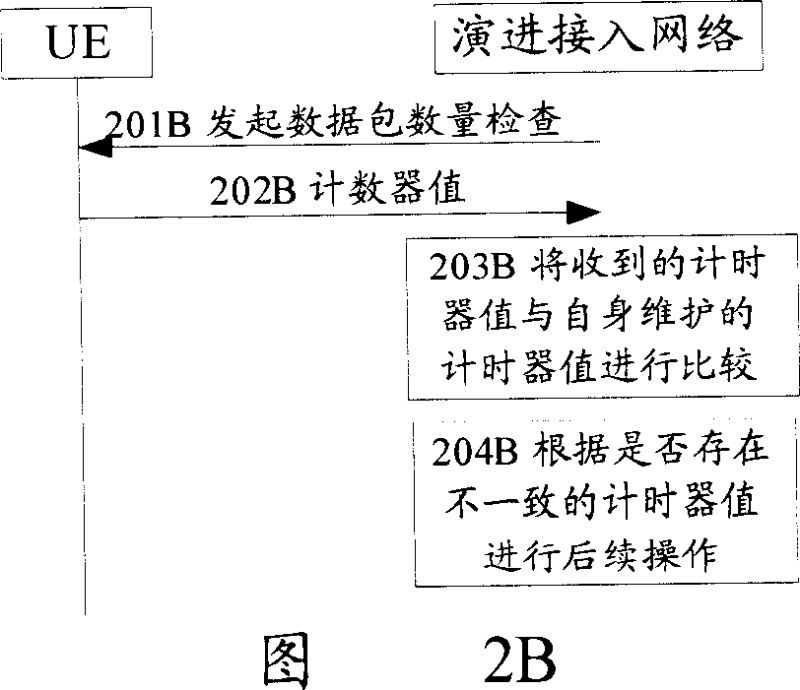
Method for realizing safety warranty in evolution accessing network
ActiveCN101039314ADetermine securityImplement local authenticationTransmissionArithmometerShared secret
The present invention discloses a method of realizing security assurance in an evolutive access network, a UE and the evolutive access network separately maintain more than one arithmometers which are used for expressing data flow transmitted between the UE and the evolutive access network. The method comprises: when the evolutive access network satisfies the scheduled qualifications, an inspection of data flow is executed to the UE; the UE or the evolutive access network compares the arithmometer value from themselves with that from the opposite terminal; the evolutive access network performs the following disposal based on the comparing result of that whether there exists an conflicting arithmometer value; and the security of the evolutive access network is ensured with basis of the inspection results. Furthermore, information or commands, messages transmitted between the UE and the evolutive access network are totally protected by a shared secret-key therebetween, thus a periodic authentication is realized by this total protection.
Owner:北京禾怡管理咨询有限公司
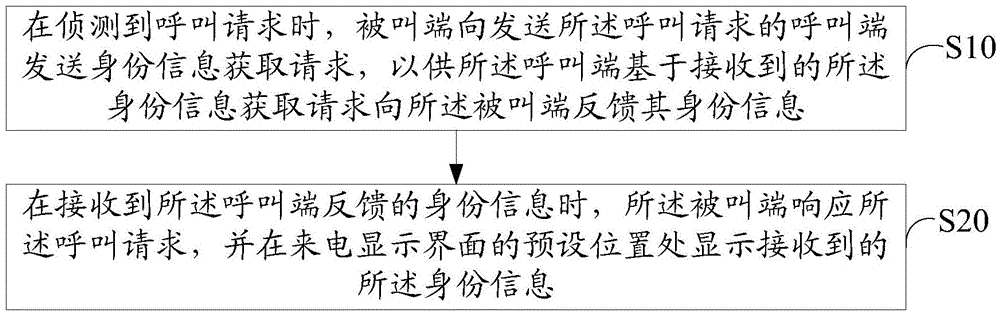
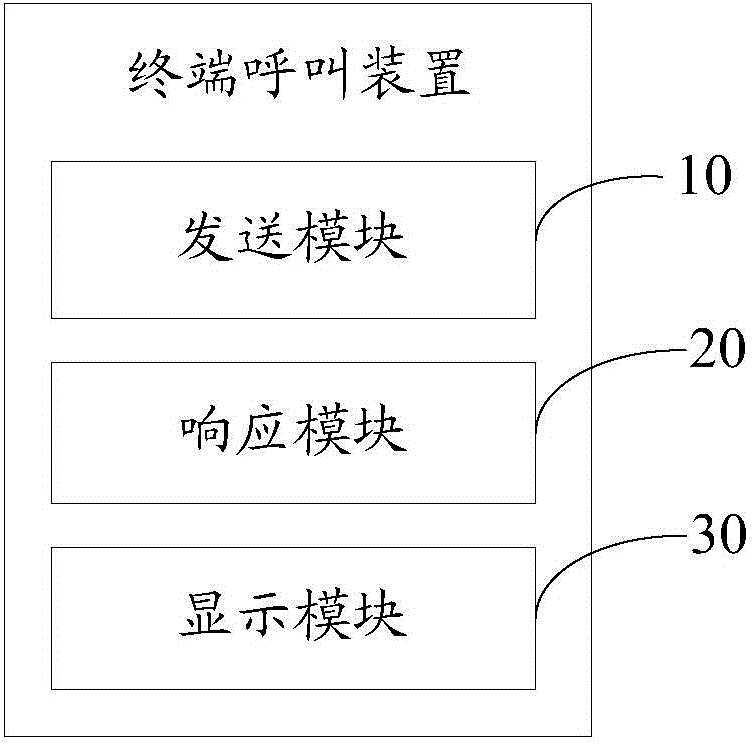
Terminal communication method and device
The invention discloses a terminal communication method. The terminal communication method comprises the following steps that when a calling request is detected, a called end sends an identify information obtaining request to a calling end which sends the calling request, so that the calling end obtains the request based on the received identify information and feeds the identify information back to the called end; when the identify information fed back by the calling end is received, the called end responds to the calling request and displays the received identify information on a preset position of a calling display interface. The invention further discloses a terminal communication device. According to the terminal communication method and the terminal communication device, information of a calling party is displayed on the calling display interface in time before a user switches on the calling, and the safety of the calling is determined; the method and the device are very convenient and rapid.
Owner:NUBIA TECHNOLOGY CO LTD
Engineering structure fundamental frequency test wireless data collection system
ActiveCN106248200ADetermine securityFast operationTransmission systemsSubsonic/sonic/ultrasonic wave measurementCollection systemWireless data
The invention discloses an engineering structure fundamental frequency test wireless data collection system comprising an acceleration sensor, an analog signal processor, an analog-digital signal conversion and data latching device, a programmable logic controller, a main control CPU controller, an electric conversion and data communication connector and a power supply module. The main control CPU controller adopted in the engineering structure fundamental frequency test wireless data collection system is a DSP processor manufactured by American TI company, parallel multiplication and integer or floating point data ALU operation in a single period can be performed, high data operation speed can be fulfilled, and a large-data-amount calculation can be finished. In the engineering structure fundamental frequency test wireless data collection system, a mobile 3G communication technologies which are now prevalently applied are adopted for data communication, large scope monitoring of a structure can be realized via the system without wire arrangement, many procedures in on-site monitoring processes can be eliminated, and structure monitoring reliability of the system can be ensured. The acceleration sensor of the engineering structure fundamental frequency test wireless data collection system is characterized by high precision, high sensitivity output, high dynamic range, good linearity, stable and reliable performance and the like.
Owner:大连九州创智科技有限公司
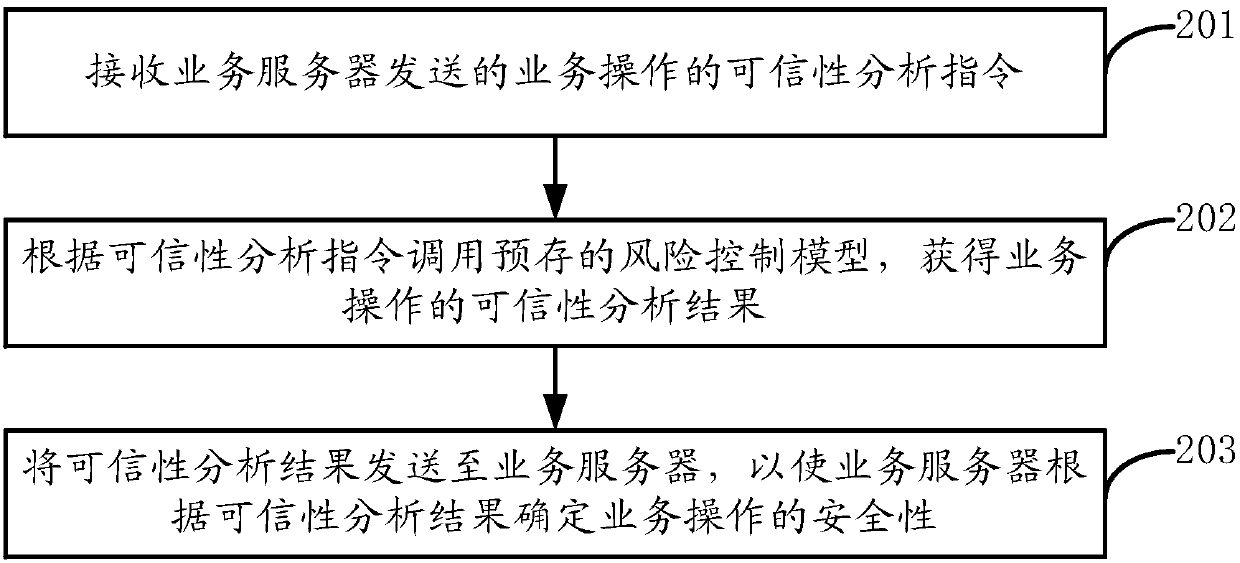
Method for verifying safety of business operation, device, terminal and server
ActiveCN105516071ATrue reflection of social relationshipsTrue reflection of living habitsUser identity/authority verificationComputer security arrangementsRisk ControlSoftware engineering
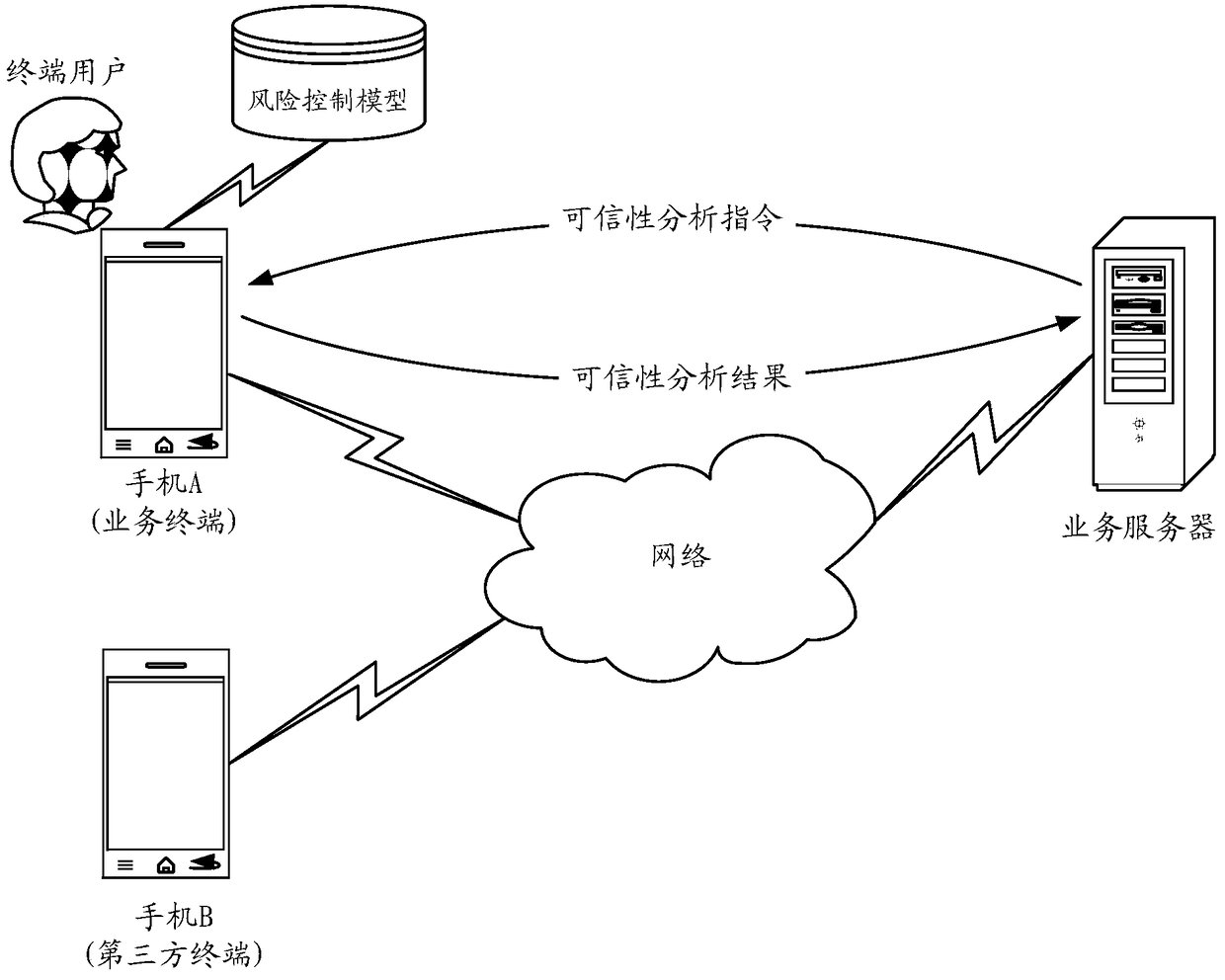
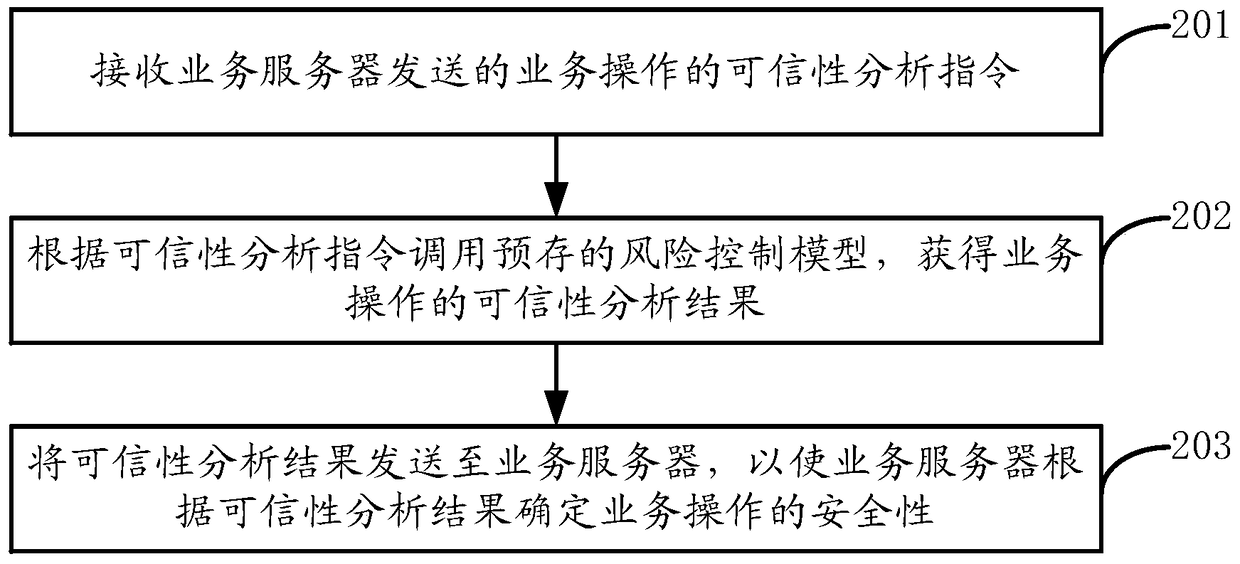
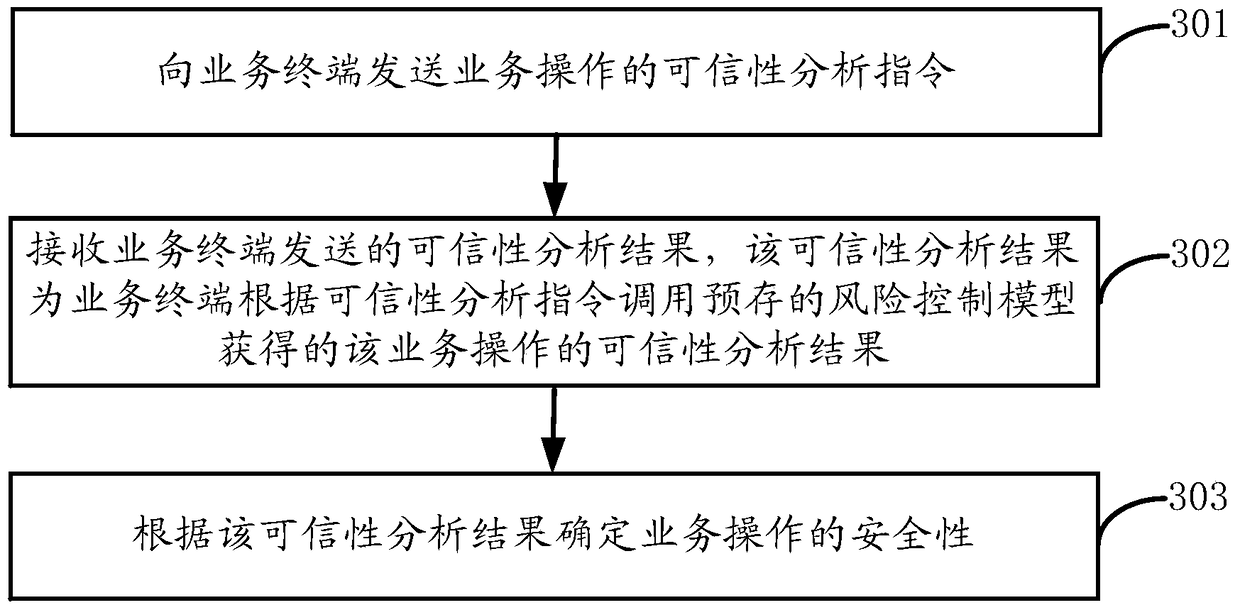
The invention discloses a method for verifying safety of business operation, a device, a terminal and a server. The method comprises steps of receiving a credibility analysis instruction of the business operation sent by a business sever; calling a pre-stored risk control module according to the credibility analysis instruction and obtaining a credibility analysis result of the business operation; and sending the credibility analysis result to the business server so as to allow the business server to determine safety of the business operation according to the credibility analysis result. According to the invention, by use of the risk control module in a business terminal, the credibility analysis result of the business operation can be obtained, so precision of safety verification of the business operation can be improved.
Owner:ADVANCED NEW TECH CO LTD
Method and system for detecting request safety
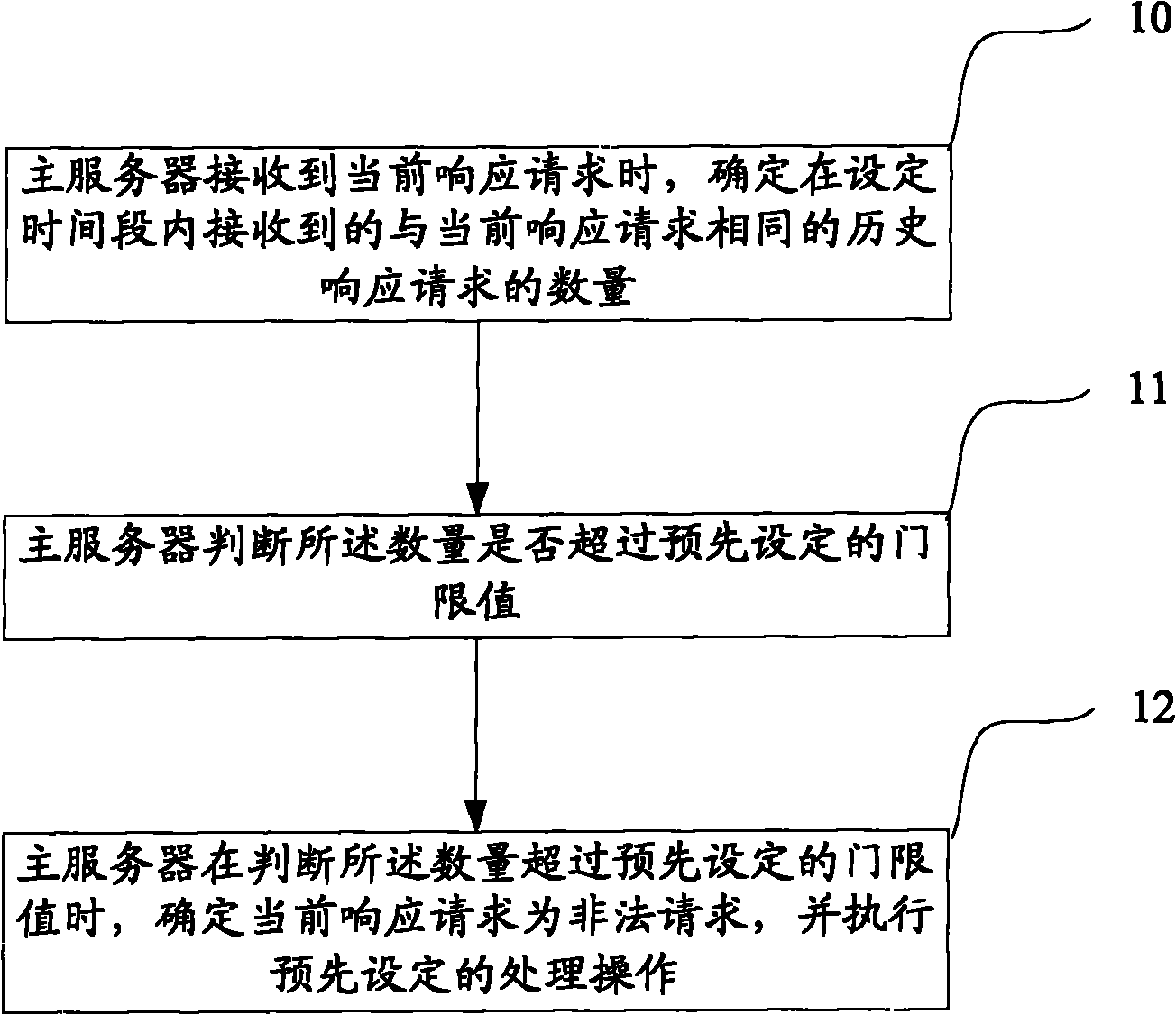
The embodiment of the invention discloses a method and a system for detecting request safety, relating to the network safety field and being used for providing a proposal for detecting response request safety. In the method, the number of the past response requests which are the same as the present response requests and are received in a given time slot is determined when a main server receives the present response requests; the main server judges whether the number exceeds a preset threshold value; and when judging that the number exceeds the preset threshold value, the main server determines that the present response requests are illegal requests and exerts a preset treatment operation. When in use, the invention can effectively detect the safety of the response requests of an application server.
Owner:BLUEDON INFORMATION SECURITY TECH CO LTD
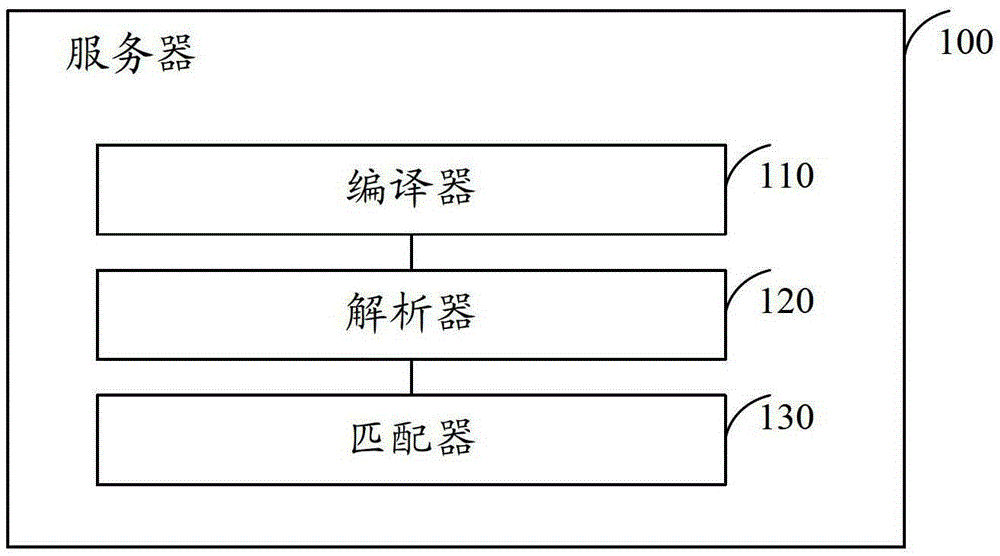
Method, server and system for detecting safety of file sample
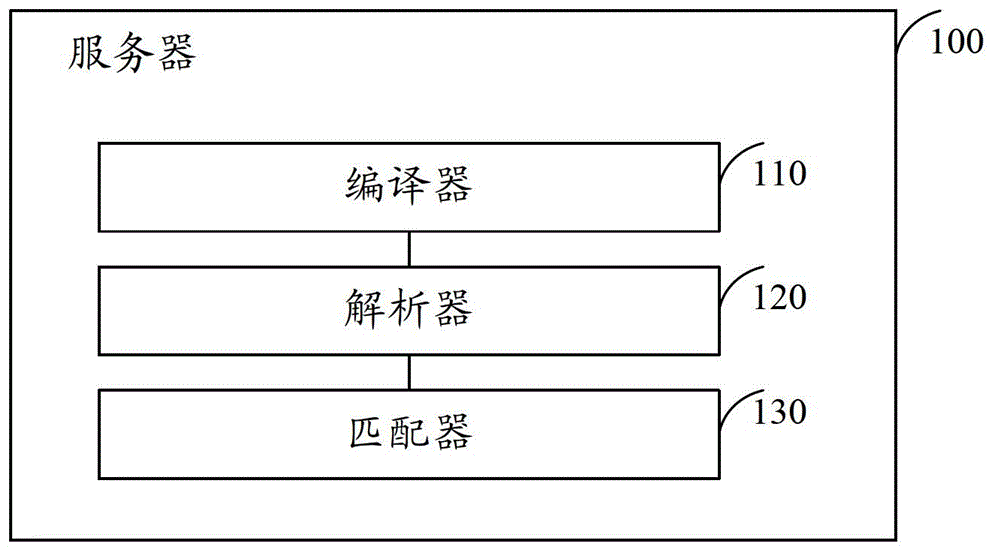
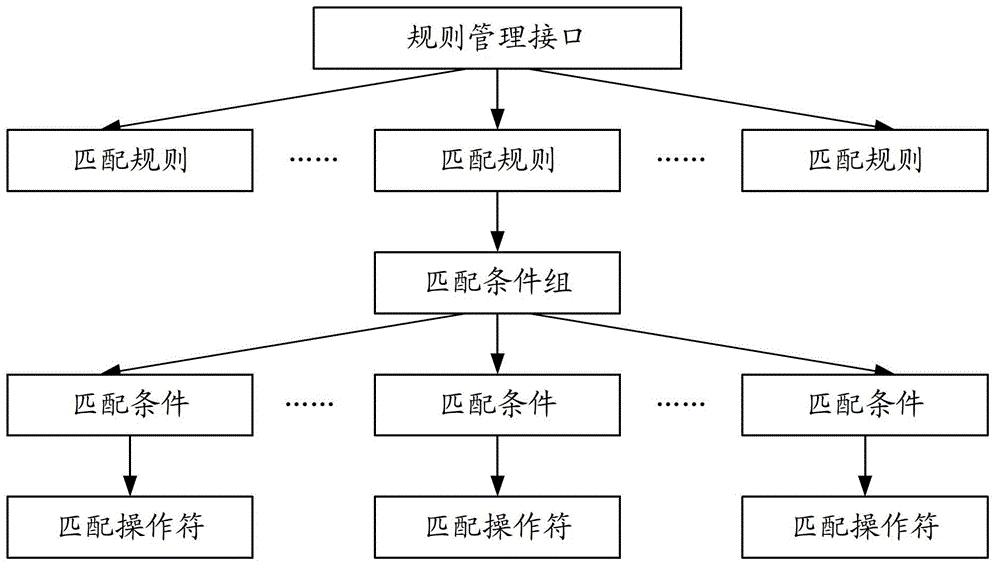
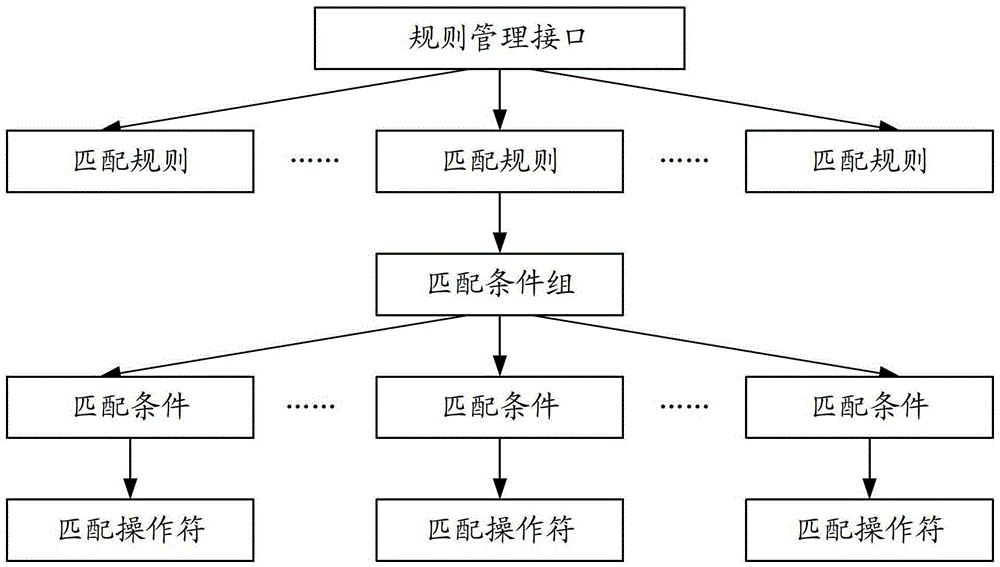
The invention discloses a method, a server and a system for detecting the safety of a file sample. The method comprises the following step of configuring rule description of rules to generate a source file containing each rule description; analyzing each rule from the source file, and constructing a rule management interface according to the configured rule organism structure by utilizing each analyzed rule, wherein the rule management interface comprises a plurality of matching rules; and receiving characteristics of an inputted file sample, matching and comparing the characteristics of the file sample with the matching rules through the rule management interface, and returning a matching result to a client so that the client determines the safety of the file sample according to the matching result. The method, the server and the system for detecting the safety of the file sample, disclosed by the invention, can solve a problem that rogue programs are leaked in judgment during detection generated by the fact that the change of rules for the detection is difficult and wastes too much time, and the change speed of the rules can not follow up the variation speed of the virus in the prior art.
Owner:BEIJING QIHOO TECH CO LTD
Method for confirming stress intensity factor distribution on member crack tip
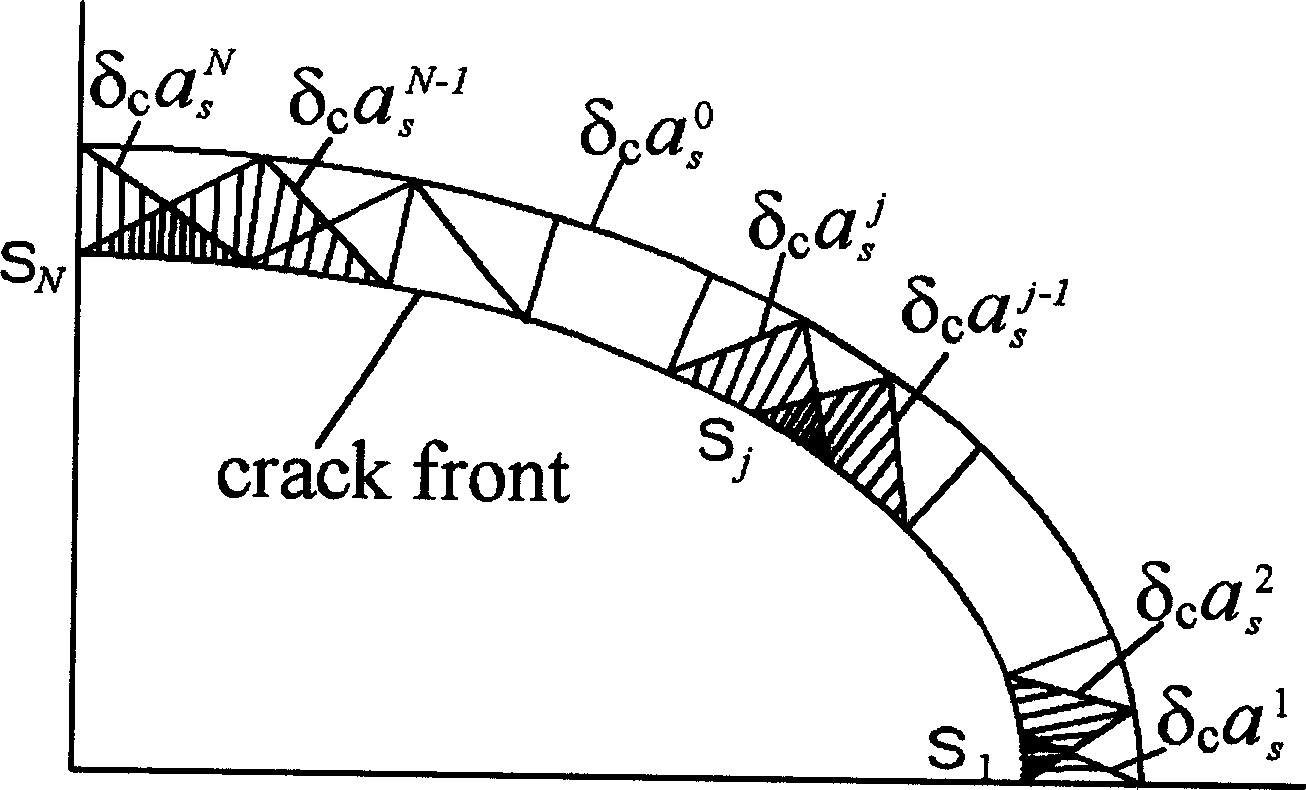
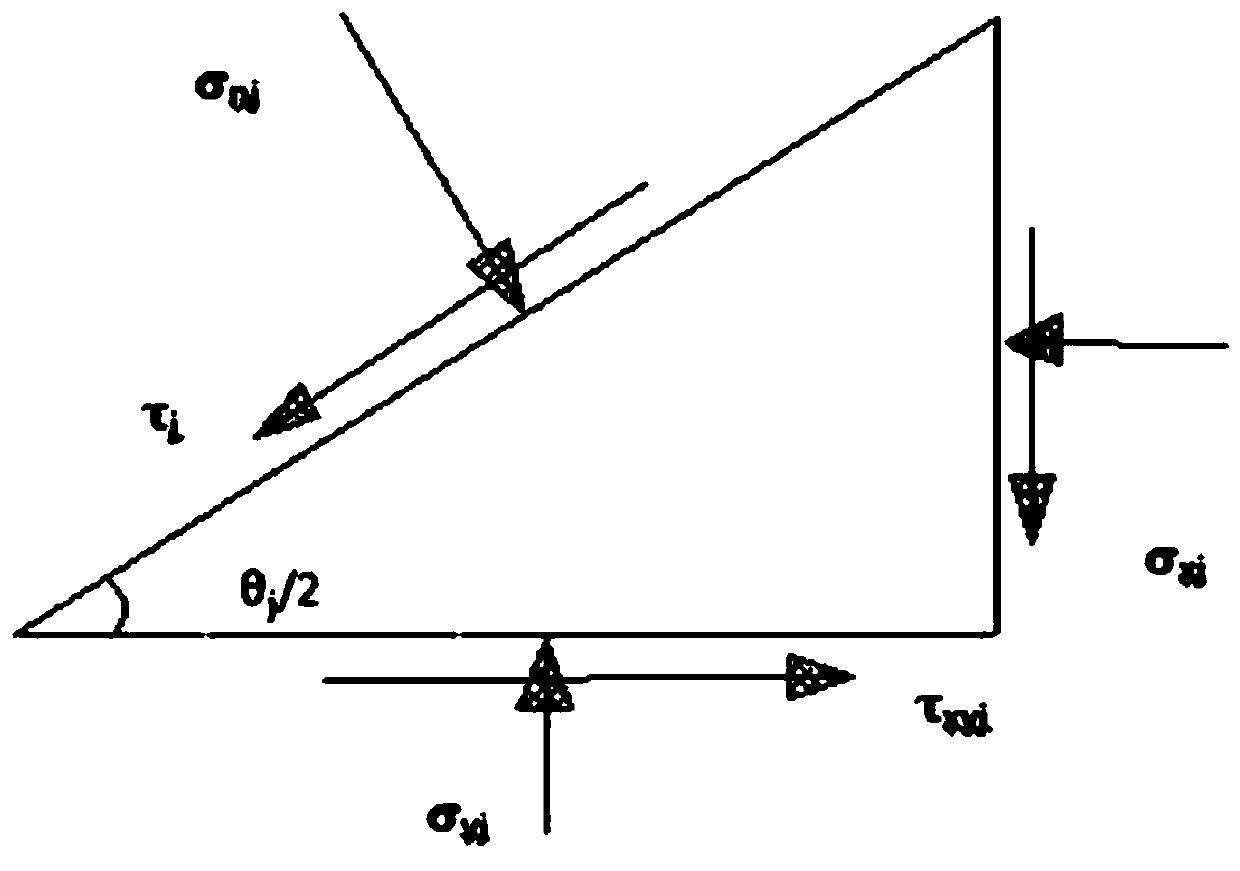
InactiveCN1866245ADetermine securityDetermining Fatigue LifeComplex mathematical operationsLocal variationEngineering
The disclosed determining method for crack front stress intensity factor distribution of a structural member comprises: providing the thermal load, surface force load and body force load, as well as the general weight function base equation acted by any of three loads; dividing the front into N-1 subsegments by N nodes, and using a basic interpolation function N(s) and local variation function N'j(s) for every node j. This invention can determine the factor distribution for curve-type 3D crack with high precision and efficiency by finite modes and interpolation way.
Owner:ZHEJIANG UNIV OF TECH
Internet bar monitoring system
InactiveCN104601348AEnsure healthy and orderly developmentDetermine securityCharacter and pattern recognitionClosed circuit television systemsTime informationMonitoring system
An Internet bar monitoring system of the present invention includes: multiple cameras; a bar counter server; and a monitoring central server, wherein the bar counter server includes: a card reader reading ID card information, a fingerprint reader registering fingerprint information, and a server database recording network browsing information, and the server database includes ID card information, on-line time information, and network browsing remaining balance information; and the monitoring central server stores a fingerprint of a person corresponding to the ID card information, reads the fingerprint information and the ID card information registered by the bar counter server, compares the fingerprint information with the currently-stored fingerprint information, and the ID card information with an ID card corresponding to the currently-stored fingerprint information, and returns a comparison result to the bar counter server. The system of the present invention determines whether the ID for the network browsing person is true according to the match of the fingerprints; the bar counter server would stop providing the Internet service if the age of the network browsing person is smaller than 18, or if the on-line time exceeds 8 hours, thereby ensuring the Internet bar to be developed in a healthy and ordered way, and also guaranteeing the safety of the Internet bar and the network browsing person.
Owner:李竹君
Method for network security management and terminal
InactiveCN106209918AImprove securityDetermine securityTransmissionSecurity arrangementNetwork addressNetwork management
The embodiment of the invention discloses a method for network security management and a terminal. The method comprises the steps of obtaining network access information generated when a terminal carries out network access operation in a to-be-tested network according to a preset network address; judging whether operation abnormal data caused by the network access operation and / or network attack data obtained from a server exist in the network access information; and if so, determining the security of the to-be-tested network based on the network attack data and / or the operation abnormal data. By adoption of the embodiment, a user can independently select to connect to a security network based on the demand thereof, and the networking security of the user is protected.
Owner:SHENZHEN GIONEE COMM EQUIP
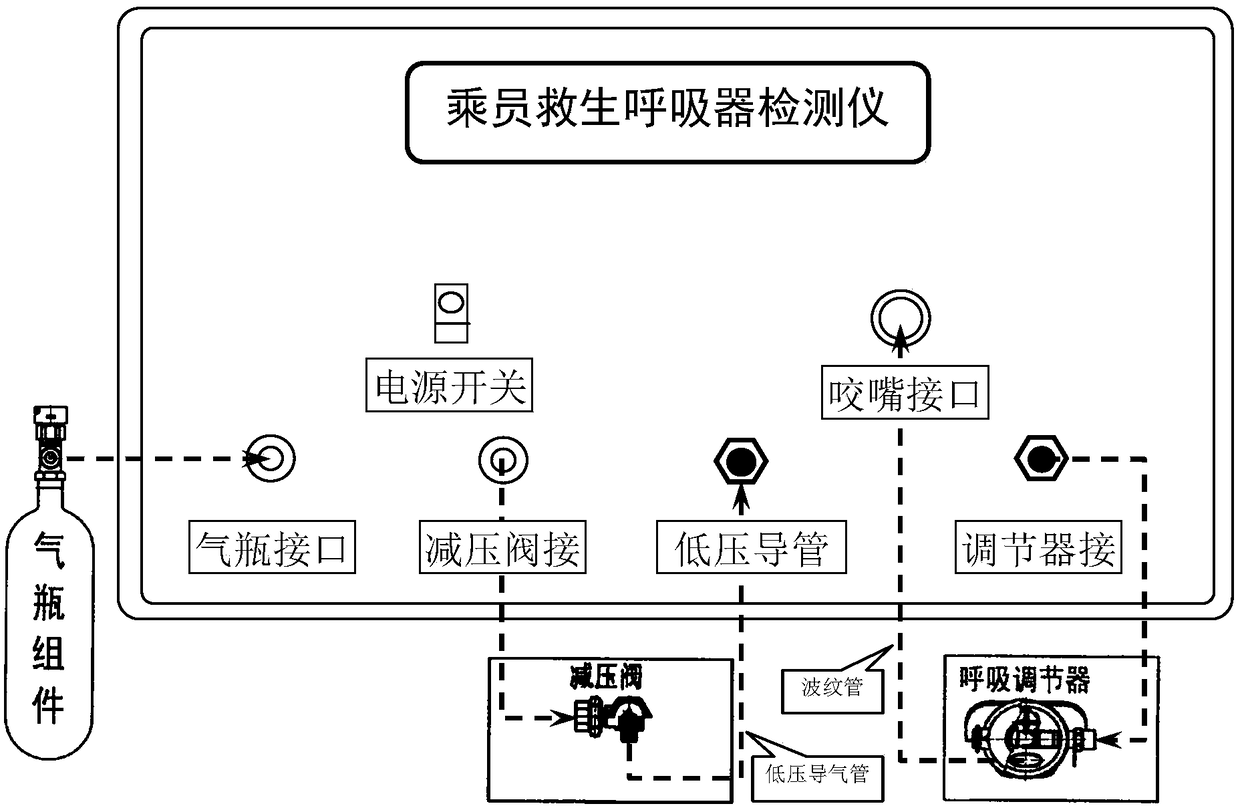
Respirator detector and detecting method thereof
InactiveCN109470427AEasy to operateTroubleshooting Linkage Wobble ProblemsMeasurement of fluid loss/gain rateEngineeringPressure reduction
The invention discloses a respirator detector. The respirator detector comprises a to-be-tested respirator air bottle, a high-pressure sensor, a first cut-off valve, to-be-tested respirator pressure reduction valve, a medium-pressure sensor, a second cut-off valve, a to-be-tested respirator adjusting device, an artificial lung and a low-pressure sensor wherein one end of the high-pressure sensor is connected with the to-be-tested respirator air bottle, the other end is connected with a signal receiving end, one end of the first cut-off valve is connected with the to-be-tested respirator air bottle, the to-be-tested respirator pressure reduction valve is connected with the first cut-off valve, one end of the medium-pressure sensor is connected with the respirator pressure reduction valve, the other end is connected with a signal receiving end, the second cut-off valve is connected with the to-be-tested respirator pressure reduction valve, the to-be-tested respirator adjusting device isconnected with the second cut-off valve, the artificial lung is connected with the respirator adjusting device, one end of the low-pressure sensor is connected with the artificial lung, and the otherend is connected with a signal receiving end. The invention further provides a detecting method of the respirator detector, and the airtightness of a whole device, the outlet pressure of the respirator pressure reduction valve, the respiration resistance of a respirator adjusting device and flow rate detection can be detected in one attempt.
Owner:中国人民解放军陆军装甲兵学院士官学校
Earth slope seismic stability analysis method combining equal reference unit method and sliding surface method
InactiveCN109632460AConsider stress-strain propertiesNot only considering the dynamic characteristicsStrength propertiesTime rangeSlope stability analysis
The invention discloses an earth slope seismic stability analysis method combining an equal parameter unit method and a sliding surface method. The earth slope seismic stability analysis method comprises the following steps that firstly, the static load is applied in a grading mode, according to the change conditions of the stress strain in the soil after applying static load of each stage, and the mechanical parameters are corrected, a constitutive model is constructed as a mathematical model of the stress-strain relation according to actual stress strain characteristics, after all the staticloads are applied, and the calculated accumulated stress is the static stress in the preseismic earth slope; then, according to the anti-seismic design requirements of the earth slope, an earthquakeacceleration time-range relation is determined, and then inputting is carried out by adopting a two-stage time period method; and finally, the static force and the power reaction are calculated, and the effective force of certain points in the soil slope is obtained. According to the earth slope seismic stability analysis method, the problem that in the prior art, an earthquake, an soil slope structure and a power characteristic of the material cannot be considered at the same time in the soil slope stability analysis is solved.
Owner:XIAN UNIV OF TECH
Network security management method and terminal
InactiveCN106302519ASecurity securityDetermine securityData switching networksNetwork addressingThe Internet
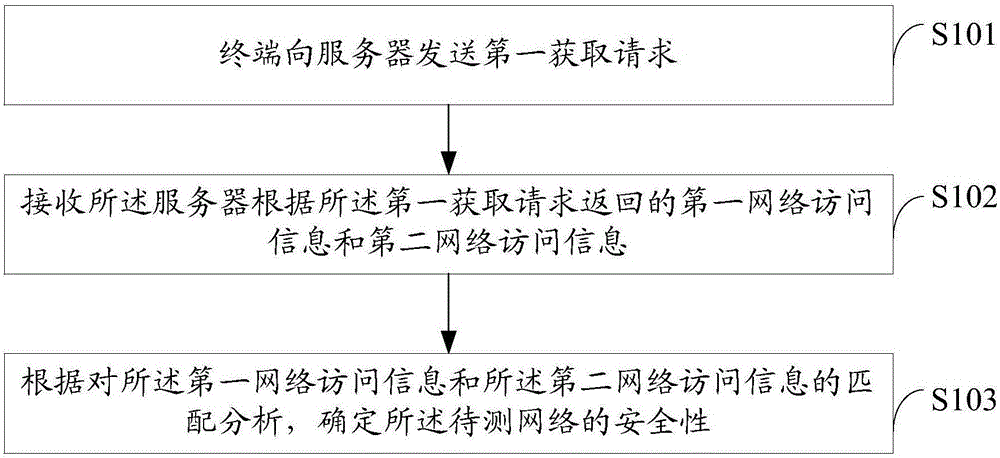
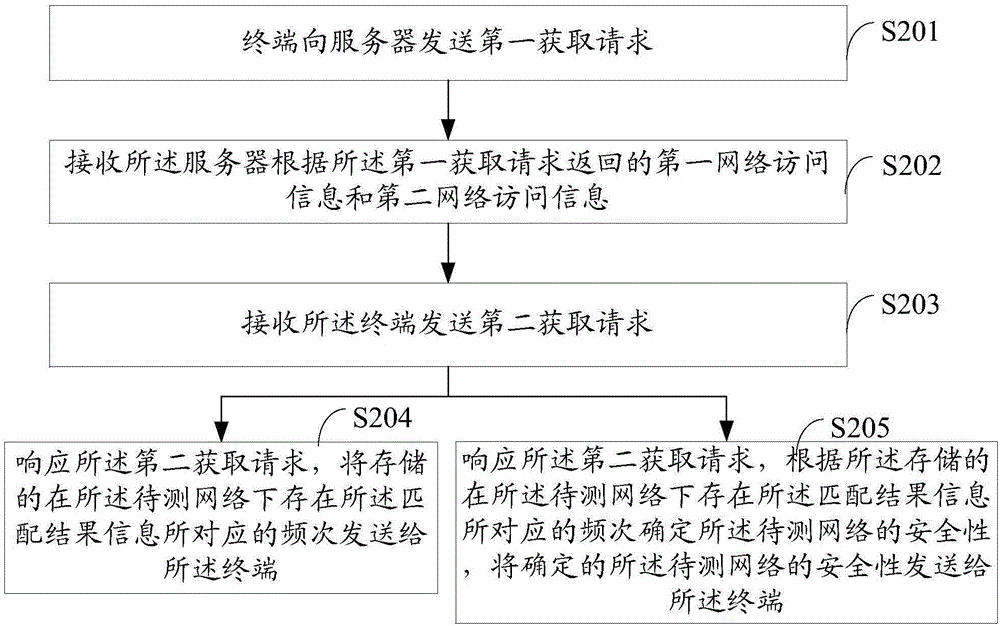
An embodiment of the present invention discloses a network security management method and terminal, wherein the method comprises: sending a first acquisition request to a server from the terminal; receiving the first network accessing information and the second network accessing information returned by the server according to the first acquisition request wherein the first network accessing information is network accessing information stored in the server and generated by the network accessing operation of the server under the network to be tested according to a preset network address and the second network accessing information is network accessing information stored in the server and generated by the network accessing operation of the server in a preset security network according to a preset network address, the internet accessing information including accessing scripts and accessing links; and matching and analyzing the first network accessing information and the second network accessing information to determine the security of the network to be tested. According to the embodiment of the invention, a user can choose to be connected with a security network according to his or her requirement, therefore, ensuring the security of accessing a network.
Owner:SHENZHEN GIONEE COMM EQUIP
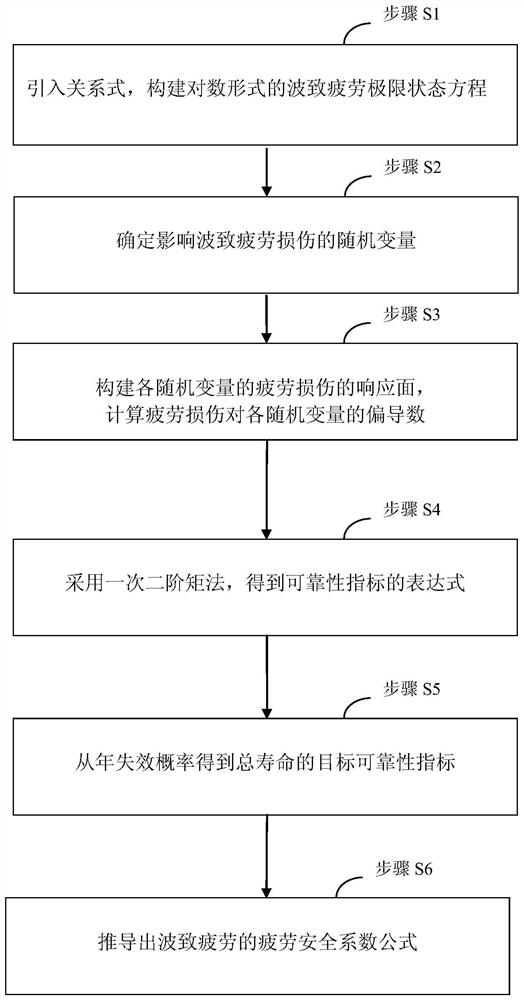
Method for determining wave-induced fatigue safety factor of marine riser based on reliability
ActiveCN108563846AEffectively determine safetyDetermine securityGeometric CADDesign optimisation/simulationFatigue damageSecond order moments
A method for determining the wave-induced fatigue safety factor of the marine riser based on reliability is provided. The method comprises: introducing a relational expression, and constructing the wave-induced fatigue limit state equation in logarithm; determining the random variables affecting the wave-induced fatigue damage; constructing a response surface of the fatigue damage of each random variable, and calculating the partial derivative of the fatigue damage to each random variable; using a second-order moment method to obtain an expression of the wave-induced fatigue reliability indexof the riser; obtaining a target reliability index of the total life of the riser from the annual failure probability; deriving a safety factor formula of the wave-induced fatigue; and giving a calculation flow and examples. The method provided by the present invention can be used to guide the design and evaluation of wave-induced fatigue strength of the marine riser.
Owner:ZHEJIANG UNIV OF TECH +1
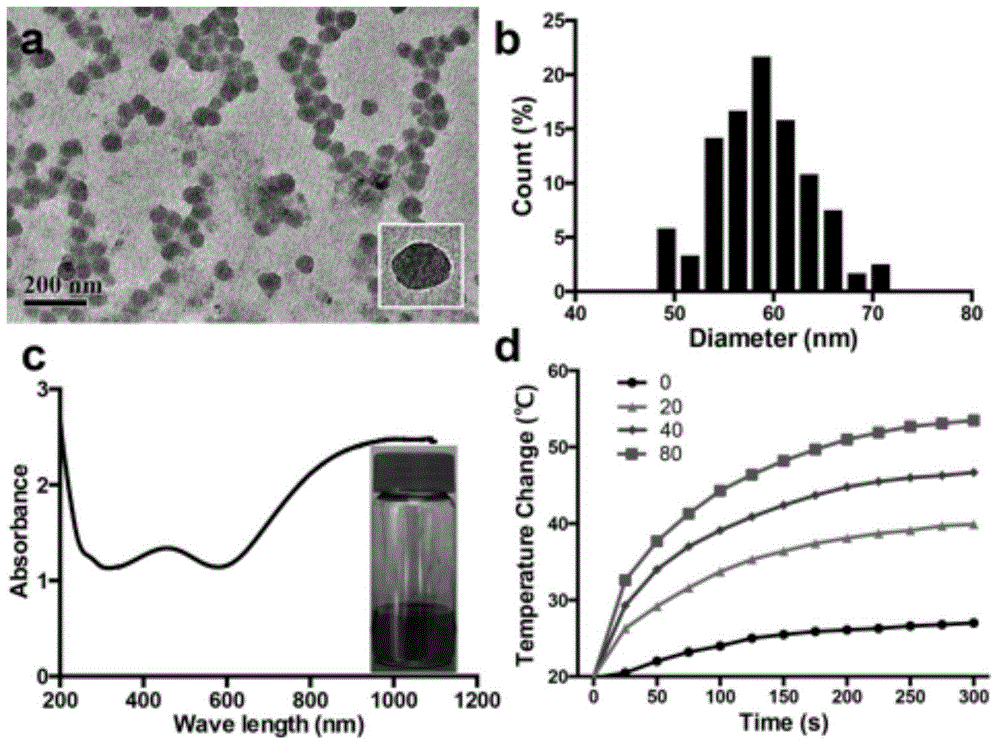
Polypyrrole nano particle having photo-thermal effect, preparation method and application thereof
InactiveCN105833269AGood light stabilityHigh photothermal conversion effectPowder deliveryEnergy modified materialsInfraredPercent Diameter Stenosis
The invention belongs to the crossing field of nano engineering and cell biology, and relates to a polypyrrole nano particle having a photo-thermal effect, a preparation method and an application thereof. The nano particle generates heat under irradiation of near infrared ray and can be used for preparing a medicine preparation for treating hemadostenosis caused by inflammatory reaction in blood vessel and vascular smooth muscle cell proliferation. In the invention, on the basis of killing effects on chronic inflammatory cells in vitro with photo-thermal therapy of the nano particle and near infrared laser, an application test of mouse vascular chronic inflammation and in an arteriostenosis model is carried out further, and a result proves that the nano particle can locally enter the focus of the chronic inflammation in artery, and can be used for inhibiting the local chronic inflammation with near infrared ray local irradiation, thereby inhibiting restenosis after intracavitary therapy and being used for evaluating the restenosis after intracavitary therapy through MRI.
Owner:SHANGHAI NINTH PEOPLES HOSPITAL AFFILIATED TO SHANGHAI JIAO TONG UNIV SCHOOL OF MEDICINE
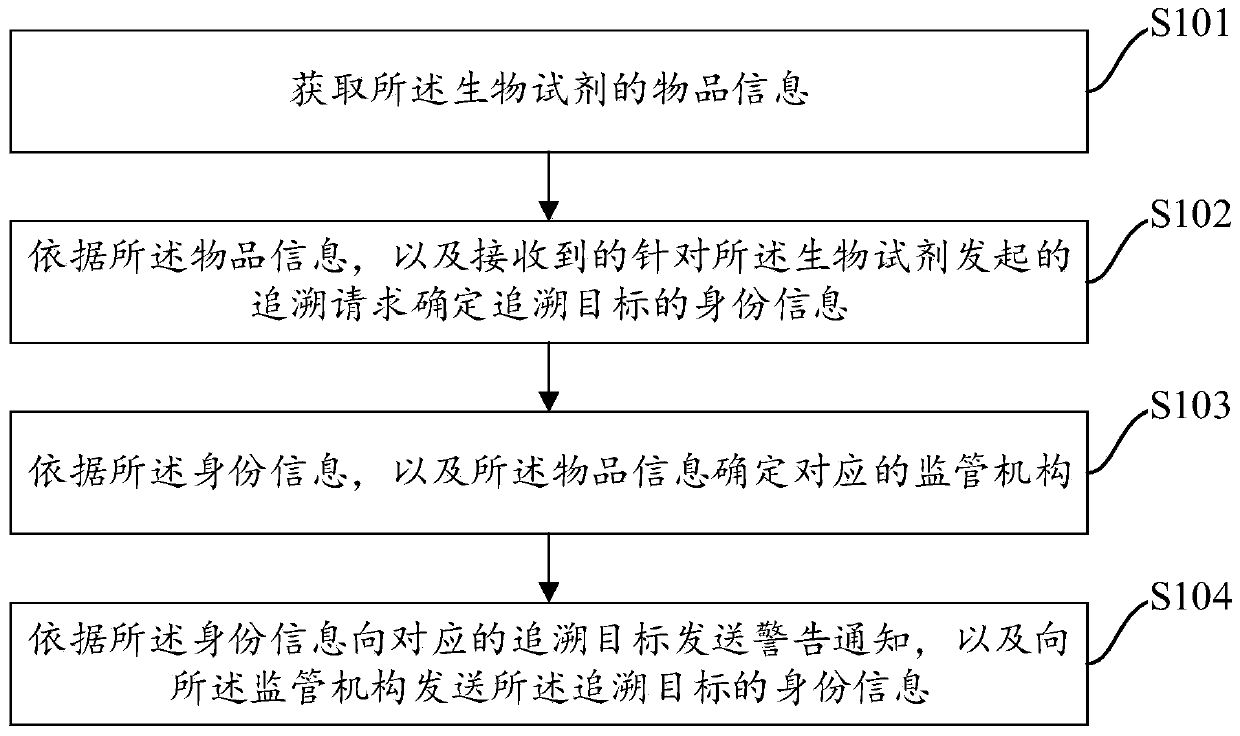
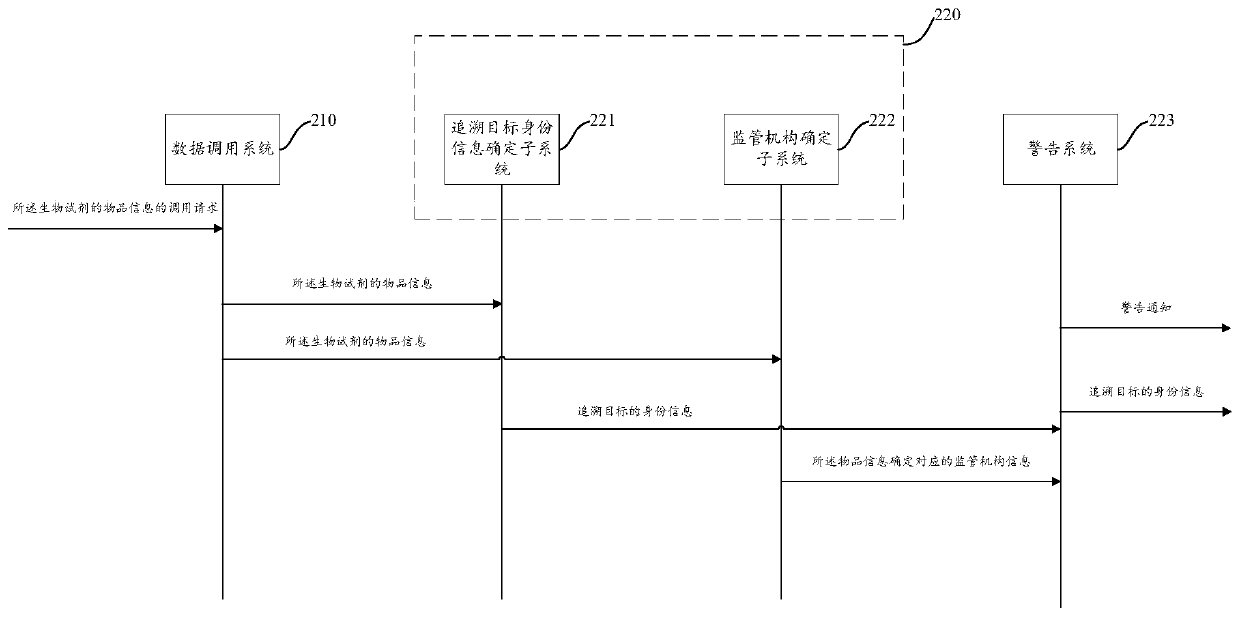
Management method, system, equipment for entry and exit biological reagents of border port, and medium
The invention provides a management method, system and equipment for an entry and exit biological reagent of a border port and a medium, the system is applied to tracing of the entry and exit biological reagent, and under the condition that the biological reagent is traced, the method comprises the following steps: obtaining article information of the biological reagent; determining identity information of a tracing target according to the article information and a received tracing request initiated for the biological reagent; determining a corresponding supervision mechanism according to theidentity information and the article information; and sending a warning notification to a corresponding tracing target according to the identity information, and sending the identity information of the tracing target to the supervision institution. The method can well determine the overseas calendar or source of the scientific research biological reagent and the safety and quality of the scientific research biological reagent, and fully meets the requirements of customers.
Owner:SHENZHEN ACAD OF INSPECTION & QUARANTINE
Cloud native application health detection method and device, computer equipment and storage medium
PendingCN114153696AGuaranteed accuracyDetermine securityHardware monitoringNon-redundant fault processingDynamic dataReal-time computing
The invention discloses a cloud native application health detection method and device, computer equipment and a storage medium. The method comprises the following steps: acquiring a cloud native application, and determining at least one application component from the cloud native application; performing static data analysis on each application component to obtain a static analysis result corresponding to each application component; performing dynamic data analysis on each application component to obtain a dynamic analysis result corresponding to each application component; and obtaining a health detection result corresponding to the cloud native application according to the static analysis result and the dynamic analysis result corresponding to the at least one application component. According to the method, the accuracy of the health detection result corresponding to the cloud native application can be guaranteed, and the security of the cloud native application can be determined according to the health detection result.
Owner:招商局金融科技有限公司
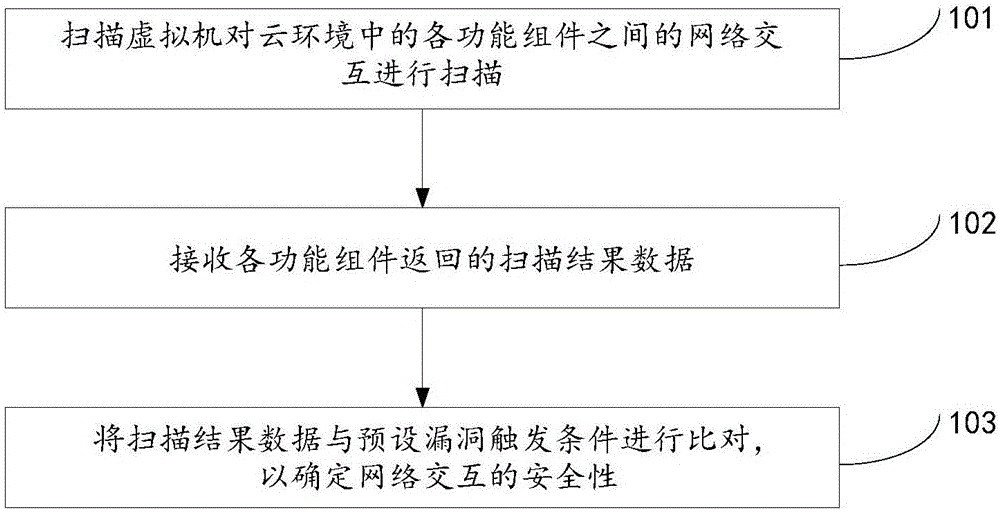
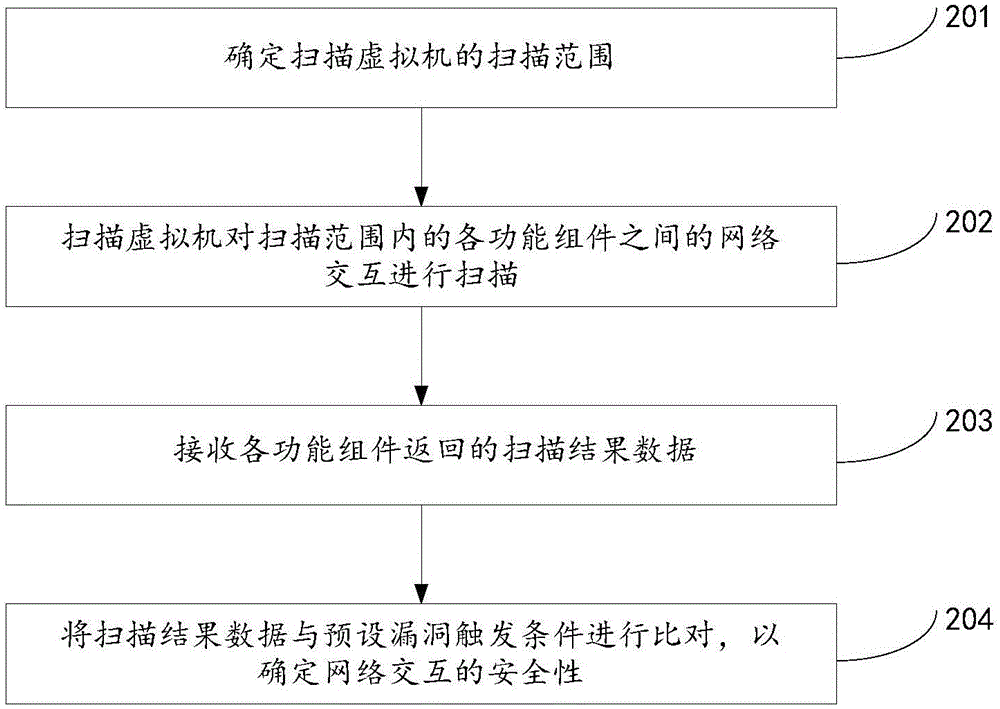
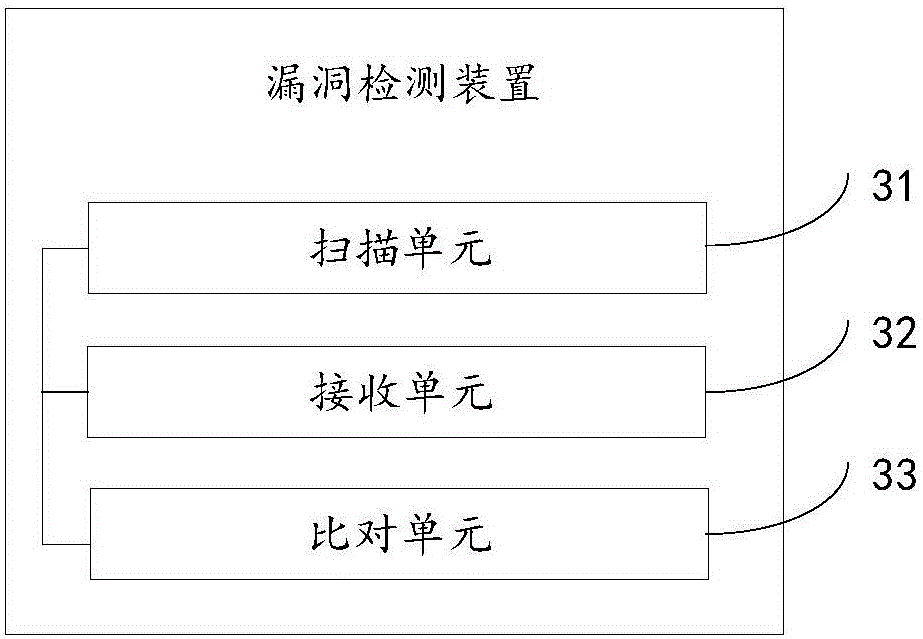
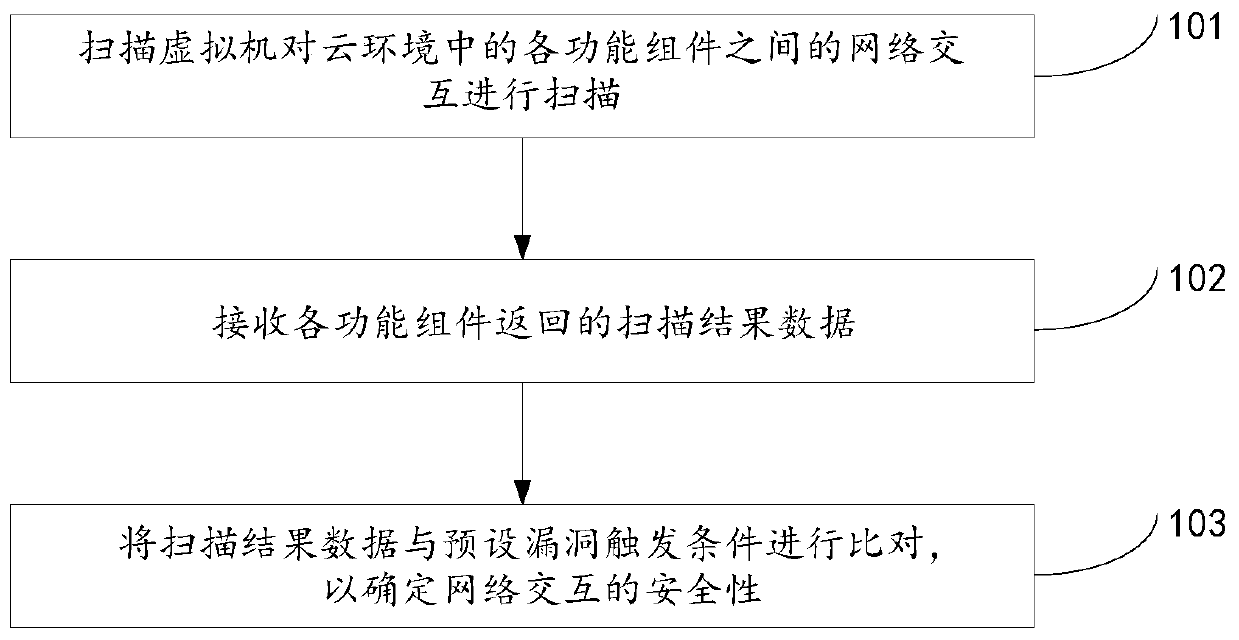
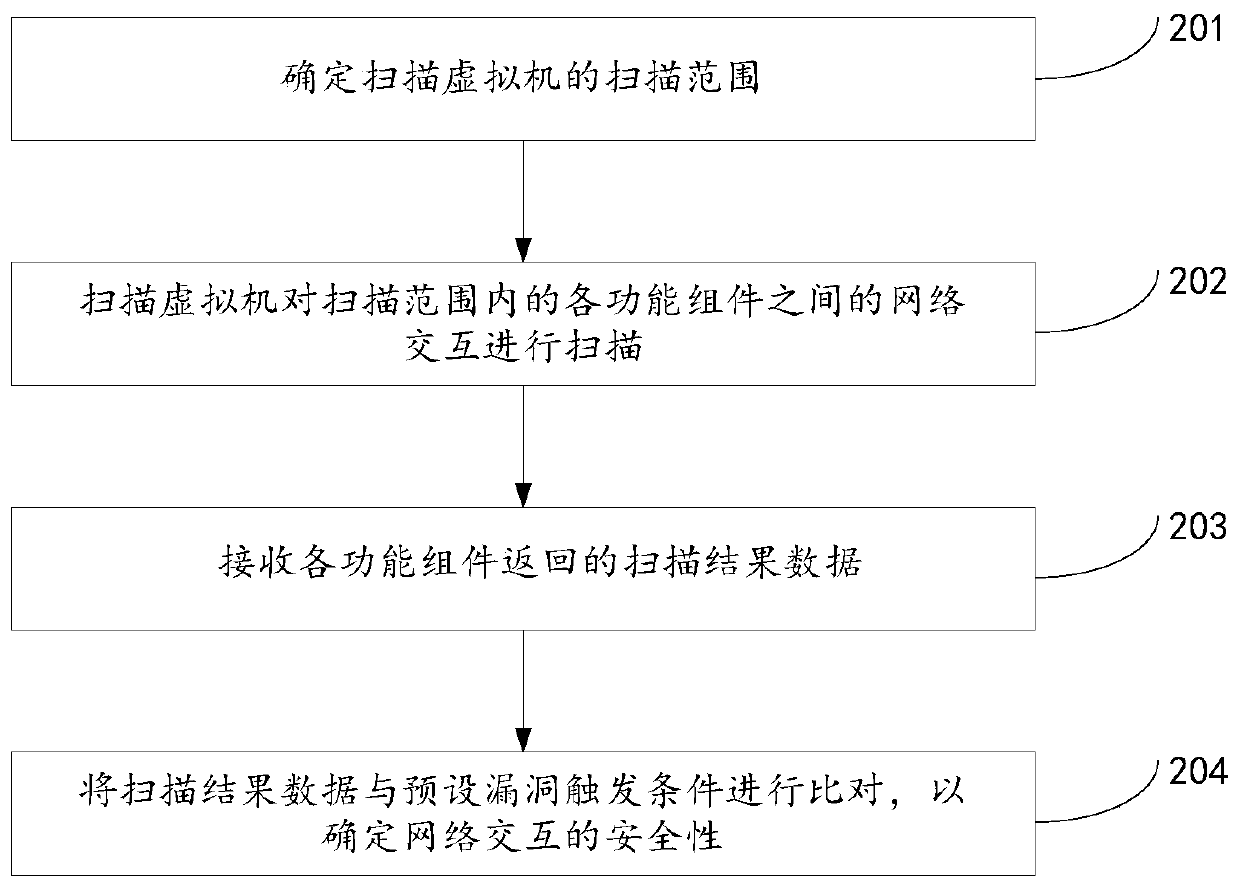
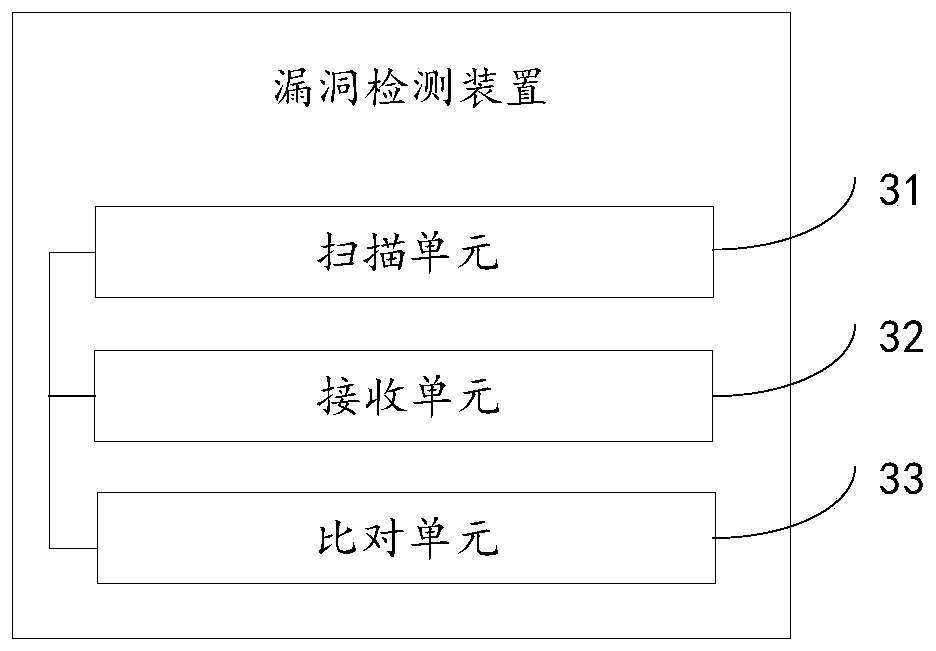
Vulnerability detection method and device
ActiveCN106357664ADetermine securityMeet the needs of vulnerability scanningTransmissionVulnerability detectionVulnerability scanning
The invention discloses a vulnerability detection method and device, which relate to the technical field of internet, and are invented for solving the problem that an existing vulnerability scanning method cannot meet the scanning requirement under a cloud environment. The method provided by the invention comprises the steps of scanning network interaction between each two functional units in the cloud environment through a scanning virtual machine, wherein the scanning virtual machine is located in the cloud environment; receiving scanning result data returned by each functional unit; comparing the scanning result data with a preset vulnerability triggering condition and determining the safety of the network interaction. The vulnerability detection method and device provided by the invention are applied in a process of performing vulnerability scanning on the network interaction between the different functional units in the cloud environment.
Owner:BEIJING QIHOO TECH CO LTD +1
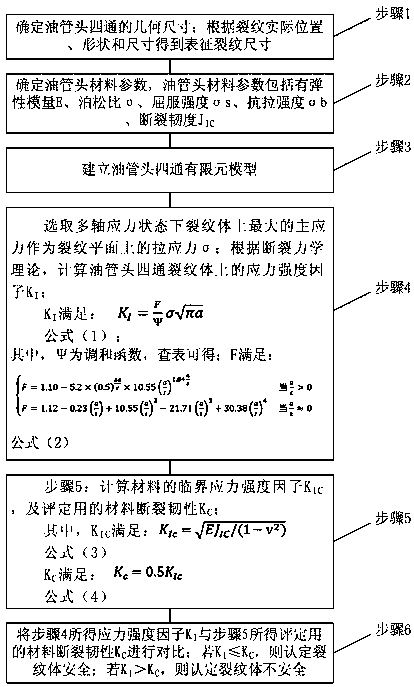
Safety evaluation method for well head tubing head spool with crack defect
InactiveCN108362487AAccurate stress distributionAccurate Simulation CalculationsGeometric CADMachine part testingStress distributionElement model
The invention belongs to the technical field of safety evaluation of well head device structural members with the defects, and especially relates to a safety evaluation method for a well head tubing head spool with a crack defect. The method improves the matching degree of a stress distribution finite element simulation calculation value of the tubing head spool with the actual member stress distribution through the impact on the stress distribution of the tubing head spool from constraint conditions generated by different assembly modes, and can achieve the more accurate safety evaluation ofthe of the tubing head spool with the crack defect. The method comprises the steps: determining the physical dimension of the tubing head spool, and calculating and obtaining a representative crack size; determining the parameters of a tubing head material; building a tubing head spool finite element model; calculating a stress strength factor KI of a crack body of the tubing head spool; calculating a critical stress strength factor KIC of the material and a material crack toughness KC for evaluation; comparing the stress strength factor KI with the material crack toughness KC for evaluation,and determining the safety performances of the crack body.
Owner:CHINA PETROLEUM & CHEM CORP +1
Method for computing voltage sensitivity of automatic voltage control system
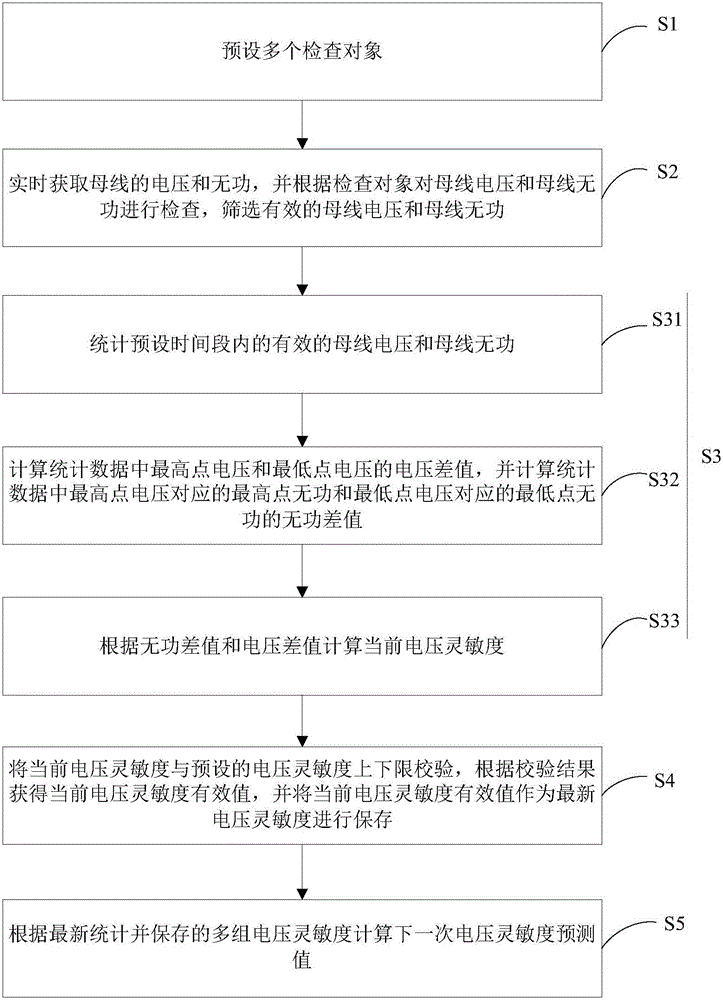
ActiveCN106602572ATrends in line withHigh speedAc network voltage adjustmentReactive power compensationAutomatic controlControl system
The invention discloses a method for computing the voltage sensitivity of an automatic voltage control system. The method, by setting examination items, screens the acquired data, strictly examines data used during the computing, is conducive to guaranteeing the quality of the acquired data, effectively prevents bad data from influencing the result of the computing, and increases the precision in computing current voltage sensitivity. According to the invention, when computing the prediction value of the voltage sensitivity, the method uses an algorithm similar to weighted average, by collecting statistics from historical record of voltage sensitivity and the changing trend of numerical values, to compute the actual voltage sensitivity which best conforms to next adjustment, such that the computed prediction value of the voltage sensitivity more conforms to the changing trend of a power grid within a short time period in the future, can effectively increase the speed and precision of actual adjustment of the automatic voltage control system and also increases the percent of pass of the adjustment.
Owner:LEADZONE SMART GRID TECH
Network security management method and terminal
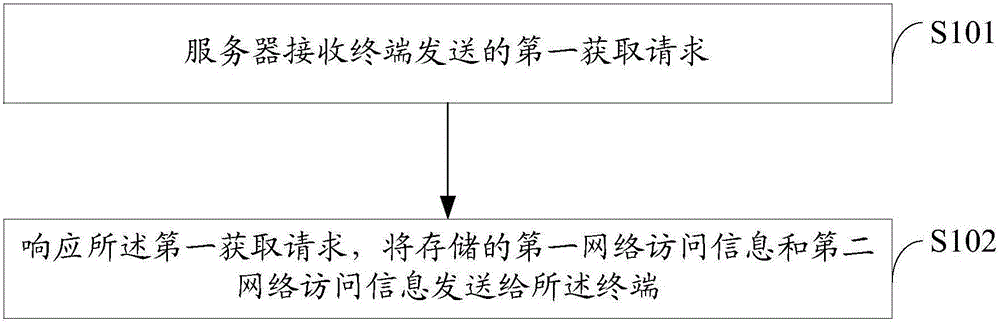
InactiveCN106411862ADetermine securitySafety derived/determinedData switching networksThe InternetNetwork addressing
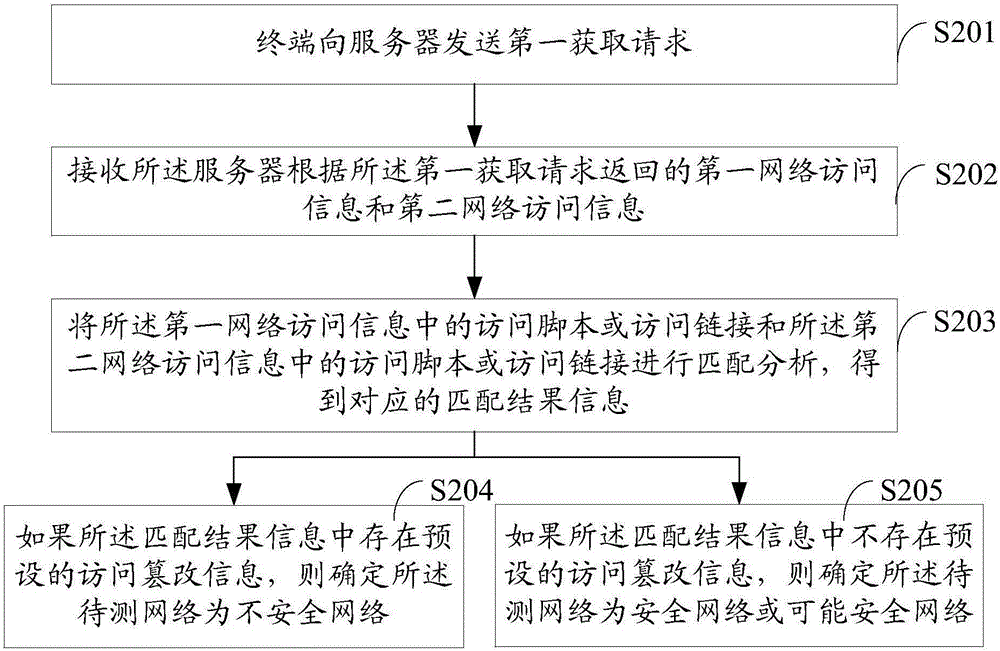
The embodiment of the invention discloses a network security management method and a terminal. The method comprises the following steps: receiving a first acquisition request sent by the terminal through a server; and transmitting stored first network access information and second network access information to the terminal in response to the first acquisition request, wherein the first network access information refers to network access information which is stored in the server and generated by a network access operation performed according to a preset network address under a network to be tested, the second network access information refers to network access information which is stored in the server and generated by a network access operation performed according to a preset network address under a preset secure network, and the network access information includes access scripts or access links. Through adoption of the network security management method, the terminal can be independently and selectively connected to the secure network according to the demand of a user, and the Internet-surfing security is ensured for the user.
Owner:SHENZHEN GIONEE COMM EQUIP
A test method for wind pressure resistance performance of film-coated glass
InactiveCN104198309BDetermine securitySecurity responseMaterial strength using repeated/pulsating forcesDesign standardGlass cutter
A test method for wind pressure resistance performance of filmed glass, the steps are as follows: Step 1, confirm that the curtain wall test piece meets the design requirements; Hit the central part of the glass, semi-tempered or ordinary glass should be scratched with a glass knife in the middle of the glass, the crack length should not be less than 200mm; step 3, repeated pressure testing, the test pressure difference is averaged at 0.4 times the design wind load standard value Value, with 1 / 4 of the average value as the amplitude, carry out positive and negative pressure fluctuation detection, the fluctuation pressure cycle is 5s ~ 7s, and the number of fluctuations is not less than 10 times. This method is a test method for evaluating the wind pressure resistance performance of filmed glass after it is broken. It clearly puts forward the concept and test method of the residual wind pressure resistance strength of filmed glass after it is broken, which is beneficial to the safety performance of filmed glass after it is broken. Quantitative evaluation.
Owner:CHINA ACAD OF BUILDING RES
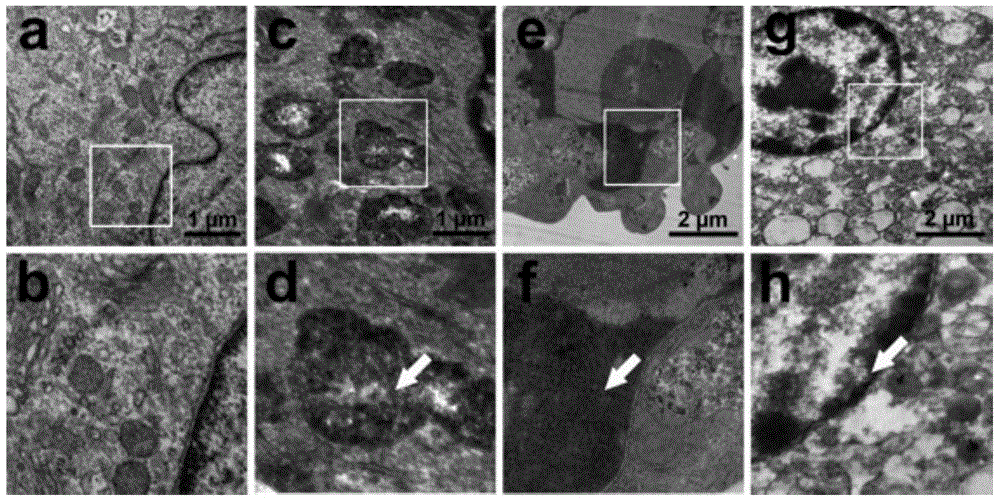
Construction and application of transgenic mouse model for exosome tracing
PendingCN114686518ADetermine securityHydrolasesGenetically modified cellsTransgenesisMolecular biology
The invention discloses a construction method and application of a transgenic mouse model for exosome tracing. The specific implementation process mainly comprises the following steps: constructing plasmids for expressing stop-EGFP-tracrRNA and expressing crRNA or sgRNA; construction of donor cells and verification of exosomes; constructing, breeding and identifying transgenic mice; the five parts are verified by the tracing exosome transgenic mouse model, and finally the transgenic mouse model for tracing the exosome is successfully obtained; the successful construction of the model lays a foundation for the research of the exosome as a gene drug carrier, and scientists can more easily and clearly observe the distribution of the exosome in vivo under pathological or physiological conditions.
Owner:NANJING UNIV
Multifunctional rear view mirror for motorcycle
InactiveCN105438342AFunction increaseNot easy to loseCycle mirrorsCycle containersComputer scienceRear-view mirror
The invention provides a multifunctional rear view mirror for a motorcycle, comprising a support rod, a rear-mounted box I, a rear-mounted box II, a second mirror frame, a first mirror face, a second mirror face and a first mirror frame, wherein the rear-mounted box I is mounted at the right side of the support rod; the first mirror frame is mounted in front of the rear-mounted box I; the first mirror face is mounted in the first mirror frame; an mounting groove is arranged at the joint between the first mirror frame and the rear-mounted box I; the second mirror frame is mounted in the mounting groove by a bolt; the second mirror face is mounted in the second mirror frame; and the rear-mounted box II is mounted behind the second mirror frame. Compared with the prior art, the multifunctional rear view mirror provided by the invention has the beneficial effects that an article storing part for placing articles is additionally arranged on the rear view mirror so as to be convenient for a driver to carry about the articles, and the articles cannot be lost easily; and by additionally arranging the second mirror face, the visual field of the rear view mirror is widened. The multifunctional rear view mirror provided by the invention is simple in structure and convenient to use; and the rear-mounted box I can be locked by connecting a lock body and a lock catch, so that the article storing safety can be further ensured.
Owner:CHONGQING YONGCHUAN DISTRICT BANGWEI MACHINERY MFG CO LTD
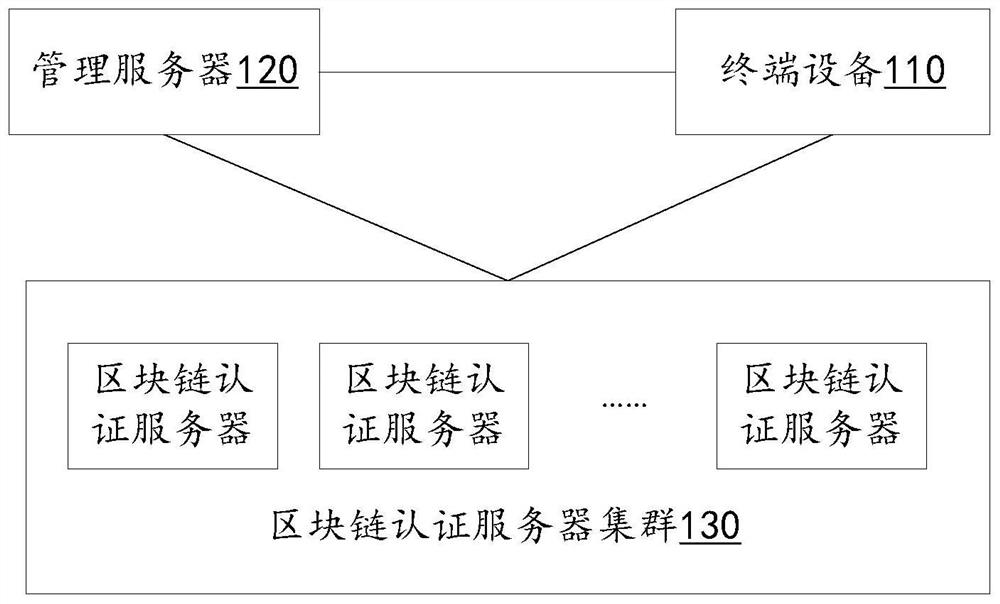
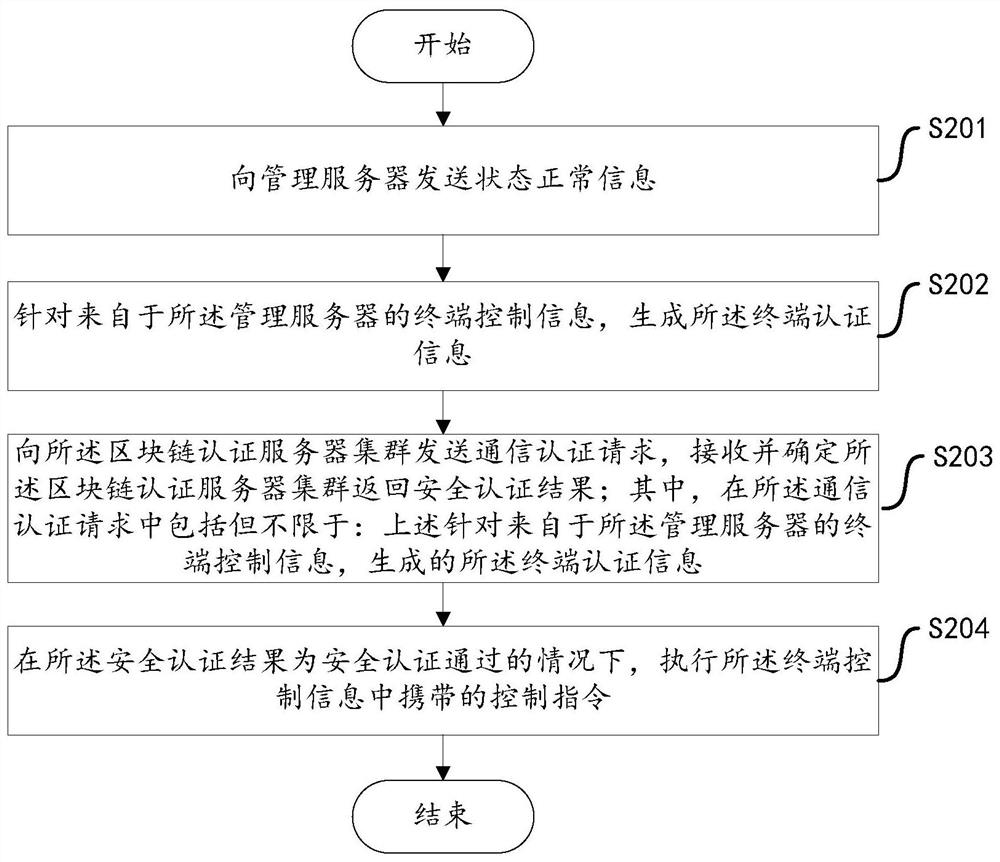
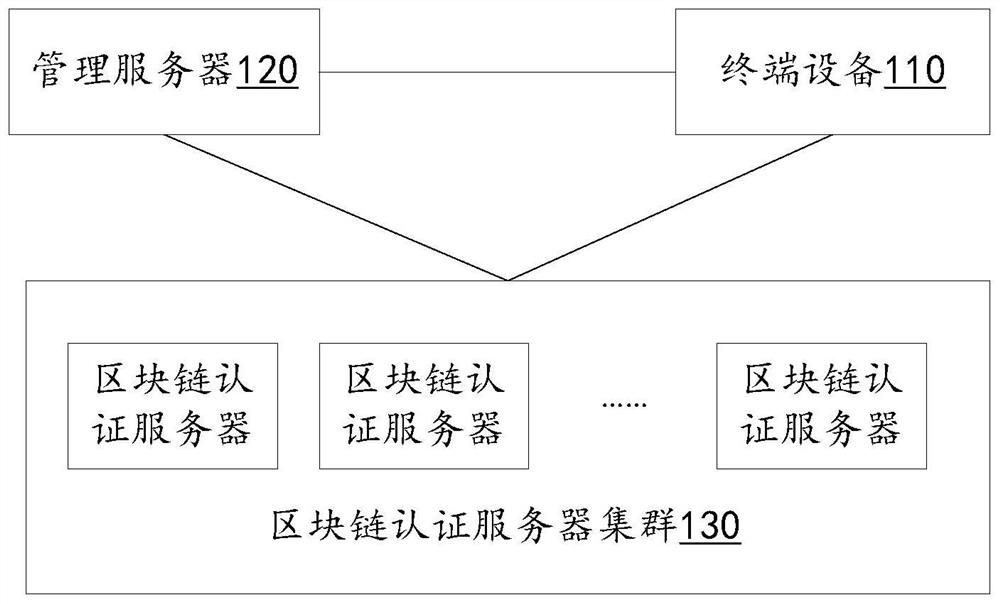
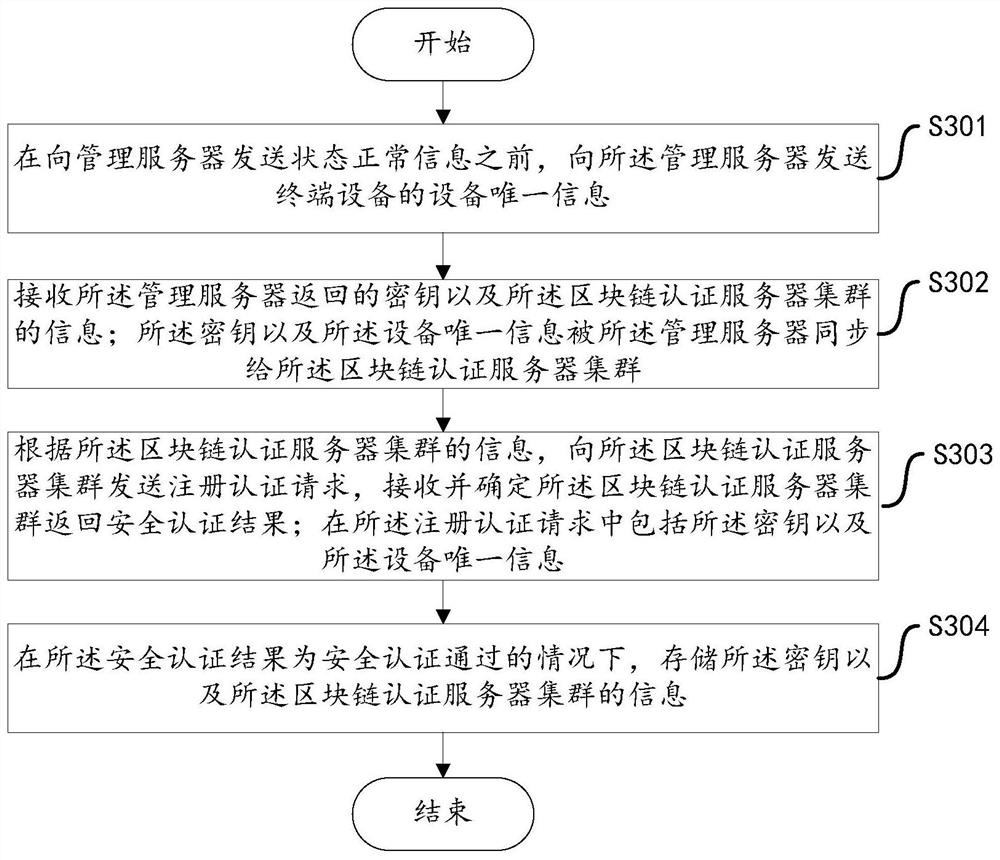
Security authentication system, method, apparatus, device, and computer-readable storage medium
The invention discloses a safety authentication system, method, device, equipment and computer-readable storage medium. The method includes: the terminal device sends normal state information to the management server; the management server generates terminal control information and terminal authentication information; the terminal device generates terminal authentication information according to the terminal control information; sends a communication authentication request to the block chain authentication server cluster, receives And determine that the block chain authentication server cluster returns the security authentication result; the communication authentication request includes terminal authentication information; the block chain authentication server cluster performs security on the terminal authentication information included in the communication authentication request according to the terminal authentication information from the management server. Authentication, returning the security authentication result to the terminal device; when the security authentication result is that the security authentication is passed, the terminal device executes the control instruction carried in the terminal control information. The invention can determine the security of the transmission link between the terminal equipment and the management server.
Owner:GREE ELECTRIC APPLIANCES INC +1
A reliability-based method for determining the wave-induced fatigue safety factor of marine risers
ActiveCN108563846BEffectively determine safetyDetermine securityGeometric CADDesign optimisation/simulationFatigue damageFatigue Intensity
A reliability-based method for determining the wave-induced fatigue safety factor of marine risers. The relational expression is introduced to construct the wave-induced fatigue limit state equation in logarithmic form; the random variables affecting the wave-induced fatigue damage are determined; the fatigue of each random variable is constructed. The partial derivative of fatigue damage to each random variable is calculated based on the response surface of the damage; the first order second moment method is used to obtain the expression of the reliability index of the riser wave-induced fatigue; the target reliability index of the total life of the riser is obtained from the annual failure probability ;Finally deduce the safety factor formula of wave-induced fatigue; give the calculation process and examples. The present invention can be used to guide the design and evaluation of marine riser wave-induced fatigue strength.
Owner:ZHEJIANG UNIV OF TECH +1
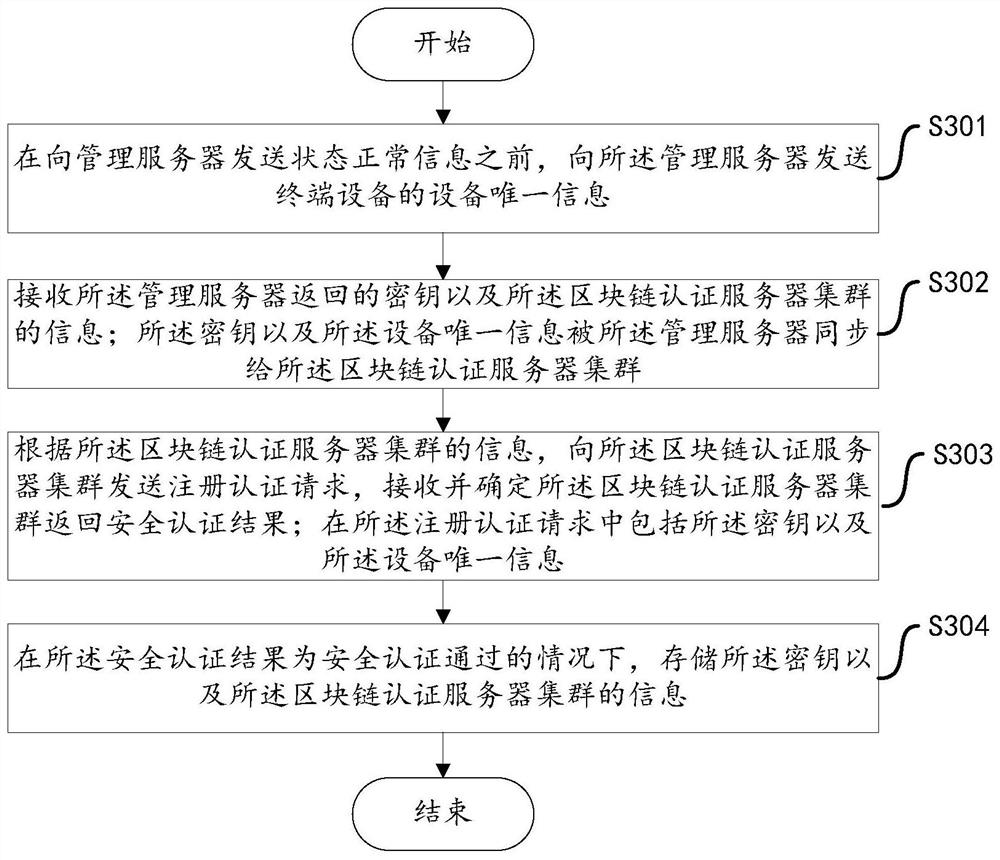
Safety authentication system, method, device, equipment and computer readable storage medium
The invention discloses a safety authentication system, a method, a device, equipment and a computer readable storage medium. The method comprises the steps that terminal equipment sends state normal information to a management server; the management server generates terminal control information and terminal authentication information; the terminal equipment generates terminal authentication information for the terminal control information; a communication authentication request is sent to the blockchain authentication server cluster, and a safety authentication result returned by the blockchain authentication server cluster isreceived and determined; the communication authentication request comprises terminal authentication information; the block chain authentication server cluster performs safety authentication on the terminal authentication information included in the communication authentication request according to the terminal authentication information from the management server, and returns a safety authentication result to the terminal equipment; and the terminal equipment executes the control instruction carried in the terminal control information when the safety authentication result is that the safety authentication is passed. According to the invention, the safety of the transmission link between the terminal equipment and the management server can be determined.
Owner:GREE ELECTRIC APPLIANCES INC +1
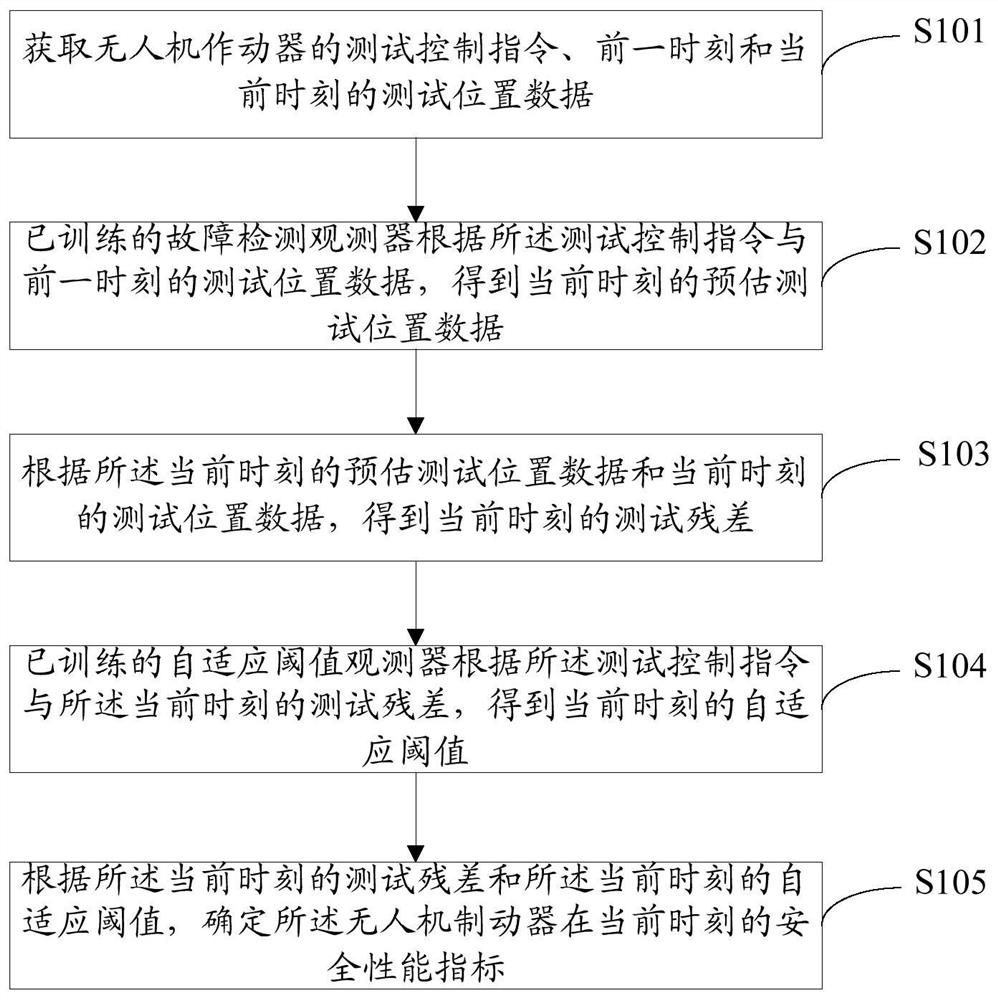
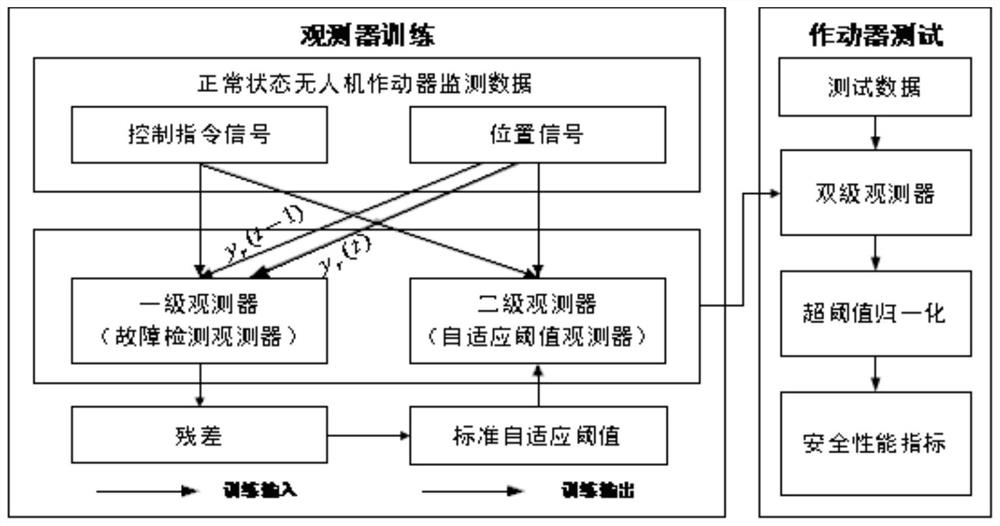
Unmanned aerial vehicle actuator real-time safety performance evaluation method based on two-stage observer
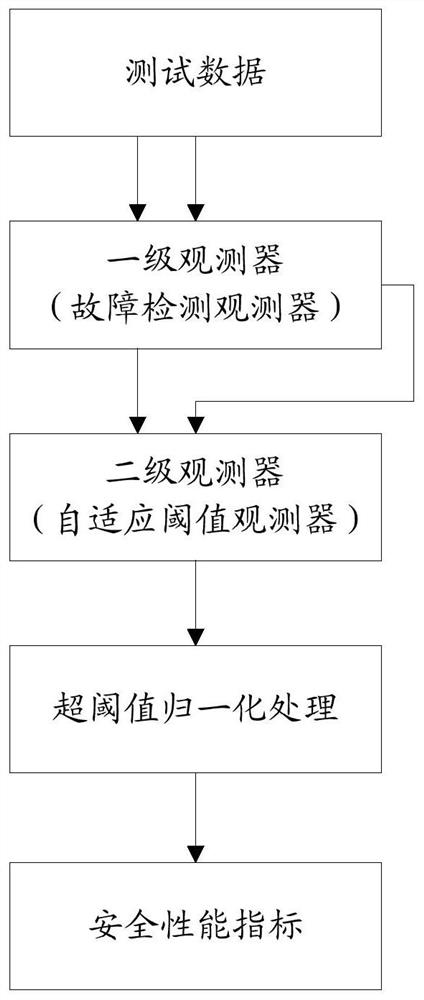
PendingCN111680356AAddress riskSolve the problem of early warning and control capabilitiesGeometric CADDesign optimisation/simulationSimulationUncrewed vehicle
The invention discloses an unmanned aerial vehicle actuator real-time safety performance evaluation method based on a two-stage observer, and relates to the field of unmanned aerial vehicles, and themethod comprises the steps: obtaining a test control instruction of an unmanned aerial vehicle actuator and test position data of a previous moment and a current moment; enabling the trained fault detection observer to obtain estimated test position data at the current moment according to the test control instruction and the test position data at the previous moment; obtaining a test residual error at the current moment according to the estimated test position data at the current moment and the test position data at the current moment; enabling a trained adaptive threshold observer to obtain an adaptive threshold at the current moment according to the test control instruction and the test residual error at the current moment; and determining the safety performance index of the unmanned aerial vehicle brake at the current moment according to the test residual error at the current moment and the self-adaptive threshold value at the current moment.
Owner:BEIHANG UNIV
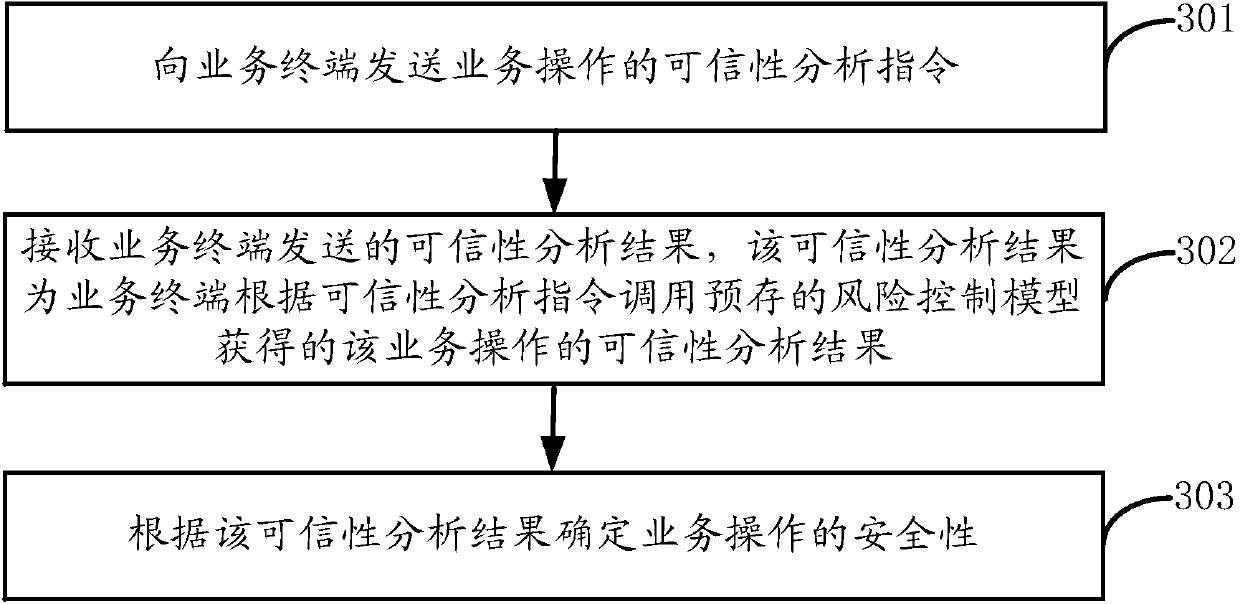
Method, device, terminal and server for verifying business operation security
ActiveCN105516071BDetermine securityTrue reflection of social relationshipsUser identity/authority verificationComputer security arrangementsRisk ControlOperation safety
This application discloses a method, device, terminal and server for verifying the security of business operations. The method includes: receiving a business operation credibility analysis command sent by the business server; calling a pre-stored risk control model according to the credibility analysis command to obtain The credibility analysis result of the business operation; sending the credibility analysis result to the business server, so that the business server can determine the security of the business operation according to the credibility analysis result. By applying the embodiment of the present application, the internal risk control model of the service terminal can be used to obtain the reliability analysis result of the service operation, thereby improving the accuracy of the security verification of the service operation.
Owner:ADVANCED NEW TECH CO LTD
Vulnerability detection method and device
ActiveCN106357664BDetermine securityMeet the needs of vulnerability scanningTransmissionThe InternetEngineering
The invention discloses a vulnerability detection method and device, which relate to the technical field of internet, and are invented for solving the problem that an existing vulnerability scanning method cannot meet the scanning requirement under a cloud environment. The method provided by the invention comprises the steps of scanning network interaction between each two functional units in the cloud environment through a scanning virtual machine, wherein the scanning virtual machine is located in the cloud environment; receiving scanning result data returned by each functional unit; comparing the scanning result data with a preset vulnerability triggering condition and determining the safety of the network interaction. The vulnerability detection method and device provided by the invention are applied in a process of performing vulnerability scanning on the network interaction between the different functional units in the cloud environment.
Owner:BEIJING QIHOO TECH CO LTD +1
Method, server and system for detecting security of file samples
Owner:BEIJING QIHOO TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com