Method and system for detecting request safety
A technology for detecting requests and security, applied in the field of network security, can solve problems such as illegal intrusion, server security cannot be well guaranteed, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0025] In order to be able to effectively detect the security of the response request to the application server, an embodiment of the present invention provides a method for detecting the security of the request. The security of the current response request.
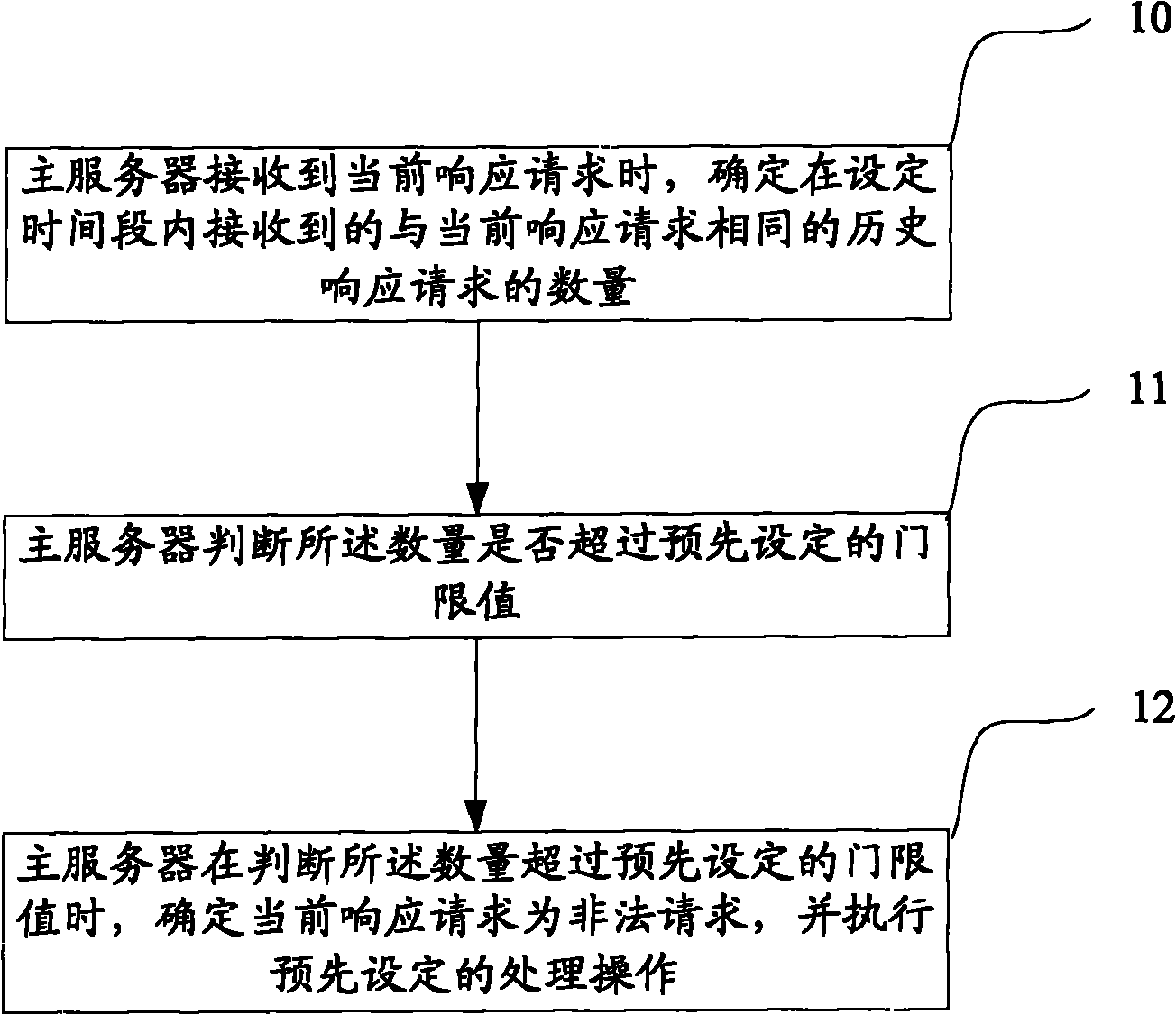
[0026] see figure 1 , the detection request security provided by the embodiment of the present invention includes:
[0027] Step 10: When the main server receives the current response request, determine the number of historical response requests received within the set time period that are the same as the current response request;
[0028] Step 11: The master server judges whether the quantity exceeds a preset threshold;
[0029] Step 12: When the master server judges that the number exceeds the preset threshold value, it determines that the current response request is an illegal request, and executes a preset processing operation.
[0030] In step 10, the historical response request identical to the current response ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com