Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
81results about How to "Avoid the risk of theft" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
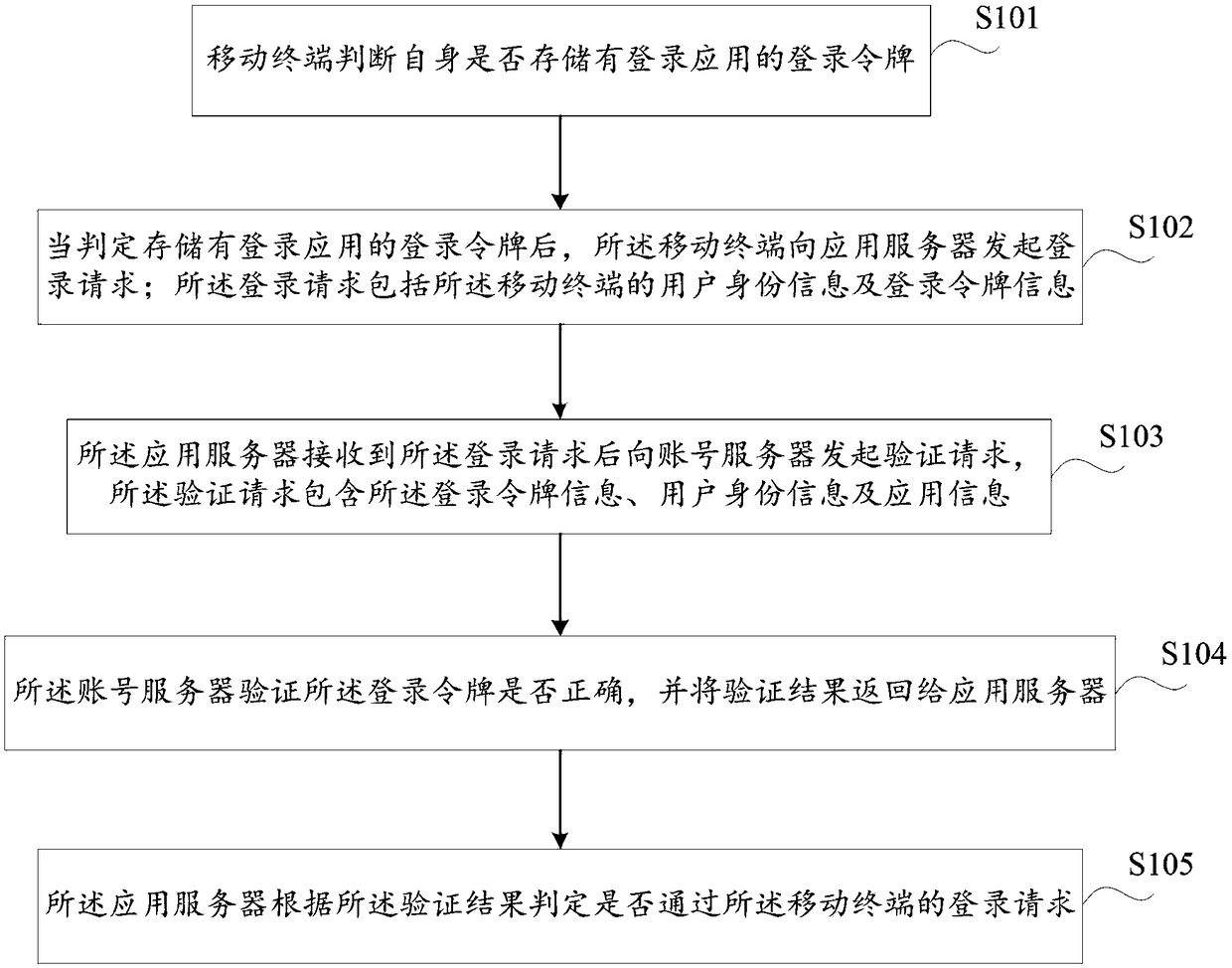
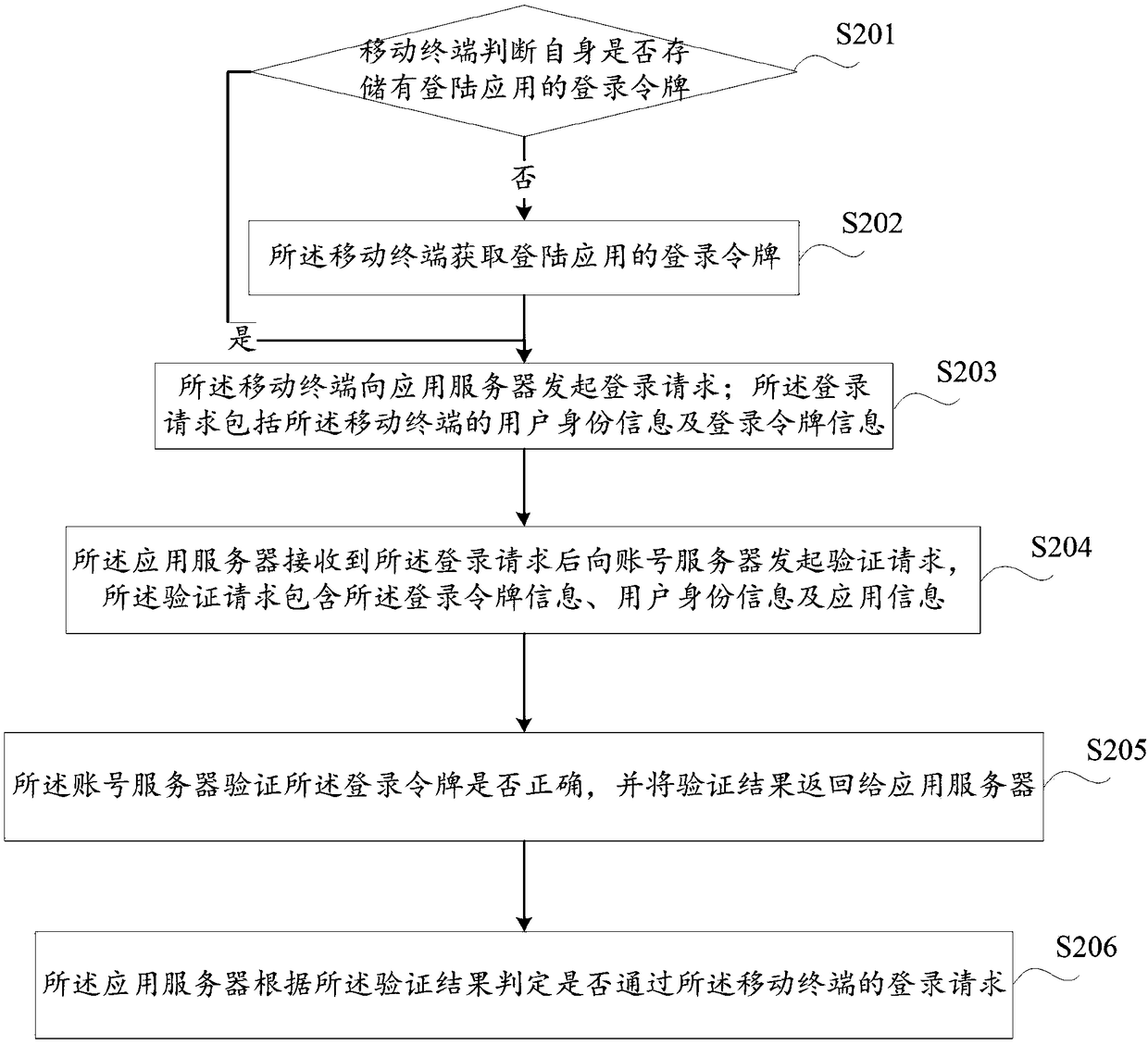
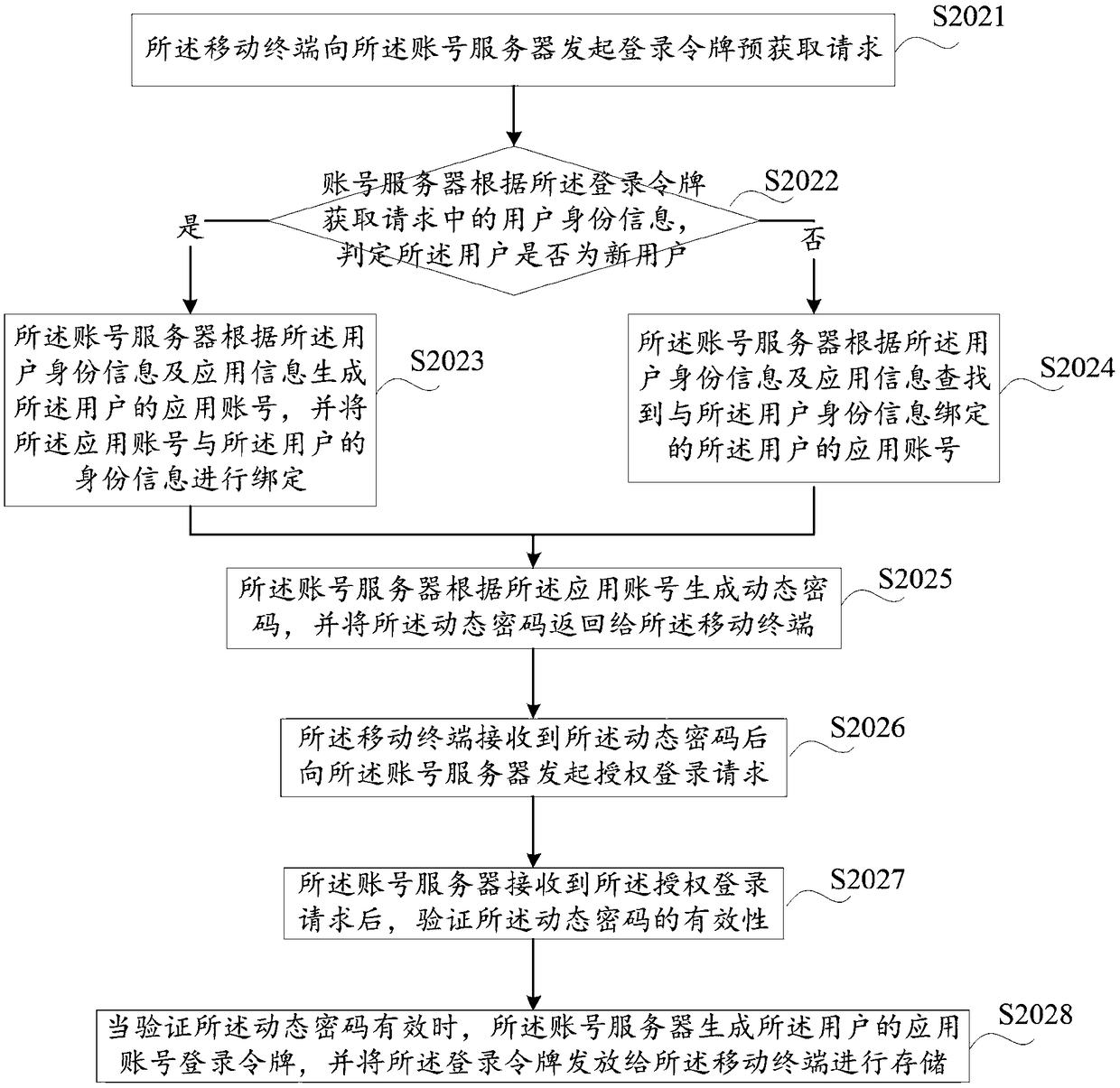
A method and a system of mobile terminal secret-free login
InactiveCN109089264AImprove login experienceImprove conversion rateDigital data authenticationTransmissionApplication serverInternet privacy
The invention discloses a method for a mobile terminal to log in free of secret, which comprises the following steps: the mobile terminal judges whether the mobile terminal stores a login token of thelogin application; when it is judged that the login token of the login application is stored, the mobile terminal initiates a login request to the application server; the login request includes useridentity information and login token information of the mobile terminal. After receiving the login request, the application server sends an authentication request to the account server. The authentication request includes login token information, user identity information and application information. The account server verifies whether the login token is correct and returns the verification resultto the application server. The application server determines whether the login request passes through the mobile terminal according to the verification result. The invention avoids the user from inputting account number and password through one key login, thereby improving the user login experience and the user conversion rate, and making the user far away from the risk that the account number password is stolen.
Owner:JIANGSU MANYUN SOFTWARE TECH CO LTD
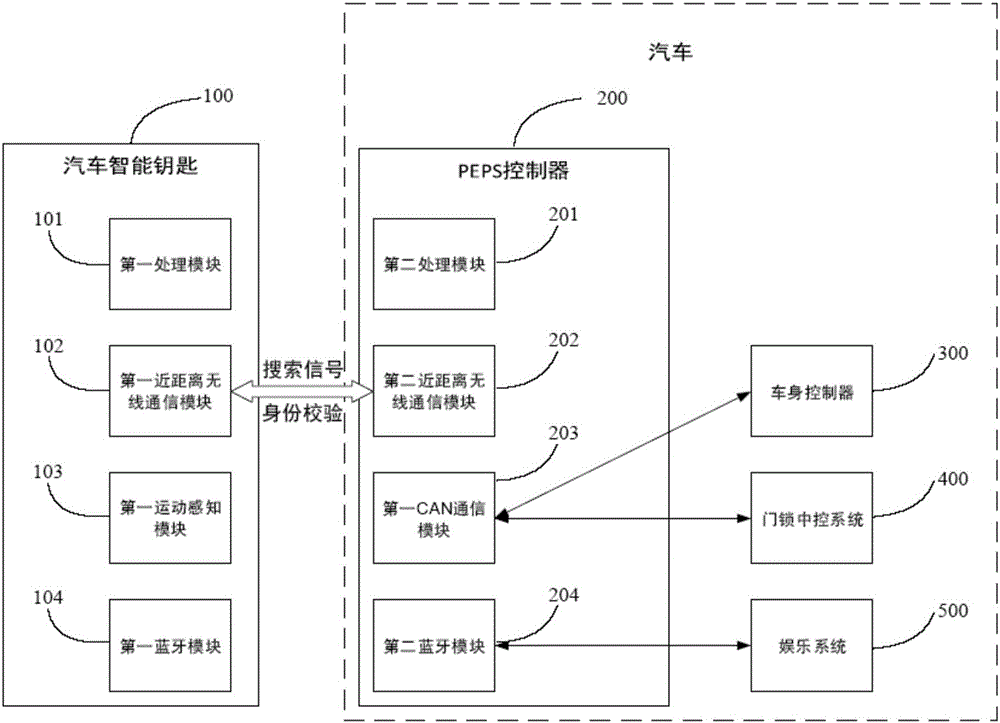
Keyless control system of automobile
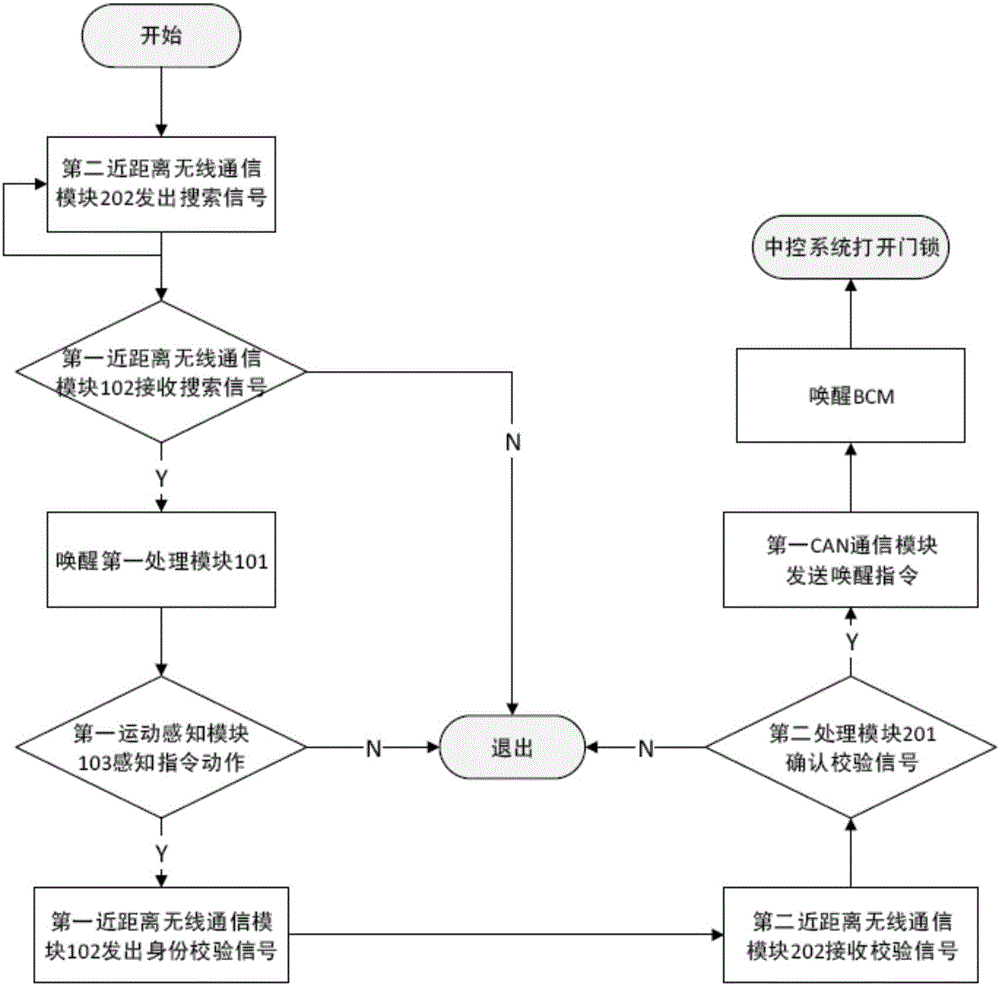
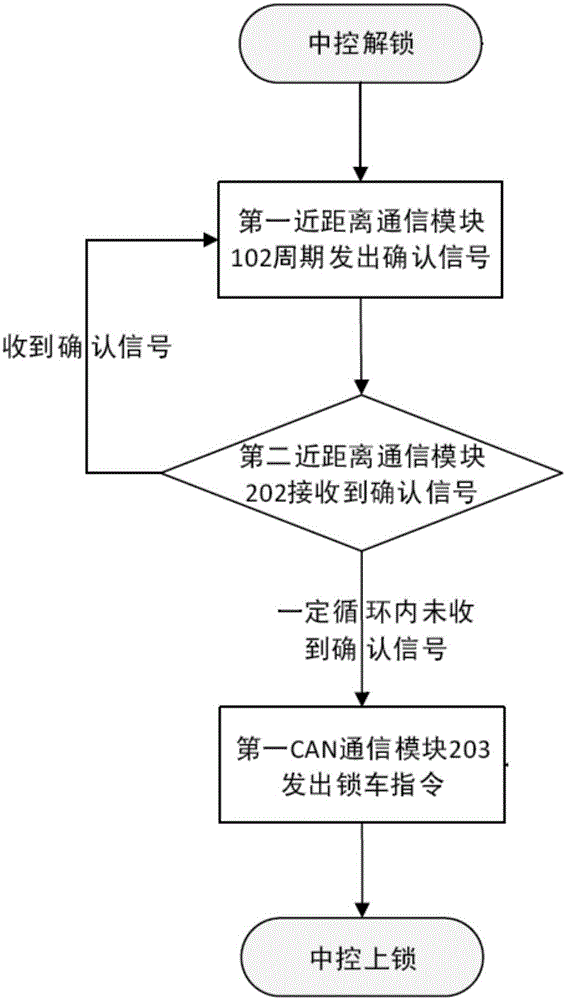
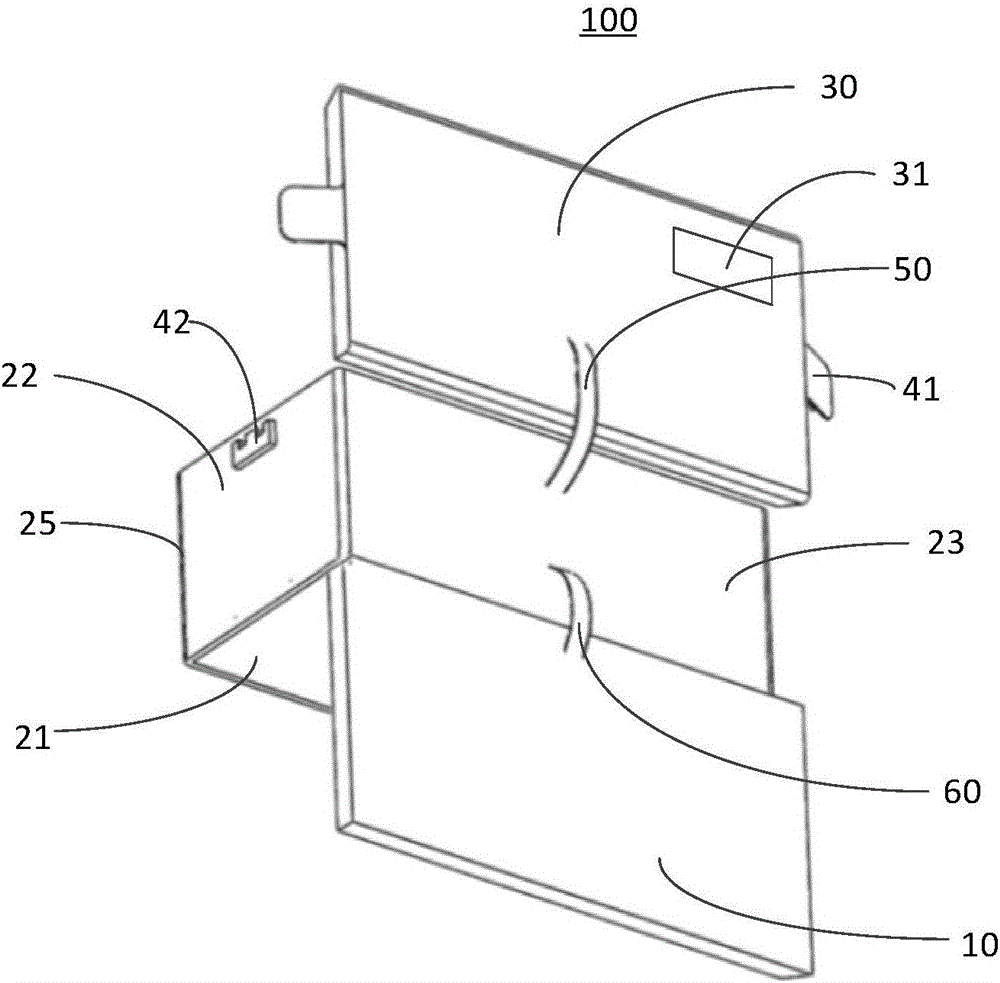
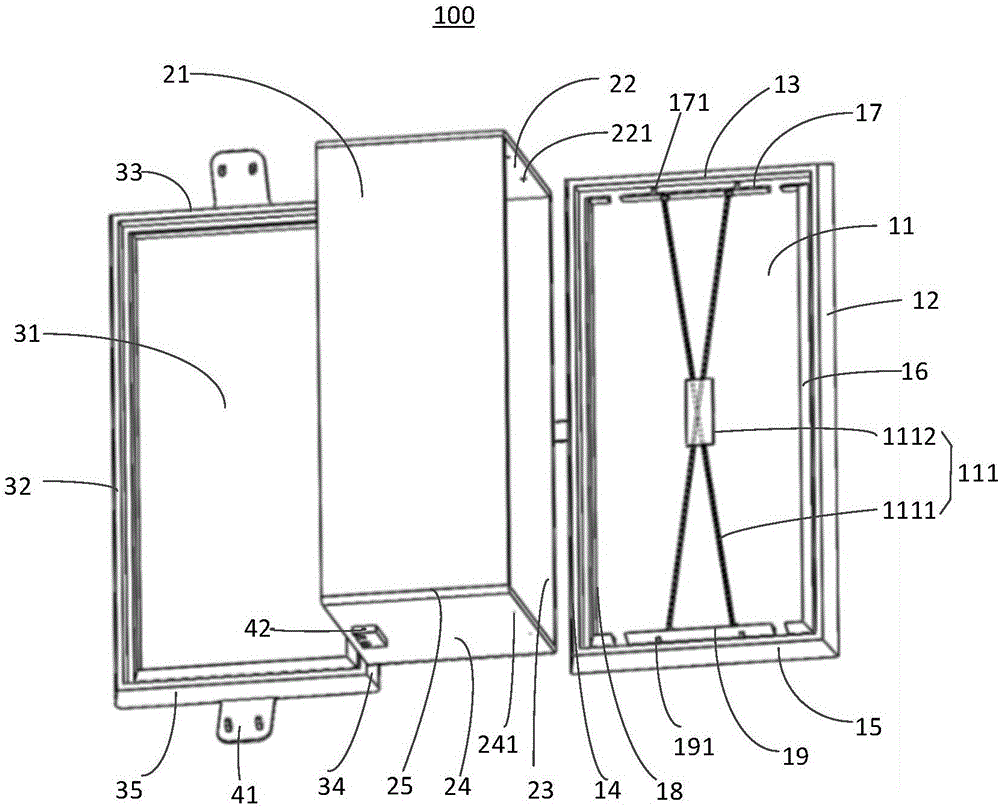
InactiveCN106274796AAvoid the risk of theftExpansionAnti-theft devicesControl systemElectromagnetic signal
The invention relates to a keyless control system of an automobile. The keyless control system is characterized by comprising an automobile intelligent key and a PEPS controller, wherein the PEPS controller is connected with an automobile body controller of the automobile and a door lock central control system of the automobile; the automobile intelligent key comprises a first processing module, a first close-range wireless communication module and a first movement sensing module; and the PEPS controller comprises a second processing module, a second close-range wireless communication module and a first CAN communication module. According to the keyless control system disclosed by the invention, the information of command movements of an owner of the automobile is detected by the first movement sensing module, and the movement commands of the owner of the automobile is checked, so that the risk that the electromagnetic signal of the PEPS controller is intercepted and transferred so that the electromagnetic signal is possibly stolen can be effectively avoided; and in addition, the first movement sensing module is arranged, so that the capacity expansion of the automobile intelligent key can be greatly extended, and more intelligent applications can be realized.
Owner:TSINGHUA UNIV
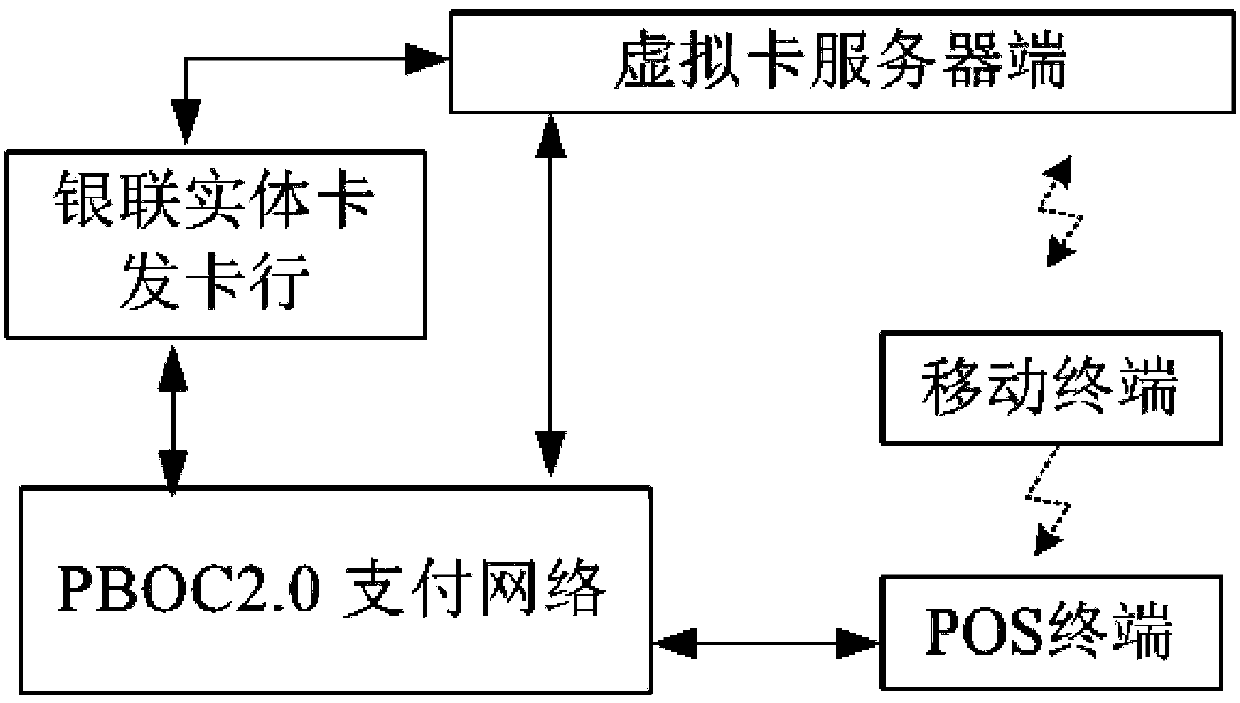
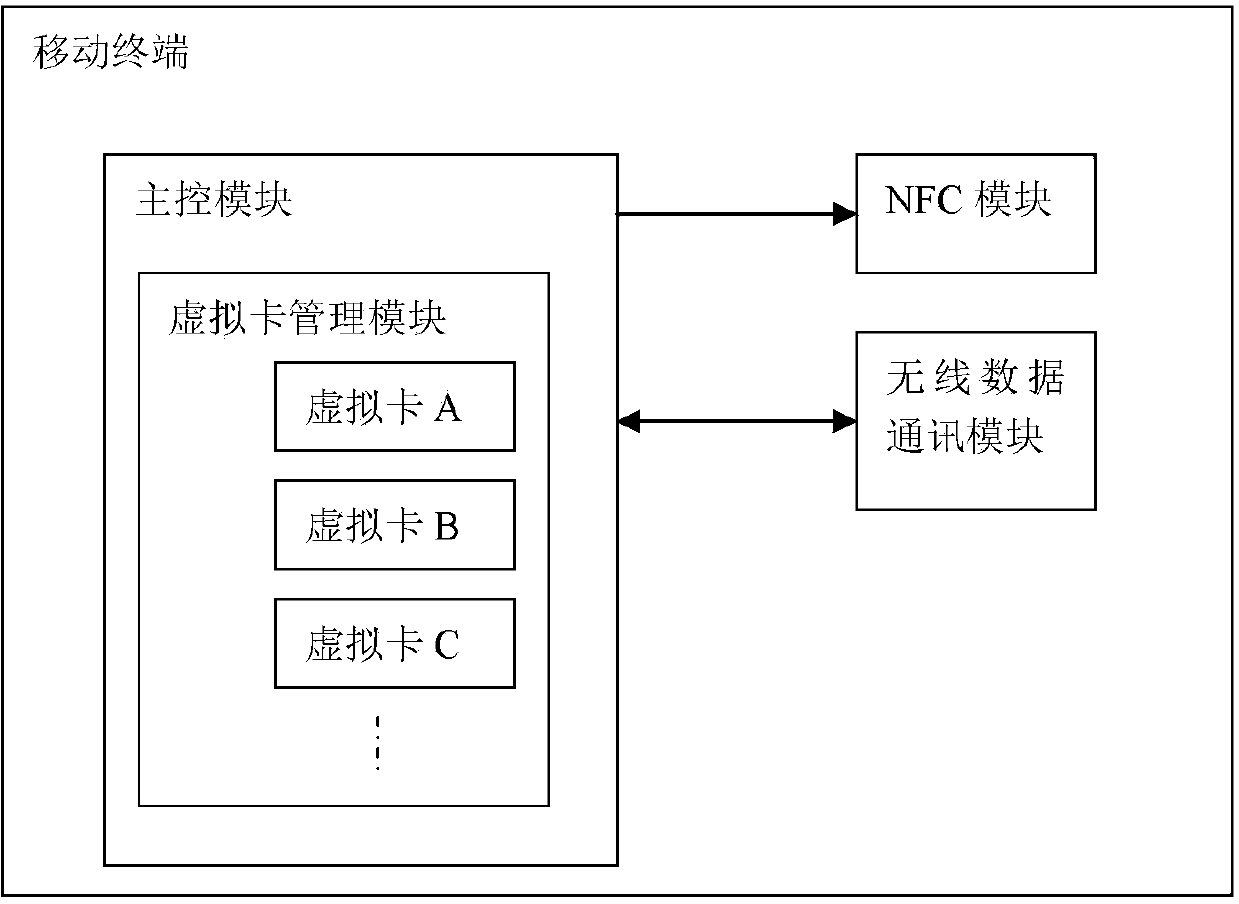
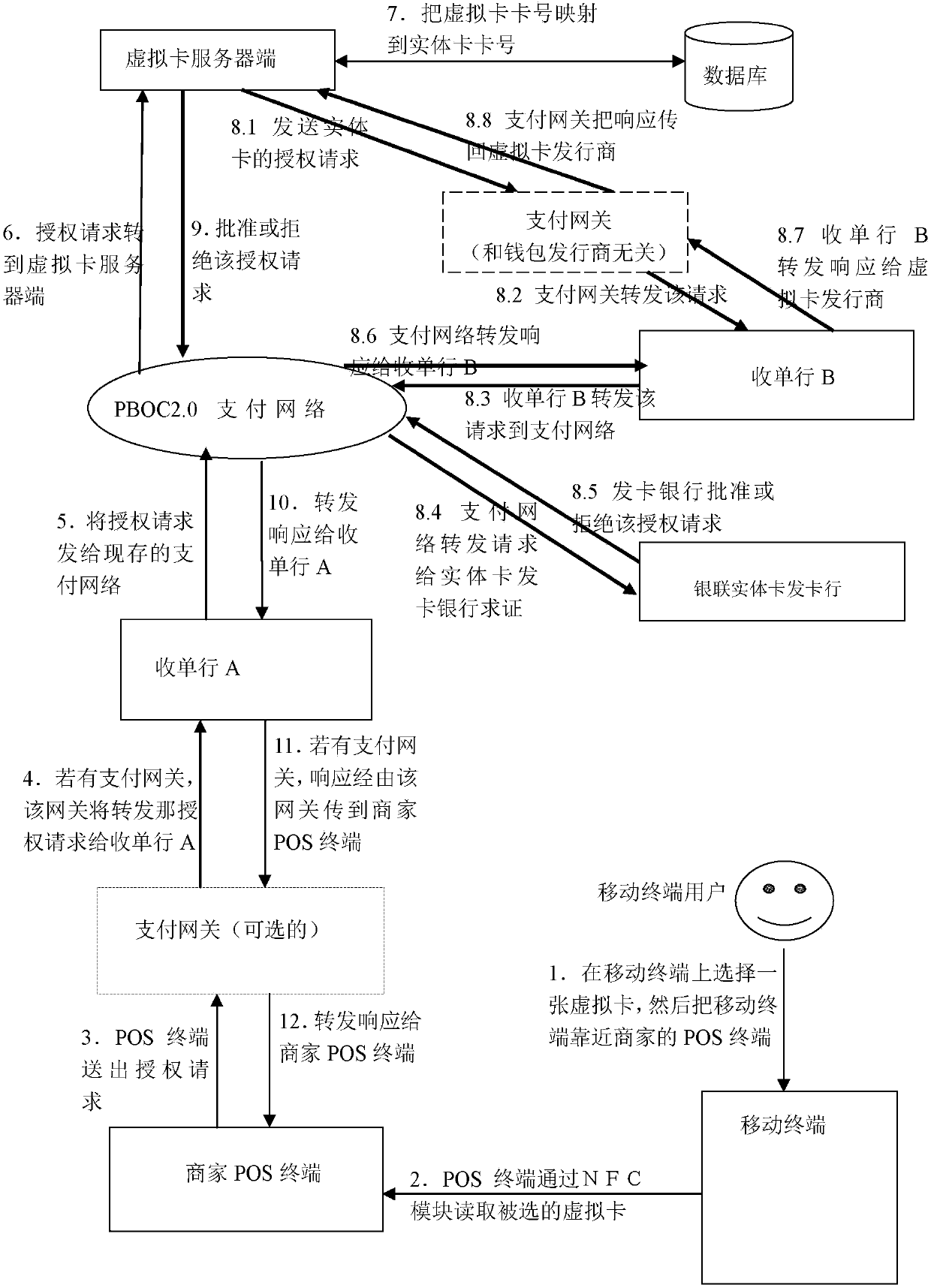
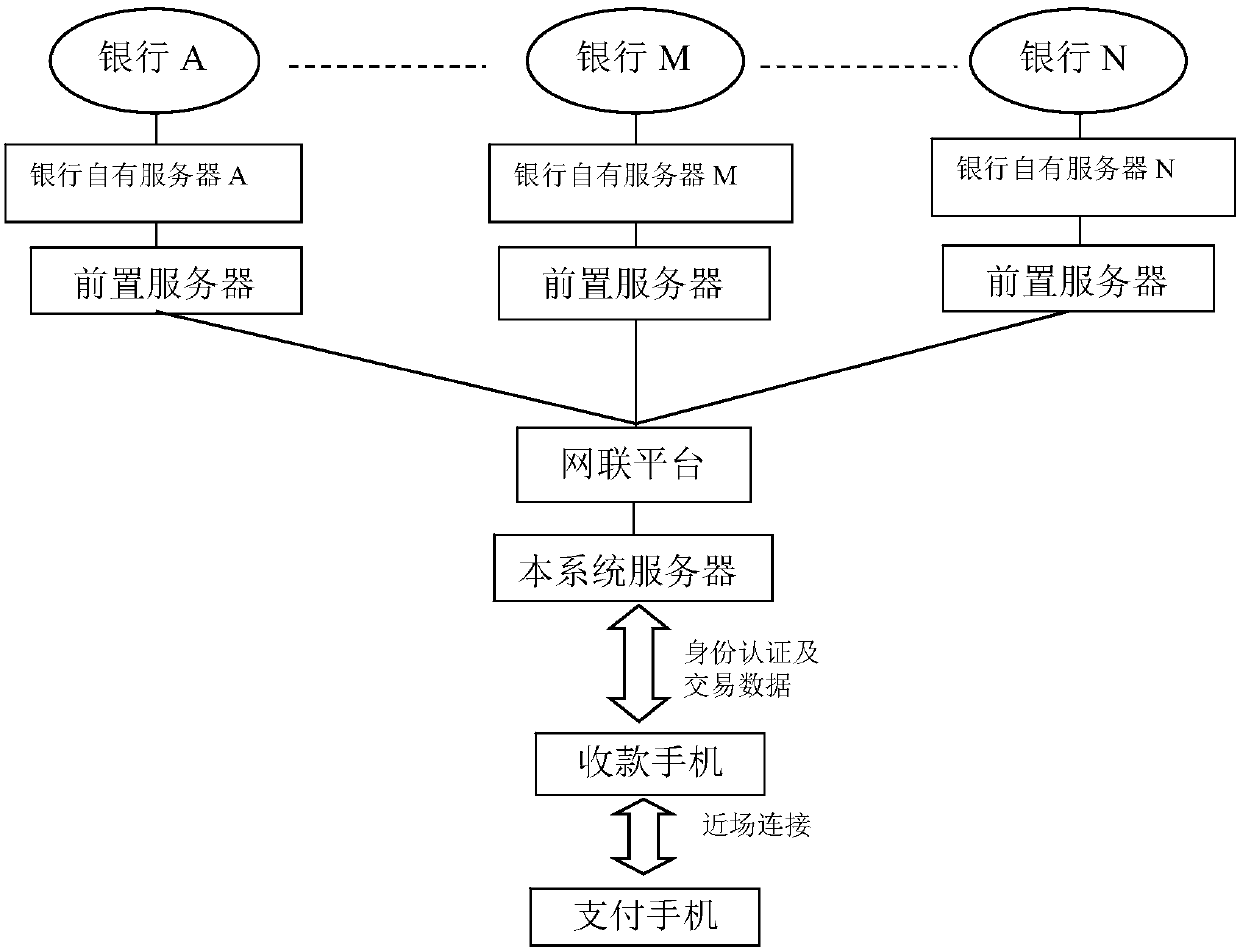
Intelligent payment system based on PBOC payment network and mobile terminal thereof
The invention provides an intelligent payment system based on a PBOC payment network and a mobile terminal thereof, and relates to the technical fields of transaction payment systems and mobile payment. The intelligent payment system overcomes the technical defects that a plurality of China Unionpay solid cards in the prior art are inconvenient to carry, a current phone wallet is inconvenient to use, and the capital safety is poor. The system comprises the mobile terminal, a POS terminal and a virtual card server side. The mobile terminal comprises a main control module, a near-field communication module connected with the main control module, and a virtual card management module arranged in the main control module. At least one virtual card is arranged in the virtual card management module. The POS terminal is connected with the PBOC payment network and used for being matched with the near-field communication module on the mobile terminal for reading related information of the virtual card selected by the virtual card management module, sending an authorization request to the virtual card server side, and receiving payment response returned by the PBOC payment network. The system solves the problem of inconvenience of carrying the China Unionpay solid cards by users, and is convenient and fast to operate and use, money does not need to be saved in advance, the cards do not need to be recharged, capital accumulation is avoided, and capital in all the China Unionpay solid cards is independent, and flexible to use.
Owner:深圳市可秉资产管理合伙企业(有限合伙)
Offline mobile payment method and system
InactiveCN104867008AAvoid lossReduce riskAcutation objectsPoint-of-sale network systemsMobile paymentComputer science
The invention discloses an offline mobile payment method. The method can realize non-contact type offline payment of a POS terminal, and result of the non-contact type offline payment is the same with that of card swiping payment. The method comprises that software is used to process source data including magnetic stripe information of a bankcard so that the source data passes a coding unit and a waveform modulation unit successively, and a modulation signal is generated; a smart phone outputs the modulation signal to a magnetic pulse emitter; the magnetic pulse emitter converts the modulation signal into a magnetic pulse signal, and transmits the magnetic pulse signal to a magnetic head of the POS terminal; and the POS terminal converts the magnetic pulse signal into magnetic stripe information of the bankcard, and payment is carried out. The invention also discloses an offline mobile payment system corresponding to the method.
Owner:SHANGHAI WEARAPAY INC
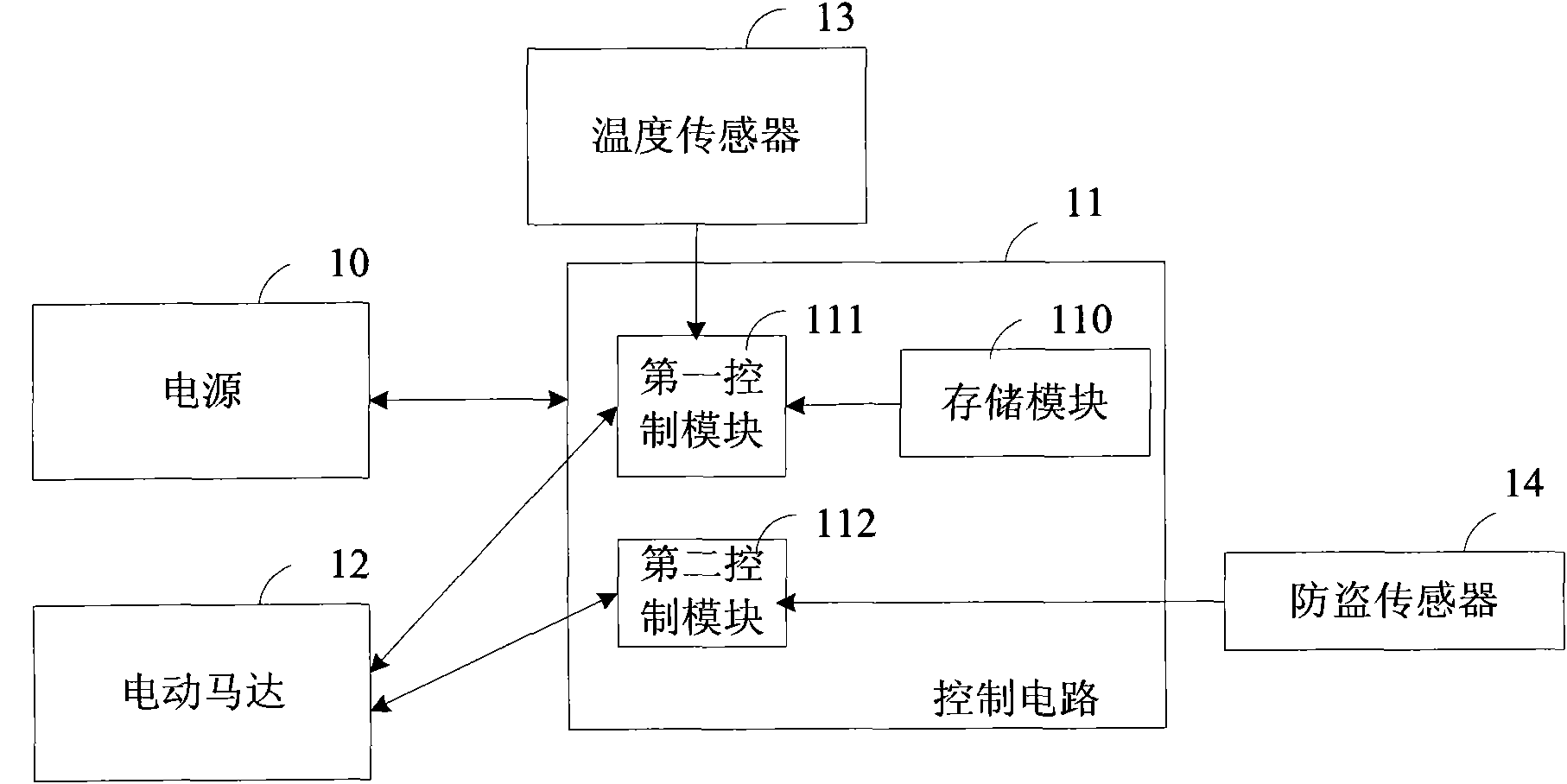
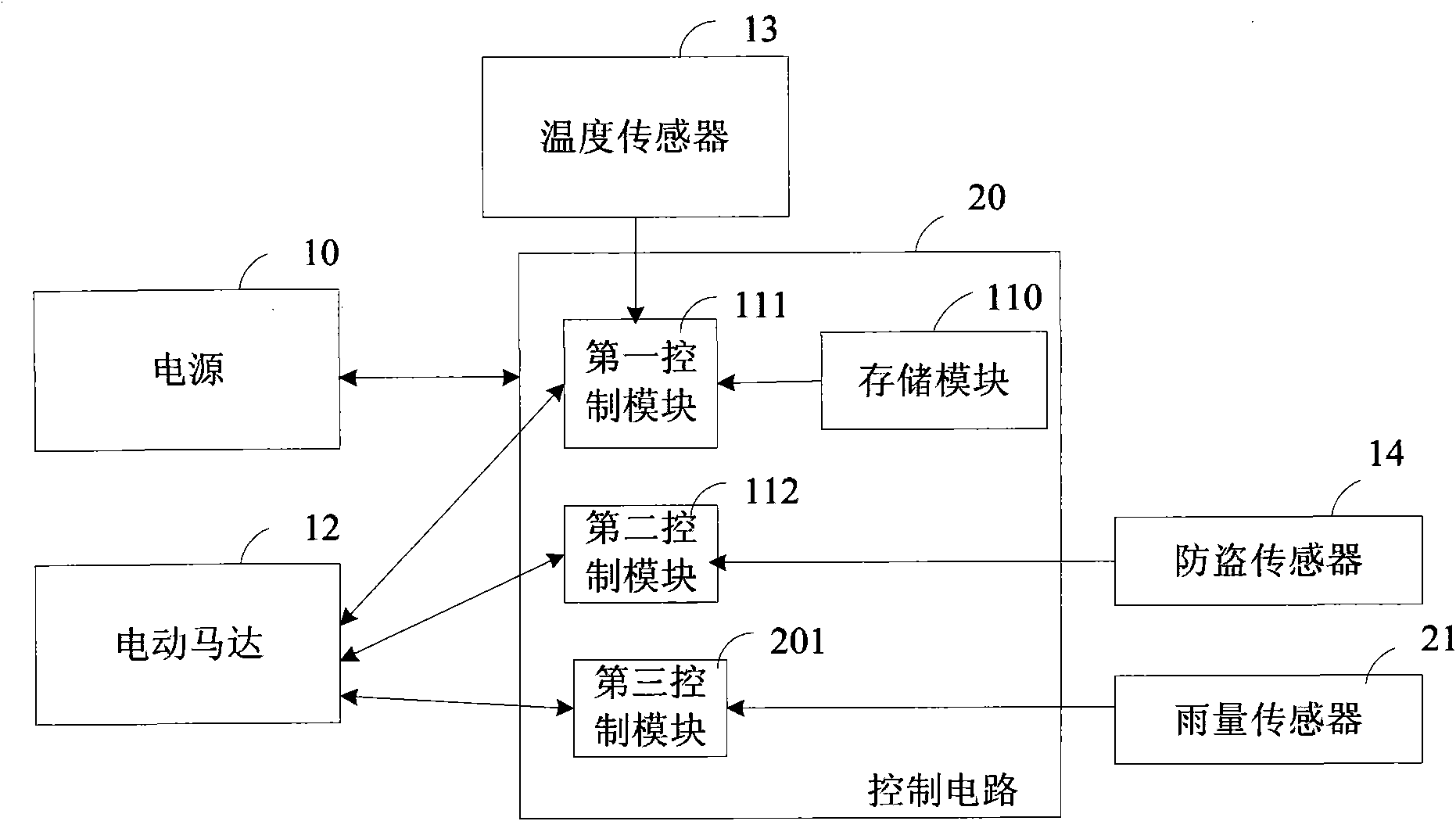
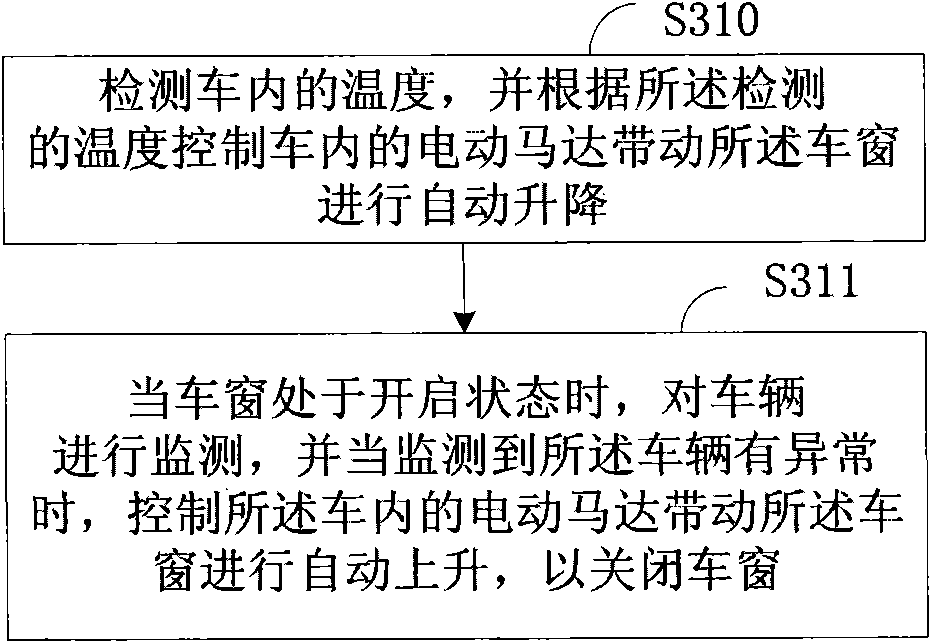
Device and method for controlling automatic ascending and descending of vehicular windows
InactiveCN101892788AAvoid the risk of theftAvoid the risk of entering the carPower-operated mechanismTemperature controlEngineering
The embodiment of the invention provides a device and a method for controlling automatic ascending and descending of vehicular windows. The device comprises an electric motor, a temperature sensor, an anti-theft sensor, a control circuit and a power supply, wherein the electric motor is used for driving the windows to ascend and descend automatically; the temperature sensor is used for detecting the temperature in a vehicle; the anti-theft sensor is used for monitoring the vehicle to generate a monitoring signal; the control circuit is used for controlling the electric motor to drive the vehicular windows to ascend and descend automatically according to the temperature sent by the temperature sensor and / or controlling the electric motor to drive the vehicular windows to ascend automatically so as to close the vehicular windows according to the monitoring signal sent by the anti-theft sensor; and the power supply is used for supplying power to the electric motor, the temperature sensor, the anti-theft sensor and the control circuit. By implementing the device and the method, besides unnecessary injury caused by excess temperature in the vehicle to human bodies can be prevented, the vehicle can be prevented from being stolen.
Owner:DONGFENG MOTOR CO LTD
Express delivery box, express delivery box recycling system, express delivery system and express delivery method
InactiveCN106364793AAvoid the risk of theftAffect the secondary useLocking devicesTerminal serverPassword
The invention relates to the technical field of logistics, in particular to an express delivery box, an express delivery box recycling system, an express delivery system and an express delivery method. The express delivery box comprises a box bottom, a box body, a box cover and a coded lock, wherein the box body surrounds the box bottom and can be folded, the box cover covers the box body, and the box cover and the box body can be fixedly combined in a covering manner through the coded lock. The box body is detachably connected with the box cover and the box bottom, and after the box body is separated from the box cover and the box bottom, the box body can be folded into a plane structure; and the box cover and / or the box body are / is provided with identification codes marking the identity information of the express delivery box, and after a user terminal scans the recognition codes, the identity information of the express delivery box can be obtained from a terminal server, and the identity information comprises a password through which the coded lock can be opened. According to the express delivery box, the stealing risk that an express delivery packet is manually taken apart and glued again is avoided, and environment pollution and resource waste caused by usage of plastic adhesive tape are reduced. The identification codes are used for replacing an express delivery bill, the express delivery receiving and dispatching efficiency is improved, and information disclosure of users is avoided.
Owner:姚江南
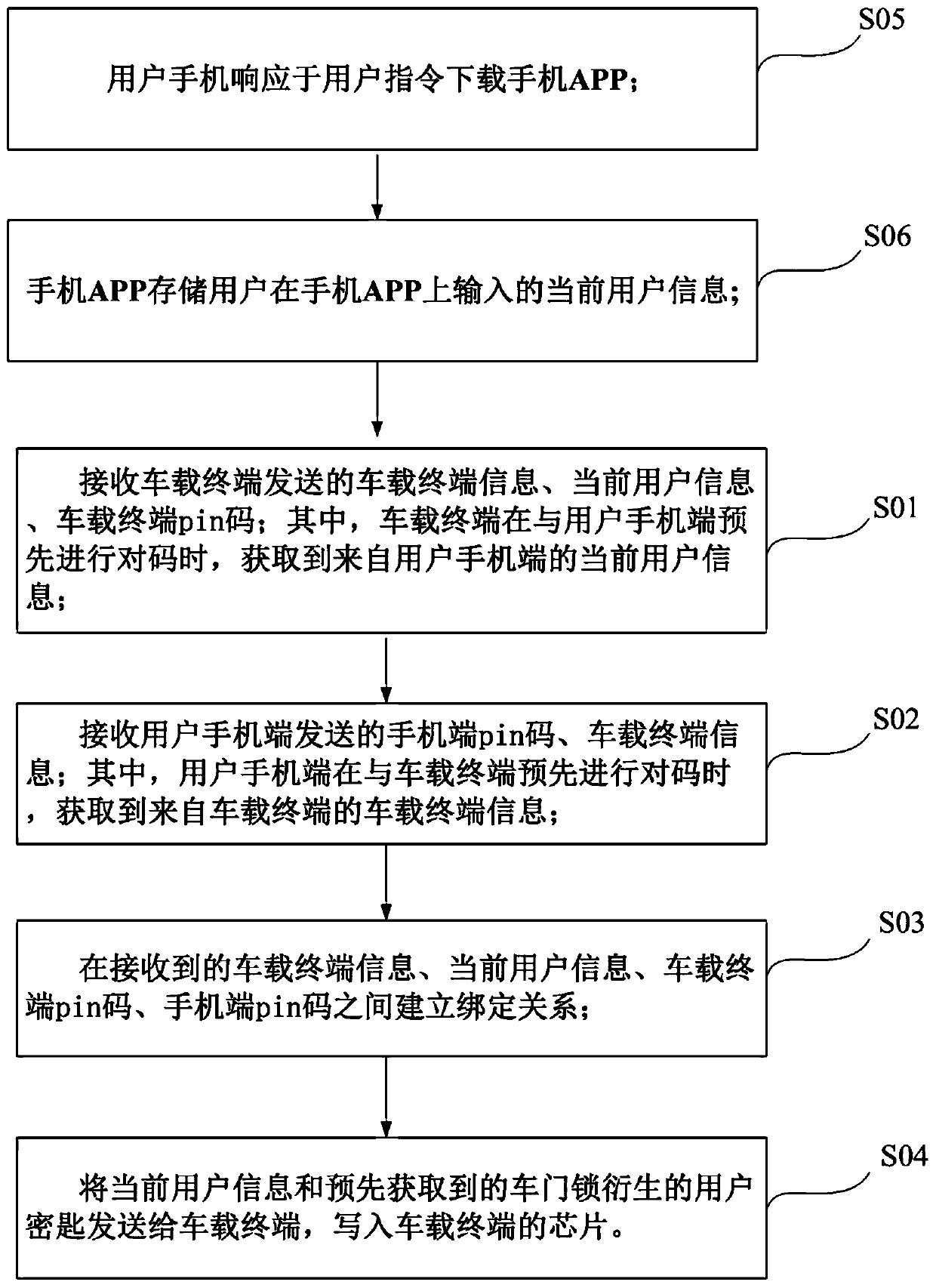
Unlocking method and unlocking system with mobile phone as automobile key
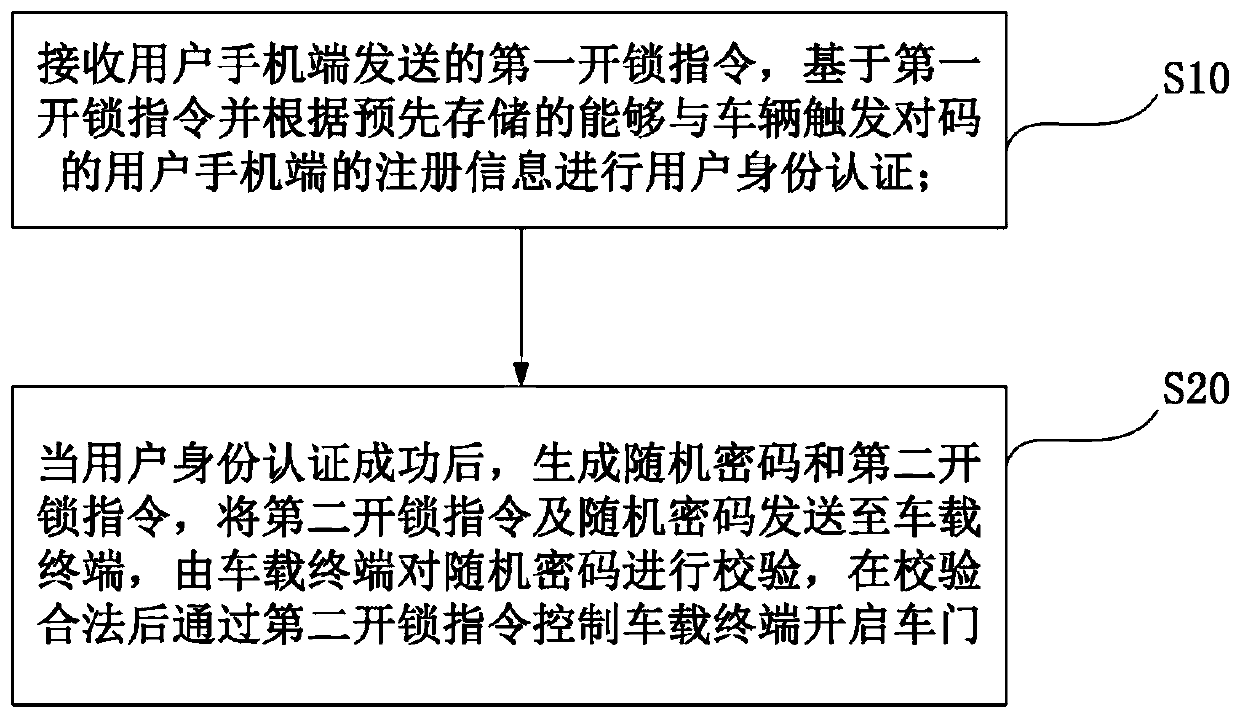
ActiveCN110381199APrevent theftImprove securityAnti-theft devicesSubstation equipmentPasswordComputer terminal
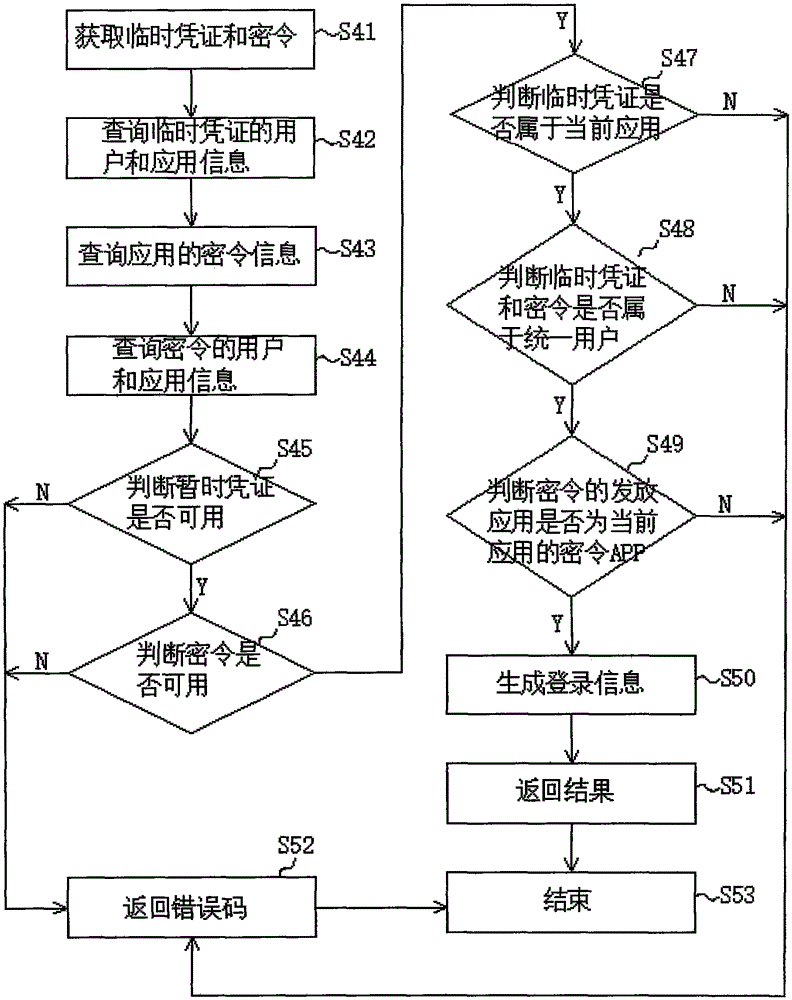
The invention provides an unlocking method and an unlocking system with a mobile phone as an automobile key, and relates to the technical field of vehicle control. The unlocking method with the mobilephone as the automobile key comprises the following steps: receiving a first unlocking instruction sent by a user mobile phone terminal, and performing user identity authentication based on the firstunlocking instruction and according to pre-stored registration information of the user mobile phone terminal capable of triggering code matching with an automobile; and after the user identity authentication succeeds, generating a random password and a second unlocking instruction, sending the second unlocking instruction and the random password to the vehicle-mounted terminal, verifying the random password by the vehicle-mounted terminal, and controlling the vehicle-mounted terminal to open the vehicle door through the second unlocking instruction after the random password is verified to belegal. When the vehicle receives the unlocking instruction, the user identity authentication needs to be conducted firstly, the vehicle can be started only after joint authentication of the mobile phone terminal and the vehicle-mounted terminal, the safety performance of the vehicle is improved, and the problem that the vehicle is stolen due to the fact that a mobile phone is lost is avoided.
Owner:GEELY AUTOMOBILE INST NINGBO CO LTD +1
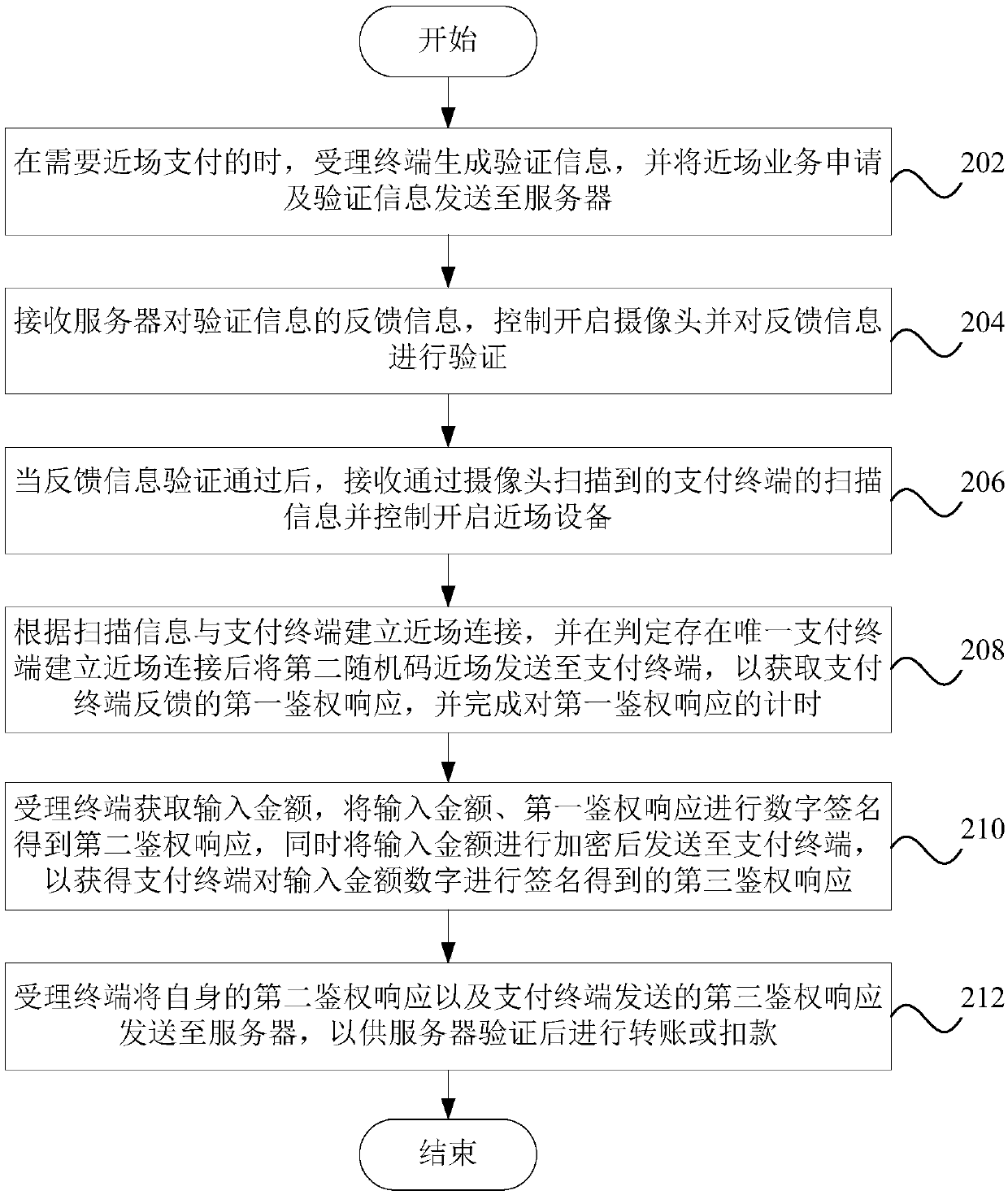
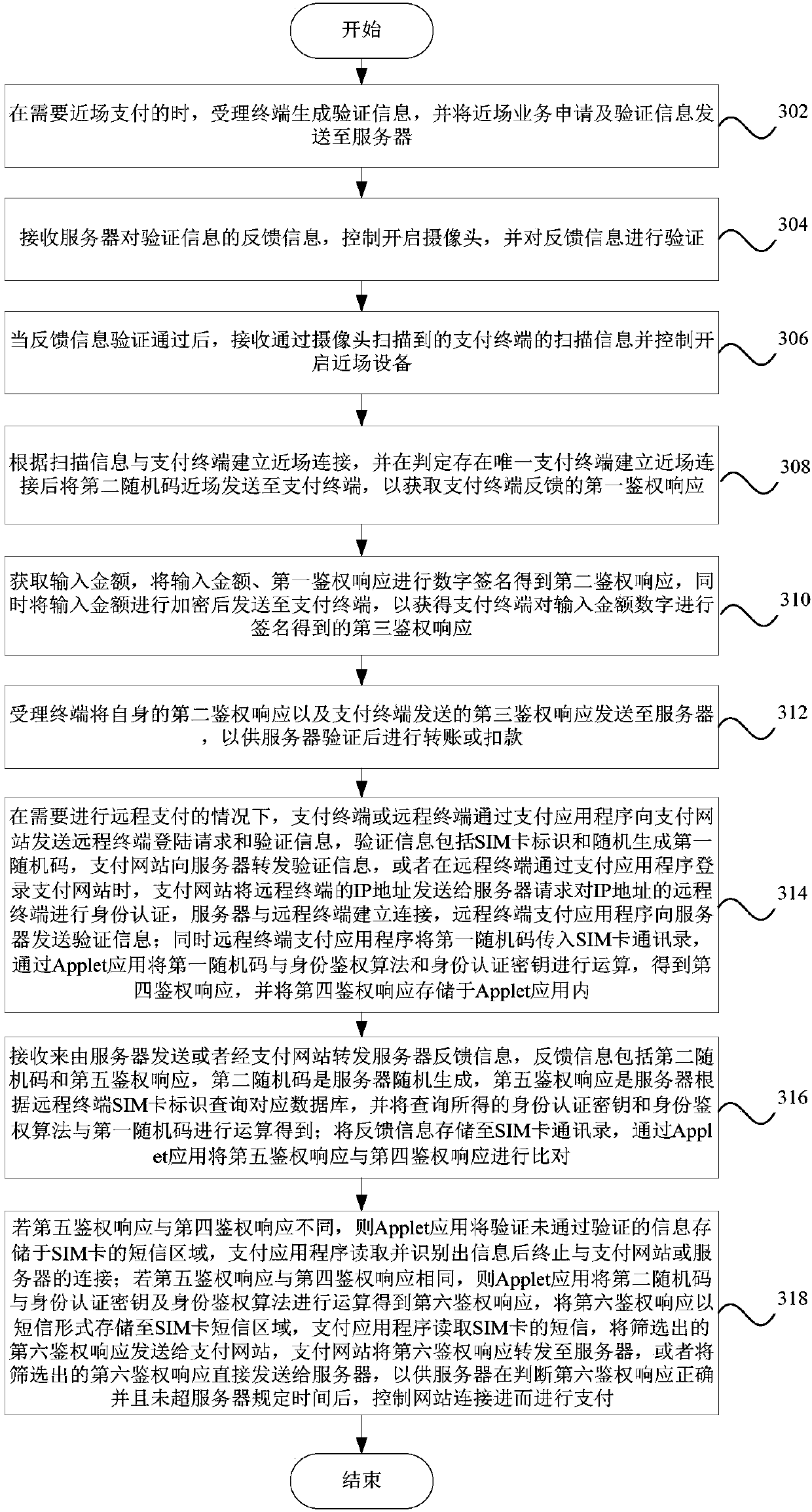
Mobile payment method and device, computer equipment and readable storage medium
PendingCN110232568AEnsure safetyGuaranteed fundsDigital data protectionPayment protocolsDigital signatureComputer terminal
The invention provides a mobile payment method and device, computer equipment and a readable storage medium. The mobile payment method comprises: when near-field payment is carried out, enabling an acceptance terminal to generate verification information and send a near-field service application and the verification information to a server; receiving feedback information of the server to the verification information, controlling to start the camera, and verifying the feedback information; when the verification is passed, receiving scanning information, scanned by the camera, of the payment terminal, and controlling the near-field device to be started; establishing a near-field connection with the payment terminal according to the scanning information, and sending a second random code nearfield to the payment terminal to obtain a first authentication response after it is judged that the unique payment terminal establishes the near-field connection; obtaining an input amount, performingdigital signature on the input amount and the first authentication response to obtain a second authentication response, encrypting the input amount, and sending the encrypted input amount to a payment terminal for digital signature to obtain a third authentication response; and enabling the acceptance terminal to send the second authentication response and the third authentication response to theserver for verification.
Owner:CHINA MOBILE GROUP SICHUAN +1
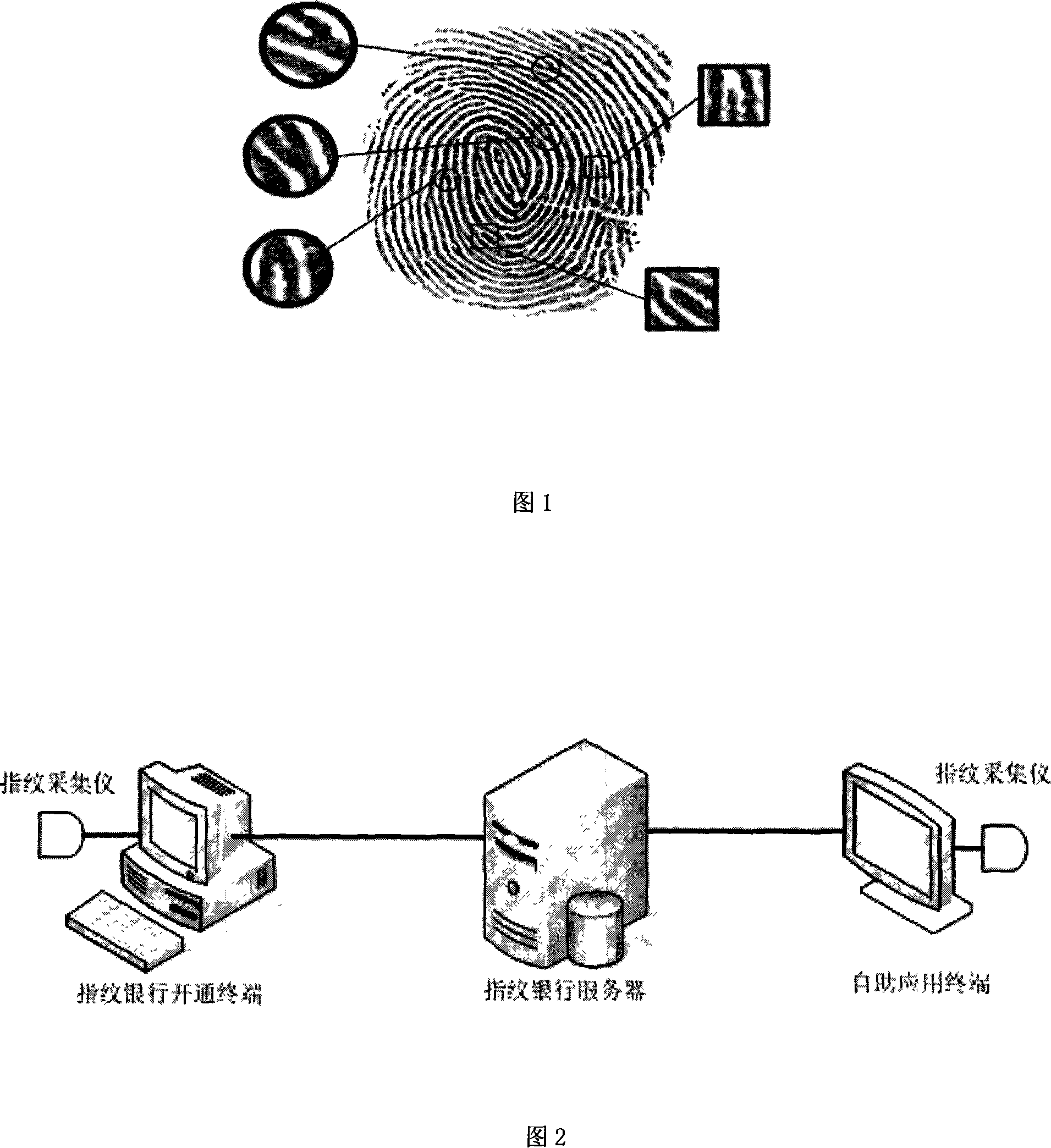
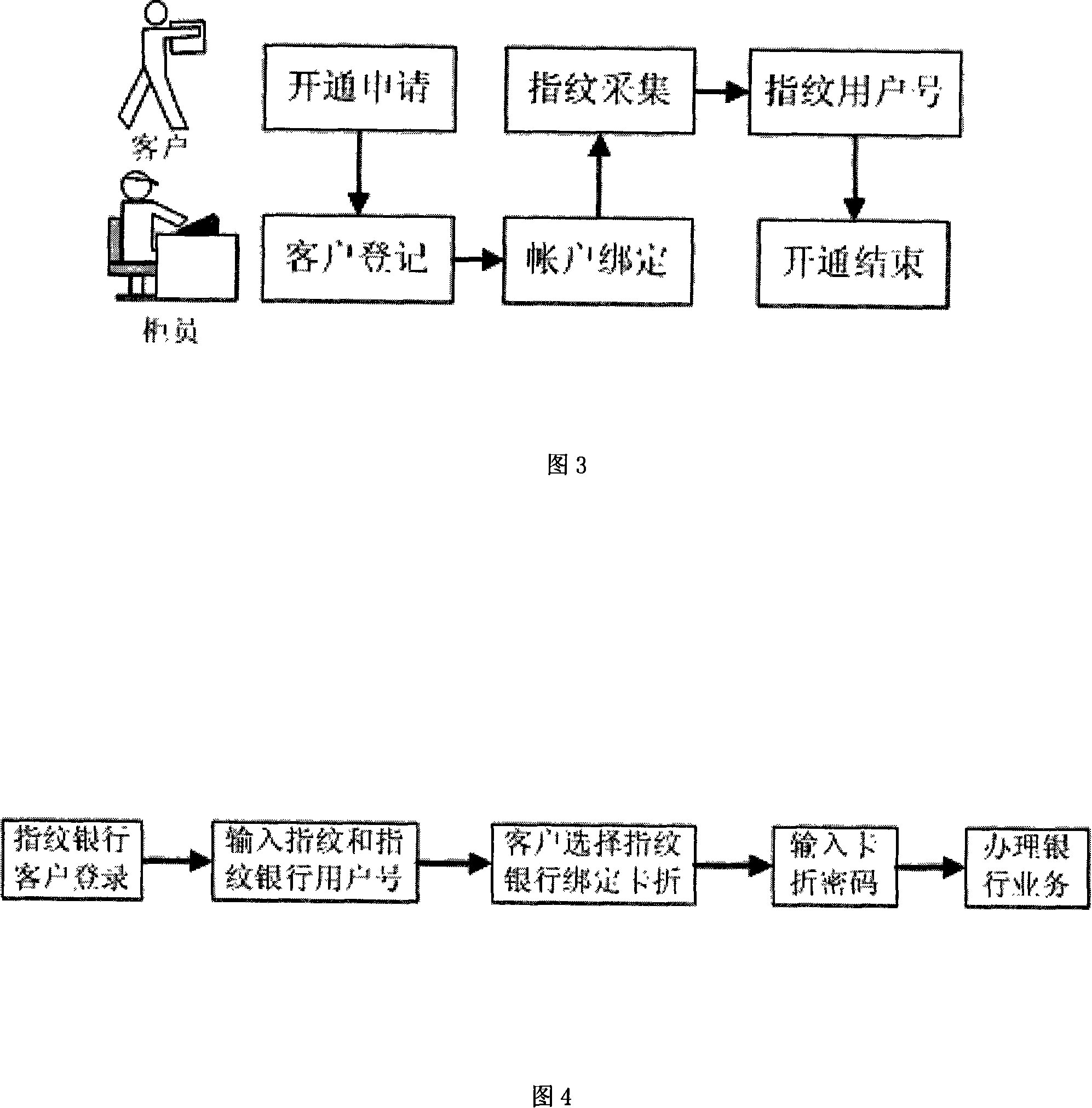
Finger print bank system
InactiveCN101162534AImprove securityImprove reliabilityComplete banking machinesAcutation objectsPaymentRelevant information
The invention provides a fingerprint banking system, wherein, a bank can adopt fingerprint recognition, an advanced modern biological recognition technology, to replace the prior financial payment carriers such as card and deposit book; therefore, a bank customer can complete banking operations such as preengagement, deposit and draw money, transfer of account and paying fees just by a finger; thus, the invention realizes process reengineering for banking business. The system comprises an open terminal, an application terminal and a system server, wherein, through the opening terminal, a customer can confirm a fingerprint banking system customer account number and inputs fingerprint information to open related services; the customer can input the fingerprint banking system customer account number and fingerprint into the application terminal for handling banking businesses; the system server which stores the fingerprint banking system customer account number, fingerprint template and related information of the customer provides confirmation service of fingerprint recognition information. The system is sure to bring a brand new reform in banking payment form and business operation flow.
Owner:BEIJING RURAL COMML BANK CO LTD
Web system oriented logging-in method
ActiveCN105978994AAvoid the risk of theftEasy to implementDigital data authenticationTransmissionComputer terminalEncryption
The invention relates to a Web system oriented logging-in method. The method comprises the following steps: when a user employs a browser to access a Web system which is not logged-in, the Web system submits session identification data between the browser and the Web system and a temporary stored identifier of the session identification data to a mobile logging-in server for temporary storage, meanwhile displays the temporary stored identifier in a form of bar codes through a user browser; a mobile logging-in assistant in a user mobile terminal obtains the temporary stored identifier through scanning the bar codes and submits the temporary stored identifier to the mobile logging-in server; after completion of identity authentication of the user, the mobile logging-in server replaces the user to log-in the Web system by using the session identification data corresponding to the temporary stored identifier, or returns the session identification data corresponding to the temporary stored identifier to the mobile logging-in assistant for logging-in the Web system, or encrypts the session identification data corresponding to the temporary stored identifier by using a user encryption key and then returns the session identification data corresponding to the temporary stored identifier to the mobile logging-in assistant for logging-in the Web system after the session identification data are decrypted.
Owner:WUHAN UNIV OF TECH
Storage cabinet
InactiveCN107752474AEasy to useEasy to viewCredit registering devices actuationCabinetsPasswordAlarm device
The invention discloses a locker, which comprises a cabinet body. The cabinet body is provided with several layers of cabinet frames, and a plurality of cabinet grooves are distributed on each layer of cabinet frames. Cabinet boxes are slidably installed in the cabinet grooves. The locker By setting up a camera device and a buzzer alarm, the camera device and the buzzer alarm are connected to the controller, when the password input device continuously enters the wrong password for the set number of times, the camera device takes pictures of the person who is unlocking and stores them for convenience The user checks the specific situation, and the buzzer alarm emits a sharp alarm sound to deter the abnormal unlocking personnel and remind other personnel, thus making the use of the locker safer and effectively avoiding the traditional Due to the risk of being stolen without a protective alarm device, the locker has relatively high safety in use.
Owner:谭庭活
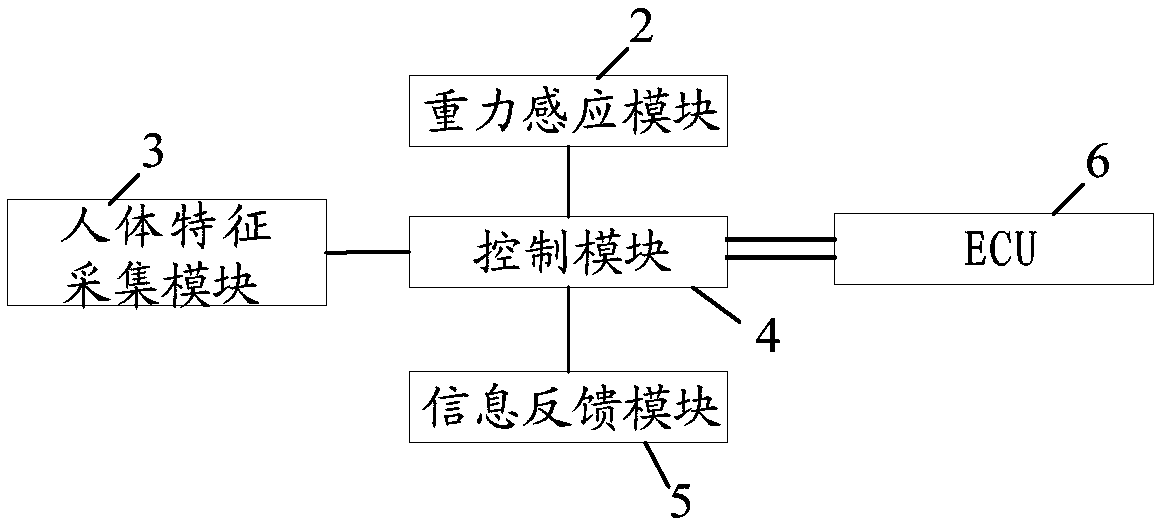
Multifunctional steering wheel and vehicle
InactiveCN107585201AImprove securityImprove comfortAnti-theft devicesHand wheelsElectronic control unitElectricity
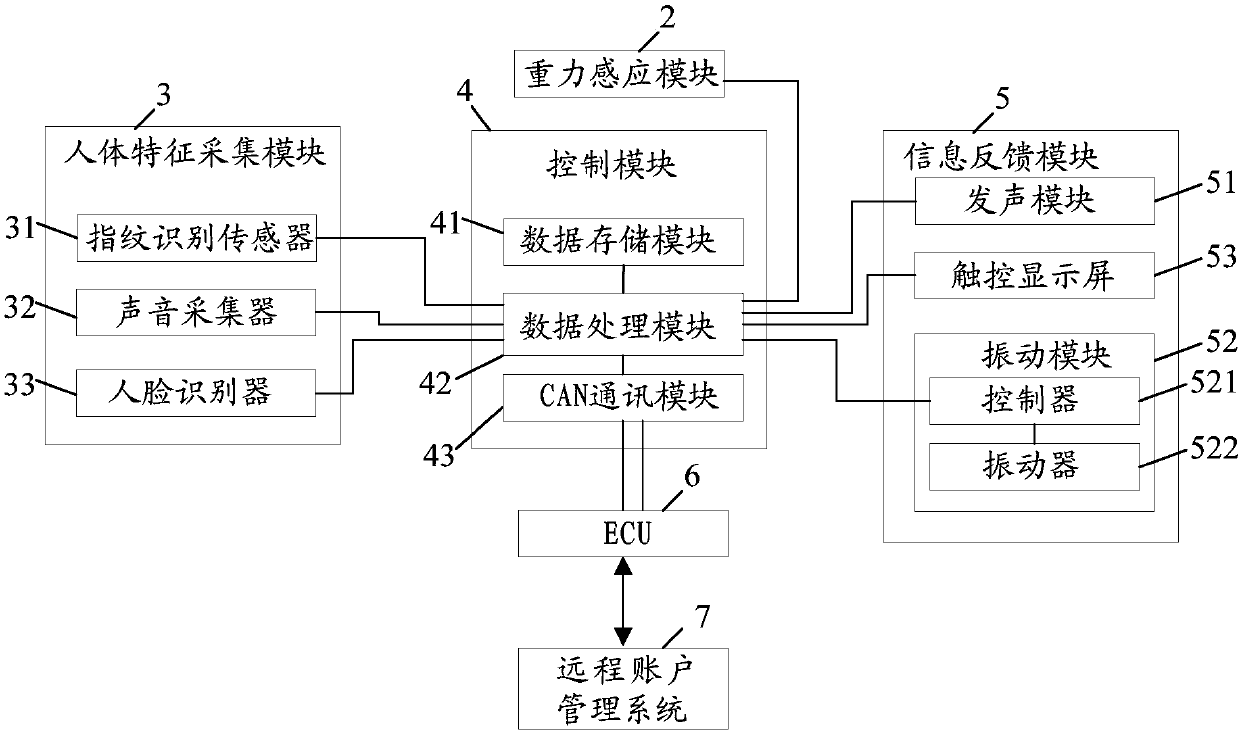
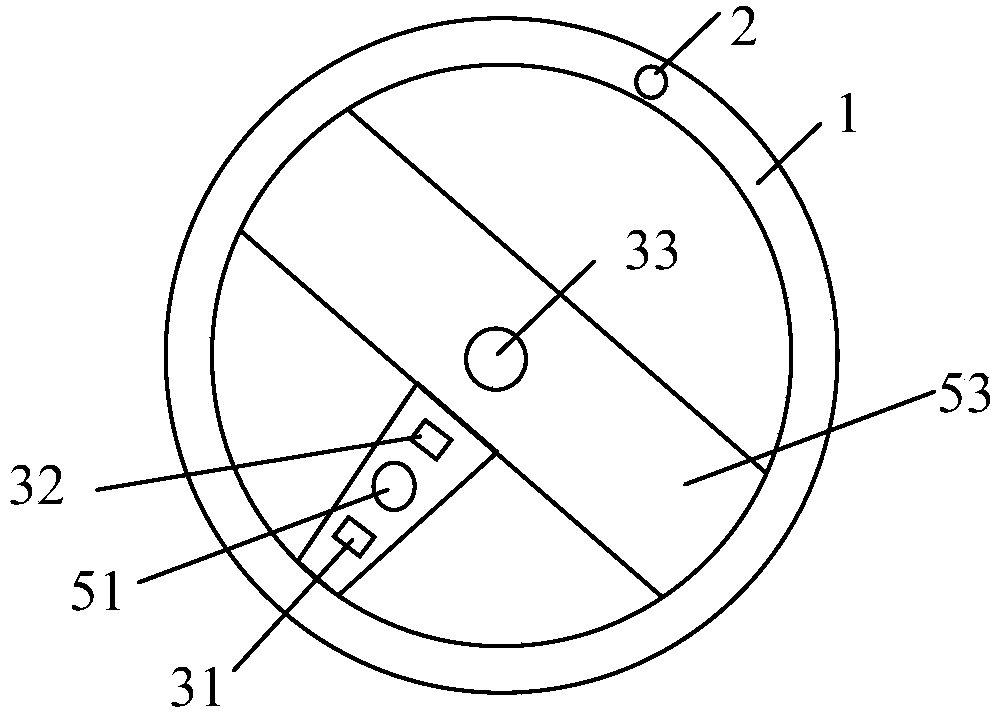
The invention provides a multifunctional steering wheel and a vehicle, and relates to the technical field of vehicle intellectualization. The multifunctional steering wheel comprises a steering wheelbody, a gravity induction module arranged on the disc body of the steering wheel body, a human body characteristic acquiring module, a control module, and an information feedback module, wherein the human body characteristic acquiring module, the control module, and the information feedback module are arranged on the T-shaped body of the steering wheel body; the gravity induction module, the humanbody characteristic acquiring module and the information feedback module are electrically connected with the control module; the control module is used for comparing human body characteristic information acquired by the human body characteristic acquiring module with prestored human body characteristic information to obtain a comparison result, and outputting the comparison result through the information feedback module; and after comparison is successful, the prestored human body characteristic information matched with the acquired human body characteristic information, and corresponding vehicle setting information are output to an electronic control unit (ECU) through a controller area network (CAN) bus. Through the adoption of the multifunctional steering wheel provided by the invention, the function that a driver can be identified in many ways is realized, and driving feeling is improved.
Owner:BEIJING ELECTRIC VEHICLE
Microcontroller chip with data extraction encryption function
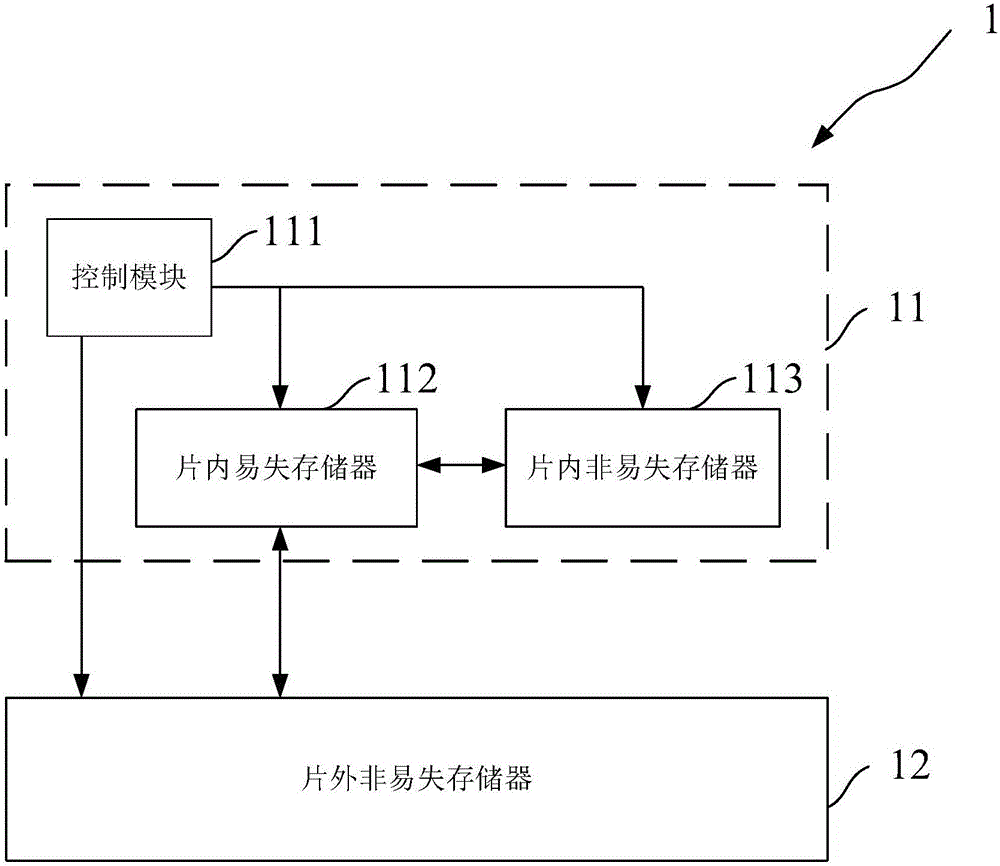
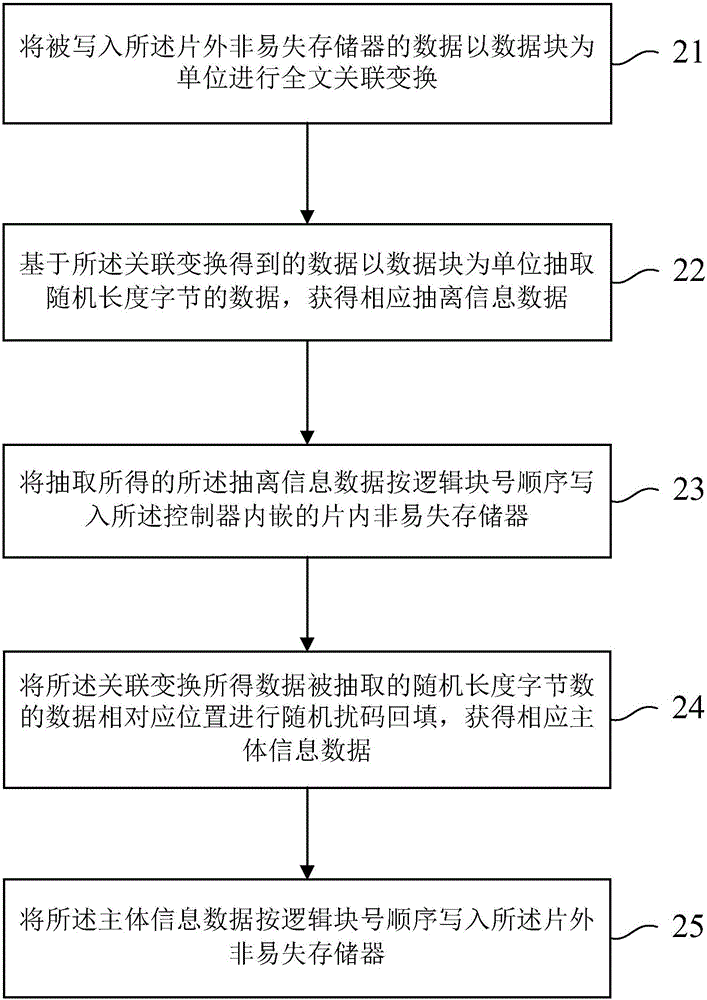
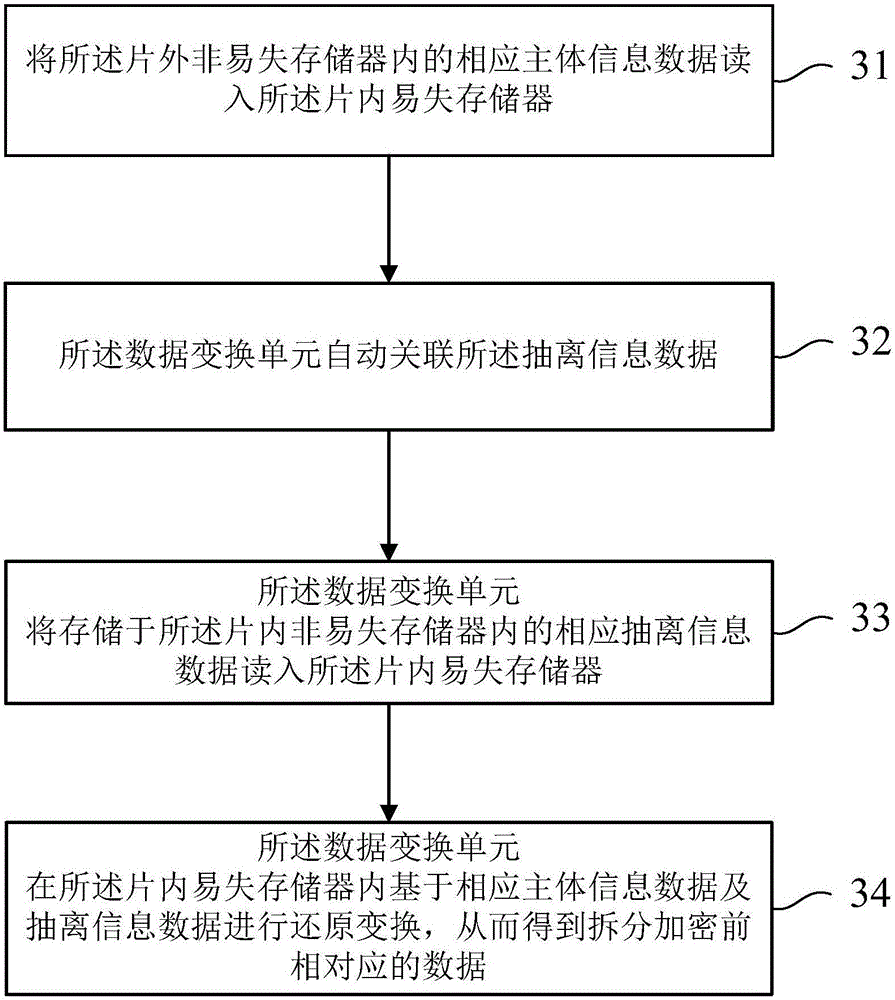
ActiveCN105159611AAvoid encryption and decryption calculationsReduce chip costProgramme controlInput/output to record carriersData transformationSystematic code
The invention relates to a microcontroller chip with a data extraction encryption function. A small-capacity random access nonvolatile memory is arranged in the chip while the chip is provided with an off-chip nonvolatile memory access interface. When the chip is used, after a data transformation unit embedded into the microcontroller chip carries out full-text correlative transformation on a code and critical data, the code and the critical data are split into two parts which are respectively stored in the on-chip nonvolatile memory and the off-chip nonvolatile memory, wherein the data transformation unit aggregates and recovers two parts of data whendata are read. The code and the data of the off-chip nonvolatile memory are transformed and the data are incomplete, so that the code and the data cannot be stolen or illegally accessed. According to the microcontroller chip, the risk of illegal access of data is effectively avoided when the code and the critical data of the existing embedded system are external, and meanwhile, the high operand cost of a conventional encryption algorithm and the risk introduced during key transfer are reduced, and thus an efficient and cheap data protection solution is provided for the embedded system.
Owner:南京伍安信息科技有限公司
Unified account information management method based on biological characteristic encryption
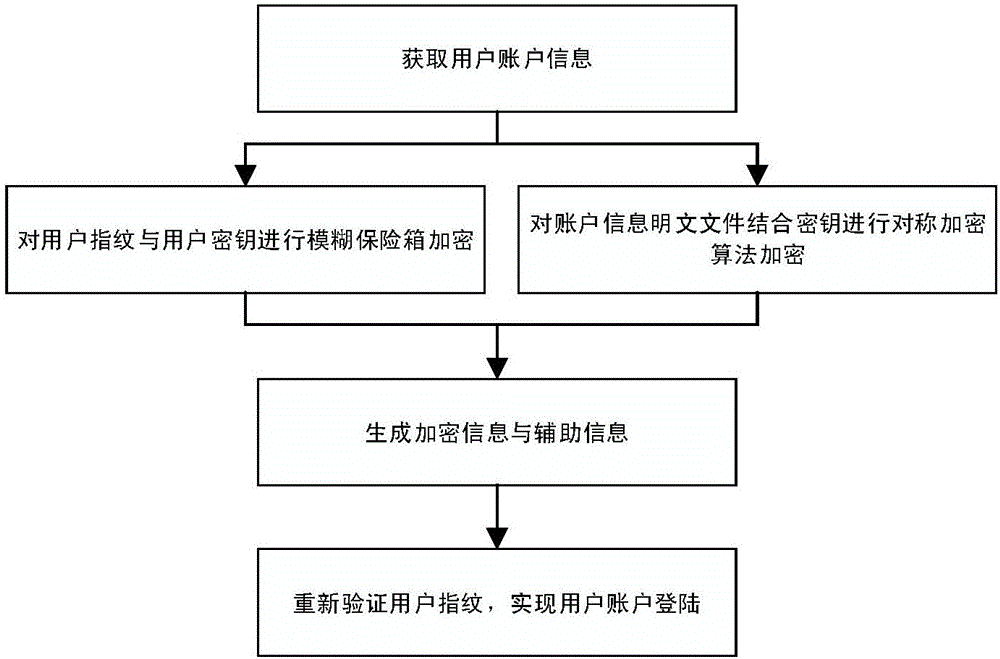
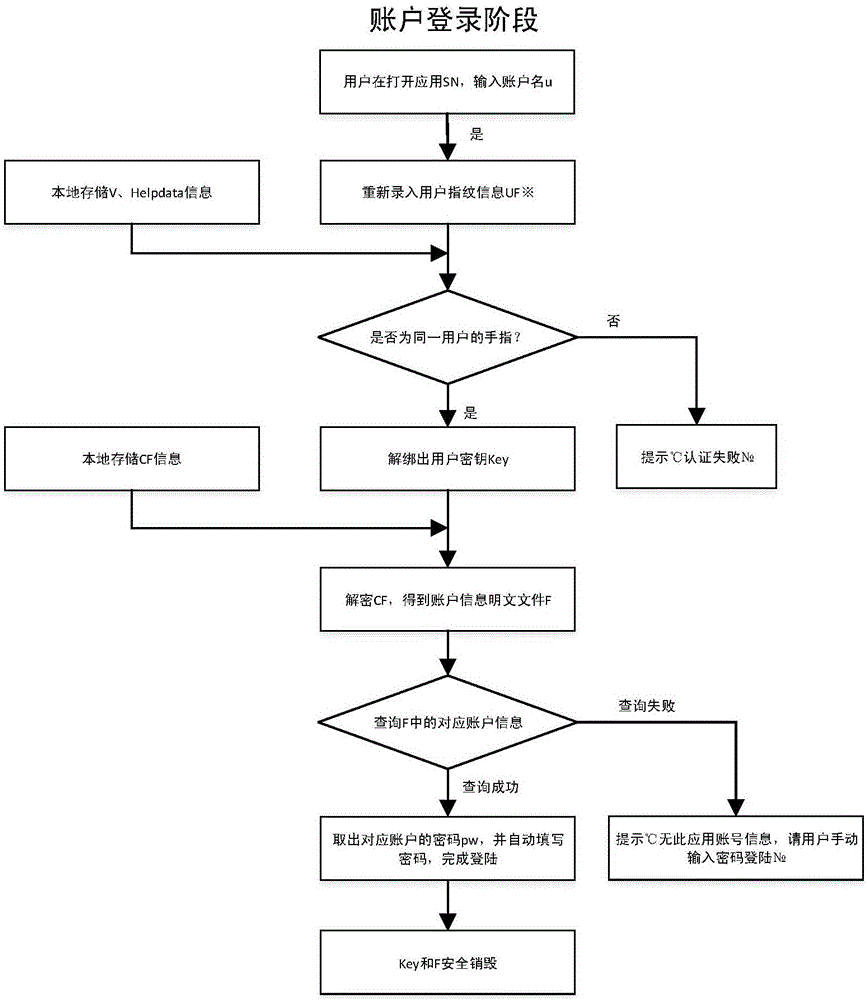
InactiveCN106789017AImprove convenienceImprove work efficiencyKey distribution for secure communicationUser identity/authority verificationPlaintextProtection mechanism
The invention discloses a unified account information management method based on biological characteristic encryption. The management method particularly includes the steps: 1 acquiring user account information; 2 performing crypto-binding on biologic characteristic information and secret keys by the aid of a fuzzy vault algorithm; 3 encrypting plain text files of the account information by the aid of a symmetric encryption algorithm; 4 generating encryption data and auxiliary information; 5 logging user accounts. According to the management method, user fingerprint characteristics and user secret keys are bound by the aid of fuzzy vault technology, the user secret keys and fingerprint security are greatly protected, the plain text files of the account information are encrypted by the aid of the symmetric encryption algorithm, and the security of the user account information is effectively ensured by the aid of a dual-protection mechanism. By the management method, user account information is integrally managed, and user convenience is achieved while security of the account information is ensured.
Owner:XIDIAN UNIV
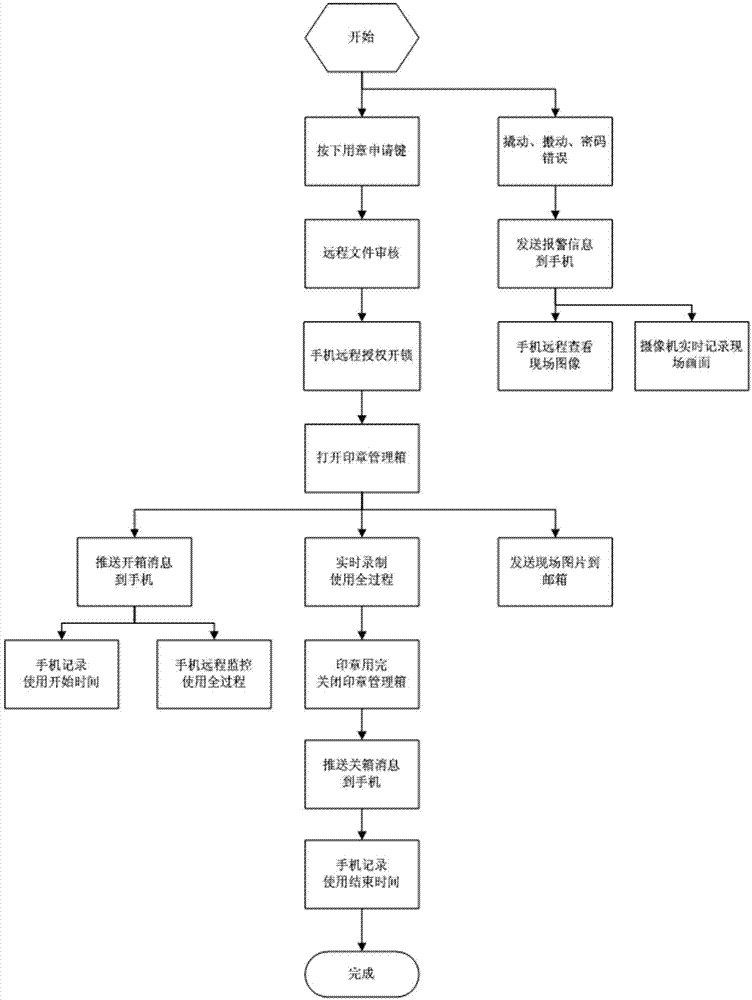
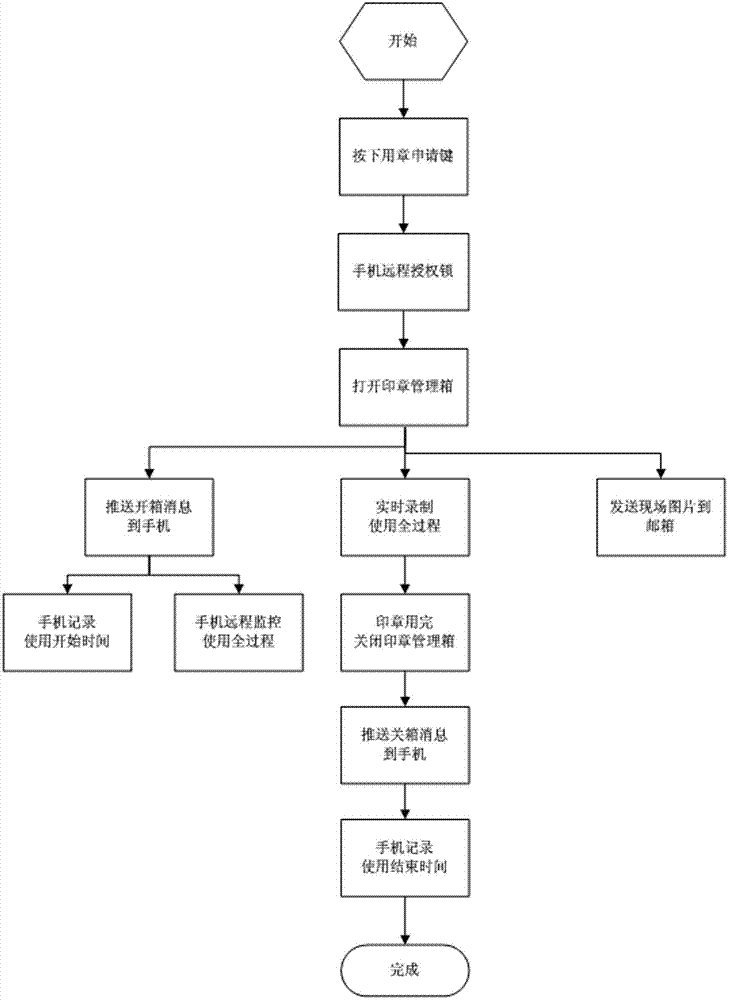
Seal remote operation system based on Internet of things and operation method thereof
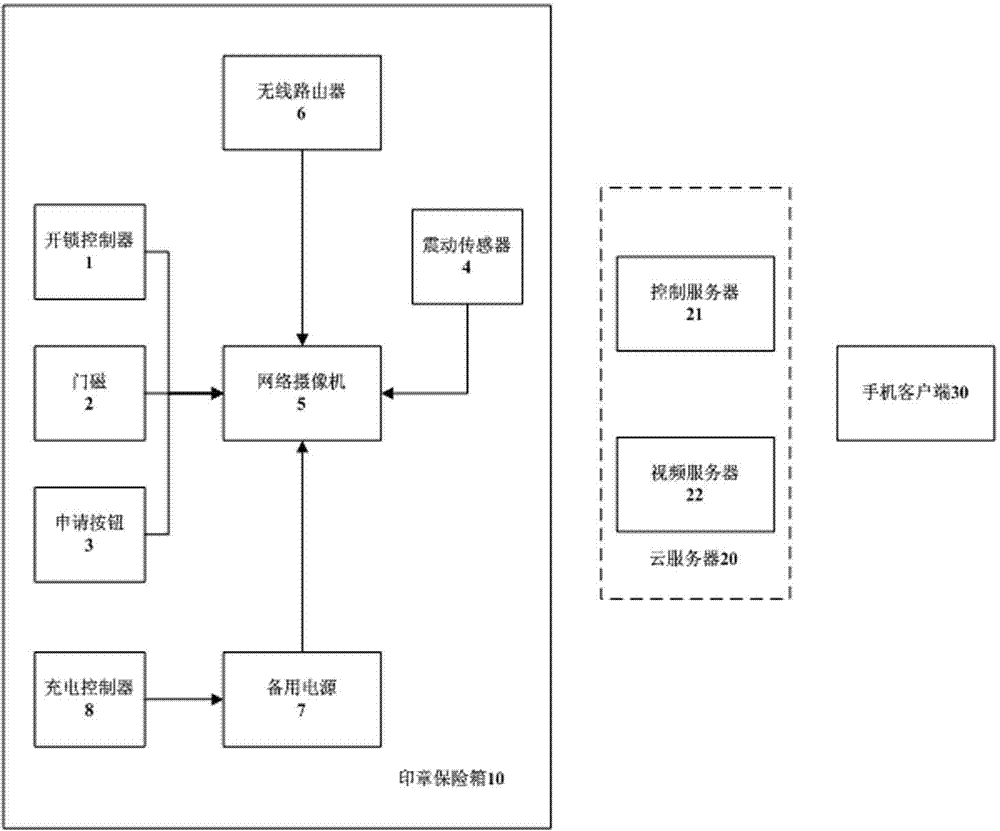
InactiveCN104850045AAvoid the risk of theftEasy to carry and useProgramme controlComputer controlWireless routerThe Internet
The invention relates to a seal remote operation system based on the Internet of things. A seal safekeeping box is connected with a cloud server, and communicates with a mobile phone client through the cloud server. The cloud server is composed of a control server and a video server. The seal safekeeping box is provided with an unlocking controller, a door magnet and an application button, all of which are connected with a network camera. The network camera is connected with a wireless router. A seal connected by a thin steel wire is placed in the seal safekeeping box. The length of the thin steel wire makes the seal freely move in the shooting range of the network camera. By adopting the seal remote operation system based on the Internet of things and an operation method thereof, a seal owner can receive seal taking information in real time even when the seal owner is not on the scene, the use of seals can be remotely authorized, and the seal using process can be monitored in real time, so as to achieve the purpose of seal safekeeping, taking and using whole-process control.
Owner:赵一泽 +1
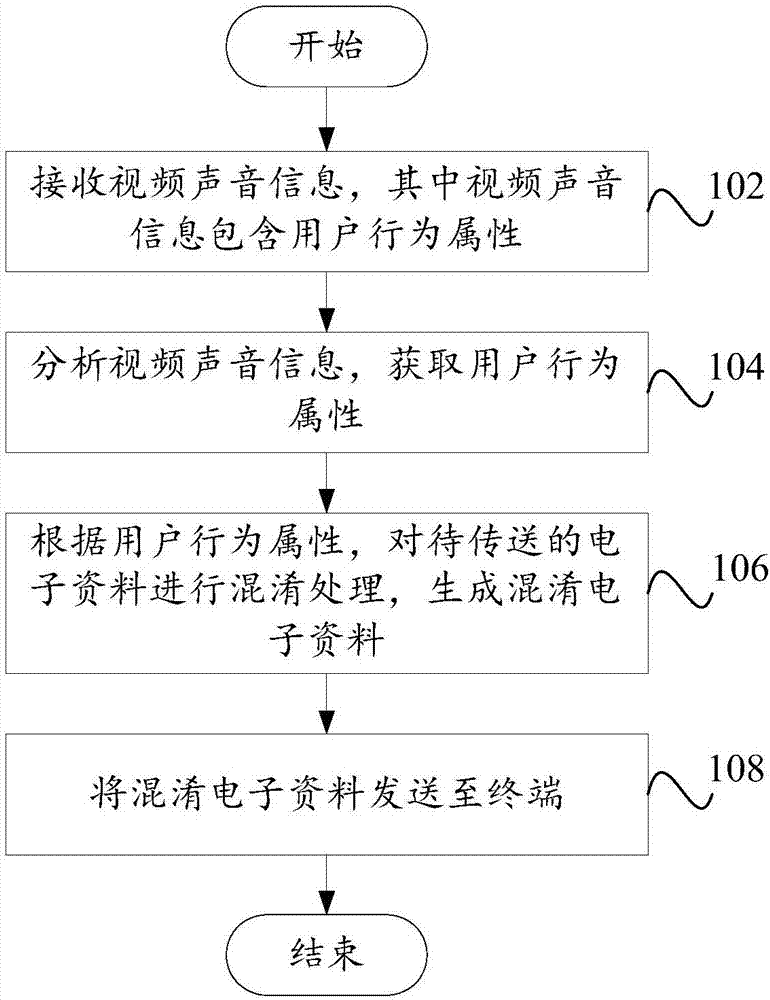
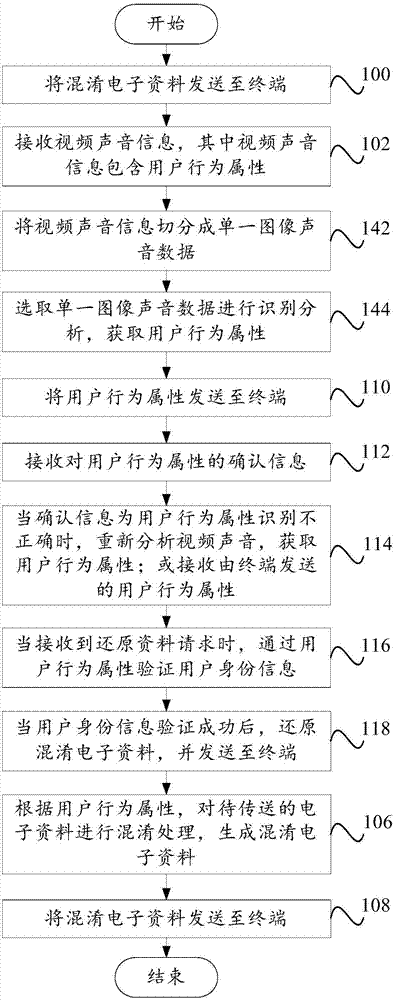
Confusion technology method and apparatus of artificial intelligence
ActiveCN107292133ASolve complexitySolve the shortcomings of low attack resistanceProgram/content distribution protectionState of artBrute force
The invention provides a confusion technology method and apparatus of artificial intelligence. The confusion technology method of the artificial intelligence comprises the steps of receiving video sound information, wherein the video sound information contains a user behavior attribute; analyzing the video sound information to obtain the user behavior attribute; according to the user behavior attribute, performing confusion processing on to-be-transmitted electronic data to generate confused electronic data; and sending the confused electronic data to a terminal. According to the method and the apparatus, the shortcomings of low complexity and poor attack resistance of a confusion technology in the prior art are overcome; massive resources can be prevented from being subjected to brute force cracking; secure storage of electronic confidential data is realized; and the risk of stealing the electronic confidential data is avoided.
Owner:ZICT TECH CO LTD
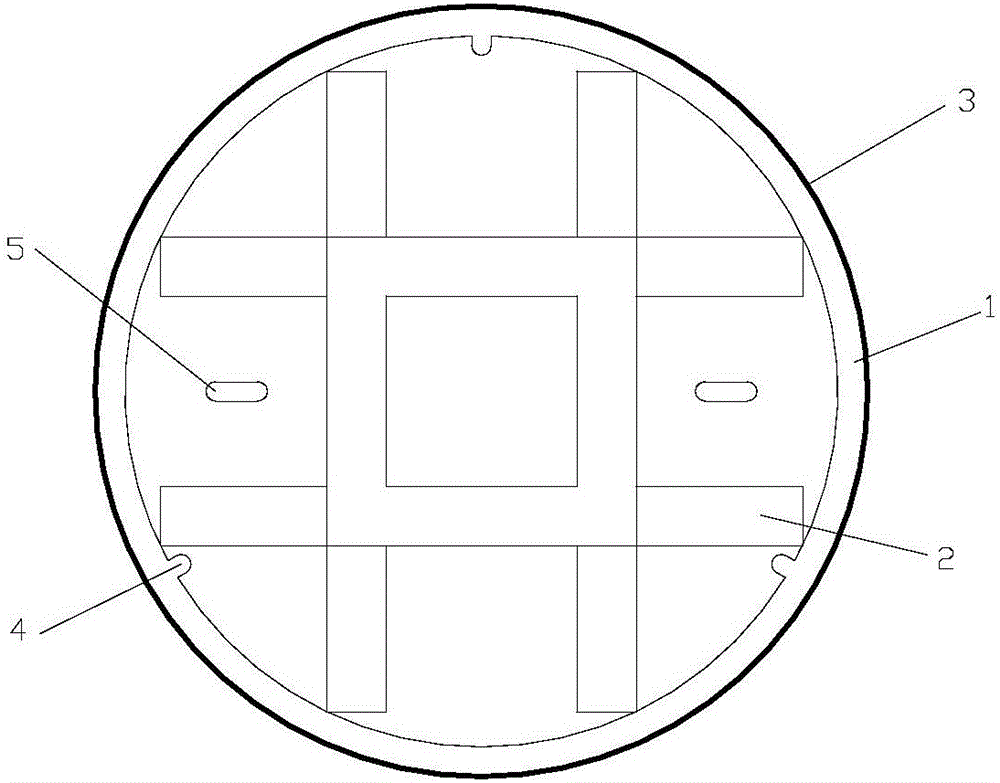
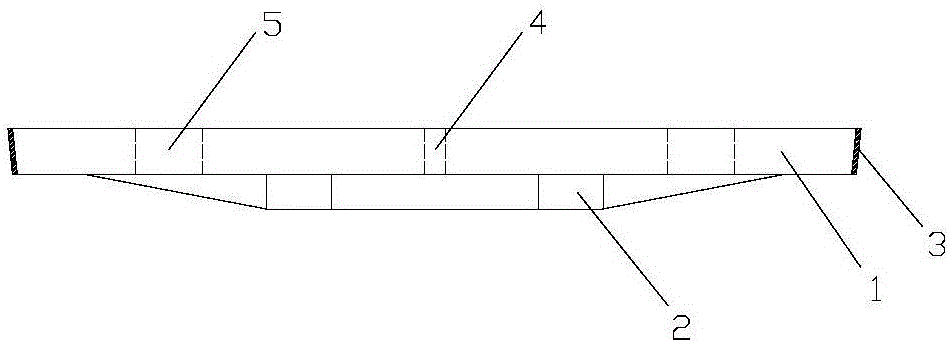
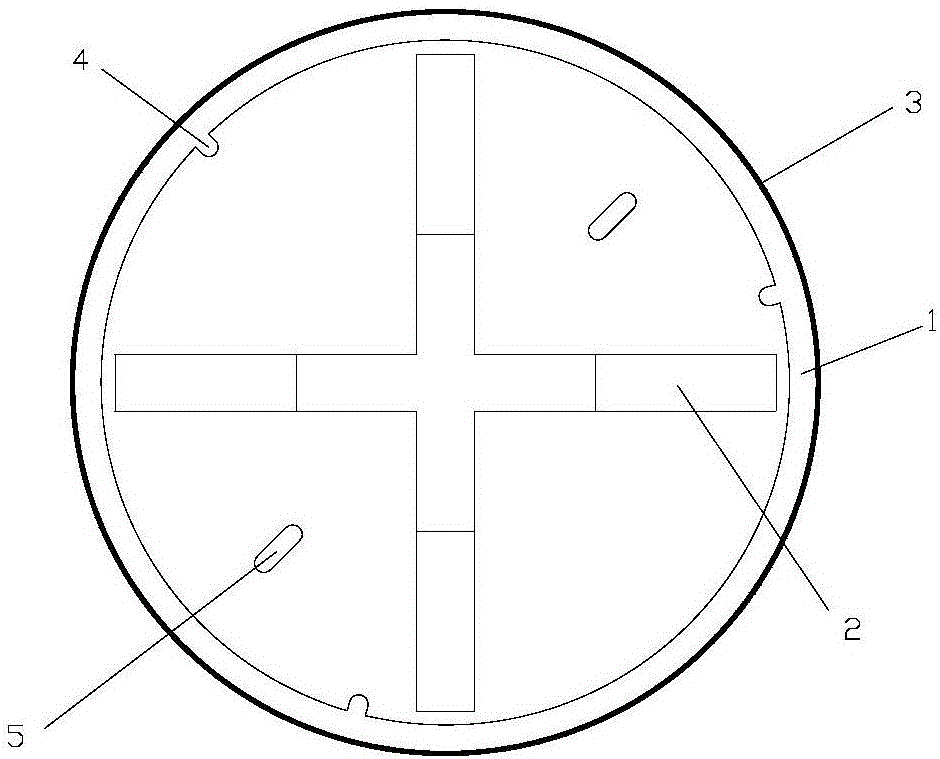
Ultrahigh-performance concrete well lid for municipal and electric power engineering and manufacturing technique of ultrahigh-performance concrete well lid
InactiveCN106759512ASmall structure sizeReduces the possibility of rustArtificial islandsCeramic shaping apparatusStructure of the EarthToughness
The invention relates to an ultrahigh-performance concrete well lid for municipal and electric power engineering and a manufacturing technique of the ultrahigh-performance concrete well lid. The ultrahigh-performance concrete well lid comprises an ultrahigh-performance concrete well lid body and a well lid steel hoop wrapping the periphery of the concrete well lid body. The concrete well lid body is composed of an upper circular truncated cone-shaped well lid structure and a lower ribbed structure and formed by pouring ultrahigh-performance concrete through an integral mold at a time. The circular truncated cone-shaped well lid structure is of a big-end-up structure with the upper surface being a plane. The well lid steel hoop is of a big-end-up circular ring-shaped structure. The vertical height of the well lid steel hoop is identical to the height of the circular truncated cone-shaped well lid structure. According to the ultrahigh-performance concrete well lid and the manufacturing technique thereof, by utilizing the material properties including high strength, high toughness and high durability of the ultrahigh-performance concrete, the structural dimension of the well lid can be effectively decreased, then the dead weight is reduced, the impact resistance of the well lid is improved, the service life of the well lid is prolonged, and noise pollution and using cost in the using process are reduced. The ultrahigh-performance concrete well lid is suitable for municipal engineering construction, the problem of current urban road well lids can be solved, and the functions of protecting the environment and beautifying the environment are achieved.
Owner:湖州瑞坤工程材料有限公司
Solar road lamp assembly
InactiveCN106439721AAvoid the risk of theftIncrease the difficulty of constructionMechanical apparatusLight source combinationsSolar street lightEngineering
The invention relates to a solar road lamp assembly. A control circuit system is connected with a photovoltaic solar panel, a storage battery and a solar lamp through wires, the storage battery is mounted in a lamp shade, the photovoltaic solar panel is arranged at the upper part of the lamp shade and comprises a main photovoltaic panel and auxiliary photovoltaic panels, limiting plates are arranged at the hinge parts of the main photovoltaic panel and the auxiliary photovoltaic panels, the adjacent photovoltaic panels are arranged in an overlapped manner, and the number of the auxiliary photovoltaic panels is more than one. According to the invention, by arranging the storage battery in a lamp post, burglary prevention is realized; the cell panel is arranged into a foldable cell panel, and the photovoltaic solar panel is folded together by utilizing hinging arrangement; by integrating the storage battery, a photovoltaic power generating panel and a light source together, burglary prevention is realized; and the cell panel is arranged into the foldable cell panel, the photovoltaic solar panel can be unfolded to receive sunlight and can also be folded by utilizing the hinging arrangement, and the mounting and transporting difficulty of the photovoltaic solar panel is reduced under the condition of ensuring the energy supply of the solar road lamp.
Owner:李小红
Object storage cabinet
InactiveCN107811435AEasy to useEasy to viewCabinetsApparatus for meter-controlled dispensingPasswordEngineering
The invention discloses an object storage cabinet. The object storage cabinet comprises a cabinet body, the cabinet body is provided with several layers of cabinet shelves, each layer of storage shelfis provided with multiple cabinet grooves, and cabinet boxes are slidably installed in the cabinet grooves. The object storage cabinet is provided with a shooting device and a buzzer alarm, the shooting device and the buzzer alarm are connected with a controller, when a wrong code password is continuously input by a code input device for a set frequency, the shooting device shoots personnel who conduct unlocking to store images to make it convenient for a user to check the detailed situations while the buzzer alarm gives out acute alarm sound to shock personnel who conduct abnormal unlockingabnormal and prompt other personnel, thus the storage cabinet is safer to use, it is avoided that a traditional object storage cabinet has the risk of being stolen due to the absence of a protection and alarming device, and the object storage cabinet has high using safety.
Owner:鹤山市富泰康金属制品有限公司
Charging system
ActiveCN105515131AImprove transmission efficiencyWon't wear outBatteries circuit arrangementsElectric powerElectrical batteryEngineering
A charging system comprises batteries and a charging device. The charging device comprises a box, a conveying rail and a grabbing device are arranged in the box, a battery inlet and a battery outlet are formed in the box, and matched magnetic inductors are arranged on the rail and the batteries, and comprise iron cores and coils wound on the iron cores. In the use process, the battery is placed on the rail and conveyed into the box through the rail to be charged, the coils are powered on, the iron cores are magnetic and attracted together through magnetism, and the grabbing device is responsible for grabbing the fully charged batteries on the conveying rail to the battery outlet.
Owner:宁波市新达量具有限公司
Method for obtaining application data, authentication certificate server and gateway
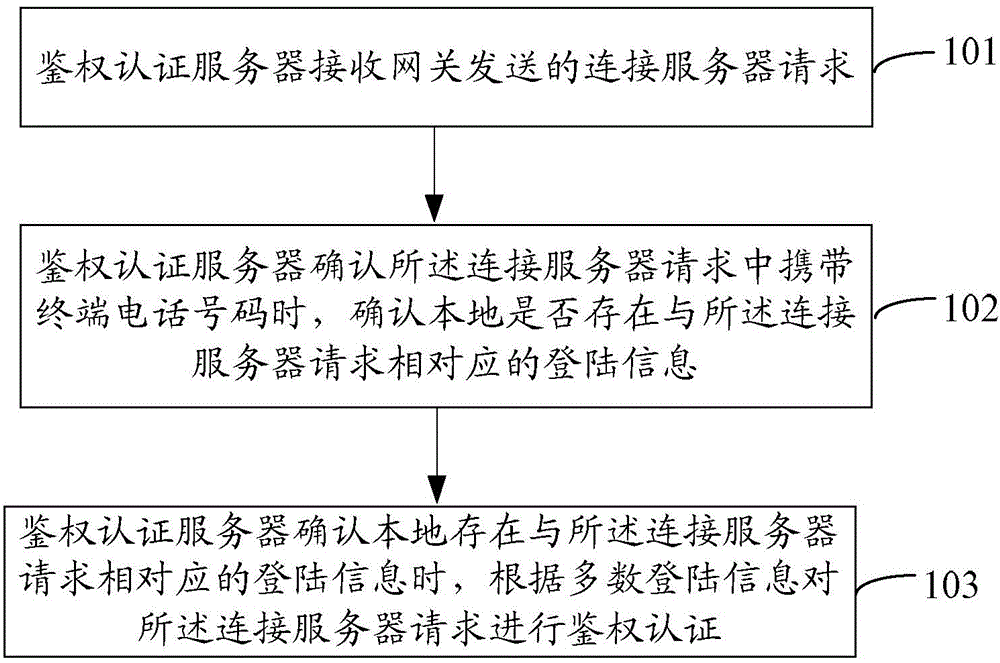
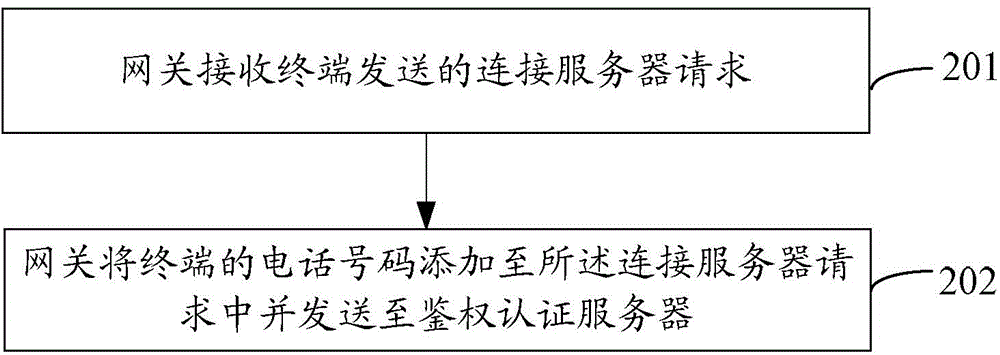
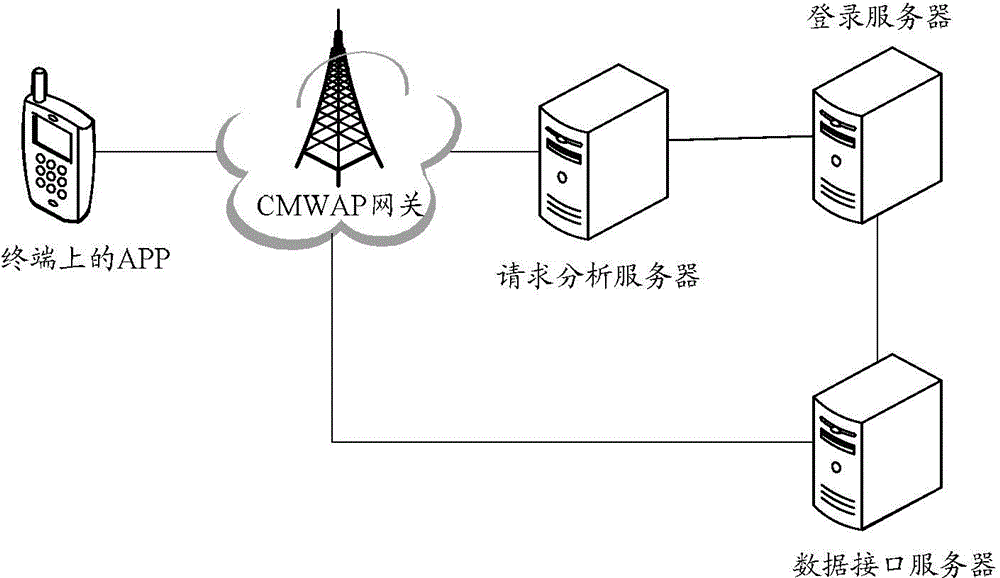
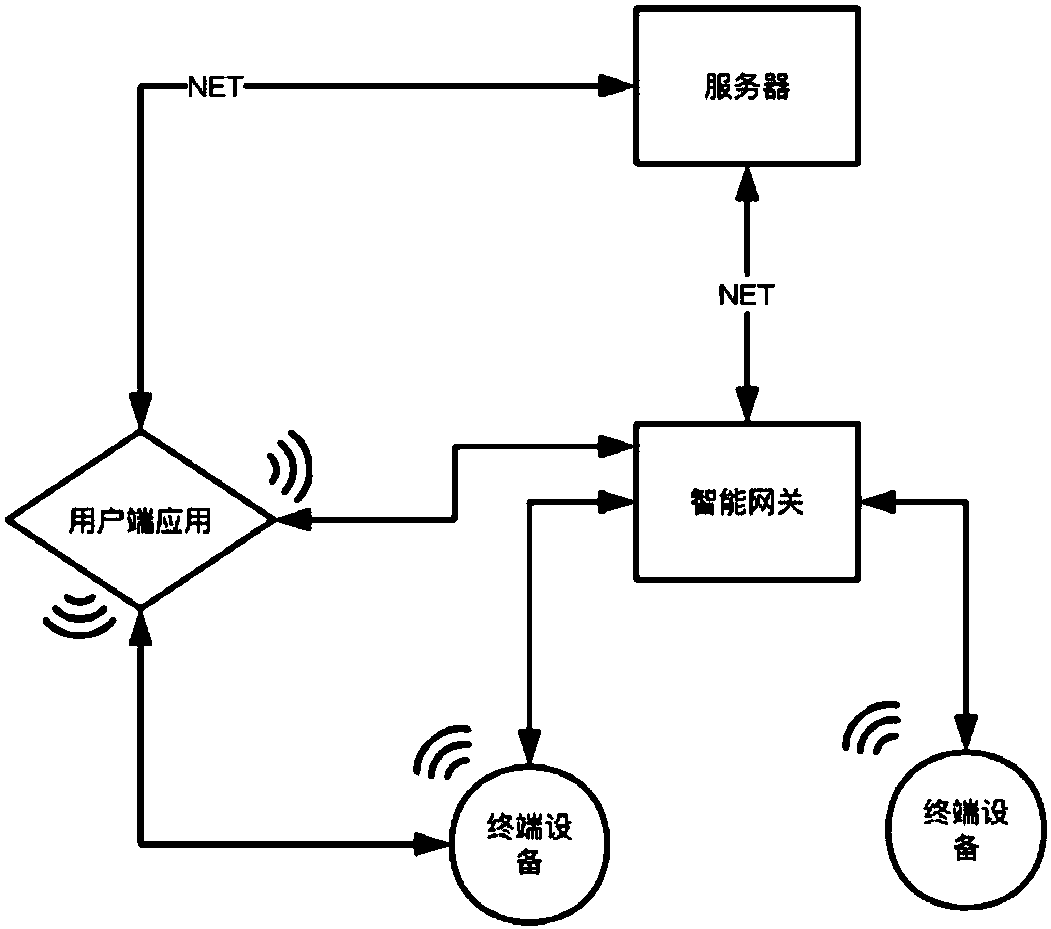
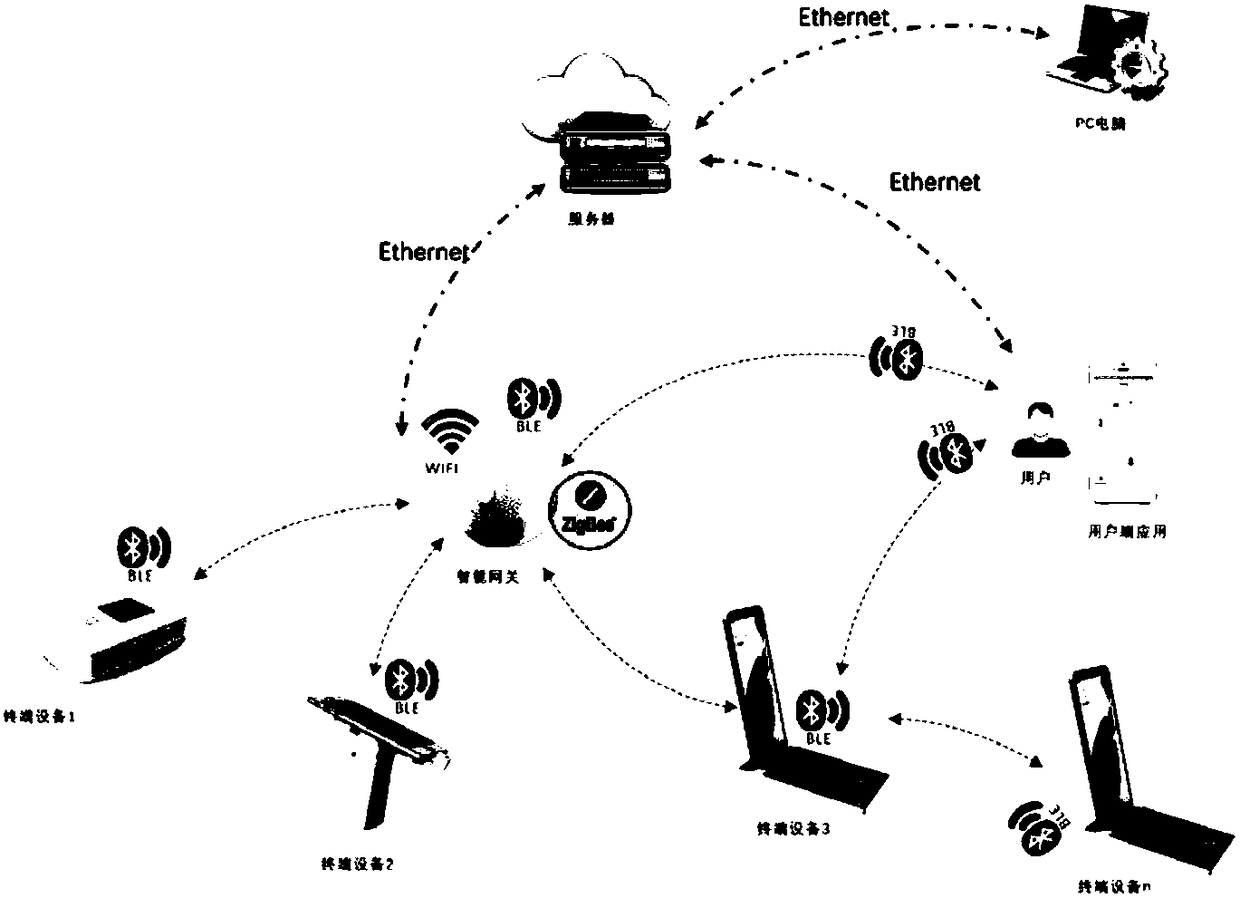
ActiveCN105635060AAvoid the risk of theftSimple processTransmissionComputer terminalAuthentication server
The invention discloses a method for obtaining the application data, and the method comprises the steps that a terminal APP transmits a server connection request to an authentication certificate server through a gateway; the gateway obtains a telephone number of the terminal when an application service requested by the server connection request is in a gateway whitelist, the obtained telephone number is added to the server connection request and a new server connection request is generated, and then the new server connection request is transmitted to the authentication certificate server; the authentication certificate server confirms that the server connection request carries the telephone number of the terminal, and then confirms that there is log-in information corresponding to the server connection request locally; the authentication of the server connection request is carried out according to the log-in information; when the authentication is passed, a request for obtaining the data requested by the server connection request is sent to a data interface server; and the data interface server returns the request data to the APP. The invention also discloses an authentication certificate server and the gateway.
Owner:CHINA MOBILE GROUP SICHUAN
Smart retail secure system
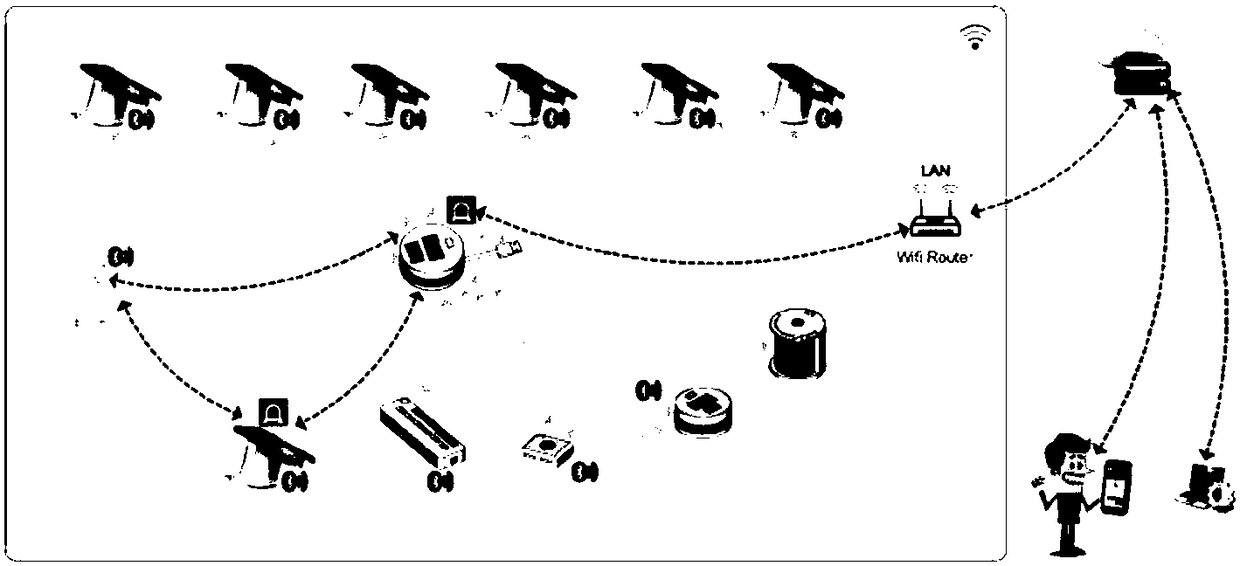
InactiveCN108449397AAvoid the risk of theftImprove sales performanceBuying/selling/leasing transactionsTransmissionComputer hardwareStatistical analysis
The invention discloses a smart retail secure system, comprising terminal devices, a smart gateway and a server. Each terminal device comprises a wireless communication module and a signal receiving module. The smart gateway is a medium for information interaction between the terminal devices or between the terminal devices and the server. The server comprises a database and a device authentication module. The database stores user information of the terminal devices. The device authentication module set encryption packets for the terminal devices. Real-time monitoring can be carried out on a plurality of products. Valuable operations such as risk prewarning, remote anomaly pushing and data statistic analysis can be carried out. In particular, for cable assemblies, cable lifetime prewarningcan be carried out through resistance value feedback. The risk that commodities are stolen due to damage of a device is effectively prevented. On the basis of a network, according to the system, a client is helped to carry out remote prewarning and remote device monitoring. A user can fully grasp the condition in a shop on the premise of not patrolling the shop. The working efficiency is improved.
Owner:HANGZHOU LANGHONG TECH
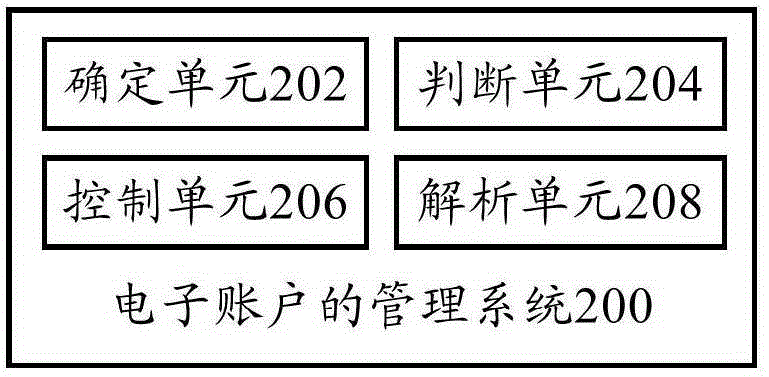
Method and system for managing electronic accounts and terminal
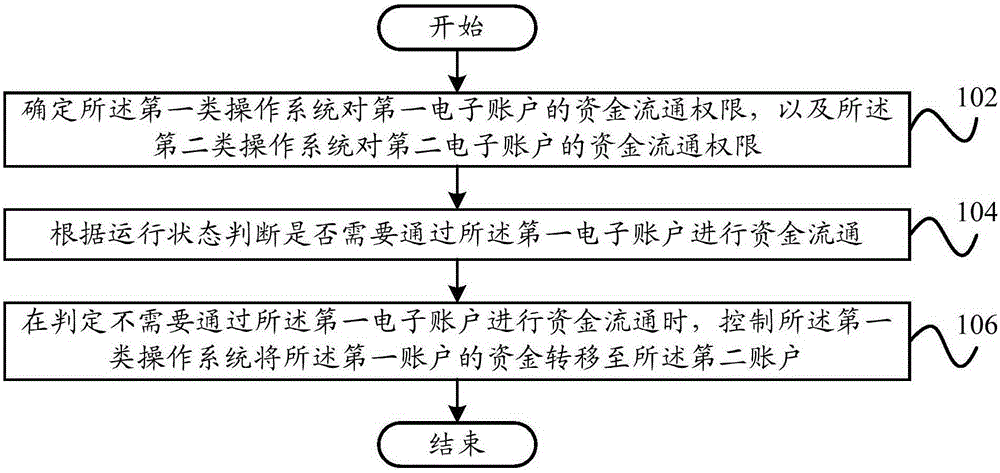
ActiveCN105205668AAvoid the risk of theftEnsure safetyProtocol authorisationOperational systemComputer terminal
The invention provides a method and system for managing electronic accounts and a terminal. The method for managing the electronic accounts includes the steps that the transaction authority of a first-class operating system for the first electronic account and the transaction authority of a second-class operating system for the second electronic account are determined; whether fund circulation needs to be conducted through the first electronic account or not is judged according to the operating state; when it is judged that fund circulation does not need to be conducted through the first electronic account, the first-class operating system is controlled to transfer funds of the second electronic account to the first electronic account. By the adoption of the technical scheme, the transaction authorities can be judged and controlled according to the double systems and the operating state, the risk that the funds are stolen is avoided, the safety of the funds is guaranteed, and the user experience is improved.
Owner:YULONG COMPUTER TELECOMM SCI (SHENZHEN) CO LTD
Intelligent antitheft shared parking lot for non-motor vehicles
PendingCN110782537AEasy to operateAvoid the risk of theftTicket-issuing apparatusCash registersEmbedded systemAutomotive engineering
The present invention relates to the field of parking lot technologies, and discloses an intelligent antitheft shared parking lot for non-motor vehicles. The parking lot comprises a fence. An exit isdisposed on one side of the fence, and a code scanning barrier gate is disposed at the exit. A side wall of the code scanning barrier gate is fixedly connected to an AI face recognition machine. Supporting bars are fixedly connected to four corners on the top of the fence. An upper surface of the supporting bar is fixedly connected to an infrared monitor. Multiple stand columns are disposed insidethe fence, and top parts of the multiple stand columns are jointly movably connected to a parking shed. Multiple groups of fixed blocks corresponding to the stand columns are fixedly connected to thebottom of the parking shed, and each group comprises two fixed blocks. According to the intelligent antitheft shared parking lot for non-motor vehicles, scanning can be performed simply and fast, toopen or close a gate immediately. Charges are clear and detailed. Payment at different times and monthly payment are available. Voice prompt makes parking standardized and orderly, so that city appearance is improved. Monitoring and shooting are performed in a whole process, vehicle losses are prevented, evidences are provided for larceny cases, cases are solved as quickly as possible, and the parking shed can be conveniently disassembled or assembled.
Owner:安徽金卫士科技发展有限公司
Cloud intelligent Internet of Things based irrigation terminal
PendingCN109997664AEasy to uploadGood senseWatering devicesCultivating equipmentsComputer moduleComputer terminal
The invention belongs to the technical field of irrigation equipment and particularly discloses a Cloud intelligent Internet of Things based irrigation terminal which comprises a box. The box comprises a box cover and a shell, the box cover and the box are fixed together through four drawing type mounting lugs, and a mainboard is fixedly connected to the inner front face of the shell through screws and provided with a GPRS module and comprises a central processing unit, a database, a signal transceiving module, a control module and a touch module. The bottom of the box is provided with a flowmeter interface, a USB interface and a pressure sensor interface. By arrangement of the USB interface, convenience in system upgrading of a controller is achieved, and lawbreakers are prevented from cracking, so that high safety is realized; by arrangement of the GPRS module, data can be uploaded to the cloud conveniently, so that operating personnel can control the controller remotely; by arrangement of the sensor, information of a charge card can be conveniently sensed by the controller without insertion of the card into the controller, so that the risk of card theft is avoided, and convenience and practicality are realized.
Owner:河南瑞通水利工程建设集团有限公司
Login method based on confidential order of trusted equipment
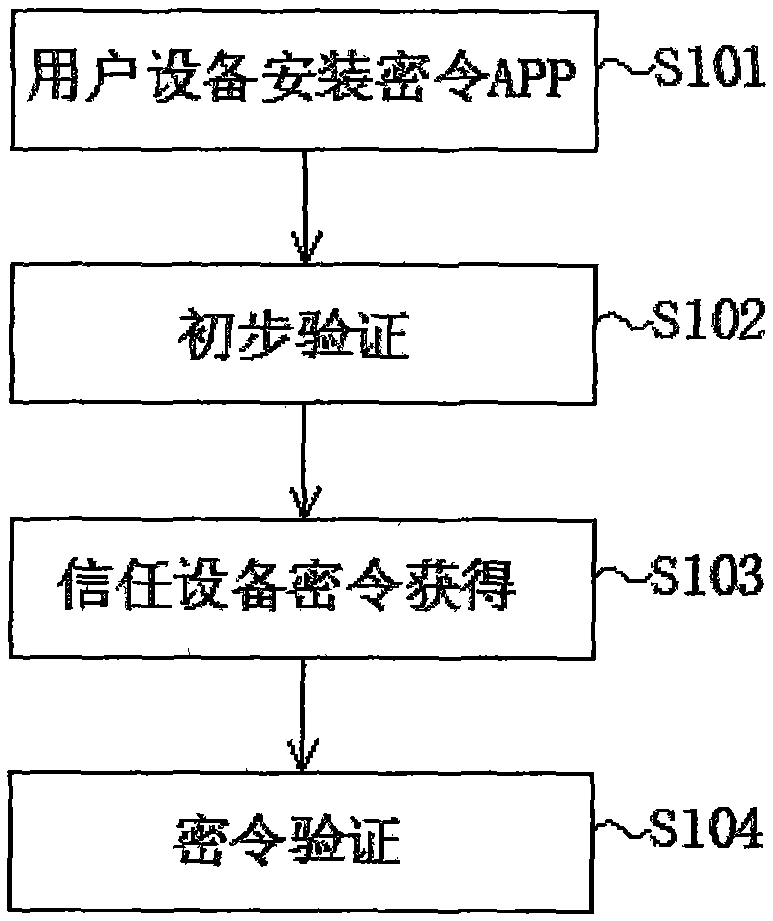
InactiveCN105471891AEnsure information securityAvoid the risk of theftTransmissionInternet privacyPassword
The invention relates to the technical field of system login, and particularly relates to a login method based on a confidential order of trusted equipment. The login method comprises the following steps: a step S101: user equipment installs a confidential order APP and binds the equipment under the account per se to make the equipment become trusted equipment after logging in the APP, so as to obtain a corresponding login confidential order; a step S102: primary verification: in a login process, a user completes primary verification when inputting a username and a password; a step S103: acquisition of the confidential order of the trusted equipment: after completing the primary verification, the system will send a unique confidential order to the APP of the trusted equipment, and meanwhile, the system will remind the user to input the confidential order displayed on the APP; and a step S104: confidential order verification: after the user opens the APP and inputs the corresponding confidential order, the system verifies the confidential order. By adopting the method, the information security of the user is further guaranteed by the confidential order provided by the APP, and meanwhile, the login state of the user can be reminded by the APP in real time, in order to avoid the stolen risk of the account.
Owner:HUNAN ANTVISION SOFTWARE
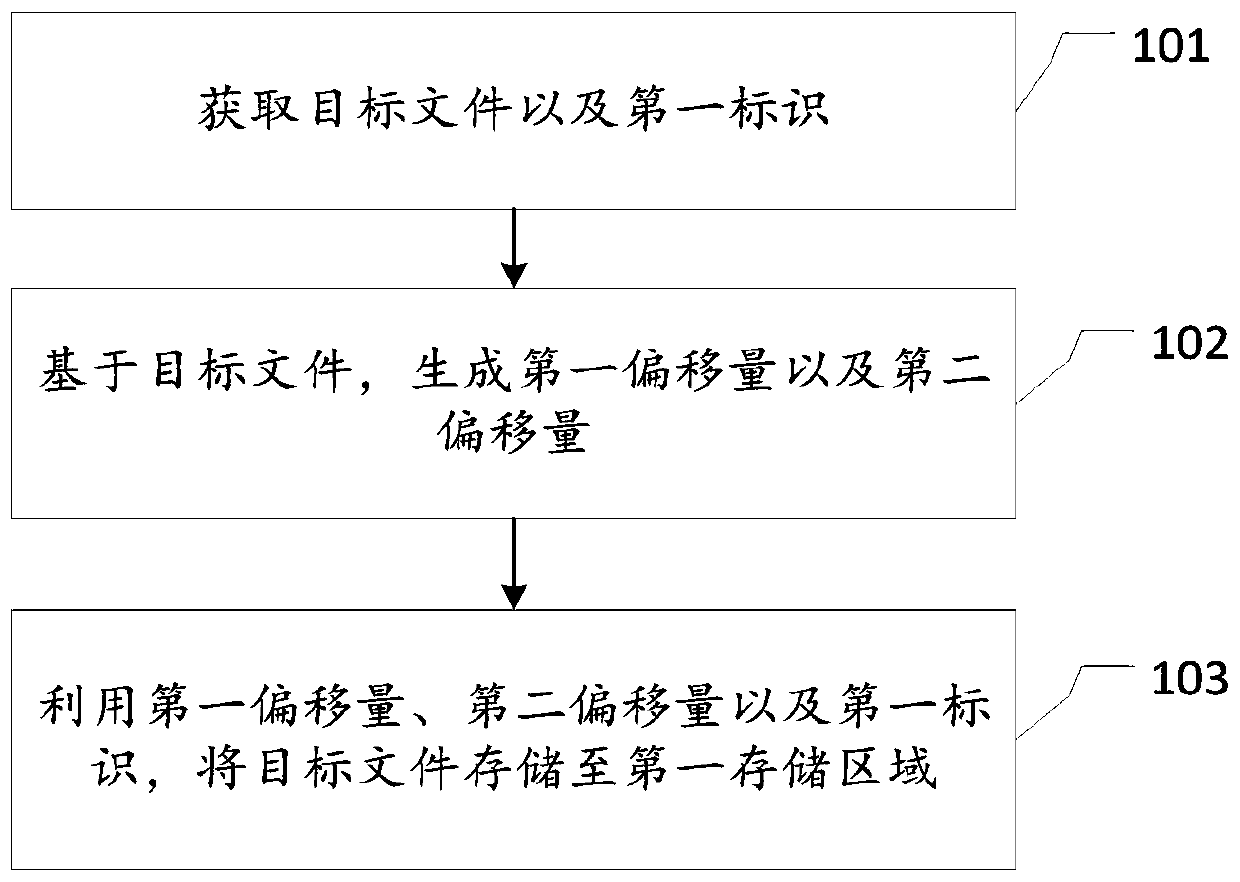
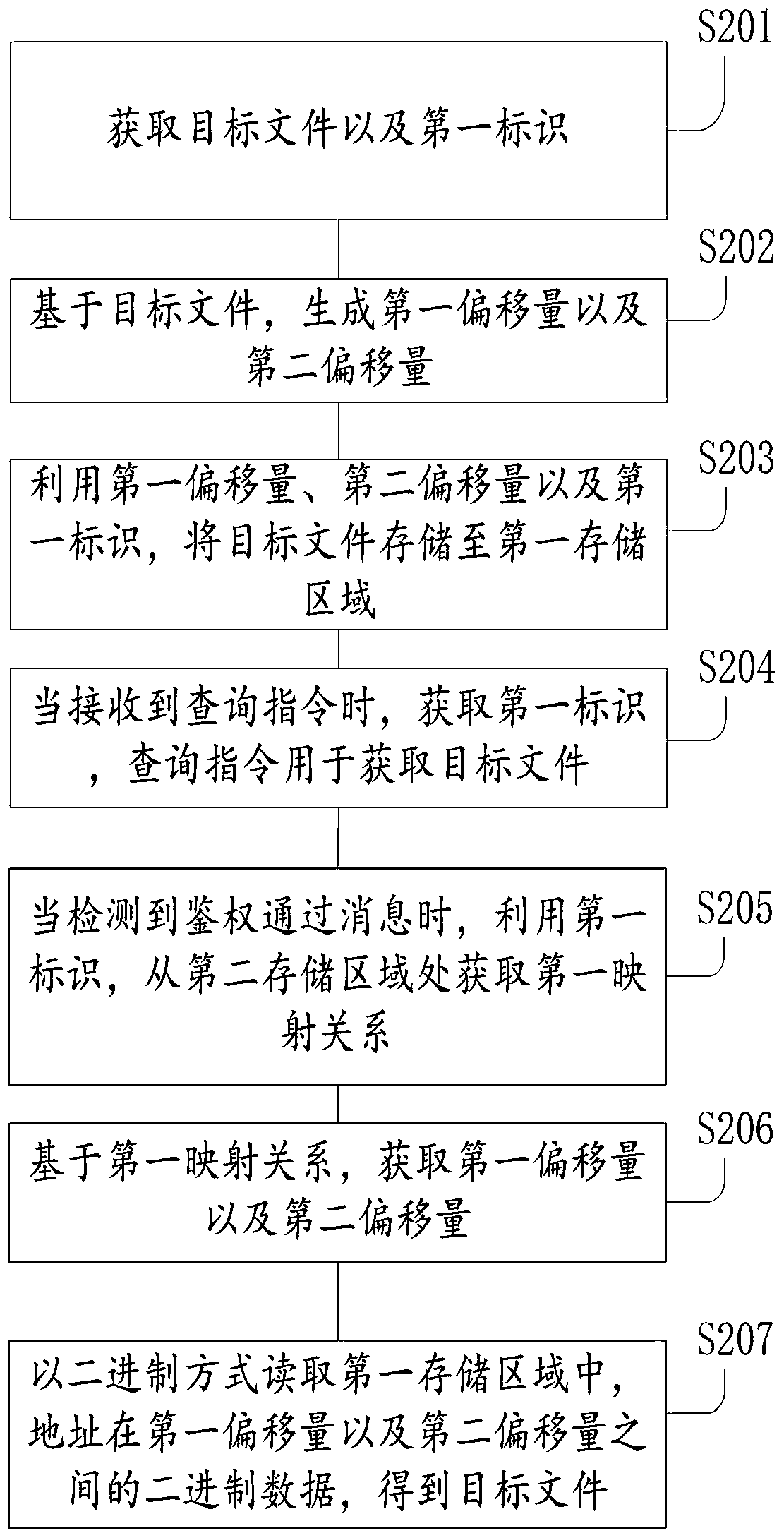
File storage method and device, electronic equipment and medium
PendingCN110968549AAvoid the risk of being easily stolen by malicious usersAvoid the risk of theftFile system administrationSpecial data processing applicationsEngineeringObject file
The invention discloses a file storage method and device, electronic equipment and a medium. After a target file and a first identifier corresponding to the target file are obtained, a first offset and a second offset generated based on the first offset and the data size of the target file can be generated based on the target file, and then the target file is stored in a first storage area by utilizing the first offset, the second offset and the first identifier. According to the technical scheme, after the target file is obtained, the corresponding first offset and second offset are generatedaccording to the data size of the target file, and the shifted target file is stored after shifting operation is conducted on the target file through the two offsets. Therefore, the risk that the target file is easily stolen by malicious users due to the fact that the target file is directly stored in related technologies can be avoided.
Owner:OPPO CHONGQING INTELLIGENT TECH CO LTD
Game login method and device and electronic equipment
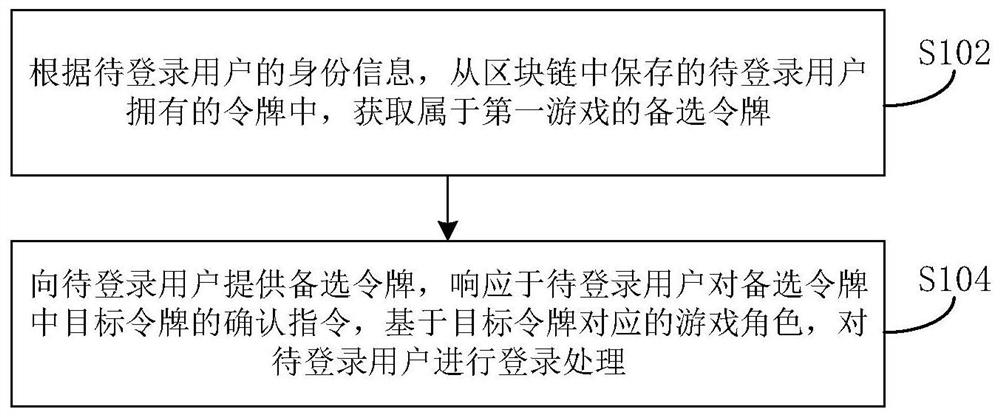
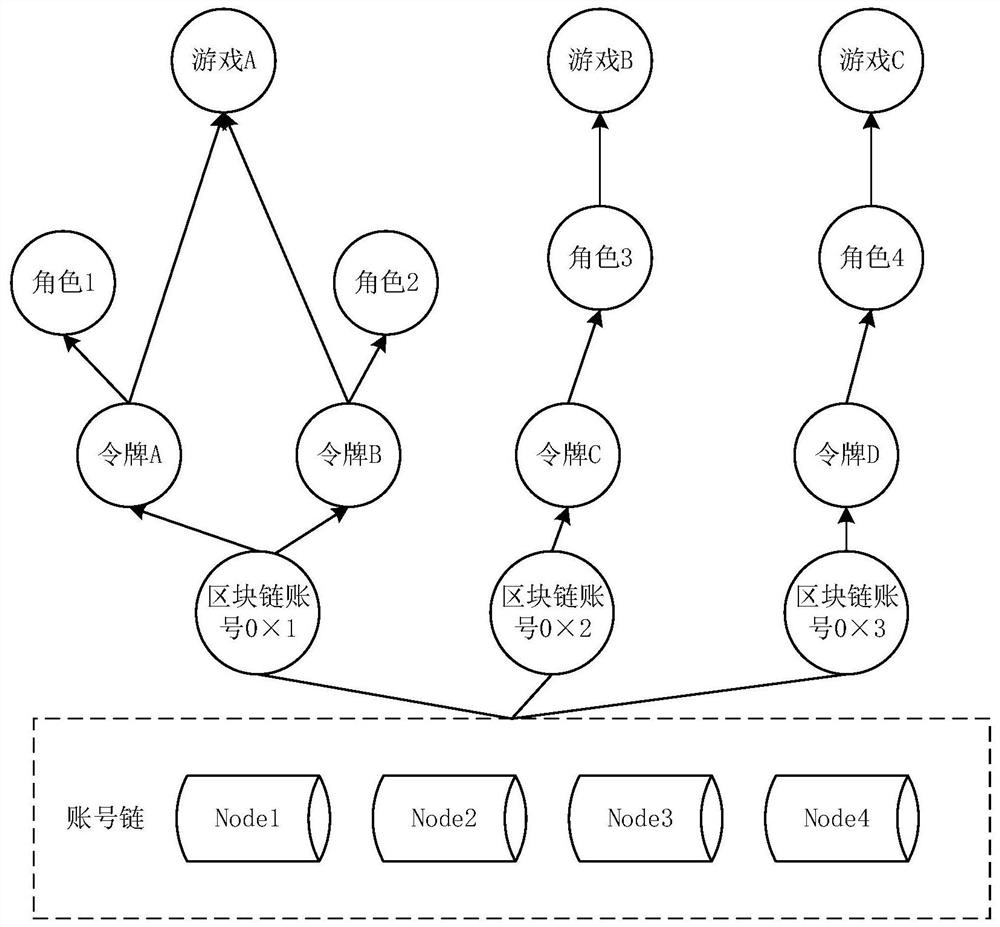
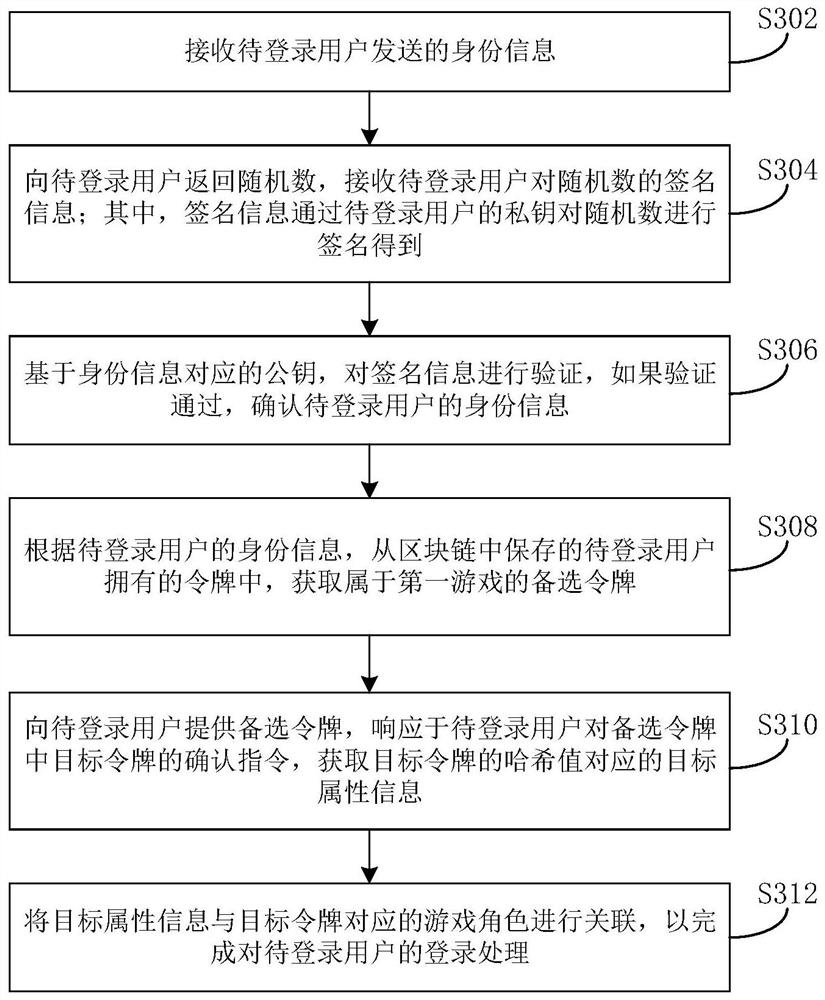
PendingCN112354190AImprove reliabilityImprove securityVideo gamesThird partyHuman–computer interaction
The invention provides a game login method and device and electronic equipment, and the method comprises the steps of enabling a game server to obtain alternative tokens belonging to a first game fromtokens owned by a to-be-logged-in user and stored in a blockchain according to the identity information of the to-be-logged-in user; and providing the alternative token for the to-be-logged-in user,and performing login processing on the to-be-logged-in user based on the game role corresponding to the target token in response to a confirmation instruction of the to-be-logged-in user for the target token in the alternative token. According to the method, tokens of all game roles owned by a game user are stored through a block chain, and when the game is logged in, a game server obtains all tokens corresponding to the game from the block chain and logs in the game through a target token selected by the user; the game login mode does not depend on third-party service, the risk that the account is lost or stolen is avoided, and the reliability and safety of game login are improved.
Owner:NETEASE (HANGZHOU) NETWORK CO LTD
Drive motor for vehicle
ActiveCN109217534ACompact structureImprove reliabilityGearing controlMechanical energy handlingDrive motorEngineering
The invention discloses a driving motor of a vehicle. The driving motor of the vehicle comprises a housing, a rotor, a locking wheel and a parking pawl mechanism. The rotor is arranged in the housing.The locking wheel is positioned in the housing and fixedly arranged on the rotor, and the outer peripheral surface of the locking wheel is provided with a plurality of locking grooves spaced apart along the circumferential direction of the locking wheel; The parking pawl mechanism is located within the housing, and is configured to be selectively insertable into or disengaged from the locking groove to lock or unlock the rotor. The parking pawl mechanism is configured to be selectively insertable into or disengaged from the locking groove to lock or unlock the rotor. As that house, the rotor,the locking wheel and the par pawl mechanism cooperate, the structure of the drive motor can be made more compact, the reliability of the drive motor can be improved, and the theft risk caused by theexternal wiring can be effectively avoided.
Owner:BEIJING ELECTRIC VEHICLE
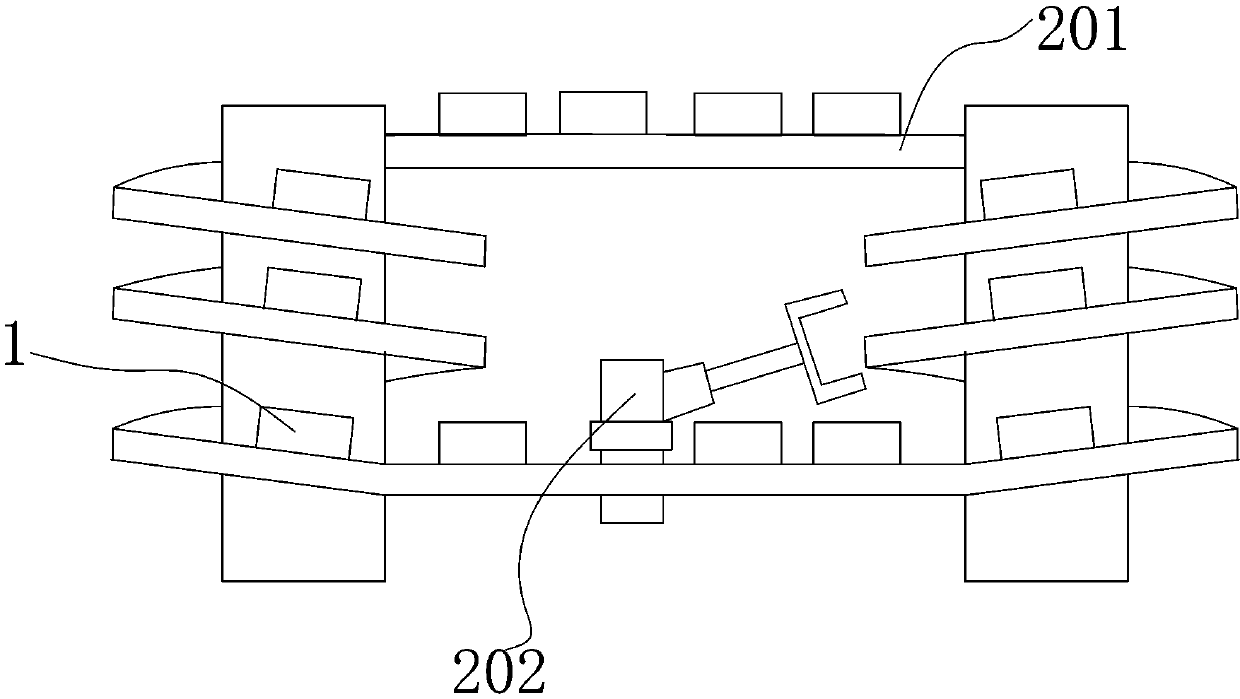
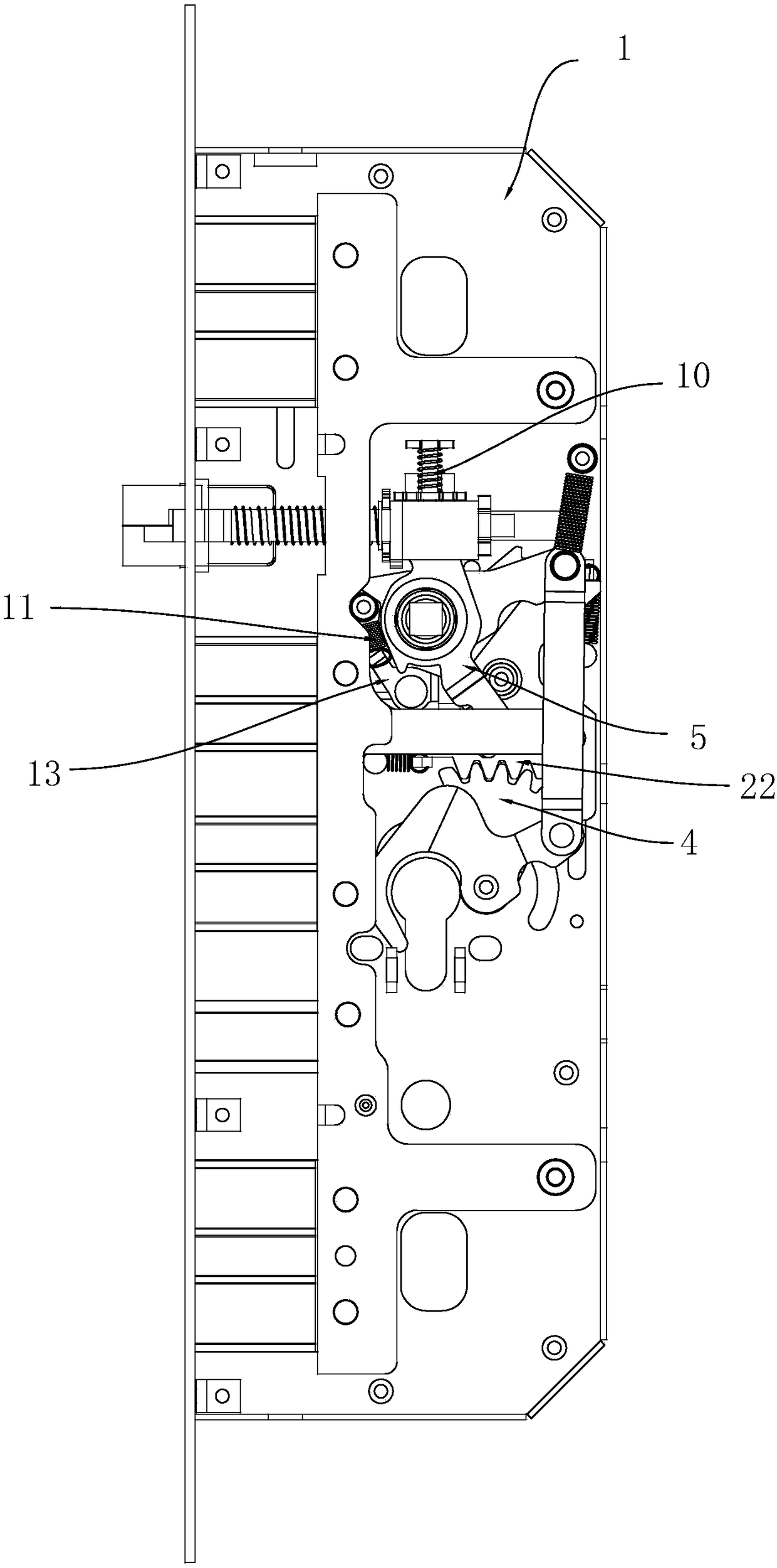
Automatic anti-theft lock
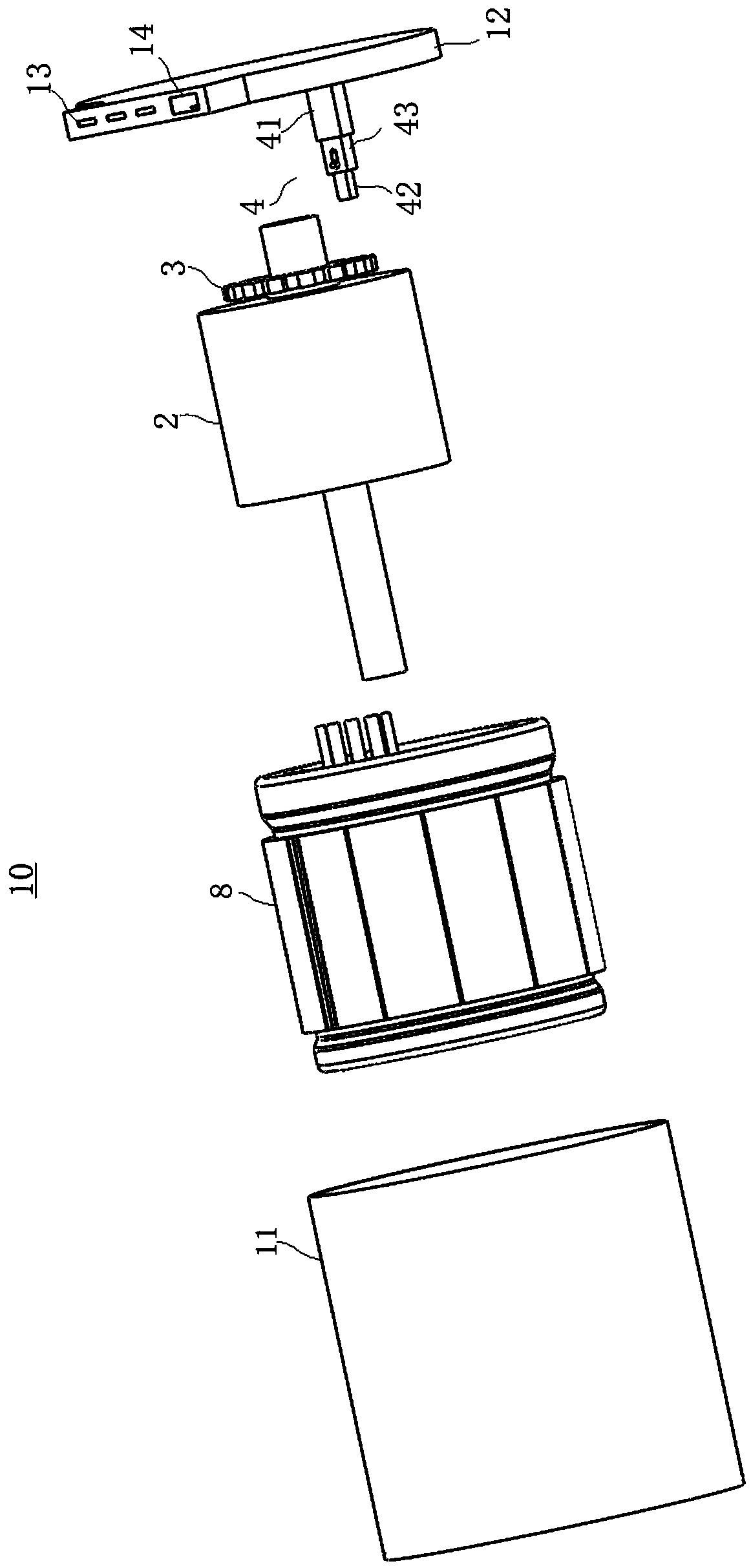
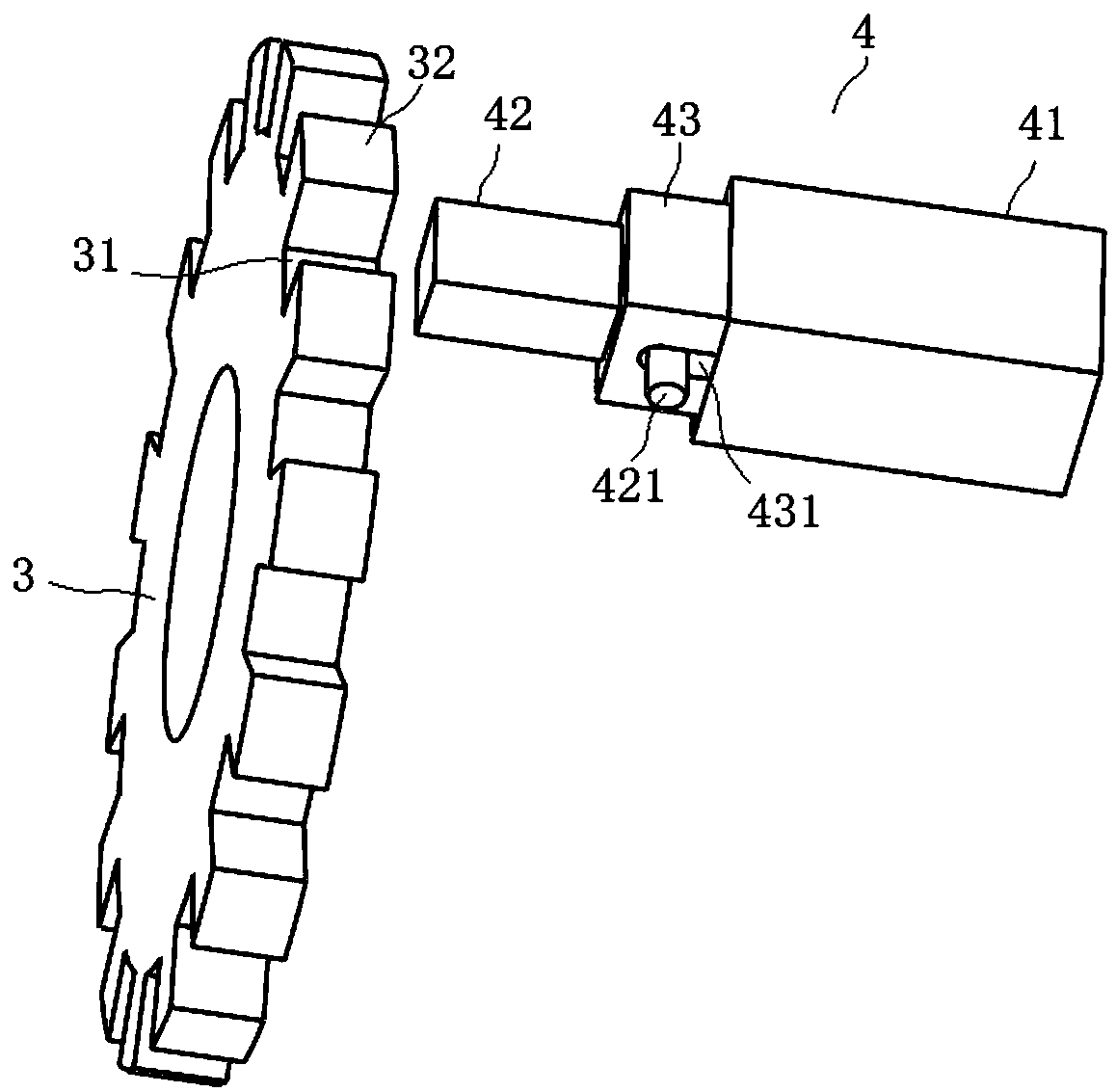
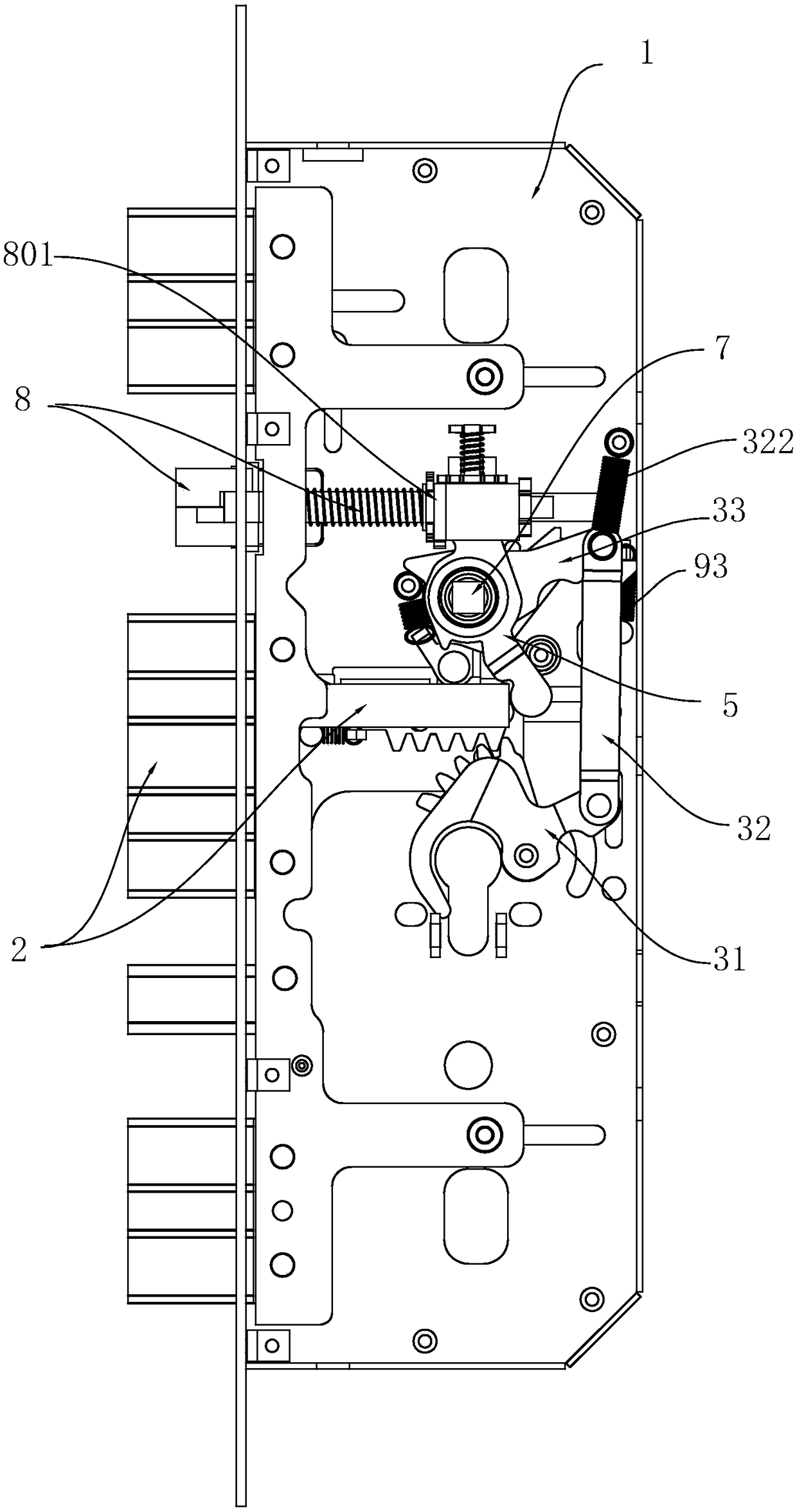
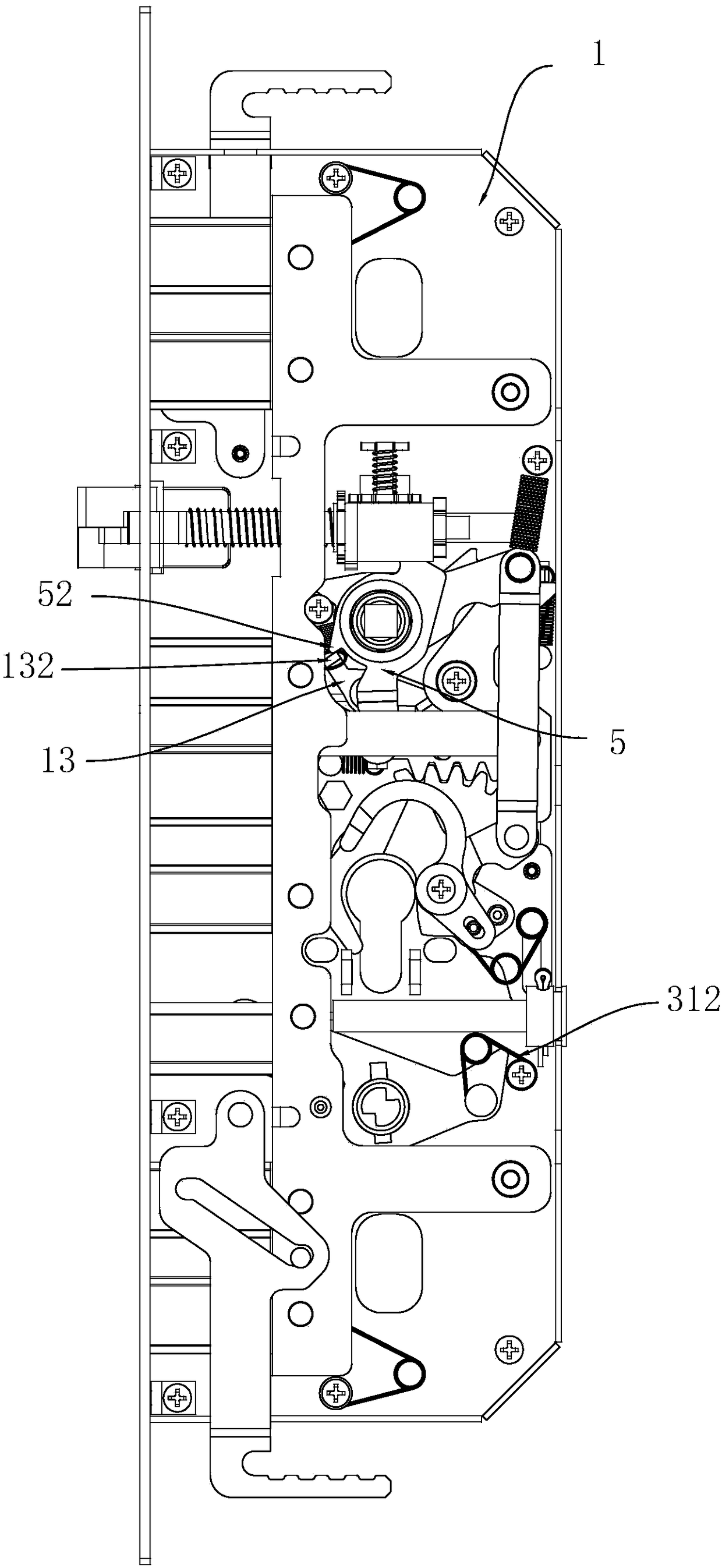
The invention relates to an automatic anti-theft lock and solves the problem of strenuous unlocking in the prior art. According to the technical scheme, a force accumulation component is arranged in amain locking dog assembly, a locking mechanism is in linked cooperation with the force accumulation component, the force accumulation component is enabled to accumulate force, and the force accumulation component drives the main locking dog assembly to be locked under the action of accumulated force; an opening mechanism drives the main locking dog assembly to be retracted inwards so as to realize unlocking, the main locking dog assembly is retracted inwards to be in place and forms braking with a braking component on the opening mechanism, and during braking, the opening mechanism drives a latch bolt of a latch bolt assembly to extend out of a lock box. The automatic anti-theft lock has effects as follows: the locking mechanism drives the force accumulation component on the main lockingdog assembly to accumulate force, the main locking dog assembly and a heaven-earth rod assembly are popped out under the action of the accumulated force on the force accumulation component, and afterthe assemblies are popped out in place, the accumulated force on the force accumulation component disappears; when the lock is opened by the opening mechanism, the accumulated force on the force accumulation component is not required to be resistant, the force accumulation component is not required to accumulate force, and the purpose of labor-saving locking is achieved.
Owner:程新民
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com